Lab Exercises and Solutions
|
|
|
- Barry Allison
- 5 years ago
- Views:
Transcription
1 Lab Exercises and Solutions Lab Exercises and Solutions Lab - 1 (4 Real time hours) NT-Server - Installation Steps The installation (or just install) process is divided into various steps or procedures. First of all is the text (or DOS) phase, which copies files and establishes a boot-up facility on floppy disks or the hard drive. The second phase (the so-called GUI phase) actually loads the drivers and runs in the true Windows NT phase. The following steps explain the basic installation procedure: 1. The initial part of the text mode involves booting into the installation process. There are several ways to accomplish this. The most obvious is booting from the install floppies. Likewise you can access the installation CD from the DOS prompt and start the installation by running WinNT (or WinNT /b, which copies the boot files to a hard drive rather than floppy drives) from the I386 director. If you are upgrading the installation from Windows NT 3.51, you can run winnt32 in the same manner. Likewise, you can run WinNT or winnt32 with /u to perform an install in unattended mode. On RISC-based machines, the install process is somewhat different. For example, NT is installed onto Alpha-based machines by running applications directly from the CD (and you don t use switches as /b). These differences will be detailed in the appropriate sections. The setup will run automatically and will boot onto the install CD if the system BIOS supports this feature. If an install CD is not found (unless you are running the winnt or winnt32 methods from an install directory), the install will abort after Disk When given the choice between Default and Custom, choose Custom Install Method. This option enables you to see and select the application that are being installed. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 1
2 3. Verify the system components that the detection procedure summarizes for you. If the list is incorrect, restart Setup. When the system displays the message Setup is inspecting your computer s hardware configuration, press F6. This action should allow you to bypass autodetection of the hardware; you can then indicate the components that are present. (At this point, you can also install legacy SCSI drivers, etc.) 4. You will be asked to choose file formats. Many people suggest that you have a small FAT partition as drive C: so that you can do file maintenance via DOS. However, installing a FAT partition is a violation of C2 security(if that s important to you). Use NTFS wherever possible, especially with modern large drives (greater than a gigabyte). 5. If the drive has not been formatted, you will be given the opportunity to partition and format the drive. Even if you ask for NTFS, the initial format is FAT and then it is subsequently converted to NTFS on the next reboot. 6. Select the directory to which NT will be installed. Using the default name (winnt) is a good idea (you can change the drive). 7. Enter your name and your company name. 8. Enter the Administrator password. This is very important. Choose a password that s at least seven characters long and has a nonsense symbol in it. 9. Supply a unique name for the computer that is, a name that does not exist elsewhere in the network or domain. 10. When the network portion of the install continues, you are given the following choices: Do not connect the computer to the network at this time. This computer will participate on a network via(default); Wired directly to a network via ISDN or a standard network cable. Remote access via a standard modem. 2 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
3 Lab Exercises and Solutions This is a marked change from previous setups and reflects the new wizard incorporation. Unless you have prior knowledge of a problem with a network interface card(nic), there should be no problem joining a network. On the other hand, there are cases where NT is installed and crashes only when the network driver is initialized. A server needs an NIC. If there are suspected problems, install the Msloopback adapter, after NT is running, install the NIC. If you know that the NIC is okay, continue with the installation process. 11. Now we come to our first serious choice. What NIC is on the server? By the way, a server by definition must have a network card or other means of providing for service. For some NICs, autodetection, detect the NIC manually. 12. Choose the networking protocol. The install defaults to IPX/SPX and NetBEUI. The former is needed if you are using interconnectivity to a Novel network. The latter works well in a Microsoft environment. My choice, however, is TCP/IP, because it is the fastest growing of the protocols. If you do choose a TCP/IP protocol, you are asked if you have Dynamic Host Configuration Protocol (DHCP) to install or connect to. This of course is dictated by the network environment into which the machine is being installed. 13. The server installation defaults to installing as a Primary Domain Controller(PDC). You can set up the installation as a Backup Domain Controller(BDC), but this option presupposes the existing presence of PDC on the network. Finally, you can install as a standalone server. 14. When asked to determine the time zone you are in, set the system information accordingly. 15. The final issue of note is establishing the video configuration. This is easier in Version 4.0 than in previous version. You simply select the resolution you want. You will be asked to reboot. After rebooting, you can change the resolution on-the-fly, but changing to a larger font, etc., requires a reboot. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 3
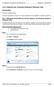
4 Lab - 2 (4 Real Time hours) Ex 1 Logon Process 1. When Windows NT starts getting loaded and the Begin Logon dialog box will be displayed. 2. Keep the <Ctrl> and <Alt> keys pressed and then press <Delete> key once. The logon information dialog box gets displayed With Administrator as user name and the default domain name. 3. Password in Windows NT is case sensitive, therefore make sure that the characters typed are all in capital letters. If you click the right password Windows NT displays a graphic user interface that is very similar to that of Windows 95 interface. 4. Click on the Start button. 5. Click on the Program menu. 6. Point the mouse pointer on Administrative Tools. 7. Windows NT pops up another sub menu as shown in Fig. 8. Click on the User Manager for Domains option. 4 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
5 Lab Exercises and Solutions The User Manager Window gets displayed in the screen as shown in Fig. Ex 2 Create User Accounts 1. Click on the User menu. 2. Click on New User option as shown in Fig. Windows NT displays New User dialog box as shown in Fig and cursor is placed in the Username box. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 5
6 Administrators on the primary domain controller (PDC) and backup domain controller(bdc) cannot make the same user as the database directory of one gets replicated to another. As a result, the administrator on PDC computer will create users Charles, Alan and James ( do the steps 3 to 14) where as the administrator on BDC computer will create users Patrick, Brian and Richard (do the step 15 using steps 3 to 12) Steps for Administrator on PDC: 3. Type the username as Charles. 4. Press<Tab> to move to Full Name box. 5. Type Carter Charles. 6. Press <Tab> to move to Description box. 7. Type Working as Senior Executive Technical. 8. Press Tab to move to Password box. 9. Type password The text you type will be displayed as stars, as a result you will not be able to view what you are typing, therefore care has to be taken accordingly Passwords are case sensitive. 10. Press Tab to move to Confirm Password box. 11. Type password Your screen must look the one as shown in Fig. 6 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
7 Lab Exercises and Solutions 12. Click on the Add button. Notice that the Cancel button below the Add screen has changed into Close button and New User window gets refreshed. 13. Create the below given user accounts with respective details. Userna me Full Name Description Passwor d Alan Deigo Alan Vice passwor President d James Neihaus Manager passwor James d Confirm passwor d password password 14. Click on the Close button after you have created all three user accounts. Steps for Administrator on BDC: 15. Create the below given user accounts with respective details: Userna Full Name Descripti Passwor Confirm me on d password Patrick Adams Chairman passwor password Patrick d Brian D Costa Executive passwor Password Brian d Richard King Executive Passwor Password Richard d Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 7
8 Ex 3 First you will have to create a home directory called Users, which must have share rights. 1. Click on the Start button. 2. Click on Programs menu. 3. Click on Window NT Explorer. 4. Click on the root directory. 5. Click on the File main menu, click on the New option. 6. Click on the Folder sub option. 7. Type Users and press <Enter> 8. Right-click on the Users folder, a menu drops down. 9. Click on the Sharing option, the folder properties dialog box gets displayed. In this case the title of the window will be Users properties as shown in Fig. 10. Click on the Shared As radio button : The share name box gets filled with the folder s name as shown in Fig. Notice that the Apply button gets highlighted. The Apply button is pressed prior to OK button only when you want to change some other settings before you press the OK button. 11. Click on the OK button : Notice that a small hand appears below the folder Users indicating that the folder has been shared. 8 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
9 Lab Exercises and Solutions 12. Click on the File main menu : Click on the Exit option. The Windows NT explorer will close. 13. Click on the User Manager NT-LAB on the taskbar. 14. Click on the user account Alan to select it. 15. Click on the User main menu and click on properties as shown in Fig. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 9
10 16. Click on the Profile button as shown in Fig. Windows NT displays a dialog box called User Environment Profile as shown in Fig. 10 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
11 Lab Exercises and Solutions 17. Click on the Connect radio button, Z: appears automatically which will be used for the users to get connected to the server. In case, the Z: does not appear, click on the drop down button and select Z: 18. Click on the To box and type \\nt_server2\users\%username% Here nt_server2 is the name of the computer. Users is the share folder name and %username% is a system defined variable for the username. 19. Click on the OK button. Similarly to assign home directories for Charles and James together do the following steps. 20. Click on the OK button to close the user properties dialog box. 21. Click on Charles user name. 22. Keep the <Ctrl> key pressed and then Click on James username. Notice that both get selected as shown in Fig. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 11
12 23. Notice that both get selected as shown in Fig. 24. Click on the Profile button as shown in Fig 12 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
13 Lab Exercises and Solutions 25. Repeat steps 17 to Open the Windows NT Explorer to verify whether the home directories have been created.the users folders should look like as shown in Fig. Ex 4 Set Logon Hours Restriction 1. Select all three users i.e. Alan, Charles and James with the help of <Ctrl> key. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 13
14 2. Click on User main menu. 3. Click on Properties option. 4. Click on the Hours button. A logon hours dialog box is displayed on the screen as shown in Fig. The above calendar displays the number of hours the users can work in a week. The calendar starts at 12.59AM to 12.59PM. The dotted box placed in the first row and first column position is used for restricting the hours. Restrict the working hours of the users to your lab session hours. In this case we will be restricting the users to work between 11 am to 1 pm. 5. Click on the first box and drag it to the last box in the Sunday row as shown in Fig. 14 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
15 Lab Exercises and Solutions 6. Click on the Disallow button. You will notice that the thick line going across the boxes has been deleted indicating that the users cannot access the server on Sundays as shown in Fig. 7. Similarly, disallow users from midnight to 11am and 1 pm to midnight as shown in Fig. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 15
16 Ex 5 Set Workstation Restrictions 1. Click on the Logon-To button Logon workstation dialog box gets displayed on the screen as shown in Fig. 8. Click on the Users May Log Onto These Workstations radio button. Note that all the numbers become highlighted. 9. Click in the first box. 10. Type the name of your computer. In this case, type nt_server2 as shown in Fig. 11. Click on the OK button to close the Logon Workstation dialog box. Set Account Restriction 16 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
17 Lab Exercises and Solutions 1. Click on the Account button. The account information dialog box gets displayed on the screen as shown in Fig. 2. Click on the End of radio button. Notice that Windows NT adds 30 days to your system date and displays it in the end of date box. The date is displayed in the American format i.e. mm/dd/yy. This date value can be changed. 3. Click on the OK button to close the account information dialog box. Test the user log on 1. Click on the User main menu and then click on Exit option to close the User Manager for Domains dialog box. 2. Click on the Start button. 3. Click on the Shutdown option. The Shutdown dialog box appears on the screen. 4. Click on the last radio button i.e. Close all programs and log on as different user?. 5. Click on the Yes button. Windows NT closes all the programs open and displays the Begin logon dialog box on the screen. 6. Keep the<ctrl> and <Alt>keys pressed and then press <Delete> key once. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 17
18 7. Click in the Username box and delete the user name Administrator. 8. Type Alan. 9. Press <Tab> to move to the password box. 10. Type password, Note that all characters should be in small case because this was the format in which we had given the password. 11. Click on the OK button so that Windows NT starts authenticating Alan s account. Windows NT prompts with a logon message as The local policy of this system does not permit you to logon interactively The above message indicates that the users cannot work on the server machine. So as make the users work on the server locally, the administrator has to assign the log on locally rights to the users. 12. Click on the OK button. Granting User Rights Policy 1. Click in the Username box. Delete the username Alan. 2. Type Administrator and press <Tab> to move to password box. 3. Type hai and click on the OK button. 4. Open the User Manager for Domains utility. 5. Click on the Policies main menu as shown in Fig. 6. Click on the User Rights option. The user rights policy dialog box 18 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
19 Lab Exercises and Solutions appears on the screen as shown in Fig. 7. Click on the drop-down arrow of the Right box as shown in Fig. Scroll the list by the help of vertical scroll bar within the drop down list as shown in Fig. 8. Click on the Log on Locally rights. Notice that those who can log on locally to the server are listed in the Grant To box as shown in Fig. 9. Click on the Add button. To add the users you just created. The Add Users and Groups dialog box gets displayed on the screen as shown in Fig. 10. Click on the Everyone group from the Names box as shown in the Fig. All the users created come under the Everyone group. If only some of the users have to be given rights for working on the server, then you will have to click the Show Users button to view all the users and select the user you Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 19
20 would like to give access to. The moment a user or group gets selected, the Add button gets highlighted. 11. Click on the Add button. Note that the Everyone group gets displayed in the Add Names box as shown in the below Fig. 12. Click on the OK button to close the User Rights Policy dialog box. Note that the Everyone group has appeared in the Grant To box as shown in the Fig. 13. Click on the User main menu. 14. Click on the Exit option to exit from User Manager for Domains. 15. Click on the Start button and click on Shutdown option. This time the last option will be selected by default. 16. Click on the Yes button to shut down the computer and log on as different user. 17. Test the user logon of Alan. Windows NT displays a welcome screen as the user logs on for the first time as shown in Fig. 20 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
21 Lab Exercises and Solutions 18. Click on the Close button to close the Welcome Screen and proceed further. 19. Open the User Manager for Domains. The user Alan will not be able to change or delete any settings done by the Administrator though he is able to view all of them. 20. Try to access the properties of the use Alan. Windows NT displays an error as shown in Fig. 21. Click on the OK button. You will notice most of the options are either dimmed or they are not functioning. 22. Try to delete any other user. Windows NT will display you the same error as Access is denied. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 21
22 23. Open the Windows NT Explorer. Notice that at the end of folder s tree a network folder gets attached as Z drive as shown in Fig. This indicates that the folders and profile you had created and assigned are working. 24. Log Off and Log On as Administrator. 25. Change the system time to plus one hour i.e. if current time is 1.00PM then make the system time as 2PM. The user does not have the privilege to change the system time as a result you will have to log on as administrator to change the system time. 26. Log Off and Log On once again as Alan. Windows NT will deny access to the server by displaying the following message. Your account has time restrictions that prevent you from logging on at this time. Please try again later. Ex 6 Managing Trust Relationship with User Manager for Domains In order to establish a trust relationship between two domains, follow these steps. 1. If domain A wants to trust users from domain B, an administrator in domain A should first add domain B to the list of domains it trusts. See the Fig for the Trust Relationships dialog box. In this first action, if you were in domain A, you would add domain B to the Trusted Domains list. To do 22 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
23 Lab Exercises and Solutions this, click the Add button and then you will be prompted to enter the domain and a password, and to confirm the password. 2. The administrator on domain B would have to use the same window to add domain A to its list of trusting domains. Click the Add button and then enter the password you obtained from the administrator of domain A. 3. If you want to establish a two-way trust relationship, you would perform these first two steps on the opposite domain controllers. Note: You can establish trust relationships only between NT networked domains. LAN Manager 2.x clients cannot understand the trust relationships created by the preceding procedures. This is why they do not understand local groups. Lab - 3 ( 2 Real time hours) Creating a Real-Time Chart In this exercise, you will set up a real-time chart and generate activity. To enable disk counters 1. Log on as Administrator, and in the Password box, type password. 2. Click Start, point to Programs, and then click Command Prompt. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 23
24 3. At the command prompt, type diskperf y and then press ENTER.This step is necessary to enable monitoring of disk counters. 4. Shut down and restart your computer. To set up the chart 1. Log on as Administrator, and in the Password box, type password. 2. Click Start, point to Programs, point to Administrative Tools (Common) and click Performance Monitor. 3. On the View menu, click Chart. 4. On the Edit menu, click Add to chart. The Add to Chart dialog box appears. 24 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
25 Lab Exercises and Solutions 5. Using the information provided in the following table, click the following counters that become available for the Memory, Physical Disk, and Processor Object. Click Add after each counter that you add. Object Counter Instance Description Memory Cache Not Memory allocates as file cache. bytes Applica ble Memory Pages/Se c Not Applica ble The number of pages read from or written to disk to resolve memory references to pages that were not in memory at the time of reference. Physical Disk %Disk Time 0 Percentage of time physical disk is busy. Physical Avg.Disk 0 Average number of bytes Disk Bytes/Re ad transferred from disk. Physical Avg.Disk 0 Average number of bytes Disk Bytes/W transferred to disk. rite Processo r %Privileg ed 0 Percentage of processor time spent in Privilege Mode. Time Processo %Process 0 Percentage of time processor r or Time Processo r %User Time 0 Percentage of processor time spent in User Mode. The graph appears, displaying the real-time activities of the memory, physical disk and processor objects. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 25
26 To generate chart activity 1. With Performance Monitor still running, click Start, point to Programs, point to Accessories, and then click Calculator. 2. Begin doing calculations. This will generate CPU cycles. 3. Close the Calculator. 4. Return to the Performance Monitor Chart. 5. Select the %Processor Time counter. Notice the %Processor Time average. Note: To highlight a specific counter on the chart, select a counter, and then press CTRL+H. 26 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
27 Lab Exercises and Solutions 6. Minimize the Chart window. 7. Load and minimize both Windows NT Explorer and the Disk Administrator. 8. Return to the Performance Monitor Chart. 9. Notice the activity, such as spikes, on the chart. 10. Close Windows NT Explorer and Disk Administrator. Logging Processor Activity In this exercise, you will log information and then display the information in a chart. To log information 1. On the View menu in Performance Monitor, click Log. 2. On the Edit menu, click Add To Log. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 27
28 The Add To Log dialog box appears. 3. In the Objects dialog box, hold down the CTRL key while you click Memory, Physical Disk, and Processor, and then click Add. 4. Click Done. 5. On the Options menu, click Log. The Log Options dialog box appears. 6. In the File Name box type lab1.log 28 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
29 Lab Exercises and Solutions 7. Under Update Time, click Periodic Update. 8. In the Interval box, click 1, and then click Start Log. The Performance Monitor window appears, showing information on the log you are creating. Remember that when a log starts, all the counters for the selected object automatically begin recording data. 9. Create processor activity by starting applications or moving the mouse. 10. Collect at least 1 megabyte(mb) of data. Check the File Size box in the Performance Monitor window to determine when your file reaches 1MB. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 29
30 11. On the Options menu, click Log. 12. Click Stop Log. a. To display logged information 1. On the View menu, click Chart. 2. On the Options menu, click Data From. The Data From dialog box appears. 3. In the Data From dialog box, click the button with the ellipse( ) on it. The Open Input Log File dialog box appears. 4. Click the lab1.log and then click Open. The Data From dialog box appears, indicating data values will be displayed from your log file. 5. Click OK. 30 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
31 Lab Exercises and Solutions 6. On the Edit menu, click Add To Chart. 7. Using the information provided in the following table, click the following counters that become available for the Memory, Physical Disk, and Processor Objects. Click Add after each counter that you add. Object Counter Instance Memory Available bytes Not applicable Memory Pages/Sec Not applicable Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 31
32 Physical Disk %Disk Time 0 Physical Disk Avg.Disk Bytes/Read 0 Physical Disk Avg.Disk Bytes/Write 0 Processor %Privileged Time 0 Processor %Processor Time 0 Processor %User Time 0 The chart displays the information collected in your log. To create a report 1. On the View menu, click Report. 2. On the Edit menu, click Add to Report. The Add to Report dialog box appears. 3. Using the information provided in the following table, click the following counters that become available for the Memory, Physical Disk, and Processor objects. Click Add after each counter that you add. 32 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
33 Lab Exercises and Solutions Object Counter Instance Memory Available bytes Not applicable Memory Pages/Sec Not applicable Physical Disk %Disk Time 0 Physical Disk Physical Disk Avg.Disk Bytes/Read Avg.Disk Bytes/Write 0 0 Processor %Privileged Time 0 Processor %Processor Time 0 Processor %User Time 0 4. Click Done. The report displays the information collected in your log. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 33
34 Lab - 4 (2 Real Time Hours) Event Viewer The event viewer is a utility in Windows NT that examines and manages the event log. There are three types of event logs. System log, Security log and application log. To start working with Event Viewer, do the following steps. 1. Click on the Start Button. 2. Click on the Program menu. 3. Click on the Administrative Tools. 4. Click on the Event Viewer utility. Windows NT displays the screen as shown in Fig. By default, the event viewer displays the system log events. The events that are significant to the components of the computer itself are recorded in the system log. For example, a hardware conflict is detected in the system, then the log of that event will be recorded in the system log. To view the application log events. 5. Click on the Log main menu of the Event Viewer. 6. Click on Application Log as shown in Fig. 34 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
35 Lab Exercises and Solutions NT displays a screen, where all events are displayed that get recorded when application are logged. In other words, the events are added when backup processes end. For example, an event is added to application when an alert condition is triggered, when NT repairs inconsistencies on the disk during process, the AUTOCHK program adds an event to this log when it is fixed. The Security log records the events based on the auditing settings that are specified in the User Manager for Domains. By default, NT specifies the Do Not Audit option, which as a result no log get recorded in the security log. Only the administrator has the rights to view the security log. To view the security log first the audit option has to be configured, do the following steps: 7. Open the User Manager for Domains. 8. Click on the Policies main menu. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 35
36 9. Click on the Audit sub option as shown in Fig 10. Select the Events as shown in Fig. 11. Click on the OK button in the Audit Policy dialog box. 12. Close the User Manager for Domains. 13. Open the Notepad and try opening and closing one or more files in it. 14. Close the Notepad. Click on the Event Viewer from the task bar. A sample screen of security log is shown in Fig. The details of each event can be viewed by double clicking the event. 36 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
37 Lab Exercises and Solutions Lab - 5 ( 1 Real time hours) Disk Administrator The most important part of Windows NT is the disk storage space. The server administrator needs to organize the hard disk so as to divide it into partitions and volumes and make use of free disk space in the most efficient manner. Disk Administrator is a graphical utility that is used for administering your disk resources on an NT computer. As compared to DOS commands, it is a combination of CHKDSK, FORMAT and FDISK commands. The Disk Administrator provides the following functions. Graphically displays the status of all the disks. Create and Delete disk partitions. Format, Label and assign drive letters to disk drives. Scan disk and recover from errors. Create and delete fault tolerance. Create or extend volume sets. Migrate disk configuration from one installation to another. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 37
38 Navigating in Disk Administrator 1. Click on the Start button. 2. Click on the Programs menu. 3. Click on Administrative Tools(Common) option. 4. Click on Disk Administrator utility. 5. Click on the OK button. NT displays another message window as shown in Fig, that the signature was not found. Signature is a logical sequence of disk drives, which is written by Windows NT before starting the disk administrator. This message does not appear for the next time. If you take the hard disk from one computer to another, NT will recognize it as it had made the signature on it in the previous machine. NT displays the Disk Administrator dialog box as shown in Fig. Creating a Logical drive 1. Click in the Free space area. NT will enclose the free space with a rectangle indicating that the area has be 38 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
39 Lab Exercises and Solutions 2. Click on the Partition main menu. 3. Click on Create option. NT displays a confirmation box as shown in Fig, for non-compatibility of the partition with MS-DOS. 4. Click on Yes button. NT displays the create primary partition dialog box as shown in Fig asking for the number of bytes you would like to keep in this partition i.e. the partition size. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 39
40 5. Type the partition size to the half of maximum size displayed. In this case, the total size is 4503 MB as such the partition size is taken as 2250 MB. 6. Click on the OK button. 40 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
41 Lab Exercises and Solutions Notice that NT displays the created logical area as unformatted and assigns a drive letter as G: as shown in Fig. Before you proceed further, you will have to commit the change you have made, do the following steps to achieve it. 7. Click on the Partition main menu. 8. Click on Commit Changes Now option as shown in Fig. NT displays a confirmation box for saving changes as shown in Fig. 9. Click on the Yes button. NT prompt you with a message dialog box confirming the changes saved as shown in Fig. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 41
42 10. Click on the OK button. 11. Right-Click on the F drive. A menu pops-up. 12. Click on the Format option. NT displays the Format dialog box as shown in Fig. 13. Convert the File system to NTFS and in the volume label; type RADIANT_NTFS as shown in Fig. 42 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
43 Lab Exercises and Solutions 14. Click on the Start button in the Format window. NT displays the warning dialog box for data erase as shown in Fig. 15. Click on the OK button. Notice that the formatting starts as it gets displayed in the last rectangle as shown in Fig. After the format is complete. Windows NT displays the complete dialog box as shown in Fig. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 43
44 16. Click on the OK button. The F drive gets the volume label as you specified and it becomes highlighted to as that it was gray earlier indicating that the partition was not formatted. 17. Close the Disk Administrator window by clicking the close button. 18. Open Windows NT Explorer. Notice that one more drive has been added to your drive tree structure. The New Directory Creating and Extending Volume Sets Just as you can take one physical disk and divide it into separate partitions that each have a drive letter assigned to them, you can also create what is called a Volume set. A Volume set is a collection of free space areas of up to 32 disks that can be assigned a single drive letter. The space gets used sequentially from one area to the next, but appears to the user or program as a single drive. You can use this to create logical disks that are larger than the one you usually have, or use it to reclaim deleted partitions and reuse them as larger volumes. To create a volume set, follow these steps: 1. Select the first free space by clicking the graphical representation of it on the Disk Administrator Window. 44 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
45 Lab Exercises and Solutions 2. While holding down the Control key, click the next free space you want to add to the volume set. Continue holding down the Control key to keep adding more free spaces to the volume set. 3. When you have finished selecting the spaces to be used to create the volume set, select the Partition Create Volume Set. You will be asked to select the maximum size for the volume, based on the total available space in the free spaces 4. Click on OK. To extend a volume set, follow these steps: 1. Select the volume set first from the graphical display that you want to extend. Then using the Control key and by clicking on additional space, add to the volume set. 2. From the pull-down Partition menu, select Extend volume set and then in the resulting window, choose the total size for the volume set. 3. Click OK. To delete an area from a volume set, you must delete the volume set first. To delete a volume set, select it and then select Delete from the pull-down Partition menu. Lab - 6 (1 Real time hours) Printing in Windows NT Environment a. Adding a printer 1. Log on as Administrator. 2. Choose Start, Settings, Printers as shown in Fig. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 45
46 3. Double-click on the Add Printer icon as shown in Fig. This displays the Add Printer Wizard as shown in Fig. 4. Choose My Computer and click on Next button. 46 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
47 Lab Exercises and Solutions 5. Select LPT1 from the Available Ports as shown in Fig and click on the Next button. 6. Select the manufacturer and printer as per your printer model and click on the Next button. Note : By default the printer name you specified is displayed in the Printer Name dialog box. b. Sharing a printer 1. Continue with the previous exercise. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 47
48 2. Accept the Default Printer name and click on Next button. 3. A dialog box will be displayed prompting you to type the Printer 4. Name is automatically filled but the user can also type the Printer Name. 5. Do not change the name of the Printer. 6. Click on Next button. 7. Click on Shared option circle as shown in Fig. 48 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
49 Lab Exercises and Solutions 8. Type the Printer name in the share name text box as shown in Fig. 9. Click on Next button. 10. Select the No radio button for not printing the test page as shown in Fig. 11. Click on the Finish button. This will copy printer files, create a printer and display the printer icon with a hand holding the icon. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 49
50 Lab - 7 ( 1 Real Time Hours) Registry More Cautions About Editing the Registry If you are just learning about the Registry, you are probably eager to wade right in and modify a value entry. Before you do, however, let me just talk about using caution when manipulating the Registry. The vast majority of Registry items correspond to some setting in the Control Panel, Server Manager, User Manager for Domains, or the like. In general, don t use the Registry to modify a value that can be modified otherwise. So a Question will arise, Why, then learn about the Registry Editor? Here are three reasons: Some settings- importance ones- can be altered only with the Registry Editor, so there is no getting around the fact that an NT administrator has to be proficient with the Registry Editor. You can use the Registry Editor to change system value entries on remote computers. Here is a simple example. You are in New York, and you want to change the background color on a server in Atlanta. One way to do so would be to get on a plane and travel to Atlanta to run the Control Panel on the NT machine at that location. A better way, however, would be to start up the Registry Editor, choose Registry Select Computer, and edit the Registry of the remote computer. (This way assumes that you are running NT Server, and you have the security access to change the Registry of the remote computer: that is, you are a member of the Administrator group on that computer.) A program called REGINI.EXE that comes with the Resource Kit enables you to write scripts to modify the Registry. Such a tool is quite powerful. You could write a REGINI script, for example, to reconfigure an NT setup completely. Again, however, before you start messing with that program, be sure that you have become proficient with the Registry. As explained earlier, you can get into all kinds of trouble when working with the Registry Editor. Imagine what kind of automated disasters you could start at 100MHx with a bad REGINI script! 50 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
51 Lab Exercises and Solutions Changing the Registry Step 1: Description This task enables the Administrator to change the Registry. Step 2 : Action 1. To open the Registry Editor, choose Start Run. 2. In the command line, type REGEDT32 and press Enter. 3. Click Window and choose HKEY_LOCAL_MACHINE. Maximize that window, and you see a screen somewhat like the one in Fig. 4. Modify the value entry in HKEY_LOCAL_MACHINE\ Software\ Microsoft\WindowsNT\CurrentVersion. To do so, double-click the Software key and then double-click the Microsoft key. Next, double-click the Windows NT key, and finally, double-click the CurrentVersion key. You will see a screen as shown in Fig. On the left pane, you still see the Registry structure. On the right, you see the value entries in the RegisteredOrganization subkey. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 51
52 5. Double-click RegisteredOrganization, and you see a screen like the one in Fig. 6. Highlight the old value and replace it with Radiant Software Ltd. Click OK and then close the Registry Editor. 7. Click Help and About for any program (even the Registry Editor will do), and you will see that your organization is now Radiant Software Ltd. 8. By this task, you learned how to use the Registry to change the name of your organization. Altering Registry Data Poking around is not a desirable action or a time-saver, and this points out a glaring weakness of the Registry Editor: it has no effective search routine. Suppose you know that you have something called RegisteredOrganization, but you have no idea where it lives in the Registry. You are just out of luck. REGEDT32 includes a View/Find key, but you can use it to search only the 52 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
53 Lab Exercises and Solutions names of keys, not value entries. Because RegisteredOrganization is a value name within the keycurrentversion, you can search for it only when you know that the key s name is CurrentVersion, which is not very likely. You can use REGEDIT.EXE to search both key names and values. But don t use this program because it might damage the Registry? You can use REGEDIT to view, but not edit, the Registry. This application displays the Registry as one tree and makes finding particular values easy, because it searches for partial matches. Searching for a key in the Registry Editor Step 1: Description This task enables the Administrator to find a key in the Registry. Step 2: Action 1. Log onto the Windows NT server as Administrator. 2. Choose Start Run and type regedit32. You should see a Registry Editor similar to the one 3. Choose View Find key. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 53
54 4. In the Find box of the Find key dialog box, type the name of the key you want to find. 5. If you want to restrict the scope of the search or define the search direction, select the Match Whole Word Only box, the Match Case option, or Up or Down in the Direction box. 6. To see the next occurrence of the key name you specified, click Find Next. 7. Click Find. Because key names are not unique, searching for additional occurrences of the key name you specified, click Find Next. 8. Click Find. Because key names are not unique, searching for additional occurrences of a specific key name is a good idea, to ensure that you find the key you want. 9. Working with the Registry is a key system administration responsibility. Before you can alter any entry, you need to find the entry. This task showed you how to find a key. 10. Now that you have found the key, you can edit the value using the Registry Editor. Editing a key with the Registry Editor Step 1: Description This task enables the Administrator to edit a key in the Registry. Step 2: Action 54 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
55 Lab Exercises and Solutions 1. In the right pane of the Registry Editor window, double-click the value entry, or from the Editor men, choose the String, Binary, Dword, or Multi String command as appropriate for the selected value. 2. Edit the value that appears in the related Editor dialog box and then click OK. 3. Working with the Registry is a key system administrator responsibility. This task showed you how to edit a value. Adding a key to the Registry Editor Step 1: Description This task enables the Administrator to add a key to the Registry. Step 2: Action 1. Select the key or subkey under which you want the new key to appear. Then choose Edit Add key, or press the Ins key. 2. In the Key Name box of the Add Key dialog box, type the name you want to assign your key. The key name cannot contain a backslash(\). It must be unique in relation to other subkeys at the same level in the hierarchy; that is, Key1 and Key2 can each have a subkey named Key3, but Keyl cannot have two subkeys named Key3. 3. Leave the Class box blank, as this entry is reserved for future use. 4. Click OK to display the new key in the Registry Editor Window. 5. This task showed you how to add a key to the Registry using the Registry Editor. Saving a Registry Key Step 1: Description This task enables the Administrator to save a Registry key. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 55
56 Step 2: Action 1. Select the key you want to save as a hive file on a disk. 2. Choose Registry Save Key and then complete the filename information in the Save Key dialog box. Under the FAT file system, this filename cannot have an extension. When the key you are saving is the Registry of a remote computer, the drive and path you specify for the file name are relative to the remote computer. 3. This task showed you how to save a Registry key using the Registry Editor. Restoring a Registry key Step 1: Description This task enables the Administrator to restore a Registry key. Step 2: Action 1. Select the key where you want to restore the hive. 2. Choose Registry Restore and then complete the filename information in the Restore Key dialog box to specify the hive you want to restore. If you are running the FAT file system, this filename cannot have an extension. Also, when you are restoring a key on a remote computer, the drive and path of the filename are relative to the remote computer. If you want to add a key temporarily to a system, use the Restore Volatile command. When you use this command, the Registry makes a volatile copy, which disappears when the system is restarted. 3. This task showed you how to restore a Registry. You cannot restore keys or subkeys that have open handles. For this reason, you cannot restore the SAM or SECURITY subtrees (Windows NT always has handles open in these keys). You use the Restore command only for special conditions, such as restoration of user profiles on a damaged system. Backing Up and Restoring a Registry You might need to restore backed-up versions of Registry hives, for example, when you replace your current Windows NT computer, when a disk 56 Centre for Information Technology and Engineering, Manonmaniam Sundaranar University
57 Lab Exercises and Solutions controller or hard disk goes bad, or when an electrical failure Zaps large parts of a disk. By now, you should understand that the Registry is important and should be protected. It protects itself pretty well with its LOG files, but how can you back it up? Unfortunately, the fact that Registry hive files are always open makes it tough for you to back up the Registry, because most backup utilities are stymied by open files. The NTBackup program that comes with NT works well, but it backs up to tape only. Nevertheless, if you use NTBackup which is pretty good, particularly for its price- then you should tell it to back up the Registry every night. Outside NTBackup are a couple of other protection possibilities. A program named RDISK creates emergency repair disks. And the Resource Kit includes two useful utilities: the REGBACK.EXE program enables you to back up a Registry file, and the REGREST.EXE restore it. Backing Up Registry Hives You can back up Registry hives using one of the four methods. Using a tape drive and the Windows NT backup program (NTBackup), select the Backup Local Registry option in the Backup Information dialog box to include automatically a copy of the local Registry files in the backup set. If you don t have a tape drive, run the REGBACK.EXE program from the Windows NT Resource Tool Kit, or use another tool that uses the same techniques to backup Registry files. Start the computer under a different operating system. Then copy all files in the SystemRoot\SYSTEM32\CONFIG directory to a safe backup location. Use the Save key command in the Registry Editor. This command essentially performs the RegBack procedure manually. Centre for Information Technology and Engineering, Manonmaniam Sundaranar University 57
Windows Me Navigating
 LAB PROCEDURE 11 Windows Me Navigating OBJECTIVES 1. Explore the Start menu. 2. Start an application. 3. Multi-task between applications. 4. Moving folders and files around. 5. Use Control Panel settings.
LAB PROCEDURE 11 Windows Me Navigating OBJECTIVES 1. Explore the Start menu. 2. Start an application. 3. Multi-task between applications. 4. Moving folders and files around. 5. Use Control Panel settings.
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Lesson 1: Preparing for Installation
 2-2 Chapter 2 Installing Windows XP Professional Lesson 1: Preparing for Installation When you install Windows XP Professional, the Windows XP Professional Setup program allows you to specify how to install
2-2 Chapter 2 Installing Windows XP Professional Lesson 1: Preparing for Installation When you install Windows XP Professional, the Windows XP Professional Setup program allows you to specify how to install
3 INSTALLING WINDOWS XP PROFESSIONAL
 INSTALLING WINDOWS XP PROFESSIONAL.1 Preparing for installation Objectives.1.1 Windows XP Professional Hardware Requirements.1.2 Hardware Compatibility List (HCL) check.1. Hard Disk Partition.1.4 Required
INSTALLING WINDOWS XP PROFESSIONAL.1 Preparing for installation Objectives.1.1 Windows XP Professional Hardware Requirements.1.2 Hardware Compatibility List (HCL) check.1. Hard Disk Partition.1.4 Required
Exam : Title. : A+ OS Technologies
 Exam : 220-302 Title : A+ OS Technologies QUESTION 1 Under Windows 2000 you consistently receive out of memory messages when running multiple applications. To avoid having to upgrade RAM immediately you?
Exam : 220-302 Title : A+ OS Technologies QUESTION 1 Under Windows 2000 you consistently receive out of memory messages when running multiple applications. To avoid having to upgrade RAM immediately you?
Automating the Windows 2000 Installation
 Chapter 2 Automating the Windows 2000 Installation MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Perform an unattended installation of Windows 2000 Professional. Install Windows 2000 Professional by
Chapter 2 Automating the Windows 2000 Installation MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Perform an unattended installation of Windows 2000 Professional. Install Windows 2000 Professional by
Lesson 3: Identifying Key Characteristics of Workgroups and Domains
 1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
8 MANAGING SHARED FOLDERS & DATA
 MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
Sun VirtualBox Installation Tutorial
 Sun VirtualBox Installation Tutorial Installing Linux Mint 5 LTS Guest OS By Dennis Berry Welcome to the world of virtualization and Linux. This tutorial is intended to help users who are new to the world
Sun VirtualBox Installation Tutorial Installing Linux Mint 5 LTS Guest OS By Dennis Berry Welcome to the world of virtualization and Linux. This tutorial is intended to help users who are new to the world
The Fundamentals. Document Basics
 3 The Fundamentals Opening a Program... 3 Similarities in All Programs... 3 It's On Now What?...4 Making things easier to see.. 4 Adjusting Text Size.....4 My Computer. 4 Control Panel... 5 Accessibility
3 The Fundamentals Opening a Program... 3 Similarities in All Programs... 3 It's On Now What?...4 Making things easier to see.. 4 Adjusting Text Size.....4 My Computer. 4 Control Panel... 5 Accessibility
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003
 Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
Step-by-Step Guide to Installing Cluster Service
 Page 1 of 23 TechNet Home > Products & Technologies > Windows 2000 Server > Deploy > Configure Specific Features Step-by-Step Guide to Installing Cluster Service Topics on this Page Introduction Checklists
Page 1 of 23 TechNet Home > Products & Technologies > Windows 2000 Server > Deploy > Configure Specific Features Step-by-Step Guide to Installing Cluster Service Topics on this Page Introduction Checklists
Chapter. Configuring the Windows 2000 Environment MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER
 Chapter 4 Configuring the Windows 2000 Environment MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Implement, manage, and troubleshoot disk devices. Install, configure, and manage DVD and CD-ROM devices.
Chapter 4 Configuring the Windows 2000 Environment MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Implement, manage, and troubleshoot disk devices. Install, configure, and manage DVD and CD-ROM devices.
Windows 2000 Safe Mode
 LAB PROCEDURE 29 Windows 2000 Safe Mode OBJECTIVES 1. Restart and try various startup options. RESOURCES Troubleshooting 1. Marcraft 8000 Trainer with Windows 2000 installed 2. A PS2 mouse 3. A LAN connection
LAB PROCEDURE 29 Windows 2000 Safe Mode OBJECTIVES 1. Restart and try various startup options. RESOURCES Troubleshooting 1. Marcraft 8000 Trainer with Windows 2000 installed 2. A PS2 mouse 3. A LAN connection
Chapter. Accessing Files and Folders MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER
 Chapter 10 Accessing Files and Folders MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Monitor, manage, and troubleshoot access to files and folders. Configure, manage, and troubleshoot file compression
Chapter 10 Accessing Files and Folders MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Monitor, manage, and troubleshoot access to files and folders. Configure, manage, and troubleshoot file compression
ChromQuest 4.2 Chromatography Data System
 ChromQuest 4.2 Chromatography Data System Installation Guide CHROM-97200 Revision A April 2005 2006 Thermo Electron Corporation. All rights reserved. Surveyor is a registered trademark and ChromQuest is
ChromQuest 4.2 Chromatography Data System Installation Guide CHROM-97200 Revision A April 2005 2006 Thermo Electron Corporation. All rights reserved. Surveyor is a registered trademark and ChromQuest is
Lesson 2: Editing the Registry
 Lesson 2: Editing the Registry Lesson 2 Editing the Registry 4-15 Windows XP Professional stores hardware and software settings centrally in a hierarchical database called the Registry, which replaces
Lesson 2: Editing the Registry Lesson 2 Editing the Registry 4-15 Windows XP Professional stores hardware and software settings centrally in a hierarchical database called the Registry, which replaces
Optional Lab: Customize Settings in Windows Vista
 12.2.4 Optional Lab: Customize Settings in Windows Vista Introduction Print and complete this lab. This lab is comprised of five parts. This lab is designed to be completed in multiple lab sessions. Part
12.2.4 Optional Lab: Customize Settings in Windows Vista Introduction Print and complete this lab. This lab is comprised of five parts. This lab is designed to be completed in multiple lab sessions. Part
Windows Server 2003 Installation and Configuration Lab Manual Presented by
 Windows Server 2003 Installation and Configuration Lab Manual Presented by Table of Contents Module 2 - Installing Windows Server 2003 R2 and Configuration 3 Module 3 - Installing Hardware, Devices and
Windows Server 2003 Installation and Configuration Lab Manual Presented by Table of Contents Module 2 - Installing Windows Server 2003 R2 and Configuration 3 Module 3 - Installing Hardware, Devices and
Preparing for and Dealing With Windows NT Start-up Problems
 Preparing for and Dealing With Windows NT Start-up Problems Agilent ChemStation Products "Success depends on preparation." Read this document now; schedule regular backups and perform disk maintenance
Preparing for and Dealing With Windows NT Start-up Problems Agilent ChemStation Products "Success depends on preparation." Read this document now; schedule regular backups and perform disk maintenance
Bridge Cable User s Guide
 Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
HP Server tc2110 Network Operating System Installation Guide
 HP Server tc2110 Network Operating System Installation Guide For: Microsoft Windows NT 4.0 Server Microsoft Windows 2000 Server and Microsoft Small Business Server 2000 Novell NetWare 5.1 and Novell Small
HP Server tc2110 Network Operating System Installation Guide For: Microsoft Windows NT 4.0 Server Microsoft Windows 2000 Server and Microsoft Small Business Server 2000 Novell NetWare 5.1 and Novell Small
Chapter 6: Connecting Windows Workstations
 Chapter 6: Connecting Windows Workstations 153 Chapter 6 Connecting Windows Workstations Because this is a book about using Linux on a Microsoft Windows-based network, this chapter shows you how to connect
Chapter 6: Connecting Windows Workstations 153 Chapter 6 Connecting Windows Workstations Because this is a book about using Linux on a Microsoft Windows-based network, this chapter shows you how to connect
Introduction to the. Managed XP Service (For Students) Mark Morley Bob Booth December 2004 AP-Win7. University of Sheffield.
 Introduction to the Managed XP Service (For Students) Mark Morley Bob Booth December 2004 AP-Win7 Contents University of Sheffield 1. INTRODUCTION... 4 2. USING A MANAGED SERVICE MACHINE... 5 2.1 LOGGING
Introduction to the Managed XP Service (For Students) Mark Morley Bob Booth December 2004 AP-Win7 Contents University of Sheffield 1. INTRODUCTION... 4 2. USING A MANAGED SERVICE MACHINE... 5 2.1 LOGGING
NEC Versa 4200 Windows 98 Upgrade Information
 NEC Versa 4200 Windows 98 Upgrade Information Follow the instructions provided in this document to upgrade your NEC Versa 4200 system to Microsoft Windows 98. Please read these notes in their entirety.
NEC Versa 4200 Windows 98 Upgrade Information Follow the instructions provided in this document to upgrade your NEC Versa 4200 system to Microsoft Windows 98. Please read these notes in their entirety.
Installing the IBM ServeRAID Cluster Solution
 Installing the IBM ServeRAID Cluster Solution For IBM Netfinity ServeRAID-4x Ultra160 SCSI Controllers Copyright IBM Corp. 2000 1 2 IBM Netfinity Installing the IBM ServeRAID Cluster Solution Chapter 1.
Installing the IBM ServeRAID Cluster Solution For IBM Netfinity ServeRAID-4x Ultra160 SCSI Controllers Copyright IBM Corp. 2000 1 2 IBM Netfinity Installing the IBM ServeRAID Cluster Solution Chapter 1.
NEC Versa 500D/550D Windows 98 Upgrade Information
 NEC Versa 500D/550D Windows 98 Upgrade Information Follow the instructions provided in this document to upgrade your NEC Versa 500D/550D system to Microsoft Windows 98. Please read these notes in their
NEC Versa 500D/550D Windows 98 Upgrade Information Follow the instructions provided in this document to upgrade your NEC Versa 500D/550D system to Microsoft Windows 98. Please read these notes in their
LevelOne FNS bay/1usb Soho NAS. User s Manual
 LevelOne FNS-1000 1- bay/1usb Soho NAS User s Manual Table of Contents Introduction... 2 The FNS-1000 NAS Server... 2 FNS-1000 Features... 2 Package Contents... 2 System Requirements... 2 Disclaimer...
LevelOne FNS-1000 1- bay/1usb Soho NAS User s Manual Table of Contents Introduction... 2 The FNS-1000 NAS Server... 2 FNS-1000 Features... 2 Package Contents... 2 System Requirements... 2 Disclaimer...
CONTENTS. SysReturn_Manaual Updata 06/4/24. Chapter1 Introducing SysReturn Introduction to SysReturn Features and Functions...
 CONTENTS Chapter1 Introducing SysReturn... 3 Introduction to SysReturn... 3 Features and Functions... 3 Chapter2 Glossary... 5 Chapter3 System Requirement... 6 Hardware Requirement... 6 Software Requirement...
CONTENTS Chapter1 Introducing SysReturn... 3 Introduction to SysReturn... 3 Features and Functions... 3 Chapter2 Glossary... 5 Chapter3 System Requirement... 6 Hardware Requirement... 6 Software Requirement...
Function. Description
 Function Check In Get / Checkout Description Checking in a file uploads the file from the user s hard drive into the vault and creates a new file version with any changes to the file that have been saved.
Function Check In Get / Checkout Description Checking in a file uploads the file from the user s hard drive into the vault and creates a new file version with any changes to the file that have been saved.
PROMISE ARRAY MANAGEMENT ( PAM) USER MANUAL
 PROMISE ARRAY MANAGEMENT ( PAM) USER MANUAL Copyright 2002, Promise Technology, Inc. Copyright by Promise Technology, Inc. (Promise Technology). No part of this manual may be reproduced or transmitted
PROMISE ARRAY MANAGEMENT ( PAM) USER MANUAL Copyright 2002, Promise Technology, Inc. Copyright by Promise Technology, Inc. (Promise Technology). No part of this manual may be reproduced or transmitted
Windows XP. A Quick Tour of Windows XP Features
 Windows XP A Quick Tour of Windows XP Features Windows XP Windows XP is an operating system, which comes in several versions: Home, Media, Professional. The Windows XP computer uses a graphics-based operating
Windows XP A Quick Tour of Windows XP Features Windows XP Windows XP is an operating system, which comes in several versions: Home, Media, Professional. The Windows XP computer uses a graphics-based operating
Configuring Linux as an NIS Client
 Configuring Linux as an NIS Client Estimated Time: 30 minutes Objective Equipment Scenario Procedures To configure a Linux Red Hat system as an NIS server and client. A computer with Linux Red Hat 7.X
Configuring Linux as an NIS Client Estimated Time: 30 minutes Objective Equipment Scenario Procedures To configure a Linux Red Hat system as an NIS server and client. A computer with Linux Red Hat 7.X
Legacy Client Chart (LCC) Installation Guide for Purkinje System
 Legacy Client Chart (LCC) Installation Guide for Purkinje System A Guide to Run and Configure the Legacy Client Chart (LCC) Solution For questions about using this guide please contact IMS@aohc.org Table
Legacy Client Chart (LCC) Installation Guide for Purkinje System A Guide to Run and Configure the Legacy Client Chart (LCC) Solution For questions about using this guide please contact IMS@aohc.org Table
SANS Institute - Operations Essentials. Operating System Installation Guidelines. Windows XP Professional Installation. Creating Boot Disks
 SANS Institute - Operations Essentials Operating System Installation Guidelines The following document guides you step-by-step through the process of creating a dualboot system. Even if you do not use
SANS Institute - Operations Essentials Operating System Installation Guidelines The following document guides you step-by-step through the process of creating a dualboot system. Even if you do not use
MODEMSHARE MILLENNIUM USER GUIDE
 MODEMSHARE MILLENNIUM USER GUIDE Version 1 Copyright Information in this document is subject to change without notice. Although reasonable care has been exercised in the preparation of this manual, SpartaCom
MODEMSHARE MILLENNIUM USER GUIDE Version 1 Copyright Information in this document is subject to change without notice. Although reasonable care has been exercised in the preparation of this manual, SpartaCom
User Guide. Version 2.1
 Kaseya Backup and Disaster Recovery User Guide Version 2.1 August 11, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT
Kaseya Backup and Disaster Recovery User Guide Version 2.1 August 11, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT
All About Mapped Drives
 All About Mapped Drives All About Mapped Drives Intro to Mapped Hard Drives Mapped drives can be very useful when it comes to moving data around on an office or home network and they do have their usefulness.
All About Mapped Drives All About Mapped Drives Intro to Mapped Hard Drives Mapped drives can be very useful when it comes to moving data around on an office or home network and they do have their usefulness.
Intel Server RAID Controller U2-1 Integration Guide For Microsoft* Windows NT* 4.0
 Intel Server RAID Controller U2-1 Integration Guide For Microsoft* Windows NT* 4.0 Revision 1.0 February 2000 Revision History Revision Revision History Date 1.0 Initial Release 02/10/00 Intel Corporation
Intel Server RAID Controller U2-1 Integration Guide For Microsoft* Windows NT* 4.0 Revision 1.0 February 2000 Revision History Revision Revision History Date 1.0 Initial Release 02/10/00 Intel Corporation
Software Conversion Guide
 Eagle SSE Software Conversion Guide Release 17 (Server Level 29) EL2157 This manual contains reference information about software products from Activant Solutions Inc. The software described in this manual
Eagle SSE Software Conversion Guide Release 17 (Server Level 29) EL2157 This manual contains reference information about software products from Activant Solutions Inc. The software described in this manual
Reinstalling Windows 95/98/ME/2000 Professional
 Reinstalling Windows 95/98/ME/2000 Professional Who needs this handout? If you have been instructed to reinstall Windows on your computer as a result of a recommendation from a computer consulting professional,
Reinstalling Windows 95/98/ME/2000 Professional Who needs this handout? If you have been instructed to reinstall Windows on your computer as a result of a recommendation from a computer consulting professional,
L AB: W I N D O W S 7 V I R T U A L I Z A T I O N
 Revision Date: 5/31/2013 Time 1.0 Hours O V E R V IEW In this lab, you will set up a Virtual PC Environment that you can configure at home to complete the lab activities in this course. L AB ACTIVIT IES
Revision Date: 5/31/2013 Time 1.0 Hours O V E R V IEW In this lab, you will set up a Virtual PC Environment that you can configure at home to complete the lab activities in this course. L AB ACTIVIT IES
WINDOWS NT BASICS
 WINDOWS NT BASICS 9.30.99 Windows NT Basics ABOUT UNIVERSITY TECHNOLOGY TRAINING CENTER The University Technology Training Center (UTTC) provides computer training services with a focus on helping University
WINDOWS NT BASICS 9.30.99 Windows NT Basics ABOUT UNIVERSITY TECHNOLOGY TRAINING CENTER The University Technology Training Center (UTTC) provides computer training services with a focus on helping University
Topcat. Installation Guide. Version 1.03
 Microlynx Software Engineering Topcat Installation Guide Version 1.03 1998 Microlynx Software Engineering ii Copyright 1998 Microlynx Software Engineering Neither the whole nor any part of the information
Microlynx Software Engineering Topcat Installation Guide Version 1.03 1998 Microlynx Software Engineering ii Copyright 1998 Microlynx Software Engineering Neither the whole nor any part of the information
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems
 IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems 5.0 Introduction 1. What controls almost all functions on a computer? The operating system 5.1 Explain the purpose of an operating system 2.
IT ESSENTIALS V. 4.1 Module 5 Fundamental Operating Systems 5.0 Introduction 1. What controls almost all functions on a computer? The operating system 5.1 Explain the purpose of an operating system 2.
Installation and Administration Guide
 SWIFTNet Interfaces SWIFTAlliance Workstation 6.0 Installation and Administration Guide This guide is intended for the person responsible for installing and administering SWIFTAlliance Workstation. Prior
SWIFTNet Interfaces SWIFTAlliance Workstation 6.0 Installation and Administration Guide This guide is intended for the person responsible for installing and administering SWIFTAlliance Workstation. Prior
Chapter 12: Advanced Operating Systems
 : Advanced Operating Systems IT Essentials: PC Hardware and Software v4.0 1 Purpose of this Presentation To provide to instructors an overview of : List of chapter objectives Overview of the chapter contents,
: Advanced Operating Systems IT Essentials: PC Hardware and Software v4.0 1 Purpose of this Presentation To provide to instructors an overview of : List of chapter objectives Overview of the chapter contents,
Device Manager. Managing Devices CHAPTER
 2 CHAPTER This chapter describes how to perform routine device management tasks using the Administrator Console. It provides information on managing the devices within your Cisco VXC Manager environment.
2 CHAPTER This chapter describes how to perform routine device management tasks using the Administrator Console. It provides information on managing the devices within your Cisco VXC Manager environment.
For additional support please call Cost Effective Computers at This guide was printed on 9/22/2004.
 Hardware and Windows Basics... 2 Start Up... 3 Starting the Computer... 3 Starting the Pharmacy System... 3 Flip Screen... 4 Starting a Workstation... 4 Shutdown Server (or Windows Workstation)... 4 Backups...
Hardware and Windows Basics... 2 Start Up... 3 Starting the Computer... 3 Starting the Pharmacy System... 3 Flip Screen... 4 Starting a Workstation... 4 Shutdown Server (or Windows Workstation)... 4 Backups...
Section 2 Getting Started
 Section 2 Getting Started ECDL Section 2 Getting Started By the end of this section you should be able to: Start, restart and close down a device Log on and log off Windows Recognise and use the Desktop
Section 2 Getting Started ECDL Section 2 Getting Started By the end of this section you should be able to: Start, restart and close down a device Log on and log off Windows Recognise and use the Desktop
Introduction to Personal Computing
 Introduction to Personal Computing Academic Computing Services www.ku.edu/acs Abstract: This document explains the basics of the Microsoft Windows operating system. It is intended for users who are either
Introduction to Personal Computing Academic Computing Services www.ku.edu/acs Abstract: This document explains the basics of the Microsoft Windows operating system. It is intended for users who are either
SATARaid Serial ATA RAID Management Software
 SATARaid Serial ATA RAID Management Software 05/12/04 Silicon Image, Inc. 1060 East Arques Ave. Sunnyvale CA 94085 (408) 616-4000 www.siliconimage.com Copyright 2003, Silicon Image, Inc. All rights reserved.
SATARaid Serial ATA RAID Management Software 05/12/04 Silicon Image, Inc. 1060 East Arques Ave. Sunnyvale CA 94085 (408) 616-4000 www.siliconimage.com Copyright 2003, Silicon Image, Inc. All rights reserved.
Version 11. NOVASTOR CORPORATION NovaBACKUP
 NOVASTOR CORPORATION NovaBACKUP Version 11 2009 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
NOVASTOR CORPORATION NovaBACKUP Version 11 2009 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
Contents. Getting Started...1. Managing Your Drives...9. Backing Up & Restoring Folders Synchronizing Folders...52
 Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
Exam: Title : Windows 2000 Pro. Ver :
 Exam: 070-210 Title : Windows 2000 Pro Ver : 01.26.04 QUESTION 1 You purchase a USB board, ISDN terminal adapter for your Windows 2000 Professional portable computer. You plug the device into the USB port.
Exam: 070-210 Title : Windows 2000 Pro Ver : 01.26.04 QUESTION 1 You purchase a USB board, ISDN terminal adapter for your Windows 2000 Professional portable computer. You plug the device into the USB port.
A+ Guide to Managing and Maintaining Your PC, 7e. Chapter 16 Fixing Windows Problems
 A+ Guide to Managing and Maintaining Your PC, 7e Chapter 16 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
A+ Guide to Managing and Maintaining Your PC, 7e Chapter 16 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
Implementing Messaging Security for Exchange Server Clients
 Implementing Messaging Security for Exchange Server Clients Objectives Scenario At the end of this lab, you will be able to: Protect e-mail messages using S/MIME signing and encryption Manage e-mail attachment
Implementing Messaging Security for Exchange Server Clients Objectives Scenario At the end of this lab, you will be able to: Protect e-mail messages using S/MIME signing and encryption Manage e-mail attachment
Network Administration
 16-Bit Core - Loading... 3:28 32-Bit Core - Loading... 3:27 802.3... 1:36 802.4... 1:36 802.5... 1:36 A Account Database Synchronization... 11:29 Account Policy... 7:20 Account Policy - Managing... 7:22
16-Bit Core - Loading... 3:28 32-Bit Core - Loading... 3:27 802.3... 1:36 802.4... 1:36 802.5... 1:36 A Account Database Synchronization... 11:29 Account Policy... 7:20 Account Policy - Managing... 7:22
Apptix Online Backup by Mozy User Guide
 Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Apptix Online Backup by Mozy User Guide 1.10.1.2 Contents Chapter 1: Overview...5 Chapter 2: Installing Apptix Online Backup by Mozy...7 Downloading the Apptix Online Backup by Mozy Client...7 Installing
Intermediate/Advanced. Faculty Development Workshop FSE Faculty retreat April 18, 2012
 Intermediate/Advanced Faculty Development Workshop FSE Faculty retreat April 18, 2012 Remote Desktop Sharing Quick Reference Guide for Moderators The Moderator or a Participant may request control of another
Intermediate/Advanced Faculty Development Workshop FSE Faculty retreat April 18, 2012 Remote Desktop Sharing Quick Reference Guide for Moderators The Moderator or a Participant may request control of another
Supporting Networked Computers
 CHAPTER 7 Supporting Networked Computers After completing this chapter, you will be able to: Define the main concepts of networking, including the roles of TCP/IP, IP addresses, and subnet masks. Set up
CHAPTER 7 Supporting Networked Computers After completing this chapter, you will be able to: Define the main concepts of networking, including the roles of TCP/IP, IP addresses, and subnet masks. Set up
Part 1: Understanding Windows XP Basics
 542362 Ch01.qxd 9/18/03 9:54 PM Page 1 Part 1: Understanding Windows XP Basics 1: Starting Up and Logging In 2: Logging Off and Shutting Down 3: Activating Windows 4: Enabling Fast Switching between Users
542362 Ch01.qxd 9/18/03 9:54 PM Page 1 Part 1: Understanding Windows XP Basics 1: Starting Up and Logging In 2: Logging Off and Shutting Down 3: Activating Windows 4: Enabling Fast Switching between Users
Windows* 2003 Cluster Implementation Guide for the Intel RAID controller SRCU42X
 Windows* 2003 Cluster Implementation Guide for the Intel RAID controller SRCU42X Revision 1.0 May 2003 Enterprise Platforms and Services Marketing Disclaimers Information in this document is provided in
Windows* 2003 Cluster Implementation Guide for the Intel RAID controller SRCU42X Revision 1.0 May 2003 Enterprise Platforms and Services Marketing Disclaimers Information in this document is provided in
Full file at
 Chapter 2 Solutions Answers to the Chapter 2 Review Questions 1. The Melissa virus was transported by. c. e-mail 2. Which of the following are used for updates in Windows XP Professional? (Choose all that
Chapter 2 Solutions Answers to the Chapter 2 Review Questions 1. The Melissa virus was transported by. c. e-mail 2. Which of the following are used for updates in Windows XP Professional? (Choose all that
VISUAL QUICKPRO GUIDE
 VISUAL QUICKPRO GUIDE Red Hat Linux 6 Harold Davis Peachpit Press Visual QuickPro Guide Red Hat Linux 6 Harold Davis Peachpit Press 1249 Eighth Street Berkeley, CA 94710 510/524-2178 800/283-9444 510/524-2221
VISUAL QUICKPRO GUIDE Red Hat Linux 6 Harold Davis Peachpit Press Visual QuickPro Guide Red Hat Linux 6 Harold Davis Peachpit Press 1249 Eighth Street Berkeley, CA 94710 510/524-2178 800/283-9444 510/524-2221
GUARD1 PLUS Documentation. Version TimeKeeping Systems, Inc. GUARD1 PLUS and THE PIPE are registered trademarks
 GUARD1 PLUS Documentation Version 3.02 2000-2005 TimeKeeping Systems, Inc. GUARD1 PLUS and THE PIPE are registered trademarks i of TimeKeeping Systems, Inc. Table of Contents Welcome to Guard1 Plus...
GUARD1 PLUS Documentation Version 3.02 2000-2005 TimeKeeping Systems, Inc. GUARD1 PLUS and THE PIPE are registered trademarks i of TimeKeeping Systems, Inc. Table of Contents Welcome to Guard1 Plus...
Online Demo Guide. Barracuda PST Enterprise. Introduction (Start of Demo) Logging into the PST Enterprise
 Online Demo Guide Barracuda PST Enterprise This script provides an overview of the main features of PST Enterprise, covering: 1. Logging in to PST Enterprise 2. Client Configuration 3. Global Configuration
Online Demo Guide Barracuda PST Enterprise This script provides an overview of the main features of PST Enterprise, covering: 1. Logging in to PST Enterprise 2. Client Configuration 3. Global Configuration
5 MANAGING USER ACCOUNTS AND GROUPS
 MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
Administrator for Enterprise Clients: User s Guide. Second Edition
 Administrator for Enterprise Clients: User s Guide Second Edition The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2002. Administrator for Enterprise Clients: User s
Administrator for Enterprise Clients: User s Guide Second Edition The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2002. Administrator for Enterprise Clients: User s
NEC PowerMate VT 300 Series Release Notes
 NEC PowerMate VT 300 Series Release Notes The PowerMate VT 300 Series Release Notes provide up-to-date information on installing the applications that come with your computer. These notes also provide
NEC PowerMate VT 300 Series Release Notes The PowerMate VT 300 Series Release Notes provide up-to-date information on installing the applications that come with your computer. These notes also provide
Windows 2000 Disk Management
 LAB PROCEDURE 25 Windows 2000 Disk Management OBJECTIVES 1. Use Disk Cleanup. 2. Backup a file. 3. Restore a backup. 4. Compress a file. 5. Encrypt a file. Troubleshooting RESOURCES 1. Marcraft 8000 Trainer
LAB PROCEDURE 25 Windows 2000 Disk Management OBJECTIVES 1. Use Disk Cleanup. 2. Backup a file. 3. Restore a backup. 4. Compress a file. 5. Encrypt a file. Troubleshooting RESOURCES 1. Marcraft 8000 Trainer
Recent Operating System Class notes 04 Managing Users on Windows XP March 22, 2004
 Recent Operating System Class notes 04 Managing Users on Windows XP March 22, 2004 You log into a system to notify the system who you are. When you log off, any files you have opened are cleaned up, and
Recent Operating System Class notes 04 Managing Users on Windows XP March 22, 2004 You log into a system to notify the system who you are. When you log off, any files you have opened are cleaned up, and
Paragon Exact Image. User Manual CONTENTS. Introduction. Key Features. Installation. Package Contents. Minimum System Requirements.
 Paragon Exact Image User Manual CONTENTS Introduction Key Features Installation Package Contents Minimum System Requirements Basic Concepts Backup Operations Scheduling Interface Overview General Layout
Paragon Exact Image User Manual CONTENTS Introduction Key Features Installation Package Contents Minimum System Requirements Basic Concepts Backup Operations Scheduling Interface Overview General Layout
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 7 Fixing Windows Problems
 : Managing, Maintaining, and Troubleshooting, 5e Chapter 7 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
: Managing, Maintaining, and Troubleshooting, 5e Chapter 7 Fixing Windows Problems Objectives Learn what to do when a hardware device, application, or Windows component gives a problem Learn what to do
Trouble Shooting. Access Rights. Application Crashed. CSV File Will Not Open. file://c:\users\antonym\appdata\local\temp\~hh6280.
 Page 1 of 11 This section contains helpful hints when something goes wrong. Access Rights Application Crashed CSV File Will Not Open Issues with Opening Application (Data Link Properties Help) Incorrect
Page 1 of 11 This section contains helpful hints when something goes wrong. Access Rights Application Crashed CSV File Will Not Open Issues with Opening Application (Data Link Properties Help) Incorrect
Access Gateway Client User's Guide
 Sysgem Access Gateway Access Gateway Client User's Guide Sysgem AG Sysgem is a trademark of Sysgem AG. Other brands and products are registered trademarks of their respective holders. 2013-2015 Sysgem
Sysgem Access Gateway Access Gateway Client User's Guide Sysgem AG Sysgem is a trademark of Sysgem AG. Other brands and products are registered trademarks of their respective holders. 2013-2015 Sysgem
K2 ServerSave Installation and User Guide
 K2 ServerSave Installation and User Guide Chapter 1: Introduction 1.1 What is K2 ServerSave? Welcome to the K2 ServerSave Server Edition User Guide. This guide briefly describes the K2 ServerSave Application
K2 ServerSave Installation and User Guide Chapter 1: Introduction 1.1 What is K2 ServerSave? Welcome to the K2 ServerSave Server Edition User Guide. This guide briefly describes the K2 ServerSave Application
Server Edition. V8 Peregrine User Manual. for Microsoft Windows
 Server Edition V8 Peregrine User Manual for Microsoft Windows Copyright Notice and Proprietary Information All rights reserved. Attix5, 2015 Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
Server Edition V8 Peregrine User Manual for Microsoft Windows Copyright Notice and Proprietary Information All rights reserved. Attix5, 2015 Trademarks - Microsoft, Windows, Microsoft Windows, Microsoft
RAID User Guide. Edition. Trademarks V1.0 P/N: U25-A2-0E
 RAID User Guide Edition V1.0 P/N: 91-187-U25-A2-0E Trademarks All brand or product names mentioned are trademarks or registered trademarks of their respective holders. 1 2004-12-15, 9:01 Contents Intel
RAID User Guide Edition V1.0 P/N: 91-187-U25-A2-0E Trademarks All brand or product names mentioned are trademarks or registered trademarks of their respective holders. 1 2004-12-15, 9:01 Contents Intel
A+ Guide to Managing & Maintaining Your PC, 8th Edition. Chapter 11 Optimizing Windows
 Chapter 11 Optimizing Windows Objectives Learn about Windows utilities and tools you can use to solve problems with Windows Learn how to optimize Windows to improve performance Learn how to manually remove
Chapter 11 Optimizing Windows Objectives Learn about Windows utilities and tools you can use to solve problems with Windows Learn how to optimize Windows to improve performance Learn how to manually remove
How to install the software of ZNS8022
 How to install the software of ZNS8022 1. Please connect ZNS8022 to your PC after finished assembly. 2. Insert Installation CD to your CD-ROM drive and initiate the auto-run program. The wizard will run
How to install the software of ZNS8022 1. Please connect ZNS8022 to your PC after finished assembly. 2. Insert Installation CD to your CD-ROM drive and initiate the auto-run program. The wizard will run
Recent Operating System Class notes 08 Administrative Tools (Part one) April 14, 2004
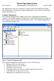 Recent Operating System Class notes 08 Administrative Tools (Part one) April 14, 2004 The administrative tools are a collection of system control and configuration utilities. The administrative tools include
Recent Operating System Class notes 08 Administrative Tools (Part one) April 14, 2004 The administrative tools are a collection of system control and configuration utilities. The administrative tools include
Network Planning and Implementation
 Network Planning and Implementation SYLLABUS 3.1 Designing network 3.1.1 Accessing network needs- applications, users, network services, security and safety, growth and capacity planning 3.1.2 Meeting
Network Planning and Implementation SYLLABUS 3.1 Designing network 3.1.1 Accessing network needs- applications, users, network services, security and safety, growth and capacity planning 3.1.2 Meeting
GUARD1 PLUS Manual Version 2.8
 GUARD1 PLUS Manual Version 2.8 2002 TimeKeeping Systems, Inc. GUARD1 PLUS and THE PIPE are registered trademarks of TimeKeeping Systems, Inc. Table of Contents GUARD1 PLUS... 1 Introduction How to get
GUARD1 PLUS Manual Version 2.8 2002 TimeKeeping Systems, Inc. GUARD1 PLUS and THE PIPE are registered trademarks of TimeKeeping Systems, Inc. Table of Contents GUARD1 PLUS... 1 Introduction How to get
WinSCP. Author A.Kishore/Sachin
 WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
WinSCP WinSCP is a freeware windows client for the SCP (secure copy protocol), a way to transfer files across the network using the ssh (secure shell) encrypted protocol. It replaces other FTP programs
_APP A_541_10/31/06. Appendix A. Backing Up Your Project Files
 1-59863-307-4_APP A_541_10/31/06 Appendix A Backing Up Your Project Files At the end of every recording session, I back up my project files. It doesn t matter whether I m running late or whether I m so
1-59863-307-4_APP A_541_10/31/06 Appendix A Backing Up Your Project Files At the end of every recording session, I back up my project files. It doesn t matter whether I m running late or whether I m so
ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/efsguide.htm
 Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the
Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the
Nortel Contact Center Routine Maintenance NN
 NN44400-514 Document status: Standard Document issue: 01.03 Document date: 26 February 2010 Product release: Release 7.0 Job function: Administration Type: Technical Document Language type: English Copyright
NN44400-514 Document status: Standard Document issue: 01.03 Document date: 26 February 2010 Product release: Release 7.0 Job function: Administration Type: Technical Document Language type: English Copyright
Enter your Appserv username and password to sign in to the Website
 Appserv Desktop Access Logging on from a Windows 10 Device Step 1. To sign in to the Appserv Desktop Access website, either enter the following address into the Microsoft Edge browser address bar, or click
Appserv Desktop Access Logging on from a Windows 10 Device Step 1. To sign in to the Appserv Desktop Access website, either enter the following address into the Microsoft Edge browser address bar, or click
Macrorit Partition Expert 4.3.5
 Content Macrorit Partition Expert 4.3.5... 1 User Manual... 1 Welcome... 1 About Macrorit Partition Expert... 1 Main Features... 1 Advanced Features... 1 Tools... 2 Unique Technology... 2 System Requirements:...
Content Macrorit Partition Expert 4.3.5... 1 User Manual... 1 Welcome... 1 About Macrorit Partition Expert... 1 Main Features... 1 Advanced Features... 1 Tools... 2 Unique Technology... 2 System Requirements:...
SUPERTRAK EX8300, EX8350 RAID 6 UPGRADE & PRIMER
 SUPERTRAK EX8300, EX8350 RAID 6 UPGRADE & PRIMER Version 1.1 2005 Promise Technology, Inc. All rights reserved. SuperTrak EX8300, EX8350 RAID 6 Upgrade & Primer Copyright 2005 Promise Technology, Inc.
SUPERTRAK EX8300, EX8350 RAID 6 UPGRADE & PRIMER Version 1.1 2005 Promise Technology, Inc. All rights reserved. SuperTrak EX8300, EX8350 RAID 6 Upgrade & Primer Copyright 2005 Promise Technology, Inc.
Offline Array Recovery Procedures SuperTrak SX6000 and UltraTrak
 Version 5b Offline Array Recovery Procedures SuperTrak SX6000 and UltraTrak This document describes the procedures for protecting data and restoring array status to arrays that have gone OFFLINE. Promise
Version 5b Offline Array Recovery Procedures SuperTrak SX6000 and UltraTrak This document describes the procedures for protecting data and restoring array status to arrays that have gone OFFLINE. Promise
Virtual CD TS 1 Introduction... 3
 Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
Lab: Implementing SMS 2003 SP1 Features
 Lab: Implementing SMS 2003 SP1 Features Objectives After completing this lab, you will be able to: Identify an SMS 2003 SP1 site. Implement SMS 2003 SP1 folders. Implement a configurable HTTP port in SMS
Lab: Implementing SMS 2003 SP1 Features Objectives After completing this lab, you will be able to: Identify an SMS 2003 SP1 site. Implement SMS 2003 SP1 folders. Implement a configurable HTTP port in SMS
Applied ICT Skills MS Windows
 Applied ICT Skills MS Windows Lesson 1 - How to install an operating system into computer? Windows 7 is perhaps the best Microsoft operating system and is very easy to install compared to other windows.
Applied ICT Skills MS Windows Lesson 1 - How to install an operating system into computer? Windows 7 is perhaps the best Microsoft operating system and is very easy to install compared to other windows.
Computer Essentials Session 1 Lesson Plan
 Note: Completing the Mouse Tutorial and Mousercise exercise which are available on the Class Resources webpage constitutes the first part of this lesson. ABOUT PROGRAMS AND OPERATING SYSTEMS Any time a
Note: Completing the Mouse Tutorial and Mousercise exercise which are available on the Class Resources webpage constitutes the first part of this lesson. ABOUT PROGRAMS AND OPERATING SYSTEMS Any time a
Windows NT Server Printer Driver Upgrade Instructions
 Windows NT Server Printer Driver Upgrade Instructions The steps detailed below describe the most reliable method to upgrade printer driver versions after v1.6.0227a on a Windows NT 4.0 Server that is shared
Windows NT Server Printer Driver Upgrade Instructions The steps detailed below describe the most reliable method to upgrade printer driver versions after v1.6.0227a on a Windows NT 4.0 Server that is shared
Introduction to IBM Rational HATS For IBM System i (5250)
 Introduction to IBM Rational HATS For IBM System i (5250) Introduction to IBM Rational HATS 1 Lab instructions This lab teaches you how to use IBM Rational HATS to create a Web application capable of transforming
Introduction to IBM Rational HATS For IBM System i (5250) Introduction to IBM Rational HATS 1 Lab instructions This lab teaches you how to use IBM Rational HATS to create a Web application capable of transforming
In the Insight console, access advanced features by right-clicking on a student computer in either the Detail or Thumbnail view.
 On the teacher computer, there is small Insight icon in the taskbar. The taskbar is located in the bottom right corner of the computer screen. Double-click the icon to open Insight. You can right-click
On the teacher computer, there is small Insight icon in the taskbar. The taskbar is located in the bottom right corner of the computer screen. Double-click the icon to open Insight. You can right-click
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
