Ethernet Hub. Campus Network Design. Hubs. Sending and receiving Ethernet frames via a hub
|
|
|
- Leonard Garrison
- 6 years ago
- Views:
Transcription
1 Campus Network Design Thana Hongsuwan Ethernet Hub 2003, Cisco Systems, Inc. All rights reserved , Cisco Systems, Inc. All rights reserved. BCMSN v Sending and receiving Ethernet frames via a hub Hubs? 5555 So, what does a hub do when it receives information? Remember, a hub is nothing more than a multi-port repeater. Nope 5555 Nope The hub will flood it out all ports except for the incoming port. Hub is a layer 1 device. A hub does NOT look at layer 2 addresses, so it is fast in transmitting data. Disadvantage with hubs: A hub or series of hubs is a single collision domain. A collision will occur if any two or more devices transmit at the same time within the collision domain. More on this later. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v For me! Nope 2003, Cisco Systems, Inc. All rights reserved. BCMSN v
2 Hubs For me! Another disadvantage with hubs is that is take up unnecessary bandwidth on other links. Bridge 5555 Nope Wasted bandwidth Nope Nope 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Traffic and LAN Size Bridged LAN Segments A: total traffic 6 Mbps B: total traffic 5 Mbps A sw/ B: traffic 7 Mbps Bridge B sw/ A: traffic 6 Mbps Joining LAN segments with a hub or repeater increases traffic. All machines share the same media (same collision domain). A+B: total traffic 11 Mbps repeater A bridge only forwards packets when necessary. learns network addresses of machines connected to each port doesn t forward traffic between machines on same port provides packet buffering and retiming, reducing collisions does forward all broadcast traffic may forward multicast traffic 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
3 Transparent Bridging Types of Bridges Transparent bridges were first developed at Digital Equipment Corporation (Digital) in the early 1980s. Work into the IEEE standard. Transparent bridges are very popular in Ethernet/IEEE networks. When transparent bridges are powered on, they learn the workstation locations by analyzing the source address of incoming frames from all attached networks. If a bridge sees a frame arrive on port 1 from Host A, the bridge concludes that Host A can be reached through the segment connected to port 1. Through this process, transparent bridges build a table Transparent Bridge Remote bridge with identical data link protocol Can support different physical media Translating Bridge Connection with different data link protocol Frame conversion For example, Ethernet to Token ring or Token ring to Ethernet May require assembly and reassembly Transmission rate conversion 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Bridging and Switching Why Bridging and Switching? Bridges forward traffic based on MAC level address A bridge may perform protocol conversion or speed matching between different LAN types Bridges provides buffering of packets A is a bridge with all ports use the same frame type; also called a LAN to distinguish from an ATM or telecommunications Decrease traffic on LAN segments Extend LAN without increasing congestion Bridge different network protocols Speed matching Security Reliability: fault isolation and bandwidth balancing 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
4 LAN Extension Bridging Different Protocols Fast Ethernet 300 m 300 m Fast Ethernet Ethernet bridge Token Ring a can extend length limit of network, since it provides packet retiming and retransmission bridge: different media and protocol to extend length limit es are not subject to repeater count limit on ethernet a bridge can convert frame formats requires compatible network addresses, e.g. ethernet & token ring are OK, but not ethernet and ATM frame conversion may lose some information about the frame 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Protocol Conversion Problems Speed Matching Ethernet Frame 1 byte Start delimiter 1 byte SOH Token Ring Frame 1 Access control Destination Source Frame length Data address address CRC 1 Frame control Destination Source Frame End Frame Data address address CRC delimiter status Ethernet does not have frame address seen or copied bits (set by receiver in Token Ring Frame Status byte) Ethernet does not have priorities or access control flags Token Ring frame may be too long for ethernet Maximum throughput of ethernet and token ring not the same: some frames may be dropped Token Ring doesn t have a length field: bridge must buffer and compute Fast Ethernet hub 100 Mbps ethernet Gigabit Ethernet server Fast Ethernet server 10 Mbps Ethernet hub 10 Mbps ethernet A can connect segments operating at different speeds How to handle overload of a slow or busy segment? back pressure (false collisions) drop frames Ethernet es can support 10, 100 Mbps, and gigabit Bridging ethernets is simple: packet formats are the same 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
5 Security Ethernet Switches and Bridges Hub: shared media access Switch: selective access ooooh.. rats! A hub forwards all packets to all ports. Any host can listen to packets to/from another host, using programs like tcpdump, etherwatch, or snoop. A only forwards packets to port containing the destination host. Computers on other ports cannot eavesdrop. Address learning Forward/filter decision Loop avoidance 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Address Learning Abbreviated MAC addresses Switch operate in promiscuous mode Switches are also known as learning bridges or learning es. A has a source address table in cache (RAM) where it stores source MAC addresses after it learns about them. A receives an Ethernet frame and searches the source address table for the Destination MAC address. If it finds a match, it filters the frame by only sending it out that port. If there is not a match if floods it out all ports. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v No Destination Address in table, Flood 1 Abbreviated MAC addresses How does it learn source MAC addresses? First, the will see if the SA () is in it s table. If it is, it resets the timer (more in a moment). If it is NOT in the table it adds it, with the port number. Next, in our scenario, the will flood the frame out all other ports, because the DA is not in the source address table. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v
6 Destination Address in table, Filter Destination Address in table, Filter Abbreviate d MAC addresses Most communications involve some sort of client-server relationship or exchange of information. Now sends data back to. The sees if it has the SA stored. It does NOT so it adds it. (This will help next time sends to.) Next, it checks the DA and in our case it can filter the frame, by sending it only out port 1. Abbreviated MAC addresses Now, because both MAC addresses are in the s table, any information exchanged between and can be sent (filtered) out the appropriate port. What happens when two devices send to same destination? What if this was a hub? Where is (are) the collision domain(s) in this example? 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v No Collisions in Switch, Buffering Collision Domains Collision Domains Abbreviated MAC addresses Unlike a hub, a collision does NOT occur, which would cause the two PCs to have to retransmit the frames. Instead the buffers the frames and sends them out port #6 one at a time. The sending PCs have no idea that there was another PC that wanted to send to the same destination. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v Abbreviated MAC addresses When there is only one device on a port, the collision domain is only between the PC and the. (microsegment) With a full-duplex PC and port, there will be no collision, since the devices and the medium can send and receive at the same time. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v
7 Other Information How long are addresses kept in the? 5 minutes is common on most vendor es. How do computers know the Destination MAC address? ARP Caches and ARP Requests Abbreviated MAC addresses How many addresses can be kept in the table? Depends on the size of the cache, but 1,024 addresses is common. What about Layer 2 broadcasts? Layer 2 broadcasts (DA = all 1 s) is flooded out all ports. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v What happens here? Notice the Source Address Table has multiple entries for port # , Cisco Systems, Inc. All rights reserved. BCMSN v What happens here? What happens here? The filters the frame out port #1. But the hub is only a layer 1 device, so it floods it out all ports. Where is the collision domain? Collision Domain , Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
8 Mac Address Table Table Aging Mechanism Much of the performance of a bridge is depend on the design of the address table search algorithm. How big should the address table be? If the table is full, what should I do with new potential entries? 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v What is CAM? Can this method of learning addresses be extended to a network of bridges? Content Addressable Memory is a special kind of memory! Read operation in traditional memory: Input is address location of the content that we are interested in it. Output is the content of that address. In CAM it is the reverse: Input is associated with something stored in the memory. Output is location where the associated content is stored. Q. How does B2 see the network? A port 1 port 2 B1 X B port 1 port 2 B2 Y C Z 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
9 Can this method of learning addresses be extended to a network of bridges? Q. How does B2 see the network? A. B2 sees that A, X, B and Y are on port 1 (B1 is transparent!) Its forwarding table is A 1 B 1 C 2 X 1 Y 1 Z 2 port 1 port 2 B2 Ethernet latency Latency is the period of time from when the beginning of a frame enters to when the end of the frame exits the. Latency is directly related to the configured ing process and volume of traffic. A X B Y C Z 2003, Cisco Systems, Inc. All rights reserved. BCMSN v B2 Abbreviated MAC addresses 2003, Cisco Systems, Inc. All rights reserved. BCMSN v Memory buffering Memory Buffering Abbreviated MAC addresses An Ethernet may use a buffering technique to store and forward frames. Buffering may also be used when the destination port is busy. The area of memory where the stores the data is called the memory buffer. This memory buffer can use two methods for forwarding frame: port-based memory buffering shared memory buffering In port-based memory buffering frames are stored in queues that are linked to specific incoming ports. Shared memory buffering deposits all frames into a common memory buffer which all the ports on the share. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
10 Two ing methods Transmitting Frames Cut-Through Switch checks destination address and immediately begins forwarding frame. Store and Forward Complete frame is received and checked before forwarding. Store-and-forward The entire frame is received before any forwarding takes place. The destination and source addresses are read and filters are applied before the frame is forwarded. CRC Check done Cut-through The frame is forwarded through the before the entire frame is received. This mode decreases the latency of the transmission, but also reduces error detection. Depends on the model of the. Fragment-Free Switch checks the first 64 bytes, then immediately begins forwarding frame. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Cut-through Cut-through : Fragment Free Cut-through Fast-forward Offers the lowest level of latency. Fast-forward ing immediately forwards a packet after reading the destination address. There may be times when packets are relayed with errors. Although this occurs infrequently and the destination network adapter will discard the faulty packet upon receipt. Cut-through Fragment-free Fragment-free ing filters out collision fragments before forwarding begins. In a properly functioning network, collision fragments must be smaller than 64 bytes. Anything greater than 64 bytes is a valid packet and is usually received without error. Fragment-free ing waits until the packet is determined not to be a collision fragment before forwarding. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
11 Bridge performance Ethernet Hubs vs. Ethernet Switches A bridge performs two performance-intensive operations: It implements the decision-making algorithms table lookup, filter/forward decision, and table maintenance. The worst case situation : every port bombarded with the maximum number of frame. This generally occurs with minimum length frames. (64 bytes) How maximum rate of forwarding for 10, 100,1000 Mb/s Bridge that can performs, call Wire Speed It move data among its ports. (data flow) From data flow perspective, the worst case is to have the longest possible frames, Bridge with 24 ports of 100 Mb/s = 24 x 100 Mb/s = 2.4 Gb/s Bridge that can performs, call Non Blocking An Ethernet is a packet for Ethernet frames Buffering of frames prevents collisions. Each port is isolated and builds its own collision domain An Ethernet Hub does not perform buffering: Collisions occur if two frames arrive at the same time. Hub Switch Input Buffers HighSpeed Backplane Output Buffers 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Ethernet Hubs vs. Ethernet Switches Full- and Half-Duplex Full- and Half-Duplex Half-duplex: send or receive, one at a time. Full-duplex: send and receive simultaneously. 10 Mbps Ethernet supports half-duplex; fullduplex is not consistently implemented. 100 Mbps supports half- and full-duplex. A repeater can only operate in half-duplex mode. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
12 Ethernet Duplex Mismatch Half-Duplex Design One of the most common causes of performance issues on 10/100Mb Ethernet links is when one port on the link is operating at half-duplex while the other port is operating at full-duplex. If one end of a connection (device or Ethernet ) is set for auto-negotiation, and fails to see auto-negotiation at the other end, the former sets itself to the default, half-duplex. Auto-negotiation can sometimes fail, even when both sides are set to auto (although this isn t as prevalent as in the past). Ethernet Controller Collision Detection Ethernet NIC Tx Loopback Rx Transmit Receive Tx Loopback Rx Collision Detection Ethernet NIC Ethernet Controller Ethernet physical connector provides several circuits Most important are TX (transmit), RX (receive), and CD (collision detection) 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Full-Duplex Ethernet Design Auto-Negotiation Eases Configuration Full Duplex Ethernet Controller Collision Detection Tx Loopback Rx TX RX Loopback Full Duplex Ethernet Controller Transmit circuit connects directly to receive circuit No collisions Significant performance improvement Eliminates contention on Ethernet point-to-point links Uses a single port for each full-duplex connection Tx Rx Collision Detection Starting from Fast Ethernet For UTP cables Auto negotiation about duplex mode (half or full), maximum speed (10 or 100 Mbps), and flow control support. Avoid configuration headache. The same RJ45 jack can support 10 or 100Mbps and half or full duplex mode, how do you know which setting you should use when you plug your RJ45 into a hub or a s port? So, the best setting that you should choose is autonegotiation. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
13 Auto-Negotiation Message Format Auto-Negotiation Message Transfer Because link speed is one of the parameter that needs to negotiate, the auto-negotiation message cannot be transferred at a chosen speed (e.g., 10 or 100 Mbps). Instead, it is transmitted at a predetermined clock rate. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Switch Congestion Flow Controls Needed When Ethernets Switches Are Used When a hub is used to connect all sending hosts (halfduplex mode), Ethernet s MAC algorithm is an effective flow/congestion control (backoff) and retransmission (up to 16 times) method. However, when a is used and full-duplex mode is used, each host now has its own collision domain and no longer works. Frames now may be lost due to buffer overflow inside the. Hosts no longer know this type of collision. Congestion control cannot automatically be performed. Also, retransmission cannot automatically be performed. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
14 Backpressure Can Be Used In Half- Duplex Mode IEEE 802.3x Flow Control If a uses half-duplex mode to connect to hosts, although each host has its own collision domain, we can use some methods to ask sending hosts to slow down their sending rates: Force collisions with incoming frames Make it appear as if the channel is busy If a uses full-duplex mode, the above two methods won t work. We need an explicit flow control for ed full-duplex Ethernet es. Introduced for Fast and Gigabit Ethernets. Introduce special MAC-layer control packets (PAUSE packets) to enable or disable frame transmission. Thus a more generic MAC framework is defined and an entity called (MAC Control) is introduced. MAC Control is responsible for generating, sending, receiving, and performing the PAUSE operation. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v IEEE 802.3x Architecture MAC Control Frame Format 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
15 PAUSE Frame Pause Time Pause_time field: number of pause-quanta (from 0 to 65535) which indicate the pause time pause-quanta = 512 bit time speed equal or less than 100 Mb/s T-Pause in bit time = pause-quanta * 512 Speed greather than 100 Mb/s T-Pause in bit time = pause-quanta * 512 * , Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v PAUSE Function PAUSE Frame Implementation Implement a simple stop-start flow control scheme. If a device wants to temporarily inhibit incoming frames, it sends a PAUSE frame to the full-duplex partner. This PAUSE frame contains a parameter indicating the length of time the partner should wait before sending more frames. If the device wants to cancel the timer at its partner which is set up by its previous PAUSE frame, the device can send another PAUSE frame that contains a parameter of zero time. PAUSE frames have higher priority over normal data frames. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
16 Must Stop Transmission in 512 Bit Time Buffer Thresholds to Control When to Issue PAUSE Frames After receiving a PAUSE frame, the receiver has 512 bit time to decode it. No more new transmission is allowed after this 512 bit time period. The buffer space (above the high watermark and below the low watermark) should be larger than link RTT * link BW. Otherwise, frames may be dropped or link utilization may not be 100%. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Input-Buffered Switches Assumed for IEEE 802.3x IEEE 802.3x is a linklevel flow control scheme. It uses the buffer occupancy level of an input port to determine whether to inhibit frames from incoming. Unfortunately, this scheme does not work for output-buffered. (Why? because there will be no queue in input ports.) IEEE 802.3x May Cause Low Link Utilization IEEE 802.3x is a link-level flow control applied to input-buffered es. If the input-buffered has the HOL blocking problem, then using IEEE 802.3x will not further lower the link utilization. (It is already low.) However, if the input port uses virtual output queuing (one queue for each output port) to avoid the HOL blocking problem, using IEEE 802.3x may further lower the link utilization. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
17 Low Link Utilization Example Basic Switch Specification (TL-SG1016D) Output port 1 is busy or blocked all the time. Switch B Switch A P1, P1, P1, P1 Output port 2 is idle. PAUSE P1 P2 P2 P2 After receiving the PAUSE frame, A cannot send any more frame to B. However, sending P2 should be allowed because P2 can be immediately forwarded when it arrives at B. 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Switch Specification (TL-SG1016D) 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
18 Cisco 100 Series 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v Cisco 100 Series Cisco 100 Series 2003, Cisco Systems, Inc. All rights reserved. BCMSN v , Cisco Systems, Inc. All rights reserved. BCMSN v
19 End. 2003, Cisco Systems, Inc. All rights reserved. 1-73
Introducing Campus Networks
 Cisco Enterprise Architecture Introducing Campus Networks 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Campus Data Center Combines switching
Cisco Enterprise Architecture Introducing Campus Networks 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Campus Data Center Combines switching
Chapter 5: Ethernet. Introduction to Networks - R&S 6.0. Cisco Networking Academy. Mind Wide Open
 Chapter 5: Ethernet Introduction to Networks - R&S 6.0 Cisco Networking Academy Mind Wide Open Chapter 5 - Sections 5.1 Ethernet Protocol Describe the Ethernet MAC address and frame fields 5.2 LAN Switches
Chapter 5: Ethernet Introduction to Networks - R&S 6.0 Cisco Networking Academy Mind Wide Open Chapter 5 - Sections 5.1 Ethernet Protocol Describe the Ethernet MAC address and frame fields 5.2 LAN Switches
Chapter 9. Ethernet. Part II
 Chapter 9 Ethernet Part II CCNA1-1 Chapter 9-2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks must go
Chapter 9 Ethernet Part II CCNA1-1 Chapter 9-2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks must go
More on LANS. LAN Wiring, Interface
 More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
Chapter 2. Switch Concepts and Configuration. Part I
 Chapter 2 Switch Concepts and Configuration Part I CCNA3-1 Chapter 2-1 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor,
Chapter 2 Switch Concepts and Configuration Part I CCNA3-1 Chapter 2-1 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor,
Lecture 8: Switched Ethernet and Collision Domains
 Lecture 8: Switched Ethernet and Collision Domains Dr. Mohammed Hawa Electrical Engineering Department University of Jordan EE426: Communication Networks Ethernet Installations 2 1 Twisted Pair and Fiber
Lecture 8: Switched Ethernet and Collision Domains Dr. Mohammed Hawa Electrical Engineering Department University of Jordan EE426: Communication Networks Ethernet Installations 2 1 Twisted Pair and Fiber
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next Thursday, Sep 25th Today: Link Layer
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next Thursday, Sep 25th Today: Link Layer
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Administrivia Homework I out later today, due next Thursday Today: Link Layer (cont.)
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Administrivia Homework I out later today, due next Thursday Today: Link Layer (cont.)
Interface The exit interface a packet will take when destined for a specific network.
 The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
Chapter 4 NETWORK HARDWARE
 Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Part3. Local Area Networks (LAN)
 Part3 Local Area Networks (LAN) LAN Characteristics Small geographical area Relatively high data rate Single management Topologies Bus, star, ring Specifications at physical and data link layer mostly
Part3 Local Area Networks (LAN) LAN Characteristics Small geographical area Relatively high data rate Single management Topologies Bus, star, ring Specifications at physical and data link layer mostly
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next ursday, Sep 27th Today: Link Layer
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Janno< Administrivia Homework I out later today, due next ursday, Sep 27th Today: Link Layer
Objectives. Hexadecimal Numbering and Addressing. Ethernet / IEEE LAN Technology. Ethernet
 2007 Cisco Systems, Inc. All rights reserved. Cisco Public Objectives Ethernet Network Fundamentals Chapter 9 ITE PC v4.0 Chapter 1 1 Introduce Hexadecimal number system Describe the features of various
2007 Cisco Systems, Inc. All rights reserved. Cisco Public Objectives Ethernet Network Fundamentals Chapter 9 ITE PC v4.0 Chapter 1 1 Introduce Hexadecimal number system Describe the features of various
Computer Networks Principles LAN - Ethernet
 Computer Networks Principles LAN - Ethernet Prof. Andrzej Duda duda@imag.fr http://duda.imag.fr 1 Interconnection structure - layer 3 interconnection layer 3 router subnetwork 1 interconnection layer 2
Computer Networks Principles LAN - Ethernet Prof. Andrzej Duda duda@imag.fr http://duda.imag.fr 1 Interconnection structure - layer 3 interconnection layer 3 router subnetwork 1 interconnection layer 2
Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs.
 Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
19: Networking. Networking Hardware. Mark Handley
 19: Networking Mark Handley Networking Hardware Lots of different hardware: Modem byte at a time, FDDI, SONET packet at a time ATM (including some DSL) 53-byte cell at a time Reality is that most networking
19: Networking Mark Handley Networking Hardware Lots of different hardware: Modem byte at a time, FDDI, SONET packet at a time ATM (including some DSL) 53-byte cell at a time Reality is that most networking
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca
 CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Today: Link Layer (cont.) Framing Reliability Error correction Sliding window Medium
CSCI-1680 Link Layer Wrap-Up Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Today: Link Layer (cont.) Framing Reliability Error correction Sliding window Medium
CSCI Computer Networks
 CSCI-1680 - Computer Networks Link Layer III: LAN & Switching Chen Avin Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti, Peterson & Davie, Rodrigo Fonseca Today: Link Layer (cont.)
CSCI-1680 - Computer Networks Link Layer III: LAN & Switching Chen Avin Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti, Peterson & Davie, Rodrigo Fonseca Today: Link Layer (cont.)
CCNA Exploration Network Fundamentals. Chapter 09 Ethernet
 CCNA Exploration Network Fundamentals Chapter 09 Ethernet Updated: 07/07/2008 1 9.0.1 Introduction 2 9.0.1 Introduction Internet Engineering Task Force (IETF) maintains the functional protocols and services
CCNA Exploration Network Fundamentals Chapter 09 Ethernet Updated: 07/07/2008 1 9.0.1 Introduction 2 9.0.1 Introduction Internet Engineering Task Force (IETF) maintains the functional protocols and services
Internetwork Basic. Possible causes of LAN traffic congestion are
 Internetworking 1 C H A P T E R 2 Internetworking Basics Internetworking Model The OSI Reference Model Ethernet Networking Wireless Networking Data Encapsulation Topic 3 1 Internetwork Basic 4 Possible
Internetworking 1 C H A P T E R 2 Internetworking Basics Internetworking Model The OSI Reference Model Ethernet Networking Wireless Networking Data Encapsulation Topic 3 1 Internetwork Basic 4 Possible
Image courtesy Cisco Systems, Inc. Illustration of a Cisco Catalyst switch
 by Jeff Tyson If you have read other HowStuffWorks articles on networking or the Internet, then you know that a typical network consists of nodes (computers), a connecting medium (wired or wireless) and
by Jeff Tyson If you have read other HowStuffWorks articles on networking or the Internet, then you know that a typical network consists of nodes (computers), a connecting medium (wired or wireless) and
Switched Ethernet Virtual LANs
 Switched Ethernet Virtual LANs Computer Networks Lecture 4 http://goo.gl/pze5o8 Switched Ethernet 2 LAN Switches Behave as bridges (operates in the logical tree topology) Switching is implemented by hardware
Switched Ethernet Virtual LANs Computer Networks Lecture 4 http://goo.gl/pze5o8 Switched Ethernet 2 LAN Switches Behave as bridges (operates in the logical tree topology) Switching is implemented by hardware
Chapter 9 Ethernet Part 1
 Chapter 9 Ethernet Part 1 Introduction to Ethernet Ethernet Local Area Networks (LANs) LAN (Local Area Network) - A computer network connected through a wired or wireless medium by networking devices (s,
Chapter 9 Ethernet Part 1 Introduction to Ethernet Ethernet Local Area Networks (LANs) LAN (Local Area Network) - A computer network connected through a wired or wireless medium by networking devices (s,
Configuring Interfaces and Circuits
 CHAPTER 5 This chapter describes how to configure the CSS interfaces and circuits and how to bridge interfaces to Virtual LANs (VLANs). Information in this chapter applies to all CSS models, except where
CHAPTER 5 This chapter describes how to configure the CSS interfaces and circuits and how to bridge interfaces to Virtual LANs (VLANs). Information in this chapter applies to all CSS models, except where
Data Link Layer. Our goals: understand principles behind data link layer services: instantiation and implementation of various link layer technologies
 Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
Medium Access Protocols
 Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Data Link Layer, Part 5. Medium Access Control
 CS 455 Medium Access Control, Page 1 Data Link Layer, Part 5 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang s courses at GMU
CS 455 Medium Access Control, Page 1 Data Link Layer, Part 5 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang s courses at GMU
Summary of MAC protocols
 Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Layer 2 functionality bridging and switching
 Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Section 3 Understanding Ethernet and Switch Operations
 Section 3 Understanding Ethernet and Switch Operations Ethernet is the technology of choice for today s LANs. It is fast, has low costs, and is easy to maintain. Today s Ethernet standards support speeds
Section 3 Understanding Ethernet and Switch Operations Ethernet is the technology of choice for today s LANs. It is fast, has low costs, and is easy to maintain. Today s Ethernet standards support speeds
Introduction to Ethernet. Guy Hutchison 8/30/2006
 Introduction to Ethernet Guy Hutchison 8/30/2006 What is Ethernet? Local area transport protocol Layer 2 of the OSI stack Zero/minimal configuration Low-cost, high performance Best-effort delivery Original
Introduction to Ethernet Guy Hutchison 8/30/2006 What is Ethernet? Local area transport protocol Layer 2 of the OSI stack Zero/minimal configuration Low-cost, high performance Best-effort delivery Original
Chapter 5 Reading Organizer After completion of this chapter, you should be able to:
 Chapter 5 Reading Organizer After completion of this chapter, you should be able to: Describe the operation of the Ethernet sublayers. Identify the major fields of the Ethernet frame. Describe the purpose
Chapter 5 Reading Organizer After completion of this chapter, you should be able to: Describe the operation of the Ethernet sublayers. Identify the major fields of the Ethernet frame. Describe the purpose
Switching & ARP Week 3
 Switching & ARP Week 3 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 Many Slides courtesy of Tony Chen 1 Ethernet Using Switches In the last few years, switches have quickly
Switching & ARP Week 3 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 Many Slides courtesy of Tony Chen 1 Ethernet Using Switches In the last few years, switches have quickly
Data Link Layer, Part 3 Medium Access Control. Preface
 Data Link Layer, Part 3 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make a single machine-readable
Data Link Layer, Part 3 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make a single machine-readable
Cajun P550/P880 Manger User Guide
 Cajun P550/P880 Manger User Guide March 2001 Cajun P550/P880 5.1 Manager User Guide Copyright 2001 Avaya Inc. ALL RIGHTS RESERVED The products, specifications, and other technical information regarding
Cajun P550/P880 Manger User Guide March 2001 Cajun P550/P880 5.1 Manager User Guide Copyright 2001 Avaya Inc. ALL RIGHTS RESERVED The products, specifications, and other technical information regarding
Chapter 6 Connecting Device
 Computer Networks Al-Mustansiryah University Elec. Eng. Department College of Engineering Fourth Year Class Chapter 6 Connecting Device 6.1 Functions of network devices Separating (connecting) networks
Computer Networks Al-Mustansiryah University Elec. Eng. Department College of Engineering Fourth Year Class Chapter 6 Connecting Device 6.1 Functions of network devices Separating (connecting) networks
1: Review Of Semester Provide an overview of encapsulation.
 1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
IEEE Ethernet. Eric Karlsson Thomas Karlsson Morgan Kejerhag
 IEEE 802.3 - Ethernet Eric Karlsson Thomas Karlsson Morgan Kejerhag Today s Presentation Switching and bridging Auto negotiation Power-over-Ethernet Ethernet Performance Ethernet in WAN Switching and Bridging
IEEE 802.3 - Ethernet Eric Karlsson Thomas Karlsson Morgan Kejerhag Today s Presentation Switching and bridging Auto negotiation Power-over-Ethernet Ethernet Performance Ethernet in WAN Switching and Bridging
CS 43: Computer Networks Switches and LANs. Kevin Webb Swarthmore College December 5, 2017
 CS 43: Computer Networks Switches and LANs Kevin Webb Swarthmore College December 5, 2017 Ethernet Metcalfe s Ethernet sketch Dominant wired LAN technology: cheap $20 for NIC first widely used LAN technology
CS 43: Computer Networks Switches and LANs Kevin Webb Swarthmore College December 5, 2017 Ethernet Metcalfe s Ethernet sketch Dominant wired LAN technology: cheap $20 for NIC first widely used LAN technology
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin,
 Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Some portions courtesy Srini Seshan or David Wetherall
 CSE 123 Computer Networks Fall 2009 Lecture 6: Data-Link III: Hubs, Bridges and Switches Some portions courtesy Srini Seshan or David Wetherall Misc Homework solutions have been posted I ll post a sample
CSE 123 Computer Networks Fall 2009 Lecture 6: Data-Link III: Hubs, Bridges and Switches Some portions courtesy Srini Seshan or David Wetherall Misc Homework solutions have been posted I ll post a sample
Reminder: Datalink Functions Computer Networking. Datalink Architectures
 Reminder: Datalink Functions 15-441 15 441 15-641 Computer Networking Lecture 5 Media Access Control Peter Steenkiste Fall 2015 www.cs.cmu.edu/~prs/15-441-f15 Framing: encapsulating a network layer datagram
Reminder: Datalink Functions 15-441 15 441 15-641 Computer Networking Lecture 5 Media Access Control Peter Steenkiste Fall 2015 www.cs.cmu.edu/~prs/15-441-f15 Framing: encapsulating a network layer datagram
Principles behind data link layer services
 Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
ECE 333: Introduction to Communication Networks Fall Lecture 19: Medium Access Control VII
 ECE : Introduction to Communication Networks Fall 2002 Lecture 9: Medium Access Control VII More on token ring networks LAN bridges and switches. More on token rings In the last lecture we began discussing
ECE : Introduction to Communication Networks Fall 2002 Lecture 9: Medium Access Control VII More on token ring networks LAN bridges and switches. More on token rings In the last lecture we began discussing
Introduction to Networking Devices
 Introduction to Networking Devices Objectives Explain the uses, advantages, and disadvantages of repeaters, hubs, wireless access points, bridges, switches, and routers Define the standards associated
Introduction to Networking Devices Objectives Explain the uses, advantages, and disadvantages of repeaters, hubs, wireless access points, bridges, switches, and routers Define the standards associated
STEVEN R. BAGLEY PACKETS
 STEVEN R. BAGLEY PACKETS INTRODUCTION Talked about how data is split into packets Allows it to be multiplexed onto the network with data from other machines But exactly how is it split into packets and
STEVEN R. BAGLEY PACKETS INTRODUCTION Talked about how data is split into packets Allows it to be multiplexed onto the network with data from other machines But exactly how is it split into packets and
NT1210 Introduction to Networking. Unit 5:
 NT1210 Introduction to Networking Unit 5: Chapter 5, Ethernet LANs 1 Objectives Identify the major needs and stakeholders for computer networks and network applications. Identify the classifications of
NT1210 Introduction to Networking Unit 5: Chapter 5, Ethernet LANs 1 Objectives Identify the major needs and stakeholders for computer networks and network applications. Identify the classifications of
Module 5. Broadcast Communication Networks. Version 2 CSE IIT, Kharagpur
 Module 5 Broadcast Communication Networks Lesson 5 High Speed LANs Token Ring Based Specific Instructional Objectives On completion, the student will be able to: Explain different categories of High Speed
Module 5 Broadcast Communication Networks Lesson 5 High Speed LANs Token Ring Based Specific Instructional Objectives On completion, the student will be able to: Explain different categories of High Speed
FCC COMPLIANCE STATEMENT
 FCC COMPLIANCE STATEMENT This equipment has been tested and found to comply with the limits of a Class A computing devices, pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable
FCC COMPLIANCE STATEMENT This equipment has been tested and found to comply with the limits of a Class A computing devices, pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable
Hubs. twisted pair. hub. 5: DataLink Layer 5-1
 Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at : adapters detect collisions provides net management
Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at : adapters detect collisions provides net management
Designing the Switched Workgroup 3-1
 This chapter covers the following topics: Selecting An Appropriate Switch For Your Network The HP Family of AdvanceStack Switches Understanding Switching Technology Switch Operations Network Switch Market
This chapter covers the following topics: Selecting An Appropriate Switch For Your Network The HP Family of AdvanceStack Switches Understanding Switching Technology Switch Operations Network Switch Market
Media Access Control (MAC) Sub-layer and Ethernet
 Media Access Control (MAC) Sub-layer and Ethernet Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF MAC Sub-layer The MAC sub-layer is a sub-layer
Media Access Control (MAC) Sub-layer and Ethernet Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF MAC Sub-layer The MAC sub-layer is a sub-layer
Full file at
 Guide to Networking Essentials, Sixth Edition 2-1 Chapter 2 Network Hardware Essentials At a Glance Instructor s Manual Table of Contents Overview Objectives Tips Quick Quizzes Class Discussion Topics
Guide to Networking Essentials, Sixth Edition 2-1 Chapter 2 Network Hardware Essentials At a Glance Instructor s Manual Table of Contents Overview Objectives Tips Quick Quizzes Class Discussion Topics
Introduction to Routers and LAN Switches
 Introduction to Routers and LAN Switches Session 3048_05_2001_c1 2001, Cisco Systems, Inc. All rights reserved. 3 Prerequisites OSI Model Networking Fundamentals 3048_05_2001_c1 2001, Cisco Systems, Inc.
Introduction to Routers and LAN Switches Session 3048_05_2001_c1 2001, Cisco Systems, Inc. All rights reserved. 3 Prerequisites OSI Model Networking Fundamentals 3048_05_2001_c1 2001, Cisco Systems, Inc.
Part 5: Link Layer Technologies. CSE 3461: Introduction to Computer Networking Reading: Chapter 5, Kurose and Ross
 Part 5: Link Layer Technologies CSE 3461: Introduction to Computer Networking Reading: Chapter 5, Kurose and Ross 1 Outline PPP ATM X.25 Frame Relay 2 Point to Point Data Link Control One sender, one receiver,
Part 5: Link Layer Technologies CSE 3461: Introduction to Computer Networking Reading: Chapter 5, Kurose and Ross 1 Outline PPP ATM X.25 Frame Relay 2 Point to Point Data Link Control One sender, one receiver,
CCNA Exploration1 Chapter 7: OSI Data Link Layer
 CCNA Exploration1 Chapter 7: OSI Data Link Layer LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Explain the role of Data Link layer protocols in data transmission; Objectives Describe how the
CCNA Exploration1 Chapter 7: OSI Data Link Layer LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Explain the role of Data Link layer protocols in data transmission; Objectives Describe how the
Troubleshooting Transparent Bridging Environments
 CHAPTER Troubleshooting Transparent Bridging Environments Transparent bridges were first developed at Digital Equipment Corporation (Digital) in the early 1980s and are now very popular in Ethernet/IEEE
CHAPTER Troubleshooting Transparent Bridging Environments Transparent bridges were first developed at Digital Equipment Corporation (Digital) in the early 1980s and are now very popular in Ethernet/IEEE
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
NETWORKING COMPONENTS
 1) OBJECTIVES NETWORKING COMPONENTS The objectives of this chapter are to familiarize with the following: - i) The LAN components ii) iii) iv) Repeater Hub Bridge v) Router vi) Gateway 2) INTRODUCTION
1) OBJECTIVES NETWORKING COMPONENTS The objectives of this chapter are to familiarize with the following: - i) The LAN components ii) iii) iv) Repeater Hub Bridge v) Router vi) Gateway 2) INTRODUCTION
CH : 15 LOCAL AREA NETWORK OVERVIEW
 CH : 15 LOCAL AREA NETWORK OVERVIEW P. 447 LAN (Local Area Network) A LAN consists of a shared transmission medium and a set of hardware and software for interfacing devices to the medium and regulating
CH : 15 LOCAL AREA NETWORK OVERVIEW P. 447 LAN (Local Area Network) A LAN consists of a shared transmission medium and a set of hardware and software for interfacing devices to the medium and regulating
Prepared by Agha Mohammad Haidari Network Manager ICT Directorate Ministry of Communication & IT
 Network Basics Prepared by Agha Mohammad Haidari Network Manager ICT Directorate Ministry of Communication & IT E-mail :Agha.m@mcit.gov.af Cell:0700148122 After this lesson,you will be able to : Define
Network Basics Prepared by Agha Mohammad Haidari Network Manager ICT Directorate Ministry of Communication & IT E-mail :Agha.m@mcit.gov.af Cell:0700148122 After this lesson,you will be able to : Define
DES P MANUAL WEBSMART SWITCH V1.05
 DES-1100-10P MANUAL WEBSMART SWITCH V1.05 Table of Content Getting Started...3 WEB Configuration...4 Home...4 System...5 Power Over Ethernet...6 LED Power Saving...8 Fundamentals...9 Security...21 Statistics...22
DES-1100-10P MANUAL WEBSMART SWITCH V1.05 Table of Content Getting Started...3 WEB Configuration...4 Home...4 System...5 Power Over Ethernet...6 LED Power Saving...8 Fundamentals...9 Security...21 Statistics...22
Fundamentals of Networking Introduction to Networking Devices
 Fundamentals of Networking Introduction to Networking Devices Kuldeep Sonar 1 NIC (Network Interface Card) A network interface provides connectivity from an end-user PC or laptop to the public network.
Fundamentals of Networking Introduction to Networking Devices Kuldeep Sonar 1 NIC (Network Interface Card) A network interface provides connectivity from an end-user PC or laptop to the public network.
Troubleshooting Transparent Bridging Environments
 Troubleshooting Transparent Bridging Environments Document ID: 10543 This information from the Internetwork Troubleshooting Guide was first posted on CCO here. As a service to our customers, selected chapters
Troubleshooting Transparent Bridging Environments Document ID: 10543 This information from the Internetwork Troubleshooting Guide was first posted on CCO here. As a service to our customers, selected chapters
More on Link Layer. Recap of Last Class. Interconnecting Nodes in LAN (Local-Area Network) Interconnecting with Hubs. Computer Networks 9/21/2009
 More on Link Layer Kai Shen Recap of Last Class Ethernet dominant link layer technology for local-area l networks Ethernet frame structure Ethernet multiple access control CSMA/CD, exponential back-off
More on Link Layer Kai Shen Recap of Last Class Ethernet dominant link layer technology for local-area l networks Ethernet frame structure Ethernet multiple access control CSMA/CD, exponential back-off
Concept Questions Demonstrate your knowledge of these concepts by answering the following questions in the space provided.
 83 Chapter 6 Ethernet Technologies and Ethernet Switching Ethernet and its associated IEEE 802.3 protocols are part of the world's most important networking standards. Because of the great success of the
83 Chapter 6 Ethernet Technologies and Ethernet Switching Ethernet and its associated IEEE 802.3 protocols are part of the world's most important networking standards. Because of the great success of the
CISCO SYSTEM ADMINISTRATION (41)
 CISCO SYSTEM ADMININSTRATION PAGE 1 OF 11 CONTESTANT ID# Time Rank CISCO SYSTEM ADMINISTRATION (41) Regional 2012 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification:
CISCO SYSTEM ADMININSTRATION PAGE 1 OF 11 CONTESTANT ID# Time Rank CISCO SYSTEM ADMINISTRATION (41) Regional 2012 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification:
Internetworking Models The OSI Reference Model
 Internetworking Models When networks first came into being, computers could typically communicate only with computers from the same manufacturer. In the late 1970s, the Open Systems Interconnection (OSI)
Internetworking Models When networks first came into being, computers could typically communicate only with computers from the same manufacturer. In the late 1970s, the Open Systems Interconnection (OSI)
Configuring Link Aggregation on the ML-MR-10 card
 CHAPTER 34 Configuring Link Aggregation on the ML-MR-10 card This chapter applies to the ML-MR-10 card and describes how to configure link aggregation for the ML-Series cards, both EtherChannel and packet-over-sonet/sdh
CHAPTER 34 Configuring Link Aggregation on the ML-MR-10 card This chapter applies to the ML-MR-10 card and describes how to configure link aggregation for the ML-Series cards, both EtherChannel and packet-over-sonet/sdh
Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on
 CBCN4103 Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on the correct path across the complete network
CBCN4103 Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on the correct path across the complete network
7010INT Data Communications Lecture 7 The Network Layer
 Introduction 7010INT Data Communications Lecture 7 The Layer Internetworking & Devices Connecting LANs Routing Backbone networks Virtual LANs Addressing Application Presentation Session Data Link Physical
Introduction 7010INT Data Communications Lecture 7 The Layer Internetworking & Devices Connecting LANs Routing Backbone networks Virtual LANs Addressing Application Presentation Session Data Link Physical
Introduction to the Catalyst 3920
 CHAPTER 1 Introduction to the Catalyst 3920 This chapter contains the following information about the Catalyst 3920: Product Overview Physical Characteristics of the Catalyst 3920 System Architecture Product
CHAPTER 1 Introduction to the Catalyst 3920 This chapter contains the following information about the Catalyst 3920: Product Overview Physical Characteristics of the Catalyst 3920 System Architecture Product
Introduction to Open System Interconnection Reference Model
 Chapter 5 Introduction to OSI Reference Model 1 Chapter 5 Introduction to Open System Interconnection Reference Model Introduction The Open Systems Interconnection (OSI) model is a reference tool for understanding
Chapter 5 Introduction to OSI Reference Model 1 Chapter 5 Introduction to Open System Interconnection Reference Model Introduction The Open Systems Interconnection (OSI) model is a reference tool for understanding
Bridging and Switching Basics
 CHAPTER 4 Bridging and Switching Basics This chapter introduces the technologies employed in devices loosely referred to as bridges and switches. Topics summarized here include general link-layer device
CHAPTER 4 Bridging and Switching Basics This chapter introduces the technologies employed in devices loosely referred to as bridges and switches. Topics summarized here include general link-layer device
1 GSW Bridging and Switching
 1 Sandwiched between the physical and media access layers of local area networking (such as Ethernet) and the routeing of the Internet layer of the IP protocol, lies the thorny subject of bridges. Bridges
1 Sandwiched between the physical and media access layers of local area networking (such as Ethernet) and the routeing of the Internet layer of the IP protocol, lies the thorny subject of bridges. Bridges
King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2
 King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2 IP Addressing and Subnetting: Establishing Elementary Networks using Hubs, Switches and Routers. Objectives:
King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2 IP Addressing and Subnetting: Establishing Elementary Networks using Hubs, Switches and Routers. Objectives:
SYSTEMS ADMINISTRATION USING CISCO (315)
 Page 1 of 10 Contestant Number: Time: Rank: SYSTEMS ADMINISTRATION USING CISCO (315) REGIONAL 2014 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification: 1.
Page 1 of 10 Contestant Number: Time: Rank: SYSTEMS ADMINISTRATION USING CISCO (315) REGIONAL 2014 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification: 1.
The Network Layer and Routers
 The Network Layer and Routers Daniel Zappala CS 460 Computer Networking Brigham Young University 2/18 Network Layer deliver packets from sending host to receiving host must be on every host, router in
The Network Layer and Routers Daniel Zappala CS 460 Computer Networking Brigham Young University 2/18 Network Layer deliver packets from sending host to receiving host must be on every host, router in
Switching and Forwarding Reading: Chapter 3 1/30/14 1
 Switching and Forwarding Reading: Chapter 3 1/30/14 1 Switching and Forwarding Next Problem: Enable communication between hosts that are not directly connected Fundamental Problem of the Internet or any
Switching and Forwarding Reading: Chapter 3 1/30/14 1 Switching and Forwarding Next Problem: Enable communication between hosts that are not directly connected Fundamental Problem of the Internet or any
LAN PROTOCOLS. Beulah A AP/CSE
 LAN PROTOCOLS Beulah A AP/CSE IEEE STANDARDS In 1985, the Computer Society of the IEEE started a project, called Project 802, to set standards to enable intercommunication among equipment from a variety
LAN PROTOCOLS Beulah A AP/CSE IEEE STANDARDS In 1985, the Computer Society of the IEEE started a project, called Project 802, to set standards to enable intercommunication among equipment from a variety
Network.... communication system for connecting end- systems. End-systems a.k.a. hosts PCs, workstations dedicated computers network components
 Networking 1 Network... communication system for connecting end- systems End-systems a.k.a. hosts PCs, workstations dedicated computers network components 2 Multiaccess vs.. Point-to-point Multiaccess
Networking 1 Network... communication system for connecting end- systems End-systems a.k.a. hosts PCs, workstations dedicated computers network components 2 Multiaccess vs.. Point-to-point Multiaccess
Certified NCIA Network Basic v0.1
 Certified NCIA Network Basic v0.1 Chapter 2. EtherNet 1 Network Basic v0.1 Chapter 2 EtherNet 2. LAN switching - HUB vs Switch -Switch Operation 3. Ethernet Troubleshooting - ARP protocol - ARP Troubleshooting
Certified NCIA Network Basic v0.1 Chapter 2. EtherNet 1 Network Basic v0.1 Chapter 2 EtherNet 2. LAN switching - HUB vs Switch -Switch Operation 3. Ethernet Troubleshooting - ARP protocol - ARP Troubleshooting
Portable 2-Port Gigabit Wirespeed Streams Generator & Network TAP
 Portable 2-Port Gigabit Wirespeed Streams Generator & Network TAP NuDOG-301C OVERVIEW NuDOG-301C is a handheld device with two Gigabit ports for Ethernet testing. The main functions of NuDOG-301C include
Portable 2-Port Gigabit Wirespeed Streams Generator & Network TAP NuDOG-301C OVERVIEW NuDOG-301C is a handheld device with two Gigabit ports for Ethernet testing. The main functions of NuDOG-301C include
OSI Reference Model. Computer Networks lab ECOM Prepared By : Eng. Motaz Murtaja Eng. Ola Abd Elatief
 Islamic University of Gaza Faculty of Engineering Computer Engineering Department Computer Networks lab ECOM 4121 OSI Reference Model Prepared By : Eng. Motaz Murtaja Eng. Ola Abd Elatief May /2010 OSI
Islamic University of Gaza Faculty of Engineering Computer Engineering Department Computer Networks lab ECOM 4121 OSI Reference Model Prepared By : Eng. Motaz Murtaja Eng. Ola Abd Elatief May /2010 OSI
Table of Contents 1 Ethernet Interface Configuration Commands 1-1
 Table of Contents 1 Ethernet Interface Configuration Commands 1-1 broadcast-suppression 1-1 description 1-2 display brief interface 1-3 display interface 1-4 display loopback-detection 1-8 duplex 1-9 flow-control
Table of Contents 1 Ethernet Interface Configuration Commands 1-1 broadcast-suppression 1-1 description 1-2 display brief interface 1-3 display interface 1-4 display loopback-detection 1-8 duplex 1-9 flow-control
ET4254 Communications and Networking 1
 Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Management Software AT-S67 AT-S68. User s Guide FOR USE WITH AT-FS7016 AND AT-FS7024 SMART SWITCHES VERSION PN Rev A
 Management Software AT-S67 AT-S68 User s Guide FOR USE WITH AT-FS7016 AND AT-FS7024 SMART SWITCHES VERSION 1.0.0 PN 613-50494-00 Rev A Copyright 2003 Allied Telesyn, Inc. 960 Stewart Drive Suite B, Sunnyvale,
Management Software AT-S67 AT-S68 User s Guide FOR USE WITH AT-FS7016 AND AT-FS7024 SMART SWITCHES VERSION 1.0.0 PN 613-50494-00 Rev A Copyright 2003 Allied Telesyn, Inc. 960 Stewart Drive Suite B, Sunnyvale,
LAN Interconnection and Other Link Layer Protocols
 LAN Interconnection and Other Link Layer Protocols Ethernet dominant link layer technology for local-area networks Ethernet frame structure Kai Shen Dept. of Computer Science, University of Rochester Ethernet
LAN Interconnection and Other Link Layer Protocols Ethernet dominant link layer technology for local-area networks Ethernet frame structure Kai Shen Dept. of Computer Science, University of Rochester Ethernet
LAN Interconnection. different interconnecting devices, many approaches Vasile Dadarlat- Local Area Computer Networks
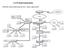 LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
Performance of a Switched Ethernet: A Case Study
 Performance of a Switched Ethernet: A Case Study M. Aboelaze A Elnaggar Dept. of Computer Science Dept of Electrical Engineering York University Sultan Qaboos University Toronto Ontario Alkhod 123 Canada
Performance of a Switched Ethernet: A Case Study M. Aboelaze A Elnaggar Dept. of Computer Science Dept of Electrical Engineering York University Sultan Qaboos University Toronto Ontario Alkhod 123 Canada
Packet Switching on L2 (LAN Level)
 Packet Switching on L2 (LAN Level) Transparent Bridging (TB), Spanning Tree Protocol (STP), Rapid STP, L2 Bridging versus L3 Routing Agenda Introduction Transparent Bridging Basics Spanning Tree Protocol
Packet Switching on L2 (LAN Level) Transparent Bridging (TB), Spanning Tree Protocol (STP), Rapid STP, L2 Bridging versus L3 Routing Agenda Introduction Transparent Bridging Basics Spanning Tree Protocol
Mixed-Media Bridging
 CHAPTER 31 Mixed-Media Bridging Background Transparent bridges are found predominantly in Ethernet networks, and source-route bridges (SRBs) are found almost exclusively in Ring networks. For more information
CHAPTER 31 Mixed-Media Bridging Background Transparent bridges are found predominantly in Ethernet networks, and source-route bridges (SRBs) are found almost exclusively in Ring networks. For more information
M242 COMPUTER NETWORS AND SECURITY
 M242 COMPUTER NETWORS AND SECURITY 2.1. Network Models: UNIT - II OSI MODEL AND LAN PROTOCOLS 1. Explain Network model A network is a combination of hardware and software that sends data from one location
M242 COMPUTER NETWORS AND SECURITY 2.1. Network Models: UNIT - II OSI MODEL AND LAN PROTOCOLS 1. Explain Network model A network is a combination of hardware and software that sends data from one location
Cisco Cisco Certified Network Associate (CCNA)
 Cisco 200-125 Cisco Certified Network Associate (CCNA) http://killexams.com/pass4sure/exam-detail/200-125 Question: 769 Refer to exhibit: Which destination addresses will be used by Host A to send data
Cisco 200-125 Cisco Certified Network Associate (CCNA) http://killexams.com/pass4sure/exam-detail/200-125 Question: 769 Refer to exhibit: Which destination addresses will be used by Host A to send data
Direct Link Networks (II)
 Direct Link Networks (II) Computer Networking Lecture 03 HKU SPACE Community College January 30, 2012 HKU SPACE CC CN Lecture 03 1/25 Outline Reliable Link Service Stop-and-Wait Sliding Window Media Access
Direct Link Networks (II) Computer Networking Lecture 03 HKU SPACE Community College January 30, 2012 HKU SPACE CC CN Lecture 03 1/25 Outline Reliable Link Service Stop-and-Wait Sliding Window Media Access
Local Area Networks. Ethernet LAN
 Local Area Networks Ethernet 802.3 LAN -7-1 Local Area Networks (Lokale Netze) Wide Area Network LAN -7-2 Local Area Networks What is a LAN? Multiple systems attached to an often shared medium high total
Local Area Networks Ethernet 802.3 LAN -7-1 Local Area Networks (Lokale Netze) Wide Area Network LAN -7-2 Local Area Networks What is a LAN? Multiple systems attached to an often shared medium high total
Request for Comments: 2889 Category: Informational Spirent Communications August Benchmarking Methodology for LAN Switching Devices
 Network Working Group Request for Comments: 2889 Category: Informational R. Mandeville CQOS Inc. J. Perser Spirent Communications August 2000 Status of this Memo Benchmarking Methodology for LAN Switching
Network Working Group Request for Comments: 2889 Category: Informational R. Mandeville CQOS Inc. J. Perser Spirent Communications August 2000 Status of this Memo Benchmarking Methodology for LAN Switching
Transparent Bridging and VLAN
 Transparent Bridging and VLAN Plug and Play Networking (C) Herbert Haas 2005/03/11 Algorhyme I think that I shall never see a graph more lovely than a tree a graph whose crucial property is loop-free connectivity.
Transparent Bridging and VLAN Plug and Play Networking (C) Herbert Haas 2005/03/11 Algorhyme I think that I shall never see a graph more lovely than a tree a graph whose crucial property is loop-free connectivity.
3. What could you use if you wanted to reduce unnecessary broadcast, multicast, and flooded unicast packets?
 Nguyen The Nhat - Take Exam Exam questions Time remaining: 00: 00: 51 1. Which command will give the user TECH privileged-mode access after authentication with the server? username name privilege level
Nguyen The Nhat - Take Exam Exam questions Time remaining: 00: 00: 51 1. Which command will give the user TECH privileged-mode access after authentication with the server? username name privilege level
COMPUTER NETWORKS MODEL QUESTION PAPER WITH SOLUTION. (c) Peer-to-peer processes are processes on two or more devices communicating at a
 COMPUTER NETWORKS MODEL QUESTION PAPER WITH SOLUTION Q-1(a) In half-duplex transmission, only one entity can send at a time; in a full-duplex transmission, both entities can send at the same time. (b)
COMPUTER NETWORKS MODEL QUESTION PAPER WITH SOLUTION Q-1(a) In half-duplex transmission, only one entity can send at a time; in a full-duplex transmission, both entities can send at the same time. (b)
