Timer DRAM DDD FM9001 DRAM
|
|
|
- April Welch
- 5 years ago
- Views:
Transcription
1 indiana university computer science department technical report no. 385 Derivation of a DRAM Memory Interface by Sequential Decomposition Kamlesh Rath, Bhaskar Bose, and Steven D. Johnson june 993 To appear in the proceedings of the 993 IEEE International Conference on Computer Design (ICCD '93 ), Cambridge, Massachusetts, October, 993.
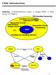
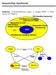
2 Derivation of a DRAM Memory Interface by Sequential Decomposition Kamlesh Rath y, Bhaskar Bose, and Steven D. Johnson Computer Science Department Indiana University Bloomington, IN Abstract Design and synthesis of DRAM based memory systems has been a dicult task in high-level system synthesis because of the relatively complex protocols involved. In this paper, we illustrate a method for topdown design of a DRAM memory interface using a transformational approach. Sequential decomposition of the DRAM memory interface entails extraction of a DRAM memory object from a system description that incorporates the read/write protocol and accounts for refresh cycles. We apply sequential decomposition to a non-trivial example, a formally derived realization of the Nqthm FM900 microprocessor specication [], called DDD-FM900 [2]. Introduction Derivation is a formalization of synthesis with more emphasis on \correct construction" than on design automation. Our tools are a set of transformations that are used to engineer an implementation from a specication, with each transformation accumulating information about the implementation. In a functional framework, a transformation called system factorization [3] was used earlier to extract functional components with naive interaction schemes. As a generalization of system factorization, we have developed sequential decomposition basedonanitestatemachine model to decompose a system description into interacting sequential machines [4]. A description of the interaction of a component with its environment is a parameter in the decomposition. Research reported herein was supported, in part, by NSF, under grants numbered MIP and MIP and by NASA, under grant number NGT To appear in Proceedings of ICCD '93, IEEE. y rathk@cs.indiana.edu A realization of the Nqthm FM900 [] specication, called DDD-FM900 [2], was derived using the DDD [5] system. The derivation involved using system factorization to decompose the memory component. Factorization imposed restrictions on the design limiting the memory to a static RAM realization. We now look at this example in the context of sequential decomposition to realize a DRAM memory.. Related Research Several researchers have looked at the issues involved in system synthesis. Borriello uses timing diagrams to specify the interface of a circuit and synthesis tools to generate the interface automatically [6]. While Boriello develops these external interface specications as a means to guide synthesis, our goal is to use them to guide design decomposition. Yajnik and Ciesielski [7] perform top-down machine decomposition by partitioning outputs and states in state graphs with the objective of performance and area optimization of synthesized PA circuits. Specication at dierent levels of abstraction and partitioning of control and data ow graphs for synthesis have been considered by Kuehlmann and Bergamaschi [8] to obtain smaller layouts. Our approach is to enable designers to decompose machines into logically and functionally distinct components. We do not use heuristics to partition a design based on layout constraints. Wolf et.al use a nite state machine model to specify a network of communicating machines and have control manipulation transformations to search the design space [9]. Drusinsky and Harel have used state-charts for bottom-up hierarchical specication [0] by embedding simpler state machines at a lower level of specication into states at a higher level of specication. The tree of state machines is then synthesized into a network of PAs.
3 In related formal methods research, Kurshan [] veries reactive systems by stepwise reduction and re- nement using -automata with language and process homomorphism. Davie [2] has used constraints on the target architecture and the context of a design in CIRCA to reduce the complexity of verication. As an alternative to bottom-up verication techniques, our approach facilitates top-down design by factoring sequential components from designs using transformations..2 DDD-FM900 The DDD-FM900 is a general purpose microprocessor realized in FPGAs, mechanically derived from Hunt's Nqthm FM900 specication []. The FM900 is a 32-bit microprocessor mechanically veried in the Nqthm theorem prover and implemented in SI ogic's gate array technology. Details of the derivation of the DDD-FM900 are reported in [2]. This paper shows the steps involved in the decomposition of a DRAM memory sub-system from the DDD-FM900 system description. Starting with specications for DRAM and DDD-FM900, we will derive the system organization shown in Figure. Timer DRAM DDD FM900 DRAM Manager Memory 2 Preliminaries Figure : System Organization We use Interface Specication anguage (IS) [4] to specify the interaction of a machine with its environment. All communication is modeled as values over connected ports. IS is based on nite state machine semantics, details of which are discussed in [4]. The complementation operation on machines is briey discussed. We discuss the notion of path implementation and show its use in the derivation exercise. A machine is dened as M = hs;t;r;f;p;vi, where S is the set of states, T is a non-empty set of transitions, r is the reset/start state, f is the nal state, P is the set of ports, and V is a domain of values. The set of ports (P = CI [ CO [ DI [ DO) isa union of the sets of control inputs, control outputs, data inputs, and data outputs. A transition is dened from a source state to a target state, s! s2,where is a label. = c + d, where the assignment functions are c : CI [ CO 7! f0; ; #g and d : DI[DO 7! V. The don't care value is denoted as #. The care set for a label denotes the set of ports that do not have don't care values according to the label. care = fp j(p) 6= #g. 2. Complement The environment of a machine can be constructed using the complement operation. For every output(input) port in a machine, a input(output) port is created in its complement. The complement machine retains the sets of values, states, reset, and nal states. For every transition, the complement machine has the same value on the corresponding ports. The set of transitions in the complement are: T = fs! s2 j s! s2 2 T and = Rename()g where Rename()(p 0 )=(p) ifp 0 = rename(p). 2.2 Path Implementation Each path from the reset state to the nal state in the complementmachine represents a valid sequence of interactions to complete a protocol. A machine can interact with an implementation of any interaction path of its complement machine. Sequential decomposition of a component from a system is accomplished by incorporating the appropriate path implementation of the complement of the componentinto the description of the rest of the system. Denition 2.: Theinclusion relationover transition labels is dened as: 2 () 8p 2 care : (p)= 2 (p) Denition 2.2: A maximal relation over states (S S S 2 )isapath simulation relation if s p s 2 implies:. 9s! s 0 ;s 2 2! s 0 2 : 2 ^ s 0 p s s! s 0 : (care \ CI ) 6= ) 2 9s 2! s 0 ^ 2 2 ^ s 0 p s 0 2 3: 9s! s ;s 2! s 0 :s 6= s 0 ^ (care 2 \ CI ) 6= ) (9s 2 22! s 0 2 :s 2 6= s 0 2 ^ 2 22 ^ s0 p s 0 2) ^ ((9s 2 2! s2 : 2) _ 23 (9s 2! sk : 23 ^ s p s k )) Denition 2.3: A machine M is path implemented by machine M 2 (M v p M 2 )if, r p r 2 ^ f p f 2, where r ;r 2 are the start states, and f ;f 2 are the nal states of M ;M 2.
4 3 DRAM Specication Simplied timing diagrams of the read and CASbefore-RAS refresh cycles adapted from the datasheets of the 256K-bit DRAM, TI-TMS4256, [3] are shown in Figures 2 and 3. The write cycle is similar to the read cycle. The state machine denoted by the DRAM speci- cation is shown in Figure 4. The read, write and refresh cycles are represented as three paths from the reset state to the nal state. The environment ofthe DRAM (DRAM), constructed using the complement operation, will be transformed into a path implementation that can interact with the DDD-FM900 and a refresh timer. RAS CAS ADDR DATA OUT RD/WT Hi Z Row Col Data,rw:,rw: dout/v read,not(rw):, not(rw):din/v write t0 t t2 Figure 2: Read cycle timing diagram CAS RAS t3 Figure 3: Refresh cycle timing diagram t [t a (C)] 50ns t 3 [t w (RH)] 90ns t 0 + t [t a (R)] 00ns t 4 [t w (R)] 00ns t 2 [t dis (CH)] 30ns The formulae above show the setup and hold timing constraints for normal read, write and CAS-before- RAS refresh cycles, and are used to manually choose the system clock speed. All the above constraints can be satised by choosing a clock interval greater than 00ns (clock speed < 0MHz) and letting t 0 ;t ;t 2 ;t 3 ; and t 4 correspond to a clock interval. DRAM(; cas; addr; dout; din; rw) 4 = ((; await cas; ; cas; ; not(cas); ) (; await ; not(cas) : addr=v row ;cas; ; t4 rw : addr=v col ; not(cas); ; rw : dout=v read ;) (; await ; not(cas) : addr=v row ;cas; ; not(rw) : addr=v col ; not(cas); ; not(rw) : din=v write ;)) The IS specication of the DRAM (shown above) is formulated from its timing diagrams and the chosen clock speed., rw are the control input ports. dout, anddin, addr are the data output and input ports. Figure 4: DRAM state diagram 4 Refresh Timer Derivation The DRAM specication lacks the information that a refresh cycle must be performed within 4ms of the previous refresh cycle. For a clock speed of 0Mhz, allowing a read/write cycle time of 400ns and refresh cycle time of 300ns, we use a 3.3ms timer to start the refresh cycle. The timer is set at the end of each refresh cycle and holds the done signal until it is set again. The timer can be specied in IS as : Timer(set; done) = 4 (; done until set) done set done Timer set, done, done, Path Implementation of DRAM Refresh Cycle Figure 5: Transformation of Timer 2 DRAM Refresh Cycle The next step in the derivation is to transform the complement of Timer (Timer) into a path implementation of Timer and DRAM (refresh cycle). The wait transition labeled done (marked in Figure 5) is unrolled into a state and a transition with the same label. The state marked 2 in Figure 5 is transformed into a wait state. The labels in corresponding transitions of the two path implementations are then unied.
5 5 Derivation of Read and Write Cycles In the next step of the derivation, the read and write operations on the abstract memory in DDD- FM900 are decomposed into a sequential component using the IS specications given below. The complements of the Read and Write descriptions are then transformed into a path implementation of DRAM. Read(dtack; strobe; RW; ADDR; DOUT) 4 = [; strobe; RW :ADDR=V addr until dtack :DIN=V read ] Write(dtack; strobe; RW; ADDR; DIN) 4 = [; strobe; not(rw) : ADDR=V addr ; DOUT=V write until dtack] (absmem mem0 read mem... (vdec tmp) tmp) DDD FM900 fragment with read operation ADDR/Vaddr ADDR/Vaddr Read Interface Specification Figure 6: DDD-FM900 Read Interface As shown in Figure 6, we incorporate the interface for Read into a lower level descripton of the DDD- FM900 by replacing each transition containing the read-mem operation with Read. The ports in Read are added to the DDD-FM900 description. Similarly, the write-mem operations in DDD-FM900 are replaced by instances of Write. 3 Read ADDR/Vaddr, addr/row(v addr),rw:, addr/col(v addr ),rw: ADDR/ Vaddr, dout/v read Path Implementation of DRAM read cycle Figure 7: Transformation of Read 4,rw:, rw: dout/v read DRAM read cycle Figure 7 shows the transformation of Read to a path implementation of DRAM (read cycle). The wait loop in the state marked 3 in Figure 7 is unrolled twice. The state marked 4 in Figure 7 is transformed into a wait state. The labels of the resulting state diagram are then unied. Similarly, Write is transformed to a path implementation of DRAM (write cycle), all accomplished by a predetermined set of available transformations. 6 Conclusion In this paper we have described the steps involved in the derivation of a DRAM memory sub-system using sequential decomposition. The DRAM manager is derived by transformation of the complements of the interface specications of the DRAM memory,the refresh timer, and the DDD-FM900, into a path implementation of each component. Each component in the system can then be synthesized with the assurance that it can interact with the rest of the system. References [] W. A. Hunt, \A formal HD and its use in the FM900 verication," in Mechanized Reasoning in Hardware Design, Prentice-Hall, 992. [2] B. Bose and S. D. Johnson, \DDD-FM900: Derivation of a veried microprocessor: An exercise in integrating verication with formal derivation," in Proceedings of CHARME '93, Springer, NCS 683. [3] S. D. Johnson, \Manipulating logical organization with system factorizations," in Hardware Specication, Verication and Synthesis: Mathematical Aspects, pp. 260{28, Springer, July 989. NCS 408. [4] K. Rath and S. D. Johnson, \Toward a basis for protocol specication and process decomposition," in Proceedings of CHD '93, Elsevier. [5] S. D. Johnson and B. Bose, \A system for mechanized digital design derivation," in Proceedings of ACM International Workshop on Formal Methods in VSI Design, January 99. [6] G. Borriello, \Specication and synthesis of interface logic," High-evel VSI Synthesis, 99. [7] M. K. Yajnik and M. J. Ciesielski, \Finite state machine decomposition using multi-way partitioning," in Proceedings of ICCD '92, pp. 320{323, IEEE. [8] A. Kuehlmann and R. A. Bergamaschi, \High-level state machine specication and synthesis," in Proceedings of ICCD '92, pp. 536{539, IEEE. [9] W. Wolf, A. Takach, and T.-C. ee, \Architectural optimization methods for control-dominated machines," High-evel VSI Synthesis, 99. [0] D. Drusinsky and D. Harel, \Using statecharts for hardware description and synthesis," Transactions on CAD, vol. 8, pp. 798{807, July 989. [] R. P. Kurshan, \Analysis of discrete event simulation," in Stepwise Renement of Distributed Systems pp. 44{453, Springer, July 989. NCS 430. [2] B. S. Davie, A Formal, Hierarchical Design and Validation Methodology for VSI. PhD thesis, University of Edinburgh, 988. [3] Texas Instruments, MOS Memory Data Book, 989.
opa opa opa opa opb opb opb op op ins) opa opb opb op ins) 8,9, 10,11 opa
 indiana university computer science department technical report no. 389 Behavior Tables: A Basis for System Representation and Transformational System Synthesis Kamlesh Rath, M. Esen Tuna, and Steven D.
indiana university computer science department technical report no. 389 Behavior Tables: A Basis for System Representation and Transformational System Synthesis Kamlesh Rath, M. Esen Tuna, and Steven D.
computer science department technical report no. 386 A Case Study of the Use of Formal Techniques to Achieve June 1993
 indiana university computer science department technical report no 386 System Factorization in Codesign A Case Study of the Use of Formal Techniques to Achieve Hardware-Software Decomposition Bhaskar Bose,
indiana university computer science department technical report no 386 System Factorization in Codesign A Case Study of the Use of Formal Techniques to Achieve Hardware-Software Decomposition Bhaskar Bose,
computer science department technical report no. 380 An Exercise in Integrating Verication with Formal Derivation may 1993
 indiana university computer science department technical report no. 380 DDD-FM9001: Derivation of a Veried Microprocessor An Exercise in Integrating Verication with Formal Derivation Bhaskar Bose and Steven
indiana university computer science department technical report no. 380 DDD-FM9001: Derivation of a Veried Microprocessor An Exercise in Integrating Verication with Formal Derivation Bhaskar Bose and Steven
Sequential-System Factorization. Kamlesh Rath. Submitted to the faculty of the University Graduate School. in partial fulllment of the requirements
 Sequential-System Factorization by Kamlesh Rath Submitted to the faculty of the University Graduate School in partial fulllment of the requirements for the degree Doctor of Philosophy in the Department
Sequential-System Factorization by Kamlesh Rath Submitted to the faculty of the University Graduate School in partial fulllment of the requirements for the degree Doctor of Philosophy in the Department
computer science department technical report no. 372 Integrating Boolean Verication with Formal Derivation february 1993
 indiana university computer science department technical report no. 372 Integrating Boolean Verication with Formal Derivation Bhaskar Bose, Steven D. Johnson, and Shyamsundar Pullela february 1993 To appear
indiana university computer science department technical report no. 372 Integrating Boolean Verication with Formal Derivation Bhaskar Bose, Steven D. Johnson, and Shyamsundar Pullela february 1993 To appear
DDD-FM9001: Derivation of a Verified Microprocessor t
 DDD-FM9001: Derivation of a Verified Microprocessor t An Exercise in Integrating Verification with Formal Derivation Bhaskar Bose and Steven D. Johnson Indiana University, Bloomington IN 47405, USA Abstract.
DDD-FM9001: Derivation of a Verified Microprocessor t An Exercise in Integrating Verification with Formal Derivation Bhaskar Bose and Steven D. Johnson Indiana University, Bloomington IN 47405, USA Abstract.
A Boolean Expression. Reachability Analysis or Bisimulation. Equation Solver. Boolean. equations.
 A Framework for Embedded Real-time System Design? Jin-Young Choi 1, Hee-Hwan Kwak 2, and Insup Lee 2 1 Department of Computer Science and Engineering, Korea Univerity choi@formal.korea.ac.kr 2 Department
A Framework for Embedded Real-time System Design? Jin-Young Choi 1, Hee-Hwan Kwak 2, and Insup Lee 2 1 Department of Computer Science and Engineering, Korea Univerity choi@formal.korea.ac.kr 2 Department
Rance Cleaveland The Concurrency Factory is an integrated toolset for specication, simulation,
 The Concurrency Factory Software Development Environment Rance Cleaveland (rance@csc.ncsu.edu) Philip M. Lewis (pml@cs.sunysb.edu) y Scott A. Smolka (sas@cs.sunysb.edu) y Oleg Sokolsky (oleg@ccc.com) y
The Concurrency Factory Software Development Environment Rance Cleaveland (rance@csc.ncsu.edu) Philip M. Lewis (pml@cs.sunysb.edu) y Scott A. Smolka (sas@cs.sunysb.edu) y Oleg Sokolsky (oleg@ccc.com) y
Solve the Data Flow Problem
 Gaining Condence in Distributed Systems Gleb Naumovich, Lori A. Clarke, and Leon J. Osterweil University of Massachusetts, Amherst Computer Science Department University of Massachusetts Amherst, Massachusetts
Gaining Condence in Distributed Systems Gleb Naumovich, Lori A. Clarke, and Leon J. Osterweil University of Massachusetts, Amherst Computer Science Department University of Massachusetts Amherst, Massachusetts
Assign auniquecodeto each state to produce a. Given jsj states, needed at least dlog jsje state bits. (minimum width encoding), at most jsj state bits
 State Assignment The problem: Assign auniquecodeto each state to produce a logic level description. Given jsj states, needed at least dlog jsje state bits (minimum width encoding), at most jsj state bits
State Assignment The problem: Assign auniquecodeto each state to produce a logic level description. Given jsj states, needed at least dlog jsje state bits (minimum width encoding), at most jsj state bits
DDD-FM9001: Derivation of a Veried Microprocessor y by Bhaskar Bose Submitted to the faculty of the Graduate School in partial fulllment of the requir
 DDD-FM9001: Derivation of a Veried Microprocessor y by Bhaskar Bose Submitted to the faculty of the Graduate School in partial fulllment of the requirements for the degree Doctor of Philosophy in the Department
DDD-FM9001: Derivation of a Veried Microprocessor y by Bhaskar Bose Submitted to the faculty of the Graduate School in partial fulllment of the requirements for the degree Doctor of Philosophy in the Department
Centre for Parallel Computing, University of Westminster, London, W1M 8JS
 Graphical Construction of Parallel Programs G. R. Ribeiro Justo Centre for Parallel Computing, University of Westminster, London, WM 8JS e-mail: justog@wmin.ac.uk, Abstract Parallel programming is not
Graphical Construction of Parallel Programs G. R. Ribeiro Justo Centre for Parallel Computing, University of Westminster, London, WM 8JS e-mail: justog@wmin.ac.uk, Abstract Parallel programming is not
Problem Set 10 Solutions
 CSE 260 Digital Computers: Organization and Logical Design Problem Set 10 Solutions Jon Turner thru 6.20 1. The diagram below shows a memory array containing 32 words of 2 bits each. Label each memory
CSE 260 Digital Computers: Organization and Logical Design Problem Set 10 Solutions Jon Turner thru 6.20 1. The diagram below shows a memory array containing 32 words of 2 bits each. Label each memory
Don't Cares in Multi-Level Network Optimization. Hamid Savoj. Abstract
 Don't Cares in Multi-Level Network Optimization Hamid Savoj University of California Berkeley, California Department of Electrical Engineering and Computer Sciences Abstract An important factor in the
Don't Cares in Multi-Level Network Optimization Hamid Savoj University of California Berkeley, California Department of Electrical Engineering and Computer Sciences Abstract An important factor in the
are discussed in Section 4. Finally, in Section 5, we make conclusions and give some directions for future research. 2 Formalization We aim at a const
 Constraints Specication at Higher Levels of Abstraction Felice Balarin, Jerry Burch, Luciano Lavagno, Yosinori Watanabe Cadence Berkeley Laboratories Berkeley, CA Roberto Passerone, Alberto Sangiovanni-Vincentelli
Constraints Specication at Higher Levels of Abstraction Felice Balarin, Jerry Burch, Luciano Lavagno, Yosinori Watanabe Cadence Berkeley Laboratories Berkeley, CA Roberto Passerone, Alberto Sangiovanni-Vincentelli
Introduction read-only memory random access memory
 Memory Interface Introduction Simple or complex, every microprocessorbased system has a memory system. Almost all systems contain two main types of memory: read-only memory (ROM) and random access memory
Memory Interface Introduction Simple or complex, every microprocessorbased system has a memory system. Almost all systems contain two main types of memory: read-only memory (ROM) and random access memory
A Note on Fairness in I/O Automata. Judi Romijn and Frits Vaandrager CWI. Abstract
 A Note on Fairness in I/O Automata Judi Romijn and Frits Vaandrager CWI P.O. Box 94079, 1090 GB Amsterdam, The Netherlands judi@cwi.nl, fritsv@cwi.nl Abstract Notions of weak and strong fairness are studied
A Note on Fairness in I/O Automata Judi Romijn and Frits Vaandrager CWI P.O. Box 94079, 1090 GB Amsterdam, The Netherlands judi@cwi.nl, fritsv@cwi.nl Abstract Notions of weak and strong fairness are studied
PPS : A Pipeline Path-based Scheduler. 46, Avenue Felix Viallet, Grenoble Cedex, France.
 : A Pipeline Path-based Scheduler Maher Rahmouni Ahmed A. Jerraya Laboratoire TIMA/lNPG,, Avenue Felix Viallet, 80 Grenoble Cedex, France Email:rahmouni@verdon.imag.fr Abstract This paper presents a scheduling
: A Pipeline Path-based Scheduler Maher Rahmouni Ahmed A. Jerraya Laboratoire TIMA/lNPG,, Avenue Felix Viallet, 80 Grenoble Cedex, France Email:rahmouni@verdon.imag.fr Abstract This paper presents a scheduling
History: Combinational Logic! single FSM! Hierarchy. Facilities for managing networks of FSMs MISII. Facilities for handling latches
 FSM Introduction History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
FSM Introduction History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
History: Combinational Logic! single FSM! Hierarchy. Facilities for managing networks of FSMs MISII. Facilities for handling latches
 Sequential Synthesis History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
Sequential Synthesis History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
AMD actual programming and testing on a system board. We will take a simple design example and go through the various stages of this design process.
 actual programming and testing on a system board. We will take a simple design example and go through the various stages of this design process. Conceptualize A Design Problem Select Device Implement Design
actual programming and testing on a system board. We will take a simple design example and go through the various stages of this design process. Conceptualize A Design Problem Select Device Implement Design
A technique for adding range restrictions to. August 30, Abstract. In a generalized searching problem, a set S of n colored geometric objects
 A technique for adding range restrictions to generalized searching problems Prosenjit Gupta Ravi Janardan y Michiel Smid z August 30, 1996 Abstract In a generalized searching problem, a set S of n colored
A technique for adding range restrictions to generalized searching problems Prosenjit Gupta Ravi Janardan y Michiel Smid z August 30, 1996 Abstract In a generalized searching problem, a set S of n colored
Chordal graphs and the characteristic polynomial
 Discrete Mathematics 262 (2003) 211 219 www.elsevier.com/locate/disc Chordal graphs and the characteristic polynomial Elizabeth W. McMahon ;1, Beth A. Shimkus 2, Jessica A. Wolfson 3 Department of Mathematics,
Discrete Mathematics 262 (2003) 211 219 www.elsevier.com/locate/disc Chordal graphs and the characteristic polynomial Elizabeth W. McMahon ;1, Beth A. Shimkus 2, Jessica A. Wolfson 3 Department of Mathematics,
160 M. Nadjarbashi, S.M. Fakhraie and A. Kaviani Figure 2. LUTB structure. each block-level track can be arbitrarily connected to each of 16 4-LUT inp
 Scientia Iranica, Vol. 11, No. 3, pp 159{164 c Sharif University of Technology, July 2004 On Routing Architecture for Hybrid FPGA M. Nadjarbashi, S.M. Fakhraie 1 and A. Kaviani 2 In this paper, the routing
Scientia Iranica, Vol. 11, No. 3, pp 159{164 c Sharif University of Technology, July 2004 On Routing Architecture for Hybrid FPGA M. Nadjarbashi, S.M. Fakhraie 1 and A. Kaviani 2 In this paper, the routing
Towards Verifying VHDL Descriptions of Processors.
 Towards Verifying VHDL Descriptions of Processors Laurent Arditi Helene Collavizza Universite de Nice { Sophia Antipolis, I3S, CNRS-URA 1376 arditi@unice.fr, helen@essi.fr Abstract We present a system
Towards Verifying VHDL Descriptions of Processors Laurent Arditi Helene Collavizza Universite de Nice { Sophia Antipolis, I3S, CNRS-URA 1376 arditi@unice.fr, helen@essi.fr Abstract We present a system
Optimized Implementation of Logic Functions
 June 25, 22 9:7 vra235_ch4 Sheet number Page number 49 black chapter 4 Optimized Implementation of Logic Functions 4. Nc3xe4, Nb8 d7 49 June 25, 22 9:7 vra235_ch4 Sheet number 2 Page number 5 black 5 CHAPTER
June 25, 22 9:7 vra235_ch4 Sheet number Page number 49 black chapter 4 Optimized Implementation of Logic Functions 4. Nc3xe4, Nb8 d7 49 June 25, 22 9:7 vra235_ch4 Sheet number 2 Page number 5 black 5 CHAPTER
DESIGN OF AN FFT PROCESSOR
 1 DESIGN OF AN FFT PROCESSOR Erik Nordhamn, Björn Sikström and Lars Wanhammar Department of Electrical Engineering Linköping University S-581 83 Linköping, Sweden Abstract In this paper we present a structured
1 DESIGN OF AN FFT PROCESSOR Erik Nordhamn, Björn Sikström and Lars Wanhammar Department of Electrical Engineering Linköping University S-581 83 Linköping, Sweden Abstract In this paper we present a structured
TIMED PETRI NETS FOR SOFTWARE APPLICATIONS
 The International Workshop on Discrete-Event System Design, DESDes 01, June 27 29, 2001; Przytok near Zielona Gora, Poland TIMED PETRI NETS FOR SOFTWARE APPLICATIONS Grzegorz ANDRZEJEWSKI Computer Engineering
The International Workshop on Discrete-Event System Design, DESDes 01, June 27 29, 2001; Przytok near Zielona Gora, Poland TIMED PETRI NETS FOR SOFTWARE APPLICATIONS Grzegorz ANDRZEJEWSKI Computer Engineering
Proc. XVIII Conf. Latinoamericana de Informatica, PANEL'92, pages , August Timed automata have been proposed in [1, 8] to model nite-s
![Proc. XVIII Conf. Latinoamericana de Informatica, PANEL'92, pages , August Timed automata have been proposed in [1, 8] to model nite-s Proc. XVIII Conf. Latinoamericana de Informatica, PANEL'92, pages , August Timed automata have been proposed in [1, 8] to model nite-s](/thumbs/74/70328679.jpg) Proc. XVIII Conf. Latinoamericana de Informatica, PANEL'92, pages 1243 1250, August 1992 1 Compiling Timed Algebras into Timed Automata Sergio Yovine VERIMAG Centre Equation, 2 Ave de Vignate, 38610 Gieres,
Proc. XVIII Conf. Latinoamericana de Informatica, PANEL'92, pages 1243 1250, August 1992 1 Compiling Timed Algebras into Timed Automata Sergio Yovine VERIMAG Centre Equation, 2 Ave de Vignate, 38610 Gieres,
Enhancing Integrated Layer Processing using Common Case. Anticipation and Data Dependence Analysis. Extended Abstract
 Enhancing Integrated Layer Processing using Common Case Anticipation and Data Dependence Analysis Extended Abstract Philippe Oechslin Computer Networking Lab Swiss Federal Institute of Technology DI-LTI
Enhancing Integrated Layer Processing using Common Case Anticipation and Data Dependence Analysis Extended Abstract Philippe Oechslin Computer Networking Lab Swiss Federal Institute of Technology DI-LTI
Enumeration of Full Graphs: Onset of the Asymptotic Region. Department of Mathematics. Massachusetts Institute of Technology. Cambridge, MA 02139
 Enumeration of Full Graphs: Onset of the Asymptotic Region L. J. Cowen D. J. Kleitman y F. Lasaga D. E. Sussman Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139 Abstract
Enumeration of Full Graphs: Onset of the Asymptotic Region L. J. Cowen D. J. Kleitman y F. Lasaga D. E. Sussman Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139 Abstract
Datapath Allocation. Zoltan Baruch. Computer Science Department, Technical University of Cluj-Napoca
 Datapath Allocation Zoltan Baruch Computer Science Department, Technical University of Cluj-Napoca e-mail: baruch@utcluj.ro Abstract. The datapath allocation is one of the basic operations executed in
Datapath Allocation Zoltan Baruch Computer Science Department, Technical University of Cluj-Napoca e-mail: baruch@utcluj.ro Abstract. The datapath allocation is one of the basic operations executed in
Synchronization Expressions: Characterization Results and. Implementation. Kai Salomaa y Sheng Yu y. Abstract
 Synchronization Expressions: Characterization Results and Implementation Kai Salomaa y Sheng Yu y Abstract Synchronization expressions are dened as restricted regular expressions that specify synchronization
Synchronization Expressions: Characterization Results and Implementation Kai Salomaa y Sheng Yu y Abstract Synchronization expressions are dened as restricted regular expressions that specify synchronization
1 Introduction Data format converters (DFCs) are used to permute the data from one format to another in signal processing and image processing applica
 A New Register Allocation Scheme for Low Power Data Format Converters Kala Srivatsan, Chaitali Chakrabarti Lori E. Lucke Department of Electrical Engineering Minnetronix, Inc. Arizona State University
A New Register Allocation Scheme for Low Power Data Format Converters Kala Srivatsan, Chaitali Chakrabarti Lori E. Lucke Department of Electrical Engineering Minnetronix, Inc. Arizona State University
On Checkpoint Latency. Nitin H. Vaidya. In the past, a large number of researchers have analyzed. the checkpointing and rollback recovery scheme
 On Checkpoint Latency Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail: vaidya@cs.tamu.edu Web: http://www.cs.tamu.edu/faculty/vaidya/ Abstract
On Checkpoint Latency Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail: vaidya@cs.tamu.edu Web: http://www.cs.tamu.edu/faculty/vaidya/ Abstract
FPGA Interfacing of HD44780 Based LCD Using Delayed Finite State Machine (FSM)
 FPGA Interfacing of HD44780 Based LCD Using Delayed Finite State Machine (FSM) Edwin NC Mui Custom R & D Engineer Texco Enterprise Ptd. Ltd. {blackgrail2000@hotmail.com} Abstract This paper presents a
FPGA Interfacing of HD44780 Based LCD Using Delayed Finite State Machine (FSM) Edwin NC Mui Custom R & D Engineer Texco Enterprise Ptd. Ltd. {blackgrail2000@hotmail.com} Abstract This paper presents a
MOCHA: Modularity in Model Checking??? Computing Science Research Center, Bell Laboratories.
 MOCHA: Modularity in Model Checking??? R. Alur 1, T.A. Henzinger 2, F.Y.C. Mang 2, S. Qadeer 2, S.K. Rajamani 2, and S. Tasiran 2 1 Computer & Information Science Department, University ofpennsylvania,
MOCHA: Modularity in Model Checking??? R. Alur 1, T.A. Henzinger 2, F.Y.C. Mang 2, S. Qadeer 2, S.K. Rajamani 2, and S. Tasiran 2 1 Computer & Information Science Department, University ofpennsylvania,
the application rule M : x:a: B N : A M N : (x:a: B) N and the reduction rule (x: A: B) N! Bfx := Ng. Their algorithm is not fully satisfactory in the
 The Semi-Full Closure of Pure Type Systems? Gilles Barthe Institutionen for Datavetenskap, Chalmers Tekniska Hogskola, Goteborg, Sweden Departamento de Informatica, Universidade do Minho, Braga, Portugal
The Semi-Full Closure of Pure Type Systems? Gilles Barthe Institutionen for Datavetenskap, Chalmers Tekniska Hogskola, Goteborg, Sweden Departamento de Informatica, Universidade do Minho, Braga, Portugal
perspective, logic programs do have a notion of control ow, and the in terms of the central control ow the program embodies.
 Projections of Logic Programs Using Symbol Mappings Ashish Jain Department of Computer Engineering and Science Case Western Reserve University Cleveland, OH 44106 USA email: jain@ces.cwru.edu Abstract
Projections of Logic Programs Using Symbol Mappings Ashish Jain Department of Computer Engineering and Science Case Western Reserve University Cleveland, OH 44106 USA email: jain@ces.cwru.edu Abstract
ENGIN 112 Intro to Electrical and Computer Engineering
 ENGIN 112 Intro to Electrical and Computer Engineering Lecture 30 Random Access Memory (RAM) Overview Memory is a collection of storage cells with associated input and output circuitry Possible to read
ENGIN 112 Intro to Electrical and Computer Engineering Lecture 30 Random Access Memory (RAM) Overview Memory is a collection of storage cells with associated input and output circuitry Possible to read
100-hour Design Cycle: A Test Case. keeping the specication close to the conceptualization. 2. Use of standard languages for input specications.
 100-hour Design Cycle: A Test Case Daniel D. Gajski, Loganath Ramachandran, Peter Fung 3, Sanjiv Narayan 1 and Frank Vahid 2 University of California, Irvine, CA 3 Matsushita Electric Works, Research and
100-hour Design Cycle: A Test Case Daniel D. Gajski, Loganath Ramachandran, Peter Fung 3, Sanjiv Narayan 1 and Frank Vahid 2 University of California, Irvine, CA 3 Matsushita Electric Works, Research and
An FPGA Project for use in a Digital Logic Course
 Session 3226 An FPGA Project for use in a Digital Logic Course Daniel C. Gray, Thomas D. Wagner United States Military Academy Abstract The Digital Computer Logic Course offered at the United States Military
Session 3226 An FPGA Project for use in a Digital Logic Course Daniel C. Gray, Thomas D. Wagner United States Military Academy Abstract The Digital Computer Logic Course offered at the United States Military
Partitioning of Mealy Finite State Machines
 Partitioning of Mealy Finite State Machines Arkadiusz Bukowiec Luis Gomes University of Zielona Góra, Institute of Computer Engineering and Electronics, Zielona Góra, Poland (e-mail: a.bukowiec@iie.uz.zgora.pl)
Partitioning of Mealy Finite State Machines Arkadiusz Bukowiec Luis Gomes University of Zielona Góra, Institute of Computer Engineering and Electronics, Zielona Góra, Poland (e-mail: a.bukowiec@iie.uz.zgora.pl)
More Course Information
 More Course Information Labs and lectures are both important Labs: cover more on hands-on design/tool/flow issues Lectures: important in terms of basic concepts and fundamentals Do well in labs Do well
More Course Information Labs and lectures are both important Labs: cover more on hands-on design/tool/flow issues Lectures: important in terms of basic concepts and fundamentals Do well in labs Do well
Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
An Agent Modeling Language Implementing Protocols through Capabilities
 An Agent Modeling Language Implementing Protocols through Capabilities Nikolaos Spanoudakis 1,2 1 Technical University of Crete, Greece nikos@science.tuc.gr Pavlos Moraitis 2 2 Paris Descartes University,
An Agent Modeling Language Implementing Protocols through Capabilities Nikolaos Spanoudakis 1,2 1 Technical University of Crete, Greece nikos@science.tuc.gr Pavlos Moraitis 2 2 Paris Descartes University,
Digital Circuit Verification using Partially-Ordered State Models
 Digital Circuit Verification using Partially-Ordered State Models Randal E. Bryant School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 USA Carl-Johan H. Seger Department of Computer
Digital Circuit Verification using Partially-Ordered State Models Randal E. Bryant School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 USA Carl-Johan H. Seger Department of Computer
ECE 2300 Digital Logic & Computer Organization
 ECE 2300 Digital Logic & Computer Organization Spring 201 Memories Lecture 14: 1 Announcements HW6 will be posted tonight Lab 4b next week: Debug your design before the in-lab exercise Lecture 14: 2 Review:
ECE 2300 Digital Logic & Computer Organization Spring 201 Memories Lecture 14: 1 Announcements HW6 will be posted tonight Lab 4b next week: Debug your design before the in-lab exercise Lecture 14: 2 Review:
Marcel Jacomet Roger Walti Lukas Winzenried Jaime Perez Martin Gysel. and verication of the FPGAs.
 : A Low Cost Rapid Prototyping and Test System f ASICs and FPGAs Marcel Jacomet Roger Walti Lukas Winzenried Jaime Perez Martin Gysel Biel School of Engineering, MicroLab{I3S, CH-2501 Biel, Switzerland
: A Low Cost Rapid Prototyping and Test System f ASICs and FPGAs Marcel Jacomet Roger Walti Lukas Winzenried Jaime Perez Martin Gysel Biel School of Engineering, MicroLab{I3S, CH-2501 Biel, Switzerland
for the MADFA construction problem have typically been kept as trade secrets (due to their commercial success in applications such as spell-checking).
 A Taxonomy of Algorithms for Constructing Minimal Acyclic Deterministic Finite Automata Bruce W. Watson 1 watson@openfire.org www.openfire.org University of Pretoria (Department of Computer Science) Pretoria
A Taxonomy of Algorithms for Constructing Minimal Acyclic Deterministic Finite Automata Bruce W. Watson 1 watson@openfire.org www.openfire.org University of Pretoria (Department of Computer Science) Pretoria
High-Level Test Synthesis. Tianruo Yang and Zebo Peng. Department of Computer and Information Science
 An Ecient Algorithm to Integrate Scheduling and Allocation in High-Level Synthesis Tianruo Yang and Zebo Peng Department of Computer and Information Science Linkoping University, S-581 83, Linkoping, Sweden
An Ecient Algorithm to Integrate Scheduling and Allocation in High-Level Synthesis Tianruo Yang and Zebo Peng Department of Computer and Information Science Linkoping University, S-581 83, Linkoping, Sweden
UMBC. Select. Read. Write. Output/Input-output connection. 1 (Feb. 25, 2002) Four commonly used memories: Address connection ... Dynamic RAM (DRAM)
 Memory Types Two basic types: ROM: Read-only memory RAM: Read-Write memory Four commonly used memories: ROM Flash (EEPROM) Static RAM (SRAM) Dynamic RAM (DRAM) Generic pin configuration: Address connection
Memory Types Two basic types: ROM: Read-only memory RAM: Read-Write memory Four commonly used memories: ROM Flash (EEPROM) Static RAM (SRAM) Dynamic RAM (DRAM) Generic pin configuration: Address connection
Distributed Systems Programming (F21DS1) Formal Verification
 Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
LOGIC SYNTHESIS AND VERIFICATION ALGORITHMS. Gary D. Hachtel University of Colorado. Fabio Somenzi University of Colorado.
 LOGIC SYNTHESIS AND VERIFICATION ALGORITHMS by Gary D. Hachtel University of Colorado Fabio Somenzi University of Colorado Springer Contents I Introduction 1 1 Introduction 5 1.1 VLSI: Opportunity and
LOGIC SYNTHESIS AND VERIFICATION ALGORITHMS by Gary D. Hachtel University of Colorado Fabio Somenzi University of Colorado Springer Contents I Introduction 1 1 Introduction 5 1.1 VLSI: Opportunity and
State Machine Specification. State Minimization. State Assignment. Logic Synthesis. Tech Mapping. Test Generation
 Synthesis for Logical Initializability of Synchronous Finite State Machines Montek Singh Steven M. Nowick Department of Computer Science Columbia University 24 Amsterdam Ave: Mailcode 4 New York, NY 27
Synthesis for Logical Initializability of Synchronous Finite State Machines Montek Singh Steven M. Nowick Department of Computer Science Columbia University 24 Amsterdam Ave: Mailcode 4 New York, NY 27
DRAFT for FINAL VERSION. Accepted for CACSD'97, Gent, Belgium, April 1997 IMPLEMENTATION ASPECTS OF THE PLC STANDARD IEC
 DRAFT for FINAL VERSION. Accepted for CACSD'97, Gent, Belgium, 28-3 April 1997 IMPLEMENTATION ASPECTS OF THE PLC STANDARD IEC 1131-3 Martin hman Stefan Johansson Karl-Erik rzen Department of Automatic
DRAFT for FINAL VERSION. Accepted for CACSD'97, Gent, Belgium, 28-3 April 1997 IMPLEMENTATION ASPECTS OF THE PLC STANDARD IEC 1131-3 Martin hman Stefan Johansson Karl-Erik rzen Department of Automatic
Hardware Resources in Digital Systems Teaching
 Hardware Resources in Digital Systems Teaching Yimin Xie, David Wong and Yinan Kong Department of Physics and Engineering Macquarie University Sydney, NSW 2109, Australia ABSTRACT This paper provides an
Hardware Resources in Digital Systems Teaching Yimin Xie, David Wong and Yinan Kong Department of Physics and Engineering Macquarie University Sydney, NSW 2109, Australia ABSTRACT This paper provides an
ECSE-2610 Computer Components & Operations (COCO)
 ECSE-2610 Computer Components & Operations (COCO) Part 18: Random Access Memory 1 Read-Only Memories 2 Why ROM? Program storage Boot ROM for personal computers Complete application storage for embedded
ECSE-2610 Computer Components & Operations (COCO) Part 18: Random Access Memory 1 Read-Only Memories 2 Why ROM? Program storage Boot ROM for personal computers Complete application storage for embedded
StateClock: a Tool for Timed Reactive Modules
 StateClock: a Tool for Timed Reactive Modules Jonathan S. Ostroff Department Of Computer Science, York University, Toronto, Canada, M3J 1P3. Email: jonathan@yorku.ca Abstract: We provide an overview of
StateClock: a Tool for Timed Reactive Modules Jonathan S. Ostroff Department Of Computer Science, York University, Toronto, Canada, M3J 1P3. Email: jonathan@yorku.ca Abstract: We provide an overview of
Deduction and Logic Implementation of the Fractal Scan Algorithm
 Deduction and Logic Implementation of the Fractal Scan Algorithm Zhangjin Chen, Feng Ran, Zheming Jin Microelectronic R&D center, Shanghai University Shanghai, China and Meihua Xu School of Mechatronical
Deduction and Logic Implementation of the Fractal Scan Algorithm Zhangjin Chen, Feng Ran, Zheming Jin Microelectronic R&D center, Shanghai University Shanghai, China and Meihua Xu School of Mechatronical
Microcontroller Systems. ELET 3232 Topic 11: General Memory Interfacing
 Microcontroller Systems ELET 3232 Topic 11: General Memory Interfacing 1 Objectives To become familiar with the concepts of memory expansion and the data and address bus To design embedded systems circuits
Microcontroller Systems ELET 3232 Topic 11: General Memory Interfacing 1 Objectives To become familiar with the concepts of memory expansion and the data and address bus To design embedded systems circuits
Design Progression With VHDL Helps Accelerate The Digital System Designs
 Fourth LACCEI International Latin American and Caribbean Conference for Engineering and Technology (LACCET 2006) Breaking Frontiers and Barriers in Engineering: Education, Research and Practice 21-23 June
Fourth LACCEI International Latin American and Caribbean Conference for Engineering and Technology (LACCET 2006) Breaking Frontiers and Barriers in Engineering: Education, Research and Practice 21-23 June
Dynamic Scheduling and Synchronization Synthesis of Concurrent Digital Systems under System-Level Constraints
 Dynamic Scheduling and Synchronization Synthesis of Concurrent Digital Systems under System-Level Constraints Claudionor N. Coelho Jr. Giovanni De Micheli Center for Integrated Systems Center for Integrated
Dynamic Scheduling and Synchronization Synthesis of Concurrent Digital Systems under System-Level Constraints Claudionor N. Coelho Jr. Giovanni De Micheli Center for Integrated Systems Center for Integrated
Abstract. Detection) protocol. Using a combination of temporal logic and algebraic specications we describe the
 An Algebraic-Temporal Specication of a CSMA/CD-Protocol Mohamed Jmaiel Technische Universitat Berlin Franklinstr. 28/29, Sekr. FR 5-13 D{10587 Berlin Tel. +49 30 314 21763, Fax. +49 30 314 73623. email:
An Algebraic-Temporal Specication of a CSMA/CD-Protocol Mohamed Jmaiel Technische Universitat Berlin Franklinstr. 28/29, Sekr. FR 5-13 D{10587 Berlin Tel. +49 30 314 21763, Fax. +49 30 314 73623. email:
An Overview of the DE Hardware Description Language and Its Application in Formal Verification of the FM9001 Microprocessor
 An Overview of the DE Hardware Description Language and Its Application in Formal Verification of the FM9001 Microprocessor Cuong Chau ckcuong@cs.utexas.edu Department of Computer Science The University
An Overview of the DE Hardware Description Language and Its Application in Formal Verification of the FM9001 Microprocessor Cuong Chau ckcuong@cs.utexas.edu Department of Computer Science The University
A framework for automatic generation of audio processing applications on a dual-core system
 A framework for automatic generation of audio processing applications on a dual-core system Etienne Cornu, Tina Soltani and Julie Johnson etienne_cornu@amis.com, tina_soltani@amis.com, julie_johnson@amis.com
A framework for automatic generation of audio processing applications on a dual-core system Etienne Cornu, Tina Soltani and Julie Johnson etienne_cornu@amis.com, tina_soltani@amis.com, julie_johnson@amis.com
Refine boundary at resolution r. r+1 r. Update context information CI(r) based on CI(r-1) Classify at resolution r, based on CI(r), update CI(r)
 Context Based Multiscale Classication of Images Jia Li Robert M. Gray EE Department EE Department Stanford Univ., CA 94305 Stanford Univ., CA 94305 jiali@isl.stanford.edu rmgray@stanford.edu Abstract This
Context Based Multiscale Classication of Images Jia Li Robert M. Gray EE Department EE Department Stanford Univ., CA 94305 Stanford Univ., CA 94305 jiali@isl.stanford.edu rmgray@stanford.edu Abstract This
A taxonomy of race. D. P. Helmbold, C. E. McDowell. September 28, University of California, Santa Cruz. Santa Cruz, CA
 A taxonomy of race conditions. D. P. Helmbold, C. E. McDowell UCSC-CRL-94-34 September 28, 1994 Board of Studies in Computer and Information Sciences University of California, Santa Cruz Santa Cruz, CA
A taxonomy of race conditions. D. P. Helmbold, C. E. McDowell UCSC-CRL-94-34 September 28, 1994 Board of Studies in Computer and Information Sciences University of California, Santa Cruz Santa Cruz, CA
Computer Memory. Textbook: Chapter 1
 Computer Memory Textbook: Chapter 1 ARM Cortex-M4 User Guide (Section 2.2 Memory Model) STM32F4xx Technical Reference Manual: Chapter 2 Memory and Bus Architecture Chapter 3 Flash Memory Chapter 36 Flexible
Computer Memory Textbook: Chapter 1 ARM Cortex-M4 User Guide (Section 2.2 Memory Model) STM32F4xx Technical Reference Manual: Chapter 2 Memory and Bus Architecture Chapter 3 Flash Memory Chapter 36 Flexible
CS429: Computer Organization and Architecture
 CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: November 28, 2017 at 14:31 CS429 Slideset 18: 1 Random-Access Memory
CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: November 28, 2017 at 14:31 CS429 Slideset 18: 1 Random-Access Memory
ccopyright by Aamod Arvind Sane 1998
 TECHNIQUES FOR DEVELOPING CORRECT, FAST, AND ROBUST IMPLEMENTATIONS OF DISTRIBUTED PROTOCOLS BY AAMOD ARVIND SANE THESIS Submitted in partial fulllment of the requirements for the degree of Doctor of Philosophy
TECHNIQUES FOR DEVELOPING CORRECT, FAST, AND ROBUST IMPLEMENTATIONS OF DISTRIBUTED PROTOCOLS BY AAMOD ARVIND SANE THESIS Submitted in partial fulllment of the requirements for the degree of Doctor of Philosophy
Mobile Robot Path Planning Software and Hardware Implementations
 Mobile Robot Path Planning Software and Hardware Implementations Lucia Vacariu, Flaviu Roman, Mihai Timar, Tudor Stanciu, Radu Banabic, Octavian Cret Computer Science Department, Technical University of
Mobile Robot Path Planning Software and Hardware Implementations Lucia Vacariu, Flaviu Roman, Mihai Timar, Tudor Stanciu, Radu Banabic, Octavian Cret Computer Science Department, Technical University of
Skill. Robot/ Controller
 Skill Acquisition from Human Demonstration Using a Hidden Markov Model G. E. Hovland, P. Sikka and B. J. McCarragher Department of Engineering Faculty of Engineering and Information Technology The Australian
Skill Acquisition from Human Demonstration Using a Hidden Markov Model G. E. Hovland, P. Sikka and B. J. McCarragher Department of Engineering Faculty of Engineering and Information Technology The Australian
A Simplied NP-complete MAXSAT Problem. Abstract. It is shown that the MAX2SAT problem is NP-complete even if every variable
 A Simplied NP-complete MAXSAT Problem Venkatesh Raman 1, B. Ravikumar 2 and S. Srinivasa Rao 1 1 The Institute of Mathematical Sciences, C. I. T. Campus, Chennai 600 113. India 2 Department of Computer
A Simplied NP-complete MAXSAT Problem Venkatesh Raman 1, B. Ravikumar 2 and S. Srinivasa Rao 1 1 The Institute of Mathematical Sciences, C. I. T. Campus, Chennai 600 113. India 2 Department of Computer
CS429: Computer Organization and Architecture
 CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: April 9, 2018 at 12:16 CS429 Slideset 17: 1 Random-Access Memory
CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: April 9, 2018 at 12:16 CS429 Slideset 17: 1 Random-Access Memory
Thomas Gabler and Sabine Marz{Rossel. Corporate Research and Development. Siemens AG. Munich, Germany
 An Approach to Guided Incremental Specication Thomas Gabler and Sabine Marz{Rossel Corporate Research and Development Siemens AG Munich, Germany Abstract In this paper we present an approach to guided
An Approach to Guided Incremental Specication Thomas Gabler and Sabine Marz{Rossel Corporate Research and Development Siemens AG Munich, Germany Abstract In this paper we present an approach to guided
Transport protocols are of practical. login, le transfer, and remote procedure. calls. will operate on and therefore are generally
 Hazard-Free Connection Release Jennifer E. Walter Department of Computer Science Texas A&M University College Station, TX 77843-3112, U.S.A. Jennifer L. Welch Department of Computer Science Texas A&M University
Hazard-Free Connection Release Jennifer E. Walter Department of Computer Science Texas A&M University College Station, TX 77843-3112, U.S.A. Jennifer L. Welch Department of Computer Science Texas A&M University
Embedded Systems: Hardware Components (part I) Todor Stefanov
 Embedded Systems: Hardware Components (part I) Todor Stefanov Leiden Embedded Research Center Leiden Institute of Advanced Computer Science Leiden University, The Netherlands Outline Generic Embedded System
Embedded Systems: Hardware Components (part I) Todor Stefanov Leiden Embedded Research Center Leiden Institute of Advanced Computer Science Leiden University, The Netherlands Outline Generic Embedded System
From Formal Requirements to Implementation: a Java Targeted Development Method. Eva Coscia. Advisor: Prof. Gianna Reggio.
 From Formal Requirements to Implementation: a Java Targeted Development Method Eva Coscia Advisor: Prof. Gianna Reggio Thesis Proposal Dottorato in Infomatica Dipartimento di Informatica e Scienze dell'informazione
From Formal Requirements to Implementation: a Java Targeted Development Method Eva Coscia Advisor: Prof. Gianna Reggio Thesis Proposal Dottorato in Infomatica Dipartimento di Informatica e Scienze dell'informazione
Abstract formula. Net formula
 { PEP { More than a Petri Net Tool ABSTRACT Bernd Grahlmann and Eike Best The PEP system (Programming Environment based on Petri Nets) supports the most important tasks of a good net tool, including HL
{ PEP { More than a Petri Net Tool ABSTRACT Bernd Grahlmann and Eike Best The PEP system (Programming Environment based on Petri Nets) supports the most important tasks of a good net tool, including HL
Design with Microprocessors
 Design with Microprocessors Year III Computer Sci. English 1-st Semester Lecture 12: Memory interfacing Typical Memory Hierarchy [1] On-Chip Components Control edram Datapath RegFile ITLB DTLB Instr Data
Design with Microprocessors Year III Computer Sci. English 1-st Semester Lecture 12: Memory interfacing Typical Memory Hierarchy [1] On-Chip Components Control edram Datapath RegFile ITLB DTLB Instr Data
On Checkpoint Latency. Nitin H. Vaidya. Texas A&M University. Phone: (409) Technical Report
 On Checkpoint Latency Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail: vaidya@cs.tamu.edu Phone: (409) 845-0512 FAX: (409) 847-8578 Technical Report
On Checkpoint Latency Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail: vaidya@cs.tamu.edu Phone: (409) 845-0512 FAX: (409) 847-8578 Technical Report
Software Implementation of Break-Up Algorithm for Logic Minimization
 vol. 2, no. 6. 2, pp. 141-145, 2017 DOI: https://doi.org/10.24999/ijoaem/02060034 Software Implementation of Break-Up Algorithm for Logic Minimization Koustuvmoni Bharadwaj and Sahadev Roy Abstract In
vol. 2, no. 6. 2, pp. 141-145, 2017 DOI: https://doi.org/10.24999/ijoaem/02060034 Software Implementation of Break-Up Algorithm for Logic Minimization Koustuvmoni Bharadwaj and Sahadev Roy Abstract In
Johns Hopkins Math Tournament Proof Round: Point Set Topology
 Johns Hopkins Math Tournament 2019 Proof Round: Point Set Topology February 9, 2019 Problem Points Score 1 3 2 6 3 6 4 6 5 10 6 6 7 8 8 6 9 8 10 8 11 9 12 10 13 14 Total 100 Instructions The exam is worth
Johns Hopkins Math Tournament 2019 Proof Round: Point Set Topology February 9, 2019 Problem Points Score 1 3 2 6 3 6 4 6 5 10 6 6 7 8 8 6 9 8 10 8 11 9 12 10 13 14 Total 100 Instructions The exam is worth
Chapter 5. Digital Design and Computer Architecture, 2 nd Edition. David Money Harris and Sarah L. Harris. Chapter 5 <1>
 Chapter 5 Digital Design and Computer Architecture, 2 nd Edition David Money Harris and Sarah L. Harris Chapter 5 Chapter 5 :: Topics Introduction Arithmetic Circuits umber Systems Sequential Building
Chapter 5 Digital Design and Computer Architecture, 2 nd Edition David Money Harris and Sarah L. Harris Chapter 5 Chapter 5 :: Topics Introduction Arithmetic Circuits umber Systems Sequential Building
commodore semiconductor group NMOS 950 Rittenhouse Rd., Norristown, PA Tel.: 215/ TWX: 510/ (MEMORY, I/O, TIMER ARRAY)
 commodore semiconductor group NMOS 950 Rittenhouse Rd., Norristown, PA 19403 Tel.: 215/666-7950 TWX: 510/660-4168 6532 (MEMORY, I/O, TIMER ARRAY) THE 6532 CONCEPT- The 6532 is designed to operate in conjunction
commodore semiconductor group NMOS 950 Rittenhouse Rd., Norristown, PA 19403 Tel.: 215/666-7950 TWX: 510/660-4168 6532 (MEMORY, I/O, TIMER ARRAY) THE 6532 CONCEPT- The 6532 is designed to operate in conjunction
6. Case Study: Formal Verification of RISC Processors using HOL
 6. Case Study: Formal Verification of RISC Processors using HOL Page Motivation RISC Verification Model Deriving Formal Specifications Verification Tasks Pipeline Correctness Processor Specific Definitions
6. Case Study: Formal Verification of RISC Processors using HOL Page Motivation RISC Verification Model Deriving Formal Specifications Verification Tasks Pipeline Correctness Processor Specific Definitions
Transistors NODES. Time (sec) No. of Nodes/Transistors
 Binary Tree Structure for Formal Verication of Combinational ICs FATMA A. EL-LICY, and HODA S. ABDEL-ATY-ZOHDY Microelectronics System Design Laboratory Department of Electrical and Systems Engineering
Binary Tree Structure for Formal Verication of Combinational ICs FATMA A. EL-LICY, and HODA S. ABDEL-ATY-ZOHDY Microelectronics System Design Laboratory Department of Electrical and Systems Engineering
APPLICATION OF MULTIPLE-VALUED SWITCH-LEVEL ALGEBRA TO THE DESIGN AND ANALYSIS OF PASS-TRANSISTOR SWITCH NETWORKS
 APPICATION OF MUTIPEVAUED SWITCEVE AGEBRA TO TE DESIGN AND ANAYSIS OF PASSTRANSISTOR SWITC NETWORKS Mou u Dept. of Computer Engineering Shanghai Institute of Railway Technology Shanghai, CINA 2333 Kenneth
APPICATION OF MUTIPEVAUED SWITCEVE AGEBRA TO TE DESIGN AND ANAYSIS OF PASSTRANSISTOR SWITC NETWORKS Mou u Dept. of Computer Engineering Shanghai Institute of Railway Technology Shanghai, CINA 2333 Kenneth
Hardware Design Environments. Dr. Mahdi Abbasi Computer Engineering Department Bu-Ali Sina University
 Hardware Design Environments Dr. Mahdi Abbasi Computer Engineering Department Bu-Ali Sina University Outline Welcome to COE 405 Digital System Design Design Domains and Levels of Abstractions Synthesis
Hardware Design Environments Dr. Mahdi Abbasi Computer Engineering Department Bu-Ali Sina University Outline Welcome to COE 405 Digital System Design Design Domains and Levels of Abstractions Synthesis
Address connections Data connections Selection connections
 Interface (cont..) We have four common types of memory: Read only memory ( ROM ) Flash memory ( EEPROM ) Static Random access memory ( SARAM ) Dynamic Random access memory ( DRAM ). Pin connections common
Interface (cont..) We have four common types of memory: Read only memory ( ROM ) Flash memory ( EEPROM ) Static Random access memory ( SARAM ) Dynamic Random access memory ( DRAM ). Pin connections common
Low Cost Convolutional Code Based Concurrent Error Detection in FSMs
 Low Cost Convolutional Code Based Concurrent Error Detection in FSMs Konstantinos Rokas & Yiorgos Makris Electrical Engineering Department Yale University {konstantinos.rokas, yiorgos.makris}@yale.edu
Low Cost Convolutional Code Based Concurrent Error Detection in FSMs Konstantinos Rokas & Yiorgos Makris Electrical Engineering Department Yale University {konstantinos.rokas, yiorgos.makris}@yale.edu
Set Manipulation with Boolean Functional Vectors for Symbolic Reachability Analysis
 Set Manipulation with Boolean Functional Vectors for Symbolic Reachability Analysis Amit Goel Department of ECE, Carnegie Mellon University, PA. 15213. USA. agoel@ece.cmu.edu Randal E. Bryant Computer
Set Manipulation with Boolean Functional Vectors for Symbolic Reachability Analysis Amit Goel Department of ECE, Carnegie Mellon University, PA. 15213. USA. agoel@ece.cmu.edu Randal E. Bryant Computer
Dynamic Logic David Harel, The Weizmann Institute Dexter Kozen, Cornell University Jerzy Tiuryn, University of Warsaw The MIT Press, Cambridge, Massac
 Dynamic Logic David Harel, The Weizmann Institute Dexter Kozen, Cornell University Jerzy Tiuryn, University of Warsaw The MIT Press, Cambridge, Massachusetts, 2000 Among the many approaches to formal reasoning
Dynamic Logic David Harel, The Weizmann Institute Dexter Kozen, Cornell University Jerzy Tiuryn, University of Warsaw The MIT Press, Cambridge, Massachusetts, 2000 Among the many approaches to formal reasoning
A Methodology and Tool Framework for Supporting Rapid Exploration of Memory Hierarchies in FPGAs
 A Methodology and Tool Framework for Supporting Rapid Exploration of Memory Hierarchies in FPGAs Harrys Sidiropoulos, Kostas Siozios and Dimitrios Soudris School of Electrical & Computer Engineering National
A Methodology and Tool Framework for Supporting Rapid Exploration of Memory Hierarchies in FPGAs Harrys Sidiropoulos, Kostas Siozios and Dimitrios Soudris School of Electrical & Computer Engineering National
ECE 545 Lecture 12. Datapath vs. Controller. Structure of a Typical Digital System Data Inputs. Required reading. Design of Controllers
 ECE 545 Lecture 12 Design of Controllers Finite State Machines and Algorithmic State Machine (ASM) Charts Required reading P. Chu, using VHDL Chapter 1, Finite State Machine: Principle & Practice Chapter
ECE 545 Lecture 12 Design of Controllers Finite State Machines and Algorithmic State Machine (ASM) Charts Required reading P. Chu, using VHDL Chapter 1, Finite State Machine: Principle & Practice Chapter
Appears in Proc. IEEE Int l Conf. on Robotics and Automation San Francisco, CA April 22-28, 2000
 Appears in Proc. IEEE Int l Conf. on Robotics and Automation San Francisco, CA April 22-28, 2000 Using Model Checking to Guarantee Safety in Automatically-Synthesized Real-Time Controllers David J. Musliner,
Appears in Proc. IEEE Int l Conf. on Robotics and Automation San Francisco, CA April 22-28, 2000 Using Model Checking to Guarantee Safety in Automatically-Synthesized Real-Time Controllers David J. Musliner,
to automatically generate parallel code for many applications that periodically update shared data structures using commuting operations and/or manipu
 Semantic Foundations of Commutativity Analysis Martin C. Rinard y and Pedro C. Diniz z Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 fmartin,pedrog@cs.ucsb.edu
Semantic Foundations of Commutativity Analysis Martin C. Rinard y and Pedro C. Diniz z Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 fmartin,pedrog@cs.ucsb.edu
Eulerian subgraphs containing given edges
 Discrete Mathematics 230 (2001) 63 69 www.elsevier.com/locate/disc Eulerian subgraphs containing given edges Hong-Jian Lai Department of Mathematics, West Virginia University, P.O. Box. 6310, Morgantown,
Discrete Mathematics 230 (2001) 63 69 www.elsevier.com/locate/disc Eulerian subgraphs containing given edges Hong-Jian Lai Department of Mathematics, West Virginia University, P.O. Box. 6310, Morgantown,
Assertion Checker Synthesis for FPGA Emulation
 Assertion Checker Synthesis for FPGA Emulation Chengjie Zang, Qixin Wei and Shinji Kimura Graduate School of Information, Production and Systems, Waseda University, 2-7 Hibikino, Kitakyushu, 808-0135,
Assertion Checker Synthesis for FPGA Emulation Chengjie Zang, Qixin Wei and Shinji Kimura Graduate School of Information, Production and Systems, Waseda University, 2-7 Hibikino, Kitakyushu, 808-0135,
