Assembly Instruction Level Reverse Execution for Debugging
|
|
|
- Cori Fox
- 5 years ago
- Views:
Transcription
1 Assembly Instruction Level Reverse Execution for Debugging PhD Dissertation Defense by Tankut Akgul Advisor: Vincent J. Mooney School of Electrical and Computer Engineering Georgia Institute of Technology March 2004
2 Outline Background Reverse Execution Definition Previous Work Reverse Execution Methodology Program Slicing Definition Previous Work Program Slicing Methodology Experimental Results 2
3 Background Start the program Detect an error Determine the bug location(s) Restart the program Remove the bug(s) and recompile the program Errorfree program Debugging is a repetitive process! 3
4 Outline Background Reverse Execution Definition Previous Work Reverse Execution Methodology Program Slicing Definition Previous Work Program Slicing Methodology Experimental Results 4
5 Definition of Reverse Execution Reverse execution: Taking a program T from its current state S i to a previous state S j Source code level reverse execution: Reverse execution where S j can be as early as one source code statement before state S i Instruction level reverse execution: Reverse execution where S j can be as early as one assembly instruction before state S i 5
6 Previous Work Debugging Optimistic Simulations Database Applications Interactive Systems Editors Program development environments 6
7 Previous Work in Reverse Execution Restore earlier state Periodic checkpointing Incremental checkpointing Regenerate part of earlier state Source transformation Build a reversible processor with reversible circuit elements (Pendulum) 7
8 Previous Work in Reverse Execution Periodic checkpointing: Memory usage for state saving: 12KB + 12KB + 12KB + 12KB + 12KB = 60KB Incremental checkpointing: Memory usage for state saving: 4KB + 8KB + 4KB + 4KB + 4KB = 24KB = 4KB 8
9 Previous Work in Reverse Execution Source Transformation: Sample () { int x, y; y = 0; x += 10; if (x > 15) y++; else y; } Source code State saved for each destructive operation Sample () { int x, y; save y; y = 0; x += 10; if (x > 15) { b = 0; y++; } else { b = 1; y; } } Transformed code Sample_rev () { int x, y; if (b == 0) y; else y++; x = 10; restore y; } Reverse code Destructive operation: An operation whose target operand is different than its source operands C. Carothers, K. Perumalla and R. Fujimoto, Efficient Optimistic Parallel Simulations using Reverse Computation, in Proceedings of ACM/IEEE/SCS Workshop on Parallel and Distributed Simulation (PADS), Atlanta, USA, May
10 Previous Work in Reverse Execution Heavy use of state saving State saving = memory and time overheads during forward execution No direct instruction level reverse execution support 10
11 Outline Background Reverse Execution Definition Previous Work Reverse Execution Methodology Program Slicing Definition Previous Work Program Slicing Methodology Experimental Results 11
12 Reverse Execution Methodology Assumptions: State that cannot be modified directly does not include debugging information E.g., condition status register Physical memory is treated as a uniform entity Exact physical memory state is not preserved E.g., a value not in cache can be brought into cache after recovery Sequential execution model Indirect calls are made to welldefined target points 12
13 Reverse Execution Methodology We define the state of a processor as follows: S = ( PC, M', R' ) PC : program counter M' : directly modified memory values R' : directly modified register values In order to reverse execute a program, do the following: Construct a reverse program RT for an input program T Recover M' and R' by executing RT in place of T Recover the program counter value by using the correspondence between T and RT 13
14 Reverse Execution Methodology Reverse Code Generation (RCG) steps: 1. Divide the original program into program partitions 2. Generate the reverse of the instructions. The reverse of an instruction is called a Reverse Instruction Group (RIG) 3. Combine the RIGs 3.a Combine the RIGs to generate the reverse of each basic block (RBB) 3.b Combine the RBBs to generate the reverse of each partition 3.c Combine the reverse partitions to generate the reverse of whole program 14
15 Reverse Execution Methodology start Partition the input program while constructing a call graph Build a modified value graph for current partition Read an instruction α from current partition Generate a RIG for α N end of BB? Y Connect the RBB to reverse program Connect the reverse partition to reverse program, go to next partition N end of partition? Y end of program? Y end N 15
16 Step 1: Program Partitioning Partitions are regions of code delimited by function call or indirect branch instructions that may exist within the original code e.g., in PowerPC instruction set: bl : function call instruction blr : branch to link register instruction (indirect) 16
17 main: Step1: Program Partitioning li r 3,0x5 bl foo addi r 12, r 12, 1 blr foo: li r 11, 3 ori r 12, r 3, 15 divw r 10, r 3, r 11 cmpwi r 10, 100 bg L1 sub r 11, r 3, r 12 b L2 L1: addi r 12, r 10, 1 sub r 11, r 12, r 3 L2: mullw r 12, r 11, r 10 blr first partition of main second partition of main single partition of foo main: li r 3,0x5 bl foo addi r 12, r 12, 1 blr foo: li r 11, 3 ori r 12, r 3, 15 divw r 10, r 3, r 11 cmpwi r 10, 100 bg L1 sub r 11, r 3, r 12 b L2 L1: addi r 12, r 10, 1 sub r 11, r 12, r 3 L2: mullw r 12, r 11, r 10 blr 17
18 Methodology (Continued) Reverse Code Generation (RCG) steps: 1. Divide the program into program partitions (single entrysingle exit regions). 2. Generate the reverse of the instructions. The reverse of an instruction is called a Reverse Instruction Group (RIG) 3. Combine the RIGs 3.a Combine the RIGs to generate the reverse of each basic block (RBB) 3.b Combine the RBBs to generate the reverse of each partition 3.c Combine the reverse partitions to generate the reverse of whole program 18
19 Step 2: RIG Generation Three techniques to generate a RIG: 1. Redefine technique 2. Extractfromuse technique 3. State saving technique 19
20 Step 2: RIG Generation (Cont.) r 1 = r 2 + r 3 start r 2 < 0 false true r 1 = r 2 Find the definitions of r 1 reaching P Recover r 1 by selectively reexecuting the found definitions or by selectively extracting the found definitions out of later uses of those definitions r 4 = r 1 + r 3 r 1 = r 2 4 P α RIG for α : if r 2 < 0 r 1 = r 4 r 3 or r 1 = r 2 else r 1 = r 2 + r 3 exit Extractfromuse Redefine 20
21 Step2: RIG Generation (Cont.) r 1 1 Select operator r 1 = r 2 + r 3 r 1 3 = Φ(r 11,r 12 ) r 4 1 r 1 4 start r 2 < 0 false true r 1 2 r 4 = r 1 + r 3 r 1 = r 2 4 exit r 1 = r 2 P α P' Rename Values Generate a directed graph called modified value graph (MVG) Find the definition of r 1 reaching P Recover r 1 using available nodes at P' r 1 0 RIG for α : r 4 0 r 1 2 r 20 < 0 r 1 3 Φ r 1 4 r r r r 0 2 r 0 3 if r 2 < 0 r 1 = r 4 r 3 or r 1 = r 2 else r 1 = r 2 + r 3 21
22 Methodology (Continued) Three steps to generate a complete reverse program: 1. Divide the program into program partitions (single entrysingle exit regions). 2. Generate the reverse of the instructions. The reverse of an instruction is called a Reverse Instruction Group (RIG) 3. Combine the RIGs 3.a Combine the RIGs to generate the reverse of each basic block (RBB) 3.b Combine the RBBs to generate the reverse of each partition 3.c Combine the reverse partitions to generate the reverse of whole program 22
23 Step 3.a: Constructing the RBBs BB 1 i 1 i 2 RBB 1 RIG 2 RIG 1 BB 2 i 3 BB 3 i 5 i 4 i 6 i 7 RBB 2 RIG 4 RBB 3 RIG 7 RIG 3 RIG 6 RIG 5 BB 4 i 8 RBB 4 RIG 8 Bottomup placement order within BBs 23
24 Step 3.b: Combining the RBBs start? start BB 1 α 1 α 2 RBB 6 RIG 9 α 5 BB 2 BB 3 cb α 6 BB 4? α 8 α 7? α 3 α 4 BB 5 RBB 5 RBB RIG 4 7 RIG 8 RBB 3 cb RIG RBB 4 RIG 6 2 RIG 3 RIG 5 BB 6 α 9 exit BB: Basic Block RBB: Reverse of a BB cb: Conditional branch RBB 1 RIG 2 RIG 1 cb exit 24
25 Step 3.c: Combining the Reverse Partitions A 0 A 1 A 2 main: cmp r1, r2 bl g; blr g: mtlr r0 bclrl // call g // return m 1 m 2 g 1 // set a func. ptr. // call by the func. ptr. A 0 start m 1 g 1 m 2 A 2 A 2 A 2 A 0 A 1 A 3 A 2 g 2 A 2 A 4 h A 3 A 4 blr h: blr // return // return g 2 h end A 3 Push addresses on the dynamically taken edges into stack Pop the addresses from stack during reverse execution and branch to reverses of popped addresses 25
26 Recovering the Program Counter Input Program RCG algorithm Reverse Program Reverse of the input program Program being debugged Inversion Table Designates the entry point into the reverse program for every instruction in the input program Input instruction address 0x0 0x4 0x8 RIG address 0x4000 0x3FFC 0x3FE0 26
27 Complexity Byte Recover (Node n) { if (n.available == true) return true; m children(n) do { stat = Recover(m); if stat!= available break; } m parents(n) do { stat = Recover(m); if (stat == available) { z siblings(n) do { stat = Recover(z); if (stat!= available) break; } } if (stat == available) break; } Write_RIG(); } N : number of nodes in an MVG # of assembly instructions in a code M : average degree of a node (# of neighbors) K : maximum number of repetitive applications of redefine and extractfromuse techniques allowed M is independent of total code size for fixed partition size Complexity = O(N M K ) On a 1 GHz CPU, 1 iteration 1 nsec N = 1,000,000, M = 10, K = 3 1 sec 27
28 Outline Background Reverse Execution Definition Previous Work Reverse Execution Methodology Program Slicing Definition Previous Work Program Slicing Methodology Experimental Results 28
29 Program Slicing Static Slice: A set of program statements that may influence a variable V at statement S. C = (V, S) is a static slicing criterion. Dynamic Slice: A set of program statements that influence a variable V at an execution instance q of statement S given a set of program inputs X. C = (X, V, S q ) is a dynamic slicing criterion. 29
30 Program Slicing Two ways to influence a variable: Data dependency y = z; x = y + 1; x is data dependent on y and z Control dependency if (y < 0) x = 1; x is control dependent on y A slice is a set of all statements that compute dependencies of a variable 30
31 Program Slicing Pass = 0 ; Fail = 0 ; Count = 0 ; while (!eof()) { TotalMarks=0; scanf("%d",marks); if (Marks >= 40) Pass = Pass + 1; if (Marks < 40) Fail = Fail + 1; Count = Count + 1; TotalMarks = TotalMarks+Marks ; } average = TotalMarks/Count; /* This is the point of interest */ printf("the average is %d\n",average) ; PassRate = Pass/Count*100 ; printf( Pass rate is %d\n",passrate) ; Original Program while (!eof()) { TotalMarks=0; scanf("%d",marks); Count = Count + 1; TotalMarks = TotalMarks+Marks; } average = TotalMarks/Count; printf("the average is %d\n",average) ; Slice w.r.t.. average average Example is taken from Prof. Mark Harman s webpage at 31
32 Previous Work in Program Slicing Static Slicing (Weiser) Control flow graph analysis No runtime information Static Slicing (Ottenstein et al.) Program dependency graph analysis No runtime information Dynamic Slicing (Korel and Laski) Control flow graph analysis Program execution trajectory Dynamic Slicing (Agrawal et al.) Dynamic dependence graph (DDG) analysis Program execution trajectory 32
33 Outline Background Reverse Execution Definition Previous Work Reverse Execution Methodology Program Slicing Definition Previous Work Program Slicing Methodology Experimental Results 33
34 RCG with Slicing (RCGS) Forward execution Input program Dynamic slicing table Fullscale reverse execution Reverse program local MVGs Global MVG Reduced reverse program Reverse execution along a dynamic slice Orange arrows indicate the base static analysis performed only once per program Blue arrows indicate the extended static analysis performed for each dynamic slice Green arrows indicate the actions performed by the debugger 34
35 Contributions of RCGS Reverse execution along a dynamic slice Faster reverse execution No complete execution trajectory is required Less runtime memory usage Not only reveals dynamic slice instructions but also obtains runtime values of variables More efficient debugging 35
36 Reverse Execution Along a Dynamic Slice stw li li ori li %r0,0x4(%r1) %r8,0x64 %r10,0x1 %r12,%r10,0x0 %r11,0x1 Determine data dependencies statically Determine control flow dynamically cmpw %r8,%r11 blt 0x1000c0 add %r9,%r12,%r10 ori %r10,%r12,0x0 ori %r12,%r9,0x0 addi %r11,%r11,0x1 b 0x1000a4 Merge static information with dynamic information to reverse execute along the dynamic slice bclr 0x14,0x0 36
37 Generation of a Reduced Reverse Program 37
38 Experimentation Platform Background Debug Mode (BDM) Interface PC Windows 2000 MBX860 MPC860 processor 4MB DRAM, 2MB Flash RTC, four 16bit timers, watchdog 38
39 Comparisons Reverse Execution with Incremental State Saving (ISS) Save state before each instruction Reverse Execution with Incremental State Saving for Destructive Instructions (ISSDI) Save state before each destructive instruction Reverse Execution with RCG 39
40 Benchmarks Benchmark Executable object size (bytes) Selection sort 3104 Matrix multiply 3308 ADPCM encoder 6908 LZW 4636 ADPCM: Adaptive Differential Pulse Code Modulation LZW: Lempel Ziv Welch 40
41 Benchmarks Benchmark Selection sort (100 inputs) Selection sort (1000 inputs) Selection sort (10000 inputs) Matrix multiply (4x4) Matrix multiply (40x40) Matrix multiply (400x400) ADPCM (32KB input data) ADPCM (64KB input data) ADPCM (128KB input data) LZW (1KB input data) LZW (4KB input data) LZW (16KB input data) 1 tick = 0.4 microseconds on MBX860 Raw Execution Time (decrementer ticks) 21,187 2,000, ,539, , ,183, , ,280 1,496,649 1,380,413 16,063, ,451,339 41
42 Experiment 1 Instrument each benchmark with state saving instructions at appropriate points for ISS, ISSDI and RCG Forward execute each instrumented benchmark from the beginning until the end Measure forward execution times 42
43 Instrumented Forward Execution Time Benchmark ISS ISSDI RCG ISS/ RCG ISSDI/ RCG Selection sort (100 inputs) X 1.24X Selection sort (1000 inputs) X 1.27X Selection sort (10000 inputs) X 1.27X Matrix multiply (4x4) X 1.70X Matrix multiply (40x40) X 1.88X Matrix multiply (400x400) X 1.90X ADPCM (32KB input data) X 1.20X ADPCM (64KB input data) X 1.20X ADPCM (128KB input data) X 1.20X LZW (1KB input data) X 1.31X LZW (4KB input data) X 1.34X LZW (16KB input data) X 1.31X ISS: Incremental State Saving, ISSDI: Incremental State Saving for Destructive Instructions 43
44 Forward Execution Time Overhead % Overhead ISS ISSDI RCG % Overhead ISS ISSDI RCG Selection Sort (100) Selection Sort (1000) Selection Sort (10000) Matrix Multiply (4x4) Matrix Multiply (40x40) Matrix Multiply (400x400) % Overhead LZW (1KB) LZW (4KB) LZW (16KB) ISS ISSDI RCG % Overhead ADPCM (32KB) ADPCM (64KB) ADPCM (128KB) ISS ISSDI RCG Overhead = instrumented execution time raw execution time raw execution time 44
45 Experiment 2 Reverse execute each benchmark from the end until the beginning (by executing the reverse versions) Measure reverse execution times 45
46 Reverse Execution Time Benchmark ISS ISSDI RCG ISS/ RCG ISSDI/ RCG Selection sort (100 inputs) X 0.74X Selection sort (1000 inputs) Selection sort (10000 inputs) Matrix multiply (4x4) X 0.60X Matrix multiply (40x40) X 0.53X Matrix multiply (400x400) ADPCM (32KB input data) X 0.82X ADPCM (64KB input data) X ADPCM (128KB input data) LZW (1KB input data) LZW (4KB input data) LZW (16KB input data)
47 Experiment 3 Forward execute each instrumented benchmark from the beginning until the end Measure memory usage for state saving 47
48 Memory Usage for State Saving ISS (KB) ISSDI (KB) RCG (KB) ISS / RCG ISSDI / RCG Selection sort (100 inputs) X 6.3X Selection sort (1000 inputs) X 27X Selection sort (10000 inputs) X 55X Matrix multiply (4x4) X 14X Matrix multiply (40x40) X 143X Matrix multiply (400x400) X 1404X ADPCM (32KB input data) X 2X ADPCM (64KB input data) X 2X ADPCM (128KB input data) X 2X LZW (1KB input data) X 35X LZW (4KB input data) X 112X LZW (16KB input data) X 354X 48
49 Experiment 4 Forward execute original 400x400 matrix multiply from the beginning to various intermediate points and measure the execution times Reverse execute 400x400 matrix multiply using RCG from the end to various intermediate points and measure reverse execution times 49
50 Program Reexecute Approach vs. RCG 500 Time (seconds) Outermost loop iteration count Forward execution Reverse execution via RCG starting point for forward execution 400x400 matrix multiply starting point for reverse execution 50
51 Experiment 5 Extract three slices for each benchmark Reverse execute each benchmark fully starting from end of each slice until beginning of each slice Reverse execute each benchmark along computed slices only Measure the reverse execution times 51
52 Fullscale Reverse Execution vs. Reverse Execution Along a Slice time (microseconds) time (seconds) slice1 slice2 slice3 Selection Sort (10 inputs) slice1 slice2 slice3 ADPCM Encoder (128KB input) full reverse execution time (microseconds) time (seconds) slice1 slice2 slice3 Matrix Multiply (4x4) slice1 slice2 slice3 LZW (128KB input) reverse execution along a dynamic slice 52
53 Fullscale Reverse Execution vs. Reverse Execution Along a Slice time (microseconds) 1.00E E E E E E E E E E E E E E E E+01 4x4 multiply 40x40 multiply 400x400 multiply Matrix Multiply time (microseconds) 1.00E E E E E E E E E E E E E E integers 100 integers 1000 integers Selection Sort full reverse execution reverse execution along the dynamic slice 53
54 Experiment 6 Extract three slices for each benchmark Measure average runtime memory requirement for reverse execution along three slices with RCGS Measure average runtime memory requirement for reverse execution along three slices with ISS plus execution trajectory (ET) approach 54
55 Runtime Memory Requirements bytes RCGS ISS+ET Selection Sort (10 inputs) bytes RCGS ISS+ET Matrix Multiply (4x4) kilobytes RCGS ISS+ET megabytes RCGS ISS+ET ADPCM Encoder (128KB input) LZW (128KB input) RCGS memory usage ISS memory usage ET memory usage RCGS: RCG with Slicing ET: Execution Trajectory 55
56 Reverse Debugger Execute forward Step forward Execute backward Step backward Source window Memory window Register window Breakpoint window 56
57 Reverse Debugger Reverse Debugger Code Specs Number of C lines ~7000 Number of files 19 57
58 Conclusion Reduced debugging time with localized reexecutions Very low time and memory overheads in forward execution by using reverse code Reverse execution up to an assembly instruction level granularity Dynamic slicing support to speed up reverse execution without execution trajectory requirement 58
59 Publications T. Akgul, V. J. Mooney and S. Pande, A Fast Assembly Level Reverse Execution Method via Dynamic Slicing, accepted for publication in Proceedings of the 26 th International Conference on Software Engineering (ICSE'04), May T. Akgul and V. J. Mooney, Assembly Instruction Level Reverse Execution for Debugging, submitted to Transactions on Software Engineering and Methodology (TOSEM) on December 2002, accepted with minor revision. T. Akgul and V. J. Mooney, Instructionlevel Reverse Execution for Debugging, Proceedings of the Workshop on Program Analysis for Software Tools and Engineering (PASTE'02), pp. 1825, November T. Akgul and V. J. Mooney, Instructionlevel Reverse Execution for Debugging, Technical Report GITCC0249, September T. Akgul, P. Kuacharoen, V. Mooney and V. Madisetti, "A Debugger RTOS for Embedded Systems," Proceedings of the 27th EUROMICRO Conference (EUROMICRO'01), pp , September P. Kuacharoen, T. Akgul, V. Mooney and V. Madisetti, "Adaptability, Extensibility, and Flexibility in RealTime Operating Systems," Proceedings of the EUROMICRO Symposium on Digital Systems Design (EUROMICRO'01), pp , September T. Akgul, P. Kuacharoen, V. J. Mooney and V. K. Madisetti, A Debugger Operating System for Embedded Systems,'' U.S. Patent Application, no , April 17, P. Kuacharoen, T. Akgul, V. J. Mooney and V. K. Madisetti, A Dynamic Operating System,'' U.S. Patent Application, no , April 17,
60 Thank you! 60
ASSEMBLY INSTRUCTION LEVEL REVERSE EXECUTION FOR DEBUGGING. Tankut Akgul
 ASSEMBLY INSTRUCTION LEVEL REVERSE EXECUTION FOR DEBUGGING A Thesis Presented to The Academic Faculty by Tankut Akgul In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy School
ASSEMBLY INSTRUCTION LEVEL REVERSE EXECUTION FOR DEBUGGING A Thesis Presented to The Academic Faculty by Tankut Akgul In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy School
Embedded Software Streaming via Block Stream
 Embedded Software Streaming via Block Stream A Dissertation by Pramote Kucharoen Dissertation Advisor Professor Vincent J. Mooney III 7 April 2004 Outline Introduction Related Work Block Streaming Stream-Enabled
Embedded Software Streaming via Block Stream A Dissertation by Pramote Kucharoen Dissertation Advisor Professor Vincent J. Mooney III 7 April 2004 Outline Introduction Related Work Block Streaming Stream-Enabled
Instruction-level Reverse Execution for Debugging
 Instruction-level Reverse Execution for Debugging Tankut Akgul and Vincent J. Mooney III School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta, GA 333 {tankut, mooney}@ece.gatech.edu
Instruction-level Reverse Execution for Debugging Tankut Akgul and Vincent J. Mooney III School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta, GA 333 {tankut, mooney}@ece.gatech.edu
Class 6. Review; questions Assign (see Schedule for links) Slicing overview (cont d) Problem Set 3: due 9/8/09. Program Slicing
 Class 6 Review; questions Assign (see Schedule for links) Slicing overview (cont d) Problem Set 3: due 9/8/09 1 Program Slicing 2 1 Program Slicing 1. Slicing overview 2. Types of slices, levels of slices
Class 6 Review; questions Assign (see Schedule for links) Slicing overview (cont d) Problem Set 3: due 9/8/09 1 Program Slicing 2 1 Program Slicing 1. Slicing overview 2. Types of slices, levels of slices
(5) Question 2. Give the two most important factors for effective debugging. Jonathan W. Valvano
 EE445M/EE380L Quiz 1 Spring 2013 Page 1 of 5 First Name: Last Name: March 1, 2013, 10:00 to 10:50am Quiz 1 is a closed book exam. You may have one 8.5 by 11 inch sheet of hand-written crib notes, but no
EE445M/EE380L Quiz 1 Spring 2013 Page 1 of 5 First Name: Last Name: March 1, 2013, 10:00 to 10:50am Quiz 1 is a closed book exam. You may have one 8.5 by 11 inch sheet of hand-written crib notes, but no
Machine Language Instructions Introduction. Instructions Words of a language understood by machine. Instruction set Vocabulary of the machine
 Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Branch Addressing. Jump Addressing. Target Addressing Example. The University of Adelaide, School of Computer Science 28 September 2015
 Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Computer Organization & Assembly Language Programming (CSE 2312)
 Computer Organization & Assembly Language Programming (CSE 2312) Lecture 15: Running ARM Programs in QEMU and Debugging with gdb Taylor Johnson Announcements and Outline Homework 5 due Thursday Midterm
Computer Organization & Assembly Language Programming (CSE 2312) Lecture 15: Running ARM Programs in QEMU and Debugging with gdb Taylor Johnson Announcements and Outline Homework 5 due Thursday Midterm
Practical Malware Analysis
 Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Run-time Environments. Lecture 13. Prof. Alex Aiken Original Slides (Modified by Prof. Vijay Ganesh) Lecture 13
 Run-time Environments Lecture 13 by Prof. Vijay Ganesh) Lecture 13 1 What have we covered so far? We have covered the front-end phases Lexical analysis (Lexer, regular expressions,...) Parsing (CFG, Top-down,
Run-time Environments Lecture 13 by Prof. Vijay Ganesh) Lecture 13 1 What have we covered so far? We have covered the front-end phases Lexical analysis (Lexer, regular expressions,...) Parsing (CFG, Top-down,
Course Administration
 Fall 2018 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture Introduction 4/4 Avinash Karanth Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701
Fall 2018 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture Introduction 4/4 Avinash Karanth Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701
SECTION 5: STRUCTURED PROGRAMMING IN MATLAB. ENGR 112 Introduction to Engineering Computing
 SECTION 5: STRUCTURED PROGRAMMING IN MATLAB ENGR 112 Introduction to Engineering Computing 2 Conditional Statements if statements if else statements Logical and relational operators switch case statements
SECTION 5: STRUCTURED PROGRAMMING IN MATLAB ENGR 112 Introduction to Engineering Computing 2 Conditional Statements if statements if else statements Logical and relational operators switch case statements
Systems Architecture I
 Systems Architecture I Topics Assemblers, Linkers, and Loaders * Alternative Instruction Sets ** *This lecture was derived from material in the text (sec. 3.8-3.9). **This lecture was derived from material
Systems Architecture I Topics Assemblers, Linkers, and Loaders * Alternative Instruction Sets ** *This lecture was derived from material in the text (sec. 3.8-3.9). **This lecture was derived from material
Stack Frames. September 2, Indiana University. Geoffrey Brown, Bryce Himebaugh 2015 September 2, / 15
 Stack Frames Geoffrey Brown Bryce Himebaugh Indiana University September 2, 2016 Geoffrey Brown, Bryce Himebaugh 2015 September 2, 2016 1 / 15 Outline Preserving Registers Saving and Restoring Registers
Stack Frames Geoffrey Brown Bryce Himebaugh Indiana University September 2, 2016 Geoffrey Brown, Bryce Himebaugh 2015 September 2, 2016 1 / 15 Outline Preserving Registers Saving and Restoring Registers
CS 352 Compilers: Principles and Practice Final Examination, 12/11/05
 CS 352 Compilers: Principles and Practice Final Examination, 12/11/05 Instructions: Read carefully through the whole exam first and plan your time. Note the relative weight of each question and part (as
CS 352 Compilers: Principles and Practice Final Examination, 12/11/05 Instructions: Read carefully through the whole exam first and plan your time. Note the relative weight of each question and part (as
LAB C Translating Utility Classes
 LAB C Translating Utility Classes Perform the following groups of tasks: LabC1.s 1. Create a directory to hold the files for this lab. 2. Create and run the following two Java classes: public class IntegerMath
LAB C Translating Utility Classes Perform the following groups of tasks: LabC1.s 1. Create a directory to hold the files for this lab. 2. Create and run the following two Java classes: public class IntegerMath
Preventing Stalls: 1
 Preventing Stalls: 1 2 PipeLine Pipeline efficiency Pipeline CPI = Ideal pipeline CPI + Structural Stalls + Data Hazard Stalls + Control Stalls Ideal pipeline CPI: best possible (1 as n ) Structural hazards:
Preventing Stalls: 1 2 PipeLine Pipeline efficiency Pipeline CPI = Ideal pipeline CPI + Structural Stalls + Data Hazard Stalls + Control Stalls Ideal pipeline CPI: best possible (1 as n ) Structural hazards:
MIPS function continued
 MIPS function continued Review Functions Series of related instructions one after another in memory Called through the jal instruction Pointed to by a label like any other Returns by calling Stack Top
MIPS function continued Review Functions Series of related instructions one after another in memory Called through the jal instruction Pointed to by a label like any other Returns by calling Stack Top
MODULE 4 INSTRUCTIONS: LANGUAGE OF THE MACHINE
 MODULE 4 INSTRUCTIONS: LANGUAGE OF THE MACHINE 1 ARCHITECTURE MODEL The basic instruction set of a computer is comprised of sequences of REGISTER TRANSFERS. Example: Add A, B, C Register B # A
MODULE 4 INSTRUCTIONS: LANGUAGE OF THE MACHINE 1 ARCHITECTURE MODEL The basic instruction set of a computer is comprised of sequences of REGISTER TRANSFERS. Example: Add A, B, C Register B # A
Since ESE GATE PSUs ELECTRICAL ENGINEERING COMPUTER FUNDAMENTALS. Volume - 1 : Study Material with Classroom Practice Questions
 Since 20 ESE GATE PSUs ELECTRICAL ENGINEERING COMPUTER FUNDAMENTALS Volume - : Study Material with Classroom Practice Questions Computer Fundamentals (Solutions for Classroom Practice Questions). Number
Since 20 ESE GATE PSUs ELECTRICAL ENGINEERING COMPUTER FUNDAMENTALS Volume - : Study Material with Classroom Practice Questions Computer Fundamentals (Solutions for Classroom Practice Questions). Number
Islamic University Gaza Engineering Faculty Department of Computer Engineering ECOM 2125: Assembly Language LAB. Lab # 7. Procedures and the Stack
 Islamic University Gaza Engineering Faculty Department of Computer Engineering ECOM 2125: Assembly Language LAB Lab # 7 Procedures and the Stack April, 2014 1 Assembly Language LAB Runtime Stack and Stack
Islamic University Gaza Engineering Faculty Department of Computer Engineering ECOM 2125: Assembly Language LAB Lab # 7 Procedures and the Stack April, 2014 1 Assembly Language LAB Runtime Stack and Stack
Control Instructions. Computer Organization Architectures for Embedded Computing. Thursday, 26 September Summary
 Control Instructions Computer Organization Architectures for Embedded Computing Thursday, 26 September 2013 Many slides adapted from: Computer Organization and Design, Patterson & Hennessy 4th Edition,
Control Instructions Computer Organization Architectures for Embedded Computing Thursday, 26 September 2013 Many slides adapted from: Computer Organization and Design, Patterson & Hennessy 4th Edition,
Control Instructions
 Control Instructions Tuesday 22 September 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class Instruction Set
Control Instructions Tuesday 22 September 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class Instruction Set
MIPS Functions and the Runtime Stack
 MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
 Chapter 1 Microprocessor architecture ECE 3120 Dr. Mohamed Mahmoud http://iweb.tntech.edu/mmahmoud/ mmahmoud@tntech.edu Outline 1.1 Computer hardware organization 1.1.1 Number System 1.1.2 Computer hardware
Chapter 1 Microprocessor architecture ECE 3120 Dr. Mohamed Mahmoud http://iweb.tntech.edu/mmahmoud/ mmahmoud@tntech.edu Outline 1.1 Computer hardware organization 1.1.1 Number System 1.1.2 Computer hardware
Program Analysis. Program Analysis
 Program Analysis Class #4 Program Analysis Dynamic Analysis 1 Static VS Dynamic Analysis Static analysis operates on a model of the SW (without executing it) If successful, produces definitive information
Program Analysis Class #4 Program Analysis Dynamic Analysis 1 Static VS Dynamic Analysis Static analysis operates on a model of the SW (without executing it) If successful, produces definitive information
Name: University of Michigan uniqname: (NOT your student ID number!)
 The University of Michigan - Department of EECS EECS370 Introduction to Computer Organization Midterm Exam 1 October 22, 2009 Name: University of Michigan uniqname: (NOT your student ID number!) Open book,
The University of Michigan - Department of EECS EECS370 Introduction to Computer Organization Midterm Exam 1 October 22, 2009 Name: University of Michigan uniqname: (NOT your student ID number!) Open book,
Chapter 2. Computer Abstractions and Technology. Lesson 4: MIPS (cont )
 Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
sarm User Guide Note that a space must appear before the operation field because any word beginning in the first column is a label
 sarm User Guide The sarm is program that implements an experimental CPU simulator. It is called experimental because it is not yet complete, and it also incorporates facilities that are not conventionally
sarm User Guide The sarm is program that implements an experimental CPU simulator. It is called experimental because it is not yet complete, and it also incorporates facilities that are not conventionally
Grundlagen Microcontroller Processor Core. Günther Gridling Bettina Weiss
 Grundlagen Microcontroller Processor Core Günther Gridling Bettina Weiss 1 Processor Core Architecture Instruction Set Lecture Overview 2 Processor Core Architecture Computes things > ALU (Arithmetic Logic
Grundlagen Microcontroller Processor Core Günther Gridling Bettina Weiss 1 Processor Core Architecture Instruction Set Lecture Overview 2 Processor Core Architecture Computes things > ALU (Arithmetic Logic
EECE.3170: Microprocessor Systems Design I Summer 2017 Homework 4 Solution
 1. (40 points) Write the following subroutine in x86 assembly: Recall that: int f(int v1, int v2, int v3) { int x = v1 + v2; urn (x + v3) * (x v3); Subroutine arguments are passed on the stack, and can
1. (40 points) Write the following subroutine in x86 assembly: Recall that: int f(int v1, int v2, int v3) { int x = v1 + v2; urn (x + v3) * (x v3); Subroutine arguments are passed on the stack, and can
ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design
 ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu School of Engineering Brown University Spring 2014 Sources: Computer
ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu School of Engineering Brown University Spring 2014 Sources: Computer
Separating Access Control Policy, Enforcement, and Functionality in Extensible Systems. Robert Grimm University of Washington
 Separating Access Control Policy, Enforcement, and Functionality in Extensible Systems Robert Grimm University of Washington Extensions Added to running system Interact through low-latency interfaces Form
Separating Access Control Policy, Enforcement, and Functionality in Extensible Systems Robert Grimm University of Washington Extensions Added to running system Interact through low-latency interfaces Form
Chapter 2 Instructions Sets. Hsung-Pin Chang Department of Computer Science National ChungHsing University
 Chapter 2 Instructions Sets Hsung-Pin Chang Department of Computer Science National ChungHsing University Outline Instruction Preliminaries ARM Processor SHARC Processor 2.1 Instructions Instructions sets
Chapter 2 Instructions Sets Hsung-Pin Chang Department of Computer Science National ChungHsing University Outline Instruction Preliminaries ARM Processor SHARC Processor 2.1 Instructions Instructions sets
Architecture II. Computer Systems Laboratory Sungkyunkwan University
 MIPS Instruction ti Set Architecture II Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Making Decisions (1) Conditional operations Branch to a
MIPS Instruction ti Set Architecture II Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Making Decisions (1) Conditional operations Branch to a
Computer Organization & Assembly Language Programming. CSE 2312 Lecture 15 Addressing and Subroutine
 Computer Organization & Assembly Language Programming CSE 2312 Lecture 15 Addressing and Subroutine 1 Sections in 8088 Code TEXT section, for the processor instructions. DATA section for the initialization
Computer Organization & Assembly Language Programming CSE 2312 Lecture 15 Addressing and Subroutine 1 Sections in 8088 Code TEXT section, for the processor instructions. DATA section for the initialization
Computer Organization & Assembly Language Programming (CSE 2312)
 Computer Organization & Assembly Language Programming (CSE 2312) Lecture 16: Processor Pipeline Introduction and Debugging with GDB Taylor Johnson Announcements and Outline Homework 5 due today Know how
Computer Organization & Assembly Language Programming (CSE 2312) Lecture 16: Processor Pipeline Introduction and Debugging with GDB Taylor Johnson Announcements and Outline Homework 5 due today Know how
An Overview of the BLITZ Computer Hardware
 An Overview of the BLITZ Computer Hardware Introduction Harry H. Porter III Department of Computer Science Portland State University The BLITZ computer was designed solely to support the development of
An Overview of the BLITZ Computer Hardware Introduction Harry H. Porter III Department of Computer Science Portland State University The BLITZ computer was designed solely to support the development of
UNIT-II. Part-2: CENTRAL PROCESSING UNIT
 Page1 UNIT-II Part-2: CENTRAL PROCESSING UNIT Stack Organization Instruction Formats Addressing Modes Data Transfer And Manipulation Program Control Reduced Instruction Set Computer (RISC) Introduction:
Page1 UNIT-II Part-2: CENTRAL PROCESSING UNIT Stack Organization Instruction Formats Addressing Modes Data Transfer And Manipulation Program Control Reduced Instruction Set Computer (RISC) Introduction:
Chapter 6 Programming the LC-3
 Chapter 6 Programming the LC-3 Based on slides McGraw-Hill Additional material 4/5 Lewis/Martin Aside: Booting the Computer How does it all begin? We have LC-3 hardware and a program, but what next? Initial
Chapter 6 Programming the LC-3 Based on slides McGraw-Hill Additional material 4/5 Lewis/Martin Aside: Booting the Computer How does it all begin? We have LC-3 hardware and a program, but what next? Initial
Complex Instruction Sets
 Complex Instruction Sets CSE 410, Spring 2004 Computer Systems http://www.cs.washington.edu/education/courses/410/04sp/ 5-May-2004 cse410-16-cisc 2004 University of Washington 1 Reading Readings and References»
Complex Instruction Sets CSE 410, Spring 2004 Computer Systems http://www.cs.washington.edu/education/courses/410/04sp/ 5-May-2004 cse410-16-cisc 2004 University of Washington 1 Reading Readings and References»
Summer 2017 ECE 3056
 Assignment 2 Due Dates: Part I C++ Program: 11:55 pm, Friday June 2 nd, 2017 Part II Homework Problems: Prior to the beginning of class, Thursday June 1 st, 2017 NOTE: for students in Atlanta, you are
Assignment 2 Due Dates: Part I C++ Program: 11:55 pm, Friday June 2 nd, 2017 Part II Homework Problems: Prior to the beginning of class, Thursday June 1 st, 2017 NOTE: for students in Atlanta, you are
WearDrive: Fast and Energy Efficient Storage for Wearables
 WearDrive: Fast and Energy Efficient Storage for Wearables Reza Shisheie Cleveland State University CIS 601 Wearable Computing: A New Era 2 Wearable Computing: A New Era Notifications Fitness/Healthcare
WearDrive: Fast and Energy Efficient Storage for Wearables Reza Shisheie Cleveland State University CIS 601 Wearable Computing: A New Era 2 Wearable Computing: A New Era Notifications Fitness/Healthcare
Programming the ARM. Computer Design 2002, Lecture 4. Robert Mullins
 Programming the ARM Computer Design 2002, Lecture 4 Robert Mullins 2 Quick Recap The Control Flow Model Ordered list of instructions, fetch/execute, PC Instruction Set Architectures Types of internal storage
Programming the ARM Computer Design 2002, Lecture 4 Robert Mullins 2 Quick Recap The Control Flow Model Ordered list of instructions, fetch/execute, PC Instruction Set Architectures Types of internal storage
The CPU and Memory. How does a computer work? How does a computer interact with data? How are instructions performed? Recall schematic diagram:
 The CPU and Memory How does a computer work? How does a computer interact with data? How are instructions performed? Recall schematic diagram: 1 Registers A register is a permanent storage location within
The CPU and Memory How does a computer work? How does a computer interact with data? How are instructions performed? Recall schematic diagram: 1 Registers A register is a permanent storage location within
Bisection Debugging. 1 Introduction. Thomas Gross. Carnegie Mellon University. Preliminary version
 Bisection Debugging Thomas Gross School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Institut für Computer Systeme ETH Zürich CH 8092 Zürich Preliminary version Abstract This paper
Bisection Debugging Thomas Gross School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Institut für Computer Systeme ETH Zürich CH 8092 Zürich Preliminary version Abstract This paper
Computer Architecture. MIPS Instruction Set Architecture
 Computer Architecture MIPS Instruction Set Architecture Instruction Set Architecture An Abstract Data Type Objects Registers & Memory Operations Instructions Goal of Instruction Set Architecture Design
Computer Architecture MIPS Instruction Set Architecture Instruction Set Architecture An Abstract Data Type Objects Registers & Memory Operations Instructions Goal of Instruction Set Architecture Design
Changing the Embedded World TM. Module 3: Getting Started Debugging
 Changing the Embedded World TM Module 3: Getting Started Debugging Module Objectives: Section 1: Introduce Debugging Techniques Section 2: PSoC In-Circuit Emulator (ICE) Section 3: Hands on Debugging a
Changing the Embedded World TM Module 3: Getting Started Debugging Module Objectives: Section 1: Introduce Debugging Techniques Section 2: PSoC In-Circuit Emulator (ICE) Section 3: Hands on Debugging a
Computer Architecture
 Computer Architecture Chapter 2 Instructions: Language of the Computer Fall 2005 Department of Computer Science Kent State University Assembly Language Encodes machine instructions using symbols and numbers
Computer Architecture Chapter 2 Instructions: Language of the Computer Fall 2005 Department of Computer Science Kent State University Assembly Language Encodes machine instructions using symbols and numbers
Exam 1. Date: March 1, 2019
 Exam 1 Date: March 1, 2019 UT EID: Printed Name: Last, First Your signature is your promise that you have not cheated and will not cheat on this exam, nor will you help others to cheat on this exam: Signature:
Exam 1 Date: March 1, 2019 UT EID: Printed Name: Last, First Your signature is your promise that you have not cheated and will not cheat on this exam, nor will you help others to cheat on this exam: Signature:
PHBREAK: RISC ISP architecture the MIPS ISP. you read: text Chapter 3 CS 350
 PHBREAK: RISC ISP architecture the MIPS ISP you read: text Chapter 3 Summary of main points: Two objectives; 1] Describe the MIPS ISP architecture 2] expose the Reduced Instruction Set Computer (RISC)
PHBREAK: RISC ISP architecture the MIPS ISP you read: text Chapter 3 Summary of main points: Two objectives; 1] Describe the MIPS ISP architecture 2] expose the Reduced Instruction Set Computer (RISC)
ECE 473 Computer Architecture and Organization Project: Design of a Five Stage Pipelined MIPS-like Processor Project Team TWO Objectives
 ECE 473 Computer Architecture and Organization Project: Design of a Five Stage Pipelined MIPS-like Processor Due: December 8, 2011 Instructor: Dr. Yifeng Zhu Project Team This is a team project. All teams
ECE 473 Computer Architecture and Organization Project: Design of a Five Stage Pipelined MIPS-like Processor Due: December 8, 2011 Instructor: Dr. Yifeng Zhu Project Team This is a team project. All teams
Computer Architecture, EIT090 exam
 Department of Information Technology Lund University Computer Architecture, EIT090 exam 15-12-2004 I. Problem 1 (15 points) Briefly (1-2 sentences) describe the following items/concepts concerning computer
Department of Information Technology Lund University Computer Architecture, EIT090 exam 15-12-2004 I. Problem 1 (15 points) Briefly (1-2 sentences) describe the following items/concepts concerning computer
컴퓨터개념및실습. 기말고사 review
 컴퓨터개념및실습 기말고사 review Sorting results Sort Size Compare count Insert O(n 2 ) Select O(n 2 ) Bubble O(n 2 ) Merge O(n log n) Quick O(n log n) 5 4 (lucky data set) 9 24 5 10 9 36 5 15 9 40 14 39 15 45 (unlucky
컴퓨터개념및실습 기말고사 review Sorting results Sort Size Compare count Insert O(n 2 ) Select O(n 2 ) Bubble O(n 2 ) Merge O(n log n) Quick O(n log n) 5 4 (lucky data set) 9 24 5 10 9 36 5 15 9 40 14 39 15 45 (unlucky
Stacks and Subroutines
 Chapters 8 Stacks and Subroutines Embedded Systems with ARM Cortext-M Updated: Tuesday, March 6, 2018 Basic Idea llarge programs are hard to handle lwe can break them to smaller programs lthey are called
Chapters 8 Stacks and Subroutines Embedded Systems with ARM Cortext-M Updated: Tuesday, March 6, 2018 Basic Idea llarge programs are hard to handle lwe can break them to smaller programs lthey are called
Data-Flow Based Detection of Loop Bounds
 Data-Flow Based Detection of Loop Bounds Christoph Cullmann and Florian Martin AbsInt Angewandte Informatik GmbH Science Park 1, D-66123 Saarbrücken, Germany cullmann,florian@absint.com, http://www.absint.com
Data-Flow Based Detection of Loop Bounds Christoph Cullmann and Florian Martin AbsInt Angewandte Informatik GmbH Science Park 1, D-66123 Saarbrücken, Germany cullmann,florian@absint.com, http://www.absint.com
Chapter 2A Instructions: Language of the Computer
 Chapter 2A Instructions: Language of the Computer Copyright 2009 Elsevier, Inc. All rights reserved. Instruction Set The repertoire of instructions of a computer Different computers have different instruction
Chapter 2A Instructions: Language of the Computer Copyright 2009 Elsevier, Inc. All rights reserved. Instruction Set The repertoire of instructions of a computer Different computers have different instruction
Adventures In Real-Time Performance Tuning, Part 2
 Adventures In Real-Time Performance Tuning, Part 2 The real-time for Linux patchset does not guarantee adequate real-time behavior for all target platforms. When using real-time Linux on a new platform
Adventures In Real-Time Performance Tuning, Part 2 The real-time for Linux patchset does not guarantee adequate real-time behavior for all target platforms. When using real-time Linux on a new platform
Repetition and Loop Statements Chapter 5
 Repetition and Loop Statements Chapter 5 1 Chapter Objectives To understand why repetition is an important control structure in programming To learn about loop control variables and the three steps needed
Repetition and Loop Statements Chapter 5 1 Chapter Objectives To understand why repetition is an important control structure in programming To learn about loop control variables and the three steps needed
This is a handout for source details that are would be impossible to read off a slide. Also, it should prove handy for later reference.
 GDC 2012 March 5-9 Runtime CPU Performance Spike Detection using Manual and Compiler Automated Instrumentation Adisak Pochanayon : adisak@wbgames.com Principal Software Engineer, Mortal Kombat Team Netherrealm
GDC 2012 March 5-9 Runtime CPU Performance Spike Detection using Manual and Compiler Automated Instrumentation Adisak Pochanayon : adisak@wbgames.com Principal Software Engineer, Mortal Kombat Team Netherrealm
Chapter 4 C Program Control
 1 Chapter 4 C Program Control Copyright 2007 by Deitel & Associates, Inc. and Pearson Education Inc. All Rights Reserved. 2 Chapter 4 C Program Control Outline 4.1 Introduction 4.2 The Essentials of Repetition
1 Chapter 4 C Program Control Copyright 2007 by Deitel & Associates, Inc. and Pearson Education Inc. All Rights Reserved. 2 Chapter 4 C Program Control Outline 4.1 Introduction 4.2 The Essentials of Repetition
GCC2 versus GCC4 compiling AltiVec code
 GCC2 versus GCC4 compiling AltiVec code Grzegorz Kraszewski 1. Introduction An official compiler for MorphOS operating system is still GCC 2.95.3. It is considered outdated
GCC2 versus GCC4 compiling AltiVec code Grzegorz Kraszewski 1. Introduction An official compiler for MorphOS operating system is still GCC 2.95.3. It is considered outdated
ECE251: Tuesday September 11
 ECE251: Tuesday September 11 Finish Branch related instructions Stack Subroutines Note: Lab 3 is a 2 week lab, starting this week and covers the Stack and Subroutines. Labs: Lab #2 is due this week. Lab
ECE251: Tuesday September 11 Finish Branch related instructions Stack Subroutines Note: Lab 3 is a 2 week lab, starting this week and covers the Stack and Subroutines. Labs: Lab #2 is due this week. Lab
CS 61c: Great Ideas in Computer Architecture
 MIPS Instruction Formats July 2, 2014 Review New registers: $a0-$a3, $v0-$v1, $ra, $sp New instructions: slt, la, li, jal, jr Saved registers: $s0-$s7, $sp, $ra Volatile registers: $t0-$t9, $v0-$v1, $a0-$a3
MIPS Instruction Formats July 2, 2014 Review New registers: $a0-$a3, $v0-$v1, $ra, $sp New instructions: slt, la, li, jal, jr Saved registers: $s0-$s7, $sp, $ra Volatile registers: $t0-$t9, $v0-$v1, $a0-$a3
ARM Cortex M3 Instruction Set Architecture. Gary J. Minden March 29, 2016
 ARM Cortex M3 Instruction Set Architecture Gary J. Minden March 29, 2016 1 Calculator Exercise Calculate: X = (45 * 32 + 7) / (65 2 * 18) G. J. Minden 2014 2 Instruction Set Architecture (ISA) ISAs define
ARM Cortex M3 Instruction Set Architecture Gary J. Minden March 29, 2016 1 Calculator Exercise Calculate: X = (45 * 32 + 7) / (65 2 * 18) G. J. Minden 2014 2 Instruction Set Architecture (ISA) ISAs define
Functions. Ray Seyfarth. August 4, Bit Intel Assembly Language c 2011 Ray Seyfarth
 Functions Ray Seyfarth August 4, 2011 Functions We will write C compatible function C++ can also call C functions using extern "C" {...} It is generally not sensible to write complete assembly programs
Functions Ray Seyfarth August 4, 2011 Functions We will write C compatible function C++ can also call C functions using extern "C" {...} It is generally not sensible to write complete assembly programs
CS 61C: Great Ideas in Computer Architecture. MIPS Instruction Formats
 CS 61C: Great Ideas in Computer Architecture MIPS Instruction Formats Instructor: Justin Hsia 6/27/2012 Summer 2012 Lecture #7 1 Review of Last Lecture New registers: $a0-$a3, $v0-$v1, $ra, $sp Also: $at,
CS 61C: Great Ideas in Computer Architecture MIPS Instruction Formats Instructor: Justin Hsia 6/27/2012 Summer 2012 Lecture #7 1 Review of Last Lecture New registers: $a0-$a3, $v0-$v1, $ra, $sp Also: $at,
Evolution of ISAs. Instruction set architectures have changed over computer generations with changes in the
 Evolution of ISAs Instruction set architectures have changed over computer generations with changes in the cost of the hardware density of the hardware design philosophy potential performance gains One
Evolution of ISAs Instruction set architectures have changed over computer generations with changes in the cost of the hardware density of the hardware design philosophy potential performance gains One
ECE251: Tuesday September 12
 ECE251: Tuesday September 12 Finish Branch related instructions Stack Subroutines Note: Lab 3 is a 2 week lab, starting this week and covers the Stack and Subroutines. Labs: Lab #2 is due this week. Lab
ECE251: Tuesday September 12 Finish Branch related instructions Stack Subroutines Note: Lab 3 is a 2 week lab, starting this week and covers the Stack and Subroutines. Labs: Lab #2 is due this week. Lab
ECE251: Tuesday September 18
 ECE251: Tuesday September 18 Subroutine Parameter Passing (Important) Allocating Memory in Subroutines (Important) Recursive Subroutines (Good to know) Debugging Hints Programming Hints Preview of I/O
ECE251: Tuesday September 18 Subroutine Parameter Passing (Important) Allocating Memory in Subroutines (Important) Recursive Subroutines (Good to know) Debugging Hints Programming Hints Preview of I/O
CS107 Handout 13 Spring 2008 April 18, 2008 Computer Architecture: Take II
 CS107 Handout 13 Spring 2008 April 18, 2008 Computer Architecture: Take II Example: Simple variables Handout written by Julie Zelenski and Nick Parlante A variable is a location in memory. When a variable
CS107 Handout 13 Spring 2008 April 18, 2008 Computer Architecture: Take II Example: Simple variables Handout written by Julie Zelenski and Nick Parlante A variable is a location in memory. When a variable
Last time: forwarding/stalls. CS 6354: Branch Prediction (con t) / Multiple Issue. Why bimodal: loops. Last time: scheduling to avoid stalls
 CS 6354: Branch Prediction (con t) / Multiple Issue 14 September 2016 Last time: scheduling to avoid stalls 1 Last time: forwarding/stalls add $a0, $a2, $a3 ; zero or more instructions sub $t0, $a0, $a1
CS 6354: Branch Prediction (con t) / Multiple Issue 14 September 2016 Last time: scheduling to avoid stalls 1 Last time: forwarding/stalls add $a0, $a2, $a3 ; zero or more instructions sub $t0, $a0, $a1
MIPS R-format Instructions. Representing Instructions. Hexadecimal. R-format Example. MIPS I-format Example. MIPS I-format Instructions
 Representing Instructions Instructions are encoded in binary Called machine code MIPS instructions Encoded as 32-bit instruction words Small number of formats encoding operation code (opcode), register
Representing Instructions Instructions are encoded in binary Called machine code MIPS instructions Encoded as 32-bit instruction words Small number of formats encoding operation code (opcode), register
Instruction Set Principles and Examples. Appendix B
 Instruction Set Principles and Examples Appendix B Outline What is Instruction Set Architecture? Classifying ISA Elements of ISA Programming Registers Type and Size of Operands Addressing Modes Types of
Instruction Set Principles and Examples Appendix B Outline What is Instruction Set Architecture? Classifying ISA Elements of ISA Programming Registers Type and Size of Operands Addressing Modes Types of
EPPC Exception Processing
 10-1 Exception Terms User Mode Supervisor Mode The Privilege Level that Applications run in. The Privilege Level that the Operating System runs in. Also called Privileged Mode Exception An event which
10-1 Exception Terms User Mode Supervisor Mode The Privilege Level that Applications run in. The Privilege Level that the Operating System runs in. Also called Privileged Mode Exception An event which
Computer Architecture Homework #1 Due: September 7, 2007 (F) (4 PM in ITT 305 mailbox or under my office door, ITT 313)
 Computer Architecture Homework #1 Due: September 7, 2007 (F) (4 PM in ITT 305 mailbox or under my office door, ITT 313) Type of Instruction Memory Access (Load and Store) Move Load Address Arithmetic Instruction
Computer Architecture Homework #1 Due: September 7, 2007 (F) (4 PM in ITT 305 mailbox or under my office door, ITT 313) Type of Instruction Memory Access (Load and Store) Move Load Address Arithmetic Instruction
An Assembler for the MSSP Distiller Eric Zimmerman University of Illinois, Urbana Champaign
 An Assembler for the MSSP Distiller Eric Zimmerman University of Illinois, Urbana Champaign Abstract It is important to have a means of manually testing a potential optimization before laboring to fully
An Assembler for the MSSP Distiller Eric Zimmerman University of Illinois, Urbana Champaign Abstract It is important to have a means of manually testing a potential optimization before laboring to fully
Thomas Polzer Institut für Technische Informatik
 Thomas Polzer tpolzer@ecs.tuwien.ac.at Institut für Technische Informatik Branch to a labeled instruction if a condition is true Otherwise, continue sequentially beq rs, rt, L1 if (rs == rt) branch to
Thomas Polzer tpolzer@ecs.tuwien.ac.at Institut für Technische Informatik Branch to a labeled instruction if a condition is true Otherwise, continue sequentially beq rs, rt, L1 if (rs == rt) branch to
A Processor. Kevin Walsh CS 3410, Spring 2010 Computer Science Cornell University. See: P&H Chapter , 4.1-3
 A Processor Kevin Walsh CS 3410, Spring 2010 Computer Science Cornell University See: P&H Chapter 2.16-20, 4.1-3 Let s build a MIPS CPU but using Harvard architecture Basic Computer System Registers ALU
A Processor Kevin Walsh CS 3410, Spring 2010 Computer Science Cornell University See: P&H Chapter 2.16-20, 4.1-3 Let s build a MIPS CPU but using Harvard architecture Basic Computer System Registers ALU
A Novel Deadlock Avoidance Algorithm and Its Hardware Implementation
 A ovel Deadlock Avoidance Algorithm and Its Hardware Implementation + Jaehwan Lee and *Vincent* J. Mooney III Hardware/Software RTOS Group Center for Research on Embedded Systems and Technology (CREST)
A ovel Deadlock Avoidance Algorithm and Its Hardware Implementation + Jaehwan Lee and *Vincent* J. Mooney III Hardware/Software RTOS Group Center for Research on Embedded Systems and Technology (CREST)
CS 61C: Great Ideas in Computer Architecture More RISC-V Instructions and How to Implement Functions
 CS 61C: Great Ideas in Computer Architecture More RISC-V Instructions and How to Implement Functions Instructors: Krste Asanović and Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 9/14/17 Fall
CS 61C: Great Ideas in Computer Architecture More RISC-V Instructions and How to Implement Functions Instructors: Krste Asanović and Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 9/14/17 Fall
Project Debugging with MDK-ARM
 Project Debugging with MDK-ARM Notes: This document assumes MDK-ARM Version 5.xx (µvision5 ) is installed with the required ST-Link USB driver, device family pack (STM32F4xx for STM32F4-Discovery board;
Project Debugging with MDK-ARM Notes: This document assumes MDK-ARM Version 5.xx (µvision5 ) is installed with the required ST-Link USB driver, device family pack (STM32F4xx for STM32F4-Discovery board;
CS650 Computer Architecture. Lecture 9 Memory Hierarchy - Main Memory
 CS65 Computer Architecture Lecture 9 Memory Hierarchy - Main Memory Andrew Sohn Computer Science Department New Jersey Institute of Technology Lecture 9: Main Memory 9-/ /6/ A. Sohn Memory Cycle Time 5
CS65 Computer Architecture Lecture 9 Memory Hierarchy - Main Memory Andrew Sohn Computer Science Department New Jersey Institute of Technology Lecture 9: Main Memory 9-/ /6/ A. Sohn Memory Cycle Time 5
A Processor! Hakim Weatherspoon CS 3410, Spring 2010 Computer Science Cornell University. See: P&H Chapter , 4.1-3
 A Processor! Hakim Weatherspoon CS 3410, Spring 2010 Computer Science Cornell University See: P&H Chapter 2.16-20, 4.1-3 Announcements! HW2 available later today HW2 due in one week and a half Work alone
A Processor! Hakim Weatherspoon CS 3410, Spring 2010 Computer Science Cornell University See: P&H Chapter 2.16-20, 4.1-3 Announcements! HW2 available later today HW2 due in one week and a half Work alone
Instruction Set Architecture. "Speaking with the computer"
 Instruction Set Architecture "Speaking with the computer" The Instruction Set Architecture Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture Digital Design
Instruction Set Architecture "Speaking with the computer" The Instruction Set Architecture Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture Digital Design
CSCI 402: Computer Architectures. Instructions: Language of the Computer (4) Fengguang Song Department of Computer & Information Science IUPUI
 CSCI 402: Computer Architectures Instructions: Language of the Computer (4) Fengguang Song Department of Computer & Information Science IUPUI op Instruction address 6 bits 26 bits Jump Addressing J-type
CSCI 402: Computer Architectures Instructions: Language of the Computer (4) Fengguang Song Department of Computer & Information Science IUPUI op Instruction address 6 bits 26 bits Jump Addressing J-type
Emulation. Michael Jantz
 Emulation Michael Jantz Acknowledgements Slides adapted from Chapter 2 in Virtual Machines: Versatile Platforms for Systems and Processes by James E. Smith and Ravi Nair Credit to Prasad A. Kulkarni some
Emulation Michael Jantz Acknowledgements Slides adapted from Chapter 2 in Virtual Machines: Versatile Platforms for Systems and Processes by James E. Smith and Ravi Nair Credit to Prasad A. Kulkarni some
Basic C Programming (2) Bin Li Assistant Professor Dept. of Electrical, Computer and Biomedical Engineering University of Rhode Island
 Basic C Programming (2) Bin Li Assistant Professor Dept. of Electrical, Computer and Biomedical Engineering University of Rhode Island Data Types Basic Types Enumerated types The type void Derived types
Basic C Programming (2) Bin Li Assistant Professor Dept. of Electrical, Computer and Biomedical Engineering University of Rhode Island Data Types Basic Types Enumerated types The type void Derived types
Linux Memory Layout. Lecture 6B Machine-Level Programming V: Miscellaneous Topics. Linux Memory Allocation. Text & Stack Example. Topics.
 Lecture 6B Machine-Level Programming V: Miscellaneous Topics Topics Linux Memory Layout Understanding Pointers Buffer Overflow Upper 2 hex digits of address Red Hat v. 6.2 ~1920MB memory limit FF C0 Used
Lecture 6B Machine-Level Programming V: Miscellaneous Topics Topics Linux Memory Layout Understanding Pointers Buffer Overflow Upper 2 hex digits of address Red Hat v. 6.2 ~1920MB memory limit FF C0 Used
Processor. Han Wang CS3410, Spring 2012 Computer Science Cornell University. See P&H Chapter , 4.1 4
 Processor Han Wang CS3410, Spring 2012 Computer Science Cornell University See P&H Chapter 2.16 20, 4.1 4 Announcements Project 1 Available Design Document due in one week. Final Design due in three weeks.
Processor Han Wang CS3410, Spring 2012 Computer Science Cornell University See P&H Chapter 2.16 20, 4.1 4 Announcements Project 1 Available Design Document due in one week. Final Design due in three weeks.
Chapter 2. Instructions: Language of the Computer. Adapted by Paulo Lopes
 Chapter 2 Instructions: Language of the Computer Adapted by Paulo Lopes Instruction Set The repertoire of instructions of a computer Different computers have different instruction sets But with many aspects
Chapter 2 Instructions: Language of the Computer Adapted by Paulo Lopes Instruction Set The repertoire of instructions of a computer Different computers have different instruction sets But with many aspects
HW1 Solutions. Type Old Mix New Mix Cost CPI
 HW1 Solutions Problem 1 TABLE 1 1. Given the parameters of Problem 6 (note that int =35% and shift=5% to fix typo in book problem), consider a strength-reducing optimization that converts multiplies by
HW1 Solutions Problem 1 TABLE 1 1. Given the parameters of Problem 6 (note that int =35% and shift=5% to fix typo in book problem), consider a strength-reducing optimization that converts multiplies by
Black Box Debugging of Embedded Systems
 Black Box Debugging of Embedded Systems Introduction: Alexandru Ariciu Background in hacking Worked as a hacker for my whole life Worked in corporate security before (Pentester) Currently an ICS Penetration
Black Box Debugging of Embedded Systems Introduction: Alexandru Ariciu Background in hacking Worked as a hacker for my whole life Worked in corporate security before (Pentester) Currently an ICS Penetration
Memory management units
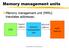 Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
2) Using the same instruction set for the TinyProc2, convert the following hex values to assembly language: x0f
 CS2 Fall 28 Exam 2 Name: ) The Logisim TinyProc2 has four instructions, each using 8 bits. The instruction format is DR SR SR2 OpCode with OpCodes of for add, for subtract, and for multiply. Load Immediate
CS2 Fall 28 Exam 2 Name: ) The Logisim TinyProc2 has four instructions, each using 8 bits. The instruction format is DR SR SR2 OpCode with OpCodes of for add, for subtract, and for multiply. Load Immediate
Summary: Open Questions:
 Summary: The paper proposes an new parallelization technique, which provides dynamic runtime parallelization of loops from binary single-thread programs with minimal architectural change. The realization
Summary: The paper proposes an new parallelization technique, which provides dynamic runtime parallelization of loops from binary single-thread programs with minimal architectural change. The realization
EN2910A: Advanced Computer Architecture Topic 02: Review of classical concepts
 EN2910A: Advanced Computer Architecture Topic 02: Review of classical concepts Prof. Sherief Reda School of Engineering Brown University S. Reda EN2910A FALL'15 1 Classical concepts (prerequisite) 1. Instruction
EN2910A: Advanced Computer Architecture Topic 02: Review of classical concepts Prof. Sherief Reda School of Engineering Brown University S. Reda EN2910A FALL'15 1 Classical concepts (prerequisite) 1. Instruction
Computing platforms. Design methodology. Consumer electronics architectures. System-level performance and power analysis.
 Computing platforms Design methodology. Consumer electronics architectures. System-level performance and power analysis. Evaluation boards Designed by CPU manufacturer or others. Includes CPU, memory,
Computing platforms Design methodology. Consumer electronics architectures. System-level performance and power analysis. Evaluation boards Designed by CPU manufacturer or others. Includes CPU, memory,
https://asd-pa.perfplusk12.com/admin/admin_curric_maps_display.aspx?m=5507&c=618&mo=18917&t=191&sy=2012&bl...
 Page 1 of 13 Units: - All - Teacher: ProgIIIJavaI, CORE Course: ProgIIIJavaI Year: 2012-13 Intro to Java How is data stored by a computer system? What does a compiler do? What are the advantages of using
Page 1 of 13 Units: - All - Teacher: ProgIIIJavaI, CORE Course: ProgIIIJavaI Year: 2012-13 Intro to Java How is data stored by a computer system? What does a compiler do? What are the advantages of using
Procedure Calling. Procedure Calling. Register Usage. 25 September CSE2021 Computer Organization
 CSE2021 Computer Organization Chapter 2: Part 2 Procedure Calling Procedure (function) performs a specific task and return results to caller. Supporting Procedures Procedure Calling Calling program place
CSE2021 Computer Organization Chapter 2: Part 2 Procedure Calling Procedure (function) performs a specific task and return results to caller. Supporting Procedures Procedure Calling Calling program place
