Step 3: Select This computer is part of business network,., click next
|
|
|
- Cornelia Bennett
- 5 years ago
- Views:
Transcription
1 GPFS Installation Notes 1. Install Windows 2. Join domain with the domain administrator account Step 1: go to System Step 2: Click on Network ID Step 3: Select This computer is part of business network,., click next 1 P age
2 Step 4: Select My company uses a network with a domain, click next 2 P age
3 Step 5: Enter the User name in the form Domain name will then become inactive and should be empty. (enter your password too of course..), click next Step 6: Computer name: whatever you want to call it, and Computer Domain is ADNS.UNSW.EDU.AU, click Next Step 7: enter username in the form z123456_sa and Domain ADUNSW, click OK 3 P age
4 4 P age Step 8: Add the AD root account put in root for username and ADUNSW for domain. the only thing is now when you restart the computer it will try to log you on to the domain (which is where i got a bit confused) and you ll need to put LIFTOUT PC\liftout as the username in order to log back in to the local admin account.
5 3. While logged in as the local mahcine admin, run GPFS auto run installer 4. Enter domain name and root password to continue. Ensure that you use Test passwords 5 P age
6 5. Click save and run and you should have the following output 6. Installation does two reboot automatically, the process may take up to 5 minutes to complete. DO NOT LOGIN and interrupt. After second reboot, login as domain\root 7. Upon the completion of installation, you see the following desktop, including: 6 P age
7 8. Fix for incorrect username follows, this might be fixed in future with a domain alternation. Run the following commands, taking note to substitute the correct root password. 8.1 mkpasswd c >> /etc/passwd 8.2 sed I s/adunsw+root/root/ /etc/passwd 8.3 exit out of the Admin Korn Shell and start it up again 8.4 Stop the ssh server with: 8.5 Remove the ssh server with: 8.6 ssh host config y u root w ROOT Password HERE 7 P age
8 8.7 Start the ssh server with: cygrunsrv start sshd 8 P age
9 9. Create a local ssh key with, ssh keygen t rsa, then press enter to get the defaults 10. ssh to DDN VM at as root via GPFS Admin Korn Shell ssh Edit /etc/hosts and ensure that the ip address of the new client is there 12. Copy this file back to the client machine 9 P age
10 13. Copy the vm s authorized_keys file to the client with the command scp ~/.ssh/authorized_keys gpfs02:/root/.ssh/ 14. In another shell on the client, add the contents of the hosts file that you just copied to the local machines hosts file using: cat hosts >> /cygdrive/c/windows/system32/drivers/etc/hosts 15. If the node already exists on the GPFS cluster (node reinstallation), then you can add it back to the cluster, using the commands as shown bellow 15.1 [root@ls vm1 ~]# mmauth genkey propagate N gpfs [root@ls vm1 ~]# mmsdrrestore N gpfs [root@ls vm1 ~]# mmstartup N gpfs If auto installation not working properly, go to GS3 folder to run 3 programs from the top one by one. 10 P age
11 17. Add client node to GPFS with "mmaddnode N gpfs02" and then accept the license "mmchlicense client accept N gpfs02" 18. To start up node, type "mmstartup" and enter on the local node terminal 19. Check gpfs02 status, type "mmgetstate" to confirm if gpfs02 is active, if not, just wait and check again till gsclient becomes active 20. mount gpfs, type "mmmount gpfs01" and enter on the local terminal, it may take 2 minutes to mount. You may need to click on the Windows driver prompt and tell it to accept the gpfs client driver 11 P age
12 21. After reboot, G drive may take a 2 minutes to shown up on My Computer depending on the pc and network performance 12 P age
Reset the Admin Password with the ExtraHop Rescue CD
 Reset the Admin Password with the ExtraHop Rescue CD Published: 2018-01-19 This guide explains how to reset the administration password on physical and virtual ExtraHop appliances with the ExtraHop Rescue
Reset the Admin Password with the ExtraHop Rescue CD Published: 2018-01-19 This guide explains how to reset the administration password on physical and virtual ExtraHop appliances with the ExtraHop Rescue
Configure HOSTNAME by adding the hostname to the file /etc/sysconfig/network. Do the same to all the all nodes.
 Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Configure HOSTNAME by adding the hostname to the file /etc/sysconfig/network. Do the same to all the other 3(4) nodes.
 Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Application Scenarios of DG-NS5004 Cloud Storage Syncbox Feature
 Application Scenarios of DG-NS5004 Cloud Storage Syncbox Feature To automatically sync & update a specific drive/ data folder on a PC to a NAS:- * Once the syncbox Server is loaded on NAS, it will be displayed
Application Scenarios of DG-NS5004 Cloud Storage Syncbox Feature To automatically sync & update a specific drive/ data folder on a PC to a NAS:- * Once the syncbox Server is loaded on NAS, it will be displayed
Cryptography Application : SSH. Cyber Security & Network Security March, 2017 Dhaka, Bangladesh
 Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Introduction to Linux Workshop 2. The George Washington University SEAS Computing Facility
 Introduction to Linux Workshop 2 The George Washington University SEAS Computing Facility Course Goals SSH and communicating with other machines Public/Private key generation,.ssh directory, and the config
Introduction to Linux Workshop 2 The George Washington University SEAS Computing Facility Course Goals SSH and communicating with other machines Public/Private key generation,.ssh directory, and the config
LECTURE 7. Readings: - SSH: The Definitive Guide; D.J. Barret et al.; O Reilly Lecture outline: - SSH. Marco Spaziani Brunella, Manuel Campo
 LECTURE 7 Readings: - SSH: The Definitive Guide; D.J. Barret et al.; O Reilly Lecture outline: - SSH Remote Managing In real life, physical access to network nodes is not always an option. Often, we need
LECTURE 7 Readings: - SSH: The Definitive Guide; D.J. Barret et al.; O Reilly Lecture outline: - SSH Remote Managing In real life, physical access to network nodes is not always an option. Often, we need
Aliases are set manually or in a login script. Aliases that were set manually will be gone the next time you login.
 Page 1 and 2: question without commands. Page 3 7 : questions with answers. Aliases are set manually or in a login script. Aliases that were set manually will be gone the next time you login. 1. List your
Page 1 and 2: question without commands. Page 3 7 : questions with answers. Aliases are set manually or in a login script. Aliases that were set manually will be gone the next time you login. 1. List your
Automated Configuration and Administration of a Storage-class Memory System to Support Supercomputer-based Scientific Workflows
 Automated Configuration and Administration of a Storage-class Memory System to Support Supercomputer-based Scientific Workflows J. Bernard 1, P. Morjan 2, B. Hagley 3, F. Delalondre 1, F. Schürmann 1,
Automated Configuration and Administration of a Storage-class Memory System to Support Supercomputer-based Scientific Workflows J. Bernard 1, P. Morjan 2, B. Hagley 3, F. Delalondre 1, F. Schürmann 1,
SSH. What is Safely 6/19/ June 2018 PacNOG 22, Honiara, Solomon Islands Supported by:
 SSH 25-29 June 2018 PacNOG 22, Honiara, Solomon Islands Supported by: Issue Date: Revision: 1 What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows
SSH 25-29 June 2018 PacNOG 22, Honiara, Solomon Islands Supported by: Issue Date: Revision: 1 What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows
What is Secure. Authenticated I know who I am talking to. Our communication is Encrypted
 Crypto App - SSH 1 What is Secure Authenticated I know who I am talking to Our communication is Encrypted Telnet clear text Servers Terminal clear text Routers SSH encrypted channel encrypted text Servers
Crypto App - SSH 1 What is Secure Authenticated I know who I am talking to Our communication is Encrypted Telnet clear text Servers Terminal clear text Routers SSH encrypted channel encrypted text Servers
Quick Installation Guide for RHV/Ovirt
 Quick Installation Guide for RHV/Ovirt 2017 Chengdu Vinchin Technology Co. Ltd. All rights reserved. CONTENTS 1. Create New Virtual Machine...2 2. Install Backup Server ( as master)...5 3. Install Backup
Quick Installation Guide for RHV/Ovirt 2017 Chengdu Vinchin Technology Co. Ltd. All rights reserved. CONTENTS 1. Create New Virtual Machine...2 2. Install Backup Server ( as master)...5 3. Install Backup
CSCI 350 Virtual Machine Setup Guide
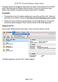 CSCI 350 Virtual Machine Setup Guide This guide will take you through the steps needed to set up the virtual machine to do the PintOS project. Both Macintosh and Windows will run just fine. We have yet
CSCI 350 Virtual Machine Setup Guide This guide will take you through the steps needed to set up the virtual machine to do the PintOS project. Both Macintosh and Windows will run just fine. We have yet
Start Up and Shutdown Procedures (Unix)
 Start Up and Shutdown Procedures (Unix) Start Up On Main Console 1. Press the Server main power button ON 2. The system will automatically go through the start-up procedures, which will be displayed on
Start Up and Shutdown Procedures (Unix) Start Up On Main Console 1. Press the Server main power button ON 2. The system will automatically go through the start-up procedures, which will be displayed on
ssh and handson Matsuzaki maz Yoshinobu 1
 ssh and handson Matsuzaki maz Yoshinobu maz@iij.ad.jp 1 Secure Shell (ssh) Replacement for unsecure tools/protocols rsh and telnet Usually listen on tcp/22 Whole communication is encrypted
ssh and handson Matsuzaki maz Yoshinobu maz@iij.ad.jp 1 Secure Shell (ssh) Replacement for unsecure tools/protocols rsh and telnet Usually listen on tcp/22 Whole communication is encrypted
Jackson State University Department of Computer Science CSC / Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
2016 TaxSlayer Pro Desktop. Logging in to the Program Usernames/Passwords
 2016 TaxSlayer Pro Desktop Logging in to the Program Usernames/Passwords Contents Logging in to the Program... 2 First Time Logging In... 2 Forgot Username/Password Preparer... 4 Logging in as ADMIN...
2016 TaxSlayer Pro Desktop Logging in to the Program Usernames/Passwords Contents Logging in to the Program... 2 First Time Logging In... 2 Forgot Username/Password Preparer... 4 Logging in as ADMIN...
Author A.Kishore/Sachin WinSCP
 WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
InterWorx Server Administrator SSH Guide. by InterWorx LLC
 InterWorx Server Administrator SSH Guide by InterWorx LLC Contents 1 SSH guide 2 1.1 History.................................................. 2 1.2 Shell Users graph.............................................
InterWorx Server Administrator SSH Guide by InterWorx LLC Contents 1 SSH guide 2 1.1 History.................................................. 2 1.2 Shell Users graph.............................................
Cryptography Application : SSH. 7 Sept 2017, Taichung, Taiwan
 Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Windows 10 IoT QSG Edited Draft
 Initial Setup and Configuration Windows 10 IoT QSG Edited Draft By default, when you first boot up your new Windows 10 IoT 10ZiG Thin Client, you are automatically logged in as Administrator. While logged
Initial Setup and Configuration Windows 10 IoT QSG Edited Draft By default, when you first boot up your new Windows 10 IoT 10ZiG Thin Client, you are automatically logged in as Administrator. While logged
Remote Access to Unix Machines
 Remote Access to Unix Machines Alvin R. Lebeck Department of Computer Science Department of Electrical and Computer Engineering Duke University Overview We are using OIT Linux machines for some homework
Remote Access to Unix Machines Alvin R. Lebeck Department of Computer Science Department of Electrical and Computer Engineering Duke University Overview We are using OIT Linux machines for some homework
WinSCP. Author A.Kishore/Sachin
 WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
Using RDP with Azure Linux Virtual Machines
 Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Cryptography - SSH. Network Security Workshop May 2017 Phnom Penh, Cambodia
 Cryptography - SSH Network Security Workshop 29-31 May 2017 Phnom Penh, Cambodia What is Safely Authentication I know who I am talking with Our communication is Encrypted Telnet Servers Terminal Routers
Cryptography - SSH Network Security Workshop 29-31 May 2017 Phnom Penh, Cambodia What is Safely Authentication I know who I am talking with Our communication is Encrypted Telnet Servers Terminal Routers
FEPS. SSH Access with Two-Factor Authentication. RSA Key-pairs
 FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
Cryptography - SSH. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography - SSH Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 What is Secure Authentication I know who I am talking to Our communication is Encrypted Telnet Servers Terminal
Cryptography - SSH Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 What is Secure Authentication I know who I am talking to Our communication is Encrypted Telnet Servers Terminal
Building Block Installation - Admins
 Building Block Installation - Admins Overview To use your Blackboard Server with Panopto, you first need to install the Panopto Building Block on your Blackboard server. You then need to add Blackboard
Building Block Installation - Admins Overview To use your Blackboard Server with Panopto, you first need to install the Panopto Building Block on your Blackboard server. You then need to add Blackboard
Configuring a Standalone VCL Environment using VMware Server 2.0
 Configuring a Standalone VCL Environment using VMware Server 2.0 DISCLAIMER! This document provides instuctions for configuring a standalone VCL environment running on a single computer which is able to
Configuring a Standalone VCL Environment using VMware Server 2.0 DISCLAIMER! This document provides instuctions for configuring a standalone VCL environment running on a single computer which is able to
GIT. A free and open source distributed version control system. User Guide. January, Department of Computer Science and Engineering
 GIT A free and open source distributed version control system User Guide January, 2018 Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Table of Contents What is
GIT A free and open source distributed version control system User Guide January, 2018 Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Table of Contents What is
Configuring SSH Public Key Authentication
 6AOSCG0060-29A January 2014 Configuration Guide Configuring SSH Public Key Authentication This guide describes how to configure and use Secure Shell (SSH) public key authentication on products running
6AOSCG0060-29A January 2014 Configuration Guide Configuring SSH Public Key Authentication This guide describes how to configure and use Secure Shell (SSH) public key authentication on products running
SmartCash SmartNode SCRIPT Setup Guide v2.2. Windows 10. Date: 20/02/2018. By (Jazz) yoyomonkey
 SmartCash SmartNode SCRIPT Setup Guide v2.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at
SmartCash SmartNode SCRIPT Setup Guide v2.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at
Before you start you must ensure that you have your most recent backup available and it can be read by the computer that you are restoring RMS to.
 RMS Server Crash Recovery Procedure Overview Important Information Step One - Regional Settings Step Two - Windows Updates Step Three - Install SQL Express 2008 Step Four - Create RMSWIN folder Step Five
RMS Server Crash Recovery Procedure Overview Important Information Step One - Regional Settings Step Two - Windows Updates Step Three - Install SQL Express 2008 Step Four - Create RMSWIN folder Step Five
CIS 231 Windows 10 Install Lab # 3
 CIS 231 Windows 10 Install Lab # 3 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in
CIS 231 Windows 10 Install Lab # 3 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in
Siemens PLM Software. HEEDS MDO Setting up a Windows-to- Linux Compute Resource.
 Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Troubleshooting the Installation
 CHAPTER 5 This chapter provides information about basic troubleshooting tips and error messages that you may encounter during the installation of the Cisco Linux operating system or the Cisco IPICS server
CHAPTER 5 This chapter provides information about basic troubleshooting tips and error messages that you may encounter during the installation of the Cisco Linux operating system or the Cisco IPICS server
Test Lab Introduction to the Test Lab Linux Cluster Environment
 Test Lab 1.0 - Introduction to the Test Lab Linux Cluster Environment Test lab is a set of three disposable cluster environments that can be used for systems research. All three environments are accessible
Test Lab 1.0 - Introduction to the Test Lab Linux Cluster Environment Test lab is a set of three disposable cluster environments that can be used for systems research. All three environments are accessible
Siemens PLM Software. HEEDS MDO Setting up a Windows-to- Windows Compute Resource.
 Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Windows Compute Resource www.redcedartech.com. Setting up a Windows-to-Windows Compute Resource Contents Introduction 1 On Remote Machine
Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Windows Compute Resource www.redcedartech.com. Setting up a Windows-to-Windows Compute Resource Contents Introduction 1 On Remote Machine
Installation of Cisco Business Edition 6000H/M
 Installation Overview, page 1 Installation Task Flow of Cisco Business Edition 6000H/M, page 2 Installation Overview This chapter describes the tasks that you must perform to install software on your Business
Installation Overview, page 1 Installation Task Flow of Cisco Business Edition 6000H/M, page 2 Installation Overview This chapter describes the tasks that you must perform to install software on your Business
DGS-3630-Series Switches
 DGS-3630-Series Switches Switch Management Interfaces Adding Administrator Account Enabling Remote Management (SSH) Changing Switch IP Address Saving Configuration Resetting to Factory Defaults Switch
DGS-3630-Series Switches Switch Management Interfaces Adding Administrator Account Enabling Remote Management (SSH) Changing Switch IP Address Saving Configuration Resetting to Factory Defaults Switch
How to open ports in the DSL router firmware version 2.xx and above
 How to open ports in the DSL router firmware version 2.xx and above This example shows how to open port 3389 (which is used by Remote Desktop service) in the DSL router running firmware version 2.xx or
How to open ports in the DSL router firmware version 2.xx and above This example shows how to open port 3389 (which is used by Remote Desktop service) in the DSL router running firmware version 2.xx or
InControl 2 Software Appliance Setup Guide
 InControl 2 Software Appliance Setup Guide (Last updated: 2017-11) Contents 1. Introduction Minimum Hardware Requirements 2. For VMware ESXi 6.0 and ESXi 5.5 (SCSI) Networking Creating InControl and DB
InControl 2 Software Appliance Setup Guide (Last updated: 2017-11) Contents 1. Introduction Minimum Hardware Requirements 2. For VMware ESXi 6.0 and ESXi 5.5 (SCSI) Networking Creating InControl and DB
TELE301 Lab16 - The Secure Shell
 TELE301 Lab16 - The Secure Shell Department of Telecommunications May 7, 2002 Contents 1 Introduction 2 2 OpenSSH 2 3 Replacing Telnet 2 4 Logging in without a password 2 5 SSH Agent 3 5.1 SSH Add..............................
TELE301 Lab16 - The Secure Shell Department of Telecommunications May 7, 2002 Contents 1 Introduction 2 2 OpenSSH 2 3 Replacing Telnet 2 4 Logging in without a password 2 5 SSH Agent 3 5.1 SSH Add..............................
Managing the Mobility Express Network
 Under the Management tab on the navigation pane, an admin users can do the following: 1 Configure access to the Mobility Express controller 2 Manage Admin Accounts 3 Configure Time 4 Perform a Software
Under the Management tab on the navigation pane, an admin users can do the following: 1 Configure access to the Mobility Express controller 2 Manage Admin Accounts 3 Configure Time 4 Perform a Software
WA2342 NoSQL Systems Comparison. Lab Server VM Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
More Raspian. An editor Configuration files Shell scripts Shell variables System admin
 More Raspian An editor Configuration files Shell scripts Shell variables System admin Nano, a simple editor Nano does not require the mouse. You must use your keyboard to move around the file and make
More Raspian An editor Configuration files Shell scripts Shell variables System admin Nano, a simple editor Nano does not require the mouse. You must use your keyboard to move around the file and make
Xcalenets Console Setup Guide. Xcalenets Console Setup Guide (Standalone version)
 Xcalenets Console Setup Guide Xcalenets Console Setup Guide (Standalone version) 1 Content CONTENT... 2 Getting Started to Xcalenets Console Setup... 3 Account Level Introduction... 3 Login Console Setup...
Xcalenets Console Setup Guide Xcalenets Console Setup Guide (Standalone version) 1 Content CONTENT... 2 Getting Started to Xcalenets Console Setup... 3 Account Level Introduction... 3 Login Console Setup...
CS 200. User IDs, Passwords, Permissions & Groups. User IDs, Passwords, Permissions & Groups. CS 200 Spring 2017
 CS 200 User IDs, Passwords, Permissions & Groups 1 Needed to control access to sharepoints and their contents Because Macs & PCs now support multiple accounts, user IDs and passwords are also needed on
CS 200 User IDs, Passwords, Permissions & Groups 1 Needed to control access to sharepoints and their contents Because Macs & PCs now support multiple accounts, user IDs and passwords are also needed on
Cisco HyperFlex Upgrade Guide for Microsoft Hyper-V, Release 3.5
 First Published: 2018-10-16 Last Modified: 2018-11-19 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2018-10-16 Last Modified: 2018-11-19 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Getting started with Raspberry Pi (and WebIoPi framework)
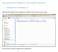 Getting started with Raspberry Pi (and WebIoPi framework) 1. Installing the OS on the Raspberry Pi Download the image file from the Raspberry Pi website. It ll be a zip file as shown below: Unzip the file
Getting started with Raspberry Pi (and WebIoPi framework) 1. Installing the OS on the Raspberry Pi Download the image file from the Raspberry Pi website. It ll be a zip file as shown below: Unzip the file
An Overview of SSH. Presentation to Linux Users of Victoria. Melbourne, August 26, 2017
 An Overview of SSH Presentation to Linux Users of Victoria Melbourne, August 26, 2017 http://levlafayette.com Utilisation and Rationale The most common use of SSH (secure shell) is remote login access
An Overview of SSH Presentation to Linux Users of Victoria Melbourne, August 26, 2017 http://levlafayette.com Utilisation and Rationale The most common use of SSH (secure shell) is remote login access
Lab 7 Configuring Basic Router Settings with IOS CLI
 Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Guideline for the installation of C-MOR Video Surveillance Virtual Machine on VMware ESX Server
 This guideline illustrates the installation of the C-MOR Video Surveillance Virtual Machine on VMware ESX Server. This manual applies to C-MOR version 4 with 64 bit operating system. First download the
This guideline illustrates the installation of the C-MOR Video Surveillance Virtual Machine on VMware ESX Server. This manual applies to C-MOR version 4 with 64 bit operating system. First download the
CTEC1863/2018F Bonus Lab Page 1 of 5
 CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
Upgrading Software and Firmware
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
Configure Dynamic Host Configuration Protocol (DHCP) Image Upgrade Settings on a Switch through the Command Line Interface (CLI)
 Configure Dynamic Host Configuration Protocol (DHCP) Image Upgrade Settings on a Switch through the Command Line Interface (CLI) Objective The Dynamic Host Configuration Protocol (DHCP) image upgrade feature
Configure Dynamic Host Configuration Protocol (DHCP) Image Upgrade Settings on a Switch through the Command Line Interface (CLI) Objective The Dynamic Host Configuration Protocol (DHCP) image upgrade feature
Installing and Upgrading Cisco Network Registrar Virtual Appliance
 CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
R9.7 erwin License Server:
 R9.7 erwin License Server: Installation and Setup This is a quick guide to setting-up a erwin DM License Server. NOTES: - Concurrent licensing is available for only erwin r8.2 and later releases! - Concurrent
R9.7 erwin License Server: Installation and Setup This is a quick guide to setting-up a erwin DM License Server. NOTES: - Concurrent licensing is available for only erwin r8.2 and later releases! - Concurrent
1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu. FireFox
 CIS 231 Windows 7 Install Lab #2 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
CIS 231 Windows 7 Install Lab #2 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
WCM 6.0 Pro MS/SP Software Recovery Installation Guide
 Release Date: 2013/09/23 WCM 6.0 Pro MS/SP Software Recovery Installation Guide Once the OS is restored or re-imaged successfully on the system, please follow below installation guide to complete all the
Release Date: 2013/09/23 WCM 6.0 Pro MS/SP Software Recovery Installation Guide Once the OS is restored or re-imaged successfully on the system, please follow below installation guide to complete all the
Symantec NetBackup Appliances Hands-On Lab
 Symantec NetBackup Appliances Hands-On Lab Description NetBackup Appliances Hands On Lab This lab assumes a prerequisite knowledge of NetBackup, specifically configuring storage units, creating backup
Symantec NetBackup Appliances Hands-On Lab Description NetBackup Appliances Hands On Lab This lab assumes a prerequisite knowledge of NetBackup, specifically configuring storage units, creating backup
Filesharing. Jason Healy, Director of Networks and Systems
 Filesharing Jason Healy, Director of Networks and Systems Last Updated Mar 18, 2008 2 Contents 1 Name of Project Here 5 1.1 Introduction.............................. 5 1.2 Initial Setup..............................
Filesharing Jason Healy, Director of Networks and Systems Last Updated Mar 18, 2008 2 Contents 1 Name of Project Here 5 1.1 Introduction.............................. 5 1.2 Initial Setup..............................
Setting up PuTTY. Software* Download PuTTY 6/9/18. Microsoft Windows 7 (64-bit) PuTTY 0.70 (64-bit) PuTTYgen 0.70 (64-bit) WinSCP 5.13.
 Software* Setting up PuTTY CTEC1767 Data Communications & Networking CTEC1863 Operating Systems CTEC1906 Internet Computing Microsoft Windows 7 (64-bit) PuTTY 0.70 (64-bit) PuTTYgen 0.70 (64-bit) WinSCP
Software* Setting up PuTTY CTEC1767 Data Communications & Networking CTEC1863 Operating Systems CTEC1906 Internet Computing Microsoft Windows 7 (64-bit) PuTTY 0.70 (64-bit) PuTTYgen 0.70 (64-bit) WinSCP
SSH Product Overview
 SSH Product Overview SSH Product Overview Understanding SSH SSH Discovery and Remediation Agentless SSH Agent Based SSH 2018 Venafi. All Rights Reserved. 2 Where is SSH used? File Transfer & Remote Script
SSH Product Overview SSH Product Overview Understanding SSH SSH Discovery and Remediation Agentless SSH Agent Based SSH 2018 Venafi. All Rights Reserved. 2 Where is SSH used? File Transfer & Remote Script
New Dropbox Users (don t have a Dropbox account set up with your Exeter account)
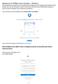 The setup process will determine if you already have a Dropbox account associated with an Exeter email address, and if so, you'll be given a choice to move those contents to your Phillips Exeter Dropbox
The setup process will determine if you already have a Dropbox account associated with an Exeter email address, and if so, you'll be given a choice to move those contents to your Phillips Exeter Dropbox
Building a virtual network Maher Saad, Chestnut Residence, University of Toronto
 Building a virtual network Maher Saad, Chestnut Residence, University of Toronto Disclaimer The author of this document shall not carry responsibility for any damage to the network, computer(s) software
Building a virtual network Maher Saad, Chestnut Residence, University of Toronto Disclaimer The author of this document shall not carry responsibility for any damage to the network, computer(s) software
Retrieve Download File from CSDI Installation Instructions
 Retrieve Download File from CSDI Installation Instructions Rev. 12-001 FOOD & NUTRITION MANAGEMENT SYSTEMS This instruction sheet provides instructions for installing our Retrieve Download File from CSDI
Retrieve Download File from CSDI Installation Instructions Rev. 12-001 FOOD & NUTRITION MANAGEMENT SYSTEMS This instruction sheet provides instructions for installing our Retrieve Download File from CSDI
How to Back Up and Restore Application Consistent Snapshots of SQL and Exchange Databases
 How to Back Up and Restore Application Consistent Snapshots of SQL and Exchange Databases How To#: 4041 Title: How to Back Up and Restore Application Consistent Snapshots of SQL and Exchange Databases
How to Back Up and Restore Application Consistent Snapshots of SQL and Exchange Databases How To#: 4041 Title: How to Back Up and Restore Application Consistent Snapshots of SQL and Exchange Databases
CIS 231 Windows 7 Install Lab #2
 CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
The following topics explain how to get started configuring Firepower Threat Defense. Table 1: Firepower Device Manager Supported Models
 The following topics explain how to get started configuring Firepower Threat Defense. Is This Guide for You?, page 1 Logging Into the System, page 2 Setting Up the System, page 6 Configuration Basics,
The following topics explain how to get started configuring Firepower Threat Defense. Is This Guide for You?, page 1 Logging Into the System, page 2 Setting Up the System, page 6 Configuration Basics,
Installing the Is2 Onsite Version - HVAC Office System
 Installing the Is2 Onsite Version - HVAC Office System This document describes the full onsite server installation of the Is2 database files, the database server, and the application server. The full program
Installing the Is2 Onsite Version - HVAC Office System This document describes the full onsite server installation of the Is2 database files, the database server, and the application server. The full program
Deploying Cisco UCS Central
 This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
802.11g Super-G 108Mb Wireless Access Point Quick Installation Guide
 802.11g Super-G 108Mb Wireless Access Point Quick Installation Guide The enclosed Hardware Installation Guide gives you a step-by-step explanation of how to install your 108Mb Super-G PCI Adapter. Further
802.11g Super-G 108Mb Wireless Access Point Quick Installation Guide The enclosed Hardware Installation Guide gives you a step-by-step explanation of how to install your 108Mb Super-G PCI Adapter. Further
Lab - System Restore in Windows 8
 Lab - System Restore in Windows 8 Introduction In this lab, you will create a restore point and use it to restore your computer. Recommended Equipment A computer running Windows 8 Step 1: Create a restore
Lab - System Restore in Windows 8 Introduction In this lab, you will create a restore point and use it to restore your computer. Recommended Equipment A computer running Windows 8 Step 1: Create a restore
Installation. Power on and initial setup. Before You Begin. Procedure
 Power on and initial setup, page 1 Customize ESXi host for remote access, page 4 Access and configure ESXi host, page 6 Deploy virtual machines, page 13 Install applications on virtual machines, page 14
Power on and initial setup, page 1 Customize ESXi host for remote access, page 4 Access and configure ESXi host, page 6 Deploy virtual machines, page 13 Install applications on virtual machines, page 14
ITDUMPS QUESTION & ANSWER. Accurate study guides, High passing rate! IT dumps provides update free of charge in one year!
 ITDUMPS QUESTION & ANSWER Accurate study guides, High passing rate! IT dumps provides update free of charge in one year! HTTP://WWW.ITDUMPS.COM Exam : 1Z0-100 Title : Oracle Linux 5 and 6 System Administration
ITDUMPS QUESTION & ANSWER Accurate study guides, High passing rate! IT dumps provides update free of charge in one year! HTTP://WWW.ITDUMPS.COM Exam : 1Z0-100 Title : Oracle Linux 5 and 6 System Administration
Using RANCID. Contents. 1 Introduction Goals Notes Install rancid Add alias Configure rancid...
 Using RANCID Contents 1 Introduction 2 1.1 Goals................................. 2 1.2 Notes................................. 2 2 Install rancid 2 2.1 Add alias............................... 3 2.2 Configure
Using RANCID Contents 1 Introduction 2 1.1 Goals................................. 2 1.2 Notes................................. 2 2 Install rancid 2 2.1 Add alias............................... 3 2.2 Configure
Labtainer Student Guide
 Labtainer Student Guide January 18, 2018 1 Introduction This manual is intended for use by students performing labs with Labtainers. Labtainers assume you have a Linux system, e.g., a virtual machine.
Labtainer Student Guide January 18, 2018 1 Introduction This manual is intended for use by students performing labs with Labtainers. Labtainers assume you have a Linux system, e.g., a virtual machine.
No More Passwords (with SSH)
 No More Passwords (with SSH) Ted Dustman March 30, 2009 Contents 1 Introduction 1 1.1 Local or Remote?................................. 1 1.2 SSH Command Set................................ 1 2 Authentication
No More Passwords (with SSH) Ted Dustman March 30, 2009 Contents 1 Introduction 1 1.1 Local or Remote?................................. 1 1.2 SSH Command Set................................ 1 2 Authentication
How to setup Failover in Linux NVR
 How to setup Failover in Linux NVR Application Note Version 1.0 1 Preface This application note instructs you on how to set up the failover function and identify the failover function's status. We strongly
How to setup Failover in Linux NVR Application Note Version 1.0 1 Preface This application note instructs you on how to set up the failover function and identify the failover function's status. We strongly
Lenovo NE1032 and NE1032T Switch
 Lenovo NE1032 and NE1032T Switch Quickstart Guide Document Version 1.0: 10/2018 Scale Computing 2018 1 Table of Contents Introduction 3 Requirements 3 Connect to the Switch 4 Over the Network 4 Console
Lenovo NE1032 and NE1032T Switch Quickstart Guide Document Version 1.0: 10/2018 Scale Computing 2018 1 Table of Contents Introduction 3 Requirements 3 Connect to the Switch 4 Over the Network 4 Console
User Inputs for Installation
 APPENDIXA This appendix provides information on the user inputs during LMS 4.1 installation. Note For information on the Installation of LMS 4.1, see Performing Installation of LMS 4.1. This appendix contains:
APPENDIXA This appendix provides information on the user inputs during LMS 4.1 installation. Note For information on the Installation of LMS 4.1, see Performing Installation of LMS 4.1. This appendix contains:
How Do I Recover infiniti Remotes and Line Cards?
 How Do I Recover infiniti Remotes and Line Cards? Date: June 26, 2008 Overview This FAQ contains the following information and procedures pertaining to ids Release 6.0.1 and later: Before Attempting to
How Do I Recover infiniti Remotes and Line Cards? Date: June 26, 2008 Overview This FAQ contains the following information and procedures pertaining to ids Release 6.0.1 and later: Before Attempting to
Using the SSM Administration Console
 CHAPTER 6 Your user role controls whether you can access the SSM Administration Console. The following information is included in this section: SSM Administration Console Overview, page 6-1 Launching the
CHAPTER 6 Your user role controls whether you can access the SSM Administration Console. The following information is included in this section: SSM Administration Console Overview, page 6-1 Launching the
Configuring Administrative Operations
 Configuring Administrative Operations This section includes the following topics: Administrative Operation Conventions, page 1 Configuring Backup Operations, page 1 Restoring a Backup Configuration, page
Configuring Administrative Operations This section includes the following topics: Administrative Operation Conventions, page 1 Configuring Backup Operations, page 1 Restoring a Backup Configuration, page
ssh keys, yum, ntp, rsync
 ssh keys, yum, ntp, rsync 1 CST8177 Linux Operating Systems II Saturday 25-April-15 9:00-11:00 T119/T126 2 ifconfig to find your VM's ip address so you can ssh to it ssh key login yum ntp tar scp rsync
ssh keys, yum, ntp, rsync 1 CST8177 Linux Operating Systems II Saturday 25-April-15 9:00-11:00 T119/T126 2 ifconfig to find your VM's ip address so you can ssh to it ssh key login yum ntp tar scp rsync
What you will need. 1 P a g e
 Windows 7 Professional/Ultimate Scan to Folder setup (Windows 7 Home is not supported) (Other versions of Windows may be different) (You may need to refer to your Windows documentation) What you will need
Windows 7 Professional/Ultimate Scan to Folder setup (Windows 7 Home is not supported) (Other versions of Windows may be different) (You may need to refer to your Windows documentation) What you will need
SmartCash SmartNode Setup Guide v1.2. Windows 10. Date: 13/01/2018. By (Jazz) yoyomonkey
 SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide V1.2 Windows 10 13/01/2018 By (Jazz) yoyomonkey Page 1
 SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
Unzip the provided Minix Virtual Machine. This will provide you with the files Minix3.1.8.vdi and Minix LCOM.vbox.
 Setting up Minix with Virtualbox Download and install the latest version of VirtualBox from here: https://www.virtualbox.org/wiki/downloads. Download the Minix Virtual Machine here: https://feupload.fe.up.pt/get/jrrtavgkcxf2hy4.
Setting up Minix with Virtualbox Download and install the latest version of VirtualBox from here: https://www.virtualbox.org/wiki/downloads. Download the Minix Virtual Machine here: https://feupload.fe.up.pt/get/jrrtavgkcxf2hy4.
Troubleshooting Cisco APIC-EM Multi-Host
 The following procedures may be used to troubleshoot a Cisco APIC-EM multi-host configuration: Changing the Settings in a Multi-Host Cluster, page 1 Removing a Single Host from a Multi-Host Cluster, page
The following procedures may be used to troubleshoot a Cisco APIC-EM multi-host configuration: Changing the Settings in a Multi-Host Cluster, page 1 Removing a Single Host from a Multi-Host Cluster, page
Windows 7 BYOD on MCSD WiFi
 Windows 7 BYOD on MCSD WiFi Revised 100114 - CWH These instructions will show how to connect a Windows 7 laptop to the District WiFi (MartinSchools). These instructions are to be used only with BYOD devices.
Windows 7 BYOD on MCSD WiFi Revised 100114 - CWH These instructions will show how to connect a Windows 7 laptop to the District WiFi (MartinSchools). These instructions are to be used only with BYOD devices.
Managing Virtual Machines
 CHAPTER 7 A virtual machine is a software computer (just like a physical computer), which runs an operating system and applications. Virtual machines run on the VMware vsphere Hypervisor TM. You can use
CHAPTER 7 A virtual machine is a software computer (just like a physical computer), which runs an operating system and applications. Virtual machines run on the VMware vsphere Hypervisor TM. You can use
Reimage Procedures. Firepower 2100 Series Software Reimage and Disaster Recovery
 Firepower 2100 Series Software Reimage and Disaster Recovery Procedures, page 1 Firepower 2100 Series Software Reimage and Disaster Recovery Procedures In some cases, you may want to reset your system
Firepower 2100 Series Software Reimage and Disaster Recovery Procedures, page 1 Firepower 2100 Series Software Reimage and Disaster Recovery Procedures In some cases, you may want to reset your system
Managing Virtual Machines
 CHAPTER 6 Last Updated: September 17, 2012 A virtual machine is a software computer (just like a physical computer) that runs an operating system and applications. Virtual machines run on the VMware vsphere
CHAPTER 6 Last Updated: September 17, 2012 A virtual machine is a software computer (just like a physical computer) that runs an operating system and applications. Virtual machines run on the VMware vsphere
snom.com snom ONE mini Quick Start Guide
 snom.com snom ONE mini Quick Start Guide Copyright All rights reserved. This document is supplied by snom technology. No part of this document may be reproduced, republished or retransmitted in any form
snom.com snom ONE mini Quick Start Guide Copyright All rights reserved. This document is supplied by snom technology. No part of this document may be reproduced, republished or retransmitted in any form
Click on Close button to close Network Connection Details. You are back to the Local Area Connection Status window.
 How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
Dell Storage Compellent Integration Tools for VMware
 Dell Storage Compellent Integration Tools for VMware Version 4.0 Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your
Dell Storage Compellent Integration Tools for VMware Version 4.0 Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your
WA2503 Hadoop Programming on the. Hortonworks Data Platform. Lab Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc.
 WA2503 Hadoop Programming on the Hortonworks Data Platform Lab Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2
WA2503 Hadoop Programming on the Hortonworks Data Platform Lab Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2
