5 Managing Logins. For Help. In this Chapter... Login Account Concepts, 5-2
|
|
|
- Edward Clarke
- 5 years ago
- Views:
Transcription
1 5 Managing Logins In this Chapter... Login Account Concepts, 5-2 The root Login Account, 5-3 Managing User Login Accounts, 5-5 Customizing Login Account Environments, 5-6 Passwords, 5-10 For Help HP-UX Reference HP-UX reference information is available on the Internet at: System Administrator Manager (SAM) To start SAM, enter: /usr/sbin/sam at a shell window prompt. For help inside of SAM, From the dialog, click Help. Press F1 for context-sensitive help on a specific field Reference 3070 User and Service manuals are located on 3070 system controllers and on factory-supplied updates. More Help See In Case of Difficulty on page Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-1
2 Login Account Concepts To access a system, a user must have a login account established by the system administrator consisting of a login name and password. A login account can be assigned to either an individual (such as mike) or a group (such as testdev1). For example, Mike could have his own login account mike that uniquely identifies him. If given the password, Mike could also access the system using the login account testdev1 if testdev1 was setup to identify a group of users rather than an individual. Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-2
3 The root Login Account This section contains: Introduction, 5-3 Login as root, 5-3 If the root Password is Lost or Forgotten, 5-3 The Switch User (su) Command, 5-4 If Users Need Administrator Privileges, 5-4 Introduction The root login account contains powerful privileges. Be careful consider the results of commands before entering them. Some operations only the root user can perform include: Setting the system s date and time. Mounting or unmounting file systems. Shutting down the system. Adding or removing users. Bypassing all system protection. Manipulating any file. Stopping any process. Login as root CAUTION Never login as root then leave the system unattended. Anyone could then access the system with full privileges and cause serious damage. A general security practice is to login as root only to perform system administration tasks, then logout when finished. Enter at a shell window prompt: a login (wait for the prompt) b root (enter the password when prompted) If the root Password is Lost or Forgotten Contact your Agilent support representative. For more information, see In Case of Difficulty on page Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-3
4 The Switch User (su) Command On a system being accessed with someone else s login, the root user can become a user in one of two ways. At a shell window prompt, enter either of the following: a su This retains the previous user's home directory. b su -root /home/root is established as the home directory. The HP-UX prompt will change to a # indicating a temporary login. When finished, logout to the prior login by entering: Administrative permissions for login account are color-coded in SAM as shown in Table 5-1. Table 5-1 Color-Code for Administrative Permissions in SAM SAM Color Definitions for Administrative Permissions Green = All Yellow = Some Red = None Now the user of the login account can perform allowed administrative tasks using SAM. For system security, remove temporary and limited accounts when they no longer have a use. exit If Users Need Administrator Privileges The root user can give any login account administrative capabilities using SAM: 1 Enter: sam -r 2 Select a subset of the total administrative permissions to give to a login account. All or part of the administrative permissions can be given to any login account. Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-4
5 Managing User Login Accounts This section contains: Introduction, 5-5 List of Login Accounts, 5-5 Add a Login Account, 5-5 Remove a Login Account, 5-5 Introduction The system is shipped configured with several predefined logins. It may be necessary to define additional logins. List of Login Accounts SAM allows access to the system s list of all accounts. To view the list: 1 Start SAM. 2 Click Accounts for Users and Groups > Users. Add a Login Account If it should become necessary to add a user login: 1 Login as root then start SAM. 2 Click Accounts for Users and Groups > Users 3 Select the appropriate template: Table 5-2 shows the four user groups from which to choose: Table 5-2 For example, if you click Actions > User Templates > Select > Operator, the new login account will be placed in the Operator group and the associated environment customization will be configured. 4 Add the new login account: Click Actions > Add Use a unique name and password for LoginName. Remove a Login Account Remove a user login when it is no longer valid. 1 Start SAM. The Four User Groups service operator user qsys 2 Select the user then click Actions > Remove. Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-5
6 Customizing Login Account Environments This section contains: Introduction, 5-6 To View Environment Files, 5-6 The Structure of Default Environment Files, 5-6 To Edit an Environment File, 5-6 Advanced Editing, 5-7 Introduction It is possible to configure login accounts to behave differently. For example, one account could be configured to automatically start BT-BASIC, and another to automatically open a shell window. We recommend that you keep customization to a minimum. If you decide to customize a user login environment, begin with simple changes such as customizing the colors of windows. Before making changes, create a copy of the unmodified file under a different name to easily recover from a mistake for example, copy.profile to.profile_old Use SAM to set environment customizations when adding a login account. To View Environment Files To view environment files, at a shell window prompt enter: ll -a The Structure of Default Environment Files When a login account is added, default environment files are copied to the login account home directory /home/<login_name>. These default environment files all begin with a period for example,.profile Sample user login directory structure files are shown in Figure 5-1 on page 5-8 and listed in Table 5-3 on page 5-8. The structure is based on master files that reside in the /opt/hp3070/lib directory. The master files have the form sys.<filename> For example, the master file for.hp3070 is sys.hp3070 To Edit an Environment File For example, use vi to edit.profile At a shell window prompt enter: vi.profile Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-6
7 Advanced Editing There is a group of.xdefaults text files that determine the behavior of applications that use X-Windows. The behaviors include how window colors display. There are several of these files, which have names like.xdefs-512 or.xdefs-1280, each of which is for a specific video display. The number in the file name matches the resolution of the display for which the file is intended. The files are located in /var/hp3070/lib/xdefs, and can be viewed (using more) to determine their use. You probably will not need to edit these files because the CDE provides many tools that allows interactive modification of the appearance of a user s X-Windows environment. Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-7
8 Figure 5-1 User Login Directory Structure / home other users john other users.profile.dtprofile.xsession.hp3070.x11start.usertype.exrc.dt.vdtwmrc directories Table 5-3 Login Files.hp3070.profile User login files Description Defines global values for the 3070 system environment and is one of the most important environment files not a part of standard HP-UX. The.hp3070 file is described in more detail in The.hp3070 File on page Defines the environment associated with an individual login, including search paths to alternate directories, the terminal type, and whether to start windows. This file is read each time the associated user logs in. Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-8
9 Table 5-3 User login files (continued) Login Files.dtprofile.xsession.dt.usertype.x11start.exrc Description Defines the environment associated with an individual login using a CDE environment. In the CDE environment, reading the.profile file is controlled by the.dtprofile file. An X-Windows startup script used by the test system if you are not running the Agilent CDE environment. X-Windows is the software package that lets you work in multiple windows. A directory that contains the file dtwmrc and directories sessions and types. The file dtwmrc defines the environment associated with each user s login when using the CDE environment, which runs by default. The directories are set up and used by CDE. Contains a string that identifies what type of user account this is; for example, operator or service. Specifies the default actions for the X-Windows environment if you are not running the CDE environment, including which programs are automatically run at login and whether those programs appear as windows or as icons. (Optional) Defines terminal characteristics and key definitions for use by the vi and ex editors. This file is a renamed local copy (which can be customized to control how vi works) of the file /etc/d.exrc Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-9
10 Passwords This section contains: Introduction, 5-10 Change the Password, 5-10 Re-establish a Login Account Password, 5-10 Setup Passwords on Logins without Passwords, 5-10 Introduction To maintain system integrity, passwords should be created with: At least 6 characters. One or more non-alphabetic characters. Passwords should not be a family name or birthday, or other word associated with the user. Change the Password Users should change their password regularly. Any login account user can change their own password by entering at a shell window prompt: passwd Re-establish a Login Account Password This process is useful in case a user forgets his or her password. The root user can re-establish any login account password: 1 Log in as root 2 Enter: passwd followed by the name of the login whose password is to be re-established. For example, enter: passwd sarah 3 Enter a new password. Verify the entry. 4 Inform the user of the password. Any login account user can change their own password by entering at a shell window prompt: passwd Setup Passwords on Logins without Passwords To add a password to a login when no password previously existed: 1 Login as root 2 Start SAM 3 Click Accounts for Users and Groups > Users Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-10
11 4 Click the account for which you want to add password protection. 5 Click Actions > Modify > Change Password 6 Enter a password (then re-enter it for validation) then click OK. Agilent Technologies Administering Agilent 3070 UNIX Systems (UNIX 10.X) 5-11
8 Managing Quality Reporting Software
 8 Managing Quality Reporting Software In this Chapter... Datalogging, 8-2 Agilent PR PLUS, 8-5 Agilent Pushbutton Q-STATS, 8-9 For Help HP-UX Reference HP-UX reference information is available on the Internet
8 Managing Quality Reporting Software In this Chapter... Datalogging, 8-2 Agilent PR PLUS, 8-5 Agilent Pushbutton Q-STATS, 8-9 For Help HP-UX Reference HP-UX reference information is available on the Internet
View Security and Access Privileges
 View Security and Access Privileges Individual access privileges to graphical objects in a View application can be implemented by adding users to the View target and assigning each user an appropriate
View Security and Access Privileges Individual access privileges to graphical objects in a View application can be implemented by adding users to the View target and assigning each user an appropriate
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003
 Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
System Administration
 CHAPTER 8 System Administration As your network inventory and user base grow, you need to perform certain system administration tasks to accommodate that growth. This chapter describes some of the features
CHAPTER 8 System Administration As your network inventory and user base grow, you need to perform certain system administration tasks to accommodate that growth. This chapter describes some of the features
Command-Line Interface (CLI) Basics
 4 CHAPTER This chapter is intended as a quick reference, not as a step-by-step explanation of the Cisco IOS. The chapter describes basic Cisco IOS software command-line interfaces that you may need to
4 CHAPTER This chapter is intended as a quick reference, not as a step-by-step explanation of the Cisco IOS. The chapter describes basic Cisco IOS software command-line interfaces that you may need to
Nortel Quality Monitoring Search and Replay Guide
 Nortel Quality Monitoring Search and Replay Guide NN44480-106 Product release 7.0 Standard 02.02 November 2009 Nortel Quality Monitoring Search and Replay Guide Publication number: NN44480-106 Product
Nortel Quality Monitoring Search and Replay Guide NN44480-106 Product release 7.0 Standard 02.02 November 2009 Nortel Quality Monitoring Search and Replay Guide Publication number: NN44480-106 Product
Using Templates. 5.4 Using Templates
 5.4 Using Templates Templates are used to create master files for control panel programming data to speed up programming of a new account. A template gives you a very quick and easy way to add a customer
5.4 Using Templates Templates are used to create master files for control panel programming data to speed up programming of a new account. A template gives you a very quick and easy way to add a customer
Virtual CD TS 1 Introduction... 3
 Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
HP-UX System Administration Course Overview. Skills Gained. Who will the Course Benefit?
 HP-UX System Administration Course Overview This Hewlett Packard HP-UX System Administration training course is designed to give delegates practical experience in the administration of an HP-UX UNIX System.
HP-UX System Administration Course Overview This Hewlett Packard HP-UX System Administration training course is designed to give delegates practical experience in the administration of an HP-UX UNIX System.
EMS Installation. Workstation Requirements CHAPTER. EMS Lite (Windows 95/98) EMS NT (Windows NT 4.0)
 CHAPTER 2 EMS Installation This chapter provides instructions for installing the Element Management System (EMS) software on a user workstation. Workstation Requirements The following sections list the
CHAPTER 2 EMS Installation This chapter provides instructions for installing the Element Management System (EMS) software on a user workstation. Workstation Requirements The following sections list the
Contents. Why You Should Read This Manual...ix. 1. Introduction... 1
 Contents Why You Should Read This Manual...ix 1. Introduction... 1 Understanding Security... 2 Group and User Accounts... 2 Application Features... 3 Security Areas... 3 Using Windows Security... 7 Synchronizing
Contents Why You Should Read This Manual...ix 1. Introduction... 1 Understanding Security... 2 Group and User Accounts... 2 Application Features... 3 Security Areas... 3 Using Windows Security... 7 Synchronizing
Start Up and Shutdown Procedures (Unix)
 Start Up and Shutdown Procedures (Unix) Start Up On Main Console 1. Press the Server main power button ON 2. The system will automatically go through the start-up procedures, which will be displayed on
Start Up and Shutdown Procedures (Unix) Start Up On Main Console 1. Press the Server main power button ON 2. The system will automatically go through the start-up procedures, which will be displayed on
Starting ParTEST. Select Start, Programs ParTEST ParTEST Enter your User Name and password
 Starting ParTEST User Login Select Start, Programs ParTEST ParTEST Enter your User Name and password If you still logged into ParTEST as the Administrator Select File, Logout. Enter your User name and
Starting ParTEST User Login Select Start, Programs ParTEST ParTEST Enter your User Name and password If you still logged into ParTEST as the Administrator Select File, Logout. Enter your User name and
e-submission System User Manual Publication Related Matters
 e-submission System User Manual For Publication Related Matters March 2018 Version 2.2 Table of Contents 1.5 SUBMISSION MANAGEMENT... 19 1.5.1 Edit Saved Submission For Publication... 19 1.5.2 Approve
e-submission System User Manual For Publication Related Matters March 2018 Version 2.2 Table of Contents 1.5 SUBMISSION MANAGEMENT... 19 1.5.1 Edit Saved Submission For Publication... 19 1.5.2 Approve
HP-UX System Administration
 HP-UX System Administration This intensive course is designed for experienced UNIX administrators who like to understand the differences between HP-UX and standard UNIX. It is essential that students have
HP-UX System Administration This intensive course is designed for experienced UNIX administrators who like to understand the differences between HP-UX and standard UNIX. It is essential that students have
LiveNX Upgrade Guide from v5.2.0 to v5.2.1
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.2.0 to v5.2.1 UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the LiveAction
LIVEACTION, INC. LiveNX Upgrade Guide from v5.2.0 to v5.2.1 UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the LiveAction
Cmpt 101 Lab 1 - Outline
 Cmpt 101 Lab 1 - Outline Instructions: Work through this outline completely once directed to by your Lab Instructor and fill in the Lab 1 Worksheet as indicated. Contents PART 1: GETTING STARTED... 2 PART
Cmpt 101 Lab 1 - Outline Instructions: Work through this outline completely once directed to by your Lab Instructor and fill in the Lab 1 Worksheet as indicated. Contents PART 1: GETTING STARTED... 2 PART
Administering Agilent 3070 Systems MS Windows NT and January 2004
 Administering Agilent 3070 Systems MS Windows NT and 2000 January 2004 Contents Administering Agilent 3070 Systems (MS Windows NT and 2000) 1 Introduction About This Manual... 1-1 Who Should Use This Manual...
Administering Agilent 3070 Systems MS Windows NT and 2000 January 2004 Contents Administering Agilent 3070 Systems (MS Windows NT and 2000) 1 Introduction About This Manual... 1-1 Who Should Use This Manual...
Save Current Customization... 1
 Quick Reference Guide Saving & Applying Filters in Data Warehouse You can save your customizations/filters for your own personal use with the Save Current Customization feature. The Create Bookmark Link
Quick Reference Guide Saving & Applying Filters in Data Warehouse You can save your customizations/filters for your own personal use with the Save Current Customization feature. The Create Bookmark Link
5 MANAGING USER ACCOUNTS AND GROUPS
 MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
Performing Maintenance Operations
 This chapter describes how to back up and restore Cisco Mobility Services Engine (MSE) data and how to update the MSE software. It also describes other maintenance operations. Guidelines and Limitations,
This chapter describes how to back up and restore Cisco Mobility Services Engine (MSE) data and how to update the MSE software. It also describes other maintenance operations. Guidelines and Limitations,
How to make a Work Profile for Windows 10
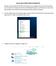 How to make a Work Profile for Windows 10 Setting up a new profile for Windows 10 requires you to navigate some screens that may lead you to create the wrong type of account. By following this guide, we
How to make a Work Profile for Windows 10 Setting up a new profile for Windows 10 requires you to navigate some screens that may lead you to create the wrong type of account. By following this guide, we
ModeChanger
 35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
Managing NCS User Accounts
 7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
Welcome To Account Manager 2.0
 Account Manager 2.0 Manage Unlimited FileMaker Servers, Databases, Privileges, and Users Effortlessly! The ultimate tool for FileMaker Database Administrators. Welcome To Account Manager 2.0 What Is Account
Account Manager 2.0 Manage Unlimited FileMaker Servers, Databases, Privileges, and Users Effortlessly! The ultimate tool for FileMaker Database Administrators. Welcome To Account Manager 2.0 What Is Account
Troubleshooting. Troubleshooting the CAM Installation CHAPTER
 CHAPTER 9 Troubleshooting This chapter presents some scripts and procedures that might prove useful in troubleshooting and maintaining your Cisco Access Manager (CAM) software. The following topics are
CHAPTER 9 Troubleshooting This chapter presents some scripts and procedures that might prove useful in troubleshooting and maintaining your Cisco Access Manager (CAM) software. The following topics are
Dreamweaver is a full-featured Web application
 Create a Dreamweaver Site Dreamweaver is a full-featured Web application development tool. Dreamweaver s features not only assist you with creating and editing Web pages, but also with managing and maintaining
Create a Dreamweaver Site Dreamweaver is a full-featured Web application development tool. Dreamweaver s features not only assist you with creating and editing Web pages, but also with managing and maintaining
Jackson State University Department of Computer Science CSC / Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
TotalView. Installation Guide. November 2004 version 6.6
 TotalView Installation Guide November 2004 version 6.6 Copyright 1998 2004 by Etnus LLC. All rights reserved. Copyright 1996 1998 by Dolphin Interconnect Solutions, Inc. Copyright 1993 1996 by BBN Systems
TotalView Installation Guide November 2004 version 6.6 Copyright 1998 2004 by Etnus LLC. All rights reserved. Copyright 1996 1998 by Dolphin Interconnect Solutions, Inc. Copyright 1993 1996 by BBN Systems
Optional Labs. 0Handouts: 2002 ProsoftTraining All Rights Reserved. Version 3.07
 0Handouts: Optional Lab 1-1: Understanding the /etc/securetty file In this lab, you will examine a PAM component, the /etc/securetty file. 1. Boot into Linux as root. Open a Telnet client and attempt to
0Handouts: Optional Lab 1-1: Understanding the /etc/securetty file In this lab, you will examine a PAM component, the /etc/securetty file. 1. Boot into Linux as root. Open a Telnet client and attempt to
Visara Master Console Center. Software Installation P/N
 Visara Master Console Center Software Installation P/N 707133-001 Visara Master Console Center Technical Support Contacting the Visara Intellicenter For US domestic customers, Visara provides technical
Visara Master Console Center Software Installation P/N 707133-001 Visara Master Console Center Technical Support Contacting the Visara Intellicenter For US domestic customers, Visara provides technical
Getting Started with Cisco WebEx Meeting Applications
 CHAPTER 6 Getting Started with Cisco WebEx Meeting Applications Revised: September, 2010, Contents Modifying Your Provisioned Cisco WebEx Account, page 6-1 Setting Proxy Permissions, page 6-5 Productivity
CHAPTER 6 Getting Started with Cisco WebEx Meeting Applications Revised: September, 2010, Contents Modifying Your Provisioned Cisco WebEx Account, page 6-1 Setting Proxy Permissions, page 6-5 Productivity
UNIX Essentials Featuring Solaris 10 Op System
 A Active Window... 7:11 Application Development Tools... 7:7 Application Manager... 7:4 Architectures - Supported - UNIX... 1:13 Arithmetic Expansion... 9:10 B Background Processing... 3:14 Background
A Active Window... 7:11 Application Development Tools... 7:7 Application Manager... 7:4 Architectures - Supported - UNIX... 1:13 Arithmetic Expansion... 9:10 B Background Processing... 3:14 Background
LABVIEW. Contents RELEASE NOTES. Version 6.1
 RELEASE NOTES LABVIEW Version 6.1 These release notes introduce you to LabVIEW, describe the system requirements for the LabVIEW software, and contain installation instructions. The LabVIEW 6.1 Professional
RELEASE NOTES LABVIEW Version 6.1 These release notes introduce you to LabVIEW, describe the system requirements for the LabVIEW software, and contain installation instructions. The LabVIEW 6.1 Professional
Perceptive XML Integration for Epic
 Perceptive XML Integration for Epic Installation and Setup Guide Version: 2.0.x Written by: Product Knowledge, R&D Date: May 2018 2008-2018 Hyland Software, Inc. and its affiliates. Table of Contents About
Perceptive XML Integration for Epic Installation and Setup Guide Version: 2.0.x Written by: Product Knowledge, R&D Date: May 2018 2008-2018 Hyland Software, Inc. and its affiliates. Table of Contents About
USER MANUAL. LG Simple Editor.
 USER MANUAL LG Simple Editor http://partner.lge.com 2 CONTENTS LG SIMPLE EDITOR...3 --System Requirements...3 --Install and Delete LG Simple Editor...4 Installation Deletion --Running LG Simple Editor...7
USER MANUAL LG Simple Editor http://partner.lge.com 2 CONTENTS LG SIMPLE EDITOR...3 --System Requirements...3 --Install and Delete LG Simple Editor...4 Installation Deletion --Running LG Simple Editor...7
MDS - UNIX SYSTEM ADMINISTRATOR MANUAL. INTRODUCTION... i
 MDS - UNIX SYSTEM ADMINISTRATOR MANUAL INTRODUCTION........................... i SUPER USER MENU.......................... 1 1 SET USER PRIVILEGE..................... 2 2 MAKE USER.........................
MDS - UNIX SYSTEM ADMINISTRATOR MANUAL INTRODUCTION........................... i SUPER USER MENU.......................... 1 1 SET USER PRIVILEGE..................... 2 2 MAKE USER.........................
Lab Router Configuration Using Setup Instructor Version 2500
 Lab 2.2.1 Router Configuration Using Setup Instructor Version 2500 Objective Use the System Configuration dialog (setup). Establish some basic router configurations. Background/Preparation A new router
Lab 2.2.1 Router Configuration Using Setup Instructor Version 2500 Objective Use the System Configuration dialog (setup). Establish some basic router configurations. Background/Preparation A new router
eftp Application User Guide
 Team A eftp User Guide 1/30 eftp Application User Guide Table of Contents Page 1. Acknowledgement 2 2. Introduction a. Welcome eftp Audience 3 b. What s in this manual 3 c. Manual Conventions 3 d. Getting
Team A eftp User Guide 1/30 eftp Application User Guide Table of Contents Page 1. Acknowledgement 2 2. Introduction a. Welcome eftp Audience 3 b. What s in this manual 3 c. Manual Conventions 3 d. Getting
OOOCTA Version 4.1. Installation and Users Guide.
 OOOCTA Version 4.1 Installation and Users Guide www.telnetport25.com Contents Introduction... 2 Pre-Requisites... 2 Changes from Version 3.5... 2 Changes from Version 4.0... 2 Installation and Setup...
OOOCTA Version 4.1 Installation and Users Guide www.telnetport25.com Contents Introduction... 2 Pre-Requisites... 2 Changes from Version 3.5... 2 Changes from Version 4.0... 2 Installation and Setup...
There are two tools with which you should be familiar: the program su, and more importantly, sudo. Here we see how to use them.
 Operating Systems and Systems Integration Administration, the root User and Configuring sudo 1 Aim The aim of this activity is to understand the purpose of the root account, and the security risks of logging
Operating Systems and Systems Integration Administration, the root User and Configuring sudo 1 Aim The aim of this activity is to understand the purpose of the root account, and the security risks of logging
Maintaining the System Software
 CHAPTER 2 This chapter covers the tasks required for maintaining a Content Engine. Upgrading the System Software, page 2-1 Recovering the System Software, page 2-2 Maintaining the Hard Disk Storage, page
CHAPTER 2 This chapter covers the tasks required for maintaining a Content Engine. Upgrading the System Software, page 2-1 Recovering the System Software, page 2-2 Maintaining the Hard Disk Storage, page
Lab E2: bypassing authentication and resetting passwords
 Lab E2: bypassing authentication and resetting passwords TTM4175 September 7, 2015 The purpose of this lab is to learn about techniques for bypassing the authentication and access control of Windows and
Lab E2: bypassing authentication and resetting passwords TTM4175 September 7, 2015 The purpose of this lab is to learn about techniques for bypassing the authentication and access control of Windows and
Windows 2000 / XP / Vista User Guide
 Windows 2000 / XP / Vista User Guide Version 5.5.1.0 September 2008 Backup Island v5.5 Copyright Notice The use and copying of this product is subject to a license agreement. Any other use is prohibited.
Windows 2000 / XP / Vista User Guide Version 5.5.1.0 September 2008 Backup Island v5.5 Copyright Notice The use and copying of this product is subject to a license agreement. Any other use is prohibited.
Greco Systems. License Manager. Operation Manual OM A division of e-dnc Inc. 303 E Gurley St. #522 Prescott, AZ USA
 G r e c o S y s t e m s License Manager Operation Manual OM-3039 Greco Systems A division of e-dnc Inc. 303 E Gurley St. #522 Prescott, AZ 86301 USA 800-234-7326 SAFETY Protect yourself! Follow these precautions:
G r e c o S y s t e m s License Manager Operation Manual OM-3039 Greco Systems A division of e-dnc Inc. 303 E Gurley St. #522 Prescott, AZ 86301 USA 800-234-7326 SAFETY Protect yourself! Follow these precautions:
NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1
 NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1 Objective At the conclusion of this lab, the student will be able to add and delete users, create and assign users to groups, and assign users
NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1 Objective At the conclusion of this lab, the student will be able to add and delete users, create and assign users to groups, and assign users
Lab Authentication, Authorization, and Accounting
 Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
DTVaultLock User s Manual
 DTVaultLock User s Manual DTVaultLock is a DataTraveler Vault tool that enables you to create and access a user defined password-protected area called a Privacy Zone, on your DataTraveler Vault drive.
DTVaultLock User s Manual DTVaultLock is a DataTraveler Vault tool that enables you to create and access a user defined password-protected area called a Privacy Zone, on your DataTraveler Vault drive.
DOCUMENT SECURITY IN WORD 2010
 DOCUMENT SECURITY IN WORD 2010 http://www.tutorialspoint.com/word/word_document_security.htm Copyright tutorialspoint.com Microsoft Word provides a high level of security for your word generated documents.
DOCUMENT SECURITY IN WORD 2010 http://www.tutorialspoint.com/word/word_document_security.htm Copyright tutorialspoint.com Microsoft Word provides a high level of security for your word generated documents.
Using the VMware vcenter Orchestrator Client. vrealize Orchestrator 5.5.1
 Using the VMware vcenter Orchestrator Client vrealize Orchestrator 5.5.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Using the VMware vcenter Orchestrator Client vrealize Orchestrator 5.5.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
How to Configure Impersonation for OneDrive for Business Data Sources
 How to Configure Impersonation for OneDrive for Business Data Sources Before Getting Started Download and install the SharePoint Online Management Shell from the Microsoft Windows Download Center to a
How to Configure Impersonation for OneDrive for Business Data Sources Before Getting Started Download and install the SharePoint Online Management Shell from the Microsoft Windows Download Center to a
WinSCP. Author A.Kishore/Sachin
 WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
Aretics T7 Installation Manual
 Aretics T7 Installation Manual 1(24) Aretics T7 Installation Manual This document describes how to manage Aretics T7 in your IT environment. Here you will find information about installing the system,
Aretics T7 Installation Manual 1(24) Aretics T7 Installation Manual This document describes how to manage Aretics T7 in your IT environment. Here you will find information about installing the system,
WORKFLOW TRAINING. Reviewing an Agenda Item Through Laserfiche Client. Updated May 2017
 WORKFLOW TRAINING Reviewing an Agenda Item Through Laserfiche Client Updated May 2017 CONTENTS Reviewing an Agenda Item... 3 Updating Template with Word Document Open & Saving Document with Track Changes...
WORKFLOW TRAINING Reviewing an Agenda Item Through Laserfiche Client Updated May 2017 CONTENTS Reviewing an Agenda Item... 3 Updating Template with Word Document Open & Saving Document with Track Changes...
Lesson 3: Identifying Key Characteristics of Workgroups and Domains
 1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
Using the SSM Administration Console
 CHAPTER 6 Your user role controls whether you can access the SSM Administration Console. The following information is included in this section: SSM Administration Console Overview, page 6-1 Launching the
CHAPTER 6 Your user role controls whether you can access the SSM Administration Console. The following information is included in this section: SSM Administration Console Overview, page 6-1 Launching the
Setup Smart Login for Windows V2
 Setup Smart Login for Windows V2 Smart Login allows workstations to login to a Smart-Net server without having to join a domain. Smart Login is suitable for both laptops and desktop PC s. Features Users
Setup Smart Login for Windows V2 Smart Login allows workstations to login to a Smart-Net server without having to join a domain. Smart Login is suitable for both laptops and desktop PC s. Features Users
Managing WCS User Accounts
 7 CHAPTER This chapter describes how to configure global email parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Viewing or Editing User Information,
7 CHAPTER This chapter describes how to configure global email parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Viewing or Editing User Information,
Remote Support 19.1 Web Rep Console
 Remote Support 19.1 Web Rep Console 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the property
Remote Support 19.1 Web Rep Console 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the property
The tool can also be accessed by clicking the Self Service Password Manager icon on your desktop, or by visiting:
 Self Service Password Manager Last revised: April 2017 Last reviewed: April 2017 Information Technology Division Next review: September 2018 This guide should be used to learn how to set-up a Self Service
Self Service Password Manager Last revised: April 2017 Last reviewed: April 2017 Information Technology Division Next review: September 2018 This guide should be used to learn how to set-up a Self Service
StormTracker EMS 2.3 Installation Instructions. Contents. Document Number EMS-A2-GN10-00 July 2002
 StormTracker EMS 2.3 Installation Instructions Document Number EMS-A2-GN10-00 July 2002 Contents Overview... 2 Basic StormTracker EMS Functionality... 2 Oware and StormTracker EMS... 2 Supported Systems...
StormTracker EMS 2.3 Installation Instructions Document Number EMS-A2-GN10-00 July 2002 Contents Overview... 2 Basic StormTracker EMS Functionality... 2 Oware and StormTracker EMS... 2 Supported Systems...
SuiteFactory on the Web
 SuiteFactory on the Web This document is meant to be a guide to be used, (at least the first time), along with a CCI employee to get you started and to point out important facts and features. Prerequisites
SuiteFactory on the Web This document is meant to be a guide to be used, (at least the first time), along with a CCI employee to get you started and to point out important facts and features. Prerequisites
File Menu Commands. Save Running Config to PC. Deliver Configuration to Router CHAPTER40. Save Running Config to Router s Startup Config
 CHAPTER40 The following options are available from the Cisco Router and Security Device Manager (Cisco SDM) File menu. Save Running Config to PC Saves the router s running configuration file to a text
CHAPTER40 The following options are available from the Cisco Router and Security Device Manager (Cisco SDM) File menu. Save Running Config to PC Saves the router s running configuration file to a text
bs^ir^qfkd=obcib`qflk= prfqb=clo=u
 bs^ir^qfkd=obcib`qflk= prfqb=clo=u cçê=u=táåççïë=póëíéãë cçê=lééåsjp=eçëíë cçê=f_j=eçëíë 14.1 bî~äì~íáåö=oéñäéåíáçå=u This guide provides a quick overview of features in Reflection X. This evaluation guide
bs^ir^qfkd=obcib`qflk= prfqb=clo=u cçê=u=táåççïë=póëíéãë cçê=lééåsjp=eçëíë cçê=f_j=eçëíë 14.1 bî~äì~íáåö=oéñäéåíáçå=u This guide provides a quick overview of features in Reflection X. This evaluation guide
Dreamweaver is a full-featured Web application
 Create a Dreamweaver Site Dreamweaver is a full-featured Web application development tool. Dreamweaver s features not only assist you with creating and editing Web pages, but also with managing and maintaining
Create a Dreamweaver Site Dreamweaver is a full-featured Web application development tool. Dreamweaver s features not only assist you with creating and editing Web pages, but also with managing and maintaining
TIBCO BusinessConnect EBICS Protocol Installation and Configuration. Software Release 1.0 December 2011
 TIBCO BusinessConnect EBICS Protocol Installation and Configuration Software Release 1.0 December 2011 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED
TIBCO BusinessConnect EBICS Protocol Installation and Configuration Software Release 1.0 December 2011 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED
Using Integration Utility
 CHAPTER 3 CiscoWorks Integration Utility downloads Network Management Integration Data Bundle (NMIDB) and integrates LAN Management Solutions (LMS) applications, icons, MIBs, and traps with third-party
CHAPTER 3 CiscoWorks Integration Utility downloads Network Management Integration Data Bundle (NMIDB) and integrates LAN Management Solutions (LMS) applications, icons, MIBs, and traps with third-party
Linux Essentials. Smith, Roderick W. Table of Contents ISBN-13: Introduction xvii. Chapter 1 Selecting an Operating System 1
 Linux Essentials Smith, Roderick W. ISBN-13: 9781118106792 Table of Contents Introduction xvii Chapter 1 Selecting an Operating System 1 What Is an OS? 1 What Is a Kernel? 1 What Else Identifies an OS?
Linux Essentials Smith, Roderick W. ISBN-13: 9781118106792 Table of Contents Introduction xvii Chapter 1 Selecting an Operating System 1 What Is an OS? 1 What Is a Kernel? 1 What Else Identifies an OS?
SoftPro 360 User Guide
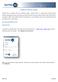 SoftPro 360 User Guide SoftPro 360 is included with your ProForm license. SoftPro 360 is a revolutionary product which enables requesting services and receiving orders from third party providers directly
SoftPro 360 User Guide SoftPro 360 is included with your ProForm license. SoftPro 360 is a revolutionary product which enables requesting services and receiving orders from third party providers directly
Introduction to the UNIX command line
 Introduction to the UNIX command line Steven Abreu Introduction to Computer Science (ICS) Tutorial Jacobs University s.abreu@jacobs-university.de September 19, 2017 Overview What is UNIX? UNIX Shell Commands
Introduction to the UNIX command line Steven Abreu Introduction to Computer Science (ICS) Tutorial Jacobs University s.abreu@jacobs-university.de September 19, 2017 Overview What is UNIX? UNIX Shell Commands
Remote Support Web Rep Console
 Remote Support Web Rep Console 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Remote Support Web Rep Console 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Minimum System Requirements The following are the minimum system requirements needed to run and install Premium Pro Enterprise:
 Overview Premium Pro Enterprise is the next generation of the Premium Pro family of applications. It is a Javabased application that houses multiple products and tax years in a single interface. It requires
Overview Premium Pro Enterprise is the next generation of the Premium Pro family of applications. It is a Javabased application that houses multiple products and tax years in a single interface. It requires
About This Book. Who Should Use This Book. Highlighting. Case Sensitivity in AIX. iii
 About This Book The AIX 5L Version 5.2 Operating System Installation: Getting Started guide provides system administrators with information about how to install and configure the AIX operating system on
About This Book The AIX 5L Version 5.2 Operating System Installation: Getting Started guide provides system administrators with information about how to install and configure the AIX operating system on
User Guide. Version 8.0
 User Guide Version 8.0 Contents 1 Getting Started... iii 1.1... About... iii 2 Logging In... 4 2.1... Choosing Security Questions... 4 3 The File Manager... 5 3.1... Uploading a file... 6 3.2... Downloading
User Guide Version 8.0 Contents 1 Getting Started... iii 1.1... About... iii 2 Logging In... 4 2.1... Choosing Security Questions... 4 3 The File Manager... 5 3.1... Uploading a file... 6 3.2... Downloading
Creating a distribution group
 Creating a distribution group You can group a number of selected contacts together, for example all of your team. This is known as a distribution group or list. Using a distribution group, you can email
Creating a distribution group You can group a number of selected contacts together, for example all of your team. This is known as a distribution group or list. Using a distribution group, you can email
PictureTel. Utilizing PictureTel 330 NetConference SNMP Support with HP OpenView for UNIX
 PictureTel Utilizing PictureTel 330 NetConference SNMP Support with HP OpenView for UNIX 1.0 Introduction Page 2 This document describes the NetConference SNMP functionality, how to integrate the NetConference
PictureTel Utilizing PictureTel 330 NetConference SNMP Support with HP OpenView for UNIX 1.0 Introduction Page 2 This document describes the NetConference SNMP functionality, how to integrate the NetConference
Computer Basics. Logging onto Windows
 Computer Basics DRN uses Windows PCs for all of its day-to-day operations. You will need to master the details of this section in order to perform your daily tasks. Fortunately, these basics are very simple
Computer Basics DRN uses Windows PCs for all of its day-to-day operations. You will need to master the details of this section in order to perform your daily tasks. Fortunately, these basics are very simple
Xton Access Manager GETTING STARTED GUIDE
 Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
Xton Access Manager GETTING STARTED GUIDE XTON TECHNOLOGIES, LLC PHILADELPHIA Copyright 2017. Xton Technologies LLC. Contents Introduction... 2 Technical Support... 2 What is Xton Access Manager?... 3
ALLIEDVIEW-UM 1.6 USER'S GUIDE
 ALLIEDVIEW-UM 1.6 USER'S GUIDE PN 613-000381 Rev B Page 1 of 129 Copyright 2002-2007 Allied Telesis K. K. All rights reserved. No part of this publication may be reproduced without prior written permission
ALLIEDVIEW-UM 1.6 USER'S GUIDE PN 613-000381 Rev B Page 1 of 129 Copyright 2002-2007 Allied Telesis K. K. All rights reserved. No part of this publication may be reproduced without prior written permission
EA/Studio Installation Guide
 EA/Studio 1.5.2 Installation Guide Copyright 1994-2008 Embarcadero Technologies, Inc. Embarcadero Technologies, Inc. 100 California Street, 12th Floor San Francisco, CA 94111 U.S.A. All rights reserved.
EA/Studio 1.5.2 Installation Guide Copyright 1994-2008 Embarcadero Technologies, Inc. Embarcadero Technologies, Inc. 100 California Street, 12th Floor San Francisco, CA 94111 U.S.A. All rights reserved.
USER S MANUAL. - Security Server. Security Server. Security Server. smar. First in Fieldbus MAY / 06 VERSION 8 FOUNDATION
 - Security Server Security Server USER S MANUAL smar First in Fieldbus MAY / 06 Security Server VERSION 8 TM FOUNDATION P V I E W S S V M E www.smar.com Specifications and information are subject to change
- Security Server Security Server USER S MANUAL smar First in Fieldbus MAY / 06 Security Server VERSION 8 TM FOUNDATION P V I E W S S V M E www.smar.com Specifications and information are subject to change
1Z Oracle Linux Fundamentals (Oracle Partner Network) Exam Summary Syllabus Questions
 1Z0-409 Oracle Linux Fundamentals (Oracle Partner Network) Exam Summary Syllabus Questions Table of Contents Introduction to 1Z0-409 Exam on Oracle Linux Fundamentals (Oracle Partner Network)... 2 Oracle
1Z0-409 Oracle Linux Fundamentals (Oracle Partner Network) Exam Summary Syllabus Questions Table of Contents Introduction to 1Z0-409 Exam on Oracle Linux Fundamentals (Oracle Partner Network)... 2 Oracle
Once a USB drive has been inserted into an encrypted machine, the Dell Data Protection software will recognize the unencrypted device.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Rev 7/10. Online Community. USER Help Guide
 Rev 7/10 Online Community USER Help Guide Contents Welcome 2 Logging In 3 Finding Your Church Organization 3 User Name/Password Reminders 4 Changing User Name/Password 5 My Profile 6 Viewing Your Profile
Rev 7/10 Online Community USER Help Guide Contents Welcome 2 Logging In 3 Finding Your Church Organization 3 User Name/Password Reminders 4 Changing User Name/Password 5 My Profile 6 Viewing Your Profile
Lab 1: Accessing the Linux Operating System Spring 2009
 CIS 90 Linux Lab Exercise Lab 1: Accessing the Linux Operating System Spring 2009 Lab 1: Accessing the Linux Operating System This lab takes a look at UNIX through an online experience on an Ubuntu Linux
CIS 90 Linux Lab Exercise Lab 1: Accessing the Linux Operating System Spring 2009 Lab 1: Accessing the Linux Operating System This lab takes a look at UNIX through an online experience on an Ubuntu Linux
UNIX / LINUX - GETTING STARTED
 UNIX / LINUX - GETTING STARTED http://www.tutorialspoint.com/unix/unix-getting-started.htm Copyright tutorialspoint.com Advertisements What is Unix? The Unix operating system is a set of programs that
UNIX / LINUX - GETTING STARTED http://www.tutorialspoint.com/unix/unix-getting-started.htm Copyright tutorialspoint.com Advertisements What is Unix? The Unix operating system is a set of programs that
Laserfiche Rio 10.3: Deployment Guide. White Paper
 Laserfiche Rio 10.3: Deployment Guide White Paper January 2018 Table of Contents How Laserfiche Licensing Works... 4 Types of Licenses... 4 Named User Licenses... 4 WebLink Public Portal Licenses... 6
Laserfiche Rio 10.3: Deployment Guide White Paper January 2018 Table of Contents How Laserfiche Licensing Works... 4 Types of Licenses... 4 Named User Licenses... 4 WebLink Public Portal Licenses... 6
User Guide. DMS-100 Family SuperNode Data Manager Enhanced Terminal Access. SDMCom012 and up Standard 06.
 297-5051-904 DMS-100 Family SuperNode Data Manager Enhanced Terminal Access User Guide SDMCom012 and up Standard 06.01 August 1999 DMS-100 Family SuperNode Data Manager Enhanced Terminal Access User Guide
297-5051-904 DMS-100 Family SuperNode Data Manager Enhanced Terminal Access User Guide SDMCom012 and up Standard 06.01 August 1999 DMS-100 Family SuperNode Data Manager Enhanced Terminal Access User Guide
CTEC1863/2018F Bonus Lab Page 1 of 5
 CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
HelpAndManual_illegal_keygen Contactor Elite Autoresponder Installation Guide
 HelpAndManual_illegal_keygen Contactor Elite Autoresponder Guide HelpAndManual_illegal_keygen Contactor Elite Autoresponder Autoresponder and Newsletter Delivery System To most web sites, their mailing
HelpAndManual_illegal_keygen Contactor Elite Autoresponder Guide HelpAndManual_illegal_keygen Contactor Elite Autoresponder Autoresponder and Newsletter Delivery System To most web sites, their mailing
LANTASTIC FOR WINDOWS 3.X USER S MANUAL. Instructions for basic networking and day-to-day use
 LANTASTIC FOR WINDOWS 3.X USER S MANUAL Instructions for basic networking and day-to-day use #9860 Edition 2_pdf [1/14/00 RK] Manual Writers/Editors: Online Writers/Editors: Designer: Rhonda Knotts Elizabeth
LANTASTIC FOR WINDOWS 3.X USER S MANUAL Instructions for basic networking and day-to-day use #9860 Edition 2_pdf [1/14/00 RK] Manual Writers/Editors: Online Writers/Editors: Designer: Rhonda Knotts Elizabeth
SSA Baan IVc4. Deployment Guide for Unix and Windows
 SSA Baan IVc4 Deployment Guide for Unix and Windows Copyright 2004 by Baan International B.V., a subsidiary of SSA Global Technologies, Inc. All rights reserved. No part of this publication may be reproduced,
SSA Baan IVc4 Deployment Guide for Unix and Windows Copyright 2004 by Baan International B.V., a subsidiary of SSA Global Technologies, Inc. All rights reserved. No part of this publication may be reproduced,
MyDataZone User s Manual
 MyDataZone User s Manual MyDataZone is a DataTraveler Secure tool that enables you to create and access a user defined password-protected area called a Privacy Zone, on your DataTraveler Secure drive.
MyDataZone User s Manual MyDataZone is a DataTraveler Secure tool that enables you to create and access a user defined password-protected area called a Privacy Zone, on your DataTraveler Secure drive.
Using the aregcmd Commands
 CHAPTER 2 This chapter describes how to use each of the aregcmd commands. The Cisco Access Registrar aregcmd command is a command-line based configuration tool. It allows you to set any Cisco Access Registrar
CHAPTER 2 This chapter describes how to use each of the aregcmd commands. The Cisco Access Registrar aregcmd command is a command-line based configuration tool. It allows you to set any Cisco Access Registrar
PowerTeacher Administrator User Guide. PowerTeacher Gradebook
 PowerTeacher Gradebook Released June 2011 Document Owner: Documentation Services This edition applies to Release 2.3 of the PowerTeacher Gradebook software and to all subsequent releases and modifications
PowerTeacher Gradebook Released June 2011 Document Owner: Documentation Services This edition applies to Release 2.3 of the PowerTeacher Gradebook software and to all subsequent releases and modifications
Proficy* HMI/SCADA - ifix C ONFIGURING S ECURITY F EATURES
 Proficy* HMI/SCADA - ifix C ONFIGURING S ECURITY F EATURES Version 5.5 January 2012 All rights reserved. No part of this publication may be reproduced in any form or by any electronic or mechanical means,
Proficy* HMI/SCADA - ifix C ONFIGURING S ECURITY F EATURES Version 5.5 January 2012 All rights reserved. No part of this publication may be reproduced in any form or by any electronic or mechanical means,
Installation Guide. Last Revision: Oct 03, Page 1-
 Installation Guide Last Revision: Oct 03, 2005 -Page 1- Contents Before You Begin... 2 Installation Overview... 2 Installation for Microsoft Windows 2000, Windows 2003, and Windows XP Professional... 3
Installation Guide Last Revision: Oct 03, 2005 -Page 1- Contents Before You Begin... 2 Installation Overview... 2 Installation for Microsoft Windows 2000, Windows 2003, and Windows XP Professional... 3
ORACLE USER PRODUCTIVITY KIT USAGE TRACKING ADMINISTRATION & REPORTING RELEASE SERVICE PACK 1 PART NO. E
 ORACLE USER PRODUCTIVITY KIT USAGE TRACKING ADMINISTRATION & REPORTING RELEASE 3.6.1 SERVICE PACK 1 PART NO. E17383-01 MARCH 2010 COPYRIGHT Copyright 1998, 2010, Oracle and/or its affiliates. All rights
ORACLE USER PRODUCTIVITY KIT USAGE TRACKING ADMINISTRATION & REPORTING RELEASE 3.6.1 SERVICE PACK 1 PART NO. E17383-01 MARCH 2010 COPYRIGHT Copyright 1998, 2010, Oracle and/or its affiliates. All rights
Password Reset Utility. Configuration
 Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Copyright. Trademarks Attachmate Corporation. All rights reserved. USA Patents Pending. WRQ ReflectionVisual Basic User Guide
 PROGRAMMING WITH REFLECTION: VISUAL BASIC USER GUIDE WINDOWS XP WINDOWS 2000 WINDOWS SERVER 2003 WINDOWS 2000 SERVER WINDOWS TERMINAL SERVER CITRIX METAFRAME CITRIX METRAFRAME XP ENGLISH Copyright 1994-2006
PROGRAMMING WITH REFLECTION: VISUAL BASIC USER GUIDE WINDOWS XP WINDOWS 2000 WINDOWS SERVER 2003 WINDOWS 2000 SERVER WINDOWS TERMINAL SERVER CITRIX METAFRAME CITRIX METRAFRAME XP ENGLISH Copyright 1994-2006
