Sentinel 4 IDS User Interface Guide
|
|
|
- Gervais May
- 6 years ago
- Views:
Transcription
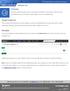
1 Sentinel 4 IDS User Interface Guide A quick primer on the available options of the Sentinel IDS s web-based user interface. Navigation Header This header will remain at the top of the page even if you need to scroll, and contains the following items: Navigation links: Contains the top-level links for the interface, as described in detail below. Current user: Displays your username. Click on your username to access links to your profile and log out of the system. Current time: Displays in military time (24-hour format), in the current time zone (which defaults to US Central time). Click the time to edit the system time zone. Find an IP tool: Enter an IPv4 IP in to this box, and press Enter. This will take you directly to that IP s detail page, which gives a summary of activity and a timeline of everything that has ever happened on your network related to that IP, including events, blocks, releases, configuration changes, and dropped packets. Title Bar This is the grey bar directly underneath the navigation header. It always contains: The system s current Location and Organization. This is editable by navigating to Configuration -> Organizational Info. The right-hand side shows important messages, and displays the current mode of the Sentinel. If there are pending configuration items, a red banner will display here, reminding you to commit your configuration changes. Also, if there are any Flagged events events that are serious enough that you should act upon them immediately a black banner with a red flag will display here. You can click on each of these items for more detail, as necessary. Dashboard This is the system s effective home page. It refreshes once an hour, and displays: A chart of activity over time and summarized by severity, and some basic statistics. You may choose to display the last 24 hours, last 7 days, last 30 days, or all activity. You can also click on the legend to hide or show different severities. Below the chart and network statistics, the dashboard displays various configuration settings and other housekeeping items, like configuration time, signature update, and software version. Sentinel v /15 1
2 Event Summary Shows a summary of every event that has ever happened on the Sentinel. Click one of the prominent links below the page title to summarize by Attack Type, Monitored IP Address, External IP Address, or if XFF recognition has been enabled X-Forwarded-For IP. Clicking the Attack Type text will take you to the Event Activity page, filtered for the corresponding summary event. The upper-right corner below the title bar always displays number of summary records, based on the current filter. If there is no filter, the number shown is the total of all activity on the Sentinel. There are four severity levels: The first three are designated 1 through 3, with 3 being critical. The fourth level is reserved for the most critical alerts; we call these Flagged alerts, and if there are any flagged alerts that you haven t reviewed, a notification banner will display in the upper right hand corner of the title bar. We take Flagged alerts seriously so should you. You can filter by keyword, including partial words and IP addresses. Click the small down-facing arrow in the filter s text box to reveal a cheat sheet for some custom filters. You can also filter out keywords by adding a dash directly in front of the word. For example, to search for alerts that contain the word CINS but do not contain the word rogue, you would enter CINS -rogue. Click the calendar icon to add a date filter; put the same date in both input boxes if you want to see a single day, or leave one of the date fields empty to get a range up to or starting from a given date. Results are paged, 50 items per page. The paging navigation appears at the bottom. Click the arrows to navigate to the first, last, previous and next page. Enter a page number in the input box and hit enter to go directly to a specific page. Badges: On the far right of every alert, there are 2 badges: The EPS badge identifies an alert as Extrusion Protection. EPS traffic can technically be inbound or outbound, but these signatures usually look for outbound traffic indicative of a botnet or malware infection within your LAN. These are usually worth your immediate attention, so we highlight them with this red badge. The REP badge identifies reputation-based alerts. These alerts are based on the reputation of the offending IP address, not the content of the IP s communication with your network. Sorting this column lets you quickly identify which alerts are signaturebased (No REP badge) and which alerts are reputation-based (blue REP badge). Event Activity Shows every event that s ever happened on the Sentinel. Think of it as an ad-hoc reporting tool where you can track down any activity that has ever occurred on the Sentinel. The way events are displayed on the page, including the keyword and date filtering, is very similar to the Event Summary page, so please refer to that section for more details. Sentinel v /15 2
3 Events on the Event Activity page are clickable, showing details about the attack, such as source and destination IP and port, protocol, and packet detail. Monitored Network IPs are displayed in blue. The actions button allows you to create a support ticket based on the specific alert, whitelist a network, see other alerts of the same type, and click through to the Alert Detail page, which includes references for the specific alert type. The IP addresses within the event detail are also clickable, allowing you to view WHOIS information, CINS information, and a detailed summary of the IP address and its history on the Sentinel. The upper-right corner below the title bar always displays total number of alerts, based on the current filter. If there is no filter, the number shown is the total of all activity on the Sentinel. Configuration This is where you can configure options specific to your network environment. Network Controls Each of the Network Control options is managed the same way: You can add, modify, or delete as many individual entries as you d like. But, once you ve completed your edits, you must click the Commit Configuration Changes button at the bottom of the page for your configuration changes to become active. Monitored Networks: Network ranges monitored by the Sentinel IPS. Any traffic destined to these networks that is deemed malicious by the Sentinel will trip an alert. Whitelisted Networks: Trusted network ranges or IP addresses outside of the monitored networks. The Sentinel will not alert on these networks for any reason. Their traffic is quite literally ignored by the Sentinel, and their activity does not show up in the Sentinel s reporting tools. Use whitelists judiciously if the Sentinel is tripping false positive activity, there is usually another remedy before we resort to whitelisting. Remote Administration: Allows the specified network access to the Sentinel s web interface. Only networks listed here and in Monitored Networks can access the web interface. Remote DNS Servers: Allows traffic to the specified network on port 53 (the standard port for DNS). If your network relies on external DNS servers for DNS resolution, enter them here. Note that malicious traffic detected on ports other than 53 will still trip alerts, even though it will always be allowed to communicate over port 53. System Controls System Settings and Tools Displays the Sentinel s current IP address, netmask, and gateway settings, and its serial number. The interface settings are displayed here, along with the NICs current status. If all is well, both NICs will show as active. In addition, if a NIC has auto-negotiated to its current setting, the page will show auto after the setting description. Sentinel v /15 3
4 The system time zone setting may be changed here. This setting is for display purposes only, and does not affect the systems core controls. That means if you d like to review a report or activity page from the perspective of a different time zone, feel free to adjust this setting as often as you d like. That can be handy when correlating event data across systems that span different time zones. Remote Logging Allows the Sentinel to log Alert data to a SEIM or remote syslog server. The setup is very straightforward, and only requires the IP and port of the remote server. You can also choose TCP or UDP; we recommend TCP, because TCP allows the Sentinel to hold the alert data in a queue in case communication to the remote server is lost temporarily. When communication is restored, the queued data is forwarded to the remote server, and there are no gaps in the timeline of the activity. Due to its stateless nature, UDP cannot queue data and makes no consideration for lost connections. Please note that the IP address in the configuration must be able to route to the SEIM or syslog server. The current format of the exported data is: Organizational Info timestamp src src port dst dst port severity attack description Organization Name: Enter your organization s name and the location of the Sentinel here. Be specific when describing the location; it helps us identify specific units more quickly, especially when companies have more than one Sentinel unit installed. Security Question/Answer: If we are unsure of your identity for any reason, we will ask you this security question. This is not specific to each individual user, so make sure all users of the Sentinel will know the answer. Billing and Shipping Addresses: Be sure to keep these addresses up to date. User Management Shows active users. Click their username to edit their account. Users are never deleted, only inactivated. If there are inactive users, a button will display next to the add a user button that will allow you to show (and edit) the inactive users. User s edit page: A user s basic personal information. A note about the 24/7 phone: Please give us a phone number where we can reach you even if your network is down. Standard office phone numbers especially VOIP systems can obviously prove to be unreachable during a network outage, so your cell phone is usually a good choice. You can choose to be texted or called after hours. There are 5 Access Levels (ACLs): Administrator: Can perform every function on the user interface, including management of other users. Also has access to the Transaction History. Sentinel v /15 4
5 Power User: Can perform every function on the interface, except management of other users. Cannot view transaction history. CBNets User: This type of user is not necessary or applicable on Sentinel IDS units. (On our standard IPS units, CBNets users can view reporting and can release blocked networks, but CANNOT change any other configuration settings like whitelists, mode, or time zone. Also cannot manage other users or view the transaction history.) Reader: Can view reporting and other activity, but cannot manage users or change any configuration settings. Perfect for management-level employees that might be required to review information but should not be allowed to change any settings. Auditor: Same as reader, but also has access to the Transaction History. As the name implies, perfect for an auditor that is required to review employee activity, but should not be allowed to configure the unit. Contact Level Primary Contact: If our monitoring system detects that the Sentinel is offline, we will contact this person as soon as possible by phone, based on their user profile preferences. If there are multiple Primary Contacts, we will attempt to contact them all. Alternate Contact: If we cannot reach a Primary Contact, we will attempt to contact the Alternate. There can be multiple Alternate Contacts, as well. If you want to be sure that you are never contacted for any reason, select None. Active? If this is checked, the user can access the Sentinel s interfaces. If this is unchecked, the user will be inactivated and unable to access the interfaces. To help keep audit trails and the Transaction History intact, users cannot be deleted. If you want to remove a user s access, simply inactivate him. Reporting All the reports default to specific time frame, but each can be customized to a different date range by using the date filter at the top of the page. Here is a brief overview of the reports available on the Sentinel: Top Attacks: Lists the top attack types and top offending IP addresses, so you can quickly find out which IPs and which types of attacks are affecting your network. Since these lists all link to more detailed reporting, this is a great starting point when researching a network issue. Activity Summary: The graphic shows all activity by day, and the summary table below it lists every attack type that hit the Sentinel for the given time period. Change the date range to a single day, and the chart will show hourly activity for that day. Service Report: A summary of everything on the Sentinel for the given time period, including some basic configuration settings, a log of user activity, and a list of the top attacks. Sentinel v /15 5
6 EPS Activity: EPS activity is an indication that your network might have an infected machine on the inside. Since this can be an urgent issue, we provide the EPS Activity page as a simple way to keep an eye on these types of alerts. It is essentially the same functional page as the Event Activity page, only filtered specifically for EPS activity, so see the Event Activity section for more details. Port Detail: This report summarizes destination protocol/port activity by volume and by unique IP address. Scheduler: Basic versions of the Top Attacks report, Activity Summary, and Service Report are available as regularly scheduled reports. This is a global setting, so any administrator or power user can control the timing of the reports and their recipients. Compliance This section gives some examples of how the Sentinel can assist you with various compliance guidelines, such as GLBA, HIPAA, PCI, and others. It also provides a link to the Transaction History of the Sentinel, assuming you have administrator or auditor permissions. Support Provides a phone number to reach us anytime ( ), a list of available documentation regarding the Sentinel, and Support Ticket submission form. Contact us anytime, any way we d love to hear from you. Detail Pages Each event on the Sentinel can be broken down in to two core components: The attack type, and the IP addresses involved. These detail pages endeavor to give you all the information you need to analyze these items on one, simple page. You will come across these pages as you drill in to events on the interface: IP Detail This page shows all the information we know about the given IP address, and lets you act upon that information. On this page you will find: The IP s country of origin A summary of alerts related to this IP A summary of configuration settings related to this IP In the case of external IP addresses, a timeline of all events and configuration activities related to this IP In the case of external IP addresses, the page also lists all the logged packets related to this IP. Using the page s actions button, you can: Whitelist the IP Sentinel v /15 6
7 See WHOIS and CINS information See all activity related to this IP on the Event Activity page. Alert Detail This page shows all the specifics of the given event, and lets you act upon that information. On this page you will find: The attack type and Sentinel-specific alert number The severity of the event EPS, Alert Only, and Reputation badges Source, destination, port, flow, protocol, and packet detail information Reference links specific to this type of alert, if available A detailed list of subsequent logged packets. Using the page s alert actions button, you can: Create a support ticket specific to the given alert Whitelist the offending IP View all alerts of this type on the Event Activity page. Sentinel v /15 7
Cisco Threat Awareness Service - Quick Start Guide. Last Updated: 16/06/16
 Cisco Threat Awareness Service - Quick Start Guide. Last Updated: 16/06/16 Contents Introduction... 1 Intended Use... 1 Portal Navigation... 2 Registering a Network Resource... 2 Adding the Network Resource
Cisco Threat Awareness Service - Quick Start Guide. Last Updated: 16/06/16 Contents Introduction... 1 Intended Use... 1 Portal Navigation... 2 Registering a Network Resource... 2 Adding the Network Resource
Dashboard User Guide For assistance, please call
 Dashboard User Guide For assistance, please call 1-866-399-8647. With these instructions, you will: PAGE 1. Login to the Clarity site, Configure 911, and Change your Password... 2 2. Set up Mobile Connect
Dashboard User Guide For assistance, please call 1-866-399-8647. With these instructions, you will: PAGE 1. Login to the Clarity site, Configure 911, and Change your Password... 2 2. Set up Mobile Connect
Viewing Capture ATP Status
 Capture ATP Viewing Capture ATP Status Configuring Capture ATP Viewing Capture ATP Status Capture ATP > Status About the Chart About the Log Table Uploading a File for Analysis Viewing Threat Reports Capture
Capture ATP Viewing Capture ATP Status Configuring Capture ATP Viewing Capture ATP Status Capture ATP > Status About the Chart About the Log Table Uploading a File for Analysis Viewing Threat Reports Capture
Account Customer Portal Manual
 Account Customer Portal Manual Table of Contents Introduction Dashboard Section Reporting Section My Settings Section My Account Section Billing Section Help Section 2 4 7 15 20 25 27 1 Introduction SMTP
Account Customer Portal Manual Table of Contents Introduction Dashboard Section Reporting Section My Settings Section My Account Section Billing Section Help Section 2 4 7 15 20 25 27 1 Introduction SMTP
McAfee Network Security Platform Administration Course
 McAfee Network Security Platform Administration Course Education Services administration course The McAfee Network Security Platform Administration course from McAfee Education Services is an essential
McAfee Network Security Platform Administration Course Education Services administration course The McAfee Network Security Platform Administration course from McAfee Education Services is an essential
CAHIIM HELP for Program Users
 CAHIIM HELP for Program Users 2018 CAHIIM Table of Contents GETTING STARTED... 1 Performing Basic Functions... 1 Logging In... 1 Logging Out... 1 Resetting Password... 1 Viewing or Changing User Information...
CAHIIM HELP for Program Users 2018 CAHIIM Table of Contents GETTING STARTED... 1 Performing Basic Functions... 1 Logging In... 1 Logging Out... 1 Resetting Password... 1 Viewing or Changing User Information...
Flowmon Application for QRadar User Guide
 Flowmon Application for QRadar User Guide Version 01.00.00 Flowmon Application for QRadar is an extension connecting IBM QRadar with events from Flowmon ADS Solution. Flowmon Application was build with
Flowmon Application for QRadar User Guide Version 01.00.00 Flowmon Application for QRadar is an extension connecting IBM QRadar with events from Flowmon ADS Solution. Flowmon Application was build with
Bill Analyser User Guide
 Bill Analyser User Guide emobile.ie/business Contents 1.0 Basic Concepts... 3 1.1 Users and Roles... 3 Standard Users... 3 Global Users... 3 eircom User Roles... 3 Available user roles... 3 1.2 Data Structure...
Bill Analyser User Guide emobile.ie/business Contents 1.0 Basic Concepts... 3 1.1 Users and Roles... 3 Standard Users... 3 Global Users... 3 eircom User Roles... 3 Available user roles... 3 1.2 Data Structure...
Sophos XG Firewall v Release Notes. Sophos XG Firewall Reports Guide v17
 Sophos XG Firewall v 15.01.0 Release Notes Sophos XG Firewall Reports Guide v17 For Sophos Customers Document Date: October 2017 Contents ii Contents Reports... 4 Basics...4 Reports Navigation... 6 Dashboards...
Sophos XG Firewall v 15.01.0 Release Notes Sophos XG Firewall Reports Guide v17 For Sophos Customers Document Date: October 2017 Contents ii Contents Reports... 4 Basics...4 Reports Navigation... 6 Dashboards...
Help Contents Manual
 Help Contents Manual TimeClick 18 018 Last Updated: February 18 1 Table of Contents WHAT TO EXPECT WITH THIS MANUAL... 4 Resources Found on Website and Blog... 4 Contact Customer Support Team... 4 PREFERENCES...
Help Contents Manual TimeClick 18 018 Last Updated: February 18 1 Table of Contents WHAT TO EXPECT WITH THIS MANUAL... 4 Resources Found on Website and Blog... 4 Contact Customer Support Team... 4 PREFERENCES...
The following topics describe how to configure correlation policies and rules.
 The following topics describe how to configure correlation policies and rules. Introduction to and Rules, page 1 Configuring, page 2 Configuring Correlation Rules, page 5 Configuring Correlation Response
The following topics describe how to configure correlation policies and rules. Introduction to and Rules, page 1 Configuring, page 2 Configuring Correlation Rules, page 5 Configuring Correlation Response
Administrator Manual
 Administrator Manual CURA Technical Support Email: cura_support@mindscope.com Phone: 1.888.322.2362 x 55 Administrator Manual Page 1 Table of Contents The Setup Module... 3 Skills... 3 Adding or Modifying
Administrator Manual CURA Technical Support Email: cura_support@mindscope.com Phone: 1.888.322.2362 x 55 Administrator Manual Page 1 Table of Contents The Setup Module... 3 Skills... 3 Adding or Modifying
Packet Tracer - Investigating the TCP/IP and OSI Models in Action (Instructor Version Optional Packet Tracer)
 (Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
(Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
XO Stats: User Guide. Monitor your circuit performance, troubleshoot, and plan future network capacity requirements
 XO Stats: User Guide Monitor your circuit performance, troubleshoot, and plan future network capacity requirements XO Stats is a web-based portal that allows you, an XO Communications data and Internet
XO Stats: User Guide Monitor your circuit performance, troubleshoot, and plan future network capacity requirements XO Stats is a web-based portal that allows you, an XO Communications data and Internet
Configuring the Botnet Traffic Filter
 CHAPTER 46 Malware is malicious software that is installed on an unknowing host. Malware that attempts network activity such as sending private data (passwords, credit card numbers, key strokes, or proprietary
CHAPTER 46 Malware is malicious software that is installed on an unknowing host. Malware that attempts network activity such as sending private data (passwords, credit card numbers, key strokes, or proprietary
Kaseya 2. User Guide. Version 7.0. English
 Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Halo Mobile App Guide. ios
 Halo Mobile App Guide ios Contents Getting Started... 4 Invitation, Registration and Activation... 4 Sign-In... 4 Messages... 5 Generating a Secure Message... 5 Message Status... 5 Quick Group Message...
Halo Mobile App Guide ios Contents Getting Started... 4 Invitation, Registration and Activation... 4 Sign-In... 4 Messages... 5 Generating a Secure Message... 5 Message Status... 5 Quick Group Message...
SIMPLIFi Compliance Software User Manual
 SIMPLIFi Compliance Software User Manual Version 1.7 2013 Simplifi-Solutions Ltd, Environmental Center, Unit B5, The Gordon Manley Building, Lancaster University, LA1 4WA Telephone: 01524 510431 Email:
SIMPLIFi Compliance Software User Manual Version 1.7 2013 Simplifi-Solutions Ltd, Environmental Center, Unit B5, The Gordon Manley Building, Lancaster University, LA1 4WA Telephone: 01524 510431 Email:
User Guide. Version R95. English
 Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
About Clients, on page 1 Monitor and Troubleshoot the Health of a Client Device, on page 10. Monitor and Troubleshoot the Health of All Client Devices
 About Clients, on page 1 Monitor and Troubleshoot the Health of All Client Devices, on page 1 Monitor and Troubleshoot the Health of a Client Device, on page 10 Trace the Path of a Device, on page 13 About
About Clients, on page 1 Monitor and Troubleshoot the Health of All Client Devices, on page 1 Monitor and Troubleshoot the Health of a Client Device, on page 10 Trace the Path of a Device, on page 13 About
Pass4sure q. Cisco Securing Cisco Networks with Sourcefire IPS
 Pass4sure.500-285.42q Number: 500-285 Passing Score: 800 Time Limit: 120 min File Version: 6.1 Cisco 500-285 Securing Cisco Networks with Sourcefire IPS I'm quite happy to announce that I passed 500-285
Pass4sure.500-285.42q Number: 500-285 Passing Score: 800 Time Limit: 120 min File Version: 6.1 Cisco 500-285 Securing Cisco Networks with Sourcefire IPS I'm quite happy to announce that I passed 500-285
This documentation explains features that are located in the Dashboards menu, this is located on the top navigation bar.
 Purpose This document describes how to use queries and filters to drill down to see the exact information you are looking for using Dashboards. Target Audience This document is intended for use by administrators
Purpose This document describes how to use queries and filters to drill down to see the exact information you are looking for using Dashboards. Target Audience This document is intended for use by administrators
My Team And Manager Reports Rev 2
 My Team And Manager Reports 20141210 Rev 2 1 Contents My Team Overview... 3 My Team Search... 7 Action Items... 8 Tasks Overview... 8 Assign Training... 11 Profile Overview... 13 Transcript... 15 Calendar
My Team And Manager Reports 20141210 Rev 2 1 Contents My Team Overview... 3 My Team Search... 7 Action Items... 8 Tasks Overview... 8 Assign Training... 11 Profile Overview... 13 Transcript... 15 Calendar
Amazing Reminders User Guide
 Amazing Reminders User Guide Contents Amazing Reminders Overview... 2 Installing Amazing Reminders... 3 Version 9.1 and higher... 3 Version 7.1.3 to Version 9.0... 4 Reminders Settings... 9 Reminders Timeframe
Amazing Reminders User Guide Contents Amazing Reminders Overview... 2 Installing Amazing Reminders... 3 Version 9.1 and higher... 3 Version 7.1.3 to Version 9.0... 4 Reminders Settings... 9 Reminders Timeframe
Managing Configurations
 CHAPTER 3 The Configurations page is your starting point for managing device configurations for network elements managed by Cisco Prime Network by using the CM tools. The following table lists the main
CHAPTER 3 The Configurations page is your starting point for managing device configurations for network elements managed by Cisco Prime Network by using the CM tools. The following table lists the main
sforce Web Services Enterprise API sforce Object Query Language sforce Custom Objects... 40
 Release Notes Winter 04 Major Announcements Dashboards... 2 Workflow Automation... 8 Advanced Page Layout Wizard... 12 Dynamic Page Layouts and Field-Level Security... 14 Team-Based Account Management...
Release Notes Winter 04 Major Announcements Dashboards... 2 Workflow Automation... 8 Advanced Page Layout Wizard... 12 Dynamic Page Layouts and Field-Level Security... 14 Team-Based Account Management...
User Guide. Version R92. English
 AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
BT CLOUD VOICE COMMUNICATOR USER GUIDE.
 BT CLOUD VOICE COMMUNICATOR iphone EDITION. USER GUIDE. WHAT S IN THIS GUIDE. 1. Introduction. 3 1.1 Overview 3 1.2 Audience 3 2. Requirements. 4 2.1 Hardware & Software Requirements 4 2.2 Licensing Requirements
BT CLOUD VOICE COMMUNICATOR iphone EDITION. USER GUIDE. WHAT S IN THIS GUIDE. 1. Introduction. 3 1.1 Overview 3 1.2 Audience 3 2. Requirements. 4 2.1 Hardware & Software Requirements 4 2.2 Licensing Requirements
Sophos Central Admin. help
 help Contents About Sophos Central... 1 Activate Your License...2 Overview... 3 Dashboard...3 Alerts...4 Logs & Reports... 10 People... 25 Devices... 34 Global Settings...50 Protect Devices...78 Endpoint
help Contents About Sophos Central... 1 Activate Your License...2 Overview... 3 Dashboard...3 Alerts...4 Logs & Reports... 10 People... 25 Devices... 34 Global Settings...50 Protect Devices...78 Endpoint
Client Setup (.NET, Internet Explorer)
 Powered By: Version 2.0 Created December, 2008 .NET & Internet Explorer Setup Client Setup (.NET, Internet Explorer) The WebTMS application itself is a windows executable program. In order to run WebTMS,
Powered By: Version 2.0 Created December, 2008 .NET & Internet Explorer Setup Client Setup (.NET, Internet Explorer) The WebTMS application itself is a windows executable program. In order to run WebTMS,
Performance Management Reporting User Guide for EPMR
 Performance Management Reporting User Guide for EPMR January, 2015 2015 by Cox Communications. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means,
Performance Management Reporting User Guide for EPMR January, 2015 2015 by Cox Communications. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means,
Virtual Security Operations Center Portal Reports User Guide. October, 2016
 Virtual Security Operations Center Portal Reports User Guide October, 2016 Copyright IBM Corporation 2010, 2013, 2014, 2016 Table of Contents OVERVIEW... 3 REPORTING HIGHLIGHTS... 3 REPORT DASHBOARD...
Virtual Security Operations Center Portal Reports User Guide October, 2016 Copyright IBM Corporation 2010, 2013, 2014, 2016 Table of Contents OVERVIEW... 3 REPORTING HIGHLIGHTS... 3 REPORT DASHBOARD...
Centerity Monitor User Guide
 Centerity Monitor 4.10 User Guide July 2018 Page 2 End-User License Agreement (EULA) This guide and the use of Centerity software is subject to Centerity s End-User License Agreement (EULA). A copy of
Centerity Monitor 4.10 User Guide July 2018 Page 2 End-User License Agreement (EULA) This guide and the use of Centerity software is subject to Centerity s End-User License Agreement (EULA). A copy of
Sentinel Drive User Guide For Android Devices and MDTs
 Sentinel Drive 4.4.5 User Guide For Android Devices and MDTs January 2017 2016 BSM Technologies Ltd., All rights reserved Page 1 About this document This guide will help you familiarize yourself with the
Sentinel Drive 4.4.5 User Guide For Android Devices and MDTs January 2017 2016 BSM Technologies Ltd., All rights reserved Page 1 About this document This guide will help you familiarize yourself with the
The Vectra App for Splunk. Table of Contents. Overview... 2 Getting started Setup... 4 Using the Vectra App for Splunk... 4
 Table of Contents Overview... 2 Getting started... 3 Installation... 3 Setup... 4 Using the Vectra App for Splunk... 4 The Vectra Dashboard... 5 Hosts... 7 Detections... 8 Correlations... 9 Technical support...
Table of Contents Overview... 2 Getting started... 3 Installation... 3 Setup... 4 Using the Vectra App for Splunk... 4 The Vectra Dashboard... 5 Hosts... 7 Detections... 8 Correlations... 9 Technical support...
WEB TIME SUPERVISOR GUIDE
 Revised 02/23/2018 WEB TIME SUPERVISOR GUIDE CLIENT RESOURCE PAYLOCITY.COM TABLE OF CONTENTS Web Time... 3 Home... 15 Employees... 28 Reports... 130 Web Kiosk Setup... 132 Glossary... 156 Index... 158
Revised 02/23/2018 WEB TIME SUPERVISOR GUIDE CLIENT RESOURCE PAYLOCITY.COM TABLE OF CONTENTS Web Time... 3 Home... 15 Employees... 28 Reports... 130 Web Kiosk Setup... 132 Glossary... 156 Index... 158
Cascade Health Alliance. User Guide. Authorization Management Provider Portal
 Cascade Health Alliance User Guide Authorization Management Provider Portal 8-16-2017 Table of Contents USING THIS GUIDE... 2 SIGNING IN... 2 PROVIDER PORTAL NAVIGATION... 3 Portal... 3 Core... 3 Resources...
Cascade Health Alliance User Guide Authorization Management Provider Portal 8-16-2017 Table of Contents USING THIS GUIDE... 2 SIGNING IN... 2 PROVIDER PORTAL NAVIGATION... 3 Portal... 3 Core... 3 Resources...
Using Diagnostic Tools
 Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Copyright 2018 ARRIS Enterprises, LLC. All rights reserved. Ruckus Incentive Center MDF Training Guide
 Ruckus Incentive Center MDF Training Guide What s included in this guide? How to apply to be a Ruckus Ready Partner How to access the Ruckus Partner Portal How to access the Ruckus Incentive Center and
Ruckus Incentive Center MDF Training Guide What s included in this guide? How to apply to be a Ruckus Ready Partner How to access the Ruckus Partner Portal How to access the Ruckus Incentive Center and
Quick Reference Guide Work Goal Form Employee
 INTRODUCTION This Quick Reference Guide provides instructions for completing your Year-End Self-Assessment via the 2016 Work Goal Year-End Review form. This Quick Reference Guide explains the process from
INTRODUCTION This Quick Reference Guide provides instructions for completing your Year-End Self-Assessment via the 2016 Work Goal Year-End Review form. This Quick Reference Guide explains the process from
How to Monitor Network Activity with the Windows Security & Firewall Logs to Detect Inbound and Outbound Attacks. Made possible by
 How to Monitor Network Activity with the Windows Security & Firewall Logs to Detect Inbound and Outbound Attacks Sponsored by 2014 Monterey Technology Group Inc. Made possible by Thanks to LOG & EVENT
How to Monitor Network Activity with the Windows Security & Firewall Logs to Detect Inbound and Outbound Attacks Sponsored by 2014 Monterey Technology Group Inc. Made possible by Thanks to LOG & EVENT
Blackboard Student Quick Reference Guide
 Blackboard Student Quick Reference Guide Welcome to Blackboard, UTT s E-Learning System! This Quick Reference Guide is designed to help get you started using Blackboard Release 9.1.120113.0. Page 1 of
Blackboard Student Quick Reference Guide Welcome to Blackboard, UTT s E-Learning System! This Quick Reference Guide is designed to help get you started using Blackboard Release 9.1.120113.0. Page 1 of
User s Manual. Version 5
 User s Manual Version 5 Copyright 2017 Safeway. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language,
User s Manual Version 5 Copyright 2017 Safeway. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language,
BIG-IP Analytics: Implementations. Version 13.1
 BIG-IP Analytics: Implementations Version 13.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles... 5 Overview:
BIG-IP Analytics: Implementations Version 13.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles... 5 Overview:
File Reputation Filtering and File Analysis
 This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
USER GUIDE for Salesforce
 for Salesforce USER GUIDE Contents 3 Introduction to Backupify 5 Quick-start guide 6 Administration 6 Logging in 6 Administrative dashboard 7 General settings 8 Account settings 9 Add services 9 Contact
for Salesforce USER GUIDE Contents 3 Introduction to Backupify 5 Quick-start guide 6 Administration 6 Logging in 6 Administrative dashboard 7 General settings 8 Account settings 9 Add services 9 Contact
L Y R A U S E R M A N U A L R A I N O T E S M O D U L E
 L Y R A U S E R M A N U A L R A I N O T E S M O D U L E CONTENTS 1. RAI Summary View... 2 1.1. RAI status... 2 1.2. Rules in RAI Summary View... 3 1.3. Customize RAI Summary View... 3 1.3.1. Show/hide
L Y R A U S E R M A N U A L R A I N O T E S M O D U L E CONTENTS 1. RAI Summary View... 2 1.1. RAI status... 2 1.2. Rules in RAI Summary View... 3 1.3. Customize RAI Summary View... 3 1.3.1. Show/hide
Paloalto Networks PCNSA EXAM
 Page No 1 m/ Paloalto Networks PCNSA EXAM Palo Alto Networks Certified Network Security Administrator Product: Full File For More Information: /PCNSA-dumps 2 Product Questions: 50 Version: 8.0 Question:
Page No 1 m/ Paloalto Networks PCNSA EXAM Palo Alto Networks Certified Network Security Administrator Product: Full File For More Information: /PCNSA-dumps 2 Product Questions: 50 Version: 8.0 Question:
REPORTS GRASP DATA. State of the Art Web-based Management Reporting Product. Recommended screen resolution 1024 x 768
 GRASP DATA State of the Art Web-based Management Reporting Product Recommended screen resolution 1024 x 768 (Locate on desktop under Control Panel / Display Settings) Website: www.graspdata.com User Name:
GRASP DATA State of the Art Web-based Management Reporting Product Recommended screen resolution 1024 x 768 (Locate on desktop under Control Panel / Display Settings) Website: www.graspdata.com User Name:
Sophos Central Admin. help
 help Contents About Sophos Central...1 Activate Your License... 2 Overview...3 Dashboard... 3 Alerts...4 Logs & Reports... 15 People...31 Devices... 41 Global Settings... 57 Protect Devices... 90 Endpoint
help Contents About Sophos Central...1 Activate Your License... 2 Overview...3 Dashboard... 3 Alerts...4 Logs & Reports... 15 People...31 Devices... 41 Global Settings... 57 Protect Devices... 90 Endpoint
Administrator Quick Guide
 1 Administrator Quick Guide Login Screen The first page employees will see when visiting their training site is the login screen. This is where employees must enter their username and password to access
1 Administrator Quick Guide Login Screen The first page employees will see when visiting their training site is the login screen. This is where employees must enter their username and password to access
GOBENCH IQ Release v
 GOBENCH IQ Release v1.2.3.3 2018-06-11 New Add-Ons / Features / Enhancements in GOBENCH IQ v1.2.3.3 GOBENCH IQ v1.2.3.3 contains several new features and enhancements ** New version of the comparison Excel
GOBENCH IQ Release v1.2.3.3 2018-06-11 New Add-Ons / Features / Enhancements in GOBENCH IQ v1.2.3.3 GOBENCH IQ v1.2.3.3 contains several new features and enhancements ** New version of the comparison Excel
Order Management Bookings - Getting Started Guide for Manufacturers
 Order Management Bookings - Getting Started Guide for Manufacturers Table Of Contents Order Management Bookings Getting Started Guide... 3 Purpose of this Document... 3 What is Order Management Bookings?...
Order Management Bookings - Getting Started Guide for Manufacturers Table Of Contents Order Management Bookings Getting Started Guide... 3 Purpose of this Document... 3 What is Order Management Bookings?...
System Configuration. The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices:
 The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices: Introduction to, page 2 Appliance Information, page 5 Custom HTTPS Certificates,
The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices: Introduction to, page 2 Appliance Information, page 5 Custom HTTPS Certificates,
Hosted Call Recording User Guide Hosted Voice Enterprise
 Hosted Call Recording User Guide Hosted Voice Enterprise April A Diehl 2/11/2016 Published Version 1.5 Copyright 2015, Bright House Networks: All rights reserved. Except as permitted under copyright law,
Hosted Call Recording User Guide Hosted Voice Enterprise April A Diehl 2/11/2016 Published Version 1.5 Copyright 2015, Bright House Networks: All rights reserved. Except as permitted under copyright law,
Configuring Logging for Access Lists
 CHAPTER 20 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This chapter includes the following
CHAPTER 20 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This chapter includes the following
Ivy migration guide Getting from Dashboard to Ivy
 Ivy migration guide Getting from Dashboard to Ivy Document history Revision Author Date Initial April Jones 2015-05-07 Rev. 1 April Jones 2015-05-14 Rev. 2 April Jones 2016-02-15 About this guide Teliax
Ivy migration guide Getting from Dashboard to Ivy Document history Revision Author Date Initial April Jones 2015-05-07 Rev. 1 April Jones 2015-05-14 Rev. 2 April Jones 2016-02-15 About this guide Teliax
User Guide. Version R93. English
 Anti-Malware User Guide Version R93 English March 17, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS
Anti-Malware User Guide Version R93 English March 17, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS
Halo Administrator GUIDE
 Halo Administrator GUIDE Contents Welcome to Halo... 3 Secure Sign-In... 4 Forgot Password... 4 Messages... 5 Create and Send a Message... 5 Message Enhancements... 6 Quick Note... 6 Mark as Urgent...
Halo Administrator GUIDE Contents Welcome to Halo... 3 Secure Sign-In... 4 Forgot Password... 4 Messages... 5 Create and Send a Message... 5 Message Enhancements... 6 Quick Note... 6 Mark as Urgent...
Raptor University. Volunteer Admin Training. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Volunteer Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes the detailed instruction of the following tasks to get you started using Raptor: Navigating Volunteer
Raptor University Volunteer Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes the detailed instruction of the following tasks to get you started using Raptor: Navigating Volunteer
Connection Logging. Introduction to Connection Logging
 The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: Introduction to, page 1 Strategies, page 2 Logging Decryptable Connections
The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: Introduction to, page 1 Strategies, page 2 Logging Decryptable Connections
SCRIBORDER E- TRANSCRIPTS - SENDING TRANSCRIPTS ELECTRONICALLY
 Training Guide BASIC FUNCTIONALITY... 2 LOGGING IN... 2 CHANGING PASSWORD... 3 HEADERS AND TABS... 4 ORDER LIST... 5 PROCESSING REQUESTS... 6 USING FILTERS... 6 COUPON CODES... 7 GRAB VS. GRAB AND PROCESS...
Training Guide BASIC FUNCTIONALITY... 2 LOGGING IN... 2 CHANGING PASSWORD... 3 HEADERS AND TABS... 4 ORDER LIST... 5 PROCESSING REQUESTS... 6 USING FILTERS... 6 COUPON CODES... 7 GRAB VS. GRAB AND PROCESS...
Lynx Mobile Enhancement Guide
 Lynx Mobile Enhancements April 29, 2011 On the evening of April 29 th, 2011, McKesson Specialty Care Solutions will enhance Lynx Mobile to add improved inventory and user management functionality. We are
Lynx Mobile Enhancements April 29, 2011 On the evening of April 29 th, 2011, McKesson Specialty Care Solutions will enhance Lynx Mobile to add improved inventory and user management functionality. We are
Seceon s Open Threat Management software
 Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Configuring Access Rules
 Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
EVERY NATION OUTLOOK WEB ACCESS (OWA) USER S GUIDE
 EVERY NATION OUTLOOK WEB ACCESS (OWA) USER S GUIDE Exchange 2003 Version Revised September 2005 TABLE OF CONTENTS WHAT S NEW IN OWA 2003?...2 General...2 Inbox and Message Composition...2 Tasks...2 INTRODUCTION
EVERY NATION OUTLOOK WEB ACCESS (OWA) USER S GUIDE Exchange 2003 Version Revised September 2005 TABLE OF CONTENTS WHAT S NEW IN OWA 2003?...2 General...2 Inbox and Message Composition...2 Tasks...2 INTRODUCTION
Connection Logging. About Connection Logging
 The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: About, page 1 Strategies, page 2 Logging Decryptable Connections with SSL
The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: About, page 1 Strategies, page 2 Logging Decryptable Connections with SSL
IS2000. Administrative Operator s Guide
 IS2000 Administrative Operator s Guide Table of Contents Logging Off... 7 Event Manager... 7 HARDWARE MANAGER... 8 Maneuvering the Hardware Tree... 8 Unlocking the Module... 8 Viewing the Hardware Tree...
IS2000 Administrative Operator s Guide Table of Contents Logging Off... 7 Event Manager... 7 HARDWARE MANAGER... 8 Maneuvering the Hardware Tree... 8 Unlocking the Module... 8 Viewing the Hardware Tree...
Virtual Communications Express Admin Guide: Call Recording
 Feature Overview The Call Recording service provides a fully hosted solution to record, store, organize, and access recordings of calls. The service can be used to help address regulatory compliance obligations,
Feature Overview The Call Recording service provides a fully hosted solution to record, store, organize, and access recordings of calls. The service can be used to help address regulatory compliance obligations,
Level 3 SM Enhanced Management - FAQs. Frequently Asked Questions for Level 3 Enhanced Management
 Level 3 SM Enhanced Management - FAQs Frequently Asked Questions for Level 3 Enhanced Management 2015 Level 3 Communications, LLC. All rights reserved. 1 LAYER 3: CONVERGED SERVICES 5 Where can I find
Level 3 SM Enhanced Management - FAQs Frequently Asked Questions for Level 3 Enhanced Management 2015 Level 3 Communications, LLC. All rights reserved. 1 LAYER 3: CONVERGED SERVICES 5 Where can I find
Call Center Administration
 Hosted VoIP Phone System Blue Platform Admin Portal Guide for Call Center Administration 1 Table of Contents 1 About this Guide... 3 2 Accessing the Hosted VoIP Phone System Administration Portal... 4
Hosted VoIP Phone System Blue Platform Admin Portal Guide for Call Center Administration 1 Table of Contents 1 About this Guide... 3 2 Accessing the Hosted VoIP Phone System Administration Portal... 4
Requisitioner Training Manual
 Requisitioner Training Manual Larry McWilliams Procurement Department lmcwilli@kent.edu Revised December 2018 0 Introduction The purpose of this training guide is to familiarize the user with FlashCart,
Requisitioner Training Manual Larry McWilliams Procurement Department lmcwilli@kent.edu Revised December 2018 0 Introduction The purpose of this training guide is to familiarize the user with FlashCart,
CLIQ Web Manager. User Manual. The global leader in door opening solutions V 6.1
 CLIQ Web Manager User Manual V 6.1 The global leader in door opening solutions Program version: 6.1 Document number: ST-003478 Date published: 2016-03-31 Language: en-gb Table of contents 1 Overview...9
CLIQ Web Manager User Manual V 6.1 The global leader in door opening solutions Program version: 6.1 Document number: ST-003478 Date published: 2016-03-31 Language: en-gb Table of contents 1 Overview...9
User Guide for Explorer Users
 User Guide for Explorer Users Version 2015.1 Hubble Suite (Edition 2) Document Information....................................................... 1 Notices.........................................................................
User Guide for Explorer Users Version 2015.1 Hubble Suite (Edition 2) Document Information....................................................... 1 Notices.........................................................................
Customer Portal User Guide
 Customer Portal User Guide COPYRIGHT NOTICE ViaWest Customer Portal User Guide is published and copyrighted 2012 by ViaWest Inc. All rights reserved. No part of this manual may be reproduced in any form,
Customer Portal User Guide COPYRIGHT NOTICE ViaWest Customer Portal User Guide is published and copyrighted 2012 by ViaWest Inc. All rights reserved. No part of this manual may be reproduced in any form,
07/ CONFIGURING SECURITY SETTINGS
 SECURITY LOG Malformed packet: Failed parsing a packed has been blocked because it is malformed. Maximum security enabled service a packet has been accepted because it belongs to a permitted service in
SECURITY LOG Malformed packet: Failed parsing a packed has been blocked because it is malformed. Maximum security enabled service a packet has been accepted because it belongs to a permitted service in
Web-Mon Guide. View E-Mon Web-Mon Product Page
 View E-Mon Web-Mon Product Page Web-Mon Guide ElectricSubmeter.com (A division of Test Equipment Depot) - 800.517.8431 99 Washington Street Melrose, MA 02176 - FAX 781.665.0780 PAGE 1 OF 47 Web-Mon User
View E-Mon Web-Mon Product Page Web-Mon Guide ElectricSubmeter.com (A division of Test Equipment Depot) - 800.517.8431 99 Washington Street Melrose, MA 02176 - FAX 781.665.0780 PAGE 1 OF 47 Web-Mon User
User Documentation. Administrator Manual.
 User Documentation Administrator Manual Proposal Software 1140 US Highway 287, Suite 400-102 Broomfield, CO 80020 USA Tel: 203.604.6597 www.proposalsoftware.com Table of Contents Open the WebPro Viewer...
User Documentation Administrator Manual Proposal Software 1140 US Highway 287, Suite 400-102 Broomfield, CO 80020 USA Tel: 203.604.6597 www.proposalsoftware.com Table of Contents Open the WebPro Viewer...
Peplink SD Switch User Manual. Published on October 25th, 2018
 Peplink SD Switch User Manual Published on October 25th, 2018 1 Table of Contents Switch Layout 4 Specifications 5 Hardware Overview 6 Quick Start Functions 7 Reset Switch 7 Connect Ethernet 7 Connect
Peplink SD Switch User Manual Published on October 25th, 2018 1 Table of Contents Switch Layout 4 Specifications 5 Hardware Overview 6 Quick Start Functions 7 Reset Switch 7 Connect Ethernet 7 Connect
Altus Call Recording. Dashboard Admin User Guide. Document Version Maryland Way, Suite 300 Brentwood, TN Tel
 Altus Call Recording Dashboard Admin User Guide Document Version 1.3 5121 Maryland Way, Suite 300 Brentwood, TN 37027 Tel +1 615.465.4001 WWW.ALTUSUC.COM Table of Contents About This Document... 5 1.1
Altus Call Recording Dashboard Admin User Guide Document Version 1.3 5121 Maryland Way, Suite 300 Brentwood, TN 37027 Tel +1 615.465.4001 WWW.ALTUSUC.COM Table of Contents About This Document... 5 1.1
Table of Contents. How SmartLINQ TruckTech+ Works Fault Code Indicators What the Driver Sees Sample Notification...
 Table of Contents How SmartLINQ TruckTech+ Works...................... 3 Fault Code Indicators What the Driver Sees... 4 Sample Email Notification... 5 What to Do After the Email Notification... 6 PACCAR
Table of Contents How SmartLINQ TruckTech+ Works...................... 3 Fault Code Indicators What the Driver Sees... 4 Sample Email Notification... 5 What to Do After the Email Notification... 6 PACCAR
Switching to Google Calendar from Microsoft Outlook Learning Center gsuite.google.com/learning-center
 Switching to Google Calendar from Microsoft Outlook 2010 Learning Center gsuite.google.com/learning-center Welcome to Google Calendar Now that you've switched from Microsoft Outlook to G Suite, learn how
Switching to Google Calendar from Microsoft Outlook 2010 Learning Center gsuite.google.com/learning-center Welcome to Google Calendar Now that you've switched from Microsoft Outlook to G Suite, learn how
WCB Online A User Guide for Tiered Service Providers
 WCB Online User Guide for Tiered Service Providers WCB Online A User Guide for Tiered Service Providers A Nova Scotians safe and secure from workplace injury Table of Contents WCB Online 1 Profile Creation
WCB Online User Guide for Tiered Service Providers WCB Online A User Guide for Tiered Service Providers A Nova Scotians safe and secure from workplace injury Table of Contents WCB Online 1 Profile Creation
Student User Guide (updated )
 Student User Guide (updated 2.06.06) Copyright 2005 iparadigms, LLC. All rights reserved. Contents Contents 1 Getting Started 4 Creating Your User Profile 4 Logging In 4 Enrolling in a Class 5 Submitting
Student User Guide (updated 2.06.06) Copyright 2005 iparadigms, LLC. All rights reserved. Contents Contents 1 Getting Started 4 Creating Your User Profile 4 Logging In 4 Enrolling in a Class 5 Submitting
Introduction Purpose... 4 Scope... 4 Icons Getting Started Logging In... 5 Logging Out... 5 Getting Help... 6 Navigating...
 Remedy Basic Features Version 2.2 Modified: 12/01/2017 TABLE OF CONTENTS Introduction... 4 Purpose... 4 Scope... 4 Icons... 4 Getting Started... 4 Logging In... 5 Logging Out... 5 Getting Help... 6 Navigating...
Remedy Basic Features Version 2.2 Modified: 12/01/2017 TABLE OF CONTENTS Introduction... 4 Purpose... 4 Scope... 4 Icons... 4 Getting Started... 4 Logging In... 5 Logging Out... 5 Getting Help... 6 Navigating...
Firewall Policy. Edit Firewall Policy/ACL CHAPTER7. Configure a Firewall Before Using the Firewall Policy Feature
 CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
Install & First Time Setup Guide
 cs@cyberonic.com CONTENTS www.cyberonic.com Install & First Time Setup Guide Cyberonic Development Team December 10, 2013 This guide should help you install and set-up the CMS software for use with a pre-configured
cs@cyberonic.com CONTENTS www.cyberonic.com Install & First Time Setup Guide Cyberonic Development Team December 10, 2013 This guide should help you install and set-up the CMS software for use with a pre-configured
Using the Manager Dashboard
 As a manager or staff member with access to review online or in-person training completions for employees in a department at UF or UF Health Shands, you can use this guide to help you complete the following
As a manager or staff member with access to review online or in-person training completions for employees in a department at UF or UF Health Shands, you can use this guide to help you complete the following
Cisco Partner Support Service (PSS) User Guide Cisco Services Connection
 Cisco Partner Support Service (PSS) User Guide Cisco Services Connection February 16, 2018 Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Cisco Partner Support Service (PSS) User Guide Cisco Services Connection February 16, 2018 Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
User Guide for TASKE Contact Web Interface
 User Guide for TASKE Contact Web Interface For Avaya Communication Manager with Application Enablement Services Version: 8.9 Date: 2011-06 This document is provided to you for informational purposes only.
User Guide for TASKE Contact Web Interface For Avaya Communication Manager with Application Enablement Services Version: 8.9 Date: 2011-06 This document is provided to you for informational purposes only.
BBVA Compass Spend Net Payables
 User Guide BBVA Compass Spend Net Payables User Guide Vault Services Table of Contents Introduction 2 Technical Requirements 2 Getting started 3 Sign In 3 General Navigation 4 Upload/Create Payment 5
User Guide BBVA Compass Spend Net Payables User Guide Vault Services Table of Contents Introduction 2 Technical Requirements 2 Getting started 3 Sign In 3 General Navigation 4 Upload/Create Payment 5
Using the Inbox to Manage Messages
 6 Using the Inbox to Manage Messages You can use the Outlook Inbox folder as well as the other mail-item folders (Drafts, Outbox, and Sent Items) to receive, send, and manage email, and send fax messages.
6 Using the Inbox to Manage Messages You can use the Outlook Inbox folder as well as the other mail-item folders (Drafts, Outbox, and Sent Items) to receive, send, and manage email, and send fax messages.
SecBlade Firewall Cards Attack Protection Configuration Example
 SecBlade Firewall Cards Attack Protection Configuration Example Keywords: Attack protection, scanning, blacklist Abstract: This document describes the attack protection functions of the SecBlade firewall
SecBlade Firewall Cards Attack Protection Configuration Example Keywords: Attack protection, scanning, blacklist Abstract: This document describes the attack protection functions of the SecBlade firewall
Centralized Policy, Virus, and Outbreak Quarantines
 Centralized Policy, Virus, and Outbreak Quarantines This chapter contains the following sections: Overview of Centralized Quarantines, page 1 Centralizing Policy, Virus, and Outbreak Quarantines, page
Centralized Policy, Virus, and Outbreak Quarantines This chapter contains the following sections: Overview of Centralized Quarantines, page 1 Centralizing Policy, Virus, and Outbreak Quarantines, page
Unified Performance Management Solution. User Guide
 Unified Performance Management Solution User Guide Copyright 2016 Colasoft. All rights reserved. Information in this document is subject to change without notice. No part of this document may be reproduced
Unified Performance Management Solution User Guide Copyright 2016 Colasoft. All rights reserved. Information in this document is subject to change without notice. No part of this document may be reproduced
Expense: Process Reports
 Expense: Process Reports User Guide for Standard Edition Applies to these SAP Concur solutions: Expense Professional/Premium edition Standard edition Travel Professional/Premium edition Standard edition
Expense: Process Reports User Guide for Standard Edition Applies to these SAP Concur solutions: Expense Professional/Premium edition Standard edition Travel Professional/Premium edition Standard edition
User Manual For SmartRoom Managers
 User Manual For SmartRoom Managers Table of Contents 1.0 Login 2.0 Confidentiality Agreement 3.0 Software Installation 4.0 Dashboard 5.0 Document Review and Index Maintenance 5.1 View by Index 5.1.1 Index
User Manual For SmartRoom Managers Table of Contents 1.0 Login 2.0 Confidentiality Agreement 3.0 Software Installation 4.0 Dashboard 5.0 Document Review and Index Maintenance 5.1 View by Index 5.1.1 Index
AccessEnforcer Version 4.0 Features List
 AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5)
 H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5) Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual
H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5) Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual
