Computer Forensics CCIC Training
|
|
|
- Stephany Gordon
- 5 years ago
- Views:
Transcription
1 Computer Forensics CCIC Training Chapter 6: Recent Files Lauren Pixley and Cassidy Elwell May 2017 (Version 1)
2 This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
3 Introduction From an investigative standpoint, you usually want to determine what files a user recently accessed. It gives you a perspective on how the user used the computer, and it also associates file activity back to the suspect. This will help demonstrate their knowledge about the existence of the files and show that they opened and viewed it. In this chapter, we will focus on link files and jump lists. Both of these artifacts will show you what files the user opened. Link Files You are going to first look in Craig s Recent folder. This is located in: C:\Users\Craig\AppData\Roaming\Microsoft\Windows\Recent Figure 6-1 Craig s Link Files in Recent Folder Copyright All rights reserved. Page 6-1
4 Chapter 6 This folder contains the user s link files. A link file, or LNK, is a Windows shortcut that points back to an original file. A link file is generally created when a file is first opened. Link files are important during analysis, because they show where files were located, when they were opened, and they contain date and time stamps associated with the file. If you look at Windows Explorer and go to the Recent folder, you can see your own link files. Figure 6-2 Link Files in Windows Explorer Note: To view the AppData folder since it is hidden, open Windows Explorer and click Organize Folder and Search Options. Check Show Hidden Files, Folders, and Drives under the View tab. If you are on a Windows 8 or 10 machine, click the View tab on Windows Explorer and check Hidden Items. If you right-click one of the link files and select properties, you can see the information about the link file (see Figure 6-3). Copyright All rights reserved. Page 6-2
5 Recent Files Figure 6-3 Link File Properties This link file is merely a pointer back to the actual file. It contains date and time stamps, the size of the file, and if you look at the Shortcut tab, you can even see where the file was located when it was opened. Figure Link File Pointing to Actual File s Location Copyright All rights reserved. Page 6-3
6 Chapter 6 Example 1 (File Opened Once) Back in Autopsy, look at the link file called Pier.lnk and click on the Results view. Autopsy will show you the path of where Pier.jpg was stored when it was opened. Figure 6-5 Link File Shows Path of Pier.jpg If you view Pier.lnk in Hex view, you can see that inside this link there is embedded data that points back to the original file that was opened. Figure 6-6 Embedded Data in Pier.lnk Copyright All rights reserved. Page 6-4
7 Recent Files There are three date and time stamps EMBEDDED within the link file. The time stamps you see in the Hex view refer back to the file Pier.jpg. Embedded Time Stamps Creation Time (Yellow) Last Access Time (Green) Last Write Time (Blue) Description This is the time that the file (Pier.jpg) was created in that local path. If the file had been copied to that location, then the Creation date/time is when it was copied. Last access times have been disabled since Windows Vista. It keeps the same date as the Creation time (UTC), but there are some variables that can change or update it. This is the time that the file (Pier.jpg) was last modified. This is not necessarily the last time it was opened. Figure 6-7 Embedded Creation, Last Access, and Last Write Times of Pier.jpg To decode these time stamps, you are going to use the tool called DCode (Version 4.02a). You can download this tool at: Once you have DCode up and running, you need to copy the time stamps out Pier.lnk in hex view and paste them into Notepad. Figure 6-8 Copy and Paste Embedded Time Stamps of Pier.lnk In DCode, set the Decode Format to Windows: 64 bit Hex Value Little Endian. Next, past the first time stamp (creation time of pier.jpg) into the Value to Decode. Hit the Decode button in the bottom right corner and you should see the decoded embedded creation time stamp (see Figure 6-9). Copyright All rights reserved. Page 6-5
8 Chapter 6 Figure 6-9 Embedded Creation Time Stamp Decoded Repeat this for the other two time stamps, and you should have the following date and time stamps: Embedded Creation Time (UTC): Fri, 20 December :15:53 UTC Embedded Access Time (UTC): Fri, 20 December :15:53 UTC Embedded Last Write Time (UTC): Fri, 20 December :48:02 UTC Next, you need to look at the date and time stamps OF the link file itself. Figure Date and Time Stamps of the Link File The time stamps in the table pane are about the link file itself and are separate from the time stamps embedded within the link file. Link File Time Stamps Created Time Description When a file is first opened, it creates a link file. The link file s Created time stamp is when the file (Pier.jpg) was FIRST opened. Modified Time This is the time when the file (Pier.jpg) was LAST opened. If this is the same as the Created time stamp, then you know that the file was only opened once. Access Time Once again, the accessed time is disabled in Windows Vista, 7, and 8. Accessed will be the same date and time as Modified. As you can see in Figure 6-10, the Created and Modified time of the link file are the same. This means that the file (Pier.jpg) was only opened once. Copyright All rights reserved. Page 6-6
9 Recent Files Here is a timeline of the file Pier.jpg (All UTC): Figure Timeline of Pier.jpg Based on Link File Since the last time this picture was modified is BEFORE the time it was created in that folder, it is likely that this file was copied to the Pictures folder. Copyright All rights reserved. Page 6-7
10 Chapter 6 Example 2 (File Opened More than Once) Take a look at the file called Cheetos.lnk and click on the Results view. Autopsy will show that this link file is pointing to a Cheetos.jpg in E:\Coupons. This is important to note, because this could mean that Craig had plugged in and used an external drive. Figure Link File Shows Path of Cheetos.jpg Next, take a look at the embedded date and time stamps in the Cheetos.lnk file. Figure Embedded Creation, Last Access, and Last Write Times of Cheetos.jpg Use the DCode tool to decode the embedded time stamps. You should have the following time stamps: Embedded Creation Time (UTC): Wed, 18 December :36:22 UTC Embedded Access Time (UTC): Fri, 20 December :00:00 UTC Embedded Last Write Time (UTC): Mon, 14 January :42:34 UTC Note: You can tell a device is FAT32 based on the Last Access Time embedded in the link file. FAT32 does not track the time of the last accessed activity, only the date. In, DCode is reporting a last accessed date of 12/20/2013 and the time is 8:00 AM (UTC). DCode is attempting to report UTC by adding 8 hours to a field that by default reports 12:00 AM. Next, take a look at the time stamps of the link file itself. Figure Date and Time Stamps of the Link File Copyright All rights reserved. Page 6-8
11 Recent Files The link file s Modified date and time is different from the Created date and time. This means that Craig opened the file more than once. Here is a timeline for the file Cheetos.jpg (All UTC): Figure Timeline of Cheetos.jpg Based on Link File If a file has been opened more than two times, you will only know the FIRST time it was opened (Link Created) and the LAST time it was opened (Link Modified). Without other information, you will not know what the date and time stamps were when it was opened in between. Copyright All rights reserved. Page 6-9
12 Chapter 6 Example 3 (No Embedded Date/Time) Another example you will want to look at is the MileyCyrus_tongue.lnk. If you look at the link file in Hex view, you will see that there aren t any date and time stamps embedded in the link file. Figure No Embedded Time Stamps in Link File for MileyCyrus_tongue.jpg There are a few situations that can cause this to occur. If the user uses the function Save as on a picture when viewing a site using Internet Explorer, a link file will be created with no embedded date and time stamps. Once the user opens the file, embedded date and time stamps will be added in the link file. A link file is also created when a user does a Save Image as in Mozilla Firefox and Google Chrome. If the file isn t opened after it has been saved, there won t be any embedded date and time stamps as well. With certain applications, if the user creates a file in an application and saves it, but never opens it, there won t be any embedded date and time stamps. Once they do open the file, embedded date and time stamps will be added to the link file. If a user saves an attachment but does not open it, there will be a link file with no embedded date and time stamps. This only applies to certain client software programs, such as Windows Live Mail. Once the user actually opens the file, embedded date and time stamps will be added. The Created time stamp of the link file shows when the picture was saved or created in an application. The Modified time stamp matches the Created time stamp because it was never opened. If the file had been opened after it was saved, it would create date and time stamps embedded within the link file. The link file s Modified time stamp would show when the file was LAST opened. So, if a link file has no embedded date and time stamps it means the user could have: 1) Used Save as on a picture in a website, but never opened the file 2) Created the file in an application, but never opened it 3) Saved an attachment through an client software, but never opened the file A link file with no embedded date and time stamps merely gives you an idea of where the file might have come from. Later, you will go through the user s and Internet history. If you see the file as an attachment or in their download history, you will know exactly where it came from. Copyright All rights reserved. Page 6-10
13 Recent Files Example 4 (File is Moved, Link File is Updated) Now that you have an understanding of link files, let s take a look at how these can help in an investigation. Look at the link file called Underage_lolita_r@ygold_001.lnk and click on the Results view. Figure 6-17 Path of Underage_lolita_r@ygold_001.jpg This link file shows that when the picture was opened, it was located in: C:\Users\Craig\Pictures If you go to that location, you will see that the picture is no longer there. Go back to the link file and look at the date and time stamps embedded in the link file. Figure Embedded Creation, Last Access, and Last Write Times of Underage_lolita_r@ygold_001.jpg Use the DCode tool to decode the embedded time stamps. You should have the following time stamps: Embedded Creation Time (UTC): Sat, 21 December :32:57 UTC Embedded Access Time (UTC): Sat, 21 December :32:57 UTC Embedded Last Write Time (UTC): Sat, 21 December :50:16 UTC Next, take a look at the date and time stamps of the link file itself. Figure Date and Time Stamps of the Link File The link file s Modified date and time is different from the Created date and time. This means that Craig opened the file more than once. Copyright All rights reserved. Page 6-11
14 Chapter 6 Here is a timeline for the file Underage_lolita_r@ygold_001.jpg (All UTC): Figure Timeline of Underage_lolita_r@ygold_001.jpg Based on Link File The embedded Last Write Time tells us that the file was last modified BEFORE the creation time. This indicates that the embedded Creation Time was when the picture was copied, not when it was actually created. The link file was FIRST opened several seconds before the embedded Creation Time, which means it could have been opened on external media or in another folder before it was copied over. When a file is opened in one location, it creates a link file. This is important to note that if a suspect then copies that same file to a different location and opens it there, a new link file is not created. The original link file is merely updated. In this case, a link file was first created for the underage picture when it was opened in another location. When it was copied and opened in the Pictures folder, that same link file s embedded data was updated. The local path displays where it was last opened, and its embedded Creation Time is updated to when the file was copied to the Pictures folder. You were able to determine the picture was opened somewhere else because the FIRST time it was opened was before the embedded Creation Time. In the next section, you will learn how jump lists can sometimes show other locations a file was opened in. Note: This type of file naming is an indicator of child pornography. Searching for child pornography on this suspect s computer would be out of the scope of your original search warrant, which was just to search for coupons. In a normal investigation, you should obtain another search warrant to further investigate and see if the suspect had child pornography. Copyright All rights reserved. Page 6-12
15 Recent Files Jump Lists Jump Lists were a new feature added to Windows 7. They are similar to the Windows shortcuts (link files) because they are designed to take a user directly to a specific file or directory used frequently or recently. Figure Jump List for Microsoft Word Jump lists are important to look at because they may contain information of file activity that is no longer present in the link files. However, you may also find file activity in link files but not in a jump list. It is important to note that these are two separate artifacts and will not always match up. There are two sets of jump lists, which are called Destination files: automaticdestinations, which are created and maintained by the operating system. customdestinations, which are maintained by the specific application. A jump list is basically a catalog of one or more link files associated with a specific application. This catalog stores the data in compound file binary (CFB) format. The jump lists are located in the following subdirectories: C:\[username]\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations C:\[username]\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations There are various tools that you can use to review the contents of these files: JumpLister from WoanWare: Windows Jump List Parser from TZWorks: For this case, use JumpLister from WoanWare. To use this tool you need to first export the jump lists. Navigate to the folder in the Tucker image that contains them. Each jump list file name starts with a hex value prefix. This prefix is the Application ID. A resource for looking up AppID s is located at: Go ahead and highlight all the jump list files in the AutomaticDestinations folder, right-click one, and select Extract File(s) (see Figure 6-22). Copyright All rights reserved. Page 6-13
16 Chapter 6 Figure 6-22 Highlight Jump Lists in AutomaticDestinations, Right-Click and Select Extract File(s) Extract these files to your case Export folder. Open up the JumpLister tool where you downloaded it, and then select File Load. Figure 6-23 Click Load in JumpLister Navigate to your export folder that contains the jump list files. Highlight and select each jump list file and click Open. If you click the jump list c e1308d73.automaticDestinations-ms in JumpLister, you can see what pictures have been opened (see Figure 6-24). Copyright All rights reserved. Page 6-14
17 Recent Files Figure Individual Entries in Photos App Jump List Note: This version of Jumplister does not display what application goes with the jump list c e1308d73. This application is the Windows 8 Photos app and it is the default photo viewer in Windows 8. In the bottom left pane, there are entries for individual files that have been opened. These entries are equivalent to a link file because they show where the file was located and it has the embedded date and time stamps. The bottom left pane also has an entry called DestList (Destination List). This list is a summary of each entry (see Figure 6-25). There are three key fields that you want to focus your attention: Number: Date/Time: Data: This number will be associated with the entry number in the bottom left pane This is the last time the file was accessed with the program This is the file location and filename Copyright All rights reserved. Page 6-15
18 Chapter 6 Figure DestList in Jumplister As you can see in Figure 6-25, the jump list shows the underage pictures that were opened on the E: drive. You did not have this information in the link files because the link files were updated. You can see in the column Date/Time that the pictures Underage_lolita_r@ygold_001.jpg and Underage_lolita_r@ygold_002.jpg were opened on the E:\ drive and in the Pictures folder on the following dates: Underage_lolita_r@ygold_001.jpg (E: Drive): Underage_lolita_r@ygold_002.jpg (E: Drive): Underage_lolita_r@ygold_001.jpg (Pictures Folder): Underage_lolita_r@ygold_002.jpg (Pictures Folder): 12/21/13 7:32:38 PM (UTC) 12/21/13 7:32:45 PM (UTC) 12/21/13 7:33:05 PM (UTC) 12/21/13 7:33:10 PM (UTC) Note: There are two other timestamps called Timestamp (New) and Timestamp (Birth). These are related to Object IDs, which is a more advanced topic. For now, just use the Date/Time stamp to determine when the file was first opened. You can export out this jump list information to a CSV file by clicking File Export Copyright All rights reserved. Page 6-16
19 Recent Files Figure Export Jump List Information to CSV File Export the files to your case s Export Folder. Now, open up Excel and go to the Data tab. Click From Text under Get External Data. Figure Get External Data from Text to Open CSV File Navigate to your Tucker Export\Jumplist folder and open the file DestList.csv. A window will open and prompt you to choose your text import options. Pick Delimited and click Next (see Figure 6-28). Copyright All rights reserved. Page 6-17
20 Chapter 6 Check the Comma delimiter and hit Finish. Figure Import DestList.csv as Delimited Figure Set Comma as Delimiter This will give you a clean report of the jump list information (see Figure 6-30). Copyright All rights reserved. Page 6-18
21 Recent Files Figure CSV of Jump List Information If you click on one of the cells in the top row and then click the Filter button under the Data tab, you can easily filter for specific text or sort the columns. Figure Filter Function in Excel under Data Tab By clicking the arrow at the end of each column header, you can select filters such as Text Filters Begins With. These are helpful if you want to only view files on external media or just the C: drive. Figure Text Filter Begins with E:\ Copyright All rights reserved. Page 6-19
Computer Forensics CCIC Training
 Computer Forensics CCIC Training Chapter 7: Recycle Bin Lauren Pixley and Cassidy Elwell May 2017 (Version 1) This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial
Computer Forensics CCIC Training Chapter 7: Recycle Bin Lauren Pixley and Cassidy Elwell May 2017 (Version 1) This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial
Computer Forensics CCIC Training
 Computer Forensics CCIC Training Chapter 12: Hidden Data Lauren Pixley and Cassidy Elwell May 2017 (Version 1) This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial
Computer Forensics CCIC Training Chapter 12: Hidden Data Lauren Pixley and Cassidy Elwell May 2017 (Version 1) This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial
Computer Forensics CCIC Training
 Computer Forensics CCIC Training Chapter 5: Starting Phase 2 Lauren Pixley and Cassidy Elwell May 2017 (Version 1) This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial
Computer Forensics CCIC Training Chapter 5: Starting Phase 2 Lauren Pixley and Cassidy Elwell May 2017 (Version 1) This work by California Cyber Training Complex is licensed under a Creative Commons Attribution-NonCommercial
Copyright TZWorks LLC Contact Info: Document applies to v0.46 of jmp
 Copyright TZWorks LLC www.tzworks.net Contact Info: info@tzworks.net Document applies to v0.46 of jmp Updated: Feb 19, 2018 Abstract jmp is a standalone, command-line tool used to extract SHLLINK artifacts
Copyright TZWorks LLC www.tzworks.net Contact Info: info@tzworks.net Document applies to v0.46 of jmp Updated: Feb 19, 2018 Abstract jmp is a standalone, command-line tool used to extract SHLLINK artifacts
Office 2016 Excel Basics 25 Video/Class Project #37 Excel Basics 25: Power Query (Get & Transform Data) to Convert Bad Data into Proper Data Set
 Office 2016 Excel Basics 25 Video/Class Project #37 Excel Basics 25: Power Query (Get & Transform Data) to Convert Bad Data into Proper Data Set Goal in video # 25: Learn about how to use the Get & Transform
Office 2016 Excel Basics 25 Video/Class Project #37 Excel Basics 25: Power Query (Get & Transform Data) to Convert Bad Data into Proper Data Set Goal in video # 25: Learn about how to use the Get & Transform
Issues in Information Systems Volume 15, Issue II, pp , 2014
 DETERMINING USER ACTIONS IN OS X BASED ON QUICKLOOK THUMBNAIL CACHE DATABASE ENTRIES Sara Newcomer, Lockheed Martin, sara.r.newcomer@lmco.com ABSTRACT The purpose of this study was to document the structure
DETERMINING USER ACTIONS IN OS X BASED ON QUICKLOOK THUMBNAIL CACHE DATABASE ENTRIES Sara Newcomer, Lockheed Martin, sara.r.newcomer@lmco.com ABSTRACT The purpose of this study was to document the structure
DOING MORE WITH EXCEL: MICROSOFT OFFICE 2010
 DOING MORE WITH EXCEL: MICROSOFT OFFICE 2010 GETTING STARTED PAGE 02 Prerequisites What You Will Learn MORE TASKS IN MICROSOFT EXCEL PAGE 03 Cutting, Copying, and Pasting Data Filling Data Across Columns
DOING MORE WITH EXCEL: MICROSOFT OFFICE 2010 GETTING STARTED PAGE 02 Prerequisites What You Will Learn MORE TASKS IN MICROSOFT EXCEL PAGE 03 Cutting, Copying, and Pasting Data Filling Data Across Columns
Manual Physical Inventory Upload Created on 3/17/2017 7:37:00 AM
 Created on 3/17/2017 7:37:00 AM Table of Contents... 1 Page ii Procedure After completing this topic, you will be able to manually upload physical inventory. Navigation: Microsoft Excel > New Workbook
Created on 3/17/2017 7:37:00 AM Table of Contents... 1 Page ii Procedure After completing this topic, you will be able to manually upload physical inventory. Navigation: Microsoft Excel > New Workbook
Code Plug Management: Contact List Import/Export. Version 1.0, Dec 16, 2015
 Code Plug Management: Contact List Import/Export Version 1.0, Dec 16, 2015 Background This presentation will show how to update and maintain contact lists in the CS750 The following applications will be
Code Plug Management: Contact List Import/Export Version 1.0, Dec 16, 2015 Background This presentation will show how to update and maintain contact lists in the CS750 The following applications will be
Importing Career Standards Benchmark Scores
 Importing Career Standards Benchmark Scores The Career Standards Benchmark assessments that are reported on the PIMS Student Fact Template for Career Standards Benchmarks can be imported en masse using
Importing Career Standards Benchmark Scores The Career Standards Benchmark assessments that are reported on the PIMS Student Fact Template for Career Standards Benchmarks can be imported en masse using
TZWorks Prefetch Parser (pf) Users Guide
 TZWorks Prefetch Parser (pf) Users Guide Abstract pf is a standalone, command-line tool that can parse Windows prefetch files. From a forensics perspective, the prefetch file offers the analyst information
TZWorks Prefetch Parser (pf) Users Guide Abstract pf is a standalone, command-line tool that can parse Windows prefetch files. From a forensics perspective, the prefetch file offers the analyst information
OBIEE. Oracle Business Intelligence Enterprise Edition. Rensselaer Business Intelligence Admissions, Undergraduate
 OBIEE Oracle Business Intelligence Enterprise Edition Rensselaer Business Intelligence Admissions, Undergraduate TABLE OF CONTENTS INTRODUCTION... 1 USER INTERFACE... 1 HOW TO LAUNCH OBIEE... 1 HOW TO
OBIEE Oracle Business Intelligence Enterprise Edition Rensselaer Business Intelligence Admissions, Undergraduate TABLE OF CONTENTS INTRODUCTION... 1 USER INTERFACE... 1 HOW TO LAUNCH OBIEE... 1 HOW TO
How to Export a Report in Cognos Analytics
 IBM Cognos Analytics How to Export a Report in Cognos Analytics Reports viewed in IBM Cognos Analytics can be exported in many formats including Excel. Some of the steps for exporting are different depending
IBM Cognos Analytics How to Export a Report in Cognos Analytics Reports viewed in IBM Cognos Analytics can be exported in many formats including Excel. Some of the steps for exporting are different depending
DOING MORE WITH EXCEL: MICROSOFT OFFICE 2013
 DOING MORE WITH EXCEL: MICROSOFT OFFICE 2013 GETTING STARTED PAGE 02 Prerequisites What You Will Learn MORE TASKS IN MICROSOFT EXCEL PAGE 03 Cutting, Copying, and Pasting Data Basic Formulas Filling Data
DOING MORE WITH EXCEL: MICROSOFT OFFICE 2013 GETTING STARTED PAGE 02 Prerequisites What You Will Learn MORE TASKS IN MICROSOFT EXCEL PAGE 03 Cutting, Copying, and Pasting Data Basic Formulas Filling Data
Microsoft Office 2007, 2010 Registry Artifacts Dustin Hurlbut September 16, 2010
 Microsoft Office 2007, 2010 Registry Artifacts Dustin Hurlbut September 16, 2010 INTRODUCTION Previous versions of Microsoft Office used application specific registry artifacts to track opened documents.
Microsoft Office 2007, 2010 Registry Artifacts Dustin Hurlbut September 16, 2010 INTRODUCTION Previous versions of Microsoft Office used application specific registry artifacts to track opened documents.
Chapter 3. Shortcuts
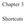 Chapter 3 Shortcuts Link Files Practical Exercise - Manually Decoding Link Files 1. Use WinHEX to open up the file named \Student Files\03_Link Files\c-3.txt.lnk. 2. First, let s look at the file header
Chapter 3 Shortcuts Link Files Practical Exercise - Manually Decoding Link Files 1. Use WinHEX to open up the file named \Student Files\03_Link Files\c-3.txt.lnk. 2. First, let s look at the file header
Exporting Contacts and Updating the Contacts in Your New Vision Source Address
 Exporting Contacts and Updating the Contacts in Your New Vision Source Email Address How to Export Yahoo Contacts You can export your contacts from Yahoo to an external file as a backup or in preparation
Exporting Contacts and Updating the Contacts in Your New Vision Source Email Address How to Export Yahoo Contacts You can export your contacts from Yahoo to an external file as a backup or in preparation
TZWorks Windows AppCompatibility Cache Utility (wacu) Users Guide
 TZWorks Windows AppCompatibility Cache Utility (wacu) Users Guide Copyright TZWorks LLC www.tzworks.net Contact Info: info@tzworks.net Document applies to v0.34 of wacu Updated: Apr 14, 2018 Abstract wacu
TZWorks Windows AppCompatibility Cache Utility (wacu) Users Guide Copyright TZWorks LLC www.tzworks.net Contact Info: info@tzworks.net Document applies to v0.34 of wacu Updated: Apr 14, 2018 Abstract wacu
MICROSOFT OneNote 2013
 Q U I C K R E F E R E N C E G U I D E MICROSOFT OneNote 2013 Microsoft OneNote 2013 is the perfect place to gather and organize your ideas, thoughts, lists, plans, timelines, and references into one file.
Q U I C K R E F E R E N C E G U I D E MICROSOFT OneNote 2013 Microsoft OneNote 2013 is the perfect place to gather and organize your ideas, thoughts, lists, plans, timelines, and references into one file.
TZWorks Timeline ActivitiesCache Parser (tac) Users Guide
 TZWorks Timeline ActivitiesCache Parser (tac) Users Guide Abstract tac is a standalone, command-line tool that parses the Windows Timeline records introduced in the April 2018 Win10 update. The Window
TZWorks Timeline ActivitiesCache Parser (tac) Users Guide Abstract tac is a standalone, command-line tool that parses the Windows Timeline records introduced in the April 2018 Win10 update. The Window
Managing Your Website with Convert Community. My MU Health and My MU Health Nursing
 Managing Your Website with Convert Community My MU Health and My MU Health Nursing Managing Your Website with Convert Community LOGGING IN... 4 LOG IN TO CONVERT COMMUNITY... 4 LOG OFF CORRECTLY... 4 GETTING
Managing Your Website with Convert Community My MU Health and My MU Health Nursing Managing Your Website with Convert Community LOGGING IN... 4 LOG IN TO CONVERT COMMUNITY... 4 LOG OFF CORRECTLY... 4 GETTING
University of North Dakota PeopleSoft Finance Tip Sheets. Utilizing the Query Download Feature
 There is a custom feature available in Query Viewer that allows files to be created from queries and copied to a user s PC. This feature doesn t have the same size limitations as running a query to HTML
There is a custom feature available in Query Viewer that allows files to be created from queries and copied to a user s PC. This feature doesn t have the same size limitations as running a query to HTML
AccessData Forensic Toolkit 5.5 Release Notes
 AccessData Forensic Toolkit 5.5 Release Notes Document Date: 8/20/2014 2014 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
AccessData Forensic Toolkit 5.5 Release Notes Document Date: 8/20/2014 2014 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
CREATING CUSTOMER MAILING LABELS
 CREATING CUSTOMER MAILING LABELS agrē has a built-in exports to make it easy to create a data file of customer address information, but how do you turn a list of names and addresses into mailing labels?
CREATING CUSTOMER MAILING LABELS agrē has a built-in exports to make it easy to create a data file of customer address information, but how do you turn a list of names and addresses into mailing labels?
HOLLIS Library Reporting: Introduction to Cognos
 Harvard University Library Library Information Services HOLLIS Library Reporting: Introduction to Cognos Contents 1. Reporting Data... 2 2. Access the Library Reporting System... 2 a. Log on to Cognos...
Harvard University Library Library Information Services HOLLIS Library Reporting: Introduction to Cognos Contents 1. Reporting Data... 2 2. Access the Library Reporting System... 2 a. Log on to Cognos...
DOCUMENTUM D2. User Guide
 DOCUMENTUM D2 User Guide Contents 1. Groups... 6 2. Introduction to D2... 7 Access D2... 7 Recommended browsers... 7 Login... 7 First-time login... 7 Installing the Content Transfer Extension... 8 Logout...
DOCUMENTUM D2 User Guide Contents 1. Groups... 6 2. Introduction to D2... 7 Access D2... 7 Recommended browsers... 7 Login... 7 First-time login... 7 Installing the Content Transfer Extension... 8 Logout...
ADVANCED INQUIRIES IN ALBEDO: PART 2 EXCEL DATA PROCESSING INSTRUCTIONS
 ADVANCED INQUIRIES IN ALBEDO: PART 2 EXCEL DATA PROCESSING INSTRUCTIONS Once you have downloaded a MODIS subset, there are a few steps you must take before you begin analyzing the data. Directions for
ADVANCED INQUIRIES IN ALBEDO: PART 2 EXCEL DATA PROCESSING INSTRUCTIONS Once you have downloaded a MODIS subset, there are a few steps you must take before you begin analyzing the data. Directions for
Course Folder and Files Instructions for download and use
 Course Folder and Files Instructions for download and use About course folders and files Please read this page carefully! Most, but not all of our courses, at certain points in each chapter, instruct you
Course Folder and Files Instructions for download and use About course folders and files Please read this page carefully! Most, but not all of our courses, at certain points in each chapter, instruct you
Working with the Logs
 CHAPTER 3 This chapter discusses the following topics: Overview of the Tasks Viewing the Logs Sorting the Logs Filtering the Logs Saving the Log Details Clearing the Logs Using the Online and Offline Modes
CHAPTER 3 This chapter discusses the following topics: Overview of the Tasks Viewing the Logs Sorting the Logs Filtering the Logs Saving the Log Details Clearing the Logs Using the Online and Offline Modes
EXCEL BASICS: MICROSOFT OFFICE 2010
 EXCEL BASICS: MICROSOFT OFFICE 2010 GETTING STARTED PAGE 02 Prerequisites What You Will Learn USING MICROSOFT EXCEL PAGE 03 Opening Microsoft Excel Microsoft Excel Features Keyboard Review Pointer Shapes
EXCEL BASICS: MICROSOFT OFFICE 2010 GETTING STARTED PAGE 02 Prerequisites What You Will Learn USING MICROSOFT EXCEL PAGE 03 Opening Microsoft Excel Microsoft Excel Features Keyboard Review Pointer Shapes
Reference Guide. Adding a Generic File Store - Importing From a Local or Network ShipWorks Page 1 of 21
 Reference Guide Adding a Generic File Store - Importing From a Local or Network Folder Page 1 of 21 Adding a Generic File Store TABLE OF CONTENTS Background First Things First The Process Creating the
Reference Guide Adding a Generic File Store - Importing From a Local or Network Folder Page 1 of 21 Adding a Generic File Store TABLE OF CONTENTS Background First Things First The Process Creating the
Oracle Business Intelligence Icon Definitions
 Oracle Business Intelligence Icon Definitions Version 1.0 JANUARY 14, 2015 OHIO UNIVERSITY Table of Contents Icon Definitions...2 1.1 Catalog Definitions for Report Consumers (ability to run reports)...2
Oracle Business Intelligence Icon Definitions Version 1.0 JANUARY 14, 2015 OHIO UNIVERSITY Table of Contents Icon Definitions...2 1.1 Catalog Definitions for Report Consumers (ability to run reports)...2
Internet Browsers with CYBER
 Internet Browsers with CYBER Updated 5/29/2018 CYBER is an internet-based application that enables multiple users in many locations to access medical records. The application s software is powered by Microsoft
Internet Browsers with CYBER Updated 5/29/2018 CYBER is an internet-based application that enables multiple users in many locations to access medical records. The application s software is powered by Microsoft
Microsoft Office 365 includes the entire Office Suite (Word, Excel, PowerPoint, Access, Publisher, Lync, Outlook, etc ) and an OneDrive account.
 Microsoft Office 365 Contents What is Office 365?... 2 What is OneDrive?... 2 What if you already have a Microsoft Account?... 2 Download Office for FREE... 3 How to Access OneDrive... 4 Office Online...
Microsoft Office 365 Contents What is Office 365?... 2 What is OneDrive?... 2 What if you already have a Microsoft Account?... 2 Download Office for FREE... 3 How to Access OneDrive... 4 Office Online...
Promo Buddy 2.0. Internet Marketing Database Software (Manual)
 Promo Buddy 2.0 Internet Marketing Database Software (Manual) PromoBuddy has been developed by: tp:// INTRODUCTION From the computer of Detlev Reimer Dear Internet marketer, More than 6 years have passed
Promo Buddy 2.0 Internet Marketing Database Software (Manual) PromoBuddy has been developed by: tp:// INTRODUCTION From the computer of Detlev Reimer Dear Internet marketer, More than 6 years have passed
BGE s Customer Consumption Data Website Guidelines
 BGE s Customer Consumption Data Website Guidelines BGE s Customer Consumption Data Web (CDWeb) application provides gas and electricity suppliers, brokers, aggregators, third-party consultants and curtailment
BGE s Customer Consumption Data Website Guidelines BGE s Customer Consumption Data Web (CDWeb) application provides gas and electricity suppliers, brokers, aggregators, third-party consultants and curtailment
Argos Basic Training. Overview: Sign in:
 Argos Basic Training Overview: Argos is a campus reporting tool that allows end-users to access and extract information from Banner and Degree Works databases in a report format. Data Blocks are the foundation
Argos Basic Training Overview: Argos is a campus reporting tool that allows end-users to access and extract information from Banner and Degree Works databases in a report format. Data Blocks are the foundation
Introduction to Cognos
 Introduction to Cognos User Handbook 7800 E Orchard Road, Suite 280 Greenwood Village, CO 80111 Table of Contents... 3 Logging In To the Portal... 3 Understanding IBM Cognos Connection... 4 The IBM Cognos
Introduction to Cognos User Handbook 7800 E Orchard Road, Suite 280 Greenwood Village, CO 80111 Table of Contents... 3 Logging In To the Portal... 3 Understanding IBM Cognos Connection... 4 The IBM Cognos
24) Type a note then click the OK button to save the note. This is a good way to keep notes on items of interest.
 23) Click File Analysis Tab - This allows forensic investigators to look for files on the system as they would on a regular system. Key file attributes are provided to assist the investigator (file size,
23) Click File Analysis Tab - This allows forensic investigators to look for files on the system as they would on a regular system. Key file attributes are provided to assist the investigator (file size,
EXCEL BASICS: MICROSOFT OFFICE 2007
 EXCEL BASICS: MICROSOFT OFFICE 2007 GETTING STARTED PAGE 02 Prerequisites What You Will Learn USING MICROSOFT EXCEL PAGE 03 Opening Microsoft Excel Microsoft Excel Features Keyboard Review Pointer Shapes
EXCEL BASICS: MICROSOFT OFFICE 2007 GETTING STARTED PAGE 02 Prerequisites What You Will Learn USING MICROSOFT EXCEL PAGE 03 Opening Microsoft Excel Microsoft Excel Features Keyboard Review Pointer Shapes
DocumentDirect for Windows (DDW) Current version 4.4 (white screen)
 DocumentDirect for Windows (DDW) Current version 4.4 (white screen) The basics how to open, navigate and how to export & save your DocumentDirect report to excel Prepared by Kittson, Norman, Roseau Counties
DocumentDirect for Windows (DDW) Current version 4.4 (white screen) The basics how to open, navigate and how to export & save your DocumentDirect report to excel Prepared by Kittson, Norman, Roseau Counties
Contents.
 Firstbeat Lifestyle Assessment User manual September 2015 1 Contents 1. System requirements... 4 2. Getting started... 5 2.1. Adobe Flash Player software installation... 5 2.2. Logging in... 5 2.3. Home
Firstbeat Lifestyle Assessment User manual September 2015 1 Contents 1. System requirements... 4 2. Getting started... 5 2.1. Adobe Flash Player software installation... 5 2.2. Logging in... 5 2.3. Home
SSRS 2016 for WITS. Web Portal User Guide. Applies to: WITS Version 18.0+
 SSRS 2016 for WITS Web Portal User Guide Applies to: WITS Version 18.0+ Microsoft SQL Server Reporting Services (SSRS) 2016 Last Updated June 1, 2017 Microsoft SQL Server 2016 Report Builder 3.0 Version
SSRS 2016 for WITS Web Portal User Guide Applies to: WITS Version 18.0+ Microsoft SQL Server Reporting Services (SSRS) 2016 Last Updated June 1, 2017 Microsoft SQL Server 2016 Report Builder 3.0 Version
Importing a txt or csv file into ArcGIS Online [AGO]
![Importing a txt or csv file into ArcGIS Online [AGO] Importing a txt or csv file into ArcGIS Online [AGO]](/thumbs/90/101387846.jpg) Importing a txt or csv file into ArcGIS Online [AGO] Spring 2014 This is how to find addresses online and copy them into an Excel spreadsheet, save them in a format that ArcGIS can use, and then import
Importing a txt or csv file into ArcGIS Online [AGO] Spring 2014 This is how to find addresses online and copy them into an Excel spreadsheet, save them in a format that ArcGIS can use, and then import
Using Microsoft Excel
 Using Microsoft Excel Table of Contents The Excel Window... 2 The Formula Bar... 3 Workbook View Buttons... 3 Moving in a Spreadsheet... 3 Entering Data... 3 Creating and Renaming Worksheets... 4 Opening
Using Microsoft Excel Table of Contents The Excel Window... 2 The Formula Bar... 3 Workbook View Buttons... 3 Moving in a Spreadsheet... 3 Entering Data... 3 Creating and Renaming Worksheets... 4 Opening
Using vletter Handwriting Software with Mail Merge in Word 2007
 Using vletter Handwriting Software with Mail Merge in Word 2007 Q: What is Mail Merge? A: The Mail Merge feature in Microsoft Word allows you to merge an address file with a form letter in order to generate
Using vletter Handwriting Software with Mail Merge in Word 2007 Q: What is Mail Merge? A: The Mail Merge feature in Microsoft Word allows you to merge an address file with a form letter in order to generate
GOOGLE APPS. GETTING STARTED Page 02 Prerequisites What You Will Learn. INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail
 GOOGLE APPS GETTING STARTED Page 02 Prerequisites What You Will Learn INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail DRIVE Page 07 Uploading Files to Google Drive Sharing/Unsharing
GOOGLE APPS GETTING STARTED Page 02 Prerequisites What You Will Learn INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail DRIVE Page 07 Uploading Files to Google Drive Sharing/Unsharing
Excel & Business Math Video/Class Project #01 Introduction to Excel. Why We Use Excel for Math. First Formula.
 Excel & Business Math Video/Class Project #01 Introduction to Excel. Why We Use Excel for Math. First Formula. Topics Covered in Video: 1) USB Drive to store files from class... 2 2) Save As to Download
Excel & Business Math Video/Class Project #01 Introduction to Excel. Why We Use Excel for Math. First Formula. Topics Covered in Video: 1) USB Drive to store files from class... 2 2) Save As to Download
Binary Markup Toolkit Quick Start Guide Release v November 2016
 Binary Markup Toolkit Quick Start Guide Release v1.0.0.1 November 2016 Overview Binary Markup Toolkit (BMTK) is a suite of software tools for working with Binary Markup Language (BML). BMTK includes tools
Binary Markup Toolkit Quick Start Guide Release v1.0.0.1 November 2016 Overview Binary Markup Toolkit (BMTK) is a suite of software tools for working with Binary Markup Language (BML). BMTK includes tools
Managing Configurations
 CHAPTER 3 The Configurations page is your starting point for managing device configurations for network elements managed by Cisco Prime Network by using the CM tools. The following table lists the main
CHAPTER 3 The Configurations page is your starting point for managing device configurations for network elements managed by Cisco Prime Network by using the CM tools. The following table lists the main
Working with Mailings
 10 Working with Mailings An Overview of the Mail Merge Process... 202 Step 1: Setting Up the Main Document... 204 Step 2: Creating a Data Source... 205 Create a data source... 205 Customize data source
10 Working with Mailings An Overview of the Mail Merge Process... 202 Step 1: Setting Up the Main Document... 204 Step 2: Creating a Data Source... 205 Create a data source... 205 Customize data source
What is OneNote? The first time you start OneNote, it asks you to sign in. Sign in with your personal Microsoft account.
 OneNote What is OneNote? OneNote is a digital notebook. In OneNote, you can: Type notes or record audio at your laptop. Sketch or write ideas on your tablet. Add picture from your phone. Find notes instantly.
OneNote What is OneNote? OneNote is a digital notebook. In OneNote, you can: Type notes or record audio at your laptop. Sketch or write ideas on your tablet. Add picture from your phone. Find notes instantly.
Windows 8.1. Tiles come in four shapes: small, medium, wide, and large. The red outlined tiles are live tiles.
 Windows 8/8.1 was Microsoft s attempt to have one operating system for all devices desktops, laptops, phones, tablets, and everything else. Some like it more than others. Microsoft Windows 10 is supposed
Windows 8/8.1 was Microsoft s attempt to have one operating system for all devices desktops, laptops, phones, tablets, and everything else. Some like it more than others. Microsoft Windows 10 is supposed
Generating a Custom Bill of Materials
 Generating a Custom Bill of Materials Old Content - visit altium.com/documentation Modified by on 6-Nov-2013 This tutorial describes how to use the Report Manager to set up a Bill of Materials (BOM) report.
Generating a Custom Bill of Materials Old Content - visit altium.com/documentation Modified by on 6-Nov-2013 This tutorial describes how to use the Report Manager to set up a Bill of Materials (BOM) report.
Software User's Manual (UM)
 Software User's Manual (UM) The Log Angeles Community Garden Inventory and Locator Team 13 Ardalan Yousefi Cole Cecil Jeff Tonkovich Shi-Xuan Zeng (Gary) Project Manager Integrated Independent Verification
Software User's Manual (UM) The Log Angeles Community Garden Inventory and Locator Team 13 Ardalan Yousefi Cole Cecil Jeff Tonkovich Shi-Xuan Zeng (Gary) Project Manager Integrated Independent Verification
Navigating URI Planning and Budgeting
 Navigating URI Planning and Budgeting Accessing URI Planning and Budgeting 2 Accessing Planning and Budgeting Planning and Budgeting is cloud-based and can be accessed via any computer with internet access.
Navigating URI Planning and Budgeting Accessing URI Planning and Budgeting 2 Accessing Planning and Budgeting Planning and Budgeting is cloud-based and can be accessed via any computer with internet access.
Alan Davies and Sarah Perry
 Alan Davies and Sarah Perry Administering Visual Analytics Sarah Perry Agenda Topics Loading data Auditing in Visual Analytics Row level security Supporting stored processes What s new in 7.4 Copyright
Alan Davies and Sarah Perry Administering Visual Analytics Sarah Perry Agenda Topics Loading data Auditing in Visual Analytics Row level security Supporting stored processes What s new in 7.4 Copyright
Introduction to Microsoft Access 2016
 Introduction to Microsoft Access 2016 A database is a collection of information that is related. Access allows you to manage your information in one database file. Within Access there are four major objects:
Introduction to Microsoft Access 2016 A database is a collection of information that is related. Access allows you to manage your information in one database file. Within Access there are four major objects:
Armatus 2.0 Administrator Procedures
 2015 Armatus 2.0 Administrator Procedures Praesidium 2015. All rights reserved. Armatus 2.0 Administrator Procedures Overview Introduction This guide shows you how to perform tasks in Armatus 2.0 Administrator
2015 Armatus 2.0 Administrator Procedures Praesidium 2015. All rights reserved. Armatus 2.0 Administrator Procedures Overview Introduction This guide shows you how to perform tasks in Armatus 2.0 Administrator
NFER Tests Analysis Tool Frequently Asked Questions
 NFER Tests Analysis Tool Frequently Asked Questions Contents Accessing the tool... 4 How do I log in?... 4 I have forgotten my password... 4 I am unable to log in... 4 My account has been locked out, how
NFER Tests Analysis Tool Frequently Asked Questions Contents Accessing the tool... 4 How do I log in?... 4 I have forgotten my password... 4 I am unable to log in... 4 My account has been locked out, how
Importing Local Contacts from Thunderbird
 1 Importing Local Contacts from Thunderbird Step 1, Export Contacts from Thunderbird In Thunderbird, select Address Book. In the Address Book, click on Personal Address Book and then select Export from
1 Importing Local Contacts from Thunderbird Step 1, Export Contacts from Thunderbird In Thunderbird, select Address Book. In the Address Book, click on Personal Address Book and then select Export from
Switching to Sheets from Microsoft Excel Learning Center gsuite.google.com/learning-center
 Switching to Sheets from Microsoft Excel 2010 Learning Center gsuite.google.com/learning-center Welcome to Sheets Now that you've switched from Microsoft Excel to G Suite, learn how to use Google Sheets
Switching to Sheets from Microsoft Excel 2010 Learning Center gsuite.google.com/learning-center Welcome to Sheets Now that you've switched from Microsoft Excel to G Suite, learn how to use Google Sheets
Importing from Blackboard Learn Grade Center Data to Banner 9 User Learning Scenarios
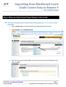 Importing from Blackboard Learn Grade Center Data to Banner 9 User Learning Scenarios Step 1: Make sure Final Grade Column Displays Letter Grade Ensure your final grade column in Grade Center has letter
Importing from Blackboard Learn Grade Center Data to Banner 9 User Learning Scenarios Step 1: Make sure Final Grade Column Displays Letter Grade Ensure your final grade column in Grade Center has letter
Use mail merge to create and print letters and other documents
 Use mail merge to create and print letters and other documents Contents Use mail merge to create and print letters and other documents... 1 Set up the main document... 1 Connect the document to a data
Use mail merge to create and print letters and other documents Contents Use mail merge to create and print letters and other documents... 1 Set up the main document... 1 Connect the document to a data
Microsoft Word 2010 Introduction to Mail Merge
 Microsoft Word 2010 Introduction to Mail Merge Elizabeth Wells February 2012 Copyright 2012 ElizabethWells All rights reserved. Except as permitted under current legislation, no part of this work may be
Microsoft Word 2010 Introduction to Mail Merge Elizabeth Wells February 2012 Copyright 2012 ElizabethWells All rights reserved. Except as permitted under current legislation, no part of this work may be
Page Topic 02 Log In to KidKare 02 Using the Navigation Menu 02 Change the Language
 Page Topic 02 Log In to KidKare 02 Using the Navigation Menu 02 Change the Language help.kidkare.com 03 Enroll a Child 03 Withdraw a Child 03 View Pending and Withdrawn Children 04 View Kids by Enrollment
Page Topic 02 Log In to KidKare 02 Using the Navigation Menu 02 Change the Language help.kidkare.com 03 Enroll a Child 03 Withdraw a Child 03 View Pending and Withdrawn Children 04 View Kids by Enrollment
How to view details for your project and view the project map
 Tutorial How to view details for your project and view the project map Objectives This tutorial shows how to access EPANET model details and visualize model results using the Map page. Prerequisites Login
Tutorial How to view details for your project and view the project map Objectives This tutorial shows how to access EPANET model details and visualize model results using the Map page. Prerequisites Login
Event Manager Instructor Start-Up Guide
 Event Manager Instructor Start-Up Guide Table of Contents Introduction... 3 What s Included in This Guide... 3 Learning Computer Terms... 3 What Is a Brower?... 3 What Is the Address Bar?... 4 What Is
Event Manager Instructor Start-Up Guide Table of Contents Introduction... 3 What s Included in This Guide... 3 Learning Computer Terms... 3 What Is a Brower?... 3 What Is the Address Bar?... 4 What Is
OBIEE. Oracle Business Intelligence Enterprise Edition. Rensselaer Business Intelligence Finance Author Training
 OBIEE Oracle Business Intelligence Enterprise Edition Rensselaer Business Intelligence Finance Author Training TABLE OF CONTENTS INTRODUCTION... 1 USER INTERFACE... 1 HOW TO LAUNCH OBIEE... 1 TERMINOLOGY...
OBIEE Oracle Business Intelligence Enterprise Edition Rensselaer Business Intelligence Finance Author Training TABLE OF CONTENTS INTRODUCTION... 1 USER INTERFACE... 1 HOW TO LAUNCH OBIEE... 1 TERMINOLOGY...
Identifying Updated Metadata and Images from a Content Provider
 University of Iowa Libraries Staff Publications 4-8-2010 Identifying Updated Metadata and Images from a Content Provider Wendy Robertson University of Iowa 2010 Wendy C Robertson Comments Includes presenter's
University of Iowa Libraries Staff Publications 4-8-2010 Identifying Updated Metadata and Images from a Content Provider Wendy Robertson University of Iowa 2010 Wendy C Robertson Comments Includes presenter's
Parish . User Manual
 Parish Email User Manual Table of Contents LOGGING IN TO PARISH EMAIL... 3 GETTING STARTED... 3 GENERAL OVERVIEW OF THE USER INTERFACE... 3 TERMINATE THE SESSION... 4 EMAIL... 4 MESSAGES LIST... 4 Open
Parish Email User Manual Table of Contents LOGGING IN TO PARISH EMAIL... 3 GETTING STARTED... 3 GENERAL OVERVIEW OF THE USER INTERFACE... 3 TERMINATE THE SESSION... 4 EMAIL... 4 MESSAGES LIST... 4 Open
A+ Guide to Managing & Maintaining Your PC, 8th Edition. Chapter 3 Introducing Windows Operating Systems
 Chapter 3 Introducing Windows Operating Systems Objectives Learn how to use Windows to interface with users, files and folders, applications, and hardware Learn about some Windows tools that you can use
Chapter 3 Introducing Windows Operating Systems Objectives Learn how to use Windows to interface with users, files and folders, applications, and hardware Learn about some Windows tools that you can use
TurningPoint AnyWhere
 TurningPoint AnyWhere TurningPoint Blackboard Registration Tool Making the Tool Available 1. From the Control Panel, select click Customization >>Tool Availability. 2. From the Tools list, check Registration
TurningPoint AnyWhere TurningPoint Blackboard Registration Tool Making the Tool Available 1. From the Control Panel, select click Customization >>Tool Availability. 2. From the Tools list, check Registration
File Management Tutorial
 Just a reminder... Files: any individual item on your computer that contains data. E.g. document, photo, spreadsheet, email, PowerPoint, etc. File Management Tutorial Folders: containers for your files
Just a reminder... Files: any individual item on your computer that contains data. E.g. document, photo, spreadsheet, email, PowerPoint, etc. File Management Tutorial Folders: containers for your files
The following instructions cover how to edit an existing report in IBM Cognos Analytics.
 IBM Cognos Analytics Edit a Report The following instructions cover how to edit an existing report in IBM Cognos Analytics. Navigate to Cognos Cognos Analytics supports all browsers with the exception
IBM Cognos Analytics Edit a Report The following instructions cover how to edit an existing report in IBM Cognos Analytics. Navigate to Cognos Cognos Analytics supports all browsers with the exception
UPLOADING AN IMAGE TO FACEBOOK AND MAKING IT YOUR PROFILE PICTURE
 UPLOADING AN IMAGE TO FACEBOOK AND MAKING IT YOUR PROFILE PICTURE PART 1: UPLOADING AN IMAGE TO FACEBOOK 1. Open your web browser. This will most likely be Internet Explorer, Mozilla Firefox, Google Chrome
UPLOADING AN IMAGE TO FACEBOOK AND MAKING IT YOUR PROFILE PICTURE PART 1: UPLOADING AN IMAGE TO FACEBOOK 1. Open your web browser. This will most likely be Internet Explorer, Mozilla Firefox, Google Chrome
AccessData AD Lab Release Notes
 AccessData AD Lab 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues for this
AccessData AD Lab 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues for this
PART 7. Getting Started with Excel
 PART 7 Getting ed with Excel When you start the application, Excel displays a blank workbook. A workbook is a file in which you store your data, similar to a three-ring binder. Within a workbook are worksheets,
PART 7 Getting ed with Excel When you start the application, Excel displays a blank workbook. A workbook is a file in which you store your data, similar to a three-ring binder. Within a workbook are worksheets,
Team-Fit Console - Navigation & Performing Actions
 Team-Fit Console - Navigation & Performing Actions 1. Navigation Tabs - page 2 2. Changing Column View - page 3 3. Actions - page 4 4. Viewing Reports - page 4 5. Navigating & Printing Reports on Various
Team-Fit Console - Navigation & Performing Actions 1. Navigation Tabs - page 2 2. Changing Column View - page 3 3. Actions - page 4 4. Viewing Reports - page 4 5. Navigating & Printing Reports on Various
Computer Basics: Step-by-Step Guide (Session 2)
 Table of Contents Computer Basics: Step-by-Step Guide (Session 2) ABOUT PROGRAMS AND OPERATING SYSTEMS... 2 THE WINDOWS 7 DESKTOP... 3 TWO WAYS TO OPEN A PROGRAM... 4 DESKTOP ICON... 4 START MENU... 5
Table of Contents Computer Basics: Step-by-Step Guide (Session 2) ABOUT PROGRAMS AND OPERATING SYSTEMS... 2 THE WINDOWS 7 DESKTOP... 3 TWO WAYS TO OPEN A PROGRAM... 4 DESKTOP ICON... 4 START MENU... 5
Frequently Asked Questions Table of Contents
 Frequently Asked Questions Table of Contents What is my user name and password?... 3 How do I change my Password?... 3 How do I set up a view?... 3 How do I load a photo to a listing?... 3 How do I run
Frequently Asked Questions Table of Contents What is my user name and password?... 3 How do I change my Password?... 3 How do I set up a view?... 3 How do I load a photo to a listing?... 3 How do I run
Download Instructions
 Download Instructions The download page provides several options for importing data back into your applications. The Excel template will automatically format the data within the commadelimited file. The
Download Instructions The download page provides several options for importing data back into your applications. The Excel template will automatically format the data within the commadelimited file. The
OBIEE. Oracle Business Intelligence Enterprise Edition. Rensselaer Business Intelligence Position Control
 OBIEE Oracle Business Intelligence Enterprise Edition Rensselaer Business Intelligence Position Control TABLE OF CONTENTS INTRODUCTION... 1 USER INTERFACE... 1 HOW TO LAUNCH OBIEE... 1 HOW TO NAVIGATE...
OBIEE Oracle Business Intelligence Enterprise Edition Rensselaer Business Intelligence Position Control TABLE OF CONTENTS INTRODUCTION... 1 USER INTERFACE... 1 HOW TO LAUNCH OBIEE... 1 HOW TO NAVIGATE...
17 - VARIABLES... 1 DOCUMENT AND CODE VARIABLES IN MAXQDA Document Variables Code Variables... 1
 17 - Variables Contents 17 - VARIABLES... 1 DOCUMENT AND CODE VARIABLES IN MAXQDA... 1 Document Variables... 1 Code Variables... 1 The List of document variables and the List of code variables... 1 Managing
17 - Variables Contents 17 - VARIABLES... 1 DOCUMENT AND CODE VARIABLES IN MAXQDA... 1 Document Variables... 1 Code Variables... 1 The List of document variables and the List of code variables... 1 Managing
MyOffice Employee. User Guide Release 4.1
 MyOffice Employee User Guide Release 4.1 Copyright 1996-2014 Sigma Systems Canada Inc. Last Revision: 2015-06-05 Sigma Systems Canada Inc., Toronto, ON, Canada The Programs (which include both the software
MyOffice Employee User Guide Release 4.1 Copyright 1996-2014 Sigma Systems Canada Inc. Last Revision: 2015-06-05 Sigma Systems Canada Inc., Toronto, ON, Canada The Programs (which include both the software
Highline College Busn 216: Computer Applications for Business (Fun and Power with Computers) Office 2016 Video #12: PowerPoint
 Highline College Busn 216: Computer Applications for Business (Fun and Power with Computers) Topics Covered in Video: Office 2016 Video #12: PowerPoint 1) Open PowerPoint 2) Save As with Name Busn 216
Highline College Busn 216: Computer Applications for Business (Fun and Power with Computers) Topics Covered in Video: Office 2016 Video #12: PowerPoint 1) Open PowerPoint 2) Save As with Name Busn 216
HOW TO USE THE EXPORT FEATURE IN LCL
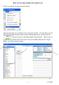 HOW TO USE THE EXPORT FEATURE IN LCL In LCL go to the Go To menu and select Export. Select the items that you would like to have exported to the file. To select them you will click the item in the left
HOW TO USE THE EXPORT FEATURE IN LCL In LCL go to the Go To menu and select Export. Select the items that you would like to have exported to the file. To select them you will click the item in the left
Searching and Favorites in Datatel Web UI 4.3
 Searching and Favorites in Datatel Web UI 4.3 Search Field The Search field uses icons and text prompts (see Figure 1) to switch between Person Search and Form Search. You can click the icon to the left
Searching and Favorites in Datatel Web UI 4.3 Search Field The Search field uses icons and text prompts (see Figure 1) to switch between Person Search and Form Search. You can click the icon to the left
AFFILIATE FAQ: CNN NEWSOURCE UPGRADED VIDEO INTERFACE Updated July 7, 2015
 AFFILIATE FAQ: CNN NEWSOURCE UPGRADED VIDEO INTERFACE Updated July 7, 2015 The Big Picture Q: What is this about? *Updated* On July 11 th 2015, CNN Newsource will debut a new video experience. Clients
AFFILIATE FAQ: CNN NEWSOURCE UPGRADED VIDEO INTERFACE Updated July 7, 2015 The Big Picture Q: What is this about? *Updated* On July 11 th 2015, CNN Newsource will debut a new video experience. Clients
Personal Directory PC Utility Reference Guide
 Introduction The PC Utility provides a fast, easy way to create or modify a for an M3904 or M3905 Series Digital Telephone. You can enter names and numbers into a file on your PC, and download (Program)
Introduction The PC Utility provides a fast, easy way to create or modify a for an M3904 or M3905 Series Digital Telephone. You can enter names and numbers into a file on your PC, and download (Program)
Paraben s Voice Logger. v User Manual
 Paraben s Voice Logger v. 1.0 User Manual Contents About Paraben s Voice Logger for Windows... 3 What s New!... 3 Getting Started... 4 System Requirements... 4 How to Use Voice Logger... 4 How to Register
Paraben s Voice Logger v. 1.0 User Manual Contents About Paraben s Voice Logger for Windows... 3 What s New!... 3 Getting Started... 4 System Requirements... 4 How to Use Voice Logger... 4 How to Register
Primo Analytics Workshop. BIBSYS Konferansen 20 March 2018
 Primo Analytics Workshop BIBSYS Konferansen 20 March 2018 Objectives By the end of this session, you will: Understand what is Primo Analytics and OBI. Have a high-level view of how Primo Analytics is working.
Primo Analytics Workshop BIBSYS Konferansen 20 March 2018 Objectives By the end of this session, you will: Understand what is Primo Analytics and OBI. Have a high-level view of how Primo Analytics is working.
Info Input Express Network Edition
 Info Input Express Network Edition Administrator s Guide A-61892 Table of Contents Using Info Input Express to Create and Retrieve Documents... 9 Compatibility... 9 Contents of this Guide... 9 Terminology...
Info Input Express Network Edition Administrator s Guide A-61892 Table of Contents Using Info Input Express to Create and Retrieve Documents... 9 Compatibility... 9 Contents of this Guide... 9 Terminology...
OWA Basics (Outlook Web Access - Application) How To The Basics
 OWA Basics (Outlook Web Access - Application) How To The Basics OWA Access: https://owa.wusd.k12.ca.us WUSD Technology Services This document has instructions for logging into Outlook Web Application (OWA)
OWA Basics (Outlook Web Access - Application) How To The Basics OWA Access: https://owa.wusd.k12.ca.us WUSD Technology Services This document has instructions for logging into Outlook Web Application (OWA)
Creating a Recording in Canvas Embedding a Recording in Canvas To embed a recording into a discussion
 Table of Contents What is Kaltura... 3 Things to Remember... 3 My Media... 3 To access My Media... 3 Upload Media... 4 To perform a media upload... 4 Viewing Videos... 6 Add New List Options... 6 Media
Table of Contents What is Kaltura... 3 Things to Remember... 3 My Media... 3 To access My Media... 3 Upload Media... 4 To perform a media upload... 4 Viewing Videos... 6 Add New List Options... 6 Media
Running PeopleSoft Query Viewer and Running Query to Excel Basic Steps
 Running PeopleSoft Query Viewer and Running Query to Excel Basic Steps Query Viewer enables you to: Search for a query using the basic or advanced search functions. Run a query (which displays results
Running PeopleSoft Query Viewer and Running Query to Excel Basic Steps Query Viewer enables you to: Search for a query using the basic or advanced search functions. Run a query (which displays results
Web Client User Guide
 ImageTag, Inc. 2016 Contents Introduction... 2 Logging Into Your KwikTag Client... 3 KwikTag Tabs and Your Landing Page... 4 Drawers Tab Features and Functions... 7 My Lists... 7 The KwikTag Library...
ImageTag, Inc. 2016 Contents Introduction... 2 Logging Into Your KwikTag Client... 3 KwikTag Tabs and Your Landing Page... 4 Drawers Tab Features and Functions... 7 My Lists... 7 The KwikTag Library...
WinFlexOne - Importer MHM Resources LLC
 WinFlexOne - Importer 2008 MHM Resources LLC WinFlexOne Importer - Employee 2 This module provides: Overview Log In Source File Importer Profile Download Activate Import Source File WinFlexOne Importer
WinFlexOne - Importer 2008 MHM Resources LLC WinFlexOne Importer - Employee 2 This module provides: Overview Log In Source File Importer Profile Download Activate Import Source File WinFlexOne Importer
AccessData Forensic Toolkit Release Notes
 AccessData Forensic Toolkit 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
AccessData Forensic Toolkit 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
Mini Guide. Lite. Citeline Edition. BizInt Smart Charts Lite Citeline Edition. Using BizInt Smart Charts Lite
 Lite Citeline Edition Mini Guide BizInt Smart Charts Lite - Citeline Edition is a Citeline-only version of BizInt Smart Charts Drug Development Suite to help you create, customize and distribute tabular
Lite Citeline Edition Mini Guide BizInt Smart Charts Lite - Citeline Edition is a Citeline-only version of BizInt Smart Charts Drug Development Suite to help you create, customize and distribute tabular
