Incident Response Exercise. June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan
|
|
|
- Conrad Russell
- 5 years ago
- Views:
Transcription
1 Incident Response Exercise June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan
2 Exercise Scenario [Systems environment] [Company A s system] OS: Debian Linux (6.0.5) [ ] Application: Web server(apache) To promote services/products Install Webapp for info-share (since Aug/2011) Can ssh login to server only from internal network Web Server Internet 2
3 Exercise Scenario [Phase 1] One day, System admin of Company A got phone call If I search company A on Google, I got strange message! Hey Company A, I can not see your web site! What is going on with our web?????? System Admin 3
4 Exercise Scenario[Investigation by system admin] System admin first accessed company A website. Web site seems working as usual. No visible error. Sys admin also asked his colleagues to check the web. Some said that they got following errors Search result What they got for company A web when accessed 4
5 Two major issues( at this moment) Website url is in Google s blacklist Web server might be compromised System admin had less knowledge about incident response. So they decide to leave this problem to AfricaCERT. 5
6 Exercise Scenario [logs] System admin shared with you only web server logs. Access log Rewrite log Check these logs and fill in following answer sheet. 6
7 CAUTION! IP addresses and domain names in this exercise is fake. Please do not access these from your laptop which is internet connected. 7
8 Connect to the IP address: User: ais01, ais02,, ais20 Password: same 8
9 Question 1 [Duration of log: When the log begin and end?] 10:21-10:59 [in this log, how many unique IP accessed to web?] 9
10 Question 2 [IP address of attacker. Pick up all that apply] [Date and time of web site compromise] 10
11 Question 3 [Describe what happen to users if they access to web site.] [What is the root cause of this incident?] 11
12 Question 4 [What Sys admin should do?] [What company A should do?] 12
13 Question 5 What We(AfricaCERT/JPCERT) can do for this case??? 13
14 HINTS AND CORRECT ANSWER 14
15 LOGS Apache log format is Combine ident status frank [10/Oct/2000:13:55: ] "GET /apache_pb.gif HTTP/1.0" SourceIP AuthID Date,time request Size of data [Reference] Apache HTTP server version 2.2 log file 15
16 HINT 1 List up all the services and applications on this server 16
17 HINT2 Pay attention to Request Methods Status code 17
18 HINT 3 If you find any suspicious IP, then use grep To pick up any access from that IP 18
19 Exercise Scenario [Extra] Upon investigation by system admin, it turned out that there is a suspicious. htaccess file on DocumentRoot directory [.httaccess content] 19
20 HINT4 The time rewrite log had changed, What was happened in Access log? 20
21 On website compromise cases Several possibility should be considered. Attackers login to the server by ssh and rewrite it. vulnerability in webapp vulnerability in language/framework(php/tomcat) Vulnerability in Operating system(linux, Win)/Server software(apache, IIS, mysql) All of these possibility should be in your mind 21
22 How we identified the problem [Two different web application on this server] wp? WordPress zenphoto Zenphoto Logs of zenphoto No suspicious line 22
23 How we identified the problem (Cont.) Next Wordpress??? Pick up all access from this guy.??????? 23
24 How we identified the problem (Cont.) Check for
25 How we identified the problem (Cont.) Compare logs Access log Rewrite log 25
26 From two log files [keyword] WordPress and timthumb.php Access from multiple ip addresses Rewrite log says access from search engines are redirected to suspicious page. Now you know how it happened? 26
27 Question 1 [Duration of log: When the log begin and end?] Begin: 07/Aug/2012:10:21:53 End: 07/Aug/2012:10:59:36 [in this log, how many unique IP accessed to web?] 78 unique IP addresses ( including one for sys admin) 27
28 Question 2 [IP address of attacker. Pick up all that apply] [Date and time of web site compromise] [from ] 2012/08/07 10:38:52 to10:50:43 [ ] 2012/08/07 10:23:59 and 10:24:29 [ ] 2012/08/07 10:22:59 to 2012/08/07 10:24:49 (every minutes) 28
29 Question 3 [Describe what happen to users if they access to web site.] After 10:41, users are redirected to After 10:50, users are redirected to [What is the root cause of this incident?] Vulnerability in WordPress plugin, timthumb.php JPCERT/CC WEEKLY REPORT WordPress の TimThumb スクリプトに脆弱性 29
30 Question 4 [What Sys admin should do?] discussion [What company A should do?] discussion 30
31 Question 5 What We(AfricaCERT/JPCERT) can do for this case??? discussion 31
32 Malicious PHP tool Enable bad guys to do any operation via web browser. Top Can execute command 32
33 .htaccess file Redirect users to arbitary sites base on the condition..htaccess file from compromised web server Cases like this(put the malicious.htaccess that redirect users to malware site) can be seen so often. 33
34 List of vulnerable sites There are several lists of vulnerable site in the internet. 34
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
WP Voting Plugin - Ohiowebtech Video Extension - Youtube Documentation
 WP Voting Plugin - Ohiowebtech Video Extension - Youtube Documentation Overview This documentation includes details about the WP Voting Plugin - Video Extension Plugin for Youtube. This extension will
WP Voting Plugin - Ohiowebtech Video Extension - Youtube Documentation Overview This documentation includes details about the WP Voting Plugin - Video Extension Plugin for Youtube. This extension will
JPCERT/CC Incident Handling Report [January 1, March 31, 2018]
![JPCERT/CC Incident Handling Report [January 1, March 31, 2018] JPCERT/CC Incident Handling Report [January 1, March 31, 2018]](/thumbs/89/100577955.jpg) JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Lecture Overview. IN5290 Ethical Hacking. Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing
 Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Advanced Threat Hunting:
 Advanced Threat Hunting: Identify and Track Adversaries Infiltrating Your Organization In Partnership with: Presented by: Randeep Gill Tony Shadrake Enterprise Security Engineer, Europe Regional Director,
Advanced Threat Hunting: Identify and Track Adversaries Infiltrating Your Organization In Partnership with: Presented by: Randeep Gill Tony Shadrake Enterprise Security Engineer, Europe Regional Director,
Setting up VPS on Ovh public cloud and installing lamp server on Ubuntu instance
 Setting up VPS on Ovh public cloud and installing lamp server on Ubuntu instance What is OVH Public Cloud Public Cloud Instances provides a choice of two types of virtual machines: the RAM instances are
Setting up VPS on Ovh public cloud and installing lamp server on Ubuntu instance What is OVH Public Cloud Public Cloud Instances provides a choice of two types of virtual machines: the RAM instances are
ULTEO OPEN VIRTUAL DESKTOP DEBIAN WHEEZY (7.0) SUPPORT
 ULTEO OPEN VIRTUAL DESKTOP V4.0.2 DEBIAN WHEEZY (7.0) SUPPORT Contents 1 Prerequisites: Debian Wheezy (7.0) 3 1.1 System Requirements.............................. 3 2 Repository 4 2.1 Online Method..................................
ULTEO OPEN VIRTUAL DESKTOP V4.0.2 DEBIAN WHEEZY (7.0) SUPPORT Contents 1 Prerequisites: Debian Wheezy (7.0) 3 1.1 System Requirements.............................. 3 2 Repository 4 2.1 Online Method..................................
We want to install putty, an ssh client on the laptops. In the web browser goto:
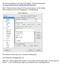 We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
Incident Response Tools
 Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Detecting Drive-by-Download Attacks based on HTTP Context-Types Ryo Kiire, Shigeki Goto Waseda University
 Detecting Drive-by-Download Attacks based on HTTP Context-Types Ryo Kiire, Shigeki Goto Waseda University 1 Outline Background Related Work Purpose Method Experiment Results Conclusion & Future Work 2
Detecting Drive-by-Download Attacks based on HTTP Context-Types Ryo Kiire, Shigeki Goto Waseda University 1 Outline Background Related Work Purpose Method Experiment Results Conclusion & Future Work 2
Detecting Lateral Movement in APTs ~Analysis Approach on Windows Event Logs~ June 17, 2016 Shingo ABE ICS security Response Group JPCERT/CC
 Detecting Lateral Movement in APTs ~Analysis Approach on Windows Event Logs~ June 17, 2016 Shingo ABE ICS security Response Group JPCERT/CC Agenda Introduction to JPCERT/CC About system-wide intrusions
Detecting Lateral Movement in APTs ~Analysis Approach on Windows Event Logs~ June 17, 2016 Shingo ABE ICS security Response Group JPCERT/CC Agenda Introduction to JPCERT/CC About system-wide intrusions
Monthly Research Web defacing attacks targeting WordPress
 Monthly Research Web defacing attacks targeting WordPress 株式会社 FFRI http://www.ffri.jp Ver 1.00.02 1 Introduction To infect with malware was main stream of web defacing attacks. But now We look again defacing
Monthly Research Web defacing attacks targeting WordPress 株式会社 FFRI http://www.ffri.jp Ver 1.00.02 1 Introduction To infect with malware was main stream of web defacing attacks. But now We look again defacing
WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN
 WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN Document Control Document Properties Title Author Document Type Filename File location
WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN Document Control Document Properties Title Author Document Type Filename File location
vol.15 August 1, 2017 JSOC Analysis Team
 vol.15 August 1, 2017 JSOC Analysis Team JSOC INSIGHT vol.15 1 Preface...2 2 Executive Summary...3 3 Trends in Severe Incidents at the JSOC...4 3.1 Trends in severe incidents... 4 3.2 Analysis of severe
vol.15 August 1, 2017 JSOC Analysis Team JSOC INSIGHT vol.15 1 Preface...2 2 Executive Summary...3 3 Trends in Severe Incidents at the JSOC...4 3.1 Trends in severe incidents... 4 3.2 Analysis of severe
Step by Step Guide Domain Security Pro
 Step by Step Guide Domain Security Pro by Mark Dulisse Copyright 2013 DomainSecurityPro.com Page 1 Copyright 2013 by DomainSecurityPro.com All rights reserved. No part of this publication may be reproduced,
Step by Step Guide Domain Security Pro by Mark Dulisse Copyright 2013 DomainSecurityPro.com Page 1 Copyright 2013 by DomainSecurityPro.com All rights reserved. No part of this publication may be reproduced,
Virtual Loaner Program
 IBM Virtual Loaner Program Virtual Loaner Program Creating and Managing a Reservation A Step-by-Step Guide What is Available Today? (as of July, 2006) System p POWER4 & POWER5 dedicated (root access) resources:
IBM Virtual Loaner Program Virtual Loaner Program Creating and Managing a Reservation A Step-by-Step Guide What is Available Today? (as of July, 2006) System p POWER4 & POWER5 dedicated (root access) resources:
epldt Web Builder Security March 2017
 epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
Web Hosting. Important features to consider
 Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Sim Bank Scheduler introduces: 1. Overview
 Sim Bank Scheduler User Manual Sim Bank Scheduler introduces: (for v1.00.1201109) Sim bank Scheduler server is Discovery Telecom s latest server software allowed SIM CARDS management and GOIP management.
Sim Bank Scheduler User Manual Sim Bank Scheduler introduces: (for v1.00.1201109) Sim bank Scheduler server is Discovery Telecom s latest server software allowed SIM CARDS management and GOIP management.
Contents. Introduction Upgrade your firmware to v Always use strong passwords Secure Web Admin user password...
 Contents Introduction... 1 1 Upgrade your firmware to v2.1.4... 2 2 Always use strong passwords... 2 2.1 Secure Web Admin user password... 2 2.2 Secure operator user password... 3 2.3 Secure extension
Contents Introduction... 1 1 Upgrade your firmware to v2.1.4... 2 2 Always use strong passwords... 2 2.1 Secure Web Admin user password... 2 2.2 Secure operator user password... 3 2.3 Secure extension
This FAQ is only applicable for hostings ordered after 23/6/2010
 Webhosting FAQ This FAQ is only applicable for hostings ordered after 23/6/2010 1. How do I access my Webhosting control panel?... 1 2. On which server is my hosting set up (IP)?... 4 3. How do I install
Webhosting FAQ This FAQ is only applicable for hostings ordered after 23/6/2010 1. How do I access my Webhosting control panel?... 1 2. On which server is my hosting set up (IP)?... 4 3. How do I install
Wordpress Security. GIMPA, November
 Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
Re3gistry development & testing - Bug #2895 Problems installing registry
 Re3gistry development & testing Bug #2895 Problems installing registry 02 Jan 2017 10:29 am Michael Östling Status: New Start date: 02 Jan 2017 Priority: Normal Due date: Assignee: Daniele Francioli %
Re3gistry development & testing Bug #2895 Problems installing registry 02 Jan 2017 10:29 am Michael Östling Status: New Start date: 02 Jan 2017 Priority: Normal Due date: Assignee: Daniele Francioli %
Http Error Code 403 Forbidden Dreamweaver Mysql
 Http Error Code 403 Forbidden Dreamweaver Mysql Dreamweaver Database Http Error Code 403 Forbidden 오류 403 Forbidden Adobe Systems Inc. Adobe Dreamweaver. 459. Dreamweaver Error 1045 오류. They can range
Http Error Code 403 Forbidden Dreamweaver Mysql Dreamweaver Database Http Error Code 403 Forbidden 오류 403 Forbidden Adobe Systems Inc. Adobe Dreamweaver. 459. Dreamweaver Error 1045 오류. They can range
How To Start Mysql Use Linux Command Line Windows 7
 How To Start Mysql Use Linux Command Line Windows 7 How can I check the number of active MySQL connections on Linux based system? You can Open the terminal App or login to the remote server using ssh:
How To Start Mysql Use Linux Command Line Windows 7 How can I check the number of active MySQL connections on Linux based system? You can Open the terminal App or login to the remote server using ssh:
Simulation Manager Configuration Guide
 Cornell University College of Veterinary Medicine Student Training Simulation Project Simulation Manager Configuration Guide 2018-Oct-1 Version 1.9 Prepared by: I-Town Design David Weiner 117 Burleigh
Cornell University College of Veterinary Medicine Student Training Simulation Project Simulation Manager Configuration Guide 2018-Oct-1 Version 1.9 Prepared by: I-Town Design David Weiner 117 Burleigh
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
Feasibility study of scenario based self training material for incident response
 24th Annual FIRST Conference Feasibility study of scenario based self training material for incident response June 21, 2012 Hitachi Incident Response Team Chief Technology and Coordination Designer Masato
24th Annual FIRST Conference Feasibility study of scenario based self training material for incident response June 21, 2012 Hitachi Incident Response Team Chief Technology and Coordination Designer Masato
Blog site (cont.) theme, 202 view creations, 205 Browser tools, 196 Buytaert, Dries, 185
 Index A Administration, 157 backups and restore (see Backups and restore website) file system, 161 log files, 162 tasks, 157 updates and security patches, 165 user accounts, 166 Aggregator module, 218
Index A Administration, 157 backups and restore (see Backups and restore website) file system, 161 log files, 162 tasks, 157 updates and security patches, 165 user accounts, 166 Aggregator module, 218
Automated Installation Guide for CentOS (PHP 7.x)
 Automated Installation Guide for CentOS (PHP 7.x) *Note: This script will not work on shared hosting, only works on CentOS dedicated server only. Prerequisites: Hardware: RAM: minimum 2 GB Processor: Core2duo
Automated Installation Guide for CentOS (PHP 7.x) *Note: This script will not work on shared hosting, only works on CentOS dedicated server only. Prerequisites: Hardware: RAM: minimum 2 GB Processor: Core2duo
Virtual Machine. Release 1.0. Howard Chivers
 Virtual Machine Release 1.0 Howard Chivers Feb 21, 2017 CONTENTS 1 Getting Started 2 1.1 The Virtual Machine.................................... 2 1.2 Exercise Documentation..................................
Virtual Machine Release 1.0 Howard Chivers Feb 21, 2017 CONTENTS 1 Getting Started 2 1.1 The Virtual Machine.................................... 2 1.2 Exercise Documentation..................................
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
Building a Web-based Health Promotion Database
 6 th International Conference on Applied Informatics Eger, Hungary, January 27 31, 2004. Building a Web-based Health Promotion Database Ádám Rutkovszky University of Debrecen, Faculty of Economics Department
6 th International Conference on Applied Informatics Eger, Hungary, January 27 31, 2004. Building a Web-based Health Promotion Database Ádám Rutkovszky University of Debrecen, Faculty of Economics Department
Computer Security Trend 2008 from Japan. SQL Injection, DNS cache poisoning, Phishing, Key logger Malware and Targeted Attacks
 Computer Security Trend 2008 from Japan SQL Injection, DNS cache poisoning, Phishing, Key logger Malware and Targeted Attacks JPCERT Coordination Center, Japan Manager of Watch and Warning Group Keisuke
Computer Security Trend 2008 from Japan SQL Injection, DNS cache poisoning, Phishing, Key logger Malware and Targeted Attacks JPCERT Coordination Center, Japan Manager of Watch and Warning Group Keisuke
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP.
 WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
Security issues. Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith
 Security issues Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith Criteria D3 D3 Recommend ways to improve web security when using web server scripting Clean browser input Don
Security issues Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith Criteria D3 D3 Recommend ways to improve web security when using web server scripting Clean browser input Don
Web Application Security Payloads. Andrés Riancho SecTor 2010, Toronto, Canada.
 Web Application Security Payloads Andrés Riancho SecTor 2010, Toronto, Canada. andres@rapid7.com$ whoami Director of Web Security @ Rapid7 Founder @ Bonsai Information Security Developer (python!) Open
Web Application Security Payloads Andrés Riancho SecTor 2010, Toronto, Canada. andres@rapid7.com$ whoami Director of Web Security @ Rapid7 Founder @ Bonsai Information Security Developer (python!) Open
Upgrading VIVO to release 1.8.1
 Upgrading VIVO to release 1.8.1 Author: Date: URL: Jim Blake Dec 1, 2017 1:32 PM https://wiki.duraspace.org/display/vivo/upgrading+vivo+to+release+1.8.1 1 of 11 Table of Contents 1 Before Performing the
Upgrading VIVO to release 1.8.1 Author: Date: URL: Jim Blake Dec 1, 2017 1:32 PM https://wiki.duraspace.org/display/vivo/upgrading+vivo+to+release+1.8.1 1 of 11 Table of Contents 1 Before Performing the
Vulnerability Assessment using Nessus
 Vulnerability Assessment using Nessus What you need Computer with VirtualBox. You can use any host OS you like, and if you prefer to use some other virtual machine software like VMware or Xen, that s fine
Vulnerability Assessment using Nessus What you need Computer with VirtualBox. You can use any host OS you like, and if you prefer to use some other virtual machine software like VMware or Xen, that s fine
5. A small dialog window appears; enter a new password twice (this is different from Dori!) and hit Go.
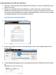 Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
WEB DESIGN & DEVELOPMENT
 WEB DESIGN & DEVELOPMENT Beautiful, functional, useful, easy to use. 46 0 1 Connec ti c ut A ve. N W Sui te 91 2 Wa s hi ng ton, DC 2 0008 INFOSHEET h e l l o @ s ab r acr e at i v e. co m 2 The right
WEB DESIGN & DEVELOPMENT Beautiful, functional, useful, easy to use. 46 0 1 Connec ti c ut A ve. N W Sui te 91 2 Wa s hi ng ton, DC 2 0008 INFOSHEET h e l l o @ s ab r acr e at i v e. co m 2 The right
Installing WordPress CMS
 Installing WordPress CMS Extract the contents of the wordpress zip file to D:/public_html/wordpress folder as shown in diagram 1. D:/public_html/wordpress is a virtual domain controlled by Apache Web server
Installing WordPress CMS Extract the contents of the wordpress zip file to D:/public_html/wordpress folder as shown in diagram 1. D:/public_html/wordpress is a virtual domain controlled by Apache Web server
For more info on Cloud9 see their documentation:
 Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Linux Essentials. Smith, Roderick W. Table of Contents ISBN-13: Introduction xvii. Chapter 1 Selecting an Operating System 1
 Linux Essentials Smith, Roderick W. ISBN-13: 9781118106792 Table of Contents Introduction xvii Chapter 1 Selecting an Operating System 1 What Is an OS? 1 What Is a Kernel? 1 What Else Identifies an OS?
Linux Essentials Smith, Roderick W. ISBN-13: 9781118106792 Table of Contents Introduction xvii Chapter 1 Selecting an Operating System 1 What Is an OS? 1 What Is a Kernel? 1 What Else Identifies an OS?
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Mysql Tutorial Create Database Username Password Through Phpmyadmin
 Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Static Webpage Development
 Dear Student, Based upon your enquiry we are pleased to send you the course curriculum for PHP Given below is the brief description for the course you are looking for: - Static Webpage Development Introduction
Dear Student, Based upon your enquiry we are pleased to send you the course curriculum for PHP Given below is the brief description for the course you are looking for: - Static Webpage Development Introduction
How To Redirect A Webpage Cheat Sheet
 How To Redirect A Webpage Cheat Sheet Need the code for your htaccess file? Check out our htaccess redirect generator here! Using Wordpress The easiest way to redirect a webpage on Wordpress is to use
How To Redirect A Webpage Cheat Sheet Need the code for your htaccess file? Check out our htaccess redirect generator here! Using Wordpress The easiest way to redirect a webpage on Wordpress is to use
Edu Expression WordPress Edition Version 1.0 Dated: 25th February, 2016
 User Guide for Edu Expression WordPress Edition Version 1.0 Dated: 25th February, 2016 Installation of Plug-in on Wordpress Login the Admin Dashboard of your Wordpress Installation Admin Plugin Add New
User Guide for Edu Expression WordPress Edition Version 1.0 Dated: 25th February, 2016 Installation of Plug-in on Wordpress Login the Admin Dashboard of your Wordpress Installation Admin Plugin Add New
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
Attacks Against Websites 3 The OWASP Top 10. Tom Chothia Computer Security, Lecture 14
 Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
Dammit Jim, I m a Mac Admin, not a Web Developer
 Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
WORDPRESS 101 A PRIMER JOHN WIEGAND
 WORDPRESS 101 A PRIMER JOHN WIEGAND CONTENTS Starters... 2 Users... 2 Settings... 3 Media... 6 Pages... 7 Posts... 7 Comments... 7 Design... 8 Themes... 8 Menus... 9 Posts... 11 Plugins... 11 To find a
WORDPRESS 101 A PRIMER JOHN WIEGAND CONTENTS Starters... 2 Users... 2 Settings... 3 Media... 6 Pages... 7 Posts... 7 Comments... 7 Design... 8 Themes... 8 Menus... 9 Posts... 11 Plugins... 11 To find a
How Breaches Really Happen
 How Breaches Really Happen www.10dsecurity.com About Dedicated Information Security Firm Clients Nationwide, primarily in financial industry Services Penetration Testing Social Engineering Vulnerability
How Breaches Really Happen www.10dsecurity.com About Dedicated Information Security Firm Clients Nationwide, primarily in financial industry Services Penetration Testing Social Engineering Vulnerability
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
Manually Create Phishing Page For Facebook 2014
 Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Services: Monitoring and Logging. 9/16/2018 IST346: Info Tech Management & Administration 1
 Services: Monitoring and Logging 9/16/2018 IST346: Info Tech Management & Administration 1 Recall: Server vs. Service A server is a computer. A service is an offering provided by server(s). HTTP 9/16/2018
Services: Monitoring and Logging 9/16/2018 IST346: Info Tech Management & Administration 1 Recall: Server vs. Service A server is a computer. A service is an offering provided by server(s). HTTP 9/16/2018
Website/Blog Admin Using WordPress
 Website/Blog Admin Using WordPress Table of Contents How to login... 2 How to get support... 2 About the WordPress dashboard... 3 WordPress pages vs posts... 3 How to add a new blog post... 5 How to edit
Website/Blog Admin Using WordPress Table of Contents How to login... 2 How to get support... 2 About the WordPress dashboard... 3 WordPress pages vs posts... 3 How to add a new blog post... 5 How to edit
Database Security Service. FAQs. Issue 19 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 19 Date 2019-04-08 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Issue 19 Date 2019-04-08 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2019. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
NET 311 INFORMATION SECURITY
 NET 311 INFORMATION SECURITY Networks and Communication Department Lec12: Software Security / Vulnerabilities lecture contents: o Vulnerabilities in programs Buffer Overflow Cross-site Scripting (XSS)
NET 311 INFORMATION SECURITY Networks and Communication Department Lec12: Software Security / Vulnerabilities lecture contents: o Vulnerabilities in programs Buffer Overflow Cross-site Scripting (XSS)
JPCERT/CC Internet Threat Monitoring Report [July 1, September 30, 2016]
![JPCERT/CC Internet Threat Monitoring Report [July 1, September 30, 2016] JPCERT/CC Internet Threat Monitoring Report [July 1, September 30, 2016]](/thumbs/90/104442060.jpg) JPCERT-IA-2016-03 Issued: 2016-11-16 JPCERT/CC Internet Threat Monitoring Report [July 1, 2016 - September 30, 2016] 1 Overview JPCERT/CC has placed multiple sensors across the Internet for monitoring
JPCERT-IA-2016-03 Issued: 2016-11-16 JPCERT/CC Internet Threat Monitoring Report [July 1, 2016 - September 30, 2016] 1 Overview JPCERT/CC has placed multiple sensors across the Internet for monitoring
DINOMI Call Center Module. Quick start guide v 1.1
 DINOMI Call Center Module Quick start guide v. DINOMI April 07 Table of contents Welcome to Dinomi Call Center... 4 Step : Install Dinomi... 5 Step : Connect to an external PBX and configure Dinomi...
DINOMI Call Center Module Quick start guide v. DINOMI April 07 Table of contents Welcome to Dinomi Call Center... 4 Step : Install Dinomi... 5 Step : Connect to an external PBX and configure Dinomi...
FREE ONLINE WEBSITE MALWARE SCANNER WEBSITE SECURITY
 PDF 11 AWESOME TOOLS FOR WEBSITE MALWARE SCANNING FREE ONLINE WEBSITE SECURITY 1 / 5 2 / 5 3 / 5 website malware scanner pdf Qualys Malware Detection helps you to scan continuously for malware against
PDF 11 AWESOME TOOLS FOR WEBSITE MALWARE SCANNING FREE ONLINE WEBSITE SECURITY 1 / 5 2 / 5 3 / 5 website malware scanner pdf Qualys Malware Detection helps you to scan continuously for malware against
Case Study. CMS for Management of Monetization Training Resources
 Case Study CMS for Management of Monetization Training Resources Client Requirement The client is a digital marketing company providing efficient strategies for marketing and data monetization to their
Case Study CMS for Management of Monetization Training Resources Client Requirement The client is a digital marketing company providing efficient strategies for marketing and data monetization to their
SuprCloakr v1.2s. Documentation. Author: tech_09
 SuprCloakr v1.2s Documentation Author: tech_09 http://www.suprcloakr.com Contents Installation... 3 Global settings... 4 Creating a campaign... 5 Cloak what?... 5 Cloak who?... 6 Cloak How?... 7 Installation
SuprCloakr v1.2s Documentation Author: tech_09 http://www.suprcloakr.com Contents Installation... 3 Global settings... 4 Creating a campaign... 5 Cloak what?... 5 Cloak who?... 6 Cloak How?... 7 Installation
Shell Script Not Running Via Cron Runs Fine Manually
 Shell Script Not Running Via Cron Runs Fine Manually to run every 15 minutes. I can execute the script manually but Crontab will not launch it successfully. shell script not running via crontab, runs fine
Shell Script Not Running Via Cron Runs Fine Manually to run every 15 minutes. I can execute the script manually but Crontab will not launch it successfully. shell script not running via crontab, runs fine
Let's have a look at the normal Joomla! URLs:
 Joomla! v 1.5 Search Engine Friendly URLs (SEF URLs) A. What are SEF URLs? SEF means search engine friendly. Websites are considered search engine friendly if the pages can easily be found by search engines.
Joomla! v 1.5 Search Engine Friendly URLs (SEF URLs) A. What are SEF URLs? SEF means search engine friendly. Websites are considered search engine friendly if the pages can easily be found by search engines.
(System) Integrity attacks System Abuse, Malicious File upload, SQL Injection
 Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
Setting Up A WordPress Blog
 Setting Up A WordPress Blog Introduction WordPress can be installed alongside an existing website to be used solely as the 'blog' element of a website, or it can be set up as the foundation for an entire
Setting Up A WordPress Blog Introduction WordPress can be installed alongside an existing website to be used solely as the 'blog' element of a website, or it can be set up as the foundation for an entire
CMS and e-commerce Solutions. version 1.0. Please, visit us at: or contact directly by
 Category Navigation for Magento User Guide version 1.0 created by IToris IToris Table of contents 1. Introduction... 3 1.1. Purpose... 3 2. Installation and License... 3 2.1. System Requirements... 3 2.2.
Category Navigation for Magento User Guide version 1.0 created by IToris IToris Table of contents 1. Introduction... 3 1.1. Purpose... 3 2. Installation and License... 3 2.1. System Requirements... 3 2.2.
LOMBA KETERAMPILAN SISWA
 LOMBA KETERAMPILAN SISWA SEKOLAH MENENGAH KEJURUAN TINGKAT NASIONAL XXV 2017 MODUL A LINUX ISLAND IT NETWORK SYSTEMS ADMINISTRATION LKS2017_ITNSA_MODUL_A 2 ISLAND A LINUX ISLAND CONTENTS This Test Project
LOMBA KETERAMPILAN SISWA SEKOLAH MENENGAH KEJURUAN TINGKAT NASIONAL XXV 2017 MODUL A LINUX ISLAND IT NETWORK SYSTEMS ADMINISTRATION LKS2017_ITNSA_MODUL_A 2 ISLAND A LINUX ISLAND CONTENTS This Test Project
ICAT Job Portal. a generic job submission system built on a scientific data catalog. IWSG 2013 ETH, Zurich, Switzerland 3-5 June 2013
 ICAT Job Portal a generic job submission system built on a scientific data catalog IWSG 2013 ETH, Zurich, Switzerland 3-5 June 2013 Steve Fisher, Kevin Phipps and Dan Rolfe Rutherford Appleton Laboratory
ICAT Job Portal a generic job submission system built on a scientific data catalog IWSG 2013 ETH, Zurich, Switzerland 3-5 June 2013 Steve Fisher, Kevin Phipps and Dan Rolfe Rutherford Appleton Laboratory
LizardThemes.com Free & Premium WordPress Themes. LizardThemes. User Guide. First Edition
 LizardThemes.com Free & Premium WordPress Themes LizardThemes User Guide First Edition Online version: http://lizardthemes.com/documentation/ 2013 Contents Chapter 1 How to start... 3 Chapter 2 Theme Settings...
LizardThemes.com Free & Premium WordPress Themes LizardThemes User Guide First Edition Online version: http://lizardthemes.com/documentation/ 2013 Contents Chapter 1 How to start... 3 Chapter 2 Theme Settings...
WWPass External Authentication Solution for IBM Security Access Manager 8.0
 WWPass External Authentication Solution for IBM Security Access Manager 8.0 Setup guide Enhance your IBM Security Access Manager for Web with the WWPass hardware authentication IBM Security Access Manager
WWPass External Authentication Solution for IBM Security Access Manager 8.0 Setup guide Enhance your IBM Security Access Manager for Web with the WWPass hardware authentication IBM Security Access Manager
Logging into the Firepower System
 The following topics describe how to log into the Firepower System: Firepower System User Accounts, on page 1 User Interfaces in Firepower Management Center Deployments, on page 3 Logging Into the Firepower
The following topics describe how to log into the Firepower System: Firepower System User Accounts, on page 1 User Interfaces in Firepower Management Center Deployments, on page 3 Logging Into the Firepower
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
Installing Joomla
 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
ForeScout Extended Module for Carbon Black
 ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
Exercises. Cacti Installation and Configuration
 Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Exercises. Cacti Installation and Configuration
 Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Manually Password Protect Directories Apache Ubuntu
 Manually Password Protect Directories Apache Ubuntu Apache can be configured to force users to login before being Password protection can be useful for securing a directory that planning to edit them manually,
Manually Password Protect Directories Apache Ubuntu Apache can be configured to force users to login before being Password protection can be useful for securing a directory that planning to edit them manually,
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE
 GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
An Introduction to. WordPress.com. ICA40311 Certificate IV in Web-Based Technologies Southbank Institute of Technology
 An Introduction to WordPress.com ICA40311 Certificate IV in Web-Based Technologies Southbank Institute of Technology Acknowledgement: This document was compiled from notes available via the WordPress.com
An Introduction to WordPress.com ICA40311 Certificate IV in Web-Based Technologies Southbank Institute of Technology Acknowledgement: This document was compiled from notes available via the WordPress.com
Using RANCID. Contents. 1 Introduction Goals Notes Install rancid Add alias Configure rancid...
 Using RANCID Contents 1 Introduction 2 1.1 Goals................................. 2 1.2 Notes................................. 2 2 Install rancid 2 2.1 Add alias............................... 3 2.2 Configure
Using RANCID Contents 1 Introduction 2 1.1 Goals................................. 2 1.2 Notes................................. 2 2 Install rancid 2 2.1 Add alias............................... 3 2.2 Configure
SQL Injection Attack Lab
 SEED Labs SQL Injection Attack Lab 1 SQL Injection Attack Lab Copyright 2006-2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation
SEED Labs SQL Injection Attack Lab 1 SQL Injection Attack Lab Copyright 2006-2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation
Build a Personal Website in WordPress
 Build a Personal Website in WordPress I. Installing WordPress Setting up a WordPress install on your own domain can be done by following these simple steps: SIGN IN TO DOMAINS 1. Go to https://domains.unf.edu
Build a Personal Website in WordPress I. Installing WordPress Setting up a WordPress install on your own domain can be done by following these simple steps: SIGN IN TO DOMAINS 1. Go to https://domains.unf.edu
WebGoat Lab session overview
 WebGoat Lab session overview Initial Setup Virtual Machine Tamper Data Web Goat Basics HTTP Basics Sniffing Web server attacks SQL Injection XSS INITIAL SETUP Tamper Data Hold alt to reveal the menu in
WebGoat Lab session overview Initial Setup Virtual Machine Tamper Data Web Goat Basics HTTP Basics Sniffing Web server attacks SQL Injection XSS INITIAL SETUP Tamper Data Hold alt to reveal the menu in
11 Most Common. WordPress Mistakes. And how to fix them
 11 Most Common WordPress Mistakes And how to fix them Introduction We all make mistakes from time to time but when it comes to WordPress, there are some mistakes that can have devastating consequences.
11 Most Common WordPress Mistakes And how to fix them Introduction We all make mistakes from time to time but when it comes to WordPress, there are some mistakes that can have devastating consequences.
Reflected XSS Cross-Site Request Forgery Other Attacks
 Reflected XSS Cross-Site Request Forgery Other Attacks CS 166: Introduction to Computer Systems Security 2/21/18 XSS, CSRF, Other Attacks 1 Reflected XSS 2/21/18 XSS, CSRF, Other Attacks 2 Recap of Persistent
Reflected XSS Cross-Site Request Forgery Other Attacks CS 166: Introduction to Computer Systems Security 2/21/18 XSS, CSRF, Other Attacks 1 Reflected XSS 2/21/18 XSS, CSRF, Other Attacks 2 Recap of Persistent
All India Council For Research & Training
 WEB DEVELOPMENT & DESIGNING Are you looking for a master program in web that covers everything related to web? Then yes! You have landed up on the right page. Web Master Course is an advanced web designing,
WEB DEVELOPMENT & DESIGNING Are you looking for a master program in web that covers everything related to web? Then yes! You have landed up on the right page. Web Master Course is an advanced web designing,
Exam4Free. Free valid exam questions and answers for certification exam prep
 Exam4Free http://www.exam4free.com Free valid exam questions and answers for certification exam prep Exam : MA0-150 Title : McAfee Certified Assessment Specialist- UH Vendors : McAfee Version : DEMO Get
Exam4Free http://www.exam4free.com Free valid exam questions and answers for certification exam prep Exam : MA0-150 Title : McAfee Certified Assessment Specialist- UH Vendors : McAfee Version : DEMO Get
Apache and... Virtual Hosts ---- aliases mod_rewrite ---- htaccess. 31 st Oct - 4 th Nov Blantyre, Malawi. Dorcas Muthoni.
 Apache and... Virtual Hosts ---- aliases mod_rewrite ---- htaccess AFNOG Chix 2011 Blantyre, Malawi 31 st Oct - 4 th Nov 2011 Dorcas Muthoni Courtesy: Hervey Allen Very good overview here: What is Apache?
Apache and... Virtual Hosts ---- aliases mod_rewrite ---- htaccess AFNOG Chix 2011 Blantyre, Malawi 31 st Oct - 4 th Nov 2011 Dorcas Muthoni Courtesy: Hervey Allen Very good overview here: What is Apache?
GRR Rapid Response. GRR ICDF2C Prague Mikhail Bushkov, Ben Galehouse
 GRR Rapid Response GRR Workshop @ ICDF2C Prague 2017 Mikhail Bushkov, Ben Galehouse Agenda Introduction to GRR Hands on work - exercises Discussion Remote Forensics at Google Scale Joe saw something weird,
GRR Rapid Response GRR Workshop @ ICDF2C Prague 2017 Mikhail Bushkov, Ben Galehouse Agenda Introduction to GRR Hands on work - exercises Discussion Remote Forensics at Google Scale Joe saw something weird,
The Wonderful World of Services. By: Stefanja
 The Wonderful World of Services By: Stefanja What Is a Service? Make the computer world go round Without Services we d have nothing A service is an application that runs in the background to enable a computer
The Wonderful World of Services By: Stefanja What Is a Service? Make the computer world go round Without Services we d have nothing A service is an application that runs in the background to enable a computer
Nextcloud 13: How to Get Started and Why You Should
 Nextcloud 13: How to Get Started and Why You Should Nextcloud could be the first step toward replacing proprietary services like Dropbox and Skype. By Marco Fioretti In its simplest form, the Nextcloud
Nextcloud 13: How to Get Started and Why You Should Nextcloud could be the first step toward replacing proprietary services like Dropbox and Skype. By Marco Fioretti In its simplest form, the Nextcloud
10 FOCUS AREAS FOR BREACH PREVENTION
 10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
Getting Started with Web Hosting, & FTP
 Getting Started with Web Hosting, Email & FTP Issue 1.01 Table of Contents Table of Contents... 1 Remove Parking from a Domain & Add Web Hosting... 3 Step 1... 3 Step 2... 3 Step 3... 4 Step 4... 4 Step
Getting Started with Web Hosting, Email & FTP Issue 1.01 Table of Contents Table of Contents... 1 Remove Parking from a Domain & Add Web Hosting... 3 Step 1... 3 Step 2... 3 Step 3... 4 Step 4... 4 Step
Yealink Device Management Platform Quick Start Guide. Applies to version or later
 Yealink Device Management Platform Quick Start Guide Applies to version 2.0.0.14 or later Overview Yealink device management platform allows administrators to efficiently realize centralized management
Yealink Device Management Platform Quick Start Guide Applies to version 2.0.0.14 or later Overview Yealink device management platform allows administrators to efficiently realize centralized management
Engineering Robust Server Software
 Engineering Robust Server Software Defense In Depth You Are Building YourAwesomeSite.com Django Built In Authen Sanitization Distrust clients Use all the best practices you know 2 You Are Building YourAwesomeSite.com
Engineering Robust Server Software Defense In Depth You Are Building YourAwesomeSite.com Django Built In Authen Sanitization Distrust clients Use all the best practices you know 2 You Are Building YourAwesomeSite.com
