Topics on the Midterm
|
|
|
- Ashley Flowers
- 5 years ago
- Views:
Transcription
1 Midterm Review
2 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
3 Data Structures So Far Array List (Extendable) Array Node List Singly or Doubly Linked List Stack Array Singly Linked List Queue Array Singly or Doubly Linked List Priority Queue Unsorted doubly-linked list Sorted doubly-linked list Heap (array-based) Adaptable Priority Queue Tree Sorted doubly-linked list with locationaware entries Heap with location-aware entries Linked Structure Binary Tree Linked Structure Array
4 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
5 Data Structures & Object-Oriented Design Definitions Principles of Object-Oriented Design Hierarchical Design in Java Abstract Data Types & Interfaces Casting Generics Pseudo-Code
6 Software must be: Readable and understandable Software Engineering Allows correctness to be verified, and software to be easily updated. Correct and complete Works correctly for all expected inputs Robust Capable of handling unexpected inputs. Adaptible All programs evolve over time. Programs should be designed so that re-use, generalization and modification is easy. Portable Easily ported to new hardware or operating system platforms. Efficient Makes reasonable use of time and memory resources.
7 Seven Important Functions Seven functions that often appear in algorithm analysis: Constant 1 Logarithmic log n Linear n N-Log-N n log n Quadratic n 2 Cubic n 3 Exponential 2 n In a log-log chart, the slope of the line corresponds to the growth rate of the function.
8 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
9 Some Math to Review Summations Logarithms and Exponents Existential and universal operators Proof techniques Basic probability existential and universal operators $g"b Loves(b, g) "g$b Loves(b, g) properties of logarithms: log b (xy) = log b x + log b y log b (x/y) = log b x - log b y log b x a = alog b x log b a = log x a/log x b properties of exponentials: a (b+c) = a b a c a bc = (a b ) c a b /a c = a (b-c) b = a log a b b c = a c*log a b
10 Definition of Big Oh cg( n) f( n) f ( n) O( g( n)) gn ( ) 0 :, ( ) ( ) c, n0 n n0 f n cg n n
11 Arithmetic Progression The running time of prefixaverages1 is O( n) The sum of the first n integers is n(n + 1) / 2 There is a simple visual proof of this fact Thus, algorithm prefixaverages1 runs in O(n 2 ) time
12 Relatives of Big-Oh big-omega f(n) is Ω(g(n)) if there is a constant c > 0 and an integer constant n 0 1 such that f(n) c g(n) for n n 0 big-theta f(n) is Θ(g(n)) if there are constants c 1 > 0 and c 2 > 0 and an integer constant n 0 1 such that c 1 g(n) f(n) c 2 g(n) for n n 0
13 Time Complexity of an Algorithm The time complexity of an algorithm is the largest time required on any input of size n. (Worst case analysis.) O(n 2 ): For any input size n n 0, the algorithm takes no more than cn 2 time on every input. Ω(n 2 ): For any input size n n 0, the algorithm takes at least cn 2 time on at least one input. θ (n 2 ): Do both.
14 Time Complexity of a Problem The time complexity of a problem is the time complexity of the fastest algorithm that solves the problem. O(n 2 ): Provide an algorithm that solves the problem in no more than this time. Remember: for every input, i.e. worst case analysis! Ω(n 2 ): Prove that no algorithm can solve it faster. Remember: only need one input that takes at least this long! θ (n 2 ): Do both.
15 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
16 Arrays
17 Arrays Array: a sequence of indexed components with the following properties: array size is fixed at the time of array s construction int[] numbers = new int [10]; array elements are placed contiguously in memory address of any element can be calculated directly as its offset from the beginning of the array consequently, array components can be efficiently inspected or updated in O(1) time, using their indices randomnumber = numbers[5]; numbers[2] = 100;
18 Arrays in Java Since an array is an object, the name of the array is actually a reference (pointer) to the place in memory where the array is stored. reference to an object holds the address of the actual object Example [ arrays as objects] int[] A={12, 24, 37, 53, 67}; int[] B=A; B[3]=5; Example [ cloning an array] int[] A={12, 24, 37, 53, 67}; int[] B=A.clone(); B[3]=5; A B A B A B A B
19 Example Example [ 2D array in Java = array of arrays] int[][] nums = new int[5][4]; int[][] nums; nums = new int[5][]; for (int i=0; i<5; i++) { nums[i] = new int[4]; }
20 Array Lists
21 The Array List ADT ( 6.1) The Array List ADT extends the notion of array by storing a sequence of arbitrary objects An element can be accessed, inserted or removed by specifying its rank (number of elements preceding it) An exception is thrown if an incorrect rank is specified (e.g., a negative rank)
22 The Array List ADT public interface IndexList<E> { /** Returns the number of elements in this list */ public int size(); /** Returns whether the list is empty. */ public boolean isempty(); /** Inserts an element e to be at index I, shifting all elements after this. */ public void add(int I, E e) throws IndexOutOfBoundsException; /** Returns the element at index I, without removing it. */ public E get(int i) throws IndexOutOfBoundsException; /** Removes and returns the element at index I, shifting the elements after this. */ public E remove(int i) throws IndexOutOfBoundsException; /** Replaces the element at index I with e, returning the previous element at i. */ public E set(int I, E e) throws IndexOutOfBoundsException; }
23 Performance In the array based implementation The space used by the data structure is O(n) size, isempty, get and set run in O(1) time add and remove run in O(n) time In an add operation, when the array is full, instead of throwing an exception, we could replace the array with a larger one. In fact java.util.arraylist implements this ADT using extendable arrays that do just this.
24 Doubling Strategy Analysis We replace the array k = log 2 n times The total time T(n) of a series of n add(o) operations is proportional to n k = n + 2 k = 2n - 1 Thus T(n) is O(n) The amortized time of an add operation is O(1)! geometric series æ çrecall: è n å r i = i =0 n+1 1- r ö 1- r ø
25 Stacks Chapter 5.1
26 The Stack ADT stores arbitrary objects Insertions and deletions follow the last-in first-out scheme Think of a spring-loaded plate dispenser Main stack operations: push(object): inserts an element object pop(): removes and returns the last inserted element The Stack ADT Auxiliary stack operations: object top(): returns the last inserted element without removing it integer size(): returns the number of elements stored boolean isempty(): indicates whether no elements are stored
27 Array-based Stack A simple way of implementing the Stack ADT uses an array We add elements from left to right A variable keeps track of the index of the top element Algorithm size() return t + 1 Algorithm pop() if isempty() then throw EmptyStackException else t t - 1 return S[t + 1] S t
28 Queues Chapters
29 Array-Based Queue Use an array of size N in a circular fashion Two variables keep track of the front and rear f index of the front element r index immediately past the rear element Array location r is kept empty normal configuration Q f r wrapped-around configuration Q r f
30 Queue Operations We use the modulo operator (remainder of division) Algorithm size() return (N - f + r) mod N Algorithm isempty() return (f = r) Note: N - f + r = (r + N) - f Q Q f r r f
31 Linked Lists Chapters
32 Singly Linked List ( 3.2) A singly linked list is a concrete data structure consisting of a sequence of nodes Each node stores element link to the next node elem next node Æ A B C D
33 Running Time Adding at the head is O(1) Removing at the head is O(1) How about tail operations?
34 Doubly Linked List Doubly-linked lists allow more flexible list management (constant time operations at both ends). prev next Nodes store: element link to the previous node link to the next node Special trailer and header (sentinel) nodes elem node header nodes/positions trailer elements
35 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
36 Iterators An Iterator is an object that enables you to traverse through a collection and to remove elements from the collection selectively, if desired. You get an Iterator for a collection by calling its iterator method. Suppose collection is an instance of a Collection. Then to print out each element on a separate line: Iterator<E> it = collection.iterator(); while (it.hasnext()) System.out.println(it.next());
37 The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List Priority Queue Abstract Sequential List Array List Vector Stack Linked List
38 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
39 Linear Recursion Design Pattern Test for base cases Begin by testing for a set of base cases (there should be at least one). Every possible chain of recursive calls must eventually reach a base case, and the handling of each base case should not use recursion. Recurse once Perform a single recursive call. (This recursive step may involve a test that decides which of several possible recursive calls to make, but it should ultimately choose to make just one of these calls each time we perform this step.) Define each possible recursive call so that it makes progress towards a base case.
40 Binary Recursion Binary recursion occurs whenever there are two recursive calls for each non-base case. Example 1: The Fibonacci Sequence
41 Formal Definition of Rooted Tree A rooted tree may be empty. Otherwise, it consists of A root node r A set of subtrees whose roots are the children of r r B C D E F G H I J K subtree
42 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
43 Tree Terminology Root: node without parent (A) Internal node: node with at least one child (A, B, C, F) External node (a.k.a. leaf ): node without children (E, I, J, K, G, H, D) Ancestors of a node: parent, grandparent, grand-grandparent, etc. A Descendant of a node: child, grandchild, grand-grandchild, etc. Siblings: two nodes having the same parent B C D Depth of a node: number of ancestors (excluding self) E F G H Height of a tree: maximum depth of any node (3) Subtree: tree consisting of a node and its descendants I J K subtree
44 Position ADT The Position ADT models the notion of place within a data structure where a single object is stored It gives a unified view of diverse ways of storing data, such as a cell of an array a node of a linked list a node of a tree Just one method: object element(): returns the element stored at the position
45 Tree ADT We use positions to abstract nodes Generic methods: integer size() boolean isempty() Iterator iterator() Iterable positions() Accessor methods: position root() position parent(p) positioniterator children(p) Query methods: boolean isinternal(p) boolean isexternal(p) boolean isroot(p) Update method: object replace(p, o) Additional update methods may be defined by data structures implementing the Tree ADT
46 Preorder Traversal A traversal visits the nodes of a tree in a systematic manner In a preorder traversal, a node is visited before its descendants Algorithm preorder(v) visit(v) for each child w of v preorder (w) 1 Make Money Fast! 2 1. Motivations 2. Methods References Greed 1.2 Avidity Stock Fraud 2.2 Ponzi Scheme 2.3 Bank Robbery
47 Postorder Traversal In a postorder traversal, a node is visited after its descendants Algorithm postorder(v) for each child w of v postorder (w) visit(v) 9 cs16/ 3 homeworks/ 7 programs/ 8 todo.txt 1K h1c.doc 3K h1nc.doc 2K DDR.java 10K Stocks.java 25K Robot.java 20K
48 Properties of Proper Binary Trees Notation n number of nodes e number of external nodes i number of internal nodes h height Properties: e = i + 1 n = 2e - 1 h i h (n - 1)/2 e 2 h h log 2 e h log 2 (n + 1) - 1
49 BinaryTree ADT The BinaryTree ADT extends the Tree ADT, i.e., it inherits all the methods of the Tree ADT Additional methods: position left(p) position right(p) boolean hasleft(p) boolean hasright(p) Update methods may be defined by data structures implementing the BinaryTree ADT
50 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
51 Priority Queue ADT A priority queue stores a collection of entries Each entry is a pair (key, value) Main methods of the Priority Queue ADT insert(k, x) inserts an entry with key k and value x removemin() removes and returns the entry with smallest key Additional methods min() returns, but does not remove, an entry with smallest key size(), isempty() Applications: Process scheduling Standby flyers
52 Entry ADT An entry in a priority queue is simply a keyvalue pair Methods: key(): returns the key for this entry value(): returns the value for this entry As a Java interface: /** * Interface for a key-value * pair entry **/ public interface Entry { public Object key(); public Object value(); }
53 Comparator ADT A comparator encapsulates the action of comparing two objects according to a given total order relation A generic priority queue uses an auxiliary comparator The comparator is external to the keys being compared When the priority queue needs to compare two keys, it uses its comparator The primary method of the Comparator ADT: compare(a, b): Returns an integer i such that i < 0 if a < b i = 0 if a = b i > 0 if a > b an error occurs if a and b cannot be compared.
54 Sequence-based Priority Queue Implementation with an unsorted list Implementation with a sorted list Performance: insert takes O(1) time since we can insert the item at the beginning or end of the sequence removemin and min take O(n) time since we have to traverse the entire sequence to find the smallest key Performance: insert takes O(n) time since we have to find the right place to insert the item removemin and min take O(1) time, since the smallest key is at the beginning Is this tradeoff inevitable?
55 Heaps Goal: O(log n) insertion O(log n) removal Remember that O(log n) is almost as good as O(1)! e.g., n = 1,000,000,000 log n 30 There are min heaps and max heaps. We will assume min heaps.
56 Min Heaps A min heap is a binary tree storing keys at its nodes and satisfying the following properties: Heap-order: for every internal node v other than the root key(v) key(parent(v)) (Almost) complete binary tree: let h be the height of the heap for i = 0,, h - 1, there are 2 i nodes of depth i at depth h 1 the internal nodes are to the left of the external nodes Only the rightmost internal node may have a single child The last node of a heap is the rightmost node of depth h
57 Upheap After the insertion of a new key k, the heap-order property may be violated Algorithm upheap restores the heap-order property by swapping k along an upward path from the insertion node Upheap terminates when the key k reaches the root or a node whose parent has a key smaller than or equal to k Since a heap has height O(log n), upheap runs in O(log n) time
58 Downheap After replacing the root key with the key k of the last node, the heap-order property may be violated Algorithm downheap restores the heap-order property by swapping key k along a downward path from the root Note that there are, in general, many possible downward paths which one do we choose??? 7 5 w 6 9
59 Downheap We select the downward path through the minimum-key nodes. Downheap terminates when key k reaches a leaf or a node whose children have keys greater than or equal to k Since a heap has height O(log n), downheap runs in O(log n) time w 6 7 w 6 9 9
60 Array-based Heap Implementation We can represent a heap with n keys by means of an array of length n + 1 Links between nodes are not explicitly stored The cell at rank 0 is not used The root is stored at rank 1. For the node at rank i the left child is at rank 2i the right child is at rank 2i + 1 the parent is at rank floor(i/2) if 2i + 1 > n, the node has no right child if 2i > n, the node is a leaf
61 Bottom-up Heap Construction We can construct a heap storing n keys using a bottom-up construction with log n phases 2 i -1 2 i -1 In phase i, pairs of heaps with 2 i -1 keys are merged into heaps with 2 i+1-1 keys Run time for construction is O(n). 2 i+1-1
62 Adaptable Priority Queues 3 a 5 g 4 e
63 Additional Methods of the Adaptable Priority Queue ADT remove(e): Remove from P and return entry e. replacekey(e,k): Replace with k and return the old key; an error condition occurs if k is invalid (that is, k cannot be compared with other keys). replacevalue(e,x): Replace with x and return the old value.
64 Location-Aware Entries A locator-aware entry identifies and tracks the location of its (key, value) object within a data structure
65 List Implementation A location-aware list entry is an object storing key value position (or rank) of the item in the list In turn, the position (or array cell) stores the entry Back pointers (or ranks) are updated during swaps header nodes/positions trailer 2 c 4 a 5 d 8 b entries
66 Heap Implementation A location-aware heap entry is an object storing key value position of the entry in the underlying heap In turn, each heap position stores an entry Back pointers are updated during entry swaps 4 a 2 d 6 b 8 g 5 e 9 c
67 Performance Times better than those achievable without location-aware entries are highlighted in red: Method Unsorted List Sorted List Heap size, isempty O(1) O(1) O(1) insert O(1) O(n) O(log n) min O(n) O(1) O(1) removemin O(n) O(1) O(log n) remove O(1) O(1) O(log n) replacekey O(1) O(n) O(log n) replacevalue O(1) O(1) O(1)
68 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
69 Maps A map models a searchable collection of key-value entries The main operations of a map are for searching, inserting, and deleting items Multiple entries with the same key are not allowed Applications: address book student-record database
70 Performance of a List-Based Map Performance: put, get and remove take O(n) time since in the worst case (the item is not found) we traverse the entire sequence to look for an item with the given key The unsorted list implementation is effective only for small maps
71 Hash Tables A hash table is a data structure that can be used to make map operations faster. While worst-case is still O(n), average case is typically O(1).
72 Polynomial accumulation: Polynomial Hash Codes We partition the bits of the key into a sequence of components of fixed length (e.g., 8, 16 or 32 bits) a 0 a 1 a n-1 We evaluate the polynomial p(z) = a 0 + a 1 z + a 2 z a n-1 z n-1 at a fixed value z, ignoring overflows Especially suitable for strings Polynomial p(z) can be evaluated in O(n) time using Horner s rule: The following polynomials are successively computed, each from the previous one in O(1) time p 0 (z) = a n-1 We have p(z) = p n-1 (z) p i (z) = a n-i-1 + zp i-1 (z) (i = 1, 2,, n -1)
73 Division: h 2 (y) = y mod N Compression Functions The size N of the hash table is usually chosen to be a prime (on the assumption that the differences between hash keys y are less likely to be multiples of primes). Multiply, Add and Divide (MAD): h 2 (y) = [(ay + b) mod p] mod N, where p is a prime number greater than N a and b are integers chosen at random from the interval [0, p 1], with a > 0.
74 Collision Handling Collisions occur when different elements are mapped to the same cell Separate Chaining: Let each cell in the table point to a linked list of entries that map there Separate chaining is simple, but requires additional memory outside the table Ø Ø Ø
75 Open Addressing: Linear Probing Open addressing: the colliding item is placed in a different cell of the table Linear probing handles collisions by placing the colliding item in the next (circularly) available table cell Each table cell inspected is referred to as a probe Colliding items lump together, so that future collisions cause a longer sequence of probes Example: h(x) = x mod 13 Insert keys 18, 41, 22, 44, 59, 32, 31, 73, in this order
76 Open Addressing: Double Hashing Double hashing is an alternative open addressing method that uses a secondary hash function h (k) in addition to the primary hash function h(x). Suppose that the primary hashing i=h(k) leads to a collision. We then iteratively probe the locations (i + jh (k)) mod N for j = 0, 1,, N - 1 The secondary hash function h (k) cannot have zero values N is typically chosen to be prime. Common choice of secondary hash function h (k): h (k) = q - k mod q, where q < N q is a prime The possible values for h (k) are 1, 2,, q
77 The dictionary ADT models a searchable collection of keyelement entries The main operations of a dictionary are searching, inserting, and deleting items Multiple items with the same key are allowed Applications: word-definition pairs credit card authorizations Dictionary ADT Dictionary ADT methods: get(k): if the dictionary has at least one entry with key k, returns one of them, else, returns null getall(k): returns an iterable collection of all entries with key k put(k, v): inserts and returns the entry (k, v) remove(e): removes and returns the entry e. Throws an exception if the entry is not in the dictionary. entryset(): returns an iterable collection of the entries in the dictionary size(), isempty()
78 A List-Based Dictionary A log file or audit trail is a dictionary implemented by means of an unsorted sequence We store the items of the dictionary in a sequence (based on a doublylinked list or array), in arbitrary order Performance: insert takes O(1) time since we can insert the new item at the beginning or at the end of the sequence find and remove take O(n) time since in the worst case (the item is not found) we traverse the entire sequence to look for an item with the given key The log file is effective only for dictionaries of small size or for dictionaries on which insertions are the most common operations, while searches and removals are rarely performed (e.g., historical record of logins to a workstation)
79 Hash Table Implementation We can also create a hash-table dictionary implementation. If we use separate chaining to handle collisions, then each operation can be delegated to a list-based dictionary stored at each hash table cell.
80 Ordered Maps and Dictionaries If keys obey a total order relation, can represent a map or dictionary as an ordered search table stored in an array. Can then support a fast find(k) using binary search. at each step, the number of candidate items is halved terminates after a logarithmic number of steps Example: find(7) 0 l 0 l m h m h l m h l=m =h
81 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
82 Loop Invariants Binary search can be implemented as an iterative algorithm (it could also be done recursively). Loop Invariant: An assertion about the current state useful for designing, analyzing and proving the correctness of iterative algorithms.
83 Establishing Loop Invariant From the Pre-Conditions on the input instance we must establish the loop invariant.
84 Maintain Loop Invariant By Induction the computation will always be in a safe location. S(0) i, S( i) i, S( i) S( i + 1)
85 Ending The Algorithm Define Exit Condition Exit Termination: With sufficient progress, the exit condition will be met. 0 km Exit When we exit, we know exit condition is true loop invariant is true from these we must establish the post conditions. Exit
86 Topics on the Midterm Data Structures & Object-Oriented Design Run-Time Analysis Linear Data Structures The Java Collections Framework Recursion Trees Priority Queues & Heaps Maps, Hash Tables & Dictionaries Iterative Algorithms & Loop Invariants
Elementary Data Structures 2
 Elementary Data Structures Priority Queues, & Dictionaries Priority Queues Sell 00 IBM $ Sell 300 IBM $0 Buy 00 IBM $9 Buy 400 IBM $8 Priority Queue ADT A priority queue stores a collection of items An
Elementary Data Structures Priority Queues, & Dictionaries Priority Queues Sell 00 IBM $ Sell 300 IBM $0 Buy 00 IBM $9 Buy 400 IBM $8 Priority Queue ADT A priority queue stores a collection of items An
Elementary Data Structures. Stacks, Queues, & Lists Amortized analysis Trees
 Elementary Data Structures Stacks, Queues, & Lists Amortized analysis Trees The Stack ADT ( 2.1.1) The Stack ADT stores arbitrary objects Insertions and deletions follow the last-in first-out scheme Think
Elementary Data Structures Stacks, Queues, & Lists Amortized analysis Trees The Stack ADT ( 2.1.1) The Stack ADT stores arbitrary objects Insertions and deletions follow the last-in first-out scheme Think
Priority Queues & Heaps. Chapter 9
 Priority Queues & Heaps Chapter 9 The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List Priority
Priority Queues & Heaps Chapter 9 The Java Collections Framework (Ordered Data Types) Interface Abstract Class Class Iterable Collection Queue Abstract Collection List Abstract Queue Abstract List Priority
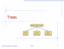
Trees. Make Money Fast! Bank Robbery. Stock Fraud. Ponzi Scheme Goodrich, Tamassia. Trees 1
 Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Trees 1 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parent-child
Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Trees 1 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parent-child
Maps, Hash Tables and Dictionaries. Chapter 10.1, 10.2, 10.3, 10.5
 Maps, Hash Tables and Dictionaries Chapter 10.1, 10.2, 10.3, 10.5 Outline Maps Hashing Dictionaries Ordered Maps & Dictionaries Outline Maps Hashing Dictionaries Ordered Maps & Dictionaries Maps A map
Maps, Hash Tables and Dictionaries Chapter 10.1, 10.2, 10.3, 10.5 Outline Maps Hashing Dictionaries Ordered Maps & Dictionaries Outline Maps Hashing Dictionaries Ordered Maps & Dictionaries Maps A map
Trees. 9/21/2007 8:11 AM Trees 1
 Trees 9/21/2007 8:11 AM Trees 1 Outline and Reading Tree ADT ( 6.1) Preorder and postorder traversals ( 6.2.3) BinaryTree ADT ( 6.3.1) Inorder traversal ( 6.3.4) Euler Tour traversal ( 6.3.4) Template
Trees 9/21/2007 8:11 AM Trees 1 Outline and Reading Tree ADT ( 6.1) Preorder and postorder traversals ( 6.2.3) BinaryTree ADT ( 6.3.1) Inorder traversal ( 6.3.4) Euler Tour traversal ( 6.3.4) Template
Priority Queues. Outline. COMP9024: Data Structures and Algorithms. Priority Queue ADT. Total Order Relations. Entry ADT
 COMP0: Data Structures and Algorithms Week Seven: Priority Queues Hui Wu Outline Priority Queues Heaps Adaptable Priority Queues Session, 0 http://www.cse.unsw.edu.au/~cs0 Priority Queue ADT Priority Queues
COMP0: Data Structures and Algorithms Week Seven: Priority Queues Hui Wu Outline Priority Queues Heaps Adaptable Priority Queues Session, 0 http://www.cse.unsw.edu.au/~cs0 Priority Queue ADT Priority Queues
Data Structures and Algorithms. Trees
 Data Structures and Algorithms Trees Tree Example Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 2 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A
Data Structures and Algorithms Trees Tree Example Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 2 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A
Data Structures. Trees, Binary trees & Binary Search Trees
 Data Structures Trees, Binary trees & Binary Search Trees Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parentchild relation Applications:
Data Structures Trees, Binary trees & Binary Search Trees Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parentchild relation Applications:
Trees. Make Money Fast! Bank Robbery. Stock Fraud. Ponzi Scheme. Trees Goodrich, Tamassia
 Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Trees 1 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parent-child
Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Trees 1 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parent-child
Priority Queue Sorting
 Priority Queue Sorting We can use a priority queue to sort a list of comparable elements 1. Insert the elements one by one with a series of insert operations 2. Remove the elements in sorted order with
Priority Queue Sorting We can use a priority queue to sort a list of comparable elements 1. Insert the elements one by one with a series of insert operations 2. Remove the elements in sorted order with
Outline. Definitions Traversing trees Binary trees
 Trees Chapter 8 Outline Definitions Traversing trees Binary trees Outline Definitions Traversing trees Binary trees Graph a b Node ~ city or computer Edge ~ road or data cable c Undirected or Directed
Trees Chapter 8 Outline Definitions Traversing trees Binary trees Outline Definitions Traversing trees Binary trees Graph a b Node ~ city or computer Edge ~ road or data cable c Undirected or Directed
Stores a collection of elements each with an associated key value
 CH9. PRIORITY QUEUES ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 201) PRIORITY QUEUES Stores a collection
CH9. PRIORITY QUEUES ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 201) PRIORITY QUEUES Stores a collection
Data Structures and Algorithms " Priority Queues!
 Data Structures and Algorithms " Priority Queues! Outline" Priority Queues! Heaps! Adaptable Priority Queues! Priority Queues" Priority Queue ADT" A priority queue stores a collection of entries! Each
Data Structures and Algorithms " Priority Queues! Outline" Priority Queues! Heaps! Adaptable Priority Queues! Priority Queues" Priority Queue ADT" A priority queue stores a collection of entries! Each
This lecture. Iterators ( 5.4) Maps. Maps. The Map ADT ( 8.1) Comparison to java.util.map
 This lecture Iterators Hash tables Formal coursework Iterators ( 5.4) An iterator abstracts the process of scanning through a collection of elements Methods of the ObjectIterator ADT: object object() boolean
This lecture Iterators Hash tables Formal coursework Iterators ( 5.4) An iterator abstracts the process of scanning through a collection of elements Methods of the ObjectIterator ADT: object object() boolean
Heaps Goodrich, Tamassia. Heaps 1
 Heaps Heaps 1 Recall Priority Queue ADT A priority queue stores a collection of entries Each entry is a pair (key, value) Main methods of the Priority Queue ADT insert(k, x) inserts an entry with key k
Heaps Heaps 1 Recall Priority Queue ADT A priority queue stores a collection of entries Each entry is a pair (key, value) Main methods of the Priority Queue ADT insert(k, x) inserts an entry with key k
Trees. Make Money Fast! Bank Robbery. Ponzi Scheme. Stock Fraud. 02/06/2006 Trees 1
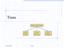 Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 02/06/2006 Trees 1 Outline and Reading Tree ADT ( 7.1.2) Preorder and postorder traversals ( 7.2.2-3) BinaryTree ADT ( 7.3.1) Inorder traversal
Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 02/06/2006 Trees 1 Outline and Reading Tree ADT ( 7.1.2) Preorder and postorder traversals ( 7.2.2-3) BinaryTree ADT ( 7.3.1) Inorder traversal
Trees. Make Money Fast! Bank Robbery. Ponzi Scheme. Stock Fraud Goodrich, Tamassia, Goldwasser Trees
 Part 4: Trees Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 2013 Goodrich, Tamassia, Goldwasser Trees 2 Example: Family Tree 2013 Goodrich, Tamassia, Goldwasser Trees 3 Example: Unix File
Part 4: Trees Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 2013 Goodrich, Tamassia, Goldwasser Trees 2 Example: Family Tree 2013 Goodrich, Tamassia, Goldwasser Trees 3 Example: Unix File
Trees. Trees. CSE 2011 Winter 2007
 Trees CSE 2011 Winter 2007 2/5/2007 10:00 PM 1 Trees Linear access time of linked lists is prohibitive Does there exist any simple data structure for which the running time of most operations (search,
Trees CSE 2011 Winter 2007 2/5/2007 10:00 PM 1 Trees Linear access time of linked lists is prohibitive Does there exist any simple data structure for which the running time of most operations (search,
Chapter 2: Basic Data Structures
 Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
Heaps 2. Recall Priority Queue ADT. Heaps 3/19/14
 Heaps 3// Presentation for use with the textbook Data Structures and Algorithms in Java, th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 0 Heaps Heaps Recall Priority Queue ADT
Heaps 3// Presentation for use with the textbook Data Structures and Algorithms in Java, th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 0 Heaps Heaps Recall Priority Queue ADT
Heaps. 2/13/2006 Heaps 1
 Heaps /13/00 Heaps 1 Outline and Reading What is a heap ( 8.3.1) Height of a heap ( 8.3.) Insertion ( 8.3.3) Removal ( 8.3.3) Heap-sort ( 8.3.) Arraylist-based implementation ( 8.3.) Bottom-up construction
Heaps /13/00 Heaps 1 Outline and Reading What is a heap ( 8.3.1) Height of a heap ( 8.3.) Insertion ( 8.3.3) Removal ( 8.3.3) Heap-sort ( 8.3.) Arraylist-based implementation ( 8.3.) Bottom-up construction
Trees. Make Money Fast! Bank Robbery. Ponzi Scheme. Stock Fraud. 1/18/2005 4:17 AM Trees 1
 Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 1/18/2005 4:17 AM Trees 1 Outline and Reading Tree ADT ( 2.3.1) Preorder and postorder traversals ( 2.3.2) BinaryTree ADT ( 2.3.3) Inorder traversal
Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery 1/18/2005 4:17 AM Trees 1 Outline and Reading Tree ADT ( 2.3.1) Preorder and postorder traversals ( 2.3.2) BinaryTree ADT ( 2.3.3) Inorder traversal
Trees 3/19/14. Mammal. Dog Pig Cat
 Presentation for use with the textbook ata Structures and lgorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 014 Trees Mammal og Pig at Trees 1 What is a Tree
Presentation for use with the textbook ata Structures and lgorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 014 Trees Mammal og Pig at Trees 1 What is a Tree
Trees and Binary Trees
 Trees and Binary Trees Become Rich Force Others to be Poor Rob Banks Stock Fraud The class notes are a compilation and edition from many sources. The instructor does not claim intellectual property or
Trees and Binary Trees Become Rich Force Others to be Poor Rob Banks Stock Fraud The class notes are a compilation and edition from many sources. The instructor does not claim intellectual property or
CH 8. HEAPS AND PRIORITY QUEUES
 CH 8. HEAPS AND PRIORITY QUEUES ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
CH 8. HEAPS AND PRIORITY QUEUES ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
CH. 8 PRIORITY QUEUES AND HEAPS
 CH. 8 PRIORITY QUEUES AND HEAPS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
CH. 8 PRIORITY QUEUES AND HEAPS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES
 HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES 2 5 6 9 7 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H., Wiley, 2014
HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES 2 5 6 9 7 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H., Wiley, 2014
Dictionaries-Hashing. Textbook: Dictionaries ( 8.1) Hash Tables ( 8.2)
 Dictionaries-Hashing Textbook: Dictionaries ( 8.1) Hash Tables ( 8.2) Dictionary The dictionary ADT models a searchable collection of key-element entries The main operations of a dictionary are searching,
Dictionaries-Hashing Textbook: Dictionaries ( 8.1) Hash Tables ( 8.2) Dictionary The dictionary ADT models a searchable collection of key-element entries The main operations of a dictionary are searching,
Final Exam. EECS 2011 Prof. J. Elder - 1 -
 Final Exam Ø Wed Apr 11 2pm 5pm Aviva Tennis Centre Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps and hash tables, binary search, loop
Final Exam Ø Wed Apr 11 2pm 5pm Aviva Tennis Centre Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps and hash tables, binary search, loop
OUTLINE. General Trees (Ch. 7.1) Binary Trees (Ch. 7.3) Tree Traversals (Ch. 7.2)
 CH 7 : TREE ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO 1 OUTLINE
CH 7 : TREE ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO 1 OUTLINE
Stock Fraud. Nancy Amato. Parasol Lab, Dept. CSE, Texas A&M University
 Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Chapter 7: Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with Data Structures
Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Chapter 7: Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with Data Structures
Heaps and Priority Queues
 Heaps and Priority Queues Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce Priority Queue ADT To discuss and illustrate Priority Queues for sorting
Heaps and Priority Queues Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce Priority Queue ADT To discuss and illustrate Priority Queues for sorting
Trees. Make Money Fast! Stock Fraud. Bank Robbery. Ponzi Scheme. Trees Goodrich, Tamassia
 Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Trees 1 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parent-child
Trees Make Money Fast! Stock Fraud Ponzi Scheme Bank Robbery Trees 1 What is a Tree In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes with a parent-child
Dictionaries. 2/17/2006 Dictionaries 1
 Dictionaries < 6 > 1 4 = 8 9 /17/006 Dictionaries 1 Outline and Reading Dictionary ADT ( 9.3) Log file ( 9.3.1) Binary search ( 9.3.3) Lookup table ( 9.3.3) Binary search tree ( 10.1) Search ( 10.1.1)
Dictionaries < 6 > 1 4 = 8 9 /17/006 Dictionaries 1 Outline and Reading Dictionary ADT ( 9.3) Log file ( 9.3.1) Binary search ( 9.3.3) Lookup table ( 9.3.3) Binary search tree ( 10.1) Search ( 10.1.1)
Data Structures Question Bank Multiple Choice
 Section 1. Fundamentals: Complexity, Algorthm Analysis 1. An algorithm solves A single problem or function Multiple problems or functions Has a single programming language implementation 2. A solution
Section 1. Fundamentals: Complexity, Algorthm Analysis 1. An algorithm solves A single problem or function Multiple problems or functions Has a single programming language implementation 2. A solution
CSED233: Data Structures (2017F) Lecture10:Hash Tables, Maps, and Skip Lists
 (2017F) Lecture10:Hash Tables, Maps, and Skip Lists Daijin Kim CSE, POSTECH dkim@postech.ac.kr Maps A map models a searchable collection of key-value entries The main operations of a map are for searching,
(2017F) Lecture10:Hash Tables, Maps, and Skip Lists Daijin Kim CSE, POSTECH dkim@postech.ac.kr Maps A map models a searchable collection of key-value entries The main operations of a map are for searching,
Trees. Data structures and Algorithms. Make Money Fast! Bank Robbery. Stock Fraud. Ponzi Scheme
 Make Money Fast! Trees Stock Fraud Ponzi Scheme Bank Robbery Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich,
Make Money Fast! Trees Stock Fraud Ponzi Scheme Bank Robbery Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich,
In a postorder traversal, a node is visited after its descendants Application: compute space used by files in a directory and its subdirectories 9 1
 What is a Tree Trees Stock Fraud Make Money Fast! Winning Lotto / Bank Robbery In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes ith a parent-child relation
What is a Tree Trees Stock Fraud Make Money Fast! Winning Lotto / Bank Robbery In computer science, a tree is an abstract model of a hierarchical structure A tree consists of nodes ith a parent-child relation
Describe how to implement deque ADT using two stacks as the only instance variables. What are the running times of the methods
 Describe how to implement deque ADT using two stacks as the only instance variables. What are the running times of the methods 1 2 Given : Stack A, Stack B 3 // based on requirement b will be reverse of
Describe how to implement deque ADT using two stacks as the only instance variables. What are the running times of the methods 1 2 Given : Stack A, Stack B 3 // based on requirement b will be reverse of
Unit 1 (9Hrs) Trees. Mahesh Sanghavi & Deepali Pawar Department of Computer Engineering, SNJB s KBJ College of Engineering, Chandwad, India
 Unit 1 (9Hrs) Trees Mahesh Sanghavi & Deepali Pawar Department of Computer Engineering, SNJB s KBJ College of Engineering, Chandwad, India The class notes are a compilation and edition from many sources.
Unit 1 (9Hrs) Trees Mahesh Sanghavi & Deepali Pawar Department of Computer Engineering, SNJB s KBJ College of Engineering, Chandwad, India The class notes are a compilation and edition from many sources.
Data Structures Lecture 12
 Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 12 Advance ADTs Maps and Hash Tables Maps A map models a searchable collection
Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 12 Advance ADTs Maps and Hash Tables Maps A map models a searchable collection
Dictionaries and Hash Tables
 Dictionaries and Hash Tables 0 1 2 3 025-612-0001 981-101-0002 4 451-229-0004 Dictionaries and Hash Tables 1 Dictionary ADT The dictionary ADT models a searchable collection of keyelement items The main
Dictionaries and Hash Tables 0 1 2 3 025-612-0001 981-101-0002 4 451-229-0004 Dictionaries and Hash Tables 1 Dictionary ADT The dictionary ADT models a searchable collection of keyelement items The main
Hash Tables Hash Tables Goodrich, Tamassia
 Hash Tables 0 1 2 3 4 025-612-0001 981-101-0002 451-229-0004 Hash Tables 1 Hash Functions and Hash Tables A hash function h maps keys of a given type to integers in a fixed interval [0, N 1] Example: h(x)
Hash Tables 0 1 2 3 4 025-612-0001 981-101-0002 451-229-0004 Hash Tables 1 Hash Functions and Hash Tables A hash function h maps keys of a given type to integers in a fixed interval [0, N 1] Example: h(x)
Priority Queues and Heaps. Heaps and Priority Queues 1
 Priority Queues and Heaps 2 5 6 9 7 Heaps and Priority Queues 1 Priority Queue ADT A priority queue stores a collection of items An item is a pair (key, element) Main methods of the Priority Queue ADT
Priority Queues and Heaps 2 5 6 9 7 Heaps and Priority Queues 1 Priority Queue ADT A priority queue stores a collection of items An item is a pair (key, element) Main methods of the Priority Queue ADT
Priority Queues and Heaps. More Data Structures. Priority Queue ADT ( 2.4.1) Total Order Relation. Sorting with a Priority Queue ( 2.4.
 More Data Structures Priority Queues and Heaps Priority Queues, Comparators, Locators, Dictionaries More Data Structures v. More Data Structures v. Priority Queue ADT (.4.) Total Order Relation A priority
More Data Structures Priority Queues and Heaps Priority Queues, Comparators, Locators, Dictionaries More Data Structures v. More Data Structures v. Priority Queue ADT (.4.) Total Order Relation A priority
Data Structures Lecture 6
 Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 6 Announcement Project Proposal due on Nov. 9 Remember to bring a hardcopy
Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 6 Announcement Project Proposal due on Nov. 9 Remember to bring a hardcopy
Programming II (CS300)
 1 Programming II (CS300) Chapter 10: Search and Heaps MOUNA KACEM mouna@cs.wisc.edu Spring 2018 Search and Heaps 2 Linear Search Binary Search Introduction to trees Priority Queues Heaps Linear Search
1 Programming II (CS300) Chapter 10: Search and Heaps MOUNA KACEM mouna@cs.wisc.edu Spring 2018 Search and Heaps 2 Linear Search Binary Search Introduction to trees Priority Queues Heaps Linear Search
Priority queues. Priority queues. Priority queue operations
 Priority queues March 30, 018 1 Priority queues The ADT priority queue stores arbitrary objects with priorities. An object with the highest priority gets served first. Objects with priorities are defined
Priority queues March 30, 018 1 Priority queues The ADT priority queue stores arbitrary objects with priorities. An object with the highest priority gets served first. Objects with priorities are defined
Lecture 3 Linear Data Structures: Arrays, Array Lists, Stacks, Queues and Linked Lists
 Lecture 3 Linear Data Structures: Arrays, Array Lists, Stacks, Queues and Linked Lists Chapters 3.1-3.3, 5.1-5.2, 6.1-1 - Core Collection Interfaces - 2 - The Java Collections Framework Interface Abstract
Lecture 3 Linear Data Structures: Arrays, Array Lists, Stacks, Queues and Linked Lists Chapters 3.1-3.3, 5.1-5.2, 6.1-1 - Core Collection Interfaces - 2 - The Java Collections Framework Interface Abstract
CSED233: Data Structures (2017F) Lecture9: Priority Queues and Heaps
 (2017F) Lecture9: Priority Queues and Heaps Daijin Kim CSE, POSTECH dkim@postech.ac.kr Priority Queue ADT A priority queue stores a coll ection of entries Each entry is a pair (key, value) Main methods
(2017F) Lecture9: Priority Queues and Heaps Daijin Kim CSE, POSTECH dkim@postech.ac.kr Priority Queue ADT A priority queue stores a coll ection of entries Each entry is a pair (key, value) Main methods
Chapter 9: Maps, Dictionaries, Hashing
 Chapter 9: 0 1 025-612-0001 2 981-101-0002 3 4 451-229-0004 Maps, Dictionaries, Hashing Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided
Chapter 9: 0 1 025-612-0001 2 981-101-0002 3 4 451-229-0004 Maps, Dictionaries, Hashing Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided
CS301 - Data Structures Glossary By
 CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
Ch02 Data Structures
 Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Ch02 Data Structures xkcd Seven http://xkcd.com/1417/ Used with permission under
Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Ch02 Data Structures xkcd Seven http://xkcd.com/1417/ Used with permission under
What is a Tree. Trees. Tree ADT ( 6.1.2) Tree Terminology. subtree. In computer science, a tree is an abstract model
 What is a Tree Trees Stock raud Make Money ast! Ponzi Scheme ank Robbery In computer science, a tree is an abstract model omputers R Us of a hierarchical structure tree consists of with a parent-child
What is a Tree Trees Stock raud Make Money ast! Ponzi Scheme ank Robbery In computer science, a tree is an abstract model omputers R Us of a hierarchical structure tree consists of with a parent-child
Course Review for Finals. Cpt S 223 Fall 2008
 Course Review for Finals Cpt S 223 Fall 2008 1 Course Overview Introduction to advanced data structures Algorithmic asymptotic analysis Programming data structures Program design based on performance i.e.,
Course Review for Finals Cpt S 223 Fall 2008 1 Course Overview Introduction to advanced data structures Algorithmic asymptotic analysis Programming data structures Program design based on performance i.e.,
The tree data structure. Trees COL 106. Amit Kumar Shweta Agrawal. Acknowledgement :Many slides are courtesy Douglas Harder, UWaterloo
 The tree data structure 1 Trees COL 106 Amit Kumar Shweta Agrawal Acknowledgement :Many slides are courtesy Douglas Harder, UWaterloo 1 Trees The tree data structure 3 A rooted tree data structure stores
The tree data structure 1 Trees COL 106 Amit Kumar Shweta Agrawal Acknowledgement :Many slides are courtesy Douglas Harder, UWaterloo 1 Trees The tree data structure 3 A rooted tree data structure stores
Hash Tables. Johns Hopkins Department of Computer Science Course : Data Structures, Professor: Greg Hager
 Hash Tables What is a Dictionary? Container class Stores key-element pairs Allows look-up (find) operation Allows insertion/removal of elements May be unordered or ordered Dictionary Keys Must support
Hash Tables What is a Dictionary? Container class Stores key-element pairs Allows look-up (find) operation Allows insertion/removal of elements May be unordered or ordered Dictionary Keys Must support
Outline. Preliminaries. Binary Trees Binary Search Trees. What is Tree? Implementation of Trees using C++ Tree traversals and applications
 Trees 1 Outline Preliminaries What is Tree? Implementation of Trees using C++ Tree traversals and applications Binary Trees Binary Search Trees Structure and operations Analysis 2 What is a Tree? A tree
Trees 1 Outline Preliminaries What is Tree? Implementation of Trees using C++ Tree traversals and applications Binary Trees Binary Search Trees Structure and operations Analysis 2 What is a Tree? A tree
Ch02 Data Structures
 Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Ch02 Data Structures xkcd Seven http://xkcd.com/1417/ Used with permission under
Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Ch02 Data Structures xkcd Seven http://xkcd.com/1417/ Used with permission under
CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS
 0 1 2 025-612-0001 981-101-0002 3 4 451-229-0004 CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH,
0 1 2 025-612-0001 981-101-0002 3 4 451-229-0004 CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH,
Course Review for. Cpt S 223 Fall Cpt S 223. School of EECS, WSU
 Course Review for Midterm Exam 1 Cpt S 223 Fall 2011 1 Midterm Exam 1 When: Friday (10/14) 1:10-2pm Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & in-class
Course Review for Midterm Exam 1 Cpt S 223 Fall 2011 1 Midterm Exam 1 When: Friday (10/14) 1:10-2pm Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & in-class
CSE 332 Winter 2015: Midterm Exam (closed book, closed notes, no calculators)
 _ UWNetID: Lecture Section: A CSE 332 Winter 2015: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will give
_ UWNetID: Lecture Section: A CSE 332 Winter 2015: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will give
Trees. CSE 373 Data Structures
 Trees CSE 373 Data Structures Readings Reading Chapter 7 Trees 2 Why Do We Need Trees? Lists, Stacks, and Queues are linear relationships Information often contains hierarchical relationships File directories
Trees CSE 373 Data Structures Readings Reading Chapter 7 Trees 2 Why Do We Need Trees? Lists, Stacks, and Queues are linear relationships Information often contains hierarchical relationships File directories
Programming II (CS300)
 1 Programming II (CS300) Chapter 12: Heaps and Priority Queues MOUNA KACEM mouna@cs.wisc.edu Fall 2018 Heaps and Priority Queues 2 Priority Queues Heaps Priority Queue 3 QueueADT Objects are added and
1 Programming II (CS300) Chapter 12: Heaps and Priority Queues MOUNA KACEM mouna@cs.wisc.edu Fall 2018 Heaps and Priority Queues 2 Priority Queues Heaps Priority Queue 3 QueueADT Objects are added and
Priority Queues & Heaps. CS16: Introduction to Data Structures & Algorithms Spring 2019
 Priority Queues & Heaps CS16: Introduction to Data Structures & Algorithms Spring 2019 Outline Priority Queues Motivation ADT Implementation Heaps insert( ) and upheap( ) removemin( ) and downheap( ) Motivation
Priority Queues & Heaps CS16: Introduction to Data Structures & Algorithms Spring 2019 Outline Priority Queues Motivation ADT Implementation Heaps insert( ) and upheap( ) removemin( ) and downheap( ) Motivation
CS251-SE1. Midterm 2. Tuesday 11/1 8:00pm 9:00pm. There are 16 multiple-choice questions and 6 essay questions.
 CS251-SE1 Midterm 2 Tuesday 11/1 8:00pm 9:00pm There are 16 multiple-choice questions and 6 essay questions. Answer the multiple choice questions on your bubble sheet. Answer the essay questions in the
CS251-SE1 Midterm 2 Tuesday 11/1 8:00pm 9:00pm There are 16 multiple-choice questions and 6 essay questions. Answer the multiple choice questions on your bubble sheet. Answer the essay questions in the
Entry and Priority Queue ADTs
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Adaptable Priority Queues 3 a 5 g 4 e Adaptable
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Adaptable Priority Queues 3 a 5 g 4 e Adaptable
Course Review. Cpt S 223 Fall 2009
 Course Review Cpt S 223 Fall 2009 1 Final Exam When: Tuesday (12/15) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
Course Review Cpt S 223 Fall 2009 1 Final Exam When: Tuesday (12/15) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
Cpt S 223 Fall Cpt S 223. School of EECS, WSU
 Course Review Cpt S 223 Fall 2012 1 Final Exam When: Monday (December 10) 8 10 AM Where: in class (Sloan 150) Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes
Course Review Cpt S 223 Fall 2012 1 Final Exam When: Monday (December 10) 8 10 AM Where: in class (Sloan 150) Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes
Sorting. Outline. Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort
 Sorting Hiroaki Kobayashi 1 Outline Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort Merge Sort Lower Bound on Comparison-Based Sorting Bucket Sort and Radix Sort Hiroaki
Sorting Hiroaki Kobayashi 1 Outline Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort Merge Sort Lower Bound on Comparison-Based Sorting Bucket Sort and Radix Sort Hiroaki
Data Structures Lecture 8
 Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 8 Recap What should you have learned? Basic java programming skills Object-oriented
Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 8 Recap What should you have learned? Basic java programming skills Object-oriented
Final Exam. CSE 2011 Prof. J. Elder Last Updated: :41 PM
 Final Exam Ø Tue, 17 Apr 2012 19:00 22:00 LAS B Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps, hashing, binary search trees, sorting,
Final Exam Ø Tue, 17 Apr 2012 19:00 22:00 LAS B Ø Closed Book Ø Format similar to midterm Ø Will cover whole course, with emphasis on material after midterm (maps, hashing, binary search trees, sorting,
Summer Final Exam Review Session August 5, 2009
 15-111 Summer 2 2009 Final Exam Review Session August 5, 2009 Exam Notes The exam is from 10:30 to 1:30 PM in Wean Hall 5419A. The exam will be primarily conceptual. The major emphasis is on understanding
15-111 Summer 2 2009 Final Exam Review Session August 5, 2009 Exam Notes The exam is from 10:30 to 1:30 PM in Wean Hall 5419A. The exam will be primarily conceptual. The major emphasis is on understanding
Priority Queue ADT ( 7.1) Heaps and Priority Queues 2. Comparator ADT ( 7.1.4) Total Order Relation. Using Comparators in C++
 Heaps and Priority Queues Priority Queue ADT (.) A priority queue stores a collection of items An item is a pair (key, element) Main methods of the Priority Queue ADT insertitem(k, o) inserts an item ith
Heaps and Priority Queues Priority Queue ADT (.) A priority queue stores a collection of items An item is a pair (key, element) Main methods of the Priority Queue ADT insertitem(k, o) inserts an item ith
FINALTERM EXAMINATION Fall 2009 CS301- Data Structures Question No: 1 ( Marks: 1 ) - Please choose one The data of the problem is of 2GB and the hard
 FINALTERM EXAMINATION Fall 2009 CS301- Data Structures Question No: 1 The data of the problem is of 2GB and the hard disk is of 1GB capacity, to solve this problem we should Use better data structures
FINALTERM EXAMINATION Fall 2009 CS301- Data Structures Question No: 1 The data of the problem is of 2GB and the hard disk is of 1GB capacity, to solve this problem we should Use better data structures
Department of Computer Science and Technology
 UNIT : Stack & Queue Short Questions 1 1 1 1 1 1 1 1 20) 2 What is the difference between Data and Information? Define Data, Information, and Data Structure. List the primitive data structure. List the
UNIT : Stack & Queue Short Questions 1 1 1 1 1 1 1 1 20) 2 What is the difference between Data and Information? Define Data, Information, and Data Structure. List the primitive data structure. List the
O(n): printing a list of n items to the screen, looking at each item once.
 UNIT IV Sorting: O notation efficiency of sorting bubble sort quick sort selection sort heap sort insertion sort shell sort merge sort radix sort. O NOTATION BIG OH (O) NOTATION Big oh : the function f(n)=o(g(n))
UNIT IV Sorting: O notation efficiency of sorting bubble sort quick sort selection sort heap sort insertion sort shell sort merge sort radix sort. O NOTATION BIG OH (O) NOTATION Big oh : the function f(n)=o(g(n))
INSTITUTE OF AERONAUTICAL ENGINEERING
 INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Course Name Course Code Class Branch DATA STRUCTURES ACS002 B. Tech
INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Course Name Course Code Class Branch DATA STRUCTURES ACS002 B. Tech
Lecture 3 Linear Data Structures
 Lecture 3 Linear Data Structures - 1 - Learning Outcomes Based on this lecture, you should: Know the basic linear data structures Be able to express each as an Abstract Data Type (ADT) Be able to specify
Lecture 3 Linear Data Structures - 1 - Learning Outcomes Based on this lecture, you should: Know the basic linear data structures Be able to express each as an Abstract Data Type (ADT) Be able to specify
AP Computer Science 4325
 4325 Instructional Unit Algorithm Design Techniques -divide-and-conquer The students will be -Decide whether an algorithm -classroom discussion -backtracking able to classify uses divide-and-conquer, -worksheets
4325 Instructional Unit Algorithm Design Techniques -divide-and-conquer The students will be -Decide whether an algorithm -classroom discussion -backtracking able to classify uses divide-and-conquer, -worksheets
9/10/2018 Algorithms & Data Structures Analysis of Algorithms. Siyuan Jiang, Sept
 9/10/2018 Algorithms & Data Structures Analysis of Algorithms Siyuan Jiang, Sept. 2018 1 Email me if the office door is closed Siyuan Jiang, Sept. 2018 2 Grades have been emailed github.com/cosc311/assignment01-userid
9/10/2018 Algorithms & Data Structures Analysis of Algorithms Siyuan Jiang, Sept. 2018 1 Email me if the office door is closed Siyuan Jiang, Sept. 2018 2 Grades have been emailed github.com/cosc311/assignment01-userid
Data Structures and Algorithms
 Berner Fachhochschule - Technik und Informatik Data Structures and Algorithms Heaps and Priority Queues Philipp Locher FS 2018 Heaps and Priority Queues Page 1 Outline Heaps Heap-Sort Priority Queues Heaps
Berner Fachhochschule - Technik und Informatik Data Structures and Algorithms Heaps and Priority Queues Philipp Locher FS 2018 Heaps and Priority Queues Page 1 Outline Heaps Heap-Sort Priority Queues Heaps
Course Review. Cpt S 223 Fall 2010
 Course Review Cpt S 223 Fall 2010 1 Final Exam When: Thursday (12/16) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
Course Review Cpt S 223 Fall 2010 1 Final Exam When: Thursday (12/16) 8-10am Where: in class Closed book, closed notes Comprehensive Material for preparation: Lecture slides & class notes Homeworks & program
1. Attempt any three of the following: 15
 (Time: 2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Make suitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written
(Time: 2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Make suitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written
a) For the binary tree shown below, what are the preorder, inorder and post order traversals.
 CS61CS61B Fall 2014 Guerrilla Section 2 Solutions 1. Trees a) For the binary tree shown below, what are the preorder, inorder and post order traversals. 23 / \ 47 0 / / \ 9 15 100 / \ / \ \ 1 935 12 42
CS61CS61B Fall 2014 Guerrilla Section 2 Solutions 1. Trees a) For the binary tree shown below, what are the preorder, inorder and post order traversals. 23 / \ 47 0 / / \ 9 15 100 / \ / \ \ 1 935 12 42
Data Structures Lecture 7
 Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 7 Recap We have talked about object oriented programing Chapter 1, 2,
Fall 2017 Fang Yu Software Security Lab. Dept. Management Information Systems, National Chengchi University Data Structures Lecture 7 Recap We have talked about object oriented programing Chapter 1, 2,
Heaps Outline and Required Reading: Heaps ( 7.3) COSC 2011, Fall 2003, Section A Instructor: N. Vlajic
 1 Heaps Outline and Required Reading: Heaps (.3) COSC 2011, Fall 2003, Section A Instructor: N. Vlajic Heap ADT 2 Heap binary tree (T) that stores a collection of keys at its internal nodes and satisfies
1 Heaps Outline and Required Reading: Heaps (.3) COSC 2011, Fall 2003, Section A Instructor: N. Vlajic Heap ADT 2 Heap binary tree (T) that stores a collection of keys at its internal nodes and satisfies
How much space does this routine use in the worst case for a given n? public static void use_space(int n) { int b; int [] A;
![How much space does this routine use in the worst case for a given n? public static void use_space(int n) { int b; int [] A; How much space does this routine use in the worst case for a given n? public static void use_space(int n) { int b; int [] A;](/thumbs/82/85312801.jpg) How much space does this routine use in the worst case for a given n? public static void use_space(int n) { int b; int [] A; } if (n
How much space does this routine use in the worst case for a given n? public static void use_space(int n) { int b; int [] A; } if (n
Module 2: Classical Algorithm Design Techniques
 Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
The questions will be short answer, similar to the problems you have done on the homework
 Introduction The following highlights are provided to give you an indication of the topics that you should be knowledgeable about for the midterm. This sheet is not a substitute for the homework and the
Introduction The following highlights are provided to give you an indication of the topics that you should be knowledgeable about for the midterm. This sheet is not a substitute for the homework and the
CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators)
 Name: Email address: Quiz Section: CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
Name: Email address: Quiz Section: CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
CS61B Fall 2014 Guerrilla Section 2 This worksheet is quite long. Longer than we ll cover in guerrilla section.
 CS61B Fall 2014 Guerrilla Section 2 This worksheet is quite long. Longer than we ll cover in guerrilla section. 1. Trees a) For the binary tree shown below, what are the preorder, inorder and post order
CS61B Fall 2014 Guerrilla Section 2 This worksheet is quite long. Longer than we ll cover in guerrilla section. 1. Trees a) For the binary tree shown below, what are the preorder, inorder and post order
MID TERM MEGA FILE SOLVED BY VU HELPER Which one of the following statement is NOT correct.
 MID TERM MEGA FILE SOLVED BY VU HELPER Which one of the following statement is NOT correct. In linked list the elements are necessarily to be contiguous In linked list the elements may locate at far positions
MID TERM MEGA FILE SOLVED BY VU HELPER Which one of the following statement is NOT correct. In linked list the elements are necessarily to be contiguous In linked list the elements may locate at far positions
CSE 332 Spring 2013: Midterm Exam (closed book, closed notes, no calculators)
 Name: Email address: Quiz Section: CSE 332 Spring 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
Name: Email address: Quiz Section: CSE 332 Spring 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
Module 1: Asymptotic Time Complexity and Intro to Abstract Data Types
 Module 1: Asymptotic Time Complexity and Intro to Abstract Data Types Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu
Module 1: Asymptotic Time Complexity and Intro to Abstract Data Types Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu
Priority Queues. Reading: 7.1, 7.2
 Priority Queues Reading: 7.1, 7.2 Generalized sorting Sometimes we need to sort but The data type is not easily mapped onto data we can compare (numbers, strings, etc) The sorting criteria changes depending
Priority Queues Reading: 7.1, 7.2 Generalized sorting Sometimes we need to sort but The data type is not easily mapped onto data we can compare (numbers, strings, etc) The sorting criteria changes depending
Tree. A path is a connected sequence of edges. A tree topology is acyclic there is no loop.
 Tree A tree consists of a set of nodes and a set of edges connecting pairs of nodes. A tree has the property that there is exactly one path (no more, no less) between any pair of nodes. A path is a connected
Tree A tree consists of a set of nodes and a set of edges connecting pairs of nodes. A tree has the property that there is exactly one path (no more, no less) between any pair of nodes. A path is a connected
Priority queues. Priority queues. Priority queue operations
 Priority queues March 8, 08 Priority queues The ADT priority queue stores arbitrary objects with priorities. An object with the highest priority gets served first. Objects with priorities are defined by
Priority queues March 8, 08 Priority queues The ADT priority queue stores arbitrary objects with priorities. An object with the highest priority gets served first. Objects with priorities are defined by
CS8391-DATA STRUCTURES
 ST.JOSEPH COLLEGE OF ENGINEERING DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERI NG CS8391-DATA STRUCTURES QUESTION BANK UNIT I 2MARKS 1.Explain the term data structure. The data structure can be defined
ST.JOSEPH COLLEGE OF ENGINEERING DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERI NG CS8391-DATA STRUCTURES QUESTION BANK UNIT I 2MARKS 1.Explain the term data structure. The data structure can be defined
