- - BER = 10-8 BER = Figure 10: throughput Vs maximum turn-around time for 16 Mbps
|
|
|
- Veronica Thornton
- 5 years ago
- Views:
Transcription
1 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 23 of x 16 IrLAP performance Throughput (bps) Max TA Time (ms) + Min TA Time =.1 ms X Min TA Time = 1 ms Min TA Time = 1 ms - - BER = 1-8 BER = 1-5 Figure 1: throughput Vs maximum turn-around time for 16 Mbps
2 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 22 of x 16 IrLAP performance Throughput (bps) Link BER Data Rate = 16 Mbps Max Ta Time = 5 ms Window Size = 127 frames Packet Size = bits + Min Ta Time =.1 ms X Min Ta Time = 1 ms Min Ta Time = 1 ms Figure 9: throughput Vs BER for 16 Mbps
3 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 21 of 24 4 x 16 IrLAP performance 3.5 Throughput (bps) Packet Size (bits) + Min TA Time =.1 ms X Min TA Time = 1 ms Min TA Time = 1 ms - - BER = 1-8 BER = 1-5 Figure 8: throughput Vs packet data size for 4 Mbps
4 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 2 of 24 4 x 16 IrLAP performance Throughput (bps) Link BER Data Rate = 4 Mbps Max Ta Time = 5 ms Window Size = 7 frames Packet Size = bits + Min TA Time =.1 ms X Min TA Time = 1 ms Min TA Time = 1 ms Figure 7: throughput Vs BER for 4 Mbps
5 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 19 of x 14 1 Throughput (bps) Packet Size (bits) + Min TA Time =.1 ms X Min TA Time = 1 ms O Min TA Time = 1 ms - - BER = 1-8 BER = 1-5 Figure 6: throughput Vs packet data size for 1152 bps
6 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 18 of x 14 1 Throughput (bps) Link BER Data Rate = 1152 bps Max TA Time = 5 ms Window Size = 7 frames Packet Size = bits + Min TA Time =.1 ms X Min TA Time = 1 ms O Min Ta Time = 1 ms Figure 5 : throughput Vs BER for 1152 bps
7 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 17 of 24 T(4) t ack T (N) t I t S I I1 I2 I3 I4 I5 I6P I7 I I1 I2 S7F a) Error free transmission at w = 3 and w = N T1(4) (w-1)t I I I1 I2 I3 I4 I5 I6P tack S3F t I I3 I4 I5 I6 b) Retransmitted frames due to error frame at w = 4 T 1(4) (w-1)ti t Fout t S t ack t I I I1 I2 I3 I4 I5 I6P SP I3 S3F c) Retransmitted frames and F-timer delay due frame error at w = 4 and w = 1 Figure 4: Determination of frame virtual transfer times
8 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 16 of p N-1 N-2 w 1 N p Figure 3: state transition diagram for the widow width process
9 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 15 of 24 Nr (3 bits) P/F Ns (3 bits) Information frame Nr (3 bits) P/F X (2 bits) 1 Supervisory frame X (3 bits) P/F Unnumbered frame X (2 bits) 1 1 Address (7 bits) C/R Control (8 bits) Information ( to bits) IrLAP packet BOF (8 bits) IrLAP packet (N bits) FCS (16/32 bits) EOF (8 bits) Physical layer frame Figure 2: IrDA frame structure
10 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 14 of 24 Applications IrLMP Information Access Service (LM-IAS) IrOBEX Tiny TP IrLAN IrCOMM IrLMP - Multiplexer (LM- MUX) IrDA Link Access Protocol (IrLAP) IrPHY to 115,2bps IrPHY & 4 Mbps Figure 2: The IrDA SIR protocol stack
11 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 13 of 24 List of Figures Figure 1: The IrDA SIR protocol stack Figure 2: IrDA frame structure Figure 3: state transition diagram for the widow width process Figure 4: Determiation of frame virtual transfer times Figure 5 : throughput Vs BER for 1152 bps Figure 6: throughput Vs packet data size for 1152 bps Figure 7: throughput Vs BER for 4 Mbps Figure 8: throughput Vs packet data size for 4 Mbps Figure 9: throughput Vs BER for 16 Mbps Figure 1: throughput Vs maximum turn-around time for 16 Mbps
12 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 12 of 24 [11] P. Barker, A. C. Boucouvalas, 'Performance modeling of the IrDA protocol for Infrared Wireless Communications', IEEE Communications magazine, 36 (12), pp , (1998) [12] W. Bux & K. Kummerle, 'Balanced HDLC Procedures: A Performance Analysis'. IEEE Transactions On Communications, com-28(11), pp (198). [13] M. Schwartz, Telecommunications Networks: Protocols, Modelling and Analysis. Reading, MA: Addison Wesely. (1987).
13 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 11 of 24 5 Conclusions The mathematical analysis presented shows that the concept of the virtual transmission time which had been previously used to analyse full-duplex wired protocols can be applied to the IrLAP protocol, being a derivative of the HDLC protocol in NRM mode. The model examines the time required for retransmission of packets and the probabilities that such retransmissions are required. Results are presented for throughput efficiency versus data message BER and other link parameter settings. The results indicate possible limitations of the present IrDA protocol in supporting higher bit rates (e.g. 1 Mbps and above) as the link turn-around frequency can severely impair the link performance. The larger window size proposed for the 16 Mbps link provides a solution but only if the link BER is optimised. If the BER becomes poor, the larger window size will impair the performance as more frame retransmissions will be required. The model presented can thus be useful in determining the link parameter settings for optimum performance of an IrDA infrared link in a particular link environment. Acknowledgements The authors would like to thank BT laboratories for their financial assistance in carrying out this research. References [1] D. J. T. Heatly, D. R.Wisely, I. Neild, & P. Cochrane, 'Optical Wireless: The Story So Far'. IEEE Communications Magazine, 36(12), (1998). [2] A. C. Boucouvalas, 'Free space infrared optical links: Eye safety issues', Proceedings of MEDIACOMM 95 - International Conference on Multimedia Communications, Southampton, UK, April 1995, pp (1995) [3] A. C. Boucouvalas, 'Eye safety Issues of Free Space Optical Links'. Focus, 23..pp 8 23, (1995) [4] A. C. Boucouvalas, 'IEC Eye Safety Classification of some consumer electronic products' IEE Colloquium on Free Space Communication Links, paper No. 13, 19th February 1996, IEE Savoy Place, London. (1996) [5] A. M. Street, K. Samaras, D. C. O'Brian, & D. J. Edwards, 'Indoor Optical Wireless Systems - A Review'. Optical and Quantum Electronics, 29, pp (1997). [6] I. Millar, M. Beale, B. J. Donoghue, K. W. Lindstrom, & S. Williams, 'The IrDA Standard for High-Speed Infrared Communications'. The Hewlett-Packard Journal, February (1) pp 1-26, (1998) [7] IrDA, Serial Infrared Physical Layer Link Specification Version 1.1, Infrared Data Association, (1995) [8] IrDA, Serial Infrared Link Access Protocol (IrLAP) Version 1.1, Infrared Data Association, (1996) [9] D.W. Suvak, Proposed Changes to IrLAP for VFIR, Infrared Data Association, (1999) [1] A. C. Boucouvalas, P. Barker, 'IrLAP protocol performance analysis of IrDA wireless communications' Electronics letters, 34 (25), pp , (1998).
14 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 1 of Analysis of 1152 Kbps and 4 Mbps links Figure 5 shows the throughput versus BER for the 1152 bps link. This shows that a link BER of 1-7 or better is required for optimum link quality, and that a BER worse that 1-6 would be quite detrimental to the throughput. It also shows that at this data rate, the effect of increasing the minimum turn-around time is not very significant. Figures 6 shows throughput versus packet data size for two values of BER: 1-8 and 1-5, therefore representing links of good and 'bad' quality respectively. The plot shows that the throughput increases with increasing packet data size. This is because as the size of the frame increases, the frequency of the link turn-around required after every 7 frames decreases, thus decreasing the frequency of acknowledgement times and turn-around delays introduced into the throughput. It can also be seen that the effect of the increase in minimum turn-around time is greater for a lower data size because of the higher link turn-around frequency. The jerky nature observed at the high end of the plot is due to the quantised reduction in frames that can be transmitted within the 5 ms maximum turn-around time, as the frame size increases. In fact at the 1152 bps data rate, the number of frames sent within 5 ms at the maximum data size of bits is 3 and not the maximum 7. For the BER of 1-5 plots it can be seen how the throughput increases with packet data size as before until around 1 3 bits after which it decreases. This is because as the packet data size increases, the probability of the frame being in error, given the same BER, also increases and begins to dominate over the improvement due to increasing data size after 1 3 bits. Figures 7 and 8 show the same analysis for the 4 Mbps link. Figure 7 shows that a BER of nearer 1-8 as compared to 1-7 for the 1152 link is required for optimum performance. It can also be seen that the effect of increasing the minimum turn-around time is much more significant. This is because at this higher data rate, the frequency of link turnaround (required after every 7 frames sent) is much higher. Figure 8 shows throughput versus packet data size for BER values of 1-8 and 1-5. This again show the increased significance of the minimum turn-around time. It can also be seen how at the higher data rate a potentially larger package size than the maximum 248 bytes could be sent. However it can be also be seen that a larger packet size with a poor BER will result in a higher probability of frame errors. 4.2 Analysis of 16 Mbps links The proposed 16 Mbps link, as well as providing a higher data rate, also presents the issue of a maximum window size, of 127 frames. It can be seen from figures 9 that the effect of the increase in the minimum turn-around time is not as great as would be expected with the increase in data rate because the larger window size results in a reduced rate of link turn-around frequency. However it can also be seen that the increase in window size results in a greater sensitivity to the BER as a larger window size means a higher probability of errors within the window and a larger average number of frames that will require retransmission. This is further demonstrated by figures 1 where the maximum turn-around time is varied for the good and bad BER values. A similar effect as for the 4 Mbps link can be seen but the degradation in performance for a bad BER is much more severe.
15 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 9 of 24 and the value of the transmission time is given by: n Pn = p n 2 (18) E[ T n ( w)] = T2 n 2 (19) where T 2 is the time for each successive retransmission of the frame and is now independent of the window width w, given by: T 2 Nt I + p( t = ti + t Fout Fout + t + t S S ) + t + t ack ack N 1 N = 1 (2) 3.3 Overall window specific virtual transmission time The overall virtual transmission time for a specific value of w can therefore be determined by using the expression in equation (12) and applying the derived expressions for the expectations of the individual cases as shown above, combined with the stated probabilities of each case arising. By using, it can be shown that. n= 2 2 n p p = (21) (1 p) t v 2 p ( w) = T( w) + pe[ T1( w)] + T2 (22) (1 p) The equations (22) and (11) provide the components for equation (9) to determine the packets virtual transmission time and thus provide a mechanism to determine the average throughput of a link against any of the link parameter settings of BER, data rate, packet data size, minimum turn-around time, maximum turn-around time, and maximum window size. Calculations could also be made to determine the link BER from the link topology and transceiver characteristics, but that is outside the scope of this paper. 4 Results and analysis The equations derived are used to plot the throughput of IrDA links using a range of system settings. Plots are produced for three data rates: namely 1152 bps, 4 Mbps and 16 Mbps, being the maximum data rates of the SIR, FIR and proposed VFIR standards respectively.
16 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 8 of 24 This case examines the situation where a frame transmitted needs to be retransmitted because it has been in error. This case has the probability of a single error, i.e. p. The time T 1 (w) denotes the time taken from the end of the initial transmission to the end of the 1 st retransmission. We need to examine whether we have additional errors following the initial error frame, and whether this includes the last frame in the sequence. i) Error not last in series Here the frame is simply retransmitted at the end of the sequence and after the REJ has been returned. This is shown in Figure 4b. T 1 ( w) = wt I + t ack (14) ii) Errors including last in series. In this case the P-bit is lost, therefore the secondary will not know that it can now transmit. If the primary has not received a response when the F-timer has expired a P bit will be sent with an RR S-frame. This situation has an additional probability of p, i.e. the probability of a specific frame (the last) following the first corrupted frame being in error. This is shown Figure 4c. T ( w) = wt + t + t + t 1 I Fout S ack (15) (iii) Single error being the last in the series This case is the same as case (ii) above with w = 1 except that there is only one error in the sequence, thus there is only the single error probability. Therefore by combining equations (14)and (15), with the stated additional probabilities the overall expectation value of T 1 (w) and the probability P 1 can be given by: P 1 = p (16) [ w) ] E T 1 ( wti + p( t = ti + tfout + t Fout S + t S + t ) + t ack ack w 1 w = 1 (17) C. Secondary retransmissions due to subsequent errors of the same frame As the initial resent frame will be the first in the series, all N frames will be retransmitted. Therefore the retransmitted frame will always be the first in the sequence. However as before if the last frame of the sequence is also in error, the P bit will not be received so the recovery only begins when the F-timer expires. The probability of n successive transmissions of the same frame being in error is p n. Thus we have:
17 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 7 of 24 Q = RQ (1) which can be shown to give N p(1 p) 1 (1 p) φ( w) = N p(1 p) 1 (1 p) w 1 N 1 N w = 1,2 LN 1 w = N (11) The virtual transmission time for a particular window width w (for equation 9) is calculated by the addition of the time to transmit the initial frame and the time required for subsequent retransmissions of the frame multiplied by the probabilities that these retransmissions are required. + t v ( w) = T ( w) Pn E[ Tn( w)] (12) n= 1 where T is the time to transmit the frame initially P n is the probability that the n th retransmission is required, and E[T n (w)] is the time expectation value of the time required for the n th retransmission only. 3.2 Calculation of Virtual Transmission Times In calculating the virtual transmission time we need to examine a number of different cases involving whether an error occurred, in what position in the sequence the error is located, whether there are additional errors in the sequence and in what positions, and whether the retransmissions of frames are themselves in error. A. Initial frame transmission time The transmission time in this situation is simply the transmission time for the I-frame unless the next frame to transmit is the first frame of a sequence (i.e. w = N) in which case the primary station must wait to receive an acknowledgement from the receiving station before continuing to transmit. This is shown in Figure 4a. t I w N T ( w) = (13) t I + tack w = N B. Retransmission of a frame in error
18 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 6 of 24 The virtual transmission time for a particular frame is found to be dependent on the window width (w) seen by that frame. The window width is defined as the number of remaining frames (from the start of the current frame) that can be sent before transmission control is passed. With IrDA, the maximum window width is determined by the maximum window size parameter, here denoted W max, negotiated during the link establishment, and the maximum turn-around time combined with the data rate and packet data size which may limit the number of frames that can be sent to below W max. We therefore use a value N to indicate the number of frames that can be sent before transmission is passed to the other station. N = min W T floor max (8) max, t I where min is the lesser of, and floor is the largest integer not exceeding. The overall virtual transmission time is determined by summing the frames virtual transmission time for all values of w, multiplied by the probability of the frame having each value of w. This is therefore given by: t v = N w= 1 φ ( w) t ( w) (9) v where t v (w) is the virtual transmission time for a frame seeing a width w, and φ(w) is the probability that the window width has a specific value of w. Each time a frame is transmitted error free (with probability 1 p), the window width reduces by 1. When it reaches 1, the window width returns to its maximum value of N. However if a frame is in error (with probability p) then it and all the following frames in the sequence will need to be retransmitted. Therefore the window width effectively returns to (N-1). The overall process can be considered as a Markov chain and represented as the state transition diagram shown in Figure 3. The value for φ(w) can then be determined by calculating the limiting (i.e. steady-state) probability distribution for the window width state set. The state transition diagram can be represented by the state transition matrix R, shown below, where the probability of going from a state i to a state j is given by the element r ij. ( N 1) ( N 2) M R = ( w) M (1) ( N ) ( N 1) p p M p M p 1 ( N 2) 1 p L O ( w) 1 p L O (1) 1 p ( N) 1 p If we define the limiting probability distribution vector Q such that Q = [φ(1) φ(w) φ(n)], using matrix multiplication we can determined Q by using:
19 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 5 of 24 The following parameters in Table 1 are used in the analysis. Parameter Description Unit C Link data baud rate bits /sec p b Link bit error rate - p Frame error probability - l I-frame message data length bits l S-frame length / I-frame overhead bits t I Transmission time of an I-frame sec t S Transmission time of an S-frame sec t ta Minimum turn-around time sec t ack Acknowledgement time sec T max Maximum turn-around time sec t Fout F-timer Time-out period sec Table 1: Analysis Parameters The values for t S, t I and t ack are calculated as follows: t S l' = (1) C t I l + l' = (2) t ack = 2 tta + ts (3) C The acknowledgement time t ack here being the time to receive back an S-frame acknowledgement after the last frame in the sequence is transmitted, thus requiring a turn-around delay at the secondary, the transmission time of the S-frame and a turn-around delay at the primary. The frame error probability p is related to the link bit error rate p b by: l+ l' p b p = 1 (1 ) (4) This is the probability that there is at least one bit in an I-frame in error. 3.1 Throughput calculation The frame throughput D f in frames per second of the link is given by the reciprocal of the virtual transmission time. This can be multiplied by the frame data length l to give the data throughput in D b in bits per second. D f 1 = (5) t v l D b = (6) Normalised Throughput t v D D C b Norm = (7)
20 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 4 of 24 lost frame or frames (i.e. failed the CRC and were discarded). The value of Vr then remains unchanged and the packet is discarded. Upon replying with an acknowledgement frame the secondary sets the Nr field to the current Vr value. Upon receiving a frame from the secondary with the F bit set (thus returning transmission control to the primary) the primary checks the Nr value against that expected, which should be equal to the current Vs value. If it is not as expected, this indicates that a retransmission of the buffered frames beginning at the indicated Nr value is now required before any new frames can be transmitted. The secondary station operates in the same way as the primary except that it does not contain a P-timer or F-timer. The secondary will immediately return transmission control to the primary if data is not immediately available for transmission [8]. A proposal has been made by IrDA to increase the maximum data rate of an IrDA link from 4 Mbps to 16 Mbps. It was recognised that at this data rate the increased frequency of link turn-around after the maximum 7 frame window size would limit the performance of the link. It has therefore also been proposed to increase the maximum window size from 7 frames to 127 frames. This requires a restructuring of the IrLAP frame control field to constitute 2 bytes in length and to have 7 bit fields for Ns and Nr [9], [1], [11]. 3. Mathematical modelling The mathematical performance model uses the concept of the virtual transmission time, denoted t v, of a packet in determining the throughput efficiency of a link. The value of t v provides the average time taken from the start of a frame's transmission to the successful arrival of the frame in-sequence at the receiving station, incorporating the time for retransmission of frame errors, and other enforced delays. If we assume continuous data transmission, then the average throughput (frames /sec) is the reciprocal of the virtual transmission time, thus representing the arrival rate of packets at the receiving application above the IrLAP layer. This method was used in an analysis of the HDLC protocol operating in ABM with a full-duplex circuit by Bux [12]. A review of the method and applications to simpler systems was also given in Schwartz [13]. The model used here involves a primary and a single secondary station operating in the data exchange phase of the IrLAP procedure. All user data (i.e. I-frames) is transmitted from the primary to the secondary only. The link is assumed to be saturated, i.e. there is data continually waiting transmission. The secondary responds with RR (Receive Ready or REJ (Reject) S-frames only. It is also assumed that an S-frame, whether from the primary or secondary, is small enough to be considered error free. The action of the P-timer is ignored in this model as we are assuming a saturated condition. However the action of the F-timer is incorporated when the primary forces a reply from the secondary if there is corruption of a P bit frame.
21 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 3 of 24 Upon link establishment devices are assigned primary and secondary station roles. There can be only one primary but potentially multiple secondaries. All data traffic must pass to or from the primary, i.e. the secondary stations cannot communicate between themselves. The IrDA frame structure is as shown in figure 2. There are three types of frame used; Supervisory frames (S-frames), Unnumbered frames (U-frames), and Information frames (I-frames). S-frames are short control frames used to issue specific commands and responses (e.g. to acknowledge received frames) and contain no user data. U-frames are used in the establishment of a link to exchange connection data or for information exchange outside of an established link. I- frames are used for the exchange of information once a link has been established. They contain the user data in the information field and have sequencing numbers for error recovery. The IrLAP packet consists of an address field, a C/R (Command /Response) bit, an 8 bit control field, and the information field which can contain up to 248 bytes of data. The control field contains a frame type identifier, the P/F bit, and frame sequence numbers and /or command /response codes depending on the frame type. The P/F bit is used to pass transmission status between devices. For the primary device it is called the P bit (Poll) and for the secondary it is called the F bit (Final). The I-frame control field contains a send sequence number Ns which cycles through values to 7. Both the I-frame and the S-frame control fields contain a receive sequence number Nr which acknowledges the receipt of frames with sequence number up to (Nr 1), thus indicating that Nr is the next expected frame sequence number. The IrLAP packet is encapsulated within the physical layer frame before transmission. The physical layer frame contains a BOF (Beginning Of Frame) and an EOF (End Of Frame) framer which both consist of the identifier and the FCS (Frame Check Sequence) which contains the result of the CRC. The IrLAP information exchange procedure is summarised as follows. Each device in a link has a send sequence variable Vs, a receive sequence variable Vr, and a window value indicating the number of frames remaining to be transmitted before transmission control is passed. In addition the primary device holds a P-Timer, which sets a limit to the transmission period of the primary device, and an F-Timer which sets a limit on the waiting time for the secondary to return transmission control. If the primary device has a data packet to send, the Ns value of the frame is assigned the current Vs value of the device and a buffer copy of the frame is made for possible retransmissions. Following transmission the value of Vs is then increased by 1 (modulo 8) and the window value decreased by 1. If the window value becomes 1, this indicates that the next frame is the last in the sequence before passing transmission control to the secondary device. This frame therefore has the P bit set to poll the secondary device. Following transmission of this frame the window value is re-set to the maximum and the F-Timer started. If the P-Timer should expire during the transmission control period of the primary due to sporadic or limited data, the primary will send an S-frame with the P bit set to poll the secondary. If the F-timer should expire following transmission of a P bit frame, this indicates that either the P bit frame has been lost, or the returning acknowledgement frame has been lost. In either case the primary must transmit an S-frame to re-poll the secondary. Upon receiving a data frame from the primary, the secondary device checks the received Ns value against the expected value. Ns should be equal to the current Vr value of the secondary. If Ns is as expected, the data packet is extracted and passed to the user. The stored value of Vr is then increased by 1 (modulo 8). If Ns is not as expected, this indicates a
22 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 2 of 24 application to use the IR link, IrLAN which provides network access via a wireless infrared LAN port, and IrOBEX which provides object exchange facilities based on the HTTP protocol. 2.1 The physical layer The IrDA physical layer provides the hardware for an IrDA infrared link, including optical transmitter and detector, and modulation and encoding hardware. The CRC (Cyclic Redundancy Check) and IrLAP packet framing are also considered to be part of the physical layer although often implemented in software. Data rates up to and including Mbps use a 16 bit CRC, while the 4 Mbps employs a 32 bit CRC. Frames that fail the CRC, thus indicating bit errors, are simply discarded and not passed to the upper IrLAP layer. The standard specifies a link distance of at least 1m with a transmission cone half angle between 15 and 3 and a receiver cone half angle of at least 15. The IR transmitter power output is limited by eye safety regulations [2]-[4]. The specified maximum output power is 5 mw/sr but typical implemented values are around 1 to 2 mw/sr. Version 1. of the physical layer provides a data baud rate of up to Kbps. This uses an RZ modulation scheme with a 3/16 pulse duration. The hardware connects to the devices serial UART interface, either internally or using an external dongal. The baud rate is thus limited to the maximum transmission rate of the devices UART chip. Version 1.1 of the physical layer provides a baud rate of up to Mbps or 4 Mbps. Rates up to Mbps use the same RZ encoding of the 1. standard but implement the CRC and framing function in hardware and connects to the devices data I/O interface. For the 4 Mbps data rate, a 4 PPM modulation scheme is used and also requires additional PPL circuitry for clock synchronisation [7]. 2.2 The IrLAP layer The IrLAP layer is the data link layer of the IrDA protocol stack and is based closely on the HDLC protocol operating in Normal Response Mode (NRM). The functions of the IrLAP layer include device discovery, link establishment, data exchange control and error recovery. Before a link can be established a device must first discover the other devices within range that it can connect to. The user can then establish a link to one of these devices. During link establishment, a number of link parameter values are negotiated. These are given below. All negotiation traffic occurs at 96 bps. Data Rate: Both devices in a connection must negotiate the same data rate. This can be up to Kbps for a the version 1. physical layer, or 4 Mbps with the version 1.1 physical layer. Maximum turn-around time: This is the maximum time that a station can hold transmission control and has an upper limit of 5 ms. Minimum turn-around time: This is a delay that must be implemented each time a device regains transmission control and is used to cover receiver latency. This has values from.1 ms to 1 ms. Maximum window size: This is the maximum number of frames that can be sent before the passing of transmission control to another device. This can have values 1 to 7. The maximum turn-around time combined with packet data size and data rate have priority over the maximum window size and thus can limit its value to below that requested. Packet data size: This is the maximum size of the information field of the IrLAP frame which contains the user data and control overheads from higher layers of the protocol. This has a maximum value of 248 bytes (16384 bits).
23 Performance Modelling of the IrDA Protocol for Infrared Wireless Communications Page 1 of Introduction Mobile and portable computers have seen a rapid growth in recent years which has led to an increasing demand for wireless data connectivity [1]. The infrared (IR) optical medium has the benefits of using lightweight, cheap and readily available components, of being restricted to the room of operation, of being spectrally unregulated and of providing potentially very high data rates. However optical power output is limited by eye-safety regulations and a desire to limit power consumption [2]-[4]. Wireless IR is therefore particularly suited to short range indoor applications [5]. The Infrared Data Association was created in 1993 to establish an open standard for short range IR data communication. The resulting IrDA SIR (Serial Infrared) protocol standard was developed to provide a simple, low cost and reliable means of data communication between IrDA compliant devices using point-to-point half-duplex IR links. Version 1. of the protocol provides a data rate of up to Kbps using a connection to the standard serial port interface, while version 1.1 provides a rate up to Mbps and 4 Mbps with high speed extension hardware [6]. The higher speed extension is often referred to as IrDA FIR (Fast Infrared). IrDA have also proposed an extension to 16 Mbps, referred to as VFIR (Very Fast Infrared). The data link layer of the protocol, IrLAP (IrDA Link Access Protocol), is based on the HDLC protocol operating in NRM (Normal Response Mode) which specifies primary and secondary station roles with all data traffic passing to or from a single primary station. This uses station polling and frame sequence numbering to indicate lost frames and force retransmissions of lost and resulting out of sequence frames. The model presented here examines the performance of an IrDA link at the IrLAP level using the concept of a frame's virtual transmission time. This indicates the time from the start of an initial frame transmission to the successful receipt of an in-sequence frame by the receiving station, thus incorporate the time for retransmissions and other frame delays using the probability of frame errors based on a specified link bit-error-rate (BER). The performance is examined in relation to the BER and other link parameter settings including link baud rate, minimum turn-around time, maximum turn-around time, maximum window size and packet data size. The model can thus be beneficial in determining the optimum parameter settings for a particular link and media environment. 2. The IrDA protocol stack The protocol stack of IrDA is shown in figure 1. There are three mandatory layers in the stack; the physical layer, the IrLAP layer and the IrLMP (IrDA Link Management Protocol) layer. The later consists of two components; the LM- MUX (Link Management Multiplexer) which provides access for multiple entities or application channels to independently use a single established IrLAP link, and the LM-IAS (Link Management Information Access Services) which provides a database of supported services which can be interrogated by a connecting device. Optional protocol components include Tiny TP, a lightweight transport component that provides credit based flow control and segmentation and reassemble functions, IrCOMM a serial cable emulation component which permits native serial
24 Performance Modelling of the IrDA Infrared Wireless Communications Protocol P. Barker, A.C. Boucouvalas, V. Vitsas Multimedia Communications Group School of Design, Engineering and Computing Bournemouth University Talbot Campus, Fern Barrow, Poole BH12 5BB, UK {pbarker, tboucouv, Revised September 2 Abstract We present a performance analysis of the IrDA (Infrared Data Association) IR data communications protocol using a mathematical throughput model based on the virtual transmission time of uni-directional IrDA data packets. The IrDA standard specifies a protocol stack for reliable short-range indoor IR wireless data communication between devices with the data link layer (IrLAP) being a HDLC derivative. The virtual transmission time provides the average end-to-end transmission time of a packet incorporating the time for retransmissions if packet errors occur or other enforced delays. Analytic results are produced for the 115.2kbit/s 4 Mbit/s and 16 Mbit/s versions. Results are given for throughput with varying link parameters of packet size, BER, data rate, minimum turn-around time and maximum turn-around time.
Performance modelling of the IrDA infrared wireless communications protocol
 INTERNATIONAL JOURNAL OF COMMUNICATION SYSTEMS Int. J. Commun. Syst. 2000; 13:589}604 Performance modelling of the IrDA infrared wireless communications protocol P. Barker*, A. C. Boucouvalas and V. Vitsas
INTERNATIONAL JOURNAL OF COMMUNICATION SYSTEMS Int. J. Commun. Syst. 2000; 13:589}604 Performance modelling of the IrDA infrared wireless communications protocol P. Barker*, A. C. Boucouvalas and V. Vitsas
A study of link processing time and propagation delay for IrDA links at Gbit/s data rate
 A study of link processing time and propagation delay for IrDA links at Gbit/s data rate P. Huang, P. Chatzimisios and A.C. Boucouvalas Multimedia Communications Research Group School of Design, Engineering
A study of link processing time and propagation delay for IrDA links at Gbit/s data rate P. Huang, P. Chatzimisios and A.C. Boucouvalas Multimedia Communications Research Group School of Design, Engineering
OPTIMUM WINDOW AND FRAME SIZE FOR IrDA LINKS
 OPTIMUM WINDOW AND FRAME SIZE FOR IrDA LINKS A.C. Boucouvalas and V.Vitsas Bournemouth University, Design, Engineering and Computing, Fern Barrow, Poole, Dorset, BH12 5BB UK {tboucouv, vvitsas} @bournemouth.ac.uk
OPTIMUM WINDOW AND FRAME SIZE FOR IrDA LINKS A.C. Boucouvalas and V.Vitsas Bournemouth University, Design, Engineering and Computing, Fern Barrow, Poole, Dorset, BH12 5BB UK {tboucouv, vvitsas} @bournemouth.ac.uk
OBEX and high speed IrDA links
 OBEX and high speed IrDA links Pi Huang and A. C. Boucouvalas Multimedia Communications Research Group School of Design, Engineering and Computing Bournemouth University, Fern Barrow, Poole, BH12 5BB,
OBEX and high speed IrDA links Pi Huang and A. C. Boucouvalas Multimedia Communications Research Group School of Design, Engineering and Computing Bournemouth University, Fern Barrow, Poole, BH12 5BB,
Optimization of IrDA IrLAP Link Access Protocol
 926 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 2, NO. 5, SEPTEMBER 2003 Optimization of IrDA IrLAP Link Access Protocol Vasileios Vitsas and Anthony C. Boucouvalas, Fellow, IEEE Abstract The widespread
926 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 2, NO. 5, SEPTEMBER 2003 Optimization of IrDA IrLAP Link Access Protocol Vasileios Vitsas and Anthony C. Boucouvalas, Fellow, IEEE Abstract The widespread
Modelling OBEX over IrDA Protocol Stack
 Modelling OBEX over IrDA Protocol Stack Pi Huang and A.C. Boucouvalas Multimedia Communications Research Group School of Design, Engineering and Computing Bournemouth University, Fern Barrow, Poole, BH12
Modelling OBEX over IrDA Protocol Stack Pi Huang and A.C. Boucouvalas Multimedia Communications Research Group School of Design, Engineering and Computing Bournemouth University, Fern Barrow, Poole, BH12
An Information Broadcasting System with Infrared Data. Communication Protocol
 An Information Broadcasting System with Infrared Data Communication Protocol DAWEI CAI YUJI SAITO YOSHIHIKO ABE Iwate Prefectural University Dept. of Information and Computer Science Takizawa, Iwate JAPAN
An Information Broadcasting System with Infrared Data Communication Protocol DAWEI CAI YUJI SAITO YOSHIHIKO ABE Iwate Prefectural University Dept. of Information and Computer Science Takizawa, Iwate JAPAN
Performance comparison of the IEEE and AIr infrared wireless MAC protocols
 Performance comparison of the IEEE 802.11 and AIr infrared wireless MAC protocols P. Barker, A.C. Boucouvalas Multimedia Communications Research Group chool of Design, Engineering & Computing Bournemouth
Performance comparison of the IEEE 802.11 and AIr infrared wireless MAC protocols P. Barker, A.C. Boucouvalas Multimedia Communications Research Group chool of Design, Engineering & Computing Bournemouth
Flow control: Ensuring the source sending frames does not overflow the receiver
 Layer 2 Technologies Layer 2: final level of encapsulation of data before transmission over a physical link responsible for reliable transfer of frames between hosts, hop by hop, i.e. on a per link basis
Layer 2 Technologies Layer 2: final level of encapsulation of data before transmission over a physical link responsible for reliable transfer of frames between hosts, hop by hop, i.e. on a per link basis
IrDA IrLAP Throughput Optimisation with Physical Layer Consideration
 IrDA IrLAP Throughput Optimisation with Physica Layer onsideration Abstract Barker, P. & Boucouvaas, A.. Mutimedia ommunications Research Group Schoo of Design, Engineering & omputing Bournemouth University,
IrDA IrLAP Throughput Optimisation with Physica Layer onsideration Abstract Barker, P. & Boucouvaas, A.. Mutimedia ommunications Research Group Schoo of Design, Engineering & omputing Bournemouth University,
Chapter 3. The Data Link Layer. Wesam A. Hatamleh
 Chapter 3 The Data Link Layer The Data Link Layer Data Link Layer Design Issues Error Detection and Correction Elementary Data Link Protocols Sliding Window Protocols Example Data Link Protocols The Data
Chapter 3 The Data Link Layer The Data Link Layer Data Link Layer Design Issues Error Detection and Correction Elementary Data Link Protocols Sliding Window Protocols Example Data Link Protocols The Data
Optical Communications
 Optical Communications Telecommunication Engineering School of Engineering University of Rome La Sapienza Rome, Italy 2004-2005 Lecture #12, June 15 2006 Wireless Optical Communications and Standards OUTLINE
Optical Communications Telecommunication Engineering School of Engineering University of Rome La Sapienza Rome, Italy 2004-2005 Lecture #12, June 15 2006 Wireless Optical Communications and Standards OUTLINE
An Efficient Selective-Repeat ARQ Scheme for Half-duplex Infrared Links under High Bit Error Rate Conditions
 This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE CCNC 26 proceedings. An Efficient Selective-Repeat ARQ Scheme for
This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE CCNC 26 proceedings. An Efficient Selective-Repeat ARQ Scheme for
Chapter 7: Data Link Control. Data Link Control Protocols
 Chapter 7: Data Link Control CS420/520 Axel Krings Page 1 Data Link Control Protocols Need layer of logic above Physical to manage exchange of data over a link frame synchronization flow control error
Chapter 7: Data Link Control CS420/520 Axel Krings Page 1 Data Link Control Protocols Need layer of logic above Physical to manage exchange of data over a link frame synchronization flow control error
Chapter 7: Data Link Control. CS420/520 Axel Krings Page 1
 Chapter 7: Data Link Control CS420/520 Axel Krings Page 1 Data Link Control Protocols Need layer of logic above Physical to manage exchange of data over a link frame synchronization flow control error
Chapter 7: Data Link Control CS420/520 Axel Krings Page 1 Data Link Control Protocols Need layer of logic above Physical to manage exchange of data over a link frame synchronization flow control error
INTERNET ARCHITECTURE & PROTOCOLS
 INTERNET ARCHITECTURE & PROTOCOLS Set # 02 Delivered By: Engr Tahir Niazi Need for Data Link Layer possibility of transmission errors receiver need to regulate the rate at which data arrive that's why
INTERNET ARCHITECTURE & PROTOCOLS Set # 02 Delivered By: Engr Tahir Niazi Need for Data Link Layer possibility of transmission errors receiver need to regulate the rate at which data arrive that's why
A Study of the Suitability of IrOBEX for High- Speed Exchange of Large Data Objects
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2003-12-05 A Study of the Suitability of Ir for High- Speed Exchange of Large Data Objects Casey T. Deccio casey@byu.net Joseph Ekstrom
Brigham Young University BYU ScholarsArchive All Faculty Publications 2003-12-05 A Study of the Suitability of Ir for High- Speed Exchange of Large Data Objects Casey T. Deccio casey@byu.net Joseph Ekstrom
Data link layer functions. 2 Computer Networks Data Communications. Framing (1) Framing (2) Parity Checking (1) Error Detection
 2 Computer Networks Data Communications Part 6 Data Link Control Data link layer functions Framing Needed to synchronise TX and RX Account for all bits sent Error control Detect and correct errors Flow
2 Computer Networks Data Communications Part 6 Data Link Control Data link layer functions Framing Needed to synchronise TX and RX Account for all bits sent Error control Detect and correct errors Flow
Data Link Layer (cont.) ( h h h ) (Sicherungsschicht) HDLC - 1.
 Data Link Layer (cont.) ( h h h ) (Sicherungsschicht) HDLC - 1 LOGICAL L LINK CONTROL MEDIUM ACCESS CONTROL PHYSICAL SIGNALING DATA LINK LAYER PHYSICAL LAYER ACCESS UNIT INTERFACE PHYSICAL MEDIA ATTACHMENT
Data Link Layer (cont.) ( h h h ) (Sicherungsschicht) HDLC - 1 LOGICAL L LINK CONTROL MEDIUM ACCESS CONTROL PHYSICAL SIGNALING DATA LINK LAYER PHYSICAL LAYER ACCESS UNIT INTERFACE PHYSICAL MEDIA ATTACHMENT
Data Link Control Protocols
 Protocols : Introduction to Data Communications Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 23 May 2012 Y12S1L07, Steve/Courses/2012/s1/its323/lectures/datalink.tex,
Protocols : Introduction to Data Communications Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 23 May 2012 Y12S1L07, Steve/Courses/2012/s1/its323/lectures/datalink.tex,
3. Data Link Layer 3-2
 3. Data Link Layer 3.1 Transmission Errors 3.2 Error Detecting and Error Correcting Codes 3.3 Bit Stuffing 3.4 Acknowledgments and Sequence Numbers 3.5 Flow Control 3.6 Examples: HDLC, PPP 3. Data Link
3. Data Link Layer 3.1 Transmission Errors 3.2 Error Detecting and Error Correcting Codes 3.3 Bit Stuffing 3.4 Acknowledgments and Sequence Numbers 3.5 Flow Control 3.6 Examples: HDLC, PPP 3. Data Link
Advanced Computer Networks. Rab Nawaz Jadoon DCS. Assistant Professor COMSATS University, Lahore Pakistan. Department of Computer Science
 Advanced Computer Networks Rab Nawaz Jadoon Department of Computer Science DCS COMSATS Institute of Information Technology Assistant Professor COMSATS University, Lahore Pakistan Advanced Computer Networks
Advanced Computer Networks Rab Nawaz Jadoon Department of Computer Science DCS COMSATS Institute of Information Technology Assistant Professor COMSATS University, Lahore Pakistan Advanced Computer Networks
(Sicherungsschicht) Chapter 5 (part 2) [Wa0001] HDLC - 1.
![(Sicherungsschicht) Chapter 5 (part 2) [Wa0001] HDLC - 1. (Sicherungsschicht) Chapter 5 (part 2) [Wa0001] HDLC - 1.](/thumbs/74/71111055.jpg) Data Link Layer (cont.) (Sicherungsschicht) Chapter 5 (part 2) [Wa0001] HDLC - 1 LOGICAL LINK CONTROL MEDIUM ACCESS CONTROL PHYSICAL SIGNALING DATA LINK LAYER PHYSICAL LAYER ACCESS UNIT INTERFACE PHYSICAL
Data Link Layer (cont.) (Sicherungsschicht) Chapter 5 (part 2) [Wa0001] HDLC - 1 LOGICAL LINK CONTROL MEDIUM ACCESS CONTROL PHYSICAL SIGNALING DATA LINK LAYER PHYSICAL LAYER ACCESS UNIT INTERFACE PHYSICAL
 ET3110 Networking and Communications UNIT 2: Communication Techniques and Data Link Control Protocol skong@itt-tech.edutech.edu Learning Objectives Identify methods of detecting errors. Use Hamming code
ET3110 Networking and Communications UNIT 2: Communication Techniques and Data Link Control Protocol skong@itt-tech.edutech.edu Learning Objectives Identify methods of detecting errors. Use Hamming code
SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY COMPUTER NETWORKS UNIT - II DATA LINK LAYER
 SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY COMPUTER NETWORKS UNIT - II DATA LINK LAYER 1. What are the responsibilities of data link layer? Specific responsibilities of
SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY COMPUTER NETWORKS UNIT - II DATA LINK LAYER 1. What are the responsibilities of data link layer? Specific responsibilities of
Data and Computer Communications
 Data and Computer Communications Chapter 7 Data Link Control Protocols Eighth Edition by William Stallings Lecture slides by Lawrie Brown Data Link Control Protocols "Great and enlightened one," said Ten-teh,
Data and Computer Communications Chapter 7 Data Link Control Protocols Eighth Edition by William Stallings Lecture slides by Lawrie Brown Data Link Control Protocols "Great and enlightened one," said Ten-teh,
Data Link Control Protocols
 Data Link Control Protocols need layer of logic above Physical to manage exchange of data over a link frame synchronization flow control error control addressing control and data link management Flow Control
Data Link Control Protocols need layer of logic above Physical to manage exchange of data over a link frame synchronization flow control error control addressing control and data link management Flow Control
William Stallings Data and Computer Communications. Chapter 7 Data Link Control
 William Stallings Data and Computer Communications Chapter 7 Data Link Control Flow Control Ensuring the sending entity does not overwhelm the receiving entity Preventing buffer overflow Transmission time
William Stallings Data and Computer Communications Chapter 7 Data Link Control Flow Control Ensuring the sending entity does not overwhelm the receiving entity Preventing buffer overflow Transmission time
The Wireless Connectivity Expert
 The Wireless Connectivity Expert 48511 Warm Springs Blvd., Suite 206, Fremont CA 94539 Tel: (510) 490-8024 Fax: (510) 623-7268 Website: http://www.actisys.com/ E-mail: irda-info@actisys.com ACT-IR100SD
The Wireless Connectivity Expert 48511 Warm Springs Blvd., Suite 206, Fremont CA 94539 Tel: (510) 490-8024 Fax: (510) 623-7268 Website: http://www.actisys.com/ E-mail: irda-info@actisys.com ACT-IR100SD
CCNA Exploration1 Chapter 7: OSI Data Link Layer
 CCNA Exploration1 Chapter 7: OSI Data Link Layer LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Explain the role of Data Link layer protocols in data transmission; Objectives Describe how the
CCNA Exploration1 Chapter 7: OSI Data Link Layer LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Explain the role of Data Link layer protocols in data transmission; Objectives Describe how the
TYPES OF ERRORS. Data can be corrupted during transmission. Some applications require that errors be detected and corrected.
 Data can be corrupted during transmission. Some applications require that errors be detected and corrected. TYPES OF ERRORS There are two types of errors, 1. Single Bit Error The term single-bit error
Data can be corrupted during transmission. Some applications require that errors be detected and corrected. TYPES OF ERRORS There are two types of errors, 1. Single Bit Error The term single-bit error
Data Link Layer (part 2)
 Data Link Layer (part 2)! Question - What is a major disadvantage of asynchronous transmission? Reference: Chapters 6 and 7 Stallings Study Guide 6! Question - What is a major disadvantage of asynchronous
Data Link Layer (part 2)! Question - What is a major disadvantage of asynchronous transmission? Reference: Chapters 6 and 7 Stallings Study Guide 6! Question - What is a major disadvantage of asynchronous
IrDA Infrared Communications: An Overview
 IrDA Infrared Communications: An Overview By Patrick J. Megowan David W. Suvak Charles D. Knutson Counterpoint Systems Foundry, Inc. {patm, davesu, knutson}@countersys.com Biographies: Patrick Megowan
IrDA Infrared Communications: An Overview By Patrick J. Megowan David W. Suvak Charles D. Knutson Counterpoint Systems Foundry, Inc. {patm, davesu, knutson}@countersys.com Biographies: Patrick Megowan
Data Link Control. Claude Rigault ENST Claude Rigault, ENST 11/3/2002. Data Link control 1
 Data Link Control Claude Rigault ENST claude.rigault@enst.fr Data Link control Data Link Control Outline General principles of Data Link Control HDLC Data Link control 2 General principles of Data Link
Data Link Control Claude Rigault ENST claude.rigault@enst.fr Data Link control Data Link Control Outline General principles of Data Link Control HDLC Data Link control 2 General principles of Data Link
Performance of UMTS Radio Link Control
 Performance of UMTS Radio Link Control Qinqing Zhang, Hsuan-Jung Su Bell Laboratories, Lucent Technologies Holmdel, NJ 77 Abstract- The Radio Link Control (RLC) protocol in Universal Mobile Telecommunication
Performance of UMTS Radio Link Control Qinqing Zhang, Hsuan-Jung Su Bell Laboratories, Lucent Technologies Holmdel, NJ 77 Abstract- The Radio Link Control (RLC) protocol in Universal Mobile Telecommunication
CS 5520/ECE 5590NA: Network Architecture I Spring Lecture 13: UDP and TCP
 CS 5520/ECE 5590NA: Network Architecture I Spring 2008 Lecture 13: UDP and TCP Most recent lectures discussed mechanisms to make better use of the IP address space, Internet control messages, and layering
CS 5520/ECE 5590NA: Network Architecture I Spring 2008 Lecture 13: UDP and TCP Most recent lectures discussed mechanisms to make better use of the IP address space, Internet control messages, and layering
Chapter 5 Peer-to-Peer Protocols. School of Info. Sci. & Eng. Shandong Univ..
 hapter 5 Peer-to-Peer Protocols School of Info. Sci. & Eng. Shandong Univ.. Outline 5. Peer-to-peer protocols and service models 5. RQ Protocols 5.3 Other daptation Functions Sliding Window Flow ontrol
hapter 5 Peer-to-Peer Protocols School of Info. Sci. & Eng. Shandong Univ.. Outline 5. Peer-to-peer protocols and service models 5. RQ Protocols 5.3 Other daptation Functions Sliding Window Flow ontrol
Chapter 5 Data-Link Layer: Wired Networks
 Sungkyunkwan University Chapter 5 Data-Link Layer: Wired Networks Prepared by Syed M. Raza and H. Choo 2018-Fall Computer Networks Copyright 2000-2018 Networking Laboratory Chapter 5 Outline 5.1 Introduction
Sungkyunkwan University Chapter 5 Data-Link Layer: Wired Networks Prepared by Syed M. Raza and H. Choo 2018-Fall Computer Networks Copyright 2000-2018 Networking Laboratory Chapter 5 Outline 5.1 Introduction
INTERNATIONAL TELECOMMUNICATION UNION. SERIES X: DATA COMMUNICATION NETWORKS: SERVICES AND FACILITIES, INTERFACES Interfaces
 INTERNATIONAL TELECOMMUNICATION UNION CCITT X.25 THE INTERNATIONAL TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE (11/1988) SERIES X: DATA COMMUNICATION NETWORKS: SERVICES AND FACILITIES, INTERFACES Interfaces
INTERNATIONAL TELECOMMUNICATION UNION CCITT X.25 THE INTERNATIONAL TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE (11/1988) SERIES X: DATA COMMUNICATION NETWORKS: SERVICES AND FACILITIES, INTERFACES Interfaces
Chapter 11 Data Link Control 11.1
 Chapter 11 Data Link Control 11.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 11-1 FRAMING The data link layer needs to pack bits into frames, so that each
Chapter 11 Data Link Control 11.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 11-1 FRAMING The data link layer needs to pack bits into frames, so that each
I. INTRODUCTION. each station (i.e., computer, telephone, etc.) directly connected to all other stations
 I. INTRODUCTION (a) Network Topologies (i) point-to-point communication each station (i.e., computer, telephone, etc.) directly connected to all other stations (ii) switched networks (1) circuit switched
I. INTRODUCTION (a) Network Topologies (i) point-to-point communication each station (i.e., computer, telephone, etc.) directly connected to all other stations (ii) switched networks (1) circuit switched
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 1 An Analytical Approach: Bianchi Model 2 Real Experimentations HoE on IEEE 802.11b Analytical Models Bianchi s Model Simulations ns-2 3 N links with the
Mohammad Hossein Manshaei manshaei@gmail.com 1393 1 An Analytical Approach: Bianchi Model 2 Real Experimentations HoE on IEEE 802.11b Analytical Models Bianchi s Model Simulations ns-2 3 N links with the
Chapter 11 Data Link Control 11.1
 Chapter 11 Data Link Control 11.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 11-1 1 FRAMING The data link layer needs to pack bits into frames,, so that
Chapter 11 Data Link Control 11.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 11-1 1 FRAMING The data link layer needs to pack bits into frames,, so that
This Lecture. BUS Computer Facilities Network Management. Line Discipline. Data Link Layer
 This Lecture US35 - Computer Facilities Network Management Synchronisation and interfacing insufficient by themselves. Need to provide: Flow control - allow the receiver to regulate the flow of data. Error
This Lecture US35 - Computer Facilities Network Management Synchronisation and interfacing insufficient by themselves. Need to provide: Flow control - allow the receiver to regulate the flow of data. Error
Institute of Computer Technology - Vienna University of Technology. L02 - Protocol Principles
 Protocol Principles Layering, CL versus CO Service, ARQ Techniques, Sequence umbers, Windowing, Flow Control Agenda Introduction 3 Layer Model and Service Types ARQ Techniques Introduction Idle RQ Continuous
Protocol Principles Layering, CL versus CO Service, ARQ Techniques, Sequence umbers, Windowing, Flow Control Agenda Introduction 3 Layer Model and Service Types ARQ Techniques Introduction Idle RQ Continuous
Basics of datacommunication
 Data communication I Lecture 1 Course Introduction About the course Basics of datacommunication How is information transported between digital devices? Essential data communication protocols Insight into
Data communication I Lecture 1 Course Introduction About the course Basics of datacommunication How is information transported between digital devices? Essential data communication protocols Insight into
CC-SCTP: Chunk Checksum of SCTP for Enhancement of Throughput in Wireless Network Environments
 CC-SCTP: Chunk Checksum of SCTP for Enhancement of Throughput in Wireless Network Environments Stream Control Transmission Protocol (SCTP) uses the 32-bit checksum in the common header, by which a corrupted
CC-SCTP: Chunk Checksum of SCTP for Enhancement of Throughput in Wireless Network Environments Stream Control Transmission Protocol (SCTP) uses the 32-bit checksum in the common header, by which a corrupted
INTERNATIONAL TELECOMMUNICATION UNION. SERIES Q: DIGITAL SUBSCRIBER SIGNALLING SYSTEM No. 1 (DSS 1), DATA LINK LAYER
 INTERNATIONAL TELECOMMUNICATION UNION CCITT Q.921 THE INTERNATIONAL TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE (11/1988) SERIES Q: DIGITAL SUBSCRIBER SIGNALLING SYSTEM No. 1 (DSS 1), DATA LINK LAYER
INTERNATIONAL TELECOMMUNICATION UNION CCITT Q.921 THE INTERNATIONAL TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE (11/1988) SERIES Q: DIGITAL SUBSCRIBER SIGNALLING SYSTEM No. 1 (DSS 1), DATA LINK LAYER
IrDA Implementation, Instant Solution and Certification
 IrDA Implementation, Instant Solution and Certification Dr. Keming W. Yeh (Yr2001, 2000 Chair, 2010 CoChair: IrDA Test/Inter-Op Committee), Dr. Lichen Wang (Yr2001, 2000 Chair, 2010 CoChair: IrDA Technical
IrDA Implementation, Instant Solution and Certification Dr. Keming W. Yeh (Yr2001, 2000 Chair, 2010 CoChair: IrDA Test/Inter-Op Committee), Dr. Lichen Wang (Yr2001, 2000 Chair, 2010 CoChair: IrDA Technical
Transport Protocols and TCP: Review
 Transport Protocols and TCP: Review CSE 6590 Fall 2010 Department of Computer Science & Engineering York University 1 19 September 2010 1 Connection Establishment and Termination 2 2 1 Connection Establishment
Transport Protocols and TCP: Review CSE 6590 Fall 2010 Department of Computer Science & Engineering York University 1 19 September 2010 1 Connection Establishment and Termination 2 2 1 Connection Establishment
Serial Communication. Spring, 2018 Prof. Jungkeun Park
 Serial Communication Spring, 2018 Prof. Jungkeun Park Serial Communication Serial communication Transfer of data over a single wire for each direction (send / receive) Process of sending data one bit at
Serial Communication Spring, 2018 Prof. Jungkeun Park Serial Communication Serial communication Transfer of data over a single wire for each direction (send / receive) Process of sending data one bit at
Infrared Data Association. Serial Infrared Link Access Protocol (IrLAP)
 Infrared Data Association Serial Infrared Link Access Protocol (IrLAP) Version 1.1 June 16, 1996 IBM Corporation Hewlett-Packard Company Apple Computer, Inc. Counterpoint Systems Foundry, Inc. Authors:
Infrared Data Association Serial Infrared Link Access Protocol (IrLAP) Version 1.1 June 16, 1996 IBM Corporation Hewlett-Packard Company Apple Computer, Inc. Counterpoint Systems Foundry, Inc. Authors:
Medium Access Protocols
 Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
ET4254 Communications and Networking 1
 Topic 10:- Local Area Network Overview Aims:- LAN topologies and media LAN protocol architecture bridges, hubs, layer 2 & 3 switches 1 LAN Applications (1) personal computer LANs low cost limited data
Topic 10:- Local Area Network Overview Aims:- LAN topologies and media LAN protocol architecture bridges, hubs, layer 2 & 3 switches 1 LAN Applications (1) personal computer LANs low cost limited data
ET4254 Communications and Networking 1
 Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Internet II. CS10 : Beauty and Joy of Computing. cs10.berkeley.edu. !!Senior Lecturer SOE Dan Garcia!!! Garcia UCB!
 cs10.berkeley.edu CS10 : Beauty and Joy of Computing Internet II!!Senior Lecturer SOE Dan Garcia!!!www.cs.berkeley.edu/~ddgarcia CS10 L17 Internet II (1)! Why Networks?! Originally sharing I/O devices
cs10.berkeley.edu CS10 : Beauty and Joy of Computing Internet II!!Senior Lecturer SOE Dan Garcia!!!www.cs.berkeley.edu/~ddgarcia CS10 L17 Internet II (1)! Why Networks?! Originally sharing I/O devices
4. Error correction and link control. Contents
 //2 4. Error correction and link control Contents a. Types of errors b. Error detection and correction c. Flow control d. Error control //2 a. Types of errors Data can be corrupted during transmission.
//2 4. Error correction and link control Contents a. Types of errors b. Error detection and correction c. Flow control d. Error control //2 a. Types of errors Data can be corrupted during transmission.
CS 123: Lecture 12, LANs, and Ethernet. George Varghese. October 24, 2006
 CS 123: Lecture 12, LANs, and Ethernet George Varghese October 24, 2006 Selective Reject Modulus failure Example w = 2, Max = 3 0 0 1 3 0 A(1) A(2) 1 0 retransmit A(1) A(2) buffer Case 1 Case 2 reject
CS 123: Lecture 12, LANs, and Ethernet George Varghese October 24, 2006 Selective Reject Modulus failure Example w = 2, Max = 3 0 0 1 3 0 A(1) A(2) 1 0 retransmit A(1) A(2) buffer Case 1 Case 2 reject
Data Link Layer. Learning Objectives. Position of the data-link layer. MCA 207, Data Communication & Networking
 Data Link Layer Bharati Vidyapeeth s Institute of Computer Applications and Management,New Delhi-63 by Vishal Jain U2. 1 Learning Objectives To introduce the design issues of data link layer. To discuss
Data Link Layer Bharati Vidyapeeth s Institute of Computer Applications and Management,New Delhi-63 by Vishal Jain U2. 1 Learning Objectives To introduce the design issues of data link layer. To discuss
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
 i ii Infrared Data Association Serial Infrared Link Access Protocol (IrLAP) Version 1.1 1 Document Status Version 1.1: This version has been approved by the IrDA. It incorporates all errata submitted
i ii Infrared Data Association Serial Infrared Link Access Protocol (IrLAP) Version 1.1 1 Document Status Version 1.1: This version has been approved by the IrDA. It incorporates all errata submitted
Exercises for the Lectures on Communication Networks
 Exercises for the Lectures on Prof. Jochen Seitz & Dipl.-Ing. Karsten Renhak Department of University of Technology Ilmenau October 5, 010 [Jochen.Seitz Karsten.Renhak]@tu-ilmenau.de Contents 1 Communication
Exercises for the Lectures on Prof. Jochen Seitz & Dipl.-Ing. Karsten Renhak Department of University of Technology Ilmenau October 5, 010 [Jochen.Seitz Karsten.Renhak]@tu-ilmenau.de Contents 1 Communication
CSMC 417. Computer Networks Prof. Ashok K Agrawala Ashok Agrawala Set 4. September 09 CMSC417 Set 4 1
 CSMC 417 Computer Networks Prof. Ashok K Agrawala 2009 Ashok Agrawala Set 4 1 The Data Link Layer 2 Data Link Layer Design Issues Services Provided to the Network Layer Framing Error Control Flow Control
CSMC 417 Computer Networks Prof. Ashok K Agrawala 2009 Ashok Agrawala Set 4 1 The Data Link Layer 2 Data Link Layer Design Issues Services Provided to the Network Layer Framing Error Control Flow Control
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 36 I/O : Networks 2008-04-25 TA Brian Zimmer CS61C L36 I/O : Networks (1) inst.eecs/~cs61c-th NASA To Develop Small Satellites NASA has
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 36 I/O : Networks 2008-04-25 TA Brian Zimmer CS61C L36 I/O : Networks (1) inst.eecs/~cs61c-th NASA To Develop Small Satellites NASA has
NWEN 243. Networked Applications. Layer 4 TCP and UDP
 NWEN 243 Networked Applications Layer 4 TCP and UDP 1 About the second lecturer Aaron Chen Office: AM405 Phone: 463 5114 Email: aaron.chen@ecs.vuw.ac.nz Transport layer and application layer protocols
NWEN 243 Networked Applications Layer 4 TCP and UDP 1 About the second lecturer Aaron Chen Office: AM405 Phone: 463 5114 Email: aaron.chen@ecs.vuw.ac.nz Transport layer and application layer protocols
Your favorite blog :www.vijay-jotani.weebly.com (popularly known as VIJAY JOTANI S BLOG..now in facebook.join ON FB VIJAY
 VISIT: Course Code : MCS-042 Course Title : Data Communication and Computer Network Assignment Number : MCA (4)/042/Assign/2014-15 Maximum Marks : 100 Weightage : 25% Last Dates for Submission : 15 th
VISIT: Course Code : MCS-042 Course Title : Data Communication and Computer Network Assignment Number : MCA (4)/042/Assign/2014-15 Maximum Marks : 100 Weightage : 25% Last Dates for Submission : 15 th
Agenda. Protocol Principles
 Agenda Protocol Principles Layering, CL vs. CO Protocols, Best-Effort vs. Reliable Services ARQ Techniques, Sequence umbers, Windowing, Bandwidth-Delay Product, Flow Control, HDLC Introduction ARQ Techniques
Agenda Protocol Principles Layering, CL vs. CO Protocols, Best-Effort vs. Reliable Services ARQ Techniques, Sequence umbers, Windowing, Bandwidth-Delay Product, Flow Control, HDLC Introduction ARQ Techniques
Chapter 3. The Data Link Layer
 Chapter 3 The Data Link Layer 1 Data Link Layer Algorithms for achieving reliable, efficient communication between two adjacent machines. Adjacent means two machines are physically connected by a communication
Chapter 3 The Data Link Layer 1 Data Link Layer Algorithms for achieving reliable, efficient communication between two adjacent machines. Adjacent means two machines are physically connected by a communication
Local Area Network Overview
 Local Area Network Overview Chapter 15 CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large systems (mainframes and
Local Area Network Overview Chapter 15 CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large systems (mainframes and
Summary of MAC protocols
 Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Chapter 15 Local Area Network Overview
 Chapter 15 Local Area Network Overview LAN Topologies Bus and Tree Bus: stations attach through tap to bus full duplex allows transmission and reception transmission propagates throughout medium heard
Chapter 15 Local Area Network Overview LAN Topologies Bus and Tree Bus: stations attach through tap to bus full duplex allows transmission and reception transmission propagates throughout medium heard
PROPOSAL OF MULTI-HOP WIRELESS LAN SYSTEM FOR QOS GUARANTEED TRANSMISSION
 PROPOSAL OF MULTI-HOP WIRELESS LAN SYSTEM FOR QOS GUARANTEED TRANSMISSION Phuc Khanh KIEU, Shinichi MIYAMOTO Graduate School of Engineering, Osaka University 2-1 Yamada-oka, Suita, Osaka, 565-871 JAPAN
PROPOSAL OF MULTI-HOP WIRELESS LAN SYSTEM FOR QOS GUARANTEED TRANSMISSION Phuc Khanh KIEU, Shinichi MIYAMOTO Graduate School of Engineering, Osaka University 2-1 Yamada-oka, Suita, Osaka, 565-871 JAPAN
ACT-IR8200P. IrDA Compliant Protocol Processor Preliminary Specification. Copyright 2003 ACTiSYS Corporation, All Rights Reserved
 48511 Warm Springs Blvd., Suite 206, Fremont, CA 94539 Tel: (510) 490-8024 Fax: (510) 623-7268 Website: http://www.actisys.com E-mail: irda-info@actisys.com IrDA Compliant Protocol Processor Preliminary
48511 Warm Springs Blvd., Suite 206, Fremont, CA 94539 Tel: (510) 490-8024 Fax: (510) 623-7268 Website: http://www.actisys.com E-mail: irda-info@actisys.com IrDA Compliant Protocol Processor Preliminary
INTERNATIONAL TELECOMMUNICATION UNION. SERIES X: DATA NETWORKS AND OPEN SYSTEM COMMUNICATION Public data networks Interfaces
 INTERNATIONAL TELECOMMUNICATION UNION ITU-T X.25 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (10/96) SERIES X: DATA NETWORKS AND OPEN SYSTEM COMMUNICATION Public data networks Interfaces Interface
INTERNATIONAL TELECOMMUNICATION UNION ITU-T X.25 TELECOMMUNICATION STANDARDIZATION SECTOR OF ITU (10/96) SERIES X: DATA NETWORKS AND OPEN SYSTEM COMMUNICATION Public data networks Interfaces Interface
Lecture (04 & 05) Packet switching & Frame Relay techniques Dr. Ahmed ElShafee
 Agenda Lecture (04 & 05) Packet switching & Frame Relay techniques Dr. Ahmed ElShafee Packet switching technique Packet switching protocol layers (X.25) Frame Relay ١ Dr. Ahmed ElShafee, ACU Fall 2011,
Agenda Lecture (04 & 05) Packet switching & Frame Relay techniques Dr. Ahmed ElShafee Packet switching technique Packet switching protocol layers (X.25) Frame Relay ١ Dr. Ahmed ElShafee, ACU Fall 2011,
Lecture (04 & 05) Packet switching & Frame Relay techniques
 Lecture (04 & 05) Packet switching & Frame Relay techniques Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU Fall 2011, Networks I Agenda Packet switching technique Packet switching protocol layers (X.25)
Lecture (04 & 05) Packet switching & Frame Relay techniques Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU Fall 2011, Networks I Agenda Packet switching technique Packet switching protocol layers (X.25)
Interface The exit interface a packet will take when destined for a specific network.
 The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
HDLC (High level Data Link Control)
 High-level Data Link Control HDLC (High level Data Link Control) Modem, EIA-232, HDLC Framing and Procedures Agenda Line Management, Modems Introduction HDLC Station Types, Modes of Operation Frame Format,
High-level Data Link Control HDLC (High level Data Link Control) Modem, EIA-232, HDLC Framing and Procedures Agenda Line Management, Modems Introduction HDLC Station Types, Modes of Operation Frame Format,
Line Protocol Basics. HDLC (High level Data Link Control) Agenda. Additional Issues
 Line Protocol Basics High-level Data Link Control HDLC (High level Data Link Control), EIA-232, HDLC Framing and Procedures line protocol basics already explained serial transmission techniques bit-synchronization
Line Protocol Basics High-level Data Link Control HDLC (High level Data Link Control), EIA-232, HDLC Framing and Procedures line protocol basics already explained serial transmission techniques bit-synchronization
Data Link Control. Outline. DLC functions
 Data Link Control #8 1 Outline functions Framing Error and flow control Performance of Example of a standard protocol- >H Open loop flow control 2 Data Link Layer Functions Data Link layer provides a error
Data Link Control #8 1 Outline functions Framing Error and flow control Performance of Example of a standard protocol- >H Open loop flow control 2 Data Link Layer Functions Data Link layer provides a error
The University of Sydney AUSTRALIA. Advanced Communication Networks
 The University of Sydney AUSTRALIA School of Electrical and Information Engineering Advanced Communication Networks Chapter 5 ISDN Data Link Layer Based on chapter 8 of Stallings ISDN-4e book Abbas Jamalipour
The University of Sydney AUSTRALIA School of Electrical and Information Engineering Advanced Communication Networks Chapter 5 ISDN Data Link Layer Based on chapter 8 of Stallings ISDN-4e book Abbas Jamalipour
3GPP TS V7.2.0 ( )
 TS 25.462 V7.2.0 (2007-03) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Radio Access Network; UTRAN Iuant interface: Signalling transport (Release 7) The present
TS 25.462 V7.2.0 (2007-03) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Radio Access Network; UTRAN Iuant interface: Signalling transport (Release 7) The present
or between microcontrollers)
 : Communication Interfaces in Embedded Systems (e.g., to interface with sensors and actuators or between microcontrollers) Spring 2016 : Communication Interfaces in Embedded Systems Spring (e.g., 2016
: Communication Interfaces in Embedded Systems (e.g., to interface with sensors and actuators or between microcontrollers) Spring 2016 : Communication Interfaces in Embedded Systems Spring (e.g., 2016
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 36 I/O : Networks TA Sameer The Yellow Dart Iyengar inst.eecs/~cs61c-ti Next year: Forget Elmo Get a Robot buddy New human-like robots that
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 36 I/O : Networks TA Sameer The Yellow Dart Iyengar inst.eecs/~cs61c-ti Next year: Forget Elmo Get a Robot buddy New human-like robots that
C H A P T E R GIGABIT ETHERNET PROTOCOL
 C H A P T E R GIGABIT ETHERNET PROTOCOL 2 39 2.1 Objectives of Research Ethernet protocol has been a robust and dominant technology and it is found to be present on more than 90 percent of all networked
C H A P T E R GIGABIT ETHERNET PROTOCOL 2 39 2.1 Objectives of Research Ethernet protocol has been a robust and dominant technology and it is found to be present on more than 90 percent of all networked
Telematics. 5rd Tutorial - LLC vs. MAC, HDLC, Flow Control, E2E-Arguments
 19540 - Telematics 5rd Tutorial - LLC vs. MAC, HDLC, Flow Control, E2E-Arguments Matthias Wa hlisch Department of Mathematics and Computer Science Institute of Computer Science 19. November, 2009 Institute
19540 - Telematics 5rd Tutorial - LLC vs. MAC, HDLC, Flow Control, E2E-Arguments Matthias Wa hlisch Department of Mathematics and Computer Science Institute of Computer Science 19. November, 2009 Institute
Reliable transmission of visible light communication data in lighting control networks
 IET Networks Research Article Reliable transmission of visible light communication data in lighting control networks ISSN 2047-4954 Received on 12th February 2017 Accepted on 12th March 2017 E-First on
IET Networks Research Article Reliable transmission of visible light communication data in lighting control networks ISSN 2047-4954 Received on 12th February 2017 Accepted on 12th March 2017 E-First on
10.1 SERIAL PORTS AND UARTS
 RS- serial ports have nine circuits, which can be used for transferring data and signalling. can emulate the serial cable line settings and status of an RS- serial port. provides multiple concurrent connections
RS- serial ports have nine circuits, which can be used for transferring data and signalling. can emulate the serial cable line settings and status of an RS- serial port. provides multiple concurrent connections
Outline: Connecting Many Computers
 Outline: Connecting Many Computers Last lecture: sending data between two computers This lecture: link-level network protocols (from last lecture) sending data among many computers 1 Review: A simple point-to-point
Outline: Connecting Many Computers Last lecture: sending data between two computers This lecture: link-level network protocols (from last lecture) sending data among many computers 1 Review: A simple point-to-point
Lecture 5. Homework 2 posted, due September 15. Reminder: Homework 1 due today. Questions? Thursday, September 8 CS 475 Networks - Lecture 5 1
 Lecture 5 Homework 2 posted, due September 15. Reminder: Homework 1 due today. Questions? Thursday, September 8 CS 475 Networks - Lecture 5 1 Outline Chapter 2 - Getting Connected 2.1 Perspectives on Connecting
Lecture 5 Homework 2 posted, due September 15. Reminder: Homework 1 due today. Questions? Thursday, September 8 CS 475 Networks - Lecture 5 1 Outline Chapter 2 - Getting Connected 2.1 Perspectives on Connecting
Impact of transmission errors on TCP performance. Outline. Random Errors
 Impact of transmission errors on TCP performance 1 Outline Impact of transmission errors on TCP performance Approaches to improve TCP performance Classification Discussion of selected approaches 2 Random
Impact of transmission errors on TCP performance 1 Outline Impact of transmission errors on TCP performance Approaches to improve TCP performance Classification Discussion of selected approaches 2 Random
Medium Access Control. IEEE , Token Rings. CSMA/CD in WLANs? Ethernet MAC Algorithm. MACA Solution for Hidden Terminal Problem
 Medium Access Control IEEE 802.11, Token Rings Wireless channel is a shared medium Need access control mechanism to avoid interference Why not CSMA/CD? 9/15/06 CS/ECE 438 - UIUC, Fall 2006 1 9/15/06 CS/ECE
Medium Access Control IEEE 802.11, Token Rings Wireless channel is a shared medium Need access control mechanism to avoid interference Why not CSMA/CD? 9/15/06 CS/ECE 438 - UIUC, Fall 2006 1 9/15/06 CS/ECE
Network Management & Monitoring
 Network Management & Monitoring Network Delay These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) End-to-end
Network Management & Monitoring Network Delay These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) End-to-end
Topics. Link Layer Services (more) Link Layer Services LECTURE 5 MULTIPLE ACCESS AND LOCAL AREA NETWORKS. flow control: error detection:
 1 Topics 2 LECTURE 5 MULTIPLE ACCESS AND LOCAL AREA NETWORKS Multiple access: CSMA/CD, CSMA/CA, token passing, channelization LAN: characteristics, i basic principles i Protocol architecture Topologies
1 Topics 2 LECTURE 5 MULTIPLE ACCESS AND LOCAL AREA NETWORKS Multiple access: CSMA/CD, CSMA/CA, token passing, channelization LAN: characteristics, i basic principles i Protocol architecture Topologies
Chapter 11 in Stallings 10 th Edition
 Local Area Network Overview Chapter 11 in Stallings 10 th Edition CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large
Local Area Network Overview Chapter 11 in Stallings 10 th Edition CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large
HDLC PROTOCOL. Michel GARDIE
 HDLC PROTOCOL Michel GARDIE INT/LOR/RIP October 15, 2007 The version of this document is temporary. There are still several mistakes. I'm sorry for that. email: michel.gardie@int-edu.eu 1985 FRANCE TELECOM
HDLC PROTOCOL Michel GARDIE INT/LOR/RIP October 15, 2007 The version of this document is temporary. There are still several mistakes. I'm sorry for that. email: michel.gardie@int-edu.eu 1985 FRANCE TELECOM
CHAPTER 15 LOCAL AREA NETWORKS ANSWERS TO QUESTIONS
 CHAPTER 15 LOCAL AREA NETWORKS ANSWERS TO QUESTIONS 15.1 Computer room networks require very high data rates and usually are concerned with transfer of large blocks of data. 15.2 Backend LAN: Backend networks
CHAPTER 15 LOCAL AREA NETWORKS ANSWERS TO QUESTIONS 15.1 Computer room networks require very high data rates and usually are concerned with transfer of large blocks of data. 15.2 Backend LAN: Backend networks
LANs Local Area Networks LANs provide an efficient network solution : To support a large number of stations Over moderately high speed
 Local Area Networks LANs provide an efficient network solution : To support a large number of stations Over moderately high speed With relatively small bit errors Multiaccess Protocols Communication among
Local Area Networks LANs provide an efficient network solution : To support a large number of stations Over moderately high speed With relatively small bit errors Multiaccess Protocols Communication among
Session Capabilities in OBEX
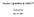 Session Capabilities in OBEX Version 0.14 July 16, 2002 Authors: David Suvak Contributors: Kevin Hendrix Extended Systems Extended Systems Revision History Revision Date Comments 0.1 30-May-01 Initial
Session Capabilities in OBEX Version 0.14 July 16, 2002 Authors: David Suvak Contributors: Kevin Hendrix Extended Systems Extended Systems Revision History Revision Date Comments 0.1 30-May-01 Initial
Data Link Layer. Overview. Links. Shivkumar Kalyanaraman
 Data Link Layer shivkuma@ecse.rpi.edu http://www.ecse.rpi.edu/homepages/shivkuma 1-1 Based in part upon the slides of Prof. Raj Jain (OSU) Overview The data link layer problem Error detection and correction
Data Link Layer shivkuma@ecse.rpi.edu http://www.ecse.rpi.edu/homepages/shivkuma 1-1 Based in part upon the slides of Prof. Raj Jain (OSU) Overview The data link layer problem Error detection and correction
