IBM. IBM Multi-Factor Authentication for z/os User's Guide. z/os. Version 1 Release 3 SC
|
|
|
- Marlene Norman
- 5 years ago
- Views:
Transcription
1 z/os IBM IBM Multi-Factor Authentication for z/os User's Guide Version 1 Release 3 SC
2 Note Before using this information and the product it supports, read the information in Notices on page 91. This edition applies to Version 1 Release 3 of IBM Multi-Factor Authentication for z/os (product number ) and to all subsequent releases and modifications until otherwise indicated in new editions. Copyright IBM Corporation 2016, US Government Users Restricted Rights Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Rocket Software, Inc. 2016, 2018
3 Contents Tables v About this information vii How to send your comments to IBM.. ix If you have a technical problem ix Summary of changes xi Summary of changes as updated May, xi Summary of changes as updated February, xi Summary of changes for Version 1 Release 3 as updated November, xi Summary of changes as updated September, 2017 xii Summary of changes as updated August, xii Summary of changes as updated February, xii Summary of changes as updated November, 2016 xiii Summary of changes as updated October, xiii Summary of changes as updated September, 2016 xiii Part 1. Introduction Chapter 1. Introduction to IBM MFA... 3 Multi-factor authentication concepts RSA Authentication Manager concepts SecurID token code SecurID PIN SecurID passcode Types of token devices PIN and token concepts: use of the password field 6 IBM TouchToken concepts IBM TouchToken OTP Preparing your Apple device for IBM TouchToken 8 IBM MFA Out-of-Band concepts General logon approach Part 2. Ouf-of-band authentication 11 Chapter 2. IBM MFA Out-of-Band authentication Enrolling your certificate for IBM MFA Certificate Authentication Logging in to an application with IBM MFA Out-of-Band Part 3. SecurID in-band authentication Chapter 3. TSO/E Fob-style hardware token Logging in with valid PIN, no passphrase Logging in with valid PIN, with passphrase.. 20 Logging in without valid PIN or passphrase.. 20 Logging in without valid PIN, with passphrase 21 Logging in with valid PIN and passphrase with compound in-band authentication Hardware token with a PINpad Logging in with valid PIN, no passphrase Logging in with valid PIN, with passphrase.. 23 Logging in without valid PIN or passphrase.. 23 Logging in without valid PIN, with passphrase 24 Logging in with valid PIN and passphrase with compound in-band authentication Soft token Logging in with valid PIN, no passphrase Logging in with valid PIN, with passphrase.. 25 Logging in without valid PIN or passphrase.. 26 Logging in without valid PIN, with passphrase 26 Logging in with valid PIN and passphrase with compound in-band authentication Chapter 4. CICS CESL transaction Fob-style hardware token Logging in with valid PIN Logging in without valid PIN Logging in with valid PIN with compound in-band authentication Hardware token with a PINpad Logging in with valid PIN Logging in without valid PIN Logging in with valid PIN with compound in-band authentication Soft token Logging in with valid PIN Logging in without valid PIN Logging in with valid PIN with compound in-band authentication Chapter 5. z/os Management Facility 35 Logging in with a fob-style hardware token Logging in with a hardware token with a PINpad 35 Logging in with a soft token z/os Management Facility with compound in-band authentication Logging in with a fob-style hardware token.. 36 Logging in with a hardware token with a PINpad Logging in with a soft token Chapter 6. IBM FTP Logging in with a fob-style hardware token Logging in with a hardware token with a PINpad 39 Logging in with a soft token IBM FTP with compound in-band authentication.. 40 Logging in with a fob-style hardware token.. 40 Logging in with a hardware token with a PINpad Logging in with a soft token Copyright IBM Corp. 2016, 2018 iii
4 Chapter 7. IBM OpenSSH Logging in with a fob-style hardware token Logging in with a hardware token with a PINpad 43 Logging in with a soft token IBM OpenSSH with compound in-band authentication Logging in with a fob-style hardware token.. 45 Logging in with a hardware token with a PINpad Logging in with a soft token Part 4. IBM TouchToken in-band authentication Chapter 8. IBM TouchToken in-band authentication Logging in to TSO with IBM TouchToken Logging in to CICS CESL with IBM TouchToken.. 49 Logging in to z/osmf with IBM TouchToken Logging in to IBM FTP with IBM TouchToken Logging in to IBM SSH with IBM TouchToken Logging in with IBM TouchToken and compound in-band authentication Chapter 9. Logging in with generic TOTP Part 5. RADIUS in-band authentication Chapter 10. IBM MFA for generic RADIUS with TSO/E Logging in with IBM MFA Compound In-Band when new PIN required Chapter 11. IBM MFA for SafeNet RADIUS with TSO/E TSO/E with Quick Log TSO/E with Quick Log and compound in-band authentication TSO/E with Challenge-Response TSO/E with Challenge-Response and compound in-band authentication Part 6. IBM CL/Supersession for z/os Chapter 12. IBM CL/SuperSession for z/os Part 7. IBM HTTP Server Chapter 13. IBM HTTP Server - Powered by Apache Logging in with IBM TouchToken Logging in with a fob-style hardware token Logging in with a hardware token with a PINpad 70 Logging in with a soft token Logging in with IBM MFA Out-of-Band Part 8. Troubleshooting Chapter 14. Troubleshooting Logging in with RSA SecurID "next token" mode.. 76 Logging in with Password Fallback Part 9. Messages Chapter 15. Multi-Factor Authentication messages Messages with AZF message numbers Part 10. Appendixes Appendix. Accessibility Accessibility features Consult assistive technologies Keyboard navigation of the user interface Dotted decimal syntax diagrams Notices Terms and conditions for product documentation.. 93 IBM Online Privacy Statement Policy for unsupported hardware Minimum supported hardware Trademarks Index iv IBM Multi-Factor Authentication for z/os User's Guide
5 Tables 1. TSO/E Logon Options for a fob-style hardware token TSO/E Logon Options for a hardware token with a PINpad TSO/E Logon Options for a soft token CICS Logon Options for a fob-style hardware token CICS Logon Options for a hardware token with a PINpad CICS Logon Options for a soft token TSO/E Logon Options for SafeNet Quick Log TSO/E Logon Options for SafeNet Quick Log with Compound In-Band TSO/E Logon Options for SafeNet Challenge-Response TSO/E Logon Options for SafeNet Challenge-Response with Compound In-Band. 61 Copyright IBM Corp. 2016, 2018 v
6 vi IBM Multi-Factor Authentication for z/os User's Guide
7 About this information This book provides instructions for using IBM Multi-Factor Authentication for z/os. It is intended primarily for system users, and assumes you are familiar with the z/os operating system. This book contains general user information, including explanations of AZF messages. For installation information, refer to IBM Multi-Factor Authentication for z/os Installation and Customization. To find any supplemental information made available after publication, go to To find the complete z/os library, go to IBM Knowledge Center ( Copyright IBM Corp. 2016, 2018 vii
8 viii IBM Multi-Factor Authentication for z/os User's Guide
9 How to send your comments to IBM We encourage you to submit comments and questions on the z/os product documentation. Your valuable feedback helps to ensure accurate and high-quality information. Important: If your comment regards a technical problem, see instead If you have a technical problem. Submit your feedback by using the appropriate method for your type of comment or question: Feedback on z/os function If your comment or question is about z/os itself, submit a request through the IBM RFE Community ( Feedback on IBM Knowledge Center function If your comment or question is about the IBM Knowledge Center functionality, for example search capabilities or how to arrange the browser view, send a detailed to IBM Knowledge Center Support at ibmkc@us.ibm.com. Feedback on the z/os product documentation and content If your comment or question is about the information that is provided in the z/os product documentation library, send a detailed to mhvrcfs@us.ibm.com. We welcome any feedback that you have, including comments on the clarity, accuracy, or completeness of the information. To help us better process your submission, include the following information: v Your name, company/university/institution name, and address v The following deliverable title and order number: IBM Multi-Factor Authentication for z/os User's Guide, SC v The section title of the specific information to which your comment or question relates v The text of your comment. When you send comments to IBM, you grant IBM a nonexclusive right to use or distribute the comments in any way appropriate without incurring any obligation to you. IBM or any other organizations use the personal information that you supply to contact you only about the issues that you submit. If you have a technical problem If you have a technical problem, do not use the feedback methods that are provided for sending comments. Instead, take one or more of the following actions: v See the IBM Support Portal (support.ibm.com). v Contact your IBM service representative. v Call IBM technical support. Copyright IBM Corp. 2016, 2018 ix
10 x IBM Multi-Factor Authentication for z/os User's Guide
11 Summary of changes This information includes terminology, maintenance, and editorial changes. Technical changes or additions to the text and illustrations for the current edition are indicated by a vertical line to the left of the change. Summary of changes as updated May, 2018 Changes made to IBM MFA for Version 1 Release 3 as updated May, New v Compound in-band authentication is updated to say that you can choose whether to enter the IBM MFA credential before or after the RACF credential. v Logging in with IBM MFA Compound In-Band when new PIN required on page 57 is added for IBM MFA for generic RADIUS. Changed v Various editorial changes have been made. Summary of changes as updated February, 2018 Changes made to IBM MFA for Version 1 Release 3 as updated February, New v Preparing your Apple device for IBM TouchToken on page 8 is updated to say that you can use either Mobile Safari on your ios device or a desktop browser to configure IBM TouchToken. The IBM TouchToken start page explains some basic information about IBM TouchToken, and contains both a QR code and a link that launch the IBM TouchToken for ios application on your device. Changed v Various editorial changes have been made. Summary of changes for Version 1 Release 3 as updated November, 2017 Changes made to IBM MFA for Version 1 Release 3 as updated November, New v Chapter 9, Logging in with generic TOTP, on page 53 is added. Generic TOTP supports common QR tokens on both Android and Apple ios devices. v IBM MFA Compound In-Band authentication is added to the following authentication factors: AZFSIDP1 ((RSA SecurID) AZFTOTP1 (IBM TouchToken) AZFRADP1 (generic RADIUS) AZFSFNP1 (SafeNet RADIUS) AZFSIDR1 (RSA SecurID RADIUS) Copyright IBM Corp. 2016, 2018 xi
12 v Chapter 10, IBM MFA for generic RADIUS with TSO/E, on page 57 is added to describe generic support. v Chapter 11, IBM MFA for SafeNet RADIUS with TSO/E, on page 59 is added to describe IBM MFA for SafeNet RADIUS support. Changed v Various editorial changes have been made. Summary of changes as updated September, 2017 Changes made to IBM MFA as updated September, 2017 New v IBM MFA Compound In-Band is added to the following authentication factors: AZFSIDP1 ((RSA SecurID) AZFTOTP1 (IBM TouchToken) AZFRADP1 (generic RADIUS) AZFSFNP1 (SafeNet RADIUS) Changed v Various editorial changes have been made. Summary of changes as updated August, 2017 Changes made to IBM MFA as updated August, 2017 New v Chapter 10, IBM MFA for generic RADIUS with TSO/E, on page 57 is added to describe generic support. v Chapter 11, IBM MFA for SafeNet RADIUS with TSO/E, on page 59 is added to describe IBM MFA for SafeNet RADIUS support. v Logging in with IBM MFA Out-of-Band on page 71 is added to show that you can log in to IBM HTTP Server - Powered by Apache with a IBM MFA Out-of-Band cache token credential. v Chapter 12, IBM CL/SuperSession for z/os, on page 65 is added to show that you can log in to IBM CL/SuperSession for z/os, V2.1 with IBM MFA. Changed v Chapter 2, IBM MFA Out-of-Band authentication, on page 13 is updated to show that you can log in with IBM MFA for SafeNet RADIUS and generic RADIUS. v Various editorial changes have been made. Summary of changes as updated February, 2017 Changes made to IBM MFA as updated February, 2017 Changed v Minor editorial updates have been made. xii IBM Multi-Factor Authentication for z/os User's Guide
13 Summary of changes as updated November, 2016 Changes made to IBM MFA as updated November, 2016 New v IBM MFA Out-of-Band concepts on page 9 and Logging in to an application with IBM MFA Out-of-Band on page 15 are added. Changed v Minor editorial updates have been made. Summary of changes as updated October, 2016 Changes made to IBM MFA as updated October, 2016 New v Chapter 13, IBM HTTP Server - Powered by Apache, on page 69 is added to describe using IBM HTTP Server - Powered by Apache with IBM MFA. Changed v Minor editorial updates have been made. Summary of changes as updated September, 2016 Changes made to IBM MFA as updated September, 2016 New v IBM TouchToken concepts on page 8 and Preparing your Apple device for IBM TouchToken on page 8 are added to show the addition of IBM TouchToken support. v Various chapters have been updated to show the addition of IBM TouchToken support. v New messages have been added in support of IBM TouchToken. Changed v Minor editorial updates have been made. Summary of changes xiii
14 xiv IBM Multi-Factor Authentication for z/os User's Guide
15 Part 1. Introduction Copyright IBM Corp. 2016,
16 2 IBM Multi-Factor Authentication for z/os User's Guide
17 Chapter 1. Introduction to IBM MFA IBM Multi-Factor Authentication for z/os, which is referred to in this document as IBM MFA, provides alternate authentication mechanisms for z/os networks that are used in conjunction with RSA SecurID-based authentication systems, Apple Touch ID devices, certificate authentication options such as PIV/CAC cards, and more. IBM MFA allows RACF to use alternate authentication mechanisms in place of the standard z/os password. The most common method for authenticating users to z/os systems is by the use of passwords or password phrases. Unfortunately, passwords can present a relatively simple point of attack for exploitation. In order for systems that rely on passwords to be secure, they must enforce password controls and provide user education. Users tend to pick common passwords, write down passwords, and unintentionally install malware that can log passwords. Additionally, building an extremely powerful dedicated password cracking computer system has become trivial and low-cost. Clients are looking for ways to raise the assurance level of their systems by requiring additional authentication factors for users. You can use IBM MFA with a large variety of applications. Some examples provided in this document include: v TSO/E. Time Sharing Options (TSO/E) allows users to create an interactive session with the z/os system. TSO provides a single-user logon capability and a basic command prompt interface to z/os. v CICS CESL. Customer Information Control System (CICS) is a family of application servers and connectors that provides industrial-strength, online transaction management and connectivity for mission-critical applications. v z/osmf. IBM z/os Management Facility (z/osmf) provides a web-based interface that allows you to manage various aspects of your z/os systems through a browser. v IBM OpenSSH. OpenSSH provides secure encryption for both remote login and file transfer. Multi-factor authentication concepts IBM MFA relies on multiple authentication factors. A multi-factor authentication system requires that multiple authentication factors be presented during logon in order to verify a user's identity. Each authentication factor must be from a separate category of credential types. Requiring multiple authentication factors improves the security of your user account. You either present the credentials directly into the application (in-band) or out-of band: v Out-of-band authentication allows you to authenticate on a user-specific web page with one or more factors to retrieve a cache token credential that you use to log in. Out-of-band authentication is described in IBM MFA Out-of-Band concepts on page 9. Out-of-band authentication methods are described in Part 2: Out-of-Band Authentication. Copyright IBM Corp. 2016,
18 v For in-band authentication, you generate a token using IBM MFA with SecurID, IBM TouchToken, IBM MFA for generic RADIUS, IBM MFA for SafeNet RADIUS, or RSA SecurID RADIUS and use that token directly to log on. In-band authentication methods are described in Part 3: In-Band Authentication. IBM MFA with SecurID In the simplest terms, for IBM MFA with SecurID, the RSA Authentication Manager determines whether the user's credentials are valid and, if so, returns success to RACF. RACF then resumes control and completes the authentication and authorization process as usual. IBM MFA with SecurID requires: v "Something you have." (The hardware or software RSA SecurID token.) v "Two things you know." (An RSA SecurID Personal Identification Number (PIN), and something you know.) IBM MFA with RADIUS IBM MFA includes support for "generic" RADIUS, SafeNet RADIUS, and RSA SecurID RADIUS. Generic RADIUS refers to the RADIUS server of your choice that returns a simple allowed/denied response. In all cases, the RADIUS server determines whether the user's credentials are valid and, if so, returns success to RACF. RACF then resumes control and completes the authentication and authorization process as usual. IBM TouchToken For IBM MFA with IBM TouchToken, you use the IBM TouchToken for ios application on supported Apple devices to generate a hashed, timed one-time password (OTP), and then use this password together with your z/os user name to log on to the z/os system. Note: If your system administrator configures your account for generic TOTP, you can log in by using common Quick Response (QR) codes on both Android and Apple ios devices. The OTP password generated by the IBM TouchToken for ios application must match the OTP password generated by the IBM TouchToken component on the z/os server. OTP passwords are regenerated at regular intervals. IBM TouchToken requires: v "Something you have." (The Apple Touch ID device, with the provisioned IBM TouchToken for ios application.) v "Something you are." (Your fingerprint.) IBM MFA Certificate Authentication IBM MFA Certificate Authentication is a general purpose certificate authentication that includes Common Access Card (CAC) and Personal Identification Verification (PIV) cards. Certificate authentication uses the client identity certificate to authenticate the user. IBM MFA Certificate Authentication requires: 4 IBM Multi-Factor Authentication for z/os User's Guide
19 v "Something you have." (The approved certificate, typically from a PIV or CAC card or other smart card.) v "Something you know." (The Personal Identification Number (PIN).) RSA Authentication Manager concepts The RSA Authentication Manager includes token codes, PINs, and passcodes as described in this section. SecurID token code The SecurID token code is a continuously regenerated number used to prove your identity. The token code is a pseudo-random 6- or 8-digit number (PRN), based on the current time, that is displayed on the RSA SecurID token device. It is presumed that only an authorized user possesses the token device. The token code is a one-time password (OTP). It is valid only while it is displayed, and it can be used only once. The token device generates a new token code at regular intervals, typically every 60 seconds. The display frequency for the token device determines the amount of time that a token code appears before the display is refreshed. SecurID PIN The SecurID PIN is conceptually similar to a PIN that you might use for financial transactions. It is a number that only you know that helps to identify you. The Personal Identification Number (PIN) is a unique 4- to 8-digit identifier that only you know. Your PIN can be of your own choosing, or system generated by RSA Authentication Manager depending on your RSA token policy. If you create your own PIN, follow the locally established rules for creating a valid PIN, including the number of characters, the reuse policy, and so forth. Your security administrator can clear and reset the PIN as needed, so it is possible that your current PIN is invalid and you need to change it. SecurID passcode A SecurID passcode is the combination of a PIN and token code. Similar to the token code, a passcode is a one-time password (OTP). It is valid only while it is displayed, and it can be used only once. There are two types of passcodes: v For hardware fob-style tokens without a PINpad, the SecurID passcode consists of your PIN followed by the token code and you must enter both. For example, if your PIN is 1234 and the token code is , you enter the passcode as v For SecurID PINpad hardware tokens and soft token applications, you enter your PIN on the pin pad and the token generates a hash-encrypted passcode from the PIN and the generated token. The token generates a new passcode at regular intervals, typically every 60 seconds. You then use the generated passcode when you log in. Chapter 1. Introduction to IBM MFA 5
20 Types of token devices Several types of RSA SecurID token devices are supported for use with IBM Multi-Factor Authentication for z/os. RSA SecurID card-style tokens and key fobs These devices generate a token code. Card-style tokens (such as the RSA SecurID 200) and key fobs (such as the RSA SecurID 800) function identically, with both displaying the token code in the LCD. RSA SecurID PINpads With an RSA SecurID PINpad token, you enter your PIN directly into the token, and the token generates a hash-encrypted six- or eight-digit passcode. For example, with the RSA SecurID 520 card-style PINpad, you enter the PIN via a 10-digit numeric pad that is contained on the card. The passcode displayed is a hash-encrypted combination of the PIN and the current token code. You can use the PINpad token in two ways: v If you have a valid PIN, enter the PIN and the token generates a hash-encrypted passcode. The passcode displayed is a hash-encrypted combination of the PIN and the current token code. The passcode can be six or eight digits, depending on the profile. v If you do not have a valid PIN, which can occur if the security administrator forces you to change it, use the token to generate a token code. You then use the generated token code to log in and change your PIN. RSA SecurID soft tokens RSA SecurID soft token applications reside on a computer or other smart device. You can use the soft token application in two ways: v If you have a valid PIN, enter the PIN and the token generates a hash-encrypted passcode. The passcode displayed is a hash-encrypted combination of the PIN and the current token code. The passcode can be six or eight digits, depending on the profile. v If you do not have a valid PIN, which can occur if the security administrator forces you to change it, use the token to generate a token code. You then use the generated token code to log in and change your PIN. Support for MVS operator console logon The MVS operator console logon does not support hard tokens. The MVS operator console logon does support soft tokens. PIN and token concepts: use of the password field Depending on the token type, IBM MFA uses the password field to contain the PIN and the token code. Consider the following example: User ID = Smith PIN = 8888 Token = IBM Multi-Factor Authentication for z/os User's Guide
21 Soft token = As described in Types of token devices on page 6, hard tokens use a physical token and a PIN. Soft tokens use software to hash the PIN into the token and generate a passcode, so you do not use a separate PIN. Typical logon Depending on the token type, IBM MFA uses the password field to contain the PIN and the token code. With passphrase support (more than 8 characters allowed for the password): v For a hard token, you enter in the password field. v For a soft token, you enter in the password field. Without passphrase support (maximum of 8 characters allowed for the password): v For a hard token, you enter in the password field. v For a hard token, you enter 8888 in the new password field. Note: You may need to enter 8888 again in the validate change field. v For a soft token, you enter in the password field. PIN-change mode Depending on the token type, IBM MFA uses the password field to contain the PIN and the token code. PIN-change mode is similar to a password change in that after you complete the normal logon, you receive a "password expired" notification. For example, assume that you want to use 9999 as the new hard token pin, or if using a soft token. With passphrase support (more than 8 characters allowed for the password): v For a hard token, you will be prompted to enter a new password. Enter 9999 in new password field. v For a soft token, you will be prompted to enter a new password. Enter in new password field. Without passphrase support (maximum of 8 characters allowed for the password): v For a hard token, you enter in the password field (unless the underlying software does this for you) in the new password field in the verify new password field. v For a soft token, you enter: Note: in the password field in new password field in the verify new password field. After the PIN change is done, you then need to re-validate with the new codes using the normal logon steps. Chapter 1. Introduction to IBM MFA 7
22 IBM TouchToken concepts IBM MFA with IBM TouchToken includes an IBM TouchToken for ios application and an IBM TouchToken one-time-password (OTP) as described in this section. IBM TouchToken provides strong authentication by combining something you have (your ios device provisioned with an IBM TouchToken account) and something you are (your fingerprint.) When logging on to your z/os account with IBM TouchToken, you use the IBM TouchToken for ios application to generate a one-time password (a token code) and use that token code in place of your RACF password. IBM TouchToken OTP IBM TouchToken combines Touch ID fingerprint biometric technology with a hashed, timed one-time password (OTP) for secure multi-factor authentication. You can consider the IBM TouchToken OTP to be a token code. The IBM TouchToken for ios application on the Apple device uses a shared secret key and the current time to generate token code values. IBM TouchToken on the z/os system then uses the same algorithm to validate user logons. IBM TouchToken requires Apple Touch ID fingerprint technology. The token code generated by the IBM TouchToken for ios application must fall within an approved sequence of token codes generated by the IBM TouchToken component on the z/os server. Token codes are regenerated at regular intervals. One-time token codes that are generated from the same secret key are identical if they are generated within a predetermined "token period" time value, which your security administrator can set at intervals of 15, 30, or 60 seconds, and a "window", which your security administrator can set from 1 to 10. Your security administrator will provide you with the URL of the IBM TouchToken registration server start page. You visit this URL from your ios web browser. Preparing your Apple device for IBM TouchToken You need to download the IBM TouchToken for ios application to your supported Apple device and then connect to the IBM TouchToken registration (HTTP) server to create an account. Before you begin You must satisfy the following prerequisites: v IBM TouchToken for ios requires Touch ID. To use Touch ID you must enable a passcode and enroll one or more fingerprints. You should also ensure that your ios device uses a complex alphanumeric passcode. If you do not already have a complex alphanumeric passcode set on your ios device, use Settings > Touch ID and Passcode > Turn Passcode On (or Change Passcode) > Passcode Options > Custom Alphanumeric Code to set one. v IBM TouchToken is secured with TLS. Depending on the TLS configuration of the IBM TouchToken registration server, your security administrator may instruct you to download and install an additional Root CA certificate to a Configuration Profile in the ios device. Never do this without explicit guidance from your 8 IBM Multi-Factor Authentication for z/os User's Guide
23 security administrator. You can then optionally view this profile from the ios device Settings > General > Profile page. 1. Download and install the IBM TouchToken for ios application from the App Store on your Apple Touch ID device. 2. Use Mobile Safari or a desktop browser to invoke the URL for the IBM TouchToken registration server. Your system administrator will provide you with this URL. The page explains some basic information about IBM TouchToken, and contains both a QR code and a link that launch the IBM TouchToken for ios application. 3. If using a desktop browser, scan the QR code with your ios device camera. If using Mobile Safari, tap the "Launch URL" link. This launches the IBM TouchToken for ios application and begins registration for a new IBM TouchToken account. 4. Tap "Begin Account Registration." 5. Enter your RACF user ID and current RACF password or passphrase. Tap Done. 6. The Set Token Alias screen includes the user ID and the touch token realm name. For security purposes, enter an alternate alias and click Save. This step is not required, but it is a Best Practice. 7. Tap Done on the Account Added screen. 8. On the IBM TouchToken screen, tap the account you just created. 9. When prompted, enter your touch ID fingerprint. 10. The application negotiates with the IBM TouchToken registration server and creates an OTP token. 11. Use this OTP token to log on to the z/os system. IBM MFA Out-of-Band concepts IBM MFA Out-of-Band authentication requires you to authenticate "out-of-band" with one or more factors to retrieve an in-band authentication code called a "cache token credential." Your security administrator must specifically configure your account for IBM MFA Out-of-Band. In IBM MFA Out-of-Band authentication, you authenticate "out-of-band" with one or more authentication factors configured by your security administrator. A user-specific IBM MFA Out-of-Band login page prompts you for all of the authentication factors you must provide. You follow the same process and provide the same information as you would for these factors without IBM MFA Out-of-Band, except that you enter the tokens on the login web page and not in your z/os application. You connect to the URL provided by your administrator and log on with your RACF user name and password or passphrase. You are then presented with a list of authentication policies. Each policy defines the factors you must supply and whether the cache token credentials can be reused and for how long they can be reused. When you select an authentication policy, you are then presented with the list of factors required to satisfy the policy. Chapter 1. Introduction to IBM MFA 9
24 General logon approach The important thing to note is that all configured authentication factors must succeed for you to receive the in-band authentication code. For example, if your account were to be configured for IBM MFA with SecurID and IBM TouchToken, both must succeed. If successful, you receive a cache token credential that you use to log in to the z/os application. As a general rule, if you are presented with an in-band request for logon credentials, enter your IBM MFA credentials. If you are presented with a request for in-band logon credentials, try your IBM MFA credentials first. This is true even if your account is configured to use PassTickets, because you may be required to first log on with IBM MFA. For IBM MFA Out-of-Band, a user-specific web page prompts you for all of the authentication credentials you must provide. 10 IBM Multi-Factor Authentication for z/os User's Guide
25 Part 2. Ouf-of-band authentication Copyright IBM Corp. 2016,
26 12 IBM Multi-Factor Authentication for z/os User's Guide
27 Chapter 2. IBM MFA Out-of-Band authentication IBM MFA Out-of-Band authentication requires you to authenticate "out-of-band" with one or more factors to retrieve a cache token credential, which you then use as your password with a z/os application. Your administrator must configure your account for IBM MFA Out-of-Band and will tell you whether you must use the IBM MFA Out-of-Band web page to log on. When prompted by the IBM MFA Out-of-Band web page, you must provide the required token(s). How you obtain the required token varies by token type. You follow the same process and provide the same information as you would for these factors without IBM MFA Out-of-Band, except that you enter the tokens on the login web page and not in your z/os application. IBM MFA with SecurID 1. For a SecurID token without a PINpad, get the 6- to 8-digit token code displayed by the token. 2. For a SecurID token with a PINpad (hardware or soft token), enter your PIN in the token and get the displayed passcode. 3. Provide it to the IBM MFA Out-of-Band web page when prompted. 4. Use the generated cache token credential as your password with the z/os application. IBM TouchToken 1. Follow the steps described in Preparing your Apple device for IBM TouchToken on page 8 to generate the OTP token. 2. Provide it to the IBM MFA Out-of-Band web page when prompted. 3. Use the generated cache token credential as your password with the z/os application. IBM MFA for generic RADIUS How you log in depends entirely on how your administrator has configured the RADIUS server. You may need to supply a valid passcode, PIN, or some other credential. Your administrator will provide you with this information. 1. Provide the RADIUS credential to the IBM MFA Out-of-Band web page when prompted. 2. Use the generated cache token credential as your password with the z/os application. IBM MFA for SafeNet RADIUS Your administrator will tell you which Gemalto SafeNet configuration applies to you. 1. In challenge-response mode, enter any single alphabetic character in the IBM MFA Out-of-Band passcode field. Copy the generated challenge and enter it in the MobilePASS application to generate a passcode. In Quick Log mode, you do not have to perform this step. Copyright IBM Corp. 2016,
28 2. Get the 6- to 8-digit token passcode displayed by the MobilePASS token. 3. For a "server-side user select" PIN, provide your PIN followed by the passcode to the IBM MFA Out-of-Band web page when prompted. For a "user selected" PIN, provide only the passcode to the IBM MFA Out-of-Band web page when prompted. 4. Use the generated cache token credential as your password with the z/os application. IBM MFA Certificate Authentication 1. When prompted by the IBM MFA Out-of-Band web page, select the client certificate you want to use to authenticate yourself. Your security administrator will typically provide guidance on which certificate to use. Note: If you are using Internet Explorer, be aware that the Windows Internet Options "Don't prompt for client certificate selection when only one certificate exists" setting can result in your not having to choose a certificate. The "Don't prompt for client certificate selection when only one certificate exists" setting is typically controlled by the system administrator. 2. For PIV/CAC cards, you must then enter your valid PIN. 3. Use the generated cache token credential as your password with the z/os application. Enrolling your certificate for IBM MFA Certificate Authentication If your administrator has configured your account for IBM MFA Certificate Authentication as part of IBM MFA Out-of-Band, you must enroll your certificate before you can use it to log on. Before you begin It is a Best Practice to clear your Windows system SSL state before enrolling your certificate. To do this, select Control Panel > Internet Options > Content > Clear SSL State. In addition, from Control Panel > Internet Options > Content > Advanced, ensure that Use "SSL 2.0" and "Use SSL 3.0" are both unchecked. About this task You must enroll your certificate before you can use it to log on with IBM MFA Certificate Authentication. The process requires action by both the administrator and the user, and the actions must occur in the correct sequence. Perform these steps only as directed by your administrator. Note: This procedure has been verified with Microsoft Internet Explorer and Google Chrome. 1. When instructed to do so by your administrator, begin the IBM MFA Certificate Authentication logon process at the web server login page provided by the administrator, such as 14 IBM Multi-Factor Authentication for z/os User's Guide
29 Login with RACF Credentials Use your RACF credentials to access the IBM MFA Out of Band login interface. User ID: 2. On the Available Authentication Policies pop-up, click on "Open Certificate Enrollment Interface." Available Authentication Policies Choose a policy to begin Out of Band authentication. Policy-Name AZFCERT1 (Certificate-based authentication) Open Certificate Enrollment Interface 3. On the Enrollment page, click on "Begin Certificate Enrollment." AZFCERT1 Enrollment Ensure that you have a certificate available to enroll. AZFCERT1 Begin Certificate Enrollment 4. Select the certificate you want to use to log in and click OK. Your security administrator will typically provide guidance on which certificate to use. Note: If you are using Internet Explorer, be aware that the Windows Internet Options "Don't prompt for client certificate selection when only one certificate exists" setting can result in your not having to choose a certificate. The "Don't prompt for client certificate selection when only one certificate exists" setting is typically controlled by the system administrator. For PIV/CAC or other smart cards, you must then enter your valid PIN. Note: If you receive an error indicating that the server certificate is invalid, it is more likely that the certificate you chose is invalid. 5. If successful, you receive a message indicating the certificate enrollment succeeded and to await further instruction from the administrator. AZFCERT1 Enrollment Ensure that you have a certificate available to enroll. AZFCERT1 -[Succeeded] Certificate enrollment succeeded. Your certificate is tagged for Review. An administrator will notify you when it is Approved. Please close your browser window. The administrator will tell you when you can use the certificate to log on, as described in Logging in to an application with IBM MFA Out-of-Band. 6. Close the browser window to end the session. Logging in to an application with IBM MFA Out-of-Band You use the IBM MFA Out-of-Band logon web page to provide the required authentication tokens. Your security administrator has determined which tokens you must provide. About this task Your security administrator will tell you if you need to use IBM MFA Out-of-Band to log in. If you are required to use IBM MFA Out-of-Band to log in and you do not, you receive a reminder error message. Chapter 2. IBM MFA Out-of-Band authentication 15
30 Note: This procedure has been verified with Microsoft Internet Explorer and Google Chrome. 1. Use a web browser to connect to the URL provided by your security administrator, typically Login with RACF Credentials Use your RACF credentials to access the IBM MFA Out of Band login interface. User ID: 2. Enter your RACF user name to log in. If the login is successful, IBM MFA Out-of-Band presents a user-specific authentication page. 3. Chose your policy and follow the web interface. If you are presented with more than one policy, your security administrator will tell you which one to use. Note: When you choose a policy in a login session, that policy is enforced for that session. If you need to choose another policy, log off and log on again to start a new session. 4. Follow the web interface to enter the required tokens. Note: Your administrator determines the maximum amount of time you have to complete all authentication factors, starting from the time you successfully entered your RACF user name. If you do not complete all authentication factors within this time period, you must start over. 5. As you successfully enter the required tokens, the IBM MFA Out-of-Band web page prompts you for the next one. 6. When you have satisfied all of your token requirements, the IBM MFA Out-of-Band web page displays the cache token credential. Cache Token Credential You have satisfied the authentication policy. CREDENTIAL Click the above Cache Token Credential to copy it to Clipboard, and use this in place of your password to access applications 7. Manually enter or copy/paste the cache token credential as your password, as appropriate. Note: If you are using Internet Explorer and use the cache token credential copy feature, be aware that Windows Internet Options settings can affect its function. Specifically, the "Allow Programmatic Clipboard Access" setting in one or more applicable zones can disable this feature or require you to respond to an additional prompt. The "Allow Programmatic Clipboard Access" setting is typically controlled by the system administrator. On the z/os system, IBM MFA validates the cache token credential and allows or denies the logon. 16 IBM Multi-Factor Authentication for z/os User's Guide
31 Part 3. SecurID in-band authentication Copyright IBM Corp. 2016,
32 18 IBM Multi-Factor Authentication for z/os User's Guide
33 Chapter 3. TSO/E How you log in to TSO/E with IBM MFA for SecurID enabled depends on the token type you are using, whether you have a valid PIN, and whether pass phrases are enabled. IBM MFA SecurID If the security administrator has enabled your account for IBM MFA, you no longer use your RACF password to log in. Instead, how you log in with TSO/E depends on the following SecurID token and TSO/E configuration choices made by your security administrator: v What type of token do you have? See Types of token devices on page 6 for the supported token types. v Whether you have a valid PIN, whether you must create a new one, or whether the system generates one for you. Your security administrator decides when you must change your PIN. v Whether pass phrases are enabled. TSO/E passwords are typically a maximum of eight characters. However, it is possible for SecurID credentials to exceed eight characters. Therefore, your security administrator may have selected an alternate TSO/E logon panel that allows you to enter longer passwords called pass phrases in the Password field. General guidelines Fob-style hardware token Observe the following guidelines: v It is a best practice to wait until the token code changes before attempting to log in. v You can use the token code only once. v If you receive an authentication failure, wait until the token code changes before attempting to log in again. Several TSO/E login options are available for use with IBM MFA if you are using a hardware token without a PINpad. Consult Table 1 on page 20 to determine which login option matches your specific configuration and then follow the link to the related section. Copyright IBM Corp. 2016,
34 Table 1. TSO/E Logon Options for a fob-style hardware token Token type Fob-style hardware token Valid PIN? Pass phrases enabled? Use this login choice... Yes No Logging in with valid PIN, no passphrase Yes Yes Logging in with valid PIN, with passphrase No No Logging in without valid PIN or passphrase No Yes Logging in without valid PIN, with passphrase on page 21 Logging in with valid PIN, no passphrase You can log in to TSO/E with a valid PIN without using pass phrases. This use case requires a fob-style hardware token. 1. Begin to log in to TSO/E with your user name. 2. Get the 6- to 8-digit token code displayed by the SecurID token. 3. Enter the 6- to 8-digit token code displayed by the SecurID token in the Password field. 4. Enter your PIN in the New Password field and press Enter. The LOGON panel appears again. 5. Re-enter your PIN to confirm it and press Enter. Logging in with valid PIN, with passphrase You can log in to TSO/E with a valid PIN when using pass phrases. This use case requires a fob-style hardware token. 1. Begin to log in to TSO/E with your user name. 2. Get the 6- to 8-digit token code displayed by the SecurID token. 3. Enter your PIN followed by the 6- to 8-digit token code displayed by the SecurID token in the Password field. For example, if your PIN is 4321 and your token code is , enter in the Password field. 4. Press Enter. Logging in without valid PIN or passphrase You can log in to TSO/E without a currently valid PIN and without using pass phrases. This use case requires a fob-style hardware token. 1. Begin to log in to TSO/E with your user name. 20 IBM Multi-Factor Authentication for z/os User's Guide
35 2. Get the 6- to 8-digit token code displayed by the SecurID token. 3. Enter the 6- to 8-digit token code displayed by the SecurID token in the Password field. Leave the New Password field empty. Press Enter. If the token code is accepted, a status message indicates that you must enter a new 4- to 8-digit PIN. Note: Do not enter the new PIN on the status message page. 4. Press Enter. The LOGON panel is displayed and you are prompted to enter a new password. 5. Enter a new PIN in the New Password field and press Enter. (If you are prompted with a system-generated PIN, use that PIN. You might also be prompted to use either the system-generated PIN or your own.) 6. Confirm the PIN. If accepted, the "new PIN accepted" message is displayed. 7. Press Enter to return to the LOGON panel. 8. Because you changed the PIN, you must log in again. Wait for the token code displayed by the SecurID token to change and get the new token code. 9. Enter the token code displayed by the SecurID token in the Password field. 10. Enter the PIN in the New Password field and press Enter. Logging in without valid PIN, with passphrase You can log in to TSO/E without a currently valid PIN using pass phrases. This use case requires a fob-style hardware token. 1. Begin to log in to TSO/E with your user name. 2. Get the 6- to 8-digit token code displayed by the SecurID token. 3. Enter the 6- to 8-digit token code displayed by the SecurID token in the Password field. Press Enter. If the token code is accepted, a status message indicates that you must enter a new 4- to 8-digit PIN. Note: Do not enter the new PIN on the status message page. 4. Press Enter. The LOGON panel is displayed and you are prompted to enter a new password. 5. Enter a new PIN in the Password field and press Enter. (If you are prompted with a system-generated PIN, use that PIN. You might also be prompted to use either the system-generated PIN or your own.) 6. Confirm the PIN. If accepted, the "new PIN accepted" message is displayed. 7. Press Enter to return to the LOGON panel. 8. Because you changed the PIN, you must log in again. Wait for the token code displayed by the SecurID token to change. Get the new token code. 9. Enter your PIN followed by the 6- to 8-digit token code displayed by the SecurID token in the Password field. Press Enter. Logging in with valid PIN and passphrase with compound in-band authentication You can log in to TSO/E with a valid PIN when using pass phrases. Your administrator must have configured your account for IBM MFA Compound In-Band. This use case requires a fob-style hardware token. Chapter 3. TSO/E 21
36 About this task Important: If your RACF password has expired, you are prompted during the compound in-band login session to change your RACF password. However, after attempting to change your password, the IBM MFA credentials are then replayed, which causes the password change operation to fail. In this case, begin a new TSO/E session, log in with your existing password and IBM MFA credentials, and then use the -New Password option on the panel to change your RACF password. 1. Begin to log in to TSO/E with your user name. 2. Get the 6- to 8-digit token code displayed by the SecurID token. 3. Enter your PIN followed by the 6- to 8-digit token code displayed by the SecurID token, followed by the separator, followed by your passphrase or password in the Password field. For example, assume the separator is the colon (:). If your PIN is 4321 your token code is , and your password is , enter : in the Password field. Note: Your security administrator can reverse the order in which you enter the credentials, so that you enter your passphrase or password first, followed by the separator. Consult your security administrator for guidance. 4. Press Enter. Hardware token with a PINpad Several TSO/E login options are available for use with IBM MFA if you are using a hardware token with a PINpad. Consult Table 2 to determine which login option matches your specific configuration and then follow the link to the related section. Table 2. TSO/E Logon Options for a hardware token with a PINpad Token type Hardware token (with PINpad) Valid PIN? Pass phrases enabled? Use this login choice... Yes No Logging in with valid PIN, no passphrase Yes Yes Logging in with valid PIN, with passphrase on page 23 No No Logging in without valid PIN or passphrase on page 23 No Yes Logging in without valid PIN, with passphrase on page 24 Logging in with valid PIN, no passphrase You can log in to TSO/E with a valid PIN without using pass phrases. This use case requires a hardware token with a PINpad. 22 IBM Multi-Factor Authentication for z/os User's Guide
IBM Multi-Factor Authentication for z/os A Product Review and Update
 IBM z Systems IBM Multi-Factor Authentication for z/os A Product Review and Update Julie Bergh jbergh@us.ibm.com Ross Cooper August 2016 A new z/os product has become available The new IBM Multi-Factor
IBM z Systems IBM Multi-Factor Authentication for z/os A Product Review and Update Julie Bergh jbergh@us.ibm.com Ross Cooper August 2016 A new z/os product has become available The new IBM Multi-Factor
SafeNet MobilePASS+ for Android. User Guide
 SafeNet MobilePASS+ for Android User Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have and keep the
SafeNet MobilePASS+ for Android User Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have and keep the
IBM. DFSMS Using the Interactive Storage Management Facility. z/os. Version 2 Release 3 SC
 z/os IBM DFSMS Using the Interactive Storage Management Facility Version 2 Release 3 SC23-656-30 Note Before using this information and the product it supports, read the information in Notices on page
z/os IBM DFSMS Using the Interactive Storage Management Facility Version 2 Release 3 SC23-656-30 Note Before using this information and the product it supports, read the information in Notices on page
RSA Authentication Manager Adapter User Guide
 IBM Security Identity Manager Version 6.0 RSA Authentication Manager Adapter User Guide SC27-4409-04 IBM Security Identity Manager Version 6.0 RSA Authentication Manager Adapter User Guide SC27-4409-04
IBM Security Identity Manager Version 6.0 RSA Authentication Manager Adapter User Guide SC27-4409-04 IBM Security Identity Manager Version 6.0 RSA Authentication Manager Adapter User Guide SC27-4409-04
Software Token Enrollment: SafeNet MobilePASS+ for Apple ios
 Software Token Enrollment: SafeNet MobilePASS+ for Apple ios Step 1: Open the Self-Enrollment email a. Open the Self-Enrollment email on your Apple ios phone. NOTE: If using a personal phone, open the
Software Token Enrollment: SafeNet MobilePASS+ for Apple ios Step 1: Open the Self-Enrollment email a. Open the Self-Enrollment email on your Apple ios phone. NOTE: If using a personal phone, open the
User Guide for Client Remote Access. Version 1.2
 User Guide for Client Remote Access Version 1.2 Table of Contents PAGE Introduction... 2 Microsoft Multi-Factor Authentication Introduction... 3-4 User Enrollment... 5-8 Accessing Remote Resources Windows
User Guide for Client Remote Access Version 1.2 Table of Contents PAGE Introduction... 2 Microsoft Multi-Factor Authentication Introduction... 3-4 User Enrollment... 5-8 Accessing Remote Resources Windows
John Petreshock IBM Poughkeepsie - z Systems Security Offering Manager
 IBM z Systems Security Conference Business Security for today and tomorrow > 27-30 September Montpellier IBM Multi-Factor Authentication for z/os John Petreshock -jpetres@us.ibm.com IBM Poughkeepsie -
IBM z Systems Security Conference Business Security for today and tomorrow > 27-30 September Montpellier IBM Multi-Factor Authentication for z/os John Petreshock -jpetres@us.ibm.com IBM Poughkeepsie -
Contents. Multi-Factor Authentication Overview. Available MFA Factors
 The purpose of this document is to provide National University student Single Sign-On users with instructions for how to configure and use Multi-Factor Authentication. Contents Multi-Factor Authentication
The purpose of this document is to provide National University student Single Sign-On users with instructions for how to configure and use Multi-Factor Authentication. Contents Multi-Factor Authentication
<Partner Name> RSA SECURID ACCESS. VMware Horizon View Client 6.2. Standard Agent Implementation Guide. <Partner Product>
 RSA SECURID ACCESS Standard Agent Implementation Guide VMware Daniel R. Pintal, RSA Partner Engineering Last Modified: August 9 th, 2016 Solution Summary VMware Horizon
RSA SECURID ACCESS Standard Agent Implementation Guide VMware Daniel R. Pintal, RSA Partner Engineering Last Modified: August 9 th, 2016 Solution Summary VMware Horizon
Bechtel Partner Access User Guide
 Bechtel Partner Access User Guide IMPORTANT: For help with this process, please contact the IS&T Service Center or your local IS&T support group: IS&T Service Center Phone: +1-571-392-6767 US Only +1 (800)
Bechtel Partner Access User Guide IMPORTANT: For help with this process, please contact the IS&T Service Center or your local IS&T support group: IS&T Service Center Phone: +1-571-392-6767 US Only +1 (800)
IBM. User's Guide. IBM Explorer for z/os. Version 3 Release 0 SC
 IBM Explorer for z/os IBM User's Guide Version 3 Release 0 SC27-8431-01 IBM Explorer for z/os IBM User's Guide Version 3 Release 0 SC27-8431-01 Note Before using this information, be sure to read the
IBM Explorer for z/os IBM User's Guide Version 3 Release 0 SC27-8431-01 IBM Explorer for z/os IBM User's Guide Version 3 Release 0 SC27-8431-01 Note Before using this information, be sure to read the
Ross Cooper, *CISSP IBM z/os Security Software Design and Development NewEra The z Exchange 10/24/2017
 IBM Multi-Factor Authentication for z/os Ross Cooper, *CISSP IBM z/os Security Software Design and Development NewEra The z Exchange 10/24/2017 Current Security Landscape 1,935 Number of security incidents
IBM Multi-Factor Authentication for z/os Ross Cooper, *CISSP IBM z/os Security Software Design and Development NewEra The z Exchange 10/24/2017 Current Security Landscape 1,935 Number of security incidents
SecuRemote for Windows 32-bit/64-bit
 SecuRemote for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
SecuRemote for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide
 STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
Integration Guide. SafeNet Authentication Manager. SAM using RADIUS Protocol with SonicWALL E-Class Secure Remote Access
 SafeNet Authentication Manager Integration Guide SAM using RADIUS Protocol with SonicWALL E-Class Secure Remote Access Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright
SafeNet Authentication Manager Integration Guide SAM using RADIUS Protocol with SonicWALL E-Class Secure Remote Access Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright
Pulse Secure Policy Secure
 Policy Secure RSA SecurID Ready Implementation Guide Last Modified: November 19, 2014 Partner Information Product Information Partner Name Pulse Secure Web Site http://www.pulsesecure.net/ Product Name
Policy Secure RSA SecurID Ready Implementation Guide Last Modified: November 19, 2014 Partner Information Product Information Partner Name Pulse Secure Web Site http://www.pulsesecure.net/ Product Name
Deployment User Guide
 Deployment User Guide Version: 010319-2 Contents STEP 1: (Windows Users Only): Determine if your PC is running the 32-bit or 64-bit version of Windows. If you are not a PC user, please proceed to step
Deployment User Guide Version: 010319-2 Contents STEP 1: (Windows Users Only): Determine if your PC is running the 32-bit or 64-bit version of Windows. If you are not a PC user, please proceed to step
isupplier Portal Registration & Instructions Last Updated: 22-Aug-17 Level 4 - Public INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL
 INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS isupplier Portal Registration & Instructions Last Updated: 22-Aug-17 Level 4 - Public Table of Contents 1 New User
INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS isupplier Portal Registration & Instructions Last Updated: 22-Aug-17 Level 4 - Public Table of Contents 1 New User
IBM Multi-Factor Authentication in a Linux on IBM Z environment - Example with z/os MFA infrastructure
 IBM Multi-Factor Authentication in a Linux on IBM Z environment - Example with z/os MFA infrastructure Dr. Manfred Gnirss IBM Client Center, Boeblingen 21.3.2018 2 Trademarks The following are trademarks
IBM Multi-Factor Authentication in a Linux on IBM Z environment - Example with z/os MFA infrastructure Dr. Manfred Gnirss IBM Client Center, Boeblingen 21.3.2018 2 Trademarks The following are trademarks
RapidIdentity Mobile Guide
 RapidIdentity Mobile Guide Welcome to the RapidIdentity Mobile Component page. The RapidIdentity Mobile guide describes the installation and configuration options for the RapidIdentity Mobile application.
RapidIdentity Mobile Guide Welcome to the RapidIdentity Mobile Component page. The RapidIdentity Mobile guide describes the installation and configuration options for the RapidIdentity Mobile application.
Secured by RSA Implementation Guide for Software Token Authenticators
 Secured by RSA Implementation Guide for Software Token Authenticators Partner Information Last Modified: June 30, 2014 Product Information Partner Name Web Site Product Name Version & Platform Product
Secured by RSA Implementation Guide for Software Token Authenticators Partner Information Last Modified: June 30, 2014 Product Information Partner Name Web Site Product Name Version & Platform Product
Guide to Deploying VMware Workspace ONE with VMware Identity Manager. SEP 2018 VMware Workspace ONE
 Guide to Deploying VMware Workspace ONE with VMware Identity Manager SEP 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Guide to Deploying VMware Workspace ONE with VMware Identity Manager SEP 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Workspace ONE UEM Integration with Apple School Manager
 VMware Workspace ONE UEM Integration with Apple School Manager VMware Workspace ONE UEM Integration with Apple School Manager VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation
VMware Workspace ONE UEM Integration with Apple School Manager VMware Workspace ONE UEM Integration with Apple School Manager VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation
Report HQ. Quick Start Guide. Report HQ Quick Start Guide - Version 1.2
 Report HQ Quick Start Guide STEP 1 Requesting An Account 1) Request an account via the Report HQ Request Form 2) Nasdaq will verify your account 3) Once your account is verified and provisioned, you will
Report HQ Quick Start Guide STEP 1 Requesting An Account 1) Request an account via the Report HQ Request Form 2) Nasdaq will verify your account 3) Once your account is verified and provisioned, you will
SafeNet Authentication Service
 SafeNet Authentication Service Push OTP Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have
SafeNet Authentication Service Push OTP Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have
MFA Enrollment Guide. Multi-Factor Authentication (MFA) Enrollment guide STAGE Environment
 Multi-Factor Authentication (MFA) Enrollment guide STAGE Environment December 2017 00 Table of Contents What is MFA and how does it impact the way I sign into applications? 2 MFA Enrollment Log-in 3 Setup
Multi-Factor Authentication (MFA) Enrollment guide STAGE Environment December 2017 00 Table of Contents What is MFA and how does it impact the way I sign into applications? 2 MFA Enrollment Log-in 3 Setup
Sync User Guide. Powered by Axient Anchor
 Sync Powered by Axient Anchor TABLE OF CONTENTS End... Error! Bookmark not defined. Last Revised: Wednesday, October 10, 2018... Error! Bookmark not defined. Table of Contents... 2 Getting Started... 7
Sync Powered by Axient Anchor TABLE OF CONTENTS End... Error! Bookmark not defined. Last Revised: Wednesday, October 10, 2018... Error! Bookmark not defined. Table of Contents... 2 Getting Started... 7
Deploying VMware Workspace ONE Intelligent Hub. October 2018 VMware Workspace ONE
 Deploying VMware Workspace ONE Intelligent Hub October 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Workspace ONE Intelligent Hub October 2018 VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Multi-factor Authentication Instructions
 What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
<Partner Name> RSA SECURID ACCESS Authenticator Implementation Guide. Intel Authenticate & Intel IPT based Token Provider for RSA SecurID
 RSA SECURID ACCESS Authenticator Implementation Guide Intel Authenticate & Intel IPT based Token Provider for RSA SecurID Jeffrey Carlson, RSA Partner Engineering Last
RSA SECURID ACCESS Authenticator Implementation Guide Intel Authenticate & Intel IPT based Token Provider for RSA SecurID Jeffrey Carlson, RSA Partner Engineering Last
Check Point GO R75. User Guide. 14 November Classification: [Public]
![Check Point GO R75. User Guide. 14 November Classification: [Public] Check Point GO R75. User Guide. 14 November Classification: [Public]](/thumbs/74/70104753.jpg) Check Point GO R75 User Guide 14 November 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point GO R75 User Guide 14 November 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes
 VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes Workspace ONE UEM v9.6 Have documentation feedback? Submit
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes Workspace ONE UEM v9.6 Have documentation feedback? Submit
MyFloridaNet-2 (MFN-2) Customer Portal/Password Management Reference Guide
 MyFloridaNet-2 (MFN-2) Customer Portal/Password Management Reference Guide REVISION RECORDS REVISION DATE DESCRIPTION 0 27 September 2017 Initial Submittal. 1 06 October 2017 Second Submittal. - 17 October
MyFloridaNet-2 (MFN-2) Customer Portal/Password Management Reference Guide REVISION RECORDS REVISION DATE DESCRIPTION 0 27 September 2017 Initial Submittal. 1 06 October 2017 Second Submittal. - 17 October
Getting Started with Duo Security Two-Factor Authentication (2FA)
 Getting Started with Duo Security Two-Factor Authentication (2FA) Table of Contents What is Two-Factor Authentication (2FA)?... 1 Why 2FA at Bates College?... 2 2FA Technologies... 3 Duo Protected Resources
Getting Started with Duo Security Two-Factor Authentication (2FA) Table of Contents What is Two-Factor Authentication (2FA)?... 1 Why 2FA at Bates College?... 2 2FA Technologies... 3 Duo Protected Resources
MFA Instructions. Getting Started. 1. Go to Apps, select Play Store 2. Search for Microsoft Authenticator 3. Click Install
 MFA Instructions Getting Started You will need the following: Your smartphone, a computer, and Internet access. Before using MFA your computer will need to be running Office 2016 if you use the full version
MFA Instructions Getting Started You will need the following: Your smartphone, a computer, and Internet access. Before using MFA your computer will need to be running Office 2016 if you use the full version
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes
 VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes AirWatch v9.3 Have documentation feedback? Submit a Documentation
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes AirWatch v9.3 Have documentation feedback? Submit a Documentation
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Guide to Deploying VMware Workspace ONE. VMware Identity Manager VMware AirWatch 9.1
 Guide to Deploying VMware Workspace ONE VMware Identity Manager 2.9.1 VMware AirWatch 9.1 Guide to Deploying VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware
Guide to Deploying VMware Workspace ONE VMware Identity Manager 2.9.1 VMware AirWatch 9.1 Guide to Deploying VMware Workspace ONE You can find the most up-to-date technical documentation on the VMware
OVERVIEW... 3 WHAT'S NEW... 3 COMPATIBILITY WITH MDM PRODUCTS... 5 CONFIGURE AN MDM MANAGED VPN PROFILE FOR CITRIX SSO... 5
 Citrix SSO Contents OVERVIEW... 3 WHAT'S NEW... 3 COMPATIBILITY WITH MDM PRODUCTS... 5 CONFIGURE AN MDM MANAGED VPN PROFILE FOR CITRIX SSO... 5 Device level VPN Profiles... 5 Per-App VPN Profiles... 7
Citrix SSO Contents OVERVIEW... 3 WHAT'S NEW... 3 COMPATIBILITY WITH MDM PRODUCTS... 5 CONFIGURE AN MDM MANAGED VPN PROFILE FOR CITRIX SSO... 5 Device level VPN Profiles... 5 Per-App VPN Profiles... 7
RACF Update: Multi-Factor Authentication is Here!
 RACF Update: Multi-Factor Authentication is Here! Ross Cooper, CISSP IBM Corporation March 9, 2017 Session: 20369 Insert Custom Session QR if Desired. RACF & MFA Update Read Only Auditor - New type of
RACF Update: Multi-Factor Authentication is Here! Ross Cooper, CISSP IBM Corporation March 9, 2017 Session: 20369 Insert Custom Session QR if Desired. RACF & MFA Update Read Only Auditor - New type of
GRS Enterprise Synchronization Tool
 GRS Enterprise Synchronization Tool Last Revised: Thursday, April 05, 2018 Page i TABLE OF CONTENTS Anchor End User Guide... Error! Bookmark not defined. Last Revised: Monday, March 12, 2018... 1 Table
GRS Enterprise Synchronization Tool Last Revised: Thursday, April 05, 2018 Page i TABLE OF CONTENTS Anchor End User Guide... Error! Bookmark not defined. Last Revised: Monday, March 12, 2018... 1 Table
Guide to Deploying VMware Workspace ONE. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1
 Guide to Deploying VMware Workspace ONE DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Guide to Deploying VMware Workspace ONE DEC 2017 VMware AirWatch 9.2 VMware Identity Manager 3.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Integration Guide. SafeNet Authentication Manager. SAM using RADIUS Protocol with Microsoft DirectAccess
 SafeNet Authentication Manager Integration Guide SAM using RADIUS Protocol with Microsoft DirectAccess Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet,
SafeNet Authentication Manager Integration Guide SAM using RADIUS Protocol with Microsoft DirectAccess Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet,
Using Workspace ONE PIV-D Manager. VMware Workspace ONE UEM 1811 VMware Workspace ONE PIV-D Manager
 Using Workspace ONE PIV-D Manager VMware Workspace ONE UEM 1811 VMware Workspace ONE PIV-D Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Using Workspace ONE PIV-D Manager VMware Workspace ONE UEM 1811 VMware Workspace ONE PIV-D Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Secure Access Manager User Guide December 2017
 Secure Access Manager User Guide December 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 INTRODUCTION... 3 SUMMARY... 3 BASIC FUNCTIONS... 3 LOGIN TO YOUR SAM ACCOUNT... 3 How to Activate your
Secure Access Manager User Guide December 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 INTRODUCTION... 3 SUMMARY... 3 BASIC FUNCTIONS... 3 LOGIN TO YOUR SAM ACCOUNT... 3 How to Activate your
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Payment Solutions MyCardRules. MyCardRules Mobile App. User Guide. Release 3.1
 Payment Solutions November 27, 2017 Installing MyCardRules... 2 Registering a Card and Creating an Account on MyCardRules... 2 Logging In to MyCardRules... 2 Registering a Card... 3 Creating an Account...
Payment Solutions November 27, 2017 Installing MyCardRules... 2 Registering a Card and Creating an Account on MyCardRules... 2 Logging In to MyCardRules... 2 Registering a Card... 3 Creating an Account...
Integration Guide. SafeNet Authentication Manager. Using RADIUS Protocol for Cisco ASA
 SafeNet Authentication Manager Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Manager Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
LANCET MOBILE FOR PATIENTS VERSION: 1.9
 An application that assists patients with the delivery and viewing of laboratory results from their mobile devices. Lancet Mobile App An application that assists patients with the delivery and viewing
An application that assists patients with the delivery and viewing of laboratory results from their mobile devices. Lancet Mobile App An application that assists patients with the delivery and viewing
Software Token. Installation and User Guide. 22 September 2017
 Software Token Installation and User Guide 22 September 2017 Notices Following are policies pertaining to proprietary rights and trademarks. Proprietary Rights The information contained in this document
Software Token Installation and User Guide 22 September 2017 Notices Following are policies pertaining to proprietary rights and trademarks. Proprietary Rights The information contained in this document
OneKey Mobile App USER GUIDE
 USER GUIDE Updated in September 2017 All rights reserved. No part of this publication may be produced or transmitted in any form or by any means, including photocopying and recording, without seeking the
USER GUIDE Updated in September 2017 All rights reserved. No part of this publication may be produced or transmitted in any form or by any means, including photocopying and recording, without seeking the
IBM. Hardware Configuration Definition Planning. z/os. Version 2 Release 3 GA
 z/os IBM Hardware Configuration Definition Planning Version 2 Release 3 GA32-0907-30 Note Before using this information and the product it supports, read the information in Notices on page 147. This edition
z/os IBM Hardware Configuration Definition Planning Version 2 Release 3 GA32-0907-30 Note Before using this information and the product it supports, read the information in Notices on page 147. This edition
SafeNet Authentication Service
 SafeNet Authentication Service Push OTP Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have
SafeNet Authentication Service Push OTP Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have
Registering a Card and Creating an Account on
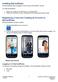 Installing MyCardRules The MyCardRules App is available for both iphones and Android phones. To install MyCardRules: 1. Search for the app in the App Store or on Google Play. 2. Follow the instructions
Installing MyCardRules The MyCardRules App is available for both iphones and Android phones. To install MyCardRules: 1. Search for the app in the App Store or on Google Play. 2. Follow the instructions
Duo Security Enrollment Guide
 Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
MANAGING ANDROID DEVICES: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE
 GUIDE APRIL 2019 PRINTED 17 APRIL 2019 MANAGING ANDROID DEVICES: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Audience Getting Started with Android
GUIDE APRIL 2019 PRINTED 17 APRIL 2019 MANAGING ANDROID DEVICES: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Audience Getting Started with Android
Guest Access User Interface Reference
 Guest Portal Settings, page 1 Sponsor Portal Application Settings, page 17 Global Settings, page 24 Guest Portal Settings Portal Identification Settings The navigation path for these settings is Work Centers
Guest Portal Settings, page 1 Sponsor Portal Application Settings, page 17 Global Settings, page 24 Guest Portal Settings Portal Identification Settings The navigation path for these settings is Work Centers
<Partner Name> <Partner Product> RSA SECURID ACCESS. NetMove SaAT Secure Starter. Standard Agent Client Implementation Guide
 RSA SECURID ACCESS Standard Agent Client Implementation Guide NetMove Daniel R. Pintal, RSA Partner Engineering Last Modified: April 4, 2018 Solution Summary Secure Starter
RSA SECURID ACCESS Standard Agent Client Implementation Guide NetMove Daniel R. Pintal, RSA Partner Engineering Last Modified: April 4, 2018 Solution Summary Secure Starter
Regions OnePassSM USER GUIDE. It s time to expect more. Regions Bank Member FDIC Revised
 Regions OnePassSM USER GUIDE Regions Bank Member FDIC Revised 110614 It s time to expect more. Regions OnePass User Guide Table of Contents Section I. OnePass Basics 3 What Is OnePass? 3 Minimum Browser
Regions OnePassSM USER GUIDE Regions Bank Member FDIC Revised 110614 It s time to expect more. Regions OnePass User Guide Table of Contents Section I. OnePass Basics 3 What Is OnePass? 3 Minimum Browser
RSA Authentication Manager 7.1 Help Desk Administrator s Guide
 RSA Authentication Manager 7.1 Help Desk Administrator s Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA,
RSA Authentication Manager 7.1 Help Desk Administrator s Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA,
MFA Pilot Instructions
 MFA Pilot Instructions Getting Started You will need the following: Your smartphone, a computer, and Internet access. Before using MFA your computer will need to be running Office 2016. If you are still
MFA Pilot Instructions Getting Started You will need the following: Your smartphone, a computer, and Internet access. Before using MFA your computer will need to be running Office 2016. If you are still
Pulse Secure Client for Chrome OS
 Pulse Secure Client for Chrome OS Quick Start Guide Published March, 2018 Release 5.2r1 Version 1.6 2018 by Pulse Secure, LLC. All rights reserved 1 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose,
Pulse Secure Client for Chrome OS Quick Start Guide Published March, 2018 Release 5.2r1 Version 1.6 2018 by Pulse Secure, LLC. All rights reserved 1 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose,
Integration Guide. SafeNet Authentication Manager. SAM using RADIUS Protocol with Check Point Security Gateway
 SafeNet Authentication Manager Integration Guide SAM using RADIUS Protocol with Check Point Security Gateway Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013
SafeNet Authentication Manager Integration Guide SAM using RADIUS Protocol with Check Point Security Gateway Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013
VMware PIV-D Manager Deployment Guide
 VMware PIV-D Manager Deployment Guide AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product is protected
VMware PIV-D Manager Deployment Guide AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product is protected
SANTA CLARA COUNTY CFET THIRD PARTY PARTNERS REMOTE ACCESS GUIDE
 SANTA CLARA COUNTY CFET THIRD PARTY PARTNERS REMOTE ACCESS GUIDE SafeNet MobilePASS App MobilePASS is secure software that allows CFET Third Party Partners to remotely connect to County of Santa Clara
SANTA CLARA COUNTY CFET THIRD PARTY PARTNERS REMOTE ACCESS GUIDE SafeNet MobilePASS App MobilePASS is secure software that allows CFET Third Party Partners to remotely connect to County of Santa Clara
Anchor User Guide. Presented by: Last Revised: August 07, 2017
 Anchor User Guide Presented by: Last Revised: August 07, 2017 TABLE OF CONTENTS GETTING STARTED... 1 How to Log In to the Web Portal... 1 How to Manage Account Settings... 2 How to Configure Two-Step Authentication...
Anchor User Guide Presented by: Last Revised: August 07, 2017 TABLE OF CONTENTS GETTING STARTED... 1 How to Log In to the Web Portal... 1 How to Manage Account Settings... 2 How to Configure Two-Step Authentication...
Multi-factor Authentication Instructions
 What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
Integration Guide. SafeNet Authentication Service. SAS using RADIUS Protocol with WatchGuard XTMv. SafeNet Authentication Service: Integration Guide
 SafeNet Authentication Service Integration Guide 1 Document Information Document Part Number 007-012745-001, Rev. A Release Date October 2014 Trademarks All intellectual property is protected by copyright.
SafeNet Authentication Service Integration Guide 1 Document Information Document Part Number 007-012745-001, Rev. A Release Date October 2014 Trademarks All intellectual property is protected by copyright.
MFA (Multi-Factor Authentication) Enrollment Guide
 MFA (Multi-Factor Authentication) Enrollment Guide Morristown Medical Center 1. Open Internet Explorer (Windows) or Safari (Mac) 2. Go to the URL: https://aka.ms/mfasetup enter your AHS email address and
MFA (Multi-Factor Authentication) Enrollment Guide Morristown Medical Center 1. Open Internet Explorer (Windows) or Safari (Mac) 2. Go to the URL: https://aka.ms/mfasetup enter your AHS email address and
Integration Guide. SafeNet Authentication Manager. Using SafeNet Authentication Manager with Citrix XenApp 6.5
 SafeNet Authentication Manager Integration Guide Using SafeNet Authentication Manager with Citrix XenApp 6.5 Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013
SafeNet Authentication Manager Integration Guide Using SafeNet Authentication Manager with Citrix XenApp 6.5 Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013
Duo Enrollment for DA Employees
 Duo Enrollment for DA Employees Duo s Multi-Factor Authentication will be used to authenticate DA employees when using DA Portal, DA s Outlook Web Access (OWA), and DA s O365. It is RECOMMENDED to have
Duo Enrollment for DA Employees Duo s Multi-Factor Authentication will be used to authenticate DA employees when using DA Portal, DA s Outlook Web Access (OWA), and DA s O365. It is RECOMMENDED to have
MyFloridaNet-2 (MFN-2) Customer Portal/ Password Management/ VPN Reference Guide
 MyFloridaNet-2 (MFN-2) Customer Portal/ Password Management/ VPN Reference Guide i VISION RECORDS REVISION DATE DESCRIPTION 0 27 September 2017 Initial Submittal. 1 Second Submittal. ii TABLE OF CONTENTS
MyFloridaNet-2 (MFN-2) Customer Portal/ Password Management/ VPN Reference Guide i VISION RECORDS REVISION DATE DESCRIPTION 0 27 September 2017 Initial Submittal. 1 Second Submittal. ii TABLE OF CONTENTS
Citrix SSO for ios. Page 1 18
 Citrix SSO for ios Page 1 18 Contents OVERVIEW... 3 WHAT'S NEW... 3 KNOWN ISSUES AND FIXED ISSUES... 4 FEATURE COMPARISON BETWEEN CITRIX VPN AND CITRIX SSO... 5 COMPATIBILITY WITH MDM PRODUCTS... 6 CONFIGURE
Citrix SSO for ios Page 1 18 Contents OVERVIEW... 3 WHAT'S NEW... 3 KNOWN ISSUES AND FIXED ISSUES... 4 FEATURE COMPARISON BETWEEN CITRIX VPN AND CITRIX SSO... 5 COMPATIBILITY WITH MDM PRODUCTS... 6 CONFIGURE
Getting Started New User. To begin, open the Multi-Factor Authentication Service in your inbox.
 Getting Started New User To begin, open the Multi-Factor Authentication Service email in your inbox. 1 1 Getting Started New User Click the link https://mfa.baptisthealth.net/portal. This link takes you
Getting Started New User To begin, open the Multi-Factor Authentication Service email in your inbox. 1 1 Getting Started New User Click the link https://mfa.baptisthealth.net/portal. This link takes you
Consumer Banking User Guide. Getting Started
 Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Integration Guide. SafeNet Authentication Manager. Using RADIUS Protocol for Citrix NetScaler 10.5
 SafeNet Authentication Manager Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Manager Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Manager
 SafeNet Authentication Manager Integration Guide Using RADIUS Protocol for F5 BIG-IP Access Policy Manager All information herein is either public information or is the property of and owned solely by
SafeNet Authentication Manager Integration Guide Using RADIUS Protocol for F5 BIG-IP Access Policy Manager All information herein is either public information or is the property of and owned solely by
RSA Ready Implementation Guide for
 RSA Ready Implementation Guide for IBM Multi-Factor Authentication for z/os V1R1 John Sammon, RSA Partner Engineering Last Modified: 4/7/16 -- 1 - Solution Summary IBM Multi-Factor Authentication for z/os,
RSA Ready Implementation Guide for IBM Multi-Factor Authentication for z/os V1R1 John Sammon, RSA Partner Engineering Last Modified: 4/7/16 -- 1 - Solution Summary IBM Multi-Factor Authentication for z/os,
Automated Sign-on for Mainframe Administrator Guide
 Automated Sign-on for Mainframe Administrator Guide 12.5.1 For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy,
Automated Sign-on for Mainframe Administrator Guide 12.5.1 For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy,
VMware Horizon Client for Windows 10 UWP User Guide. Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6
 VMware Horizon Client for Windows 10 UWP User Guide Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6 You can find the most up-to-date technical documentation on the VMware website at:
VMware Horizon Client for Windows 10 UWP User Guide Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6 You can find the most up-to-date technical documentation on the VMware website at:
IBM. Enterprise Systems Architecture/ Extended Configuration Principles of Operation. z/vm. Version 6 Release 4 SC
 z/vm IBM Enterprise Systems Architecture/ Extended Configuration Principles of Operation Version 6 Release 4 SC24-6192-01 Note: Before you use this information and the product it supports, read the information
z/vm IBM Enterprise Systems Architecture/ Extended Configuration Principles of Operation Version 6 Release 4 SC24-6192-01 Note: Before you use this information and the product it supports, read the information
SurePassID ServicePass User Guide. SurePassID Authentication Server 2017
 SurePassID ServicePass User Guide SurePassID Authentication Server 2017 Introduction This technical guide shows how users can manage their SurePassID security tokens that are compatible with SurePassID
SurePassID ServicePass User Guide SurePassID Authentication Server 2017 Introduction This technical guide shows how users can manage their SurePassID security tokens that are compatible with SurePassID
IBM. Container Pricing for IBM Z. z/os. Version 2 Release 3
 z/os IBM Container Pricing for IBM Z Version 2 Release 3 Note Before using this information and the product it supports, read the information in Notices on page 129. This edition applies to Version 2 Release
z/os IBM Container Pricing for IBM Z Version 2 Release 3 Note Before using this information and the product it supports, read the information in Notices on page 129. This edition applies to Version 2 Release
Version Monitoring Agent User s Guide SC
 Tivoli IBM Tivoli Advanced Catalog Management for z/os Version 02.01.00 Monitoring Agent User s Guide SC23-7974-00 Tivoli IBM Tivoli Advanced Catalog Management for z/os Version 02.01.00 Monitoring Agent
Tivoli IBM Tivoli Advanced Catalog Management for z/os Version 02.01.00 Monitoring Agent User s Guide SC23-7974-00 Tivoli IBM Tivoli Advanced Catalog Management for z/os Version 02.01.00 Monitoring Agent
pinremote Manual Version 4.0
 pinremote Manual Version 4.0 Page 1 Table of content 1 Introduction... 4 2 Setup... 5 2.1 Requirements server... 5 2.2 Requirements client... 5 2.3 Setup process... 6 2.3.1 Single Server... 8 2.3.2 Cluster...
pinremote Manual Version 4.0 Page 1 Table of content 1 Introduction... 4 2 Setup... 5 2.1 Requirements server... 5 2.2 Requirements client... 5 2.3 Setup process... 6 2.3.1 Single Server... 8 2.3.2 Cluster...
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
IBM. JES2 Delivery Services. z/os. Version 2 Release 3
 z/os IBM JES2 Email Delivery Services Version 2 Release 3 Note Before using this information and the product it supports, read the information in Notices on page 31. This edition applies to Version 2 Release
z/os IBM JES2 Email Delivery Services Version 2 Release 3 Note Before using this information and the product it supports, read the information in Notices on page 31. This edition applies to Version 2 Release
Multi-Factor Authentication
 Introduction (MFA) provides an additional layer of security to your NHSmail account when signing in to NHSmail via a web browser. As a Local Administrator (LA) you will have MFA automatically enabled on
Introduction (MFA) provides an additional layer of security to your NHSmail account when signing in to NHSmail via a web browser. As a Local Administrator (LA) you will have MFA automatically enabled on
VMware Horizon Client for Chrome OS User Guide. 04 JAN 2018 VMware Horizon Client for Chrome OS 4.7
 VMware Horizon Client for Chrome OS User Guide 04 JAN 2018 VMware Horizon Client for Chrome OS 4.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Horizon Client for Chrome OS User Guide 04 JAN 2018 VMware Horizon Client for Chrome OS 4.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Salesforce1 Mobile Security White Paper. Revised: April 2014
 Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
RSA Ready Implementation Guide for. GlobalSCAPE EFT Server 7.3
 RSA Ready Implementation Guide for GlobalSCAPE EFT Server 7.3 FAL, RSA Partner Engineering Last Modified: 5/19/2016 Solution Summary GlobalSCAPE Enhanced File Transfer (EFT) server can be configured to
RSA Ready Implementation Guide for GlobalSCAPE EFT Server 7.3 FAL, RSA Partner Engineering Last Modified: 5/19/2016 Solution Summary GlobalSCAPE Enhanced File Transfer (EFT) server can be configured to
User Communication Citrix SecureAuth
 Prerequisites 1 *Non-Newmont PC ONLY* If you are using any PC except your Newmont issued system, you must follow this step if you are using your Newmont issued system you can move to First Time Enrollment
Prerequisites 1 *Non-Newmont PC ONLY* If you are using any PC except your Newmont issued system, you must follow this step if you are using your Newmont issued system you can move to First Time Enrollment
EOH-SASOL - Setup Sasol Mobile Express (Client)
 EOH-SASOL - Setup Sasol Mobile Express (Client) Document Control Document Information Information Document Id SSL/BO/121/WI Document Owner Back Office Operations Manager Issue Date 18 May 2016 Last Saved
EOH-SASOL - Setup Sasol Mobile Express (Client) Document Control Document Information Information Document Id SSL/BO/121/WI Document Owner Back Office Operations Manager Issue Date 18 May 2016 Last Saved
This overview document below is for Office 365 Online Migration and Multifactor Authentication Enrollment.
 Information Technology Division Email Online Multifactor Authentication Enrollment Last revised: May 2018 Last reviewed: June 2018 This overview document below is for Office 365 Email Online Migration
Information Technology Division Email Online Multifactor Authentication Enrollment Last revised: May 2018 Last reviewed: June 2018 This overview document below is for Office 365 Email Online Migration
System Administrator s Guide Login. Updated: May 2018 Version: 2.4
 System Administrator s Guide Login Updated: May 2018 Version: 2.4 Contents CONTENTS... 2 WHAT S NEW IN THIS VERSION 2018R1 RELEASE... 4 Password Retrieval via Email (GDPR Alignment)... 4 Self-Registration
System Administrator s Guide Login Updated: May 2018 Version: 2.4 Contents CONTENTS... 2 WHAT S NEW IN THIS VERSION 2018R1 RELEASE... 4 Password Retrieval via Email (GDPR Alignment)... 4 Self-Registration
<Partner Name> <Partner Product> RSA SECURID ACCESS. VMware Horizon View 7.2 Clients. Standard Agent Client Implementation Guide
 RSA SECURID ACCESS Standard Agent Client Implementation Guide VMware Horizon View 7.2 Clients Daniel R. Pintal, RSA Partner Engineering Last Modified: September 14, 2017
RSA SECURID ACCESS Standard Agent Client Implementation Guide VMware Horizon View 7.2 Clients Daniel R. Pintal, RSA Partner Engineering Last Modified: September 14, 2017
QUICK REFERENCE GUIDE. Managed Network Security Portal Multi-Factor Authentication
 QUICK REFERENCE GUIDE Managed Network Security Portal Multi-Factor Authentication January 10, 2019 To protect our customers critical data, Windstream Enterprise has added additional security measures to
QUICK REFERENCE GUIDE Managed Network Security Portal Multi-Factor Authentication January 10, 2019 To protect our customers critical data, Windstream Enterprise has added additional security measures to
VAM. Epic epcs Value-Added Module (VAM) Deployment Guide
 VAM Epic epcs Value-Added Module (VAM) Deployment Guide Copyright Information 2018. SecureAuth is a registered trademark of SecureAuth Corporation. SecureAuth s IdP software, appliances, and other products
VAM Epic epcs Value-Added Module (VAM) Deployment Guide Copyright Information 2018. SecureAuth is a registered trademark of SecureAuth Corporation. SecureAuth s IdP software, appliances, and other products
Multi-Factor Authentication (MFA) Interoperability Profile. Karen Herrington, Virginia Tech David Walker, Internet2 September 26, 2016
 Multi-Factor Authentication (MFA) Interoperability Profile Karen Herrington, Virginia Tech David Walker, Internet2 September 26, 2016 1 Mission Working group formed at the request of the Assurance Advisory
Multi-Factor Authentication (MFA) Interoperability Profile Karen Herrington, Virginia Tech David Walker, Internet2 September 26, 2016 1 Mission Working group formed at the request of the Assurance Advisory
