Final Exam. EECS 2011 Prof. J. Elder - 1 -
|
|
|
- Edgar Rose
- 5 years ago
- Views:
Transcription
1 Final Exam Ø Wed Apr 11 2pm 5pm Aviva Tennis Centre Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps and hash tables, binary search, loop invariants, binary search trees, sorting, graphs) - 1 -
2 Suggested Study Strategy Ø Review and understand the slides. Ø Do all of the practice problems provided. Ø Review all assignments, especially assignments 3 and 4. Ø Read the textbook, especially where concepts and methods are not yet clear to you. Ø Do extra practice problems from the textbook. Ø Review the midterm and solutions for practice writing this kind of exam. Ø Practice writing clear, succint pseudocode! - 2 -
3 End of Term Review - 3 -
4 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs - 4 -
5 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs - 5 -
6 Maps Ø A map models a searchable collection of key-value entries Ø The main operations of a map are for searching, inserting, and deleting items Ø Multiple entries with the same key are not allowed Ø Applications: q address book q student-record database - 6 -
7 Performance of a List-Based Map Ø Performance: q put, get and remove take O(n) time since in the worst case (the item is not found) we traverse the entire sequence to look for an item with the given key Ø The unsorted list implementation is effective only for small maps - 7 -
8 Hash Tables Ø A hash table is a data structure that can be used to make map operations faster. Ø While worst-case is still O(n), average case is typically O(1)
9 Compression Functions Ø Division: q h 2 (y) = y mod N q The size N of the hash table is usually chosen to be a prime (on the assumption that the differences between hash keys y are less likely to be multiples of primes). Ø Multiply, Add and Divide (MAD): q h 2 (y) = [(ay + b) mod p] mod N, where ² p is a prime number greater than N ² a and b are integers chosen at random from the interval [, p 1], with a >
10 Collision Handling Ø Collisions occur when different elements are mapped to the same cell Ø Separate Chaining: q Let each cell in the table point to a linked list of entries that map there q Separate chaining is simple, but requires additional memory outside the table Ø Ø Ø
11 Open Addressing: Linear Probing Ø Open addressing: the colliding item is placed in a different cell of the table Ø Linear probing handles collisions by placing the colliding item in the next (circularly) available table cell Ø Each table cell inspected is referred to as a probe Ø Colliding items lump together, so that future collisions cause a longer sequence of probes Ø Example: q h(x) = x mod 13 q Insert keys 18, 41, 22, 44, 59, 32, 31, 73, in this order
12 Open Addressing: Double Hashing Ø Double hashing is an alternative open addressing method that uses a secondary hash function h (k) in addition to the primary hash function h(x). Ø Suppose that the primary hashing i=h(k) leads to a collision. Ø We then iteratively probe the locations (i + jh (k)) mod N for j =, 1,, N - 1 Ø The secondary hash function h (k) cannot have zero values Ø N is typically chosen to be prime. Ø Common choice of secondary hash function h (k): q h (k) = q - k mod q, where ² q < N ² q is a prime Ø The possible values for h (k) are 1, 2,, q
13 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs
14 Ordered Maps and Dictionaries Ø If keys obey a total order relation, can represent a map or dictionary as an ordered search table stored in an array. Ø Can then support a fast find(k) using binary search. q at each step, the number of candidate items is halved q terminates after a logarithmic number of steps q Example: find(7) l l m h m h l m h l=m =h
15 Loop Invariants Ø Binary search can be implemented as an iterative algorithm (it could also be done recursively). Ø Loop Invariant: An assertion about the current state useful for designing, analyzing and proving the correctness of iterative algorithms
16 Establishing Loop Invariant From the Pre-Conditions on the input instance we must establish the loop invariant
17 Maintain Loop Invariant By Induction the computation will always be in a safe location. Þ S() ü ï ï ý Þ " isi, ( ) Þ ï Þ " isi, ( ) Þ Si ( + 1) ï þ
18 Ending The Algorithm Ø Define Exit Condition Exit Ø Termination: With sufficient progress, the exit condition will be met. km Exit Ø When we exit, we know q exit condition is true q loop invariant is true from these we must establish Exit the post conditions
19 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs
20 Binary Search Trees Ø Insertion Ø Deletion Ø AVL Trees Ø Splay Trees - 2 -
21 Binary Search Tree All nodes in left subtree Any node All nodes in right subtree
22 Ø Cut sub-tree in half. Search: Define Step Ø Determine which half the key would be in. Ø Keep that half. key If key < root, then key is in left half. If key = root, then key is found If key > root, then key is in right half
23 Insertion (For Dictionary) Ø To perform operation insert(k, o), we search for key k (using TreeSearch) Ø Suppose k is not already in the tree, and let w be the leaf reached by the search Ø We insert k at node w and expand w into an internal node Ø Example: insert 5 w < > > w
24 Insertion Ø Suppose k is already in the tree, at node v. Ø We continue the downward search through v, and let w be the leaf reached by the search Ø Note that it would be correct to go either left or right at v. We go left by convention. Ø We insert k at node w and expand w into an internal node Ø Example: insert 6 2 < > > w w
25 Deletion Ø To perform operation remove(k), we search for key k Ø Suppose key k is in the tree, and let v be the node storing k Ø If node v has a leaf child w, we remove v and w from the tree with operation removeexternal(w), which removes w and its parent Ø Example: remove 4 < > 1 4 v 8 w
26 Deletion (cont.) Ø Now consider the case where the key k to be removed is stored at a node v whose children are both internal q we find the internal node w that follows v in an inorder traversal q we copy the entry stored at w into node v q we remove node w and its left child z (which must be a leaf) by means of operation removeexternal(z) Ø Example: remove v 1 5 v w z
27 Performance Ø Consider a dictionary with n items implemented by means of a binary search tree of height h q the space used is O(n) q methods find, insert and remove take O(h) time Ø The height h is O(n) in the worst case and O(log n) in the best case Ø It is thus worthwhile to balance the tree (next topic)!
28 AVL Trees Ø AVL trees are balanced. Ø An AVL Tree is a binary search tree in which the heights of siblings can differ by at most height
29 Insertion Ø Imbalance may occur at any ancestor of the inserted node. height = 3 7 height = Insert(2) 3 4 Problem!
30 Ø Step 1: Search Insertion: Rebalancing Strategy q Starting at the inserted node, traverse toward the root until an imbalance is discovered. height = Problem!
31 Insertion: Rebalancing Strategy Ø Step 2: Repair q The repair strategy is called trinode restructuring. q 3 nodes x, y and z are distinguished: ² z = the parent of the high sibling ² y = the high sibling ² x = the high child of the high sibling q We can now think of the subtree 3 rooted at z as consisting of these 3 nodes plus their 4 subtrees height = Problem!
32 Insertion: Trinode Restructuring Example Note that y is the middle value. height = h z h-1 y Restructure h-1 y h-3 T 3 h-2 x h-2 z h-2 x h-3 T 2 h-3 h-3 T T 1 T 2 T 3 T T 1 one is h-3 & one is h-4 one is h-3 & one is h
33 Removal Ø Imbalance may occur at an ancestor of the removed node. height = 3 7 height = Remove(8) 2 4 Problem!
34 Ø Step 1: Search Removal: Rebalancing Strategy q Starting at the location of the removed node, traverse toward the root until an imbalance is discovered. height = Problem!
35 Removal: Rebalancing Strategy Ø Step 2: Repair q We again use trinode restructuring. q 3 nodes x, y and z are distinguished: height = 3 7 ² z = the parent of the high sibling ² y = the high sibling ² x = the high child of the high sibling (if children are equally high, keep chain linear) Problem!
36 Removal: Trinode Restructuring - Case 1 Note that y is the middle value. height = h z Restructure h or h-1 y h-1 y h-3 T 3 h-2 x h-1 or h-2 z h-2 x T T 1 h-2 or h-3 T 2 T T 1 T 2 T 3 h-3 or h-3 & h- 4 h-2 or h-3 h-3 h-3 or h-3 & h
37 Ø Step 2: Repair Removal: Rebalancing Strategy q Unfortunately, trinode restructuring may reduce the height of the subtree, causing another imbalance further up the tree. q Thus this search and repair process must be repeated until we reach the root
38 Splay Trees Ø Self-balancing BST Ø Invented by Daniel Sleator and Bob Tarjan Ø Allows quick access to recently accessed elements D. Sleator Ø Bad: worst-case O(n) Ø Good: average (amortized) case O(log n) Ø Often perform better than other BSTs in practice R. Tarjan
39 Splaying Ø Splaying is an operation performed on a node that iteratively moves the node to the root of the tree. Ø In splay trees, each BST operation (find, insert, remove) is augmented with a splay operation. Ø In this way, recently searched and inserted elements are near the top of the tree, for quick access
40 Zig-Zig Ø Performed when the node x forms a linear chain with its parent and grandparent. q i.e., right-right or left-left z x y y x T 3 T 4 zig-zig T 1 T 2 z T 1 T 2 T 3 T 4-4 -
41 Zig-Zag Ø Performed when the node x forms a non-linear chain with its parent and grandparent q i.e., right-left or left-right z x y zig-zag z y T 1 x T 4 T 1 T 2 T 3 T 4 T 2 T
42 Zig Ø Performed when the node x has no grandparent q i.e., its parent is the root y zig x x T 4 w y w T 3 T 1 T 2 T 3 T 4 T 1 T
43 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs
44 Ø Comparison Sorting q Selection Sort q Bubble Sort q Insertion Sort q Merge Sort q Heap Sort q Quick Sort Ø Linear Sorting q Counting Sort q Radix Sort q Bucket Sort Sorting Algorithms
45 Comparison Sorts Ø Comparison Sort algorithms sort the input by successive comparison of pairs of input elements. Ø Comparison Sort algorithms are very general: they make no assumptions about the values of the input elements e.g.,3 11?
46 Sorting Algorithms and Memory Ø Some algorithms sort by swapping elements within the input array Ø Such algorithms are said to sort in place, and require only O(1) additional memory. Ø Other algorithms require allocation of an output array into which values are copied. Ø These algorithms do not sort in place, and require O(n) additional memory swap
47 Stable Sort Ø A sorting algorithm is said to be stable if the ordering of identical keys in the input is preserved in the output. Ø The stable sort property is important, for example, when entries with identical keys are already ordered by another criterion. Ø (Remember that stored with each key is a record containing some useful information.)
48 Summary of Comparison Sorts Algorithm Best Case Worst Case Average Case In Place Stable Comments Selection n 2 n 2 Yes Yes Bubble n n 2 Yes Yes Insertion n n 2 Yes Yes Good if often almost sorted Merge n log n n log n No Yes Good for very large datasets that require swapping to disk Heap n log n n log n Yes No Best if guaranteed n log n required Quick n log n n 2 n log n Yes No Usually fastest in practice
49 Comparison Sort: Decision Trees Ø For a 3-element array, there are 6 external nodes. Ø For an n-element array, there are n! external nodes
50 Comparison Sort Ø To store n! external nodes, a decision tree must have a height of at least logn! Ø Worst-case time is equal to the height of the binary decision tree. Thus T(n) Ω( logn! ) wherelogn! = n log i log n / 2 i =1 Thus T(n) Ω(nlogn) n/ 2 i =1 Ω(nlogn) Thus MergeSort & HeapSort are asymptotically optimal
51 Linear Sorts? Comparison sorts are very general, but are W ( nlog n) Faster sorting may be possible if we can constrain the nature of the input
52 CountingSort Input: Output: Index: Value v: Location of next record with digit v Algorithm: Go through the records in order putting them where they go
53 RadixSort i+1 Is sorted wrt first i digits. Sort wrt i+1st digit Is sorted wrt first i+1 digits. These are in the correct order because sorted wrt high order digit
54 RadixSort i+1 Is sorted wrt first i digits. Sort wrt i+1st digit Is sorted wrt first i+1 digits. These are in the correct order because was sorted & stable sort left sorted
55 Bucket Sort
56 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs
57 Graphs Ø Definitions & Properties Ø Implementations Ø Depth-First Search Ø Breadth-First Search
58 Properties Property 1 Σ v deg(v) = 2 E Proof: each edge is counted twice Property 2 In an undirected graph with no self-loops and no multiple edges E V ( V - 1)/2 Proof: each vertex has degree at most ( V 1) Q: What is the bound for a digraph? A : E V (V 1) Notation V E deg(v) number of vertices number of edges degree of vertex v Example n V = 4 n E = 6 n deg(v) =
59 DFS Algorithm Pattern DFS(G) Precondition: G is a graph Postcondition: all vertices in G have been visited for each vertex u V[G] color[u] = BLACK //initialize vertex for each vertex u V[G] if color[u] = BLACK //as yet unexplored DFS-Visit(u) total work = θ(v )
60 DFS Algorithm Pattern DFS-Visit (u) Precondition: vertex u is undiscovered Postcondition: all vertices reachable from u have been processed colour[u] RED for each v Adj[u] //explore edge (u,v) if color[v] = BLACK DFS-Visit(v) colour[u] GRAY total work = Adj[v] = θ(e) v V Thus running time = θ(v + E) (assuming adjacency list structure) - 6 -
61 Other Variants of Depth-First Search Ø The DFS Pattern can also be used to q Compute a forest of spanning trees (one for each call to DFSvisit) encoded in a predecessor list π[u] q Label edges in the graph according to their role in the search (see textbook) ² Tree edges, traversed to an undiscovered vertex ² Forward edges, traversed to a descendent vertex on the current spanning tree ² Back edges, traversed to an ancestor vertex on the current spanning tree ² Cross edges, traversed to a vertex that has already been discovered, but is not an ancestor or a descendent
62 BFS Algorithm Pattern BFS(G,s) Precondition: G is a graph, s is a vertex in G Postcondition: all vertices in G reachable from s have been visited for each vertex u V[G] color[u] BLACK //initialize vertex colour[s] RED Q.enqueue(s) while Q u Q.dequeue() for each v Adj[u] //explore edge (u,v) if color[v] = BLACK colour[v] RED Q.enqueue(v) colour[u] GRAY
63 Applications Ø BFS traversal can be specialized to solve the following problems in O( V + E ) time: q Compute the connected components of G q Compute a spanning forest of G q Find a simple cycle in G, or report that G is a forest q Given two vertices of G, find a path in G between them with the minimum number of edges, or report that no such path exists
64 Breadth-First Search Input: Graph G = ( V, E) (directed or undirected) and source vertex s Î V. Output: dv [ ] = shortest path distance d ( sv, ) from sto v, " vî V. p [ v] = u such that ( u, v) is last edge on a shortest path from s to v. Ø Idea: send out search wave from s. Ø Keep track of progress by colouring vertices: q Undiscovered vertices are coloured black q Just discovered vertices (on the wavefront) are coloured red. q Previously discovered vertices (behind wavefront) are coloured grey
65 BFS(G,s) Breadth-First Search Algorithm: Properties Precondition: G is a graph, s is a vertex in G Postcondition: d[u] = shortest distance δ[u] and π[u] = predecessor of u on shortest paths from s to each vertex u in G for each vertex u V[G] d[u] π[u] null color[u] = BLACK //initialize vertex colour[s] RED d[s] Q.enqueue(s) while Q u Q.dequeue() for each v Adj[u] //explore edge (u,v) if color[v] = BLACK colour[v] RED d[v] d[u] + 1 π[v] u colour[u] GRAY Q.enqueue(v) Ø Q is a FIFO queue. Ø Each vertex assigned finite d value at most once. Ø Q contains vertices with d values {i,, i, i+1,, i+1} Ø d values assigned are monotonically increasing over time.
66 Summary of Topics 1. Maps & Hash Tables 2. Binary Search & Loop Invariants 3. Binary Search Trees 4. Sorting 5. Graphs
Suggested Study Strategy
 Final Exam Thursday, 7 August 2014,19:00 22:00 Closed Book Will cover whole course, with emphasis on material after midterm (hash tables, binary search trees, sorting, graphs) Suggested Study Strategy
Final Exam Thursday, 7 August 2014,19:00 22:00 Closed Book Will cover whole course, with emphasis on material after midterm (hash tables, binary search trees, sorting, graphs) Suggested Study Strategy
Final Exam. CSE 2011 Prof. J. Elder Last Updated: :41 PM
 Final Exam Ø Tue, 17 Apr 2012 19:00 22:00 LAS B Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps, hashing, binary search trees, sorting,
Final Exam Ø Tue, 17 Apr 2012 19:00 22:00 LAS B Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps, hashing, binary search trees, sorting,
Search Trees. Chapter 11
 Search Trees Chapter 6 4 8 9 Outline Binar Search Trees AVL Trees Spla Trees Outline Binar Search Trees AVL Trees Spla Trees Binar Search Trees A binar search tree is a proper binar tree storing ke-value
Search Trees Chapter 6 4 8 9 Outline Binar Search Trees AVL Trees Spla Trees Outline Binar Search Trees AVL Trees Spla Trees Binar Search Trees A binar search tree is a proper binar tree storing ke-value
Representations of Graphs
 ELEMENTARY GRAPH ALGORITHMS -- CS-5321 Presentation -- I am Nishit Kapadia Representations of Graphs There are two standard ways: A collection of adjacency lists - they provide a compact way to represent
ELEMENTARY GRAPH ALGORITHMS -- CS-5321 Presentation -- I am Nishit Kapadia Representations of Graphs There are two standard ways: A collection of adjacency lists - they provide a compact way to represent
Introduction to Algorithms. Lecture 11
 Introduction to Algorithms Lecture 11 Last Time Optimization Problems Greedy Algorithms Graph Representation & Algorithms Minimum Spanning Tree Prim s Algorithm Kruskal s Algorithm 2 Today s Topics Shortest
Introduction to Algorithms Lecture 11 Last Time Optimization Problems Greedy Algorithms Graph Representation & Algorithms Minimum Spanning Tree Prim s Algorithm Kruskal s Algorithm 2 Today s Topics Shortest
Elementary Graph Algorithms
 Elementary Graph Algorithms Graphs Graph G = (V, E)» V = set of vertices» E = set of edges (V V) Types of graphs» Undirected: edge (u, v) = (v, u); for all v, (v, v) E (No self loops.)» Directed: (u, v)
Elementary Graph Algorithms Graphs Graph G = (V, E)» V = set of vertices» E = set of edges (V V) Types of graphs» Undirected: edge (u, v) = (v, u); for all v, (v, v) E (No self loops.)» Directed: (u, v)
Jana Kosecka. Red-Black Trees Graph Algorithms. Many slides here are based on E. Demaine, D. Luebke slides
 Jana Kosecka Red-Black Trees Graph Algorithms Many slides here are based on E. Demaine, D. Luebke slides Binary Search Trees (BSTs) are an important data structure for dynamic sets In addition to satellite
Jana Kosecka Red-Black Trees Graph Algorithms Many slides here are based on E. Demaine, D. Luebke slides Binary Search Trees (BSTs) are an important data structure for dynamic sets In addition to satellite
CS 251, LE 2 Fall MIDTERM 2 Tuesday, November 1, 2016 Version 00 - KEY
 CS 251, LE 2 Fall 2016 MIDTERM 2 Tuesday, November 1, 2016 Version 00 - KEY W1.) (i) Show one possible valid 2-3 tree containing the nine elements: 1 3 4 5 6 8 9 10 12. (ii) Draw the final binary search
CS 251, LE 2 Fall 2016 MIDTERM 2 Tuesday, November 1, 2016 Version 00 - KEY W1.) (i) Show one possible valid 2-3 tree containing the nine elements: 1 3 4 5 6 8 9 10 12. (ii) Draw the final binary search
DFS & STRONGLY CONNECTED COMPONENTS
 DFS & STRONGLY CONNECTED COMPONENTS CS 4407 Search Tree Breadth-First Search (BFS) Depth-First Search (DFS) Depth-First Search (DFS) u d[u]: when u is discovered f[u]: when searching adj of u is finished
DFS & STRONGLY CONNECTED COMPONENTS CS 4407 Search Tree Breadth-First Search (BFS) Depth-First Search (DFS) Depth-First Search (DFS) u d[u]: when u is discovered f[u]: when searching adj of u is finished
Graph Representation
 Graph Representation Adjacency list representation of G = (V, E) An array of V lists, one for each vertex in V Each list Adj[u] contains all the vertices v such that there is an edge between u and v Adj[u]
Graph Representation Adjacency list representation of G = (V, E) An array of V lists, one for each vertex in V Each list Adj[u] contains all the vertices v such that there is an edge between u and v Adj[u]
Course Review for Finals. Cpt S 223 Fall 2008
 Course Review for Finals Cpt S 223 Fall 2008 1 Course Overview Introduction to advanced data structures Algorithmic asymptotic analysis Programming data structures Program design based on performance i.e.,
Course Review for Finals Cpt S 223 Fall 2008 1 Course Overview Introduction to advanced data structures Algorithmic asymptotic analysis Programming data structures Program design based on performance i.e.,
Graphs. Graph G = (V, E) Types of graphs E = O( V 2 ) V = set of vertices E = set of edges (V V)
 Graph Algorithms Graphs Graph G = (V, E) V = set of vertices E = set of edges (V V) Types of graphs Undirected: edge (u, v) = (v, u); for all v, (v, v) E (No self loops.) Directed: (u, v) is edge from
Graph Algorithms Graphs Graph G = (V, E) V = set of vertices E = set of edges (V V) Types of graphs Undirected: edge (u, v) = (v, u); for all v, (v, v) E (No self loops.) Directed: (u, v) is edge from
COT 6405 Introduction to Theory of Algorithms
 COT 6405 Introduction to Theory of Algorithms Topic 14. Graph Algorithms 11/7/2016 1 Elementary Graph Algorithms How to represent a graph? Adjacency lists Adjacency matrix How to search a graph? Breadth-first
COT 6405 Introduction to Theory of Algorithms Topic 14. Graph Algorithms 11/7/2016 1 Elementary Graph Algorithms How to represent a graph? Adjacency lists Adjacency matrix How to search a graph? Breadth-first
Chapter 22. Elementary Graph Algorithms
 Graph Algorithms - Spring 2011 Set 7. Lecturer: Huilan Chang Reference: (1) Cormen, Leiserson, Rivest, and Stein, Introduction to Algorithms, 2nd Edition, The MIT Press. (2) Lecture notes from C. Y. Chen
Graph Algorithms - Spring 2011 Set 7. Lecturer: Huilan Chang Reference: (1) Cormen, Leiserson, Rivest, and Stein, Introduction to Algorithms, 2nd Edition, The MIT Press. (2) Lecture notes from C. Y. Chen
Design and Analysis of Algorithms
 Design and Analysis of Algorithms CSE 5311 Lecture 18 Graph Algorithm Junzhou Huang, Ph.D. Department of Computer Science and Engineering CSE5311 Design and Analysis of Algorithms 1 Graphs Graph G = (V,
Design and Analysis of Algorithms CSE 5311 Lecture 18 Graph Algorithm Junzhou Huang, Ph.D. Department of Computer Science and Engineering CSE5311 Design and Analysis of Algorithms 1 Graphs Graph G = (V,
Elementary Graph Algorithms. Ref: Chapter 22 of the text by Cormen et al. Representing a graph:
 Elementary Graph Algorithms Ref: Chapter 22 of the text by Cormen et al. Representing a graph: Graph G(V, E): V set of nodes (vertices); E set of edges. Notation: n = V and m = E. (Vertices are numbered
Elementary Graph Algorithms Ref: Chapter 22 of the text by Cormen et al. Representing a graph: Graph G(V, E): V set of nodes (vertices); E set of edges. Notation: n = V and m = E. (Vertices are numbered
CSI 604 Elementary Graph Algorithms
 CSI 604 Elementary Graph Algorithms Ref: Chapter 22 of the text by Cormen et al. (Second edition) 1 / 25 Graphs: Basic Definitions Undirected Graph G(V, E): V is set of nodes (or vertices) and E is the
CSI 604 Elementary Graph Algorithms Ref: Chapter 22 of the text by Cormen et al. (Second edition) 1 / 25 Graphs: Basic Definitions Undirected Graph G(V, E): V is set of nodes (or vertices) and E is the
Trees and Graphs Shabsi Walfish NYU - Fundamental Algorithms Summer 2006
 Trees and Graphs Basic Definitions Tree: Any connected, acyclic graph G = (V,E) E = V -1 n-ary Tree: Tree s/t all vertices of degree n+1 A root has degree n Binary Search Tree: A binary tree such that
Trees and Graphs Basic Definitions Tree: Any connected, acyclic graph G = (V,E) E = V -1 n-ary Tree: Tree s/t all vertices of degree n+1 A root has degree n Binary Search Tree: A binary tree such that
D. Θ nlogn ( ) D. Ο. ). Which of the following is not necessarily true? . Which of the following cannot be shown as an improvement? D.
 CSE 0 Name Test Fall 00 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to convert an array, with priorities stored at subscripts through n,
CSE 0 Name Test Fall 00 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to convert an array, with priorities stored at subscripts through n,
Search Trees - 2. Venkatanatha Sarma Y. Lecture delivered by: Assistant Professor MSRSAS-Bangalore. M.S Ramaiah School of Advanced Studies - Bangalore
 Search Trees - 2 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Search Trees - 2 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Minimum Spanning Trees Ch 23 Traversing graphs
 Next: Graph Algorithms Graphs Ch 22 Graph representations adjacency list adjacency matrix Minimum Spanning Trees Ch 23 Traversing graphs Breadth-First Search Depth-First Search 11/30/17 CSE 3101 1 Graphs
Next: Graph Algorithms Graphs Ch 22 Graph representations adjacency list adjacency matrix Minimum Spanning Trees Ch 23 Traversing graphs Breadth-First Search Depth-First Search 11/30/17 CSE 3101 1 Graphs
COMP 251 Winter 2017 Online quizzes with answers
 COMP 251 Winter 2017 Online quizzes with answers Open Addressing (2) Which of the following assertions are true about open address tables? A. You cannot store more records than the total number of slots
COMP 251 Winter 2017 Online quizzes with answers Open Addressing (2) Which of the following assertions are true about open address tables? A. You cannot store more records than the total number of slots
Solutions to Exam Data structures (X and NV)
 Solutions to Exam Data structures X and NV 2005102. 1. a Insert the keys 9, 6, 2,, 97, 1 into a binary search tree BST. Draw the final tree. See Figure 1. b Add NIL nodes to the tree of 1a and color it
Solutions to Exam Data structures X and NV 2005102. 1. a Insert the keys 9, 6, 2,, 97, 1 into a binary search tree BST. Draw the final tree. See Figure 1. b Add NIL nodes to the tree of 1a and color it
Search Trees - 1 Venkatanatha Sarma Y
 Search Trees - 1 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Search Trees - 1 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Comparison Sorts. Chapter 9.4, 12.1, 12.2
 Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Graph Algorithms: Chapters Part 1: Introductory graph concepts
 UMass Lowell Computer Science 91.503 Algorithms Dr. Haim Levkowitz Fall, 2007 Graph Algorithms: Chapters 22-25 Part 1: Introductory graph concepts 1 91.404 Graph Review Elementary Graph Algorithms Minimum
UMass Lowell Computer Science 91.503 Algorithms Dr. Haim Levkowitz Fall, 2007 Graph Algorithms: Chapters 22-25 Part 1: Introductory graph concepts 1 91.404 Graph Review Elementary Graph Algorithms Minimum
Graph representation
 Graph Algorithms 1 Graph representation Given graph G = (V, E). May be either directed or undirected. Two common ways to represent for algorithms: 1. Adjacency lists. 2. Adjacency matrix. When expressing
Graph Algorithms 1 Graph representation Given graph G = (V, E). May be either directed or undirected. Two common ways to represent for algorithms: 1. Adjacency lists. 2. Adjacency matrix. When expressing
Outlines: Graphs Part-2
 Elementary Graph Algorithms PART-2 1 Outlines: Graphs Part-2 Graph Search Methods Breadth-First Search (BFS): BFS Algorithm BFS Example BFS Time Complexity Output of BFS: Shortest Path Breath-First Tree
Elementary Graph Algorithms PART-2 1 Outlines: Graphs Part-2 Graph Search Methods Breadth-First Search (BFS): BFS Algorithm BFS Example BFS Time Complexity Output of BFS: Shortest Path Breath-First Tree
Course Review. Cpt S 223 Fall 2009
 Course Review Cpt S 223 Fall 2009 1 Final Exam When: Tuesday (12/15) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
Course Review Cpt S 223 Fall 2009 1 Final Exam When: Tuesday (12/15) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
CSci 231 Final Review
 CSci 231 Final Review Here is a list of topics for the final. Generally you are responsible for anything discussed in class (except topics that appear italicized), and anything appearing on the homeworks.
CSci 231 Final Review Here is a list of topics for the final. Generally you are responsible for anything discussed in class (except topics that appear italicized), and anything appearing on the homeworks.
( ) 1 B. 1. Suppose f x
 CSE Name Test Spring Last Digits of Student ID Multiple Choice. Write your answer to the LEFT of each problem. points each is a monotonically increasing function. Which of the following approximates the
CSE Name Test Spring Last Digits of Student ID Multiple Choice. Write your answer to the LEFT of each problem. points each is a monotonically increasing function. Which of the following approximates the
Tutorial. Question There are no forward edges. 4. For each back edge u, v, we have 0 d[v] d[u].
![Tutorial. Question There are no forward edges. 4. For each back edge u, v, we have 0 d[v] d[u]. Tutorial. Question There are no forward edges. 4. For each back edge u, v, we have 0 d[v] d[u].](/thumbs/88/114871846.jpg) Tutorial Question 1 A depth-first forest classifies the edges of a graph into tree, back, forward, and cross edges. A breadth-first tree can also be used to classify the edges reachable from the source
Tutorial Question 1 A depth-first forest classifies the edges of a graph into tree, back, forward, and cross edges. A breadth-first tree can also be used to classify the edges reachable from the source
Lecture 10. Elementary Graph Algorithm Minimum Spanning Trees
 Lecture 10. Elementary Graph Algorithm Minimum Spanning Trees T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo
Lecture 10. Elementary Graph Algorithm Minimum Spanning Trees T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo
Cpt S 223 Fall Cpt S 223. School of EECS, WSU
 Course Review Cpt S 223 Fall 2012 1 Final Exam When: Monday (December 10) 8 10 AM Where: in class (Sloan 150) Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes
Course Review Cpt S 223 Fall 2012 1 Final Exam When: Monday (December 10) 8 10 AM Where: in class (Sloan 150) Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes
Chapter 2: Basic Data Structures
 Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
) $ f ( n) " %( g( n)
 CSE 0 Name Test Spring 008 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to compute the sum of the n elements of an integer array is: # A.
CSE 0 Name Test Spring 008 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to compute the sum of the n elements of an integer array is: # A.
AP Computer Science 4325
 4325 Instructional Unit Algorithm Design Techniques -divide-and-conquer The students will be -Decide whether an algorithm -classroom discussion -backtracking able to classify uses divide-and-conquer, -worksheets
4325 Instructional Unit Algorithm Design Techniques -divide-and-conquer The students will be -Decide whether an algorithm -classroom discussion -backtracking able to classify uses divide-and-conquer, -worksheets
Direct Addressing Hash table: Collision resolution how handle collisions Hash Functions:
 Direct Addressing - key is index into array => O(1) lookup Hash table: -hash function maps key to index in table -if universe of keys > # table entries then hash functions collision are guaranteed => need
Direct Addressing - key is index into array => O(1) lookup Hash table: -hash function maps key to index in table -if universe of keys > # table entries then hash functions collision are guaranteed => need
Graph: representation and traversal
 Graph: representation and traversal CISC4080, Computer Algorithms CIS, Fordham Univ. Instructor: X. Zhang! Acknowledgement The set of slides have use materials from the following resources Slides for textbook
Graph: representation and traversal CISC4080, Computer Algorithms CIS, Fordham Univ. Instructor: X. Zhang! Acknowledgement The set of slides have use materials from the following resources Slides for textbook
& ( D. " mnp ' ( ) n 3. n 2. ( ) C. " n
 CSE Name Test Summer Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n " n matrices is: A. " n C. "% n B. " max( m,n, p). The
CSE Name Test Summer Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n " n matrices is: A. " n C. "% n B. " max( m,n, p). The
Course Review. Cpt S 223 Fall 2010
 Course Review Cpt S 223 Fall 2010 1 Final Exam When: Thursday (12/16) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
Course Review Cpt S 223 Fall 2010 1 Final Exam When: Thursday (12/16) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
n 2 C. Θ n ( ) Ο f ( n) B. n 2 Ω( n logn)
 CSE 0 Name Test Fall 0 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to find the maximum of the n elements of an integer array is in: A.
CSE 0 Name Test Fall 0 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to find the maximum of the n elements of an integer array is in: A.
CS251-SE1. Midterm 2. Tuesday 11/1 8:00pm 9:00pm. There are 16 multiple-choice questions and 6 essay questions.
 CS251-SE1 Midterm 2 Tuesday 11/1 8:00pm 9:00pm There are 16 multiple-choice questions and 6 essay questions. Answer the multiple choice questions on your bubble sheet. Answer the essay questions in the
CS251-SE1 Midterm 2 Tuesday 11/1 8:00pm 9:00pm There are 16 multiple-choice questions and 6 essay questions. Answer the multiple choice questions on your bubble sheet. Answer the essay questions in the
Basic Graph Algorithms
 Basic Graph Algorithms 1 Representations of Graphs There are two standard ways to represent a graph G(V, E) where V is the set of vertices and E is the set of edges. adjacency list representation adjacency
Basic Graph Algorithms 1 Representations of Graphs There are two standard ways to represent a graph G(V, E) where V is the set of vertices and E is the set of edges. adjacency list representation adjacency
Taking Stock. IE170: Algorithms in Systems Engineering: Lecture 16. Graph Search Algorithms. Recall BFS
 Taking Stock IE170: Algorithms in Systems Engineering: Lecture 16 Jeff Linderoth Department of Industrial and Systems Engineering Lehigh University February 28, 2007 Last Time The Wonderful World of This
Taking Stock IE170: Algorithms in Systems Engineering: Lecture 16 Jeff Linderoth Department of Industrial and Systems Engineering Lehigh University February 28, 2007 Last Time The Wonderful World of This
Splay Trees. (Splay Trees) Data Structures and Programming Spring / 27
 Splay Trees (Splay Trees) Data Structures and Programming Spring 2017 1 / 27 Basic Idea Invented by Sleator and Tarjan (1985) Blind rebalancing no height info kept! Worst-case time per operation is O(n)
Splay Trees (Splay Trees) Data Structures and Programming Spring 2017 1 / 27 Basic Idea Invented by Sleator and Tarjan (1985) Blind rebalancing no height info kept! Worst-case time per operation is O(n)
( ) ( ) C. " 1 n. ( ) $ f n. ( ) B. " log( n! ) ( ) and that you already know ( ) ( ) " % g( n) ( ) " #&
 CSE 0 Name Test Summer 008 Last 4 Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time for the following code is in which set? for (i=0; i
CSE 0 Name Test Summer 008 Last 4 Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time for the following code is in which set? for (i=0; i
Computer Science & Engineering 423/823 Design and Analysis of Algorithms
 s of s Computer Science & Engineering 423/823 Design and Analysis of Lecture 03 (Chapter 22) Stephen Scott (Adapted from Vinodchandran N. Variyam) 1 / 29 s of s s are abstract data types that are applicable
s of s Computer Science & Engineering 423/823 Design and Analysis of Lecture 03 (Chapter 22) Stephen Scott (Adapted from Vinodchandran N. Variyam) 1 / 29 s of s s are abstract data types that are applicable
n 2 ( ) ( ) + n is in Θ n logn
 CSE Test Spring Name Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply an m n matrix and a n p matrix is in: A. Θ( n) B. Θ( max(
CSE Test Spring Name Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply an m n matrix and a n p matrix is in: A. Θ( n) B. Θ( max(
Graph Algorithms. Definition
 Graph Algorithms Many problems in CS can be modeled as graph problems. Algorithms for solving graph problems are fundamental to the field of algorithm design. Definition A graph G = (V, E) consists of
Graph Algorithms Many problems in CS can be modeled as graph problems. Algorithms for solving graph problems are fundamental to the field of algorithm design. Definition A graph G = (V, E) consists of
CS301 - Data Structures Glossary By
 CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
CS Elementary Graph Algorithms
 CS43-09 Elementary Graph Algorithms Outline Representation of Graphs Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 1:30pm - 2:30pm or by appointments lifei@cs.gmu.edu with subject: CS43
CS43-09 Elementary Graph Algorithms Outline Representation of Graphs Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 1:30pm - 2:30pm or by appointments lifei@cs.gmu.edu with subject: CS43
CS Elementary Graph Algorithms
 CS483-09 Elementary Graph Algorithms Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 1:30pm - 2:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/ lifei/teaching/cs483_fall07/
CS483-09 Elementary Graph Algorithms Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 1:30pm - 2:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/ lifei/teaching/cs483_fall07/
Graph implementations :
 Graphs Graph implementations : The two standard ways of representing a graph G = (V, E) are adjacency-matrices and collections of adjacencylists. The adjacency-lists are ideal for sparse trees those where
Graphs Graph implementations : The two standard ways of representing a graph G = (V, E) are adjacency-matrices and collections of adjacencylists. The adjacency-lists are ideal for sparse trees those where
logn D. Θ C. Θ n 2 ( ) ( ) f n B. nlogn Ο n2 n 2 D. Ο & % ( C. Θ # ( D. Θ n ( ) Ω f ( n)
 CSE 0 Test Your name as it appears on your UTA ID Card Fall 0 Multiple Choice:. Write the letter of your answer on the line ) to the LEFT of each problem.. CIRCLED ANSWERS DO NOT COUNT.. points each. The
CSE 0 Test Your name as it appears on your UTA ID Card Fall 0 Multiple Choice:. Write the letter of your answer on the line ) to the LEFT of each problem.. CIRCLED ANSWERS DO NOT COUNT.. points each. The
Outline. 1 Introduction. 2 Algorithm. 3 Example. 4 Analysis. 5 References. Idea
 Outline Computer Science 331 Graph Search: Breadth-First Search Mike Jacobson Department of Computer Science University of Calgary Lecture #31 1 2 3 Example 4 5 References Mike Jacobson (University of
Outline Computer Science 331 Graph Search: Breadth-First Search Mike Jacobson Department of Computer Science University of Calgary Lecture #31 1 2 3 Example 4 5 References Mike Jacobson (University of
Algorithm Design and Analysis
 Algorithm Design and Analysis LECTURE 7 Greedy Graph Algorithms Topological sort Shortest paths Adam Smith The (Algorithm) Design Process 1. Work out the answer for some examples. Look for a general principle
Algorithm Design and Analysis LECTURE 7 Greedy Graph Algorithms Topological sort Shortest paths Adam Smith The (Algorithm) Design Process 1. Work out the answer for some examples. Look for a general principle
Algorithms. AVL Tree
 Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
9. The expected time for insertion sort for n keys is in which set? (All n! input permutations are equally likely.)
 CSE 0 Name Test Spring 006 Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose f ( x) is a monotonically increasing function. Which of the
CSE 0 Name Test Spring 006 Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose f ( x) is a monotonically increasing function. Which of the
Course Review for. Cpt S 223 Fall Cpt S 223. School of EECS, WSU
 Course Review for Midterm Exam 1 Cpt S 223 Fall 2011 1 Midterm Exam 1 When: Friday (10/14) 1:10-2pm Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & in-class
Course Review for Midterm Exam 1 Cpt S 223 Fall 2011 1 Midterm Exam 1 When: Friday (10/14) 1:10-2pm Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & in-class
Topics on the Midterm
 Midterm Review Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash
Midterm Review Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash
(2,4) Trees. 2/22/2006 (2,4) Trees 1
 (2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
(2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
CSE Data Structures and Introduction to Algorithms... In Java! Instructor: Fei Wang. Mid-Term Exam. CSE2100 DS & Algorithms 1
 CSE 2100 Data Structures and Introduction to Algorithms...! In Java!! Instructor: Fei Wang! Mid-Term Exam CSE2100 DS & Algorithms 1 1. True or False (20%=2%x10)! (1) O(n) is O(n^2) (2) The height h of
CSE 2100 Data Structures and Introduction to Algorithms...! In Java!! Instructor: Fei Wang! Mid-Term Exam CSE2100 DS & Algorithms 1 1. True or False (20%=2%x10)! (1) O(n) is O(n^2) (2) The height h of
Unit 2: Algorithmic Graph Theory
 Unit 2: Algorithmic Graph Theory Course contents: Introduction to graph theory Basic graph algorithms Reading Chapter 3 Reference: Cormen, Leiserson, and Rivest, Introduction to Algorithms, 2 nd Ed., McGraw
Unit 2: Algorithmic Graph Theory Course contents: Introduction to graph theory Basic graph algorithms Reading Chapter 3 Reference: Cormen, Leiserson, and Rivest, Introduction to Algorithms, 2 nd Ed., McGraw
A6-R3: DATA STRUCTURE THROUGH C LANGUAGE
 A6-R3: DATA STRUCTURE THROUGH C LANGUAGE NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE is to be answered in the TEAR-OFF
A6-R3: DATA STRUCTURE THROUGH C LANGUAGE NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE is to be answered in the TEAR-OFF
( ) + n. ( ) = n "1) + n. ( ) = T n 2. ( ) = 2T n 2. ( ) = T( n 2 ) +1
 CSE 0 Name Test Summer 00 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose you are sorting millions of keys that consist of three decimal
CSE 0 Name Test Summer 00 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose you are sorting millions of keys that consist of three decimal
Analysis of Algorithms
 Analysis of Algorithms Trees-I Prof. Muhammad Saeed Tree Representation.. Analysis Of Algorithms 2 .. Tree Representation Analysis Of Algorithms 3 Nomenclature Nodes (13) Size (13) Degree of a node Depth
Analysis of Algorithms Trees-I Prof. Muhammad Saeed Tree Representation.. Analysis Of Algorithms 2 .. Tree Representation Analysis Of Algorithms 3 Nomenclature Nodes (13) Size (13) Degree of a node Depth
( ). Which of ( ) ( ) " #& ( ) " # g( n) ( ) " # f ( n) Test 1
 CSE 0 Name Test Summer 006 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n x n matrices is: A. "( n) B. "( nlogn) # C.
CSE 0 Name Test Summer 006 Last Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n x n matrices is: A. "( n) B. "( nlogn) # C.
CS 341: Algorithms. Douglas R. Stinson. David R. Cheriton School of Computer Science University of Waterloo. February 26, 2019
 CS 341: Algorithms Douglas R. Stinson David R. Cheriton School of Computer Science University of Waterloo February 26, 2019 D.R. Stinson (SCS) CS 341 February 26, 2019 1 / 296 1 Course Information 2 Introduction
CS 341: Algorithms Douglas R. Stinson David R. Cheriton School of Computer Science University of Waterloo February 26, 2019 D.R. Stinson (SCS) CS 341 February 26, 2019 1 / 296 1 Course Information 2 Introduction
( ) D. Θ ( ) ( ) Ο f ( n) ( ) Ω. C. T n C. Θ. B. n logn Ο
 CSE 0 Name Test Fall 0 Multiple Choice. Write your answer to the LEFT of each problem. points each. The expected time for insertion sort for n keys is in which set? (All n! input permutations are equally
CSE 0 Name Test Fall 0 Multiple Choice. Write your answer to the LEFT of each problem. points each. The expected time for insertion sort for n keys is in which set? (All n! input permutations are equally
Outline. Computer Science 331. Definitions: Paths and Their Costs. Computation of Minimum Cost Paths
 Outline Computer Science 33 Computation of Minimum-Cost Paths Dijkstra s Mike Jacobson Department of Computer Science University of Calgary Lecture #34 Dijkstra s to Find Min-Cost Paths 3 Example 4 5 References
Outline Computer Science 33 Computation of Minimum-Cost Paths Dijkstra s Mike Jacobson Department of Computer Science University of Calgary Lecture #34 Dijkstra s to Find Min-Cost Paths 3 Example 4 5 References
n 2 ( ) ( ) Ο f ( n) ( ) Ω B. n logn Ο
 CSE 220 Name Test Fall 20 Last 4 Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. 4 points each. The time to compute the sum of the n elements of an integer array is in:
CSE 220 Name Test Fall 20 Last 4 Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. 4 points each. The time to compute the sum of the n elements of an integer array is in:
Week 5. 1 Analysing BFS. 2 Depth-first search. 3 Analysing DFS. 4 Dags and topological sorting. 5 Detecting cycles. CS 270 Algorithms.
 1 2 Week 5 3 4 5 General remarks We finish, by analysing it. Then we consider the second main graph- algorithm, depth-first (). And we consider one application of, of graphs. Reading from CLRS for week
1 2 Week 5 3 4 5 General remarks We finish, by analysing it. Then we consider the second main graph- algorithm, depth-first (). And we consider one application of, of graphs. Reading from CLRS for week
( ) n 3. n 2 ( ) D. Ο
 CSE 0 Name Test Summer 0 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n n matrices is: A. Θ( n) B. Θ( max( m,n, p) ) C.
CSE 0 Name Test Summer 0 Last Digits of Mav ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. The time to multiply two n n matrices is: A. Θ( n) B. Θ( max( m,n, p) ) C.
COSC 2007 Data Structures II Final Exam. Part 1: multiple choice (1 mark each, total 30 marks, circle the correct answer)
 COSC 2007 Data Structures II Final Exam Thursday, April 13 th, 2006 This is a closed book and closed notes exam. There are total 3 parts. Please answer the questions in the provided space and use back
COSC 2007 Data Structures II Final Exam Thursday, April 13 th, 2006 This is a closed book and closed notes exam. There are total 3 parts. Please answer the questions in the provided space and use back
Advanced Set Representation Methods
 Advanced Set Representation Methods AVL trees. 2-3(-4) Trees. Union-Find Set ADT DSA - lecture 4 - T.U.Cluj-Napoca - M. Joldos 1 Advanced Set Representation. AVL Trees Problem with BSTs: worst case operation
Advanced Set Representation Methods AVL trees. 2-3(-4) Trees. Union-Find Set ADT DSA - lecture 4 - T.U.Cluj-Napoca - M. Joldos 1 Advanced Set Representation. AVL Trees Problem with BSTs: worst case operation
Multiple Choice. Write your answer to the LEFT of each problem. 3 points each
 CSE 0-00 Test Spring 0 Name Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose f ( x) is a monotonically increasing function. Which of the
CSE 0-00 Test Spring 0 Name Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each. Suppose f ( x) is a monotonically increasing function. Which of the
Test 1 - Closed Book Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. 3 points each
 CSE 5311 Test 1 - Closed Book Summer 2009 Name Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. 3 points each 1. Which of the following statements is true?
CSE 5311 Test 1 - Closed Book Summer 2009 Name Last 4 Digits of Student ID # Multiple Choice. Write your answer to the LEFT of each problem. 3 points each 1. Which of the following statements is true?
Second Semester - Question Bank Department of Computer Science Advanced Data Structures and Algorithms...
 Second Semester - Question Bank Department of Computer Science Advanced Data Structures and Algorithms.... Q1) Let the keys are 28, 47, 20, 36, 43, 23, 25, 54 and table size is 11 then H(28)=28%11=6; H(47)=47%11=3;
Second Semester - Question Bank Department of Computer Science Advanced Data Structures and Algorithms.... Q1) Let the keys are 28, 47, 20, 36, 43, 23, 25, 54 and table size is 11 then H(28)=28%11=6; H(47)=47%11=3;
Graphs. Graphs. Representation of Graphs. CSE 680 Prof. Roger Crawfis. Two standard ways. Graph G = (V, E)» V = set of vertices
 Introduction to Algorithms Graph Algorithms CSE 680 Prof. Roger Crawfis Partially from io.uwinnipeg.ca/~ychen2 Graphs Graph G = (V, E)» V = set of vertices» E = set of edges (V V) V) Types of graphs» Undirected:
Introduction to Algorithms Graph Algorithms CSE 680 Prof. Roger Crawfis Partially from io.uwinnipeg.ca/~ychen2 Graphs Graph G = (V, E)» V = set of vertices» E = set of edges (V V) V) Types of graphs» Undirected:
AVL Trees Goodrich, Tamassia, Goldwasser AVL Trees 1
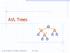 AVL Trees v 6 3 8 z 20 Goodrich, Tamassia, Goldwasser AVL Trees AVL Tree Definition Adelson-Velsky and Landis binary search tree balanced each internal node v the heights of the children of v can 2 3 7
AVL Trees v 6 3 8 z 20 Goodrich, Tamassia, Goldwasser AVL Trees AVL Tree Definition Adelson-Velsky and Landis binary search tree balanced each internal node v the heights of the children of v can 2 3 7
Trees. (Trees) Data Structures and Programming Spring / 28
 Trees (Trees) Data Structures and Programming Spring 2018 1 / 28 Trees A tree is a collection of nodes, which can be empty (recursive definition) If not empty, a tree consists of a distinguished node r
Trees (Trees) Data Structures and Programming Spring 2018 1 / 28 Trees A tree is a collection of nodes, which can be empty (recursive definition) If not empty, a tree consists of a distinguished node r
Prelim 2 Solution. CS 2110, November 19, 2015, 5:30 PM Total. Sorting Invariants Max Score Grader
 Prelim 2 CS 2110, November 19, 2015, 5:30 PM 1 2 3 4 5 6 Total Question True Short Complexity Searching Trees Graphs False Answer Sorting Invariants Max 20 15 13 14 17 21 100 Score Grader The exam is closed
Prelim 2 CS 2110, November 19, 2015, 5:30 PM 1 2 3 4 5 6 Total Question True Short Complexity Searching Trees Graphs False Answer Sorting Invariants Max 20 15 13 14 17 21 100 Score Grader The exam is closed
Dynamic Access Binary Search Trees
 Dynamic Access Binary Search Trees 1 * are self-adjusting binary search trees in which the shape of the tree is changed based upon the accesses performed upon the elements. When an element of a splay tree
Dynamic Access Binary Search Trees 1 * are self-adjusting binary search trees in which the shape of the tree is changed based upon the accesses performed upon the elements. When an element of a splay tree
Dynamic Access Binary Search Trees
 Dynamic Access Binary Search Trees 1 * are self-adjusting binary search trees in which the shape of the tree is changed based upon the accesses performed upon the elements. When an element of a splay tree
Dynamic Access Binary Search Trees 1 * are self-adjusting binary search trees in which the shape of the tree is changed based upon the accesses performed upon the elements. When an element of a splay tree
1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1
![1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1](/thumbs/85/92778785.jpg) Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 2. O(n) 2. [1 pt] What is the solution to the recurrence T(n) = T(n/2) + n, T(1)
Asymptotics, Recurrence and Basic Algorithms 1. [1 pt] What is the solution to the recurrence T(n) = 2T(n-1) + 1, T(1) = 1 2. O(n) 2. [1 pt] What is the solution to the recurrence T(n) = T(n/2) + n, T(1)
21# 33# 90# 91# 34# # 39# # # 31# 98# 0# 1# 2# 3# 4# 5# 6# 7# 8# 9# 10# #
 1. Prove that n log n n is Ω(n). York University EECS 11Z Winter 1 Problem Set 3 Instructor: James Elder Solutions log n n. Thus n log n n n n n log n n Ω(n).. Show that n is Ω (n log n). We seek a c >,
1. Prove that n log n n is Ω(n). York University EECS 11Z Winter 1 Problem Set 3 Instructor: James Elder Solutions log n n. Thus n log n n n n n log n n Ω(n).. Show that n is Ω (n log n). We seek a c >,
Red-Black Trees. Based on materials by Dennis Frey, Yun Peng, Jian Chen, and Daniel Hood
 Red-Black Trees Based on materials by Dennis Frey, Yun Peng, Jian Chen, and Daniel Hood Quick Review of Binary Search Trees n Given a node n... q All elements of n s left subtree are less than n.data q
Red-Black Trees Based on materials by Dennis Frey, Yun Peng, Jian Chen, and Daniel Hood Quick Review of Binary Search Trees n Given a node n... q All elements of n s left subtree are less than n.data q
Recitation 9. Prelim Review
 Recitation 9 Prelim Review 1 Heaps 2 Review: Binary heap min heap 1 2 99 4 3 PriorityQueue Maintains max or min of collection (no duplicates) Follows heap order invariant at every level Always balanced!
Recitation 9 Prelim Review 1 Heaps 2 Review: Binary heap min heap 1 2 99 4 3 PriorityQueue Maintains max or min of collection (no duplicates) Follows heap order invariant at every level Always balanced!
Lecture Summary CSC 263H. August 5, 2016
 Lecture Summary CSC 263H August 5, 2016 This document is a very brief overview of what we did in each lecture, it is by no means a replacement for attending lecture or doing the readings. 1. Week 1 2.
Lecture Summary CSC 263H August 5, 2016 This document is a very brief overview of what we did in each lecture, it is by no means a replacement for attending lecture or doing the readings. 1. Week 1 2.
Module 2: Classical Algorithm Design Techniques
 Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
Hash Tables. CS 311 Data Structures and Algorithms Lecture Slides. Wednesday, April 22, Glenn G. Chappell
 Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
AVL Tree Definition. An example of an AVL tree where the heights are shown next to the nodes. Adelson-Velsky and Landis
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 0 AVL Trees v 6 3 8 z 0 Goodrich, Tamassia, Goldwasser
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 0 AVL Trees v 6 3 8 z 0 Goodrich, Tamassia, Goldwasser
INSTITUTE OF AERONAUTICAL ENGINEERING
 INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Course Name Course Code Class Branch DATA STRUCTURES ACS002 B. Tech
INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Course Name Course Code Class Branch DATA STRUCTURES ACS002 B. Tech
Unit 5F: Layout Compaction
 Course contents Unit 5F: Layout Compaction Design rules Symbolic layout Constraint-graph compaction Readings: Chapter 6 Unit 5F 1 Design rules: restrictions on the mask patterns to increase the probability
Course contents Unit 5F: Layout Compaction Design rules Symbolic layout Constraint-graph compaction Readings: Chapter 6 Unit 5F 1 Design rules: restrictions on the mask patterns to increase the probability
Unit 3: Layout Compaction
 Unit 3: Layout Compaction Course contents Design rules Symbolic layout Constraint-graph compaction Readings: Chapter 6 Unit 3 1 Design rules: restrictions on the mask patterns to increase the probability
Unit 3: Layout Compaction Course contents Design rules Symbolic layout Constraint-graph compaction Readings: Chapter 6 Unit 3 1 Design rules: restrictions on the mask patterns to increase the probability
CS 270 Algorithms. Oliver Kullmann. Analysing BFS. Depth-first search. Analysing DFS. Dags and topological sorting.
 General remarks Week 5 2 We finish, by analysing it. Then we consider the second main graph- algorithm, depth-first (). And we consider one application of, of graphs. Reading from CLRS for week 5 Chapter
General remarks Week 5 2 We finish, by analysing it. Then we consider the second main graph- algorithm, depth-first (). And we consider one application of, of graphs. Reading from CLRS for week 5 Chapter
Graph Theory. Many problems are mapped to graphs. Problems. traffic VLSI circuits social network communication networks web pages relationship
 Graph Graph Usage I want to visit all the known famous places starting from Seoul ending in Seoul Knowledge: distances, costs Find the optimal(distance or cost) path Graph Theory Many problems are mapped
Graph Graph Usage I want to visit all the known famous places starting from Seoul ending in Seoul Knowledge: distances, costs Find the optimal(distance or cost) path Graph Theory Many problems are mapped
Selection, Bubble, Insertion, Merge, Heap, Quick Bucket, Radix
 Spring 2010 Review Topics Big O Notation Heaps Sorting Selection, Bubble, Insertion, Merge, Heap, Quick Bucket, Radix Hashtables Tree Balancing: AVL trees and DSW algorithm Graphs: Basic terminology and
Spring 2010 Review Topics Big O Notation Heaps Sorting Selection, Bubble, Insertion, Merge, Heap, Quick Bucket, Radix Hashtables Tree Balancing: AVL trees and DSW algorithm Graphs: Basic terminology and
Final Examination CSE 100 UCSD (Practice)
 Final Examination UCSD (Practice) RULES: 1. Don t start the exam until the instructor says to. 2. This is a closed-book, closed-notes, no-calculator exam. Don t refer to any materials other than the exam
Final Examination UCSD (Practice) RULES: 1. Don t start the exam until the instructor says to. 2. This is a closed-book, closed-notes, no-calculator exam. Don t refer to any materials other than the exam
