Malware Of The Day What s goin on here???
|
|
|
- Chester Blair
- 5 years ago
- Views:
Transcription
1 What s goin on here??? Hashes O Houlihan 87a28a a37fc229b3aa3afe97 5e4ddd2c5e6133aa409fdc9af0740e0f sha1 fa513c65cded25a7992e2b0ab03c5dd5c6d0fc2282cd64a1e11a387a3341ce18 - sha256 Yum; fresh warez, says it s not found on virustotal This one lives forever Womp womp womp
2 What s dumpbin got to say? Just a DLL; what are the exports Chmhlpr.dll??
3 Let s see the imports and save to share Paste of imports data Microsoft (R) COFF/PE Dumper Version Copyright (C) Microsoft Corporation. All rights reserved. Dump of file mikrotik-aids.bin File Type: DLL Section contains the following imports: msvcrt.dll BC Import Address Table 1000A024 Import Name Table
4 56B wcstoul 3CE _vsnwprintf 63 _CxxThrowException 158 _except_handler3 2EB _onexit 242 _lock 3A6 _unlock 101 _amsg_exit 1D5 _initterm 6A _XcptFilter 4EA memcpy 4EE memset 4FF realloc 3C8 _vsnprintf 564 wcsstr 32F _snprintf 55C wcsncpy 4DE malloc 339 _snwprintf 52F swscanf 50B sprintf 3EF _wcsicmp 480 atoi 513 strchr 526 strstr 551 wcschr 520 strncpy 485 calloc 4A6 free 362 _strlwr 8D dllonexit 4E9 memcmp CRYPT32.dll C Import Address Table 10009EA4 Import Name Table E4 CryptUnprotectData WS2_32.dll Import Address Table 10009FC8 Import Name Table
5 Ordinal 13 Ordinal 1 2E WSAEventSelect Ordinal 9 Ordinal WSASocketA Ordinal 7 3A WSAIoctl Ordinal 52 Ordinal WSACreateEvent Ordinal WSAConnect Ordinal 23 Ordinal 111 Ordinal 18 Ordinal 2 Ordinal 19 Ordinal 22 1F WSACloseEvent Ordinal 12 Ordinal 3 KERNEL32.dll Import Address Table 10009EAC Import Name Table 517 SetLastError 2E9 GetSystemDefaultUILanguage E5 CreateMutexW 281 GetModuleHandleW 5AC VirtualAllocEx 5B2 VirtualProtectEx 5AF VirtualFreeEx 582 TlsFree 26E GetLocaleInfoW 166 EnumUILanguagesW 31D GetUserDefaultUILanguage 28E GetNativeSystemInfo 2F2 GetSystemTime 581 TlsAlloc 584 TlsSetValue 583 TlsGetValue 310 GetTickCount 2F4 GetSystemTimeAsFileTime
6 224 GetCurrentProcessId 228 GetCurrentThreadId 43C QueryPerformanceCounter 550 SetUnhandledExceptionFilter 590 UnhandledExceptionFilter 56F TerminateProcess 36B InterlockedCompareExchange 36E InterlockedExchange 4BA RtlUnwind 34D HeapAlloc 351 HeapFree 2BA GetProcessHeap 356 HeapSize 223 GetCurrentProcess 5AE VirtualFree 4BB RtlZeroMemory 55F Sleep 5BB WaitForSingleObject 5DD WideCharToMultiByte 3EC MultiByteToWideChar 26A GetLastError 16D ExitProcess 1A1 FindResourceA 1B8 FreeLibrary 3C6 LoadResource 27D GetModuleFileNameW 246 GetExitCodeThread 27C GetModuleFileNameA 8E CloseHandle 123 DeleteFileW 101 CreateThread 61C lstrlena 408 OpenProcess 2B5 GetProcAddress 3C0 LoadLibraryA 27E GetModuleHandleA 3CD LocalFree 616 lstrcpya 227 GetCurrentThread USER32.dll C Import Address Table 10009FA4 Import Name Table 26A PeekMessageW 376 wsprintfw 375 wsprintfa
7 1A9 GetSystemMetrics ADVAPI32.dll Import Address Table 10009E68 Import Name Table 212 OpenProcessToken 296 RegQueryValueExW 260 RegCreateKeyExA 288 RegOpenKeyExA 1A7 LookupAccountSidW 289 RegOpenKeyExW 189 ImpersonateLoggedOnUser 20 AllocateAndInitializeSid 2BC RevertToSelf 133 FreeSid 287 RegOpenKeyA 277 RegEnumKeyExW 258 RegCloseKey 295 RegQueryValueExA OLEAUT32.dll C Import Address Table 10009F94 Import Name Table Ordinal 200 SHLWAPI.dll Import Address Table 10009F9C Import Name Table 14E StrStrIW VERSION.dll Import Address Table 10009FB8 Import Name Table 8 GetFileVersionInfoW 7 GetFileVersionInfoSizeW F VerQueryValueA
8 Summary 2000.data 3000.rdata 2000.reloc 1000.rsrc 7000.text 1000 LineRec s Next we take a REGSHOT and detonate then compare; here s the output Regshot x64 ANSI Comments: Datetime: 2018/8/13 01:24:37, 2018/8/13 01:26:37 Computer: WINDEV1802EVAL, WINDEV1802EVAL Username: User, User Keys deleted: 1 HKLM\SOFTWARE\Microsoft\Windows\Windows Error Reporting\TermReason\4588 Values deleted: 4 HKLM\SOFTWARE\Microsoft\Windows\Windows Error Reporting\TermReason\4588\Terminator: "WerCrashReportFatal" HKLM\SOFTWARE\Microsoft\Windows\Windows Error Reporting\TermReason\4588\Reason: 0x HKLM\SOFTWARE\Microsoft\Windows\Windows Error Reporting\TermReason\4588\CreationTime: E8 AE BE B4 A1 32 D4 01 HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\VolatileNotifications\41C64E6DA2DAE055: Values added: 1 HKLM\HARDWARE\DEVICEMAP\PointerClass\\Device\PointerClass11: "\REGISTRY\MACHINE\SYSTEM\ControlSet001\Services\mouclass" Values modified: 20 HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Notifications\Data\418A073AA3BC3475: F D A AA B 50 7E E0 7E DE B C A6 C A1 9F 5E AB 19 BB CB 79 BA D3 21 BC 00 2D DA D8 7E E5 A5 C F4 A4 C FA 7A BA FE D3 7A B 7D D 00 5F B 50 7E 00 0A F 19 BB B B 19 BB AB 19 BB 00 0F B0 87 B4 00 5F E6 C F A 9C B E A F0 B
9 00 7A C 95 5C 00 0C E 76 B7 00 0F AE C A6 B4 00 B A E E6 C AE A C A6 B4 00 AF A C A6 B A A HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Notifications\Data\418A073AA3BC3475: F D A AA B 50 7E E0 7E DE B C A6 C A1 9F 5E AB 19 BB CB 79 BA D3 21 BC 00 2D DA D8 7E E5 A5 C F4 A4 C FA 7A BA FE D3 7A B 7D C D 00 5F B 50 7E 00 0A F 19 BB B B 19 BB AB 19 BB 00 0F B0 87 B4 00 5F E6 C F A 9C B E A F0 B A C 95 5C 00 0C E 76 B7 00 0F AE C A6 B4 00 B A E E6 C AE A C A6 B4 00 AF A C A6 B A A HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\S \SequenceNumber: 0x F HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\S \SequenceNumber: 0x HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\S \Microsoft.MicrosoftEdge_8wekyb3d8bbwe: F3 02 F1 5A A4 32 D HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\S \Microsoft.MicrosoftEdge_8wekyb3d8bbwe: 17 B8 FB A6 A4 32 D HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\S \\Device\HarddiskVolume2\Windows\System32\OpenWith.exe: B AB C2 E7 D HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\S \\Device\HarddiskVolume2\Windows\System32\OpenWith.exe: B6 93 5B AA A4 32 D HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\SecureTimeEstimated: C D4 01 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\SecureTimeEstimated: C CC D4 01 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\SecureTimeHigh: C8 F1 24 7B D4 01 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\SecureTimeHigh: C8 C0 F7 2D D4 01 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\SecureTimeLow: C8 21 9C B D4 01 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\SecureTimeLow: C8 F0 6E 6A D4 01 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\RunTime\SecureTimeTickCount: 75 F6 0B 02 HKLM\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\RunTime\SecureTimeTickCount: 65 8A HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\S \SequenceNumber: 0x F HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\S \SequenceNumber: 0x HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\S \Microsoft.MicrosoftEdge_8wekyb3d8bbwe: F3 02 F1 5A A4 32 D HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\S \Microsoft.MicrosoftEdge_8wekyb3d8bbwe: 17 B8 FB A6 A4 32 D
10 HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\S \\Device\HarddiskVolume2\Windows\System32\OpenWith.exe: B AB C2 E7 D HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\S \\Device\HarddiskVolume2\Windows\System32\OpenWith.exe: B6 93 5B AA A4 32 D HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\SecureTimeEstimated: C D4 01 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\SecureTimeEstimated: C CC D4 01 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\SecureTimeHigh: C8 F1 24 7B D4 01 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\SecureTimeHigh: C8 C0 F7 2D D4 01 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\SecureTimeLow: C8 21 9C B D4 01 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\SecureTimeLow: C8 F0 6E 6A D4 01 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\RunTime\SecureTimeTickCount: 75 F6 0B 02 HKLM\SYSTEM\CurrentControlSet\Services\W32Time\SecureTimeLimits\RunTime\SecureTimeTickCount: 65 8A rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\ HRZR_PGYFRFFVBA : AA BB E F B D D F F E 00 4D F F F B D F F F D F F E 00 4D F F F B F 00 6E E F
11 B D D F F E 00 4D F F F B D F F rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\hrzr_pgyfrffvba: AA BD EE B D D F F E 00 4D F F F B D F F F D F F E 00 4D F F F B F 00 6E E F B D D F F E 00 4D F F F B D F F
12 rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\{1np14r77-02r7-4r5q-o744-2ro1nr5198o7} \abgrcnq.rkr: E EF BF BF BF BF BF BF BF BF BF BF FF FF FF FF 10 BD E E6 D3 01 rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\{1np14r77-02r7-4r5q-o744-2ro1nr5198o7} \abgrcnq.rkr: E FB BF BF BF BF BF BF BF BF BF BF FF FF FF FF 10 BD E E6 D3 01 rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\{1np14r77-02r7-4r5q-o744-2ro1nr5198o7} \BcraJvgu.rkr: A 5E 80 BF BF BF BF BF BF BF BF BF BF FF FF FF FF rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\{1np14r77-02r7-4r5q-o744-2ro1nr5198o7} \BcraJvgu.rkr: E BF BF BF BF BF BF BF BF BF BF FF FF FF FF rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\zvpebfbsg.nhgbtrarengrq.{r6on2q SNO-219N-2OR337O7R937}: BF BF BF BF BF BF BF BF BF BF FF FF FF FF A0 6E A2 32 D4 01 rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\zvpebfbsg.nhgbtrarengrq.{r6on2q SNO-219N-2OR337O7R937}: B5 A BF BF BF BF BF BF BF BF BF BF FF FF FF FF A0 6E A2 32 D4 01 rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\p:\hfref\hfre\qrfxgbc\ertfubg-k64-nafv.rkr: BF BF BF BF BF BF BF BF BF BF FF FF FF FF F0 CA 86 5C A4 32 D4 01 rer\userassist\{cebff5cd-ace2-4f4f f41749ea}\count\p:\hfref\hfre\qrfxgbc\ertfubg-k64-nafv.rkr: C8 B BF BF BF BF BF BF BF BF BF BF FF FF FF FF F0 CA 86 5C A4 32 D4 01 Total changes: 26
13 BUT WHAT DOES IT MEAN BAZZLE!!! Searching for relevant strings in the file doesn t help; i.e. one of the registry keys added had the word mouclass ; which isn t found hard-coded in the binary; i.e. can t be used as an IOC. Beginners should also note that these keys are pre-existing; one might see the encoded values and think AH SUSPICOUS! however, these values are rot-13 encoded by the folks at microsoft themselves [1]. They can be decoded in python3 ALAS! The warewulf knows we are on its trail!.. maybe Other decoded values taken from the above include Further digging on some of these values indicate they may be used to tell the uptime of your pc? Ah UserAssist keys are good for forensic knowledge good or bad depends on the user [2] Wingin it while debugging
14 This seems odd Hmm what s onflyout.dll When I initially downloaded this it had not been classified, was supposedly not detected in VT; didn t take long for that to change though [3]. Hmm don t know where I d begin.. Complete disassembly doesn t reveal anything obvious; i.e. shows high degree of sophisitication, which would be tell-tale of APT I suppose. A Note about VT Some say this is bad opsec, and they re probably right; there are twitter rants about how uploading to VT caused a threat actor to up and burn everything. Makes sense that these sites are being monitored by the other side when you think about it. Hopefully we ve stepped through enough to get you curious. Sources 1. UserAssit keys UserAssit key profile VT- profile --
CIS-331 Fall 2014 Exam 1 Name: Total of 109 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Summary. Verdict: Malware CLASSIFICATION DETECTION SECTION HIGH LEVEL BEHAVIOR DISTRIBUTION ACTIVITY OVERVIEW
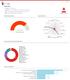 Page 1 Summary File Name: TealWake.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 5274ebb1b444f3576699f39b74599783770c36b0 MD5: 3d677e8f6bf82f7fd0a432cd9be89fc1 MALWARE Valkyrie
Page 1 Summary File Name: TealWake.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 5274ebb1b444f3576699f39b74599783770c36b0 MD5: 3d677e8f6bf82f7fd0a432cd9be89fc1 MALWARE Valkyrie
4. Specifications and Additional Information
 4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
Conclusion: Interesting, old malware. It was good to see this worm running successfully so as to get a better opportunity to view its capabilities.
 1.0 Summary Findings and observations: Mass-mailer worm. Similar to the prior sample analyzed, which I believe was derived from this new sample as this sample did not appear to have the execution issues
1.0 Summary Findings and observations: Mass-mailer worm. Similar to the prior sample analyzed, which I believe was derived from this new sample as this sample did not appear to have the execution issues
ID: Sample Name: REWjcrauz7 Cookbook: default.jbs Time: 12:14:00 Date: 29/09/2017 Version:
 ID: 33037 Sample Name: REWjcrauz7 Cookbook: default.jbs Time: 12:14:00 Date: 29/09/2017 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence Classification
ID: 33037 Sample Name: REWjcrauz7 Cookbook: default.jbs Time: 12:14:00 Date: 29/09/2017 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence Classification
CIS-331 Final Exam Spring 2015 Total of 115 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
CIS-331 Exam 2 Fall 2014 Total of 105 Points. Version 1
 Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
ID: Sample Name: QhSXTPahQj Cookbook: default.jbs Time: 07:55:34 Date: 20/06/2018 Version:
 ID: 434 Sample Name: QhSXTPahQj Cookbook: default.jbs Time: 0:55:34 Date: 20/0/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 434 Sample Name: QhSXTPahQj Cookbook: default.jbs Time: 0:55:34 Date: 20/0/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
CIS-331 Exam 2 Spring 2016 Total of 110 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
ID: Sample Name: powershell.exe Cookbook: default.jbs Time: 11:15:45 Date: 18/02/2018 Version:
 ID: 4932 Sample Name: powershell.exe Cookbook: default.jbs Time: :1:4 Date: 18/02/2018 Version: 21.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 4932 Sample Name: powershell.exe Cookbook: default.jbs Time: :1:4 Date: 18/02/2018 Version: 21.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
The cache is 4-way set associative, with 4-byte blocks, and 16 total lines
 Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Texas Tech University Spring 2017 Digital Forensics Malware Analysis
 /Reverse Engineering Tools and Techniques Background: Setup: Open Remnux inside of Virtual Box. If you do not have the Remnux Virtual Machine setup refer to the environment setup sheets for instructions.
/Reverse Engineering Tools and Techniques Background: Setup: Open Remnux inside of Virtual Box. If you do not have the Remnux Virtual Machine setup refer to the environment setup sheets for instructions.
Summary. Verdict: Malware DETECTION SECTION CLASSIFICATION HIGH LEVEL BEHAVIOR DISTRIBUTION ACTIVITY OVERVIEW
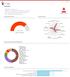 Page 1 Summary File Name: chit_na_batlu.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 02b1967cfd2fd2b27437cd69ddd679b893edca92 MD5: f7cf8df79a4624253cf6d7804af6b7ab MALWARE Valkyrie
Page 1 Summary File Name: chit_na_batlu.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 02b1967cfd2fd2b27437cd69ddd679b893edca92 MD5: f7cf8df79a4624253cf6d7804af6b7ab MALWARE Valkyrie
ID: Sample Name: vpnclientpsprovider.dll Cookbook: default.jbs Time: 20:37:41 Date: 10/02/2018 Version:
 ID: 494 Sample Name: vpnclientpsprovider.dll Cookbook: default.jbs Time: 20:3:41 Date: 10/02/2018 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
ID: 494 Sample Name: vpnclientpsprovider.dll Cookbook: default.jbs Time: 20:3:41 Date: 10/02/2018 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection
Conclusion: Interesting to see this very old piece of malware, even if it didn t fully run in the test environment.
 1.0 Summary Findings and observations: Mass-mailer worm with execution issues. Design flaws reveal functionality and signatures. This sample was first observed 14+ years ago, but doesn t seem to have any
1.0 Summary Findings and observations: Mass-mailer worm with execution issues. Design flaws reveal functionality and signatures. This sample was first observed 14+ years ago, but doesn t seem to have any
C1098 JPEG Module User Manual
 C1098 JPEG Module User Manual General Description C1098 is VGA camera module performs as a JPEG compressed still camera that can be attached to a wireless or PDA host. Users can send out a snapshot command
C1098 JPEG Module User Manual General Description C1098 is VGA camera module performs as a JPEG compressed still camera that can be attached to a wireless or PDA host. Users can send out a snapshot command
ID: Sample Name: owaauth.dll Cookbook: default.jbs Time: 06:38:57 Date: 27/04/2018 Version:
 ID: 593 Sample Name: owaauth.dll Cookbook: default.jbs Time: 0:3:5 Date: 2/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 593 Sample Name: owaauth.dll Cookbook: default.jbs Time: 0:3:5 Date: 2/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: Sample Name: HOcZW2ev9b Cookbook: default.jbs Time: 18:13:52 Date: 22/12/2017 Version:
 ID: 40853 Sample Name: HOcZW2evb Cookbook: default.jbs Time: 18::52 Date: 22/12/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 40853 Sample Name: HOcZW2evb Cookbook: default.jbs Time: 18::52 Date: 22/12/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
CIS-331 Final Exam Spring 2018 Total of 120 Points. Version 1
 Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
Triple DES and AES 192/256 Implementation Notes
 Triple DES and AES 192/256 Implementation Notes Sample Password-to-Key and KeyChange results of Triple DES and AES 192/256 implementation For InterWorking Labs customers who require detailed information
Triple DES and AES 192/256 Implementation Notes Sample Password-to-Key and KeyChange results of Triple DES and AES 192/256 implementation For InterWorking Labs customers who require detailed information
ECHO Process Instrumentation, Inc. Modbus RS485 Module. Operating Instructions. Version 1.0 June 2010
 ECHO Process Instrumentation, Inc. Modbus RS485 Module Operating Instructions Version 1.0 June 2010 ECHO Process Instrumentation, Inc. PO Box 800 Shalimar, FL 32579 PH: 850-609-1300 FX: 850-651-4777 EM:
ECHO Process Instrumentation, Inc. Modbus RS485 Module Operating Instructions Version 1.0 June 2010 ECHO Process Instrumentation, Inc. PO Box 800 Shalimar, FL 32579 PH: 850-609-1300 FX: 850-651-4777 EM:
July Registration of a Cyrillic Character Set. Status of this Memo
 Network Working Group Request for Comments: 1489 A. Chernov RELCOM Development Team July 1993 Status of this Memo Registration of a Cyrillic Character Set This memo provides information for the Internet
Network Working Group Request for Comments: 1489 A. Chernov RELCOM Development Team July 1993 Status of this Memo Registration of a Cyrillic Character Set This memo provides information for the Internet
Gateway Ascii Command Protocol
 Gateway Ascii Command Protocol Table Of Contents Introduction....2 Ascii Commands.....3 Messages Received From The Gateway....3 Button Down Message.....3 Button Up Message....3 Button Maintain Message....4
Gateway Ascii Command Protocol Table Of Contents Introduction....2 Ascii Commands.....3 Messages Received From The Gateway....3 Button Down Message.....3 Button Up Message....3 Button Maintain Message....4
ZN-DN312XE-M Quick User Guide
 ZN-DN312XE-M Quick User Guide This manual provides instructions for quick installation and basic configuration of your IP device. Step1. Connect cables to IP device Connect required cables to the device
ZN-DN312XE-M Quick User Guide This manual provides instructions for quick installation and basic configuration of your IP device. Step1. Connect cables to IP device Connect required cables to the device
Summary. Verdict: Malware DETECTION SECTION CLASSIFICATION HIGH LEVEL BEHAVIOR DISTRIBUTION ACTIVITY OVERVIEW
 Page 1 Summary File Name: 36d2a05049b9ad710ff050ae6841d06395916b5efa5bc1316e350f3bb1bca567.ex File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 336c36d486b251098dfd6877ea2e4d3cef6482ec
Page 1 Summary File Name: 36d2a05049b9ad710ff050ae6841d06395916b5efa5bc1316e350f3bb1bca567.ex File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 336c36d486b251098dfd6877ea2e4d3cef6482ec
APPLESHARE PC UPDATE INTERNATIONAL SUPPORT IN APPLESHARE PC
 APPLESHARE PC UPDATE INTERNATIONAL SUPPORT IN APPLESHARE PC This update to the AppleShare PC User's Guide discusses AppleShare PC support for the use of international character sets, paper sizes, and date
APPLESHARE PC UPDATE INTERNATIONAL SUPPORT IN APPLESHARE PC This update to the AppleShare PC User's Guide discusses AppleShare PC support for the use of international character sets, paper sizes, and date
UNH-IOL MIPI Alliance Test Program
 DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
6.1 Combinational Circuits. George Boole ( ) Claude Shannon ( )
 6. Combinational Circuits George Boole (85 864) Claude Shannon (96 2) Signals and Wires Digital signals Binary (or logical ) values: or, on or off, high or low voltage Wires. Propagate digital signals
6. Combinational Circuits George Boole (85 864) Claude Shannon (96 2) Signals and Wires Digital signals Binary (or logical ) values: or, on or off, high or low voltage Wires. Propagate digital signals
DBK24. Isolated Digital Output Chassis. Overview
 DBK24 Isolated Digital Output Chassis Overview 1 Power Requirements 2 Hardware Setup 2 Card Connection 2 Card Configuration 3 DaqBook and DaqBoard Connection 4 DaqBoard/2000 Series Board Connection 5 DaqBook
DBK24 Isolated Digital Output Chassis Overview 1 Power Requirements 2 Hardware Setup 2 Card Connection 2 Card Configuration 3 DaqBook and DaqBoard Connection 4 DaqBoard/2000 Series Board Connection 5 DaqBook
ID: Sample Name: filedata Cookbook: default.jbs Time: 03:13:04 Date: 23/01/2018 Version:
 ID: 4347 Sample Name: filedata Cookbook: default.jbs Time: 03:13:04 Date: 23/01/201 Version: 20.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification Signature
ID: 4347 Sample Name: filedata Cookbook: default.jbs Time: 03:13:04 Date: 23/01/201 Version: 20.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification Signature
6. Specifications & Additional Information
 6. Specifications & Additional Information SIIGX52004-3.1 Transceier Blocks Table 6 1 shows the transceier blocks for Stratix II GX and Stratix GX deices and compares their features. Table 6 1. Stratix
6. Specifications & Additional Information SIIGX52004-3.1 Transceier Blocks Table 6 1 shows the transceier blocks for Stratix II GX and Stratix GX deices and compares their features. Table 6 1. Stratix
CDR File Information. Comments Direct PCM
 IMPORTANT NOTICE: Robert Bosch LLC and the manufacturers whose vehicles are accessible using the CDR System urge end users to use the latest production release of the Crash Data Retrieval system software
IMPORTANT NOTICE: Robert Bosch LLC and the manufacturers whose vehicles are accessible using the CDR System urge end users to use the latest production release of the Crash Data Retrieval system software
Acquirer JCB EMV Test Card Set
 Acquirer JCB EMV Test Card Set July, 2017 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
Acquirer JCB EMV Test Card Set July, 2017 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
ID: Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/2018 Version:
 ID: 42417 Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
ID: 42417 Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
RS 232 PINOUTS. 1. We use RJ12 for all of our RS232 interfaces (Link-2-Modbus & Link-2-PC- Serial/RS232). The diagram below shows our pin out.
 RS 232 PINOUTS 1. We use RJ12 for all of our RS232 interfaces (Link-2-Modbus & Link-2-PC- Serial/RS232). The diagram below shows our pin out. 2. A DB9 Female to RJ12 Female Serial/Terminal Modular Adaptor
RS 232 PINOUTS 1. We use RJ12 for all of our RS232 interfaces (Link-2-Modbus & Link-2-PC- Serial/RS232). The diagram below shows our pin out. 2. A DB9 Female to RJ12 Female Serial/Terminal Modular Adaptor
First Data Dual Interface EMV Test Card Set. Version 1.20
 First Data Dual Interface EMV Test Card Set August, 2016 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
First Data Dual Interface EMV Test Card Set August, 2016 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
TLS 1.2 Protocol Execution Transcript
 Appendix C TLS 1.2 Protocol Execution Transcript In Section 2.3, we overviewed a relatively simple protocol execution transcript for SSL 3.0. In this appendix, we do something similar for TLS 1.2. Since
Appendix C TLS 1.2 Protocol Execution Transcript In Section 2.3, we overviewed a relatively simple protocol execution transcript for SSL 3.0. In this appendix, we do something similar for TLS 1.2. Since
First Data EMV Test Card Set. Version 1.30
 First Data EMV Test Card Set.30 January, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data EMV Test Card Set.30 January, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
Digital Lighting Systems, Inc. CD400-DMX DMX512 Four Channel Dimmer and Switch module
 , Inc. DMX512 Four Channel Dimmer and Switch module Input: 5 Amps @ 6-24 VDC Outputs: 5 Amps Maximum each, total 4 outputs 8 Amps Maximum. FRONT BACK USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION
, Inc. DMX512 Four Channel Dimmer and Switch module Input: 5 Amps @ 6-24 VDC Outputs: 5 Amps Maximum each, total 4 outputs 8 Amps Maximum. FRONT BACK USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION
PCL ISO 8859/5 Latin/Cyrillic
 Page 1 of 5 PCL Symbol Se t: 10N Unicode gly ph correspondence tables. Contact:help@redtitan.com http://pcl.to $20 U0020 Space -- -- -- -- $21 U0021 Ê Exclamation mark -- -- -- -- $22 U0022 Ë Quotation
Page 1 of 5 PCL Symbol Se t: 10N Unicode gly ph correspondence tables. Contact:help@redtitan.com http://pcl.to $20 U0020 Space -- -- -- -- $21 U0021 Ê Exclamation mark -- -- -- -- $22 U0022 Ë Quotation
ID: Sample Name: cerbermore.dll Cookbook: default.jbs Time: 19:00:07 Date: 07/04/2018 Version:
 ID: 53634 Sample Name: cerbermore.dll Cookbook: default.jbs Time: 19:00:0 Date: 0/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 53634 Sample Name: cerbermore.dll Cookbook: default.jbs Time: 19:00:0 Date: 0/04/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
First Data EMV Test Card Set. Version 2.00
 First Data EMV Test Card Set.00 February, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data EMV Test Card Set.00 February, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
Digital Lighting Systems, Inc.
 Digital Lighting Systems, Inc. Four Channel Dry Contacts Relays Switch Pack DMX512 compatible USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION The is a 4-channel DMX-512 compatible electro-mechanical
Digital Lighting Systems, Inc. Four Channel Dry Contacts Relays Switch Pack DMX512 compatible USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION The is a 4-channel DMX-512 compatible electro-mechanical
Hash Constant C Determinants leading to collisionfree
 Hash Constant C Determinants leading to collisionfree (Ernst Erich Schnoor) eschnoor@multi-matrix.de Addendum to article: Core of the CypherMatrix Method http://www.telecypher.net/corecyph.htm#z6 Object
Hash Constant C Determinants leading to collisionfree (Ernst Erich Schnoor) eschnoor@multi-matrix.de Addendum to article: Core of the CypherMatrix Method http://www.telecypher.net/corecyph.htm#z6 Object
ID: Sample Name: binary(2) Cookbook: default.jbs Time: 15:21:05 Date: 10/01/2018 Version:
 ID: 42207 Sample Name: binary(2) Cookbook: default.jbs Time: 15:21:05 Date: 10/01/2018 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 42207 Sample Name: binary(2) Cookbook: default.jbs Time: 15:21:05 Date: 10/01/2018 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
Systems/DBG Debugger Version 2.20
 Systems/DBG Debugger Version 2.20 Copyright c 2018, Dignus, LLC Systems/DBG Debugger Version 2.20 i Copyright c 2018 Dignus LLC, 8378 Six Forks Road Suite 203, Raleigh NC, 27615. World rights reserved.
Systems/DBG Debugger Version 2.20 Copyright c 2018, Dignus, LLC Systems/DBG Debugger Version 2.20 i Copyright c 2018 Dignus LLC, 8378 Six Forks Road Suite 203, Raleigh NC, 27615. World rights reserved.
Communications guide. Line Distance Protection System * F1* GE Digital Energy. Title page
 Title page GE Digital Energy D90 Plus Line Distance Protection System Communications guide D90 Plus firmware revision:.9x GE publication code: 60-9070-F (GEK-3469) GE Digital Energy 650 Markland Street
Title page GE Digital Energy D90 Plus Line Distance Protection System Communications guide D90 Plus firmware revision:.9x GE publication code: 60-9070-F (GEK-3469) GE Digital Energy 650 Markland Street
ENGI 8868/9877 Computer and Communications Security III. BLOCK CIPHERS. Symmetric Key Cryptography. insecure channel
 (a) Introduction - recall symmetric key cipher: III. BLOCK CIPHERS k Symmetric Key Cryptography k x e k y yʹ d k xʹ insecure channel Symmetric Key Ciphers same key used for encryption and decryption two
(a) Introduction - recall symmetric key cipher: III. BLOCK CIPHERS k Symmetric Key Cryptography k x e k y yʹ d k xʹ insecure channel Symmetric Key Ciphers same key used for encryption and decryption two
One subset of FEAL, called FEAL-NX, is N round FEAL using a 128-bit key without key parity.
 FEAL-NX SPECIFICATIONS 1 Introduction 1.1 Outline of the FEAL-NX cipher FEAL, the Fast Data Encipherment Algorithm, is a 64-bit block cipher algorithm that enciphers 64-bit plaintexts into 64-bit ciphertexts
FEAL-NX SPECIFICATIONS 1 Introduction 1.1 Outline of the FEAL-NX cipher FEAL, the Fast Data Encipherment Algorithm, is a 64-bit block cipher algorithm that enciphers 64-bit plaintexts into 64-bit ciphertexts
ID: Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version:
 ID: 59176 Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 59176 Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
Acquirer JCB Dual Interface EMV Test Card Set
 Acquirer JCB Dual Interface EMV Test Card Set.00 July, 2018 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing and delivering this document
Acquirer JCB Dual Interface EMV Test Card Set.00 July, 2018 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing and delivering this document
Win32 Programming. Jim Fawcett CSE775 Distributed Objects Spring 2012
 Win32 Programming Jim Fawcett CSE775 Distributed Objects Spring 2012 References Programming Applications for Microsoft Windows, 4 th Edition, Jeffrey Richter, Microsoft Press, 1999 Unicode, More Unicode
Win32 Programming Jim Fawcett CSE775 Distributed Objects Spring 2012 References Programming Applications for Microsoft Windows, 4 th Edition, Jeffrey Richter, Microsoft Press, 1999 Unicode, More Unicode
)- -% *)&%! $%!" (!*.-1 %,-+% --)+(!1 $!& *. &% '!!-%(# 000 $! )''.(%-1 )%! )' +!!%/!+ $+%, 1&)+ ' ()$ +! +%.-! 1 ).%,/%&&! +! ) %)(!!+, '*%(#!
 + 1 1 -)(, + ) )(+, (& (,)( (& +1 )(, /0 (& 000 ).(-1 ) ) ( ) )- - ))&5, &,, ) 2 3 ) 0(-14 + 5,3-0// 5. 207/ 4&/& 043 0)// 2830/ () )00-2&0(/9& / 12&3&/4& :4)&3& 47&/48 345&/43 74) )&-8 &/3& 30/ 04&-/(
+ 1 1 -)(, + ) )(+, (& (,)( (& +1 )(, /0 (& 000 ).(-1 ) ) ( ) )- - ))&5, &,, ) 2 3 ) 0(-14 + 5,3-0// 5. 207/ 4&/& 043 0)// 2830/ () )00-2&0(/9& / 12&3&/4& :4)&3& 47&/48 345&/43 74) )&-8 &/3& 30/ 04&-/(
Parallax Serial LCD 2 rows x 16 characters Non-backlit (#27976) 2 rows x 16 characters Backlit (#27977) 4 rows x 20 characters Backlit (#27979)
 599 Menlo Drive, Suite 100 Rocklin, California 95765, USA Office: (916) 624-8333 Fax: (916) 624-8003 General: info@parallax.com Technical: support@parallax.com Web Site: www.parallax.com Educational: www.stampsinclass.com
599 Menlo Drive, Suite 100 Rocklin, California 95765, USA Office: (916) 624-8333 Fax: (916) 624-8003 General: info@parallax.com Technical: support@parallax.com Web Site: www.parallax.com Educational: www.stampsinclass.com
CIS-331 Final Exam Spring 2016 Total of 120 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Fundamentals of Cryptography
 Fundamentals of Cryptography Topics in Quantum-Safe Cryptography June 23, 2016 Part III Data Encryption Standard The Feistel network design m m 0 m 1 f k 1 1 m m 1 2 f k 2 2 DES uses a Feistel network
Fundamentals of Cryptography Topics in Quantum-Safe Cryptography June 23, 2016 Part III Data Encryption Standard The Feistel network design m m 0 m 1 f k 1 1 m m 1 2 f k 2 2 DES uses a Feistel network
2-Type Series Pressurized Closures
 2-Type Series Pressurized Closures A complete pressure tight reenterable closure system for enclosing spliced connections of communications cables in a wide variety of applications. The 2-type Closure
2-Type Series Pressurized Closures A complete pressure tight reenterable closure system for enclosing spliced connections of communications cables in a wide variety of applications. The 2-type Closure
EDR Report Information
 EDR Report File Information Value VIN 5YJXCDE20HF041782 Retrieval Date 2017/06/30 02:16:00 (UTC) Retrieval User Comments Retrieval Program Information EDR Report Information Tesla EDR Reporting Service
EDR Report File Information Value VIN 5YJXCDE20HF041782 Retrieval Date 2017/06/30 02:16:00 (UTC) Retrieval User Comments Retrieval Program Information EDR Report Information Tesla EDR Reporting Service
ID: Sample Name: RasTls.exe Cookbook: default.jbs Time: 16:59:10 Date: 27/01/2018 Version:
 ID: 44111 Sample Name: RasTls.exe Cookbook: default.jbs Time: 16:5:10 Date: 27/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 44111 Sample Name: RasTls.exe Cookbook: default.jbs Time: 16:5:10 Date: 27/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
CMSC 313 Lecture 03 Multiple-byte data big-endian vs little-endian sign extension Multiplication and division Floating point formats Character Codes
 Multiple-byte data CMSC 313 Lecture 03 big-endian vs little-endian sign extension Multiplication and division Floating point formats Character Codes UMBC, CMSC313, Richard Chang 4-5 Chapter
Multiple-byte data CMSC 313 Lecture 03 big-endian vs little-endian sign extension Multiplication and division Floating point formats Character Codes UMBC, CMSC313, Richard Chang 4-5 Chapter
6.1 Font Types. Font Types
 6 Font This chapter explains basic features of GP-Pro EX's "Font" and basic ways of placing text with each font. Please start by reading "6.1 Font Types" (page 6-2) and then turn to the corresponding page.
6 Font This chapter explains basic features of GP-Pro EX's "Font" and basic ways of placing text with each font. Please start by reading "6.1 Font Types" (page 6-2) and then turn to the corresponding page.
First Data DCC Test Card Set. Version 1.30
 First Data DCC Test Card Set.30 April, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data DCC Test Card Set.30 April, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
SPAREPARTSCATALOG: CONNECTORS SPARE CONNECTORS KTM ART.-NR.: 3CM EN
 SPAREPARTSCATALOG: CONNECTORS ART.-NR.: 3CM3208201EN CONTENT SPARE CONNECTORS AA-AN SPARE CONNECTORS AO-BC SPARE CONNECTORS BD-BQ SPARE CONNECTORS BR-CD 3 4 5 6 SPARE CONNECTORS CE-CR SPARE CONNECTORS
SPAREPARTSCATALOG: CONNECTORS ART.-NR.: 3CM3208201EN CONTENT SPARE CONNECTORS AA-AN SPARE CONNECTORS AO-BC SPARE CONNECTORS BD-BQ SPARE CONNECTORS BR-CD 3 4 5 6 SPARE CONNECTORS CE-CR SPARE CONNECTORS
Technical Specification. Third Party Control Protocol. AV Revolution
 Technical Specification Third Party Control Protocol AV Revolution Document AM-TS-120308 Version 1.0 Page 1 of 31 DOCUMENT DETAILS Document Title: Technical Specification, Third Party Control Protocol,
Technical Specification Third Party Control Protocol AV Revolution Document AM-TS-120308 Version 1.0 Page 1 of 31 DOCUMENT DETAILS Document Title: Technical Specification, Third Party Control Protocol,
CSCI 454/554 Computer and Network Security. Topic 3.1 Secret Key Cryptography Algorithms
 CSCI 454/554 Computer and Network Security Topic 3.1 Secret Key Cryptography Algorithms Outline Introductory Remarks Feistel Cipher DES AES 2 Introduction Secret Keys or Secret Algorithms? Security by
CSCI 454/554 Computer and Network Security Topic 3.1 Secret Key Cryptography Algorithms Outline Introductory Remarks Feistel Cipher DES AES 2 Introduction Secret Keys or Secret Algorithms? Security by
CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 02, FALL 2012
 CMSC 33 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 2, FALL 22 TOPICS TODAY Bits of Memory Data formats for negative numbers Modulo arithmetic & two s complement Floating point formats
CMSC 33 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 2, FALL 22 TOPICS TODAY Bits of Memory Data formats for negative numbers Modulo arithmetic & two s complement Floating point formats
ID: Sample Name: calc1 Cookbook: default.jbs Time: 14:46:00 Date: 13/07/2018 Version:
 ID: 98 Sample Name: calc1 Cookbook: default.jbs Time: 14:4:00 Date: 13/0/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 98 Sample Name: calc1 Cookbook: default.jbs Time: 14:4:00 Date: 13/0/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
SPARE CONNECTORS KTM 2014
 SPAREPARTSCATALOG: // ENGINE ART.-NR.: 3208201EN CONTENT CONNECTORS FOR WIRING HARNESS AA-AN CONNECTORS FOR WIRING HARNESS AO-BC CONNECTORS FOR WIRING HARNESS BD-BQ CONNECTORS FOR WIRING HARNESS BR-CD
SPAREPARTSCATALOG: // ENGINE ART.-NR.: 3208201EN CONTENT CONNECTORS FOR WIRING HARNESS AA-AN CONNECTORS FOR WIRING HARNESS AO-BC CONNECTORS FOR WIRING HARNESS BD-BQ CONNECTORS FOR WIRING HARNESS BR-CD
Enhanced Play Fair Cipher
 P Enhanced Play Fair Cipher 1 1 Naveen KMP P, PDepartment of Information Technology, Velammal Engineering College, Chennai, Tamil Nadu, India. Abstract The theme of this research work is to design and
P Enhanced Play Fair Cipher 1 1 Naveen KMP P, PDepartment of Information Technology, Velammal Engineering College, Chennai, Tamil Nadu, India. Abstract The theme of this research work is to design and
ASCII Code - The extended ASCII table
 ASCII Code - The extended ASCII table ASCII, stands for American Standard Code for Information Interchange. It's a 7-bit character code where every single bit represents a unique character. On this webpage
ASCII Code - The extended ASCII table ASCII, stands for American Standard Code for Information Interchange. It's a 7-bit character code where every single bit represents a unique character. On this webpage
Secret Key Systems (block encoding) Encrypting a small block of text (say 64 bits) General considerations for cipher design:
 Secret Key Systems (block encoding) Encrypting a small block of text (say 64 bits) General considerations for cipher design: Secret Key Systems (block encoding) Encrypting a small block of text (say 64
Secret Key Systems (block encoding) Encrypting a small block of text (say 64 bits) General considerations for cipher design: Secret Key Systems (block encoding) Encrypting a small block of text (say 64
CS , Spring 2002 Exam 2
 Full Name: CS 15-213, Spring 2002 Exam 2 March 28, 2002 Instructions: Make sure that your exam is not missing any sheets, then write your full name and Andrew login ID on the front. Write your answers
Full Name: CS 15-213, Spring 2002 Exam 2 March 28, 2002 Instructions: Make sure that your exam is not missing any sheets, then write your full name and Andrew login ID on the front. Write your answers
About INtime Win32 and real time extension system calls
 About INtime Win32 and real time extension system calls Contents Overview How the Win32 API (iwin32) fits in the INtime environment INtime Win32 system calls Porting a Windows application to INtime Overview
About INtime Win32 and real time extension system calls Contents Overview How the Win32 API (iwin32) fits in the INtime environment INtime Win32 system calls Porting a Windows application to INtime Overview
ID: Sample Name: FileOpenInstaller.exe Cookbook: default.jbs Time: 14:35:58 Date: 14/12/2017 Version:
 ID: 40081 Sample Name: FileOpenInstaller.exe Cookbook: default.jbs Time: 14:35:58 Date: 14/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification
ID: 40081 Sample Name: FileOpenInstaller.exe Cookbook: default.jbs Time: 14:35:58 Date: 14/12/2017 Version: 20.0.0 Table of Contents Analysis Report Overview Information Detection Confidence Classification
KNX TinySerial 810. Communication Protocol. WEINZIERL ENGINEERING GmbH
 WEINZIERL ENGINEERING GmbH KNX TinySerial 810 Communication Protocol WEINZIERL ENGINEERING GmbH Bahnhofstr. 6 DE-84558 Tyrlaching GERMAY Tel. +49 8623 / 987 98-03 Fax +49 8623 / 987 98-09 E-Mail: info@weinzierl.de
WEINZIERL ENGINEERING GmbH KNX TinySerial 810 Communication Protocol WEINZIERL ENGINEERING GmbH Bahnhofstr. 6 DE-84558 Tyrlaching GERMAY Tel. +49 8623 / 987 98-03 Fax +49 8623 / 987 98-09 E-Mail: info@weinzierl.de
LynX-10 Legacy Protocol Specification Version 1.01
 LynX-10 Legacy Protocol Specification Version 1.01 Marrick Limited LynX-10 TM Legacy Protocol Specification Manual revision 1.01 Marrick Limited, Incorporated P.O. Box 950940 Lake Mary, FL 32795 (407)
LynX-10 Legacy Protocol Specification Version 1.01 Marrick Limited LynX-10 TM Legacy Protocol Specification Manual revision 1.01 Marrick Limited, Incorporated P.O. Box 950940 Lake Mary, FL 32795 (407)
ETSI TS V ( )
 TS 135 233 V12.1.0 (2014-10) TECHNICAL SPECIFICATION Universal Mobile Telecommunications System (UMTS); LTE; Specification of the TUAK algorithm set: A second example algorithm set for the 3GPP authentication
TS 135 233 V12.1.0 (2014-10) TECHNICAL SPECIFICATION Universal Mobile Telecommunications System (UMTS); LTE; Specification of the TUAK algorithm set: A second example algorithm set for the 3GPP authentication
ID: Sample Name: npzdi.exe Cookbook: default.jbs Time: 21:42:27 Date: 26/09/2017 Version:
 ID: 32777 Sample Name: npzdi.exe Cookbook: default.jbs Time: 21:42:27 Date: 26/0/2017 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence Classification
ID: 32777 Sample Name: npzdi.exe Cookbook: default.jbs Time: 21:42:27 Date: 26/0/2017 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview Information Detection Confidence Classification
ID: Sample Name: jre-8u162- windows-i586_ exe Cookbook: default.jbs Time: 03:20:07 Date: 19/01/2018 Version: 20.0.
 ID: 43064 Sample Name: jre-8u162- windows-i586_0510703339.exe Cookbook: default.jbs Time: 03:20:07 Date: 19/01/2018 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection
ID: 43064 Sample Name: jre-8u162- windows-i586_0510703339.exe Cookbook: default.jbs Time: 03:20:07 Date: 19/01/2018 Version: 20.0.0 Table of Contents Analysis Report Overview General Information Detection
PowerPrism16 Light Controllers Instruction Guide
 Part No. ELD16 (light controller in enclosure) and Part No. BLD16 (light controller only) PowerPrism16 Light Controllers Instruction Guide Animated Lighting, L.C. 7304 West 130th Street, Suite 100 Overland
Part No. ELD16 (light controller in enclosure) and Part No. BLD16 (light controller only) PowerPrism16 Light Controllers Instruction Guide Animated Lighting, L.C. 7304 West 130th Street, Suite 100 Overland
VM7000A PAPERLESS RECORDER COMMUNICATION FUNCTION OPERATION MANUAL
 VM7000A PAPERLESS RECORDER COMMUNICATION FUNCTION OPERATION MANUAL WXPVM70mnA0002E October, 2009(Rev.1) All Rights Reserved, Copyright 2009, Ohkura Electric Co.,Ltd. To use this equipment safely Thank
VM7000A PAPERLESS RECORDER COMMUNICATION FUNCTION OPERATION MANUAL WXPVM70mnA0002E October, 2009(Rev.1) All Rights Reserved, Copyright 2009, Ohkura Electric Co.,Ltd. To use this equipment safely Thank
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1
 CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
Here is a C function that will print a selected block of bytes from such a memory block, using an array-based view of the necessary logic:
 Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
CSE Computer Architecture I Fall 2011 Homework 07 Memory Hierarchies Assigned: November 8, 2011, Due: November 22, 2011, Total Points: 100
 CSE 30321 Computer Architecture I Fall 2011 Homework 07 Memory Hierarchies Assigned: November 8, 2011, Due: November 22, 2011, Total Points: 100 Problem 1: (30 points) Background: One possible organization
CSE 30321 Computer Architecture I Fall 2011 Homework 07 Memory Hierarchies Assigned: November 8, 2011, Due: November 22, 2011, Total Points: 100 Problem 1: (30 points) Background: One possible organization
ID: Sample Name: MobaXterm_installer_10.5.msi Cookbook: defaultwindowsmsicookbook.jbs Time: 18:29:36 Date: 25/05/2018 Version: 22.0.
 ID: 61258 Sample Name: MobaXterm_installer_10.5.msi Cookbook: defaultwindowsmsicookbook.jbs Time: 18:29:36 Date: 25/05/2018 Version: 22.0.0 Table of Contents Analysis Report Overview Information Detection
ID: 61258 Sample Name: MobaXterm_installer_10.5.msi Cookbook: defaultwindowsmsicookbook.jbs Time: 18:29:36 Date: 25/05/2018 Version: 22.0.0 Table of Contents Analysis Report Overview Information Detection
Chapter 13, Sequence Data Mining
 CSI 4352, Introduction to Data Mining Chapter 13, Sequence Data Mining Young-Rae Cho Associate Professor Department of Computer Science Baylor University Topics Single Sequence Mining Frequent sequence
CSI 4352, Introduction to Data Mining Chapter 13, Sequence Data Mining Young-Rae Cho Associate Professor Department of Computer Science Baylor University Topics Single Sequence Mining Frequent sequence
OOstaExcel.ir. J. Abbasi Syooki. HTML Number. Device Control 1 (oft. XON) Device Control 3 (oft. Negative Acknowledgement
 OOstaExcel.ir J. Abbasi Syooki HTML Name HTML Number دهدهی ا کتال هگزاد سیمال باینری نشانه )کاراکتر( توضیح Null char Start of Heading Start of Text End of Text End of Transmission Enquiry Acknowledgment
OOstaExcel.ir J. Abbasi Syooki HTML Name HTML Number دهدهی ا کتال هگزاد سیمال باینری نشانه )کاراکتر( توضیح Null char Start of Heading Start of Text End of Text End of Transmission Enquiry Acknowledgment
AIT 682: Network and Systems Security
 AIT 682: Network and Systems Security Topic 3.1 Secret Key Cryptography Algorithms Instructor: Dr. Kun Sun Outline Introductory Remarks Feistel Cipher DES AES 2 Introduction Secret Keys or Secret Algorithms?
AIT 682: Network and Systems Security Topic 3.1 Secret Key Cryptography Algorithms Instructor: Dr. Kun Sun Outline Introductory Remarks Feistel Cipher DES AES 2 Introduction Secret Keys or Secret Algorithms?
Digital Projector X30N/X35N
 Digital Projector X30N/X35N Operator's Guide TECHNICAL Warranty 3M warrants that when the 3M Product is used according to 3M s Intended Use Statement (www.3m.com/meetings), it will perform satisfactorily
Digital Projector X30N/X35N Operator's Guide TECHNICAL Warranty 3M warrants that when the 3M Product is used according to 3M s Intended Use Statement (www.3m.com/meetings), it will perform satisfactorily
egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO
 egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO e-government Survey 2014 United Nations Page 2 EGDI: E-Government Development Index National ID & Digital Signature Estonian Prime Minister Andrus Ansip
egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO e-government Survey 2014 United Nations Page 2 EGDI: E-Government Development Index National ID & Digital Signature Estonian Prime Minister Andrus Ansip
PCL Greek-8 - Code Page 869
 PCL Greek-8 - Code Page 869 Page 1 of 5 PCL Symbol Se t: 8G Unicode glyph correspondence tables. Contact:help@redtitan.com http://pcl.to $20 U0020 Space $90 U038A Ê Greek capita l letter iota with tonos
PCL Greek-8 - Code Page 869 Page 1 of 5 PCL Symbol Se t: 8G Unicode glyph correspondence tables. Contact:help@redtitan.com http://pcl.to $20 U0020 Space $90 U038A Ê Greek capita l letter iota with tonos
Digital Lighting Systems, Inc.
 , Inc. PD402-DMX Four Channel Dimmer and Switch Packs 4 x 2.5 Amps @ 6VDC to 24 VDC DMX52 compatible DMX52 4 x 2.5 Amps Dimmer Pack C UL US LISTED Digital Lighting Systems, Inc. USER'S MANUAL User's Manual
, Inc. PD402-DMX Four Channel Dimmer and Switch Packs 4 x 2.5 Amps @ 6VDC to 24 VDC DMX52 compatible DMX52 4 x 2.5 Amps Dimmer Pack C UL US LISTED Digital Lighting Systems, Inc. USER'S MANUAL User's Manual
USB-ASC232. ASCII RS-232 Controlled USB Keyboard and Mouse Cable. User Manual
 USB-ASC232 ASCII RS-232 Controlled USB Keyboard and Mouse Cable User Manual Thank you for purchasing the model USB-ASC232 Cable HAGSTROM ELECTRONICS, INC. is pleased that you have selected this product
USB-ASC232 ASCII RS-232 Controlled USB Keyboard and Mouse Cable User Manual Thank you for purchasing the model USB-ASC232 Cable HAGSTROM ELECTRONICS, INC. is pleased that you have selected this product
CIS-331 Final Exam Fall 2015 Total of 120 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
ID: Sample Name: FloProDesigner.exe Cookbook: default.jbs Time: 19:52:35 Date: 09/08/2018 Version:
 ID: 71847 Sample Name: FloProDesigner.exe Cookbook: default.jbs Time: 1:52:35 Date: 0/08/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
ID: 71847 Sample Name: FloProDesigner.exe Cookbook: default.jbs Time: 1:52:35 Date: 0/08/2018 Version: 23.0.0 Table of Contents Analysis Report Overview General Information Detection Confidence Classification
Digital Lighting Systems, Inc. PD405-DMX. Four Channel Dimmer and Switch Packs. DMX512 compatible. PD405-DMX-24DC DMX512 4 x 5 Amps Dimmer Pack
 Digital Lighting Systems, Inc. PD405DMX Four Channel Dimmer and Switch Packs DMX52 compatible PD405DMX24DC DMX52 4 x 5 Amps Dimmer Pack C UL US LISTED www.digitallighting.com Digital Lighting Systems,
Digital Lighting Systems, Inc. PD405DMX Four Channel Dimmer and Switch Packs DMX52 compatible PD405DMX24DC DMX52 4 x 5 Amps Dimmer Pack C UL US LISTED www.digitallighting.com Digital Lighting Systems,
Programming Notes and Examples
 LCD/USB Companion Chip Document Number: X37A-G-003-05 Copyright 2001, 2002 Epson Research and Development, Inc. All Rights Reserved. Information in this document is subject to change without notice. You
LCD/USB Companion Chip Document Number: X37A-G-003-05 Copyright 2001, 2002 Epson Research and Development, Inc. All Rights Reserved. Information in this document is subject to change without notice. You
