Scan Time Start time : Fri May 14 19:16: End time : Fri May 14 19:18:
|
|
|
- Alannah Porter
- 5 years ago
- Views:
Transcription
1 1 / 37 List of hosts Scan Time Start time : Fri May 14 19:16: End time : Fri May 14 19:18: Medium Severity problem(s) found [^] Back Number of vulnerabilities Open ports : 11 High : 0 Medium : 8 Low : 36 Remote host information Operating System : NetBIOS name : DNS name : Linux Kernel 2.6 on CentOS 4 [^] Back to Port general (0/icmp) [-/+] Traceroute Information It was possible to obtain traceroute information. Makes a traceroute to the remote host. For your information, here is the traceroute from to : ID: Nessus Scan Information
2 2 / 37 Information about this scan : Nessus version : feed version : Type of plugin feed : ProfessionalFeed (Direct) Scanner IP : Port scanner(s) : nessus_tcp_scanner Port range : default Thorough tests : no Experimental tests : no Paranoia level : 1 Report Verbosity : 1 Safe checks : yes Optimize the test : yes CGI scanning : disabled Web application tests : disabled Max hosts : 80 Max checks : 5 Recv timeout : 5 Backports : Detected Scan Start Date : 2010/5/14 19:16 Scan duration : 98 sec ID: Web Application Tests Disabled
3 3 / 37 Web application tests were not enabled during the scan. One or several web servers were detected by Nessus, but neither the CGI tests nor the Web Application Tests were enabled. If you want to get a more complete report, you should enable one of these features, or both. Please note that the scan might take significantly longer with these tests, which is why they are disabled by default. To enable specific CGI tests, go to the 'Advanced' tab, select 'Global variable settings' and set 'Enable CGI scanning'. To generic enable web application tests, go to the 'Advanced' tab, select 'Web Application Tests Settings' and set 'Enable web applications tests'. You may configure other options, for example HTTP credentials in 'Login configurations', or form-based authentication in 'HTTP login page'. ID: Common Platform Enumeration (CPE)
4 4 / 37 It is possible to enumerate CPE names that matched on the remote system. By using information obtained from a Nessus scan, this plugin reports CPE (Common Platform Enumeration) matches for various hardware and software products found on a host. Note that if an official CPE is not available for the product, this plugin computes the best possible CPE based on the information available from the scan. The remote operating system matched the following CPE : cpe:/o:centos:centos:4 -> CentOS-4 Here is the list of application CPE IDs that matched on the remote system : cpe:/a:apache:http_server: > Apache Software Foundation Apache HTTP Server cpe:/a:apache:http_server: > Apache Software Foundation Apache HTTP Server ID: OS Identification Remote operating system : Linux Kernel 2.6 on CentOS 4 Confidence Level : 95 Method : HTTP The remote host is running Linux Kernel 2.6 on CentOS 4 ID: Apache Banner Linux Distribution Disclosure
5 5 / 37 The name of the Linux distribution running on the remote host was found in the banner of the web server. This script extracts the banner of the Apache web server and attempts to determine which Linux distribution the remote host is running. Risk factor: If you do not wish to display this information, edit httpd.conf and set the directive 'ServerTokens Prod' and restart Apache. The linux distribution detected was : - CentOS 4 ID: Ethernet card brand
6 6 / 37 The manufacturer can be deduced from the Ethernet OUI. Each ethernet MAC address starts with a 24-bit 'Organizationally Unique Identifier'. These OUI are registered by IEEE. The following card manufacturers were identified : 00:13:72:xx:xx:xx : Dell Inc. ID: TCP/IP Timestamps Supported The remote service implements TCP timestamps. The remote host implements TCP timestamps, as defined by RFC1323. A side effect of this feature is that the uptime of the remote host can sometimes be computed. ID: ICMP Timestamp Request Remote Date Disclosure
7 7 / 37 It is possible to determine the exact time set on the remote host. The remote host answers to an ICMP timestamp request. This allows an attacker to know the date which is set on your machine. This may help him to defeat all your time based authentication protocols. Filter out the ICMP timestamp requests (13), and the outgoing ICMP timestamp replies (14). The difference between the local and remote clocks is -622 seconds. ID: CVE: CVE Other references: OSVDB:94 Port rpc-portmapper (111/tcp) [-/+] RPC Services Enumeration
8 8 / 37 An ONC RPC service is running on the remote host. By sending a DUMP request to the portmapper, it was possible to enumerate the ONC RPC services running on the remote port. Using this information, it is possible to connect and bind to each service by sending an RPC request to the remote port. The following RPC services are available on UDP port 111 : - program: (portmapper), version: 2 ID: RPC portmapper Service Detection An ONC RPC portmapper is running on the remote host. The RPC portmapper is running on this port. The portmapper allows someone to get the port number of each RPC service running on the remote host by sending either multiple lookup requests or a DUMP request. ID: RPC Services Enumeration
9 9 / 37 An ONC RPC service is running on the remote host. By sending a DUMP request to the portmapper, it was possible to enumerate the ONC RPC services running on the remote port. Using this information, it is possible to connect and bind to each service by sending an RPC request to the remote port. The following RPC services are available on TCP port 111 : - program: (portmapper), version: 2 ID: Port ssh (22/tcp) [-/+] SSH Protocol Version 1 Session Key Retrieval
10 10 / 37 The remote service offers an insecure cryptographic protocol. The remote SSH daemon supports connections made using the version 1.33 and/or 1.5 of the SSH protocol. These protocols are not completely cryptographically safe so they should not be used. Medium CVSS Base Score:4.0 CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N Disable compatibility with version 1 of the protocol. ID: CVE: CVE BID: 2344 Other references: OSVDB:2116 Backported Security Patch Detection (SSH)
11 11 / 37 Security patches are backported. Security patches may have been 'back ported' to the remote SSH server without changing its version number. Banner-based checks have been disabled to avoid false positives. Note that this test is informational only and does not denote any security problem. N/A Give Nessus credentials to perform local checks. ID: SSH Protocol Versions Supported
12 12 / 37 A SSH server is running on the remote host. This plugin determines the versions of the SSH protocol supported by the remote SSH daemon. The remote SSH daemon supports the following versions of the SSH protocol : SSHv1 host key fingerprint : 6e:b8:db:35:4d:c9:57:1f:83:57:ee:52:c5:a2:7e:b9 SSHv2 host key fingerprint : ec:cd:97:9f:94:96:af:df:eb:b4:3a:da:2f:ed:f8:75 ID: SSH Server Type and Version Information An SSH server is listening on this port. It is possible to obtain information about the remote SSH server by sending an empty authentication request. Risk factor: SSH version : SSH-1.99-OpenSSH_3.9p1 SSH supported authentication : publickey,gssapi-with-mic,password ID: 10267
13 13 / 37 Service Detection An SSH server is running on this port. ID: Port www (443/tcp) [-/+] Web Server Expect Header XSS
14 14 / 37 The remote web server is vulnerable to a cross-site scripting attack. The remote web server fails to sanitize the contents of an 'Expect' request header before using it to generate dynamic web content. An unauthenticated remote attacker may be able to leverage this issue to launch cross-site scripting attacks against the affected service, perhaps through specially-crafted ShockWave (SWF) files. Risk factor: Medium CVSS Base Score:4.3 CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N Check with the vendor for an update to the web server. For Apache, the issue is reportedly fixed by versions / / 2.2.2; for IBM HTTP Server, upgrade to / ; for IBM WebSphere Application Server, upgrade to Nessus was able to exploit the issue using the following request : snip
15 15 / 37 HTTP TRACE / TRACK Methods Allowed
16 16 / 37 Debugging functions are enabled on the remote web server. The remote webserver supports the TRACE and/or TRACK methods. TRACE and TRACK are HTTP methods that are used to debug web server connections. Medium CVSS Base Score:4.3 CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N Disable these methods. Refer to the plugin output for more information. To disable these methods, add the following lines for each virtual host in your configuration file : RewriteEngine on RewriteCond %{REQUEST_METHOD} ^(TRACE TRACK) RewriteRule.* - [F] Alternatively, note that Apache versions , , and 2.2 support disabling the TRACE method natively via the 'TraceEnable' directive. Nessus sent the following TRACE request : snip TRACE /Nessus html HTTP/1.1 Connection: Close Host: Pragma: no-cache User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, image/png,
17 17 / 37 SSL Version 2 (v2) Protocol Detection The remote service encrypts traffic using a protocol with known weaknesses. The remote service accepts connections encrypted using SSL 2.0, which reportedly suffers from several cryptographic flaws and has been deprecated for several years. An attacker may be able to exploit these issues to conduct man-in-the-middle attacks or decrypt communications between the affected service and clients. Risk factor: Medium CVSS Base Score:5.0 CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N Consult the application's documentation to disable SSL 2.0 and use SSL 3.0 or TLS 1.0 instead. ID: SSL Weak Cipher Suites Supported
18 18 / 37 The remote service supports the use of weak SSL ciphers. The remote host supports the use of SSL ciphers that offer either weak encryption or no encryption at all. Medium CVSS Base Score:5.0 CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N Reconfigure the affected application if possible to avoid use of weak ciphers. Here is the list of weak SSL ciphers supported by the remote server : Low Strength Ciphers (< 56-bit key) SSLv2 EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export SSLv3 EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export TLSv1 EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export The fields above are : {OpenSSL ciphername} Kx={key exchange} Au={authentication} Enc={symmetric encryption method} Mac={message authentication code} {export flag}
19 19 / 37 SSL Medium Strength Cipher Suites Supported The remote service supports the use of medium strength SSL ciphers. The remote host supports the use of SSL ciphers that offer medium strength encryption, which we currently regard as those with key lengths at least 56 bits and less than 112 bits. Medium CVSS Base Score:5.0 CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N Reconfigure the affected application if possible to avoid use of medium strength ciphers. Here are the medium strength SSL ciphers supported by the remote server : Medium Strength Ciphers (>= 56-bit and < 112-bit key) SSLv2 DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5 RC4-64-MD5 Kx=RSA Au=RSA Enc=RC4(64) Mac=MD5 SSLv3 EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1 DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1 TLSv1 EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1 DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1 The fields above are : {OpenSSL ciphername} Kx={key exchange} Au={authentication} Enc={symmetric encryption method} Mac={message authentication code} {export flag} ID: Backported Security Patch Detection (WWW)
20 20 / 37 Security patches are backported. Security patches may have been 'back ported' to the remote HTTP server without changing its version number. Banner-based checks have been disabled to avoid false positives. Note that this test is informational only and does not denote any security problem. N/A Give Nessus credentials to perform local checks. ID: HTTP methods per directory
21 21 / 37 This plugin determines which HTTP methods are allowed on various CGI directories. By calling the OPTIONS method, it is possible to determine which HTTP methods are allowed on each directory. As this list may be incomplete, the plugin also tests - if 'Thorough tests' are enabled or 'Enable web applications tests' is set to 'yes' in the scan policy - various known HTTP methods on each directory and considers them as unsupported if it receives a response code of 400, 403, 405, or 501. Note that the plugin output is only informational and does not necessarily indicate the presence of any security vulnerabilities. Risk factor: Based on the response to an OPTIONS request : - HTTP methods GET HEAD OPTIONS POST TRACE are allowed on : / ID: HyperText Transfer Protocol (HTTP) Information
22 22 / 37 Some information about the remote HTTP configuration can be extracted. This test gives some information about the remote HTTP protocol - the version used, whether HTTP Keep-Alive and HTTP pipelining are enabled, etc... This test is informational only and does not denote any security problem. Protocol version : HTTP/1.0 SSL : yes Keep-Alive : no Options allowed : GET,HEAD,POST,OPTIONS,TRACE Headers : Date: Fri, 14 May :28:28 GMT Server: Apache/ (CentOS) Accept-Ranges: bytes Content-Length: 4251 Connection: close Content-Type: text/html; charset=utf-8 ID: HTTP Server type and version
23 23 / 37 A web server is running on the remote host. This plugin attempts to determine the type and the version of the remote web server. The remote web server type is : Apache/ (CentOS) Solution : You can set the directive 'ServerTokens Prod' to limit the information emanating from the server in its response headers. ID: SSL / TLS Renegotiation Handshakes MiTM Plaintext Data Injection
24 24 / 37 The remote service allows renegotiation of TLS / SSL connections. The remote service encrypts traffic using TLS / SSL but allows a client to renegotiate the connection after the initial handshake. An unauthenticated remote attacker may be able to leverage this issue to inject an arbitrary amount of plaintext into the beginning of the application protocol stream, which could facilitate man-in-the-middle attacks if the service assumes that the sessions before and after renegotiation are from the same 'client' and merges them at the application layer. Low CVSS Base Score:2.6 CVSS2#AV:N/AC:H/Au:N/C:N/I:P/A:N Contact the vendor for specific patch information. ID: CVE: CVE BID: Other references: OSVDB:59968, OSVDB:59969, OSVDB:59970, OSVDB:59971, OSVDB:59972, OSVDB:59973, OSVDB:59974, OSVDB:60521, OSVDB:61234, OSVDB:61718, OSVDB:62210, OSVDB:62536 SSL Cipher Suites Supported
25 25 / 37 The remote service encrypts communications using SSL. This script detects which SSL ciphers are supported by the remote service for encrypting communications. Here is the list of SSL ciphers supported by the remote server : Low Strength Ciphers (< 56-bit key) SSLv2 EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export SSLv3 EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export TLSv1 EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export Medium Strength Ciphers (>= 56-bit and < 112-bit key) SSLv2 DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5 RC4-64-MD5 Kx=RSA Au=RSA Enc=RC4(64) Mac=MD5 SSLv3 EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1 DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1 TLSv1 EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
26 26 / 37 SSL Certificate Signed using Weak Hashing Algorithm The SSL certificate has been signed using a weak hash algorithm. The remote service uses an SSL certificate that has been signed using a cryptographically weak hashing algorithm - MD2, MD4, or MD5. These algorithms are known to be vulnerable to collision attacks. In theory, a determined attacker may be able to leverage this weakness to generate another certificate with the same digital signature, which could allow him to masquerade as the affected service. Risk factor: Low CVSS Base Score:2.6 CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N Contact the Certificate Authority to have the certificate reissued. ID: CVE: CVE BID: 11849, Other references: OSVDB:45106, OSVDB:45108, OSVDB:45127 SSL Certificate Information
27 27 / 37 This plugin displays the SSL certificate. This plugin connects to every SSL-related port and attempts to extract and dump the X.509 certificate. Subject Name: Country: -- State/Province: SomeState Locality: SomeCity Organization: SomeOrganization Organization Unit: SomeOrganizationalUnit Common Name: localhost.localdomain Address: root@localhost.localdomain Issuer Name: Country: -- State/Province: SomeState Locality: SomeCity Organization: SomeOrganization Organization Unit: SomeOrganizationalUnit Common Name: localhost.localdomain Address: root@localhost.localdomain Serial Number: 00 Version: 3 Signature Algorithm: MD5 With RSA Encryption Not Valid Before: May 12 06:52: GMT Not Valid After: May 12 06:52: GMT Public Key Info: Algorithm: RSA Encryption Public Key: 00 CD A D CC 03 4B C3 2C 9B A8 CC 6B CF 2A D1 9C B D5 EC 7E 0B BD 8B 43 D9 58 6D 4A 79 AD 42 3D A4 3E DC 1A 75 B0 FD D6 5A 8D DF CE 11 8E D9 BC D9 2E 52 3E 7F 24 1A C2 EC 3D CC E5 57 F3 EC 76 FA 55 0B CB A5 84 C9 D2 42 8C 5E C1 BC 25 BA 64 6B F9 EA 8B 9E 71 A8 DD F EF B F D E2 B8 6A 34 FD 88 BC E8 ED B2 7A 55 Exponent: Signature: 00 CA 2E B F 67 4F F9 9E BF DB C0 EF 6E B 10 5D 0D 1D 7F DB E8 03 0D C9 48 C1 BD 2F 3B BA F1 8B 4B FB 70 CF B D B4 BC 41 AF A8 0E BD 48 DF 90 CD E8 A7 BC D0 8E FD C D AC EC 48 5A E8 B8 38 BE 39 8A EC
28 28 / 37 Service Detection A web server is running on this port through SSLv2. ID: Service Detection An SSLv2 server answered on this port. ID: Port www (631/tcp) [-/+] HTTP methods per directory This plugin determines which HTTP methods are allowed on various CGI directories. By calling the OPTIONS method, it is possible to determine which HTTP methods are allowed on each directory. As this list may be incomplete, the plugin also tests - if 'Thorough tests' are enabled or 'Enable web applications tests' is set to 'yes' in the scan policy - various known HTTP methods on each directory and considers them as unsupported if it receives a response code of 400, 403, 405, or 501. Note that the plugin output is only informational and does not necessarily indicate the presence of any security vulnerabilities. Risk factor: Based on the response to an OPTIONS request : - HTTP methods HEAD OPTIONS POST PUT GET are allowed on : / ID: HTTP Server type and version
29 29 / 37 A web server is running on the remote host. This plugin attempts to determine the type and the version of the remote web server. The remote web server type is : CUPS/1.1 ID: Service Detection A web server is running on this port. ID: Port www (80/tcp) [-/+] Web Server Expect Header XSS
30 30 / 37 The remote web server is vulnerable to a cross-site scripting attack. The remote web server fails to sanitize the contents of an 'Expect' request header before using it to generate dynamic web content. An unauthenticated remote attacker may be able to leverage this issue to launch cross-site scripting attacks against the affected service, perhaps through specially-crafted ShockWave (SWF) files. Risk factor: Medium CVSS Base Score:4.3 CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N Check with the vendor for an update to the web server. For Apache, the issue is reportedly fixed by versions / / 2.2.2; for IBM HTTP Server, upgrade to / ; for IBM WebSphere Application Server, upgrade to Nessus was able to exploit the issue using the following request : snip
31 31 / 37 HTTP TRACE / TRACK Methods Allowed
32 32 / 37 Debugging functions are enabled on the remote web server. The remote webserver supports the TRACE and/or TRACK methods. TRACE and TRACK are HTTP methods that are used to debug web server connections. Medium CVSS Base Score:4.3 CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N Disable these methods. Refer to the plugin output for more information. To disable these methods, add the following lines for each virtual host in your configuration file : RewriteEngine on RewriteCond %{REQUEST_METHOD} ^(TRACE TRACK) RewriteRule.* - [F] Alternatively, note that Apache versions , , and 2.2 support disabling the TRACE method natively via the 'TraceEnable' directive. Nessus sent the following TRACE request : snip TRACE /Nessus html HTTP/1.1 Connection: Close Host: Pragma: no-cache User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0) Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, image/png,
33 33 / 37 Backported Security Patch Detection (WWW) Security patches are backported. Security patches may have been 'back ported' to the remote HTTP server without changing its version number. Banner-based checks have been disabled to avoid false positives. Note that this test is informational only and does not denote any security problem. N/A Give Nessus credentials to perform local checks. ID: HTTP methods per directory
34 34 / 37 This plugin determines which HTTP methods are allowed on various CGI directories. By calling the OPTIONS method, it is possible to determine which HTTP methods are allowed on each directory. As this list may be incomplete, the plugin also tests - if 'Thorough tests' are enabled or 'Enable web applications tests' is set to 'yes' in the scan policy - various known HTTP methods on each directory and considers them as unsupported if it receives a response code of 400, 403, 405, or 501. Note that the plugin output is only informational and does not necessarily indicate the presence of any security vulnerabilities. Risk factor: Based on the response to an OPTIONS request : - HTTP methods GET HEAD OPTIONS POST TRACE are allowed on : / ID: HyperText Transfer Protocol (HTTP) Information
35 35 / 37 Some information about the remote HTTP configuration can be extracted. This test gives some information about the remote HTTP protocol - the version used, whether HTTP Keep-Alive and HTTP pipelining are enabled, etc... This test is informational only and does not denote any security problem. Protocol version : HTTP/1.1 SSL : no Keep-Alive : no Options allowed : GET,HEAD,POST,OPTIONS,TRACE Headers : Date: Fri, 14 May :28:28 GMT Server: Apache/ (CentOS) Accept-Ranges: bytes Content-Length: 4251 Connection: close Content-Type: text/html; charset=utf-8 ID: HTTP Server type and version
36 36 / 37 A web server is running on the remote host. This plugin attempts to determine the type and the version of the remote web server. The remote web server type is : Apache/ (CentOS) Solution : You can set the directive 'ServerTokens Prod' to limit the information emanating from the server in its response headers. ID: Service Detection A web server is running on this port. ID: Port rpc-status (857/udp) [-/+] RPC Services Enumeration
37 37 / 37 An ONC RPC service is running on the remote host. By sending a DUMP request to the portmapper, it was possible to enumerate the ONC RPC services running on the remote port. Using this information, it is possible to connect and bind to each service by sending an RPC request to the remote port. The following RPC services are available on UDP port 857 : - program: (status), version: 1 ID: Port rpc-status (860/tcp) [-/+] RPC Services Enumeration An ONC RPC service is running on the remote host. By sending a DUMP request to the portmapper, it was possible to enumerate the ONC RPC services running on the remote port. Using this information, it is possible to connect and bind to each service by sending an RPC request to the remote port. The following RPC services are available on TCP port 860 : - program: (status), version: 1 ID: [^] Back to
PCI Detailed Vulnerability Report
 PCI Detailed Vulnerability Report Scan Date: 03/03/2012 14:28:47 Generated: 03/03/2012 14:30:13 1998-2012 Clone Systems, Inc. All rights reserved Table of Contents Part 1. Scan Information... 1 Part 2.
PCI Detailed Vulnerability Report Scan Date: 03/03/2012 14:28:47 Generated: 03/03/2012 14:30:13 1998-2012 Clone Systems, Inc. All rights reserved Table of Contents Part 1. Scan Information... 1 Part 2.
Scan Results - ( Essentials - Onsharp )
 Scan Results - www.onsharp.com ( Essentials - Onsharp ) Overview Open Ports (18) Scan ID: 7675527 Target: www.onsharp.com Max Score: 2.6 Compliance: Passing PCI compliance, Expires undefined Profile: 15
Scan Results - www.onsharp.com ( Essentials - Onsharp ) Overview Open Ports (18) Scan ID: 7675527 Target: www.onsharp.com Max Score: 2.6 Compliance: Passing PCI compliance, Expires undefined Profile: 15
Nessus Scan Report. Hosts Summary (Executive) Hosts Summary (Executive) Mon, 15 May :27:44 EDT
 Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address :
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Lab 5 Nessus Vulnerability Scan Report
 Lab 5 Nessus Vulnerability Scan Report This handout is a printout of the results of a Nessus vulnerability scan. The scan was performed on the mock IT infrastructure in the lab environment for the Jones
Lab 5 Nessus Vulnerability Scan Report This handout is a printout of the results of a Nessus vulnerability scan. The scan was performed on the mock IT infrastructure in the lab environment for the Jones
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Findings for
 Findings for 198.51.100.23 Scan started: 2017-07-11 12:30 UTC Scan ended: 2017-07-11 12:39 UTC Overview Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 80/tcp
Findings for 198.51.100.23 Scan started: 2017-07-11 12:30 UTC Scan ended: 2017-07-11 12:39 UTC Overview Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 80/tcp
ID: Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/2018 Version:
 ID: 42417 Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
ID: 42417 Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Payment Card Industry (PCI) Executive Report 11/01/2016
 Payment Card Industry (PCI) Executive Report 11/01/2016 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: Rural Computer Consultants
Payment Card Industry (PCI) Executive Report 11/01/2016 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: Rural Computer Consultants
Release note Tornaborate
 Release note 1.2.6 Tornaborate 2015-09-10 Contents 1 Summary 4 2 Additional important information about this release 5 3 Upgrade 6 3.1 Prerequisites................................... 6 3.2 How to apply
Release note 1.2.6 Tornaborate 2015-09-10 Contents 1 Summary 4 2 Additional important information about this release 5 3 Upgrade 6 3.1 Prerequisites................................... 6 3.2 How to apply
Scan Report Executive Summary
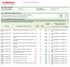 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report. June 12, 2016
 Scan Report June 12, 2016 Summary This document reports on the results of an automatic security scan. The scan started at Sun Jun 12 20:28:41 2016 UTC and ended at Sun Jun 12 20:48:24 2016 UTC. The report
Scan Report June 12, 2016 Summary This document reports on the results of an automatic security scan. The scan started at Sun Jun 12 20:28:41 2016 UTC and ended at Sun Jun 12 20:48:24 2016 UTC. The report
Scan Report Executive Summary
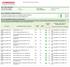 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):ekk.worldtravelink.com
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Overview of SSL/TLS. Luke Anderson. 12 th May University Of Sydney.
 Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
HTTP Protocol and Server-Side Basics
 HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
Brocade will no longer provide security updates as End of Life (EOL) was January 18, 2013.
 Component: SSH CVSS Score: N/A No CVE: https://access.redhat.com/solutions/420283 ncircle vulnerability scanner reports insecure SSH HMAC algorithms enabled. Advises disabling MD5 HMAC algorithms and any
Component: SSH CVSS Score: N/A No CVE: https://access.redhat.com/solutions/420283 ncircle vulnerability scanner reports insecure SSH HMAC algorithms enabled. Advises disabling MD5 HMAC algorithms and any
Scan Report. Contents. November 15, Result Overview 2
 Scan Report November 15, 2016 This document reports on the results of an automatic security scan. All dates are displayed using the timezone Coordinated Universal Time, which is abbreviated UTC. The task
Scan Report November 15, 2016 This document reports on the results of an automatic security scan. All dates are displayed using the timezone Coordinated Universal Time, which is abbreviated UTC. The task
TLS 1.2 Protocol Execution Transcript
 Appendix C TLS 1.2 Protocol Execution Transcript In Section 2.3, we overviewed a relatively simple protocol execution transcript for SSL 3.0. In this appendix, we do something similar for TLS 1.2. Since
Appendix C TLS 1.2 Protocol Execution Transcript In Section 2.3, we overviewed a relatively simple protocol execution transcript for SSL 3.0. In this appendix, we do something similar for TLS 1.2. Since
CIS-331 Fall 2014 Exam 1 Name: Total of 109 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
ID: Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version:
 ID: 59176 Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 59176 Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Why bother? Causes of data breaches OWASP. Top ten attacks. Now what? Do it yourself Questions?
 Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
TLS1.2 IS DEAD BE READY FOR TLS1.3
 TLS1.2 IS DEAD BE READY FOR TLS1.3 28 March 2017 Enterprise Architecture Technology & Operations Presenter Photo Motaz Alturayef Jubial Cyber Security Conference 70% Privacy and security concerns are
TLS1.2 IS DEAD BE READY FOR TLS1.3 28 March 2017 Enterprise Architecture Technology & Operations Presenter Photo Motaz Alturayef Jubial Cyber Security Conference 70% Privacy and security concerns are
Version: $Revision: 1142 $
 Check for SSL Weak Ciphers Application: https Port: 443 ScriptID: 103440 Weak ciphers offered by this service: SSL2_RC4_128_MD5 SSL2_RC4_128_EXPORT40_WITH_MD5 SSL2_RC2_CBC_128_CBC_WITH_MD5 SSL2_RC2_CBC_128_CBC_EXPORT40_WITH_MD5
Check for SSL Weak Ciphers Application: https Port: 443 ScriptID: 103440 Weak ciphers offered by this service: SSL2_RC4_128_MD5 SSL2_RC4_128_EXPORT40_WITH_MD5 SSL2_RC2_CBC_128_CBC_WITH_MD5 SSL2_RC2_CBC_128_CBC_EXPORT40_WITH_MD5
Payment Card Industry (PCI) Executive Report 11/07/2017
 Payment Card Industry (PCI) Executive Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
Payment Card Industry (PCI) Executive Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
SSL Report: bourdiol.xyz ( )
 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > bourdiol.xyz > 217.70.180.152 SSL Report: bourdiol.xyz (217.70.180.152) Assessed on: Sun Apr 19 12:22:55 PDT 2015 HIDDEN
Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > bourdiol.xyz > 217.70.180.152 SSL Report: bourdiol.xyz (217.70.180.152) Assessed on: Sun Apr 19 12:22:55 PDT 2015 HIDDEN
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Scan Report. March 6, 2015
 Scan Report March 6, 2015 This document reports on the results of an automatic security scan. The scan started at Fri Mar 6 14:05:50 2015 UTC and ended at Fri Mar 6 14:11:32 2015 UTC. The report first
Scan Report March 6, 2015 This document reports on the results of an automatic security scan. The scan started at Fri Mar 6 14:05:50 2015 UTC and ended at Fri Mar 6 14:11:32 2015 UTC. The report first
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security
 SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
SEEM4540 Open Systems for E-Commerce Lecture 03 Internet Security Consider 2. Based on DNS, identified the IP address of www.cuhk.edu.hk is 137.189.11.73. 1. Go to http://www.cuhk.edu.hk 3. Forward the
ID: Cookbook: urldownload.jbs Time: 08:25:02 Date: 29/10/2018 Version: Fire Opal
 ID: Cookbook: urldownload.jbs Time: 0:25:02 Date: 29//201 Version: 24.0.0 Fire Opal Table of Contents Table of Contents Analysis Report http://15.1..14/neko.sh Overview General Information Detection Confidence
ID: Cookbook: urldownload.jbs Time: 0:25:02 Date: 29//201 Version: 24.0.0 Fire Opal Table of Contents Table of Contents Analysis Report http://15.1..14/neko.sh Overview General Information Detection Confidence
Scan Report. March 6, 2015
 Scan Report March 6, 2015 This document reports on the results of an automatic security scan. The scan started at Fri Mar 6 14:15:40 2015 UTC and ended at Fri Mar 6 14:25:44 2015 UTC. The report first
Scan Report March 6, 2015 This document reports on the results of an automatic security scan. The scan started at Fri Mar 6 14:15:40 2015 UTC and ended at Fri Mar 6 14:25:44 2015 UTC. The report first
SSL Report: printware.co.uk ( )
 1 of 5 26/06/2015 14:27 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > printware.co.uk SSL Report: printware.co.uk (194.143.166.5) Assessed on: Fri, 26 Jun 2015 12:53:08
1 of 5 26/06/2015 14:27 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > printware.co.uk SSL Report: printware.co.uk (194.143.166.5) Assessed on: Fri, 26 Jun 2015 12:53:08
Citrix XenApp and XenDesktop 7.6 LTSR FIPS Sample Deployments
 Citrix XenApp and XenDesktop 7.6 LTSR FIPS 140-2 Sample Deployments Table of contents Introduction... 2 Audience... 2 Security features introduced in XenApp and XenDesktop 7.6 LTSR... 2 FIPS 140-2 with
Citrix XenApp and XenDesktop 7.6 LTSR FIPS 140-2 Sample Deployments Table of contents Introduction... 2 Audience... 2 Security features introduced in XenApp and XenDesktop 7.6 LTSR... 2 FIPS 140-2 with
Encryption. INST 346, Section 0201 April 3, 2018
 Encryption INST 346, Section 0201 April 3, 2018 Goals for Today Symmetric Key Encryption Public Key Encryption Certificate Authorities Secure Sockets Layer Simple encryption scheme substitution cipher:
Encryption INST 346, Section 0201 April 3, 2018 Goals for Today Symmetric Key Encryption Public Key Encryption Certificate Authorities Secure Sockets Layer Simple encryption scheme substitution cipher:
CIS-331 Exam 2 Spring 2016 Total of 110 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Security Policy Document Version 3.3. Tropos Networks
 Tropos Control Element Management System Security Policy Document Version 3.3 Tropos Networks October 1 st, 2009 Copyright 2009 Tropos Networks. This document may be freely reproduced whole and intact
Tropos Control Element Management System Security Policy Document Version 3.3 Tropos Networks October 1 st, 2009 Copyright 2009 Tropos Networks. This document may be freely reproduced whole and intact
CIS-331 Exam 2 Fall 2014 Total of 105 Points. Version 1
 Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
CIS-331 Final Exam Spring 2015 Total of 115 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Host Identity Sources
 The following topics provide information on host identity sources: Overview: Host Data Collection, on page 1 Determining Which Host Operating Systems the System Can Detect, on page 2 Identifying Host Operating
The following topics provide information on host identity sources: Overview: Host Data Collection, on page 1 Determining Which Host Operating Systems the System Can Detect, on page 2 Identifying Host Operating
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
Produced by. Mobile Application Development. Higher Diploma in Science in Computer Science. Eamonn de Leastar
 Mobile Application Development Higher Diploma in Science in Computer Science Produced by Eamonn de Leastar (edeleastar@wit.ie) Department of Computing, Maths & Physics Waterford Institute of Technology
Mobile Application Development Higher Diploma in Science in Computer Science Produced by Eamonn de Leastar (edeleastar@wit.ie) Department of Computing, Maths & Physics Waterford Institute of Technology
4. Specifications and Additional Information
 4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
ENGI 8868/9877 Computer and Communications Security III. BLOCK CIPHERS. Symmetric Key Cryptography. insecure channel
 (a) Introduction - recall symmetric key cipher: III. BLOCK CIPHERS k Symmetric Key Cryptography k x e k y yʹ d k xʹ insecure channel Symmetric Key Ciphers same key used for encryption and decryption two
(a) Introduction - recall symmetric key cipher: III. BLOCK CIPHERS k Symmetric Key Cryptography k x e k y yʹ d k xʹ insecure channel Symmetric Key Ciphers same key used for encryption and decryption two
Understanding Cisco Cybersecurity Fundamentals
 210-250 Understanding Cisco Cybersecurity Fundamentals NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 210-250 Exam on Understanding Cisco
210-250 Understanding Cisco Cybersecurity Fundamentals NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 210-250 Exam on Understanding Cisco
Scan Report. March 6, 2015
 Scan Report March 6, 2015 This document reports on the results of an automatic security scan. The scan started at Fri Mar 6 13:29:13 2015 UTC and ended at Fri Mar 6 13:34:10 2015 UTC. The report first
Scan Report March 6, 2015 This document reports on the results of an automatic security scan. The scan started at Fri Mar 6 13:29:13 2015 UTC and ended at Fri Mar 6 13:34:10 2015 UTC. The report first
Security in Bomgar Remote Support
 Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Payment Card Industry (PCI) Technical Report 11/07/2017
 Payment Card Industry (PCI) Technical Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
Payment Card Industry (PCI) Technical Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
McAfee Network Security Platform 8.1
 Revision C McAfee Network Security Platform 8.1 (8.1.7.91-8.1.3.124 Manager-M-series Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known
Revision C McAfee Network Security Platform 8.1 (8.1.7.91-8.1.3.124 Manager-M-series Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known
Cipher Suite Practices and Pitfalls:
 Cipher Suite Practices and Pitfalls: An Overview of Cipher Suite Configuration and Pitfalls on BIG-IP PRESENTED BY: A cipher suite is a named combination of authentication, encryption, message authentication
Cipher Suite Practices and Pitfalls: An Overview of Cipher Suite Configuration and Pitfalls on BIG-IP PRESENTED BY: A cipher suite is a named combination of authentication, encryption, message authentication
Computer Security. 10r. Recitation assignment & concept review. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 10r. Recitation assignment & concept review Paul Krzyzanowski Rutgers University Spring 2018 April 3, 2018 CS 419 2018 Paul Krzyzanowski 1 1. What is a necessary condition for perfect
Computer Security 10r. Recitation assignment & concept review Paul Krzyzanowski Rutgers University Spring 2018 April 3, 2018 CS 419 2018 Paul Krzyzanowski 1 1. What is a necessary condition for perfect
::/Topics/Configur...
 1 / 5 Configuration Cain & Abel requires the configuration of some parameters; everything can be set from the main configuration dialog. Sniffer Tab Here you can set the network card to be used by Cain's
1 / 5 Configuration Cain & Abel requires the configuration of some parameters; everything can be set from the main configuration dialog. Sniffer Tab Here you can set the network card to be used by Cain's
E-commerce security: SSL/TLS, SET and others. 4.1
 E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
TLS 1.1 Security fixes and TLS extensions RFC4346
 F5 Networks, Inc 2 SSL1 and SSL2 Created by Netscape and contained significant flaws SSL3 Created by Netscape to address SSL2 flaws TLS 1.0 Standardized SSL3 with almost no changes RFC2246 TLS 1.1 Security
F5 Networks, Inc 2 SSL1 and SSL2 Created by Netscape and contained significant flaws SSL3 Created by Netscape to address SSL2 flaws TLS 1.0 Standardized SSL3 with almost no changes RFC2246 TLS 1.1 Security
Chapter 5: Vulnerability Analysis
 Chapter 5: Vulnerability Analysis Technology Brief Vulnerability analysis is a part of the scanning phase. In the Hacking cycle, vulnerability analysis is a major and important part. In this chapter, we
Chapter 5: Vulnerability Analysis Technology Brief Vulnerability analysis is a part of the scanning phase. In the Hacking cycle, vulnerability analysis is a major and important part. In this chapter, we
01/02/2014 SECURITY ASSESSMENT METHODOLOGIES SENSEPOST 2014 ALL RIGHTS RESERVED
 01/02/2014 SECURITY ASSESSMENT METHODOLOGIES SENSEPOST 2014 ALL RIGHTS RESERVED Contents 1. Introduction 3 2. Security Testing Methodologies 3 2.1 Internet Footprint Assessment 4 2.2 Infrastructure Assessments
01/02/2014 SECURITY ASSESSMENT METHODOLOGIES SENSEPOST 2014 ALL RIGHTS RESERVED Contents 1. Introduction 3 2. Security Testing Methodologies 3 2.1 Internet Footprint Assessment 4 2.2 Infrastructure Assessments
Secret Key Systems (block encoding) Encrypting a small block of text (say 64 bits) General considerations for cipher design:
 Secret Key Systems (block encoding) Encrypting a small block of text (say 64 bits) General considerations for cipher design: Secret Key Systems (block encoding) Encrypting a small block of text (say 64
Secret Key Systems (block encoding) Encrypting a small block of text (say 64 bits) General considerations for cipher design: Secret Key Systems (block encoding) Encrypting a small block of text (say 64
ID: Cookbook: urldownload.jbs Time: 18:48:38 Date: 19/06/2018 Version:
 ID: 64646 Cookbook: urldownload.jbs Time: 1:4:3 Date: 19/06/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
ID: 64646 Cookbook: urldownload.jbs Time: 1:4:3 Date: 19/06/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
WAP Security. Helsinki University of Technology S Security of Communication Protocols
 WAP Security Helsinki University of Technology S-38.153 Security of Communication Protocols Mikko.Kerava@iki.fi 15.4.2003 Contents 1. Introduction to WAP 2. Wireless Transport Layer Security 3. Other WAP
WAP Security Helsinki University of Technology S-38.153 Security of Communication Protocols Mikko.Kerava@iki.fi 15.4.2003 Contents 1. Introduction to WAP 2. Wireless Transport Layer Security 3. Other WAP
Computer Networks. Wenzhong Li. Nanjing University
 Computer Networks Wenzhong Li Nanjing University 1 Chapter 7. Network Security Network Attacks Cryptographic Technologies Message Integrity and Authentication Key Distribution Firewalls Transport Layer
Computer Networks Wenzhong Li Nanjing University 1 Chapter 7. Network Security Network Attacks Cryptographic Technologies Message Integrity and Authentication Key Distribution Firewalls Transport Layer
Scan report for Scanned on :47:40
 Scan report for www.cc-emblavez.fr Scanned on 2015-02-03 08:47:40 SQL Error Description Your website contains one or more SQL-error(s). Make sure to remove them or have them fixed as soon as possible.
Scan report for www.cc-emblavez.fr Scanned on 2015-02-03 08:47:40 SQL Error Description Your website contains one or more SQL-error(s). Make sure to remove them or have them fixed as soon as possible.
SSL Visibility and Troubleshooting
 Page 1 of 6 view online Avi Vantage provides a number of features to help understand the utilization of SSL traffic and troubleshoot SSL-related issues. Visibility Every virtual service provides a number
Page 1 of 6 view online Avi Vantage provides a number of features to help understand the utilization of SSL traffic and troubleshoot SSL-related issues. Visibility Every virtual service provides a number
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Project 4: Penetration Test
 Project description Project 4: Penetration Test April 28, 2014 Bing Hao The learning objective of this project is to gain hands on experiences with the usage and functionality of Nmap, Neussus and Metsploit.
Project description Project 4: Penetration Test April 28, 2014 Bing Hao The learning objective of this project is to gain hands on experiences with the usage and functionality of Nmap, Neussus and Metsploit.
Scan Results May 31, 2013
 Scan Results May 31, 2013 Report Summary User Name: Roberto Chana Login Name: sebyt-rc Company: SELLBYTEL GROUP S.A User Role: Manager Address: Av. Diagonal 197 4th floor City: Barcelona State: ne Zip:
Scan Results May 31, 2013 Report Summary User Name: Roberto Chana Login Name: sebyt-rc Company: SELLBYTEL GROUP S.A User Role: Manager Address: Av. Diagonal 197 4th floor City: Barcelona State: ne Zip:
The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to
 1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
SSL Report: ( )
 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > www.workbench.nationaldataservice.org SSL Report: www.workbench.nationaldataservice.org (141.142.210.100) Assessed on:
Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > www.workbench.nationaldataservice.org SSL Report: www.workbench.nationaldataservice.org (141.142.210.100) Assessed on:
ICS 351: Today's plan. IPv6 routing protocols (summary) HTML HTTP web scripting languages certificates (review) cookies
 ICS 351: Today's plan IPv6 routing protocols (summary) HTML HTTP web scripting languages certificates (review) cookies IPv6 routing almost the same routing protocols as for IPv4: RIPng, OSPFv6, BGP with
ICS 351: Today's plan IPv6 routing protocols (summary) HTML HTTP web scripting languages certificates (review) cookies IPv6 routing almost the same routing protocols as for IPv4: RIPng, OSPFv6, BGP with
Transport Layer Security
 CEN585 Computer and Network Security Transport Layer Security Dr. Mostafa Dahshan Department of Computer Engineering College of Computer and Information Sciences King Saud University mdahshan@ksu.edu.sa
CEN585 Computer and Network Security Transport Layer Security Dr. Mostafa Dahshan Department of Computer Engineering College of Computer and Information Sciences King Saud University mdahshan@ksu.edu.sa
User Manual. Admin Report Kit for IIS 7 (ARKIIS)
 User Manual Admin Report Kit for IIS 7 (ARKIIS) Table of Contents 1 Admin Report Kit for IIS 7... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements... 2 1.4 Technical Support...
User Manual Admin Report Kit for IIS 7 (ARKIIS) Table of Contents 1 Admin Report Kit for IIS 7... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements... 2 1.4 Technical Support...
ID: Cookbook: urldownload.jbs Time: 20:31:22 Date: 09/08/2018 Version:
 ID: 153 Cookbook: urldownload.jbs Time: 20:31:22 Date: 09/0/201 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis Advice Signature
ID: 153 Cookbook: urldownload.jbs Time: 20:31:22 Date: 09/0/201 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis Advice Signature
Network Vulnerability Scan
 Network Vulnerability Scan Aug 28, 2018 Ethnio, Inc. 6121 W SUNSET BLVD LOS angeles, CA 90028 Tel (888) 879-7439 ETHN.io Summary Ethnio conducts ongoing network vulnerability scans using both Qualys and
Network Vulnerability Scan Aug 28, 2018 Ethnio, Inc. 6121 W SUNSET BLVD LOS angeles, CA 90028 Tel (888) 879-7439 ETHN.io Summary Ethnio conducts ongoing network vulnerability scans using both Qualys and
But where'd that extra "s" come from, and what does it mean?
 SSL/TLS While browsing Internet, some URLs start with "http://" while others start with "https://"? Perhaps the extra "s" when browsing websites that require giving over sensitive information, like paying
SSL/TLS While browsing Internet, some URLs start with "http://" while others start with "https://"? Perhaps the extra "s" when browsing websites that require giving over sensitive information, like paying
SSL Report: sharplesgroup.com ( )
 1 of 5 26/06/2015 14:28 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > sharplesgroup.com SSL Report: sharplesgroup.com (176.58.116.26) Assessed on: Fri, 26 Jun 2015
1 of 5 26/06/2015 14:28 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > sharplesgroup.com SSL Report: sharplesgroup.com (176.58.116.26) Assessed on: Fri, 26 Jun 2015
Protocol Comparisons: OpenSSH, SSL/TLS (AT-TLS), IPSec
 Protocol Comparisons: OpenSSH, SSL/TLS (AT-TLS), IPSec Author: Gwen Dente, IBM Gaithersburg, MD Acknowledgments: Alfred Christensen, IBM Erin Farr, IBM Christopher Meyer, IBM Linwood Overby, IBM Richard
Protocol Comparisons: OpenSSH, SSL/TLS (AT-TLS), IPSec Author: Gwen Dente, IBM Gaithersburg, MD Acknowledgments: Alfred Christensen, IBM Erin Farr, IBM Christopher Meyer, IBM Linwood Overby, IBM Richard
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6
 FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
Security in the Privileged Remote Access Appliance
 Security in the Privileged Remote Access Appliance 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
Security in the Privileged Remote Access Appliance 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
OSI Session / presentation / application Layer. Dr. Luca Allodi - Network Security - University of Trento, DISI (AA 2015/2016)
 OSI Session / presentation / application Layer Dr. Luca Allodi - Network Security - University of Trento, DISI (AA 2015/2016) 1 Higher level protocols On top of IP, TCP, UDP, etc. there are a plethora
OSI Session / presentation / application Layer Dr. Luca Allodi - Network Security - University of Trento, DISI (AA 2015/2016) 1 Higher level protocols On top of IP, TCP, UDP, etc. there are a plethora
ID: Cookbook: browseurl.jbs Time: 09:46:57 Date: 19/10/2018 Version: Fire Opal
 ID: 85066 Cookbook: browseurl.jbs Time: 09:46:57 Date: 19/10/2018 Version: 24.0.0 Fire Opal Table of Contents Table of Contents Analysis Report http://lux-motors.com/nnngg/nngbbgh/fffee Overview General
ID: 85066 Cookbook: browseurl.jbs Time: 09:46:57 Date: 19/10/2018 Version: 24.0.0 Fire Opal Table of Contents Table of Contents Analysis Report http://lux-motors.com/nnngg/nngbbgh/fffee Overview General
Foundstone 7.0 Patch 6 Release Notes
 Foundstone 7.0 Patch 6 Release Notes These release notes describe the changes and updates for Foundstone 7.0, patch 6. This application installs only the patch needed to update the Foundstone system. Foundstone
Foundstone 7.0 Patch 6 Release Notes These release notes describe the changes and updates for Foundstone 7.0, patch 6. This application installs only the patch needed to update the Foundstone system. Foundstone
UNH-IOL MIPI Alliance Test Program
 DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
Triple DES and AES 192/256 Implementation Notes
 Triple DES and AES 192/256 Implementation Notes Sample Password-to-Key and KeyChange results of Triple DES and AES 192/256 implementation For InterWorking Labs customers who require detailed information
Triple DES and AES 192/256 Implementation Notes Sample Password-to-Key and KeyChange results of Triple DES and AES 192/256 implementation For InterWorking Labs customers who require detailed information
SSL Report: cartridgeworld.co.uk ( )
 1 of 5 26/06/2015 14:21 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > cartridgeworld.co.uk SSL Report: cartridgeworld.co.uk (95.138.147.104) Assessed on: Fri, 26 Jun
1 of 5 26/06/2015 14:21 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > cartridgeworld.co.uk SSL Report: cartridgeworld.co.uk (95.138.147.104) Assessed on: Fri, 26 Jun
Lecture Nov. 21 st 2006 Dan Wendlandt ISP D ISP B ISP C ISP A. Bob. Alice. Denial-of-Service. Password Cracking. Traffic.
 15-441 Lecture Nov. 21 st 2006 Dan Wendlandt Worms & Viruses Phishing End-host impersonation Denial-of-Service Route Hijacks Traffic modification Spyware Trojan Horse Password Cracking IP Spoofing DNS
15-441 Lecture Nov. 21 st 2006 Dan Wendlandt Worms & Viruses Phishing End-host impersonation Denial-of-Service Route Hijacks Traffic modification Spyware Trojan Horse Password Cracking IP Spoofing DNS
Renegotiating TLS. Marsh Ray Steve Dispensa PhoneFactor, Inc. v1.1 November 4, Summary
 Renegotiating TLS Marsh Ray Steve Dispensa PhoneFactor, Inc. v1.1 November 4, 2009 Summary Transport Layer Security (TLS, RFC 5246 and previous, including SSL v3 and previous) is subject to a number of
Renegotiating TLS Marsh Ray Steve Dispensa PhoneFactor, Inc. v1.1 November 4, 2009 Summary Transport Layer Security (TLS, RFC 5246 and previous, including SSL v3 and previous) is subject to a number of
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
MTAT Applied Cryptography
 MTAT.07.017 Applied Cryptography Transport Layer Security (TLS) Advanced Features University of Tartu Spring 2016 1 / 16 Client Server Authenticated TLS ClientHello ServerHello, Certificate, ServerHelloDone
MTAT.07.017 Applied Cryptography Transport Layer Security (TLS) Advanced Features University of Tartu Spring 2016 1 / 16 Client Server Authenticated TLS ClientHello ServerHello, Certificate, ServerHelloDone
SECURING DOMINO LDAP. Open Mic June 10th 2015
 SECURING DOMINO LDAP Open Mic June 10th 2015 AGENDA Background Domino Directory Assistance Domino LDAP Server Domino LDAP in a Post-Poodle World Questions 2 BACKGROUND We consider this presentation a continuation
SECURING DOMINO LDAP Open Mic June 10th 2015 AGENDA Background Domino Directory Assistance Domino LDAP Server Domino LDAP in a Post-Poodle World Questions 2 BACKGROUND We consider this presentation a continuation
TIBCO Cloud Integration Security Overview
 TIBCO Cloud Integration Security Overview TIBCO Cloud Integration is secure, best-in-class Integration Platform as a Service (ipaas) software offered in a multi-tenant SaaS environment with centralized
TIBCO Cloud Integration Security Overview TIBCO Cloud Integration is secure, best-in-class Integration Platform as a Service (ipaas) software offered in a multi-tenant SaaS environment with centralized
Linux Network Administration
 Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
Secure Remote Connections with OpenSSH Objective At the conclusion of this module, the student will be able to: Configure the ssh daemon start, stop, and restart sshd 17 January 2005 NETW 111 - SSH 2 SSH
The StrideLinx Remote Access Solution comprises the StrideLinx router, web-based platform, and VPN client.
 Introduction: Intended Audience The StrideLinx Remote Access Solution is designed to offer safe and secure remote access to industrial equipment worldwide for efficient remote troubleshooting, programming
Introduction: Intended Audience The StrideLinx Remote Access Solution is designed to offer safe and secure remote access to industrial equipment worldwide for efficient remote troubleshooting, programming
Strategic Infrastructure Security
 Strategic Infrastructure Security Course Number: SCPSIS Length: Certification Exam There are no exams currently associated with this course. Course Overview This course picks up right where Tactical Perimeter
Strategic Infrastructure Security Course Number: SCPSIS Length: Certification Exam There are no exams currently associated with this course. Course Overview This course picks up right where Tactical Perimeter
Applications & Application-Layer Protocols: The Web & HTTP
 CPSC 360 Network Programming Applications & Application-Layer Protocols: The Web & HTTP Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu http://www.cs.clemson.edu/~mweigle/courses/cpsc360
CPSC 360 Network Programming Applications & Application-Layer Protocols: The Web & HTTP Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu http://www.cs.clemson.edu/~mweigle/courses/cpsc360
ID: Cookbook: urldownload.jbs Time: 19:58:34 Date: 02/05/2018 Version:
 ID: 57706 Cookbook: urldownload.jbs Time: 19:5:34 Date: 02/05/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 57706 Cookbook: urldownload.jbs Time: 19:5:34 Date: 02/05/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
Question No: 2 Which identifier is used to describe the application or process that submitted a log message?
 Volume: 65 Questions Question No: 1 Which definition of a fork in Linux is true? A. daemon to execute scheduled commands B. parent directory name of a file pathname C. macros for manipulating CPU sets
Volume: 65 Questions Question No: 1 Which definition of a fork in Linux is true? A. daemon to execute scheduled commands B. parent directory name of a file pathname C. macros for manipulating CPU sets
Ethical Hacking and Countermeasures: Web Applications, Second Edition. Chapter 3 Web Application Vulnerabilities
 Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
