TechTip: How to Secure the Web Query Login Page (or Any Other Web-Based Application)
|
|
|
- Abraham Riley
- 6 years ago
- Views:
Transcription
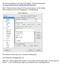
1 TechTip: How to Secure the Web Query Login Page (or Any Other Web-Based Application) Published Thursday, 05 March :00 by MC Press On-line [Reprinted with permission from itechnology Manager, published by MC Press, LP; Written by Robert Andrews- Add another layer of security to all of your Web applications. The IBM i is a great platform for running Web applications. These applications can take advantage of Apache, PHP, and MySQL, all running natively on IBM i. Or you may be using a purchased application such as DB2 Web Query for IBM i. One common thread amongst them is that they can use the IBM i user profiles and passwords. This is both a blessing and a curse. While it allows for fewer user profiles for the end user, it also exposes your administrative user profiles, such as QSECOFR. A user at the login screen could put in QSECOFR, make three wrong guesses at the password, and lock out the account. In this TechTip, I will provide a method of securing these Web-based login interfaces. The method to accomplish this is to first present the users with a login and password box that does not authenticate against user profiles. Once they pass this first challenge, they will then be presented with the application login, which does go against their user profiles. As an example, I will be using the DB2 Web Query application. The first step is to create a validation list. This is done via the Create Validation List command: CRTVLDL VLDL(MYLIB/WEBQUERY) You then need to make sure that the application can read the list. Therefore, you need to grant *PUBLIC *USE authority: GRTOBJAUT OBJ(MYLIB/WEBQUERY) OBJTYPE(*VLDL) USER(*PUBLIC) AUT(*USE) Working with validations from a command line is impossible. There are APIs that can be called, but those would require you to write a program. Luckily, the HTTP Administration tool provides a GUI to work with them. From a Web browser, go to Log in and click the Advanced section on top. From there, click Internet Users and Groups in the second row. In the task list on the left will be an option to Add Internet User. Here, you set the user name and password you want from the users before they get access to the real application login page. For the validation list parameter, enter mylib/webquery (as shown in Figure 1). Click Apply to add the user name. You can add as many user names as you like.
2 Figure 1: Add an Internet user. Now that you have the validation list created, you need to set the Web application to use it. For this, go to the Apache configuration. On the top bar, select Setup. On the second bar, select HTTP Servers. From the drop-down box for Server, select the Web instance for your application. Here, for Web Query, I selected WQLWI7. Since security is set at the location level, select the location drop-down and change it to the Web server root, /. If you want more-granular control, you can add locations by selecting Container Management on the left and then the Locations tab. Once you are at Location /, select Security on the left and choose the Authentication tab. Set the User authentication method to Internet users in the validation list. Enter the realm name for the application. This is used in the login prompt that is presented to the users. Keep in mind they will not see the Web application yet when they are prompted for this user name and password. You will see this in Figure 5 below. Click Add to get a line for a new authorization list. Again, point to your validation list as mylib/webquery and click Continue and Apply.
3 Figure 2: Choose authentication settings. Click on the Control Access tab to put your new authentication settings to work. When we define Web security, it is based on two factors: who and where. Normally, these are set to anyone from anywhere. However, you now want to tell the application to allow access from anywhere provided the users can authenticate to the validation list. To do this, change the "who" section to require authentication: a valid user name and password. Remember from Figure 2, we told the application to look at the validation list for valid user authentication. This is shown in Figure 3. Figure 3: Control access for "who." You don't need to adjust the "where" setting. By default, it is set to allow access from anywhere. However, if you wanted to further secure it by allowing only certain IP addresses, you could. You could use this to limit access only to users while in the office or to a set of certain IP addresses. The last step is to tell the application to enforce both the who (someone on our validation list) and the where (anywhere) as shown in Figure 4. If you set the control access policy to who or where, then
4 everyone would pass the where test and not be prompted. Again, you could get fancy here by not prompting people in the office while prompting those coming from the public Internet. Apply your changes. Figure 4: Choose your control access policy. Since these changes update the Apache configuration file, you need to restart your Web server for the changes to be picked up. Once you do, when users attempt to log in to the Web application, they will first be presented with the pop-up login box shown in Figure 5. Here, you can see where the realm name is shown. Figure 5: Internet users can now log in. Once the users provide a valid login and password from the validation list, they are presented with the Web application login page. Here, we can see Web Query as a sample. This login then uses the IBM i user profiles and passwords.
5 Figure 6: Users can log in to Web Query with their IBM i user profiles. In this TechTip, I introduced you to an additional layer of security that you can add to your Web applications. While I provided a very basic example, I hope to have caught your interest in the various other ways you can add security to your Web-based applications.
TechTip: Exploit DB2 Web Query's Defined and Computed Fields
 TechTip: Exploit DB2 Web Query's Defined and Computed Fields Published Thursday, 04 September 2008 19:00 by MC Press On-line [Reprinted with permission from itechnology Manager, published by MC Press,
TechTip: Exploit DB2 Web Query's Defined and Computed Fields Published Thursday, 04 September 2008 19:00 by MC Press On-line [Reprinted with permission from itechnology Manager, published by MC Press,
Installation guide for Choic Multi User Edition
 Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Configuration of Microsoft SQL Server Express
 Configuration of Microsoft SQL Server Express Copyright 2017 NetSupport Ltd All rights reserved Configuration of Microsoft SQL Server Express and NetSupport DNA Installation Requirements If installing
Configuration of Microsoft SQL Server Express Copyright 2017 NetSupport Ltd All rights reserved Configuration of Microsoft SQL Server Express and NetSupport DNA Installation Requirements If installing
Using Jive for Outlook
 Using Jive for Outlook TOC 2 Contents Using Jive for Outlook...3 Client System Requirements... 3 Getting Started with Jive for Outlook... 3 Jview and View as email...4 Viewing Social Information... 4 Finding
Using Jive for Outlook TOC 2 Contents Using Jive for Outlook...3 Client System Requirements... 3 Getting Started with Jive for Outlook... 3 Jview and View as email...4 Viewing Social Information... 4 Finding
Setting up the Master Computer
 Setting up the Master Computer for gofish the O FISH-AL Sales Program Be forwarned, non-technical translation for what is to come: blah, blah, doze off and blah-blah. Last updated March 12, 2016 I appologize
Setting up the Master Computer for gofish the O FISH-AL Sales Program Be forwarned, non-technical translation for what is to come: blah, blah, doze off and blah-blah. Last updated March 12, 2016 I appologize
9.0 Help for End Users Release Notes Using Jive for Outlook...5
 Contents 2 Contents 9.0 Help for End Users... 3 Release Notes... 4 Using Jive for Outlook...5 Client System Requirements...5 Getting Started with Jive for Outlook...5 Jview and View as email... 7 Viewing
Contents 2 Contents 9.0 Help for End Users... 3 Release Notes... 4 Using Jive for Outlook...5 Client System Requirements...5 Getting Started with Jive for Outlook...5 Jview and View as email... 7 Viewing
#Uncomment the second line to enable any form of FTP write command. #write_enable=yes
 Installing and configuring Apache 2 in Linux Please note that dashes (-) are used to indicate what you should type, they should not be included in the command. Install Linux on an old desktop, dual core
Installing and configuring Apache 2 in Linux Please note that dashes (-) are used to indicate what you should type, they should not be included in the command. Install Linux on an old desktop, dual core
The SOAPbox User s Guide
 The SOAPbox User s Guide Application Documentation Version 1.3 THE SOCIAL FOUNDRY November 9, 2012 The SOAPbox User s Guide Application Documentation Version 1.3 Congratulations on your purchase of the
The SOAPbox User s Guide Application Documentation Version 1.3 THE SOCIAL FOUNDRY November 9, 2012 The SOAPbox User s Guide Application Documentation Version 1.3 Congratulations on your purchase of the
Hello, and welcome to the Alexicomtech tutorial. I will show you step by step how to set up your interactive pages. Please feel free to ask questions
 Hello, and welcome to the Alexicomtech tutorial. I will show you step by step how to set up your interactive pages. Please feel free to ask questions at any time. The first step is to open your internet
Hello, and welcome to the Alexicomtech tutorial. I will show you step by step how to set up your interactive pages. Please feel free to ask questions at any time. The first step is to open your internet
Xton Access Manager GETTING STARTED GUIDE
 Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
EXERCISE 3: PUBLISHING AN ODM DATABASE WITH WATERONEFLOW
 EXERCISE 3: PUBLISHING AN ODM DATABASE WITH WATERONEFLOW As far as your local setup goes, you are now ready for action with your ODM database. But what if you want to share the data with others online?
EXERCISE 3: PUBLISHING AN ODM DATABASE WITH WATERONEFLOW As far as your local setup goes, you are now ready for action with your ODM database. But what if you want to share the data with others online?
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
Installing Oxwall completely in Amazon Cloud
 Contents Installing Oxwall completely in Amazon Cloud... 1 PART 1 Creating AWS Instance... 1 Section 1 Security Group... 1 Section 2 - A LAMP-friendly instance... 2 Section 3 - The Elastic IP... 5 PART
Contents Installing Oxwall completely in Amazon Cloud... 1 PART 1 Creating AWS Instance... 1 Section 1 Security Group... 1 Section 2 - A LAMP-friendly instance... 2 Section 3 - The Elastic IP... 5 PART
You will need to enter your outgoing mail server information, here is a list of common outgoing mail servers for free accounts:
 MacTrak Installation Guide 1. Run the installer (Note: When installation is complete the system will need to be rebooted, please make sure you save and close any other applications running on your system)
MacTrak Installation Guide 1. Run the installer (Note: When installation is complete the system will need to be rebooted, please make sure you save and close any other applications running on your system)
Infoblox Authenticated DHCP
 Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Setting up a database for multi-user access
 BioNumerics Tutorial: Setting up a database for multi-user access 1 Aims There are several situations in which multiple users in the same local area network (LAN) may wish to work with a shared BioNumerics
BioNumerics Tutorial: Setting up a database for multi-user access 1 Aims There are several situations in which multiple users in the same local area network (LAN) may wish to work with a shared BioNumerics
RoomWizard. Instructions for Lotus Domino Synchronization Software Installation
 RoomWizard Instructions for Lotus Domino Synchronization Software Installation RoomWizard TM Instructions for Lotus Domino Synchronization Software Installation Part number 370-0156-05 2017 Steelcase Corporation
RoomWizard Instructions for Lotus Domino Synchronization Software Installation RoomWizard TM Instructions for Lotus Domino Synchronization Software Installation Part number 370-0156-05 2017 Steelcase Corporation
Pastel Evolution BIC Web Reporting User Guide
 Pastel Evolution BIC Web Reporting User Guide Prerequisites: Pastel Evolution Business Intelligence Centre.NET Framework 3.5 Internet Information Services (version 6 and upwards) Microsoft Excel 2003 /
Pastel Evolution BIC Web Reporting User Guide Prerequisites: Pastel Evolution Business Intelligence Centre.NET Framework 3.5 Internet Information Services (version 6 and upwards) Microsoft Excel 2003 /
Joomla 3.X Global Settings Part III Server Settings
 Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
SETUP FOR OUTLOOK (Updated October, 2018)
 EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
INSTALLING RACHEL ON SYNOLOGY GIAKONDA IT
 INSTALLING RACHEL ON SYNOLOGY GIAKONDA IT To add RACHEL to a Synology server there are a few stages to go through. First we need to ready the server for web use. Then we have to obtain a copy of the RACHEL
INSTALLING RACHEL ON SYNOLOGY GIAKONDA IT To add RACHEL to a Synology server there are a few stages to go through. First we need to ready the server for web use. Then we have to obtain a copy of the RACHEL
HelpAndManual_illegal_keygen Contactor Elite Autoresponder Installation Guide
 HelpAndManual_illegal_keygen Contactor Elite Autoresponder Guide HelpAndManual_illegal_keygen Contactor Elite Autoresponder Autoresponder and Newsletter Delivery System To most web sites, their mailing
HelpAndManual_illegal_keygen Contactor Elite Autoresponder Guide HelpAndManual_illegal_keygen Contactor Elite Autoresponder Autoresponder and Newsletter Delivery System To most web sites, their mailing
Integrating SAS Analytics into Your Web Page
 Paper SAS2145-2018 Integrating SAS Analytics into Your Web Page James Kochuba and David Hare, SAS Institute Inc. ABSTRACT SAS Viya adds enhancements to the SAS Platform that include the ability to access
Paper SAS2145-2018 Integrating SAS Analytics into Your Web Page James Kochuba and David Hare, SAS Institute Inc. ABSTRACT SAS Viya adds enhancements to the SAS Platform that include the ability to access
Administration Guide
 Administration Guide This guide will cover how to customize and lock down the SCOM 2012 Maintenance Mode Scheduler for your end users. Table of Contents Customize Look and Feel... 2 Enable Auditing of
Administration Guide This guide will cover how to customize and lock down the SCOM 2012 Maintenance Mode Scheduler for your end users. Table of Contents Customize Look and Feel... 2 Enable Auditing of
Users Guide. Kerio Technologies
 Users Guide Kerio Technologies C 1997-2006 Kerio Technologies. All rights reserved. Release Date: June 8, 2006 This guide provides detailed description on Kerio WebSTAR 5, version 5.4. Any additional modifications
Users Guide Kerio Technologies C 1997-2006 Kerio Technologies. All rights reserved. Release Date: June 8, 2006 This guide provides detailed description on Kerio WebSTAR 5, version 5.4. Any additional modifications
Relativity's mobile app Guide
 Relativity's mobile app Guide March 2, 2016 - Version 1.1 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Relativity's mobile app Guide March 2, 2016 - Version 1.1 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
WA1973 IBM Business Process Manager 8.0 Programming Using IBM Integration Designer. Classroom Setup Guide. Web Age Solutions Inc.
 WA1973 IBM Business Process Manager 8.0 Programming Using IBM Integration Designer Classroom Setup Guide Web Age Solutions Inc. Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware...3
WA1973 IBM Business Process Manager 8.0 Programming Using IBM Integration Designer Classroom Setup Guide Web Age Solutions Inc. Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware...3
Installing MediaWiki using VirtualBox
 Installing MediaWiki using VirtualBox Install VirtualBox with your package manager or download it from the https://www.virtualbox.org/ website and follow the installation instructions. Load an Image For
Installing MediaWiki using VirtualBox Install VirtualBox with your package manager or download it from the https://www.virtualbox.org/ website and follow the installation instructions. Load an Image For
Mysql Tutorial Create Database Username Password Through Phpmyadmin
 Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Adobe Sign for MS Dynamics 365 CRM
 Adobe Sign for MS Dynamics 365 CRM User Guide v7 Last Updated: May 31, 2018 2018 Adobe Systems Incorporated. All rights reserved Contents Overview... 3 Gaining Access to Adobe Sign...4 Sending for Signature...
Adobe Sign for MS Dynamics 365 CRM User Guide v7 Last Updated: May 31, 2018 2018 Adobe Systems Incorporated. All rights reserved Contents Overview... 3 Gaining Access to Adobe Sign...4 Sending for Signature...
How to Integrate an External Authentication Server
 How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
Your . A setup guide. Last updated March 7, Kingsford Avenue, Glasgow G44 3EU
 fuzzylime WE KNOW DESIGN WEB DESIGN AND CONTENT MANAGEMENT 19 Kingsford Avenue, Glasgow G44 3EU 0141 416 1040 hello@fuzzylime.co.uk www.fuzzylime.co.uk Your email A setup guide Last updated March 7, 2017
fuzzylime WE KNOW DESIGN WEB DESIGN AND CONTENT MANAGEMENT 19 Kingsford Avenue, Glasgow G44 3EU 0141 416 1040 hello@fuzzylime.co.uk www.fuzzylime.co.uk Your email A setup guide Last updated March 7, 2017
Install Apache, PHP And MySQL On CentOS 7 (LAMP)
 Install Apache, PHP And MySQL On CentOS 7 (LAMP) Version 1.0 Authors: Till Brehm , Falko Timme Updates: Srijan Kishore Follow Howtoforge
Install Apache, PHP And MySQL On CentOS 7 (LAMP) Version 1.0 Authors: Till Brehm , Falko Timme Updates: Srijan Kishore Follow Howtoforge
9.4 Authentication Server
 9 Useful Utilities 9.4 Authentication Server The Authentication Server is a password and account management system for multiple GV-VMS. Through the Authentication Server, the administrator can create the
9 Useful Utilities 9.4 Authentication Server The Authentication Server is a password and account management system for multiple GV-VMS. Through the Authentication Server, the administrator can create the
MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL. 31 January 2017
 MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL 31 January 2017 Contents 1 Introduction... 2 1.1 Prerequisite for configuring the multi-factor authentication:... 2 1.1.1 On the Guest side... 2 1.1.2
MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL 31 January 2017 Contents 1 Introduction... 2 1.1 Prerequisite for configuring the multi-factor authentication:... 2 1.1.1 On the Guest side... 2 1.1.2
SynwaySMS SMS Center. User Manual
 SynwaySMS SMS Center User Manual Version: 1.0.0.0 Synway Information Engineering Co., Ltd Content Content... 1 1 Brief Introduction... 2 2 SynwaySMS Installation... 3 3 SynwaySMS Management... 7 3.1 Login...
SynwaySMS SMS Center User Manual Version: 1.0.0.0 Synway Information Engineering Co., Ltd Content Content... 1 1 Brief Introduction... 2 2 SynwaySMS Installation... 3 3 SynwaySMS Management... 7 3.1 Login...
Interim Registration
 Interim Registration Students will need to do two things with Banner Web to register for an Interim project: Look at the descriptions of the projects and write down the project name and Course Reference
Interim Registration Students will need to do two things with Banner Web to register for an Interim project: Look at the descriptions of the projects and write down the project name and Course Reference
Lesson 3 Transcript: Part 1 of 2 - Tools & Scripting
 Lesson 3 Transcript: Part 1 of 2 - Tools & Scripting Slide 1: Cover Welcome to lesson 3 of the db2 on Campus lecture series. Today we're going to talk about tools and scripting, and this is part 1 of 2
Lesson 3 Transcript: Part 1 of 2 - Tools & Scripting Slide 1: Cover Welcome to lesson 3 of the db2 on Campus lecture series. Today we're going to talk about tools and scripting, and this is part 1 of 2
Configuring Anonymous Access to Analysis Files in TIBCO Spotfire 7.5
 Configuring Anonymous Access to Analysis Files in TIBCO Spotfire 7.5 Introduction Use Cases for Anonymous Authentication Anonymous Authentication in TIBCO Spotfire 7.5 Enabling Anonymous Authentication
Configuring Anonymous Access to Analysis Files in TIBCO Spotfire 7.5 Introduction Use Cases for Anonymous Authentication Anonymous Authentication in TIBCO Spotfire 7.5 Enabling Anonymous Authentication
Destiny Library Manager
 Destiny Library Manager Setting Up One Search Your teachers and students can take advantage of your school s subscription databases all in one place through Destiny One Search. One Search saves staff and
Destiny Library Manager Setting Up One Search Your teachers and students can take advantage of your school s subscription databases all in one place through Destiny One Search. One Search saves staff and
NextMD Patient Portal Guide
 Internet Security Below are some suggestions to help keep your health information secure: Use a password that is easy to remember but difficult for others to guess. Some web browsers will ask you to save
Internet Security Below are some suggestions to help keep your health information secure: Use a password that is easy to remember but difficult for others to guess. Some web browsers will ask you to save
PHP: Cookies, Sessions, Databases. CS174. Chris Pollett. Sep 24, 2008.
 PHP: Cookies, Sessions, Databases. CS174. Chris Pollett. Sep 24, 2008. Outline. How cookies work. Cookies in PHP. Sessions. Databases. Cookies. Sometimes it is useful to remember a client when it comes
PHP: Cookies, Sessions, Databases. CS174. Chris Pollett. Sep 24, 2008. Outline. How cookies work. Cookies in PHP. Sessions. Databases. Cookies. Sometimes it is useful to remember a client when it comes
Introduction to Office 365 and OneDrive
 Introduction to Office 365 and OneDrive What is Office 365? Office 365 is a web-based service that provides anywhere-access to documents and Microsoft Office tools and applications such as Word, Excel,
Introduction to Office 365 and OneDrive What is Office 365? Office 365 is a web-based service that provides anywhere-access to documents and Microsoft Office tools and applications such as Word, Excel,
Install latest version of Roundcube (Webmail) on CentOS 7
 Install latest version of Roundcube (Webmail) on CentOS 7 by Pradeep Kumar Published December 14, 2015 Updated August 3, 2017 Roundcube is a web browser based mail client & also known as webmail. It provides
Install latest version of Roundcube (Webmail) on CentOS 7 by Pradeep Kumar Published December 14, 2015 Updated August 3, 2017 Roundcube is a web browser based mail client & also known as webmail. It provides
Developing Secure IBM i Applications
 Developing Secure IBM i Applications Introductions Design and Documentation Application Ownership and Authority A Simple Security Model Integrity Considerations Resources for Security Officers Questions
Developing Secure IBM i Applications Introductions Design and Documentation Application Ownership and Authority A Simple Security Model Integrity Considerations Resources for Security Officers Questions
Developing Secure Applications for IBM i
 Developing Secure Applications for IBM i Introductions Design and Documentation Application Ownership and Authority A Simple Security Model Integrity Considerations Resources for Security Officers Questions
Developing Secure Applications for IBM i Introductions Design and Documentation Application Ownership and Authority A Simple Security Model Integrity Considerations Resources for Security Officers Questions
Zephyr Cloud for HipChat
 June 25 Zephyr Cloud for HipChat Z e p h y r, 7 7 0 7 G a t e w a y B l v d S t e 1 0 0, N e w a r k, C A 9 4 5 6 0, U S A 1 - Overview How this guide will help Zephyr Cloud for HipChat guide will guide
June 25 Zephyr Cloud for HipChat Z e p h y r, 7 7 0 7 G a t e w a y B l v d S t e 1 0 0, N e w a r k, C A 9 4 5 6 0, U S A 1 - Overview How this guide will help Zephyr Cloud for HipChat guide will guide
SharePoint. Team Site End User Guide. Table of Contents
 Table of Contents Introduction... 1 Logging in for the First Time:... 1 Areas of the team site:... 2 Navigating the team site:... 3 Adding Content to the team site:... 3 The Ribbon:... 3 Adding a Link:...
Table of Contents Introduction... 1 Logging in for the First Time:... 1 Areas of the team site:... 2 Navigating the team site:... 3 Adding Content to the team site:... 3 The Ribbon:... 3 Adding a Link:...
ISBG May LDAP: It s Time. Gabriella Davis - Technical Director The Turtle Partnership
 ISBG May 2015 LDAP: It s Time Gabriella Davis - Technical Director The Turtle Partnership gabriella@turtlepartnership.com What Is LDAP? Lightweight Directory Access Protocol Standard language for reading
ISBG May 2015 LDAP: It s Time Gabriella Davis - Technical Director The Turtle Partnership gabriella@turtlepartnership.com What Is LDAP? Lightweight Directory Access Protocol Standard language for reading
Orgnazition of This Part
 Orgnazition of This Part Table of Contents Tutorial: Organization of This Part...1 Lesson 1: Starting JReport Enterprise Server and Viewing Reports...3 Introduction...3 Installing JReport Enterprise Server...3
Orgnazition of This Part Table of Contents Tutorial: Organization of This Part...1 Lesson 1: Starting JReport Enterprise Server and Viewing Reports...3 Introduction...3 Installing JReport Enterprise Server...3
With IBM BPM 8.5.5, the features needed to express both BPM solutions and case management oriented solutions comes together in one offering.
 Case Management With the release of IBM BPM 8.5.5, case management capabilities were added to the product. It must be noted that these functions are only available with IBM BPM Advanced and the Basic Case
Case Management With the release of IBM BPM 8.5.5, case management capabilities were added to the product. It must be noted that these functions are only available with IBM BPM Advanced and the Basic Case
WorldCat Knowledge Base Release Notes for Contents
 WorldCat Knowledge Base Release Notes for 2014-07-27 Contents New Features... 2 Knowledge Base Cooperative Data Management: Phase Three... 2 Enhancements... 3 Migration to WorldShare Interface Complete...
WorldCat Knowledge Base Release Notes for 2014-07-27 Contents New Features... 2 Knowledge Base Cooperative Data Management: Phase Three... 2 Enhancements... 3 Migration to WorldShare Interface Complete...
Real Application Security Administration
 Oracle Database Real Application Security Administration Console (RASADM) User s Guide 12c Release 2 (12.2) E85615-01 June 2017 Real Application Security Administration Oracle Database Real Application
Oracle Database Real Application Security Administration Console (RASADM) User s Guide 12c Release 2 (12.2) E85615-01 June 2017 Real Application Security Administration Oracle Database Real Application
Overview of Web Interface to CenturyLink B2B Gateway
 Overview of Web Interface to CenturyLink B2B Gateway Access and Password Policy for the Web Interface Like all Internet sites, the CenturyLink B2B web site requires an account containing both an identity
Overview of Web Interface to CenturyLink B2B Gateway Access and Password Policy for the Web Interface Like all Internet sites, the CenturyLink B2B web site requires an account containing both an identity
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
Configuring ILMT/TAD4d security to use Active Directory.
 Configuring ILMT/TAD4d security to use Active Directory. Warning: Please bear in mind that this is a technical note, and it is not a part of the official documentation. The described procedure may work
Configuring ILMT/TAD4d security to use Active Directory. Warning: Please bear in mind that this is a technical note, and it is not a part of the official documentation. The described procedure may work
Logging In - Administrators
 Logging In - Administrators On this page: The ADAMS URL The ADAMS Login Providing contact details Providing your email address or mobile number Validating your email address or mobile phone number Alternate
Logging In - Administrators On this page: The ADAMS URL The ADAMS Login Providing contact details Providing your email address or mobile number Validating your email address or mobile phone number Alternate
Media Services Online Mohammed Abukhiran. Report 13 on the work of Week 13
 Media Services Online Mohammed Abukhiran Report 13 on the work of Week 13 Berea College Nov 30, 2010 Application Development Project Concept Proposal Media Services at Berea College uses Voyger (Database
Media Services Online Mohammed Abukhiran Report 13 on the work of Week 13 Berea College Nov 30, 2010 Application Development Project Concept Proposal Media Services at Berea College uses Voyger (Database
Enhancing cloud applications by using external authentication services. 2015, 2016 IBM Corporation
 Enhancing cloud applications by using external authentication services After you complete this section, you should understand: Terminology such as authentication, identity, and ID token The benefits of
Enhancing cloud applications by using external authentication services After you complete this section, you should understand: Terminology such as authentication, identity, and ID token The benefits of
WebDirect Configuration Guide
 WebDirect Configuration Guide (The following graphics are screen shots from Microsoft ISA Server 2004/2006 which is the property of Microsoft Corp. and are included here for instructive use. Some images
WebDirect Configuration Guide (The following graphics are screen shots from Microsoft ISA Server 2004/2006 which is the property of Microsoft Corp. and are included here for instructive use. Some images
We want to install putty, an ssh client on the laptops. In the web browser goto:
 We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
Table of Contents. 2 P a g e A I M Q U I C K R E F E R E N C E G U I D E
 May 2017 Table of Contents Introduction... 3 Accessing the My ARKIVE Portal... 3 The Dashboard... 4 Accessing AIM... 4 Searching/Filtering Inventory... 5 Adding New Inventory. 9 Work Orders... 11 Adding
May 2017 Table of Contents Introduction... 3 Accessing the My ARKIVE Portal... 3 The Dashboard... 4 Accessing AIM... 4 Searching/Filtering Inventory... 5 Adding New Inventory. 9 Work Orders... 11 Adding
USING DIRECT DATABASE DRIVERS
 USING DIRECT DATABASE 1 DRIVERS Overview 2 S-PLUS Commands for Importing and Exporting 3 Dialogs for Importing and Exporting 6 Import From Database 6 Export to Database 10 How Direct Data Sources are Stored
USING DIRECT DATABASE 1 DRIVERS Overview 2 S-PLUS Commands for Importing and Exporting 3 Dialogs for Importing and Exporting 6 Import From Database 6 Export to Database 10 How Direct Data Sources are Stored
How to Get a Free Account
 1 How to Get a Free Email Account This is a free service. You will not be charged in any way to use this service. If you choose this option and signup you can get your email anywhere at home, work, on
1 How to Get a Free Email Account This is a free service. You will not be charged in any way to use this service. If you choose this option and signup you can get your email anywhere at home, work, on
Envision Access Setup Guide
 Envision Access Setup Guide How To Setup Employees For Envision Access 2 EnvisionAccess Setup Guide Employee Setup EnvisionAccess Once a technician has Installed EnvisionAccess you can begin your setup
Envision Access Setup Guide How To Setup Employees For Envision Access 2 EnvisionAccess Setup Guide Employee Setup EnvisionAccess Once a technician has Installed EnvisionAccess you can begin your setup
Basic, Step-by-Step Installation Manual
 Basic, Step-by-Step Installation Manual Introduction The purpose of this document is to provide very detailed, step-by-step instructions for installing the software that someone with limited technical
Basic, Step-by-Step Installation Manual Introduction The purpose of this document is to provide very detailed, step-by-step instructions for installing the software that someone with limited technical
SBCC Web File System - Xythos
 Table of Contents Table of Contents...1 Purpose...1 Login Procedure...1 Creating and Sharing a Web Folder for MAT153...2 Dreamweaver Remote Info...4 I Forgot My Pipeline Credentials...6 Purpose This purpose
Table of Contents Table of Contents...1 Purpose...1 Login Procedure...1 Creating and Sharing a Web Folder for MAT153...2 Dreamweaver Remote Info...4 I Forgot My Pipeline Credentials...6 Purpose This purpose
Navigate to Cognos Cognos Analytics supports all browsers with the exception of Microsoft Edge.
 IBM Cognos Analytics Create a Crosstab The following instructions cover how to create a crosstab report in IBM Cognos Analytics. A crosstab is a report type in Cognos that displays an analytical look at
IBM Cognos Analytics Create a Crosstab The following instructions cover how to create a crosstab report in IBM Cognos Analytics. A crosstab is a report type in Cognos that displays an analytical look at
Using MS OneDrive for Business
 Using MS OneDrive for Business OneDrive for Business is a perfect place to store all of your documents in the cloud. They will always be at your fingertips whether you are on a laptop, an IPad or your
Using MS OneDrive for Business OneDrive for Business is a perfect place to store all of your documents in the cloud. They will always be at your fingertips whether you are on a laptop, an IPad or your
PHP for PL/SQL Developers. Lewis Cunningham JP Morgan Chase
 PHP for PL/SQL Developers Lewis Cunningham JP Morgan Chase 1 What is PHP? PHP is a HTML pre-processor PHP allows you to generate HTML dynamically PHP is a scripting language usable on the web, the server
PHP for PL/SQL Developers Lewis Cunningham JP Morgan Chase 1 What is PHP? PHP is a HTML pre-processor PHP allows you to generate HTML dynamically PHP is a scripting language usable on the web, the server
SUPERHUB OFFICE 365 OUTLOOK POP3 SETUP GUIDE
 SUPERHUB OFFICE 365 OUTLOOK POP3 SETUP GUIDE 2018 Superhub Limited. All right reserved. Table of Contents 1. Get Started... 3 2. Add New Account... 5 3. Get Help and Support... 10 The guide is to describe
SUPERHUB OFFICE 365 OUTLOOK POP3 SETUP GUIDE 2018 Superhub Limited. All right reserved. Table of Contents 1. Get Started... 3 2. Add New Account... 5 3. Get Help and Support... 10 The guide is to describe
maxecurity Product Suite
 maxecurity Product Suite Domain Administrator s Manual Firmware v2.2 ii Table of Contents BASICS... 1 Understanding how maxecurity products work in your company... 1 Getting started as a Domain Administrator...
maxecurity Product Suite Domain Administrator s Manual Firmware v2.2 ii Table of Contents BASICS... 1 Understanding how maxecurity products work in your company... 1 Getting started as a Domain Administrator...
Licensing eggplant Functional
 Published on Documentation (http://docs.testplant.com) Home > Getting Started > Licensing Licensing Licensing eggplant Functional To run eggplant Functional on your machine, you must license it. If you
Published on Documentation (http://docs.testplant.com) Home > Getting Started > Licensing Licensing Licensing eggplant Functional To run eggplant Functional on your machine, you must license it. If you
ESS Security Enhancements
 ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
Remote Support DETAILS How to set up and connect
 Introduction Brainy's Useful Docs Remote Support DETAILS How to set up and connect Updated: 27 May 2009 It is possible to establish a remote connection between two computers over the internet for a variety
Introduction Brainy's Useful Docs Remote Support DETAILS How to set up and connect Updated: 27 May 2009 It is possible to establish a remote connection between two computers over the internet for a variety
DIRECTORY INTEGRATION: USING ACTIVE DIRECTORY FOR AUTHENTICATION. Gabriella Davis The Turtle Partnership
 DIRECTORY INTEGRATION: USING ACTIVE DIRECTORY FOR AUTHENTICATION Gabriella Davis The Turtle Partnership In This Session Review possible use cases for multiple directories Understand security implications
DIRECTORY INTEGRATION: USING ACTIVE DIRECTORY FOR AUTHENTICATION Gabriella Davis The Turtle Partnership In This Session Review possible use cases for multiple directories Understand security implications
ULTEO OPEN VIRTUAL DESKTOP DEBIAN WHEEZY (7.0) SUPPORT
 ULTEO OPEN VIRTUAL DESKTOP V4.0.2 DEBIAN WHEEZY (7.0) SUPPORT Contents 1 Prerequisites: Debian Wheezy (7.0) 3 1.1 System Requirements.............................. 3 2 Repository 4 2.1 Online Method..................................
ULTEO OPEN VIRTUAL DESKTOP V4.0.2 DEBIAN WHEEZY (7.0) SUPPORT Contents 1 Prerequisites: Debian Wheezy (7.0) 3 1.1 System Requirements.............................. 3 2 Repository 4 2.1 Online Method..................................
Virtual Loaner Program Using Save & Restore
 Virtual Loaner Program Using Save & Restore Author: Ram M Devulapalli Document Owner: Ram M Devulapalli Document Version 2.0 August 1 st, 2010. Copyright IBM Corp 2010-1 - Table of Contents Why use the
Virtual Loaner Program Using Save & Restore Author: Ram M Devulapalli Document Owner: Ram M Devulapalli Document Version 2.0 August 1 st, 2010. Copyright IBM Corp 2010-1 - Table of Contents Why use the
4D WebSTAR V User Guide for Mac OS. Copyright (C) D SA / 4D, Inc. All rights reserved.
 4D WebSTAR V User Guide for Mac OS Copyright (C) 2002 4D SA / 4D, Inc. All rights reserved. The software described in this manual is governed by the grant of license provided in this package. The software
4D WebSTAR V User Guide for Mac OS Copyright (C) 2002 4D SA / 4D, Inc. All rights reserved. The software described in this manual is governed by the grant of license provided in this package. The software
EventSentry Quickstart Guide
 Contents I Part I About This Guide 2 Part II Overview 3 Part III Installing EventSentry 6 1 Installation with... Setup 7 2 Management Application... 8 3 Configuration... 9 4 Remote Update... 12 5 Heartbeat
Contents I Part I About This Guide 2 Part II Overview 3 Part III Installing EventSentry 6 1 Installation with... Setup 7 2 Management Application... 8 3 Configuration... 9 4 Remote Update... 12 5 Heartbeat
Power Development Platform Connecting to your PDP system user guide
 Power Development Platform Connecting to your PDP system user guide Document Version 4 May 9, 2017 FOREWORD This document is intended for the users trying to access PDP for the first time. This document
Power Development Platform Connecting to your PDP system user guide Document Version 4 May 9, 2017 FOREWORD This document is intended for the users trying to access PDP for the first time. This document
Configuring an Enhanced Standard Security Policy
 Configuring an Enhanced Standard Security Policy What is an enhanced standard security policy? Implementing an enhanced standard security policy Configuring an Enhanced Standard Security Policy What is
Configuring an Enhanced Standard Security Policy What is an enhanced standard security policy? Implementing an enhanced standard security policy Configuring an Enhanced Standard Security Policy What is
Locate your Advanced Tools and Applications
 MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
Installation guide for Choic . Enterprise Edition. When Installing On The Same Server As: Microsoft s Exchange 2000 & 2003 Mail Servers
 Installation guide for ChoiceMail Enterprise Edition When Installing On The Same Server As: Microsoft s Exchange 2000 & 2003 Mail Servers May, 2004 Version 2.5.2 Table of Contents Page Downloading and
Installation guide for ChoiceMail Enterprise Edition When Installing On The Same Server As: Microsoft s Exchange 2000 & 2003 Mail Servers May, 2004 Version 2.5.2 Table of Contents Page Downloading and
Oracle Database. Installation and Configuration of Real Application Security Administration (RASADM) Prerequisites
 Oracle Database Real Application Security Administration 12c Release 1 (12.1) E61899-04 May 2015 Oracle Database Real Application Security Administration (RASADM) lets you create Real Application Security
Oracle Database Real Application Security Administration 12c Release 1 (12.1) E61899-04 May 2015 Oracle Database Real Application Security Administration (RASADM) lets you create Real Application Security
Revision 1.0v01 and above March 2012
 QueueIt! Chapter 1 Introduction QueueIt! Installation and User Guide Revision 1.0v01 and above March 2012 2012 Best Wave, LLC Scottsdale, AZ All Rights Reserved Worldwide Not to be reproduced in whole
QueueIt! Chapter 1 Introduction QueueIt! Installation and User Guide Revision 1.0v01 and above March 2012 2012 Best Wave, LLC Scottsdale, AZ All Rights Reserved Worldwide Not to be reproduced in whole
OmniFind, Part II: Integrating OmniFind Text Search Server with DB2 Web Query
 OmniFind, Part II: Integrating OmniFind Text Search Server with DB2 Web Query Published Wednesday, 08 July 2009 01:00 by MC Press On-line [Reprinted with permission from itechnology Manager, published
OmniFind, Part II: Integrating OmniFind Text Search Server with DB2 Web Query Published Wednesday, 08 July 2009 01:00 by MC Press On-line [Reprinted with permission from itechnology Manager, published
CPM Quick Start Guide V2.2.0
 CPM Quick Start Guide V2.2.0 1 Content 1 Introduction... 3 1.1 Launching the instance... 3 1.2 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 3 3 Creating a Simple Backup
CPM Quick Start Guide V2.2.0 1 Content 1 Introduction... 3 1.1 Launching the instance... 3 1.2 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 3 3 Creating a Simple Backup
Cloud UC. Program Downloads I WOULD LIKE TO... DOWNLOADING THE CLIENT SOFTWARE
 I WOULD LIKE TO... Cloud UC Program Downloads Avaya Cloud allows you to setup your telephone to be used the way you want it to. There are additional programs that extend the abilities of the application
I WOULD LIKE TO... Cloud UC Program Downloads Avaya Cloud allows you to setup your telephone to be used the way you want it to. There are additional programs that extend the abilities of the application
SWITS User Manual. Accessing SWITS. This document focuses on the elements required to Access SWITS. Total Pages: 5
 SWITS User Manual This document focuses on the elements required to Access SWITS Total Pages: 5 Accessing SWITS Using Your Browser to Access SWITS Identity Management Context Creating a shortcut California
SWITS User Manual This document focuses on the elements required to Access SWITS Total Pages: 5 Accessing SWITS Using Your Browser to Access SWITS Identity Management Context Creating a shortcut California
Part 1: Understanding Windows XP Basics
 542362 Ch01.qxd 9/18/03 9:54 PM Page 1 Part 1: Understanding Windows XP Basics 1: Starting Up and Logging In 2: Logging Off and Shutting Down 3: Activating Windows 4: Enabling Fast Switching between Users
542362 Ch01.qxd 9/18/03 9:54 PM Page 1 Part 1: Understanding Windows XP Basics 1: Starting Up and Logging In 2: Logging Off and Shutting Down 3: Activating Windows 4: Enabling Fast Switching between Users
Using SQL-server as database engine
 This tutorial explains on a step by step base how to configure YDOC-Insights for usage with a SQL-server database. (How to manage SQL-server itself is not part of this tutorial) CONTENTS CONTENTS 1 1.
This tutorial explains on a step by step base how to configure YDOC-Insights for usage with a SQL-server database. (How to manage SQL-server itself is not part of this tutorial) CONTENTS CONTENTS 1 1.
How do I connect to Peachtree using ODBC/OLEDB?
 Answer ID: 25514 Last Updated: 9/11/09 Summary: How do I connect to Peachtree using ODBC/OLEDB? Question: How do I connect to Peachtree using ODBC/OLEDB? Answer: Peachtree 2010 (Pro Accounting and later)
Answer ID: 25514 Last Updated: 9/11/09 Summary: How do I connect to Peachtree using ODBC/OLEDB? Question: How do I connect to Peachtree using ODBC/OLEDB? Answer: Peachtree 2010 (Pro Accounting and later)
Using the New UCOP UAT Validation Reports For Undergraduate Admissions
 To access the new UAT validation reports in Cognos for Course Enrollment data, please follow the instructions outlined below: 1. Copy and paste the following link into your browser - http://data.ucop.edu.
To access the new UAT validation reports in Cognos for Course Enrollment data, please follow the instructions outlined below: 1. Copy and paste the following link into your browser - http://data.ucop.edu.
WWPass External Authentication Solution for IBM Security Access Manager 8.0
 WWPass External Authentication Solution for IBM Security Access Manager 8.0 Setup guide Enhance your IBM Security Access Manager for Web with the WWPass hardware authentication IBM Security Access Manager
WWPass External Authentication Solution for IBM Security Access Manager 8.0 Setup guide Enhance your IBM Security Access Manager for Web with the WWPass hardware authentication IBM Security Access Manager
Lesson 7: Defining an Application
 35 Lesson 7: Defining an Application In this lesson, we will define two new applications in the realm server, with an endpoint for each application. We will also define two new transports to be used by
35 Lesson 7: Defining an Application In this lesson, we will define two new applications in the realm server, with an endpoint for each application. We will also define two new transports to be used by
Installation Guide For Choic . Enterprise Edition. When Installing On The Same Server As: Microsoft s Exchange 5.5 Mail Server
 Installation Guide For ChoiceMail Enterprise Edition When Installing On The Same Server As: Microsoft s Exchange 5.5 Mail Server May, 2004 Version 2.5.2 Table of Contents Page Downloading and Running the
Installation Guide For ChoiceMail Enterprise Edition When Installing On The Same Server As: Microsoft s Exchange 5.5 Mail Server May, 2004 Version 2.5.2 Table of Contents Page Downloading and Running the
Bitnami MariaDB for Huawei Enterprise Cloud
 Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
The Connector Version 2.0 Microsoft Project to Atlassian JIRA Connectivity
 The Connector Version 2.0 Microsoft Project to Atlassian JIRA Connectivity User Manual Ecliptic Technologies, Inc. Copyright 2011 Page 1 of 99 What is The Connector? The Connector is a Microsoft Project
The Connector Version 2.0 Microsoft Project to Atlassian JIRA Connectivity User Manual Ecliptic Technologies, Inc. Copyright 2011 Page 1 of 99 What is The Connector? The Connector is a Microsoft Project
OKTA users provisioning for Vable platform
 OKTA users provisioning for Vable platform Features Requirements Step-by-step Configuration Instructions Requesting Vable OKTA integration Adding Vable private application to organization account Configuring
OKTA users provisioning for Vable platform Features Requirements Step-by-step Configuration Instructions Requesting Vable OKTA integration Adding Vable private application to organization account Configuring
