SEQ without stages. valc register file ALU. Stat ZF/SF. instr. length PC+9. R[srcA] R[srcB] srca srcb dstm dste. Data in Data out. Instr. Mem.
|
|
|
- Lawrence Sharp
- 5 years ago
- Views:
Transcription
1 Exam Review 1
2 SEQ without stages 2 0xF 0xF %rsp valc register file PC+9 PC + Instr. Mem. instr. length ra rb %rsp 0xF 0xF %rsp srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 8 ALU alua vale alub add/sub xor/and (function of instr.) Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF
3 SEQ with stages fetch decode 0xF 0xF %rsp valc register file execute PC+9 memory PC + Instr. Mem. instr. length ra rb %rsp 0xF 0xF %rsp srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 8 ALU alua vale alub add/sub xor/and (function of instr.) Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF writeback 3
4 SEQ with stages fetch decode 0xF 0xF %rsp valc register file execute PC+9 memory PC + Instr. Mem. instr. length ra rb %rsp 0xF 0xF %rsp srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 8 ALU alua vale alub add/sub xor/and (function of instr.) Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF writeback 3
5 SEQ with stages %rsp 0xF rule: signal to next stage (except flow control) fetch decode 0xF valc register file execute PC+9 memory PC + Instr. Mem. instr. length ra rb %rsp 0xF 0xF %rsp srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 8 ALU alua vale alub add/sub xor/and (function of instr.) Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF writeback 3
6 SEQ with stages (actually sequential) fetch PC + Instr. Mem. instr. length decode ra rb %rsp 0xF 0xF %rsp 0xF 0xF %rsp valc register file srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 writeback execute 8 ALU alua vale alub add/sub xor/and (function of instr.) PC+9 memory Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF 4
7 adding pipeline registers fetch decode 0xF 0xF %rsp valc register file execute PC+9 memory PC + Instr. Mem. instr. length ra rb %rsp 0xF 0xF %rsp srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 8 ALU alua vale alub add/sub xor/and (function of instr.) Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF writeback 5
8 adding pipeline registers decode not shown control logic fetch 0xF 0xF %rsp valc register file execute PC+9 memory PC + Instr. Mem. instr. length ra rb %rsp 0xF 0xF %rsp srca srcb dstm dste R[srcA] R[srcB] next R[dstM] next R[dstE] 0 8 ALU alua vale alub add/sub xor/and (function of instr.) Data in Data out Addr Mem. in write? function of opcode Stat ZF/SF writeback 5
9 pipeline with different hazards 6 example: 4-stage pipeline: fetch/decode/execute+memory/writeback // 4 stage // 5 stage addq %rax, %r8 // // W subq %rax, %r9 // W // M xorq %rax, %r10 // EM // E andq %r8, %r11 // D // D
10 pipeline with different hazards 6 example: 4-stage pipeline: fetch/decode/execute+memory/writeback // 4 stage // 5 stage addq %rax, %r8 // // W subq %rax, %r9 // W // M xorq %rax, %r10 // EM // E andq %r8, %r11 // D // D addq/andq is hazard with 5-stage pipeline addq/andq is not a hazard with 4-stage pipeline
11 exercise: different pipeline 7 split execute into two stages: F/D/E1/E2/M/W result only available after second execute stage where does forwarding, stalls occur? cycle # addq %rcx, %r9 F D E1 E2 M W addq %r9, %rbx F D D E1 E2 M W addq %rax, %r9 F F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W
12 exercise: different pipeline 8 split execute into two stages: F/D/E1/E2/M/W cycle # addq %rcx, %r9 F D E1 E2 M W addq %r9, %rbx F D E1 E2 M W addq %r9, %rbx F D D E1 E2 M W addq %rax, %r9 F D E1 E2 M W addq %rax, %r9 F F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W
13 exercise: different pipeline 8 split execute into two stages: F/D/E1/E2/M/W cycle # addq %rcx, %r9 F D E1 E2 M W addq %r9, %rbx F D E1 E2 M W addq %r9, %rbx F D D E1 E2 M W addq %rax, %r9 F D E1 E2 M W addq %rax, %r9 F F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W
14 exercise: different pipeline 8 split execute into two stages: F/D/E1/E2/M/W cycle # addq %rcx, %r9 F D E1 E2 M W addq %r9, %rbx F D E1 E2 M W addq %r9, %rbx F D D E1 E2 M W addq %rax, %r9 F D E1 E2 M W addq %rax, %r9 F F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W
15 exercise: different pipeline 8 split execute into two stages: F/D/E1/E2/M/W cycle # addq %rcx, %r9 F D E1 E2 M W addq %r9, %rbx F D E1 E2 M W addq %r9, %rbx F D D E1 E2 M W addq %rax, %r9 F D E1 E2 M W addq %rax, %r9 F F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W
16 exercise: different pipeline 8 split execute into two stages: F/D/E1/E2/M/W cycle # addq %rcx, %r9 F D E1 E2 M W addq %r9, %rbx F D E1 E2 M W addq %r9, %rbx F D D E1 E2 M W addq %rax, %r9 F D E1 E2 M W addq %rax, %r9 F F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W rmmovq %r9, (%rbx) F D E1 E2 M W
17 ex.: dependencies and hazards (1) 9 addq %rax, %rbx subq %rax, %rcx irmovq $100, %rcx addq %rcx, %r10 addq %rbx, %r10 where are dependencies? which are hazards in our pipeline? which are resolved with forwarding?
18 ex.: dependencies and hazards (1) 9 addq %rax, %rbx subq %rax, %rcx irmovq $100, %rcx addq %rcx, %r10 addq %rbx, %r10 where are dependencies? which are hazards in our pipeline? which are resolved with forwarding?
19 ex.: dependencies and hazards (1) 9 addq %rax, %rbx subq %rax, %rcx irmovq $100, %rcx addq %rcx, %r10 addq %rbx, %r10 where are dependencies? which are hazards in our pipeline? which are resolved with forwarding?
20 ex.: dependencies and hazards (1) 9 addq %rax, %rbx subq %rax, %rcx irmovq $100, %rcx addq %rcx, %r10 addq %rbx, %r10 where are dependencies? which are hazards in our pipeline? which are resolved with forwarding?
21 ex.: dependencies and hazards (2) 10 mrmovq 0(%rax) %rbx addq %rbx %rcx foo: jne foo addq %rcx %rdx mrmovq (%rdx) %rcx where are dependencies? which are hazards in our pipeline? which are resolved with forwarding?
22 11 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value multiple places to put values with same index avoid conflict misses
23 11 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value set set
24 adding associativity 11 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value way 0 way
25 11 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value m = 8 bit addresses S = 2 = 2 s sets s = 1 (set) index bits B = 2 = 2 b byte block size b = 1 (block) offset bits t = m (s + b) = 6 tag bits
26 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value mem[0x00] 0 mem[0x01] address (hex) result (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
27 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value mem[0x00] 0 mem[0x01] address (hex) result (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
28 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value mem[0x00] mem[0x01] mem[0x62] mem[0x63] 0 address (hex) result (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
29 adding associativity index valid tag value valid tag value mem[0x00] mem[0x01] mem[0x62] mem[0x63] address (hex) 2-way set associative, 2 byte blocks, 2 sets result mem[0x60] mem[0x61] (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
30 adding associativity index valid tag value valid tag value mem[0x00] mem[0x01] mem[0x62] mem[0x63] address (hex) 2-way set associative, 2 byte blocks, 2 sets result mem[0x60] mem[0x61] (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
31 adding associativity index valid tag value valid tag value mem[0x00] mem[0x01] mem[0x62] mem[0x63] address (hex) 2-way set associative, 2 byte blocks, 2 sets result mem[0x60] mem[0x61] (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
32 adding associativity 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value mem[0x00] mem[0x01] mem[0x62] mem[0x63] mem[0x60] mem[0x61] 0 address (hex) result (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset needs to replace block in set 0! 11
33 adding associativity index valid tag value valid tag value mem[0x00] mem[0x01] mem[0x62] mem[0x63] address (hex) 2-way set associative, 2 byte blocks, 2 sets result mem[0x60] mem[0x61] (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss tag indexoffset 11
34 cache operation (associative) index offset valid tag data valid tag data AA BB tag 1 11 B4 B = data (B5) AND = AND OR is hit? (1)
35 cache operation (associative) index offset valid tag data valid tag data AA BB tag 1 11 B4 B = data (B5) AND = AND OR is hit? (1)
36 cache operation (associative) index offset valid tag data valid tag data AA BB tag 1 11 B4 B = data (B5) AND = AND OR is hit? (1)
37 associative lookup possibilities 13 none of the blocks for the index are valid none of the valid blocks for the index match the tag something else is stored there one of the blocks for the index is valid and matches the tag
38 Tag-Index-Offset formulas (complete) 14 m memory addreses bits (Y86-64: 64) E number of blocks per set ( ways ) S = 2 s number of sets s (set) index bits B = 2 b block size b (block) offset bits t = m (s + b) tag bits C = B S E cache size (excluding metadata)
39 replacement policies 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value LRU mem[0x00] mem[0x01] mem[0x60] mem[0x61] mem[0x62] mem[0x63] 0 1 address (hex) result (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss how to decide where to insert 0x64? 15
40 replacement policies 2-way set associative, 2 byte blocks, 2 sets index valid tag value valid tag value LRU mem[0x00] mem[0x01] mem[0x60] mem[0x61] mem[0x62] mem[0x63] 0 1 address (hex) result (00) miss (01) hit (63) miss (61) miss (62) hit (00) hit (64) miss track which block was read least recently updated on every access 15
41 example replacement policies 16 least recently used and approximations take advantage of temporal locality exact: log 2 (E!) bits per set for E-way cache good approximations: E to 2E bits first-in, first-out counter per set where to replace next (pseudo-)random no extra information!
42 write-through v. write-back 17 option 1: write-through 1 write 10 to 0xABCD CPU Cache ABCD: FF RAM 11CD: 42 ABCD: FF
43 write-through v. write-back 17 option 1: write-through 1 write 10 to 0xABCD 2 write 10 to 0xABCD CPU Cache ABCD: 10 RAM 11CD: 42 ABCD: 10
44 write-through v. write-back 17 option 2: write-back 1 write 10 to 0xABCD CPU Cache ABCD: 10 (dirty) RAM 11CD: 42 ABCD: FF
45 write-through v. write-back option 2: write-back 1 write 10 to 0xABCD 3 write 10 to ABCD CPU 2 read Cache from ABCD: 10 0x11CD (dirty) (conflicts) when replaced send value to memory RAM 11CD: 42 ABCD: 10 17
46 write-through v. write-back 17 1 write 10 to 0xABCD 3 write 10 to ABCD CPU 2 Cache 4 read read RAM ABCD: 10 from from (dirty) 11CD: 42 0x11CD 0x11CD ABCD: 10 (conflicts) read new value to store in cache
47 18 writeback policy changed value! 2-way set associative, 4 byte blocks, 2 sets index valid tag value dirty valid tag value dirty LRU mem[0x00] mem[0x01] mem[0x60]* mem[0x61]* mem[0x62] mem[0x63] = dirty (different than memory) needs to be written if evicted
48 allocate on write? 19 processor writes less than whole cache block block not yet in cache two options: write-allocate fetch rest of cache block, replace written part write-no-allocate send write through to memory guess: not read soon?
49 20 write-allocate 2-way set associative, LRU, writeback index valid tag value dirty valid tag value dirty LRU mem[0x00] mem[0x01] mem[0x60]* mem[0x61]* mem[0x62] mem[0x63] writing 0xFF into address 0x04? index 0, tag
50 20 write-allocate 2-way set associative, LRU, writeback index valid tag value dirty valid tag value dirty LRU mem[0x00] mem[0x01] mem[0x60]* mem[0x61]* mem[0x62] mem[0x63] writing 0xFF into address 0x04? index 0, tag step 1: find least recently used block
51 20 write-allocate 2-way set associative, LRU, writeback index valid tag value dirty valid tag value dirty LRU mem[0x00] mem[0x01] mem[0x60]* mem[0x61]* mem[0x62] mem[0x63] writing 0xFF into address 0x04? index 0, tag step 1: find least recently used block step 2: possibly writeback old block
52 20 write-allocate 2-way set associative, LRU, writeback index valid tag value dirty valid tag value dirty LRU mem[0x00] mem[0x01] xFF mem[0x05] mem[0x62] mem[0x63] writing 0xFF into address 0x04? index 0, tag step 1: find least recently used block step 2: possibly writeback old block step 3a: read in new block to get mem[0x05] step 3b: update LRU information
53 21 write-no-allocate 2-way set associative, LRU, writeback index valid tag value dirty valid tag value dirty LRU mem[0x00] mem[0x01] mem[0x60]* mem[0x61]* mem[0x62] mem[0x63] writing 0xFF into address 0x04? step 1: is it in cache yet? step 2: no, just send it to memory
54 fast writes 22 write 10 to 0xABCD write buffer 0xABCD: 10 0x1234: 20 CPU write 20 to 0x1234 Cache RAM write appears to complete immediately when placed in buffer memory can be much slower
55 exercise (1) 23 initial cache: 64-byte blocks, 64 sets, 8 ways/set If we leave the other parameters listed above unchanged, which will probably reduce the number of capacity misses in a typical program? (Multiple may be correct.) A. quadrupling the block size (256-byte blocks, 64 sets, 8 ways/set) B. quadrupling the number of sets C. quadrupling the number of ways/set
56 exercise (2) 24 initial cache: 64-byte blocks, 8 ways/set, 64KB cache If we leave the other parameters listed above unchanged, which will probably reduce the number of capacity misses in a typical program? (Multiple may be correct.) A. quadrupling the block size (256-byte block, 8 ways/set, 64KB cache B. quadrupling the number of ways/set C. quadrupling the cache size
57 exercise (3) 25 initial cache: 64-byte blocks, 8 ways/set, 64KB cache If we leave the other parameters listed above unchanged, which will probably reduce the number of conflict misses in a typical program? (Multiple may be correct.) A. quadrupling the block size (256-byte block, 8 ways/set, 64KB cache B. quadrupling the number of ways/set C. quadrupling the cache size
58 C and cache misses (1) 26 int array[1024]; // 4KB array int even_sum = 0, odd_sum = 0; for (int i = 0; i < 1024; i += 2) { even_sum += array[i + 0]; odd_sum += array[i + 1]; } Assume everything but array is kept in registers (and the compiler does not do anything funny). How many data cache misses on a 2KB direct-mapped cache with 16B cache blocks?
59 C and cache misses (2) 27 int array[1024]; // 4KB array int even_sum = 0, odd_sum = 0; for (int i = 0; i < 1024; i += 2) even_sum += array[i + 0]; for (int i = 1; i < 1024; i += 2) odd_sum += array[i + 1]; Assume everything but array is kept in registers (and the compiler does not do anything funny). How many data cache misses on a 2KB direct-mapped cache with 16B cache blocks? Would a set-associtiave cache be better?
60 thinking about cache storage (1) 28 2KB direct-mapped cache with 16B blocks set 0: address 0 to 15, (0 to 15) + 2KB, (0 to 15) + 4KB, set 1: address 16 to 31, (16 to 31) + 2KB, (16 to 31) + 4KB, set 127: address 2032 to 2047, (2032 to 2047) + 2KB,
61 thinking about cache storage (1) 28 2KB direct-mapped cache with 16B blocks set 0: address 0 to 15, (0 to 15) + 2KB, (0 to 15) + 4KB, set 1: address 16 to 31, (16 to 31) + 2KB, (16 to 31) + 4KB, set 127: address 2032 to 2047, (2032 to 2047) + 2KB,
62 thinking about cache storage (1) 28 2KB direct-mapped cache with 16B blocks set 0: address 0 to 15, (0 to 15) + 2KB, (0 to 15) + 4KB, block at 0: array[0] through array[3] set 1: address 16 to 31, (16 to 31) + 2KB, (16 to 31) + 4KB, block at 16: array[4] through array[7] set 127: address 2032 to 2047, (2032 to 2047) + 2KB, block at 2032: array[508] through array[511]
63 thinking about cache storage (1) 2KB direct-mapped cache with 16B blocks set 0: address 0 to 15, (0 to 15) + 2KB, (0 to 15) + 4KB, block at 0: array[0] through array[3] block at 0+2KB: array[512] through array[515] set 1: address 16 to 31, (16 to 31) + 2KB, (16 to 31) + 4KB, block at 16: array[4] through array[7] block at 16+2KB: array[516] through array[519] set 127: address 2032 to 2047, (2032 to 2047) + 2KB, block at 2032: array[508] through array[511] block at KB: array[1020] through array[1023] 28
64 thinking about cache storage (2) 29 2KB 2-way set associative cache with 16B blocks: block addresses set 0: address 0, 0 + 2KB, 0 + 4KB, set 1: address 16, KB, KB, set 63: address 1008, KB, KB
65 thinking about cache storage (2) 2KB 2-way set associative cache with 16B blocks: block addresses set 0: address 0, 0 + 2KB, 0 + 4KB, block at 0: array[0] through array[3] set 1: address 16, KB, KB, address 16: array[4] through array[7] set 63: address 1008, KB, KB address 1008: array[252] through array[255] 29
66 thinking about cache storage (2) 2KB 2-way set associative cache with 16B blocks: block addresses set 0: address 0, 0 + 2KB, 0 + 4KB, block at 0: array[0] through array[3] block at 0+1KB: array[256] through array[259] block at 0+2KB: array[512] through array[515] set 1: address 16, KB, KB, address 16: array[4] through array[7] set 63: address 1008, KB, KB address 1008: array[252] through array[255] 29
67 thinking about cache storage (2) 2KB 2-way set associative cache with 16B blocks: block addresses set 0: address 0, 0 + 2KB, 0 + 4KB, block at 0: array[0] through array[3] block at 0+1KB: array[256] through array[259] block at 0+2KB: array[512] through array[515] set 1: address 16, KB, KB, address 16: array[4] through array[7] set 63: address 1008, KB, KB address 1008: array[252] through array[255] 29
68 C and cache misses (3) typedef struct { int a_value, b_value; int boring_values[126]; } item; item items[8]; // 4 KB array int a_sum = 0, b_sum = 0; for (int i = 0; i < 8; ++i) a_sum += items[i].a_value; for (int i = 0; i < 8; ++i) b_sum += items[i].b_value; Assume everything but items is kept in registers (and the compiler does not do anything funny). How many data cache misses on a 2KB direct-mapped cache with 16B cache blocks? 30
69 C and cache misses (3, rewritten?) 31 item array[1024]; // 4 KB array int a_sum = 0, b_sum = 0; for (int i = 0; i < 1024; i += 128) a_sum += array[i]; for (int i = 1; i < 1024; i += 128) b_sum += array[i];
70 C and cache misses (4) typedef struct { int a_value, b_value; int boring_values[126]; } item; item items[8]; // 4 KB array int a_sum = 0, b_sum = 0; for (int i = 0; i < 8; ++i) a_sum += items[i].a_value; for (int i = 0; i < 8; ++i) b_sum += items[i].b_value; Assume everything but items is kept in registers (and the compiler does not do anything funny). How many data cache misses on a 4-way set associative 2KB direct-mapped cache with 16B cache blocks? 32
71 a note on matrix storage 33 A N N matrix represent as array makes dynamic sizes easier: float A_2d_array[N][N]; float * A_flat = malloc(n * N); A_flat[i * N + j] === A_2d_array[i][j]
72 locality exercise (1) 34 /* version 1 */ for (int i = 0; i < N; ++i) for (int j = 0; j < N; ++j) A[i] += B[j] * C[i * N + j] /* version 2 */ for (int j = 0; j < N; ++j) for (int i = 0; i < N; ++i) A[i] += B[j] * C[i * N + j]; exercise: which has better temporal locality in A? in B? in C? how about spatial locality?
73 array usage: block 35 A ik block (I K) A kj block (K J) B ij block (I J) inner loop keeps blocks from A, B in cache
74 array usage: block 35 A ik block (I K) A kj block (K J) B ij block (I J) B ij calculation uses strips from A K calculations for one load (cache miss)
75 array usage: block 35 A ik block (I K) A kj block (K J) B ij block (I J) A ik calculation uses strips from A, B J calculations for one load (cache miss)
76 array usage: block 35 A ik block (I K) A kj block (K J) B ij block (I J) (approx.) KIJ fully cached calculations for KI + IJ + KJ loads (assuming everything stays in cache)
77 cache blocking efficiency 36 load I K elements of A ik : do > J multiplies with each load K J elements of A kj : do I multiplies with each load I J elements of B ij : do K adds with each bigger blocks more work per load! catch: IK + KJ + IJ elements must fit in cache
78 cache blocking rule of thumb 37 fill the most of the cache with useful data and do as much work as possible from that example: my desktop 32KB L1 cache I = J = K = 48 uses elements, or 27KB. assumption: conflict misses aren t important
79 flat 2D arrays and cache blocks 38 A[0] A[N] A x0 A xn
associativity terminology
 Caching 1 2 associativity terminology direct-mapped one block per set E-way set associative E blocks per set E ways in the cache fully associative one set total (everything in one set) 3 Tag-Index-Offset
Caching 1 2 associativity terminology direct-mapped one block per set E-way set associative E blocks per set E ways in the cache fully associative one set total (everything in one set) 3 Tag-Index-Offset
Pipelining 3: Hazards/Forwarding/Prediction
 Pipelining 3: Hazards/Forwarding/Prediction 1 pipeline stages 2 fetch instruction memory, most PC computation decode reading register file execute computation, condition code read/write memory memory read/write
Pipelining 3: Hazards/Forwarding/Prediction 1 pipeline stages 2 fetch instruction memory, most PC computation decode reading register file execute computation, condition code read/write memory memory read/write
Pipelining 4 / Caches 1
 Pipelining 4 / Caches 1 1 2 after forwarding/prediction where do we still need to stall? memory output needed in fetch ret followed by anything memory output needed in exceute mrmovq or popq + use (in
Pipelining 4 / Caches 1 1 2 after forwarding/prediction where do we still need to stall? memory output needed in fetch ret followed by anything memory output needed in exceute mrmovq or popq + use (in
exercise 4 byte blocks, 4 sets index valid tag value 00
 Caching (part 2) 1 exercise 3 address (hex) result 00000000 (00) 00000001 (01) 01100011 (63) 01100001 (61) 01100010 (62) 00000000 (00) 01100100 (64) 4 byte blocks, 4 sets index valid tag value 00 01 10
Caching (part 2) 1 exercise 3 address (hex) result 00000000 (00) 00000001 (01) 01100011 (63) 01100001 (61) 01100010 (62) 00000000 (00) 01100100 (64) 4 byte blocks, 4 sets index valid tag value 00 01 10
write-through v. write-back write-through v. write-back write-through v. write-back option 1: write-through write 10 to 0xABCD CPU RAM Cache ABCD: FF
 write-through v. write-back option 1: write-through 1 write 10 to 0xABCD CPU Cache ABCD: FF RAM 11CD: 42 ABCD: FF 1 2 write-through v. write-back option 1: write-through write-through v. write-back option
write-through v. write-back option 1: write-through 1 write 10 to 0xABCD CPU Cache ABCD: FF RAM 11CD: 42 ABCD: FF 1 2 write-through v. write-back option 1: write-through write-through v. write-back option
minor HCL update Pipe Hazards (finish) / Caching post-quiz Q1 B post-quiz Q1 D new version of hclrs.tar:
 minor HCL update Pipe Hazards (finish) / Caching new version of hclrs.tar: removes poptest.yo from list of tests for seqhw, pipehw2 gives error if you try to assign to register output: register xy { foo
minor HCL update Pipe Hazards (finish) / Caching new version of hclrs.tar: removes poptest.yo from list of tests for seqhw, pipehw2 gives error if you try to assign to register output: register xy { foo
SEQ part 3 / HCLRS 1
 SEQ part 3 / HCLRS 1 Changelog 1 Changes made in this version not seen in first lecture: 21 September 2017: data memory value MUX input for call is PC + 10, not PC 21 September 2017: slide 23: add input
SEQ part 3 / HCLRS 1 Changelog 1 Changes made in this version not seen in first lecture: 21 September 2017: data memory value MUX input for call is PC + 10, not PC 21 September 2017: slide 23: add input
bitwise (finish) / SEQ part 1
 bitwise (finish) / SEQ part 1 1 Changelog 1 Changes made in this version not seen in first lecture: 14 September 2017: slide 16-17: the x86 arithmetic shift instruction is sar, not sra last time 2 bitwise
bitwise (finish) / SEQ part 1 1 Changelog 1 Changes made in this version not seen in first lecture: 14 September 2017: slide 16-17: the x86 arithmetic shift instruction is sar, not sra last time 2 bitwise
selected anonymous feedback: VM Exam Review final format/content logistics
 selected anonymous feedback: VM Exam Review too few concrete examples of translation in lecture students were poorly prepared for memory HW holy hell, dont be giving us this memory hw and not give us the
selected anonymous feedback: VM Exam Review too few concrete examples of translation in lecture students were poorly prepared for memory HW holy hell, dont be giving us this memory hw and not give us the
selected anonymous feedback: VM
 Exam Review 1 selected anonymous feedback: VM 2 too few concrete examples of translation in lecture students were poorly prepared for memory HW holy hell, dont be giving us this memory hw and not give
Exam Review 1 selected anonymous feedback: VM 2 too few concrete examples of translation in lecture students were poorly prepared for memory HW holy hell, dont be giving us this memory hw and not give
Cache Performance II 1
 Cache Performance II 1 cache operation (associative) 111001 index offset valid tag valid tag data data 1 10 1 00 00 11 AA BB tag 1 11 1 01 B4 B5 33 44 = data (B5) AND = AND OR is hit? (1) 2 cache operation
Cache Performance II 1 cache operation (associative) 111001 index offset valid tag valid tag data data 1 10 1 00 00 11 AA BB tag 1 11 1 01 B4 B5 33 44 = data (B5) AND = AND OR is hit? (1) 2 cache operation
Changelog. Changes made in this version not seen in first lecture: 13 Feb 2018: add slide on constants and width
 HCL 1 Changelog 1 Changes made in this version not seen in first lecture: 13 Feb 2018: add slide on constants and width simple ISA 4: mov-to-register 2 irmovq $constant, %ryy rrmovq %rxx, %ryy mrmovq 10(%rXX),
HCL 1 Changelog 1 Changes made in this version not seen in first lecture: 13 Feb 2018: add slide on constants and width simple ISA 4: mov-to-register 2 irmovq $constant, %ryy rrmovq %rxx, %ryy mrmovq 10(%rXX),
CS 3330 Exam 2 Fall 2017 Computing ID:
 S 3330 Fall 2017 Exam 2 Variant page 1 of 8 Email I: S 3330 Exam 2 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if we
S 3330 Fall 2017 Exam 2 Variant page 1 of 8 Email I: S 3330 Exam 2 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if we
layers of abstraction
 Exam Review 1 layers of abstraction 2 x += y Higher-level language: C add %rbx, %rax 60 03 SIXTEEN Assembly: X86-64 Machine code: Y86 Hardware Design Language: HCLRS Gates / Transistors / Wires / Registers
Exam Review 1 layers of abstraction 2 x += y Higher-level language: C add %rbx, %rax 60 03 SIXTEEN Assembly: X86-64 Machine code: Y86 Hardware Design Language: HCLRS Gates / Transistors / Wires / Registers
CS 3330 Exam 2 Spring 2017 Name: EXAM KEY Computing ID: KEY
 S 3330 Spring 2017 Exam 2 Variant E page 1 of 6 Email I: KEY S 3330 Exam 2 Spring 2017 Name: EXM KEY omputing I: KEY Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write
S 3330 Spring 2017 Exam 2 Variant E page 1 of 6 Email I: KEY S 3330 Exam 2 Spring 2017 Name: EXM KEY omputing I: KEY Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write
CS 3330 Exam 3 Fall 2017 Computing ID:
 S 3330 Fall 2017 Exam 3 Variant E page 1 of 16 Email I: S 3330 Exam 3 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if
S 3330 Fall 2017 Exam 3 Variant E page 1 of 16 Email I: S 3330 Exam 3 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if
CSC 252: Computer Organization Spring 2018: Lecture 11
 CSC 252: Computer Organization Spring 2018: Lecture 11 Instructor: Yuhao Zhu Department of Computer Science University of Rochester Action Items: Assignment 3 is due March 2, midnight Announcement Programming
CSC 252: Computer Organization Spring 2018: Lecture 11 Instructor: Yuhao Zhu Department of Computer Science University of Rochester Action Items: Assignment 3 is due March 2, midnight Announcement Programming
Changelog. Performance. locality exercise (1) a transformation
 Changelog Performance Changes made in this version not seen in first lecture: 26 October 2017: slide 28: remove extraneous text from code 1 1 locality exercise (1) a transformation /* version 1 */ for
Changelog Performance Changes made in this version not seen in first lecture: 26 October 2017: slide 28: remove extraneous text from code 1 1 locality exercise (1) a transformation /* version 1 */ for
Changelog. Changes made in this version not seen in first lecture: 26 October 2017: slide 28: remove extraneous text from code
 Performance 1 Changelog 1 Changes made in this version not seen in first lecture: 26 October 2017: slide 28: remove extraneous text from code locality exercise (1) 2 /* version 1 */ for (int i = 0; i
Performance 1 Changelog 1 Changes made in this version not seen in first lecture: 26 October 2017: slide 28: remove extraneous text from code locality exercise (1) 2 /* version 1 */ for (int i = 0; i
last time Exam Review on the homework on office hour locations hardware description language programming language that compiles to circuits
 last time Exam Review hardware description language programming language that compiles to circuits stages as conceptual division not the order things happen easier to figure out wiring stage-by-stage?
last time Exam Review hardware description language programming language that compiles to circuits stages as conceptual division not the order things happen easier to figure out wiring stage-by-stage?
CS 3330: SEQ part September 2016
 1 CS 3330: SEQ part 2 15 September 2016 Recall: Timing 2 compute new values between rising edges compute compute compute compute clock signal registers, memories change at rising edges next value register
1 CS 3330: SEQ part 2 15 September 2016 Recall: Timing 2 compute new values between rising edges compute compute compute compute clock signal registers, memories change at rising edges next value register
CS429: Computer Organization and Architecture
 CS429: Computer Organization and Architecture Dr Bill Young Department of Computer Sciences University of Texas at Austin Last updated: March 15, 2018 at 10:58 CS429 Slideset 13: 1 The ISA Byte 0 1 2 3
CS429: Computer Organization and Architecture Dr Bill Young Department of Computer Sciences University of Texas at Austin Last updated: March 15, 2018 at 10:58 CS429 Slideset 13: 1 The ISA Byte 0 1 2 3
Foundations of Computer Systems
 18-600 Foundations of Computer Systems Lecture 7: Processor Architecture & Design John P. Shen & Gregory Kesden September 20, 2017 Lecture #7 Processor Architecture & Design Lecture #8 Pipelined Processor
18-600 Foundations of Computer Systems Lecture 7: Processor Architecture & Design John P. Shen & Gregory Kesden September 20, 2017 Lecture #7 Processor Architecture & Design Lecture #8 Pipelined Processor
Computer Organization: A Programmer's Perspective
 A Programmer's Perspective Instruction Set Architecture Gal A. Kaminka galk@cs.biu.ac.il Outline: CPU Design Background Instruction sets Logic design Sequential Implementation A simple, but not very fast
A Programmer's Perspective Instruction Set Architecture Gal A. Kaminka galk@cs.biu.ac.il Outline: CPU Design Background Instruction sets Logic design Sequential Implementation A simple, but not very fast
CS 261 Fall Mike Lam, Professor. CPU architecture
 CS 261 Fall 2017 Mike Lam, Professor CPU architecture Topics CPU stages and design Pipelining Y86 semantics CPU overview A CPU consists of Combinational circuits for computation Sequential circuits for
CS 261 Fall 2017 Mike Lam, Professor CPU architecture Topics CPU stages and design Pipelining Y86 semantics CPU overview A CPU consists of Combinational circuits for computation Sequential circuits for
CS:APP Chapter 4 Computer Architecture Sequential Implementation
 CS:APP Chapter 4 Computer Architecture Sequential Implementation Randal E. Bryant Carnegie Mellon University CS:APP Y86 Instruction Set Byte ra rb ra rb V rb rb V ra D rb ra rb D D rb ra ra rb D ra rb
CS:APP Chapter 4 Computer Architecture Sequential Implementation Randal E. Bryant Carnegie Mellon University CS:APP Y86 Instruction Set Byte ra rb ra rb V rb rb V ra D rb ra rb D D rb ra ra rb D ra rb
Recitation #6. Architecture Lab
 18-600 Recitation #6 Architecture Lab Overview Where we are Archlab Intro Optimizing a Y86 program Intro to HCL Optimizing Processor Design Where we Are Archlab Intro Part A: write and simulate Y86-64
18-600 Recitation #6 Architecture Lab Overview Where we are Archlab Intro Optimizing a Y86 program Intro to HCL Optimizing Processor Design Where we Are Archlab Intro Part A: write and simulate Y86-64
The ISA. Fetch Logic
 The ISA CS429: Computer Organization and Architecture Dr Bill Young Department of Computer Science University of Texas at Austin Last updated: July 5, 2018 at 11:55 Byte 0 1 2 3 4 5 6 7 8 9 halt 0 0 nop
The ISA CS429: Computer Organization and Architecture Dr Bill Young Department of Computer Science University of Texas at Austin Last updated: July 5, 2018 at 11:55 Byte 0 1 2 3 4 5 6 7 8 9 halt 0 0 nop
Slide Set 9. for ENCM 369 Winter 2018 Section 01. Steve Norman, PhD, PEng
 Slide Set 9 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
Slide Set 9 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
CS:APP Chapter 4 Computer Architecture Wrap-Up Randal E. Bryant Carnegie Mellon University
 CS:APP Chapter 4 Computer Architecture Wrap-Up Randal E. Bryant Carnegie Mellon University http://csapp.cs.cmu.edu CS:APP Overview Wrap-Up of PIPE Design Performance analysis Fetch stage design Exceptional
CS:APP Chapter 4 Computer Architecture Wrap-Up Randal E. Bryant Carnegie Mellon University http://csapp.cs.cmu.edu CS:APP Overview Wrap-Up of PIPE Design Performance analysis Fetch stage design Exceptional
cmovxx ra, rb 2 fn ra rb irmovq V, rb 3 0 F rb V rmmovq ra, D(rB) 4 0 ra rb D mrmovq D(rB), ra 5 0 ra rb D OPq ra, rb 6 fn ra rb jxx Dest 7 fn Dest
 Computer Architecture: Y86-64 Sequential Implementation CSci 2021: Machine Architecture and Organization October 31st, 2018 Your instructor: Stephen McCamant Based on slides originally by: Randy Bryant
Computer Architecture: Y86-64 Sequential Implementation CSci 2021: Machine Architecture and Organization October 31st, 2018 Your instructor: Stephen McCamant Based on slides originally by: Randy Bryant
Changes made in this version not seen in first lecture:
 1 Changelog 1 Changes made in this version not seen in first lecture: 11 April 2018: loop unrolling v cache blocking (2): corrected second example which just did no loop unrolling or cache blocking before
1 Changelog 1 Changes made in this version not seen in first lecture: 11 April 2018: loop unrolling v cache blocking (2): corrected second example which just did no loop unrolling or cache blocking before
Computer Architecture I: Outline and Instruction Set Architecture. CENG331 - Computer Organization. Murat Manguoglu
 Computer Architecture I: Outline and Instruction Set Architecture CENG331 - Computer Organization Murat Manguoglu Adapted from slides of the textbook: http://csapp.cs.cmu.edu/ Outline Background Instruction
Computer Architecture I: Outline and Instruction Set Architecture CENG331 - Computer Organization Murat Manguoglu Adapted from slides of the textbook: http://csapp.cs.cmu.edu/ Outline Background Instruction
cmovxx ra, rb 2 fn ra rb irmovq V, rb 3 0 F rb V rmmovq ra, D(rB) 4 0 ra rb D mrmovq D(rB), ra 5 0 ra rb D OPq ra, rb 6 fn ra rb jxx Dest 7 fn Dest
 Computer Architecture: Y86-64 Sequential Implementation CSci 2021: Machine Architecture and Organization Lecture #19, March 4th, 2016 Your instructor: Stephen McCamant Based on slides originally by: Randy
Computer Architecture: Y86-64 Sequential Implementation CSci 2021: Machine Architecture and Organization Lecture #19, March 4th, 2016 Your instructor: Stephen McCamant Based on slides originally by: Randy
Intel x86-64 and Y86-64 Instruction Set Architecture
 CSE 2421: Systems I Low-Level Programming and Computer Organization Intel x86-64 and Y86-64 Instruction Set Architecture Presentation J Read/Study: Bryant 3.1 3.5, 4.1 Gojko Babić 03-07-2018 Intel x86
CSE 2421: Systems I Low-Level Programming and Computer Organization Intel x86-64 and Y86-64 Instruction Set Architecture Presentation J Read/Study: Bryant 3.1 3.5, 4.1 Gojko Babić 03-07-2018 Intel x86
CS:APP Chapter 4 Computer Architecture Wrap-Up Randal E. Bryant Carnegie Mellon University
 CS:APP Chapter 4 Computer Architecture Wrap-Up Randal E. Bryant Carnegie Mellon University http://csapp.cs.cmu.edu CS:APP2e Overview Wrap-Up of PIPE Design Exceptional conditions Performance analysis Fetch
CS:APP Chapter 4 Computer Architecture Wrap-Up Randal E. Bryant Carnegie Mellon University http://csapp.cs.cmu.edu CS:APP2e Overview Wrap-Up of PIPE Design Exceptional conditions Performance analysis Fetch
Key Point. What are Cache lines
 Caching 1 Key Point What are Cache lines Tags Index offset How do we find data in the cache? How do we tell if it s the right data? What decisions do we need to make in designing a cache? What are possible
Caching 1 Key Point What are Cache lines Tags Index offset How do we find data in the cache? How do we tell if it s the right data? What decisions do we need to make in designing a cache? What are possible
Overview. CS429: Computer Organization and Architecture. Y86 Instruction Set. Building Blocks
 Overview CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: March 15, 2018 at 10:54 How do we build a digital computer?
Overview CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: March 15, 2018 at 10:54 How do we build a digital computer?
Lecture 12. Memory Design & Caches, part 2. Christos Kozyrakis Stanford University
 Lecture 12 Memory Design & Caches, part 2 Christos Kozyrakis Stanford University http://eeclass.stanford.edu/ee108b 1 Announcements HW3 is due today PA2 is available on-line today Part 1 is due on 2/27
Lecture 12 Memory Design & Caches, part 2 Christos Kozyrakis Stanford University http://eeclass.stanford.edu/ee108b 1 Announcements HW3 is due today PA2 is available on-line today Part 1 is due on 2/27
Virtual Memory (2) 1
 Virtual Memory (2) 1 Changelog 1 Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Virtual Memory (2) 1 Changelog 1 Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Foundations of Computer Systems
 18-600 Foundations of Computer Systems Lecture 8: Pipelined Processor Design John P. Shen & Gregory Kesden September 25, 2017 Lecture #7 Processor Architecture & Design Lecture #8 Pipelined Processor Design
18-600 Foundations of Computer Systems Lecture 8: Pipelined Processor Design John P. Shen & Gregory Kesden September 25, 2017 Lecture #7 Processor Architecture & Design Lecture #8 Pipelined Processor Design
Changelog. More Performance. loop unrolling (ASM) exam graded
 Changelog More Performance Changes made in this version not seen in first lecture: 7 November 2017: reassociation: a (b (c d))) ((a b) c) d to be more consistent with assembly 7 November 2017: reassociation:
Changelog More Performance Changes made in this version not seen in first lecture: 7 November 2017: reassociation: a (b (c d))) ((a b) c) d to be more consistent with assembly 7 November 2017: reassociation:
God created the integers, all else is the work of man Leopold Kronecker
 Sequential Hardware God created the integers, all else is the work of man Leopold Kronecker (He believed in the reduction of all mathematics to arguments involving only the integers and a finite number
Sequential Hardware God created the integers, all else is the work of man Leopold Kronecker (He believed in the reduction of all mathematics to arguments involving only the integers and a finite number
Changelog. Virtual Memory (2) exercise: 64-bit system. exercise: 64-bit system
 Changelog Virtual Memory (2) Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Changelog Virtual Memory (2) Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Caches. Hiding Memory Access Times
 Caches Hiding Memory Access Times PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O N T R O L ALU CTL INSTRUCTION FETCH INSTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMORY
Caches Hiding Memory Access Times PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O N T R O L ALU CTL INSTRUCTION FETCH INSTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMORY
Computer Science 104:! Y86 & Single Cycle Processor Design!
 Computer Science 104: Y86 & Single Cycle Processor Design Alvin R. Lebeck Slides based on those from Randy Bryant 1 CS:APP Administrative Homework #4 My office hours today 11:30-12:30 Reading: text 4.3
Computer Science 104: Y86 & Single Cycle Processor Design Alvin R. Lebeck Slides based on those from Randy Bryant 1 CS:APP Administrative Homework #4 My office hours today 11:30-12:30 Reading: text 4.3
Memory Technology. Caches 1. Static RAM (SRAM) Dynamic RAM (DRAM) Magnetic disk. Ideal memory. 0.5ns 2.5ns, $2000 $5000 per GB
 Memory Technology Caches 1 Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per GB Ideal memory Average access time similar
Memory Technology Caches 1 Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per GB Ideal memory Average access time similar
Changes made in this version not seen in first lecture:
 More Performance 1 Changelog 1 Changes made in this version not seen in first lecture: 7 November 2017: reassociation: a (b (c d))) ((a b) c) d to be more consistent with assembly 7 November 2017: reassociation:
More Performance 1 Changelog 1 Changes made in this version not seen in first lecture: 7 November 2017: reassociation: a (b (c d))) ((a b) c) d to be more consistent with assembly 7 November 2017: reassociation:
CS 3330 Exam 2 Spring 2016 Name: EXAM KEY Computing ID: KEY
 S 3330 Spring 2016 xam 2 Variant U page 1 of 6 mail I: KY S 3330 xam 2 Spring 2016 Name: XM KY omputing I: KY Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters
S 3330 Spring 2016 xam 2 Variant U page 1 of 6 mail I: KY S 3330 xam 2 Spring 2016 Name: XM KY omputing I: KY Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters
CPSC 313, 04w Term 2 Midterm Exam 2 Solutions
 1. (10 marks) Short answers. CPSC 313, 04w Term 2 Midterm Exam 2 Solutions Date: March 11, 2005; Instructor: Mike Feeley 1a. Give an example of one important CISC feature that is normally not part of a
1. (10 marks) Short answers. CPSC 313, 04w Term 2 Midterm Exam 2 Solutions Date: March 11, 2005; Instructor: Mike Feeley 1a. Give an example of one important CISC feature that is normally not part of a
The University of Michigan - Department of EECS EECS 370 Introduction to Computer Architecture Midterm Exam 2 solutions April 5, 2011
 1. Performance Principles [5 pts] The University of Michigan - Department of EECS EECS 370 Introduction to Computer Architecture Midterm Exam 2 solutions April 5, 2011 For each of the following comparisons,
1. Performance Principles [5 pts] The University of Michigan - Department of EECS EECS 370 Introduction to Computer Architecture Midterm Exam 2 solutions April 5, 2011 For each of the following comparisons,
Where Have We Been? Logic Design in HCL. Assembly Language Instruction Set Architecture (Y86) Finite State Machines
 Where Have We Been? Assembly Language Instruction Set Architecture (Y86) Finite State Machines States and Transitions Events Where Are We Going? Tracing Instructions at the Register Level Build a CPU!
Where Have We Been? Assembly Language Instruction Set Architecture (Y86) Finite State Machines States and Transitions Events Where Are We Going? Tracing Instructions at the Register Level Build a CPU!
Cache memories are small, fast SRAM-based memories managed automatically in hardware. Hold frequently accessed blocks of main memory
 Cache Memories Cache memories are small, fast SRAM-based memories managed automatically in hardware. Hold frequently accessed blocks of main memory CPU looks first for data in caches (e.g., L1, L2, and
Cache Memories Cache memories are small, fast SRAM-based memories managed automatically in hardware. Hold frequently accessed blocks of main memory CPU looks first for data in caches (e.g., L1, L2, and
Computer Architecture CS372 Exam 3
 Name: Computer Architecture CS372 Exam 3 This exam has 7 pages. Please make sure you have all of them. Write your name on this page and initials on every other page now. You may only use the green card
Name: Computer Architecture CS372 Exam 3 This exam has 7 pages. Please make sure you have all of them. Write your name on this page and initials on every other page now. You may only use the green card
Memory. Lecture 22 CS301
 Memory Lecture 22 CS301 Administrative Daily Review of today s lecture w Due tomorrow (11/13) at 8am HW #8 due today at 5pm Program #2 due Friday, 11/16 at 11:59pm Test #2 Wednesday Pipelined Machine Fetch
Memory Lecture 22 CS301 Administrative Daily Review of today s lecture w Due tomorrow (11/13) at 8am HW #8 due today at 5pm Program #2 due Friday, 11/16 at 11:59pm Test #2 Wednesday Pipelined Machine Fetch
Sequential Implementation
 CS:APP Chapter 4 Computer Architecture Sequential Implementation Randal E. Bryant adapted by Jason Fritts http://csapp.cs.cmu.edu CS:APP2e Hardware Architecture - using Y86 ISA For learning aspects of
CS:APP Chapter 4 Computer Architecture Sequential Implementation Randal E. Bryant adapted by Jason Fritts http://csapp.cs.cmu.edu CS:APP2e Hardware Architecture - using Y86 ISA For learning aspects of
Computer Architecture Sample Test 1
 Computer Architecture Sample Test 1 Question 1. Suppose we have 32-bit memory addresses, a byte-addressable memory, and a 512 KB (2 19 bytes) cache with 32 (2 5 ) bytes per block. a) How many total lines
Computer Architecture Sample Test 1 Question 1. Suppose we have 32-bit memory addresses, a byte-addressable memory, and a 512 KB (2 19 bytes) cache with 32 (2 5 ) bytes per block. a) How many total lines
Data Hazard vs. Control Hazard. CS429: Computer Organization and Architecture. How Do We Fix the Pipeline? Possibilities: How Do We Fix the Pipeline?
 Data Hazard vs. Control Hazard CS429: Computer Organization and Architecture There are two types of hazards that interfere with flow through a pipeline. Dr. Bill Young Department of Computer Science University
Data Hazard vs. Control Hazard CS429: Computer Organization and Architecture There are two types of hazards that interfere with flow through a pipeline. Dr. Bill Young Department of Computer Science University
Comprehensive Exams COMPUTER ARCHITECTURE. Spring April 3, 2006
 Comprehensive Exams COMPUTER ARCHITECTURE Spring 2006 April 3, 2006 ID Number 1 /15 2 /20 3 /20 4 /20 Total /75 Problem 1. ( 15 points) Logic Design: A three-input switching function is expressed as f(a,
Comprehensive Exams COMPUTER ARCHITECTURE Spring 2006 April 3, 2006 ID Number 1 /15 2 /20 3 /20 4 /20 Total /75 Problem 1. ( 15 points) Logic Design: A three-input switching function is expressed as f(a,
CS429: Computer Organization and Architecture
 CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: April 4, 2018 at 07:36 CS429 Slideset 16: 1 Data Hazard vs. Control
CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: April 4, 2018 at 07:36 CS429 Slideset 16: 1 Data Hazard vs. Control
void twiddle1(int *xp, int *yp) { void twiddle2(int *xp, int *yp) {
 Optimization void twiddle1(int *xp, int *yp) { *xp += *yp; *xp += *yp; void twiddle2(int *xp, int *yp) { *xp += 2* *yp; void main() { int x = 3; int y = 3; twiddle1(&x, &y); x = 3; y = 3; twiddle2(&x,
Optimization void twiddle1(int *xp, int *yp) { *xp += *yp; *xp += *yp; void twiddle2(int *xp, int *yp) { *xp += 2* *yp; void main() { int x = 3; int y = 3; twiddle1(&x, &y); x = 3; y = 3; twiddle2(&x,
Pipelined processors and Hazards
 Pipelined processors and Hazards Two options Processor HLL Compiler ALU LU Output Program Control unit 1. Either the control unit can be smart, i,e. it can delay instruction phases to avoid hazards. Processor
Pipelined processors and Hazards Two options Processor HLL Compiler ALU LU Output Program Control unit 1. Either the control unit can be smart, i,e. it can delay instruction phases to avoid hazards. Processor
CS356: Discussion #9 Memory Hierarchy and Caches. Marco Paolieri Illustrations from CS:APP3e textbook
 CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
EEC 483 Computer Organization
 EEC 48 Computer Organization 5. The Basics of Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set (memory) Unlike registers or memory,
EEC 48 Computer Organization 5. The Basics of Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set (memory) Unlike registers or memory,
Systems I. Datapath Design II. Topics Control flow instructions Hardware for sequential machine (SEQ)
 Systems I Datapath Design II Topics Control flow instructions Hardware for sequential machine (SEQ) Executing Jumps jxx Dest 7 fn Dest fall thru: XX XX Not taken target: XX XX Taken Read 5 bytes Increment
Systems I Datapath Design II Topics Control flow instructions Hardware for sequential machine (SEQ) Executing Jumps jxx Dest 7 fn Dest fall thru: XX XX Not taken target: XX XX Taken Read 5 bytes Increment
Topics of this Slideset. CS429: Computer Organization and Architecture. Instruction Set Architecture. Why Y86? Instruction Set Architecture
 Topics of this Slideset CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Intro to Assembly language Programmer visible state Y86
Topics of this Slideset CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Intro to Assembly language Programmer visible state Y86
CS429: Computer Organization and Architecture
 CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: October 11, 2017 at 17:42 CS429 Slideset 6: 1 Topics of this Slideset
CS429: Computer Organization and Architecture Dr. Bill Young Department of Computer Sciences University of Texas at Austin Last updated: October 11, 2017 at 17:42 CS429 Slideset 6: 1 Topics of this Slideset
CS 152 Computer Architecture and Engineering. Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste!
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste!
Caches and Memory Hierarchy: Review. UCSB CS240A, Winter 2016
 Caches and Memory Hierarchy: Review UCSB CS240A, Winter 2016 1 Motivation Most applications in a single processor runs at only 10-20% of the processor peak Most of the single processor performance loss
Caches and Memory Hierarchy: Review UCSB CS240A, Winter 2016 1 Motivation Most applications in a single processor runs at only 10-20% of the processor peak Most of the single processor performance loss
CPSC 313, Summer 2013 Final Exam Solution Date: June 24, 2013; Instructor: Mike Feeley
 CPSC 313, Summer 2013 Final Exam Solution Date: June 24, 2013; Instructor: Mike Feeley 1 (10 marks) This question is concerned with the general principles of pipelining, dependencies and hazards. First,
CPSC 313, Summer 2013 Final Exam Solution Date: June 24, 2013; Instructor: Mike Feeley 1 (10 marks) This question is concerned with the general principles of pipelining, dependencies and hazards. First,
Byte. cmovle 7 1. halt 0 0 addq 6 0 nop 1 0 subq 6 1 cmovxx ra, rb 2 fn ra rb andq 6 2 irmovq V, rb 3 0 F rb V xorq 6 3. cmovl 7 2.
 Y86-6 Instruc&on Set Computer rchitecture Sequen&al Implementa&on CSCI 202: Machine rchitecture and Organiza&on Byte 0 2 3 5 6 7 8 9 2 fn r rb irmovq V, rb 3 0 F rb V 0 r rb Pen- Chung Yew epartment Computer
Y86-6 Instruc&on Set Computer rchitecture Sequen&al Implementa&on CSCI 202: Machine rchitecture and Organiza&on Byte 0 2 3 5 6 7 8 9 2 fn r rb irmovq V, rb 3 0 F rb V 0 r rb Pen- Chung Yew epartment Computer
Caching Basics. Memory Hierarchies
 Caching Basics CS448 1 Memory Hierarchies Takes advantage of locality of reference principle Most programs do not access all code and data uniformly, but repeat for certain data choices spatial nearby
Caching Basics CS448 1 Memory Hierarchies Takes advantage of locality of reference principle Most programs do not access all code and data uniformly, but repeat for certain data choices spatial nearby
data block 0, word 0 block 0, word 1 block 1, word 0 block 1, word 1 block 2, word 0 block 2, word 1 block 3, word 0 block 3, word 1 Word index cache
 Taking advantage of spatial locality Use block size larger than one word Example: two words Block index tag () () Alternate representations Word index tag block, word block, word block, word block, word
Taking advantage of spatial locality Use block size larger than one word Example: two words Block index tag () () Alternate representations Word index tag block, word block, word block, word block, word
Donn Morrison Department of Computer Science. TDT4255 Memory hierarchies
 TDT4255 Lecture 10: Memory hierarchies Donn Morrison Department of Computer Science 2 Outline Chapter 5 - Memory hierarchies (5.1-5.5) Temporal and spacial locality Hits and misses Direct-mapped, set associative,
TDT4255 Lecture 10: Memory hierarchies Donn Morrison Department of Computer Science 2 Outline Chapter 5 - Memory hierarchies (5.1-5.5) Temporal and spacial locality Hits and misses Direct-mapped, set associative,
LECTURE 11. Memory Hierarchy
 LECTURE 11 Memory Hierarchy MEMORY HIERARCHY When it comes to memory, there are two universally desirable properties: Large Size: ideally, we want to never have to worry about running out of memory. Speed
LECTURE 11 Memory Hierarchy MEMORY HIERARCHY When it comes to memory, there are two universally desirable properties: Large Size: ideally, we want to never have to worry about running out of memory. Speed
Memory Hierarchies &
 Memory Hierarchies & Cache Memory CSE 410, Spring 2009 Computer Systems http://www.cs.washington.edu/410 4/26/2009 cse410-13-cache 2006-09 Perkins, DW Johnson and University of Washington 1 Reading and
Memory Hierarchies & Cache Memory CSE 410, Spring 2009 Computer Systems http://www.cs.washington.edu/410 4/26/2009 cse410-13-cache 2006-09 Perkins, DW Johnson and University of Washington 1 Reading and
CSE 2021: Computer Organization
 CSE 2021: Computer Organization Lecture-12a Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CSE 2021: Computer Organization Lecture-12a Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CPSC 121: Models of Computation Lab #9: A Working Computer
 CPSC 121: Models of Computation Lab #9: A Working Computer Objectives In this lab, we revisit the Y86 processor, which you saw components of in labs 4 and 6. Recall that in lab 4, you learned about the
CPSC 121: Models of Computation Lab #9: A Working Computer Objectives In this lab, we revisit the Y86 processor, which you saw components of in labs 4 and 6. Recall that in lab 4, you learned about the
Chapter 5A. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5A Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) Fast, expensive Dynamic RAM (DRAM) In between Magnetic disk Slow, inexpensive Ideal memory Access time of SRAM
Chapter 5A Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) Fast, expensive Dynamic RAM (DRAM) In between Magnetic disk Slow, inexpensive Ideal memory Access time of SRAM
Kathryn Chan, Kevin Bi, Ryan Wong, Waylon Huang, Xinyu Sui
 Caches III CSE 410 Winter 2017 Instructor: Justin Hsia Teaching Assistants: Kathryn Chan, Kevin Bi, Ryan Wong, Waylon Huang, Xinyu Sui Please stop charging your phone in public ports "Just by plugging
Caches III CSE 410 Winter 2017 Instructor: Justin Hsia Teaching Assistants: Kathryn Chan, Kevin Bi, Ryan Wong, Waylon Huang, Xinyu Sui Please stop charging your phone in public ports "Just by plugging
Caches and Memory Hierarchy: Review. UCSB CS240A, Fall 2017
 Caches and Memory Hierarchy: Review UCSB CS24A, Fall 27 Motivation Most applications in a single processor runs at only - 2% of the processor peak Most of the single processor performance loss is in the
Caches and Memory Hierarchy: Review UCSB CS24A, Fall 27 Motivation Most applications in a single processor runs at only - 2% of the processor peak Most of the single processor performance loss is in the
CSE 2021: Computer Organization
 CSE 2021: Computer Organization Lecture-12 Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CSE 2021: Computer Organization Lecture-12 Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CS 3330 Exam 1 Fall 2017 Computing ID:
 S 3330 Fall 2017 xam 1 Variant page 1 of 8 mail I: S 3330 xam 1 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if we are
S 3330 Fall 2017 xam 1 Variant page 1 of 8 mail I: S 3330 xam 1 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if we are
Control Hazards - branching causes problems since the pipeline can be filled with the wrong instructions.
 Control Hazards - branching causes problems since the pipeline can be filled with the wrong instructions Stage Instruction Fetch Instruction Decode Execution / Effective addr Memory access Write-back Abbreviation
Control Hazards - branching causes problems since the pipeline can be filled with the wrong instructions Stage Instruction Fetch Instruction Decode Execution / Effective addr Memory access Write-back Abbreviation
CS:APP Chapter 4 Computer Architecture Sequential Implementation
 CS:APP Chapter 4 Computer Architecture Sequential Implementation Randal E. Bryant Carnegie Mellon University http://csapp.cs.cmu.edu CS:APP Y86 Instruction Set Byte 0 1 2 3 4 5 nop 0 0 halt 1 0 rrmovl
CS:APP Chapter 4 Computer Architecture Sequential Implementation Randal E. Bryant Carnegie Mellon University http://csapp.cs.cmu.edu CS:APP Y86 Instruction Set Byte 0 1 2 3 4 5 nop 0 0 halt 1 0 rrmovl
cmovxx ra, rb 2 fn ra rb irmovq V, rb 3 0 F rb V rmmovq ra, D(rB) 4 0 ra rb mrmovq D(rB), ra 5 0 ra rb OPq ra, rb 6 fn ra rb jxx Dest 7 fn Dest
 Instruction Set Architecture Computer Architecture: Instruction Set Architecture CSci 2021: Machine Architecture and Organization Lecture #16, February 24th, 2016 Your instructor: Stephen McCamant Based
Instruction Set Architecture Computer Architecture: Instruction Set Architecture CSci 2021: Machine Architecture and Organization Lecture #16, February 24th, 2016 Your instructor: Stephen McCamant Based
Last class. Caches. Direct mapped
 Memory Hierarchy II Last class Caches Direct mapped E=1 (One cache line per set) Each main memory address can be placed in exactly one place in the cache Conflict misses if two addresses map to same place
Memory Hierarchy II Last class Caches Direct mapped E=1 (One cache line per set) Each main memory address can be placed in exactly one place in the cache Conflict misses if two addresses map to same place
Registers. Instruction Memory A L U. Data Memory C O N T R O L M U X A D D A D D. Sh L 2 M U X. Sign Ext M U X ALU CTL INSTRUCTION FETCH
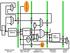 PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O T R O L ALU CTL ISTRUCTIO FETCH ISTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMOR ACCESS WRITE BACK A D D A D D A L U
PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O T R O L ALU CTL ISTRUCTIO FETCH ISTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMOR ACCESS WRITE BACK A D D A D D A L U
Meltdown and Spectre: Complexity and the death of security
 Meltdown and Spectre: Complexity and the death of security May 8, 2018 Meltdown and Spectre: Wait, my computer does what? May 8, 2018 Meltdown and Spectre: Whoever thought that was a good idea? May 8,
Meltdown and Spectre: Complexity and the death of security May 8, 2018 Meltdown and Spectre: Wait, my computer does what? May 8, 2018 Meltdown and Spectre: Whoever thought that was a good idea? May 8,
CENG 3420 Computer Organization and Design. Lecture 08: Cache Review. Bei Yu
 CENG 3420 Computer Organization and Design Lecture 08: Cache Review Bei Yu CEG3420 L08.1 Spring 2016 A Typical Memory Hierarchy q Take advantage of the principle of locality to present the user with as
CENG 3420 Computer Organization and Design Lecture 08: Cache Review Bei Yu CEG3420 L08.1 Spring 2016 A Typical Memory Hierarchy q Take advantage of the principle of locality to present the user with as
Exam-2 Scope. 3. Shared memory architecture, distributed memory architecture, SMP, Distributed Shared Memory and Directory based coherence
 Exam-2 Scope 1. Memory Hierarchy Design (Cache, Virtual memory) Chapter-2 slides memory-basics.ppt Optimizations of Cache Performance Memory technology and optimizations Virtual memory 2. SIMD, MIMD, Vector,
Exam-2 Scope 1. Memory Hierarchy Design (Cache, Virtual memory) Chapter-2 slides memory-basics.ppt Optimizations of Cache Performance Memory technology and optimizations Virtual memory 2. SIMD, MIMD, Vector,
CS 152 Computer Architecture and Engineering. Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste
Caches III CSE 351 Spring
 Caches III CSE 351 Spring 2018 https://what-if.xkcd.com/111/ Making memory accesses fast! Cache basics Principle of locality Memory hierarchies Cache organization Direct-mapped (sets; index + tag) Associativity
Caches III CSE 351 Spring 2018 https://what-if.xkcd.com/111/ Making memory accesses fast! Cache basics Principle of locality Memory hierarchies Cache organization Direct-mapped (sets; index + tag) Associativity
Computer Science 104:! Y86 & Single Cycle Processor Design!
 Computer Science 104: Y86 & Single Cycle Processor Design Alvin R. Lebeck Slides based on those from Randy Bryant CS:APP Administrative HW #4 Due tomorrow tonight HW #5 up soon ing: 4.1-4.3 Today Review
Computer Science 104: Y86 & Single Cycle Processor Design Alvin R. Lebeck Slides based on those from Randy Bryant CS:APP Administrative HW #4 Due tomorrow tonight HW #5 up soon ing: 4.1-4.3 Today Review
Roadmap. Java: Assembly language: OS: Machine code: Computer system:
 Roadmap C: car *c = malloc(sizeof(car)); c->miles = 100; c->gals = 17; float mpg = get_mpg(c); free(c); Assembly language: Machine code: get_mpg: pushq movq... popq ret %rbp %rsp, %rbp %rbp 0111010000011000
Roadmap C: car *c = malloc(sizeof(car)); c->miles = 100; c->gals = 17; float mpg = get_mpg(c); free(c); Assembly language: Machine code: get_mpg: pushq movq... popq ret %rbp %rsp, %rbp %rbp 0111010000011000
Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
Agenda Cache memory organization and operation Chapter 6 Performance impact of caches Cache Memories
 Agenda Chapter 6 Cache Memories Cache memory organization and operation Performance impact of caches The memory mountain Rearranging loops to improve spatial locality Using blocking to improve temporal
Agenda Chapter 6 Cache Memories Cache memory organization and operation Performance impact of caches The memory mountain Rearranging loops to improve spatial locality Using blocking to improve temporal
Caches III. CSE 351 Spring Instructor: Ruth Anderson
 Caches III CSE 351 Spring 2017 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Office Hours Changes check
Caches III CSE 351 Spring 2017 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Office Hours Changes check
5. Memory Hierarchy Computer Architecture COMP SCI 2GA3 / SFWR ENG 2GA3. Emil Sekerinski, McMaster University, Fall Term 2015/16
 5. Memory Hierarchy Computer Architecture COMP SCI 2GA3 / SFWR ENG 2GA3 Emil Sekerinski, McMaster University, Fall Term 2015/16 Movie Rental Store You have a huge warehouse with every movie ever made.
5. Memory Hierarchy Computer Architecture COMP SCI 2GA3 / SFWR ENG 2GA3 Emil Sekerinski, McMaster University, Fall Term 2015/16 Movie Rental Store You have a huge warehouse with every movie ever made.
Caches Concepts Review
 Caches Concepts Review What is a block address? Why not bring just what is needed by the processor? What is a set associative cache? Write-through? Write-back? Then we ll see: Block allocation policy on
Caches Concepts Review What is a block address? Why not bring just what is needed by the processor? What is a set associative cache? Write-through? Write-back? Then we ll see: Block allocation policy on
