New Region Incrementing Visual Cryptography Scheme
|
|
|
- Cecil Greene
- 6 years ago
- Views:
Transcription
1 New Regon Incrementng Vsual Cryptography Scheme Chng-Nung Yang Hsang-Wen Shh Yu-Yng Chu Len Harn CSIE Dept Natonal Dong Hwa Unversty Hualen Tawan CSEE Dept Unversty of Mssour-Kansas Cty Kansas Mssour USA Abstract - Recently Wang ntroduced a novel ( n) regon ncrementng vsual cryptography scheme (RIVCS) whch can gradually reconstruct vsual secrets wth multple secrecy levels n a sngle mage A secret mage s dvded nto multple regons where each regon has a certan level of secrecy Any t shadow mages where tn can be used to reveal (t) levels of secrets However n Wang s scheme the colors of reconstructed mages for some secrecy levels are reversed (the black whte are reversed) In ths paper we propose the ( n)-rivcs revealng the correct colors for all regons We also gve a modfed verson to enhance the contrast reduce the sze of shadow mage compared wth Wang s scheme Keywords: Secret sharng mage secret sharng vsual cryptography vsual secret sharng Introducton A (k n) secret mage sharng scheme (SISS) where k n encrypts a secret mage nto n shadow mages (known as ) satsfyng the threshold property Any k or more can reconstruct a secret mage whle the secret cannot be revealed from less than k There are two maor categores n SISS: one s the vsual cryptography scheme (VCS) the other s the polynomal-based SISS (PSISS) In VCS any k partcpants may photocopy ther on transparences stack them on an overhead proector to vsually decode the secret through the human vsual system wthout hardware computaton However VCS has the poor vsual qualty of a reconstructed mage whch comes from ts ntrnsc property usng the ORoperaton for decodng [] On the contrary PSISS can recover a dstorton-less secret mage by usng Lagrange nterpolaton [-4] Although VCS cannot recover the orgnal secret mage VCS provdes new secure magng applcatons eg vsual authentcaton steganography mage encrypton due to the ease of decodng (the stackngto-see property) In VCS a secret pxel s exped to m (referred to as the pxel expanson) subpxels The vsual qualty of a reconstructed mage n VCS s degraded by a large pxel expanson thus most studes try to enhance the vsual qualty or reduce the pxel expanson Some of them even had no pxel expanson (m=) whch are known as the probablstc VCS (PVCS) [5-7] The authors n [8] extend the PVCS to share grey-scale mages color mages The conventonal VCS wth the fxed m (>) unlke the PVCS s so called as the determnstc VCS (DVCS) A so-called mult-secret VCS (MVCS) explores the possbltes of sharng multple secret mages [9-4] The MVCS can reveal the dfferent secret mages by stackng at dfferent postons Other VCSs wth specfc features (such as cheatng preventon solvng msalgnment problem achevng the deal contrast) were accordngly proposed [5-9] Some novel applcatons of VCS combnng watermark fngerprnt Google street vew bar code were also ntroduced [-3] Up to date there are vast research papers on VCS n the lterature recently a book coverng an extensve range of topcs related to VCS s publshed [4] Smlar to MVCS Wang recently proposed a regon ncrementng VCS (RIVCS) [5] whch reveals multple mages However there are two dfferences between RIVCS MVCS: () MVCS has multple secret mages whle RIVCS dvde a secret mage wth multple regons where each regon has an mage Thus a complete secret mage n RIVCS s composed of multple mages () In a ( n)- MVCS we reconstruct the dfferent secret mages by stackng two at dfferent postons The ( n)-rivcs reveal (n) dfferent mages gradually by stackng two three n respectvely In Wang s scheme the colors of the reconstructed mage for some secrecy levels are reversed (the black whte are reversed) In ths paper we propose the ( n)-rivcs whch shows the correct colors n all regons When toleratng the reverse of black whte colors our modfed ( n)-rivcs enhances the contrast reduces the shadow sze compared wth Wang s ( n)-rivcs for most cases The rest of ths paper s organzed as follows In Secton two exstng VCSs Naor Shamr s VCS [] Wang s RIVCS [5] are descrbed In Secton 3 we ntroduce two approaches for constructon of ( n)-rivcs Experment comparson follow n Secton 4 Conclusons are drawn n Secton 5 Prevous works Our new RIVCS scheme s based on the conventonal VCS We gve a systematc way to mplement ( n)-rivcs show the mprovement compared wth Wang s ( n)- RIVCS We descrbe Naor Shamr s VCS to realze the
2 constructons propertes of (k n)-vcs Also we brefly revew Wang s RIVCS Naor Shamr s VCS Naor Shamr s VCS [] encrypted a black--whte secret mage nto nose-lke by expng a secret pxel nto m subpxels The szes of the pxel the subpxel are equal Hence the shadow sze s m tmes exped In Naor Shamr s VCS a whteness s used to dstngush the black color from the whte color e mh h W (respectvely ml l W) represents a whte (respectvely black) secret pxel where h l are the whteness of the whte color black color l<hm A (k n)-vcs s desgned by two base n m matrces wth elements denotng the whte black subpxels respectvely When sharng a whte (respectvely black) secret pxel a dealer romly chooses m subpxels n one row of a matrx n the set C (respectvely C ) whch ncludes all matrces obtaned by permutng the columns n (respectvely ) to a relatve shadow Let OR r = denote an OR-ed vector of any r rows n H() be the Hammng weght functon Then the base matrces of a (k n)- VCS should satsfy the followng two condtons Securty condton Contrast condton [Securty]: H OR r = OR [Contrast]: H OR r (m l) OR (m h)) for r=k where l<hm H r for r(k ) H r The securty condton assures a (k n)-vcs of the perfect secrecy On the other h the contrast condton defnes the dfferent contrasts of black whte colors so that a secret mage can be revealed Example: Construct a ( )-VCS of h= l= m= by OR H OR = It s observed that H = HOR = OR H = satsfy contrast securty condtons For smplcty we use xyw to x y represent ( ) ts permutatons In a reconstructed mage a black color s W a whte color s W Thus we can vsually decode the secret mage ecause every -subpxel block n s W are nose-lke The contrast for ths ( )-VCS s ( h l)/ m =/ Wang s RIVCS Wang s ( n)-rivcs s very smlar to the scalable ( n)-pisss [6 7 8] whch has the threshold property the scalable decodng capablty (the scalablty) The scalablty s that the amount of secret nformaton s proportonal to the number of used n reconstructon Wang s ( n)-rivcs s exactly same to the scalable ( n)- PISSS usng mult-secret mode except that they use dfferent decodng methods In Wang s ( n)-rivcs when stackng (+) one can decode the -th secrecy level regon where = (n) For example n a ( 4)-RIVCS the secret mage s dvded nto three secret level regons as shown n Fg (a) When stackng two three four we can decode the -th th 3-th secrecy level regons respectvely (see Fgs (b-d)) (a) (c) (d) Fg A partton of three secrecy level regons for the ( 4)-RIVCS: (a) three secrecy-level decomposton the revealed regon when stackng two (c) the revealed regon when stackng three (d) the revealed regon when stackng four Let matrx encodng a whte (respectvely black) pxel for the -th secrecy level regon These matrces should meet the followng two condtons: () all matrces must have the same extenson of pxel expanson n order to arrange the subpxels of all regons n a shadow () the regons where no secret s revealed n the reconstructed mage should be nose-lke The bass matrces ( ) of Wang s ( 3)-RIVCS wth m=4 are gven as follows (respectvely ) (n) represent the () From Eq () t s observed that any one shadow has W subpxels thus are nose-lke When stackng any two we have 3W (stackng any two rows n ) W (stackng any two rows n ) for the - th secrecy level regon we have 3W (stackng any two rows n ) for the -th secrecy level regon Thus the -th level secret s recovered ts contrast s /4 The contrasts of -th -th secrecy levels are /4 (stackng three rows n ) /4 (stackng three rows n ) respectvely Note: there was a typo error n [5] The author showed that the contrast of -th secrecy level s / when stackng three 3 The proposed RIVCS In [5] the bass matrces ( n)-rivcss wth n= are drectly gven However the author dd not demonstrate how to desgn the bass matrces Also from Eq () the
3 colors of -th secrecy level regon are reversed 3W n the whte matrx s darker than W n the black matrx In ths paper our man contrbuton s to gve a systematc constructon for ( n)-rivcs whch the appeared colors are correct for all regons We also show a modfed verson wth the reverse color for some secrecy levels lke Wang s scheme to enhance the contrast reduce the shadow sze 3 The ( n)-rivcs wth correct color for all regons The proposed ( n)-rivcs s based on (n) (t n)-vcs tn Let ( tn ) ( tn) are the black whte base ( tn) ( tn) matrces of a (t n)-vcs The base matrces tn for n=3 4 5 obtaned from Naor Shamr s VCS [] Droste s VCS [9] are shown as follows These matrces wll be used to construct our ( n)-rivcs ase matrces used for constructng our ( n)-rivcs 3n5 are shown as follows Naor Shamr s ( 3)-VCS: (3) (3) Naor Shamr s (3 3)-VCS: (33) (33) Naor Shamr s ( 4)-VCS: (4) (4) Naor Shamr s (3 4)-VCS: (34) (34) Naor Shamr s (4 4)-VCS: (44) (44) Naor Shamr s reverse ( 5)-VCS: (5) (5) Naor Shamr s (3 5)-VCS: (35) (35) Droste s (4 5)-VCS: (45) (45) Naor Shamr s (5 5)-VCS: (55) (55) Suppose that the background color of a secret mage s whte Then the base matrces of ( n)-rivcs where (n) are desgned as follows ( n) (3 n) ( n n) = n () ( n) (3 n) ( n) ( n n) n Theorem : The base matrces n Eq () satsfy ( n)-rivc wth the correct colors for all regons Proof: A ( n)-rivc wth the correct colors for all regons should satsfy the followng two condtons: () when stackng or fewer n we have the same black whte subpxels (securty condton) () when stackng (+) we have the more black subpxels n than those n (contrast condton the colors are correct for all regons) From Eq () the dfference of ( ) s n ( n) ( ) Obvously n ( n) are the base matrce of (+ n)-vcs satsfy the above two condtons Ths mples that also satsfy these two condtons y Eq () we obtan bass matrces for ( 3)-RVCS wth m=7: (3) (33) (3) (33) (3) (33) Usng the same approach we can derve the bass matrces of ( 4)-RIVCS wth m=8 ( 5)-RIVCS wth m=44 as shown n Eqs (4) (5) respectvely (3)
4 (4) (34) (44) (4) (34) (44) 3 (4) (34) (44) (4) (34) (44) 3 (4) (5) (35) (45) (55) 3 4 (5) (35) (45) (55) (5) (35) (45) (55) (5) (5) (35) (45) (55) (5) (35) (45) (55) 3 4 Although the ( n)-rivcs obtaned from Eq () has the correct colors for all regons ts pxel expanson s sgnfcantly ncreased Next we demonstrate a modfed verson to reduce the shadow sze enhance the contrast 3 The modfed ( n)-rivcs In Wang s ( n)-rivc the shared mage s a b-level mage Therefore the secret nformaton s not compromsed even though the black whte colors are reversed When loosenng the restrcton of revealng the correct color our constructon can be modfed to reduce the pxel expanson enhances the contrast compared wth Wang scheme ( n) Let be the black whte base matrces of a (+ n)-vcs where (n) { } Let he base matrx ( n ) ( n) be e ( n ) = ( n ) ( ) mod ( ) n ( n) = The modfed ( n)-rivcs wth where (n) are desgned as follows Let the matrx operaton be the unon mnus operatons of column vectors Our modfed ( n)-rivc s to fnd a mnmum m n the unon matrx ( n ) (3 n) ( nn ) n n Eq (6) by choosng from or for (n) ( n) (3 n) ( n n) = n n ( n) ( n) n (6-) For the -st secrecy level regon we only assure that one cannot vsually see the secret from any sngle shadow Hence the matrx n Eq (6-) can be modfed as Eq (6-) to mprove the contrast of -st secrecy level regon when stackng more than two The values of m m n Eq (6-) are chosen to let the number of one n a row s exactly same to ( n) m m (6-) Proof: A ( n)-rivc should satsfy the followng two condtons: () when stackng or fewer n we have the same black whte subpxels (securty condton) () stackng (+) we have dfferent black subpxels n (contrast condton) From Eq (6-) the dfference of () s ( n ) ( ) n ( ) (or n ( n) ) So satsfy these two condtons Although ( n ) may be n or we can stll dstngush the colors n a b-level mage but the color may be reversed or not For = from Eq (6-) we have the same black whte sub pxels n each row for Obvously stackng any two or more n [ ( n ) ] has more black subpxels than m m those n The values of m m are chosen to make the number of one n a row exactly same to thus a sngle shadow n condton satsfes the securty The matrces of the modfed ( 3)-RIVCS wth m=4 are shown n Eq (7) usng Naor Shamr s (3) (3) (3) (33) (3) (3) (33) (33) (33) (7) If we use (3) (3) we can obtan the same matrces as Wang s ( 3)-RIVCS The matrces of the modfed ( 4)-RIVCS wth m= the modfed ( 5)-RIVCS wth m= are shown n Eqs (8) (9) respectvely (4) (34) (44) 3 (4) (34) (34) (44) (44) 3 3 (8) Theorem : The base matrces n Eq (6) satsfy ( n)-rivc
5 (5) (35) (45) (55) 3 4 (5) (35) (3 5) (45) (45) 3 3 (55) (55) Experment comparson Four schemes are expermented to demonstrate the performance of our ( n)-rivcs the modfed ( n)- RIVCS Scheme # s Wang s ( 3)-RIVCS Scheme # s the proposed ( 3)-RIVCS Scheme #3 s our modfed ( 3)- RIVCS Scheme #4 s our modfed ( 5)-RIVCS As shown n Fg (a) the secret mage used for these schemes s a prnted-text secret mage embracng AC abc 3 αβγ It s dvded nto two regons where AC 3 (9) s the -th secrecy level abc s the -th secrecy level Ths two secrecy-level decomposton s shown n Fg s used for Schemes # # #3 For testng Scheme #4 we need four secrecy-level decomposton Fg (c) shows four secrecy regons: AC (-th secrecy level) abc (-th secrecy level) 3 (3-th secrecy level) αβγ (4-th secrecy level) background whle the color of abc s darker than background Ths s the so-called ncorrect color problem n Wang s scheme (a) Fg 3 Wang s ( 3)-RIVCS: (a) stackng two to gan -th level secret (c) stackng all three to gan -th level secret Scheme # usng Eq (3) solves ths ncorrect color problem ecause the pxel expanson s m=7 we add one all- column n the matrces to possbly assure the reconstructed mage of the rght aspect rato The reconstructed mages of Scheme # are shown n Fg 4 From the reconstructed mages (Fgs 4(a) ) all prnted texts are darker than background solve he problem of ncorrect color n Wang scheme (a) Fg 4 The proposed ( 3)-RIVCS wth the correct colors for all regons: (a) stackng two to gan -th level secret stackng all three to gan -th level secret The proposed ( n)-rivcs has the large pxel expanson but demonstrates the correct color Our modfed RIVCS has the less shadow sze Scheme #3 usng Eq (7) has m=4 same to Scheme # Fg 5 shows the reconstructed mages of Scheme #3 Although both ( 3)-RIVCSs have the same pxel expanson m=4 Wang s scheme has =/4 for the -th secrecy level regon when stackng three whle our scheme enhances the contrast to =/ It s observed that AC 3 n Fg 5 s really clearer than Fg 3 (a) (c) Fg The secret mage the secrecy-level decomposton: (a) the secret mage two secrecy-level decomposton used for ( 3)-RIVCS (c) four secrecy-level decomposton used for ( 5)-RIVCS The reconstructed mages of Scheme # are shown n Fg 3 The revealed secrets for stackng two all three are respectvely AC 3 It s observed that the color of (Fg 3(a)) abc AC 3 (Fg 3) s lghter than (a) Fg 5 The modfed ( 3)-RIVCS: (a) stackng any two to gan -th level secret stackng all three to gan -th level secret Expermental results of Scheme #4 are shown n Fg 6 We gradually reveal the secret mages wth dfferent secrecy levels when stackng Scheme #4 has the pxel expanson m= lesser than m=3 n Wang s ( 5)- RVICS
6 (a) the color for all regons thus there s no loss of nformaton esdes our modfed scheme mproves Wang s scheme for some cases Actually our man contrbuton s to gve the systematc constructon of ( n)-rivcs whle the authors n [5] dd not demonstrate how to construct ther matrces n the ( n)-rivcs 5 Concluson Ths work gves a systematc way to construct two types of ( n)-rivcss Also we theoretcally prove that our schemes are ( n)-rivcss The proposed ( n)-rivcs reveals the correct colors for all regons the modfed ( n)-rivcs has the less shadow sze enhances the contrast (c) (d) Fg 6 Our modfed ( 5)-RIVCS: (a) stackng two to obtan -th level secret stackng three to obtan -th level secret (c) stackng four to obtan 3-th level secret (d) stackng fve to obtan 4- th level secret The pxel expansons for the proposed ( n)-rivcs the modfed ( n)-rivcs Wang s ( n)-rivcs where 3n5 are llustrated n Table I Although the proposed scheme has the large pxel expanson t reveals the correct colors for all regons Our modfed scheme has the same pxel expanson for n=3 4 the smaller pxel expanson for n=5 The contrasts of our modfed ( n)- RIVCS Wang s ( n)-rivcs are shown n Table II where the astersk denotes the better contrast It s observed that our modfed scheme s better for most cases TALE I COMPARISON OF PIXEL EXPANSION ( n)-rivcs proposed scheme modfed scheme Wang scheme n = n =4 8 n = ( 3)-RIVCS secrecy level ( 4)-RIVCS secrecy level ( 5)-RIVCS secrecy level TALE II COMPARISON OF CONTRASTS contrast of our scheme (Wang scheme) stackng stackng 3 stackng 4 stackng 5 -th /4 (/4) / * (/4) -th /4 (/4) -th /5 (/5) 3/ (3/) /5 * (3/) -th / (/) /5 * (/) 3-th / (/) -th /5 * (4/3) 3/ * (6/3) 7/ * (7/3) 7/ * (7/3) -th / * (/3) / (3/3 * ) 3/ (6/3 * ) 3-th / * (/3) 3/ * (3/3) 4-th / * (/3) In fact the b-level lumnance contrast for dfferent levels of secrets reduces the pxel expanson exhbts the revealed secrets wth hgher lumnance contrast The reverse of color often does not compromse the secret when the color of the secret mage s not our secret nformaton However f the color of text s also the secret nformaton the ncorrectcolor problem wll compromse the secret Our scheme has 6 Acknowledgment Ths work was supported n part by the Natonal Scence Councl proect under Grant NSC H the Testbed@TWISC Natonal Scence Councl under the Grant NSC -9-E-6-7 References [] M Naor A Shamr Vsual cryptography Eurocrypt 94 vol LNCS pp - [] CC Chang YP Hseh CH Ln Sharng secrets n stego mages wth authentcaton Pattern Recognton vol 4 pp [3] CN Yang C Cou A Comment on sharng secrets n stego mages wth authentcaton Pattern Recognton vol 4 pp [4] Z Eslam SH Razzagh J Zarepour Ahmadabad Secret mage sharng wth authentcaton-channg dynamc embeddng Journal of Systems & Software vol 84 pp [5] R ITO H Kuwakado H Tanaka Image sze nvarant vsual cryptography IEICE Trans on Fund of Elect Comm Comp Sc vol E8-A pp [6] CN Yang New vsual secret sharng schemes usng probablstc method Pattern Recognton Letters vol 5 pp [7] S Cmato R De Prsco A De Sants Probablstc vsual cryptography schemes The Computer Journal vol 49 pp [8] D Wang F Y X L Probablstc vsual secret sharng schemes for grey-scale mages color mages Informaton Scences vol 8 pp 89-8 [9] HC Wu CC Chang Sharng vsual mult-secrets usng crcle shares Computer Stards & Interfaces vol 8 pp [] SJ Shyu SY Huang YK Lee RZ Wang K Chen Sharng multple secrets n vsual cryptography Pattern Recognton vol 4 pp
7 [] J Feng HC Wu CS Tsa YF Chang YP Chu Vsual Secret sharng for multple secrets Pattern Recognton vol 4 pp [] LG Fang YM L Yu Mult-secret vsual cryptography based on reversed mages Informaton Computng vol 4 pp [3] KH Lee PL Chu A hgh contrast capacty effcent vsual cryptography scheme for the encrypton of multple secret mages Optcs Communcatons vol 84 pp73 74 [4] CN Yang T-H Chung A general mult-secret vsual cryptography scheme Optcs Communcatons vol 83 pp [5] DS Tsa TH Chen G Horng A cheatng preventon scheme for bnary vsual cryptography wth homogeneous secret mages Pattern Recognton vol 4 pp [6] CN Yang AG Peng TS Chen MTVSS: (M)salgnment (T)olerant (V)sual (S)ecret (S)harng on Resolvng Algnment Dffculty Sgnal Processng vol 89 pp [7] F Lu CK Wu XJ Ln The algnment problem of vsual cryptography schemes Desgns Codes Cryptography vol 5 pp [8] S Cmato A DeSants AL Ferrara Masucc Ideal contrast vsual cryptography schemes wthreversng Informaton Processng Letters vol 93 pp [9] CN Yanh CC Wang TS Chen Vsual cryptography schemes wth reversng The Computer Journal vol 5 pp [] Surekha G Swamy KS Rao A multple watermarkng technque for mages based on vsual cryptography Computer Applcatons vol pp 77-8 [] T Monoth Anto P Tamperproof transmsson of fngerprnts usng vsual cryptography schemes Proceda Computer Scence vol pp [] J Wer W Yan Resoluton varant vsual cryptography for street vew of Google maps ISCAS Pars France May 3 June pp [3] CN Yang TS Chen MH Chng Embed addtonal prvate nformaton nto two-dmensonal barcodes by the vsual secret sharng scheme Integrated Computer-Aded Engneerng vol 3 pp [8] CN Yang YY Chu A general (k n) scalable secret mage sharng scheme wth the smooth scalablty to be pulshed at Journal of Systems & Software [9] Droste New results on vsual cryptography n CRYPTO 96 vol LNCS pp 4 45 [4] S Cmato CN Yang Vsual cryptography secret mage sharng CRC Press Taylor & Francs [5] RZ Wang Regon ncrementng vsual cryptography IEEE Sgnal Processng Letters vol 6 pp [6] RZ Wang SJ Shyu Scalable secret mage sharng Sgnal Processng: Image Communcaton vol pp [7] CN Yang Sn-Mng Huang Constructons propertes of k out of n scalable secret mage sharng Optcs Communcatons vol 83 pp 75-76
Parallelism for Nested Loops with Non-uniform and Flow Dependences
 Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
THE SECRET image sharing scheme (SISS) is an important
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 22, NO. 5, MAY 22 799 k Out of n Region Incrementing Scheme in Visual Cryptography Ching-Nung Yang, Senior Member, IEEE, Hsiang-Wen
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL. 22, NO. 5, MAY 22 799 k Out of n Region Incrementing Scheme in Visual Cryptography Ching-Nung Yang, Senior Member, IEEE, Hsiang-Wen
PYTHON IMPLEMENTATION OF VISUAL SECRET SHARING SCHEMES
 PYTHON IMPLEMENTATION OF VISUAL SECRET SHARING SCHEMES Ruxandra Olmd Faculty of Mathematcs and Computer Scence, Unversty of Bucharest Emal: ruxandra.olmd@fm.unbuc.ro Abstract Vsual secret sharng schemes
PYTHON IMPLEMENTATION OF VISUAL SECRET SHARING SCHEMES Ruxandra Olmd Faculty of Mathematcs and Computer Scence, Unversty of Bucharest Emal: ruxandra.olmd@fm.unbuc.ro Abstract Vsual secret sharng schemes
Private Information Retrieval (PIR)
 2 Levente Buttyán Problem formulaton Alce wants to obtan nformaton from a database, but she does not want the database to learn whch nformaton she wanted e.g., Alce s an nvestor queryng a stock-market
2 Levente Buttyán Problem formulaton Alce wants to obtan nformaton from a database, but she does not want the database to learn whch nformaton she wanted e.g., Alce s an nvestor queryng a stock-market
Improvement of Spatial Resolution Using BlockMatching Based Motion Estimation and Frame. Integration
 Improvement of Spatal Resoluton Usng BlockMatchng Based Moton Estmaton and Frame Integraton Danya Suga and Takayuk Hamamoto Graduate School of Engneerng, Tokyo Unversty of Scence, 6-3-1, Nuku, Katsuska-ku,
Improvement of Spatal Resoluton Usng BlockMatchng Based Moton Estmaton and Frame Integraton Danya Suga and Takayuk Hamamoto Graduate School of Engneerng, Tokyo Unversty of Scence, 6-3-1, Nuku, Katsuska-ku,
VISUAL cryptography (VC) is a technique that encrypts a
 4336 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 23, NO. 10, OCTOBER 2014 Sharng Vsual Secrets n Sngle Image Random Dot Stereograms Ka-Hu Lee and Pe-Lng Chu Abstract Vsual cryptography schemes (VCSs generate
4336 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 23, NO. 10, OCTOBER 2014 Sharng Vsual Secrets n Sngle Image Random Dot Stereograms Ka-Hu Lee and Pe-Lng Chu Abstract Vsual cryptography schemes (VCSs generate
A Binarization Algorithm specialized on Document Images and Photos
 A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
Related-Mode Attacks on CTR Encryption Mode
 Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
A Lossless Watermarking Scheme for Halftone Image Authentication
 IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.6 No.2B, February 2006 147 A Lossless Watermarkng Scheme for Halftone Image Authentcaton Jeng-Shyang Pan, Hao Luo, and Zhe-Mng Lu,
IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.6 No.2B, February 2006 147 A Lossless Watermarkng Scheme for Halftone Image Authentcaton Jeng-Shyang Pan, Hao Luo, and Zhe-Mng Lu,
Enhanced Watermarking Technique for Color Images using Visual Cryptography
 Informaton Assurance and Securty Letters 1 (2010) 024-028 Enhanced Watermarkng Technque for Color Images usng Vsual Cryptography Enas F. Al rawashdeh 1, Rawan I.Zaghloul 2 1 Balqa Appled Unversty, MIS
Informaton Assurance and Securty Letters 1 (2010) 024-028 Enhanced Watermarkng Technque for Color Images usng Vsual Cryptography Enas F. Al rawashdeh 1, Rawan I.Zaghloul 2 1 Balqa Appled Unversty, MIS
Content Based Image Retrieval Using 2-D Discrete Wavelet with Texture Feature with Different Classifiers
 IOSR Journal of Electroncs and Communcaton Engneerng (IOSR-JECE) e-issn: 78-834,p- ISSN: 78-8735.Volume 9, Issue, Ver. IV (Mar - Apr. 04), PP 0-07 Content Based Image Retreval Usng -D Dscrete Wavelet wth
IOSR Journal of Electroncs and Communcaton Engneerng (IOSR-JECE) e-issn: 78-834,p- ISSN: 78-8735.Volume 9, Issue, Ver. IV (Mar - Apr. 04), PP 0-07 Content Based Image Retreval Usng -D Dscrete Wavelet wth
Pattern Recognition 43 (2010) Contents lists available at ScienceDirect. Pattern Recognition. journal homepage:
 Pattern Recognton 43 (2010) 397 -- 404 Contents lsts avalable at ScenceDrect Pattern Recognton ournal homepage: www.elsever.com/locate/pr Secret mage sharng based on cellular automata and steganography
Pattern Recognton 43 (2010) 397 -- 404 Contents lsts avalable at ScenceDrect Pattern Recognton ournal homepage: www.elsever.com/locate/pr Secret mage sharng based on cellular automata and steganography
2x x l. Module 3: Element Properties Lecture 4: Lagrange and Serendipity Elements
 Module 3: Element Propertes Lecture : Lagrange and Serendpty Elements 5 In last lecture note, the nterpolaton functons are derved on the bass of assumed polynomal from Pascal s trangle for the fled varable.
Module 3: Element Propertes Lecture : Lagrange and Serendpty Elements 5 In last lecture note, the nterpolaton functons are derved on the bass of assumed polynomal from Pascal s trangle for the fled varable.
A fast algorithm for color image segmentation
 Unersty of Wollongong Research Onlne Faculty of Informatcs - Papers (Arche) Faculty of Engneerng and Informaton Scences 006 A fast algorthm for color mage segmentaton L. Dong Unersty of Wollongong, lju@uow.edu.au
Unersty of Wollongong Research Onlne Faculty of Informatcs - Papers (Arche) Faculty of Engneerng and Informaton Scences 006 A fast algorthm for color mage segmentaton L. Dong Unersty of Wollongong, lju@uow.edu.au
A Fast Content-Based Multimedia Retrieval Technique Using Compressed Data
 A Fast Content-Based Multmeda Retreval Technque Usng Compressed Data Borko Furht and Pornvt Saksobhavvat NSF Multmeda Laboratory Florda Atlantc Unversty, Boca Raton, Florda 3343 ABSTRACT In ths paper,
A Fast Content-Based Multmeda Retreval Technque Usng Compressed Data Borko Furht and Pornvt Saksobhavvat NSF Multmeda Laboratory Florda Atlantc Unversty, Boca Raton, Florda 3343 ABSTRACT In ths paper,
Load Balancing for Hex-Cell Interconnection Network
 Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
High Payload Reversible Data Hiding Scheme Using Difference Segmentation and Histogram Shifting
 JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 11, NO. 1, MARCH 2013 9 Hgh Payload Reversble Data Hdng Scheme Usng Dfference Segmentaton and Hstogram Shftng Yung-Chen Chou and Huang-Chng L Abstract
JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 11, NO. 1, MARCH 2013 9 Hgh Payload Reversble Data Hdng Scheme Usng Dfference Segmentaton and Hstogram Shftng Yung-Chen Chou and Huang-Chng L Abstract
Hybrid Non-Blind Color Image Watermarking
 Hybrd Non-Blnd Color Image Watermarkng Ms C.N.Sujatha 1, Dr. P. Satyanarayana 2 1 Assocate Professor, Dept. of ECE, SNIST, Yamnampet, Ghatkesar Hyderabad-501301, Telangana 2 Professor, Dept. of ECE, AITS,
Hybrd Non-Blnd Color Image Watermarkng Ms C.N.Sujatha 1, Dr. P. Satyanarayana 2 1 Assocate Professor, Dept. of ECE, SNIST, Yamnampet, Ghatkesar Hyderabad-501301, Telangana 2 Professor, Dept. of ECE, AITS,
Wavefront Reconstructor
 A Dstrbuted Smplex B-Splne Based Wavefront Reconstructor Coen de Vsser and Mchel Verhaegen 14-12-201212 2012 Delft Unversty of Technology Contents Introducton Wavefront reconstructon usng Smplex B-Splnes
A Dstrbuted Smplex B-Splne Based Wavefront Reconstructor Coen de Vsser and Mchel Verhaegen 14-12-201212 2012 Delft Unversty of Technology Contents Introducton Wavefront reconstructon usng Smplex B-Splnes
A Fast Visual Tracking Algorithm Based on Circle Pixels Matching
 A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
Learning the Kernel Parameters in Kernel Minimum Distance Classifier
 Learnng the Kernel Parameters n Kernel Mnmum Dstance Classfer Daoqang Zhang 1,, Songcan Chen and Zh-Hua Zhou 1* 1 Natonal Laboratory for Novel Software Technology Nanjng Unversty, Nanjng 193, Chna Department
Learnng the Kernel Parameters n Kernel Mnmum Dstance Classfer Daoqang Zhang 1,, Songcan Chen and Zh-Hua Zhou 1* 1 Natonal Laboratory for Novel Software Technology Nanjng Unversty, Nanjng 193, Chna Department
Virtual Machine Migration based on Trust Measurement of Computer Node
 Appled Mechancs and Materals Onlne: 2014-04-04 ISSN: 1662-7482, Vols. 536-537, pp 678-682 do:10.4028/www.scentfc.net/amm.536-537.678 2014 Trans Tech Publcatons, Swtzerland Vrtual Machne Mgraton based on
Appled Mechancs and Materals Onlne: 2014-04-04 ISSN: 1662-7482, Vols. 536-537, pp 678-682 do:10.4028/www.scentfc.net/amm.536-537.678 2014 Trans Tech Publcatons, Swtzerland Vrtual Machne Mgraton based on
Module Management Tool in Software Development Organizations
 Journal of Computer Scence (5): 8-, 7 ISSN 59-66 7 Scence Publcatons Management Tool n Software Development Organzatons Ahmad A. Al-Rababah and Mohammad A. Al-Rababah Faculty of IT, Al-Ahlyyah Amman Unversty,
Journal of Computer Scence (5): 8-, 7 ISSN 59-66 7 Scence Publcatons Management Tool n Software Development Organzatons Ahmad A. Al-Rababah and Mohammad A. Al-Rababah Faculty of IT, Al-Ahlyyah Amman Unversty,
Tsinghua University at TAC 2009: Summarizing Multi-documents by Information Distance
 Tsnghua Unversty at TAC 2009: Summarzng Mult-documents by Informaton Dstance Chong Long, Mnle Huang, Xaoyan Zhu State Key Laboratory of Intellgent Technology and Systems, Tsnghua Natonal Laboratory for
Tsnghua Unversty at TAC 2009: Summarzng Mult-documents by Informaton Dstance Chong Long, Mnle Huang, Xaoyan Zhu State Key Laboratory of Intellgent Technology and Systems, Tsnghua Natonal Laboratory for
Shape-adaptive DCT and Its Application in Region-based Image Coding
 Internatonal Journal of Sgnal Processng, Image Processng and Pattern Recognton, pp.99-108 http://dx.do.org/10.14257/sp.2014.7.1.10 Shape-adaptve DCT and Its Applcaton n Regon-based Image Codng Yamn Zheng,
Internatonal Journal of Sgnal Processng, Image Processng and Pattern Recognton, pp.99-108 http://dx.do.org/10.14257/sp.2014.7.1.10 Shape-adaptve DCT and Its Applcaton n Regon-based Image Codng Yamn Zheng,
Cluster Analysis of Electrical Behavior
 Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
An Image Compression Algorithm based on Wavelet Transform and LZW
 An Image Compresson Algorthm based on Wavelet Transform and LZW Png Luo a, Janyong Yu b School of Chongqng Unversty of Posts and Telecommuncatons, Chongqng, 400065, Chna Abstract a cylpng@63.com, b y27769864@sna.cn
An Image Compresson Algorthm based on Wavelet Transform and LZW Png Luo a, Janyong Yu b School of Chongqng Unversty of Posts and Telecommuncatons, Chongqng, 400065, Chna Abstract a cylpng@63.com, b y27769864@sna.cn
A Secured Method for Image Steganography Based On Pixel Values
 A Secured Method for Image Steganography Based On Pxel Values Tarun Gulat #, Sanskrt Gupta * # Assocate Professor, Electroncs and Communcaton Engneerng Department, MMEC, M.M.U., Mullana, Ambala, Haryana,
A Secured Method for Image Steganography Based On Pxel Values Tarun Gulat #, Sanskrt Gupta * # Assocate Professor, Electroncs and Communcaton Engneerng Department, MMEC, M.M.U., Mullana, Ambala, Haryana,
Article Reversible Dual-Image-Based Hiding Scheme Using Block Folding Technique
 Artcle Reversble Dual-Image-Based Hdng Scheme Usng Block Foldng Technque Tzu-Chuen Lu, * and Hu-Shh Leng Department of Informaton Management, Chaoyang Unversty of Technology, Tachung 4349, Tawan Department
Artcle Reversble Dual-Image-Based Hdng Scheme Usng Block Foldng Technque Tzu-Chuen Lu, * and Hu-Shh Leng Department of Informaton Management, Chaoyang Unversty of Technology, Tachung 4349, Tawan Department
Available online at Available online at Advanced in Control Engineering and Information Science
 Avalable onlne at wwwscencedrectcom Avalable onlne at wwwscencedrectcom Proceda Proceda Engneerng Engneerng 00 (2011) 15000 000 (2011) 1642 1646 Proceda Engneerng wwwelsevercom/locate/proceda Advanced
Avalable onlne at wwwscencedrectcom Avalable onlne at wwwscencedrectcom Proceda Proceda Engneerng Engneerng 00 (2011) 15000 000 (2011) 1642 1646 Proceda Engneerng wwwelsevercom/locate/proceda Advanced
PCA Based Gait Segmentation
 Honggu L, Cupng Sh & Xngguo L PCA Based Gat Segmentaton PCA Based Gat Segmentaton Honggu L, Cupng Sh, and Xngguo L 2 Electronc Department, Physcs College, Yangzhou Unversty, 225002 Yangzhou, Chna 2 Department
Honggu L, Cupng Sh & Xngguo L PCA Based Gat Segmentaton PCA Based Gat Segmentaton Honggu L, Cupng Sh, and Xngguo L 2 Electronc Department, Physcs College, Yangzhou Unversty, 225002 Yangzhou, Chna 2 Department
Specifications in 2001
 Specfcatons n 200 MISTY (updated : May 3, 2002) September 27, 200 Mtsubsh Electrc Corporaton Block Cpher Algorthm MISTY Ths document shows a complete descrpton of encrypton algorthm MISTY, whch are secret-key
Specfcatons n 200 MISTY (updated : May 3, 2002) September 27, 200 Mtsubsh Electrc Corporaton Block Cpher Algorthm MISTY Ths document shows a complete descrpton of encrypton algorthm MISTY, whch are secret-key
A new remote user authentication scheme for multi-server architecture
 Future Generaton Computer Systems 19 (2003) 13 22 A new remote user authentcaton scheme for mult-server archtecture Iuon-Chang Ln a, Mn-Shang Hwang b,, L-Hua L b a Department of Computer Scence and Informaton
Future Generaton Computer Systems 19 (2003) 13 22 A new remote user authentcaton scheme for mult-server archtecture Iuon-Chang Ln a, Mn-Shang Hwang b,, L-Hua L b a Department of Computer Scence and Informaton
Discriminative Dictionary Learning with Pairwise Constraints
 Dscrmnatve Dctonary Learnng wth Parwse Constrants Humn Guo Zhuoln Jang LARRY S. DAVIS UNIVERSITY OF MARYLAND Nov. 6 th, Outlne Introducton/motvaton Dctonary Learnng Dscrmnatve Dctonary Learnng wth Parwse
Dscrmnatve Dctonary Learnng wth Parwse Constrants Humn Guo Zhuoln Jang LARRY S. DAVIS UNIVERSITY OF MARYLAND Nov. 6 th, Outlne Introducton/motvaton Dctonary Learnng Dscrmnatve Dctonary Learnng wth Parwse
Multi-stable Perception. Necker Cube
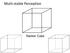 Mult-stable Percepton Necker Cube Spnnng dancer lluson, Nobuuk Kaahara Fttng and Algnment Computer Vson Szelsk 6.1 James Has Acknowledgment: Man sldes from Derek Hoem, Lana Lazebnk, and Grauman&Lebe 2008
Mult-stable Percepton Necker Cube Spnnng dancer lluson, Nobuuk Kaahara Fttng and Algnment Computer Vson Szelsk 6.1 James Has Acknowledgment: Man sldes from Derek Hoem, Lana Lazebnk, and Grauman&Lebe 2008
Cordial and 3-Equitable Labeling for Some Star Related Graphs
 Internatonal Mathematcal Forum, 4, 009, no. 31, 1543-1553 Cordal and 3-Equtable Labelng for Some Star Related Graphs S. K. Vadya Department of Mathematcs, Saurashtra Unversty Rajkot - 360005, Gujarat,
Internatonal Mathematcal Forum, 4, 009, no. 31, 1543-1553 Cordal and 3-Equtable Labelng for Some Star Related Graphs S. K. Vadya Department of Mathematcs, Saurashtra Unversty Rajkot - 360005, Gujarat,
The Research of Support Vector Machine in Agricultural Data Classification
 The Research of Support Vector Machne n Agrcultural Data Classfcaton Le Sh, Qguo Duan, Xnmng Ma, Me Weng College of Informaton and Management Scence, HeNan Agrcultural Unversty, Zhengzhou 45000 Chna Zhengzhou
The Research of Support Vector Machne n Agrcultural Data Classfcaton Le Sh, Qguo Duan, Xnmng Ma, Me Weng College of Informaton and Management Scence, HeNan Agrcultural Unversty, Zhengzhou 45000 Chna Zhengzhou
Enhanced AMBTC for Image Compression using Block Classification and Interpolation
 Internatonal Journal of Computer Applcatons (0975 8887) Volume 5 No.0, August 0 Enhanced AMBTC for Image Compresson usng Block Classfcaton and Interpolaton S. Vmala Dept. of Comp. Scence Mother Teresa
Internatonal Journal of Computer Applcatons (0975 8887) Volume 5 No.0, August 0 Enhanced AMBTC for Image Compresson usng Block Classfcaton and Interpolaton S. Vmala Dept. of Comp. Scence Mother Teresa
Smoothing Spline ANOVA for variable screening
 Smoothng Splne ANOVA for varable screenng a useful tool for metamodels tranng and mult-objectve optmzaton L. Rcco, E. Rgon, A. Turco Outlne RSM Introducton Possble couplng Test case MOO MOO wth Game Theory
Smoothng Splne ANOVA for varable screenng a useful tool for metamodels tranng and mult-objectve optmzaton L. Rcco, E. Rgon, A. Turco Outlne RSM Introducton Possble couplng Test case MOO MOO wth Game Theory
A Modified Median Filter for the Removal of Impulse Noise Based on the Support Vector Machines
 A Modfed Medan Flter for the Removal of Impulse Nose Based on the Support Vector Machnes H. GOMEZ-MORENO, S. MALDONADO-BASCON, F. LOPEZ-FERRERAS, M. UTRILLA- MANSO AND P. GIL-JIMENEZ Departamento de Teoría
A Modfed Medan Flter for the Removal of Impulse Nose Based on the Support Vector Machnes H. GOMEZ-MORENO, S. MALDONADO-BASCON, F. LOPEZ-FERRERAS, M. UTRILLA- MANSO AND P. GIL-JIMENEZ Departamento de Teoría
Identify the Attack in Embedded Image with Steganalysis Detection Method by PSNR and RGB Intensity
 Internatonal Journal of Computer Systems (ISSN: 394-1065), Volume 03 Issue 07, July, 016 Avalable at http://www.jcsonlne.com/ Identfy the Attack n Embedded Image wth Steganalyss Detecton Method by PSNR
Internatonal Journal of Computer Systems (ISSN: 394-1065), Volume 03 Issue 07, July, 016 Avalable at http://www.jcsonlne.com/ Identfy the Attack n Embedded Image wth Steganalyss Detecton Method by PSNR
Reversible Dual-Image-Based Hiding Scheme Using Block Folding Technique
 S S symmetry Artcle Reversble Dual-Image-Based Hdng Scheme Usng Block Foldng Technque Tzu-Chuen Lu Tzu-Chuen Lu 1, 1, * and Hu-Shh Leng * ID and Hu-Shh Leng 1 Department Informaton Management, Chaoyang
S S symmetry Artcle Reversble Dual-Image-Based Hdng Scheme Usng Block Foldng Technque Tzu-Chuen Lu Tzu-Chuen Lu 1, 1, * and Hu-Shh Leng * ID and Hu-Shh Leng 1 Department Informaton Management, Chaoyang
A Hybrid Semi-Blind Gray Scale Image Watermarking Algorithm Based on DWT-SVD using Human Visual System Model
 A Hybrd Sem-Blnd Gray Scale Image Watermarkng Algorthm Based on DWT-SVD usng Human Vsual System Model Rajesh Mehta r Scence & Engneerng, USICT Guru Gobnd Sngh Indrarprastha Unversty New Delh, Inda rajesh00ust@gmal.com
A Hybrd Sem-Blnd Gray Scale Image Watermarkng Algorthm Based on DWT-SVD usng Human Vsual System Model Rajesh Mehta r Scence & Engneerng, USICT Guru Gobnd Sngh Indrarprastha Unversty New Delh, Inda rajesh00ust@gmal.com
Conditional Speculative Decimal Addition*
 Condtonal Speculatve Decmal Addton Alvaro Vazquez and Elsardo Antelo Dep. of Electronc and Computer Engneerng Unv. of Santago de Compostela, Span Ths work was supported n part by Xunta de Galca under grant
Condtonal Speculatve Decmal Addton Alvaro Vazquez and Elsardo Antelo Dep. of Electronc and Computer Engneerng Unv. of Santago de Compostela, Span Ths work was supported n part by Xunta de Galca under grant
An Image Fusion Approach Based on Segmentation Region
 Rong Wang, L-Qun Gao, Shu Yang, Yu-Hua Cha, and Yan-Chun Lu An Image Fuson Approach Based On Segmentaton Regon An Image Fuson Approach Based on Segmentaton Regon Rong Wang, L-Qun Gao, Shu Yang 3, Yu-Hua
Rong Wang, L-Qun Gao, Shu Yang, Yu-Hua Cha, and Yan-Chun Lu An Image Fuson Approach Based On Segmentaton Regon An Image Fuson Approach Based on Segmentaton Regon Rong Wang, L-Qun Gao, Shu Yang 3, Yu-Hua
Computer Generated Integral Imaging (II) System Using Depth-Camera
 Computer Generated Integral Imagng (II) System Usng Depth-Camera Md. Sharful Islam 1, Md. Tarquzzaman 2 1,2 Department of Informaton and Communcaton Engneerng, Islamc Unversty, Kushta-7003, Bangladesh
Computer Generated Integral Imagng (II) System Usng Depth-Camera Md. Sharful Islam 1, Md. Tarquzzaman 2 1,2 Department of Informaton and Communcaton Engneerng, Islamc Unversty, Kushta-7003, Bangladesh
A New Approach For the Ranking of Fuzzy Sets With Different Heights
 New pproach For the ankng of Fuzzy Sets Wth Dfferent Heghts Pushpnder Sngh School of Mathematcs Computer pplcatons Thapar Unversty, Patala-7 00 Inda pushpndersnl@gmalcom STCT ankng of fuzzy sets plays
New pproach For the ankng of Fuzzy Sets Wth Dfferent Heghts Pushpnder Sngh School of Mathematcs Computer pplcatons Thapar Unversty, Patala-7 00 Inda pushpndersnl@gmalcom STCT ankng of fuzzy sets plays
Security Enhanced Dynamic ID based Remote User Authentication Scheme for Multi-Server Environments
 Internatonal Journal of u- and e- ervce, cence and Technology Vol8, o 7 0), pp7-6 http://dxdoorg/07/unesst087 ecurty Enhanced Dynamc ID based Remote ser Authentcaton cheme for ult-erver Envronments Jun-ub
Internatonal Journal of u- and e- ervce, cence and Technology Vol8, o 7 0), pp7-6 http://dxdoorg/07/unesst087 ecurty Enhanced Dynamc ID based Remote ser Authentcaton cheme for ult-erver Envronments Jun-ub
MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION
 MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION Paulo Quntlano 1 & Antono Santa-Rosa 1 Federal Polce Department, Brasla, Brazl. E-mals: quntlano.pqs@dpf.gov.br and
MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION Paulo Quntlano 1 & Antono Santa-Rosa 1 Federal Polce Department, Brasla, Brazl. E-mals: quntlano.pqs@dpf.gov.br and
Loop Permutation. Loop Transformations for Parallelism & Locality. Legality of Loop Interchange. Loop Interchange (cont)
 Loop Transformatons for Parallelsm & Localty Prevously Data dependences and loops Loop transformatons Parallelzaton Loop nterchange Today Loop nterchange Loop transformatons and transformaton frameworks
Loop Transformatons for Parallelsm & Localty Prevously Data dependences and loops Loop transformatons Parallelzaton Loop nterchange Today Loop nterchange Loop transformatons and transformaton frameworks
Collaboratively Regularized Nearest Points for Set Based Recognition
 Academc Center for Computng and Meda Studes, Kyoto Unversty Collaboratvely Regularzed Nearest Ponts for Set Based Recognton Yang Wu, Mchhko Mnoh, Masayuk Mukunok Kyoto Unversty 9/1/013 BMVC 013 @ Brstol,
Academc Center for Computng and Meda Studes, Kyoto Unversty Collaboratvely Regularzed Nearest Ponts for Set Based Recognton Yang Wu, Mchhko Mnoh, Masayuk Mukunok Kyoto Unversty 9/1/013 BMVC 013 @ Brstol,
Loop Transformations for Parallelism & Locality. Review. Scalar Expansion. Scalar Expansion: Motivation
 Loop Transformatons for Parallelsm & Localty Last week Data dependences and loops Loop transformatons Parallelzaton Loop nterchange Today Scalar expanson for removng false dependences Loop nterchange Loop
Loop Transformatons for Parallelsm & Localty Last week Data dependences and loops Loop transformatons Parallelzaton Loop nterchange Today Scalar expanson for removng false dependences Loop nterchange Loop
An efficient method to build panoramic image mosaics
 An effcent method to buld panoramc mage mosacs Pattern Recognton Letters vol. 4 003 Dae-Hyun Km Yong-In Yoon Jong-Soo Cho School of Electrcal Engneerng and Computer Scence Kyungpook Natonal Unv. Abstract
An effcent method to buld panoramc mage mosacs Pattern Recognton Letters vol. 4 003 Dae-Hyun Km Yong-In Yoon Jong-Soo Cho School of Electrcal Engneerng and Computer Scence Kyungpook Natonal Unv. Abstract
6.854 Advanced Algorithms Petar Maymounkov Problem Set 11 (November 23, 2005) With: Benjamin Rossman, Oren Weimann, and Pouya Kheradpour
 6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
Steps for Computing the Dissimilarity, Entropy, Herfindahl-Hirschman and. Accessibility (Gravity with Competition) Indices
 Steps for Computng the Dssmlarty, Entropy, Herfndahl-Hrschman and Accessblty (Gravty wth Competton) Indces I. Dssmlarty Index Measurement: The followng formula can be used to measure the evenness between
Steps for Computng the Dssmlarty, Entropy, Herfndahl-Hrschman and Accessblty (Gravty wth Competton) Indces I. Dssmlarty Index Measurement: The followng formula can be used to measure the evenness between
Human Face Recognition Using Generalized. Kernel Fisher Discriminant
 Human Face Recognton Usng Generalzed Kernel Fsher Dscrmnant ng-yu Sun,2 De-Shuang Huang Ln Guo. Insttute of Intellgent Machnes, Chnese Academy of Scences, P.O.ox 30, Hefe, Anhu, Chna. 2. Department of
Human Face Recognton Usng Generalzed Kernel Fsher Dscrmnant ng-yu Sun,2 De-Shuang Huang Ln Guo. Insttute of Intellgent Machnes, Chnese Academy of Scences, P.O.ox 30, Hefe, Anhu, Chna. 2. Department of
An Optimal Algorithm for Prufer Codes *
 J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
Skew Angle Estimation and Correction of Hand Written, Textual and Large areas of Non-Textual Document Images: A Novel Approach
 Angle Estmaton and Correcton of Hand Wrtten, Textual and Large areas of Non-Textual Document Images: A Novel Approach D.R.Ramesh Babu Pyush M Kumat Mahesh D Dhannawat PES Insttute of Technology Research
Angle Estmaton and Correcton of Hand Wrtten, Textual and Large areas of Non-Textual Document Images: A Novel Approach D.R.Ramesh Babu Pyush M Kumat Mahesh D Dhannawat PES Insttute of Technology Research
Lecture 5: Multilayer Perceptrons
 Lecture 5: Multlayer Perceptrons Roger Grosse 1 Introducton So far, we ve only talked about lnear models: lnear regresson and lnear bnary classfers. We noted that there are functons that can t be represented
Lecture 5: Multlayer Perceptrons Roger Grosse 1 Introducton So far, we ve only talked about lnear models: lnear regresson and lnear bnary classfers. We noted that there are functons that can t be represented
Dynamic wetting property investigation of AFM tips in micro/nanoscale
 Dynamc wettng property nvestgaton of AFM tps n mcro/nanoscale The wettng propertes of AFM probe tps are of concern n AFM tp related force measurement, fabrcaton, and manpulaton technques, such as dp-pen
Dynamc wettng property nvestgaton of AFM tps n mcro/nanoscale The wettng propertes of AFM probe tps are of concern n AFM tp related force measurement, fabrcaton, and manpulaton technques, such as dp-pen
Kent State University CS 4/ Design and Analysis of Algorithms. Dept. of Math & Computer Science LECT-16. Dynamic Programming
 CS 4/560 Desgn and Analyss of Algorthms Kent State Unversty Dept. of Math & Computer Scence LECT-6 Dynamc Programmng 2 Dynamc Programmng Dynamc Programmng, lke the dvde-and-conquer method, solves problems
CS 4/560 Desgn and Analyss of Algorthms Kent State Unversty Dept. of Math & Computer Scence LECT-6 Dynamc Programmng 2 Dynamc Programmng Dynamc Programmng, lke the dvde-and-conquer method, solves problems
High-Boost Mesh Filtering for 3-D Shape Enhancement
 Hgh-Boost Mesh Flterng for 3-D Shape Enhancement Hrokazu Yagou Λ Alexander Belyaev y Damng We z Λ y z ; ; Shape Modelng Laboratory, Unversty of Azu, Azu-Wakamatsu 965-8580 Japan y Computer Graphcs Group,
Hgh-Boost Mesh Flterng for 3-D Shape Enhancement Hrokazu Yagou Λ Alexander Belyaev y Damng We z Λ y z ; ; Shape Modelng Laboratory, Unversty of Azu, Azu-Wakamatsu 965-8580 Japan y Computer Graphcs Group,
Using Fuzzy Logic to Enhance the Large Size Remote Sensing Images
 Internatonal Journal of Informaton and Electroncs Engneerng Vol. 5 No. 6 November 015 Usng Fuzzy Logc to Enhance the Large Sze Remote Sensng Images Trung Nguyen Tu Huy Ngo Hoang and Thoa Vu Van Abstract
Internatonal Journal of Informaton and Electroncs Engneerng Vol. 5 No. 6 November 015 Usng Fuzzy Logc to Enhance the Large Sze Remote Sensng Images Trung Nguyen Tu Huy Ngo Hoang and Thoa Vu Van Abstract
FEATURE EXTRACTION. Dr. K.Vijayarekha. Associate Dean School of Electrical and Electronics Engineering SASTRA University, Thanjavur
 FEATURE EXTRACTION Dr. K.Vjayarekha Assocate Dean School of Electrcal and Electroncs Engneerng SASTRA Unversty, Thanjavur613 41 Jont Intatve of IITs and IISc Funded by MHRD Page 1 of 8 Table of Contents
FEATURE EXTRACTION Dr. K.Vjayarekha Assocate Dean School of Electrcal and Electroncs Engneerng SASTRA Unversty, Thanjavur613 41 Jont Intatve of IITs and IISc Funded by MHRD Page 1 of 8 Table of Contents
Data Hiding and Image Authentication for Color-Palette Images
 Data Hdng and Image Authentcaton for Color-Palette Images Chh-Yang Yn ( 殷志揚 ) and Wen-Hsang Tsa ( 蔡文祥 ) Department of Computer & Informaton Scence Natonal Chao Tung Unversty 00 Ta Hsueh Rd., Hsnchu, Tawan
Data Hdng and Image Authentcaton for Color-Palette Images Chh-Yang Yn ( 殷志揚 ) and Wen-Hsang Tsa ( 蔡文祥 ) Department of Computer & Informaton Scence Natonal Chao Tung Unversty 00 Ta Hsueh Rd., Hsnchu, Tawan
Semi-Fragile Watermarking Scheme for Authentication of JPEG Images
 Tamkang Journal of Scence and Engneerng, Vol. 10, No 1, pp. 5766 (2007) 57 Sem-Fragle Watermarkng Scheme for Authentcaton of JPEG Images Chh-Hung n 1 *, Tung-Shh Su 2 and Wen-Shyong Hseh 2,3 1 Department
Tamkang Journal of Scence and Engneerng, Vol. 10, No 1, pp. 5766 (2007) 57 Sem-Fragle Watermarkng Scheme for Authentcaton of JPEG Images Chh-Hung n 1 *, Tung-Shh Su 2 and Wen-Shyong Hseh 2,3 1 Department
Classifier Selection Based on Data Complexity Measures *
 Classfer Selecton Based on Data Complexty Measures * Edth Hernández-Reyes, J.A. Carrasco-Ochoa, and J.Fco. Martínez-Trndad Natonal Insttute for Astrophyscs, Optcs and Electroncs, Lus Enrque Erro No.1 Sta.
Classfer Selecton Based on Data Complexty Measures * Edth Hernández-Reyes, J.A. Carrasco-Ochoa, and J.Fco. Martínez-Trndad Natonal Insttute for Astrophyscs, Optcs and Electroncs, Lus Enrque Erro No.1 Sta.
Subspace clustering. Clustering. Fundamental to all clustering techniques is the choice of distance measure between data points;
 Subspace clusterng Clusterng Fundamental to all clusterng technques s the choce of dstance measure between data ponts; D q ( ) ( ) 2 x x = x x, j k = 1 k jk Squared Eucldean dstance Assumpton: All features
Subspace clusterng Clusterng Fundamental to all clusterng technques s the choce of dstance measure between data ponts; D q ( ) ( ) 2 x x = x x, j k = 1 k jk Squared Eucldean dstance Assumpton: All features
Face Detection with Deep Learning
 Face Detecton wth Deep Learnng Yu Shen Yus122@ucsd.edu A13227146 Kuan-We Chen kuc010@ucsd.edu A99045121 Yzhou Hao y3hao@ucsd.edu A98017773 Mn Hsuan Wu mhwu@ucsd.edu A92424998 Abstract The project here
Face Detecton wth Deep Learnng Yu Shen Yus122@ucsd.edu A13227146 Kuan-We Chen kuc010@ucsd.edu A99045121 Yzhou Hao y3hao@ucsd.edu A98017773 Mn Hsuan Wu mhwu@ucsd.edu A92424998 Abstract The project here
A New Feature of Uniformity of Image Texture Directions Coinciding with the Human Eyes Perception 1
 A New Feature of Unformty of Image Texture Drectons Concdng wth the Human Eyes Percepton Xng-Jan He, De-Shuang Huang, Yue Zhang, Tat-Mng Lo 2, and Mchael R. Lyu 3 Intellgent Computng Lab, Insttute of Intellgent
A New Feature of Unformty of Image Texture Drectons Concdng wth the Human Eyes Percepton Xng-Jan He, De-Shuang Huang, Yue Zhang, Tat-Mng Lo 2, and Mchael R. Lyu 3 Intellgent Computng Lab, Insttute of Intellgent
Fuzzy Filtering Algorithms for Image Processing: Performance Evaluation of Various Approaches
 Proceedngs of the Internatonal Conference on Cognton and Recognton Fuzzy Flterng Algorthms for Image Processng: Performance Evaluaton of Varous Approaches Rajoo Pandey and Umesh Ghanekar Department of
Proceedngs of the Internatonal Conference on Cognton and Recognton Fuzzy Flterng Algorthms for Image Processng: Performance Evaluaton of Varous Approaches Rajoo Pandey and Umesh Ghanekar Department of
Optimal Workload-based Weighted Wavelet Synopses
 Optmal Workload-based Weghted Wavelet Synopses Yoss Matas School of Computer Scence Tel Avv Unversty Tel Avv 69978, Israel matas@tau.ac.l Danel Urel School of Computer Scence Tel Avv Unversty Tel Avv 69978,
Optmal Workload-based Weghted Wavelet Synopses Yoss Matas School of Computer Scence Tel Avv Unversty Tel Avv 69978, Israel matas@tau.ac.l Danel Urel School of Computer Scence Tel Avv Unversty Tel Avv 69978,
A Clustering Algorithm for Chinese Adjectives and Nouns 1
 Clusterng lgorthm for Chnese dectves and ouns Yang Wen, Chunfa Yuan, Changnng Huang 2 State Key aboratory of Intellgent Technology and System Deptartment of Computer Scence & Technology, Tsnghua Unversty,
Clusterng lgorthm for Chnese dectves and ouns Yang Wen, Chunfa Yuan, Changnng Huang 2 State Key aboratory of Intellgent Technology and System Deptartment of Computer Scence & Technology, Tsnghua Unversty,
Local Quaternary Patterns and Feature Local Quaternary Patterns
 Local Quaternary Patterns and Feature Local Quaternary Patterns Jayu Gu and Chengjun Lu The Department of Computer Scence, New Jersey Insttute of Technology, Newark, NJ 0102, USA Abstract - Ths paper presents
Local Quaternary Patterns and Feature Local Quaternary Patterns Jayu Gu and Chengjun Lu The Department of Computer Scence, New Jersey Insttute of Technology, Newark, NJ 0102, USA Abstract - Ths paper presents
A high precision collaborative vision measurement of gear chamfering profile
 Internatonal Conference on Advances n Mechancal Engneerng and Industral Informatcs (AMEII 05) A hgh precson collaboratve vson measurement of gear chamferng profle Conglng Zhou, a, Zengpu Xu, b, Chunmng
Internatonal Conference on Advances n Mechancal Engneerng and Industral Informatcs (AMEII 05) A hgh precson collaboratve vson measurement of gear chamferng profle Conglng Zhou, a, Zengpu Xu, b, Chunmng
Sum of Linear and Fractional Multiobjective Programming Problem under Fuzzy Rules Constraints
 Australan Journal of Basc and Appled Scences, 2(4): 1204-1208, 2008 ISSN 1991-8178 Sum of Lnear and Fractonal Multobjectve Programmng Problem under Fuzzy Rules Constrants 1 2 Sanjay Jan and Kalash Lachhwan
Australan Journal of Basc and Appled Scences, 2(4): 1204-1208, 2008 ISSN 1991-8178 Sum of Lnear and Fractonal Multobjectve Programmng Problem under Fuzzy Rules Constrants 1 2 Sanjay Jan and Kalash Lachhwan
The Research of Ellipse Parameter Fitting Algorithm of Ultrasonic Imaging Logging in the Casing Hole
 Appled Mathematcs, 04, 5, 37-3 Publshed Onlne May 04 n ScRes. http://www.scrp.org/journal/am http://dx.do.org/0.436/am.04.584 The Research of Ellpse Parameter Fttng Algorthm of Ultrasonc Imagng Loggng
Appled Mathematcs, 04, 5, 37-3 Publshed Onlne May 04 n ScRes. http://www.scrp.org/journal/am http://dx.do.org/0.436/am.04.584 The Research of Ellpse Parameter Fttng Algorthm of Ultrasonc Imagng Loggng
Simulation Based Analysis of FAST TCP using OMNET++
 Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
R s s f. m y s. SPH3UW Unit 7.3 Spherical Concave Mirrors Page 1 of 12. Notes
 SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
Integrated Expression-Invariant Face Recognition with Constrained Optical Flow
 Integrated Expresson-Invarant Face Recognton wth Constraned Optcal Flow Chao-Kue Hseh, Shang-Hong La 2, and Yung-Chang Chen Department of Electrcal Engneerng, Natonal Tsng Hua Unversty, Tawan 2 Department
Integrated Expresson-Invarant Face Recognton wth Constraned Optcal Flow Chao-Kue Hseh, Shang-Hong La 2, and Yung-Chang Chen Department of Electrcal Engneerng, Natonal Tsng Hua Unversty, Tawan 2 Department
A Five-Point Subdivision Scheme with Two Parameters and a Four-Point Shape-Preserving Scheme
 Mathematcal and Computatonal Applcatons Artcle A Fve-Pont Subdvson Scheme wth Two Parameters and a Four-Pont Shape-Preservng Scheme Jeqng Tan,2, Bo Wang, * and Jun Sh School of Mathematcs, Hefe Unversty
Mathematcal and Computatonal Applcatons Artcle A Fve-Pont Subdvson Scheme wth Two Parameters and a Four-Pont Shape-Preservng Scheme Jeqng Tan,2, Bo Wang, * and Jun Sh School of Mathematcs, Hefe Unversty
A NOTE ON FUZZY CLOSURE OF A FUZZY SET
 (JPMNT) Journal of Process Management New Technologes, Internatonal A NOTE ON FUZZY CLOSURE OF A FUZZY SET Bhmraj Basumatary Department of Mathematcal Scences, Bodoland Unversty, Kokrajhar, Assam, Inda,
(JPMNT) Journal of Process Management New Technologes, Internatonal A NOTE ON FUZZY CLOSURE OF A FUZZY SET Bhmraj Basumatary Department of Mathematcal Scences, Bodoland Unversty, Kokrajhar, Assam, Inda,
Load-Balanced Anycast Routing
 Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Joint Example-based Depth Map Super-Resolution
 Jont Example-based Depth Map Super-Resoluton Yanje L 1, Tanfan Xue,3, Lfeng Sun 1, Janzhuang Lu,3,4 1 Informaton Scence and Technology Department, Tsnghua Unversty, Bejng, Chna Department of Informaton
Jont Example-based Depth Map Super-Resoluton Yanje L 1, Tanfan Xue,3, Lfeng Sun 1, Janzhuang Lu,3,4 1 Informaton Scence and Technology Department, Tsnghua Unversty, Bejng, Chna Department of Informaton
A Novel Adaptive Descriptor Algorithm for Ternary Pattern Textures
 A Novel Adaptve Descrptor Algorthm for Ternary Pattern Textures Fahuan Hu 1,2, Guopng Lu 1 *, Zengwen Dong 1 1.School of Mechancal & Electrcal Engneerng, Nanchang Unversty, Nanchang, 330031, Chna; 2. School
A Novel Adaptve Descrptor Algorthm for Ternary Pattern Textures Fahuan Hu 1,2, Guopng Lu 1 *, Zengwen Dong 1 1.School of Mechancal & Electrcal Engneerng, Nanchang Unversty, Nanchang, 330031, Chna; 2. School
A Simple and Efficient Goal Programming Model for Computing of Fuzzy Linear Regression Parameters with Considering Outliers
 62626262621 Journal of Uncertan Systems Vol.5, No.1, pp.62-71, 211 Onlne at: www.us.org.u A Smple and Effcent Goal Programmng Model for Computng of Fuzzy Lnear Regresson Parameters wth Consderng Outlers
62626262621 Journal of Uncertan Systems Vol.5, No.1, pp.62-71, 211 Onlne at: www.us.org.u A Smple and Effcent Goal Programmng Model for Computng of Fuzzy Lnear Regresson Parameters wth Consderng Outlers
Hermite Splines in Lie Groups as Products of Geodesics
 Hermte Splnes n Le Groups as Products of Geodescs Ethan Eade Updated May 28, 2017 1 Introducton 1.1 Goal Ths document defnes a curve n the Le group G parametrzed by tme and by structural parameters n the
Hermte Splnes n Le Groups as Products of Geodescs Ethan Eade Updated May 28, 2017 1 Introducton 1.1 Goal Ths document defnes a curve n the Le group G parametrzed by tme and by structural parameters n the
Learning-Based Top-N Selection Query Evaluation over Relational Databases
 Learnng-Based Top-N Selecton Query Evaluaton over Relatonal Databases Lang Zhu *, Wey Meng ** * School of Mathematcs and Computer Scence, Hebe Unversty, Baodng, Hebe 071002, Chna, zhu@mal.hbu.edu.cn **
Learnng-Based Top-N Selecton Query Evaluaton over Relatonal Databases Lang Zhu *, Wey Meng ** * School of Mathematcs and Computer Scence, Hebe Unversty, Baodng, Hebe 071002, Chna, zhu@mal.hbu.edu.cn **
Some Tutorial about the Project. Computer Graphics
 Some Tutoral about the Project Lecture 6 Rastersaton, Antalasng, Texture Mappng, I have already covered all the topcs needed to fnsh the 1 st practcal Today, I wll brefly explan how to start workng on
Some Tutoral about the Project Lecture 6 Rastersaton, Antalasng, Texture Mappng, I have already covered all the topcs needed to fnsh the 1 st practcal Today, I wll brefly explan how to start workng on
ON SOME ENTERTAINING APPLICATIONS OF THE CONCEPT OF SET IN COMPUTER SCIENCE COURSE
 Yordzhev K., Kostadnova H. Інформаційні технології в освіті ON SOME ENTERTAINING APPLICATIONS OF THE CONCEPT OF SET IN COMPUTER SCIENCE COURSE Yordzhev K., Kostadnova H. Some aspects of programmng educaton
Yordzhev K., Kostadnova H. Інформаційні технології в освіті ON SOME ENTERTAINING APPLICATIONS OF THE CONCEPT OF SET IN COMPUTER SCIENCE COURSE Yordzhev K., Kostadnova H. Some aspects of programmng educaton
For instance, ; the five basic number-sets are increasingly more n A B & B A A = B (1)
 Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
Learning a Class-Specific Dictionary for Facial Expression Recognition
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 16, No 4 Sofa 016 Prnt ISSN: 1311-970; Onlne ISSN: 1314-4081 DOI: 10.1515/cat-016-0067 Learnng a Class-Specfc Dctonary for
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 16, No 4 Sofa 016 Prnt ISSN: 1311-970; Onlne ISSN: 1314-4081 DOI: 10.1515/cat-016-0067 Learnng a Class-Specfc Dctonary for
SCALABLE AND VISUALIZATION-ORIENTED CLUSTERING FOR EXPLORATORY SPATIAL ANALYSIS
 SCALABLE AND VISUALIZATION-ORIENTED CLUSTERING FOR EXPLORATORY SPATIAL ANALYSIS J.H.Guan, F.B.Zhu, F.L.Ban a School of Computer, Spatal Informaton & Dgtal Engneerng Center, Wuhan Unversty, Wuhan, 430079,
SCALABLE AND VISUALIZATION-ORIENTED CLUSTERING FOR EXPLORATORY SPATIAL ANALYSIS J.H.Guan, F.B.Zhu, F.L.Ban a School of Computer, Spatal Informaton & Dgtal Engneerng Center, Wuhan Unversty, Wuhan, 430079,
The Greedy Method. Outline and Reading. Change Money Problem. Greedy Algorithms. Applications of the Greedy Strategy. The Greedy Method Technique
 //00 :0 AM Outlne and Readng The Greedy Method The Greedy Method Technque (secton.) Fractonal Knapsack Problem (secton..) Task Schedulng (secton..) Mnmum Spannng Trees (secton.) Change Money Problem Greedy
//00 :0 AM Outlne and Readng The Greedy Method The Greedy Method Technque (secton.) Fractonal Knapsack Problem (secton..) Task Schedulng (secton..) Mnmum Spannng Trees (secton.) Change Money Problem Greedy
FRACTAL COMPRESSION TECHNIQUE FOR COLOR IMAGES USING VARIABLE BLOCK
 ISSN: 0976-910 (ONLINE) ICTACT JOURNAL ON IMAGE AND VIDEO PROCESSING, NOVEMBER 017, VOLUME: 08, ISSUE: 0 DOI: 10.1917/jvp.017.030 FRACTAL COMPRESSION TECHNIQUE FOR COLOR IMAGES USING VARIABLE BLOCK Nsar
ISSN: 0976-910 (ONLINE) ICTACT JOURNAL ON IMAGE AND VIDEO PROCESSING, NOVEMBER 017, VOLUME: 08, ISSUE: 0 DOI: 10.1917/jvp.017.030 FRACTAL COMPRESSION TECHNIQUE FOR COLOR IMAGES USING VARIABLE BLOCK Nsar
An Efficient Genetic Algorithm with Fuzzy c-means Clustering for Traveling Salesman Problem
 An Effcent Genetc Algorthm wth Fuzzy c-means Clusterng for Travelng Salesman Problem Jong-Won Yoon and Sung-Bae Cho Dept. of Computer Scence Yonse Unversty Seoul, Korea jwyoon@sclab.yonse.ac.r, sbcho@cs.yonse.ac.r
An Effcent Genetc Algorthm wth Fuzzy c-means Clusterng for Travelng Salesman Problem Jong-Won Yoon and Sung-Bae Cho Dept. of Computer Scence Yonse Unversty Seoul, Korea jwyoon@sclab.yonse.ac.r, sbcho@cs.yonse.ac.r
A Robust Webpage Information Hiding Method Based on the Slash of Tag
 Advanced Engneerng Forum Onlne: 2012-09-26 ISSN: 2234-991X, Vols. 6-7, pp 361-366 do:10.4028/www.scentfc.net/aef.6-7.361 2012 Trans Tech Publcatons, Swtzerland A Robust Webpage Informaton Hdng Method Based
Advanced Engneerng Forum Onlne: 2012-09-26 ISSN: 2234-991X, Vols. 6-7, pp 361-366 do:10.4028/www.scentfc.net/aef.6-7.361 2012 Trans Tech Publcatons, Swtzerland A Robust Webpage Informaton Hdng Method Based
Solving two-person zero-sum game by Matlab
 Appled Mechancs and Materals Onlne: 2011-02-02 ISSN: 1662-7482, Vols. 50-51, pp 262-265 do:10.4028/www.scentfc.net/amm.50-51.262 2011 Trans Tech Publcatons, Swtzerland Solvng two-person zero-sum game by
Appled Mechancs and Materals Onlne: 2011-02-02 ISSN: 1662-7482, Vols. 50-51, pp 262-265 do:10.4028/www.scentfc.net/amm.50-51.262 2011 Trans Tech Publcatons, Swtzerland Solvng two-person zero-sum game by
Priority-Based Scheduling Algorithm for Downlink Traffics in IEEE Networks
 Prorty-Based Schedulng Algorthm for Downlnk Traffcs n IEEE 80.6 Networks Ja-Mng Lang, Jen-Jee Chen, You-Chun Wang, Yu-Chee Tseng, and Bao-Shuh P. Ln Department of Computer Scence Natonal Chao-Tung Unversty,
Prorty-Based Schedulng Algorthm for Downlnk Traffcs n IEEE 80.6 Networks Ja-Mng Lang, Jen-Jee Chen, You-Chun Wang, Yu-Chee Tseng, and Bao-Shuh P. Ln Department of Computer Scence Natonal Chao-Tung Unversty,
On Some Entertaining Applications of the Concept of Set in Computer Science Course
 On Some Entertanng Applcatons of the Concept of Set n Computer Scence Course Krasmr Yordzhev *, Hrstna Kostadnova ** * Assocate Professor Krasmr Yordzhev, Ph.D., Faculty of Mathematcs and Natural Scences,
On Some Entertanng Applcatons of the Concept of Set n Computer Scence Course Krasmr Yordzhev *, Hrstna Kostadnova ** * Assocate Professor Krasmr Yordzhev, Ph.D., Faculty of Mathematcs and Natural Scences,
