Cubro Network Security Series
|
|
|
- Eric Walker
- 6 years ago
- Views:
Transcription
1 Cubro Security Series PRODUCT REVIEW Security At a glance In order to meet the demands of the operators and fastdeveloping network, Cubro delivers the network secure sockets layer analysis products -- NSA. Focusing on high performance real-time SSL decryption processing, NSA provides common encryption/decryption algorithm and supports SSL3.0/TLS1.0/TLS1.1/TLS1.2. In addition, NSA can restore the TCP data flow of the decrypted data and ensure the session integrity with new TCP sequences. Functions/Benefits: Built-in logical crypto acceleration engine, supporting common hash algorithms, symmetric key ciphers, and asymmetric key operations. SSL/TLS supported: SSL3.0, TLS1.0, TLS1.1, TLS1.2. Hash algorithms supported: SHA1, MD5, SHA256, SHA224, SHA384, SHA512, AES, HMAC. Symmetric key ciphers supported: DES CBC, 3DES CBC, AES-128 CBC, AES-256 CBC, RC4,RC2, IDEA... Asymmetric key operations: RSA and ECDH. Note: ECDH decryption is not supported. Key management: supporting key self-learning from private key list and binding specified IP address toprivate key. Flow restoration: when SSL/TLS is decrypted, NSA can rebuild the packets without SSL/TLS header and calculate TCP sequence and fix TCP/IP checksum. Definition A network securty appliance is a active or passive device which receives traffic from TAPs and Packet Brokers or from live links. Advantages of Cubro Probe Small foot print Low power design Empedded Processor design Can be customized to customer s requirement Support of any kind of SFP and SFP+ (also 10 Gbit BASE_T), 40 x 1/10 Gbit
2 PRODUCT CAPABILITIES / FEATURES Packets output: NSA can output encrypted flow and plain flow separately. Optionally, TCP port info can be modified from 443 to 80 as decryption is done. Session management: supporting TCP-reassembly such as out-of-order packets, TCP state tracking. SSL/TLS session correlating: correlating SSL/TLS sessions with session id or ticket when keys can be reused. Performance: decryption performance is 5Gbps with 10 millions of sessions online for NSA40 SSL Inspector Proxy 10GbE 10GbE Cleartext Tap ports Monitoring Device (i.e. WireShark) SSL Encrypted Packets from Hi-Perf TCP/IP SSL Server Proxy SSL Client Hi-Perf TCP/IP SSL Encrypted Packets toserver(s) Cleartext Tap Packets Multicor Processor 2
3 TECHNICAL DATA / SPECIFICATIONS INPUTS * Several 1, 10, interfaces can be used as inputs from TAPs or NPB. NSA 40D CPU 1 & CPU 2 connected via a internal Packetmaster On EXA40 and EXA40D a NPB is build in the probe. Managemt Ports 40 x 10 Gbit NSA 40 CPU 1 connected via a internal Packetmaster Managemt Ports 40 x 10 Gbit OUTPUTS * Several 1, 10, interfaces can be used as inputs from TAPs or NPB. Operating specifications: Operating Temperature: 0ºC to 45ºC Storage Temperature: -10ºC to 70ºC Relative Humidity: 10% min, 95% max Non-condensing Mechanical specifications: Dimension (HxWxD): W= mm, L=532 mm, H=44,4 mm Weight: 9,4 kg Electrical specifications: On EXA40 and EXA40D a NPB is build in the Security Appliance. PERFORMANCE Advanced multi core CPU design Lowest power usage per Gbit traffic processing in the Industry. Input Power: V, 2A, Hz V DC Maximum Power Consumption: W Certifications: Fully RoHS compliant CE compliant Safety - UL / CSA C / IEC (2005) EN (2006) MANAGEMENT Management Port: (1) RJ45 10/100/1000 Mbit Configuration (CLI) Port: (1) RS-232 DB9 USB 3.0 for software update INDICATORS Per RJ45 port: Speed, Link/ Activity Per SFP+ port: Status, Rx, Tx, Link Per Device: Power, Status 3
4 AVAILABLE NSA UNITS Product Type NSA40 NSA40D Monitoring Ports 40 x 10 Gbit SFP+ 40 x 10 Gbit SFP+ Management Ports 1 x RS 232 RJ45 & 1 x FE RJ45 & USB 2.0 Hardware Specs Memory 64G DDR3 1333MHz ECC 128G DDR3 1333MHz ECC CPU MIPS Core multi-core processor MIPS Core multi-core processor Throughput 20Gbps 40Gbps Performance Specs Decryption Performance 5Gbps 10Gbps Sessions 10M online (maximum) 20M online (maximum) Decryption Feature Monitoring Feature SSL/TLS Protocol Key Ciphers & Operations Hash Algorithms Packet Preprocessing Session Management SSL3.0, TLS1.0, TLS1.1, TLS1.2 Symmetric: DES CBC, 3DES CBC, AES-128 CBC, AES-256 CBC, RC4, RC2, IDEA, etc. Asymmetric: RSA. SHA1, MD5, SHA256, SHA224, SHA384, SHA512, AES, HMAC IP-reassembly Tunnel identification such as GTP/GRE, supporting protocol processing inside the tunnel TCP-reassembly such as out-of-order packets, TCP state tracking Correlating SSL/TLS sessions with session id or ticket Flow Restoration Rebuilding the packets without SSL/TLS header and calculating TCP sequence and fixing TCP/IP checksum, supporting GTP-U tunnel 4
5 TYPICAL APPLICATION Server-Side (In the Data Center) ServerCerts. + Private Keys Tap ports Root Client-Side (In the Enterprise) Proxy re-signs ServerCerts Tap ports ORDERING INFORMATION Product Components: Cubro Security Appliance AC/DC power supply European power cord (no SFPs included) Part Number Description For more information please check our website 5
Cubro FlowVista Series
 Cubro FlowVista Series PRODUCT REVIEW Network Probe At a glance Definition A Probe is a passive device which receives network traffic from TAPs and Packet Brokers and extracts meta data. Advantages of
Cubro FlowVista Series PRODUCT REVIEW Network Probe At a glance Definition A Probe is a passive device which receives network traffic from TAPs and Packet Brokers and extracts meta data. Advantages of
Cubro Packetmaster EX48600
 Cubro Packetmaster EX48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX48600 is a high performance network packet broker up to Layer 4 that aggregates, filters, duplicates,
Cubro Packetmaster EX48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX48600 is a high performance network packet broker up to Layer 4 that aggregates, filters, duplicates,
Cubro Packetmaster EX48600
 Cubro Packetmaster EX48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links; duplicates, aggregates
Cubro Packetmaster EX48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links; duplicates, aggregates
Cubro Sessionmaster EXA40 series
 Cubro Sessionmaster EXA40 series PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links, duplicates, aggregates
Cubro Sessionmaster EXA40 series PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links, duplicates, aggregates
Cubro Sessionmaster EXA48600
 Cubro Sessionmaster EXA48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links, duplicates, aggregates
Cubro Sessionmaster EXA48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links, duplicates, aggregates
Cubro Packetmaster EX32/32(+)
 Cubro Packetmaster EX32/32(+) PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX32/32(+) is the newest high performance network packet broker that aggregates, filters, load balances
Cubro Packetmaster EX32/32(+) PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX32/32(+) is the newest high performance network packet broker that aggregates, filters, load balances
Cubro Packetmaster EX2 Series
 Cubro Series PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance Definition The Cubro Packetmaster (Network Packet Broker) EX2 Series, based on a new designed ASIC, is a switch like device. EX2 Series
Cubro Series PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance Definition The Cubro Packetmaster (Network Packet Broker) EX2 Series, based on a new designed ASIC, is a switch like device. EX2 Series
Cubro Packetmaster EX12
 Cubro Packetmaster EX12 PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance Definition The Packetmaster EX12 is a network packet broker and network controller switch that aggregates, filters and load
Cubro Packetmaster EX12 PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance Definition The Packetmaster EX12 is a network packet broker and network controller switch that aggregates, filters and load
CUBRO. Cubro Packetmaster EX Functions. 20 x 40 Gbps 4 x 100 Gbps NPB
 Version 1.0 April. 2015 Cubro Packetmaster EX 20400 Link/Port Aggregation Functions 20 x 40 Gbps 4 x 100 Gbps NPB The Packetmaster EX 20400 is a modern Network Packet Broker and network controller switch
Version 1.0 April. 2015 Cubro Packetmaster EX 20400 Link/Port Aggregation Functions 20 x 40 Gbps 4 x 100 Gbps NPB The Packetmaster EX 20400 is a modern Network Packet Broker and network controller switch
Cubro Packetmaster EX32100
 Cubro Packetmaster EX32100 PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX32100 is a network packet broker and network controller switch that aggregates, filters and load balances
Cubro Packetmaster EX32100 PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX32100 is a network packet broker and network controller switch that aggregates, filters and load balances
Cubro Sessionmaster EXA32100
 Cubro Sessionmaster EXA32100 PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Sessionmaster EXA32100 is a network packet broker and network controller switch that aggregates, filters and load
Cubro Sessionmaster EXA32100 PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Sessionmaster EXA32100 is a network packet broker and network controller switch that aggregates, filters and load
Cubro Packetmaster EX2 Series
 Cubro Packetmaster EX2 Series PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Cubro Packetmaster EX2 series devices are Network Packet Brokers (switch-like devices) based on a newly designed
Cubro Packetmaster EX2 Series PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance The Cubro Packetmaster EX2 series devices are Network Packet Brokers (switch-like devices) based on a newly designed
VISION ONE: SECURITY WITHOUT SACRIFICE
 VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
AIR-WLC K9 Datasheet. Overview. Check its price: Click Here. Quick Specs
 AIR-WLC4402-12-K9 Datasheet Check its price: Click Here Overview Cisco 4400 Series Wireless LAN Controller provides systemwide wireless LAN functions for medium to large-sized facilities. By automating
AIR-WLC4402-12-K9 Datasheet Check its price: Click Here Overview Cisco 4400 Series Wireless LAN Controller provides systemwide wireless LAN functions for medium to large-sized facilities. By automating
VISION ONE: SECURITY WITHOUT SACRIFICE
 VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
Mobil Core Monitoring Session aware load balancing of GTPv1 and GTPv2 traffic to multiple probes
 Sessionmaster EXA Series Version 1.1 Okt. 2015 Technical Features & Models : Sessionmaster EXA 28 Ports 28 x 10 Gbit SFP+ Throughput 280 Gbps Application Presentation Session Transport Network Application
Sessionmaster EXA Series Version 1.1 Okt. 2015 Technical Features & Models : Sessionmaster EXA 28 Ports 28 x 10 Gbit SFP+ Throughput 280 Gbps Application Presentation Session Transport Network Application
GTP Load Balancing. How to do GTP Load Balancing with Cubro Products. 27 Sep
 GTP Load Balancing How to do GTP Load Balancing with Cubro Products 27 Sep 2017 www.cubro.com GTP Load Balancing GTP: GPRS Tunneling Protocol GTP is used to transport packet data from the enodeb to the
GTP Load Balancing How to do GTP Load Balancing with Cubro Products 27 Sep 2017 www.cubro.com GTP Load Balancing GTP: GPRS Tunneling Protocol GTP is used to transport packet data from the enodeb to the
Cisco Wireless LAN Controller Module
 Cisco Wireless LAN Controller Modules Simple and secure wireless deployment and management for small and medium-sized businesses (SMBs) and enterprise branch offices Product Overview Cisco Wireless LAN
Cisco Wireless LAN Controller Modules Simple and secure wireless deployment and management for small and medium-sized businesses (SMBs) and enterprise branch offices Product Overview Cisco Wireless LAN
Lecture 9a: Secure Sockets Layer (SSL) March, 2004
 Internet and Intranet Protocols and Applications Lecture 9a: Secure Sockets Layer (SSL) March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Security Achieved by
Internet and Intranet Protocols and Applications Lecture 9a: Secure Sockets Layer (SSL) March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Security Achieved by
Cisco VPN Internal Service Module for Cisco ISR G2
 Data Sheet Cisco VPN Internal Service Module for Cisco ISR G2 Compact Versatile High-Performance VPN Module The Cisco VPN Internal Service Module (VPN ISM) is a module for the Cisco Integrated Services
Data Sheet Cisco VPN Internal Service Module for Cisco ISR G2 Compact Versatile High-Performance VPN Module The Cisco VPN Internal Service Module (VPN ISM) is a module for the Cisco Integrated Services
Parallelizing IPsec: switching SMP to On is not even half the way
 Parallelizing IPsec: switching SMP to On is not even half the way Steffen Klassert secunet Security Networks AG Dresden June 11 2010 Table of contents Some basics about IPsec About the IPsec performance
Parallelizing IPsec: switching SMP to On is not even half the way Steffen Klassert secunet Security Networks AG Dresden June 11 2010 Table of contents Some basics about IPsec About the IPsec performance
Scaling Acceleration Capacity from 5 to 50 Gbps and Beyond with Intel QuickAssist Technology
 SOLUTION BRIEF Intel QuickAssist Technology Scaling Acceleration Capacity from 5 to 5 Gbps and Beyond with Intel QuickAssist Technology Equipment manufacturers can dial in the right capacity by choosing
SOLUTION BRIEF Intel QuickAssist Technology Scaling Acceleration Capacity from 5 to 5 Gbps and Beyond with Intel QuickAssist Technology Equipment manufacturers can dial in the right capacity by choosing
Encrypted Phone Configuration File Setup
 This chapter provides information about encrypted phone configuration files setup. After you configure security-related settings, the phone configuration file contains sensitive information, such as digest
This chapter provides information about encrypted phone configuration files setup. After you configure security-related settings, the phone configuration file contains sensitive information, such as digest
User Plane Monitoring for a Mobile Network Operator (MNO)
 User Plane Monitoring for a Mobile Network Operator (MNO) Jan 2018 www.cubro.com User Plane Monitoring for a MNO The challenges Growing traffic High costs Complicated network architecture The Cubro solution
User Plane Monitoring for a Mobile Network Operator (MNO) Jan 2018 www.cubro.com User Plane Monitoring for a MNO The challenges Growing traffic High costs Complicated network architecture The Cubro solution
Comparing TCP performance of tunneled and non-tunneled traffic using OpenVPN. Berry Hoekstra Damir Musulin OS3 Supervisor: Jan Just Keijser Nikhef
 Comparing TCP performance of tunneled and non-tunneled traffic using OpenVPN Berry Hoekstra Damir Musulin OS3 Supervisor: Jan Just Keijser Nikhef Outline Introduction Approach Research Results Conclusion
Comparing TCP performance of tunneled and non-tunneled traffic using OpenVPN Berry Hoekstra Damir Musulin OS3 Supervisor: Jan Just Keijser Nikhef Outline Introduction Approach Research Results Conclusion
Configuring SSL Security
 CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
FIPS SECURITY POLICY FOR
 FIPS 140-2 SECURITY POLICY FOR SPECTRAGUARD ENTERPRISE SENSOR August 26, 2011 FIPS 140-2 LEVEL-2 SECURITY POLICY FOR AIRTIGHT NETWORKS SPECTRAGUARD ENTERPRISE SENSOR 1. Introduction This document describes
FIPS 140-2 SECURITY POLICY FOR SPECTRAGUARD ENTERPRISE SENSOR August 26, 2011 FIPS 140-2 LEVEL-2 SECURITY POLICY FOR AIRTIGHT NETWORKS SPECTRAGUARD ENTERPRISE SENSOR 1. Introduction This document describes
Communication Interface
 Communication Interface Com'X 200 Technical data sheet Communications Functions and characteristics PB112041 Ethernet GPRS data logger function The collects and stores wages consumptions (Water, Air, Gas,
Communication Interface Com'X 200 Technical data sheet Communications Functions and characteristics PB112041 Ethernet GPRS data logger function The collects and stores wages consumptions (Water, Air, Gas,
Packetmaster EX2 - A desktop NPB
 Packetmaster EX2 - A desktop NPB Learn about all the useful applications June 2018 www.cubro.com EX2 & EX2+ - A desktop NPB Packetmaster EX2 The Swiss army knife network device Cubro Packetmaster EX2 The
Packetmaster EX2 - A desktop NPB Learn about all the useful applications June 2018 www.cubro.com EX2 & EX2+ - A desktop NPB Packetmaster EX2 The Swiss army knife network device Cubro Packetmaster EX2 The
Cipher Suite Configuration Mode Commands
 The Cipher Suite Configuration Mode is used to configure the building blocks for SSL cipher suites, including the encryption algorithm, hash function, and key exchange. Important The commands or keywords/variables
The Cipher Suite Configuration Mode is used to configure the building blocks for SSL cipher suites, including the encryption algorithm, hash function, and key exchange. Important The commands or keywords/variables
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
The question paper contains 40 multiple choice questions with four choices and students will have to pick the correct one (each carrying ½ marks.).
 Time: 3hrs BCA III Network security and Cryptography Examination-2016 Model Paper 2 M.M:50 The question paper contains 40 multiple choice questions with four choices and students will have to pick the
Time: 3hrs BCA III Network security and Cryptography Examination-2016 Model Paper 2 M.M:50 The question paper contains 40 multiple choice questions with four choices and students will have to pick the
Performance implication of elliptic curve TLS
 MSc Systems & Network Engineering Performance implication of elliptic curve TLS Maikel de Boer - maikel.deboer@os3.nl Joris Soeurt - joris.soeurt@os3.nl April 1, 2012 Abstract During our research we tested
MSc Systems & Network Engineering Performance implication of elliptic curve TLS Maikel de Boer - maikel.deboer@os3.nl Joris Soeurt - joris.soeurt@os3.nl April 1, 2012 Abstract During our research we tested
Findings for
 Findings for 198.51.100.23 Scan started: 2017-07-11 12:30 UTC Scan ended: 2017-07-11 12:39 UTC Overview Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 80/tcp
Findings for 198.51.100.23 Scan started: 2017-07-11 12:30 UTC Scan ended: 2017-07-11 12:39 UTC Overview Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 443/tcp - NEW Medium: Port 80/tcp
GigaVUE-2404 // Data Sheet
 Mgmt Console M/S Rdy 10/100/1000 PORTS (SFP) G1 G2 G3 G4 G1 G2 G3 G4 1 1 2 2 3 3 4 5 4 5 6 6 7 7 8 8 SLOT 2 PORTS 9 16 SLOT 1 PORTS G1-G4 PORTS 1-8 SLOT 3 PORTS 17 24 PS ALARM CUTOFF UP WHEN INSTALLED
Mgmt Console M/S Rdy 10/100/1000 PORTS (SFP) G1 G2 G3 G4 G1 G2 G3 G4 1 1 2 2 3 3 4 5 4 5 6 6 7 7 8 8 SLOT 2 PORTS 9 16 SLOT 1 PORTS G1-G4 PORTS 1-8 SLOT 3 PORTS 17 24 PS ALARM CUTOFF UP WHEN INSTALLED
Acme Packet Net-Net 9200
 Acme Packet Overview Acme Packet s platform offers carrier-grade performance, capacity and availability for service provider and large enterprise deployments in a single 7RU chassis-based system. The operates
Acme Packet Overview Acme Packet s platform offers carrier-grade performance, capacity and availability for service provider and large enterprise deployments in a single 7RU chassis-based system. The operates
Cisco VPN 3002 Hardware Client Security Policy
 Introduction This non-proprietary Cryptographic Module Security Policy describes how the VPN 3002 and 3002 8E Hardware Client (Firmware version FIPS 3.6.7.F) meets the security requirements of FIPS 140-2,
Introduction This non-proprietary Cryptographic Module Security Policy describes how the VPN 3002 and 3002 8E Hardware Client (Firmware version FIPS 3.6.7.F) meets the security requirements of FIPS 140-2,
2804 Hybrid Packet Broker
 2804 Hybrid Packet Broker Multi-functional Bypass Packet Broker The Niagara 2804 hybrid packet broker uniquely combines multipurpose bypass functionality with a fully featured network packet broker. The
2804 Hybrid Packet Broker Multi-functional Bypass Packet Broker The Niagara 2804 hybrid packet broker uniquely combines multipurpose bypass functionality with a fully featured network packet broker. The
TLS 1.1 Security fixes and TLS extensions RFC4346
 F5 Networks, Inc 2 SSL1 and SSL2 Created by Netscape and contained significant flaws SSL3 Created by Netscape to address SSL2 flaws TLS 1.0 Standardized SSL3 with almost no changes RFC2246 TLS 1.1 Security
F5 Networks, Inc 2 SSL1 and SSL2 Created by Netscape and contained significant flaws SSL3 Created by Netscape to address SSL2 flaws TLS 1.0 Standardized SSL3 with almost no changes RFC2246 TLS 1.1 Security
The case for ubiquitous transport-level encryption
 1/25 The case for ubiquitous transport-level encryption Andrea Bittau, Michael Hamburg, Mark Handley, David Mazières, and Dan Boneh Stanford and UCL November 18, 2010 Goals 2/25 What would it take to encrypt
1/25 The case for ubiquitous transport-level encryption Andrea Bittau, Michael Hamburg, Mark Handley, David Mazières, and Dan Boneh Stanford and UCL November 18, 2010 Goals 2/25 What would it take to encrypt
GigaVUE-420 Specifications
 Mgmnt Console M/S Rdy Pwr 1 2 3 4 N(a) NETWORK N(b) INLINE TOOL T(a) T(b) GigaLINK-Cu GigaLINK-SR GigaLINK-ER GigaVUE-420 Specifications Gigamon Systems Giga PORT Giga TAP-Tx Giga TAP-Sx Split Ratio :70/30
Mgmnt Console M/S Rdy Pwr 1 2 3 4 N(a) NETWORK N(b) INLINE TOOL T(a) T(b) GigaLINK-Cu GigaLINK-SR GigaLINK-ER GigaVUE-420 Specifications Gigamon Systems Giga PORT Giga TAP-Tx Giga TAP-Sx Split Ratio :70/30
Acme Packet Net-Net 3820
 Acme Packet Overview Acme Packet s is our mid-range platform for enterprises and service providers. The 1RU features Acme Packet s custom hardware design tightly integrated with Net-Net OS to provide the
Acme Packet Overview Acme Packet s is our mid-range platform for enterprises and service providers. The 1RU features Acme Packet s custom hardware design tightly integrated with Net-Net OS to provide the
Easy To Install. Easy To Manage. Always Up-To-Date.
 WATCHGUARD FIREBOX SYSTEM Easy To Install. Easy To Manage. Always Up-To-Date. Overview The WatchGuard Firebox System is a comprehensive firewall and VPN security solution that reduces the time and resources
WATCHGUARD FIREBOX SYSTEM Easy To Install. Easy To Manage. Always Up-To-Date. Overview The WatchGuard Firebox System is a comprehensive firewall and VPN security solution that reduces the time and resources
Dell Software, Inc. Dell SonicWALL NSA Series SM 9600, SM 9400, SM 9200, NSA FIPS Non-Proprietary Security Policy
 Dell Software, Inc. Dell SonicWALL NSA Series SM 9600, SM 9400, SM 9200, NSA 6600 FIPS 140-2 Non-Proprietary Security Policy Level 2 Version 1.3 June 25, 2015 1 Copyright Notice Copyright 2015 Dell Software,
Dell Software, Inc. Dell SonicWALL NSA Series SM 9600, SM 9400, SM 9200, NSA 6600 FIPS 140-2 Non-Proprietary Security Policy Level 2 Version 1.3 June 25, 2015 1 Copyright Notice Copyright 2015 Dell Software,
Datapath. Encryption
 Datapath The following refers to the IKE/IPsec datapath implementation of overlay tunnels between Silver Peak devices. VXOA Release 7.3 (Regular "IPsec" mode with IKE) 8.0 (Regular "IPsec" mode with IKE)
Datapath The following refers to the IKE/IPsec datapath implementation of overlay tunnels between Silver Peak devices. VXOA Release 7.3 (Regular "IPsec" mode with IKE) 8.0 (Regular "IPsec" mode with IKE)
Appliance Comparison Chart
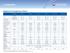 Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Data Security and Privacy. Topic 14: Authentication and Key Establishment
 Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
FIPS Management. FIPS Management Overview. Configuration Changes in FIPS Mode
 This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
Datapath. Encryption
 Datapath The following refers to the IKE/IPsec datapath implementation of overlay tunnels between Silver Peak devices. VXOA Release 7.3 (Regular "IPsec" mode with IKE) 8.0 (Regular "IPsec" mode with IKE)
Datapath The following refers to the IKE/IPsec datapath implementation of overlay tunnels between Silver Peak devices. VXOA Release 7.3 (Regular "IPsec" mode with IKE) 8.0 (Regular "IPsec" mode with IKE)
IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots
 IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots Юлий Явич, IXIA 1 Enterprise Carriers/ Service Providers 74 45 15 of the Fortune 100 of the top 50 carriers of the top 15 NEMs NEMs Customer Focused
IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots Юлий Явич, IXIA 1 Enterprise Carriers/ Service Providers 74 45 15 of the Fortune 100 of the top 50 carriers of the top 15 NEMs NEMs Customer Focused
PHYSICAL INTERFACES 5406R
 PHYSICAL INTERFACES 5406R zl2 Switch (J9821A): 6 open module slots 5412R zl2 Switch (J9822A): 12 open module slots Supports a maximum of 288 autosensing 10/100/1000 ports or 288 SFP ports or 96 SFP+ ports
PHYSICAL INTERFACES 5406R zl2 Switch (J9821A): 6 open module slots 5412R zl2 Switch (J9822A): 12 open module slots Supports a maximum of 288 autosensing 10/100/1000 ports or 288 SFP ports or 96 SFP+ ports
AC3000 Tri-Band Wireless Gigabit Dual-WAN VPN SMB Router TEW-829DRU (v1.0r)
 AC3000 Tri-Band Wireless Gigabit Dual-WAN SMB Router (v1.0r) Dual-WAN ports support load-balancing and fail-over modes 8 x Gigabit LAN ports, 1 x Console port SSL, IPsec, PPTP, and L2TP w/ipsec support
AC3000 Tri-Band Wireless Gigabit Dual-WAN SMB Router (v1.0r) Dual-WAN ports support load-balancing and fail-over modes 8 x Gigabit LAN ports, 1 x Console port SSL, IPsec, PPTP, and L2TP w/ipsec support
Apex Lynx DATASHEET. DS-1030-E 1 of 5
 DS-1030-E 1 of 5 Apex Lynx Overview The Apex Lynx is an ultra-high performance all-outdoor point-to-point wireless microwave system designed for carrier, enterprise, service provider, and government networks.
DS-1030-E 1 of 5 Apex Lynx Overview The Apex Lynx is an ultra-high performance all-outdoor point-to-point wireless microwave system designed for carrier, enterprise, service provider, and government networks.
IPSec. Slides by Vitaly Shmatikov UT Austin. slide 1
 IPSec Slides by Vitaly Shmatikov UT Austin slide 1 TCP/IP Example slide 2 IP Security Issues Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service
IPSec Slides by Vitaly Shmatikov UT Austin slide 1 TCP/IP Example slide 2 IP Security Issues Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service
INTERNET PROTOCOL SECURITY (IPSEC) GUIDE.
 INTERNET PROTOCOL SECURITY (IPSEC) GUIDE www.insidesecure.com INTRODUCING IPSEC NETWORK LAYER PACKET SECURITY With the explosive growth of the Internet, more and more enterprises are looking towards building
INTERNET PROTOCOL SECURITY (IPSEC) GUIDE www.insidesecure.com INTRODUCING IPSEC NETWORK LAYER PACKET SECURITY With the explosive growth of the Internet, more and more enterprises are looking towards building
RUGE. Rugged IP load generator (Ruge) Ruge gives your network a serious beating. Just to make sure it does not fail when it is time to go live.
 PRODUCT DATA SHEET Rugged IP load generator (Ruge) RUGE Ruge gives your network a serious beating. Just to make sure it does not fail when it is time to go live. Introduction Rugged IP load generator (Ruge)
PRODUCT DATA SHEET Rugged IP load generator (Ruge) RUGE Ruge gives your network a serious beating. Just to make sure it does not fail when it is time to go live. Introduction Rugged IP load generator (Ruge)
PE310G4SPI9 Quad Port Fiber 10 Gigabit Ethernet PCI Express Server Adapter Intel 82599ES Based
 PE310G4SPI9 Quad Port Fiber 10 Gigabit Ethernet PCI Express Server Adapter Intel 82599ES Based Product Description Silicom s 10 Gigabit Ethernet PCI Express server adapters are designed for Servers and
PE310G4SPI9 Quad Port Fiber 10 Gigabit Ethernet PCI Express Server Adapter Intel 82599ES Based Product Description Silicom s 10 Gigabit Ethernet PCI Express server adapters are designed for Servers and
TAP Aggregation-Network Visibility and Security
 Data Center & Cloud Computing DATASHEET TAP Aggregation-Network Visibility and Security Model: T5800-8TF12S REV.1.0 2018 TAP Aggregation 01 Overview The FS T5800 TAP (Test Access Port) Series Switches
Data Center & Cloud Computing DATASHEET TAP Aggregation-Network Visibility and Security Model: T5800-8TF12S REV.1.0 2018 TAP Aggregation 01 Overview The FS T5800 TAP (Test Access Port) Series Switches
CSCE 715: Network Systems Security
 CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse.sc.edu University of South Carolina Web Security Web is now widely used by business, government, and individuals But Internet and Web are
CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse.sc.edu University of South Carolina Web Security Web is now widely used by business, government, and individuals But Internet and Web are
THUNDER CFW APPLIANCE SPECIFICATIONS
 SPEC SHEET CFW APPLIANCE SPECIFICATIONS 840 1030S 3030S 3040 DCFW Throughput 5 Gbps 10 Gbps 30 Gbps 30 Gbps DCFW Layer 4 CPS 200K 300K 500K 500K DCFW Concurrent Sessions 8 Million 16 Million 32 Million
SPEC SHEET CFW APPLIANCE SPECIFICATIONS 840 1030S 3030S 3040 DCFW Throughput 5 Gbps 10 Gbps 30 Gbps 30 Gbps DCFW Layer 4 CPS 200K 300K 500K 500K DCFW Concurrent Sessions 8 Million 16 Million 32 Million
Total No. of Questions : 09 ] [ Total No.of Pages : 02
![Total No. of Questions : 09 ] [ Total No.of Pages : 02 Total No. of Questions : 09 ] [ Total No.of Pages : 02](/thumbs/86/93170507.jpg) CS / IT 321 (CR) Total No. of Questions : 09 ] [ Total No.of Pages : 02 III/IV B. TECH. DEGREE EXAMINATIONS, OCT / NOV - 2015 Second Semester COMPUTER SCIENCE & ENGINEERING NETWK SECURITY Time : Three
CS / IT 321 (CR) Total No. of Questions : 09 ] [ Total No.of Pages : 02 III/IV B. TECH. DEGREE EXAMINATIONS, OCT / NOV - 2015 Second Semester COMPUTER SCIENCE & ENGINEERING NETWK SECURITY Time : Three
Ixia xstream TM 10. Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks. Aggregation and Filtering DATA SHEET
 Ixia xstream TM 10 Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks The Ixia xstream 10 is a network packet broker purpose-built for fail-safe inline security tools deployment and out-of-band
Ixia xstream TM 10 Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks The Ixia xstream 10 is a network packet broker purpose-built for fail-safe inline security tools deployment and out-of-band
Giga Lynx DATASHEET. DS-1029-F 1 of 5
 DS-1029-F 1 of 5 Giga Lynx Overview The Giga Lynx is an ultra-high performance split architecture point-to-point wireless microwave system designed for carrier, enterprise, service provider, and government
DS-1029-F 1 of 5 Giga Lynx Overview The Giga Lynx is an ultra-high performance split architecture point-to-point wireless microwave system designed for carrier, enterprise, service provider, and government
Meru Networks. Security Gateway SG1000 Cryptographic Module Security Policy Document Version 1.2. Revision Date: June 24, 2009
 Security Gateway SG1000 Cryptographic Module Security Policy Document Version 1.2 Meru Networks Revision Date: June 24, 2009 Copyright Meru Networks 2008. May be reproduced only in its original entirety
Security Gateway SG1000 Cryptographic Module Security Policy Document Version 1.2 Meru Networks Revision Date: June 24, 2009 Copyright Meru Networks 2008. May be reproduced only in its original entirety
Ixia xbalancer. A Purpose-Built Load Balancer for 10G Networks. The Load Balancing Solution DATA SHEET. Highlights
 Ixia xbalancer A Purpose-Built Load Balancer for 10G Networks Ixia s xbalancer is a load balancing appliance for monitoring high-speed network traffic and cost-effective way to share the increasing traffic
Ixia xbalancer A Purpose-Built Load Balancer for 10G Networks Ixia s xbalancer is a load balancing appliance for monitoring high-speed network traffic and cost-effective way to share the increasing traffic
GigaVUE-420 // Data Sheet
 Mgmnt Console M/S Rdy Pwr 1 2 3 4 NETWORK N(a) N(b) INLINE TOOL T(a) T(b) GigaLINK-Cu GigaLINK-SR GigaLINK-ER The Smart Route To Visibility Gigamon Systems Giga PORT Giga TAP-Tx Giga TAP-Sx Split Ratio
Mgmnt Console M/S Rdy Pwr 1 2 3 4 NETWORK N(a) N(b) INLINE TOOL T(a) T(b) GigaLINK-Cu GigaLINK-SR GigaLINK-ER The Smart Route To Visibility Gigamon Systems Giga PORT Giga TAP-Tx Giga TAP-Sx Split Ratio
Understand the TLS handshake Understand client/server authentication in TLS. Understand session resumption Understand the limitations of TLS
 Last Updated: Oct 31, 2017 Understand the TLS handshake Understand client/server authentication in TLS RSA key exchange DHE key exchange Explain certificate ownership proofs in detail What cryptographic
Last Updated: Oct 31, 2017 Understand the TLS handshake Understand client/server authentication in TLS RSA key exchange DHE key exchange Explain certificate ownership proofs in detail What cryptographic
XPSMCMCO0000EM Modbus TCPIP diagnostic expansion module with screw term
 Characteristics Modbus TCPIP diagnostic expansion module with screw term Main Range of product Product or component type Device short name [Us] rated supply voltage Complementary Power dissipation in W
Characteristics Modbus TCPIP diagnostic expansion module with screw term Main Range of product Product or component type Device short name [Us] rated supply voltage Complementary Power dissipation in W
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to
 1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
Install the ExtraHop session key forwarder on a Windows server
 Install the ExtraHop session key forwarder on a Windows server Published: 2018-12-17 Perfect Forward Secrecy (PFS) is a property of secure communication protocols that enables short-term, completely private
Install the ExtraHop session key forwarder on a Windows server Published: 2018-12-17 Perfect Forward Secrecy (PFS) is a property of secure communication protocols that enables short-term, completely private
Fregata. DDoS Mitigation Solution. Technical Specifications & Datasheet 1G-5G
 Fregata DDoS Mitigation Solution Technical Specifications & Datasheet 1G-5G Amidst fierce competition, your business cannot afford to slow down With HaltDos, you don t have to sacrifice productivity and
Fregata DDoS Mitigation Solution Technical Specifications & Datasheet 1G-5G Amidst fierce competition, your business cannot afford to slow down With HaltDos, you don t have to sacrifice productivity and
TravelHawk Pro KEY FEATURES AND BENEFITS SPEC SHEET PORTABLE WIRELESS NETWORK TROUBLESHOOTING TOOL
 PORTABLE WIRELESS NETWORK TROUBLESHOOTING TOOL A unique, portable live wireless network troubleshooting tool that captures over 3 Gbit/s of data on local storage with comprehensive end-to-end wireless
PORTABLE WIRELESS NETWORK TROUBLESHOOTING TOOL A unique, portable live wireless network troubleshooting tool that captures over 3 Gbit/s of data on local storage with comprehensive end-to-end wireless
Open Source Internet Security
 Open Source Internet Security Company / Product Overview October, 2016 http://www.wolfssl.com (425) 245-8247 ABOUT US Founded: 2004 Location: Bozeman, MT Seattle, WA Portland, OR Our Focus: Open Source
Open Source Internet Security Company / Product Overview October, 2016 http://www.wolfssl.com (425) 245-8247 ABOUT US Founded: 2004 Location: Bozeman, MT Seattle, WA Portland, OR Our Focus: Open Source
Computer Security. 10r. Recitation assignment & concept review. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 10r. Recitation assignment & concept review Paul Krzyzanowski Rutgers University Spring 2018 April 3, 2018 CS 419 2018 Paul Krzyzanowski 1 1. What is a necessary condition for perfect
Computer Security 10r. Recitation assignment & concept review Paul Krzyzanowski Rutgers University Spring 2018 April 3, 2018 CS 419 2018 Paul Krzyzanowski 1 1. What is a necessary condition for perfect
Security IP-Cores. AES Encryption & decryption RSA Public Key Crypto System H-MAC SHA1 Authentication & Hashing. l e a d i n g t h e w a y
 AES Encryption & decryption RSA Public Key Crypto System H-MAC SHA1 Authentication & Hashing l e a d i n g t h e w a y l e a d i n g t h e w a y Secure your sensitive content, guarantee its integrity and
AES Encryption & decryption RSA Public Key Crypto System H-MAC SHA1 Authentication & Hashing l e a d i n g t h e w a y l e a d i n g t h e w a y Secure your sensitive content, guarantee its integrity and
CCR1009 CCR1009. Cloud Core Router. The CCR1009 is a powerful Ethernet router based on the cutting edge TILERA 9 core CPU.
 Cloud Core Router CCR1009 The CCR1009 is a powerful Ethernet router based on the cutting edge TILERA 9 core CPU. Two models are available: low-cost model CCR1009-8G-1S with with 1GB of RAM, eight Gigabit
Cloud Core Router CCR1009 The CCR1009 is a powerful Ethernet router based on the cutting edge TILERA 9 core CPU. Two models are available: low-cost model CCR1009-8G-1S with with 1GB of RAM, eight Gigabit
Apex Orion DATASHEET. DS-1026-E 1 of 5
 DS-1026-E 1 of 5 Apex Orion Overview The Apex Orion is an ultra-high performance all-outdoor point-to-point wireless microwave system designed for carrier, enterprise, service provider, and government
DS-1026-E 1 of 5 Apex Orion Overview The Apex Orion is an ultra-high performance all-outdoor point-to-point wireless microwave system designed for carrier, enterprise, service provider, and government
Flexible and scalable five enterprise-grade Smart-1 dedicated management appliances. Full Threat Visibility
 SMART-1 SECURITY MANAGEMENT PLATFORM All-in-one security management solution, with policy management, integrated threat visibility, workflow and orchestration, empowering Check Point Infinity Architecture
SMART-1 SECURITY MANAGEMENT PLATFORM All-in-one security management solution, with policy management, integrated threat visibility, workflow and orchestration, empowering Check Point Infinity Architecture
FGS-2616X L2+ Managed GbE Fiber Switches
 FGS-2616X L2+ Managed GbE Fiber Switches FGS-2616XD FGS-2616XA FGS-2616X Overview FGS-2616X series L2+ Managed Switch are next-generation Fiber Switch offering full suite of L2 features and additional
FGS-2616X L2+ Managed GbE Fiber Switches FGS-2616XD FGS-2616XA FGS-2616X Overview FGS-2616X series L2+ Managed Switch are next-generation Fiber Switch offering full suite of L2 features and additional
ASA5525-FPWR-K9 Datasheet. Overview. Check its price: Click Here. Quick Specs
 ASA5525-FPWR-K9 Datasheet Check its price: Click Here Overview Cisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-
ASA5525-FPWR-K9 Datasheet Check its price: Click Here Overview Cisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-
Acme Packet Net-Net 14000
 Acme Packet Overview The is Acme Packet s high-end platform for service providers who require the highest levels of performance and capacity, and the operational benefits of ATCA-compliant chassis-based
Acme Packet Overview The is Acme Packet s high-end platform for service providers who require the highest levels of performance and capacity, and the operational benefits of ATCA-compliant chassis-based
Protocols, Technologies and Standards Secure network protocols for the OSI stack P2.1 WLAN Security WPA, WPA2, IEEE i, IEEE 802.1X P2.
 P2 Protocols, Technologies and Standards Secure network protocols for the OSI stack P2.1 WLAN Security WPA, WPA2, IEEE 802.11i, IEEE 802.1X P2.2 IP Security IPsec transport mode (host-to-host), ESP and
P2 Protocols, Technologies and Standards Secure network protocols for the OSI stack P2.1 WLAN Security WPA, WPA2, IEEE 802.11i, IEEE 802.1X P2.2 IP Security IPsec transport mode (host-to-host), ESP and
SINGLEstream Link Aggregation Tap (SS-100)
 SINGLEstream Link Aggregation Tap (SS-00) Optional 3-Unit Rack Mount Datacom Systems SINGLEstream 0/00 Link Aggregation Tap provides a superior solution for 4x7 monitoring of full-duplex Ethernet links.
SINGLEstream Link Aggregation Tap (SS-00) Optional 3-Unit Rack Mount Datacom Systems SINGLEstream 0/00 Link Aggregation Tap provides a superior solution for 4x7 monitoring of full-duplex Ethernet links.
Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP,
 Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP, VPN, and Firewalls 32.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 32.2 Figure 32.1 Common structure
Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP, VPN, and Firewalls 32.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 32.2 Figure 32.1 Common structure
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
PE210G2P316 Dual Port 10 Gigabit Ethernet PCI Express Packet Processor Server Adapter
 PE210G2P316 Dual Port 10 Gigabit Ethernet PCI Express Product Description Silicom s 10 Gigabit Ethernet PCI Express NetLogic Packet Processor Server adaptor is targeted for network applications, such as
PE210G2P316 Dual Port 10 Gigabit Ethernet PCI Express Product Description Silicom s 10 Gigabit Ethernet PCI Express NetLogic Packet Processor Server adaptor is targeted for network applications, such as
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
TLS/sRTP Voice Recording AddPac Technology
 Secure IP Telephony Solution (TLS/SRTP Protocol) TLS/sRTP Voice Recording AddPac Technology 2015, Sales and Marketing www.addpac.com Contents Secure IP Telephony Service Diagram Secure VoIP Protocol &
Secure IP Telephony Solution (TLS/SRTP Protocol) TLS/sRTP Voice Recording AddPac Technology 2015, Sales and Marketing www.addpac.com Contents Secure IP Telephony Service Diagram Secure VoIP Protocol &
Datasheet. Gigabit Passive Optical Network. Models: UF-OLT, UF-OLT-4, UF-Nano, UF-LOCO. GPON End-to-End Solution. High-Performance, Provider OLT
 Gigabit Passive Optical Network Models: UF-OLT, UF-OLT-4, UF-Nano, UF-LOCO GPON End-to-End Solution High-Performance, Provider OLT Low-Cost, Robust ONU CPE High-Performance GPON Configuring a fiber network
Gigabit Passive Optical Network Models: UF-OLT, UF-OLT-4, UF-Nano, UF-LOCO GPON End-to-End Solution High-Performance, Provider OLT Low-Cost, Robust ONU CPE High-Performance GPON Configuring a fiber network
Data Sheet FUJITSU Server PRIMERGY CX2550 M1 Dual Socket Server Node
 Data Sheet FUJITSU Server PRIMERGY CX2550 M1 Dual Socket Server Node Data Sheet FUJITSU Server PRIMERGY CX2550 M1 Dual Socket Server Node Standard server node for PRIMERGY CX400 M1 multi-node server system
Data Sheet FUJITSU Server PRIMERGY CX2550 M1 Dual Socket Server Node Data Sheet FUJITSU Server PRIMERGY CX2550 M1 Dual Socket Server Node Standard server node for PRIMERGY CX400 M1 multi-node server system
24-Port: 20 x (100/1000M) SFP + 4 x Combo (10/100/1000T or 100/1000M SFP)
 BGS-20DSFP4C Managed Fiber Switch 24-Port: 20 x (100/1000M) SFP + 4 x Combo (10/100/1000T or 100/1000M SFP) Key Features L2+ features provide better manageability, security, QOS, and performance IEEE 802.3az
BGS-20DSFP4C Managed Fiber Switch 24-Port: 20 x (100/1000M) SFP + 4 x Combo (10/100/1000T or 100/1000M SFP) Key Features L2+ features provide better manageability, security, QOS, and performance IEEE 802.3az
E-commerce security: SSL/TLS, SET and others. 4.1
 E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
MIMO Junior Evo MMJ342LV
 MIMO Junior Evo MMJ342LV Model: MMJ342LV KEY FEATURES Qualcomm Atheros AR9342 MIPS 74Kc 560MHz CPU 64MB System Memory 1B NOR Flash On-board 5GHz max output power (per chain) IEEE 802.11n compliant & backward
MIMO Junior Evo MMJ342LV Model: MMJ342LV KEY FEATURES Qualcomm Atheros AR9342 MIPS 74Kc 560MHz CPU 64MB System Memory 1B NOR Flash On-board 5GHz max output power (per chain) IEEE 802.11n compliant & backward
The Xirrus Wi Fi Array XS4, XS8 Security Policy Document Version 1.0. Xirrus, Inc.
 The Xirrus Wi Fi Array XS4, XS8 Security Policy Document Version 1.0 Xirrus, Inc. March 8, 2011 Copyright Xirrus, Inc. 2011. May be reproduced only in its original entirety [without revision]. Page 1 TABLE
The Xirrus Wi Fi Array XS4, XS8 Security Policy Document Version 1.0 Xirrus, Inc. March 8, 2011 Copyright Xirrus, Inc. 2011. May be reproduced only in its original entirety [without revision]. Page 1 TABLE
HMISTO " wide screen touch panel, Ethernet
 Characteristics 4.3" wide screen touch panel, Ethernet Main Range of product Product or component type Software designation Operating system Complementary Display size Display type Display colour Pixel
Characteristics 4.3" wide screen touch panel, Ethernet Main Range of product Product or component type Software designation Operating system Complementary Display size Display type Display colour Pixel
CONNECTRIX MDS-9250I SWITCH
 Specification Sheet MDS-9250i CONNECTRIX MDS-9250I SWITCH Multipurpose Switch The Connectrix MDS-9250i Multilayer Switch offers up to forty 16 Gigabit per second (Gb/s) Fibre Channel ports, two 1/10 Gigabit
Specification Sheet MDS-9250i CONNECTRIX MDS-9250I SWITCH Multipurpose Switch The Connectrix MDS-9250i Multilayer Switch offers up to forty 16 Gigabit per second (Gb/s) Fibre Channel ports, two 1/10 Gigabit
Transport Layer Security
 Transport Layer Security TRANSPORT LAYER SECURITY PERFORMANCE TESTING OVERVIEW Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL), are the most popular cryptographic protocols
Transport Layer Security TRANSPORT LAYER SECURITY PERFORMANCE TESTING OVERVIEW Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL), are the most popular cryptographic protocols
