Watermarking 2D Vector Maps in the Mesh-Spectral Domain
|
|
|
- Kathlyn Wilkins
- 5 years ago
- Views:
Transcription
1 Watermarkng 2D Vector Maps n the Mesh-Spectral Doman 1 Ryutarou Ohbuch, 1 Hroo Ueda, 2 Shuh Endoh ohbuch@acm.org, k7026@kk.yamanash.ac.p, endoshu@p.bm.com 1 Computer Scence Department, Unversty of Yamanash Takeda, Kofu-sh, Yamanash-ken, , Japan. 2 GIS Busness Promoton, IBM Japan. Abstract Ths paper proposes a dgtal watermarkng algorthm for 2D vector dgtal maps. The watermark s a robust, nformed-detecton watermark to be used to prevent such abuses as an ntellectual property rghts volaton. The algorthm proposed n ths paper embeds watermarks n the frequency-doman representaton of a 2D vector dgtal map. Our method treats vertces n the map as a pont set, and mposes connectvty among the ponts by usng Delaunay trangulaton. The method then computes the mesh-spectral coeffcents [Karn00] from the mesh created. Modfcatons of the coeffcents accordng to the message bts, and nverse transformng the coeffcents back nto the coordnate doman produces the watermarked map. Our evaluaton experments showed that the watermark produced by the method s resstant aganst addtve random nose, smlarty transformaton, vertex nserton and removal. It s also resstant, to some extent, aganst croppng. Compared to our prevous algorthm [Ohbuch02], the algorthm descrbed n ths paper showed sgnfcantly mproved attack reslency. 1. Introducton Applcatons of dgtal maps have been ncreasng rapdly. They are used, for example, n car navgaton systems, locaton-based servces for cellular phones wth GPS (Global Postonng System) capablty, web-based map servces, and n geographcal nformaton systems (GIS) for cty plannng or dsaster management. Dgtal maps are easy to update, duplcate, and dstrbute. As a dgtal data, dgtal maps are very easy to update, duplcate, and dstrbute. They are also prone to such abuses as llegal duplcaton and llegal dstrbuton. Geographcal maps may be publshed by a government agency and shared (wth fees) among map producng companes. Map companes add value to the base maps. For example, a car-navgaton map should have up-to-date buldng postons, road and buldng outlnes, buldng ownershp, road sgns, busness and shop data (e.g., gas statons, hotels, and convenence stores), all of whch are the result of the work whch s often human-resource ntensve. Dgtal watermarkng s a possble approach to counter abuses of dgtal meda data, such as texts, audo data, mages, moves, as well as 2D dgtal maps [16, 6, 12]. Dgtal watermarkng adds a structure called watermark to the target data obect (mostly) mperceptbly to the users and nseparably from the obect. The nformaton encoded n the watermark can be used, for example, to dentfy the copyrght owner or to detect tamperng. Two-dmensonal (2D) dgtal maps can be classfed nto ether raster- or vector-dgtal maps (Fgure 1). A raster dgtal map represents a map as raster mage data,.e., an mage represented by a 2D array of pxels. A lmtaton of raster dgtal maps s qualty degradaton caused by rotaton, scalng, and other geometrcal transformatons. Many web-based map servces uses raster dgtal maps exactly for ths reason; raster dgtal maps havng lmted resoluton have a lmted value for reuse or redstrbuton. As an mage data, most of the watermarkng algorthm developed for dgtal mages [16, 6, 12] can be appled to the raster dgtal map. A vector dgtal map, on the other hand, employs geometrcal prmtves such as ponts, lnes, polylnes, and polygons to represent obects n the maps, such as buldng outlnes, roads, rvers, reference ponts for strngs, and contour CS dept. Fgure 1. Raster (left) and vector (rght) dgtal maps. 1
2 lnes. Unlke the raster dgtal maps, the vector dgtal maps have an advantage of beng able to be scaled and rotated wthout loss of qualty. Ths advantage, on the other hand, makes a vector dgtal map a more valuable target for theft than an mage dgtal map. Ths paper presents a robust, nformed-detecton watermarkng algorthm for 2D vector dgtal maps. The watermarkng algorthm treats vertces n the map as a pont set, and creates a 2D mesh out of the pont set by usng Delaunay trangulaton. The algorthm then transforms the mesh shape nto a frequency doman representaton by usng the mesh spectral analyss technque proposed by Karn et al [14, 15]. The algorthm modfes the most sgnfcant, that s, the low-frequency coeffcents to encode watermark message bts. An nverse transformaton back nto the spatal doman creates a watermarked map. Experments showed that the watermark produced by the method s resstant aganst (1) addtve random nose, (2) global Affne transformaton, (3) vertex nserton and deleton, and (4) scramblng of obect orders n the fle. It s also resstant, to a certan extent, aganst (5) croppng. The method s mldly resstant to local deformatons as well. Compared to our prevous algorthm [22], the algorthm descrbed n ths paper showed sgnfcantly mproved attack reslency. The rest of the paper s organzed as follows. After revewng prevous work n the next secton, we wll present our watermarkng algorthm Secton 2. We then descrbe the results of evaluaton experments n Secton 3, followed by a concluson and future work n Secton Prevous Work We know of only a few publshed works on watermarkng vector dgtal maps [18, 17, 10]. Kurhara et al [18] encoded nformaton nto ndvdual vertex coordnate, and ther watermarks are qute fragle, among others, aganst addtve random nose. Endoh, Masuda, Kana, and Ohbuch collaboratvely developed nearly a dozen algorthms to watermark vector dgtal maps [10]. These watermarkng methods are avalable as a part of the GIS map development toolkt. These watermarkng methods targeted ether vertex coordnate or vertex connectvty for watermarkng. Ktamura et al reported, n detal, one of the algorthms developed by the collaboraton [17]. In the Ktamura s method, a vector dgtal map s converted nto a 2D array of scalar values,.e., a raster mage. They subdvded the dgtal map unformly nto a rectangular grd, and treated each rectangle of the grd as a pxel of a raster mage. As the pxel value of the mages, they used the average of the areas of buldngs defned by polygons that fall nsde each rectangular pxel. The mage s then watermarked by usng a method smlar to a wavelet-based magewatermarkng algorthm. We have prevously reported a watermarkng algorthm for 2D vector dgtal maps [22]. The algorthm used a smple dea of translatng a set of vertces n a unformly subdvded rectangular regon for embeddng a message bt. The drecton of translaton of the set of vertces n a rectangle encoded a bt of the watermark message. The algorthm employed modfed quad-tree [27] subdvson to create the rectangles adaptvely to the densty of vertces. A depth-frst traversal of the quad tree created an orderng among the pxels. By averagng the dsplacement of the vertces upon extracton, and by repeatedly embeddng the same message many tmes over a map, the watermarks produced by the method are resstant aganst addtve random nose, As a watermarkng target, a three-dmensonal (3D) polygonal mesh s somewhat smlar to a 2D vector map; both are defned as a set of vertces (wth ether 2D or 3D coordnate values) and ther connectvty. There are algorthms for watermarkng 3D meshes [19, 20, 13, 1, 29, 24, 28, 32, 30, 5, 23]. These algorthms alter ether vertex coordnate or vertex connectvty of the meshes for watermarkng. Many of the recent 3D mesh watermarkng methods employed transformed-doman approaches to watermarkng [13, 24, 21, 30, 5, 23]. A method n ths class would transform the mesh nto a doman that reflects the noton of frequency and modfy the most sgnfcant, low frequency components of the mesh shape to embed watermark messages. By modfyng the low frequency component, the watermarks embedded by usng these frequency-doman technques are resstant aganst addtve random nose, mesh smoothng (.e., low-pass flterng), and other attacks. Our ntal deas queston was f we could apply technques developed for 3D polygonal meshes to watermarkng 2D vector dgtal maps. Of course, there are dfferences between 2D vector dgtal maps and 3D polygonal meshes, one of whch s the relatve ease of pose normalzaton. One of the maor dffcultes n watermarkng 3D meshes s that of pose normalzaton, that s, normalzaton of the poston, sze, and orentaton of the orgnal and watermarked 3D meshes. Pose normalzaton of a 3D model s qute 2
3 dffcult f mesh smplfcaton or remeshng has been appled n addton to geometrcal transformaton. In the case of the 2D vector maps, however, pose normalzaton s relatvely easy. A reference map to algn a watermarked map aganst can be found most of the tme, so the scale and the orentaton of the watermarked map can be normalzed easly. In the algorthm reported n ths paper, we adopted the frequency doman mesh watermarkng approach of [21, 23]. We also explot a characterstc of 2D vector dgtal maps, namely, the ease of pose normalzaton, n developng our robust, nformed-detecton watermarkng algorthm for 2D vector dgtal maps descrbed n ths paper. 2. The algorthm Our watermarkng algorthm embeds message bts nto a 2D vector dgtal map by modfyng a frequency doman representaton of the map. Fgure 2 shows an overvew of the embeddng and extracton steps. To compute the frequency doman representaton, the algorthm frst establshes connectvty among vertces of the map by usng Delaunay trangulaton, creatng a 2D mesh that covers every vertex n the map. The mesh s then transformed nto a frequency doman representaton by usng mesh spectral analyss proposed by Karn and others [14, 15]. Modfcaton of the frequency doman coeffcents accordng to the message bts embeds a watermark. Inverse transformng the modfed coeffcent back nto the coordnate doman produces a map wth the watermark embedded. The modfcaton of coeffcents n the frequency doman ultmately dsplaces vertex coordnates n the spatal doman. For computatonal effcency and for robustness aganst croppng, a map s frst dvded nto many rectangular subareas. We employed the k-d tree subdvson [9, 27] adaptvely to the densty of vertces n the map so that sub-areas have approxmately equal numbers of vertces. Aforementoned mesh spectral analyss and watermark embeddng s performed for each of the sub-areas. By embeddng the same watermark repeatedly n multple sub-areas, the watermark becomes reslent aganst croppng. The watermark s reslent aganst random nose and other attacks snce the watermark s embedded nto the low frequency component of the mesh verson of the map. The watermark s an nformed- (or non-blnd-) detecton watermark. Watermarks are extracted by Embeddng Reference map M Delaunay meshng Patch generaton Spectral analyss Modulaton Spectral synthess Watermarked map ˆM Watermark message Extracton Reference Watermarked map M map ˆM Pose normalzaton Vertex matchng Delaunay meshng Patch generaton Spectral analyss Demodulaton Watermark message Fgure 2. An overvew of the watermark embeddng and extracton steps. comparng the reference map (the map before watermarkng, whch may be escrowed) wth the watermarked and possbly attacked watermark map. To extract the watermark, the two maps are frst geometrcally regstered by usng an teratve optmzaton process to mnmze dstance among a set of landmarks. Ths regstraton could remove an Affne transformaton appled to the watermarked map. Then, the area subdvson equal to the one used for the embeddng s recreated on the reference map, and the subdvson s transferred to the watermarked map. For each correspondng sub-area, mesh spectral analyss and then comparson of spectral coeffcents recovers the embedded watermark. 3
4 2.1. Embeddng Meshng and area subdvson A vector dgtal map s a collecton of polygons and polylnes that are not connected to each other. We frst connect all the vertces nto a sngle mesh by usng Delaunay trangulaton [9]. Fgure 3a shows a vector dgtal map and ts Delaunay mesh s shown n Fgure 3b. The algorthm then creates multple rectangular submeshes, called watermarkng patches. The purpose of subdvson nto watermarkng patches are twofold; (1) to ncrease reslency aganst croppng attacks by repeatedly embeddng the same watermark nto multple patches of a map, and (2) to reduce computatonal cost of egenanalyss, the core of the mesh spectral analyss, by reducng the mesh sze. The patches generated should contan roughly equal number of vertces, and that the number of vertces must exceed certan threshold to ensure the payload (.e., the amount of watermark message bts embeddable.) We employed k-d tree [9, 27] to adaptvely subdvde the mesh nto patches of roughly equal vertex counts. An example of the patches generated by ths technque s shown n Fgure 3c, overlad on the orgnal map Spectral analyss (a) Orgnal map. (b) Vertces of the map to the left are Delaunay trangulated. Mesh spectral analyss has been ntroduced by Karn and Gotsman to analyze shapes of 3D polygonal mesh models for compressng ther geometry [14, 15]. Ohbuch et al. [21, 23], and later, Cayre et al [5], appled the technque for watermarkng 3D polygonal meshes n the frequency or mesh spectral doman. We borrow the technque for watermarkng 2D vector dgtal maps by convertng the maps nto 2D meshes pror to watermarkng. There are several dfferent mesh Laplacan matrces [4, 3, 8]. We employ Bggs defnton of mesh Laplacan R for the algorthm descrbed n ths paper. R = I HA (1) In the formula, I s the dentty matrx and H s a dagonal matrx whose dagonal element H = 1 d s the recprocal of the degree (or valence) of the vertex. A s the adacency matrx whose elements are defned as below; 1, f vertces and are adacent; a = (2) 0, otherwse. Fgure 4a shows a smple mesh and Fgure 4b shows ts Laplacan matrx. A polygonal mesh M havng n vertces yelds a Laplacan matrx R of sze n n. Egenanalyss of R produces n egenvalues λ and n n-dmensonal egenvectors w (1 n). Proectng each component of the vertex coordnate v = ( x, y) (1 n) separately onto the -th normalzed egenvectors e e = w w (1 n) (3) (c) Watermark patches are generated adaptvely to the local vertex counts. Fgure 3. Vertces are trangulated to create a mesh, whch s then subdvded nto watermark patches. 4
5 produces n mesh spectral coeffcent vectors r = ( rs,, rt, ) (1 n). The subscrpts s, and t denote orthogonal coordnate axes n the mesh-spectral doman correspondng to the spatal axes x and y. We form the matrx R for a watermark patch usng the connectvty wthn the patch. Edges connectng the patch wth other patches are not ncluded n our Laplacan matrx. The nverse transformaton, the mesh-spectral synthess, s smply a lnear combnaton of the bass e scaled by the mesh spectral coeffcents r. ( ) ( ) T 1 2 n = s,1e1 + s,2e2 + + s, nen T 1, 2,..., n = t,1e1 + t,2e2 + + t, nen. x, x,..., x r r r, y y y r r r The spectral coeffcents represent the noton of frequency (n the sense of the Fourer transformaton) of the shape of the mesh, especally f (1) the lengths of edges are unform over the mesh, and that (2) the degrees of vertces are unform over the mesh [14, 15]. The mesh produced by the Delaunay trangulaton has more unform edge length than by the other trangulaton methods gven a set of ponts. However, as t s obvous from the example shown n Fgure 3, the trangles n the mesh have a wde range of sze and varyng aspect rato that may nterfere wth the Frequency decomposton of the mesh shape by usng the mesh spectral analyss. A E B C D (a) A smple example mesh. A B C D E F A B C D E F (b) The Laplacan matrx for the mesh. Fgure 4. An example of the mesh Laplacan matrx. F (4) Modulaton After the spectral coeffcents are computed, a watermark s embedded nto the map by modfyng the spectral coeffcents accordng to the message bts. The algorthm employs a smple modulaton method smlar to Hartung s [11]. The data to be embedded s an m- dmensonal bt vector a = ( a1, a2,..., am ) n whch each bt takes values { 0,1 }. Each bt a s spread spatally over the map by duplcatng each symbol by chp rate c, producng a watermark symbol vector b = ( b1, b2,... b mc ), b { 0,1} of length mc. Repeatedly embeddng the same bt c tmes ncreases reslency of the watermark aganst addtve random nose. If a watermark patch contans more vertces than the specfed mnmum d, the maxmum value for the repetton s c = floor( L n) where n s the number of bts of the payload, the watermark message. For example, a mesh contans 480 vertces and the payload s 128 bt, chp rate c can be 1, 2, or 3. Each element b of the symbol vector b s then repeated or spread c tmes; b = a, c < ( + 1) c (5) After the spreadng, the bt vector b s converted to an embeddng symbol vector b = ( b 1, b 2,... b mc ), b { 1,1} by the followng mappng to create a zero-mean sgnal; 1, f b = 0; b = (6) 1, f b = 1. Assume that there are L usable rectangles and that th rectangle contans M vertces. Let v m, be the coordnate of mth vertex (1 < m< M) n the th rectangle pror to the watermarkng, p { 1,1} be the pseudo-random number sequence (PRNS) generated from a known key k w, and α ( α > 0) be the modulaton ampltude. The coordnate s ˆ. m of the vertex after watermarkng s computed by the followng formula; s = s + b p α (7) ˆ The extracton requres the key w k used for the embeddng. Key dstrbuton can be acheved by usng a publc-key cryptography scheme, for example. The modulaton ampltude α n the mesh spectral doman should be chosen so that the vertex dsplacement n the spatal doman won t affect vsual qualtes of maps. The geographcal map standard by the Geographcal Survey Insttute of Japan states that the maxmal error arrowed n a 1/2500-scale map s 0.3mm, whch corresponds to 75 cm n the real world. Perturbaton of 5
6 vertces on the map by 2 or 3 nteger coordnate ponts, that are, 20 or 30 cm n the real world, should be acceptable as long as the dscontnuty artfacts ntroduced by the dsplacements are unnotceable. Snce the spatal doman dsplacement s determned by the formula (4), both the modulaton ampltude α as well as the number of coeffcents modfed, that s, the chp rate c, determnes the vertex dsplacement n the spatal doman. The vertex dsplacement s roughly proportonal to the product of α c Extracton Pose normalzaton Pror to the extracton, an affne transformaton appled to the watermarked map ˆM s removed. Ths s a rather smple case of so-called affne matchng problem (e.g., [6, 26]). In our algorthm, a set of correspondng pars of landmarks are selected n the maps M and ˆM. Then, the sum of Eucldan dstance between the landmark pars s mnmzed. Ths mnmzaton s performed by repettvely applyng mnscule rotaton, translaton, and scalng transformatons. Our algorthm uses the coordnate of the lower-left corner of a strng that s assocated wth a buldng (or any other land obect) for the matchng. Correspondence between a par of landmarks n the maps can be establshed easly by smply comparng the strngs attached to them. We typcally employ about 30 to 80 landmark pars for the pose normalzaton. In terms of watermarkng, the most sgnfcant dfference between 2D vector dgtal map and the 3D polygonal meshes les n the relatve dffculty of the pose normalzaton. For 2D vector dgtal maps, accurate pose normalzaton s possble even after affne transformaton usng (lterally) landmarks. For 3D mesh models, even wth reference mesh, such normalzaton can be qute dffcult f the mesh had gone through geometrcal transformaton combned wth mesh smplfcaton and other connectvty changes Vertex matchng After the pose normalzaton, vertces that are ether nserted or deleted due to attacks are found by comparng the coordnate values of the reference map M and the watermarked map ˆM. To deal wth the vertex-nserton attack, the algorthm chooses a vertex n ˆM that s nsde the crcle of dameter t of the vertex v r of M. If there s more than one such vertex, the vertex closest to v r s used. To deal wth the vertex-removal attack, f no vertex n ˆM s found nsde the crcle of dameter t of the vertex v r of M, a vertex v w s nserted nto ˆM. The nserted vertex v w has the coordnate of v r. The coordnate value of v r s of course ncorrect; t s smply treated as nose by the extracton algorthm. The dameter t s a user-defned parameter. We chose the value of t=100 cm for the experments descrbed below. The value s chosen based on the maxmal error of 75 cm (n the real-world scale) arrowed n a 1/2500-scale Japanese geographcal map Meshng and patch generaton The reference map M s Delaunay trangulated, and the watermarkng patches are created. The trangulaton and the patches on M are exactly the same as the ones used for embeddng. The trangulaton and the patchfcaton are then transferred to the watermarked map ˆM. Usng the vertex-to-vertex correspondence between the maps M and ˆM establshed above Spectral Analyss The spectral analyss s performed frst on the reference mesh, whch produces exactly the same set of egenvectors and mesh spectral coeffcents as the ones computed for the M durng embeddng. Note that the egenvectors computed for the M can be used to derve mesh spectral coeffcents for the ˆM, for they have the same connectvty. Expensve egenvalue decomposton computaton need to be performed only once per patch for the reference map M Demodulaton To extract a message bt, the algorthm compares a mesh spectral coeffcent of M wth the correspondng coeffcents of ˆM. Let s assume that the th coeffcents of ˆM and ˆM are s and s ˆ, respectvely, and that p s the same PRNS as s used for embeddng, generated from the same stego-key k w. Then, the sum of the products q can be computed as follows; ( + 1) c 1 ( + 1) c 1 2 = ( ˆ ) = α = c = c (8) q s s p b p If p s the same for embeddng and extracton, and f dsturbances of the vertex coordnates of ˆM (e.g., addtve random nose) are neglgble, q = c α b (9) 6
7 where q takes one of the two values { αc, αc}. Snce α and c are always postve, smply testng for the sgns of q recovers the orgnal message bt sequence a, a = sgn( q ) (10) 3.1. Perceptblty Perceptblty of the watermark depends on varous The strng a can easly be converted to the orgnal message bt sequence b by applyng an nverse of the mappng as the embeddng. 3. Experments and results In all the experments descrbed below, we used the followng parameters. Mnmum patch sze d: d = 480 s used. The perceptblty experment used d = 128 as well. Payload: A message of sze 128 bt s embedded. Modulaton ampltude α : α = 1.0 and α = 1.5. Chp rate c: c=1 for the cases where d 128, and c=2 and c=3 for the cases where d 480. For the experments, we used the 6 maps lsted n (a) Orgnal map (enlarged.) (b) d=128, c=1, α =1.0 (c) d=128, c=1, α =1.5 Map A Map B Map C (d) d=480, c=2, α =1.0 (e) d=480, c=3, α =1.0 Map D Map E Map F Fgure 5. Sx maps used for the evaluaton experment. Fgure 5. As we target maps that manly represent houses and buldngs, we choose the maps from the urban and suburban resdental and commercal areas. (f) d=480, c=2, α =1.5 (g) d=480, c=3, α =1.5 Fgure 6. Perceptblty of the watermark usng varous watermarkng parameters. parameters, ncludng the payload m, patch sze d, the chp rate c, and the modulaton ampltude α. An ncrease n c or α mproves the attack reslency but t decreases the vsual qualty of the map. The effect of the patch sze d s 7
8 subtler. For example, a larger patch would have a hgher reslency aganst addtve random nose, but the resultng decrease n the number of patches per map reduces the reslency aganst croppng attacks. Fgure 6a-6g shows the effect on vsual qualty of the map of the watermarkng, usng 6 combnatons of watermarkng parameters. The fgure shows the map area of the sze approxmately 30m 30m n the real world. A hgher chp rate c and the hgher ampltude α (of the coeffcents modulaton) clearly degraded the vsual qualty of the map. In ths example, parameters d=480, c=2, α=1.0 showed the least amount of dstorton. It also showed acceptable performance n terms of attack reslency n the experments that follows Reslency aganst attacks We expermentally evaluated the attack reslency of the watermark usng the followng attacks; 1. Translaton: Translate all the vertces n the map by 1000 unts and 500 unts, respectvely, toward postve x and y drectons. 2. Upscalng: Unformly enlarge the map by the factor Downscalng: Unformly shrnks the map by 0.3 (attack 3a) and 0.6 (attack 3b) tmes the orgnal. Coordnate values are rounded to the nearest ntegers. 4. Rotate: Rotate the map by 45 degree about the upperleft corner (0,0) (attack 4a) or the center (3750, 2500) (attach 4b) of the map. 5. Smlarty transformaton: The map s rotated by 45 degree about the center of the map (3750, 2500), translated, and then downscaled by the factor of 0.6. Coordnate values are rounded to the nearest ntegers after the downscalng. 6. Local deformaton: The map s subdvded unformly nto rectangular grd of sze 10 10, and the vertces nsde each rectangle are rotated by 1 degree about the center of the rectangle. Gven the vertex coordnate of ( x, y ), the drecton of rotaton for the coordnate s clockwse f ( x+ y)mod2= 0, counterclockwse f otherwse. 7. Obect order scramblng: The order of appearance of obects (e.g., polygons of buldng outlnes) n a data fle s scrambled. 8. Vertex nserton: Vertces are added to target obects.e., polygons and polylnes, whle tryng to preserve the appearance of the map. In the experment, 3000 vertces are added to a map. 9. Addtve random nose: Random nose havng the ampltudes of ether α =10 cm, 30cm, or 50cm (attacks 9a, 9b, and 9c, respectvely) s added to the vertex coordnate. 10. Croppng: Each map s cropped accordng to the 8 croppng patterns shown n Fgure 7. Areas of the cropped maps vared from 1/2 to 1/16 of the orgnal. Table 2 shows the results of the experments. In Table 2, all the bt error rates are the average over the sx maps used for the experment. Table 2 also ncludes the results obtaned usng our prevous watermarkng method [22] for comparson. Some of the boxes are left vacant, as these fgures are not avalable for our prevous method. Overall, the new frequency doman watermarkng method descrbed n ths paper sgnfcantly outperformed our prevous algorthm n terms of attack reslency. Comparng between the chp rates of 2 and 3, the results produced by the hgher chp rate of c=3 produced somewhat less error than the lower chp rate of c=2. The new watermark s robust aganst translaton, upscalng, or rotaton n whch case no error occurred. The new watermark s mmune to vertex nserton and scramblng of obect order n the map data fle as expected. Pattern 1 Pattern 2 Pattern 3 Pattern 4 Pattern 5 Pattern 6 Pattern 7 Pattern 8 Fgure 7. Eght croppng patterns used for the experments. Downscalng by the factor of 0.3 caused errors due to the round off error of the coordnate values. A combnaton of rotaton, translaton, and downscalng also caused errors, most lkely due to the round off error due to downscalng. 8
9 The watermark showed sgnfcant error after the local deformaton. Unlke a global geometrcal transformaton (e.g., smlarty transformaton), local random deformaton can t be compensated for by our pose normalzaton method. The watermarks also showed sgnfcant errors after the croppng that reduced the area of the map down to 1/2~1/16 of the orgnal. In both attacks, the error rates of the new algorthm are agan much lower than those usng our prevous method. 4. Concluson and future work In ths paper, we presented a frequency-doman watermarkng algorthm for vector dgtal maps. The algorthm embeds bts nto a map by modfyng frequency doman representaton of the map. The mesh spectral coeffcents are computed by frst convertng the Experments showed that the watermarks produced by our new method descrbed n ths paper are more reslent than our prevous algorthm [22]. The watermark produced by new algorthm s reslent, to some extent, aganst such attacks as addtve random nose, addton of vertces, rotaton, scalng, and croppng of the map. Our future work ncludes mprovements n attack reslency. For example, reslency aganst addtve random nose or other frequency dependent attacks can be mproved by computng a better frequency doman representaton of the shape. We also need to fnd a quanttatve measure of dstorton that reflects human percepton, as well as standard sets of attacks and maps that can be used for obectvely evaluatng and comparng the proposed map watermarkng methods. Table 2. Bt error rates due to varous attacks. The payload was 128 bt. The N/M and N/A n the boxes ndcate, respectvely, not measured and not avalable. New method Prevous method Mnmum vertex counts per patch d Modulaton ampltude α Chp rate c 2 3 (1) Translaton 0.0 % 0.0 % 0.0 % (2) Upscalng ( 5.5) 0.0 % 0.0 % 0.0 % (3) Downscalng (3a) % 0.0 % 0.7 % (3b) % 0.0 % --- (4) Rotaton (4a) Center at (0, 0), 45 degree 0.0 % 0.0 % 0.0 % (4b) Center at (3750, 2500), 45 degree 0.0 % 0.0 % 0.0 % (5) Smlarty transformaton ((4b)+(1)+(3a)) 0.1 % 0.0 % 1.0 % (6) Local deformaton 9.2 % 8.1 % 45.2 % (7) Obect order scramblng 0.0 % 0.0 % 0.0 % (8) Vertex nserton (3000 vertces) 0.0 % 0.0 % 0.0 % (9a) α=10cm 0.0 % 0.0 % 0.0 % (9) Addtve (9b) α=30cm 0.1 % 0.0 % --- random nose (9c) α=50cm 5.9 % 3.4 % 8.5 % (10a) Pattern % 0.0 % 1.4 % (10b) Pattern % 0.4 % 1.8 % (10c) Pattern % 1.3 % 7.0 % (10) Croppng (10d) Pattern % 0.0 % 6.8 % (10e) Pattern % 0.0 % 16.7 % (10f) Pattern % 0.4 % 15.0 % (10g) Pattern % 0.4 % 11.3 % (10h) Pattern % 15.1 % 35.9 % map nto a mesh by usng Delaunay trangulaton, and then applyng mesh spectral analyss proposed by Karn et al [14, 15]. References [1] O. Benedens, Geometry-Based Watermarkng of 3D Models, IEEE CG&A, pp , January/February
10 [2] O. Benedens, C. Busch, Towards Blnd Detecton of Robust Watermarks n Polygonal Models, Proc. EUROGRAPHICS 2000 (Computer Graphcs Forum, Volume 19(2000), No. 3) [3] N. Bggs, Algebrac Graph Theory (2 nd Ed.). Cambrdge Unversty Press, [4] B. Bollobás, Modern Graph Theory, Sprnger, [5] F. Cayre, P. Rondao Alface & H. Maître, Compresson and watermarkng of 3D trangle meshes, SPIE 47th Annual Meetng, Jul. 2002, Seattle, WA (2002) [6] G. S. Cox, G. DeJager, A survey of pont pattern matchng technques and a new approach to pont pattern recognton, Proc. South Afrcan Symposum on Communcatons and Sgnal Processng 1993, pp [7] Ingemar J. Cox, Matthew L. Mller, Jeffrey A. Bloom, DIGITAL WATERMARKING, Morgan Kaufmann Publshers, [8] F. R. K. Chung, Spectral Graph Theory, Number. 92 n Regonal Conference Seres n Mathematcs, Amercan Mathematcal Socety, [9] M. de Berg, M. van Kreveld, M. Overmars, O. Schwarzkopf, Computatonal Geometry: Algorthms and Applcatons, 2 nd edton, Sprnger, [10] Shuh Endoh, Hrosh Masuda, Ryutarou Ohbuch, Satosh Kana, Development of Dgtal Watermarkng Technology for Vector Dgtal Maps, IPA Technology Expo 2001 Reports, 2001 (Japanese). [11] F. Hartung, P. Esert, and B. Grod, Dgtal Watermarkng of MPEG-4 Facal Anmaton Parameters, Computers and Graphcs, Vol. 22, No. 4, pp , Elsever, [12] Nel F. Johnson, Zoran Durc, and Sushl Jaoda, Informaton Hdng: Steganography and Watermarkng Attacks and Countermeasures, Kluwer Academc Publshers, [13] S. Kana, H. Date, and T. Kshnam, Dgtal Watermarkng for 3D Polygons usng Multresoluton Wavelet Decomposton, Proc. Sxth IFIP WG 5.2 GEO-6, pp , Tokyo, Japan, December ( kana/wm1-geo6.pdf) [14] Zach Karn, Crag Gotsman, Spectral Compresson of Mesh Geometry, Proc. SIGGRAPH 2000, pp , [15] Zach Karn, Crag Gotsman, 3D Mesh Compresson Usng Fxed Spectral Bases, Proc. Graphcs Interface 2001, pp. 1-8, [16] S. Katzenbesser, F. A. P. Pettcolas, Dgtal Watermarkng, Artech House, London, [17] I. Ktamura, S. Kana, and T. Kshnam, Watermarkng Vector Dgtal Map usng Wavelet Transformaton, Proc. Annual Conference of the Geographcal Informaton Systems Assocaton (GISA) 2000, Vol. 9, pp , 2000 (Japanese). [18] M. Kurhara, N. Komatsu, H. Arta, Watermarkng Vector Dgtal Maps, Specal Interest Group Report Vol. 2000, No. 36, Informaton Processng Socety of Japan (IPSJ), (Computer Securty No , 2000) (Japanese). [19] R. Ohbuch, H. Masuda, and M. Aono, Watermarkng Three-Dmensonal Polygonal Models, Proc. ACM Multmeda 97, pp , Seattle, Washngton, USA, November [20] R. Ohbuch, H. Masuda, and M. Aono, Watermarkng Three-Dmensonal Polygonal Models Through Geometrc and Topologcal Modfcatons, pp , IEEE JSAC, May [21] Ryutarou Ohbuch, Shgeo Takahash, Takahko Myazawa, and Ako Mukayama, Watermarkng 3D Polygonal Meshes n the Mesh Spectral Doman, n Proc. Graphcs Interface 2001, pp. 9-17, Ontaro, Canada, June, [22] Ryutarou Ohbuch, Hro Ueda, Shu Endoh, Robust Watermarkng of Vector Dgtal Maps, n Proc. IEEE Conference on Multmeda and Expo 2002 (ICME 2002), Lausanne, Swstzerland, August 26-29, [23] Ryutarou Ohbuch, Ako Mukayama, Shgeo Takahash, A Frequency-Doman Approach to Watermarkng 3D Shapes, Computer Graphcs Forum 21(3), pp , 2002 (Proc. EUROGRAPHICS 2002) [24] Eml Praun, Hugues Hoppe, Adam Fnkelsten, Robust Mesh Watermarkng, Proc. SIGGRAPH 99, pp , Aug [25] W. H. Press et al., Numercal Recpes n C-The Art of Scentfc Programmng, 2 nd Ed., Cambrdge Unversty Press, Cambrdge, UK, [26] I. Rothe, H. Suesse, K. Voss, The method of normalzaton to determne nvarants, IEEE Trans. on PAMI, Vol. 18, No. 4 (1996), pp [27] H. Samet, The Desgn and Analyss of Spatal Data Structures, Addson-Wesley, Readng, MA, [28] M. G. Wagner, Robust Watermarkng of Polygonal Meshes, Proc. Geometrc Modelng & Processng 2000, pp , Hong Kong, Aprl 10-12, [29] B-L. Yeo and M. M. Yeung, Watermarkng 3D Obects for Verfcaton, IEEE CG&A, pp , January/February [30] Kangkang Yn, Zhgeng Pan, Jaoyng Sh, Davd Zhang, Robust mesh watermarkng based on multresoluton processng, Computers & Graphcs, Vol. 25 (2001), pp Acknowledgements We thank Zenrn Co. Ltd. for lendng us the map data for the experments. We d lke to thank Prof. Hrosh Masuda of the Unversty of Tokyo and Prof. Satosh Kana of Hokkado Unversty for valuable dscussons and comments. We also thank Prof. Shgeo Takahash for useful comments. A part of ths research s funded by the grant No from the Mnstry of Educaton, Culture, Sports, Scences, and Technology of Japan, as well as the Okawa Foundaton of Informaton and Telecommuncatons. 10
Hybrid Non-Blind Color Image Watermarking
 Hybrd Non-Blnd Color Image Watermarkng Ms C.N.Sujatha 1, Dr. P. Satyanarayana 2 1 Assocate Professor, Dept. of ECE, SNIST, Yamnampet, Ghatkesar Hyderabad-501301, Telangana 2 Professor, Dept. of ECE, AITS,
Hybrd Non-Blnd Color Image Watermarkng Ms C.N.Sujatha 1, Dr. P. Satyanarayana 2 1 Assocate Professor, Dept. of ECE, SNIST, Yamnampet, Ghatkesar Hyderabad-501301, Telangana 2 Professor, Dept. of ECE, AITS,
Key-Selective Patchwork Method for Audio Watermarking
 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volume 4, Number 4, July 2010 Key-Selectve Patchwork Method for Audo Watermarkng 1 Ch-Man Pun, 2 Jng-Jng Jang 1, Frst and Correspondng
Internatonal Journal of Dgtal Content Technology and ts Applcatons Volume 4, Number 4, July 2010 Key-Selectve Patchwork Method for Audo Watermarkng 1 Ch-Man Pun, 2 Jng-Jng Jang 1, Frst and Correspondng
A Fast Visual Tracking Algorithm Based on Circle Pixels Matching
 A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
A Fast Content-Based Multimedia Retrieval Technique Using Compressed Data
 A Fast Content-Based Multmeda Retreval Technque Usng Compressed Data Borko Furht and Pornvt Saksobhavvat NSF Multmeda Laboratory Florda Atlantc Unversty, Boca Raton, Florda 3343 ABSTRACT In ths paper,
A Fast Content-Based Multmeda Retreval Technque Usng Compressed Data Borko Furht and Pornvt Saksobhavvat NSF Multmeda Laboratory Florda Atlantc Unversty, Boca Raton, Florda 3343 ABSTRACT In ths paper,
A Binarization Algorithm specialized on Document Images and Photos
 A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
Improvement of Spatial Resolution Using BlockMatching Based Motion Estimation and Frame. Integration
 Improvement of Spatal Resoluton Usng BlockMatchng Based Moton Estmaton and Frame Integraton Danya Suga and Takayuk Hamamoto Graduate School of Engneerng, Tokyo Unversty of Scence, 6-3-1, Nuku, Katsuska-ku,
Improvement of Spatal Resoluton Usng BlockMatchng Based Moton Estmaton and Frame Integraton Danya Suga and Takayuk Hamamoto Graduate School of Engneerng, Tokyo Unversty of Scence, 6-3-1, Nuku, Katsuska-ku,
Content Based Image Retrieval Using 2-D Discrete Wavelet with Texture Feature with Different Classifiers
 IOSR Journal of Electroncs and Communcaton Engneerng (IOSR-JECE) e-issn: 78-834,p- ISSN: 78-8735.Volume 9, Issue, Ver. IV (Mar - Apr. 04), PP 0-07 Content Based Image Retreval Usng -D Dscrete Wavelet wth
IOSR Journal of Electroncs and Communcaton Engneerng (IOSR-JECE) e-issn: 78-834,p- ISSN: 78-8735.Volume 9, Issue, Ver. IV (Mar - Apr. 04), PP 0-07 Content Based Image Retreval Usng -D Dscrete Wavelet wth
A Hybrid Semi-Blind Gray Scale Image Watermarking Algorithm Based on DWT-SVD using Human Visual System Model
 A Hybrd Sem-Blnd Gray Scale Image Watermarkng Algorthm Based on DWT-SVD usng Human Vsual System Model Rajesh Mehta r Scence & Engneerng, USICT Guru Gobnd Sngh Indrarprastha Unversty New Delh, Inda rajesh00ust@gmal.com
A Hybrd Sem-Blnd Gray Scale Image Watermarkng Algorthm Based on DWT-SVD usng Human Vsual System Model Rajesh Mehta r Scence & Engneerng, USICT Guru Gobnd Sngh Indrarprastha Unversty New Delh, Inda rajesh00ust@gmal.com
Enhanced Watermarking Technique for Color Images using Visual Cryptography
 Informaton Assurance and Securty Letters 1 (2010) 024-028 Enhanced Watermarkng Technque for Color Images usng Vsual Cryptography Enas F. Al rawashdeh 1, Rawan I.Zaghloul 2 1 Balqa Appled Unversty, MIS
Informaton Assurance and Securty Letters 1 (2010) 024-028 Enhanced Watermarkng Technque for Color Images usng Vsual Cryptography Enas F. Al rawashdeh 1, Rawan I.Zaghloul 2 1 Balqa Appled Unversty, MIS
MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION
 MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION Paulo Quntlano 1 & Antono Santa-Rosa 1 Federal Polce Department, Brasla, Brazl. E-mals: quntlano.pqs@dpf.gov.br and
MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION Paulo Quntlano 1 & Antono Santa-Rosa 1 Federal Polce Department, Brasla, Brazl. E-mals: quntlano.pqs@dpf.gov.br and
Analysis of Continuous Beams in General
 Analyss of Contnuous Beams n General Contnuous beams consdered here are prsmatc, rgdly connected to each beam segment and supported at varous ponts along the beam. onts are selected at ponts of support,
Analyss of Contnuous Beams n General Contnuous beams consdered here are prsmatc, rgdly connected to each beam segment and supported at varous ponts along the beam. onts are selected at ponts of support,
Steps for Computing the Dissimilarity, Entropy, Herfindahl-Hirschman and. Accessibility (Gravity with Competition) Indices
 Steps for Computng the Dssmlarty, Entropy, Herfndahl-Hrschman and Accessblty (Gravty wth Competton) Indces I. Dssmlarty Index Measurement: The followng formula can be used to measure the evenness between
Steps for Computng the Dssmlarty, Entropy, Herfndahl-Hrschman and Accessblty (Gravty wth Competton) Indces I. Dssmlarty Index Measurement: The followng formula can be used to measure the evenness between
Parallelism for Nested Loops with Non-uniform and Flow Dependences
 Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Robust Video Watermarking Using Image Normalization, Motion Vector and Perceptual Information
 Robust Vdeo Watermarkng Usng Image ormalzaton, Moton Vector and Perceptual Informaton Cedllo-Hernández Antono 1, Cedllo-Hernández Manuel 1, akano-myatake Marko 1, García-Vázquez Mreya S. 2 1 Postgraduate
Robust Vdeo Watermarkng Usng Image ormalzaton, Moton Vector and Perceptual Informaton Cedllo-Hernández Antono 1, Cedllo-Hernández Manuel 1, akano-myatake Marko 1, García-Vázquez Mreya S. 2 1 Postgraduate
High-Boost Mesh Filtering for 3-D Shape Enhancement
 Hgh-Boost Mesh Flterng for 3-D Shape Enhancement Hrokazu Yagou Λ Alexander Belyaev y Damng We z Λ y z ; ; Shape Modelng Laboratory, Unversty of Azu, Azu-Wakamatsu 965-8580 Japan y Computer Graphcs Group,
Hgh-Boost Mesh Flterng for 3-D Shape Enhancement Hrokazu Yagou Λ Alexander Belyaev y Damng We z Λ y z ; ; Shape Modelng Laboratory, Unversty of Azu, Azu-Wakamatsu 965-8580 Japan y Computer Graphcs Group,
Accounting for the Use of Different Length Scale Factors in x, y and z Directions
 1 Accountng for the Use of Dfferent Length Scale Factors n x, y and z Drectons Taha Soch (taha.soch@kcl.ac.uk) Imagng Scences & Bomedcal Engneerng, Kng s College London, The Rayne Insttute, St Thomas Hosptal,
1 Accountng for the Use of Dfferent Length Scale Factors n x, y and z Drectons Taha Soch (taha.soch@kcl.ac.uk) Imagng Scences & Bomedcal Engneerng, Kng s College London, The Rayne Insttute, St Thomas Hosptal,
Computer Animation and Visualisation. Lecture 4. Rigging / Skinning
 Computer Anmaton and Vsualsaton Lecture 4. Rggng / Sknnng Taku Komura Overvew Sknnng / Rggng Background knowledge Lnear Blendng How to decde weghts? Example-based Method Anatomcal models Sknnng Assume
Computer Anmaton and Vsualsaton Lecture 4. Rggng / Sknnng Taku Komura Overvew Sknnng / Rggng Background knowledge Lnear Blendng How to decde weghts? Example-based Method Anatomcal models Sknnng Assume
R s s f. m y s. SPH3UW Unit 7.3 Spherical Concave Mirrors Page 1 of 12. Notes
 SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
Collaboratively Regularized Nearest Points for Set Based Recognition
 Academc Center for Computng and Meda Studes, Kyoto Unversty Collaboratvely Regularzed Nearest Ponts for Set Based Recognton Yang Wu, Mchhko Mnoh, Masayuk Mukunok Kyoto Unversty 9/1/013 BMVC 013 @ Brstol,
Academc Center for Computng and Meda Studes, Kyoto Unversty Collaboratvely Regularzed Nearest Ponts for Set Based Recognton Yang Wu, Mchhko Mnoh, Masayuk Mukunok Kyoto Unversty 9/1/013 BMVC 013 @ Brstol,
Range images. Range image registration. Examples of sampling patterns. Range images and range surfaces
 Range mages For many structured lght scanners, the range data forms a hghly regular pattern known as a range mage. he samplng pattern s determned by the specfc scanner. Range mage regstraton 1 Examples
Range mages For many structured lght scanners, the range data forms a hghly regular pattern known as a range mage. he samplng pattern s determned by the specfc scanner. Range mage regstraton 1 Examples
Simplification of 3D Meshes
 Smplfcaton of 3D Meshes Addy Ngan /4/00 Outlne Motvaton Taxonomy of smplfcaton methods Hoppe et al, Mesh optmzaton Hoppe, Progressve meshes Smplfcaton of 3D Meshes 1 Motvaton Hgh detaled meshes becomng
Smplfcaton of 3D Meshes Addy Ngan /4/00 Outlne Motvaton Taxonomy of smplfcaton methods Hoppe et al, Mesh optmzaton Hoppe, Progressve meshes Smplfcaton of 3D Meshes 1 Motvaton Hgh detaled meshes becomng
Shape Representation Robust to the Sketching Order Using Distance Map and Direction Histogram
 Shape Representaton Robust to the Sketchng Order Usng Dstance Map and Drecton Hstogram Department of Computer Scence Yonse Unversty Kwon Yun CONTENTS Revew Topc Proposed Method System Overvew Sketch Normalzaton
Shape Representaton Robust to the Sketchng Order Usng Dstance Map and Drecton Hstogram Department of Computer Scence Yonse Unversty Kwon Yun CONTENTS Revew Topc Proposed Method System Overvew Sketch Normalzaton
Research Article Hamming Code Based Watermarking Scheme for 3D Model Verification
 Mathematcal Problems n Engneerng, Artcle ID 241093, 7 pages http://dx.do.org/10.1155/2014/241093 Research Artcle Hammng Code Based Watermarkng Scheme for 3D Model Verfcaton Jen-Tse Wang, 1 Y-Chng Chang,
Mathematcal Problems n Engneerng, Artcle ID 241093, 7 pages http://dx.do.org/10.1155/2014/241093 Research Artcle Hammng Code Based Watermarkng Scheme for 3D Model Verfcaton Jen-Tse Wang, 1 Y-Chng Chang,
Fitting & Matching. Lecture 4 Prof. Bregler. Slides from: S. Lazebnik, S. Seitz, M. Pollefeys, A. Effros.
 Fttng & Matchng Lecture 4 Prof. Bregler Sldes from: S. Lazebnk, S. Setz, M. Pollefeys, A. Effros. How do we buld panorama? We need to match (algn) mages Matchng wth Features Detect feature ponts n both
Fttng & Matchng Lecture 4 Prof. Bregler Sldes from: S. Lazebnk, S. Setz, M. Pollefeys, A. Effros. How do we buld panorama? We need to match (algn) mages Matchng wth Features Detect feature ponts n both
Quality Improvement Algorithm for Tetrahedral Mesh Based on Optimal Delaunay Triangulation
 Intellgent Informaton Management, 013, 5, 191-195 Publshed Onlne November 013 (http://www.scrp.org/journal/m) http://dx.do.org/10.36/m.013.5601 Qualty Improvement Algorthm for Tetrahedral Mesh Based on
Intellgent Informaton Management, 013, 5, 191-195 Publshed Onlne November 013 (http://www.scrp.org/journal/m) http://dx.do.org/10.36/m.013.5601 Qualty Improvement Algorthm for Tetrahedral Mesh Based on
User Authentication Based On Behavioral Mouse Dynamics Biometrics
 User Authentcaton Based On Behavoral Mouse Dynamcs Bometrcs Chee-Hyung Yoon Danel Donghyun Km Department of Computer Scence Department of Computer Scence Stanford Unversty Stanford Unversty Stanford, CA
User Authentcaton Based On Behavoral Mouse Dynamcs Bometrcs Chee-Hyung Yoon Danel Donghyun Km Department of Computer Scence Department of Computer Scence Stanford Unversty Stanford Unversty Stanford, CA
Face Recognition University at Buffalo CSE666 Lecture Slides Resources:
 Face Recognton Unversty at Buffalo CSE666 Lecture Sldes Resources: http://www.face-rec.org/algorthms/ Overvew of face recognton algorthms Correlaton - Pxel based correspondence between two face mages Structural
Face Recognton Unversty at Buffalo CSE666 Lecture Sldes Resources: http://www.face-rec.org/algorthms/ Overvew of face recognton algorthms Correlaton - Pxel based correspondence between two face mages Structural
An Image Compression Algorithm based on Wavelet Transform and LZW
 An Image Compresson Algorthm based on Wavelet Transform and LZW Png Luo a, Janyong Yu b School of Chongqng Unversty of Posts and Telecommuncatons, Chongqng, 400065, Chna Abstract a cylpng@63.com, b y27769864@sna.cn
An Image Compresson Algorthm based on Wavelet Transform and LZW Png Luo a, Janyong Yu b School of Chongqng Unversty of Posts and Telecommuncatons, Chongqng, 400065, Chna Abstract a cylpng@63.com, b y27769864@sna.cn
An Optimal Algorithm for Prufer Codes *
 J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
Image Representation & Visualization Basic Imaging Algorithms Shape Representation and Analysis. outline
 mage Vsualzaton mage Vsualzaton mage Representaton & Vsualzaton Basc magng Algorthms Shape Representaton and Analyss outlne mage Representaton & Vsualzaton Basc magng Algorthms Shape Representaton and
mage Vsualzaton mage Vsualzaton mage Representaton & Vsualzaton Basc magng Algorthms Shape Representaton and Analyss outlne mage Representaton & Vsualzaton Basc magng Algorthms Shape Representaton and
Reading. 14. Subdivision curves. Recommended:
 eadng ecommended: Stollntz, Deose, and Salesn. Wavelets for Computer Graphcs: heory and Applcatons, 996, secton 6.-6., A.5. 4. Subdvson curves Note: there s an error n Stollntz, et al., secton A.5. Equaton
eadng ecommended: Stollntz, Deose, and Salesn. Wavelets for Computer Graphcs: heory and Applcatons, 996, secton 6.-6., A.5. 4. Subdvson curves Note: there s an error n Stollntz, et al., secton A.5. Equaton
Managing CAD Data as a Multimedia Data Type Using Digital Watermarking
 Managng CAD Data as a Multmeda Data Type Usng Dgtal Watermarkng Ryutarou Ohbuch, 2 Hrosh Masuda Yamanash Unversty, Computer Scence Department (ohbuch@acm.org) 2 Tokyo Unversty, Artfacts Research Center
Managng CAD Data as a Multmeda Data Type Usng Dgtal Watermarkng Ryutarou Ohbuch, 2 Hrosh Masuda Yamanash Unversty, Computer Scence Department (ohbuch@acm.org) 2 Tokyo Unversty, Artfacts Research Center
Lobachevsky State University of Nizhni Novgorod. Polyhedron. Quick Start Guide
 Lobachevsky State Unversty of Nzhn Novgorod Polyhedron Quck Start Gude Nzhn Novgorod 2016 Contents Specfcaton of Polyhedron software... 3 Theoretcal background... 4 1. Interface of Polyhedron... 6 1.1.
Lobachevsky State Unversty of Nzhn Novgorod Polyhedron Quck Start Gude Nzhn Novgorod 2016 Contents Specfcaton of Polyhedron software... 3 Theoretcal background... 4 1. Interface of Polyhedron... 6 1.1.
3D vector computer graphics
 3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
S1 Note. Basis functions.
 S1 Note. Bass functons. Contents Types of bass functons...1 The Fourer bass...2 B-splne bass...3 Power and type I error rates wth dfferent numbers of bass functons...4 Table S1. Smulaton results of type
S1 Note. Bass functons. Contents Types of bass functons...1 The Fourer bass...2 B-splne bass...3 Power and type I error rates wth dfferent numbers of bass functons...4 Table S1. Smulaton results of type
Identify the Attack in Embedded Image with Steganalysis Detection Method by PSNR and RGB Intensity
 Internatonal Journal of Computer Systems (ISSN: 394-1065), Volume 03 Issue 07, July, 016 Avalable at http://www.jcsonlne.com/ Identfy the Attack n Embedded Image wth Steganalyss Detecton Method by PSNR
Internatonal Journal of Computer Systems (ISSN: 394-1065), Volume 03 Issue 07, July, 016 Avalable at http://www.jcsonlne.com/ Identfy the Attack n Embedded Image wth Steganalyss Detecton Method by PSNR
Corner-Based Image Alignment using Pyramid Structure with Gradient Vector Similarity
 Journal of Sgnal and Informaton Processng, 013, 4, 114-119 do:10.436/jsp.013.43b00 Publshed Onlne August 013 (http://www.scrp.org/journal/jsp) Corner-Based Image Algnment usng Pyramd Structure wth Gradent
Journal of Sgnal and Informaton Processng, 013, 4, 114-119 do:10.436/jsp.013.43b00 Publshed Onlne August 013 (http://www.scrp.org/journal/jsp) Corner-Based Image Algnment usng Pyramd Structure wth Gradent
FEATURE EXTRACTION. Dr. K.Vijayarekha. Associate Dean School of Electrical and Electronics Engineering SASTRA University, Thanjavur
 FEATURE EXTRACTION Dr. K.Vjayarekha Assocate Dean School of Electrcal and Electroncs Engneerng SASTRA Unversty, Thanjavur613 41 Jont Intatve of IITs and IISc Funded by MHRD Page 1 of 8 Table of Contents
FEATURE EXTRACTION Dr. K.Vjayarekha Assocate Dean School of Electrcal and Electroncs Engneerng SASTRA Unversty, Thanjavur613 41 Jont Intatve of IITs and IISc Funded by MHRD Page 1 of 8 Table of Contents
Semi-Fragile Watermarking Scheme for Authentication of JPEG Images
 Tamkang Journal of Scence and Engneerng, Vol. 10, No 1, pp. 5766 (2007) 57 Sem-Fragle Watermarkng Scheme for Authentcaton of JPEG Images Chh-Hung n 1 *, Tung-Shh Su 2 and Wen-Shyong Hseh 2,3 1 Department
Tamkang Journal of Scence and Engneerng, Vol. 10, No 1, pp. 5766 (2007) 57 Sem-Fragle Watermarkng Scheme for Authentcaton of JPEG Images Chh-Hung n 1 *, Tung-Shh Su 2 and Wen-Shyong Hseh 2,3 1 Department
Cluster Analysis of Electrical Behavior
 Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
On the Optimality of Spectral Compression of Meshes
 On the Optmalty of Spectral Compresson of Meshes MIRELA BEN-CHEN AND CRAIG GOTSMAN Center for Graphcs and Geometrc Computng Technon Israel Insttute of Technology Spectral compresson of trangle meshes has
On the Optmalty of Spectral Compresson of Meshes MIRELA BEN-CHEN AND CRAIG GOTSMAN Center for Graphcs and Geometrc Computng Technon Israel Insttute of Technology Spectral compresson of trangle meshes has
The Codesign Challenge
 ECE 4530 Codesgn Challenge Fall 2007 Hardware/Software Codesgn The Codesgn Challenge Objectves In the codesgn challenge, your task s to accelerate a gven software reference mplementaton as fast as possble.
ECE 4530 Codesgn Challenge Fall 2007 Hardware/Software Codesgn The Codesgn Challenge Objectves In the codesgn challenge, your task s to accelerate a gven software reference mplementaton as fast as possble.
High Payload Reversible Data Hiding Scheme Using Difference Segmentation and Histogram Shifting
 JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 11, NO. 1, MARCH 2013 9 Hgh Payload Reversble Data Hdng Scheme Usng Dfference Segmentaton and Hstogram Shftng Yung-Chen Chou and Huang-Chng L Abstract
JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 11, NO. 1, MARCH 2013 9 Hgh Payload Reversble Data Hdng Scheme Usng Dfference Segmentaton and Hstogram Shftng Yung-Chen Chou and Huang-Chng L Abstract
Local Quaternary Patterns and Feature Local Quaternary Patterns
 Local Quaternary Patterns and Feature Local Quaternary Patterns Jayu Gu and Chengjun Lu The Department of Computer Scence, New Jersey Insttute of Technology, Newark, NJ 0102, USA Abstract - Ths paper presents
Local Quaternary Patterns and Feature Local Quaternary Patterns Jayu Gu and Chengjun Lu The Department of Computer Scence, New Jersey Insttute of Technology, Newark, NJ 0102, USA Abstract - Ths paper presents
SLAM Summer School 2006 Practical 2: SLAM using Monocular Vision
 SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
Problem Definitions and Evaluation Criteria for Computational Expensive Optimization
 Problem efntons and Evaluaton Crtera for Computatonal Expensve Optmzaton B. Lu 1, Q. Chen and Q. Zhang 3, J. J. Lang 4, P. N. Suganthan, B. Y. Qu 6 1 epartment of Computng, Glyndwr Unversty, UK Faclty
Problem efntons and Evaluaton Crtera for Computatonal Expensve Optmzaton B. Lu 1, Q. Chen and Q. Zhang 3, J. J. Lang 4, P. N. Suganthan, B. Y. Qu 6 1 epartment of Computng, Glyndwr Unversty, UK Faclty
Image Alignment CSC 767
 Image Algnment CSC 767 Image algnment Image from http://graphcs.cs.cmu.edu/courses/15-463/2010_fall/ Image algnment: Applcatons Panorama sttchng Image algnment: Applcatons Recognton of object nstances
Image Algnment CSC 767 Image algnment Image from http://graphcs.cs.cmu.edu/courses/15-463/2010_fall/ Image algnment: Applcatons Panorama sttchng Image algnment: Applcatons Recognton of object nstances
Robust Watermarking for Text Images Based on Arnold Scrambling and DWT-DCT
 Internatonal Conference on Mechatroncs Electronc Industral and Control Engneerng (MEIC 015) Robust Watermarkng for Text Images Based on Arnold Scramblng and DWT-DCT Fan Wu College of Informaton Scence
Internatonal Conference on Mechatroncs Electronc Industral and Control Engneerng (MEIC 015) Robust Watermarkng for Text Images Based on Arnold Scramblng and DWT-DCT Fan Wu College of Informaton Scence
A fast algorithm for color image segmentation
 Unersty of Wollongong Research Onlne Faculty of Informatcs - Papers (Arche) Faculty of Engneerng and Informaton Scences 006 A fast algorthm for color mage segmentaton L. Dong Unersty of Wollongong, lju@uow.edu.au
Unersty of Wollongong Research Onlne Faculty of Informatcs - Papers (Arche) Faculty of Engneerng and Informaton Scences 006 A fast algorthm for color mage segmentaton L. Dong Unersty of Wollongong, lju@uow.edu.au
Hermite Splines in Lie Groups as Products of Geodesics
 Hermte Splnes n Le Groups as Products of Geodescs Ethan Eade Updated May 28, 2017 1 Introducton 1.1 Goal Ths document defnes a curve n the Le group G parametrzed by tme and by structural parameters n the
Hermte Splnes n Le Groups as Products of Geodescs Ethan Eade Updated May 28, 2017 1 Introducton 1.1 Goal Ths document defnes a curve n the Le group G parametrzed by tme and by structural parameters n the
Information Hiding Watermarking Detection Technique by PSNR and RGB Intensity
 www..org 3 Informaton Hdng Watermarkng Detecton Technque by PSNR and RGB Intensty 1 Neha Chauhan, Akhlesh A. Waoo, 3 P. S. Patheja 1 Research Scholar, BIST, Bhopal, Inda.,3 Assstant Professor, BIST, Bhopal,
www..org 3 Informaton Hdng Watermarkng Detecton Technque by PSNR and RGB Intensty 1 Neha Chauhan, Akhlesh A. Waoo, 3 P. S. Patheja 1 Research Scholar, BIST, Bhopal, Inda.,3 Assstant Professor, BIST, Bhopal,
Some Tutorial about the Project. Computer Graphics
 Some Tutoral about the Project Lecture 6 Rastersaton, Antalasng, Texture Mappng, I have already covered all the topcs needed to fnsh the 1 st practcal Today, I wll brefly explan how to start workng on
Some Tutoral about the Project Lecture 6 Rastersaton, Antalasng, Texture Mappng, I have already covered all the topcs needed to fnsh the 1 st practcal Today, I wll brefly explan how to start workng on
Modeling, Manipulating, and Visualizing Continuous Volumetric Data: A Novel Spline-based Approach
 Modelng, Manpulatng, and Vsualzng Contnuous Volumetrc Data: A Novel Splne-based Approach Jng Hua Center for Vsual Computng, Department of Computer Scence SUNY at Stony Brook Talk Outlne Introducton and
Modelng, Manpulatng, and Vsualzng Contnuous Volumetrc Data: A Novel Splne-based Approach Jng Hua Center for Vsual Computng, Department of Computer Scence SUNY at Stony Brook Talk Outlne Introducton and
KEYWORDS: Digital Image Watermarking, Discrete Wavelet Transform, General Regression Neural Network, Human Visual System. 1.
 An Adaptve Dgtal Image Watermarkng Based on Image Features n Dscrete Wavelet Transform Doman and General Regresson Neural Network Ayoub Taher Group of IT Engneerng, Payam Noor Unversty, Broujen, Iran ABSTRACT:
An Adaptve Dgtal Image Watermarkng Based on Image Features n Dscrete Wavelet Transform Doman and General Regresson Neural Network Ayoub Taher Group of IT Engneerng, Payam Noor Unversty, Broujen, Iran ABSTRACT:
UB at GeoCLEF Department of Geography Abstract
 UB at GeoCLEF 2006 Mguel E. Ruz (1), Stuart Shapro (2), June Abbas (1), Slva B. Southwck (1) and Davd Mark (3) State Unversty of New York at Buffalo (1) Department of Lbrary and Informaton Studes (2) Department
UB at GeoCLEF 2006 Mguel E. Ruz (1), Stuart Shapro (2), June Abbas (1), Slva B. Southwck (1) and Davd Mark (3) State Unversty of New York at Buffalo (1) Department of Lbrary and Informaton Studes (2) Department
Compiler Design. Spring Register Allocation. Sample Exercises and Solutions. Prof. Pedro C. Diniz
 Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Term Weighting Classification System Using the Chi-square Statistic for the Classification Subtask at NTCIR-6 Patent Retrieval Task
 Proceedngs of NTCIR-6 Workshop Meetng, May 15-18, 2007, Tokyo, Japan Term Weghtng Classfcaton System Usng the Ch-square Statstc for the Classfcaton Subtask at NTCIR-6 Patent Retreval Task Kotaro Hashmoto
Proceedngs of NTCIR-6 Workshop Meetng, May 15-18, 2007, Tokyo, Japan Term Weghtng Classfcaton System Usng the Ch-square Statstc for the Classfcaton Subtask at NTCIR-6 Patent Retreval Task Kotaro Hashmoto
Edge Detection in Noisy Images Using the Support Vector Machines
 Edge Detecton n Nosy Images Usng the Support Vector Machnes Hlaro Gómez-Moreno, Saturnno Maldonado-Bascón, Francsco López-Ferreras Sgnal Theory and Communcatons Department. Unversty of Alcalá Crta. Madrd-Barcelona
Edge Detecton n Nosy Images Usng the Support Vector Machnes Hlaro Gómez-Moreno, Saturnno Maldonado-Bascón, Francsco López-Ferreras Sgnal Theory and Communcatons Department. Unversty of Alcalá Crta. Madrd-Barcelona
K-means and Hierarchical Clustering
 Note to other teachers and users of these sldes. Andrew would be delghted f you found ths source materal useful n gvng your own lectures. Feel free to use these sldes verbatm, or to modfy them to ft your
Note to other teachers and users of these sldes. Andrew would be delghted f you found ths source materal useful n gvng your own lectures. Feel free to use these sldes verbatm, or to modfy them to ft your
Multi-stable Perception. Necker Cube
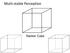 Mult-stable Percepton Necker Cube Spnnng dancer lluson, Nobuuk Kaahara Fttng and Algnment Computer Vson Szelsk 6.1 James Has Acknowledgment: Man sldes from Derek Hoem, Lana Lazebnk, and Grauman&Lebe 2008
Mult-stable Percepton Necker Cube Spnnng dancer lluson, Nobuuk Kaahara Fttng and Algnment Computer Vson Szelsk 6.1 James Has Acknowledgment: Man sldes from Derek Hoem, Lana Lazebnk, and Grauman&Lebe 2008
Cell Count Method on a Network with SANET
 CSIS Dscusson Paper No.59 Cell Count Method on a Network wth SANET Atsuyuk Okabe* and Shno Shode** Center for Spatal Informaton Scence, Unversty of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113-8656, Japan
CSIS Dscusson Paper No.59 Cell Count Method on a Network wth SANET Atsuyuk Okabe* and Shno Shode** Center for Spatal Informaton Scence, Unversty of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113-8656, Japan
A MOVING MESH APPROACH FOR SIMULATION BUDGET ALLOCATION ON CONTINUOUS DOMAINS
 Proceedngs of the Wnter Smulaton Conference M E Kuhl, N M Steger, F B Armstrong, and J A Jones, eds A MOVING MESH APPROACH FOR SIMULATION BUDGET ALLOCATION ON CONTINUOUS DOMAINS Mark W Brantley Chun-Hung
Proceedngs of the Wnter Smulaton Conference M E Kuhl, N M Steger, F B Armstrong, and J A Jones, eds A MOVING MESH APPROACH FOR SIMULATION BUDGET ALLOCATION ON CONTINUOUS DOMAINS Mark W Brantley Chun-Hung
Research and Application of Fingerprint Recognition Based on MATLAB
 Send Orders for Reprnts to reprnts@benthamscence.ae The Open Automaton and Control Systems Journal, 205, 7, 07-07 Open Access Research and Applcaton of Fngerprnt Recognton Based on MATLAB Nng Lu* Department
Send Orders for Reprnts to reprnts@benthamscence.ae The Open Automaton and Control Systems Journal, 205, 7, 07-07 Open Access Research and Applcaton of Fngerprnt Recognton Based on MATLAB Nng Lu* Department
A NEW AUDIO WATERMARKING METHOD BASED
 A NEW AUDIO WATERMARKING METHOD BASED ON DISCRETE COSINE TRANSFORM WITH A GRAY IMAGE Mohammad Ibrahm Khan 1, Md. Iqbal Hasan Sarker 2, Kaushk Deb 3 and Md. Hasan Furhad 4 1,2,3 Department of Computer Scence
A NEW AUDIO WATERMARKING METHOD BASED ON DISCRETE COSINE TRANSFORM WITH A GRAY IMAGE Mohammad Ibrahm Khan 1, Md. Iqbal Hasan Sarker 2, Kaushk Deb 3 and Md. Hasan Furhad 4 1,2,3 Department of Computer Scence
An Image Fusion Approach Based on Segmentation Region
 Rong Wang, L-Qun Gao, Shu Yang, Yu-Hua Cha, and Yan-Chun Lu An Image Fuson Approach Based On Segmentaton Regon An Image Fuson Approach Based on Segmentaton Regon Rong Wang, L-Qun Gao, Shu Yang 3, Yu-Hua
Rong Wang, L-Qun Gao, Shu Yang, Yu-Hua Cha, and Yan-Chun Lu An Image Fuson Approach Based On Segmentaton Regon An Image Fuson Approach Based on Segmentaton Regon Rong Wang, L-Qun Gao, Shu Yang 3, Yu-Hua
Learning the Kernel Parameters in Kernel Minimum Distance Classifier
 Learnng the Kernel Parameters n Kernel Mnmum Dstance Classfer Daoqang Zhang 1,, Songcan Chen and Zh-Hua Zhou 1* 1 Natonal Laboratory for Novel Software Technology Nanjng Unversty, Nanjng 193, Chna Department
Learnng the Kernel Parameters n Kernel Mnmum Dstance Classfer Daoqang Zhang 1,, Songcan Chen and Zh-Hua Zhou 1* 1 Natonal Laboratory for Novel Software Technology Nanjng Unversty, Nanjng 193, Chna Department
Optimal Workload-based Weighted Wavelet Synopses
 Optmal Workload-based Weghted Wavelet Synopses Yoss Matas School of Computer Scence Tel Avv Unversty Tel Avv 69978, Israel matas@tau.ac.l Danel Urel School of Computer Scence Tel Avv Unversty Tel Avv 69978,
Optmal Workload-based Weghted Wavelet Synopses Yoss Matas School of Computer Scence Tel Avv Unversty Tel Avv 69978, Israel matas@tau.ac.l Danel Urel School of Computer Scence Tel Avv Unversty Tel Avv 69978,
Tsinghua University at TAC 2009: Summarizing Multi-documents by Information Distance
 Tsnghua Unversty at TAC 2009: Summarzng Mult-documents by Informaton Dstance Chong Long, Mnle Huang, Xaoyan Zhu State Key Laboratory of Intellgent Technology and Systems, Tsnghua Natonal Laboratory for
Tsnghua Unversty at TAC 2009: Summarzng Mult-documents by Informaton Dstance Chong Long, Mnle Huang, Xaoyan Zhu State Key Laboratory of Intellgent Technology and Systems, Tsnghua Natonal Laboratory for
2x x l. Module 3: Element Properties Lecture 4: Lagrange and Serendipity Elements
 Module 3: Element Propertes Lecture : Lagrange and Serendpty Elements 5 In last lecture note, the nterpolaton functons are derved on the bass of assumed polynomal from Pascal s trangle for the fled varable.
Module 3: Element Propertes Lecture : Lagrange and Serendpty Elements 5 In last lecture note, the nterpolaton functons are derved on the bass of assumed polynomal from Pascal s trangle for the fled varable.
Machine Learning: Algorithms and Applications
 14/05/1 Machne Learnng: Algorthms and Applcatons Florano Zn Free Unversty of Bozen-Bolzano Faculty of Computer Scence Academc Year 011-01 Lecture 10: 14 May 01 Unsupervsed Learnng cont Sldes courtesy of
14/05/1 Machne Learnng: Algorthms and Applcatons Florano Zn Free Unversty of Bozen-Bolzano Faculty of Computer Scence Academc Year 011-01 Lecture 10: 14 May 01 Unsupervsed Learnng cont Sldes courtesy of
Development of an Active Shape Model. Using the Discrete Cosine Transform
 Development of an Actve Shape Model Usng the Dscrete Cosne Transform Kotaro Yasuda A Thess n The Department of Electrcal and Computer Engneerng Presented n Partal Fulfllment of the Requrements for the
Development of an Actve Shape Model Usng the Dscrete Cosne Transform Kotaro Yasuda A Thess n The Department of Electrcal and Computer Engneerng Presented n Partal Fulfllment of the Requrements for the
BioTechnology. An Indian Journal FULL PAPER. Trade Science Inc.
 [Type text] [Type text] [Type text] ISSN : 0974-74 Volume 0 Issue BoTechnology 04 An Indan Journal FULL PAPER BTAIJ 0() 04 [684-689] Revew on Chna s sports ndustry fnancng market based on market -orented
[Type text] [Type text] [Type text] ISSN : 0974-74 Volume 0 Issue BoTechnology 04 An Indan Journal FULL PAPER BTAIJ 0() 04 [684-689] Revew on Chna s sports ndustry fnancng market based on market -orented
y and the total sum of
 Lnear regresson Testng for non-lnearty In analytcal chemstry, lnear regresson s commonly used n the constructon of calbraton functons requred for analytcal technques such as gas chromatography, atomc absorpton
Lnear regresson Testng for non-lnearty In analytcal chemstry, lnear regresson s commonly used n the constructon of calbraton functons requred for analytcal technques such as gas chromatography, atomc absorpton
Helsinki University Of Technology, Systems Analysis Laboratory Mat Independent research projects in applied mathematics (3 cr)
 Helsnk Unversty Of Technology, Systems Analyss Laboratory Mat-2.08 Independent research projects n appled mathematcs (3 cr) "! #$&% Antt Laukkanen 506 R ajlaukka@cc.hut.f 2 Introducton...3 2 Multattrbute
Helsnk Unversty Of Technology, Systems Analyss Laboratory Mat-2.08 Independent research projects n appled mathematcs (3 cr) "! #$&% Antt Laukkanen 506 R ajlaukka@cc.hut.f 2 Introducton...3 2 Multattrbute
A Robust Method for Estimating the Fundamental Matrix
 Proc. VIIth Dgtal Image Computng: Technques and Applcatons, Sun C., Talbot H., Ourseln S. and Adraansen T. (Eds.), 0- Dec. 003, Sydney A Robust Method for Estmatng the Fundamental Matrx C.L. Feng and Y.S.
Proc. VIIth Dgtal Image Computng: Technques and Applcatons, Sun C., Talbot H., Ourseln S. and Adraansen T. (Eds.), 0- Dec. 003, Sydney A Robust Method for Estmatng the Fundamental Matrx C.L. Feng and Y.S.
Inverse-Polar Ray Projection for Recovering Projective Transformations
 nverse-polar Ray Projecton for Recoverng Projectve Transformatons Yun Zhang The Center for Advanced Computer Studes Unversty of Lousana at Lafayette yxz646@lousana.edu Henry Chu The Center for Advanced
nverse-polar Ray Projecton for Recoverng Projectve Transformatons Yun Zhang The Center for Advanced Computer Studes Unversty of Lousana at Lafayette yxz646@lousana.edu Henry Chu The Center for Advanced
University of Erlangen-Nuremberg. Cauerstrae 7, Erlangen, Germany. and edges. Each node is labeled by a feature vector that characterizes
 Deformable Templates for the Localzaton of Anatomcal Structures n Radologc Images Wolfgang Sorgel and Bernd Grod Telecommuncatons Laboratory Unversty of Erlangen-Nuremberg Cauerstrae 7, 91058 Erlangen,
Deformable Templates for the Localzaton of Anatomcal Structures n Radologc Images Wolfgang Sorgel and Bernd Grod Telecommuncatons Laboratory Unversty of Erlangen-Nuremberg Cauerstrae 7, 91058 Erlangen,
Combining Multiresolution Shape Descriptors for 3D Model Retrieval
 Ryutarou Ohbuch, Yushn Hata, Combnng Multresoluton Shape Descrptors for 3D Model Retreval, Accepted, Proc. WSCG 2006, Plzen, Czech Republc, Jan. 30~Feb. 3, 2006. Combnng Multresoluton Shape Descrptors
Ryutarou Ohbuch, Yushn Hata, Combnng Multresoluton Shape Descrptors for 3D Model Retreval, Accepted, Proc. WSCG 2006, Plzen, Czech Republc, Jan. 30~Feb. 3, 2006. Combnng Multresoluton Shape Descrptors
Recognizing Faces. Outline
 Recognzng Faces Drk Colbry Outlne Introducton and Motvaton Defnng a feature vector Prncpal Component Analyss Lnear Dscrmnate Analyss !"" #$""% http://www.nfotech.oulu.f/annual/2004 + &'()*) '+)* 2 ! &
Recognzng Faces Drk Colbry Outlne Introducton and Motvaton Defnng a feature vector Prncpal Component Analyss Lnear Dscrmnate Analyss !"" #$""% http://www.nfotech.oulu.f/annual/2004 + &'()*) '+)* 2 ! &
Robust Blind Video Watermark Algorithm in Transform Domain Combining with 3D Video Correlation
 JOURNAL OF MULTIMEDIA, VOL. 8, NO. 2, APRIL 2013 161 Robust Blnd Vdeo Watermark Algorthm n Transform Doman Combnng wth 3D Vdeo Correlaton DING Ha-yang 1,3 1. Informaton Securty Center, Bejng Unversty of
JOURNAL OF MULTIMEDIA, VOL. 8, NO. 2, APRIL 2013 161 Robust Blnd Vdeo Watermark Algorthm n Transform Doman Combnng wth 3D Vdeo Correlaton DING Ha-yang 1,3 1. Informaton Securty Center, Bejng Unversty of
A B-Snake Model Using Statistical and Geometric Information - Applications to Medical Images
 A B-Snake Model Usng Statstcal and Geometrc Informaton - Applcatons to Medcal Images Yue Wang, Eam Khwang Teoh and Dnggang Shen 2 School of Electrcal and Electronc Engneerng, Nanyang Technologcal Unversty
A B-Snake Model Usng Statstcal and Geometrc Informaton - Applcatons to Medcal Images Yue Wang, Eam Khwang Teoh and Dnggang Shen 2 School of Electrcal and Electronc Engneerng, Nanyang Technologcal Unversty
Improved SIFT-Features Matching for Object Recognition
 Improved SIFT-Features Matchng for Obect Recognton Fara Alhwarn, Chao Wang, Danela Rstć-Durrant, Axel Gräser Insttute of Automaton, Unversty of Bremen, FB / NW Otto-Hahn-Allee D-8359 Bremen Emals: {alhwarn,wang,rstc,ag}@at.un-bremen.de
Improved SIFT-Features Matchng for Obect Recognton Fara Alhwarn, Chao Wang, Danela Rstć-Durrant, Axel Gräser Insttute of Automaton, Unversty of Bremen, FB / NW Otto-Hahn-Allee D-8359 Bremen Emals: {alhwarn,wang,rstc,ag}@at.un-bremen.de
A Lossless Watermarking Scheme for Halftone Image Authentication
 IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.6 No.2B, February 2006 147 A Lossless Watermarkng Scheme for Halftone Image Authentcaton Jeng-Shyang Pan, Hao Luo, and Zhe-Mng Lu,
IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.6 No.2B, February 2006 147 A Lossless Watermarkng Scheme for Halftone Image Authentcaton Jeng-Shyang Pan, Hao Luo, and Zhe-Mng Lu,
Efficient Compression of 3D Dynamic Mesh Sequences
 Effcent Compresson of 3D Dynamc Mesh Sequences Rachda Amoun and Wolfgang Straßer WSI / GRIS Unversty of Tübngen, Germany {amoun, strasser}@grs.un-tuebngen.de Fgure : Sample frames of the anmatons used
Effcent Compresson of 3D Dynamc Mesh Sequences Rachda Amoun and Wolfgang Straßer WSI / GRIS Unversty of Tübngen, Germany {amoun, strasser}@grs.un-tuebngen.de Fgure : Sample frames of the anmatons used
IMPLEMENTATION OF QIM BASED AUDIO WATERMARKING USING HYBRID TRANSFORM OF SWT-DCT-SVD METHODS OPTIMIZED WITH GENETIC ALORITHM
 IMPLEMENTATION OF QIM BASED AUDIO WATERMARKING USING HYBRID TRANSFORM OF SWT-DCT-SVD METHODS OPTIMIZED WITH GENETIC ALORITHM Ryan Amnullah 1, Gelar Budman 2, Irma Saftr 3 1, 2, 3 FakultasTeknk Elektro,
IMPLEMENTATION OF QIM BASED AUDIO WATERMARKING USING HYBRID TRANSFORM OF SWT-DCT-SVD METHODS OPTIMIZED WITH GENETIC ALORITHM Ryan Amnullah 1, Gelar Budman 2, Irma Saftr 3 1, 2, 3 FakultasTeknk Elektro,
Related-Mode Attacks on CTR Encryption Mode
 Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Enhanced AMBTC for Image Compression using Block Classification and Interpolation
 Internatonal Journal of Computer Applcatons (0975 8887) Volume 5 No.0, August 0 Enhanced AMBTC for Image Compresson usng Block Classfcaton and Interpolaton S. Vmala Dept. of Comp. Scence Mother Teresa
Internatonal Journal of Computer Applcatons (0975 8887) Volume 5 No.0, August 0 Enhanced AMBTC for Image Compresson usng Block Classfcaton and Interpolaton S. Vmala Dept. of Comp. Scence Mother Teresa
Secure and Fast Fingerprint Authentication on Smart Card
 SETIT 2005 3 rd Internatonal Conference: Scences of Electronc, Technologes of Informaton and Telecommuncatons March 27-31, 2005 TUNISIA Secure and Fast Fngerprnt Authentcaton on Smart Card Y. S. Moon*,
SETIT 2005 3 rd Internatonal Conference: Scences of Electronc, Technologes of Informaton and Telecommuncatons March 27-31, 2005 TUNISIA Secure and Fast Fngerprnt Authentcaton on Smart Card Y. S. Moon*,
Constructing Minimum Connected Dominating Set: Algorithmic approach
 Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
A New Watermarking Method of 3D Mesh Model
 TELKOMNIKA Indonesan Journal of Electrcal Engneerng Vol., No., Februar 4, pp. 6 ~ 67 DOI: http://dx.do.org/.59/telomna.v.85 6 A New Watermarng Method of D Mesh Model Lu Jng*, Wang Ynghu, He Wenjuan, L
TELKOMNIKA Indonesan Journal of Electrcal Engneerng Vol., No., Februar 4, pp. 6 ~ 67 DOI: http://dx.do.org/.59/telomna.v.85 6 A New Watermarng Method of D Mesh Model Lu Jng*, Wang Ynghu, He Wenjuan, L
Outline. Discriminative classifiers for image recognition. Where in the World? A nearest neighbor recognition example 4/14/2011. CS 376 Lecture 22 1
 4/14/011 Outlne Dscrmnatve classfers for mage recognton Wednesday, Aprl 13 Krsten Grauman UT-Austn Last tme: wndow-based generc obect detecton basc ppelne face detecton wth boostng as case study Today:
4/14/011 Outlne Dscrmnatve classfers for mage recognton Wednesday, Aprl 13 Krsten Grauman UT-Austn Last tme: wndow-based generc obect detecton basc ppelne face detecton wth boostng as case study Today:
LECTURE : MANIFOLD LEARNING
 LECTURE : MANIFOLD LEARNING Rta Osadchy Some sldes are due to L.Saul, V. C. Raykar, N. Verma Topcs PCA MDS IsoMap LLE EgenMaps Done! Dmensonalty Reducton Data representaton Inputs are real-valued vectors
LECTURE : MANIFOLD LEARNING Rta Osadchy Some sldes are due to L.Saul, V. C. Raykar, N. Verma Topcs PCA MDS IsoMap LLE EgenMaps Done! Dmensonalty Reducton Data representaton Inputs are real-valued vectors
Support Vector Machines
 /9/207 MIST.6060 Busness Intellgence and Data Mnng What are Support Vector Machnes? Support Vector Machnes Support Vector Machnes (SVMs) are supervsed learnng technques that analyze data and recognze patterns.
/9/207 MIST.6060 Busness Intellgence and Data Mnng What are Support Vector Machnes? Support Vector Machnes Support Vector Machnes (SVMs) are supervsed learnng technques that analyze data and recognze patterns.
Suppression for Luminance Difference of Stereo Image-Pair Based on Improved Histogram Equalization
 Suppresson for Lumnance Dfference of Stereo Image-Par Based on Improved Hstogram Equalzaton Zhao Llng,, Zheng Yuhu 3, Sun Quansen, Xa Deshen School of Computer Scence and Technology, NJUST, Nanjng, Chna.School
Suppresson for Lumnance Dfference of Stereo Image-Par Based on Improved Hstogram Equalzaton Zhao Llng,, Zheng Yuhu 3, Sun Quansen, Xa Deshen School of Computer Scence and Technology, NJUST, Nanjng, Chna.School
Lecture 13: High-dimensional Images
 Lec : Hgh-dmensonal Images Grayscale Images Lecture : Hgh-dmensonal Images Math 90 Prof. Todd Wttman The Ctadel A grayscale mage s an nteger-valued D matrx. An 8-bt mage takes on values between 0 and 55.
Lec : Hgh-dmensonal Images Grayscale Images Lecture : Hgh-dmensonal Images Math 90 Prof. Todd Wttman The Ctadel A grayscale mage s an nteger-valued D matrx. An 8-bt mage takes on values between 0 and 55.
Classifier Selection Based on Data Complexity Measures *
 Classfer Selecton Based on Data Complexty Measures * Edth Hernández-Reyes, J.A. Carrasco-Ochoa, and J.Fco. Martínez-Trndad Natonal Insttute for Astrophyscs, Optcs and Electroncs, Lus Enrque Erro No.1 Sta.
Classfer Selecton Based on Data Complexty Measures * Edth Hernández-Reyes, J.A. Carrasco-Ochoa, and J.Fco. Martínez-Trndad Natonal Insttute for Astrophyscs, Optcs and Electroncs, Lus Enrque Erro No.1 Sta.
Modular PCA Face Recognition Based on Weighted Average
 odern Appled Scence odular PCA Face Recognton Based on Weghted Average Chengmao Han (Correspondng author) Department of athematcs, Lny Normal Unversty Lny 76005, Chna E-mal: hanchengmao@163.com Abstract
odern Appled Scence odular PCA Face Recognton Based on Weghted Average Chengmao Han (Correspondng author) Department of athematcs, Lny Normal Unversty Lny 76005, Chna E-mal: hanchengmao@163.com Abstract
2D Raster Graphics. Integer grid Sequential (left-right, top-down) scan. Computer Graphics
 2D Graphcs 2D Raster Graphcs Integer grd Sequental (left-rght, top-down scan j Lne drawng A ver mportant operaton used frequentl, block dagrams, bar charts, engneerng drawng, archtecture plans, etc. curves
2D Graphcs 2D Raster Graphcs Integer grd Sequental (left-rght, top-down scan j Lne drawng A ver mportant operaton used frequentl, block dagrams, bar charts, engneerng drawng, archtecture plans, etc. curves
Geometrically Invariant Watermarking Scheme Based on Local Feature Points
 JOURNAL OF MULTIMEDIA, VOL. 7, NO. 3, JUNE 0 3 Geometrcally Invarant Watermarkng Scheme Based on Local Feature Ponts L Jng School of Computer and Informaton Engneerng, Henan Unversty of Economcs and Law,
JOURNAL OF MULTIMEDIA, VOL. 7, NO. 3, JUNE 0 3 Geometrcally Invarant Watermarkng Scheme Based on Local Feature Ponts L Jng School of Computer and Informaton Engneerng, Henan Unversty of Economcs and Law,
Load Balancing for Hex-Cell Interconnection Network
 Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
