Laboratory Exercise: Session Data
|
|
|
- Lora Miles
- 5 years ago
- Views:
Transcription
1 Goals Laboratory Exercise: Session Data 1. To understand its basic components and architecture of a session based network monitoring system. 2. To be able to install and configure one such system, based on SiLK, and to understand how these components operate in that context. 3. To be able to use the data collected to perform common network auditing tasks. 4. To understand the tradeoffs between full packet and session data capture with respect to network security monitoring. Prerequisites Before you can begin with this particularly chapter, you will need to set up a virtual network environment with several different virtual machines with which a number of different software packages will be installed. First thing you need to do is ensure that everything is updated on your SecurityOnion system 1. To do this run the following command: $ sudo soup Do not worry if it takes a long time to update, this is to be expected and should not cause concern. Once it has been updated close down the VM. You can now go about setting up the network environment that you will be using for this chapter. See below for a diagram of the machines and setup required: 1https://github.com/Security-Onion-Solutions/security-onion/wiki/Upgrade 1
2 We will refer to vbox0 as the DMZ, and vbox1 as the LAN. We will refer to the bridged network as the WAN, note that this implies your native host is in the WAN. Let s take it one step at a time. Clone the M0n0wall VM that you used in the previous exercise and call it M0n0wall2. Change the settings of the M0n0wall VM so that one network adapter is set to bridge mode and the other is set to host only (vmbox0). Go ahead and boot up the M0n0wall VM. Check that the interfaces are set up correctly by swapping them so that the LAN is em1 and the WAN is em0. Change the LAN IP address on the M0n0wall machine to [EXPAND ON THIS POINT]. The next step is to change your Ubuntu machine and the SecurityOnion so they are set to be on the vmbox0 interface. Load up the Ubuntu machine and browse to the IP address of the new M0n0wall LAN ( ). Set up a new DHCP reservation with the Ubuntu MAC address to and save the settings. Go to VirtualBox and ensure that your SecurityOnion machine has two network adapters that are both set to be host-only and connected to the (vmbox0) interface too. Once you have done this, load up SecurityOnion. Run the ifconfig command and write down the two MAC addresses. Now go back to your Ubuntu machine and, using the M0n0wall web interface, add two more DHCP reservations for the SecurityOnion Ethernet adapters. A diagram below shows you what it should now look like. Go ahead and reboot both the Ubuntu and SecurityOnion VM s. Once they are loaded back up you should see the new IP addresses. 2
3 Load up the M0n0wall2 machine and change its LAN IP address to Determine which interface needs to be on the LAN and which needs to be on the WAN. Change the Ubuntu-LAN machine so it is running on the vmbox1 interface then go ahead and boot that machine up too. Log into the M0n0wall2 machine and set its WAN IP address to be set by DHCP server (the M0n0wall machine will do set it). Restart both M0n0wall 2 and the Ubuntu-LAN machine in that order. At this point everything should be booted up and running. You have now set up the environment that you will need for the rest of this chapter. To understand its basic components and architecture of a session based network monitoring system. Approach - Execution The - Cautions (Optional) To be able to install and configure one such system, based on SiLK, and to understand how these components operate in that context. 3
4 Approach - Execution What you need to do now is download and install all of the tools that are necessary for SiLK to run. It is important that you finish each step in order before you move onto the next step otherwise it can cause problems later on with the installations. SecurityOnion Setup Before you can process with any further steps you need to run the SecurityOnion setup on your machine first. On the desktop there is an icon called Setup. Double click that to begin. The first section of the setup is to configure the network interfaces, so when prompted, select Yes, configure /etc/network/interfaces!. Your management interface should be set to eth1. You should use DHCP addressing (remember that you have previously setup a reserved IP address on the M0n0wall so it will not change). It will then ask if you would like to configure the monitor interfaces, once again select No and check the eth0 box. You will then be presented with a summary screen like that shown below. Check that it matches and then click Yes, make changes!. Once this is completed it will ask you to reboot before continuing to the second phase of the Setup. Go ahead and reboot the machine. After it has rebooted you will need to run the setup again so you can continue with the second phase. 4
5 It will ask you to confirm that you want to skip the network configuration setup because it appears that it has already been completed. You should skip the step and then select the Quick Setup on the next page. The next part is to determine which interface you want to monitor traffic on, select eth0 like shown below: It will then ask you to provide an address for Snorby. Whilst we will not be using it right now, it may still be useful in future so go ahead and input your address here. It will then ask you to create your Sguil username then continue to make your Sguil password. The next step is it will ask you whether you want to enable ELSA, select yes. Finally it will again give you a summary, like that shown below. Confirm the settings and select Yes, proceed with the changes!. You are now ready to proceed with the next stages. 5
6 Downloading On your SecurityOnion machine, create a new directory where you are going to download all the packages. In this instance it will be referred to as Installs. Change directory to there and then issue the following commands: $ wget $ wget $ wget Once you have issued all three commands, your directory should that shown below: like Installation The analysis of flow data requires a flow generator and a collector. So, before you can begin collecting and analyzing session data with SiLK you need to ensure that you have data to collect. In this case, you will be installing the YAF flow generation utility. YAF generates IPFIX flow data, which is quite flexible. Collection will be handled by the rwflowpack component of SiLK, and analysis will be provided through the SiLK rwtool suite. To install these tools, you will need a couple of prerequisites. You can install these in one fell swoop by running this command: $ sudo apt-get install glib2.0 libglib2.0-dev libpcap-dev g+ + python-dev As part of the installation process it will inform you that additional disk space will be used and request you confirm it. Select Y. It will then begin the installation of the necessary packages. Once this process is complete there will be a number of packages that are no longer required and can be removed from the system. To do this, run the following command: 6
7 $ sudo apt-get autoremove With this done, you can install fixbuf using these steps: 1. Extract the archive and go to the newly extracted folder $ tar xvzf libfixbuf tar.gz $ cd libfixbuf-1.3.0/ 2. Configure, make, and install the package $./configure $ make $ sudo make install Before you can install YAF you need to remember to go back into the previous Installs directory. To do so issue: $ cd../ Now you can install YAF with these steps: 1. Extract the archive and go to the newly extracted folder $ tar xvzf yaf tar.gz $ cd yaf-2.4.0/ 2. Export the PKG configuration path $ export PKG_CONFIG_PATH=/usr/local/lib/pkgconfig 3. Configure with applabel enabled 7
8 $./configure --enable-applabel 4. Make and install the package $ make $ sudo make install If you try to run YAF right now, you ll notice an error. You need to continue the installation process before it will run properly. This process continues by installing SiLK with these steps: 1. Change directory to the previous Installs directory $ cd../ 2. Extract the archive and go to the newly extracted folder $ tar xvzf silk tar.gz $ cd silk-3.7.2/ 3. Configure with a specified fixbuf path and python enabled $./configure --with-libfixbuf=/usr/local/lib/pkgconfig/ --with-python 4. Make and install the package $ make $ sudo make install You will know that SiLK has installed properly if you see a SiLK summary commands, like that shown below: 8
9 With everything installed, you need to make sure that all of the libraries we need are linked properly so that the LD_LIBRARY_PATH variable doesn t have to be exported each time you use SiLK. This is can be done by creating a file named silk.conf in the /etc/ld.so.conf.d/ directory with the following contents: /usr/local/lib /usr/local/lib/silk To apply this change, run: $ sudo ldconfig Configuring Now you have to configure SiLK to use rwflowpack to collect the flow data you generate. You need three files to make this happen: silk.conf, sensors.conf, and rwflowpack.conf. NOTE: In what follows, whenever you see <$SENSOR-$INTERFACE> it stands for SecurityOnion-eth0. Silk.conf You will start by creating the silk.conf site configuration file. This file controls how SiLK parses data, and contains a list of sensors. It can be found in the previously unzipped SiLK installation tarball at silk /site/twoway/silk.conf. You need to copy it to a directory that Security Onion uses to store several other configuration files: $ sudo cp silk.conf /etc/nsm/<$sensor-$interface>/ 9
10 Sensors.conf The sensor configuration file sensors.conf is used to define the sensors that will be generating session data, and their characteristics. This file should be created at /etc/nsm/<$sensor-$interface>/sensors.conf. For this example, your sensors.conf will look like this: probe S0 ipfix listen-on-port protocol tcp listen-as-host end probe group my-network ipblocks /24 ipblocks /24 end group sensor S0 ipfix-probes S0 external-ipblocks remainder end sensor This sensors.conf has three different sections: probe, group, and sensor. The probe section tells SiLK where to expect to receive data from for the identified sensor. Here, you ve identified sensor S0, and told SiLK to expect to receive ipfix data from this sensor via the TCP protocol over port You ve also defined the IP address of the sensor as the IPv4 address of the collector, The group section allows you to create a variable containing IP Blocks. Because of the way SiLK bins flow data, it is important to define internal and external network ranges on a per sensor basis so that your queries that are based upon flow direction (inbound, outbound, inbound web traffic, outbound web traffic, etc.) are accurate. In your configuration, you ve defined a group called my-network that has two ipblocks, /24 and /24. The last section is the sensor section, which you use to define the characteristics of the S0 sensor. Here you have specified that the sensor 10
11 will be generating IPFIX data, and that my-network group defines the internal IP ranges for the sensor, with the remainder being considered external. When it is all completed, your file should look like the below in the correct location: Rwflowpack.conf The last configuration step is to modify rwflowpack.conf, which is the configuration file for the rwflowpack process that listens for and collects flow records. This file can be found at /usr/local/share/silk/etc/rwflowpack.conf. First, you need to copy this file to /etc/nsm/<$sensor-$interface>/ $ sudo cp /usr/local/share/silk/etc/rwflowpack.conf /etc/nsm/<$sensor- $INTERFACE>/ Now you need to change seven values in the newly copied file: ENABLED=yes This will enable rwflowpack statedirectory=/nsm/sensor_data/<$sensor-$interface>/silk 11
12 A convenience variable used for setting the location of other various SiLK files and folders CREATE_DIRECTORIES=yes This will allow for the creation of specified data subdirectories SENSOR_CONFIG=/etc/nsm/<$SENSOR-$INTERFACE>/sensors.conf The path to the sensor configuration file DATA_ROOTDIR=/nsm/sensor_data/<$SENSOR-$INTERFACE>/silk/ The base directory for SiLK data storage SITE_CONFIG=/etc/nsm/<$SENSOR-$INTERFACE>/silk.conf The path to the site configuration file LOG_TYPE=legacy Sets the logging format to legacy LOG_DIR=/var/log/ The path for log storage Finally, you need to copy rwflowpack startup script into init.d so that you can start it like a normal service. This command will do that: $ sudo cp /usr/local/share/silk/etc/init.d/rwflowpack /etc/init.d Once you ve copied this file, you need to change one path in it. Open the file, and replace the code where SCRIPT_CONFIG is set to read: SCRIPT_CONFIG= /etc/nsm//<$sensor-$interface>/rwflowpack.conf Starting Everything Up Now that everything is configured, you should be able to start rwflowpack and YAF and begin collecting data. First, you can start rwflowpack by simply typing the following: $ sudo service rwflowpack start If everything went well, you should see a success message OK like that shown on the following page. 12
13 Cautions - When creating the silk.conf file, make sure you are in the right directory. - To edit the contents of the silk.conf file you will need to ensure that you elevate your privileges using sudo otherwise it will only open as read only given the directory you are in. - Be cautious when you are walking through the setup. During this time it might be possible that your network interfaces change certain settings that are required. After the reboot be sure that your network interfaces are set to Promiscuous mode: Allow All. - Additionally, if your rwflowpack does not start for some reason the first place you want to look at for errors is in the log file which is located at: /var/log/rwflowpack-[date].log. - You might also check that the eth0 still has the IP address To be able to use the data collected to perform common network auditing tasks. Approach - Execution Now that your collector is waiting for data, you can start YAF to begin generating flow data. Begin by installing YAF, libfixbuf and Silk on the Ubuntu-LAN machine, like you did with SecurityOnion. Once you have installed these, the same way in which you did for your Ubuntu machine, you need to make some additional alterations to your SecurityOnion machine. That machine also has an inbuilt firewall called 13
14 ufw. [EXPAND ON UFW HERE]. Go back to your SecurityOnion machine and add the following rules: $ ufw allow 18001/tcp $ ufw allow 1234 These two rules will allow tcp connections on port through, which will be used by your sensors, and allow connections on port 1234 that is going to be part of your testing. Once you have done so it should look like the below: Now that is all complete you can now go ahead and run the command needed for YAF to work. On the Ubuntu-LAN machine, issue the following command: $ sudo nohup /usr/local/bin/yaf --silk --ipfix=tcp --live=pcap --output= ipfix-port= in=eth0 --applabel --max-payload=384 & You ll notice that several of the arguments you are calling in this YAF execution string match values you ve configured in your SiLK configuration files. You can verify that everything started up correctly by running ps aux to make sure that the process is running, as shown below: 14
15 If YAF doesn t appear to be running, you can check the nohup.out file for any error messages that might have been generated. That s it! If your sensor interface is seeing traffic, then YAF should begin generating IPFIX flow data and sending it to rwflowpack for collection. You have to tell the SiLK rwtools where the site configuration file is on your SecurityOnion machine. This can be done by exporting the SILK_CONFIG_FILE variable. $ export SILK_CONFIG_FILE=/etc/nsm/<$SENSOR-$INTERFACE>/silk.conf $ export SILK_DATA_ROOTDIR=/nsm/sensor_data/<$SENSOR-$INTERFACE>/silk/ If you don t want to have to do the above every time you log into the system, you can place these lines in your ~/.bashrc file. You should be able to use rwfilter now. If everything is setup correctly and you are capturing data, you should see some output from this command: $ rwfilter --sensor=s0 --proto= type=all --pass=stdout rwcut The next step is to make several different web connections from the LAN machine to various Internet websites and also use nc to make several different connection on a range of ports. This will show you how it can be successfully parse lots of different type of data to show you relevant information. On your SecurityOnion machine issue the various commands below in order to collect three different types of information: 15
16 Use SiLK to analyse the top web site addresses accessed. Go back onto your Ubuntu-LAN machine and start browsing a number of different websites. Be sure to visit your popular websites more than once for the purposes of this part of the exercise. Once you ve done that after 5-10 minutes of activity go back to your SecurityOnion machine and issue the following command: $ rwfilter --sensor=s0 --application=80,443 --proto= type=all --pass=stdout rwstats --top --count=20 --fields=sip,dip,sport,dport,duration,application --value=records > TopWebsites There are two different types of switches for the rwfilter command; selection and partitioning switches. Select switches can determine the type of collection on which sensor to process along with the flow direction of the traffic. Partitioning switches on the other hand allows you to set what type of traffic behaviour is in the pass file and the rest in the fail file, depending on if the traffic flow stream matches the requirements or not 2. The command above tells SiLK to use the sensor S0, the one that you had set up earlier on the Ubuntu-LAN machine, in order to inspect the packets and if it matches a traffic signature of either HTTP or HTTPS to process it as part of the pass file. This would be sent to standard out (the screen). It then gets piped through rwstats to commute a top list from the data in the pass file 3. It does this by counting the top 20 records with the fields source IP, destination IP, source port, destination port, duration of the flow and the application that was used. Finally all of the aggregated data got piped out to a file called TopWebsites which you can look at to see your data. The biggest issue with this command is the fact that are often so many other connections that are pulled when a user connects to a website that there is just a massive amount of different flows. The problem is one 2http://tools.netsa.cert.org/silk/rwfilter.html 3http://tools.netsa.cert.org/silk/rwstats.html 16
17 would not necessarily want to limit it to outgoing only because then you wouldn t see what was coming in, which is arguably more important. Look at the rwstats command and see what interesting statistics you can find out with the data that you have accumulated. Use SiLK to determine the total volume of data that was observed, minute by minute. rwfilter --sensor=s0 --application=80,443 --proto= type=all --pass=stdout rwcount --bin-size=60 > WebVolume Similar to the first command you can use rwfilter in the same manner as before to process certain data based on the web application. This time you should use rwcount as your piped filter because this allows flow records to be summarized across time 4 such as observing data minute by minute. The bin-size is set to 60 seconds because the default was 30 seconds and the output is sent to a file called WebVolume. Additionally, rwcount should be used in this instance because it automatically provides the records, bytes and packets as separate columns thus giveing a good visual representation of the total volume across different collection methods. This command is the easiest to read from a user point of view. You could quickly see the traffic by minute using a number of different methods. It told you the amount of packets, records and bytes in total for that minute. This would be a quick easy way to monitor your network traffic levels if there was a need. Use SiLK to analyse the time and volume of non-web traffic. Before you issue your next command, go back to your Ubuntu-LAN machine and setup an nc connection to the SecurityOnion machine. Set up the listener on the SecurityOnion machine and then start writing some example text between the two machines using nc. This should be enough to generate some data for the next example. 4https://tools.netsa.cert.org/silk/rwcount.html 17
18 rwfilter --sensor=s0 --sport=0-79,81-442, dport=0-79,81-442, proto= type=all --pass=stdout rwuniq --fields= sip,dip,sport,dport,stime,etime,duration,application --values=bytes,packets,records > Non-WebTraffic Trying to analyse the time and volume of non-web traffic is more challenging because you are endeavouring to find a way in which you can analyze both time and volume as well as discard any web traffic. In the example on the previous page it uses source and destination ports to exclude anything from or to ports 80 or 443. This should leave you with traffic relating to the nc commands that you sent using port 1234 and any other none related web traffic, such as DNS requests perhaps. The rwuniq command was implemented because this gives you the ability to use time and volume data in within the specified fields. In the example above the source IP, destination IP, source Port, destination Port, start Time of the flow, end Time of the flow, Duration of the flow and what application was used. Using all three different value types should hopefully allow you to get as much volume data as possible by using bytes, packets and records. All of the outputted data to Non-WebTraffic. Cautions (Optional) - Need to set up your WAN interface so that it uses DHCP on M0n0wall2. - Ensure that the DNS Forwarder is on with the M0n0wall2 machine. To understand the tradeoffs between full packet and session data capture with respect to network security monitoring. Approach - Execution You 18
19 - Cautions (Optional) Reflections 19
Configure YAF on the Bivio 2000 Series
 Configure YAF on the Bivio 2000 Series This wiki entry covers installing YAF on a Bivio 2000, collecting and transmitting the data to a SiLK Repository. The Bivio has up to six application processors which
Configure YAF on the Bivio 2000 Series This wiki entry covers installing YAF on a Bivio 2000, collecting and transmitting the data to a SiLK Repository. The Bivio has up to six application processors which
Netflow in Daily Information Security Operations
 Netflow in Daily Information Security Operations Mike Pochan Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 Copyright 2016 Carnegie Mellon University This material is based
Netflow in Daily Information Security Operations Mike Pochan Software Engineering Institute Carnegie Mellon University Pittsburgh, PA 15213 Copyright 2016 Carnegie Mellon University This material is based
LAN Setup Reflection
 LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection. Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external?
 LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
Fun with Flow. Richard Friedberg rf [at] cert.org Carnegie Mellon University
![Fun with Flow. Richard Friedberg rf [at] cert.org Carnegie Mellon University Fun with Flow. Richard Friedberg rf [at] cert.org Carnegie Mellon University](/thumbs/80/81762596.jpg) Fun with Flow Richard Friedberg rf [at] cert.org Objectives Flow Primer Why do I care? Tools Capabilities and examples Almost live demo Build it! Where to go for more 2 What is flow? The simple version:
Fun with Flow Richard Friedberg rf [at] cert.org Objectives Flow Primer Why do I care? Tools Capabilities and examples Almost live demo Build it! Where to go for more 2 What is flow? The simple version:
Wireless-G Router User s Guide
 Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
2 Installing the Software
 INSTALLING 19 2 Installing the Software 2.1 Installation Remember the hour or two of slogging through software installation I promised (or warned) you about in the introduction? Well, it s here. Unless
INSTALLING 19 2 Installing the Software 2.1 Installation Remember the hour or two of slogging through software installation I promised (or warned) you about in the introduction? Well, it s here. Unless
1 Installation (briefly)
 Jumpstart Linux Bo Waggoner Updated: 2014-09-15 Abstract A basic, rapid tutorial on Linux and its command line for the absolute beginner. Prerequisites: a computer on which to install, a DVD and/or USB
Jumpstart Linux Bo Waggoner Updated: 2014-09-15 Abstract A basic, rapid tutorial on Linux and its command line for the absolute beginner. Prerequisites: a computer on which to install, a DVD and/or USB
iptables and ip6tables An introduction to LINUX firewall
 7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
6.1. Getting Started Guide
 6.1 Getting Started Guide Netmon Getting Started Guide 2 Contents Contents... 2 Appliance Installation... 3 IP Address Assignment (Optional)... 3 Logging In For the First Time... 5 Initial Setup... 6 License
6.1 Getting Started Guide Netmon Getting Started Guide 2 Contents Contents... 2 Appliance Installation... 3 IP Address Assignment (Optional)... 3 Logging In For the First Time... 5 Initial Setup... 6 License
Bridge Cable User s Guide
 Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
InControl 2 Software Appliance Setup Guide
 InControl 2 Software Appliance Setup Guide (Last updated: 2017-11) Contents 1. Introduction Minimum Hardware Requirements 2. For VMware ESXi 6.0 and ESXi 5.5 (SCSI) Networking Creating InControl and DB
InControl 2 Software Appliance Setup Guide (Last updated: 2017-11) Contents 1. Introduction Minimum Hardware Requirements 2. For VMware ESXi 6.0 and ESXi 5.5 (SCSI) Networking Creating InControl and DB
SiLK Installation Handbook SiLK
 SiLK Installation Handbook SiLK-3.16.0 CERT Coordination Center c 2003 2017 Carnegie Mellon University License available in Appendix D The canonical location for this handbook is http://tools.netsa.cert.org/silk/silk-install-handbook.pdf
SiLK Installation Handbook SiLK-3.16.0 CERT Coordination Center c 2003 2017 Carnegie Mellon University License available in Appendix D The canonical location for this handbook is http://tools.netsa.cert.org/silk/silk-install-handbook.pdf
Installation and Setup Guide
 Installation and Setup Guide to Diana SUNDE VDI Cloud Computing Terminal 1 1 Hardware Configuration of Host PC (Server)----------------------------------------------------3 2 The Installation of vpoint
Installation and Setup Guide to Diana SUNDE VDI Cloud Computing Terminal 1 1 Hardware Configuration of Host PC (Server)----------------------------------------------------3 2 The Installation of vpoint
ELE409 SPRING2018 LAB0
 ELE409 SPRING2018 LAB0 Getting familiar with the LXDE system Objectives: Pre-Lab: 1. Burn the linux system onto a micro-sd card 2. Get familiar with basic linux commands 3. Be able to communicate with
ELE409 SPRING2018 LAB0 Getting familiar with the LXDE system Objectives: Pre-Lab: 1. Burn the linux system onto a micro-sd card 2. Get familiar with basic linux commands 3. Be able to communicate with
OpenStack Havana All-in-One lab on VMware Workstation
 OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
Installing Altiris Agent on Ubuntu
 Installing Altiris Agent on Ubuntu DISCLAIMER: Altiris does not warrant that their software will run on Ubuntu using the Unix Agent version 6.2, which as of publication of this article, is the latest release.
Installing Altiris Agent on Ubuntu DISCLAIMER: Altiris does not warrant that their software will run on Ubuntu using the Unix Agent version 6.2, which as of publication of this article, is the latest release.
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
AimSniff. Jason Healy, Director of Networks and Systems
 AimSniff Jason Healy, Director of Networks and Systems Last Updated Mar 18, 2008 2 Contents 1 AimSniff 5 1.1 Introduction.............................. 5 1.2 Dependencies............................. 5
AimSniff Jason Healy, Director of Networks and Systems Last Updated Mar 18, 2008 2 Contents 1 AimSniff 5 1.1 Introduction.............................. 5 1.2 Dependencies............................. 5
How to install the software of ZNS8022
 How to install the software of ZNS8022 1. Please connect ZNS8022 to your PC after finished assembly. 2. Insert Installation CD to your CD-ROM drive and initiate the auto-run program. The wizard will run
How to install the software of ZNS8022 1. Please connect ZNS8022 to your PC after finished assembly. 2. Insert Installation CD to your CD-ROM drive and initiate the auto-run program. The wizard will run
Using RDP with Azure Linux Virtual Machines
 Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
R: A Proposed Analysis and Visualization Environment for Network Security Data
 R: A Proposed Analysis and Visualization Environment for Network Security Data Josh McNutt 2005 Carnegie Mellon University Outline SiLK Tools Analyst s Desktop Introduction to R R-SiLK
R: A Proposed Analysis and Visualization Environment for Network Security Data Josh McNutt 2005 Carnegie Mellon University Outline SiLK Tools Analyst s Desktop Introduction to R R-SiLK
Getting Started with the Deployment Console and Deploying the Clients Per PXE Network Booting using their MAC address. Quick Guide
 Getting Started with the Deployment Console and Deploying the Clients Per PXE Network Booting using their MAC address Quick Guide Deployment Manager 2 Quick Guide 1 Introduction...3 1.1 Installing the
Getting Started with the Deployment Console and Deploying the Clients Per PXE Network Booting using their MAC address Quick Guide Deployment Manager 2 Quick Guide 1 Introduction...3 1.1 Installing the
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Getting Started Guide. Installation and Setup Instructions. For version Copyright 2009 Code 42 Software, Inc. All rights reserved
 Installation and Setup Instructions For version 06.11.2009 Copyright 2009 Code 42 Software, Inc. All rights reserved About This Guide This guide shows you how to install, activate and back up with CrashPlan
Installation and Setup Instructions For version 06.11.2009 Copyright 2009 Code 42 Software, Inc. All rights reserved About This Guide This guide shows you how to install, activate and back up with CrashPlan
WA2592 Applied Data Science and Big Data Analytics. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc.
 WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
This material is based on work supported by the National Science Foundation under Grant No
 Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
NSX-T Upgrade Guide. VMware NSX-T 2.1
 VMware NSX-T 2.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to docfeedback@vmware.com
VMware NSX-T 2.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to docfeedback@vmware.com
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
User Guide NAS 3.0 Adapter (NAS30U2)
 T E C H N O L O G I E S User Guide NAS 3.0 Adapter (NAS30U2) www.addonics.com v5.1.11 Technical Support If you need any assistance to get your unit functioning properly, please have your product information
T E C H N O L O G I E S User Guide NAS 3.0 Adapter (NAS30U2) www.addonics.com v5.1.11 Technical Support If you need any assistance to get your unit functioning properly, please have your product information
OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE. In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses:
 OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE VirtualBox Install VirtualBox In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses: 192.168.1.2/24 192.168.2.2/24 192.168.3.2/24
OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE VirtualBox Install VirtualBox In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses: 192.168.1.2/24 192.168.2.2/24 192.168.3.2/24
Lab #5 Guide: Installing Ubuntu as a Virtual Machine
 Lab #5 Guide: Installing Ubuntu as a Virtual Machine CTEC1863/2018F Operating Systems Mike Boldin Tools, Materials and Equipment Oracle VirtualBox software official site: https://www.virtualbox.org/wiki/downloads
Lab #5 Guide: Installing Ubuntu as a Virtual Machine CTEC1863/2018F Operating Systems Mike Boldin Tools, Materials and Equipment Oracle VirtualBox software official site: https://www.virtualbox.org/wiki/downloads
Setting Up U P D AT E D 1 / 3 / 1 6
 Setting Up A GUIDE TO SETTING UP YOUR VIRTUAL MACHINE FOR PYTHON U P D AT E D 1 / 3 / 1 6 Why use a virtual machine? Before we begin, some motivation. Python can be installed on your host OS and many of
Setting Up A GUIDE TO SETTING UP YOUR VIRTUAL MACHINE FOR PYTHON U P D AT E D 1 / 3 / 1 6 Why use a virtual machine? Before we begin, some motivation. Python can be installed on your host OS and many of
COMPUTER NETWORKS. CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary
 COMPUTER NETWORKS CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary Introduction: Wireshark and tshark Running tshark Running Wireshark Exercise: Analyze HTTP traffic
COMPUTER NETWORKS CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary Introduction: Wireshark and tshark Running tshark Running Wireshark Exercise: Analyze HTTP traffic
We want to install putty, an ssh client on the laptops. In the web browser goto:
 We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
LENOVO THINKSTATION P520C, P520, P720, & P920 WINDOWS 10 INSTALLATION
 LENOVO THINKSTATION P520C, P520, P720, & P920 WINDOWS 10 INSTALLATION Contents OVERVIEW SECTION 1 BIOS & PRE-INSTALLATION STEPS SECTION 2 WINDOWS 10 INSTALLATION SECTION 3 WINDOWS 10 UPGRADE USING MEDIA
LENOVO THINKSTATION P520C, P520, P720, & P920 WINDOWS 10 INSTALLATION Contents OVERVIEW SECTION 1 BIOS & PRE-INSTALLATION STEPS SECTION 2 WINDOWS 10 INSTALLATION SECTION 3 WINDOWS 10 UPGRADE USING MEDIA
Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 3: Simulating DHCP Snooping and DNS Cache Poisoning through
Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 3: Simulating DHCP Snooping and DNS Cache Poisoning through
VIRTUALIZATION MANAGER ENTERPRISE EDITION GETTING STARTED GUIDE. Product: Virtual Iron Virtualization Manager Version: 4.2
 VIRTUALIZATION MANAGER ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron Virtualization Manager to configure
VIRTUALIZATION MANAGER ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron Virtualization Manager to configure
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability.
 CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
Protocol Analysis: Capturing Packets
 Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
Lab E2: bypassing authentication and resetting passwords
 Lab E2: bypassing authentication and resetting passwords TTM4175 September 7, 2015 The purpose of this lab is to learn about techniques for bypassing the authentication and access control of Windows and
Lab E2: bypassing authentication and resetting passwords TTM4175 September 7, 2015 The purpose of this lab is to learn about techniques for bypassing the authentication and access control of Windows and
CS356 Lab NIL (Lam) In this lab you will learn: Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore!
 CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
Inception Cloud User s Guide
 Inception Cloud User s Guide 1 Overview Creating an inception cloud consists of preparing your workstation, preparing the VM environment by adding a temporary boot-up machine, and then executing the orchestrator
Inception Cloud User s Guide 1 Overview Creating an inception cloud consists of preparing your workstation, preparing the VM environment by adding a temporary boot-up machine, and then executing the orchestrator
Install the Marionnet network simulator on Kali Linux Light vbox-i686
 Install the Marionnet network simulator on Kali Linux Light 2017.1-vbox-i686 August 26, 2017 by Lucian Visinescu (this work is licensed under CC BY-NC 4.0) This installation is based on Install the Marionnet
Install the Marionnet network simulator on Kali Linux Light 2017.1-vbox-i686 August 26, 2017 by Lucian Visinescu (this work is licensed under CC BY-NC 4.0) This installation is based on Install the Marionnet
Welcome to getting started with Ubuntu Server. This System Administrator Manual. guide to be simple to follow, with step by step instructions
 Welcome to getting started with Ubuntu 12.04 Server. This System Administrator Manual guide to be simple to follow, with step by step instructions with screenshots INDEX 1.Installation of Ubuntu 12.04
Welcome to getting started with Ubuntu 12.04 Server. This System Administrator Manual guide to be simple to follow, with step by step instructions with screenshots INDEX 1.Installation of Ubuntu 12.04
EAN-Network Configuration
 EAN-Network Configuration PN: EAN-Network-Configuration 1/25/2018 SightLine Applications, Inc. Contact: Web: sightlineapplications.com Sales: sales@sightlineapplications.com Support: support@sightlineapplications.com
EAN-Network Configuration PN: EAN-Network-Configuration 1/25/2018 SightLine Applications, Inc. Contact: Web: sightlineapplications.com Sales: sales@sightlineapplications.com Support: support@sightlineapplications.com
Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development
 Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Deploy the ExtraHop Discover Appliance with Hyper-V
 Deploy the ExtraHop Discover Appliance with Hyper-V Published: 2018-07-16 The following procedures explain how to deploy the ExtraHop Discover EDA 1000v and EDA 2000v virtual appliance on the Microsoft
Deploy the ExtraHop Discover Appliance with Hyper-V Published: 2018-07-16 The following procedures explain how to deploy the ExtraHop Discover EDA 1000v and EDA 2000v virtual appliance on the Microsoft
Operating Systems Lab 1. Class topic: Installation of the operating system. Install Ubuntu on Oracle VirtualBox
 Operating Systems Lab 1 Class topic: Installation of the operating system. Install Ubuntu on Oracle VirtualBox Oracle VirtualBox is a cross-platform virtualization application. It installs on your existing
Operating Systems Lab 1 Class topic: Installation of the operating system. Install Ubuntu on Oracle VirtualBox Oracle VirtualBox is a cross-platform virtualization application. It installs on your existing
Creating and Managing a Content Server Cluster
 CHAPTER 10 This chapter describes the main features, system requirements, setup, and management of a Cisco TelePresence Content Server (TCS) cluster. To a user, a Content Server Cluster behaves exactly
CHAPTER 10 This chapter describes the main features, system requirements, setup, and management of a Cisco TelePresence Content Server (TCS) cluster. To a user, a Content Server Cluster behaves exactly
How to Dual-Boot OS X and Ubuntu
 How to Dual-Boot OS X and Ubuntu Nailen Matschke - nailen@caltech.edu 10/3/2015 What you need: 1. A USB drive with at least 2 GB of space, that you don t mind wiping 2. A copy of Ubuntu (available here),
How to Dual-Boot OS X and Ubuntu Nailen Matschke - nailen@caltech.edu 10/3/2015 What you need: 1. A USB drive with at least 2 GB of space, that you don t mind wiping 2. A copy of Ubuntu (available here),
Installing Komplete 5 with Direct Install
 Installing Komplete 5 with Direct Install This document discusses how to use Receptor s Direct Install feature to install and update Komplete 5, its plugins, and its libraries. In order to install Komplete
Installing Komplete 5 with Direct Install This document discusses how to use Receptor s Direct Install feature to install and update Komplete 5, its plugins, and its libraries. In order to install Komplete
Installation of the DigitalSystemsVM virtual machine
 Installation of the DigitalSystemsVM virtual machine Notice This document explains how to install the DigitalSystemsVM virtual machine on a computer with Linux Ubuntu 16.04 LTS. If questions or problems
Installation of the DigitalSystemsVM virtual machine Notice This document explains how to install the DigitalSystemsVM virtual machine on a computer with Linux Ubuntu 16.04 LTS. If questions or problems
Installation Manual InfraManage.NET Installation Instructions for Ubuntu
 Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Networks Lab Pod Diagram
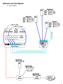 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
VI. Corente Services Client
 VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
How to Install a DHCP Server in Ubuntu and Debian
 How to Install a DHCP Server in Ubuntu and Debian Source : https://www.tecmint.com/install-dhcp-server-in-ubuntu-debian/ Dynamic Host Configuration Protocol (DHCP) is a network protocol that is used to
How to Install a DHCP Server in Ubuntu and Debian Source : https://www.tecmint.com/install-dhcp-server-in-ubuntu-debian/ Dynamic Host Configuration Protocol (DHCP) is a network protocol that is used to
halef Documentation ETS
 ETS Apr 02, 2018 Contents 1 OpenVXML Without Tears 1 2 Halef Setup Process 19 i ii CHAPTER 1 OpenVXML Without Tears 1 Authors Vikram Ramanarayanan and Eugene Tsuprun (with inputs from the OpenVXML Setup
ETS Apr 02, 2018 Contents 1 OpenVXML Without Tears 1 2 Halef Setup Process 19 i ii CHAPTER 1 OpenVXML Without Tears 1 Authors Vikram Ramanarayanan and Eugene Tsuprun (with inputs from the OpenVXML Setup
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine
 IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
Once the VM is started, the VirtualBox OS Manager window can be closed. But our Ubuntu VM is still running.
 How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
Contents. Note: pay attention to where you are. Note: Plaintext version. Note: pay attention to where you are... 1 Note: Plaintext version...
 Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
bitcurator-access-webtools Quick Start Guide Last updated: May 8th, 2018 Release(s): and later
 bitcurator-access-webtools Quick Start Guide Last updated: May 8th, 2018 Release(s): 0.8.2 and later About bitcurator-access-webtools The bitcurator-access-webtools service allows users to browse file
bitcurator-access-webtools Quick Start Guide Last updated: May 8th, 2018 Release(s): 0.8.2 and later About bitcurator-access-webtools The bitcurator-access-webtools service allows users to browse file
Firewall Policy. Edit Firewall Policy/ACL CHAPTER7. Configure a Firewall Before Using the Firewall Policy Feature
 CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
Port Forwarding & Case Study
 Introduction TalkTalk's responsibility lies with ensuring that this facility works on their routers, they cannot be held responsible for you devices that you are trying to forward to. This document not
Introduction TalkTalk's responsibility lies with ensuring that this facility works on their routers, they cannot be held responsible for you devices that you are trying to forward to. This document not
MP01 Quick Start Guide
 MP01 Quick Start Guide Version: V2.0 2011-10-12 Table of Contents MP01 QUICK START GUIDE... 2 1. USE MP01 TO SET UP A WIFI TELEPHONY NETWORK AND MAKE INTERNAL PHONE CALLS... 2 1.1 STEP 1-LOGIN TO THE MP01
MP01 Quick Start Guide Version: V2.0 2011-10-12 Table of Contents MP01 QUICK START GUIDE... 2 1. USE MP01 TO SET UP A WIFI TELEPHONY NETWORK AND MAKE INTERNAL PHONE CALLS... 2 1.1 STEP 1-LOGIN TO THE MP01
Deploy the ExtraHop Discover Appliance with Hyper-V
 Deploy the ExtraHop Discover Appliance with Hyper-V Published: 2018-12-14 The following procedures explain how to deploy the ExtraHop Discover EDA 1000v and EDA 2000v virtual appliance on the Microsoft
Deploy the ExtraHop Discover Appliance with Hyper-V Published: 2018-12-14 The following procedures explain how to deploy the ExtraHop Discover EDA 1000v and EDA 2000v virtual appliance on the Microsoft
VIRTUALIZATION MANAGER ENTERPRISE EDITION GETTING STARTED GUIDE
 VIRTUALIZATION MANAGER ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron Virtualization Manager to configure
VIRTUALIZATION MANAGER ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron Virtualization Manager to configure
Labtainer Student Guide
 Labtainer Student Guide January 18, 2018 1 Introduction This manual is intended for use by students performing labs with Labtainers. Labtainers assume you have a Linux system, e.g., a virtual machine.
Labtainer Student Guide January 18, 2018 1 Introduction This manual is intended for use by students performing labs with Labtainers. Labtainers assume you have a Linux system, e.g., a virtual machine.
Open a browser and download the Apache Tomcat 7 and Oracle JDBC 6 JAR from these locations. The Oracle site may require that you register as a user.
 Installing Tomcat 7 on CentOS 7 David J. Walling, March 8 th, 2017 Email: david@davidjwalling.com This how to describes a process to download and install Apache Tomcat 7 on a CentOS 7 virtual machine using
Installing Tomcat 7 on CentOS 7 David J. Walling, March 8 th, 2017 Email: david@davidjwalling.com This how to describes a process to download and install Apache Tomcat 7 on a CentOS 7 virtual machine using
Lab 14 - Introduction to the PABLO Payload Autonomy Computer
 Lab 14 - Introduction to the PABLO Payload Autonomy Computer 2.680 Unmanned Marine Vehicle Autonomy, Sensing and Communications Spring, 2018 Michael Benjamin, mikerb@mit.edu Paul Robinette, paulrobi@mit.edu
Lab 14 - Introduction to the PABLO Payload Autonomy Computer 2.680 Unmanned Marine Vehicle Autonomy, Sensing and Communications Spring, 2018 Michael Benjamin, mikerb@mit.edu Paul Robinette, paulrobi@mit.edu
Building a 64-bit CentOS 7 Workstation using Oracle Virtual Box
 Building a 64-bit CentOS 7 Workstation using Oracle Virtual Box jthomas Enterprises, 2016 Building a CentOS 7 Workstation using Oracle VirtualBox 1 Section 1 Before You Begin This section details the environment
Building a 64-bit CentOS 7 Workstation using Oracle Virtual Box jthomas Enterprises, 2016 Building a CentOS 7 Workstation using Oracle VirtualBox 1 Section 1 Before You Begin This section details the environment
ROCK-POND REPORTING 2.1
 ROCK-POND REPORTING 2.1 Installation and Setup Guide Revised on 09/25/2014 TABLE OF CONTENTS ROCK-POND REPORTING 2.1... 1 SUPPORT FROM ROCK-POND SOLUTIONS... 2 ROCK-POND REPORTING OVERVIEW... 2 INFRASTRUCTURE
ROCK-POND REPORTING 2.1 Installation and Setup Guide Revised on 09/25/2014 TABLE OF CONTENTS ROCK-POND REPORTING 2.1... 1 SUPPORT FROM ROCK-POND SOLUTIONS... 2 ROCK-POND REPORTING OVERVIEW... 2 INFRASTRUCTURE
Install some base packages. I recommend following this guide as root on a new VPS or using sudo su, it will make running setup just a touch easier.
 Nagios 4 on Ubuntu 16 Install some base packages. I recommend following this guide as root on a new VPS or using sudo su, it will make running setup just a touch easier. apt-get install php-gd build-essential
Nagios 4 on Ubuntu 16 Install some base packages. I recommend following this guide as root on a new VPS or using sudo su, it will make running setup just a touch easier. apt-get install php-gd build-essential
VI-CENTER EXTENDED ENTERPRISE EDITION GETTING STARTED GUIDE. Version: 4.5
 VI-CENTER EXTENDED ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron VI-Center to configure and manage virtual
VI-CENTER EXTENDED ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron VI-Center to configure and manage virtual
Dark Web Investigation Setup Guide.
 Dark Web Investigation Setup Guide www.hunch.ly What the hell is the dark web? There is a lot of confusion about what the dark web is vs. the deep web. The dark web is part of the Internet that is not
Dark Web Investigation Setup Guide www.hunch.ly What the hell is the dark web? There is a lot of confusion about what the dark web is vs. the deep web. The dark web is part of the Internet that is not
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
The Python Mini-Degree Development Environment Guide
 The Python Mini-Degree Development Environment Guide By Zenva Welcome! We are happy to welcome you to the premiere Python development program available on the web The Python Mini-Degree by Zenva. This
The Python Mini-Degree Development Environment Guide By Zenva Welcome! We are happy to welcome you to the premiere Python development program available on the web The Python Mini-Degree by Zenva. This
WiSE-MNet. Wireless Simulation Environment for Multimedia Networks. User s Manual. Christian Nastasi
 WiSE-MNet Wireless Simulation Environment for Multimedia Networks User s Manual Christian Nastasi (c.nastasi@sssup.it, nastasichr@gmail.com) December 4, 2011 Contents 1 Introduction 1 2 Overview 2 2.1
WiSE-MNet Wireless Simulation Environment for Multimedia Networks User s Manual Christian Nastasi (c.nastasi@sssup.it, nastasichr@gmail.com) December 4, 2011 Contents 1 Introduction 1 2 Overview 2 2.1
Installing MediaWiki using VirtualBox
 Installing MediaWiki using VirtualBox Install VirtualBox with your package manager or download it from the https://www.virtualbox.org/ website and follow the installation instructions. Load an Image For
Installing MediaWiki using VirtualBox Install VirtualBox with your package manager or download it from the https://www.virtualbox.org/ website and follow the installation instructions. Load an Image For
NSX-T Upgrade Guide. VMware NSX-T 2.0
 VMware NSX-T 2.0 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to docfeedback@vmware.com
VMware NSX-T 2.0 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to docfeedback@vmware.com
Linux Essentials Objectives Topics:
 Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Share Drobo on a Network: Apple Airport Extreme
 D R O B O A P P L I C A T I O N N O T E S E R I E S Share Drobo on a Network: Apple Airport Extreme This application note describes how we at Data Robotics share files wirelessly that are stored on a Drobo
D R O B O A P P L I C A T I O N N O T E S E R I E S Share Drobo on a Network: Apple Airport Extreme This application note describes how we at Data Robotics share files wirelessly that are stored on a Drobo
Installing NS-2 on Ubuntu & 12.10
 Installing NS-2 on Ubuntu 10.04 & 12.10 for windows users from the ground up Eslam Mostafa Mahmoud Ayman Mahmoud Ezz Mahmoud Mohsen Mahmoud Rashad Mostafa Kishk gp.team.2013@gmail.com Contents Introduction...
Installing NS-2 on Ubuntu 10.04 & 12.10 for windows users from the ground up Eslam Mostafa Mahmoud Ayman Mahmoud Ezz Mahmoud Mohsen Mahmoud Rashad Mostafa Kishk gp.team.2013@gmail.com Contents Introduction...
The instructions in this document are applicable to personal computers running the following Operating Systems:
 Preliminary Notes The instructions in this document are applicable to personal computers running the following Operating Systems: Microsoft Windows from version 7 up to 10 Apple Mac OS X from versions
Preliminary Notes The instructions in this document are applicable to personal computers running the following Operating Systems: Microsoft Windows from version 7 up to 10 Apple Mac OS X from versions
Without further ado, let s go over and have a look at what I ve come up with.
 JIRA Integration Transcript VLL Hi, my name is Jonathan Wilson and I m the service management practitioner with NHS Digital based in the United Kingdom. NHS Digital is the provider of services to the National
JIRA Integration Transcript VLL Hi, my name is Jonathan Wilson and I m the service management practitioner with NHS Digital based in the United Kingdom. NHS Digital is the provider of services to the National
Installation and Setup Guide
 Installation and Setup Guide to Diana SUNDE VDI Cloud Computing Terminal Contents 1 Host PC (or Server) hardware Configuration Requirements...3 2 Installation of vpoint version 1.1.0.10...3 2.1 Installation
Installation and Setup Guide to Diana SUNDE VDI Cloud Computing Terminal Contents 1 Host PC (or Server) hardware Configuration Requirements...3 2 Installation of vpoint version 1.1.0.10...3 2.1 Installation
WA2393 Data Science for Solution Architects. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2393 Data Science for Solution Architects Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2393 Data Science for Solution Architects Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
APPENDIX B: INSTALLATION AND SETUP
 APPENDIX B: INSTALLATION AND SETUP Page A. Overview... B:1 How do I install and setup ICMS?... B:1 Do I need special security rights to install ICMS?... B:1 Installation Basics... B:1 How do I get a quick
APPENDIX B: INSTALLATION AND SETUP Page A. Overview... B:1 How do I install and setup ICMS?... B:1 Do I need special security rights to install ICMS?... B:1 Installation Basics... B:1 How do I get a quick
Orchid Core VMS Installation Guide
 Orchid Core VMS Installation Guide Version 2.2.2 Orchid Core VMS Installation Guide v2.2.2 1 C O N T E N T S About the Orchid Core VMS Installation Guide 2 Installation 3 Working in Windows 3 Working in
Orchid Core VMS Installation Guide Version 2.2.2 Orchid Core VMS Installation Guide v2.2.2 1 C O N T E N T S About the Orchid Core VMS Installation Guide 2 Installation 3 Working in Windows 3 Working in
Lab 2: Creating Secure Architectures
 Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Print Audit 6. Print Audit 6 Documentation Apr :07. Version: Date:
 Print Audit 6 Version: Date: 37 21-Apr-2015 23:07 Table of Contents Browse Documents:..................................................... 3 Database Documentation.................................................
Print Audit 6 Version: Date: 37 21-Apr-2015 23:07 Table of Contents Browse Documents:..................................................... 3 Database Documentation.................................................
Install and Configure Ubuntu on a VirtualBox Virtual Machine
 Install and Configure Ubuntu on a VirtualBox Virtual Machine Ronald Mak Department of Computer Engineering Department of Computer Science January 11, 2019 Introduction Because the class will use Linux
Install and Configure Ubuntu on a VirtualBox Virtual Machine Ronald Mak Department of Computer Engineering Department of Computer Science January 11, 2019 Introduction Because the class will use Linux
CROWDCOIN MASTERNODE SETUP COLD WALLET ON WINDOWS WITH LINUX VPS
 CROWDCOIN MASTERNODE SETUP COLD WALLET ON WINDOWS WITH LINUX VPS This tutorial shows the steps required to setup your Crowdcoin Masternode on a Linux server and run your wallet on a Windows operating system
CROWDCOIN MASTERNODE SETUP COLD WALLET ON WINDOWS WITH LINUX VPS This tutorial shows the steps required to setup your Crowdcoin Masternode on a Linux server and run your wallet on a Windows operating system
Agility2018-TCPdump Documentation
 Agility2018-TCPdump Documentation Release.01 David Larsen Aug 10, 2018 Switches 1 F5 tcpdump and Wireshark 3 1.1 tcpdump Switches............................................ 3 1.2 tcpdump Filters..............................................
Agility2018-TCPdump Documentation Release.01 David Larsen Aug 10, 2018 Switches 1 F5 tcpdump and Wireshark 3 1.1 tcpdump Switches............................................ 3 1.2 tcpdump Filters..............................................
PVS Deployment in the Cloud. Last Updated: June 17, 2016
 PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
PVS Deployment in the Cloud Last Updated: June 17, 2016 Contents Amazon Web Services Introduction 3 Software Requirements 4 Set up a NAT Gateway 5 Install PVS on the NAT Gateway 11 Example Deployment 12
VPN and GNU/Linux at the University of South Wales
 VPN and GNU/Linux at the University of South Wales These notes are designed to help staff and research students at the University of South Wales connect to their desktop machines using GNU/Linux. You will
VPN and GNU/Linux at the University of South Wales These notes are designed to help staff and research students at the University of South Wales connect to their desktop machines using GNU/Linux. You will
WA2342 NoSQL Systems Comparison. Lab Server VM Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
DFL-700 FAQ ? 6) The service I need to use is not listed in the group of pre-defined services. How do I create a custom
 DFL-700 FAQ Table of Contents Page 1) How do I do a factory reset 2 2) How do you backup the DFL-700 s configuration? 2 3) How do I block URLs using the Content Filtering function? 3 4) How do I limit
DFL-700 FAQ Table of Contents Page 1) How do I do a factory reset 2 2) How do you backup the DFL-700 s configuration? 2 3) How do I block URLs using the Content Filtering function? 3 4) How do I limit
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
