1.3 Analyzing the performance of various configurations and protocols
|
|
|
- Derick Christopher Atkinson
- 5 years ago
- Views:
Transcription
1 1.3 Analyzing the performance of various configurations and protocols Original TCP versus the above modified one: To compare the performance between the operation of TCP with congestion control and the operation of TCP as implemented. The main objective is for students to examine how TCP responds to a congested network. The concepts involved in the lab include network congestion and the host responsibilities for communicating over a network. This lab requires three PC s connected to a switch. One PC is designated as the target host and the other two PC s will transfer a file from the target host using FTP. A load is placed on the network to simulate congestion and the file is transferred, first by the host using the normal TCP and then by the host using the modified version. This procedure is performed multiple times to determine average statistics. The students are then asked to summarize the results and draw conclusions about the performance differences and the underlying implications for hosts operating in a network environment. REQUIREMENTS: One Linux(fedora) Virtual PC s. Two Windows(xp) Virtual PC s. One Windows 7 PC with VMware Workstation FTP-Application layer protocol TCP-Transport layer protocol Internet connection VMware Workstation Wireshark-win rc1 Class C IP Address. NETWORK TOPOLOGY: 1
2 SIMULATION OUTPUT PROCEDURES: 1. Double Click pc-1 and get into Desktop 2. Click the traffic generator 3. Configure as follows 4. Click send button. 5. View the simulation tab 6. And click the Auto Capture/Play button see the animation 7. Increase the Load by providing more PING command 8. Note the packet loss 9. Plot the summary and performance report based on the above study. 2
3 FTP TRAFFIC GENERATION: REAL TIME PROCEDURES: File Transfer Protocol (FTP) is the standard mechanism provided by TCP/IP for copying a file from one host to another. 3
4 FTP uses the services of TCP. It needs two TCP connections. The well-known port 21 is used for the control connection and the well-known port 20 for the data connection. FTP OPERATIONS: USING CONTROL CONNECTION: USING THE DATA CONNECTION: COMMAND PROCESSING: FILE TRANSFER: 4
5 INSTALLING FTP SERVER: STEP1: Start the virtual PC s. Installing FTP server in your Linux Operating system. STEP2: Login to Root user account. STEP3: Installing FTP server from the internet.using Command line Installation. Installing FTP server from the internet. Using GUI mode installation. 5
6 STEP4: Power on the FTP server using Linux commands. (chkconfig vsftpd on) STEP5: Start the FTP server service. Using this command (service vsftpd start) STEP6: Check the FTP server status. Using this command (service vsftpd status) STEP7: Add tcp protocol entries into our Iptables. iptables -A INPUT -p tcp --dport 20 -j ACCEPT iptables -A INPUT -p tcp --dport 21 -j ACCEPT 6
7 STEP8: Enable Linux Machine Firewall. Using this command (setup). STEP9: Assign the ip address to windows xp clients. Host A IP address 7
8 Host B ip address STEP10: Assign the IP Address to FTP server STEP11: Edit the ftp server configuration file. #vi /etc/vsftpd/vsftpd.con 8
9 STEP12: Make some changes and add some lines to your vsftpd.conf configuration file. local_root=public_html use_localtime=yes STEP13: Remove the # symbol. And make some changes. 9
10 STEP14: Add this two lines end of the file. Then save and quit. (:wq). local_root=public_html use_localtime=yes STEP15: Add your FTP login user account to your Chroot_list file. #vi /etc.vsftpd.chroot_list 10
11 Save and quit chroot_list file (Esc:wq). STEP16: Restart the ftp Server (#service vsftpd restart) STEP17: Check the FTP server status (#service vsftpd status) Our FTP server configuration has been completed 11
12 VERIFY FTP SERVER CONFIGURATION: Command Line Interface Login Method Go to Host A or Host B Open host A command prompt window. Type the following command C:/>ftp Enter your FTP Server user name and password to login your FTP server. Type the ftp>ls command List out the ftp server file. 12
13 Get the file from FTP server using ftp>recv sample command Graphical User Interface Login Method: Open Internet Explorer Browser. Type the FTP server address in the address bar. ftp://
14 Enter your FTP server user name and password to login. User name: fedora Password: namasiva Ftp server has been successfully login. Copy files from FTP server. Using normal copy and paste operation. 14
15 Paste the file on your Host A Desktop location. View the file content. Just open it. 15
16 HOST A TCP Protocol Analyzing: Open Wireshark application and select the LAN interface. Start the capture button before the FTP server login. All the incoming and outgoing information s are captured. Our FTP server Login id password also captured. Close the FTP server connection: using Ftp>quit command RESULT: 16
17 Thus the experiment was configured successfully. 17
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic. Topology. Objectives. Background / Scenario
 BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
Introduction to Firewalls using IPTables
 Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
How to open ports in the DSL router firmware version 2.xx and above
 How to open ports in the DSL router firmware version 2.xx and above This example shows how to open port 3389 (which is used by Remote Desktop service) in the DSL router running firmware version 2.xx or
How to open ports in the DSL router firmware version 2.xx and above This example shows how to open port 3389 (which is used by Remote Desktop service) in the DSL router running firmware version 2.xx or
Use of the TCP/IP Protocols and the OSI Model in Packet Tracer
 Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
iptables and ip6tables An introduction to LINUX firewall
 7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
7 19-22 November, 2017 Dhaka, Bangladesh iptables and ip6tables An introduction to LINUX firewall Imtiaz Rahman SBAC Bank Ltd AGENDA iptables and ip6tables Structure Policy (DROP/ACCEPT) Syntax Hands on
Packet Tracer: Novice Session 2007 Cisco Systems, Inc. All rights reserved. Cisco Public. Packet Tracer: Novice Session
 Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Virtual-Machine-Based Network Exercises for Introductory Computer Networking Courses
 Virtual-Machine-Based Network Exercises for Introductory Computer Networking Courses Robert Montante Bloomsburg University of Pennsylvania Encore Presentation CCSC-Northeastern April 7, 2017 Overview First
Virtual-Machine-Based Network Exercises for Introductory Computer Networking Courses Robert Montante Bloomsburg University of Pennsylvania Encore Presentation CCSC-Northeastern April 7, 2017 Overview First
Lab I: Using tcpdump and Wireshark
 Objectives To get the student familiar with basic network protocol analyzer, tools and equipment used in later labs, including tcpdump and Wireshark. Lab Readings Go to http://www.tcpdump.org/tcpdump_man.html
Objectives To get the student familiar with basic network protocol analyzer, tools and equipment used in later labs, including tcpdump and Wireshark. Lab Readings Go to http://www.tcpdump.org/tcpdump_man.html
Lab 1: Packet Sniffing and Wireshark
 Lab 1: Packet Sniffing and Wireshark Fengwei Zhang Wayne State University Course: Cyber Security Practice 1 Packet Sniffer Packet sniffer is a basic tool for observing network packet exchanges in a computer
Lab 1: Packet Sniffing and Wireshark Fengwei Zhang Wayne State University Course: Cyber Security Practice 1 Packet Sniffer Packet sniffer is a basic tool for observing network packet exchanges in a computer
CNPE Communications and Networks Lab Book: Data Transmission Over Digital Networks
 Lab Book: Data Transmission Over Digital Networks Contents Data Transmission Over Digital Networks... 3 Lab Objectives... 3 Lab Resources... 3 Task 1 Build the Home Network... 3 Task 2 Configure IP Addresses...
Lab Book: Data Transmission Over Digital Networks Contents Data Transmission Over Digital Networks... 3 Lab Objectives... 3 Lab Resources... 3 Task 1 Build the Home Network... 3 Task 2 Configure IP Addresses...
LAB 3 Optimizing Quality of Service
 LAB 3 Optimizing Quality of Service Objectives In this lab students are introduced to the ladder topology, gain an understanding of what negatively effects a network s Quality of Service, and learn how
LAB 3 Optimizing Quality of Service Objectives In this lab students are introduced to the ladder topology, gain an understanding of what negatively effects a network s Quality of Service, and learn how
Connect the PC and Log into the GUI
 CHAPTER 3 Connect the PC and Log into the GUI This chapter explains how to connect PCs and workstations to the Cisco ONS 15600 SDH and how to log into Cisco Transport Controller (CTC) software, which is
CHAPTER 3 Connect the PC and Log into the GUI This chapter explains how to connect PCs and workstations to the Cisco ONS 15600 SDH and how to log into Cisco Transport Controller (CTC) software, which is
CIS 192 Linux Lab Exercise
 CIS 192 Linux Lab Exercise Lab 8: Samba Spring 2009 Lab 8: Samba The purpose of this lab is to share files among Windows and Linux hosts on a common network. The goal is to browse directories on the Linux
CIS 192 Linux Lab Exercise Lab 8: Samba Spring 2009 Lab 8: Samba The purpose of this lab is to share files among Windows and Linux hosts on a common network. The goal is to browse directories on the Linux
Packet Tracer: Novice Session. Packet Tracer: Novice Session 2007 Cisco Systems, Inc. All rights reserved. Cisco Public
 Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
CS 716: Introduction to communication networks. Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay
 CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
PT Activity 5.6.1: Packet Tracer Skills Integration Challenge Topology Diagram
 Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
WINDOWS NT 4.0 USER GUIDE
 WINDOWS NT 4.0 USER GUIDE This guide will assist you in connecting to Nauticom using your Windows NT 4.0 Operating System. Click Start. Select Settings, and click Control Panel. Double click the Network
WINDOWS NT 4.0 USER GUIDE This guide will assist you in connecting to Nauticom using your Windows NT 4.0 Operating System. Click Start. Select Settings, and click Control Panel. Double click the Network
Access Switch VLAN Y Y.1 /24
 Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Lab Capturing and Analyzing Network Traffic
 Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
Assignment 3 Firewalls
 LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
Lab - Using Wireshark to Examine TCP and UDP Captures
 Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Lab 3a Using the vi editor
 Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Immotec Systems, Inc. SQL Server 2008 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
NETOP HOST ON A TERMINAL SERVER
 27.09.2017 NETOP HOST ON A TERMINAL SERVER Contents 1 Introduction... 2 1.1 Incoming traffic... 2 1.2 Outgoing traffic... 2 2 Using a Netop Gateway with the Netop Host on a Terminal Server... 3 2.1 Install
27.09.2017 NETOP HOST ON A TERMINAL SERVER Contents 1 Introduction... 2 1.1 Incoming traffic... 2 1.2 Outgoing traffic... 2 2 Using a Netop Gateway with the Netop Host on a Terminal Server... 3 2.1 Install
Computer Security Spring Assignment 4. The purpose of this assignment is to gain experience in network security and network attacks.
 Computer Security Spring 2015 CS 4351/5352 Professor L. Longpré Introduction: Assignment 4 The purpose of this assignment is to gain experience in network security and network attacks. General description:
Computer Security Spring 2015 CS 4351/5352 Professor L. Longpré Introduction: Assignment 4 The purpose of this assignment is to gain experience in network security and network attacks. General description:
CS356 Lab NIL (Lam) In this lab you will learn: Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore!
 CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
UNIVERSITY OF BOLTON SCHOOL OF CREATIVE TECHNOLOGIES COMPUTER AND NETWORK SECURITY SEMESTER TWO EXAMINATIONS 2016/2017 NETWORK SECURITY
 [CRT03] UNIVERSITY OF BOLTON SCHOOL OF CREATIVE TECHNOLOGIES COMPUTER AND NETWORK SECURITY SEMESTER TWO EXAMINATIONS 2016/2017 NETWORK SECURITY MODULE NO: CPU6004 Date: Tuesday 16 th May 2017 Time: 14:00-16:00
[CRT03] UNIVERSITY OF BOLTON SCHOOL OF CREATIVE TECHNOLOGIES COMPUTER AND NETWORK SECURITY SEMESTER TWO EXAMINATIONS 2016/2017 NETWORK SECURITY MODULE NO: CPU6004 Date: Tuesday 16 th May 2017 Time: 14:00-16:00
CNBK Communications and Networks Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems
 Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
Lab Book: Purpose of Hardware and Protocols Associated with Networking Computer Systems Contents Purpose of Hardware and Protocols Associated with Computer Networks... 3 Lab Objectives... 3 Lab Resources...
IT INFRASTRUCTURE PROJECT PHASE I INSTRUCTIONS
 Project Overview IT INFRASTRUCTURE PROJECT PHASE I INSTRUCTIONS This project along with the Phase II IT Infrastructure Project will help you understand how a network administrator improves network performance
Project Overview IT INFRASTRUCTURE PROJECT PHASE I INSTRUCTIONS This project along with the Phase II IT Infrastructure Project will help you understand how a network administrator improves network performance
This material is based on work supported by the National Science Foundation under Grant No
 Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
Source: http://en.wikipedia.org/wiki/file:firewall.png This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations
NETWORK CONFIGURATION AND SERVICES. route add default gw /etc/init.d/apache restart
 NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
FACILITY REQUIREMENTS GUIDE VMware Virtual Data Center (VDC/vClass) Cloud Lab Environment Revision 18 Feb 24th, 2017
 FACILITY REQUIREMENTS GUIDE VMware Virtual Data Center (VDC/vClass) Cloud Lab Environment Revision 18 Feb 24th, 2017 This document identifies the classroom, equipment, and networking requirements necessary
FACILITY REQUIREMENTS GUIDE VMware Virtual Data Center (VDC/vClass) Cloud Lab Environment Revision 18 Feb 24th, 2017 This document identifies the classroom, equipment, and networking requirements necessary
WINDOWS 95 SETUP GUIDE
 WINDOWS 95 SETUP GUIDE This guide will assist you in connecting to Nauticom using your Windows 95 Operating System. Double-click My Computer. Look for a folder called Dial-Up Networking. If you do not
WINDOWS 95 SETUP GUIDE This guide will assist you in connecting to Nauticom using your Windows 95 Operating System. Double-click My Computer. Look for a folder called Dial-Up Networking. If you do not
Stateless Firewall Implementation
 Stateless Firewall Implementation Network Security Lab, 2016 Group 16 B.Gamaliel K.Noellar O.Vincent H.Tewelde Outline : I. Enviroment Setup II. Today s Task III. Conclusion 2 Lab Objectives : After this
Stateless Firewall Implementation Network Security Lab, 2016 Group 16 B.Gamaliel K.Noellar O.Vincent H.Tewelde Outline : I. Enviroment Setup II. Today s Task III. Conclusion 2 Lab Objectives : After this
Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development
 Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Immotec Systems, Inc. SQL Server 2008 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
The following virtual machines are required for completion of this lab: Exercise I: Mapping a Network Topology Using
 Module 08: Sniffers Objective The objective of this lab is to make students learn to sniff a network and analyze packets for any attacks on the network. The primary objectives of this lab are to: Sniff
Module 08: Sniffers Objective The objective of this lab is to make students learn to sniff a network and analyze packets for any attacks on the network. The primary objectives of this lab are to: Sniff
CS 4351/5352 Computer Security, assignment 4. Due date: Sunday, May 18, noon.
 CS 4351/5352 Computer Security, assignment 4. Due date: Sunday, May 18, noon. This assignment may be done individually, or in a group of 2. You can discuss general concepts about the assignment (e.g.,
CS 4351/5352 Computer Security, assignment 4. Due date: Sunday, May 18, noon. This assignment may be done individually, or in a group of 2. You can discuss general concepts about the assignment (e.g.,
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
Firewall Simulation COMP620
 Firewall Simulation COMP620 Firewall Simulation The simulation allows participants to configure their own simulated firewalls using Cisco-like syntax. Participants can take benign or malicious actions
Firewall Simulation COMP620 Firewall Simulation The simulation allows participants to configure their own simulated firewalls using Cisco-like syntax. Participants can take benign or malicious actions
CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal
 CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal Tasks: Time: 2:00 hrs (Task 1-6 should take 45 min; the rest of the time is for Ethereal) 1 - Verify that TCP/IP is installed on
CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal Tasks: Time: 2:00 hrs (Task 1-6 should take 45 min; the rest of the time is for Ethereal) 1 - Verify that TCP/IP is installed on
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Hands-On Activity. Firewall Simulation. Simulated Network. Firewall Simulation 3/19/2010. On Friday, February 26, we will be meeting in
 Hands-On Activity Firewall Simulation COMP620 On Friday, February 26, we will be meeting in the Graham 212 lab to participate in a firewall configuration simulation. This simulator was written by Dr. Williams
Hands-On Activity Firewall Simulation COMP620 On Friday, February 26, we will be meeting in the Graham 212 lab to participate in a firewall configuration simulation. This simulator was written by Dr. Williams
Lab: Configure Wireless Security
 16.3.1 Lab: Configure Wireless Security Introduction Print and complete this lab. In this lab, you will configure and test the wireless settings on the Linksys WRT300N. Recommended Equipment Two computers
16.3.1 Lab: Configure Wireless Security Introduction Print and complete this lab. In this lab, you will configure and test the wireless settings on the Linksys WRT300N. Recommended Equipment Two computers
Packet Tracer Simulation - TCP and UDP Communications
 Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation
Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Communication protocols and services
 This chapter describes various protocols and that may be enabled on Modberry. SSH Connection SSH service is started up on boot and already preinstalled and configured. You may access your device through
This chapter describes various protocols and that may be enabled on Modberry. SSH Connection SSH service is started up on boot and already preinstalled and configured. You may access your device through
Port Forwarding Technical Support Guide
 Port Forwarding Technical Support Guide Copyright Copyright 2015 NetComm Wireless Limited. All rights reserved. The information contained herein is proprietary to NetComm Wireless. No part of this document
Port Forwarding Technical Support Guide Copyright Copyright 2015 NetComm Wireless Limited. All rights reserved. The information contained herein is proprietary to NetComm Wireless. No part of this document
Lab 4: Network Packet Capture and Analysis using Wireshark
 Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
APPLICATION NOTE AN0004 CHANGING THE IP ADDRESS ON AN EWSi PORTAL PLUS CONTROLLER WITH WINDOWS 7
 INTRODUCTION Before installing an EWSi Portal Plus Controller on a network it is necessary to change the default IP address of the unit to one supplied by the network administrator. The following screen
INTRODUCTION Before installing an EWSi Portal Plus Controller on a network it is necessary to change the default IP address of the unit to one supplied by the network administrator. The following screen
Department Of Computer Science
 Department Of Computer Science Laboratory Manual Prepared By: Muhammad Nouman Farooq Lecturer and Course Coordinator Course: Computer Communication and Networks (CS-205) Page 1 of 43 Table of Contents
Department Of Computer Science Laboratory Manual Prepared By: Muhammad Nouman Farooq Lecturer and Course Coordinator Course: Computer Communication and Networks (CS-205) Page 1 of 43 Table of Contents
WA2342 NoSQL Systems Comparison. Lab Server VM Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
LevelOne FBR User s Manual. 1W, 4L 10/100 Mbps ADSL Router. Ver
 LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
Lab Configure Cisco IOS Firewall CBAC on a Cisco Router
 Lab 3.8.3 Configure Cisco IOS Firewall CBAC on a Cisco Router Objective Scenario Topology Estimated Time: 35 minutes Number of Team Members: Two teams with four students per team In this lab, students
Lab 3.8.3 Configure Cisco IOS Firewall CBAC on a Cisco Router Objective Scenario Topology Estimated Time: 35 minutes Number of Team Members: Two teams with four students per team In this lab, students
Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs
 Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs Intended Audience This document is aimed at IT technical support professionals
Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs Intended Audience This document is aimed at IT technical support professionals
TerraSAR-X Services Data Download via FTPS or Aspera Connect. Version 1.1. AIRBUS DEFENCE AND SPACE Intelligence
 TerraSAR-X Services Data Download via FTPS or Aspera Connect Version 1.1 AIRBUS DEFENCE AND SPACE Intelligence 1 Common For accessing and downloading TerraSAR-X Services data either FTPS or Aspera Connect
TerraSAR-X Services Data Download via FTPS or Aspera Connect Version 1.1 AIRBUS DEFENCE AND SPACE Intelligence 1 Common For accessing and downloading TerraSAR-X Services data either FTPS or Aspera Connect
[Pick the date] DS-300 Configuration Guide v 5.7
![[Pick the date] DS-300 Configuration Guide v 5.7 [Pick the date] DS-300 Configuration Guide v 5.7](/thumbs/95/123865984.jpg) DS-300 Version 5.7 Web based configuration Troubleshooting Guide 1. LOGIN SETTINGS By Default, after getting a DHCP IP address from DS-300, open any Internet browser and type in the URL address for Customer
DS-300 Version 5.7 Web based configuration Troubleshooting Guide 1. LOGIN SETTINGS By Default, after getting a DHCP IP address from DS-300, open any Internet browser and type in the URL address for Customer
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab)
 PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
COMPUTER NETWORKING LAB EXERCISES (TP) 4
 Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions
 Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
Firewalls. IT443 Network Security Administration Slides courtesy of Bo Sheng
 Firewalls IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Internet Security Mechanisms Prevent: Firewall, IPsec, SSL Detect: Intrusion Detection Survive/ Response: Recovery, Forensics
Firewalls IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Internet Security Mechanisms Prevent: Firewall, IPsec, SSL Detect: Intrusion Detection Survive/ Response: Recovery, Forensics
Lab 8: Firewalls ASA Firewall Device
 Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Network Security Laboratory 23 rd May STATEFUL FIREWALL LAB
 Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Practical Network Defense Labs
 Practical Network Defense Labs ABOUT This document showcases my practical hands-on engagements in the elearnsecurity HERA labs environment for the Network Defense Professional certification course. I utilized
Practical Network Defense Labs ABOUT This document showcases my practical hands-on engagements in the elearnsecurity HERA labs environment for the Network Defense Professional certification course. I utilized
ACCESSING TIPQA THROUGH MOOG S SUPPLIER PORTAL
 ACCESSING TIPQA THROUGH MOOG S SUPPLIER PORTAL PROCESS FLOW PURPOSE: This document illustrates how to access the TIPQA software application using a Partners account. If you need assistance with installation
ACCESSING TIPQA THROUGH MOOG S SUPPLIER PORTAL PROCESS FLOW PURPOSE: This document illustrates how to access the TIPQA software application using a Partners account. If you need assistance with installation
HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS
 HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS How To Securely Configure a Linux Host to Run Containers To run containers securely, one must go through a multitude of steps to ensure that a)
HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS How To Securely Configure a Linux Host to Run Containers To run containers securely, one must go through a multitude of steps to ensure that a)
Lab - Configure the Firewall in Windows 8
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Turn On Windows Firewall Manually Windows 7 Remote Desktop
 Turn On Windows Firewall Manually Windows 7 Remote Desktop Learn how to use advanced settings for the Windows 7 firewall to create exceptions for specific services. In the right 7 firewall. Don't use Remote
Turn On Windows Firewall Manually Windows 7 Remote Desktop Learn how to use advanced settings for the Windows 7 firewall to create exceptions for specific services. In the right 7 firewall. Don't use Remote
NET323 D: NETWORKS PROTOCOLS
 1 NET323 D: NETWORKS PROTOCOLS Networks and Communication Systems Department TA. Anfal AlHazzaa Lab # 2 : Hub Vs. Switch Lab Objectives 2 To create two small LANs contain three PCs using Packet Tracer
1 NET323 D: NETWORKS PROTOCOLS Networks and Communication Systems Department TA. Anfal AlHazzaa Lab # 2 : Hub Vs. Switch Lab Objectives 2 To create two small LANs contain three PCs using Packet Tracer
I m InTouch Installation Guide for the DSL/Cable environment with a Linksys router Models: BEFSRU31, BEFSR41 V.2, BEFSR11
 I m InTouch router configuration p. 1 I m InTouch Installation Guide for the DSL/Cable environment with a Linksys router Models: BEFSRU31, BEFSR41 V.2, BEFSR11 Note: Different models may vary slightly
I m InTouch router configuration p. 1 I m InTouch Installation Guide for the DSL/Cable environment with a Linksys router Models: BEFSRU31, BEFSR41 V.2, BEFSR11 Note: Different models may vary slightly
Computer Security Spring Firewalls. Aggelos Kiayias University of Connecticut
 Computer Security Spring 2008 Firewalls Aggelos Kiayias University of Connecticut Idea: Monitor inbound/ outbound traffic at a communication point Firewall firewall Internet LAN A firewall can run on any
Computer Security Spring 2008 Firewalls Aggelos Kiayias University of Connecticut Idea: Monitor inbound/ outbound traffic at a communication point Firewall firewall Internet LAN A firewall can run on any
Network II Lab 03 Part 01: Ping command in simula on mode
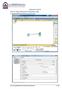 Network II Lab 03 Part 01: Ping command in simula on mode 1. Open the file saved from the previous lab. [Dr. Ahmed ElShafee, ACU Fall 2011, Network II] 1 / 18 2. add simple packet from client to server
Network II Lab 03 Part 01: Ping command in simula on mode 1. Open the file saved from the previous lab. [Dr. Ahmed ElShafee, ACU Fall 2011, Network II] 1 / 18 2. add simple packet from client to server
Connect the PC and Log into the GUI
 CHAPTER 3 Connect the PC and Log into the GUI This chapter explains how to connect PCs and workstations to the Cisco ONS 15454 and how to log into Cisco Transport Controller (CTC) software, which is the
CHAPTER 3 Connect the PC and Log into the GUI This chapter explains how to connect PCs and workstations to the Cisco ONS 15454 and how to log into Cisco Transport Controller (CTC) software, which is the
Step-by-Step Guide to Ansur Executive 3.0 With or without Electronic Signatures
 Step-by-Step Guide to Ansur Executive 3.0 With or without Electronic Signatures Table of Contents Background...3 Set up Central PC:...4 Configuring SQL Server 2005:... 11 Ansur Executive Server Installation:...
Step-by-Step Guide to Ansur Executive 3.0 With or without Electronic Signatures Table of Contents Background...3 Set up Central PC:...4 Configuring SQL Server 2005:... 11 Ansur Executive Server Installation:...
Load Balancing Bloxx Web Filter. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Bloxx Web Filter Deployment Guide v1.3.5 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Load Balancing Bloxx Web Filter Deployment Guide v1.3.5 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
A specific IP with specific Ports and Protocols uses a dedicated WAN (Load Balance Policy).
 21. Multiple WAN Vigor 3300Bplus has three WAN interfaces, while Vigor 3300 and Vigor 3300V both have four WAN interfaces. With the Load Balance feature, you can use multiple WAN links simultaneously.
21. Multiple WAN Vigor 3300Bplus has three WAN interfaces, while Vigor 3300 and Vigor 3300V both have four WAN interfaces. With the Load Balance feature, you can use multiple WAN links simultaneously.
CIS 76 VLab Pod Setup
 CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
Connect the PC and Log into the GUI
 CHAPTER 3 This chapter explains how to connect Windows PCs and Solaris workstations to the Cisco ONS 15310-CL and Cisco ONS 15310-MA, and how to log into Cisco Transport Controller (CTC) software. CTC
CHAPTER 3 This chapter explains how to connect Windows PCs and Solaris workstations to the Cisco ONS 15310-CL and Cisco ONS 15310-MA, and how to log into Cisco Transport Controller (CTC) software. CTC
Lab 8: Introduction to Pen Testing (HPING)
 Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Turn On Windows Firewall Manually Windows 7 Remote Desktop Connection
 Turn On Windows Firewall Manually Windows 7 Remote Desktop Connection Learn how to use advanced settings for the Windows 7 firewall to create exceptions for specific services. In the right 7 firewall.
Turn On Windows Firewall Manually Windows 7 Remote Desktop Connection Learn how to use advanced settings for the Windows 7 firewall to create exceptions for specific services. In the right 7 firewall.
Novell VPN Client for Linux
 Novell VPN Client for Linux User and Administrator Guide Novell VPN Client for Linux 1.0 July 17, 2006 USER AND ADMINISTRATOR GUIDE www.novell.com Legal Notices Novell, Inc. makes no representations or
Novell VPN Client for Linux User and Administrator Guide Novell VPN Client for Linux 1.0 July 17, 2006 USER AND ADMINISTRATOR GUIDE www.novell.com Legal Notices Novell, Inc. makes no representations or
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
CCNA R&S: Introduction to Networks. Chapter 7: The Transport Layer
 CCNA R&S: Introduction to Networks Chapter 7: The Transport Layer Frank Schneemann 7.0.1.1 Introduction 7.0.1.2 Class Activity - We Need to Talk Game 7.1.1.1 Role of the Transport Layer The primary responsibilities
CCNA R&S: Introduction to Networks Chapter 7: The Transport Layer Frank Schneemann 7.0.1.1 Introduction 7.0.1.2 Class Activity - We Need to Talk Game 7.1.1.1 Role of the Transport Layer The primary responsibilities
NET Control & NET User. User Manual. Rogev computers
 NET Control & NET User User Manual Rogev computers http://www.rogev.co.il Content 1. System Requirement... 3 1-1 Magic card... 3 1-2 Windows operating system... 3 1-3 Client computers... 3 1-4 Master computer...
NET Control & NET User User Manual Rogev computers http://www.rogev.co.il Content 1. System Requirement... 3 1-1 Magic card... 3 1-2 Windows operating system... 3 1-3 Client computers... 3 1-4 Master computer...
ScopTEL TM IP PBX Software. DNS Server Configuration Wizard
 ScopTEL TM IP PBX Software DNS Server Configuration Wizard Network Module - ifconfig A newly installed server uses DHCP to get an IP address from a DHCP server on the network so make sure the eth0 interface
ScopTEL TM IP PBX Software DNS Server Configuration Wizard Network Module - ifconfig A newly installed server uses DHCP to get an IP address from a DHCP server on the network so make sure the eth0 interface
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
On the left hand side of the screen, click on Setup Wizard and go through the Wizard.
 Q: How do I configure the TEW-435/504BRM (b1) to a DSL, PPPoE connection? A: Step 1 Open your web browser and type the IP address of the TEW-435/504BRM in the address bar. The default IP address is 192.168.0.1.
Q: How do I configure the TEW-435/504BRM (b1) to a DSL, PPPoE connection? A: Step 1 Open your web browser and type the IP address of the TEW-435/504BRM in the address bar. The default IP address is 192.168.0.1.
LifeKeeper for Windows Module 3: Configuration
 LifeKeeper for Windows Module 3: Configuration Learning Objectives At the end of this module, you will understand: How to use the LifeKeeper GUI client to configure and monitor various aspects of clustered
LifeKeeper for Windows Module 3: Configuration Learning Objectives At the end of this module, you will understand: How to use the LifeKeeper GUI client to configure and monitor various aspects of clustered
WA2592 Applied Data Science and Big Data Analytics. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc.
 WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
Lab 1: Creating Secure Architectures (Revision)
 Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
Installing Nagios Log Server with VMware Workstation Player
 LS Installing Nagios Log Server with VMware Workstation Player This document is intended to outline the steps required to install Nagios Log Server within VMware Workstation Player. Still need installation
LS Installing Nagios Log Server with VMware Workstation Player This document is intended to outline the steps required to install Nagios Log Server within VMware Workstation Player. Still need installation
Experiment 3: Protocol Visualization with Packet Tracer
 Experiment 3: Protocol Visualization with Packet Tracer Learning Objectives: Explore Packet Tracer Real-time mode Explore the Logical Workspace Explore Packet Tracer operation Connect devices Examine a
Experiment 3: Protocol Visualization with Packet Tracer Learning Objectives: Explore Packet Tracer Real-time mode Explore the Logical Workspace Explore Packet Tracer operation Connect devices Examine a
Using the SSM Administration Console
 CHAPTER 6 Your user role controls whether you can access the SSM Administration Console. The following information is included in this section: SSM Administration Console Overview, page 6-1 Launching the
CHAPTER 6 Your user role controls whether you can access the SSM Administration Console. The following information is included in this section: SSM Administration Console Overview, page 6-1 Launching the
Deploy IBM Spectrum Control Virtual Appliance into VMware Workstation V10.0 or later IBM
 Deploy IBM Spectrum Control Virtual Appliance into VMware Workstation V10.0 or later IBM ii Deploy IBM Spectrum Control Virtual Appliance into VMware Workstation V10.0 or later Contents Deploy IBM Spectrum
Deploy IBM Spectrum Control Virtual Appliance into VMware Workstation V10.0 or later IBM ii Deploy IBM Spectrum Control Virtual Appliance into VMware Workstation V10.0 or later Contents Deploy IBM Spectrum
Ftp Command Line Manual Windows Example Port 22
 Ftp Command Line Manual Windows Example Port 22 Session, Logging, Console/scripting mode, Operations, Configuration enables passive ( =on ) or active ( =off ) transfer mode (FTP protocol only). winscp.exe
Ftp Command Line Manual Windows Example Port 22 Session, Logging, Console/scripting mode, Operations, Configuration enables passive ( =on ) or active ( =off ) transfer mode (FTP protocol only). winscp.exe
Lab #9: Basic Linux Networking
 CTEC1767 Data Communications & Networking 2017 Lab #9: Basic Linux Networking Understanding Linux networks starts with understanding Linux network commands and the information they provide. We will use
CTEC1767 Data Communications & Networking 2017 Lab #9: Basic Linux Networking Understanding Linux networks starts with understanding Linux network commands and the information they provide. We will use
