For correct operation of the AutoLogon feature when using the Georgia SoftWorks SSH2/Telnet Client two steps must occur.
|
|
|
- Deirdre Charles
- 6 years ago
- Views:
Transcription
1 Automatic Logon Autologon This feature allows you to pre-configure a list of IP addresses that will be able to connect and log on without any User ID, Password or Domain prompting when using the Georgia SoftWorks SSH2/Telnet Clients or 3 rd Party Clients. Autologon is useful in many situations; however the real power of this feature is realized when coupled with the Session Saver for fast and easy connection establishment. For example when a connection is broken due to a link failure you can reconnect without the time consuming UserID, Password and Domain prompts and resume work exactly where you left off before the link failure. The configuration procedure for Automatic Logon is different for GSW Clients and Third Party Clients. A list of IP address can be associated with either GSW Clients or 3 rd Party Clients but NOT both. Automatic Logon for GSW Clients is configured using the gs_auto.txt file. Automatic Logon for Third Party Clients is configured using the gs_logon.txt file. The format of the files is exactly the same but it is important to remember which files are used for each client type. Note: An IP address cannot be associated with both a GSW Client and a Third Party Client. No overlap between IP Address ranges defined in the gs_auto.txt and gs_logon.txt is allowed. Unpredictable results will occur. Autologon with GSW Clients For correct operation of the AutoLogon feature when using the Georgia SoftWorks SSH2/Telnet Client two steps must occur. First, the Georgia SoftWorks Telnet/SSH2 Client must be enabled for automatic logon. GSW Desktop Clients Automatic Logon is enabled using the command line parameter a when initiating the client. GSW Mobile Clients Automatic Logon is enabled by checking the Autologon checkbox on the Session Settings Session menu options. Second, a server side configuration text file is used for specifying the IP address that will autologon. The name of the file for the Georgia SoftWorks SSH2/Telnet Client is gs_auto.txt and is installed in the GSW UTS Root Directory. All Clients connecting with IP addresses specified in the gs_auto.txt file must be GSW Clients AND the IP Addresses CAN NOT also be used in the 3 rd Party Automatic Logon configuration text file. No overlap between IP Address ranges defined in the gs_logon.txt and gs_auto.txt is allowed. 1
2 The order of the fields in the gs_auto.txt file is as follows: Field IP Address Domain User Name Password Description The IP address of the client Specify the dot. character if no domain is used. The User ID for the connection The Password Table 14 Automatic Logon Specifications gs_auto.txt when using GSW Clients An IP address can be associated to autologon with a Georgia SoftWorks OR a 3 rd Party Client but NOT both. No overlap between IP Address ranges defined in the gs_auto.txt and gs_logon.txt is allowed. For example the following entry in the file: rayr sharpbook Instructs the system that when a user connects from the IP Address that the connection should be authenticated as./rayr with the password set to sharpbook. The # character in the first column designates a comment line. NOTE1: The IP address must start in the first column. IP Address Ranges and wildcards are allowed. NOTE2: For security reasons it is prudent to set the file gs_auto.txt to allow only SYSTEM Read Access. NO other accounts should be allowed to access this file. NOTE3: The format of this file is the same as gs_logon.txt, the automatic logon configuration file used with 3 rd party clients. Only the name of the file is different. 2
3 Automatic Logon 3 rd Party Clients This feature allows you to pre-configure a list of IP addresses that will be able to connect and log on without any User ID, Password or Domain prompting when using 3 rd Party Clients. Autologon is useful in many situations; however the real power of this feature is realized when coupled with the Session Saver and/or used with RF Data collection devices for fast and easy connection establishment. For example when a connection is broken due to a link failure you can reconnect without the time consuming UserID, Password and Domain prompts and resume work exactly where you left off before the link failure. A server side text file is used for specifying the IP addresses that will autologon. The name of the file is gs_logon.txt and is installed in the UTS Root Directory. No client configuration is required for 3 rd party clients. The order of the fields in the gs_logon.txt file is as follows: Field IP Address Domain User Name Password Description The IP address of the client Specify the dot. character if no domain is used. The User ID for the connection The Password Table 15 - Automatic Logon Specifications gs_logon.txt when using 3 rd Party Clients An IP address can be associated to autologon with a Georgia SoftWorks OR a 3 rd Party Client but NOT both. No overlap between IP Address ranges defined in the gs_logon.txt and gs_auto.txt is allowed. For example the following entry in the file: rayr sharpbook Instructs the system that when a user connects from the IP Address that the connection should be authenticated as./rayr with the password set to sharpbook. The # character in the first column designates a comment line. 3
4 NOTE1: The IP address must start in the first column. IP Address Ranges and Wildcards are allowed. NOTE2: For security reasons it is prudent to set the file gs_logon.txt to allow only SYSTEM Read Access. NO other accounts should be allowed to access this file. NOTE3: The format of this file is the same as gs_auto.txt, the automatic logon configuration file used with the Georgia SoftWorks Telnet/SSH2 clients. Only the name of the file is different. 4
5 Automatic Logon Summary Automatic Logon requires Server Side Configuration and Client Side Configuration for GSW Clients. Server Side Configuration Automatic Logon Configuration File on Server GSW Client Third Party Client Edit specific Server File that contains Automatic Logon Information gs_auto.txt gs_logon.txt Table 16 - Automatic Logon Configuration Files Client Side Configuration for Automatic Logon GSW Desktop Client Client Side Configuration GSW Mobile Client Third Party Client Add the command line parameter -a when initiating the client. This tells the client not to send logon information to the server. Example in the GS_SClnt.bat file Check the Box in the configuration options off exist once1.bat do call exist once1.bat do del once1.bat None a if errorlevel 2 goto gs_clnt.new gs_clnt.exe > exist once2.bat do call exist once2.bat do del start Table 17 - Automatic Logon Client Side Configuration 5
GEORGIA SOFTWORKS. February 15, GSW ConnectBot Android Client for SSH/Telnet. GSW ConnectBot. Users Guide
 GEORGIA SOFTWORKS February 15, 2018 GSW ConnectBot Android Client for SSH/Telnet GSW ConnectBot Users Guide THIS PAGE INTENTIONALLY LEFT BLANK ii GEORGIA SOFTWORKS February 15, 2018 Georgia SoftWorks Public
GEORGIA SOFTWORKS February 15, 2018 GSW ConnectBot Android Client for SSH/Telnet GSW ConnectBot Users Guide THIS PAGE INTENTIONALLY LEFT BLANK ii GEORGIA SOFTWORKS February 15, 2018 Georgia SoftWorks Public
GEORGIA SOFTWORKS. Universal Terminal Server for Windows Vista/7/8/10/2003/2008/2012/2016. For GSW Telnet Server and GSW SSH Server.
 GEORGIA SOFTWORKS Universal Terminal Server for Windows Vista/7/8/10/2003/2008/2012/2016 For GSW Telnet Server and GSW SSH Server User s Guide T H I S P A G E I N T E N T I O N A L L Y L E F T B L A N
GEORGIA SOFTWORKS Universal Terminal Server for Windows Vista/7/8/10/2003/2008/2012/2016 For GSW Telnet Server and GSW SSH Server User s Guide T H I S P A G E I N T E N T I O N A L L Y L E F T B L A N
San Jacinto College. Secure SSL VPN Instruction Manual. Contents
 1 San Jacinto College Secure SSL VPN Instruction Manual The new Secure SSL VPN provides a more secure and convenient method of accessing San Jacinto College resources remotely. This document provides an
1 San Jacinto College Secure SSL VPN Instruction Manual The new Secure SSL VPN provides a more secure and convenient method of accessing San Jacinto College resources remotely. This document provides an
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Appserv Internal Desktop Access Mac OS Device with Safari Browser. Enter your Appserv username and password to sign in to the Website
 Appserv Desktop Access Logging on from a Mac OS device Step 1. To sign in to the Appserv Desktop Access website, enter the following address into the Safari browser address bar. Please Note: This documentation
Appserv Desktop Access Logging on from a Mac OS device Step 1. To sign in to the Appserv Desktop Access website, enter the following address into the Safari browser address bar. Please Note: This documentation
How to Configure Connection Fallback using Multiple VPN Gateways
 How to Configure Connection Fallback using Multiple VPN Gateways Configure the Barracuda VPN Client for Windows to silently switch to fallback VPN gateways when a VPN gateway is not reachable, such as
How to Configure Connection Fallback using Multiple VPN Gateways Configure the Barracuda VPN Client for Windows to silently switch to fallback VPN gateways when a VPN gateway is not reachable, such as
Client Configuration Guide
 Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Instructions for connecting to the FDIBA Wireless Network (Windows Vista)
 Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
EZ-Snapshot for Windows NT, 2000 & XP
 EZ-Snapshot for Windows NT, 2000 & XP Before you can use EZ-Snapshot, you must first sign up for the service. To do this, obtain an application form at the VCC Help Desk, or print a copy from the RCS directory
EZ-Snapshot for Windows NT, 2000 & XP Before you can use EZ-Snapshot, you must first sign up for the service. To do this, obtain an application form at the VCC Help Desk, or print a copy from the RCS directory
How to Change Screensaver in Windows 10
 How to Change Screensaver in Windows 10 Windows 10 provides 6 Screensavers by default. It is a good practise to set a Screensaver if your computer remains idle for a few minutes. The below post describes
How to Change Screensaver in Windows 10 Windows 10 provides 6 Screensavers by default. It is a good practise to set a Screensaver if your computer remains idle for a few minutes. The below post describes
Installing the WinSCP Secure FTP Client
 Draft 0.9 Page 1 of 6 Installing the WinSCP Secure FTP Client This document will instruct you to install the WinSCP application that will provide Secure FTP (SFTP) access to your website folder. So why
Draft 0.9 Page 1 of 6 Installing the WinSCP Secure FTP Client This document will instruct you to install the WinSCP application that will provide Secure FTP (SFTP) access to your website folder. So why
Thank you for choosing ASAP s Remote QuickBooks hosting! The following will guide you through the set up of your new or updated user profile.
 Thank you for choosing ASAP s Remote QuickBooks hosting! The following will guide you through the set up of your new or updated user profile. Please select from the following options to begin setup: Windows
Thank you for choosing ASAP s Remote QuickBooks hosting! The following will guide you through the set up of your new or updated user profile. Please select from the following options to begin setup: Windows
Configure Wireless for Windows 7
 Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Internet access system through the Wireless Network of the University of Bologna
 Internet access system through the Wireless Network of the University of Bologna (last update 6/3/2017) Printable service summary document: the updated version is available online at the address http://www.unibo.it/almawifi
Internet access system through the Wireless Network of the University of Bologna (last update 6/3/2017) Printable service summary document: the updated version is available online at the address http://www.unibo.it/almawifi
Securewireless Windows 7 Setup Guide
 Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Manually Configuring Windows 8 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Running TCL Scripts on an IDENTIKEY Appliance. Creation date: 24/06/2016 Last Review: 26/07/2016 Revision number: 2
 KB 160094 Running TCL Scripts on an IDENTIKEY Appliance Creation date: 24/06/2016 Last Review: 26/07/2016 Revision number: 2 Document type: How To Security status: EXTERNAL Summary Executing a TCL script
KB 160094 Running TCL Scripts on an IDENTIKEY Appliance Creation date: 24/06/2016 Last Review: 26/07/2016 Revision number: 2 Document type: How To Security status: EXTERNAL Summary Executing a TCL script
Remote Access to Unix Machines
 Remote Access to Unix Machines Alvin R. Lebeck Department of Computer Science Department of Electrical and Computer Engineering Duke University Overview We are using OIT Linux machines for some homework
Remote Access to Unix Machines Alvin R. Lebeck Department of Computer Science Department of Electrical and Computer Engineering Duke University Overview We are using OIT Linux machines for some homework
Lab - Common Windows CLI Commands
 Introduction In this lab, you will use CLI commands to manage files and folders in Windows. Recommended Equipment A computer running Windows Step 1: Access the Windows command prompt. a. Log on to a computer
Introduction In this lab, you will use CLI commands to manage files and folders in Windows. Recommended Equipment A computer running Windows Step 1: Access the Windows command prompt. a. Log on to a computer
Installing and Configuring Citrix XenApp 6.5 (Part 1)
 Installing and Configuring Citrix XenApp 6.5 (Part 1) Introduction The first part of this series describes the installation steps of the first server (which will create the XenApp environment) and the
Installing and Configuring Citrix XenApp 6.5 (Part 1) Introduction The first part of this series describes the installation steps of the first server (which will create the XenApp environment) and the
Browser Set-Up Instructions
 Browser Set-Up Instructions Before visiting the Assessment LinkBC site for the first time, you must configure your Internet Explorer browser: o to recognize the Assessment LinkBC site as a trusted site,
Browser Set-Up Instructions Before visiting the Assessment LinkBC site for the first time, you must configure your Internet Explorer browser: o to recognize the Assessment LinkBC site as a trusted site,
Application Note: Installing Remote Management Agents Using Service Account Manager Rev 2 June 1, 2006
 Application Note: Installing Remote Management Agents Using Service Account Manager Rev 2 June 1, 2006 Lieberman Software Corporation http://www.liebsoft.com Abstract The Microsoft Windows Server Resource
Application Note: Installing Remote Management Agents Using Service Account Manager Rev 2 June 1, 2006 Lieberman Software Corporation http://www.liebsoft.com Abstract The Microsoft Windows Server Resource
January 12, Prepared by Dina Borisov, Product manager Jetro Platforms. All rights reserved.
 January 12, 2016 Prepared by Dina Borisov, Product manager 2015 Jetro Platforms. All rights reserved. Contents acockpit5 RDP Android Client... 3 Setting Two factor Authentication... 5 Configuring Two Factor
January 12, 2016 Prepared by Dina Borisov, Product manager 2015 Jetro Platforms. All rights reserved. Contents acockpit5 RDP Android Client... 3 Setting Two factor Authentication... 5 Configuring Two Factor
Enter your Appserv username and password to sign in to the Website
 Appserv Desktop Access Logging on from a Windows 10 Device Step 1. To sign in to the Appserv Desktop Access website, either enter the following address into the Microsoft Edge browser address bar, or click
Appserv Desktop Access Logging on from a Windows 10 Device Step 1. To sign in to the Appserv Desktop Access website, either enter the following address into the Microsoft Edge browser address bar, or click
SETUP FOR OUTLOOK (Updated October, 2018)
 EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
Defender Desktop Login GrIDsure Token User Guide
 Desktop Login GrIDsure Token User Guide Introduction This guide describes what the user will see when using Desktop Login with GrIDsure tokens. The logon procedure will vary slightly depending on the platform
Desktop Login GrIDsure Token User Guide Introduction This guide describes what the user will see when using Desktop Login with GrIDsure tokens. The logon procedure will vary slightly depending on the platform
Click All Programs Open Text Host explorer / Connection Central (Doing this brings up a Connection Central panel).
 Secure Host Explorer FTP Setup Setup Instructions Host Explorer is the terminal emulation software that allows users to connect their PC to the mainframe in a secure environment. For example, this allows
Secure Host Explorer FTP Setup Setup Instructions Host Explorer is the terminal emulation software that allows users to connect their PC to the mainframe in a secure environment. For example, this allows
Operational Reporting Web Viewer Installation and Users Guide
 Operational Reporting Web Viewer Installation and Users Guide Table of Contents Disclaimer... 3 What is Operational Reporting Web Viewer?... 4 Installation Requirements... 5 Installation Instructions...
Operational Reporting Web Viewer Installation and Users Guide Table of Contents Disclaimer... 3 What is Operational Reporting Web Viewer?... 4 Installation Requirements... 5 Installation Instructions...
Johns Hopkins
 Wireless Configuration Guide: Windows 8 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 7, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 8 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 7, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Installing and Connecting to DGL PM Server
 Installing and Connecting to DGL PM Server Go to www.dglpm.co.uk and click SUPPORT along the top. To access the download use the Click Here option as seen in the screenshot below. Left click Download DGL
Installing and Connecting to DGL PM Server Go to www.dglpm.co.uk and click SUPPORT along the top. To access the download use the Click Here option as seen in the screenshot below. Left click Download DGL
Key File Generation. November 14, NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171
 Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
VMware Horizon Client Installation Guide (Windows)
 VMware Horizon Client Installation Guide (Windows) (Please note: The steps in this document must be followed exactly as shown in order to ensure a proper installation.) Requirements: You must have an existing
VMware Horizon Client Installation Guide (Windows) (Please note: The steps in this document must be followed exactly as shown in order to ensure a proper installation.) Requirements: You must have an existing
Automated Sign-on for Mainframe Administrator Guide
 Automated Sign-on for Mainframe Administrator Guide 12.5.1 For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy,
Automated Sign-on for Mainframe Administrator Guide 12.5.1 For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy,
Outlook 2010 Setup Guide (POP3 Transmailaccess)
 Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
How to Install, Configure and Use sftp (Windows Version)
 How to Install, Configure and Use sftp (Windows Version) The sftp secure File Transfer Protocol allows you to transfer patient datasets to and from IDT s server securely. All data transfers are encrypted
How to Install, Configure and Use sftp (Windows Version) The sftp secure File Transfer Protocol allows you to transfer patient datasets to and from IDT s server securely. All data transfers are encrypted
Manual UCSFwpa Configuration for Windows 7
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Password Reset Utility. Configuration
 Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
RU-VPN2 - GlobalProtect Installation for Windows
 RU-VPN2 - GlobalProtect Installation for Windows Use RU-VPN2 for a secure connection to Ryerson's Administrative system via the Internet. To use RU- VPN2, you will need to install and use client software
RU-VPN2 - GlobalProtect Installation for Windows Use RU-VPN2 for a secure connection to Ryerson's Administrative system via the Internet. To use RU- VPN2, you will need to install and use client software
How do I configure my LPL client to use SSL for incoming mail?
 How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
External Authentication with Ultra Protect v7.2 SSL VPN Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Ultra Protect v7.2 SSL VPN Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External Authentication with Ultra Protect v7.2 SSL VPN Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External Authentication with Citrix GoToMyPc Corporate Edition Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Citrix GoToMyPc Corporate Edition Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External Authentication with Citrix GoToMyPc Corporate Edition Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
Aqua Accelerated Protocol (AAP) User Manual
 Aqua Accelerated Protocol (AAP) User Manual Table of Contents About Aqua Accelerated Protocol...3 Features... 3 System Requirements... 4 Hardware... 4 Software (AAP Client)... 4 Software (Server Connecting
Aqua Accelerated Protocol (AAP) User Manual Table of Contents About Aqua Accelerated Protocol...3 Features... 3 System Requirements... 4 Hardware... 4 Software (AAP Client)... 4 Software (Server Connecting
Lab 11-1 Lab User Profiles and Tracking
 In the following lab instructions, you will be setting up groups, users, and passwords to require password-protected login to Kofax Capture modules. Rights will be assigned to the groups and users that
In the following lab instructions, you will be setting up groups, users, and passwords to require password-protected login to Kofax Capture modules. Rights will be assigned to the groups and users that
GEORGIA SOFTWORKS. Rocket Terminal Engine for Windows NT/XP/VISTA/2000/2003. User Manual
 GEORGIA SOFTWORKS Rocket Terminal Engine for Windows NT/XP/VISTA/2000/2003 User Manual THIS PAGE INTENTIONALLY LEFT BLANK GEORGIA SOFTWORKS Rocket Terminal Engine Copyright 1997-2007, Georgia SoftWorks,
GEORGIA SOFTWORKS Rocket Terminal Engine for Windows NT/XP/VISTA/2000/2003 User Manual THIS PAGE INTENTIONALLY LEFT BLANK GEORGIA SOFTWORKS Rocket Terminal Engine Copyright 1997-2007, Georgia SoftWorks,
Step-by-step installation guide for monitoring untrusted servers using Operations Manager
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Configuring EAP-FAST CHAPTER
 CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
PCGENESIS TECHNICAL SYSTEM OPERATIONS GUIDE
 PCGENESIS TECHNICAL SYSTEM OPERATIONS GUIDE 11/14/2012 User Interface Procedures [Set Site Color Option, V1.00] Revision History Date Version Description Author 11/14/2012 1.00 12.03.00 Create new document.
PCGENESIS TECHNICAL SYSTEM OPERATIONS GUIDE 11/14/2012 User Interface Procedures [Set Site Color Option, V1.00] Revision History Date Version Description Author 11/14/2012 1.00 12.03.00 Create new document.
Introduction. 1. Deactivating Anti-Executable. 2. Updating the virus definitions. 3. Reactivating Anti-Executable.
 Introduction The process of updating virus definitions on workstations protected by Faronics Anti-Executable Enterprise involves three fundamental steps: 1. Deactivating Anti-Executable. 2. Updating the
Introduction The process of updating virus definitions on workstations protected by Faronics Anti-Executable Enterprise involves three fundamental steps: 1. Deactivating Anti-Executable. 2. Updating the
Stratco Business Management Software Installation Instructions
 Stratco Business Management Software Installation Instructions Last revised 16 th August 2013 Contents Read First... 2 Section 1 First Time Installation... 3 Section 2 Install Stratco Business Management
Stratco Business Management Software Installation Instructions Last revised 16 th August 2013 Contents Read First... 2 Section 1 First Time Installation... 3 Section 2 Install Stratco Business Management
Registering for classes Help
 Registering for classes Help Before You Begin 1. Create your class schedule from the material provided by your campus. 2. Prepare additional schedules in the event courses on your first choice schedule
Registering for classes Help Before You Begin 1. Create your class schedule from the material provided by your campus. 2. Prepare additional schedules in the event courses on your first choice schedule
CITRIX REMOTE PC SKADDEN REMOTE ACCESS PAGE CONNECT TO SKADDEN SYSTEMS REMOTELY DOWNLOAD & INSTALL CITRIX LOG ON TO REMOTE DESKTOP
 CITRIX REMOTE PC SKADDEN REMOTE ACCESS PAGE Skadden Remote URL: http://skadlink.skadden.com Citrix Remote Desktop: Allows access to the Skadden network as if you were in the office. Outlook WebMail: Allows
CITRIX REMOTE PC SKADDEN REMOTE ACCESS PAGE Skadden Remote URL: http://skadlink.skadden.com Citrix Remote Desktop: Allows access to the Skadden network as if you were in the office. Outlook WebMail: Allows
WDC RDS Connection for Android Users
 WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
Connecting to the Cloud
 Connecting to the Cloud Step 1. Log off the current Outlook client. Step 2. Shutdown Lync (if used): Left click the Show Hidden Icons button on the taskbar. (For most PCs this is the bottom right corner.)
Connecting to the Cloud Step 1. Log off the current Outlook client. Step 2. Shutdown Lync (if used): Left click the Show Hidden Icons button on the taskbar. (For most PCs this is the bottom right corner.)
Installing PCS Director in a Citrix or Terminal Services Environment
 Installing PCS Director in a Citrix or Terminal Services Environment Summary This document explains how to install PCS Director in a Citrix Metaframe or a Terminal Services environment. It also includes
Installing PCS Director in a Citrix or Terminal Services Environment Summary This document explains how to install PCS Director in a Citrix Metaframe or a Terminal Services environment. It also includes
Using Expressions Web to Edit an FCNet Department Web Site
 Using Expressions Web to Edit an FCNet Department Web Site Here are the steps to open and edit a site on the new FcWebDept shared department web site server using Microsoft Expression Web 4. The steps
Using Expressions Web to Edit an FCNet Department Web Site Here are the steps to open and edit a site on the new FcWebDept shared department web site server using Microsoft Expression Web 4. The steps
SAP NAVIGATION QUICK REFERENCE CARD
 SAP NAVIGATION QUICK REFERENCE CARD Table of Contents: Log On To the SAP System 3 Change Your Password 5 SAP System Messages / Information 6 SAP Buttons / Screen Features 7 Open a New Session 9 Use Transaction
SAP NAVIGATION QUICK REFERENCE CARD Table of Contents: Log On To the SAP System 3 Change Your Password 5 SAP System Messages / Information 6 SAP Buttons / Screen Features 7 Open a New Session 9 Use Transaction
For the Beginner: c) Click the settings tab to set screen resolution d) Set resolution with slider bar.
 For the Beginner: Preparing and Logging In to Run JobSite OnLine 1) Jobsite works best with a screen resolution of at least 800 x 600 preferably 1024 x 768. To set this, follow the instructions below.
For the Beginner: Preparing and Logging In to Run JobSite OnLine 1) Jobsite works best with a screen resolution of at least 800 x 600 preferably 1024 x 768. To set this, follow the instructions below.
UMDNJ Wireless Documentation Windows 7
 UMDNJ Wireless Documentation Windows 7 The following documentation will provide instructions for configuring the Microsoft Windows 7 native wireless client. There are wireless adapters that have 3 rd party
UMDNJ Wireless Documentation Windows 7 The following documentation will provide instructions for configuring the Microsoft Windows 7 native wireless client. There are wireless adapters that have 3 rd party
Payschools Parent Portal User Guide Electronic Free or Reduced Meal Application Tracking
 Payschools Parent Portal User Guide Electronic Free or Reduced Meal Application Tracking Welcome to the Payschools Parent Portal. In just a few steps, you can create a Free and Reduced Meal application
Payschools Parent Portal User Guide Electronic Free or Reduced Meal Application Tracking Welcome to the Payschools Parent Portal. In just a few steps, you can create a Free and Reduced Meal application
AWC Connect. This document has instructions for: Installing the WatchGuard VPN Client and Connecting the VPN to Woodmark
 AWC Connect Use the AWC Connect VPN client to browse mapped network drives and navigate the intranet just as if you were sitting in your office. AWC Connect is for AWCissued Windows PCs only. This document
AWC Connect Use the AWC Connect VPN client to browse mapped network drives and navigate the intranet just as if you were sitting in your office. AWC Connect is for AWCissued Windows PCs only. This document
APP-J: WHAT IS APPLICATION JUKEBOX?
 APP-J: WHAT IS APPLICATION JUKEBOX? Use Application Jukebox (App-J) to run University software on any Windows PC or laptop. Launch apps from the Application Jukebox web page Install the Application Jukebox
APP-J: WHAT IS APPLICATION JUKEBOX? Use Application Jukebox (App-J) to run University software on any Windows PC or laptop. Launch apps from the Application Jukebox web page Install the Application Jukebox
Protection Blocking. Inspection. Web-Based
 Protection Blocking Inspection Web-Based Anti-Virus & removal of dangerous attachments. Prevent your server from being used as open-relay. Stop mail-loops. Blocks open relay sources. Isolate known spam
Protection Blocking Inspection Web-Based Anti-Virus & removal of dangerous attachments. Prevent your server from being used as open-relay. Stop mail-loops. Blocks open relay sources. Isolate known spam
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
User Account Manager
 CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
Grandstream Networks, Inc. Grandstream Firmware Upgrade Utility Tool User Guide (Version: )
 Grandstream Networks, Inc. Grandstream Firmware Upgrade Utility Tool User Guide (Version: 1.0.0.15) Table of Contents OVERVIEW... 3 UPGRADE USING THE UTILITY TOOL... 4 Page 2 OVERVIEW Grandstream provides
Grandstream Networks, Inc. Grandstream Firmware Upgrade Utility Tool User Guide (Version: 1.0.0.15) Table of Contents OVERVIEW... 3 UPGRADE USING THE UTILITY TOOL... 4 Page 2 OVERVIEW Grandstream provides
RU-VPN2 - GlobalProtect Installation for Windows
 RU-VPN2 - GlobalProtect Installation for Windows Use RU-VPN2 for a secure connection to Ryerson's Administrative system via the Internet. To use RU-VPN2, you will need to install and use client software
RU-VPN2 - GlobalProtect Installation for Windows Use RU-VPN2 for a secure connection to Ryerson's Administrative system via the Internet. To use RU-VPN2, you will need to install and use client software
Citrix GoToAssist Express User Guide
 Citrix GoToAssist Express User Guide Citrix Online 2008 Citrix Online, LLC. All rights reserved. 6500 Hollister Avenue Goleta, CA 93117 (888) (888) 621-0538 Fax: (805) 690-6471 Table of Contents System
Citrix GoToAssist Express User Guide Citrix Online 2008 Citrix Online, LLC. All rights reserved. 6500 Hollister Avenue Goleta, CA 93117 (888) (888) 621-0538 Fax: (805) 690-6471 Table of Contents System
MULTI-FACTOR AUTHENTICATION SET-UP
 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
MXmeeting User Manual for PC Users
 MXmeeting User Manual for PC Users Zultys, Inc. 771 Vaqueros Ave Sunnyvale, CA 94085 support@zultys.com http://www.zultys.com Contents Preface... 3 Organization... 3 Terms... 3 1. Setting up MXmeeting...
MXmeeting User Manual for PC Users Zultys, Inc. 771 Vaqueros Ave Sunnyvale, CA 94085 support@zultys.com http://www.zultys.com Contents Preface... 3 Organization... 3 Terms... 3 1. Setting up MXmeeting...
Wireless Setup Instructions for Windows 7
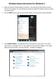 Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
Configuring Remote Access using the RDS Gateway
 Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Johns Hopkins
 Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows 8, 7, XP, Mac OS X, Linux, and Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows 8, 7, XP, Mac OS X, Linux, and Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
This is an example of a data filter which would allow this specific FormImprint user to see those patients with a room number between 135 and 156.
 FormImprint The FormImprint module is used for on-demand printing of forms. Blank forms and forms with data can be printed as needed. The screen below shows a typical FormImprint screen. The steps to printing
FormImprint The FormImprint module is used for on-demand printing of forms. Blank forms and forms with data can be printed as needed. The screen below shows a typical FormImprint screen. The steps to printing
Adding your IMAP Mail Account in Outlook 2013 on Windows
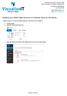 Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Setup Smart Login for Windows V2
 Setup Smart Login for Windows V2 Smart Login allows workstations to login to a Smart-Net server without having to join a domain. Smart Login is suitable for both laptops and desktop PC s. Features Users
Setup Smart Login for Windows V2 Smart Login allows workstations to login to a Smart-Net server without having to join a domain. Smart Login is suitable for both laptops and desktop PC s. Features Users
Axel Menu. Publishing Applications and Securing the Desktop for Windows TSE. November Ref.: AxMenuE-11
 Axel Menu Publishing Applications and Securing the Desktop for Windows TSE November 2008 - Ref.: AxMenuE-11 The reproduction of this material, in part or whole, is strictly prohibited. For additional information,
Axel Menu Publishing Applications and Securing the Desktop for Windows TSE November 2008 - Ref.: AxMenuE-11 The reproduction of this material, in part or whole, is strictly prohibited. For additional information,
Manually Configuring Windows 7 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
Once you login, you are taken to your User Profile Page with a few tabs at the top of the page
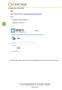 To Launch into a Class and Lab Login Login at the web address: https://centriq.learnondemand.net Enter -- Username: firstname.lastname 1 Password: Premier12 Once you login, you are taken to your User Profile
To Launch into a Class and Lab Login Login at the web address: https://centriq.learnondemand.net Enter -- Username: firstname.lastname 1 Password: Premier12 Once you login, you are taken to your User Profile
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
Using FileZilla to Connect to Your SFTP Account
 Using FileZilla to Connect to Your SFTP Account 2016 17 Academic Year Changes Previously, Wyoming Transcript Center users connected to the National Student Clearinghouse (Clearinghouse) servers using the
Using FileZilla to Connect to Your SFTP Account 2016 17 Academic Year Changes Previously, Wyoming Transcript Center users connected to the National Student Clearinghouse (Clearinghouse) servers using the
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
SmartSearch Cloud Hosting Set-Up Guide
 127 Church Street, New Haven, CT 06510 O: (203) 789-0889 E: sales@square-9.com www.square-9.com Contents Introduction... 3 Configuration & Workarounds... 3 Will the client machines have VPN access to the
127 Church Street, New Haven, CT 06510 O: (203) 789-0889 E: sales@square-9.com www.square-9.com Contents Introduction... 3 Configuration & Workarounds... 3 Will the client machines have VPN access to the
TPMC-8X Release Notes
 Page 1 of 10 product: TPMC-8X version: 1.00.01.69 file: tpmc-8x_1.00.01.69.csz build date: 18-Feb-2009 i. Version 1.00.01.69 ii. Version 1.00.01.56 iii. Version 1.00.01.34 iv. Version 1.00.00.35 v. Version
Page 1 of 10 product: TPMC-8X version: 1.00.01.69 file: tpmc-8x_1.00.01.69.csz build date: 18-Feb-2009 i. Version 1.00.01.69 ii. Version 1.00.01.56 iii. Version 1.00.01.34 iv. Version 1.00.00.35 v. Version
VPN/RDP Laptop and Workstation Usage instructions:
 VPN/RDP Laptop and Workstation Usage instructions: This document details how to use the laptops and workstations provided to users which connect to the secure NEST environment using VPN connectivity. Note
VPN/RDP Laptop and Workstation Usage instructions: This document details how to use the laptops and workstations provided to users which connect to the secure NEST environment using VPN connectivity. Note
DocumentDirect for the Internet. User s Guide
 DocumentDirect for the Internet User s Guide Copyright 2008-2015 UMB Financial Corporation. (External) Version 3.0 07012015 FINAL July 2015 UMB Reg. U.S. Pat. & Tm. Off. Table of Contents iii Contents
DocumentDirect for the Internet User s Guide Copyright 2008-2015 UMB Financial Corporation. (External) Version 3.0 07012015 FINAL July 2015 UMB Reg. U.S. Pat. & Tm. Off. Table of Contents iii Contents
Configuring 802.1X Authentication Client for Windows 8
 Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Provisioning Databases
 DAT219x Provisioning Databases Lab 00 Getting Started Estimated time to complete this lab is 60 minutes Overview In this lab, you will provision a Microsoft Azure Virtual Machine (VM) that will be used
DAT219x Provisioning Databases Lab 00 Getting Started Estimated time to complete this lab is 60 minutes Overview In this lab, you will provision a Microsoft Azure Virtual Machine (VM) that will be used
SecurEnvoy Microsoft Server Agent
 SecurEnvoy Microsoft Server Agent SecurEnvoy Global HQ Merlin House, Brunel Road, Theale, Reading. RG7 4TY Tel: 0845 2600010 Fax: 0845 260014 www.securenvoy.com SecurEnvoy Microsoft Server Agent Installation
SecurEnvoy Microsoft Server Agent SecurEnvoy Global HQ Merlin House, Brunel Road, Theale, Reading. RG7 4TY Tel: 0845 2600010 Fax: 0845 260014 www.securenvoy.com SecurEnvoy Microsoft Server Agent Installation
Budget DataMart. BDM Hyperion (System 9) Workspace and Interactive Reporting (IR) module
 Hhttp://www.bdmhyperion.uconn.edu/H Budget DataMart BDM Hyperion (System 9) Workspace and Interactive Reporting (IR) module This document provides information and instruction. Where to find the new BDM
Hhttp://www.bdmhyperion.uconn.edu/H Budget DataMart BDM Hyperion (System 9) Workspace and Interactive Reporting (IR) module This document provides information and instruction. Where to find the new BDM
UNIT 9 Introduction to Linux and Ubuntu
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
Start Here. P5100 Fingerprint Reader. Quick Installation Guide. Verifi. IMPORTANT. This installation manual is for Windows 8.1.
 Verifi P5100 Fingerprint Reader with ROBOFORM PASSWORD MANAGER Start Here IMPORTANT. This installation manual is for Windows 8.1 Quick Installation Guide Windows Logon Make sure you have the following:
Verifi P5100 Fingerprint Reader with ROBOFORM PASSWORD MANAGER Start Here IMPORTANT. This installation manual is for Windows 8.1 Quick Installation Guide Windows Logon Make sure you have the following:
Quick Start Guide Getting started with NSN Connect
 Quick Start Guide Table of contents: - Glossary - Accessing your computers - Closing connection - Key features - Security Advice - Frequently Asked Questions (FAQs) - Requirements About NSN Connect and
Quick Start Guide Table of contents: - Glossary - Accessing your computers - Closing connection - Key features - Security Advice - Frequently Asked Questions (FAQs) - Requirements About NSN Connect and
QuickBooks for Windows Conversion Instructions
 QuickBooks for Windows Conversion Instructions Web Connect Introduction As Yolo Federal Credit Union completes its system conversion, you will need to modify your QuickBooks settings to ensure the smooth
QuickBooks for Windows Conversion Instructions Web Connect Introduction As Yolo Federal Credit Union completes its system conversion, you will need to modify your QuickBooks settings to ensure the smooth
Remote Desktop Services Guide. Android DG ITEC ESIO - STANDARDS
 Remote Desktop Services Guide Android DG ITEC ESIO - STANDARDS Table of Contents Table of Contents... 2 1 Introduction... 3 2 Download and Install Citrix Receiver... 3 3 RSA Authentication... 4 4 Setting
Remote Desktop Services Guide Android DG ITEC ESIO - STANDARDS Table of Contents Table of Contents... 2 1 Introduction... 3 2 Download and Install Citrix Receiver... 3 3 RSA Authentication... 4 4 Setting
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
Command Line Interface The basics
 Command Line Interface The basics Marco Berghoff, SCC, KIT Steinbuch Centre for Computing (SCC) Funding: www.bwhpc-c5.de Motivation In the Beginning was the Command Line by Neal Stephenson In contrast
Command Line Interface The basics Marco Berghoff, SCC, KIT Steinbuch Centre for Computing (SCC) Funding: www.bwhpc-c5.de Motivation In the Beginning was the Command Line by Neal Stephenson In contrast
