Efficient Two Dimensional-IP Routing: An Incremental Deployment Design
|
|
|
- Gloria Thornton
- 5 years ago
- Views:
Transcription
1 Efficien Two Dimensional-IP Rouing: An Incremenal Deploymen Design Shu Yang Tsinghua Universiy Dan Wang Hong Kong Polyechnic Universiy Mingwei Xu Tsinghua Universiy Jianping Wu Tsinghua Universiy Absrac China Educaion and Research Nework 2 (CER- NET2) is deploying Two Dimensional-IP (TwoD-IP) rouing. Tha is, he forwarding decision of each rouer is no only based on he desinaion address, bu also on he source address. One driving force is ha he nework needs he abiliy o diver raffic flows (idenified by heir source and desinaion IPs and we call hem he VIP flows) o pre-defined pahs (we call hem he VIP pahs). There are also increasing demands on load balancing, securiy issues, ec. A pure IP based soluion is favored over MPLS. An imporan research issue owards TwoD-IP rouing is he deploymen of he TwoD-IP rouing scheme. I is widely known ha making changes o he nework layer is nooriously difficul. The proposed scheme should have leas impac on he curren Inerne proocols and infrasrucure. A node-by-node incremenal deploymen scheme is highly preferred. Obviously, wihou full deploymen, he resuling pahs for raffic diversion may deviae from he required VIP pahs. The incremenal deploymen scheme should minimize such deviaion. In his paper, we formulae he problem as finding a deploymen sequence where he VIP raffic flows should follow he VIP pahs given 1) he number of nodes o be deployed and 2) he exra burden each rouer can spare for TwoD-IP rouing. We novelly ransform our problem o boolean clauses and develop efficien soluions following he MAX-SAT problem. Afer deploying par of he rouers, nework opology and VIP flows may change, which will enlarge he deviaion of he resuling pahs from he required VIP pahs. To reduce he deviaion, we devise a new proocol called PaFid, ha makes rouers adapively change heir forwarding operaions according o opology and VIP flow informaion. We develop a dynamic programming based algorihm for he adapive forwarding problem. We evaluae our algorihms using comprehensive simulaions wih BRITE generaed opologies and real world opologies. We conduc a case sudy on CERNET2 configuraions. Compared o an ad-hoc deploymen and an arbirary TwoD-IP forwarding, our algorihms compue a deploymen sequence ha achieves close o opimal performance afer deploying a few nodes. Besides, our adapive forwarding proocol can grealy improve he performance when nework opology and VIP flows change. I. INTRODUCTION China Educaion and Research Nework 2 (CERNET2), he world s larges IPv6 backbone nework (including 59 Giga-PoPs), provides services o end users in Chinese u- niversiies across over 22 major ciies. CERNET2 is an operaional nework, ye i also underakes experimenal purposes for new infrasrucure and proocols validaion. CERNET2 is currenly deploying source IP funcionaliies for QoS and securiy reasons. A he edge rouers, CERNET2 has deployed SAVI (Source Address Validaion Improvemen) [1], where he source address of each packe is checked. SAVI guaranees ha each packe will hold an auhenicaed source IP address, and hus enhances he securiy of he nework. We are now deploying Two Dimensional-IP (TwoD-IP) rouing [2]. More specifically, he forwarding decisions of inermediae rouers will be based no only on he desinaion addresses, bu also he source addresses. One driving force is policy rouing, i.e., he nework has he abiliy o diver raffic flows (idenified by heir source and desinaion IPs and we call hem he VIP flows) o pre-defined pahs (we call hem he VIP pahs). CERNET2 has wo inernaional exchange ceners connecing o he Inerne, Beijing (CNGI- 6IX) and Shanghai (CNGI-SHIX). For example, we find in operaion ha CNGI-6IX is very congesed wih an average hroughpu of 1.18Gbps in February 211; and CNGI-SHIX is much more spared wih a maximal hroughpu of 8.3Mbps a he same ime. Wih an overall consideraions on securiy, load balancing, policy rouing, we chose o enhance he nework wih source IP funcionaliies. We have developed a prooype rouer (BiEngine 124) and are designing TwoD-IP rouing wih suppor from Naional Basic Research Program of China (973). There are many research issues o address for TwoD-IP rouing. An imporan problem is he deploymen of he TwoD-IP rouing scheme. Unlike SAVI, which was deployed on edge rouers, TwoD-IP rouing requires upgrade of he CERNET2. I is widely known ha making changes o he nework layer is nooriously difficul. The proposed scheme should have leas impac on he curren Inerne proocol sack and infrasrucure. A node-by-node incremenal deploymen scheme is highly preferred. Clearly, if only parial nodes are deployed, a VIP flow may no sricly follow is VIP pah. We need o minimize he deviaion. In his paper, we define a deviaion ha is pracically meaningful. We formulae a problem where we need o derive a deploymen sequence and minimize he deviaion given he number of nodes o be deployed. We show ha he problem is NP-complee by reducing i o a dense-k subgraph problem. We hen novelly ransform our problem o boolean clauses and develop algorihms
2 Desinaion Table Source Table )*+, TDable Figure 1: Example of TwoD-IP rouing 2 3 #$%$%$# #$%$%$& #$%$%$' #$%$%$(!" Mapping Table following he principle of he branch-and-bound algorihm for MAX-SAT. We sudy several closely relaed problems for differen pracical scenarios. We develop efficien algorihms for hese problems o compue incremenal deploymen sequence. Alhough we provide guidelines on deploymen sequence, he ISPs may do no wan o follow he sequence. Even if hey follow, nework opology and VIP flows may change afer deploying. These facors can all enlarge he deviaion. To reduce he deviaion, we propose o le he deployed rouers adapively change heir forwarding operaions, according o nework opology and VIP informaion. We develop a proocol call PaFid, which collecs he needed informaion and conrols he forwarding operaions of rouers. We also design a dynamic programming based algorihm, which is opimal for reducing he deviaion. We conduc comprehensive simulaions using BRITE generaed opologies. We also evaluae our algorihms using he opology of China Educaion and Research Nework (CER- NET), a medium scale IPv4 nework wih 11 rouers and 238 links. The resuls show ha our algorihm can achieve close o opimal performance by deploying a few carefully seleced nodes. The adapive forwarding mechanism can grealy improve he performance, when ISPs do no follow he opimal deploymen sequence, or nework opology and VIP flows change afer deploying. Besides, he adapive forwarding mechanism only srech a lile for he pah ha VIP raffic flows hrough. We carry ou a case sudy wih CERNET2 configuraion and our primary concerned VIP raffic flows. We sugges he deploymen sequence of TwoD-IP rouing. By deploying 5 rouers, we can successfully diver our concerned VIP raffic flows from he congesed CNGI-6IX o CNGI-SHIX. II. BACKGROUND AND THE OPTIMAL INCREMENTAL DEPLOYMENT PROBLEM A. Background on TwoD-IP Rouing We firs give he background of he TwoD-IP rouing in our conex. In each rouer, here is a TwoD-IP forwarding able, which is made up of wo ables sored in TCAMs and wo ables sored in SRAM (see Fig. 1). One able in TCAM sores he desinaion prefixes (we call i desinaion able hereafer), and he oher able in TCAM sores he source prefixes (we call i source able hereafer). One able in SRAM is a wo dimensional able ha sores he indexed nex hop of each rule in TwoD-IP (we call i TD-able hereafer) and we call each cell in he array TD-cell (or in shor cell if no ambiguiy). Anoher able in SRAM sores he mapping relaion of index values and nex hops (we call i mapping-able hereafer). When a packe arrives, he rouer firs exracs he source address and desinaion address. Using he LMF rule, he rouer finds he mached source and desinaion prefixes in boh source and desinaion ables ha reside in he TCAMs. According o he mached enry, he source able will oupu a column address and he desinaion able will oupu a row address. Combined wih he row and column addresses, he rouer can find a cell in he TD-able, and reurn an index value. Using he index value, he rouer looks up he mapping able, and reurn he nex hop ha he packe will be forwarded o. For example, in Fig. 1, a packe wih a desinaion address of 11 and source address of 1111 will mach 1* in he desinaion able, and 111* in he source able. The desinaion able will oupu 1 s row, and he source able will oupu 1 s column. The cell in 1 s row and 1 s column of TD-able is 2, which corresponds o 1.. in he mapping able. Thus he packe will be forwarded o 1... The updaes of TwoD-IP forwarding able can be manually configurable for regisered VIP flows. Our curren
3 CERNET2 requiremen of divering a few raffic flows will end up in his way. In he fuure, when more source IP funcionaliies are needed and VIP raffic flows are more dynamic, a decenralized (e.g., OSPF-like) or cenralized (e.g., OpenFlow-like) mechanism can be developed. B. The Opimal Incremenal Deploymen Problem Le G = (V,E) be a nework, where V is he se of nodes, and E is he se of links. In his nework we have muliple VIP raffic flows. Le T denoe he se of raffic flows, and T be a VIP raffic flow. Le he source and desinaion prefixes ofbep s (),P d (), can be represened as < P s (),P d () >. In his paper, we ofen omi he desinaion prefix, i.e., only use he source prefix o idenify a flow if here is no ambiguiy. For each, he user expecs i o ravel on a pre-defined VIP pah (which usually is no he shores pah). We use VIP() = {v,v1,...,vj,...} o denoe he VIP pah for. For a desinaion IP prefix P d (we omi he raffic if here is no ambiguiy). On a nodev, we call i forwarding an operaion I d v(p d ) o map P d o a se of nex hops I d v(p d ) = {a,a 1,...,a j,...}, each of which can lead he packes o he desinaion (saisfying [3] o be loop-free and failureoleran). In convenional rouing, he resul of a forwarding I d v (P d) is a single nex hop on he shores pah. For a source IP prefix, we call i Two Dimensional-IP (TwoD-IP) forwarding as an operaioni s v(p s ) o mapp s o a nex hop a {a,a 1,...,a j,...}. TwoD-IP rouing is ha for each packe, he rouers perform a forwarding operaion and a TwoD-IP forwarding operaion o find a nex hop on he pre-defined VIP pah (noe ha for packes of non-vip raffic, a forwarding operaion already resuls in a nex hop). Le he pah of a packe forwarded by TwoD-IP rouing be L(P s ) = {v,v 1,...,v j,...}; here we only use he source prefix P s o denoe a packe for simpliciy. If we deploy node v, his node is TwoD-IP forwarding capable, i.e., his node can perform operaion I s v (P s). A deploymen G is a se of nodes V V ha are deployed o be TwoD-IP forwarding capable. If we do no deploy node v, v will use convenional shores pah rouing. In a deploymen process, le κ be he number of nodes we wan o deploy. Since a deploymen G may include a subse of nodes, he resuling pah for a VIP raffic flow may deviae from is VIP(). Noe ha given G, for a VIP raffic (idenified by is P s ), is pah is deermined. Le L(G,P s ) denoe such pah. Clearly, we wan such deviaion o be small. To quanify such deviaion, In our formulaion, we used hamming disance o represen he deviaion beween pahs. While hamming disance is a well-known indicaor of he differences beween vecors and was widely used by previous works [4], here exiss oher meaningful merics. We will consider oher merics and heir comparison in our fuure work. Noe ha we do no exclude oher meaningful merics and hey should be discussed in our fuure work. We define D(L i,l j ) = max{ L i, L j } L i L j he disance beween wo pahs L i and L j. Since shores pah is used if a node is no deployed, we always have L(G,P s ) VIP(). Thus, Observaion 1. D(VIP(),L(G,P s )) = VIP() VIP() L(G,P s ). Our objecive is ha given he number of rouers ha we wan o deploy, find a deploymen ha minimizes he oal disance of he pahs of he VIP flows and heir pre-defined VIP pahs. Problem 1. Opimal Deploymen: Given κ, find a deploymen G o where G o = κ so ha D(VIP(),L(Go,P s )) is minimized. In pracice, according o differen volume of he VIP raffic flows, we may need o assign differen weighs, i.e., w for flow. In our problem formulaion, we can add his weigh o he disance and modify D(VIP(),L(Go,P s )) o w D(VIP(),L(G o,p s )) o show differen imporance of in he aggregaed disance. In his paper, we will focus our sudy on he unweighed problem. Our analysis and soluions will no change in he weighed version. We will briefly menion he weighed case in our case sudy. As said, incremenal deploymen is highly favored in pracice. Le G i = V i and G j = V j be wo deploymens. We call G j incremenal o G i if V i V j. An incremenal deploymen is a series of deploymen G,G 1,...,G j,..., such ha G j is incremenal o G i if i < j. Thus, Problem 2. Opimal Incremenal Deploymen: Given κ,κ 1,...,κ j,..., find an incremenal deploymen, G o,go 1,...,Go j,..., such ha Go i = κ i, and G o i is an opimal deploymen. Table I: Noaion Lis Noaion Definiion Noaion Definiion V se of nodes Iv d forwarding operaion raffic flows Iv s TwoD-IP forwarding T se of raffic flows G a deploymen VIP() VIP pah for L(G,P s) TwoD-IP pah P s source IP prefix κ deployed number P d desinaion IP prefix Table II: Forwarding operaions for he rouers c in Fig. 2 Desinaion Ic( ) d P d = {e} (11 ) (a) Convenional Desinaion Ic d( ) Source Is c ( ) P d = P {d,e} s( ) d (11 ) non-vip e (b) TwoD-IP We illusrae our definiions wih an example opology in Fig. 2. Here we assume a is he source and e is he desinaion. For a raffic flow he shores pah from a o e
4 b a c e VIP( / ) shores d Figure 2: Nework opology and VIP pahs is {a,c,e}. Assume here is one VIP flow and one non- VIP flow. Assume he pre-defined VIP pah is VIP( ) = {a,b,c,d,e}. As discussed, he VIP flow is idenified by is source IP prefix and desinaion IP prefix. Assume he source and desinaion prefixes of are P s ( ) = ( ) and P d ( ) = (11 ); he source and desinaion prefixes of non-vip flow is (1 ) and (11 ). The forwarding operaion on node c for convenional rouing is shown in Table III(a). To achieve TwoD-IP rouing, node c should forward he packes of o d, and he packes of non-vip flow o e, ha is, I s c (P s( )) = d. We show he forwarding operaion and TwoD-IP forwarding operaion on node c for TwoD-IP rouing in Table III(b). Assume we deploy one node, i.e., κ = 1 and we selec c, i.e., deploymen G = {c}. Then L(G,P s ) = {a,c,d,e}, and D(VIP( ),L(G,P s )) = 5 4 = 1. The opimal deploymen is G o = {c}. III. OPTIMAL INCREMENTAL DEPLOYMENT We will firs develop an algorihm for he opimal deploymen given he number of nodes o be deployed (Problem 1). We show i can be naurally exended o solve he opimal incremenal deploymen (Problem 2). Theorem 1. Finding he opimal deploymen (Problem 1) is NP-Complee. Proof: I is easy o see ha he decision problem of validaing a given opimal deploymen is solvable in polynomial ime. Therefore, finding he opimal deploymen is in NP class. To show his problem is NP-hard, we reduce he dense-k subgraph problem o i; he former is known o be NP-complee [5]. The dense-k subgraph problem is, given a graph (V,E) and a posiive ineger k, find a subse G k V where G k = k, so ha he number of induced edges is minimized, i.e., ((u,v) E) (G k G k ). We expand (V,E) o a nework (V,E ), where V = (u,v) E {u, v, p, q}, E = (u,v) E {(u,v), (u,p), (v,p), (v,q), (q,p)}. And we add a VIP raffic flow = {u,v,p,q} for each (u,v) E. Fig. 3 shows he ransformaion. We nex show ha he opimal deploymen G o where G o = κ = k in (V,E ), is equal o he soluion G k o dense-k problem. If u,v G o, hen L(G o,p s ) = {u,v,p,q}; if u G o,v G o, hen L(G o,p s ) = {u,v,q}; else L(G o,p s ) = {u,p,q} v u v u Figure 3: Transformaion from a graph (shores pah from u o q). Thus only if u,v G o, D(VIP(),L(G o,p s )) =, else D(VIP(),L(G o,p s )) = 4 3 = 1. Obviously, D(VIP(),L(Go,P s )) = E ((u,v) E) (G o G o ). So i is equal o maximize ((u,v) E) (G o G o ). Obviously, G k = G o. Though he opimal deploymen problem is NP-complee, if κ, he number of nodes o be deployed, is a consan, he problem is polynomial-ime solvable even we perform exhausive search. However, if κ is large, a sraigh-forward exhausive search is compuaionally unaccepable. Therefore, whenκis large, we develop a heurisic where we divide κ ino small κ and find he deploymen for each individual κ. This also naurally leads o an algorihm for he opimal incremenal deploymen problem. We firs define passing-hrough propery of each node. Inuiively, v has passing-hrough propery if v is on boh he pah of he VIP raffic flow and is pre-defined VIP pah. Definiion 1. Node v has passing-hrough propery for raffic under deploymen G, if v VIP() L(G,P s ()). Clearly, he more nodes have passing-hrough propery, he smaller he oal disance. Le C(v,P s ()) denoe he passing-hrough propery of v for raffic. We develop Algorihm Passing-Through() o evaluaec(v,p s ()) of all nodes. Inuiively, evaluaion of passing-hrough properies of all nodes needs o check all possible deploymens G, which is exponenial. We develop a novel Algorihm Passing- Through() which does no need o perform an exhaus search in he soluion space. We will use Algorihm Passing- Through() as a subrouine o solve he opimal deploymen problem. Le θ v be an indicaor variable for node v, if v ges deployed, θ v = 1, else θ v =. Our idea is ha we do no need o make an assignmen oθ a he beginning (which will reflec o a specific deploymen). We use his absrac θ and ransfer he problem o a generalized MAX-SAT problem. Our soluion hus does no need o specify he deploymen. We firs use an example in Fig. 2 o explain our idea. For example, node c has (or does no have) passing-hrough propery if and only if {(θ a θ b ) θ a } is equal o one (or zero). We see ha node c has passing-hrough propery in wo condiions: 1) a is no deployed or 2) boh a and b are deployed. In condiion 1), since a is no deployed, he raffic will follow convenional shores pah rouing. In condiion q p
5 2), since a is deployed, a will perform TwoD-IP forwarding and he raffic will flow he VIP pah o node b. Since b is also deployed and will perform TwoD-IP forwarding, he raffic will be forwarded o c. Correspondingly, {(θ a θ b ) θ a } is equal o 1 if 1) θ a = or 2) θ a = 1 and θ b = 1. We hus provide a mapping beween clause saisfacion and our problem. Similarly, we can see ha he passing-hrough propery of node a,b,d,e can be ransformed o clauses 1, {θ a }, {(θ a θ b θ c ) ( θ a θ c )}, {(θ a θ b θ c ) ( θ a θ c ) (θ a θ b θ c ) ( θ a θ c ) (θ a θ b )} respecively. We define s child(v,) as he firs successor node ha is on boh VIP() and he shores pah. For example, in Fig. 2, s child(a, ) = c, indicaing ha c is he firs successor node on VIP( ) = {a,b,c,d,e} and also on he shores pah from a o e. Algorihm Passing-Through() compues he passing-hrough properies of each node as follows. Algorihm 1: Passing-Through(V IP()) Oupu : C(v,P s()), v VIP() 1 begin 2 C(v,Ps()) 1 // v is he source node 3 s child(v,) compue s child(v,) 4 for i = 1 o VIP() 1 do 5 s child(v i,) compue s child(vi,) 6 if v i = s child(vi 1,) hen C(v i,ps()) C(vi 1,P s()) 7 else C(v i,ps()) C(vi 1,P s()) (θ v i 1) 8 for j = o i 2 do 9 if v i = s child(vj,) hen C(vi,Ps()) C(v i,ps()) (C(vj,Ps()) ( θ v j )) The inpu of Algorihm Passing-Through() is a VIP pah V IP(), and he oupu is he passing-hrough properies of each node on V IP(). Basically, Algorihm Passing- Through() follows a dynamic programming srucure. We show an example of Algorihm Passing-Through() using Fig. 2 as he inpu. We show he las round execuion of Algorihm Passing-Through() o compue C(e,P s ( )). As shown in Fig. 2, s child(d, ) = e and d is he predecessor node of e along VIP( ). And node b, c saisfy s child(b, ) = e, s child(c, ) = e. So C(e,P s ( )) = C(d,P s ( )) (C(b,P s ( )) θ b ) (C(c,P s ( )) θ c ). Theorem 2. The complexiy of Algorihm Passing-Through() is O( VIP() 2 ), which is bounded by O( V 2 ). Proof: The loop in line 4 has o run for VIP() 1 imes, and he complexiy of compue s child(v, ) is bounded by O( V IP() ). Thus, he heorem ges proved. We now solve he opimal deploymen problem. Recall he generalized MAX-SAT problem as: given a se U of variables θ i, a collecion of clauses, where each clause is a disjuncion of conjuncion of lierals (e.g., (θ i θ j ) θ j ), find a ruh assignmen such ha he number of saisfied clauses is maximized. We develop our Op-Deploy() following he branch-and-bound algorihm for MAX-SAT [6]. We improve he branch-and-bound algorihm by exploring he search ree in a deph-firs order. A each node, he algorihm compares he number of clauses violaed (unsaisfied wih cerainy) by he bes assignmen (called upper bound ub), wih he number of clauses violaed by he curren assignmen plus an underesimaion. The underesimaion is he number of clauses ha become violaed if we exend he curren parial assignmen ino a complee assignmen. If he curren assignmen plus he underesimaion is greaer han he bes assignmen, he subree of he node is pruned, else he algorihm searches one level deeper ino he ree. If a clause is cerain o be saisfied, i will be removed from he union of clauses (Γ). Iniially, ub is compued by a local random search procedure call GSAT() [7]. When each sep he algorihm searches deeper, a variable in Γ is seleced following J-W rule [8], which gives precedence o variable in shorer clauses. The inpus of Algorihm Op-Deploy() are ub, Γ and κ. The oupus of he Algorihm Op-Deploy() are he opimal deploymen G o and he minimum disance. Algorihm 2: Op-Deploy(ub, Γ, κ) Iniialize : Γ v V IP(),θ C(v,Ps()),ub v 1 GSAT(Γ) Oupu : < G o,ub > 1 begin 2 if Γ = or Γ only conains violaed clauses hen // reurn he number of violaed clauses 3 reurn <, violaed num(γ) > 4 if lower bound(γ) > ub hen reurn <, > 5 u selec variable(γ)// following J-W rule 6 if v V θv < κ hen // se θv o be 1 in Γ 7 < G,ub 1 > Op-Deploy(ub,Γ θ u,κ) 8 if ub 1 ub hen ub ub 1 9 < G,ub 2 > Op-Deploy(ub,Γ θ u,κ) // se θ v o be 1 if ub 2 ub hen ub ub 2, reurn < G,ub > 11 else reurn < G {u},ub > Theorem 3. The complexiy of Algorihm Op-Deploy() is O( ( ) V κ T max VIP() 2 ), which is bounded by O( V κ+2 T ). Proof: The algorihm has o check a mos ( ) V κ cases. Each case has a mos T max VIP() clauses, each clause has a mos max VIP() variables. This complexiy is exponenial. However, we can see ha if κ is consan, he complexiy becomes polynomial and we can perform exhausive search. Bu when κ is large, he compuing ime increases fas wih κ. To reduce compuing ime, we develop a heurisic, which compues Op-Deploy(ub, Γ, κ) by running Op-Deploy(ub, Γ, 1) for κ imes. The complexiy is hen reduced oo( V 3 T κ). Noe ha his heurisic can naurally be used o solve our opimal incremenal deploymen problem. We call i Inc-
6 Deploy() for fuure reference. Nex, we reduce he search space of our problem given a key observaion as follows. Observaion 2. D(VIP(),L(G,P s )) = if and only if for i VIP() 2, θ v i = 1 when s child(v i ) vi+1. Proof: The correcness proof is in Appendix. A. Le K = {v i s child(vi ) vi+1,, i VIP() 2 }, Observaion 2 shows ha we only need o deploy nodes in K o guaranee ha he pahs ha VIP flows are idenical wih pre-defined VIP pahs. We call he nodes in K key nodes. Table III: Algorihm Table Algorihm Problem Definiion Problem Op-Deploy() Opimal Deploymen Problem 1 Inc-Deploy() Opimal Incremenal Deploymen Problem 2 Adp-Forward() Adapive Forwarding Problem 3 IV. ADAPTIVE FORWARDING The deploymen sequence derived from Algorihm Inc- Deploy() is fixed. In pracice, he deploymen may need o be more flexible. Even he deploymen sequence is seled, he nework opology or VIP pahs may change. As such, we need a more adapive deploymen scheme. To address his problem, our idea is o make he deployed rouers adapive in he forwarding operaion, i.e., I s v (P s). More specifically, a deployed rouer may change he TwoD-IP forwarding operaion of VIP flows. Le J(G) = {I s v(p s ()) v G, T }, we call J(G) an adapive forwarding for deploymen G. Our objecive is ha given G, find an adapive forwarding ha minimizes he oal disance beween he pahs of he VIP raffic flows and heir predefined VIP pahs. Formally, e a b c f VIP( ) shores d Figure 4: Adapive forwarding example Problem 3. Adapive Forwarding: Given a deploymen G, find an adapive forwarding J(G) ha minimizes he oal disance D(VIP(),L(G,P s)). We use an example in Fig. 4 o illusrae he definiion. Here we assume a is he source and d is he desinaion. The shores pah from a o d is {a, b, c, d}. Assume here is one VIP flow whose VIP pah is {a,b,e,f,d}. Afer deploying node a, i.e., G = {a}, he disance beween he pah of and he pre-defined VIP pah is D(VIP( ),L(G,P s ( ))) = 5 3 = 2. Wihin adapive forwarding, node a can diver he raffic of o node e, i.e., I s a (P s( )) = e, hen he raffic of flows along{a,e,f,d}, and he disance decreases o be 1. To find he adapive forwarding, we devise a cenralized proocol, ha can change he forwarding operaions of each rouer according o he opology and VIP flow informaion. We also develop a dynamic programming based algorihm, ha compues he adapive forwarding operaions. A. PaFid Overview Unlike in he opimal deploymen scheme, where we can simply deploy, here we need o deploy a new proocol o faciliae he compuing and changing of he forwarding operaions. In his secion, we devise PaFid (Proocol for Adapive Forwarding during Incremenal Deploymen), which is a cenralized proocol ha can collec opology and VIP flow informaion, and reurn he compued resuls o each rouer. PaFid is based on cenralized conrol, because he conroller can easily obain he global opology and VIP flow informaion, and flexibiliy change he forwarding operaions on each rouer. In Fig. 5, we show he informaion flow of PaFid. Wihin PaFid, deployed rouers sends he opology informaion o he conroller, users send VIP flow informaion o he conroller, and he conroller compues he adapive forwarding, hen reurns he forwarding operaions o each rouer. We lis he hree main communicaion procedures of PaFid as following. Topology Informaion: The deployed rouers should noify he conroller of he rouers being deployed. The noificaion should be sen once a rouer is deployed, and sen periodically o mainain a sof sae on he conroller. And one of he deployed rouer should send he global nework opology informaion o he conroller (we assume ha link sae rouing proocol (e.g., OSPF) is used). VIP Flow Informaion: User can subscribe VIP flows o he conroller. The VIP flow informaion includes he rouers sequence ha he flow passes by. The conroller is responsible for VIP flows validaion, including user ideniy validaion and pah validaion, i.e., saisfying [3] o guaranee loop-free. Noe ha users generally refers o he eniies ha se up he VIP flows, rouers hemselves can also be users. Forwarding Operaion informaion: Afer compuaion, he conroller sends back he forwarding operaions o each rouer. And rouers insall he forwarding operaions ino heir forwarding ables.
7 Users Conroller VIP flows Topology Forwarding operaions Deployed Rouers Un-deployed Rouers Proof: The loop in line 2 runs for T imes, he loop in line 5 runs for V imes. The complexiy of he acion (line 8) o find he lowes cos neighbor o reach he desinaion is O( V ). However, for each VIP pah, we can perform a ranking algorihm on all node of V based on heir coss o reach he desinaion. The lowes complexiy of ranking algorihms will be ( V log( V )). Figure 5: Informaion flow of PaFid B. Adapive Forwarding Algorihm Afer collecing he opology and VIP flow informaion, he conroller of PaFid should compue he adapive forwarding. In his secion, we develop a dynamic programming based algorihm Adp-Forward() which is opimal. To be loop-free and failure-oleran, we adop he deflecion rules in [3]. In his paper, due o page limi, we use he simples one hop down rule, i.e., a rouer can diver vip raffic o any neighbor given ha he neighbor is closer o he desinaion. Algorihms using oher rules can be found in [9]. To avoid high srech of VIP pahs, we define ǫ as he maximum srech raio, such ha L(G,Ps) VIP() ǫ. Algorihm 3: Adp-Forward(G, ǫ) Oupu : J 1 begin 2 for T do V IP() 1 3 λ = ǫ VIP(), d = v 4 R = V {d}, f(d,i) = 1, i λ 1 5 while R do 6 Selec u R ha is closes o d 7 if u G hen 8 Find N V, v N if (u,v) E, and v is closer o d 9 f(u,i) = min v N f(v,i 1)+I u VIP(), 1 i λ 1 1 f(u,) = 11 Iv(P s s()) = w, where w N,f(w,i 1) = min v N f(v,i 1) 12 else 13 Find w, he successor of u along shores pah 14 f(u,i) = f(w,i 1)+I u V IP(),1 i λ 1, f(u,) = 15 R = R u 16 reurn J(G) = {Iv s (Ps())}, T,v G The inpu of Adp-Forward() is a deploymen G, i.e., he subse of rouers ha have sen noificaions o he conroller, and he maximum srech raio ǫ. The oupu of Adp- Forward() is he adapive forwarding, i.e., he forwarding operaions for all VIP flows on each deployed rouer. In Algorihm Adp-Forward,I u V IP() is an indicaor funcion, such hai u V IP() = 1 ifu VIP(), else I u V IP() =. Theorem 4. The complexiy of Adp-Forward() is O( V log( V ) T ). V. IMPLEMENTATION We realize he algorihm Inc-Deploy() as an offline sofware ha runs on PC hoss. We also implemen he PaFid on rouers and a PC hos ha acs as he cenralized conroller. On a commercial rouer (BiEngine 12) ha has been equipped wih TwoD-IP, we realize he inerfaces hrough which we can change he forwarding operaions of he rouer. We implemen PaFid, such ha VIP flows informaion is mainained in he conroller, and he deployed rouers will send boh opology and VIP flow informaion o he conroller. We realize he conroller as a module in OpenFlow [1], which can provide cenralized conrol on forwarding operaions of rouers over he nework. Afer collecing he needed informaion, he conroller will send back he forwarding operaions o rouers hrough he predefined inerfaces. A. Simulaion Seup VI. PERFORMANCE EVALUATION We evaluae he performance of our TwoD-IP rouing scheme using boh BRITE [11] generaed opologies and CERNET. A case sudy on CERNET2 is in he nex secion. 1) Topology: We generae opologies wih nodes from 5 o 4. To se up a VIP flow, we firs randomly selec a pair of source-desinaion nodes, and hen randomly selec is VIP pah which 1) is no he shores pah and 2) saisfies he rules in [3] o preven rouing loops. The number of VIP flows is beween 1 and 1. The maximum srech raio of adapive forwarding is se o be 1.5. The defaul values and oher parameers of our evaluaion are in Table IV. Table IV: Parameer Table VIP flows No. Nodes links/new node Mode Rouer Only Model Placemen α / β ǫ Waxman Random.15/ 1.5 We also use he opology of CERNET, which is a medium-scale IPv4 nework wih 11 rouers and 238 links. We compare our algorihm wih random deploymen (RD). We admi ha random deploymen is arificial, and service providers may aemp oher schemes. We hus compare wih human-like deploymen (HD), ha only selecs key nodes o deploy (see Observaion 2). Noe however, HD is based on an observaion wihin he conribuion
8 of our sudy. Besides, we also se full deploymen (FD) as a benchmark for comparison. Our evaluaion meric is he averaged normalized disance (or in shor a-disance hereafer) beween he pahs compued by our algorihms and he pre-defined VIP pahs. Formally, a-disance equals o D(L(G,Ps),VIP()) V IP(). The smaller he a-disance, he beer. If a-disance equals o zero, he performance is idenical o he FD, i.e., he compued pahs are idenical o he predefined VIP pahs. The resuls shown in his secion are averaged by en random and independen experimens. B. Simulaion Resuls 1) Opimal Incremenal Deploymen: Fig. 6(a) shows a ypical incremenal deploymen process and compares differen deploymen algorihms. There are 15 nodes and 3 VIP flows. We deploy hree nodes in every incremenal sep. In Fig. 6(a), we see ha even we do no deploy any rouer, he a-disance is sill around 5%. This is because he shores pah can ravel hrough a few VIP nodes already. When we deploy more nodes, he a-disance decreases. However, Algorihm Inc-Deploy() performs beer han RD and HD. For example, afer we deploy 33 nodes, he nodes chosen by Algorihm Inc-Deploy() mach he nodes on he VIP pahs very well, and he a-disance is only 2.2%. On he conrary, if we randomly choose 36 nodes o deploy, he a-disance is 39.8%, if randomly choose 36 key nodes o deploy, he a-disance is 17.82%. When we look ino he deails of he simulaion race, we see ha here are only 4 nodes ha do no mach he VIP nodes using Algorihm Inc-Deploy(), while here are 68 VIP nodes no covered using RD, 31 VIP nodes no covered by HD. We emphasize again ha he essence of incremenal deploymen is o demonsrae he benefis of TwoD-IP rouing when deploying as few nodes as possible. Clearly, our algorihm achieves his. In Fig. 6(a), we see ha for he pahs compued by RD, he a-disance o he VIP pahs can even increase afer more nodes are deployed. For example, when 36 nodes are deployed, he a-disance is 36.78%. Afer we deploy anoher 3 nodes, he a-disance increases o 37.36%. On he conrary, we see in Fig. 6(a), his never happens o Inc-Deploy(). We also evaluae adapive forwarding Adp- Forward() in Fig. 6(a). We see ha is impac is quie small. Boh HD and Inc-Deploy() will achieve opimal performance afer deploying all key nodes, however, he a-disance of Inc- Deploy() decreases much faser han HD. Fig. 6(b) shows he impac of he incremenal sep size. We compare he performance for four sep sizes, 1, 2, 5, 1 (i.e., 1, 2, 5, 1 nodes are deployed in each incremenal sep). We see ha here is no much difference beween differen sep sizes. Therefore, our heurisic algorihm, using small sep size o reduce he compuaional complexiy, is saisfacory. In Fig. 7, we sudy he impac of he nework size. We see ha for Inc-Deploy() and HD, he a-disance decreases when he nework size increases. For RD, he a-disance increases when he nework size increases. This is because when he nework is larger, he number of nodes ha belong o VIP pahs increases slower han he oal number of nodes. Since Inc-Deploy(), and HD always choose from his se of nodes, he performance improves. On he conrary, RD selecs randomly from all nodes, making is performance decrease. In Fig. 7, we also compare differen deploy algorihms wihin wo differen deploymen raios, 1%, 2% (i.e., 1%, and 2% of all nodes are deployed). Clearly, he more nodes deployed, he shorer he a-disance. And by deploying 1% more nodes wihin RD, he improvemen (i.e., he gap beween 1% and 2% deploymen raio) is smaller han Inc-Deploy() and HD. Alhough he a-disance boh Inc- Deploy() and HD decrease wih nework size, he a-disance of Inc-Deploy() drops more quickly o be zero, especially when deploymen raio is low. The resul indicaes ha beer performance can be achieved by deployed carefully seleced nodes based on our algorihm, especially a he iniial sage of incremenal deploymen. In Fig. 8, we sudy he impac of he number of VIP raffic flows. In pracice, when he number of VIP raffic flows increases, we will also deploy more nodes o be TwoD- IP capable. Thus, we se an increasing raio x beween he number of VIP flows and he nodes deployed, i.e., every x addiional nodes will be deployed when here is one addiional VIP raffic flow. We compare differen deploy algorihms wihin wo differen raios 1 and. We see ha he a-disance decreases when he number of VIP flows increases for all algorihms. This shows ha deploying more nodes has higher posiive impac. RD performs he wors, even he increasing raio of RD is 1, is performance is sill worse han Inc-Deploy() wih increasing raio of. When he raio is high, he a-disance of HD is quie small. However, when he raio is low, he a-disance of HD is almos as worse as RD. 2) Adapive Forwarding: We use Inc-Adp(), RD-Adp and HD-Adp o denoe adapive forwarding running on nodes seleced by Inc-Deploy(), RD and HD. Fig. 9 shows he impacs of adapive forwarding on a random deploymen process (RD or HD) ha does no follow he opimal incremenal deploymen. We deploy hree nodes in every incremenal sep. We see ha adapive forwarding improves boh RD and HD. For example, if we randomly choose 9 nodes o deploy, he a-disance is 34.71%, however, he a-disance decreases o be 27.65% if we use adapive forwarding beween hese 9 nodes; if we randomly choose 12 key nodes o deploy, he a-disance is 28.49%, and he a-disance decreases o be 22.93% if adapive forwarding is used. In he exreme case, adapive forwarding improves RD by over 7% maximally, while improves HD by 5.5% maximally. This is because RD will choose non-key nodes, which can also ac as relay nodes o furher decrease he a-disance.
9 a disance RD HD Inc Deploy Inc Adp Number of Deployed Nodes (a) Comparison of differen deploymen algorihms a disance Sep Size:1.1 Sep Size:2 Sep Size:5 Sep Size: Number of Deployed Nodes (b) Impac of sep size Figure 6: a-disance as a funcion of number of deployed nodes RD HD a disance RD:1% RD:2% HD:1% HD:2% Inc UDeploy:1% Inc UDeploy:2% Nework Size Figure 7: a-disance as a funcion of nework size a disance Inc UDeploy: Inc UDeploy:1 RD: RD:1 HD: HD:1 a disance RD HD RD Adp HD Adp a disance Inc Deploy Inc Adp Nework Size Figure 8: a-disance as a funcion of number of VIP flows Number of Deployed Nodes Figure 9: a-disance as a funcion of number of deployed nodes Number of changed VIP flows Figure 1: a-disance as a funcion number of vip flows a disance Inc Deploy Inc Adp Number of changed nodes Figure 11: a-disance as a funcion of number of changed nodes a disance a disance RD Adp(6 deployed nodes) Maximum srech raio 8 HD Adp(15 deployed nodes) Maximum srech raio Figure 12: a-disance as a funcion of he maximum srech raio In Fig. 1, we sudy he benefis of adapive forwarding when VIP flows change. Afer seing up 3 VIP flows and choosing 3 nodes o deploy according o Inc-Deploy(), we generae 1-7 new VIP flows. We see ha when he number of VIP flow increases, he a-disance will increase. The more he new VIP flows join in, he larger he a-disance. However, wih adapive forwarding, he a-disance increases slower, i.e., he gap beween Inc-Deploy() and Inc-Adp() becomes larger when more VIP flows generaed. This is because adapive forwarding can regulae he VIP flows ha are away from he righ VIP pahs. In Fig. 11, we sudy he benefis of adapive forwarding when opology changes. Afer deploying 3 nodes, we randomly revoke 5-1 exised or add 5-3 new nodes 1. The a-disance will increase when more nodes are added. This is because when new nodes are added, he forwarding acion (e.g., he nex hop on he shores pah) of each node may change. Thus he a-disance will increases because he deployed nodes are compued based on he original opology. Wih adapive forwarding, he a-disance increases slower. The resul is similar wih Fig. 1, indicaing ha hrough adapive forwarding, we can achieve subsanial benefis when VIP flows or nework opology change. In Fig. 12, we sudy he impac of he maximum srech raio on adapive forwarding. We se maximum srech raio o be when randomly deploying 6 nodes or 15 key 1 he influenced VIP flows will be regeneraed
10 nodes. Fig. 12 shows ha he a-disance increases when he maximum srech raio increases from 1. o 1.2. However, he a-disance remain almos he same when he maximum srech raio is larger han 1.2. This is because adapive forwarding only slighly srech he pah, by a mos 2%. 3) Simulaion Resuls on CERNET: We furher validae our resuls using CERNET. Due o page limi, we only evaluae opimal incremenal deploymen algorihms. Fig. 13(a) shows an opimal incremenal deploymen process by deploying wo nodes a each sep. We see ha he a- disance is 26.7% even we do no deploy any rouer, his is because of he low conneciviy of CERNET opology. When we deploy more nodes, he a-disance decreases and Inc-Deploy() performs much beer han RD and HD. Afer deploying 8 nodes, he a-disance of Inc-Deploy() is 1.78%, he a-disance of RD is sill 22.49%, and he a-disance of HD is 5.92%. Fig. 13(b) shows he impac of he number of VIP flows. Here, we se he increasing raio o be.1 and.5, i.e., deploying.1 and.5 nodes afer adding a VIP flow. In Fig. 13(b), a-disance decreases wih he number of VIP flows. Inc-Deploy() decreases faser and performs he bes. HD achieves nearly opimal resul when he raio is high, bu much worse when he raio is low. VII. TWOD-IP ROUTING FOR CERNET2: A CASE Chengdu 1Gbps 2.5Gbps Zhengzhou Lanzhou Chongqing Beijing Wuhan CNGI-6IX Guangzhou Tianjin STUDY Shenyang Chuangchun Hefei Changsha Jinan Xiamen Najing Dalian Figure 15: CERNET2 opology FOREIGN INTERNET Haerbin CNGI-SHIX Hangzhou Shanghai We conduc a case sudy wih he real opology and prefix informaion of CERNET2. Our work also serves as a reference for he fuure deploymen of TwoD-IP rouing on CERNET2. We wan o move he ou-going Inernaional raffic of hree universiies, i.e., THU (in Beijing, wih 38 prefixes), HUST (in Wuhan, wih 18 prefixes) and SCUT (in Guangzhou, wih 28 prefixes) o CNGI- SHIX (Shanghai poral). There will be hree VIP pahs, VIP( ) ={Beijing, Tianjin, Jinan, Hefei, Nanjing, Shanghai}, VIP( 1 ) ={Wuhan, Nanjing, Shanghai} and VIP( 2 ) ={Guangzhou, Xiamen, Hangzhou, Shanghai}. In he CERNET2 scenario, we apply he weighed version of our problems and each VIP raffic flow is assigned a weigh ha is proporional o he raffic volume. In our case, we se he weighs o w = 19.6,w 1 = 5.1,w 2 = 11. (for deails of he weigh assignmen, please refer o [9]). Fig. 14(a) shows he opimal incremenal deploymen process, where we deploy nodes one by one. We compare Inc-Deploy() and HD algorihm (here nodes are randomly seleced from he VIP pahs, he candidae node se includes Beijing, Tianjin, Jinan, Hefei, Nanjing, Shanghai, Wuhan, Guangzhou, Xiamen, Hangzhou). For Inc-Deploy(), he deploymen sequence we sugges is Guangzhou, Wuhan, Jinan, Tianjin and Beijing. We see ha afer deploying he rouer of Guangzhou (occupies 3.8% of he oal raffic), he a- disance falls from 1% o 69.2%. For HD o achieve similar performance, we need o deploy rouers a five ciies. VIII. RELATED WORK There is lile work on wo dimensional rouing since IP rouing won over circui based rouing such as PNNI [12]. Because of he imporan semanic in source address, recen years see more research on giving sources conrol. IP (loose/sric) source rouing [13] allows he sender o ake full conrol of he rouing pah. However, due o securiy reason [14], source rouing is disabled in mos neworks. In addiion, source rouing is inefficien because of he addiional IP opion header, and i hands mos conrol o he end users, which is unfavorable for ISP operaors. MPLS [15] is ofen used o manage raffic per-flow. However, due o he conrol and managemen overheads, MPLS raises concern for scaling when he number of label swiching pahs (LSPs) increases [16]. The more he LSPs, he heavier he sysem burden [17]. MPLS only suppors limied number of LSPs (one Cisco moderae rouer suppors 6 LSPs, according o daa in 25 [18]). There are many oher rouing schemes ha have been inegraed wih source address lookup. Such as Policy based rouing (PBR) [19], Cusomer-specific rouing [2], Muliopology rouing [21], and even overlay rouing [22], which is beyond he nework layer. However, for an ISP, a ligh weigh, pure IP-based, more nework conrollable soluion is favored. Due o securiy and accouning problems, CERNET2 has deployed SAVI o validae he source address of each packe a he edge poins of he nework. Currenly, SAVI has been insalled by more han 1 universiy campus nework. Confirmed SAVI users are more han 9, [23]. CERNET2 hen decides o make full use of source address for beer reliabiliy, securiy and raffic disribuion by inegraing he source address lookup ino IP rouing. Incremenal design is advocaed [24] for nework layer proposals. Many proocols and new algorihms can be in-
11 a disance RD HD Inc UDeploy Inc Adp Number of Deployed Nodes (a) a-disance as a funcion of number of deployed nodes on CERNET a disance Figure 13: Simulaion on CERNET Inc UDeploy:.1 Inc UDeploy:.5 RD:.1 RD:.5 HD:.1 HD: Nework Size (b) a-disance as a funcion of number of VIP flows on CERNET a disance Wuhan.4 Guangzhou Jinan Tianjin HD Inc UDeploy Beijing Number of Deployed Nodes (a) a-disance as a funcion of number of deployed nodes on CERNET2 Figure 14: Simulaion on CERNET2 cremenally deployed [3][25][26]. Our problem is specific and unique o TwoD-IP rouing. Thus a design from scrach is needed. IX. CONCLUSION AND FUTURE WORK In his paper, we presened a sudy of TwoD-IP rouing where he forwarding decisions is no only based on he desinaion IP addresses bu also on he source IP addresses. Our focus is on incremenal deploymen requiremen, a pracical concern of CERNET2. We formulaed our problem such ha we need o find a deploymen sequence given he number of deployed nodes. We proved he problem o be NP-complee. We hen novelly ransformed our problem o boolean clauses and developed an efficien algorihm following he principles of branch-and-bound algorihm for MAX-SAT. We evaluaed our algorihms comprehensively using CER- NET and oher opologies. We showed ha by deploying a few nodes suggesed by our deploymen sequence can successfully manage he raffic flows, and adapive forwarding mechanism can flexibiliy manage he raffic flows when opology or VIP flows change. We hen presened a case sudy on CERNET2 and provided a fine deploymen sequence. Based on our specific consideraion, we use hamming meric o represen he deviaion beween pahs. While here are oher meaningful meric in graph heory, our nex work includes rying differen merics for oher consideraions. We asserively use summaion of individual pah disance o express he oal deviaion, validaion REFERENCES [1] J. Wu, J. Bi, M. Bagnulo, F. Baker, and C. Vog, Source address validaion improvemen framework, Inerne Draf, Mar 211, draf-ief-savi-framework-4.x. [2] M. Xu, J. Wu, S. Yang, and D. Wang, Two dimensional ip rouing archiecure, Inerne Draf, Mar 212, draf-xurgwg-wod-ip-rouing-.x. [3] X. Yang and D. Weherall, Source selecable pah diversiy via rouing deflecions, in Proc. ACM SIGCOMM 6, New York, NY, Sep 26. [4] L. Trevisan, When hamming mees euclid: he approximabiliy of geomeric sp and ms, in Proc. ACM STOC 97, El Paso, TE, May [5] U. Feige, G. Korsarz, and D. Peleg, The dense k-subgraph problem, Algorihmica, vol. 29, pp , 21. [6] T. Alsine, F. Manya, and J. Planes, Improved branch and bound algorihms for max-sa, in Proc. Theory and Applicaions of Saisfiabiliy Tesing (SAT 3), Porofino, Ialy, May 23. [7] B. Selman, H. Levesque, and D. Michell, A new mehod for solving hard saisfiabiliy problems, in Proc. of he enh naional conference on Arificial inelligence (AAAI 92), San Jose, CA, July [8] J. Hooker and V. Vinay, Branching rules for saisfiabiliy, Journal of Auomaed Reasoning, vol. 15, pp , [9] S. Yang, D. Wang, M. Xu, and J. Wu, Efficien wo dimensional-ip rouing: An incremenal deploymen design, Tsinghua Universiy, Tech. Rep., July 211. [Online]. Available: hp:// [1] N. McKeown, T. Anderson, H. Balakrishnan, G. Parulkar, L. Peerson, J. Rexford, S. Shenker, and J. Turner, Openflow: enabling innovaion in campus neworks, SIGCOMM Compu. Commun. Rev., vol. 38, no. 2, pp , Mar 28. [11] Brie: Boson universiy represenaive inerne opology generaor, hp:// [12] Privae Nework-Nework Inerface Specificaion v1.(pnni), ATM Forum Technical Commiee, Mar [13] D. Esrin, T. Li, Y. Rekher, K. Varadhan, and D. Zappala, Source Demand Rouing: Packe Forma and Forwarding Specificaion (Version 1), RFC 194 (Informaional), Inerne Engineering Task Force, May [14] C. Perkins, IP Encapsulaion wihin IP, RFC 23 (Sandards Track), Inerne Engineering Task Force, Oc [15] E. Rosen, A. Viswanahan, and R. Callon, Muliproocol Label Swiching Archiecure, RFC 331 (Sandards Track), Inerne Engineering Task Force, Jan. 21. [16] S. Yasukawa, A. Farrel, and O. Komolafe, An Analysis of Scaling Issues in MPLS-TE Core Neworks, RFC 5439 (Informaional), Inerne Engineering Task Force, Feb. 29. [17] C. Mez, C. Barh, and C. Filsfils, Beyond mpls... less is more, Inerne Compuing, IEEE, vol. 11, no. 5, pp , Sep 27.
12 [18] S. Kandula, D. Kaabi, B. Davie, and A. Charny, Walking he ighrope: responsive ye sable raffic engineering, in Proc. ACM SIGCOMM 5, Philadelphia, Pennsylvania, USA, Aug 25. [19] Policy-Based Rouing (whie paper), Cisco, [2] J. Fu and J. Rexford, Efficien ip-address lookup wih a shared forwarding able for muliple virual rouers, in Proc. ACM CoNEXT 8, Madrid, Spain, Dec 28. [21] N. Wang, K.-H. Ho, and G. Pavlou, Adapive muli-opology igp based raffic engineering wih near-opimal nework performance, in Proc. IFIP-TC6 NETWORKING 8, Singapore, May 28. [22] D. Andersen, H. Balakrishnan, F. Kaashoek, and R. Morris, Resilien Overlay Neworks, in Proc. ACM SOSP 1, Banff, Canada, Ocober 21. [23] Cngi-cerne2 savi deploymen updae, hp:// /8/slides/savi-2.pdf, CERNET, March 211. [24] N. M. K. Chowdhury and R. Bouaba, A survey of nework virualizaion, Compuer Neworks, vol. 54, pp , April 21. [25] Q.Li, D.Wang, M.Xu, and J.Yang, On he scalabiliy of rouer forwarding ables: Nexhop selecable fib aggregaion, in Proc. IEEE INFOCOM 11, mini-conference, Shanghai, China, Apr 211. [26] K. Ramakrishnan, S. Floyd, and D. Black, The Addiion of Explici Congesion Noificaion (ECN) o IP, RFC 3168 (Sandards Track), Inerne Engineering Task Force, Sep. 21. A. Proof for Observaion 2 APPENDIX Proof: fff I s easy o prove ha i is a sufficien condiion. Wih precondiion ha C(v,P s ()) is 1, suppose ha for all j < k, C(v j,p s()) are 1. Then if s child(v k 1,P s ()) = v k, C(v,P k s ()) mus be 1, else according o Observaion 2 we have θ v k 1 = 1, hus C(v k,p s()) is 1. So we can conclude ha all clauses C(v,P s ()) are 1. Then we prove ha he condiion is necessary. According o Algorihm 1, if s child(v,p j s ()) v j+1 here mus exis k < j such ha s child(v k 1. Indica- (s child(v k,p s ()) v k+1 ) and θ k v ing here mus be k 1 < k such ha s child(v k1 v j+1 1, and θ v j,p s()) =,P s ()) v k1+1 and θ k v 1 1. Thus here is a ineger sequence k > k 1 > k 2... unil k l = (l > ), obviously, if s child(v,p s ()) v 1, θ v mus equal o 1 (else C(v 1,P s()) will be ). Thus he assumpion is false.
COSC 3213: Computer Networks I Chapter 6 Handout # 7
 COSC 3213: Compuer Neworks I Chaper 6 Handou # 7 Insrucor: Dr. Marvin Mandelbaum Deparmen of Compuer Science York Universiy F05 Secion A Medium Access Conrol (MAC) Topics: 1. Muliple Access Communicaions:
COSC 3213: Compuer Neworks I Chaper 6 Handou # 7 Insrucor: Dr. Marvin Mandelbaum Deparmen of Compuer Science York Universiy F05 Secion A Medium Access Conrol (MAC) Topics: 1. Muliple Access Communicaions:
Shortest Path Algorithms. Lecture I: Shortest Path Algorithms. Example. Graphs and Matrices. Setting: Dr Kieran T. Herley.
 Shores Pah Algorihms Background Seing: Lecure I: Shores Pah Algorihms Dr Kieran T. Herle Deparmen of Compuer Science Universi College Cork Ocober 201 direced graph, real edge weighs Le he lengh of a pah
Shores Pah Algorihms Background Seing: Lecure I: Shores Pah Algorihms Dr Kieran T. Herle Deparmen of Compuer Science Universi College Cork Ocober 201 direced graph, real edge weighs Le he lengh of a pah
Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 6.0 Version
 Tes - Accredied Configuraion Engineer (ACE) Exam - PAN-OS 6.0 Version ACE Exam Quesion 1 of 50. Which of he following saemens is NOT abou Palo Alo Neworks firewalls? Sysem defauls may be resored by performing
Tes - Accredied Configuraion Engineer (ACE) Exam - PAN-OS 6.0 Version ACE Exam Quesion 1 of 50. Which of he following saemens is NOT abou Palo Alo Neworks firewalls? Sysem defauls may be resored by performing
Implementing Ray Casting in Tetrahedral Meshes with Programmable Graphics Hardware (Technical Report)
 Implemening Ray Casing in Terahedral Meshes wih Programmable Graphics Hardware (Technical Repor) Marin Kraus, Thomas Erl March 28, 2002 1 Inroducion Alhough cell-projecion, e.g., [3, 2], and resampling,
Implemening Ray Casing in Terahedral Meshes wih Programmable Graphics Hardware (Technical Repor) Marin Kraus, Thomas Erl March 28, 2002 1 Inroducion Alhough cell-projecion, e.g., [3, 2], and resampling,
Computational Geometry in Wireless Networks - Routing. Presented by Heather M. Michaud
 Compaional Geomery in Wireless Neworks - Roing Presened by Heaher M. Michad 1 Ad Hoc Wireless Neworks No fixed pre-exising infrasrcre Nodes can be saic or mobile Assme nodes don move dring roing or opology
Compaional Geomery in Wireless Neworks - Roing Presened by Heaher M. Michad 1 Ad Hoc Wireless Neworks No fixed pre-exising infrasrcre Nodes can be saic or mobile Assme nodes don move dring roing or opology
Coded Caching with Multiple File Requests
 Coded Caching wih Muliple File Requess Yi-Peng Wei Sennur Ulukus Deparmen of Elecrical and Compuer Engineering Universiy of Maryland College Park, MD 20742 ypwei@umd.edu ulukus@umd.edu Absrac We sudy a
Coded Caching wih Muliple File Requess Yi-Peng Wei Sennur Ulukus Deparmen of Elecrical and Compuer Engineering Universiy of Maryland College Park, MD 20742 ypwei@umd.edu ulukus@umd.edu Absrac We sudy a
Chapter 8 LOCATION SERVICES
 Disribued Compuing Group Chaper 8 LOCATION SERVICES Mobile Compuing Winer 2005 / 2006 Overview Mobile IP Moivaion Daa ransfer Encapsulaion Locaion Services & Rouing Classificaion of locaion services Home
Disribued Compuing Group Chaper 8 LOCATION SERVICES Mobile Compuing Winer 2005 / 2006 Overview Mobile IP Moivaion Daa ransfer Encapsulaion Locaion Services & Rouing Classificaion of locaion services Home
A Matching Algorithm for Content-Based Image Retrieval
 A Maching Algorihm for Conen-Based Image Rerieval Sue J. Cho Deparmen of Compuer Science Seoul Naional Universiy Seoul, Korea Absrac Conen-based image rerieval sysem rerieves an image from a daabase using
A Maching Algorihm for Conen-Based Image Rerieval Sue J. Cho Deparmen of Compuer Science Seoul Naional Universiy Seoul, Korea Absrac Conen-based image rerieval sysem rerieves an image from a daabase using
STEREO PLANE MATCHING TECHNIQUE
 STEREO PLANE MATCHING TECHNIQUE Commission III KEY WORDS: Sereo Maching, Surface Modeling, Projecive Transformaion, Homography ABSTRACT: This paper presens a new ype of sereo maching algorihm called Sereo
STEREO PLANE MATCHING TECHNIQUE Commission III KEY WORDS: Sereo Maching, Surface Modeling, Projecive Transformaion, Homography ABSTRACT: This paper presens a new ype of sereo maching algorihm called Sereo
Simple Network Management Based on PHP and SNMP
 Simple Nework Managemen Based on PHP and SNMP Krasimir Trichkov, Elisavea Trichkova bsrac: This paper aims o presen simple mehod for nework managemen based on SNMP - managemen of Cisco rouer. The paper
Simple Nework Managemen Based on PHP and SNMP Krasimir Trichkov, Elisavea Trichkova bsrac: This paper aims o presen simple mehod for nework managemen based on SNMP - managemen of Cisco rouer. The paper
Network management and QoS provisioning - QoS in Frame Relay. . packet switching with virtual circuit service (virtual circuits are bidirectional);
 QoS in Frame Relay Frame relay characerisics are:. packe swiching wih virual circui service (virual circuis are bidirecional);. labels are called DLCI (Daa Link Connecion Idenifier);. for connecion is
QoS in Frame Relay Frame relay characerisics are:. packe swiching wih virual circui service (virual circuis are bidirecional);. labels are called DLCI (Daa Link Connecion Idenifier);. for connecion is
Assignment 2. Due Monday Feb. 12, 10:00pm.
 Faculy of rs and Science Universiy of Torono CSC 358 - Inroducion o Compuer Neworks, Winer 218, LEC11 ssignmen 2 Due Monday Feb. 12, 1:pm. 1 Quesion 1 (2 Poins): Go-ack n RQ In his quesion, we review how
Faculy of rs and Science Universiy of Torono CSC 358 - Inroducion o Compuer Neworks, Winer 218, LEC11 ssignmen 2 Due Monday Feb. 12, 1:pm. 1 Quesion 1 (2 Poins): Go-ack n RQ In his quesion, we review how
Optimal Crane Scheduling
 Opimal Crane Scheduling Samid Hoda, John Hooker Laife Genc Kaya, Ben Peerson Carnegie Mellon Universiy Iiro Harjunkoski ABB Corporae Research EWO - 13 November 2007 1/16 Problem Track-mouned cranes move
Opimal Crane Scheduling Samid Hoda, John Hooker Laife Genc Kaya, Ben Peerson Carnegie Mellon Universiy Iiro Harjunkoski ABB Corporae Research EWO - 13 November 2007 1/16 Problem Track-mouned cranes move
Lecture 18: Mix net Voting Systems
 6.897: Advanced Topics in Crypography Apr 9, 2004 Lecure 18: Mix ne Voing Sysems Scribed by: Yael Tauman Kalai 1 Inroducion In he previous lecure, we defined he noion of an elecronic voing sysem, and specified
6.897: Advanced Topics in Crypography Apr 9, 2004 Lecure 18: Mix ne Voing Sysems Scribed by: Yael Tauman Kalai 1 Inroducion In he previous lecure, we defined he noion of an elecronic voing sysem, and specified
A time-space consistency solution for hardware-in-the-loop simulation system
 Inernaional Conference on Advanced Elecronic Science and Technology (AEST 206) A ime-space consisency soluion for hardware-in-he-loop simulaion sysem Zexin Jiang a Elecric Power Research Insiue of Guangdong
Inernaional Conference on Advanced Elecronic Science and Technology (AEST 206) A ime-space consisency soluion for hardware-in-he-loop simulaion sysem Zexin Jiang a Elecric Power Research Insiue of Guangdong
Automatic Calculation of Coverage Profiles for Coverage-based Testing
 Auomaic Calculaion of Coverage Profiles for Coverage-based Tesing Raimund Kirner 1 and Waler Haas 1 Vienna Universiy of Technology, Insiue of Compuer Engineering, Vienna, Ausria, raimund@vmars.uwien.ac.a
Auomaic Calculaion of Coverage Profiles for Coverage-based Tesing Raimund Kirner 1 and Waler Haas 1 Vienna Universiy of Technology, Insiue of Compuer Engineering, Vienna, Ausria, raimund@vmars.uwien.ac.a
Y. Tsiatouhas. VLSI Systems and Computer Architecture Lab
 CMOS INEGRAED CIRCUI DESIGN ECHNIQUES Universiy of Ioannina Clocking Schemes Dep. of Compuer Science and Engineering Y. siaouhas CMOS Inegraed Circui Design echniques Overview 1. Jier Skew hroughpu Laency
CMOS INEGRAED CIRCUI DESIGN ECHNIQUES Universiy of Ioannina Clocking Schemes Dep. of Compuer Science and Engineering Y. siaouhas CMOS Inegraed Circui Design echniques Overview 1. Jier Skew hroughpu Laency
4 Error Control. 4.1 Issues with Reliable Protocols
 4 Error Conrol Jus abou all communicaion sysems aemp o ensure ha he daa ges o he oher end of he link wihou errors. Since i s impossible o build an error-free physical layer (alhough some shor links can
4 Error Conrol Jus abou all communicaion sysems aemp o ensure ha he daa ges o he oher end of he link wihou errors. Since i s impossible o build an error-free physical layer (alhough some shor links can
Scheduling. Scheduling. EDA421/DIT171 - Parallel and Distributed Real-Time Systems, Chalmers/GU, 2011/2012 Lecture #4 Updated March 16, 2012
 EDA421/DIT171 - Parallel and Disribued Real-Time Sysems, Chalmers/GU, 2011/2012 Lecure #4 Updaed March 16, 2012 Aemps o mee applicaion consrains should be done in a proacive way hrough scheduling. Schedule
EDA421/DIT171 - Parallel and Disribued Real-Time Sysems, Chalmers/GU, 2011/2012 Lecure #4 Updaed March 16, 2012 Aemps o mee applicaion consrains should be done in a proacive way hrough scheduling. Schedule
ECO-friendly Distributed Routing Protocol for Reducing Network Energy Consumption
 ECO-friendly Disribued Rouing Proocol for Reducing Nework Energy Consumpion Daisuke Arai and Kiyohio Yoshihara KDDI R&D Laboraories Inc. 2-1-15 Ohara Fujimino-shi Saiama, Japan Email: {di-arai, yosshy}@kddilabs.jp
ECO-friendly Disribued Rouing Proocol for Reducing Nework Energy Consumpion Daisuke Arai and Kiyohio Yoshihara KDDI R&D Laboraories Inc. 2-1-15 Ohara Fujimino-shi Saiama, Japan Email: {di-arai, yosshy}@kddilabs.jp
Quantitative macro models feature an infinite number of periods A more realistic (?) view of time
 INFINIE-HORIZON CONSUMPION-SAVINGS MODEL SEPEMBER, Inroducion BASICS Quaniaive macro models feaure an infinie number of periods A more realisic (?) view of ime Infinie number of periods A meaphor for many
INFINIE-HORIZON CONSUMPION-SAVINGS MODEL SEPEMBER, Inroducion BASICS Quaniaive macro models feaure an infinie number of periods A more realisic (?) view of ime Infinie number of periods A meaphor for many
Image segmentation. Motivation. Objective. Definitions. A classification of segmentation techniques. Assumptions for thresholding
 Moivaion Image segmenaion Which pixels belong o he same objec in an image/video sequence? (spaial segmenaion) Which frames belong o he same video sho? (emporal segmenaion) Which frames belong o he same
Moivaion Image segmenaion Which pixels belong o he same objec in an image/video sequence? (spaial segmenaion) Which frames belong o he same video sho? (emporal segmenaion) Which frames belong o he same
Less Pessimistic Worst-Case Delay Analysis for Packet-Switched Networks
 Less Pessimisic Wors-Case Delay Analysis for Packe-Swiched Neworks Maias Wecksén Cenre for Research on Embedded Sysems P O Box 823 SE-31 18 Halmsad maias.wecksen@hh.se Magnus Jonsson Cenre for Research
Less Pessimisic Wors-Case Delay Analysis for Packe-Swiched Neworks Maias Wecksén Cenre for Research on Embedded Sysems P O Box 823 SE-31 18 Halmsad maias.wecksen@hh.se Magnus Jonsson Cenre for Research
A Scheme to Reduce Packet Loss during PMIPv6 Handover considering Authentication
 Inernaional Conference on Compuaional Sciences and Is Applicaions ICCSA 2008 A Scheme o Reduce Loss during P Handover considering Auhenicaion Seonggeun Ryu, Gye-Young Kim, Byunggi Kim, and Youngsong Mun
Inernaional Conference on Compuaional Sciences and Is Applicaions ICCSA 2008 A Scheme o Reduce Loss during P Handover considering Auhenicaion Seonggeun Ryu, Gye-Young Kim, Byunggi Kim, and Youngsong Mun
Sam knows that his MP3 player has 40% of its battery life left and that the battery charges by an additional 12 percentage points every 15 minutes.
 8.F Baery Charging Task Sam wans o ake his MP3 player and his video game player on a car rip. An hour before hey plan o leave, he realized ha he forgo o charge he baeries las nigh. A ha poin, he plugged
8.F Baery Charging Task Sam wans o ake his MP3 player and his video game player on a car rip. An hour before hey plan o leave, he realized ha he forgo o charge he baeries las nigh. A ha poin, he plugged
Mobility Chapter 13. More Car Network Ideas. Rating. Overview. Mobile IP Internet. First steps Text book. GSM Network. No apps Mission critical
 More Car Nework Ideas Mobiliy Chaper 13 CAR2CAR Consorium: Audi, BMW, Daimler, Fia, GM, Honda, Renaul, VW 13/1 Raing Overview Area mauriy Firs seps Tex book Pracical imporance No apps Mission criical Mobile
More Car Nework Ideas Mobiliy Chaper 13 CAR2CAR Consorium: Audi, BMW, Daimler, Fia, GM, Honda, Renaul, VW 13/1 Raing Overview Area mauriy Firs seps Tex book Pracical imporance No apps Mission criical Mobile
SREM: A Novel Multicast Routing Algorithm - Comprehensive Cost Analysis
 REM: A Novel Mulicas Rouing Algorihm - Comprehensive Cos Analysis Yewen Cao and Khalid Al-Begain chool of Compuing, Universiy of Glamorgan, CF37 DL, Wales, U.K E-mail:{ycao,kbegain}@glam.ac.uk Absrac Ever-increasing
REM: A Novel Mulicas Rouing Algorihm - Comprehensive Cos Analysis Yewen Cao and Khalid Al-Begain chool of Compuing, Universiy of Glamorgan, CF37 DL, Wales, U.K E-mail:{ycao,kbegain}@glam.ac.uk Absrac Ever-increasing
An Adaptive Spatial Depth Filter for 3D Rendering IP
 JOURNAL OF SEMICONDUCTOR TECHNOLOGY AND SCIENCE, VOL.3, NO. 4, DECEMBER, 23 175 An Adapive Spaial Deph Filer for 3D Rendering IP Chang-Hyo Yu and Lee-Sup Kim Absrac In his paper, we presen a new mehod
JOURNAL OF SEMICONDUCTOR TECHNOLOGY AND SCIENCE, VOL.3, NO. 4, DECEMBER, 23 175 An Adapive Spaial Deph Filer for 3D Rendering IP Chang-Hyo Yu and Lee-Sup Kim Absrac In his paper, we presen a new mehod
NEWTON S SECOND LAW OF MOTION
 Course and Secion Dae Names NEWTON S SECOND LAW OF MOTION The acceleraion of an objec is defined as he rae of change of elociy. If he elociy changes by an amoun in a ime, hen he aerage acceleraion during
Course and Secion Dae Names NEWTON S SECOND LAW OF MOTION The acceleraion of an objec is defined as he rae of change of elociy. If he elociy changes by an amoun in a ime, hen he aerage acceleraion during
Restorable Dynamic Quality of Service Routing
 QOS ROUTING Resorable Dynamic Qualiy of Service Rouing Murali Kodialam and T. V. Lakshman, Lucen Technologies ABSTRACT The focus of qualiy-of-service rouing has been on he rouing of a single pah saisfying
QOS ROUTING Resorable Dynamic Qualiy of Service Rouing Murali Kodialam and T. V. Lakshman, Lucen Technologies ABSTRACT The focus of qualiy-of-service rouing has been on he rouing of a single pah saisfying
An Improved Square-Root Nyquist Shaping Filter
 An Improved Square-Roo Nyquis Shaping Filer fred harris San Diego Sae Universiy fred.harris@sdsu.edu Sridhar Seshagiri San Diego Sae Universiy Seshigar.@engineering.sdsu.edu Chris Dick Xilinx Corp. chris.dick@xilinx.com
An Improved Square-Roo Nyquis Shaping Filer fred harris San Diego Sae Universiy fred.harris@sdsu.edu Sridhar Seshagiri San Diego Sae Universiy Seshigar.@engineering.sdsu.edu Chris Dick Xilinx Corp. chris.dick@xilinx.com
Web System for the Remote Control and Execution of an IEC Application
 Web Sysem for he Remoe Conrol and Execuion of an IEC 61499 Applicaion Oana ROHAT, Dan POPESCU Faculy of Auomaion and Compuer Science, Poliehnica Universiy, Splaiul Independenței 313, Bucureși, 060042,
Web Sysem for he Remoe Conrol and Execuion of an IEC 61499 Applicaion Oana ROHAT, Dan POPESCU Faculy of Auomaion and Compuer Science, Poliehnica Universiy, Splaiul Independenței 313, Bucureși, 060042,
MOBILE COMPUTING. Wi-Fi 9/20/15. CSE 40814/60814 Fall Wi-Fi:
 MOBILE COMPUTING CSE 40814/60814 Fall 2015 Wi-Fi Wi-Fi: name is NOT an abbreviaion play on Hi-Fi (high fideliy) Wireless Local Area Nework (WLAN) echnology WLAN and Wi-Fi ofen used synonymous Typically
MOBILE COMPUTING CSE 40814/60814 Fall 2015 Wi-Fi Wi-Fi: name is NOT an abbreviaion play on Hi-Fi (high fideliy) Wireless Local Area Nework (WLAN) echnology WLAN and Wi-Fi ofen used synonymous Typically
MOBILE COMPUTING 3/18/18. Wi-Fi IEEE. CSE 40814/60814 Spring 2018
 MOBILE COMPUTING CSE 40814/60814 Spring 2018 Wi-Fi Wi-Fi: name is NOT an abbreviaion play on Hi-Fi (high fideliy) Wireless Local Area Nework (WLAN) echnology WLAN and Wi-Fi ofen used synonymous Typically
MOBILE COMPUTING CSE 40814/60814 Spring 2018 Wi-Fi Wi-Fi: name is NOT an abbreviaion play on Hi-Fi (high fideliy) Wireless Local Area Nework (WLAN) echnology WLAN and Wi-Fi ofen used synonymous Typically
STRING DESCRIPTIONS OF DATA FOR DISPLAY*
 SLAC-PUB-383 January 1968 STRING DESCRIPTIONS OF DATA FOR DISPLAY* J. E. George and W. F. Miller Compuer Science Deparmen and Sanford Linear Acceleraor Cener Sanford Universiy Sanford, California Absrac
SLAC-PUB-383 January 1968 STRING DESCRIPTIONS OF DATA FOR DISPLAY* J. E. George and W. F. Miller Compuer Science Deparmen and Sanford Linear Acceleraor Cener Sanford Universiy Sanford, California Absrac
An efficient approach to improve throughput for TCP vegas in ad hoc network
 Inernaional Research Journal of Engineering and Technology (IRJET) e-issn: 395-0056 Volume: 0 Issue: 03 June-05 www.irje.ne p-issn: 395-007 An efficien approach o improve hroughpu for TCP vegas in ad hoc
Inernaional Research Journal of Engineering and Technology (IRJET) e-issn: 395-0056 Volume: 0 Issue: 03 June-05 www.irje.ne p-issn: 395-007 An efficien approach o improve hroughpu for TCP vegas in ad hoc
Learning in Games via Opponent Strategy Estimation and Policy Search
 Learning in Games via Opponen Sraegy Esimaion and Policy Search Yavar Naddaf Deparmen of Compuer Science Universiy of Briish Columbia Vancouver, BC yavar@naddaf.name Nando de Freias (Supervisor) Deparmen
Learning in Games via Opponen Sraegy Esimaion and Policy Search Yavar Naddaf Deparmen of Compuer Science Universiy of Briish Columbia Vancouver, BC yavar@naddaf.name Nando de Freias (Supervisor) Deparmen
A Tool for Multi-Hour ATM Network Design considering Mixed Peer-to-Peer and Client-Server based Services
 A Tool for Muli-Hour ATM Nework Design considering Mied Peer-o-Peer and Clien-Server based Services Conac Auhor Name: Luis Cardoso Company / Organizaion: Porugal Telecom Inovação Complee Mailing Address:
A Tool for Muli-Hour ATM Nework Design considering Mied Peer-o-Peer and Clien-Server based Services Conac Auhor Name: Luis Cardoso Company / Organizaion: Porugal Telecom Inovação Complee Mailing Address:
Difficulty-aware Hybrid Search in Peer-to-Peer Networks
 Difficuly-aware Hybrid Search in Peer-o-Peer Neworks Hanhua Chen, Hai Jin, Yunhao Liu, Lionel M. Ni School of Compuer Science and Technology Huazhong Univ. of Science and Technology {chenhanhua, hjin}@hus.edu.cn
Difficuly-aware Hybrid Search in Peer-o-Peer Neworks Hanhua Chen, Hai Jin, Yunhao Liu, Lionel M. Ni School of Compuer Science and Technology Huazhong Univ. of Science and Technology {chenhanhua, hjin}@hus.edu.cn
Michiel Helder and Marielle C.T.A Geurts. Hoofdkantoor PTT Post / Dutch Postal Services Headquarters
 SHORT TERM PREDICTIONS A MONITORING SYSTEM by Michiel Helder and Marielle C.T.A Geurs Hoofdkanoor PTT Pos / Duch Posal Services Headquarers Keywords macro ime series shor erm predicions ARIMA-models faciliy
SHORT TERM PREDICTIONS A MONITORING SYSTEM by Michiel Helder and Marielle C.T.A Geurs Hoofdkanoor PTT Pos / Duch Posal Services Headquarers Keywords macro ime series shor erm predicions ARIMA-models faciliy
4. Minimax and planning problems
 CS/ECE/ISyE 524 Inroducion o Opimizaion Spring 2017 18 4. Minima and planning problems ˆ Opimizing piecewise linear funcions ˆ Minima problems ˆ Eample: Chebyshev cener ˆ Muli-period planning problems
CS/ECE/ISyE 524 Inroducion o Opimizaion Spring 2017 18 4. Minima and planning problems ˆ Opimizing piecewise linear funcions ˆ Minima problems ˆ Eample: Chebyshev cener ˆ Muli-period planning problems
Handling uncertainty in semantic information retrieval process
 Handling uncerainy in semanic informaion rerieval process Chkiwa Mounira 1, Jedidi Anis 1 and Faiez Gargouri 1 1 Mulimedia, InfoRmaion sysems and Advanced Compuing Laboraory Sfax Universiy, Tunisia m.chkiwa@gmail.com,
Handling uncerainy in semanic informaion rerieval process Chkiwa Mounira 1, Jedidi Anis 1 and Faiez Gargouri 1 1 Mulimedia, InfoRmaion sysems and Advanced Compuing Laboraory Sfax Universiy, Tunisia m.chkiwa@gmail.com,
Location. Electrical. Loads. 2-wire mains-rated. 0.5 mm² to 1.5 mm² Max. length 300 m (with 1.5 mm² cable). Example: Belden 8471
 Produc Descripion Insallaion and User Guide Transiser Dimmer (454) The DIN rail mouned 454 is a 4channel ransisor dimmer. I can operae in one of wo modes; leading edge or railing edge. All 4 channels operae
Produc Descripion Insallaion and User Guide Transiser Dimmer (454) The DIN rail mouned 454 is a 4channel ransisor dimmer. I can operae in one of wo modes; leading edge or railing edge. All 4 channels operae
Rule-Based Multi-Query Optimization
 Rule-Based Muli-Query Opimizaion Mingsheng Hong Dep. of Compuer cience Cornell Universiy mshong@cs.cornell.edu Johannes Gehrke Dep. of Compuer cience Cornell Universiy johannes@cs.cornell.edu Mirek Riedewald
Rule-Based Muli-Query Opimizaion Mingsheng Hong Dep. of Compuer cience Cornell Universiy mshong@cs.cornell.edu Johannes Gehrke Dep. of Compuer cience Cornell Universiy johannes@cs.cornell.edu Mirek Riedewald
CAMERA CALIBRATION BY REGISTRATION STEREO RECONSTRUCTION TO 3D MODEL
 CAMERA CALIBRATION BY REGISTRATION STEREO RECONSTRUCTION TO 3D MODEL Klečka Jan Docoral Degree Programme (1), FEEC BUT E-mail: xkleck01@sud.feec.vubr.cz Supervised by: Horák Karel E-mail: horak@feec.vubr.cz
CAMERA CALIBRATION BY REGISTRATION STEREO RECONSTRUCTION TO 3D MODEL Klečka Jan Docoral Degree Programme (1), FEEC BUT E-mail: xkleck01@sud.feec.vubr.cz Supervised by: Horák Karel E-mail: horak@feec.vubr.cz
Locating Internet Bottlenecks: Algorithms, Measurements, and Implications
 Locaing Inerne Bolenecks: Algorihms, Measuremens, and Implicaions Ningning Hu Li (Erran) Li Zhuoing Morley Mao Carnegie Mellon Universiy Bell Laboraories Universiy of Michigan hnn@cs.cmu.edu erranlli@bell-labs.com
Locaing Inerne Bolenecks: Algorihms, Measuremens, and Implicaions Ningning Hu Li (Erran) Li Zhuoing Morley Mao Carnegie Mellon Universiy Bell Laboraories Universiy of Michigan hnn@cs.cmu.edu erranlli@bell-labs.com
Voltair Version 2.5 Release Notes (January, 2018)
 Volair Version 2.5 Release Noes (January, 2018) Inroducion 25-Seven s new Firmware Updae 2.5 for he Volair processor is par of our coninuing effors o improve Volair wih new feaures and capabiliies. For
Volair Version 2.5 Release Noes (January, 2018) Inroducion 25-Seven s new Firmware Updae 2.5 for he Volair processor is par of our coninuing effors o improve Volair wih new feaures and capabiliies. For
Packet Scheduling in a Low-Latency Optical Interconnect with Electronic Buffers
 Packe cheduling in a Low-Laency Opical Inerconnec wih Elecronic Buffers Lin Liu Zhenghao Zhang Yuanyuan Yang Dep Elecrical & Compuer Engineering Compuer cience Deparmen Dep Elecrical & Compuer Engineering
Packe cheduling in a Low-Laency Opical Inerconnec wih Elecronic Buffers Lin Liu Zhenghao Zhang Yuanyuan Yang Dep Elecrical & Compuer Engineering Compuer cience Deparmen Dep Elecrical & Compuer Engineering
Reinforcement Learning by Policy Improvement. Making Use of Experiences of The Other Tasks. Hajime Kimura and Shigenobu Kobayashi
 Reinforcemen Learning by Policy Improvemen Making Use of Experiences of The Oher Tasks Hajime Kimura and Shigenobu Kobayashi Tokyo Insiue of Technology, JAPAN genfe.dis.iech.ac.jp, kobayasidis.iech.ac.jp
Reinforcemen Learning by Policy Improvemen Making Use of Experiences of The Oher Tasks Hajime Kimura and Shigenobu Kobayashi Tokyo Insiue of Technology, JAPAN genfe.dis.iech.ac.jp, kobayasidis.iech.ac.jp
Improving the Efficiency of Dynamic Service Provisioning in Transport Networks with Scheduled Services
 Improving he Efficiency of Dynamic Service Provisioning in Transpor Neworks wih Scheduled Services Ralf Hülsermann, Monika Jäger and Andreas Gladisch Technologiezenrum, T-Sysems, Goslarer Ufer 35, D-1585
Improving he Efficiency of Dynamic Service Provisioning in Transpor Neworks wih Scheduled Services Ralf Hülsermann, Monika Jäger and Andreas Gladisch Technologiezenrum, T-Sysems, Goslarer Ufer 35, D-1585
Motor Control. 5. Control. Motor Control. Motor Control
 5. Conrol In his chaper we will do: Feedback Conrol On/Off Conroller PID Conroller Moor Conrol Why use conrol a all? Correc or wrong? Supplying a cerain volage / pulsewidh will make he moor spin a a cerain
5. Conrol In his chaper we will do: Feedback Conrol On/Off Conroller PID Conroller Moor Conrol Why use conrol a all? Correc or wrong? Supplying a cerain volage / pulsewidh will make he moor spin a a cerain
MORPHOLOGICAL SEGMENTATION OF IMAGE SEQUENCES
 MORPHOLOGICAL SEGMENTATION OF IMAGE SEQUENCES B. MARCOTEGUI and F. MEYER Ecole des Mines de Paris, Cenre de Morphologie Mahémaique, 35, rue Sain-Honoré, F 77305 Fonainebleau Cedex, France Absrac. In image
MORPHOLOGICAL SEGMENTATION OF IMAGE SEQUENCES B. MARCOTEGUI and F. MEYER Ecole des Mines de Paris, Cenre de Morphologie Mahémaique, 35, rue Sain-Honoré, F 77305 Fonainebleau Cedex, France Absrac. In image
Protecting User Privacy in a Multi-Path Information-Centric Network Using Multiple Random-Caches
 Chu WB, Wang LF, Jiang ZJ e al. Proecing user privacy in a muli-pah informaion-cenric nework using muliple random-caches. JOURNAL OF COMPUTER SCIENCE AND TECHNOLOGY 32(3): 585 598 May 27. DOI.7/s39-7-73-2
Chu WB, Wang LF, Jiang ZJ e al. Proecing user privacy in a muli-pah informaion-cenric nework using muliple random-caches. JOURNAL OF COMPUTER SCIENCE AND TECHNOLOGY 32(3): 585 598 May 27. DOI.7/s39-7-73-2
Data Structures and Algorithms. The material for this lecture is drawn, in part, from The Practice of Programming (Kernighan & Pike) Chapter 2
 Daa Srucures and Algorihms The maerial for his lecure is drawn, in par, from The Pracice of Programming (Kernighan & Pike) Chaper 2 1 Moivaing Quoaion Every program depends on algorihms and daa srucures,
Daa Srucures and Algorihms The maerial for his lecure is drawn, in par, from The Pracice of Programming (Kernighan & Pike) Chaper 2 1 Moivaing Quoaion Every program depends on algorihms and daa srucures,
4.1 3D GEOMETRIC TRANSFORMATIONS
 MODULE IV MCA - 3 COMPUTER GRAPHICS ADMN 29- Dep. of Compuer Science And Applicaions, SJCET, Palai 94 4. 3D GEOMETRIC TRANSFORMATIONS Mehods for geomeric ransformaions and objec modeling in hree dimensions
MODULE IV MCA - 3 COMPUTER GRAPHICS ADMN 29- Dep. of Compuer Science And Applicaions, SJCET, Palai 94 4. 3D GEOMETRIC TRANSFORMATIONS Mehods for geomeric ransformaions and objec modeling in hree dimensions
Performance Evaluation of Implementing Calls Prioritization with Different Queuing Disciplines in Mobile Wireless Networks
 Journal of Compuer Science 2 (5): 466-472, 2006 ISSN 1549-3636 2006 Science Publicaions Performance Evaluaion of Implemening Calls Prioriizaion wih Differen Queuing Disciplines in Mobile Wireless Neworks
Journal of Compuer Science 2 (5): 466-472, 2006 ISSN 1549-3636 2006 Science Publicaions Performance Evaluaion of Implemening Calls Prioriizaion wih Differen Queuing Disciplines in Mobile Wireless Neworks
Evaluation and Improvement of Multicast Service in b
 Evaluaion and Improvemen of Mulicas Service in 802.11b Chrisian Bravo 1 and Agusín González 2 1 Universidad Federico Sana María, Deparmen of Elecronics. Valparaíso, Chile chbravo@elo.ufsm.cl 2 Universidad
Evaluaion and Improvemen of Mulicas Service in 802.11b Chrisian Bravo 1 and Agusín González 2 1 Universidad Federico Sana María, Deparmen of Elecronics. Valparaíso, Chile chbravo@elo.ufsm.cl 2 Universidad
Quick Verification of Concurrent Programs by Iteratively Relaxed Scheduling
 Quick Verificaion of Concurren Programs by Ieraively Relaxed Scheduling Parick Mezler, Habib Saissi, Péer Bokor, Neeraj Suri Technische Univerisä Darmsad, Germany {mezler, saissi, pbokor, suri}@deeds.informaik.u-darmsad.de
Quick Verificaion of Concurren Programs by Ieraively Relaxed Scheduling Parick Mezler, Habib Saissi, Péer Bokor, Neeraj Suri Technische Univerisä Darmsad, Germany {mezler, saissi, pbokor, suri}@deeds.informaik.u-darmsad.de
EECS 487: Interactive Computer Graphics
 EECS 487: Ineracive Compuer Graphics Lecure 7: B-splines curves Raional Bézier and NURBS Cubic Splines A represenaion of cubic spline consiss of: four conrol poins (why four?) hese are compleely user specified
EECS 487: Ineracive Compuer Graphics Lecure 7: B-splines curves Raional Bézier and NURBS Cubic Splines A represenaion of cubic spline consiss of: four conrol poins (why four?) hese are compleely user specified
User Adjustable Process Scheduling Mechanism for a Multiprocessor Embedded System
 Proceedings of he 6h WSEAS Inernaional Conference on Applied Compuer Science, Tenerife, Canary Islands, Spain, December 16-18, 2006 346 User Adjusable Process Scheduling Mechanism for a Muliprocessor Embedded
Proceedings of he 6h WSEAS Inernaional Conference on Applied Compuer Science, Tenerife, Canary Islands, Spain, December 16-18, 2006 346 User Adjusable Process Scheduling Mechanism for a Muliprocessor Embedded
An Efficient Delivery Scheme for Coded Caching
 201 27h Inernaional Teleraffic Congress An Efficien Delivery Scheme for Coded Caching Abinesh Ramakrishnan, Cedric Wesphal and Ahina Markopoulou Deparmen of Elecrical Engineering and Compuer Science, Universiy
201 27h Inernaional Teleraffic Congress An Efficien Delivery Scheme for Coded Caching Abinesh Ramakrishnan, Cedric Wesphal and Ahina Markopoulou Deparmen of Elecrical Engineering and Compuer Science, Universiy
MIC2569. Features. General Description. Applications. Typical Application. CableCARD Power Switch
 CableCARD Power Swich General Descripion is designed o supply power o OpenCable sysems and CableCARD hoss. These CableCARDs are also known as Poin of Disribuion (POD) cards. suppors boh Single and Muliple
CableCARD Power Swich General Descripion is designed o supply power o OpenCable sysems and CableCARD hoss. These CableCARDs are also known as Poin of Disribuion (POD) cards. suppors boh Single and Muliple
Distributed Task Negotiation in Modular Robots
 Disribued Task Negoiaion in Modular Robos Behnam Salemi, eer Will, and Wei-Min Shen USC Informaion Sciences Insiue and Compuer Science Deparmen Marina del Rey, USA, {salemi, will, shen}@isi.edu Inroducion
Disribued Task Negoiaion in Modular Robos Behnam Salemi, eer Will, and Wei-Min Shen USC Informaion Sciences Insiue and Compuer Science Deparmen Marina del Rey, USA, {salemi, will, shen}@isi.edu Inroducion
PART 1 REFERENCE INFORMATION CONTROL DATA 6400 SYSTEMS CENTRAL PROCESSOR MONITOR
 . ~ PART 1 c 0 \,).,,.,, REFERENCE NFORMATON CONTROL DATA 6400 SYSTEMS CENTRAL PROCESSOR MONTOR n CONTROL DATA 6400 Compuer Sysems, sysem funcions are normally handled by he Monior locaed in a Peripheral
. ~ PART 1 c 0 \,).,,.,, REFERENCE NFORMATON CONTROL DATA 6400 SYSTEMS CENTRAL PROCESSOR MONTOR n CONTROL DATA 6400 Compuer Sysems, sysem funcions are normally handled by he Monior locaed in a Peripheral
Gauss-Jordan Algorithm
 Gauss-Jordan Algorihm The Gauss-Jordan algorihm is a sep by sep procedure for solving a sysem of linear equaions which may conain any number of variables and any number of equaions. The algorihm is carried
Gauss-Jordan Algorihm The Gauss-Jordan algorihm is a sep by sep procedure for solving a sysem of linear equaions which may conain any number of variables and any number of equaions. The algorihm is carried
NRMI: Natural and Efficient Middleware
 NRMI: Naural and Efficien Middleware Eli Tilevich and Yannis Smaragdakis Cener for Experimenal Research in Compuer Sysems (CERCS), College of Compuing, Georgia Tech {ilevich, yannis}@cc.gaech.edu Absrac
NRMI: Naural and Efficien Middleware Eli Tilevich and Yannis Smaragdakis Cener for Experimenal Research in Compuer Sysems (CERCS), College of Compuing, Georgia Tech {ilevich, yannis}@cc.gaech.edu Absrac
Opportunistic Flooding in Low-Duty-Cycle Wireless Sensor Networks with Unreliable Links
 1 in Low-uy-ycle Wireless Sensor Neworks wih Unreliable Links Shuo uo, Suden Member, IEEE, Liang He, Member, IEEE, Yu u, Member, IEEE, o Jiang, Suden Member, IEEE, and Tian He, Member, IEEE bsrac looding
1 in Low-uy-ycle Wireless Sensor Neworks wih Unreliable Links Shuo uo, Suden Member, IEEE, Liang He, Member, IEEE, Yu u, Member, IEEE, o Jiang, Suden Member, IEEE, and Tian He, Member, IEEE bsrac looding
Towards a Realistic Model for Failure Propagation in Interdependent Networks
 Towards a Realisic Model for Failure Propagaion in Inerdependen Neworks Agosino Suraro, Simone Silvesri, Mauro Coni, Sajal K. Das Deparmen of Mahemaics, Universiy of Padua, email: agosino.suraro@sudeni.unipd.i,
Towards a Realisic Model for Failure Propagaion in Inerdependen Neworks Agosino Suraro, Simone Silvesri, Mauro Coni, Sajal K. Das Deparmen of Mahemaics, Universiy of Padua, email: agosino.suraro@sudeni.unipd.i,
Design Alternatives for a Thin Lens Spatial Integrator Array
 Egyp. J. Solids, Vol. (7), No. (), (004) 75 Design Alernaives for a Thin Lens Spaial Inegraor Array Hala Kamal *, Daniel V azquez and Javier Alda and E. Bernabeu Opics Deparmen. Universiy Compluense of
Egyp. J. Solids, Vol. (7), No. (), (004) 75 Design Alernaives for a Thin Lens Spaial Inegraor Array Hala Kamal *, Daniel V azquez and Javier Alda and E. Bernabeu Opics Deparmen. Universiy Compluense of
Video Content Description Using Fuzzy Spatio-Temporal Relations
 Proceedings of he 4s Hawaii Inernaional Conference on Sysem Sciences - 008 Video Conen Descripion Using Fuzzy Spaio-Temporal Relaions rchana M. Rajurkar *, R.C. Joshi and Sananu Chaudhary 3 Dep of Compuer
Proceedings of he 4s Hawaii Inernaional Conference on Sysem Sciences - 008 Video Conen Descripion Using Fuzzy Spaio-Temporal Relaions rchana M. Rajurkar *, R.C. Joshi and Sananu Chaudhary 3 Dep of Compuer
IntentSearch:Capturing User Intention for One-Click Internet Image Search
 JOURNAL OF L A T E X CLASS FILES, VOL. 6, NO. 1, JANUARY 2010 1 InenSearch:Capuring User Inenion for One-Click Inerne Image Search Xiaoou Tang, Fellow, IEEE, Ke Liu, Jingyu Cui, Suden Member, IEEE, Fang
JOURNAL OF L A T E X CLASS FILES, VOL. 6, NO. 1, JANUARY 2010 1 InenSearch:Capuring User Inenion for One-Click Inerne Image Search Xiaoou Tang, Fellow, IEEE, Ke Liu, Jingyu Cui, Suden Member, IEEE, Fang
CENG 477 Introduction to Computer Graphics. Modeling Transformations
 CENG 477 Inroducion o Compuer Graphics Modeling Transformaions Modeling Transformaions Model coordinaes o World coordinaes: Model coordinaes: All shapes wih heir local coordinaes and sies. world World
CENG 477 Inroducion o Compuer Graphics Modeling Transformaions Modeling Transformaions Model coordinaes o World coordinaes: Model coordinaes: All shapes wih heir local coordinaes and sies. world World
MoBAN: A Configurable Mobility Model for Wireless Body Area Networks
 MoBAN: A Configurable Mobiliy Model for Wireless Body Area Neworks Majid Nabi 1, Marc Geilen 1, Twan Basen 1,2 1 Deparmen of Elecrical Engineering, Eindhoven Universiy of Technology, he Neherlands 2 Embedded
MoBAN: A Configurable Mobiliy Model for Wireless Body Area Neworks Majid Nabi 1, Marc Geilen 1, Twan Basen 1,2 1 Deparmen of Elecrical Engineering, Eindhoven Universiy of Technology, he Neherlands 2 Embedded
Delayed reservation decision in optical burst switching networks with optical buffers. Title. Li, GM; Li, VOK; Li, CY; Wai, PKA
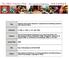 Tile Delayed reservaion decision in opical burs swiching neworks wih opical buffers Auhor(s) Li, GM; Li, VOK; Li, CY; Wai, PKA Ciaion The 3rd nernaional Conference on Communicaions and Neworking in China
Tile Delayed reservaion decision in opical burs swiching neworks wih opical buffers Auhor(s) Li, GM; Li, VOK; Li, CY; Wai, PKA Ciaion The 3rd nernaional Conference on Communicaions and Neworking in China
Nonparametric CUSUM Charts for Process Variability
 Journal of Academia and Indusrial Research (JAIR) Volume 3, Issue June 4 53 REEARCH ARTICLE IN: 78-53 Nonparameric CUUM Chars for Process Variabiliy D.M. Zombade and V.B. Ghue * Dep. of aisics, Walchand
Journal of Academia and Indusrial Research (JAIR) Volume 3, Issue June 4 53 REEARCH ARTICLE IN: 78-53 Nonparameric CUUM Chars for Process Variabiliy D.M. Zombade and V.B. Ghue * Dep. of aisics, Walchand
Effects needed for Realism. Ray Tracing. Ray Tracing: History. Outline. Foundations of Computer Graphics (Fall 2012)
 Foundaions of ompuer Graphics (Fall 2012) S 184, Lecure 16: Ray Tracing hp://ins.eecs.berkeley.edu/~cs184 Effecs needed for Realism (Sof) Shadows Reflecions (Mirrors and Glossy) Transparency (Waer, Glass)
Foundaions of ompuer Graphics (Fall 2012) S 184, Lecure 16: Ray Tracing hp://ins.eecs.berkeley.edu/~cs184 Effecs needed for Realism (Sof) Shadows Reflecions (Mirrors and Glossy) Transparency (Waer, Glass)
Fully Dynamic Algorithm for Top-k Densest Subgraphs
 Fully Dynamic Algorihm for Top-k Denses Subgraphs Muhammad Anis Uddin Nasir 1, Arisides Gionis 2, Gianmarco De Francisci Morales 3 Sarunas Girdzijauskas 4 Royal Insiue of Technology, Sweden Aalo Universiy,
Fully Dynamic Algorihm for Top-k Denses Subgraphs Muhammad Anis Uddin Nasir 1, Arisides Gionis 2, Gianmarco De Francisci Morales 3 Sarunas Girdzijauskas 4 Royal Insiue of Technology, Sweden Aalo Universiy,
Utility-Based Hybrid Memory Management
 Uiliy-Based Hybrid Memory Managemen Yang Li Saugaa Ghose Jongmoo Choi Jin Sun Hui Wang Onur Mulu Carnegie Mellon Universiy Dankook Universiy Beihang Universiy ETH Zürich While he memory fooprins of cloud
Uiliy-Based Hybrid Memory Managemen Yang Li Saugaa Ghose Jongmoo Choi Jin Sun Hui Wang Onur Mulu Carnegie Mellon Universiy Dankook Universiy Beihang Universiy ETH Zürich While he memory fooprins of cloud
Partition-based document identifier assignment (PBDIA) algorithm. (long queries)
 ( ) Pariion-based documen idenifier assignmen (PBDIA) algorihm PBDIA (long queries) (parallel IR) :,,,, d-gap Compressing an invered file can grealy improve query performance of an informaion rerieval
( ) Pariion-based documen idenifier assignmen (PBDIA) algorihm PBDIA (long queries) (parallel IR) :,,,, d-gap Compressing an invered file can grealy improve query performance of an informaion rerieval
Dynamic Route Planning and Obstacle Avoidance Model for Unmanned Aerial Vehicles
 Volume 116 No. 24 2017, 315-329 ISSN: 1311-8080 (prined version); ISSN: 1314-3395 (on-line version) url: hp://www.ijpam.eu ijpam.eu Dynamic Roue Planning and Obsacle Avoidance Model for Unmanned Aerial
Volume 116 No. 24 2017, 315-329 ISSN: 1311-8080 (prined version); ISSN: 1314-3395 (on-line version) url: hp://www.ijpam.eu ijpam.eu Dynamic Roue Planning and Obsacle Avoidance Model for Unmanned Aerial
! errors caused by signal attenuation, noise.!! receiver detects presence of errors:!
 Daa Link Layer! The Daa Link layer can be furher subdivided ino:!.! Logical Link Conrol (LLC): error and flow conrol!.! Media Access Conrol (MAC): framing and media access! differen link proocols may provide
Daa Link Layer! The Daa Link layer can be furher subdivided ino:!.! Logical Link Conrol (LLC): error and flow conrol!.! Media Access Conrol (MAC): framing and media access! differen link proocols may provide
The Beer Dock: Three and a Half Implementations of the Beer Distribution Game
 The Beer Dock 2002-08-13 17:55:44-0700 The Beer Dock: Three and a Half Implemenaions of he Beer Disribuion Game Michael J. Norh[1] and Charles M. Macal Argonne Naional Laboraory, Argonne, Illinois Absrac
The Beer Dock 2002-08-13 17:55:44-0700 The Beer Dock: Three and a Half Implemenaions of he Beer Disribuion Game Michael J. Norh[1] and Charles M. Macal Argonne Naional Laboraory, Argonne, Illinois Absrac
EP2200 Queueing theory and teletraffic systems
 EP2200 Queueing heory and eleraffic sysems Vikoria Fodor Laboraory of Communicaion Neworks School of Elecrical Engineering Lecure 1 If you wan o model neworks Or a comple daa flow A queue's he key o help
EP2200 Queueing heory and eleraffic sysems Vikoria Fodor Laboraory of Communicaion Neworks School of Elecrical Engineering Lecure 1 If you wan o model neworks Or a comple daa flow A queue's he key o help
LHP: An end-to-end reliable transport protocol over wireless data networks
 LHP: An end-o-end reliable ranspor proocol over wireless daa neworks Xia Gao, Suhas N. Diggavi, S. Muhukrishnan Absrac The nex generaion wireless neworks are posied o suppor large scale daa applicaions.
LHP: An end-o-end reliable ranspor proocol over wireless daa neworks Xia Gao, Suhas N. Diggavi, S. Muhukrishnan Absrac The nex generaion wireless neworks are posied o suppor large scale daa applicaions.
A Progressive-ILP Based Routing Algorithm for Cross-Referencing Biochips
 16.3 A Progressive-ILP Based Rouing Algorihm for Cross-Referencing Biochips Ping-Hung Yuh 1, Sachin Sapanekar 2, Chia-Lin Yang 1, Yao-Wen Chang 3 1 Deparmen of Compuer Science and Informaion Engineering,
16.3 A Progressive-ILP Based Rouing Algorihm for Cross-Referencing Biochips Ping-Hung Yuh 1, Sachin Sapanekar 2, Chia-Lin Yang 1, Yao-Wen Chang 3 1 Deparmen of Compuer Science and Informaion Engineering,
MOTION DETECTORS GRAPH MATCHING LAB PRE-LAB QUESTIONS
 NME: TE: LOK: MOTION ETETORS GRPH MTHING L PRE-L QUESTIONS 1. Read he insrucions, and answer he following quesions. Make sure you resae he quesion so I don hae o read he quesion o undersand he answer..
NME: TE: LOK: MOTION ETETORS GRPH MTHING L PRE-L QUESTIONS 1. Read he insrucions, and answer he following quesions. Make sure you resae he quesion so I don hae o read he quesion o undersand he answer..
This is the published version of a paper presented at The 2013 IEEE International Conference on Internet of Things, Beijing, China, August 2013.
 hp://www.diva-poral.org This is he published version of a paper presened a The 2013 IEEE Inernaional Conference on Inerne of Things, Beijing, China, 20-23 Augus 2013. Ciaion for he original published paper:
hp://www.diva-poral.org This is he published version of a paper presened a The 2013 IEEE Inernaional Conference on Inerne of Things, Beijing, China, 20-23 Augus 2013. Ciaion for he original published paper:
Parallel and Distributed Systems for Constructive Neural Network Learning*
 Parallel and Disribued Sysems for Consrucive Neural Nework Learning* J. Flecher Z. Obradovi School of Elecrical Engineering and Compuer Science Washingon Sae Universiy Pullman WA 99164-2752 Absrac A consrucive
Parallel and Disribued Sysems for Consrucive Neural Nework Learning* J. Flecher Z. Obradovi School of Elecrical Engineering and Compuer Science Washingon Sae Universiy Pullman WA 99164-2752 Absrac A consrucive
Rao-Blackwellized Particle Filtering for Probing-Based 6-DOF Localization in Robotic Assembly
 MITSUBISHI ELECTRIC RESEARCH LABORATORIES hp://www.merl.com Rao-Blackwellized Paricle Filering for Probing-Based 6-DOF Localizaion in Roboic Assembly Yuichi Taguchi, Tim Marks, Haruhisa Okuda TR1-8 June
MITSUBISHI ELECTRIC RESEARCH LABORATORIES hp://www.merl.com Rao-Blackwellized Paricle Filering for Probing-Based 6-DOF Localizaion in Roboic Assembly Yuichi Taguchi, Tim Marks, Haruhisa Okuda TR1-8 June
source managemen, naming, proecion, and service provisions. This paper concenraes on he basic processor scheduling aspecs of resource managemen. 2 The
 Virual Compuers A New Paradigm for Disribued Operaing Sysems Banu Ozden y Aaron J. Goldberg Avi Silberschaz z 600 Mounain Ave. AT&T Bell Laboraories Murray Hill, NJ 07974 Absrac The virual compuers (VC)
Virual Compuers A New Paradigm for Disribued Operaing Sysems Banu Ozden y Aaron J. Goldberg Avi Silberschaz z 600 Mounain Ave. AT&T Bell Laboraories Murray Hill, NJ 07974 Absrac The virual compuers (VC)
Using CANopen Slave Driver
 CAN Bus User Manual Using CANopen Slave Driver V1. Table of Conens 1. SDO Communicaion... 1 2. PDO Communicaion... 1 3. TPDO Reading and RPDO Wriing... 2 4. RPDO Reading... 3 5. CANopen Communicaion Parameer
CAN Bus User Manual Using CANopen Slave Driver V1. Table of Conens 1. SDO Communicaion... 1 2. PDO Communicaion... 1 3. TPDO Reading and RPDO Wriing... 2 4. RPDO Reading... 3 5. CANopen Communicaion Parameer
Modeling of IEEE in a Cluster of Synchronized Sensor Nodes
 Modeling of IEEE 802.15.4 in a Cluser of Synchronized Sensor Nodes Kenji Leibniz, Naoki Wakamiya, and Masayuki Muraa Graduae School of Informaion Science and Technology, Osaka Universiy, 1-5 Yamadaoka,
Modeling of IEEE 802.15.4 in a Cluser of Synchronized Sensor Nodes Kenji Leibniz, Naoki Wakamiya, and Masayuki Muraa Graduae School of Informaion Science and Technology, Osaka Universiy, 1-5 Yamadaoka,
Analysis of Various Types of Bugs in the Object Oriented Java Script Language Coding
 Indian Journal of Science and Technology, Vol 8(21), DOI: 10.17485/ijs/2015/v8i21/69958, Sepember 2015 ISSN (Prin) : 0974-6846 ISSN (Online) : 0974-5645 Analysis of Various Types of Bugs in he Objec Oriened
Indian Journal of Science and Technology, Vol 8(21), DOI: 10.17485/ijs/2015/v8i21/69958, Sepember 2015 ISSN (Prin) : 0974-6846 ISSN (Online) : 0974-5645 Analysis of Various Types of Bugs in he Objec Oriened
CS422 Computer Networks
 CS422 Compuer Neworks Lecure 2 Physical Layer Dr. Xiaobo Zhou Deparmen of Compuer Science CS422 PhysicalLayer.1 Quesions of Ineress How long will i ake o ransmi a message? How many bis are in he message
CS422 Compuer Neworks Lecure 2 Physical Layer Dr. Xiaobo Zhou Deparmen of Compuer Science CS422 PhysicalLayer.1 Quesions of Ineress How long will i ake o ransmi a message? How many bis are in he message
AML710 CAD LECTURE 11 SPACE CURVES. Space Curves Intrinsic properties Synthetic curves
 AML7 CAD LECTURE Space Curves Inrinsic properies Synheic curves A curve which may pass hrough any region of hreedimensional space, as conrased o a plane curve which mus lie on a single plane. Space curves
AML7 CAD LECTURE Space Curves Inrinsic properies Synheic curves A curve which may pass hrough any region of hreedimensional space, as conrased o a plane curve which mus lie on a single plane. Space curves
The Effects of Multi-Layer Traffic on the Survivability of IP-over-WDM Networks
 The Effecs of Muli-Layer Traffic on he Survivabiliy of IP-over-WDM Neworks Peera Pacharinanakul and David Tipper Graduae Telecommunicaions and Neworking Program, Universiy of Pisburgh, Pisburgh, PA 15260,
The Effecs of Muli-Layer Traffic on he Survivabiliy of IP-over-WDM Neworks Peera Pacharinanakul and David Tipper Graduae Telecommunicaions and Neworking Program, Universiy of Pisburgh, Pisburgh, PA 15260,
A Principled Approach to. MILP Modeling. Columbia University, August Carnegie Mellon University. Workshop on MIP. John Hooker.
 Slide A Principled Approach o MILP Modeling John Hooer Carnegie Mellon Universiy Worshop on MIP Columbia Universiy, Augus 008 Proposal MILP modeling is an ar, bu i need no be unprincipled. Slide Proposal
Slide A Principled Approach o MILP Modeling John Hooer Carnegie Mellon Universiy Worshop on MIP Columbia Universiy, Augus 008 Proposal MILP modeling is an ar, bu i need no be unprincipled. Slide Proposal
Mobile Robots Mapping
 Mobile Robos Mapping 1 Roboics is Easy conrol behavior percepion modelling domain model environmen model informaion exracion raw daa planning ask cogniion reasoning pah planning navigaion pah execuion
Mobile Robos Mapping 1 Roboics is Easy conrol behavior percepion modelling domain model environmen model informaion exracion raw daa planning ask cogniion reasoning pah planning navigaion pah execuion
Accelerating Call Route Query of Multi-domain SIP System via P2P GONG Jing, SHEN Qing-guo, SHEN Huan-sheng
 3rd Inernaional Conference on Mecharonics and Informaion Technology (ICMIT 2016) Acceleraing Call Roue Query of Muli-domain IP ysem via P2P GONG Jing, HEN Qing-guo, HEN Huan-sheng College of Communicaions
3rd Inernaional Conference on Mecharonics and Informaion Technology (ICMIT 2016) Acceleraing Call Roue Query of Muli-domain IP ysem via P2P GONG Jing, HEN Qing-guo, HEN Huan-sheng College of Communicaions
Visual Indoor Localization with a Floor-Plan Map
 Visual Indoor Localizaion wih a Floor-Plan Map Hang Chu Dep. of ECE Cornell Universiy Ihaca, NY 14850 hc772@cornell.edu Absrac In his repor, a indoor localizaion mehod is presened. The mehod akes firsperson
Visual Indoor Localizaion wih a Floor-Plan Map Hang Chu Dep. of ECE Cornell Universiy Ihaca, NY 14850 hc772@cornell.edu Absrac In his repor, a indoor localizaion mehod is presened. The mehod akes firsperson
