Security Task Manager User Guide
|
|
|
- Johnathan Woods
- 5 years ago
- Views:
Transcription
1 Security Task Manager User Guide Enhanced Process Viewer with security risk rating A. & M. Neuber Software GmbH
2 2 Security Task Manager Table of Contents Part I Features of Security Task Manager 4 Part II Using Security Task Manager Overview... 6 Viewing process details... 7 Learning more about a process (Google search)... 7 Ending a process... 7 Using quarantine folder... 8 Printing process list... 8 Exporting process list... 8 Writing a comment... 8 Checking Hosts file changes... 9 Changing the language Part III Basics Risk Rating of processes Process types Uninstalling Part IV Protecting your computer with SpyProtector Delete traces of your Internet and computer activity Disable keyboard monitoring Disable other monitoring Warning when registry is changed Index 15
3 Features of Security Task Manager Part I
4 4 Security Task Manager I. Features of Security Task Manager Security Task Manager provides advanced information about programs and processes running on the computer. For each process it shows the following information not shown in Windows Task Manger: security risk rating virus scan with 40 anti-virus engines file name and folder path description start time CPU usage graph program icon contained hidden functions (keyboard monitoring, Browser supervision, manipulation) process type (visible window, systray program, DLL, IE-Plugin, service) The Security Task Manager also recognizes virtual driver software, services, BHO or processes hidden from the Windows Task Manager.
5 Using Security Task Manager Part II
6 6 Security Task Manager II. Using Security Task Manager Overview Security Task Manager shows all active processes on your computer. The Rating tells you all relevant security functions a process contains. The listed processes can be sorted by the following properties. Click on View menu to chose, which properties are shown: Name Rating Process ID (PID) CPU and Memory Active runtime File Type Start Title and Description Company and Product Click a process to obtain more information about the process. You can: see properties end process place process in quarantine Click Show system processes button to see all internal Windows operating system processes. Windows system processes are not shown by default. When you are logged on to Windows with a standard user account, perhaps you see for some system processes: <taskeng.exe - Services - Access denied> Please run Secu rity Tas k M an ager as Administrator in this case: Right-mouse click the Secu rity Tas k M an ager icon. Then click Run as administrator. Viewing process details Click on a process to see more information about this process. Follwing properties are shown: Name Rating Company Description Type Start File Comment Receive further information or stop the process: Information from the Internet about a process Ending process
7 Using Security Task Manager 7 Putting in quarantine Learning more about a process (Google search) 1 Click on the process you want to examine. 2 Click Google button on tool bar. An information web page is displayed on where you can submit your opinion about this software/driver software, or read other user comments. You can also search for further information about this process at Google.com. Your Internet browser transmits information (e.g. operating system, language setting). Neither the Security Task Manager program nor any of its components connect to the Internet directly. Google.com is one of the most commonly used search engines, and will provide you with relevant results. Ending a process 1 Click on a process you want to close. 2 Click the button Remove. 3 Then select one of following options: End process Move file to quarantine Uninstall Ending a process can cause system instability, including crashes. Software that needed Adware programs could not work. Please save opened documents. You can create a restore point, to can restore your Windows system at any time. You need administrator rights for this dialog. To start Security Task Manager with administrator rights, please right-mouse click the Security Task Manager shortcut. Then click Run as... Using quarantine folder The quarantine folder works like the Windows Recycle Bin (trash). When you put a file into quarantine folder, the file is renamed and moved to an isolated folder. Corresponding Autostart keys in the Windows registry are deleted so the process cannot be started again. Restoring the whole process is possible at any time: Restoring processes 1 Click quarantine button on tool bar. 2 In the quarantine folder click on process you want to restore. 3 Click Restore button. You can create a Windows restore point in the system at any time. Remove dialog, to restore your Windows
8 8 Security Task Manager Printing process list 1 On File menu click Print. 2 Chose a printer and make any necessary settings (e.g. duplex print). Click Show system processes button to see all Windows internal processes. Then you can print Windows processes too. Windows system processes are not shown by default. Exporting process list 1 On File menu click Export to. 2 Chose a file type: Text file (*.txt) Website (*.html) Click Show system processes button to see also all Windows internal processes. Then you be able to save Windows processes too. Windows system processes are not shown by default. Please save the process list from time to time. A saved process list can serve as a point of comparison to help you find new processes in the future. Writing a comment You can record a remark about each process, which will be visible in the process properties. You can vote the process to change the Security Task Manager Rating. To write a comment 1 Right mouse click a process you want. 2 Click Comment... on the appearing context menu. 3 Enter you comment and your opinion about the process. Checking Hosts file changes The Windows hosts file is located in c:\windows\system32\drivers\etc folder by default. This text file contains the mappings of IP addresses to Internet domain names (e.g. If the hosts file was changed without your knowledge, there could be a malware which redirects websites (e.g. from banks, antivirus companies) to fake web pages. You can edit the hosts file with Windows notepad. To deactivate a redirection, simply delete the line. The h os ts file replaces DNS (Domain Name Service). The lm h os ts file in the same folder replaces WINS, which IP addresses to computers in your LAN network.
9 Using Security Task Manager 9 Changing the language Security Task Manager recognizes the used language (English, Deutsch, Espanol,...) automatically. To change the language do the following: 1. On View menu click Language 2. Then click the language you want. The software can easily be translated to any language. Simply translate the lgs_english.txt text file in the program's folder, and send it to. You will receive a free registration for your translation. Um die deutsch Sprache einzustellen, klicken Sie hier.
10 Basics Part III
11 Basics 11 III. Basics Risk Rating of processes Security Task Manager uses objective criteria to judge the safety risk of a process. Security Task Manager examines the process to determine if it contains critical function calls or suspicious properties. Points are allocated depending on the potential danger of these functions and properties. The sum of the points results in the Security Task Manager Risk Rating (0 to 100 points). Security Task Manager examines the processes looking for the following functionalities (sorting by dangerousness): Able to record keyboard inputs Hidden stealth process File is hidden Keyboard driver, could record inputs Could manipulate other programs Able to monitor Internet browser Starts when starting of programs Listen on port Send to port unknown program listens or sends Monitor program starts Window not visible Start when Windows starts No detailed description available Unknown file in Windows folder No Windows system file No description of the program functions: Internet, monitor, record inputs, hide, manipulate functions: not determinable Unknown company Trusted properties (reduces risk): Microsoft signed file Verisign signed file Belongs to Certified by Own comment Click on an above property to learn more about this. Highly rated programs are not always dangerous; they may just contain properties typical of
12 12 Security Task Manager some known spyware programs. Click the Show system processes button to see all internal Windows operating system processes. Windows system processes are not shown by default. Process types Security Task Manager distinguishes between the following types of processes. Click Type on View menu, to see or hide the type as column in the main window. Software DLL files Program Taskbar icon DLL ShellExecute Internet PlugIns Browser Helpers Objects Driver and Services device driver file driver Service (own process) Service (own process with desktop interaction) Service (shares process) Service (shares process with desktop interaction) Click on an above type to learn more about this. Click the Show system processes button to see all internal Windows operating system processes. Windows system processes are not shown by default. Uninstalling 1 Click Start-Settings-Control panel. 2 Click Software. 3 Click the Remove button to delete Security Task Manager from your Computer. You can also run uninstal.exe in the Security Task Manager directory
13 Protecting your computer with SpyProtector Part IV
14 14 Security Task Manager IV. Protecting your computer with SpyProtector Delete traces of your Internet and computer activity SpyProtector contains following tools to protect your computer from keylogger, spyware and trojans: Delete history Check this option to eliminate traces of Internet activities (cookies, cache, history, typed URLs) in Internet Explorer. You can also delete the recently used file list of programs (Word, ACDSee, PDF, WinZip, Mediaplayer, etc) and the recently used program list on the Windows Start menu. Block keyboard monitoring Check this option to block the redirection of all keyboard inputs to a keylogger for the current Windows session. Keyboard redirection is realized by programing a Hook function; even keyboard utilities like macro and autotext programs don't use these malicious Hook functions. Block other monitoring Check these options to block programs which log data for the current Windows session: Keyboard inputs (indirect): This prevents monitoring of internal Windows messages (e.g. keyboard inputs) by other programs. Mouse activities: This prevents monitoring of mouse movements and mouse clicks Macro: This prevents recording of user activities. This methode, often used by macro programs, is not typically used by keyloggers. Starting and ending of programs: Program starts and stops are logged. This function is frequently used by tutorial programs (computer based training) to aid user interaction with the software. Attention: Some safe and valid programs (e.g. some Macro programs) do use these Hook functions. If one of your programs stops working after selecting an option above, please deselect the option or restart your computer. Warn when your registry is changed Check this option to see a warning message when any program tries to create an autostart key in the Windows registry. Many dangerous programs use an autostart key in the Registry to activate themselves.
15 Index 15 Index - A - active runtime 6 - B - BHO 12 Browser Helpers Objects 12 - C - comment 8 CPU 6 - D - DLL 12 driver 12 - E - end process 7 export to 8 - F - file 11 folder 7 - G - Google search 7 - H - hosts file 8 - I - information about processes 6 Internet delete traces 14 looking for info about process 7 - K - process Type 12 keyboard 11, 14 keylogger 14 - L - language change 9 - M - memory 6 monitoring 11, 14 - N O - Overview 4 - P - PID 6 prevent surveilance 14 print 8 process comment 8 end 7 print 8 properties 6 rating 11 types 12 Program 12 properties of processes 6 - Q - quarantine 7 - R - rating 11 Registry Warner 14
16 16 Security Task Manager remark 8 risk of process 11 - S - save export 8 print 8 Security Task Manager Features 4 How to use 6 uninstalling 12 service 12 SpyProtector 14 start 6 - T - task 6 Taskicon 12 title 6 Type 12 - U - uninstall 12 - W - web information 7
Internet Security Application Control
 Internet Security 2012 Application Control Table of Contents Application Control... 2 What is Application Control... 2 Operational algorithm of Application Control... 2 Enabling/disabling Application Control...
Internet Security 2012 Application Control Table of Contents Application Control... 2 What is Application Control... 2 Operational algorithm of Application Control... 2 Enabling/disabling Application Control...
Avira Ultimate Protection Suite. Short guide
 Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
Manual Removal Norton Internet Security Won't Open Or
 Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Remove Manually Norton Internet Security 2012 Will Not Start
 Remove Manually Norton Internet Security 2012 Will Not Start Restart your computer to check if you can start your Norton product. I cannot connect to the Internet My Norton product does not work or displays
Remove Manually Norton Internet Security 2012 Will Not Start Restart your computer to check if you can start your Norton product. I cannot connect to the Internet My Norton product does not work or displays
Zillya Internet Security User Guide
 Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
Avira Premium Security Suite User Manual
 Avira Premium Security Suite User Manual Trademarks and Copyright Trademarks AntiVir is a registered trademark of Avira GmbH. Windows is a registered trademark of the Microsoft Corporation in the United
Avira Premium Security Suite User Manual Trademarks and Copyright Trademarks AntiVir is a registered trademark of Avira GmbH. Windows is a registered trademark of the Microsoft Corporation in the United
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
Server Edition USER MANUAL. For Microsoft Windows
 Server Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft Windows
Server Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft Windows
Ad-Aware. Anniversary Edition. User Manual
 Ad-Aware Anniversary Edition User Manual Table of Contents What Is Ad-Aware Anniversary Edition? 1 Ad-Aware Anniversary Edition Features 2 System Requirements 4 Install Ad-Aware 5 Registering Your Product
Ad-Aware Anniversary Edition User Manual Table of Contents What Is Ad-Aware Anniversary Edition? 1 Ad-Aware Anniversary Edition Features 2 System Requirements 4 Install Ad-Aware 5 Registering Your Product
CleanMyPC User Guide
 CleanMyPC User Guide Copyright 2017 MacPaw Inc. All rights reserved. macpaw.com CONTENTS Overview 3 About CleanMyPC... 3 System requirements... 3 Download and installation 4 Activation and license reset
CleanMyPC User Guide Copyright 2017 MacPaw Inc. All rights reserved. macpaw.com CONTENTS Overview 3 About CleanMyPC... 3 System requirements... 3 Download and installation 4 Activation and license reset
SICAT SUITE VERSION 1.1. Instructions for use English
 SICAT SUITE VERSION 1.1 Instructions for use English TABLE OF CONTENTS TABLE OF CONTENTS 1 Used icons and highlighting... 4 2 Safety information... 5 2.1 Identification of danger levels... 6 2.2 Qualification
SICAT SUITE VERSION 1.1 Instructions for use English TABLE OF CONTENTS TABLE OF CONTENTS 1 Used icons and highlighting... 4 2 Safety information... 5 2.1 Identification of danger levels... 6 2.2 Qualification
Quick Heal AntiVirus Pro. Tough on malware, light on your PC.
 Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
How To Remove Virus From Windows OS
 9/30/2018 How To Remove Virus From Windows OS Detailed Instructions To Remove Virus From Your MAC OS Step 1. Ending Process Running Under The Ac tivity Monitor 1. Type Activity Monitor in the Launchpad
9/30/2018 How To Remove Virus From Windows OS Detailed Instructions To Remove Virus From Your MAC OS Step 1. Ending Process Running Under The Ac tivity Monitor 1. Type Activity Monitor in the Launchpad
VI-CENTER EXTENDED ENTERPRISE EDITION GETTING STARTED GUIDE. Version: 4.5
 VI-CENTER EXTENDED ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron VI-Center to configure and manage virtual
VI-CENTER EXTENDED ENTERPRISE EDITION GETTING STARTED GUIDE This manual provides a quick introduction to Virtual Iron software, and explains how to use Virtual Iron VI-Center to configure and manage virtual
BackupVault Desktop & Laptop Edition. USER MANUAL For Microsoft Windows
 BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
FIREFOX MENU REFERENCE This menu reference is available in a prettier format at
 FIREFOX MENU REFERENCE This menu reference is available in a prettier format at http://support.mozilla.com/en-us/kb/menu+reference FILE New Window New Tab Open Location Open File Close (Window) Close Tab
FIREFOX MENU REFERENCE This menu reference is available in a prettier format at http://support.mozilla.com/en-us/kb/menu+reference FILE New Window New Tab Open Location Open File Close (Window) Close Tab
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 7 Fixing Windows Problems
 : Managing, Maintaining, and Troubleshooting, 5e Chapter 7 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
: Managing, Maintaining, and Troubleshooting, 5e Chapter 7 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
1 - The Windows XP Desktop
 1 - The Windows XP Desktop Above in fig 1.1 you can see an example of the Windows XP desktop, when you first switch on your machine and Windows XP loads it usually looks similar to that shown in our example,
1 - The Windows XP Desktop Above in fig 1.1 you can see an example of the Windows XP desktop, when you first switch on your machine and Windows XP loads it usually looks similar to that shown in our example,
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version 1.1.122415 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie...
rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version 1.1.122415 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie...
Guardian Total Security User Guide
 Guardian Total Security User Guide Guardian Total Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
Guardian Total Security User Guide Guardian Total Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
Single Product Review. escan Internet Security 11. Language: English September 2010 Last revision: 13 nd October
 Single Product Review escan Internet Security 11 Language: English September 2010 Last revision: 13 nd October 2010-1 - Content Downloading and installing the trial version... 3 Post-installation... 4
Single Product Review escan Internet Security 11 Language: English September 2010 Last revision: 13 nd October 2010-1 - Content Downloading and installing the trial version... 3 Post-installation... 4
ANNOYING COMPUTER PROBLEMS
 ANNOYING COMPUTER PROBLEMS And their solution Before you do this to your computer read this information. Feel free to print it out. This will make it easier to reference. Table of Contents 1. Computer
ANNOYING COMPUTER PROBLEMS And their solution Before you do this to your computer read this information. Feel free to print it out. This will make it easier to reference. Table of Contents 1. Computer
VMware Horizon Client for Chrome OS User Guide. 04 JAN 2018 VMware Horizon Client for Chrome OS 4.7
 VMware Horizon Client for Chrome OS User Guide 04 JAN 2018 VMware Horizon Client for Chrome OS 4.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Horizon Client for Chrome OS User Guide 04 JAN 2018 VMware Horizon Client for Chrome OS 4.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
A+ Guide to Managing and Maintaining Your PC, 7e. Chapter 16 Fixing Windows Problems
 A+ Guide to Managing and Maintaining Your PC, 7e Chapter 16 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
A+ Guide to Managing and Maintaining Your PC, 7e Chapter 16 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
Preparatory steps before you begin
 Preparatory steps before you begin If the course comes on a CD-ROM / DVD-ROM If your course is on a CD-ROM, it might be easiest to copy its entire content, i.e., the folder containing the course, to your
Preparatory steps before you begin If the course comes on a CD-ROM / DVD-ROM If your course is on a CD-ROM, it might be easiest to copy its entire content, i.e., the folder containing the course, to your
Manage Add Ons Internet Explorer 8 Registry
 Manage Add Ons Internet Explorer 8 Registry How to disable Internet Explorer 8 add-ons and toolbars in Windows XP, Vista If you do not see Information Bar, click Tools menu and select Manage Add-ons. So
Manage Add Ons Internet Explorer 8 Registry How to disable Internet Explorer 8 add-ons and toolbars in Windows XP, Vista If you do not see Information Bar, click Tools menu and select Manage Add-ons. So
User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
Open Task Manager Windows Xp Without Ctrl Alt Del
 Open Task Manager Windows Xp Without Ctrl Alt Del if YOU use ctrl alt del to get into task manager and start exlporer.exe but it still doesn't show. Describes all the possible ways to open the Task Manager
Open Task Manager Windows Xp Without Ctrl Alt Del if YOU use ctrl alt del to get into task manager and start exlporer.exe but it still doesn't show. Describes all the possible ways to open the Task Manager
Real Fast PC. Real Fast PC Win 7.
 Real Fast PC Win 7 www.realfastpc.com 1 Real Fast PC Win 7 Disclaimer: Please note that while every effort is made to ensure that the information provided in this ebook is up to date, effective, and useful,
Real Fast PC Win 7 www.realfastpc.com 1 Real Fast PC Win 7 Disclaimer: Please note that while every effort is made to ensure that the information provided in this ebook is up to date, effective, and useful,
COPYRIGHTED MATERIAL. Contents. Part I: The Basics in Depth 1. Chapter 1: Windows Attacks 3. Chapter 2: Conventional and Unconventional Defenses 51
 Acknowledgments Introduction Part I: The Basics in Depth 1 Chapter 1: Windows Attacks 3 Attack Classes 3 Automated versus Dedicated Attacker 4 Remote versus Local 7 Types of Attacks 8 Dedicated Manual
Acknowledgments Introduction Part I: The Basics in Depth 1 Chapter 1: Windows Attacks 3 Attack Classes 3 Automated versus Dedicated Attacker 4 Remote versus Local 7 Types of Attacks 8 Dedicated Manual
How To Remove Virus Without Antivirus In >>>CLICK HERE<<<
 How To Remove Virus Without Antivirus In Windows 7 Pdf Remove virus without antivirus, Here I have all necessary things and also I have steps to Few Effective Steps To Remove Virus Without Antivirus In
How To Remove Virus Without Antivirus In Windows 7 Pdf Remove virus without antivirus, Here I have all necessary things and also I have steps to Few Effective Steps To Remove Virus Without Antivirus In
Trend Micro. Apex One as a Service / Apex One. Best Practice Guide for Malware Protection. 1 Best Practice Guide Apex One as a Service / Apex Central
 Trend Micro Apex One as a Service / Apex One Best Practice Guide for Malware Protection 1 Best Practice Guide Apex One as a Service / Apex Central Information in this document is subject to change without
Trend Micro Apex One as a Service / Apex One Best Practice Guide for Malware Protection 1 Best Practice Guide Apex One as a Service / Apex Central Information in this document is subject to change without
Comodo Antivirus Software Version 2.2
 Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
KNOXPLANS for New Users
 KNOXPLANS for New Users Version 9.1, October 2018 Contents KNOXPLANS for New Users... 1 Welcome to KnoxPlans, Version 9.1... 2 Recommended Client Hardware and O/S Specifications... 2 Browser Requirements...
KNOXPLANS for New Users Version 9.1, October 2018 Contents KNOXPLANS for New Users... 1 Welcome to KnoxPlans, Version 9.1... 2 Recommended Client Hardware and O/S Specifications... 2 Browser Requirements...
NetMan Desktop Manager Quick-Start Guide
 NetMan Desktop Manager Quick-Start Guide This document describes the procedure for installing NetMan Desktop Manager. The example given here presents a standard installation scenario. For details on all
NetMan Desktop Manager Quick-Start Guide This document describes the procedure for installing NetMan Desktop Manager. The example given here presents a standard installation scenario. For details on all
Server Edition. V8 Peregrine User Manual. for Microsoft Windows
 Server Edition V8 Peregrine User Manual for Microsoft Windows Copyright Notice and Proprietary Information All rights reserved. Attix5, 2015 Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
Server Edition V8 Peregrine User Manual for Microsoft Windows Copyright Notice and Proprietary Information All rights reserved. Attix5, 2015 Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
User Guide. Quick Heal Technologies Ltd.
 User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
Installing Sophos Endpoint Security and Control on a Home Computer Contents
 Contents Licensing... 2 Apple Mac Users.... 2 Free Tools... 2 Support... 2 Installation Instructions for Windows PC... 2 Before installing Sophos for Windows... 3 Downloading Sophos Endpoint Security and
Contents Licensing... 2 Apple Mac Users.... 2 Free Tools... 2 Support... 2 Installation Instructions for Windows PC... 2 Before installing Sophos for Windows... 3 Downloading Sophos Endpoint Security and
BitRater Client. Version Rev. 1.00
 BitRater Client Version 2015 Rev. 1.00 Page 1 of 15 WELCOME The BitRater Client takes a giant leap in PC protection. All you have to do is to install the BitRater Client and restart your PC to be effectively
BitRater Client Version 2015 Rev. 1.00 Page 1 of 15 WELCOME The BitRater Client takes a giant leap in PC protection. All you have to do is to install the BitRater Client and restart your PC to be effectively
Software troubleshooting
 N E W S L E T T E R IT Computer Technical Support Newsletter Software troubleshooting November 9, 2015 Vol.2, No.4 TABLE OF CONTENTS Software troubleshooting...1 Unexplained software crashes and error
N E W S L E T T E R IT Computer Technical Support Newsletter Software troubleshooting November 9, 2015 Vol.2, No.4 TABLE OF CONTENTS Software troubleshooting...1 Unexplained software crashes and error
Barracuda Threat Scanner for Exchange
 The is a free Windows application that allows you to scan onpremises Microsoft Exchange Servers for threats in existing user mailboxes. This tool provides insight into what threats have already entered
The is a free Windows application that allows you to scan onpremises Microsoft Exchange Servers for threats in existing user mailboxes. This tool provides insight into what threats have already entered
Desktop & Laptop Edition
 Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
How To Stop Avg Search Appearing In New Tabs On Google Chrome
 How To Stop Avg Search Appearing In New Tabs On Google Chrome I'm not completely sure when it started, but new tabs seem to randomly open up when I click somewhere while working on chrome. You will opjust
How To Stop Avg Search Appearing In New Tabs On Google Chrome I'm not completely sure when it started, but new tabs seem to randomly open up when I click somewhere while working on chrome. You will opjust
Server Edition USER MANUAL. For Mac OS X
 Server Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion are registered
Server Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion are registered
GO-GLOBAL FOR WINDOWS. Host Release Notes Version (C) GRAPHON CORPORATION ALL RIGHTS RESERVED.
 GO-GLOBAL FOR WINDOWS Host Release Notes Version 4.8.2.21320 (C) GRAPHON CORPORATION 1999-2015. ALL RIGHTS RESERVED. CONTENTS 1. Enhancements 2. Issues Fixed Since 4.8.1.21223 3. Known Issues Note: Version
GO-GLOBAL FOR WINDOWS Host Release Notes Version 4.8.2.21320 (C) GRAPHON CORPORATION 1999-2015. ALL RIGHTS RESERVED. CONTENTS 1. Enhancements 2. Issues Fixed Since 4.8.1.21223 3. Known Issues Note: Version
WINDOWS XP. iii. Contents
 C O N T E N T S Preface INTRODUCTION TO 1 Chapter 1 Navigating Windows XP 3 Launching Windows 3 Working with the Mouse 4 Moving the Mouse 4 Clicking 6 Double-clicking 6 Right-clicking 6 Dragging and Dropping
C O N T E N T S Preface INTRODUCTION TO 1 Chapter 1 Navigating Windows XP 3 Launching Windows 3 Working with the Mouse 4 Moving the Mouse 4 Clicking 6 Double-clicking 6 Right-clicking 6 Dragging and Dropping
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Maintaining Computer. Disk cleanup, Disk Defragmenter Recycle bin, Security
 Maintaining Computer Disk cleanup, Disk Defragmenter Recycle bin, Security Disk cleanup Cleaning out your PC on a regular basis frees up drive space and helps it run better. One of the easiest ways to
Maintaining Computer Disk cleanup, Disk Defragmenter Recycle bin, Security Disk cleanup Cleaning out your PC on a regular basis frees up drive space and helps it run better. One of the easiest ways to
Windows Help document Part A
 Compiled by: Todd Johnstone Before starting these steps, open a Word document, save it in documents in a folder called computing problems and use that document to capture items that show as bad as you
Compiled by: Todd Johnstone Before starting these steps, open a Word document, save it in documents in a folder called computing problems and use that document to capture items that show as bad as you
Sophos Enterprise Console Help. Product version: 5.3
 Sophos Enterprise Console Help Product version: 5.3 Document date: September 2015 Contents 1 About Sophos Enterprise Console 5.3...6 2 Guide to the Enterprise Console interface...7 2.1 User interface layout...7
Sophos Enterprise Console Help Product version: 5.3 Document date: September 2015 Contents 1 About Sophos Enterprise Console 5.3...6 2 Guide to the Enterprise Console interface...7 2.1 User interface layout...7
Module 15. Troubleshooting Software
 Module 15 Troubleshooting Software Objectives 1. 4.6 Troubleshooting Software 2. 4.7 Troubleshooting Security 2 TROUBLESHOOTING SOFTWARE 3 Troubleshooting Legacy Software Installation 1. Check Microsoft
Module 15 Troubleshooting Software Objectives 1. 4.6 Troubleshooting Software 2. 4.7 Troubleshooting Security 2 TROUBLESHOOTING SOFTWARE 3 Troubleshooting Legacy Software Installation 1. Check Microsoft
Discovering Computers Fundamentals, 2011 Edition. Living in a Digital World
 Discovering Computers Fundamentals, 2011 Edition Living in a Digital World Objectives Overview Define system software and identify the two types of system software Describe the functions of an operating
Discovering Computers Fundamentals, 2011 Edition Living in a Digital World Objectives Overview Define system software and identify the two types of system software Describe the functions of an operating
Quick Heal Total Security
 For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
INSTRUCTION MANUAL BreakingSecurity.net. Revision Remcos v2.3.0
 INSTRUCTION MANUAL Revision 14 -- Remcos v2.3.0 2019 BreakingSecurity.net 1 TABLE OF CONTENTS CHAPTER 1: INTRODUCTION TO REMCOS... 3 USAGE CASES... 3 COMPATIBILITY & DEVELOPMENT... 3 STRUCTURE... 4 CHAPTER
INSTRUCTION MANUAL Revision 14 -- Remcos v2.3.0 2019 BreakingSecurity.net 1 TABLE OF CONTENTS CHAPTER 1: INTRODUCTION TO REMCOS... 3 USAGE CASES... 3 COMPATIBILITY & DEVELOPMENT... 3 STRUCTURE... 4 CHAPTER
VMware Horizon Client for Windows User Guide. Modified on 03 OCT 2017 VMware Horizon Client for Windows 4.6 VMware Horizon Client for Windows 4.6.
 VMware Horizon Client for Windows User Guide Modified on 03 OCT 2017 VMware Horizon Client for Windows 4.6 VMware Horizon Client for Windows 4.6.1 VMware Horizon Client for Windows User Guide You can find
VMware Horizon Client for Windows User Guide Modified on 03 OCT 2017 VMware Horizon Client for Windows 4.6 VMware Horizon Client for Windows 4.6.1 VMware Horizon Client for Windows User Guide You can find
User Guide. Product: GreenFolders. Version: 3.8
 User Guide Product: GreenFolders Version: 3.8 Release Date: October 2014 GreenFolders 3.8 User Guide Introduction Table of Contents 1 Introduction... 6 2 General Information... 7 2.1 Login Procedure...
User Guide Product: GreenFolders Version: 3.8 Release Date: October 2014 GreenFolders 3.8 User Guide Introduction Table of Contents 1 Introduction... 6 2 General Information... 7 2.1 Login Procedure...
The Start menu (overview)
 The Start menu (overview) The Start menu is the main gateway to your computer's programs, folders, and settings. It's called a menu because it provides a list of choices, just as a restaurant menu does.
The Start menu (overview) The Start menu is the main gateway to your computer's programs, folders, and settings. It's called a menu because it provides a list of choices, just as a restaurant menu does.
Comodo Antivirus Software Version 2.1
 Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Even a non-technical user can even operate it with ease.the user can do any task in CCS with just a few clicks.
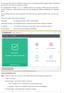 The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
This section of the release notes is reserved for notable changes and new features since the prior version.
 Release Notes Browsium Catalyst 3.1 Product Version: 3.1.2 Release Notes Updated: 9 February 2016 About this Release This document lists new features, known issues, and potential incompatibilities as of
Release Notes Browsium Catalyst 3.1 Product Version: 3.1.2 Release Notes Updated: 9 February 2016 About this Release This document lists new features, known issues, and potential incompatibilities as of
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
Radiology Associates - Office Computer Set-Up Guide
 1. Open (version 11.0 or higher) or Chrome. Type in the following web address into the browser. https://rapapacs.radresults.org/synapse 2. Type in your provided user name and password Page 1 3. Left clink
1. Open (version 11.0 or higher) or Chrome. Type in the following web address into the browser. https://rapapacs.radresults.org/synapse 2. Type in your provided user name and password Page 1 3. Left clink
Q:-1: A file deleted from disk drive A: in windows goes to
 Q:-1: A file deleted from disk drive A: in windows goes to (A) Recycle Bin (B) My Computer (C) Windows Explorer (D) Permanently deleted Q:-2: The term operating system means (A) A set of Programs Which
Q:-1: A file deleted from disk drive A: in windows goes to (A) Recycle Bin (B) My Computer (C) Windows Explorer (D) Permanently deleted Q:-2: The term operating system means (A) A set of Programs Which
Kaseya 2. User Guide. Version 2.1
 Kaseya 2 Endpoint Security User Guide Version 2.1 July 19, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Kaseya 2 Endpoint Security User Guide Version 2.1 July 19, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
How To Remove Personal Antivirus Security Pro Virus Manually
 How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
Apptix Online Backup by Mozy User Guide
 Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Typical Installation Guide. Installation Guide. Typical installation only. Standard version 2.5
 E s s e n t i a l S e c u r i t y a g a i n s t E v o l v i n g T h r e a t s Typical Installation Guide 2 Installation Guide Typical installation only Standard version 2.5 2 Copyright 1997 2005 Eset LLC.
E s s e n t i a l S e c u r i t y a g a i n s t E v o l v i n g T h r e a t s Typical Installation Guide 2 Installation Guide Typical installation only Standard version 2.5 2 Copyright 1997 2005 Eset LLC.
visionapp Remote Desktop (vrd)
 visionapp Remote Desktop () Version Overview Product Information www..com visionapp Remote Desktop at a Glance visionapp Remote Desktop is a powerful tool for managing and accessing multiple servers and
visionapp Remote Desktop () Version Overview Product Information www..com visionapp Remote Desktop at a Glance visionapp Remote Desktop is a powerful tool for managing and accessing multiple servers and
T-SYSTEMS MULTIMEDIA SOLUTIONS. User Manual
 T-SYSTEMS MULTIMEDIA SOLUTIONS User Manual doculife Desktop 6.x Date: 07.11.2016 Document Future AG 06/2016 Document Future AG holds the copyright to this documentation. This documentation or parts thereof
T-SYSTEMS MULTIMEDIA SOLUTIONS User Manual doculife Desktop 6.x Date: 07.11.2016 Document Future AG 06/2016 Document Future AG holds the copyright to this documentation. This documentation or parts thereof
Windows Me Navigating
 LAB PROCEDURE 11 Windows Me Navigating OBJECTIVES 1. Explore the Start menu. 2. Start an application. 3. Multi-task between applications. 4. Moving folders and files around. 5. Use Control Panel settings.
LAB PROCEDURE 11 Windows Me Navigating OBJECTIVES 1. Explore the Start menu. 2. Start an application. 3. Multi-task between applications. 4. Moving folders and files around. 5. Use Control Panel settings.
Information Communications Technology (CE-ICT) 6 th Class
 Information Communications Technology (CE-ICT) 6 th Class Lecture 1: Microsoft(MS) Windows Operating System (OS) Lecturer: Sophia Agenda for Today Microsoft Windows Operating System Windows Desktop Launching
Information Communications Technology (CE-ICT) 6 th Class Lecture 1: Microsoft(MS) Windows Operating System (OS) Lecturer: Sophia Agenda for Today Microsoft Windows Operating System Windows Desktop Launching
GO-GLOBAL FOR WINDOWS. Host Release Notes Version (C) GRAPHON CORPORATION ALL RIGHTS RESERVE D.
 GO-GLOBAL FOR WINDOWS Host Release Notes Version 5.0.2.25362 (C) GRAPHON CORPORATION 1999-2017. ALL RIGHTS RESERVE D. CONTENTS 1. Enhancements in Version 5.0.2.25362 2. Issues Fixed Since 5.0.2.25148 3.
GO-GLOBAL FOR WINDOWS Host Release Notes Version 5.0.2.25362 (C) GRAPHON CORPORATION 1999-2017. ALL RIGHTS RESERVE D. CONTENTS 1. Enhancements in Version 5.0.2.25362 2. Issues Fixed Since 5.0.2.25148 3.
CIS4Windows8Final. Name: Class: Date: Multiple Choice Identify the choice that best completes the statement or answers the question.
 Name: Class: Date: CIS4Windows8Final Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Windows 8 is a/an _ for a computer. a. operating system b. software
Name: Class: Date: CIS4Windows8Final Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Windows 8 is a/an _ for a computer. a. operating system b. software
Comodo Internet Security Software Version 11.0
 Comodo Internet Security Software Version 11.0 Installation Guide Guide Version 11.0.080918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Comodo Internet Security Software Version 11.0 Installation Guide Guide Version 11.0.080918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Safe Access User manual
 1 Table of contents 1. A new way to access e-banking services... 3 2. Prerequisites for installation... 3 3. Installation... 4 4. Running... 8 5. Folder shared with the PC... 9 6. Displaying documents...
1 Table of contents 1. A new way to access e-banking services... 3 2. Prerequisites for installation... 3 3. Installation... 4 4. Running... 8 5. Folder shared with the PC... 9 6. Displaying documents...
INTRODUCTION TO COMPUTERS AND WINDOWS 10
 INTRODUCTION TO COMPUTERS AND WINDOWS 10 Pam Stephens, Instructor email: pamela.stephens890@gmail.com Sign in: Take one of each handout. Please sit at a computer that is already turned on. Thank you! WHAT
INTRODUCTION TO COMPUTERS AND WINDOWS 10 Pam Stephens, Instructor email: pamela.stephens890@gmail.com Sign in: Take one of each handout. Please sit at a computer that is already turned on. Thank you! WHAT
Table of Contents. Page 1
 Table of Contents Google My Business Plugin... 2 Installation Is Not Required... 2 Generate GMB Unclaimed Data... 2 Reviewing The Unclaimed Listings... 2 Antivirus Applications... 3 AVG Antivirus... 3
Table of Contents Google My Business Plugin... 2 Installation Is Not Required... 2 Generate GMB Unclaimed Data... 2 Reviewing The Unclaimed Listings... 2 Antivirus Applications... 3 AVG Antivirus... 3
User Guide. Version R95. English
 Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Chapter 1: Introduction About the User Manual Intended Audience Conventions Used Revision History 4
 CLINCK Speed Manager User Manual Contents Chapter 1: Introduction 3 1.1 About the User Manual 3 1.2 Intended Audience 3 1.3 Conventions Used 3 1.4 Revision History 4 1.5 Overview of the CLINCK Speed Manager
CLINCK Speed Manager User Manual Contents Chapter 1: Introduction 3 1.1 About the User Manual 3 1.2 Intended Audience 3 1.3 Conventions Used 3 1.4 Revision History 4 1.5 Overview of the CLINCK Speed Manager
Kaseya 2. User Guide. Version 7.0. English
 Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Annexure E Technical Bid Format
 Annexure E Technical Bid Format ANTIVIRUS SOLUTION FOR MAIL SERVER SECURITY AND SERVER SECURITY FOR DESKTOP,LAPTOP Sr. No Description Compliance (Y/N) Remark 01 Must offer comprehensive client/server security
Annexure E Technical Bid Format ANTIVIRUS SOLUTION FOR MAIL SERVER SECURITY AND SERVER SECURITY FOR DESKTOP,LAPTOP Sr. No Description Compliance (Y/N) Remark 01 Must offer comprehensive client/server security
Customizing Windows XP
 Customizing Windows XP Mouse Moves Click Always lets you select something. It may be an icon, a button, or a menu command. Double Click Click the mouse (or trackpad) 2 times on an icon to open that document
Customizing Windows XP Mouse Moves Click Always lets you select something. It may be an icon, a button, or a menu command. Double Click Click the mouse (or trackpad) 2 times on an icon to open that document
Introduction to Windows 7. Session 1
 January 2014 Introduction to Windows 7 Session 1 1. First session, we will concentrate on understanding the Desktop, and managing Windows. 2. Discuss Logon. Show that you can set a password to access the
January 2014 Introduction to Windows 7 Session 1 1. First session, we will concentrate on understanding the Desktop, and managing Windows. 2. Discuss Logon. Show that you can set a password to access the
User Guide. Quick Heal Total Security Multi-Device. Quick Heal Technologies Ltd.
 User Guide Quick Heal Total Security Multi-Device Quick Heal Technologies Ltd. www.quickheal.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part
User Guide Quick Heal Total Security Multi-Device Quick Heal Technologies Ltd. www.quickheal.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
ESET NOD32 ANTIVIRUS 6
 ESET NOD32 ANTIVIRUS 6 User Guide (intended for product version 6.0 and higher) Microsoft Windows 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Click here to download the most recent version
ESET NOD32 ANTIVIRUS 6 User Guide (intended for product version 6.0 and higher) Microsoft Windows 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Click here to download the most recent version
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS
 KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
Panda Antivirus Server for Mac User Manual
 Panda Antivirus Server for Mac User Manual !"#$%&'()*+,$-'*(& Use of this product is subject to acceptance of the Panda Security End User License Agreement enclosed. Panda Security is registered in the
Panda Antivirus Server for Mac User Manual !"#$%&'()*+,$-'*(& Use of this product is subject to acceptance of the Panda Security End User License Agreement enclosed. Panda Security is registered in the
uses RSA Data Security, Inc. MD5 Message-Digest Algorithm, Copyright (C) , RSA Data Security,
 AVG 8.5 Free Edition User Manual Document revision 85.7 (8.9.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This product
AVG 8.5 Free Edition User Manual Document revision 85.7 (8.9.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This product
Comodo Dragon. User Guide Guide Version Software Version Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310
 Comodo Dragon Software Version 20.0 User Guide Guide Version 20.0.070312 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1. Comodo Dragon - Introduction... 4 2. System
Comodo Dragon Software Version 20.0 User Guide Guide Version 20.0.070312 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1. Comodo Dragon - Introduction... 4 2. System
Anchor User Guide. Presented by: Last Revised: August 07, 2017
 Anchor User Guide Presented by: Last Revised: August 07, 2017 TABLE OF CONTENTS GETTING STARTED... 1 How to Log In to the Web Portal... 1 How to Manage Account Settings... 2 How to Configure Two-Step Authentication...
Anchor User Guide Presented by: Last Revised: August 07, 2017 TABLE OF CONTENTS GETTING STARTED... 1 How to Log In to the Web Portal... 1 How to Manage Account Settings... 2 How to Configure Two-Step Authentication...
How to remove Adware from Mozilla Firefox
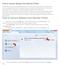 How to remove Adware from Mozilla Firefox Mozilla Firefox is one of the most popular browsers, and therefore also a popular target for installing adware and other untwanted extensions. In this article
How to remove Adware from Mozilla Firefox Mozilla Firefox is one of the most popular browsers, and therefore also a popular target for installing adware and other untwanted extensions. In this article
Unit III: Working with Windows and Applications. Chapters 5, 7, & 8
 Unit III: Working with Windows and Applications Chapters 5, 7, & 8 Learning Objectives In this unit, you will: Launch programs and navigate the Windows task bar. Perform common windows functions. Customize
Unit III: Working with Windows and Applications Chapters 5, 7, & 8 Learning Objectives In this unit, you will: Launch programs and navigate the Windows task bar. Perform common windows functions. Customize
User Guide. Version 2.1
 Kaseya Endpoint Security User Guide Version 2.1 February 23, 2010 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Kaseya Endpoint Security User Guide Version 2.1 February 23, 2010 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Sophos Central Admin. help
 help Contents About Sophos Central... 1 Activate Your License...2 Endpoint Protection...3 Dashboard...3 Alerts...4 Root Cause Analysis...9 Logs & Reports... 11 People... 24 Computers...33 Computer Groups...40
help Contents About Sophos Central... 1 Activate Your License...2 Endpoint Protection...3 Dashboard...3 Alerts...4 Root Cause Analysis...9 Logs & Reports... 11 People... 24 Computers...33 Computer Groups...40
Chapter 8 Operating Systems and Utility Programs أ.أمل زهران
 Chapter 8 Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
Chapter 8 Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
ABF Software Issues Caused by Anti-Virus Programs
 ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
