Applied Theorem Proving: Modelling Instruction Sets and Decompiling Machine Code. Anthony Fox University of Cambridge, Computer Laboratory
|
|
|
- Karin Wilkins
- 5 years ago
- Views:
Transcription
1 Applied Theorem Proving: Modelling Instruction Sets and Decompiling Machine Code Anthony Fox University of Cambridge, Computer Laboratory
2 Overview This talk will mainly focus on 1. Specifying instruction set architectures and briefly look at 2. Formally verifying machine-code programs
3 Instruction Set Architectures There are many architecture families, e.g. Alpha, ARM, MIPS, Motorola 68k, PA-RISC, PowerPC, SPARC, VAX and x86. Reference documentation is large, typically thousands of pages in length. Pseudo-code is frequently used in reference manuals when describing the semantics of instructions. This can vary from being sketchy (e.g. Intel s x86 pseudo-code is loose and contains English text) to quite rigorous and detailed (e.g. ARM). Official formal ISA models aren t in the public domain. Inhouse, simulators are normally written in some HDL (and/or C).
4 ISA Specification A couple of uses for formal ISA models are: The formalisation can act as a golden reference model. This could be used in hardware verification and for general validation work. A formal ISA model gives a precise meaning to programs, which can be used in the formal verification of code/compilers. At the moment, our group is most interested in the latter use case.
5 Styles of Formalization There are number of ways to formalize an architecture: 1. As a document containing a mathematical description. Can be readable, depending on choice of style. However, not especially useful as an artefact. 2. As code in a suitable general purpose programming language, e.g. in a well-defined functional programming language. Such languages are not that well known outside of Computer Science. Can result in fast emulation (especially Lisp). 3. As a specification in a theorem prover. Prover languages are even less well known, though typically functional in style. ACL2 is a theorem prover and programming language, which provides for fast emulation. Running HOL specifications is very slow in comparison. 4. As a specification in a domain specific language. This is the approach that we have now adopted.
6 L3 General Features ISA specifications were being written directly in HOL4 (approach 3). This had a few downsides. A new domain specific language was designed to make my life easier. Key features are: Looks imperative in style. Provides for a more natural description that is a bit closer to the pseudo-code found in reference manuals. Much easier to write and modify specifications. (In comparison to native HOL4 specifications.) L3 is not a hardware description language (HDL). The language is resolutely focussed on aiding the production of usable high-level ISA specifications. Provides export to HOL4. Provides native emulation support. (For initial testing.) Provides export to Standard ML. (For faster emulation.)
7 L3 Specific Language Features Good support for bit-vector operations. This is an essential feature. Supports pattern matching, including over bit-patterns. This is very useful when specifying instruction decoding. Helps in maintaining an instruction datatype. Used in specifying instruction decoding, encoding and assembly code parsing. Provides support for working with (system) registers that have named sub-fields (bit-ranges).
8 Under-specification and Non-determinism Computer architecture descriptions invariably contain various forms of looseness. For example, unpredictable and implementation dependent behaviour, unknown or don t care values, and non-deterministic choice. If there is lots of non-determinism then relational models are needed. ISAs are mostly deterministic, so we try to get away with writing functional specifications as much as possible. Functional models have the advantage of being easy to run. The specification corresponds with an emulator.
9 Under-specification and Non-determinism (2) L3 supports a number of ways to handle under-specification. There is a polymorphic value UNKNOWN. In HOL4 this corresponds with some fixed but unidentified value. When exporting to Standard ML a fixed choice is made, e.g. always 0, always false and so forth. You can use option types when you need to detect unknown values. For example, a value can be Some (expression) or None. You can write a specification that incorporates oracles. For example, the result is f(x) where the function f is supplied at runtime. One can raise a model exception. This corresponds with an exception in Standard ML (emulation will cease and an error will be reported).
10 L3 models To date, the following ISAs have been specified in L3: ARMv7-AR. Covers all architecture versions from ARMv4. No Neon instructions and partial floating-point support. MMU details are not modelled (they are implementation dependent). ARM-M0. The M architecture variants have a different underlying programmer s model. The specification includes cycles count information. x Covers a core subset of the instructions and just 64-bit mode. MIPS III (with some extensions). Includes a MIPS4k MMU, i.e. a model of a TLB.
11 Model Validation It is important to invest time and effort into validating ISA models. In the absence of official golden reference models, validation takes the form of running snippets of code in the model and comparing the results against development boards, emulators and PC cores. Various people have worked on this: Magnus Myreen for ARM and x Brian Campbell for ARM-M0. Mike Roe for MIPS. Validation provides some assurance but we must still be vigilant when using models.
12 Machine-code Verification Our main area of interest is the verification of low-level code. This includes supporting work on: Compilers and runtime libraries. CakeML University Cambridge and Kent. Operating system micro-kernels. Secure Embedded L4 (sel4) NICTA. Other groups at Cambridge are working on related research areas, e.g. adding security features to ISAs and concurrency memory models.
13 Machine-code Verification (2) Magnus Myreen has worked in the area of machine-code verification for a number of years. Our main tool is a decompiler. This takes machine-code as input and returns: 1. The definition of a HOL4 function. 2. A certificate theorem, which proves that this function s behaviour conforms exactly with running the machinecode. This provides a means to abstract away the large and complicated ISA model.
14 Decompiler example The following shows a call to the decompiler: val (f1_cert, f1_def) = arm_decomplib.arm_decompile_code "f1" `movw r0, #0xFFFF lsr r1, r1, #16 and r2, r2, r0, lsl #16 add r0, r1, r2`; The decompiler can accept ARM assembly code as input. This call defines a HOL4 function f1 as follows: f1 (r1,r2) = (let r0 = 65535w in let r1 = r1 16 in let r2 = r2 && r0 16 in let r0 = r1 + r2 in (r0,r1,r2))
15 Decompiler example (2) Note that the function f1 makes no reference to the ARM model itself. The certificate theorem makes the connection to the ISA model and justifies the definition. Similarly, we can decompile f2 (below right). f1 movw r0, #0xFFFF lsr r1, r1, #16 and r2, r2, r0, lsl #16 add r0, r1, r2`; f2 ror r2, r2, #16 movw r0, #0xFFFF and r2, r2, r0 ror r2, r2, #16 lsr r1, r1, #16 eor r0, r1, r2
16 Decompiler example (3) We can now prove that the function f2 is functionally identical to f1. That is, for all r1 and r2 f1 (r1, r2) = f2 (r1, r2) This is a simple proof in HOL4, since we can use the following tactic : simp [f1_def, f2_def] THEN blastlib.bblast_tac This simplifies our goal using the function definitions and then applies a bit-blasting tactic. This shows the two machine-code programs have exactly the same functionality. (They only differ in timing.) This example was simple because the programs were just sequential blocks of instructions. Code with loops/branches can be handled, provided the control flow is not too complex. The verification process can be manually guided.
17 Some links L3 and the ISA models can be downloaded from Details about the decompiler can be found at
18 Questions?
A Trustworthy Monadic Formalization of the ARMv7 Instruction Set Architecture. Anthony Fox and Magnus O. Myreen University of Cambridge
 A Trustworthy Monadic Formalization of the ARMv7 Instruction Set Architecture Anthony Fox and Magnus O. Myreen University of Cambridge Background Instruction set architectures play an important role in
A Trustworthy Monadic Formalization of the ARMv7 Instruction Set Architecture Anthony Fox and Magnus O. Myreen University of Cambridge Background Instruction set architectures play an important role in
Turning proof assistants into programming assistants
 Turning proof assistants into programming assistants ST Winter Meeting, 3 Feb 2015 Magnus Myréen Why? Why combine proof- and programming assistants? Why proofs? Testing cannot show absence of bugs. Some
Turning proof assistants into programming assistants ST Winter Meeting, 3 Feb 2015 Magnus Myréen Why? Why combine proof- and programming assistants? Why proofs? Testing cannot show absence of bugs. Some
Directions in ISA Specification. Anthony Fox. Computer Laboratory, University of Cambridge, UK
 Directions in ISA Specification Anthony Fox Computer Laboratory, University of Cambridge, UK Abstract. This rough diamond presents a new domain-specific language (DSL) for producing detailed models of
Directions in ISA Specification Anthony Fox Computer Laboratory, University of Cambridge, UK Abstract. This rough diamond presents a new domain-specific language (DSL) for producing detailed models of
Background. From my PhD (2009): Verified Lisp interpreter in ARM, x86 and PowerPC machine code
 Certification of high-level and low-level programs, IHP, Paris, 2014 CakeML A verified implementation of ML Ramana Kumar Magnus Myreen Michael Norrish Scott Owens Background From my PhD (2009): Verified
Certification of high-level and low-level programs, IHP, Paris, 2014 CakeML A verified implementation of ML Ramana Kumar Magnus Myreen Michael Norrish Scott Owens Background From my PhD (2009): Verified
Translation Validation for a Verified OS Kernel
 To appear in PLDI 13 Translation Validation for a Verified OS Kernel Thomas Sewell 1, Magnus Myreen 2, Gerwin Klein 1 1 NICTA, Australia 2 University of Cambridge, UK L4.verified sel4 = a formally verified
To appear in PLDI 13 Translation Validation for a Verified OS Kernel Thomas Sewell 1, Magnus Myreen 2, Gerwin Klein 1 1 NICTA, Australia 2 University of Cambridge, UK L4.verified sel4 = a formally verified
Verified compilers. Guest lecture for Compiler Construction, Spring Magnus Myréen. Chalmers University of Technology
 Guest lecture for Compiler Construction, Spring 2015 Verified compilers Magnus Myréen Chalmers University of Technology Mentions joint work with Ramana Kumar, Michael Norrish, Scott Owens and many more
Guest lecture for Compiler Construction, Spring 2015 Verified compilers Magnus Myréen Chalmers University of Technology Mentions joint work with Ramana Kumar, Michael Norrish, Scott Owens and many more
Randomised testing of a microprocessor model using SMT-solver state generation
 Randomised testing of a microprocessor model using SMT-solver state generation Brian Campbell Ian Stark LFCS, School of Informatics, University of Edinburgh, UK Rigorous Engineering for Mainstream Systems
Randomised testing of a microprocessor model using SMT-solver state generation Brian Campbell Ian Stark LFCS, School of Informatics, University of Edinburgh, UK Rigorous Engineering for Mainstream Systems
Directions in ISA Specification
 Directions in ISA Specification Anthony Fox Computer Laboratory, University of Cambridge, UK Abstract. This rough diamond presents a new domain-specific language (DSL) for producing detailed models of
Directions in ISA Specification Anthony Fox Computer Laboratory, University of Cambridge, UK Abstract. This rough diamond presents a new domain-specific language (DSL) for producing detailed models of
A New Verified Compiler Backend for CakeML. Yong Kiam Tan* Magnus O. Myreen Ramana Kumar Anthony Fox Scott Owens Michael Norrish
 A New Verified Compiler Backend for CakeML Yong Kiam Tan* Magnus O. Myreen Ramana Kumar Anthony Fox Scott Owens Michael Norrish 1 CakeML Has: references, modules, signatures, datatypes, exceptions,...
A New Verified Compiler Backend for CakeML Yong Kiam Tan* Magnus O. Myreen Ramana Kumar Anthony Fox Scott Owens Michael Norrish 1 CakeML Has: references, modules, signatures, datatypes, exceptions,...
CakeML. A verified implementation of ML. LFCS seminar, Edinburgh, May Magnus Myreen Chalmers University of Technology & University of Cambridge
 LFCS seminar, Edinburgh, May 2015 CakeML A verified implementation of ML Magnus Myreen Chalmers University of Technology & University of Cambridge Joint work with Ramana Kumar, Michael Norrish, Scott Owens
LFCS seminar, Edinburgh, May 2015 CakeML A verified implementation of ML Magnus Myreen Chalmers University of Technology & University of Cambridge Joint work with Ramana Kumar, Michael Norrish, Scott Owens
LYREBIRD David Cock
 davec@cse.unsw.edu.aullyrebird LYREBIRD David Cock λ What is the Motivation? Program proof is important, but there s more to do. NICTA Copyright c 2011 From Imagination to Impact 2 What is the Motivation?
davec@cse.unsw.edu.aullyrebird LYREBIRD David Cock λ What is the Motivation? Program proof is important, but there s more to do. NICTA Copyright c 2011 From Imagination to Impact 2 What is the Motivation?
Development of a Translator from LLVM to ACL2
 Development of a Translator from LLVM to ACL2 David Hardin, Jennifer Davis, David Greve, and Jedidiah McClurg July 2014 Introduction Research objectives: Reason about machine code generated from high-level
Development of a Translator from LLVM to ACL2 David Hardin, Jennifer Davis, David Greve, and Jedidiah McClurg July 2014 Introduction Research objectives: Reason about machine code generated from high-level
Chapter 2: Instructions How we talk to the computer
 Chapter 2: Instructions How we talk to the computer 1 The Instruction Set Architecture that part of the architecture that is visible to the programmer - instruction formats - opcodes (available instructions)
Chapter 2: Instructions How we talk to the computer 1 The Instruction Set Architecture that part of the architecture that is visible to the programmer - instruction formats - opcodes (available instructions)
Improved Tool Support for Machine-Code Decompilation in HOL4
 Improved Tool Support for Machine-Code Decompilation in HOL4 Anthony Fox University of Cambridge, UK Abstract. The HOL4 interactive theorem prover provides a sound logical environment for reasoning about
Improved Tool Support for Machine-Code Decompilation in HOL4 Anthony Fox University of Cambridge, UK Abstract. The HOL4 interactive theorem prover provides a sound logical environment for reasoning about
Towards a Practical, Verified Kernel
 Towards a Practical, Verified Kernel Kevin Elphinstone and Gerwin Klein, National ICT Australia and the University of New South Wales Philip Derrin, National ICT Australia Timothy Roscoe, ETH Zürich Gernot
Towards a Practical, Verified Kernel Kevin Elphinstone and Gerwin Klein, National ICT Australia and the University of New South Wales Philip Derrin, National ICT Australia Timothy Roscoe, ETH Zürich Gernot
EC 413 Computer Organization
 EC 413 Computer Organization Review I Prof. Michel A. Kinsy Computing: The Art of Abstraction Application Algorithm Programming Language Operating System/Virtual Machine Instruction Set Architecture (ISA)
EC 413 Computer Organization Review I Prof. Michel A. Kinsy Computing: The Art of Abstraction Application Algorithm Programming Language Operating System/Virtual Machine Instruction Set Architecture (ISA)
Hardware Level Organization
 Hardware Level Organization Intro MIPS 1 Major components: - memory - central processing unit - registers - the fetch/execute cycle CPU PC IR Ex Unit MAR MBR I/O AR I/O BR System Bus Main Memory 0 (the
Hardware Level Organization Intro MIPS 1 Major components: - memory - central processing unit - registers - the fetch/execute cycle CPU PC IR Ex Unit MAR MBR I/O AR I/O BR System Bus Main Memory 0 (the
CITS5501 Software Testing and Quality Assurance Formal methods
 CITS5501 Software Testing and Quality Assurance Formal methods Unit coordinator: Arran Stewart May 1, 2018 1 / 49 Sources Pressman, R., Software Engineering: A Practitioner s Approach, McGraw-Hill, 2005
CITS5501 Software Testing and Quality Assurance Formal methods Unit coordinator: Arran Stewart May 1, 2018 1 / 49 Sources Pressman, R., Software Engineering: A Practitioner s Approach, McGraw-Hill, 2005
Configurable and Extensible Processors Change System Design. Ricardo E. Gonzalez Tensilica, Inc.
 Configurable and Extensible Processors Change System Design Ricardo E. Gonzalez Tensilica, Inc. Presentation Overview Yet Another Processor? No, a new way of building systems Puts system designers in the
Configurable and Extensible Processors Change System Design Ricardo E. Gonzalez Tensilica, Inc. Presentation Overview Yet Another Processor? No, a new way of building systems Puts system designers in the
Transforming Programs into Recursive Functions
 SBMF 2008 Transforming Programs into Recursive Functions Magnus O. Myreen, Michael J. C. Gordon 1 Computer Laboratory, University of Cambridge 15 JJ Thomson Avenue, Cambridge, UK Abstract This paper presents
SBMF 2008 Transforming Programs into Recursive Functions Magnus O. Myreen, Michael J. C. Gordon 1 Computer Laboratory, University of Cambridge 15 JJ Thomson Avenue, Cambridge, UK Abstract This paper presents
ECE 486/586. Computer Architecture. Lecture # 7
 ECE 486/586 Computer Architecture Lecture # 7 Spring 2015 Portland State University Lecture Topics Instruction Set Principles Instruction Encoding Role of Compilers The MIPS Architecture Reference: Appendix
ECE 486/586 Computer Architecture Lecture # 7 Spring 2015 Portland State University Lecture Topics Instruction Set Principles Instruction Encoding Role of Compilers The MIPS Architecture Reference: Appendix
INSTITUTO SUPERIOR TÉCNICO. Architectures for Embedded Computing
 UNIVERSIDADE TÉCNICA DE LISBOA INSTITUTO SUPERIOR TÉCNICO Departamento de Engenharia Informática for Embedded Computing MEIC-A, MEIC-T, MERC Lecture Slides Version 3.0 - English Lecture 03 Title: Processor
UNIVERSIDADE TÉCNICA DE LISBOA INSTITUTO SUPERIOR TÉCNICO Departamento de Engenharia Informática for Embedded Computing MEIC-A, MEIC-T, MERC Lecture Slides Version 3.0 - English Lecture 03 Title: Processor
PROBLEM SOLVING AND PYTHON PROGRAMMING
 ALGORITHM UNIT-1 It is defined as a sequence of instructions that describe a method for solving a problem. In other words it is a step by step procedure for solving a problem. Properties of Algorithms
ALGORITHM UNIT-1 It is defined as a sequence of instructions that describe a method for solving a problem. In other words it is a step by step procedure for solving a problem. Properties of Algorithms
RISC Principles. Introduction
 3 RISC Principles In the last chapter, we presented many details on the processor design space as well as the CISC and RISC architectures. It is time we consolidated our discussion to give details of RISC
3 RISC Principles In the last chapter, we presented many details on the processor design space as well as the CISC and RISC architectures. It is time we consolidated our discussion to give details of RISC
Chapter 1. Introduction
 1 Chapter 1 Introduction An exciting development of the 21st century is that the 20th-century vision of mechanized program verification is finally becoming practical, thanks to 30 years of advances in
1 Chapter 1 Introduction An exciting development of the 21st century is that the 20th-century vision of mechanized program verification is finally becoming practical, thanks to 30 years of advances in
Embedding Cryptol in Higher Order Logic
 Embedding Cryptol in Higher Order Logic Joe Hurd Computer Laboratory Cambridge University joe.hurd@cl.cam.ac.uk 10 March 2007 Abstract This report surveys existing approaches to embedding Cryptol programs
Embedding Cryptol in Higher Order Logic Joe Hurd Computer Laboratory Cambridge University joe.hurd@cl.cam.ac.uk 10 March 2007 Abstract This report surveys existing approaches to embedding Cryptol programs
Intel X86 Assembler Instruction Set Opcode Table
 Intel X86 Assembler Instruction Set Opcode Table x86 Instruction Set Reference. Derived from the September 2014 version of the Intel 64 and IA-32 LGDT, Load Global/Interrupt Descriptor Table Register.
Intel X86 Assembler Instruction Set Opcode Table x86 Instruction Set Reference. Derived from the September 2014 version of the Intel 64 and IA-32 LGDT, Load Global/Interrupt Descriptor Table Register.
CS4617 Computer Architecture
 1/27 CS4617 Computer Architecture Lecture 7: Instruction Set Architectures Dr J Vaughan October 1, 2014 2/27 ISA Classification Stack architecture: operands on top of stack Accumulator architecture: 1
1/27 CS4617 Computer Architecture Lecture 7: Instruction Set Architectures Dr J Vaughan October 1, 2014 2/27 ISA Classification Stack architecture: operands on top of stack Accumulator architecture: 1
Lecture 4: Instruction Set Design/Pipelining
 Lecture 4: Instruction Set Design/Pipelining Instruction set design (Sections 2.9-2.12) control instructions instruction encoding Basic pipelining implementation (Section A.1) 1 Control Transfer Instructions
Lecture 4: Instruction Set Design/Pipelining Instruction set design (Sections 2.9-2.12) control instructions instruction encoding Basic pipelining implementation (Section A.1) 1 Control Transfer Instructions
Packaging Theories of Higher Order Logic
 Packaging Theories of Higher Order Logic Joe Hurd Galois, Inc. joe@galois.com Theory Engineering Workshop Tuesday 9 February 2010 Joe Hurd Packaging Theories of Higher Order Logic 1 / 26 Talk Plan 1 Introduction
Packaging Theories of Higher Order Logic Joe Hurd Galois, Inc. joe@galois.com Theory Engineering Workshop Tuesday 9 February 2010 Joe Hurd Packaging Theories of Higher Order Logic 1 / 26 Talk Plan 1 Introduction
RISC, CISC, and ISA Variations
 RISC, CISC, and ISA Variations CS 3410 Computer System Organization & Programming These slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. iclicker
RISC, CISC, and ISA Variations CS 3410 Computer System Organization & Programming These slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. iclicker
Formal Systems and their Applications
 Formal Systems and their Applications Dave Clarke (Dave.Clarke@cs.kuleuven.be) Acknowledgment: these slides are based in part on slides from Benjamin Pierce and Frank Piessens 1 Course Overview Introduction
Formal Systems and their Applications Dave Clarke (Dave.Clarke@cs.kuleuven.be) Acknowledgment: these slides are based in part on slides from Benjamin Pierce and Frank Piessens 1 Course Overview Introduction
Rockwell Collins Evolving FM Methodology
 Rockwell Collins Evolving FM Methodology Konrad Slind Trusted Systems Group Rockwell Collins January 25, 2014 Collaborators Rockwell Collins: Andrew Gacek, David Hardin, Darren Cofer, John Backes, Luas
Rockwell Collins Evolving FM Methodology Konrad Slind Trusted Systems Group Rockwell Collins January 25, 2014 Collaborators Rockwell Collins: Andrew Gacek, David Hardin, Darren Cofer, John Backes, Luas
Verification of an ML compiler. Lecture 1: An introduction to compiler verification
 Verification of an ML compiler Lecture 1: An introduction to compiler verification Marktoberdorf Summer School MOD 2017 Magnus O. Myreen, Chalmers University of Technology Introduction Your program crashes.
Verification of an ML compiler Lecture 1: An introduction to compiler verification Marktoberdorf Summer School MOD 2017 Magnus O. Myreen, Chalmers University of Technology Introduction Your program crashes.
Verified Characteristic Formulae for CakeML. Armaël Guéneau, Magnus O. Myreen, Ramana Kumar, Michael Norrish April 27, 2017
 Verified Characteristic Formulae for CakeML Armaël Guéneau, Magnus O. Myreen, Ramana Kumar, Michael Norrish April 27, 2017 Goal: write programs in a high-level (ML-style) language, prove them correct interactively,
Verified Characteristic Formulae for CakeML Armaël Guéneau, Magnus O. Myreen, Ramana Kumar, Michael Norrish April 27, 2017 Goal: write programs in a high-level (ML-style) language, prove them correct interactively,
A verified runtime for a verified theorem prover
 A verified runtime for a verified theorem prover Magnus Myreen 1 and Jared Davis 2 1 University of Cambridge, UK 2 Centaur Technology, USA Two projects meet My theorem prover is written in Lisp. Can I
A verified runtime for a verified theorem prover Magnus Myreen 1 and Jared Davis 2 1 University of Cambridge, UK 2 Centaur Technology, USA Two projects meet My theorem prover is written in Lisp. Can I
Instruction Set Principles and Examples. Appendix B
 Instruction Set Principles and Examples Appendix B Outline What is Instruction Set Architecture? Classifying ISA Elements of ISA Programming Registers Type and Size of Operands Addressing Modes Types of
Instruction Set Principles and Examples Appendix B Outline What is Instruction Set Architecture? Classifying ISA Elements of ISA Programming Registers Type and Size of Operands Addressing Modes Types of
Instruction Set Architectures. Part 1
 Instruction Set Architectures Part 1 Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture Digital Design Circuit Design 1/9/02 Some ancient history Earliest (1940
Instruction Set Architectures Part 1 Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture Digital Design Circuit Design 1/9/02 Some ancient history Earliest (1940
The design of a programming language for provably correct programs: success and failure
 The design of a programming language for provably correct programs: success and failure Don Sannella Laboratory for Foundations of Computer Science School of Informatics, University of Edinburgh http://homepages.inf.ed.ac.uk/dts
The design of a programming language for provably correct programs: success and failure Don Sannella Laboratory for Foundations of Computer Science School of Informatics, University of Edinburgh http://homepages.inf.ed.ac.uk/dts
Practical Approaches to Formal Verification. Mike Bartley, TVS
 Practical Approaches to Formal Verification Mike Bartley, TVS 1 Acknowledgements This paper is based on work performed by TVS with ARM Specific thanks should go to Laurent Arditi Bryan Dickman Daryl Stuart
Practical Approaches to Formal Verification Mike Bartley, TVS 1 Acknowledgements This paper is based on work performed by TVS with ARM Specific thanks should go to Laurent Arditi Bryan Dickman Daryl Stuart
Hakim Weatherspoon CS 3410 Computer Science Cornell University
 Hakim Weatherspoon CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, McKee, and Sirer. Prelim today Starts
Hakim Weatherspoon CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, McKee, and Sirer. Prelim today Starts
Instruction Set Architecture. "Speaking with the computer"
 Instruction Set Architecture "Speaking with the computer" The Instruction Set Architecture Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture Digital Design
Instruction Set Architecture "Speaking with the computer" The Instruction Set Architecture Application Compiler Instr. Set Proc. Operating System I/O system Instruction Set Architecture Digital Design
Lecture 4: Instruction Set Architecture
 Lecture 4: Instruction Set Architecture ISA types, register usage, memory addressing, endian and alignment, quantitative evaluation Reading: Textbook (5 th edition) Appendix A Appendix B (4 th edition)
Lecture 4: Instruction Set Architecture ISA types, register usage, memory addressing, endian and alignment, quantitative evaluation Reading: Textbook (5 th edition) Appendix A Appendix B (4 th edition)
Cover Page. The handle holds various files of this Leiden University dissertation
 Cover Page The handle http://hdl.handle.net/1887/22891 holds various files of this Leiden University dissertation Author: Gouw, Stijn de Title: Combining monitoring with run-time assertion checking Issue
Cover Page The handle http://hdl.handle.net/1887/22891 holds various files of this Leiden University dissertation Author: Gouw, Stijn de Title: Combining monitoring with run-time assertion checking Issue
Provably Correct Software
 Provably Correct Software Max Schäfer Institute of Information Science/Academia Sinica September 17, 2007 1 / 48 The Need for Provably Correct Software BUT bugs are annoying, embarrassing, and cost gazillions
Provably Correct Software Max Schäfer Institute of Information Science/Academia Sinica September 17, 2007 1 / 48 The Need for Provably Correct Software BUT bugs are annoying, embarrassing, and cost gazillions
For our next chapter, we will discuss the emulation process which is an integral part of virtual machines.
 For our next chapter, we will discuss the emulation process which is an integral part of virtual machines. 1 2 For today s lecture, we ll start by defining what we mean by emulation. Specifically, in this
For our next chapter, we will discuss the emulation process which is an integral part of virtual machines. 1 2 For today s lecture, we ll start by defining what we mean by emulation. Specifically, in this
GNATprove a Spark2014 verifying compiler Florian Schanda, Altran UK
 1 GNATprove a Spark2014 verifying compiler Florian Schanda, Altran UK Tool architecture User view Source gnatprove Verdict 2 Tool architecture More detailed view... Source Encoding CVC4 gnat2why gnatwhy3
1 GNATprove a Spark2014 verifying compiler Florian Schanda, Altran UK Tool architecture User view Source gnatprove Verdict 2 Tool architecture More detailed view... Source Encoding CVC4 gnat2why gnatwhy3
Blockchains: new home for proven-correct software. Paris, Yoichi Hirai formal verification engineer, the Ethereum Foundation
 Blockchains: new home for proven-correct software Paris, 2017-2-17 Yoichi Hirai formal verification engineer, the Ethereum Foundation Lyon: 2014 January Have you heard of a web site where you can get Bitcoin
Blockchains: new home for proven-correct software Paris, 2017-2-17 Yoichi Hirai formal verification engineer, the Ethereum Foundation Lyon: 2014 January Have you heard of a web site where you can get Bitcoin
ECE232: Hardware Organization and Design
 ECE232: Hardware Organization and Design Lecture 2: Hardware/Software Interface Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Basic computer components How does a microprocessor
ECE232: Hardware Organization and Design Lecture 2: Hardware/Software Interface Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Basic computer components How does a microprocessor
Randomised testing of a HOL 4 microprocessor model
 Randomised testing of a HOL 4 microprocessor model Brian Campbell REMS project LFCS, University of Edinburgh 31st January 2014 1 / 41 Why are we testing a processor model? Want a good model for: Cost-lifting
Randomised testing of a HOL 4 microprocessor model Brian Campbell REMS project LFCS, University of Edinburgh 31st January 2014 1 / 41 Why are we testing a processor model? Want a good model for: Cost-lifting
Creating Formally Verified Components for Layered Assurance with an LLVM-to-ACL2 Translator
 Creating Formally Verified Components for Layered Assurance with an LLVM-to-ACL2 Translator Jennifer Davis, David Hardin, Jedidiah McClurg December 2013 Introduction Research objectives: Reduce need to
Creating Formally Verified Components for Layered Assurance with an LLVM-to-ACL2 Translator Jennifer Davis, David Hardin, Jedidiah McClurg December 2013 Introduction Research objectives: Reduce need to
Lecture 3: Recursion; Structural Induction
 15-150 Lecture 3: Recursion; Structural Induction Lecture by Dan Licata January 24, 2012 Today, we are going to talk about one of the most important ideas in functional programming, structural recursion
15-150 Lecture 3: Recursion; Structural Induction Lecture by Dan Licata January 24, 2012 Today, we are going to talk about one of the most important ideas in functional programming, structural recursion
COMP3221: Microprocessors and. and Embedded Systems. Instruction Set Architecture (ISA) What makes an ISA? #1: Memory Models. What makes an ISA?
 COMP3221: Microprocessors and Embedded Systems Lecture 2: Instruction Set Architecture (ISA) http://www.cse.unsw.edu.au/~cs3221 Lecturer: Hui Wu Session 2, 2005 Instruction Set Architecture (ISA) ISA is
COMP3221: Microprocessors and Embedded Systems Lecture 2: Instruction Set Architecture (ISA) http://www.cse.unsw.edu.au/~cs3221 Lecturer: Hui Wu Session 2, 2005 Instruction Set Architecture (ISA) ISA is
Introduction to OCaml
 Fall 2018 Introduction to OCaml Yu Zhang Course web site: http://staff.ustc.edu.cn/~yuzhang/tpl References Learn X in Y Minutes Ocaml Real World OCaml Cornell CS 3110 Spring 2018 Data Structures and Functional
Fall 2018 Introduction to OCaml Yu Zhang Course web site: http://staff.ustc.edu.cn/~yuzhang/tpl References Learn X in Y Minutes Ocaml Real World OCaml Cornell CS 3110 Spring 2018 Data Structures and Functional
Changing the way the world does software
 Changing the way the world does software Automated Certification from Soup to Nuts Nick Tudor njt@drisq.com Introducing D-RisQ D-RisQ is a SME based in Malvern, UK. All personnel have a background in mathematics,
Changing the way the world does software Automated Certification from Soup to Nuts Nick Tudor njt@drisq.com Introducing D-RisQ D-RisQ is a SME based in Malvern, UK. All personnel have a background in mathematics,
An OCaml-based automated theorem-proving textbook
 0 An OCaml-based automated theorem-proving textbook John Harrison, Intel Corporation Portland Functional Programming Study Group Mon 11th May 2009 (19:00) 1 Book plug Surveys many parts of automated reasoning,
0 An OCaml-based automated theorem-proving textbook John Harrison, Intel Corporation Portland Functional Programming Study Group Mon 11th May 2009 (19:00) 1 Book plug Surveys many parts of automated reasoning,
Computer Architectures
 Computer Architectures Instruction Set Architectures 2018. április 22. Budapest Gábor Horváth associate professor BUTE Dept. of Networked Systems and Services ghorvath@hit.bme.hu 2 Instruction set architectures
Computer Architectures Instruction Set Architectures 2018. április 22. Budapest Gábor Horváth associate professor BUTE Dept. of Networked Systems and Services ghorvath@hit.bme.hu 2 Instruction set architectures
Deductive Program Verification with Why3, Past and Future
 Deductive Program Verification with Why3, Past and Future Claude Marché ProofInUse Kick-Off Day February 2nd, 2015 A bit of history 1999: Jean-Christophe Filliâtre s PhD Thesis Proof of imperative programs,
Deductive Program Verification with Why3, Past and Future Claude Marché ProofInUse Kick-Off Day February 2nd, 2015 A bit of history 1999: Jean-Christophe Filliâtre s PhD Thesis Proof of imperative programs,
LIA. Large Installation Administration. Virtualization
 LIA Large Installation Administration Virtualization 2 Virtualization What is Virtualization "a technique for hiding the physical characteristics of computing resources from the way in which other systems,
LIA Large Installation Administration Virtualization 2 Virtualization What is Virtualization "a technique for hiding the physical characteristics of computing resources from the way in which other systems,
Runtime Checking for Program Verification Systems
 Runtime Checking for Program Verification Systems Karen Zee, Viktor Kuncak, and Martin Rinard MIT CSAIL Tuesday, March 13, 2007 Workshop on Runtime Verification 1 Background Jahob program verification
Runtime Checking for Program Verification Systems Karen Zee, Viktor Kuncak, and Martin Rinard MIT CSAIL Tuesday, March 13, 2007 Workshop on Runtime Verification 1 Background Jahob program verification
COMP2121: Microprocessors and Interfacing. Instruction Set Architecture (ISA)
 COMP2121: Microprocessors and Interfacing Instruction Set Architecture (ISA) http://www.cse.unsw.edu.au/~cs2121 Lecturer: Hui Wu Session 2, 2017 1 Contents Memory models Registers Data types Instructions
COMP2121: Microprocessors and Interfacing Instruction Set Architecture (ISA) http://www.cse.unsw.edu.au/~cs2121 Lecturer: Hui Wu Session 2, 2017 1 Contents Memory models Registers Data types Instructions
How much is a mechanized proof worth, certification-wise?
 How much is a mechanized proof worth, certification-wise? Xavier Leroy Inria Paris-Rocquencourt PiP 2014: Principles in Practice In this talk... Some feedback from the aircraft industry concerning the
How much is a mechanized proof worth, certification-wise? Xavier Leroy Inria Paris-Rocquencourt PiP 2014: Principles in Practice In this talk... Some feedback from the aircraft industry concerning the
Memory management units
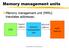 Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
Verifying Cache Coherence in ACL2. Ben Selfridge Oracle / UT Austin
 erifying Cache Coherence in ACL Ben Selfridge Oracle / UT Austin Goals of this talk Define cache coherence Present a cache coherence protocol designed Present an ACL proof that the protocol is safe (whatever
erifying Cache Coherence in ACL Ben Selfridge Oracle / UT Austin Goals of this talk Define cache coherence Present a cache coherence protocol designed Present an ACL proof that the protocol is safe (whatever
Distributed Systems 8. Remote Procedure Calls
 Distributed Systems 8. Remote Procedure Calls Paul Krzyzanowski pxk@cs.rutgers.edu 10/1/2012 1 Problems with the sockets API The sockets interface forces a read/write mechanism Programming is often easier
Distributed Systems 8. Remote Procedure Calls Paul Krzyzanowski pxk@cs.rutgers.edu 10/1/2012 1 Problems with the sockets API The sockets interface forces a read/write mechanism Programming is often easier
CIS24 Project #3. Student Name: Chun Chung Cheung Course Section: SA Date: 4/28/2003 Professor: Kopec. Subject: Functional Programming Language (ML)
 CIS24 Project #3 Student Name: Chun Chung Cheung Course Section: SA Date: 4/28/2003 Professor: Kopec Subject: Functional Programming Language (ML) 1 Introduction ML Programming Language Functional programming
CIS24 Project #3 Student Name: Chun Chung Cheung Course Section: SA Date: 4/28/2003 Professor: Kopec Subject: Functional Programming Language (ML) 1 Introduction ML Programming Language Functional programming
Isabelle/HOL:Selected Features and Recent Improvements
 /: Selected Features and Recent Improvements webertj@in.tum.de Security of Systems Group, Radboud University Nijmegen February 20, 2007 /:Selected Features and Recent Improvements 1 2 Logic User Interface
/: Selected Features and Recent Improvements webertj@in.tum.de Security of Systems Group, Radboud University Nijmegen February 20, 2007 /:Selected Features and Recent Improvements 1 2 Logic User Interface
Assuring Software Protection in Virtual Machines
 Assuring Software Protection in Virtual Machines Andrew W. Appel Princeton University 1 Software system built from components Less-trusted components More-trusted components (non-core functions) INTERFACE
Assuring Software Protection in Virtual Machines Andrew W. Appel Princeton University 1 Software system built from components Less-trusted components More-trusted components (non-core functions) INTERFACE
1. true / false By a compiler we mean a program that translates to code that will run natively on some machine.
 1. true / false By a compiler we mean a program that translates to code that will run natively on some machine. 2. true / false ML can be compiled. 3. true / false FORTRAN can reasonably be considered
1. true / false By a compiler we mean a program that translates to code that will run natively on some machine. 2. true / false ML can be compiled. 3. true / false FORTRAN can reasonably be considered
ISA and RISCV. CASS 2018 Lavanya Ramapantulu
 ISA and RISCV CASS 2018 Lavanya Ramapantulu Program Program =?? Algorithm + Data Structures Niklaus Wirth Program (Abstraction) of processor/hardware that executes 3-Jul-18 CASS18 - ISA and RISCV 2 Program
ISA and RISCV CASS 2018 Lavanya Ramapantulu Program Program =?? Algorithm + Data Structures Niklaus Wirth Program (Abstraction) of processor/hardware that executes 3-Jul-18 CASS18 - ISA and RISCV 2 Program
ECE902 Virtual Machine Final Project: MIPS to CRAY-2 Binary Translation
 ECE902 Virtual Machine Final Project: MIPS to CRAY-2 Binary Translation Weiping Liao, Saengrawee (Anne) Pratoomtong, and Chuan Zhang Abstract Binary translation is an important component for translating
ECE902 Virtual Machine Final Project: MIPS to CRAY-2 Binary Translation Weiping Liao, Saengrawee (Anne) Pratoomtong, and Chuan Zhang Abstract Binary translation is an important component for translating
An LCF-Style Interface between HOL and First-Order Logic Joe Hurd p.1/9
 An LCF-Style Interface between HOL and First-Order Logic Joe Hurd joe.hurd@cl.cam.ac.uk University of Cambridge An LCF-Style Interface between HOL and First-Order Logic Joe Hurd p.1/9 Introduction Many
An LCF-Style Interface between HOL and First-Order Logic Joe Hurd joe.hurd@cl.cam.ac.uk University of Cambridge An LCF-Style Interface between HOL and First-Order Logic Joe Hurd p.1/9 Introduction Many
CSE 141 Computer Architecture Spring Lecture 3 Instruction Set Architecute. Course Schedule. Announcements
 CSE141: Introduction to Computer Architecture CSE 141 Computer Architecture Spring 2005 Lecture 3 Instruction Set Architecute Pramod V. Argade April 4, 2005 Instructor: TAs: Pramod V. Argade (p2argade@cs.ucsd.edu)
CSE141: Introduction to Computer Architecture CSE 141 Computer Architecture Spring 2005 Lecture 3 Instruction Set Architecute Pramod V. Argade April 4, 2005 Instructor: TAs: Pramod V. Argade (p2argade@cs.ucsd.edu)
Reasoning About LLVM Code Using Codewalker
 Reasoning About LLVM Code Using Codewalker David Hardin Advanced Technology Center david.hardin@rockwellcollins.com Copyright 2015 Rockwell Collins. All rights reserved. Objectives Reason about machine
Reasoning About LLVM Code Using Codewalker David Hardin Advanced Technology Center david.hardin@rockwellcollins.com Copyright 2015 Rockwell Collins. All rights reserved. Objectives Reason about machine
Instructions: Language of the Computer
 CS359: Computer Architecture Instructions: Language of the Computer Yanyan Shen Department of Computer Science and Engineering 1 The Language a Computer Understands Word a computer understands: instruction
CS359: Computer Architecture Instructions: Language of the Computer Yanyan Shen Department of Computer Science and Engineering 1 The Language a Computer Understands Word a computer understands: instruction
Computer Model. What s in a computer? Processor Memory I/O devices (keyboard, mouse, LCD, video camera, speaker, disk, CD drive, )
 MIPS assembly Computer Model What s in a computer? Processor Memory I/O devices (keyboard, mouse, LCD, video camera, speaker, disk, CD drive, ) Computer Model register Processor ALU data 0011100..111 0011100..111
MIPS assembly Computer Model What s in a computer? Processor Memory I/O devices (keyboard, mouse, LCD, video camera, speaker, disk, CD drive, ) Computer Model register Processor ALU data 0011100..111 0011100..111
Virtual Machines and Dynamic Translation: Implementing ISAs in Software
 Virtual Machines and Dynamic Translation: Implementing ISAs in Software Krste Asanovic Laboratory for Computer Science Massachusetts Institute of Technology Software Applications How is a software application
Virtual Machines and Dynamic Translation: Implementing ISAs in Software Krste Asanovic Laboratory for Computer Science Massachusetts Institute of Technology Software Applications How is a software application
History overview Critical discussion What next (includes cool ideas from Matt)
 Linking ACL2 and HOL: past achievements and future prospects ABSTRACT. Over the years there have been several attempts to obtain the amazing automation and efficiency of ACL2 theorem proving within various
Linking ACL2 and HOL: past achievements and future prospects ABSTRACT. Over the years there have been several attempts to obtain the amazing automation and efficiency of ACL2 theorem proving within various
Undefined, Unspecified, Non-deterministic, and Implementation Defined Behavior in Verifiable Specs. Clifford Wolf Symbiotic EDA
 Undefined, Unspecified, Non-deterministic, and Implementation Defined Behavior in Verifiable Specs Clifford Wolf Symbiotic EDA 8 th RISC-V Workshop Barcelona 7-10 May, 2018 Why and how to not specify something?
Undefined, Unspecified, Non-deterministic, and Implementation Defined Behavior in Verifiable Specs Clifford Wolf Symbiotic EDA 8 th RISC-V Workshop Barcelona 7-10 May, 2018 Why and how to not specify something?
Typical Processor Execution Cycle
 Typical Processor Execution Cycle Instruction Fetch Obtain instruction from program storage Instruction Decode Determine required actions and instruction size Operand Fetch Locate and obtain operand data
Typical Processor Execution Cycle Instruction Fetch Obtain instruction from program storage Instruction Decode Determine required actions and instruction size Operand Fetch Locate and obtain operand data
Subtyping. Lecture 13 CS 565 3/27/06
 Subtyping Lecture 13 CS 565 3/27/06 Polymorphism Different varieties of polymorphism: Parametric (ML) type variables are abstract, and used to encode the fact that the same term can be used in many different
Subtyping Lecture 13 CS 565 3/27/06 Polymorphism Different varieties of polymorphism: Parametric (ML) type variables are abstract, and used to encode the fact that the same term can be used in many different
How Can You Trust Formally Verified Software?
 How Can You Trust Formally Verified Software? Alastair Reid Arm Research @alastair_d_reid https://www.theguardian.com/business/2015/may/01/us-aviation-authority-boeing-787-dreamliner-bug-could-cause-loss-of-control
How Can You Trust Formally Verified Software? Alastair Reid Arm Research @alastair_d_reid https://www.theguardian.com/business/2015/may/01/us-aviation-authority-boeing-787-dreamliner-bug-could-cause-loss-of-control
Unit 12: Memory Consistency Models. Includes slides originally developed by Prof. Amir Roth
 Unit 12: Memory Consistency Models Includes slides originally developed by Prof. Amir Roth 1 Example #1 int x = 0;! int y = 0;! thread 1 y = 1;! thread 2 int t1 = x;! x = 1;! int t2 = y;! print(t1,t2)!
Unit 12: Memory Consistency Models Includes slides originally developed by Prof. Amir Roth 1 Example #1 int x = 0;! int y = 0;! thread 1 y = 1;! thread 2 int t1 = x;! x = 1;! int t2 = y;! print(t1,t2)!
Lecture 3 Machine Language. Instructions: Instruction Execution cycle. Speaking computer before voice recognition interfaces
 Lecture 3 Machine Language Speaking computer before voice recognition interfaces 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very
Lecture 3 Machine Language Speaking computer before voice recognition interfaces 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very
Page 1. Structure of von Nuemann machine. Instruction Set - the type of Instructions
 Structure of von Nuemann machine Arithmetic and Logic Unit Input Output Equipment Main Memory Program Control Unit 1 1 Instruction Set - the type of Instructions Arithmetic + Logical (ADD, SUB, MULT, DIV,
Structure of von Nuemann machine Arithmetic and Logic Unit Input Output Equipment Main Memory Program Control Unit 1 1 Instruction Set - the type of Instructions Arithmetic + Logical (ADD, SUB, MULT, DIV,
RAISE in Perspective
 RAISE in Perspective Klaus Havelund NASA s Jet Propulsion Laboratory, Pasadena, USA Klaus.Havelund@jpl.nasa.gov 1 The Contribution of RAISE The RAISE [6] Specification Language, RSL, originated as a development
RAISE in Perspective Klaus Havelund NASA s Jet Propulsion Laboratory, Pasadena, USA Klaus.Havelund@jpl.nasa.gov 1 The Contribution of RAISE The RAISE [6] Specification Language, RSL, originated as a development
CMSC Computer Architecture Lecture 2: ISA. Prof. Yanjing Li Department of Computer Science University of Chicago
 CMSC 22200 Computer Architecture Lecture 2: ISA Prof. Yanjing Li Department of Computer Science University of Chicago Administrative Stuff! Lab1 is out! " Due next Thursday (10/6)! Lab2 " Out next Thursday
CMSC 22200 Computer Architecture Lecture 2: ISA Prof. Yanjing Li Department of Computer Science University of Chicago Administrative Stuff! Lab1 is out! " Due next Thursday (10/6)! Lab2 " Out next Thursday
CHAPTER 5 A Closer Look at Instruction Set Architectures
 CHAPTER 5 A Closer Look at Instruction Set Architectures 5.1 Introduction 293 5.2 Instruction Formats 293 5.2.1 Design Decisions for Instruction Sets 294 5.2.2 Little versus Big Endian 295 5.2.3 Internal
CHAPTER 5 A Closer Look at Instruction Set Architectures 5.1 Introduction 293 5.2 Instruction Formats 293 5.2.1 Design Decisions for Instruction Sets 294 5.2.2 Little versus Big Endian 295 5.2.3 Internal
Math 230 Assembly Programming (AKA Computer Organization) Spring MIPS Intro
 Math 230 Assembly Programming (AKA Computer Organization) Spring 2008 MIPS Intro Adapted from slides developed for: Mary J. Irwin PSU CSE331 Dave Patterson s UCB CS152 M230 L09.1 Smith Spring 2008 MIPS
Math 230 Assembly Programming (AKA Computer Organization) Spring 2008 MIPS Intro Adapted from slides developed for: Mary J. Irwin PSU CSE331 Dave Patterson s UCB CS152 M230 L09.1 Smith Spring 2008 MIPS
Industrial Hardware and Software Verification with ACL2
 Industrial Hardware and Software Verification with ACL2 Warren A. Hunt, Jr. 1, Matt Kaufmann 1, J Strother Moore 1, and Anna Slobodova 2 1 Department of Computer Science University of Texas at Austin and
Industrial Hardware and Software Verification with ACL2 Warren A. Hunt, Jr. 1, Matt Kaufmann 1, J Strother Moore 1, and Anna Slobodova 2 1 Department of Computer Science University of Texas at Austin and
Virtual Memory: From Address Translation to Demand Paging
 Constructive Computer Architecture Virtual Memory: From Address Translation to Demand Paging Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 12, 2014
Constructive Computer Architecture Virtual Memory: From Address Translation to Demand Paging Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 12, 2014
Introduction to RISC-V
 Introduction to RISC-V Jielun Tan, James Connolly February, 2019 Overview What is RISC-V Why RISC-V ISA overview Software environment Beta testing What is RISC-V RISC-V (pronounced risk-five ) is an open,
Introduction to RISC-V Jielun Tan, James Connolly February, 2019 Overview What is RISC-V Why RISC-V ISA overview Software environment Beta testing What is RISC-V RISC-V (pronounced risk-five ) is an open,
Microprocessor Architecture Dr. Charles Kim Howard University
 EECE416 Microcomputer Fundamentals Microprocessor Architecture Dr. Charles Kim Howard University 1 Computer Architecture Computer System CPU (with PC, Register, SR) + Memory 2 Computer Architecture ALU
EECE416 Microcomputer Fundamentals Microprocessor Architecture Dr. Charles Kim Howard University 1 Computer Architecture Computer System CPU (with PC, Register, SR) + Memory 2 Computer Architecture ALU
Proof Carrying Code(PCC)
 Discussion p./6 Proof Carrying Code(PCC Languaged based security policy instead of OS-based A mechanism to determine with certainity that it is safe execute a program or not Generic architecture for providing
Discussion p./6 Proof Carrying Code(PCC Languaged based security policy instead of OS-based A mechanism to determine with certainity that it is safe execute a program or not Generic architecture for providing
EEM870 Embedded System and Experiment Lecture 3: ARM Processor Architecture
 EEM870 Embedded System and Experiment Lecture 3: ARM Processor Architecture Wen-Yen Lin, Ph.D. Department of Electrical Engineering Chang Gung University Email: wylin@mail.cgu.edu.tw March 2014 Agenda
EEM870 Embedded System and Experiment Lecture 3: ARM Processor Architecture Wen-Yen Lin, Ph.D. Department of Electrical Engineering Chang Gung University Email: wylin@mail.cgu.edu.tw March 2014 Agenda
Instructions: MIPS arithmetic. MIPS arithmetic. Chapter 3 : MIPS Downloaded from:
 Instructions: Chapter 3 : MIPS Downloaded from: http://www.cs.umr.edu/~bsiever/cs234/ Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive
Instructions: Chapter 3 : MIPS Downloaded from: http://www.cs.umr.edu/~bsiever/cs234/ Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive
Robbing the Bank with a Theorem Prover
 Robbing the Bank with a Theorem Prover (Transcript of Discussion) Jolyon Clulow Cambridge University So it s a fairly provocative title, how did we get to that? Well automated tools have been successfully
Robbing the Bank with a Theorem Prover (Transcript of Discussion) Jolyon Clulow Cambridge University So it s a fairly provocative title, how did we get to that? Well automated tools have been successfully
EITF20: Computer Architecture Part2.1.1: Instruction Set Architecture
 EITF20: Computer Architecture Part2.1.1: Instruction Set Architecture Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Instruction Set Principles The Role of Compilers MIPS 2 Main Content Computer
EITF20: Computer Architecture Part2.1.1: Instruction Set Architecture Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Instruction Set Principles The Role of Compilers MIPS 2 Main Content Computer
Chapter 5 B. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 B Large and Fast: Exploiting Memory Hierarchy Dependability 5.5 Dependable Memory Hierarchy Chapter 6 Storage and Other I/O Topics 2 Dependability Service accomplishment Service delivered as
Chapter 5 B Large and Fast: Exploiting Memory Hierarchy Dependability 5.5 Dependable Memory Hierarchy Chapter 6 Storage and Other I/O Topics 2 Dependability Service accomplishment Service delivered as
CAKEML. A Verified Implementation of ML. S-REPLS 6 UCL 25 May, Ramana Kumar. Magnus Myreen. Yong Kiam Tan
 CAKEML A Verified Implementation of ML Anthony Fox Hugo Férée Armaël Guéneau Ramana Kumar Magnus Myreen Michael Norrish Scott Owens Yong Kiam Tan S-REPLS 6 UCL 25 May, 2017 The CakeML Project A functional
CAKEML A Verified Implementation of ML Anthony Fox Hugo Férée Armaël Guéneau Ramana Kumar Magnus Myreen Michael Norrish Scott Owens Yong Kiam Tan S-REPLS 6 UCL 25 May, 2017 The CakeML Project A functional
