FQA 7 System Management. 7.1 Plan 9 Services Overview
|
|
|
- Alyson Randall
- 5 years ago
- Views:
Transcription
1 FQA 7 System Management 7.1 Plan 9 Services Overview
2 Designing Plan 9, Plan 9 From Bell Labs, The Organization of Networks in Plan What is the kernel? $user hostowner hostowner authid Note: hostowner root root and hostowner hostowner processes What is the file server? only cwfs hjfs cwfs hjfs The Plan 9 File Server cwfs cwfs(4) hjfs(4) Note: Note:
3 Note: What is the auth server? Note: cron(8) Security in Plan 9,auth(8) What is the cpu server? service=cpu plan9.ini /rc/bin/cpurc cpurc Note: The Organization of Networks in Plan 9, cpu(1) exportfs(4)
4 7.1.5 What is a terminal? rio service=terminal plan9.ini /rc/bin/termrc Note: Note: 7.2 Kernel configuration and maintenance How do I mount the 9fat partition? 9fat: c: 9fs 9fs 9fat #S /dev bind b #S /dev # bind the local hard drive kernel device over /dev 9fs 9fat /dev/sdxx/9fat # specify the full path to the corresponding 9fat Note: 9fs 9fat /srv/dos 9fs 9fat 9fs 9fat dossrv(4) How do I modify plan9.ini? 9fat /n/9fat/plan9.ini Note: plan9.ini(8)
5 7.2.3 Kernel configuration file pc /sys/src/9/pc/pc Kernel drivers pc /sys/src/9/pc How do I install a new kernel? cd /sys/src/9/pc mk install # kernel is copied to /386/9pc cd /sys/src/9/pc64 mk install # kernel is copied to /amd64/9pc64 cd /sys/src/9/bcm mk install # kernel is copied to /arm/9pif 9fat Note: 9fs 9fat rm /n/9fat/9bootfat cp /386/9bootfat /n/9fat/ chmod +al /n/9fat/9bootfat # defrag magic cp /386/9pc /n/9fat/ cp /amd64/9pc64 /n/9fat/ plan9.ini bootfile
6 FQA How do I modify plan9.ini? 7.3 Fileserver configuration and maintenance Adding users cwfs echo newuser username >>/srv/cwfs.cmd hjfs echo newuser username >>/srv/hjfs.cmd cwfs echo newuser upas +username >>/srv/cwfs.cmd hjfs echo newuser upas +username >>/srv/hjfs.cmd /adm/users /usr Note: cwfs con C /srv/cwfs.cmd hjfs con C /srv/hjfs.cmd Ctrl \ con q Note: sam /sys/lib/newuser /usr/username/lib/profile newuser fs(8) cwfs hjfs(8) /lib/namespace bind c /n/other/usr/$user/tmp /usr/$user/tmp
7 cwfs tmp other mkdir /n/other/usr/$user/tmp Configuring nvram nvram factotum nvram auth/wrkey authid authdom secstore key, password authid hostowner glenda authdom 9front secstore key password password authid authdom secstore key FQA secstored). secstore FQA secstore) secstored enter secstore key: auth/wrkey bad nvram key bad authentication id bad authentication domain # You may not see these errors. authid: glenda authdom: 9front secstore key: [glenda s secstore password] password: [glenda s password] Note: nvram auth/wrkey auth(8) Setting up a listener for network connections service /n/9fat/plan9.ini service=cpu FQA How do I modify plan9.ini? FQA Configuring nvram. nvram factotum
8 fshalt r bootargs c config noauth end bootargs is (tcp, local!device) [local!/dev/sdxx/fscache] local!/dev/sdxx/fscach config: noauth auth is now disabled config: noauth auth is now enabled config: end bootargs /n/9fat/plan9.ini bootargs=local!/dev/sdxx/fscache a tcp!*!564 bootargs=local!/dev/sdxx/fs m 702 A a tcp!*!564 Note: m 702 hjfs FQA How do I modify plan9.ini? fshalt r cwfs(4) hjfs(4) FQA How do I tcp boot? Mounting a file system from userspace
9 % cwfs64x n fs f /dev/sde0/fscache # use the correct path to your fscache % mount /srv/fs /n/fs Note: Running the above commands will post the file systems s console in /srv/fs.cmd. to be announced 7.4 Auth server configuration and maintenance Configuring an auth server service=cpu plan9.ini ndb authdom service /n/9fat/plan9.ini service=cpu FQA How do I modify plan9.ini? service /cfg/pxe/ /cfg/pxe/000c292fd30c service=cpu Note: /cfg/pxe/000c292fd30c plan9.ini plan9.ini ndb authdom 00:0c:29:2f:d3:0c /24 authdom 9front /lib/ndb/local authdom ipnet ipnet=9front ip= ipmask= ipgw= auth= # add auth server s ip authdom=9front # add authdom fs= cpu= dns= dnsdomain=9front smtp= ndb(6)
10 FQA Configuring nvram. nvram factotum Note: hostowner authid auth/wrkey glenda sl /lib/ndb/auth hostid=sl uid=!sys uid=!adm uid=* sl except forsys adm auth(8) fshalt r /rc/bin/cpurc ndb keyfs keyfs authid auth/wrkey password password auth/wrkey Note: auth/wrkey FQA Adding users Avoiding an ndb entry for the auth server authdom ndb authdial() libauthsrv p9auth.example.com p9auth example.com ndb Adding users hostowner auth/keyfs
11 % auth/keyfs % auth/changeuser username Password: # type password here, will not echo Confirm password: # confirm password here, will not echo assign Inferno/POP secret? (y/n) n Expiration date (YYYYMMDD or never)[return = never]: 2 keys read Post id: User s full name: Department #: User s address: Sponsor s address: user username installed for Plan 9 Note: keys read Enter auth(8),keyfs(4) secstored factotum secstored hostowner mkdir /adm/secstore chmod 770 /adm/secstore secstored /cfg/$sysname/cpurc auth/secstored secstore(1) secstore(8) Adding users to secstore secuser /adm/secstore/who/user hostowner auth/secuser username secstored secuser FICTITIOUS FQA secstore secstore
12 Converting from ps9k1 to dp9ik Date: Wed, 6 Jan :54: From: cinap_lenrek@felloff.net To: 9front@9front.org Subject: [9front] new factotum/authsrv/keyfs Reply To: 9front@9front.org i just pushed the new code which adds dp9ik authentication support. to update a system, the following things need to be done: # make sure you have the latest libmp/libsec cd /sys/src/libmp; mk install cd /sys/src/libsec; mk install # rebuild mpc (required for libauthsrv) cd /sys/src/cmd; mk mpc.install # rebuild libauthsrv / libauth cd /sys/src/libauthsrv; mk install cd /sys/src/libauth; mk install # rebuild factotum/keyfs/authsrv cd /sys/src/cmd/auth; mk install # then rebuild kernel to include the new factotum, # but dont reboot your authserver just yet... cd /sys/src/9/pc; mk install # if your /adm/keydb is still in DES format (cat it to see # if the keyfile starts with the AES signature), you need to # convert it to use the new dp9ik protocol: # make backup cp /adm/keys /adm/keys.old auth/convkeys ap /adm/keys # now set the aes key in nvram (so authserver can decrypt # the keydb when it boots) auth/wrkey # now you can reboot the AS and once its up, you have to # set new passwords for the users. logging in with the # old p9sk1 plan9 password should continue to work if # you skip this. passwd [username] # if there are issues logging in with dp9ik because keydb # doesnt have the new key yet, you can use delkey(1) to # remove the dp9ik key from factotum as a work arround. cinap
13 7.5 Cpu server configuration and maintenance Configuring a cpu server Note: FQA 7.4 Auth server configuration and maintenance terminal cpu service /n/9fat/plan9.ini service=cpu FQA How do I modify plan9.ini? service /cfg/pxe/ /cfg/pxe/000c292fd30c service=cpu Note: /cfg/pxe/000c292fd30c plan9.ini plan9.ini service=cpu /rc/bin/cpurc /rc/bin/service listen(8) tcp17019 authdom ndb FQA Configuring an auth server FQA Configuring nvram. nvram factotum fshalt r 7.6 Terminal configuration and maintenance Configuring a terminal 9pc FQA 6.7 How do I boot from the network?
14 7.6.2 Configuring a Terminal to Accept cpu Connections hostowner cpu cpu cpu dom user password echo key proto=dp9ik dom=9front user=glenda!password=p@ssw0rd \ >/mnt/factotum/ctl aux/listen1 t tcp!*!rcpu /rc/bin/service/tcp UTC Timesync /rc/bin/termrc TIMESYNCARGS=( rla ) TIMESYNCARGS=( ra ) /rc/bin/termrc.local /rc/bin/termrc 7.7 Mail server configuration and maintenance /mail/lib/ upas Note: upas /mail/queue /mail/tmp Note: FQA DNS authoritative name server
15 Upas A Simpler Approach to Network Mail, mail(1) smtpd.conf smtpd.conf for for # outgoing mail will be sent from this domain by default defaultdomain 9front.org # do not be an open relay norelay on # disable dns verification of sender domain verifysenderdom off # do not save blocked messages saveblockedmsg off # if norelay is on, you need to set the # networks allowed to relay through # as well as the domains to accept mail for ournets / / /24 # domain names for which incoming mail is accepted ourdomains 9front.org, bell labs.co, cat v.org smtpd(6) smtp(8) rewrite rewrite.direct rewrite
16 # case conversion for postmaster postmaster alias postmaster # local mail \l!(.*) alias \1 (ttr 9front.org bell labs.co cat v.org)!(.*) alias \2 [^!@]+ translate "/bin/upas/aliasmail & " local!(.*) >> /mail/box/1/mbox # we can be just as complicated as BSD sendmail... # convert source domain address to a chain alias # convert a chain a@b@c@d... to...d!c!b!a ([^@]+)@([^@]+)@(.+) alias \2!\1@\3 ([^@]+)@([^@]+) alias \2!\1 # /mail/lib/remot will take care of gating to systems we don t know ([^!]*)!(.*) "/mail/lib/qmail \\s net!\1 " " \2 " rewrite(6) names.local names.local # postmaster goes to glenda postmaster glenda Note: postmaster@[any domain] glenda remot upas remot #!/bin/rc shift sender=$1 shift addr=$1 shift exec /bin/upas/smtp $addr $sender $* smtp(8)
17 7.7.5 SMTP over TLS /rc/bin/service/tcp587 #!/bin/rc user= {cat /dev/user} exec /bin/upas/smtpd c /sys/lib/tls/cert n $3 # to use with listen1, change $3 to $net IMAP4 over TLS /rc/bin/service/tcp993 #!/bin/rc exec tlssrv c/sys/lib/tls/cert limap4d \ r {cat $3/remote} /bin/ip/imap4d p \ r {cat $3/remote} >>[2]/sys/log/imap4d # to use with listen1, change $3 to $net Spam Filtering ratfs ratfs(4) /mail/lib/blocked # allow messages from any user at 9front.org *allow 9front.org!* # block messages from any user at bell labs.com *block bell labs.com!* # block messages from ip block of aol modems block /15 ratfs /mail/lib/blocked echo reload >/mail/ratify/ctl ratfs(4) smtpd(6) ratfs /cfg/$sysname/cpustart
18 upas/ratfs /lib/namespace mount c #s/ratify /mail/ratify Note: ratfs upas ratfs before upas scanmail scanmail(8) Troubleshooting the mail server tester.com 7.8 Web server configuration and maintenance ip/httpd rc httpd rc httpd rc httpd listen(8) listen1(8) rc httpd(8) Note:rc httpd 9front.org 7.9 TLS certificates
19 factotum ramfs p cd /tmp auth/rsagen t service=tls role=client owner=* > key chmod 600 key cp key /sys/lib/tls/key # or: store key in secstore auth/rsa2x509.c=us CN=fakedom.dom /sys/lib/tls/key \ auth/pemencode CERTIFICATE > /sys/lib/tls/cert Note: US fakedom.dom factotum /cfg/$sysname/cpustart cat /sys/lib/tls/key >>/mnt/factotum/ctl rsa(8)
20
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS ACHTUNG! Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! _sl s info is incorrect. ACHTUNG!
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS ACHTUNG! Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! _sl s info is incorrect. ACHTUNG!
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf The study of this Book is forbidden. It is wise to destroy this copy after the first reading. Whosoever disregards this does so at his own risk and peril. These
troff -ms -mpictures lp -dstdout ps2pdf The study of this Book is forbidden. It is wise to destroy this copy after the first reading. Whosoever disregards this does so at his own risk and peril. These
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf The study of this Book is forbidden. It is wise to destroy this copy after the first reading. Whosoever disregards this does so at his own risk and peril. These
troff -ms -mpictures lp -dstdout ps2pdf The study of this Book is forbidden. It is wise to destroy this copy after the first reading. Whosoever disregards this does so at his own risk and peril. These
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf
 troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
troff -ms -mpictures lp -dstdout ps2pdf 9FRONT FREQUENTLY QUESTIONED ANSWERS Those who can do, those who can t write and those who can t write make ezines. ACHTUNG! ACHTUNG! ACHTUNG! _sl s info is incorrect.
FQA 6 Networking. 6.1 Before we go any further. The Organization of Networks in Plan Network configuration
 FQA 6 Networking 6.1 Before we go any further FQA 0.1 What is Plan 9? The Organization of Networks in Plan 9 Note: /lib/rfc/grabrfc /lib/rfc/ 6.2 Network configuration ndb ndb(6): /lib/ndb/local 6.2.1
FQA 6 Networking 6.1 Before we go any further FQA 0.1 What is Plan 9? The Organization of Networks in Plan 9 Note: /lib/rfc/grabrfc /lib/rfc/ 6.2 Network configuration ndb ndb(6): /lib/ndb/local 6.2.1
FQA 4 9front Installation Guide
 FQA 4 9front Installation Guide ACHTUNG! 4.1 Pre installation Checklist Machine name, sysname Hardware installed and available. FQA 3.3 Selecting Hardware. FQA 3.2 Known Working Hardware Network settings,
FQA 4 9front Installation Guide ACHTUNG! 4.1 Pre installation Checklist Machine name, sysname Hardware installed and available. FQA 3.3 Selecting Hardware. FQA 3.2 Known Working Hardware Network settings,
FQA 8 Using 9front. 8.1 rc. Rc The Plan 9 Shell,rc(1) Prompts
 FQA 8 Using 9front i am form china here is lots of people knows and documented is chinese the time comllexity is need you test youself and you will find it conventions rules 8.1 rc rc rc rc Rc The Plan
FQA 8 Using 9front i am form china here is lots of people knows and documented is chinese the time comllexity is need you test youself and you will find it conventions rules 8.1 rc rc rc rc Rc The Plan
Ciphermail Webmail Messenger Administration Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail Webmail Messenger Administration Guide October 27, 2017, Rev: 8630 Copyright 2013-2017, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Admin login
CIPHERMAIL EMAIL ENCRYPTION Ciphermail Webmail Messenger Administration Guide October 27, 2017, Rev: 8630 Copyright 2013-2017, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Admin login
Welcome to getting started with Ubuntu Server. This System Administrator Manual. guide to be simple to follow, with step by step instructions
 Welcome to getting started with Ubuntu 12.04 Server. This System Administrator Manual guide to be simple to follow, with step by step instructions with screenshots INDEX 1.Installation of Ubuntu 12.04
Welcome to getting started with Ubuntu 12.04 Server. This System Administrator Manual guide to be simple to follow, with step by step instructions with screenshots INDEX 1.Installation of Ubuntu 12.04
Installing the Inferno Software
 Installing the Inferno Software Vita Nuova support@vitanuova.com 12 June 2003 Inferno can run as either a native operating system, in the usual way, or as a hosted virtual operating system, running as
Installing the Inferno Software Vita Nuova support@vitanuova.com 12 June 2003 Inferno can run as either a native operating system, in the usual way, or as a hosted virtual operating system, running as
Two factor authentication for Citrix NetScaler
 Two factor authentication for Citrix NetScaler logintc.com/docs/connectors/citrix-netscaler.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
Two factor authentication for Citrix NetScaler logintc.com/docs/connectors/citrix-netscaler.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
Linux Essentials Objectives Topics:
 Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
FIPS Management. FIPS Management Overview. Configuration Changes in FIPS Mode
 This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
Embedded System Design
 Embedded System Design Lecture 10 Jaeyong Chung Systems-on-Chips (SoC) Laboratory Incheon National University Environment Variables Environment variables are a set of dynamic named values that can affect
Embedded System Design Lecture 10 Jaeyong Chung Systems-on-Chips (SoC) Laboratory Incheon National University Environment Variables Environment variables are a set of dynamic named values that can affect
Chapter Two. Lesson A. Objectives. Exploring the UNIX File System and File Security. Understanding Files and Directories
 Chapter Two Exploring the UNIX File System and File Security Lesson A Understanding Files and Directories 2 Objectives Discuss and explain the UNIX file system Define a UNIX file system partition Use the
Chapter Two Exploring the UNIX File System and File Security Lesson A Understanding Files and Directories 2 Objectives Discuss and explain the UNIX file system Define a UNIX file system partition Use the
How to use Gmail to access your JBN
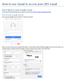 How to use Gmail to access your JBN email Step 1: Sign in or create a Google account. If you have an existing Gmail account, sign into it and skip to Step 2: Import your jbntelco email. Part A: Create
How to use Gmail to access your JBN email Step 1: Sign in or create a Google account. If you have an existing Gmail account, sign into it and skip to Step 2: Import your jbntelco email. Part A: Create
Configuring a Terminal/Comm Server
 Configuring a Terminal/Comm Server Document ID: 5466 Introduction Prerequisites Requirements Components Used Conventions Cabling Design Strategy Configure Network Diagram Configurations Command Summary
Configuring a Terminal/Comm Server Document ID: 5466 Introduction Prerequisites Requirements Components Used Conventions Cabling Design Strategy Configure Network Diagram Configurations Command Summary
Contents. About. Script. IPv6_setup_Hurricane_Electric_Tunnel_Broker
 Contents About 1 About 2 Script 3 Install Steps 4 OpenDNS Setting 5 Reducing Script Size 6 See Also This will... Set up HE's tunnel broker service. Automatically nds your wan ip at boot using whatismyip.com
Contents About 1 About 2 Script 3 Install Steps 4 OpenDNS Setting 5 Reducing Script Size 6 See Also This will... Set up HE's tunnel broker service. Automatically nds your wan ip at boot using whatismyip.com
Comodo IT and Security Manager Software Version 6.4
 Comodo IT and Security Manager Software Version 6.4 On-Premise Installation Guide Guide Version 6.4.040417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Comodo IT and
Comodo IT and Security Manager Software Version 6.4 On-Premise Installation Guide Guide Version 6.4.040417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Comodo IT and
Red Hat.Actualtests.EX200.v by.Dixon.22q. Exam Code: EX200. Exam Name: Red Hat Certified System Administrator (RHCSA) Exam
 Red Hat.Actualtests.EX200.v2014-12-02.by.Dixon.22q Number: EX200 Passing Score: 800 Time Limit: 120 min File Version: 14.5 http://www.gratisexam.com/ Exam Code: EX200 Exam Name: Red Hat Certified System
Red Hat.Actualtests.EX200.v2014-12-02.by.Dixon.22q Number: EX200 Passing Score: 800 Time Limit: 120 min File Version: 14.5 http://www.gratisexam.com/ Exam Code: EX200 Exam Name: Red Hat Certified System
Authenticating SMTP Sessions Using Client Certificates
 Authenticating SMTP Sessions Using Client Certificates This chapter contains the following sections: Overview of Certificates and SMTP Authentication, on page 1 Checking the Validity of a Client Certificate,
Authenticating SMTP Sessions Using Client Certificates This chapter contains the following sections: Overview of Certificates and SMTP Authentication, on page 1 Checking the Validity of a Client Certificate,
2017/12/27 07:31 (UTC) 1/7 Making Slackware Mail Server
 2017/12/27 07:31 (UTC) 1/7 Making Slackware Mail Server Making Slackware Mail Server This article shows how to make an Slackware machine your personal Mail Server. This howto is for Slackware 64 13.37,
2017/12/27 07:31 (UTC) 1/7 Making Slackware Mail Server Making Slackware Mail Server This article shows how to make an Slackware machine your personal Mail Server. This howto is for Slackware 64 13.37,
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
Configure Exchange 2003 Server
 Configure Exchange 2003 Server Configuring your new Exchange 2003 server for internet email with POPcon for downloading the email from POP3 mailboxes isn't hard if you just do it step by step as shown
Configure Exchange 2003 Server Configuring your new Exchange 2003 server for internet email with POPcon for downloading the email from POP3 mailboxes isn't hard if you just do it step by step as shown
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
Adding your IMAP Mail Account in Outlook 2013 on Windows
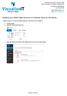 Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
CISCO SWITCH BEST PRACTICES GUIDE
 CISCO SWITCH BEST PRACTICES GUIDE Table of Contents (After Clicking Link Hit HOME to Return to TOC) 1) Add Hostname... 2 2) Add Username and Password... 2 3) Create Secret Password... 2 4) Encrypt Password...
CISCO SWITCH BEST PRACTICES GUIDE Table of Contents (After Clicking Link Hit HOME to Return to TOC) 1) Add Hostname... 2 2) Add Username and Password... 2 3) Create Secret Password... 2 4) Encrypt Password...
Upgrade Cisco Interface Module for LoRaWAN IXM using the Console
 Upgrade Cisco Interface Module for LoRaWAN IXM using the Console Contents Introduction Prerequisites Requirements Components Used Background Information Configure Step 1. Prepare the firmware images (and
Upgrade Cisco Interface Module for LoRaWAN IXM using the Console Contents Introduction Prerequisites Requirements Components Used Background Information Configure Step 1. Prepare the firmware images (and
Load Balancing Microsoft IIS. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Microsoft IIS Deployment Guide v1.6.4 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Load Balancing Microsoft IIS Deployment Guide v1.6.4 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Unix Basics. UNIX Introduction. Lecture 14
 Unix Basics Lecture 14 UNIX Introduction The UNIX operating system is made up of three parts; the kernel, the shell and the programs. The kernel of UNIX is the hub of the operating system: it allocates
Unix Basics Lecture 14 UNIX Introduction The UNIX operating system is made up of three parts; the kernel, the shell and the programs. The kernel of UNIX is the hub of the operating system: it allocates
Linux Essentials. Programming and Data Structures Lab M Tech CS First Year, First Semester
 Linux Essentials Programming and Data Structures Lab M Tech CS First Year, First Semester Adapted from PDS Lab 2014 and 2015 Login, Logout, Password $ ssh mtc16xx@192.168.---.--- $ ssh X mtc16xx@192.168.---.---
Linux Essentials Programming and Data Structures Lab M Tech CS First Year, First Semester Adapted from PDS Lab 2014 and 2015 Login, Logout, Password $ ssh mtc16xx@192.168.---.--- $ ssh X mtc16xx@192.168.---.---
EX200.Lead2pass.Exam.24q. Exam Code: EX200. Exam Name: Red Hat Certified System Administrator RHCSA. Version 14.0
 EX200.Lead2pass.Exam.24q Number: EX200 Passing Score: 800 Time Limit: 120 min File Version: 14.0 http://www.gratisexam.com/ Exam Code: EX200 Exam Name: Red Hat Certified System Administrator RHCSA Version
EX200.Lead2pass.Exam.24q Number: EX200 Passing Score: 800 Time Limit: 120 min File Version: 14.0 http://www.gratisexam.com/ Exam Code: EX200 Exam Name: Red Hat Certified System Administrator RHCSA Version
Set Up with Microsoft Outlook 2013 using POP3
 Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Laboration 2 Troubleshooting Switching and First-Hop Redundancy
 Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
idor Mobile Setup idor Mobile : idor Mobile System Manual V1.1 1
 idor Mobile Setup Table of Contents Login into the Web-GUI... 3 Network Settings... 4 Set Static IP Address... 5 Apartments... 7 Add an Apartment... 7 Edit an Apartment... 9 Delete an Apartment... 9 SIP
idor Mobile Setup Table of Contents Login into the Web-GUI... 3 Network Settings... 4 Set Static IP Address... 5 Apartments... 7 Add an Apartment... 7 Edit an Apartment... 9 Delete an Apartment... 9 SIP
Vendor: RedHat. Exam Code: EX200. Exam Name: Red Hat Certified System Administrator - RHCSA. Version: Demo
 Vendor: RedHat Exam Code: EX200 Exam Name: Red Hat Certified System Administrator - RHCSA Version: Demo EX200 Exam A QUESTION NO: 1 CRECT TEXT Configure your Host Name, IP Address, Gateway and DNS. Host
Vendor: RedHat Exam Code: EX200 Exam Name: Red Hat Certified System Administrator - RHCSA Version: Demo EX200 Exam A QUESTION NO: 1 CRECT TEXT Configure your Host Name, IP Address, Gateway and DNS. Host
Cisco Stealthwatch. Update Guide 7.0
 Cisco Stealthwatch Update Guide 7.0 Table of Contents Introduction 5 Overview 5 Audience 5 Terminology 5 New Update Process 6 Before You Begin 7 Software Version 7 Java 7 TLS 7 Default Credentials 8 Third
Cisco Stealthwatch Update Guide 7.0 Table of Contents Introduction 5 Overview 5 Audience 5 Terminology 5 New Update Process 6 Before You Begin 7 Software Version 7 Java 7 TLS 7 Default Credentials 8 Third
Seltestengine EX200 24q
 Seltestengine EX200 24q Number: EX200 Passing Score: 800 Time Limit: 120 min File Version: 22.5 http://www.gratisexam.com/ Red Hat EX200 Red Hat Certified System AdministratorRHCSA Nicely written Questions
Seltestengine EX200 24q Number: EX200 Passing Score: 800 Time Limit: 120 min File Version: 22.5 http://www.gratisexam.com/ Red Hat EX200 Red Hat Certified System AdministratorRHCSA Nicely written Questions
Securing a Wireless LAN
 Securing a Wireless LAN This module describes how to apply strong wireless security mechanisms on a Cisco 800, 1800, 2800, or 3800 series integrated services router, hereafter referred to as an access
Securing a Wireless LAN This module describes how to apply strong wireless security mechanisms on a Cisco 800, 1800, 2800, or 3800 series integrated services router, hereafter referred to as an access
GNU/Linux 101. Casey McLaughlin. Research Computing Center Spring Workshop Series 2018
 GNU/Linux 101 Casey McLaughlin Research Computing Center Spring Workshop Series 2018 rccworkshop IC;3df4mu bash-2.1~# man workshop Linux101 RCC Workshop L101 OBJECTIVES - Operating system concepts - Linux
GNU/Linux 101 Casey McLaughlin Research Computing Center Spring Workshop Series 2018 rccworkshop IC;3df4mu bash-2.1~# man workshop Linux101 RCC Workshop L101 OBJECTIVES - Operating system concepts - Linux
Appliance Installation Guide
 Appliance Installation Guide GWAVA 5 Copyright 2009. GWAVA Inc. All rights reserved. Content may not be reproduced without permission. http://www.gwava.com 1 Contents Overview... 2 Minimum System Requirements...
Appliance Installation Guide GWAVA 5 Copyright 2009. GWAVA Inc. All rights reserved. Content may not be reproduced without permission. http://www.gwava.com 1 Contents Overview... 2 Minimum System Requirements...
Overview LEARN. History of Linux Linux Architecture Linux File System Linux Access Linux Commands File Permission Editors Conclusion and Questions
 Lanka Education and Research Network Linux Architecture, Linux File System, Linux Basic Commands 28 th November 2016 Dilum Samarasinhe () Overview History of Linux Linux Architecture Linux File System
Lanka Education and Research Network Linux Architecture, Linux File System, Linux Basic Commands 28 th November 2016 Dilum Samarasinhe () Overview History of Linux Linux Architecture Linux File System
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Maintaining the System Software
 CHAPTER 2 This chapter covers the tasks required for maintaining a Content Engine. Upgrading the System Software, page 2-1 Recovering the System Software, page 2-2 Maintaining the Hard Disk Storage, page
CHAPTER 2 This chapter covers the tasks required for maintaining a Content Engine. Upgrading the System Software, page 2-1 Recovering the System Software, page 2-2 Maintaining the Hard Disk Storage, page
Booting a Galaxy Instance
 Booting a Galaxy Instance Create Security Groups First time Only Create Security Group for Galaxy Name the group galaxy Click Manage Rules for galaxy Click Add Rule Choose HTTPS and Click Add Repeat Security
Booting a Galaxy Instance Create Security Groups First time Only Create Security Group for Galaxy Name the group galaxy Click Manage Rules for galaxy Click Add Rule Choose HTTPS and Click Add Repeat Security
Linux & Shell Programming 2014
 Unit -1: Introduction to UNIX/LINUX Operating System Practical Practice Questions: Find errors (if any) otherwise write output or interpretation of following commands. (Consider default shell is bash shell.)
Unit -1: Introduction to UNIX/LINUX Operating System Practical Practice Questions: Find errors (if any) otherwise write output or interpretation of following commands. (Consider default shell is bash shell.)
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades Q2
 Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Configuring Passwords and Privileges
 Configuring Passwords and Privileges Using passwords and assigning privilege levels is a simple way of providing terminal access control in your network. This chapter describes the following topics and
Configuring Passwords and Privileges Using passwords and assigning privilege levels is a simple way of providing terminal access control in your network. This chapter describes the following topics and
Getting your department account
 02/11/2013 11:35 AM Getting your department account The instructions are at Creating a CS account 02/11/2013 11:36 AM Getting help Vijay Adusumalli will be in the CS majors lab in the basement of the Love
02/11/2013 11:35 AM Getting your department account The instructions are at Creating a CS account 02/11/2013 11:36 AM Getting help Vijay Adusumalli will be in the CS majors lab in the basement of the Love
3 Connection, Shell Serial Connection over Console Port SSH Connection Internet Connection... 5
 Contents 1 Description 2 2 Supported Devices 3 3 Connection, Shell 4 3.1 Serial Connection over Console Port...................... 4 3.2 SSH Connection................................. 4 3.3 Internet Connection...............................
Contents 1 Description 2 2 Supported Devices 3 3 Connection, Shell 4 3.1 Serial Connection over Console Port...................... 4 3.2 SSH Connection................................. 4 3.3 Internet Connection...............................
Performing Administrative Tasks
 This chapter describes how to perform administrative tasks using Cisco CMX. Users who are assigned administration privileges can perform administrative tasks. Cisco CMX User Accounts, page 1 Backing Up
This chapter describes how to perform administrative tasks using Cisco CMX. Users who are assigned administration privileges can perform administrative tasks. Cisco CMX User Accounts, page 1 Backing Up
How do I configure my LPL client to use SSL for incoming mail?
 How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
Unix System Architecture, File System, and Shell Commands
 Unix System Architecture, File System, and Shell Commands Prof. (Dr.) K.R. Chowdhary, Director COE Email: kr.chowdhary@iitj.ac.in webpage: http://www.krchowdhary.com JIET College of Engineering August
Unix System Architecture, File System, and Shell Commands Prof. (Dr.) K.R. Chowdhary, Director COE Email: kr.chowdhary@iitj.ac.in webpage: http://www.krchowdhary.com JIET College of Engineering August
Comprehensive Setup Guide for TLS on ESA
 Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Implementing DHCP for IPv6
 This module describes how to configure Dynamic Host Configuration Protocol (DHCP) for IPv6. DHCPv6 Prefix Delegation, page 1 How to Implement DHCP for IPv6, page 6 DHCPv6 Prefix Delegation The IPv6 Access
This module describes how to configure Dynamic Host Configuration Protocol (DHCP) for IPv6. DHCPv6 Prefix Delegation, page 1 How to Implement DHCP for IPv6, page 6 DHCPv6 Prefix Delegation The IPv6 Access
700 Fox Glen Barrington, Illinois ph/fx: [847] Setup Guide
![700 Fox Glen Barrington, Illinois ph/fx: [847] Setup Guide 700 Fox Glen Barrington, Illinois ph/fx: [847] Setup Guide](/thumbs/92/107779966.jpg) Email Setup Guide 1. Mac Mail Page 2 2. ios/iphone Page 7 3. Outlook 2016 Page 12 4. Outlook 2013 Page 20 5. Windows Mail Page 26 Mac Mail 1. Open Mac Mail. 2. In the top left, click Mail, then click Add
Email Setup Guide 1. Mac Mail Page 2 2. ios/iphone Page 7 3. Outlook 2016 Page 12 4. Outlook 2013 Page 20 5. Windows Mail Page 26 Mac Mail 1. Open Mac Mail. 2. In the top left, click Mail, then click Add
EX200 Q&A. DEMO Version
 Red Hat Certified System Administrator (RHCSA) Exam Q&A DEMO Version Copyright (c) 2015 Chinatag LLC. All rights reserved. Important Note Please Read Carefully For demonstration purpose only, this free
Red Hat Certified System Administrator (RHCSA) Exam Q&A DEMO Version Copyright (c) 2015 Chinatag LLC. All rights reserved. Important Note Please Read Carefully For demonstration purpose only, this free
M-Switch MIXER Evaluation Guide
 M-Switch MIXER Evaluation Guide Configuring M-Switch as a MIXER (SMTP/X.400) Gateway M-Switch MIXER Evaluation Guide Page 1 of 46 Objectives The purpose of this guide is to give the reader the tools to
M-Switch MIXER Evaluation Guide Configuring M-Switch as a MIXER (SMTP/X.400) Gateway M-Switch MIXER Evaluation Guide Page 1 of 46 Objectives The purpose of this guide is to give the reader the tools to
LECTURE 7. Readings: - SSH: The Definitive Guide; D.J. Barret et al.; O Reilly Lecture outline: - SSH. Marco Spaziani Brunella, Manuel Campo
 LECTURE 7 Readings: - SSH: The Definitive Guide; D.J. Barret et al.; O Reilly Lecture outline: - SSH Remote Managing In real life, physical access to network nodes is not always an option. Often, we need
LECTURE 7 Readings: - SSH: The Definitive Guide; D.J. Barret et al.; O Reilly Lecture outline: - SSH Remote Managing In real life, physical access to network nodes is not always an option. Often, we need
Web Authentication Proxy Configuration Example
 Web Authentication Proxy Configuration Example Document ID: 116052 Contributed by Nick Tate, Cisco TAC Engineer. May 02, 2013 Contents Introduction Prerequisites Requirements Components Used Conventions
Web Authentication Proxy Configuration Example Document ID: 116052 Contributed by Nick Tate, Cisco TAC Engineer. May 02, 2013 Contents Introduction Prerequisites Requirements Components Used Conventions
ITEC451 Network Design & Analysis Laboratory Guide: Appendix
 Linux Guide Accessing the command prompt Before you can access the command prompt, you must login to the system. The administrative user on Linux machines is named root. On most Linux distributions, you
Linux Guide Accessing the command prompt Before you can access the command prompt, you must login to the system. The administrative user on Linux machines is named root. On most Linux distributions, you
Troubleshooting CMX Connectivity with WLC
 Troubleshooting CMX Connectivity with WLC Contents Introduction Prerequisites Requirements Components Used Background Information Troubleshooting Possible Failure Scenarios Verify Reachability Time Synchronization
Troubleshooting CMX Connectivity with WLC Contents Introduction Prerequisites Requirements Components Used Background Information Troubleshooting Possible Failure Scenarios Verify Reachability Time Synchronization
Chapter 12: Advanced Operating Systems
 Chapter 12: Advanced Operating Systems IT Essentials: PC Hardware and Software v4.1 1 Chapter 12 Objectives 12.1 Select the appropriate operating system based on customer needs 12.2 Install, configure,
Chapter 12: Advanced Operating Systems IT Essentials: PC Hardware and Software v4.1 1 Chapter 12 Objectives 12.1 Select the appropriate operating system based on customer needs 12.2 Install, configure,
Configure Dynamic Host Configuration Protocol (DHCP) Image Upgrade Settings on a Switch through the Command Line Interface (CLI)
 Configure Dynamic Host Configuration Protocol (DHCP) Image Upgrade Settings on a Switch through the Command Line Interface (CLI) Objective The Dynamic Host Configuration Protocol (DHCP) image upgrade feature
Configure Dynamic Host Configuration Protocol (DHCP) Image Upgrade Settings on a Switch through the Command Line Interface (CLI) Objective The Dynamic Host Configuration Protocol (DHCP) image upgrade feature
Raspberry Pi Network Boot
 Raspberry Pi Network Boot @Phenomer October 22, 2014 1 Raspberry Pi SD initrd 2 /srv/pxe ( ) /srv/pxe /srv/pxe/tftp - TFTP /srv/pxe/tftp/pxelinux.cfg - /srv/pxe/repo - /srv/pxe/initrd - initrd % sudo mkdir
Raspberry Pi Network Boot @Phenomer October 22, 2014 1 Raspberry Pi SD initrd 2 /srv/pxe ( ) /srv/pxe /srv/pxe/tftp - TFTP /srv/pxe/tftp/pxelinux.cfg - /srv/pxe/repo - /srv/pxe/initrd - initrd % sudo mkdir
PT Activity: Configure AAA Authentication on Cisco Routers
 PT Activity: Configure AAA Authentication on Cisco Routers Instructor Version Topology Diagram Addressing Table Device Interface IP Address Subnet Mask R1 Fa0/0 192.168.1.1 255.255.255.0 S0/0/0 10.1.1.2
PT Activity: Configure AAA Authentication on Cisco Routers Instructor Version Topology Diagram Addressing Table Device Interface IP Address Subnet Mask R1 Fa0/0 192.168.1.1 255.255.255.0 S0/0/0 10.1.1.2
example.com index.html # vim /etc/httpd/conf/httpd.conf NameVirtualHost :80 <VirtualHost :80> DocumentRoot /var/www/html/
 example.com index.html # vim /etc/httpd/conf/httpd.conf NameVirtualHost 192.168.0.254:80 DocumentRoot /var/www/html/ ServerName station.domain40.example.com
example.com index.html # vim /etc/httpd/conf/httpd.conf NameVirtualHost 192.168.0.254:80 DocumentRoot /var/www/html/ ServerName station.domain40.example.com
Setting up IMAP Mail in Outlook
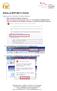 Setting up IMAP Mail in Outlook Setting up the Certificate in Internet Explorer 1. Open up Internet Explorer. Browse to https://intranet.yourschooldomain.school.nz. You will get a Certificate Error. Click
Setting up IMAP Mail in Outlook Setting up the Certificate in Internet Explorer 1. Open up Internet Explorer. Browse to https://intranet.yourschooldomain.school.nz. You will get a Certificate Error. Click
General Network Troubleshooting
 Overview Contents This document outlines some basic network troubleshooting techniques that can be used to test network connectivity. They are useful when troubleshooting issues with Crystal Enterprise
Overview Contents This document outlines some basic network troubleshooting techniques that can be used to test network connectivity. They are useful when troubleshooting issues with Crystal Enterprise
ACCURATE STUDY GUIDES, HIGH PASSING RATE! Question & Answer. Dump Step. provides update free of charge in one year!
 DUMP STEP Question & Answer ACCURATE STUDY GUIDES, HIGH PASSING RATE! Dump Step provides update free of charge in one year! http://www.dumpstep.com Exam : 650-156 Title : ISPES Cisco IronPort Security
DUMP STEP Question & Answer ACCURATE STUDY GUIDES, HIGH PASSING RATE! Dump Step provides update free of charge in one year! http://www.dumpstep.com Exam : 650-156 Title : ISPES Cisco IronPort Security
Chapter 12: Advanced Operating Systems
 : Advanced Operating Systems IT Essentials: PC Hardware and Software v4.0 1 Purpose of this Presentation To provide to instructors an overview of : List of chapter objectives Overview of the chapter contents,
: Advanced Operating Systems IT Essentials: PC Hardware and Software v4.0 1 Purpose of this Presentation To provide to instructors an overview of : List of chapter objectives Overview of the chapter contents,
Assignment 1: Build Environment
 Read the entire assignment before beginning! Submit deliverables to CourSys: https://courses.cs.sfu.ca/ Late penalty is 10% per calendar day (each 0 to 24 hour period past due, max 2 days). This assignment
Read the entire assignment before beginning! Submit deliverables to CourSys: https://courses.cs.sfu.ca/ Late penalty is 10% per calendar day (each 0 to 24 hour period past due, max 2 days). This assignment
Venafi DevOps Integrations
 Venafi DevOps Integrations Venafi Docker Key & Certificate Management Container t Version Date Description Author V1 March 20, 2017 Initial Version Walter Goulet V2 April 12, 2017 Updates per testing Walter
Venafi DevOps Integrations Venafi Docker Key & Certificate Management Container t Version Date Description Author V1 March 20, 2017 Initial Version Walter Goulet V2 April 12, 2017 Updates per testing Walter
Embedded Linux Systems. Bin Li Assistant Professor Dept. of Electrical, Computer and Biomedical Engineering University of Rhode Island
 Embedded Linux Systems Bin Li Assistant Professor Dept. of Electrical, Computer and Biomedical Engineering University of Rhode Island Generic Embedded Systems Structure User Sensors ADC microcontroller
Embedded Linux Systems Bin Li Assistant Professor Dept. of Electrical, Computer and Biomedical Engineering University of Rhode Island Generic Embedded Systems Structure User Sensors ADC microcontroller
F5 BIG-IQ Centralized Management: Licensing and Initial Setup. Version 5.1
 F5 BIG-IQ Centralized Management: Licensing and Initial Setup Version 5.1 Table of Contents Table of Contents BIG-IQ System Introduction...5 About BIG-IQ System Management...5 About secure communication
F5 BIG-IQ Centralized Management: Licensing and Initial Setup Version 5.1 Table of Contents Table of Contents BIG-IQ System Introduction...5 About BIG-IQ System Management...5 About secure communication
Course 55187B Linux System Administration
 Course Outline Module 1: System Startup and Shutdown This module explains how to manage startup and shutdown processes in Linux. Understanding the Boot Sequence The Grand Unified Boot Loader GRUB Configuration
Course Outline Module 1: System Startup and Shutdown This module explains how to manage startup and shutdown processes in Linux. Understanding the Boot Sequence The Grand Unified Boot Loader GRUB Configuration
Configuring the SSG. Basic SSG Configuration APPENDIX
 APPENDIX B This appendix illustrates some basic steps for configuring the Cisco Service Selection Gateway (SSG) to work with a Subscriber Edge Services Manager (SESM) web application. For a complete description
APPENDIX B This appendix illustrates some basic steps for configuring the Cisco Service Selection Gateway (SSG) to work with a Subscriber Edge Services Manager (SESM) web application. For a complete description
MiPDF.COM. 3. Which procedure is used to access a Cisco 2960 switch when performing an initial configuration in a secure environment?
 CCNA1 v6.0 Chapter 2 Exam Answers 2017 (100%) MiPDF.COM 1. What is the function of the kernel of an operating software? It provides a user interface that allows users to request a specific task. The kernel
CCNA1 v6.0 Chapter 2 Exam Answers 2017 (100%) MiPDF.COM 1. What is the function of the kernel of an operating software? It provides a user interface that allows users to request a specific task. The kernel
Configuring Switch Security
 CHAPTER 9 The authentication, authorization, and accounting (AAA) mechanism verifies the identity of, grants access to, and tracks the actions of users managing a switch. The Cisco MDS 9020 Fabric Switch
CHAPTER 9 The authentication, authorization, and accounting (AAA) mechanism verifies the identity of, grants access to, and tracks the actions of users managing a switch. The Cisco MDS 9020 Fabric Switch
Introduction to the UNIX command line
 Introduction to the UNIX command line Steven Abreu Introduction to Computer Science (ICS) Tutorial Jacobs University s.abreu@jacobs-university.de September 19, 2017 Overview What is UNIX? UNIX Shell Commands
Introduction to the UNIX command line Steven Abreu Introduction to Computer Science (ICS) Tutorial Jacobs University s.abreu@jacobs-university.de September 19, 2017 Overview What is UNIX? UNIX Shell Commands
Fireware-Essentials. Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.
 Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Full file at https://fratstock.eu
 Guide to UNIX Using Linux Fourth Edition Chapter 2 Solutions Answers to the Chapter 2 Review Questions 1. Your company is discussing plans to migrate desktop and laptop users to Linux. One concern raised
Guide to UNIX Using Linux Fourth Edition Chapter 2 Solutions Answers to the Chapter 2 Review Questions 1. Your company is discussing plans to migrate desktop and laptop users to Linux. One concern raised
RoamServer Windows Admin Guide
 RoamServer 6.0.0 Windows Admin Guide V E R S I O N 1.0, M A Y 2 0 1 5 Corporate Headquarters ipass Inc. 3800 Bridge Parkway Redwood Shores, CA 94065 USA www.ipass.com +1 650-232-4100 +1 650-232-0227 fx
RoamServer 6.0.0 Windows Admin Guide V E R S I O N 1.0, M A Y 2 0 1 5 Corporate Headquarters ipass Inc. 3800 Bridge Parkway Redwood Shores, CA 94065 USA www.ipass.com +1 650-232-4100 +1 650-232-0227 fx
Key Management and Distribution
 Key Management and Distribution Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Key Management and Distribution Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Basic Linux Command Line Interface Guide
 This basic Linux Command-Line Interface (CLI) Guide provides a general explanation of commonly used Bash shell commands for the Barracuda NG Firewall. You can access the command-line interface by connecting
This basic Linux Command-Line Interface (CLI) Guide provides a general explanation of commonly used Bash shell commands for the Barracuda NG Firewall. You can access the command-line interface by connecting
Linux Systems Administration Getting Started with Linux
 Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
How To Set Up A Postfix Autoresponder With Autoresponse
 By Falko Timme Published: 2009-04-02 11:34 How To Set Up A Postfix Autoresponder With Autoresponse Version 1.0 Author: Falko Timme Last edited 03/25/2009 Autoresponse is
By Falko Timme Published: 2009-04-02 11:34 How To Set Up A Postfix Autoresponder With Autoresponse Version 1.0 Author: Falko Timme Last edited 03/25/2009 Autoresponse is
At course completion. Overview. Audience profile. Course Outline. : 55187B: Linux System Administration. Course Outline :: 55187B::
 Module Title Duration : 55187B: Linux System Administration : 4 days Overview This four-day instructor-led course is designed to provide students with the necessary skills and abilities to work as a professional
Module Title Duration : 55187B: Linux System Administration : 4 days Overview This four-day instructor-led course is designed to provide students with the necessary skills and abilities to work as a professional
Configuring Secrets Management on the Avaya G250 and G350 Media Gateways - Issue 1.0
 Avaya Solution & Interoperability Test Lab Configuring Secrets Management on the Avaya G250 and G350 Media Gateways - Issue 1.0 Abstract Previous releases of the Avaya G250 and G350 Media Gateways maintained
Avaya Solution & Interoperability Test Lab Configuring Secrets Management on the Avaya G250 and G350 Media Gateways - Issue 1.0 Abstract Previous releases of the Avaya G250 and G350 Media Gateways maintained
CCNA R&S: Introduction to Networks. Chapter 10: The Application Layer
 CCNA R&S: Introduction to Networks Chapter 10: The Application Layer Frank Schneemann 10.0.1.1 Introduction 10.0.1.2 Activity - Application Investigation 10.1.1.1 OSI and TCP/IP Models Revisited The application
CCNA R&S: Introduction to Networks Chapter 10: The Application Layer Frank Schneemann 10.0.1.1 Introduction 10.0.1.2 Activity - Application Investigation 10.1.1.1 OSI and TCP/IP Models Revisited The application
"Charting the Course... MOC B: Linux System Administration. Course Summary
 Description Course Summary This four-day instructor-led course is designed to provide students with the necessary skills and abilities to work as a professional Linux system administrator. The course covers
Description Course Summary This four-day instructor-led course is designed to provide students with the necessary skills and abilities to work as a professional Linux system administrator. The course covers
Basic Linux Command Line Interface Guide
 This basic Linux Command-Line Interface (CLI) Guide provides a general explanation of commonly used Bash shell commands for the Barracuda NG Firewall. You can access the command-line interface by connecting
This basic Linux Command-Line Interface (CLI) Guide provides a general explanation of commonly used Bash shell commands for the Barracuda NG Firewall. You can access the command-line interface by connecting
CCNA Security 1.0 Student Packet Tracer Manual
 1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
Using the Offline Diagnostic Monitor Menu
 APPENDIX B Using the Offline Diagnostic Monitor Menu During the boot process, you can access the Offline Diagnostic Monitor (Offline DM) Main menu. The Offline DM Main menu allows you to perform the following
APPENDIX B Using the Offline Diagnostic Monitor Menu During the boot process, you can access the Offline Diagnostic Monitor (Offline DM) Main menu. The Offline DM Main menu allows you to perform the following
Two factor authentication for SSH using PAM RADIUS module
 Two factor authentication for SSH using PAM RADIUS module sandbox-logintc.com/docs/connectors/ssh.html Introduction LoginTC makes it easy for administrators to add multi-factor to SSH on their Unix systems.
Two factor authentication for SSH using PAM RADIUS module sandbox-logintc.com/docs/connectors/ssh.html Introduction LoginTC makes it easy for administrators to add multi-factor to SSH on their Unix systems.
