EXTENDING LAN winning the distance limitation
|
|
|
- Laureen Bennett
- 6 years ago
- Views:
Transcription
1 CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-5 WAN Extending LAN Techniques for extending LAN WAN Scalable Technologies to over come distance & number limitation Routing in WAN 1 LECT-5, S-2 Extending LANs EXTENDING LAN winning the distance limitation Why LANs are distance limited? Signal loss at physical level Coordination at logical level Engineers have developed a variety of ways to extend LAN connectivity. Most extension mechanisms use standard interface hardware and insert additional hardware components that can extend signals at longer distances. 3 Fiber optic extensions, repeaters, bridges or switches and hubs can be used for extending LANs. LECT-5, S-4 Fiber Modems Repeaters The simplest LAN extension mechanism uses optical fibers and a pair of fiber modems extend the connection between a computer and a trans-receiver. Fibers have low delayed and high bandwidth. Repeaters connects a pair of cables and is an analog device. Its main job is to repeats every signal that it hears on one side to the other. LECT-5, S-5 LECT-5, S-6 1
2 Extended Ethernet LAN with Repeaters Repeater repeats everything, collision, noise, even thunderstorm! Bridges Bridges also connects two networks, but they understand frame format. Has a separate HW address. Can talk to each other. Listens to both the networks in promiscuous mode and can copy every frame it receives intact to the other network. Thus two LANs can work as one LAN. Computers would not know on which segment they are in. LECT-5, S-7 LECT-5, S-8 Bridges Bridges can also perform frame filtering. It looks into hardware address in the frames. Relays the frames only if it is for a computer in other segment. Bridging Between Buildings How do they know which computer is in which side? How Bridges know about the computer which did not talk? LECT-5, S-9 LECT-5, S-10 Bridging Across Long Distance Cycle of Bridges Needs buffering How to avoid Cycles? (DST) Each site has a bridge. Why? LECT-5, S-11 Parallelism How computers should be distributed at two segments? LECT-5, S-12 2
3 WAN how to win the limit on the number of computers? 13 Problem of Scale: WANs The techniques shown in last few slides show how the distance limitation of LANs be extended. But, they do not solve the problem of Scale. What if we have too many computers scattered across long distances, at different places? Solution: Packet Switches moves packet from one network to another. Not only one or two but, many switches creates a network of networks. Distributed routing. LECT-5, S-14 Switching Packet Switching Computers can communicate in parallel. But costly. Thus a combination of Switch & Hub is used. One side connects to computers, other side connects to other packet switches. LECT-5, S-15 LECT-5, S-16 Back Bone WANs with Packet Switches How do they know which computer is where and where to forward? Visit to ABILANE Switch ABILENE ABILANE WEATHERMAP ROUTER TRAFFIC STATS OTHER BACKBONES (goto abovenet/ visualization) (RUSS PAGE) Computers now talk in parallel. Switches does store and forward. LECT-5, S-17 LECT-5, S-18 3
4 Physical Addressing in a WAN Example of Next Hop Forwarding Each address is divided into two parts: switch address and computer address Each switch maintains a list of next-hop-address for each destination Switches (except the final one) need not to read the computer address. LECT-5, S-19 Forwarding Table of Switch#2 LECT-5, S-20 Further Scalable WAN Routing in a WAN Scalable Network Interior and Exterior Packet Switches Scalable Address Table Universality each should know the path to any computer. Optimality the path should be optimum too. Size of address Table? LECT-5, S-21 LECT-5, S-22 Default Routing How to Determine Best Path? Disktra s shortest vector algorithm is used. How to collect Routing Information needed for Disktra s algorithm? Distance Vector Algorithm Link State Algorithm. Refresh these up! LECT-5, S-23 LECT-5, S-24 4
5 Connectionless vs. Connection-oriented Switching A packet can explicitly carry the destination address. However, if lots of packets are going to the same destination, they can carry a small label. Cost of Address field Connection Setup Cost Example ATM: VPI:VCI Path idetifier can change from switch to switch Channel identified is used only by the destination switch. Example WAN Technologies ARPANET A defense initiative started in 1960s. Legacy of Internet. Based on 56Kbps Leased serial lines. X.25 Developed by ITU,popular in Europe Used for remote terminal placement of computers. Not suitable for computer-computer communication. ISDN Objective: data networking on voice system. 64 Kbps date+ 16 Kbps control channel. LECT-5, S-25 LECT-5, S-26 Summary Example WAN Technologies -2 Frame Relay Appropriate for long distance LAN bridging Supports upto 8K frames on 1.5 Mbps or 56Kbps. SMDS (switched multi-megabit data service) Designed to carry data. Higher bandwidth than FR LAN technology can connect a community of computers. Solution to Distance Limitation Repeaters & Bridges. Solution to Scale Limitation Packet Switch for connection scaling. New Issue routing ATM most promising in WAN ensures quality of service. Available in 155 Mbps/ 622 Mbps LECT-5, S-27 10s of thousands of computers can be connected with the above Networking Infrastructure! LECT-5, S-28 Summary (cont..) Technologies: LANs: Ethernet, AppleTalk, IBM Token Ring Fast LANs: FDDI, Fast Ethernet, HIPPI, ATM, Fiber Channel. WANs: ARPANET, X.25, ISDN, SMDS, Frame Relay, ATM. LECT-5, S-29 Computing Shortest Path (Dijktra s Algorithm) W[i][j]=link cost between node i and j S[i]=all nodes except source; R[i]= source for all connected nodes otherwise zero. D[i]=W[source][i] for nodes connected from src other wise infinity. while( set S is not empty) { choose u from S closest to source; if (D[u]==infinity) no path in S, exit; delete u from S; for each v such that W[u][v] is an edge { if (v is still in S) { c=d[u]+w[u][v]; if (c < D[v]) { R[v]=R[u]; D[v]=c; }}}} LECT-5, S-30 5
6 Distributed Vector Distance Routing Table Computation Given a local routing table with weight and an incoming message; Link-State Routing Step-1: Every Switch broadcasts the status of links attached to it in regular interval. Repeat forever { wait for next message from N; for each entry in the message { if V is destination and D is cost; Step-2: Each Switch collects the c=distance to N + D; incoming messages and builds its own if V is a new destination network graph. add a new entry, for V with next hop = N and D =c; if V is there and next-hop is also N Step-3: In parallel, they independently replace local D with c; if V is there but next-hop is not N but D > c compute the best path. replace next-hop = N and local D=c; } } LECT-5, S-31 LECT-5, S-32 6
CS 4/55231 Internet Engineering
 1 Extending LANs CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-5 Why LANs are distance limited? Signal loss at physical level Coordination at logical level Engineers
1 Extending LANs CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-5 Why LANs are distance limited? Signal loss at physical level Coordination at logical level Engineers
SCALABLE INTERNET ROUTING
 CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-7 SCALABLE ROUTING 1 2 Scalability Basic Subnetting & Subnet Masks The management of global resource is a complex task.
CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-7 SCALABLE ROUTING 1 2 Scalability Basic Subnetting & Subnet Masks The management of global resource is a complex task.
Chapter 3 Part 2 Switching and Bridging. Networking CS 3470, Section 1
 Chapter 3 Part 2 Switching and Bridging Networking CS 3470, Section 1 Refresher We can use switching technologies to interconnect links to form a large network What is a hub? What is a switch? What is
Chapter 3 Part 2 Switching and Bridging Networking CS 3470, Section 1 Refresher We can use switching technologies to interconnect links to form a large network What is a hub? What is a switch? What is
Integrated t Services Digital it Network (ISDN) Digital Subscriber Line (DSL) Cable modems Hybrid Fiber Coax (HFC)
 Digital Local Loop Technologies Integrated t Services Digital it Network (ISDN) Handles voice and data Relatively l high h cost for low bandwidth (Skip) Digital Subscriber Line (DSL) Cable modems Hybrid
Digital Local Loop Technologies Integrated t Services Digital it Network (ISDN) Handles voice and data Relatively l high h cost for low bandwidth (Skip) Digital Subscriber Line (DSL) Cable modems Hybrid
Outline: Connecting Many Computers
 Outline: Connecting Many Computers Last lecture: sending data between two computers This lecture: link-level network protocols (from last lecture) sending data among many computers 1 Review: A simple point-to-point
Outline: Connecting Many Computers Last lecture: sending data between two computers This lecture: link-level network protocols (from last lecture) sending data among many computers 1 Review: A simple point-to-point
Data Transport Networks
 DC 8-1 DATACOMM John Abbott College JPC Data Transport Networks M. E. Kabay, PhD, CISSP Director of Education, ICSA President, JINBU Corp Copyright 1998 JINBU Corp. All rights reserved DC 8-2 Data Transport
DC 8-1 DATACOMM John Abbott College JPC Data Transport Networks M. E. Kabay, PhD, CISSP Director of Education, ICSA President, JINBU Corp Copyright 1998 JINBU Corp. All rights reserved DC 8-2 Data Transport
More on LANS. LAN Wiring, Interface
 More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
Chapter 6 Connecting Device
 Computer Networks Al-Mustansiryah University Elec. Eng. Department College of Engineering Fourth Year Class Chapter 6 Connecting Device 6.1 Functions of network devices Separating (connecting) networks
Computer Networks Al-Mustansiryah University Elec. Eng. Department College of Engineering Fourth Year Class Chapter 6 Connecting Device 6.1 Functions of network devices Separating (connecting) networks
Bridging and Switching Basics
 CHAPTER 4 Bridging and Switching Basics This chapter introduces the technologies employed in devices loosely referred to as bridges and switches. Topics summarized here include general link-layer device
CHAPTER 4 Bridging and Switching Basics This chapter introduces the technologies employed in devices loosely referred to as bridges and switches. Topics summarized here include general link-layer device
Local Area Network(LAN)
 Local Area Network(LAN) A local area network (LAN) is a computer network that interconnects computers within a limited area. Example: a residence, school, laboratory, university campus,office building
Local Area Network(LAN) A local area network (LAN) is a computer network that interconnects computers within a limited area. Example: a residence, school, laboratory, university campus,office building
CARRIER SENSE MULTIPLE ACCESS (CSMA):
 Lecture Handout Computer Networks Lecture No. 8 CARRIER SENSE MULTIPLE ACCESS (CSMA): There is no central control management when computers transmit on Ethernet. For this purpose the Ethernet employs CSMA
Lecture Handout Computer Networks Lecture No. 8 CARRIER SENSE MULTIPLE ACCESS (CSMA): There is no central control management when computers transmit on Ethernet. For this purpose the Ethernet employs CSMA
Lecture 7. Reminder: Homework 2, Programming Project 1 due today. Homework 3, Programming Project 2 out, due Thursday next week. Questions?
 Lecture 7 Reminder: Homework 2, Programming Project 1 due today. Homework 3, Programming Project 2 out, due Thursday next week. Questions? Thursday, September 15 CS 475 Networks - Lecture 7 1 Outline Chapter
Lecture 7 Reminder: Homework 2, Programming Project 1 due today. Homework 3, Programming Project 2 out, due Thursday next week. Questions? Thursday, September 15 CS 475 Networks - Lecture 7 1 Outline Chapter
Computers Are Your Future
 Computers Are Your Future Networks: Communicating and Sharing Resources. Network Fundamentals What You Will Learn About Basic networking concepts Advantages and disadvantages of networks Peer-to-peer and
Computers Are Your Future Networks: Communicating and Sharing Resources. Network Fundamentals What You Will Learn About Basic networking concepts Advantages and disadvantages of networks Peer-to-peer and
Network Infrastructure
 Network Infrastructure For building computer networks more complex than e.g. a short bus, some additional components are needed. They can be arranged hierarchically regarding their functionality: Repeater
Network Infrastructure For building computer networks more complex than e.g. a short bus, some additional components are needed. They can be arranged hierarchically regarding their functionality: Repeater
Ch. 4 - WAN, Wide Area Networks
 1 X.25 - access 2 X.25 - connection 3 X.25 - packet format 4 X.25 - pros and cons 5 Frame Relay 6 Frame Relay - access 7 Frame Relay - frame format 8 Frame Relay - addressing 9 Frame Relay - access rate
1 X.25 - access 2 X.25 - connection 3 X.25 - packet format 4 X.25 - pros and cons 5 Frame Relay 6 Frame Relay - access 7 Frame Relay - frame format 8 Frame Relay - addressing 9 Frame Relay - access rate
Computer Networks and Internet
 Computer Networks and Internet Objectives Computer Networks Internet 2 Computer Networks Introducing Computer Networks A computer network consists of two or more computers linked together to exchange data
Computer Networks and Internet Objectives Computer Networks Internet 2 Computer Networks Introducing Computer Networks A computer network consists of two or more computers linked together to exchange data
LAN Interconnection and Other Link Layer Protocols
 LAN Interconnection and Other Link Layer Protocols Ethernet dominant link layer technology for local-area networks Ethernet frame structure Kai Shen Dept. of Computer Science, University of Rochester Ethernet
LAN Interconnection and Other Link Layer Protocols Ethernet dominant link layer technology for local-area networks Ethernet frame structure Kai Shen Dept. of Computer Science, University of Rochester Ethernet
Internet Architecture
 Internet Architecture Lecture 2: How Computer Networks Send Data Across the Internet Assistant Teacher Samraa Adnan Al-Asadi 1 Introduction When you send information across the Internet, the Transmission
Internet Architecture Lecture 2: How Computer Networks Send Data Across the Internet Assistant Teacher Samraa Adnan Al-Asadi 1 Introduction When you send information across the Internet, the Transmission
CHAPTER -1. Introduction to Computer Networks
 CHAPTER -1 Introduction to Computer Networks PRELIMINARY DEFINITIONS computer network :: [Tanenbaum] a collection of autonomous computers interconnected by a single technology. communications network ::a
CHAPTER -1 Introduction to Computer Networks PRELIMINARY DEFINITIONS computer network :: [Tanenbaum] a collection of autonomous computers interconnected by a single technology. communications network ::a
TCOM 370 NOTES 99-1 NETWORKING AND COMMUNICATIONS
 TCOM 370 NOTES 99-1 NETWORKING AND COMMUNICATIONS Communication Networks Allow Exchange of Information between Users telephone network for voice communication interconnected computers and peripherals,
TCOM 370 NOTES 99-1 NETWORKING AND COMMUNICATIONS Communication Networks Allow Exchange of Information between Users telephone network for voice communication interconnected computers and peripherals,
CS610- Computer Network Solved Subjective From Midterm Papers
 Solved Subjective From Midterm Papers May 08,2012 MC100401285 Moaaz.pk@gmail.com Mc100401285@gmail.com PSMD01 CS610- Computer Network Midterm Examination - Fall 2011 1. Where are destination and source
Solved Subjective From Midterm Papers May 08,2012 MC100401285 Moaaz.pk@gmail.com Mc100401285@gmail.com PSMD01 CS610- Computer Network Midterm Examination - Fall 2011 1. Where are destination and source
Virtual Link Layer : Fundamentals of Computer Networks Bill Nace
 Virtual Link Layer 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia 3 Lectures left HW #2
Virtual Link Layer 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia 3 Lectures left HW #2
Introduction to WAN Technologies
 Introduction to WAN Technologies From DocWiki This article introduces the various protocols and technologies used in wide-area network (WAN) environments. Topics summarized here include point-to-point
Introduction to WAN Technologies From DocWiki This article introduces the various protocols and technologies used in wide-area network (WAN) environments. Topics summarized here include point-to-point
Extending the LAN. Context. Info 341 Networking and Distributed Applications. Building up the network. How to hook things together. Media NIC 10/18/10
 Extending the LAN Info 341 Networking and Distributed Applications Context Building up the network Media NIC Application How to hook things together Transport Internetwork Network Access Physical Internet
Extending the LAN Info 341 Networking and Distributed Applications Context Building up the network Media NIC Application How to hook things together Transport Internetwork Network Access Physical Internet
Virtual Link Layer : Fundamentals of Computer Networks Bill Nace
 Virtual Link Layer 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia 3 Lectures left HW #2
Virtual Link Layer 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia 3 Lectures left HW #2
Internetworking Part 1
 CMPE 344 Computer Networks Spring 2012 Internetworking Part 1 Reading: Peterson and Davie, 3.1 22/03/2012 1 Not all networks are directly connected Limit to how many hosts can be attached Point-to-point:
CMPE 344 Computer Networks Spring 2012 Internetworking Part 1 Reading: Peterson and Davie, 3.1 22/03/2012 1 Not all networks are directly connected Limit to how many hosts can be attached Point-to-point:
ECE 333: Introduction to Communication Networks Fall Lecture 19: Medium Access Control VII
 ECE : Introduction to Communication Networks Fall 2002 Lecture 9: Medium Access Control VII More on token ring networks LAN bridges and switches. More on token rings In the last lecture we began discussing
ECE : Introduction to Communication Networks Fall 2002 Lecture 9: Medium Access Control VII More on token ring networks LAN bridges and switches. More on token rings In the last lecture we began discussing
LAN, MAN and WAN. Basics and Comparison. University of Damascus. Computer Engineering Dept. Digital Communications. By Abdulrahman Idlbi
 In the name of Allah, the Most Gracious, the Most Merciful University of Damascus Computer Engineering Dept. Digital Communications LAN, MAN and WAN Basics and Comparison By Abdulrahman Idlbi Introduction
In the name of Allah, the Most Gracious, the Most Merciful University of Damascus Computer Engineering Dept. Digital Communications LAN, MAN and WAN Basics and Comparison By Abdulrahman Idlbi Introduction
More on Link Layer. Recap of Last Class. Interconnecting Nodes in LAN (Local-Area Network) Interconnecting with Hubs. Computer Networks 9/21/2009
 More on Link Layer Kai Shen Recap of Last Class Ethernet dominant link layer technology for local-area l networks Ethernet frame structure Ethernet multiple access control CSMA/CD, exponential back-off
More on Link Layer Kai Shen Recap of Last Class Ethernet dominant link layer technology for local-area l networks Ethernet frame structure Ethernet multiple access control CSMA/CD, exponential back-off
LAN. CS 4/55231 Internet Engineering. Kent State University Dept. of Computer Science
 1 CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-4A4 LAN 1 2 LAN Topologies-1 In the last class we saw how two computers can connect to each other. In this class we
1 CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-4A4 LAN 1 2 LAN Topologies-1 In the last class we saw how two computers can connect to each other. In this class we
BROADBAND AND HIGH SPEED NETWORKS
 BROADBAND AND HIGH SPEED NETWORKS INTRODUCTION TO DATA COMMUNICATION NETWORKS Data communications are the exchange of data between two devices via some form of transmission medium such as a wire cable.
BROADBAND AND HIGH SPEED NETWORKS INTRODUCTION TO DATA COMMUNICATION NETWORKS Data communications are the exchange of data between two devices via some form of transmission medium such as a wire cable.
ก ก Information Technology II
 ก ก 202103 Information Technology II ก ก ก ก ก (LAN), ก LAN, ก ก (LAN) ก ก ก LAN ก LAN ก LAN Topology Bus LAN Star LAN Ring LAN Wireless LAN Wireless LAN Wireless ก (LAN) ก ก ก LAN ก LAN WAN ก Random Access
ก ก 202103 Information Technology II ก ก ก ก ก (LAN), ก LAN, ก ก (LAN) ก ก ก LAN ก LAN ก LAN Topology Bus LAN Star LAN Ring LAN Wireless LAN Wireless LAN Wireless ก (LAN) ก ก ก LAN ก LAN WAN ก Random Access
ITP 140 Mobile Applications Technologies. Networks
 ITP 140 Mobile Applications Technologies Networks A First Look Under the Hood 2 3 Communication Channels Mediums for transporting data from one system to another Physical Twisted Pair (CAT-3, CAT-5/6)
ITP 140 Mobile Applications Technologies Networks A First Look Under the Hood 2 3 Communication Channels Mediums for transporting data from one system to another Physical Twisted Pair (CAT-3, CAT-5/6)
Typical Network Uses
 Computer Networks Introduction The next Great Revolution - Computer Networks- computers connected together for exchanging information Our information-oriented society - applications in education, commerce,
Computer Networks Introduction The next Great Revolution - Computer Networks- computers connected together for exchanging information Our information-oriented society - applications in education, commerce,
Goal and Outline. Computer Networking. What Do We Need? Today s Story Lecture 3: Packet Switched Networks Peter Steenkiste
 Goal and Outline 15-441 15-641 Computer Networking Lecture 3: Packet Switched Networks Peter Steenkiste Fall 2016 www.cs.cmu.edu/~prs/15 441 F16 Goal: gain a basic understanding of how you can build a
Goal and Outline 15-441 15-641 Computer Networking Lecture 3: Packet Switched Networks Peter Steenkiste Fall 2016 www.cs.cmu.edu/~prs/15 441 F16 Goal: gain a basic understanding of how you can build a
More on LANs. Roadmap. CPSC Network Programming. ! Hardware Addressing. !LAN Wiring. ! Extending LANs. ! Local Loop Digital Technologies
 CPSC 360 - Network Programming More on LANs Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu February 28, 2005 http://www.cs.clemson.edu/~mweigle/courses/cpsc360
CPSC 360 - Network Programming More on LANs Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu February 28, 2005 http://www.cs.clemson.edu/~mweigle/courses/cpsc360
LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, connecting devices are needed.
 LAN interconnecting devices INTRODUCTION LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, connecting devices are needed. Connecting devices
LAN interconnecting devices INTRODUCTION LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, connecting devices are needed. Connecting devices
Computer Networks. Andrew S. Tanenbaum
 Computer Networks Third Edition Andrew S. Tanenbaum 1 ; l Vrije Universiteit Amsterdam, The Netherlands For book and bookstore information Prentice Hall PTR Upper Saddle River, New Jersey 07458 CONTENTS
Computer Networks Third Edition Andrew S. Tanenbaum 1 ; l Vrije Universiteit Amsterdam, The Netherlands For book and bookstore information Prentice Hall PTR Upper Saddle River, New Jersey 07458 CONTENTS
Introduction to LAN Protocols
 CHAPTER 2 Chapter Goals Learn about different LAN protocols. Understand the different methods used to deal with media contention. Learn about different LAN topologies. This chapter introduces the various
CHAPTER 2 Chapter Goals Learn about different LAN protocols. Understand the different methods used to deal with media contention. Learn about different LAN topologies. This chapter introduces the various
Principles behind data link layer services
 Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
Summary of MAC protocols
 Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Network Layer. For this purpose the network layer should:
 Network Layer In the preceding tutorials we have studies how the DLL is responsible for moving the frame one end to the other end of the media, the network layer is responsible for the moving the packets
Network Layer In the preceding tutorials we have studies how the DLL is responsible for moving the frame one end to the other end of the media, the network layer is responsible for the moving the packets
Medium Access Protocols
 Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Hubs. twisted pair. hub. 5: DataLink Layer 5-1
 Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at : adapters detect collisions provides net management
Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at : adapters detect collisions provides net management
Chapter 3. Underlying Technology. TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 3 Underlying Technology TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To briefly discuss the technology of dominant
Chapter 3 Underlying Technology TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To briefly discuss the technology of dominant
Contents. Introduction to Networking. Preface...i. Introduction... xix
 Contents Introduction to Networking Introduction to Networking Preface...i Key Topics...i Course Objectives...ii Pedagogical Features...ii Learning Objectives, Unit Summaries, Discussion Questions, and
Contents Introduction to Networking Introduction to Networking Preface...i Key Topics...i Course Objectives...ii Pedagogical Features...ii Learning Objectives, Unit Summaries, Discussion Questions, and
Layer 2 functionality bridging and switching
 Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Revision of Previous Lectures
 Lecture 15 Overview Last Lecture Local area networking This Lecture Wide area networking 1 Source: chapters 8.1-8.3, 17.1, 18.1, 18.2 Next Lecture Wide area networking 2 Source: Chapter 20 COSC244 Lecture
Lecture 15 Overview Last Lecture Local area networking This Lecture Wide area networking 1 Source: chapters 8.1-8.3, 17.1, 18.1, 18.2 Next Lecture Wide area networking 2 Source: Chapter 20 COSC244 Lecture
Packet Switching Techniques
 Packet Switching Techniques 188lecture3.ppt Pasi Lassila 1 Problem Aim: Build larger networks connecting more users also spanning different network technologies Shared media networks limited number of
Packet Switching Techniques 188lecture3.ppt Pasi Lassila 1 Problem Aim: Build larger networks connecting more users also spanning different network technologies Shared media networks limited number of
Principles behind data link layer services:
 Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Principles behind data link layer services:
 Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Reminder: Datalink Functions Computer Networking. Datalink Architectures
 Reminder: Datalink Functions 15-441 15 441 15-641 Computer Networking Lecture 5 Media Access Control Peter Steenkiste Fall 2015 www.cs.cmu.edu/~prs/15-441-f15 Framing: encapsulating a network layer datagram
Reminder: Datalink Functions 15-441 15 441 15-641 Computer Networking Lecture 5 Media Access Control Peter Steenkiste Fall 2015 www.cs.cmu.edu/~prs/15-441-f15 Framing: encapsulating a network layer datagram
Computer Networks
 15-441 Computer s Lecture 3 Professor Hui Zhang Wean Hall 7126 hzhang@cs.cmu.edu 1 Review of Lecture 1 How long does it take to move 1GB data from campus to your home? 56Kbps modem 2Mbps DSL Other possibilities?
15-441 Computer s Lecture 3 Professor Hui Zhang Wean Hall 7126 hzhang@cs.cmu.edu 1 Review of Lecture 1 How long does it take to move 1GB data from campus to your home? 56Kbps modem 2Mbps DSL Other possibilities?
Networking Devices. Punch_down panels
 Networking Devices Punch_down panels Hubs Switches Bridges Routes Gateways Network Interface Cards (NICs) Wireless access points Modems 1 Punch_down panels Wiring closets Labeling schemes 2 1 Hubs The
Networking Devices Punch_down panels Hubs Switches Bridges Routes Gateways Network Interface Cards (NICs) Wireless access points Modems 1 Punch_down panels Wiring closets Labeling schemes 2 1 Hubs The
ITP 140 Mobile Applications Technologies. Networks
 ITP 140 Mobile Applications Technologies Networks A First Look Under the Hood 2 3 Communication Channels Mediums for transporting data from one system to another Physical Twisted Pair (CAT-3, CAT-5/6)
ITP 140 Mobile Applications Technologies Networks A First Look Under the Hood 2 3 Communication Channels Mediums for transporting data from one system to another Physical Twisted Pair (CAT-3, CAT-5/6)
Computer Communications and Network Basics p. 1 Overview of Computer Communications and Networking p. 2 What Does Computer Communications and
 Computer Communications and Network Basics p. 1 Overview of Computer Communications and Networking p. 2 What Does Computer Communications and Networking Technologies Mean? p. 3 What Is a Computer Network?
Computer Communications and Network Basics p. 1 Overview of Computer Communications and Networking p. 2 What Does Computer Communications and Networking Technologies Mean? p. 3 What Is a Computer Network?
Local Area Networks (LANs) SMU CSE 5344 /
 Local Area Networks (LANs) SMU CSE 5344 / 7344 1 LAN/MAN Technology Factors Topology Transmission Medium Medium Access Control Techniques SMU CSE 5344 / 7344 2 Topologies Topology: the shape of a communication
Local Area Networks (LANs) SMU CSE 5344 / 7344 1 LAN/MAN Technology Factors Topology Transmission Medium Medium Access Control Techniques SMU CSE 5344 / 7344 2 Topologies Topology: the shape of a communication
FASTER ETHERNET AND THE ATM MARKET BOUNDARY ABSTRACT
 FASTER ETHERNET AND THE ATM MARKET BOUNDARY G. Kent Webb, San Jose State University, webb_k@cob.sjsu.edu ABSTRACT As a network technology, ethernet flourished in low-cost, low-end markets. Simple to make
FASTER ETHERNET AND THE ATM MARKET BOUNDARY G. Kent Webb, San Jose State University, webb_k@cob.sjsu.edu ABSTRACT As a network technology, ethernet flourished in low-cost, low-end markets. Simple to make
IT114 NETWORK+ Learning Unit 1 Objectives: 1, 2 Time In-Class Time Out-Of-Class Hours 2-3. Lectures: Course Introduction and Overview
 IT114 NETWORK+ Course Objectives Upon successful completion of this course, the student will be able to: 1. Identify the devices and elements of computer networks; 2. Diagram network models using the appropriate
IT114 NETWORK+ Course Objectives Upon successful completion of this course, the student will be able to: 1. Identify the devices and elements of computer networks; 2. Diagram network models using the appropriate
Data Link Layer, Part 3 Medium Access Control. Preface
 Data Link Layer, Part 3 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make a single machine-readable
Data Link Layer, Part 3 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make a single machine-readable
(Network Programming) Basic Networking Hardware
 EEE 448 Computer Networks with (Network Programming) Basic Networking Hardware Lecture #2 Dept of Electrical and Electronics Engineering Çukurova University Agenda What is a network device? Network Media
EEE 448 Computer Networks with (Network Programming) Basic Networking Hardware Lecture #2 Dept of Electrical and Electronics Engineering Çukurova University Agenda What is a network device? Network Media
Lecture 1 Overview - Data Communications, Data Networks, and the Internet
 DATA AND COMPUTER COMMUNICATIONS Lecture 1 Overview - Data Communications, Data Networks, and the Internet Mei Yang Based on Lecture slides by William Stallings 1 OUTLINE Data Communications and Networking
DATA AND COMPUTER COMMUNICATIONS Lecture 1 Overview - Data Communications, Data Networks, and the Internet Mei Yang Based on Lecture slides by William Stallings 1 OUTLINE Data Communications and Networking
Networks Hardware Components
 Lec. 5 Networks Hardware Components Dr. Eng. Samy Elmokadem Chapter 8 10/12/2017 1 internetworking devices used in backbone networks After studying this Chapter you should: Know which internetworking devices
Lec. 5 Networks Hardware Components Dr. Eng. Samy Elmokadem Chapter 8 10/12/2017 1 internetworking devices used in backbone networks After studying this Chapter you should: Know which internetworking devices
19: Networking. Networking Hardware. Mark Handley
 19: Networking Mark Handley Networking Hardware Lots of different hardware: Modem byte at a time, FDDI, SONET packet at a time ATM (including some DSL) 53-byte cell at a time Reality is that most networking
19: Networking Mark Handley Networking Hardware Lots of different hardware: Modem byte at a time, FDDI, SONET packet at a time ATM (including some DSL) 53-byte cell at a time Reality is that most networking
Computer-to-Computer Networks (cont.)
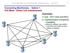 Computer-to-Computer Networks (cont.) 1 Connecting Mainframes - Option 1: Full Mesh / Direct Link Infrastructure Downsides: 1) cost - O(n 2 ) links and NICs 2) implementation complexity / scalability [
Computer-to-Computer Networks (cont.) 1 Connecting Mainframes - Option 1: Full Mesh / Direct Link Infrastructure Downsides: 1) cost - O(n 2 ) links and NICs 2) implementation complexity / scalability [
Chapter 4 NETWORK HARDWARE
 Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
CS 43: Computer Networks. 27: Media Access Contd. December 3, 2018
 CS 43: Computer Networks 27: Media Access Contd. December 3, 2018 Last Class The link layer provides lots of functionality: addressing, framing, media access, error checking could be used independently
CS 43: Computer Networks 27: Media Access Contd. December 3, 2018 Last Class The link layer provides lots of functionality: addressing, framing, media access, error checking could be used independently
COMS Introduction to Computers. Networking
 COMS 1001 Introduction to Computers Networking What's Ahead Networking layers Network Speeds Protocols, sockets, client/server Routing, DNS, Ethernet, LANs, wireless What is a Network? Loose definition:
COMS 1001 Introduction to Computers Networking What's Ahead Networking layers Network Speeds Protocols, sockets, client/server Routing, DNS, Ethernet, LANs, wireless What is a Network? Loose definition:
Network Layer: Routing
 Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
Network Layer: Routing The Problem A B R 1 R 2 R 4 R 3 Goal: for each destination, compute next hop 1 Lecture 9 2 Basic Assumptions Trivial solution: Flooding Dynamic environment: links and routers unreliable:
HWP2 Application level query routing HWP1 Each peer knows about every other beacon B1 B3
 HWP2 Application level query routing HWP1 Each peer knows about every other beacon B2 B1 B3 B4 B5 B6 11-Feb-02 Computer Networks 1 HWP2 Query routing searchget(searchkey, hopcount) Rget(host, port, key)
HWP2 Application level query routing HWP1 Each peer knows about every other beacon B2 B1 B3 B4 B5 B6 11-Feb-02 Computer Networks 1 HWP2 Query routing searchget(searchkey, hopcount) Rget(host, port, key)
Shared Access Networks. Media Access Protocols. Ethernet (802.3) Ethernet cont...
 Media Access Protocols Kameswari Chebrolu Dept. of Electrical Engineering, IIT Kanpur Shared Access Networks More than two nodes are attached to the same physical medium Normally span a small geographical
Media Access Protocols Kameswari Chebrolu Dept. of Electrical Engineering, IIT Kanpur Shared Access Networks More than two nodes are attached to the same physical medium Normally span a small geographical
M242 COMPUTER NETWORS AND SECURITY
 M242 COMPUTER NETWORS AND SECURITY 2.1. Network Models: UNIT - II OSI MODEL AND LAN PROTOCOLS 1. Explain Network model A network is a combination of hardware and software that sends data from one location
M242 COMPUTER NETWORS AND SECURITY 2.1. Network Models: UNIT - II OSI MODEL AND LAN PROTOCOLS 1. Explain Network model A network is a combination of hardware and software that sends data from one location
Configuring Transparent Bridging
 Configuring Transparent Bridging Document ID: 10676 Contents Introduction Before You Begin Conventions Prerequisites Components Used Bridging Transparent Bridging Configuration Examples Example 1: Simple
Configuring Transparent Bridging Document ID: 10676 Contents Introduction Before You Begin Conventions Prerequisites Components Used Bridging Transparent Bridging Configuration Examples Example 1: Simple
LAN Interconnection. different interconnecting devices, many approaches Vasile Dadarlat- Local Area Computer Networks
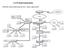 LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
Full file at
 ch02 True/False Indicate whether the statement is true or false. 1. The number of nodes on a network and the length of cable used influence the quality of communication on the network. 2. Repeaters and
ch02 True/False Indicate whether the statement is true or false. 1. The number of nodes on a network and the length of cable used influence the quality of communication on the network. 2. Repeaters and
Chapter Seven. Local Area Networks: Part 1. Data Communications and Computer Networks: A Business User s Approach Seventh Edition
 Chapter Seven Local Area Networks: Part 1 Data Communications and Computer Networks: A Business User s Approach Seventh Edition After reading this chapter, you should be able to: State the definition of
Chapter Seven Local Area Networks: Part 1 Data Communications and Computer Networks: A Business User s Approach Seventh Edition After reading this chapter, you should be able to: State the definition of
Automatic Repeat Request Data Link Layer Traffic Management
 Automatic Repeat Request Data Link Layer Traffic Management Reliable Communications with Retransmission How to transport data units over an unreliable data link in a reliable way? End to End E.g.. TCP
Automatic Repeat Request Data Link Layer Traffic Management Reliable Communications with Retransmission How to transport data units over an unreliable data link in a reliable way? End to End E.g.. TCP
Communication Networks - 3 general areas: data communications, networking, protocols
 Communication Networks - Overview CSE 3213 Fall 2011 1 7 September 2011 Course Content 3 general areas: data communications, networking, protocols 1. Data communications: basic concepts of digital communications
Communication Networks - Overview CSE 3213 Fall 2011 1 7 September 2011 Course Content 3 general areas: data communications, networking, protocols 1. Data communications: basic concepts of digital communications
Introduction to LAN Protocols
 CHAPTER 2 Introduction to LAN Protocols This chapter introduces the various media-access methods, transmission methods, topologies, and devices used in a local area network (LAN). Topics addressed focus
CHAPTER 2 Introduction to LAN Protocols This chapter introduces the various media-access methods, transmission methods, topologies, and devices used in a local area network (LAN). Topics addressed focus
Data Link Layer. Our goals: understand principles behind data link layer services: instantiation and implementation of various link layer technologies
 Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
CN [Network Devices]
![CN [Network Devices] CN [Network Devices]](/thumbs/83/88538687.jpg) Q`.1 Explain Repeater. A repeater is a device that operates only at the PHYSICAL layer. A repeater can be used to increase the length of the network by put the effect on the signal. It connects two segments
Q`.1 Explain Repeater. A repeater is a device that operates only at the PHYSICAL layer. A repeater can be used to increase the length of the network by put the effect on the signal. It connects two segments
WANs and Long Distance Connectivity. Introduction
 WANs and Long Distance Connectivity Chapters 2-3 Introduction Previous technologies covered "short" distances Can extend over short distances somewhat with bridges, hubs, repeaters, etc. but still limited
WANs and Long Distance Connectivity Chapters 2-3 Introduction Previous technologies covered "short" distances Can extend over short distances somewhat with bridges, hubs, repeaters, etc. but still limited
Darshan Institute of Engineering & Technology for Diploma Studies
 1. Explain different network devices in detail. Or Explain NIC (Network Interface Card) in detail. Network interface cards are add on cards as hardware cards on the motherboard. This is additional hardware
1. Explain different network devices in detail. Or Explain NIC (Network Interface Card) in detail. Network interface cards are add on cards as hardware cards on the motherboard. This is additional hardware
A LAN is a high-speed data network that covers a relatively small geographic area. It typically connects workstations, personal computers, printers,
 CBCN4103 A LAN is a high-speed data network that covers a relatively small geographic area. It typically connects workstations, personal computers, printers, servers, and other devices. LANs offer computer
CBCN4103 A LAN is a high-speed data network that covers a relatively small geographic area. It typically connects workstations, personal computers, printers, servers, and other devices. LANs offer computer
Chapter 11: Wide-Area Networks and the Internet
 Chapter 11: Wide-Area Networks and the Internet MULTIPLE CHOICE 1. MAN stands for: a. Manchester Access Network c. Metropolitan-Area Network b. Multiple-Area Network d. Multiple Access Network 2. Packet
Chapter 11: Wide-Area Networks and the Internet MULTIPLE CHOICE 1. MAN stands for: a. Manchester Access Network c. Metropolitan-Area Network b. Multiple-Area Network d. Multiple Access Network 2. Packet
We are going to see a basic definition of the devices you can find in a corporate wired network, so you can understand basic IT engineering jargon.
 Computer network devices, also known as communication devices, are the backbone of a data communication network. In this category we can find routers, switches, hubs, LAN cards, gateways, modems, hardware
Computer network devices, also known as communication devices, are the backbone of a data communication network. In this category we can find routers, switches, hubs, LAN cards, gateways, modems, hardware
Network Devices,Frame Relay and X.25
 Network Devices,Frame Relay and X.25 Hardware/Networking Devices: Networking hardware may also be known as network equipment computer networking devices. Network Interface Card (NIC): NIC provides a physical
Network Devices,Frame Relay and X.25 Hardware/Networking Devices: Networking hardware may also be known as network equipment computer networking devices. Network Interface Card (NIC): NIC provides a physical
Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005
 Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005 Network and Telecommunications Basics Chapter Outline The telecommunications system Network services
Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005 Network and Telecommunications Basics Chapter Outline The telecommunications system Network services
Introduction to Communication Theory
 Introduction to Communication Theory Lijun Qian Department of Electrical Engineering PVAMU Figure 1 Elements of a communication system. Elements of a communication system Transmitter To convert the message
Introduction to Communication Theory Lijun Qian Department of Electrical Engineering PVAMU Figure 1 Elements of a communication system. Elements of a communication system Transmitter To convert the message
Data Communications. Connecting Devices
 Data Communications Connecting Devices Connecting Devices Networks do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments of LANs, we use
Data Communications Connecting Devices Connecting Devices Networks do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments of LANs, we use
GAYATRI COMPUTERS Prepared by : VENKAT.G 1. Module 1: NETWORK BASICS
 GAYATRI COMPUTERS Prepared by : VENKAT.G 1 What is Networking? Module 1: NETWORK BASICS Networking: Connecting two or more computers or network devices(routers/print Servers / Firewall Devices..etc) for
GAYATRI COMPUTERS Prepared by : VENKAT.G 1 What is Networking? Module 1: NETWORK BASICS Networking: Connecting two or more computers or network devices(routers/print Servers / Firewall Devices..etc) for
Switching & ARP Week 3
 Switching & ARP Week 3 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 Many Slides courtesy of Tony Chen 1 Ethernet Using Switches In the last few years, switches have quickly
Switching & ARP Week 3 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 Many Slides courtesy of Tony Chen 1 Ethernet Using Switches In the last few years, switches have quickly
Review. Error Detection: CRC Multiple access protocols. LAN addresses and ARP Ethernet. Slotted ALOHA CSMA/CD
 Review Error Detection: CRC Multiple access protocols Slotted ALOHA CSMA/CD LAN addresses and ARP Ethernet Some slides are in courtesy of J. Kurose and K. Ross Overview Ethernet Hubs, bridges, and switches
Review Error Detection: CRC Multiple access protocols Slotted ALOHA CSMA/CD LAN addresses and ARP Ethernet Some slides are in courtesy of J. Kurose and K. Ross Overview Ethernet Hubs, bridges, and switches
Configuring Banyan VINES
 Configuring Banyan VINES This chapter describes how to configure Banyan VINES and provides configuration examples. For a complete description of the VINES commands in this chapter, refer to the Banyan
Configuring Banyan VINES This chapter describes how to configure Banyan VINES and provides configuration examples. For a complete description of the VINES commands in this chapter, refer to the Banyan
Networks 15.2 Multiplexing Technologies Access Networks 15.5 Common Peripheral Interfaces
 Chapter 15 Computer and Multimedia Networks 15.11 Basics of Computer and Multimedia Networks 15.2 Multiplexing Technologies 15.3 LAN and WAN 15.4 Access Networks 15.5 Common Peripheral Interfaces 15.6
Chapter 15 Computer and Multimedia Networks 15.11 Basics of Computer and Multimedia Networks 15.2 Multiplexing Technologies 15.3 LAN and WAN 15.4 Access Networks 15.5 Common Peripheral Interfaces 15.6
Lecture 9: Bridging. CSE 123: Computer Networks Alex C. Snoeren
 Lecture 9: Bridging CSE 123: Computer Networks Alex C. Snoeren Lecture 9 Overview Finishing up media access Ethernet Contention-free methods (rings) Moving beyond one wire Link technologies have limits
Lecture 9: Bridging CSE 123: Computer Networks Alex C. Snoeren Lecture 9 Overview Finishing up media access Ethernet Contention-free methods (rings) Moving beyond one wire Link technologies have limits
Chapter 5. The Network Layer. Network Layer Design Isues. Store-and-Forward Packet Switching 10/7/2010. Implementation of Connectionless Service
 Network Layer Design Isues Chapter 5 The Network Layer Store-and-Forward Packet Switching Services Provided to the Transport Layer Implementation of Connectionless Service Implementation of Connection-Oriented
Network Layer Design Isues Chapter 5 The Network Layer Store-and-Forward Packet Switching Services Provided to the Transport Layer Implementation of Connectionless Service Implementation of Connection-Oriented
Chapter 5. The Network Layer
 Chapter 5 The Network Layer 1 Network Layer Design Isues Store-and-Forward Packet Switching Services Provided to the Transport Layer Implementation of Connectionless Service Implementation of Connection-Oriented
Chapter 5 The Network Layer 1 Network Layer Design Isues Store-and-Forward Packet Switching Services Provided to the Transport Layer Implementation of Connectionless Service Implementation of Connection-Oriented
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Administrivia Homework I out later today, due next Thursday Today: Link Layer (cont.)
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Administrivia Homework I out later today, due next Thursday Today: Link Layer (cont.)
Introducing Campus Networks
 Cisco Enterprise Architecture Introducing Campus Networks 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Campus Data Center Combines switching
Cisco Enterprise Architecture Introducing Campus Networks 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Campus Data Center Combines switching
