Intelligent Content- Aware Data Priori2za2on and Synchroniza2on across Disconnected, Intermi<ent, Limited (DIL) Networks
|
|
|
- Posy Baldwin
- 6 years ago
- Views:
Transcription
1 Intelligent Content- Aware Data Priori2za2on and Synchroniza2on across Disconnected, Intermi<ent, Limited (DIL) Networks Approaches and Considera2ons Ma< Fisher Nik Keapproth Progeny Systems March 29, 2012 Part No: P006683, Rev: -
2 Typical Problem Areas for Afloat C 4 I Dynamic and Ad- Hoc inter- plaxorm informa2on exchanges over Disconnected, Intermi<ent, and Limited (DIL) network (SIPRnet) Evolving topology and mission è Highly variable bandwidth demands Data genera2on can exceed available bandwidth è Cannot guarantee adequate resources for all generated data to be exchanged Unreliable connec2ons è No implicit assump@on that shared data will be fully replicated as intended Informa2on objects have varying degrees of relevance to the user at different 2mesè Systems should act to focus communica@ons resources where they are most needed Decision- makers rely upon the quality and completeness of shared tac2cal informa2on è Systems should provide assurance of the integrity of the shared tac@cal informa@on Unmanaged Data Poses Risk to Mission Success 2
3 Undersea Warfare Decision Support System The Common Tactical Picture (CTP) is defined as providing situational awareness with such timeliness and accuracy that would facilitate an overt action on the part of a commander up to and including engagement with weapons. References: ASW Command and Control (C2 Study) Naval Warfare publica2on (NWP &NTTP) 32-1 Fleet Exercise Results (VS- 06, VS- 07, USWEX) Submarine combat Systems APB- 06 Capabili2es Le<er An2- Submarine Warfare (ASW) Ini2al Capabili2es Document (ICD) Global An2- Submarine Warfare (ASW ) Concept of Opera2ons (CONOPS) OPNAV N6 Moderniza2on Requirements Le<er for AN/UYQ- 100 USW- DSS CAN Study Improving Fleet ASW: Common Opera2ng Picture and Tac2cal Decision Aids, Nov Operational Need Provide an ASW Common Tactical Picture Across the ASW Enterprise which: Increases Situational Awareness Reduces Operator Workload Enables Improved Mission Planning, Search Execution, ASW Track Management and ASW Battle Management
4 ASW C 4 I Game Changer Time Late Labor Intensive Inaccurate Joint Undersea Superiority Study An2 Submarine Warfare Ini2al Capability Document (C4 for ASW) Metrics Based Planning and Execu2on Improved Sensor Search Effects Real Time CSG Synchroniza2on TDZ and LLOA around CVN SK centered on CVN ASW Master Tac2cal Plot IAW NTTP 3.21 Time Late Lacks Environmental Effects Lacks ASW Sensor Inputs and Fusions GCCS- M Carrier Strike Group Display Current Opera2ons ASW C 4 I Transforma2on CNO Vision for ASW Superiority, May Ac2ve and Passive SPP overlays using in- situ measured noise show significant differences in this dynamic environment Carrier Strike Group Screen Kilo Quick visual SA showing Threat INSIDE of CVN LLOA but OUTSIDE TDZ Automated ASW Sensor Data Exchange ASW Sensor Contact Correla2on and Fusion Shared Tac2cal Decision Aids on USW Common Tac2cal Picture USW DSS Improvements
5 USW- DSS Data Exchanges Data exchanged between DDGs, CGs, CVNs, IUSS*, and ashore command sites: Track / Contact Data Tac2cal Decision Aids (TDAs) Sensor Performance Data (measured noise and reverb) Search Plans Tac2cal Status and Orders Administra2ve Data (Force Management and Versioning) Comms via SIPRnet today; other paths under evalua2on for future systems * IUSS Informa2on exchanges are a subset of those listed 5 here
6 USW- DSS Current Approach JCIDS- level requirements for USW- DSS B2 to establish and maintain a common USW tac8cal picture between connected plaxorms Topology is managed hierarchically and implemented automa2cally to provide consistency Data is exchanged peer- to- peer to maximize reliability and minimize cri2cal nodes USW- DSS B2 employs priori8za8on of data by type to cope with DIL network When bandwidth limits are reached, priority is given en masse to certain data types over others Some data exchanges use periodic synchroniza8on mechanisms Reconcilia2on s2ll dependent on data- type priority hierarchy 6
7 Selected Pla>orm Details Roles and Status of Composi2on Membership Geographic Extent of Shared Data Filters out extraneous geospa2al data 7
8 Priori8za8on by Topic High/Med/Low Priority and BW Caps for each Bandwidth Cap Total BW limit BW Plots over Time Color Coded by Type Instantaneous Values Pie charts and values 8
9 Data Exchange Challenges - Causes Applica2ons contribute to the overall bandwidth, but: Applica2ons may be unaware of the total available bandwidth for the system Applica2ons may be unaware of the bandwidth incurred by other applica2ons Applica2ons may be unaware of the bandwidth incurred by their own data Total system bandwidth can vary based on comms performance and other systems BW limits/schemes that do not account for all factors will subop2mize the system Different data components from any one source are generally not uniformly important to the human user, and can vary in importance based on: Mission priori2es Absolute rela2onships (loca2on, threat category, 2me, speed, etc) Rela2ve rela2onships / comparisons with other data objects (range, LLOA, etc) What is present on a peer (acceptable latency or thresholds for differences in shared informa2on) Is Every Update of Every Object in One Type Always More Important than Any Update of Any Object in Another Type? 9
10 Data Exchange Challenges - Effects Operator can priori2ze between data types, but can only affect incurred bandwidth by removing shared content or subtrac2ng plaxorms (Orig_rate * num_plaxorms) > bw_avail è Conges2on Under constrained bandwidth, some data will not be exchanged è Reduced Effec2veness Data priority is applied in rigid, over- broad groupings è Stra2fied Simple, Sta2c Priori2za2on Schemes Limit Poten2al 10
11 USW- DSS Data Priori2za2on Research Synchroniza8on State (S S or Data Validity) can be calculated for each remote plaxorm Determined as a func@on of % accuracy, latency characteris@cs, and mission relevance Manage communica@ons to maximize S S Each data object should be able to be priori2zed and managed independently by the system Data objects should be able to co- mingle in priori2es between data types to maximize S S Measure Sync Quality and Maximize with an Objec2ve Func2on 11
12 Key Features of an Improved Approach Affect / control the rate of data produc2on Prevent satura2on Improve system ability to respond to network condi2ons Evaluate data objects individually Quan2fy opera2onal significance at the object level Prevent stra2fica2on by type when BW is constrained Provide synchroniza2on metrics Give users an understanding of (and confidence in) the integrity of the shared tac2cal picture Metrics should be intui2ve, easily comprehensible 12
13 USW- DSS Candidate Approach Centrally manage all cross- plaxorm informa2on exchanges Enables intermingling of data types in priority through a coordinated knowledge of bandwidth availability and need Considera2on: avoid architectural constraints requiring bilateral code changes wherever possible Dynamically priori2ze traffic to maximize an objec2ve func2on Quan2fy the state or quality of the shared situa2onal awareness Manage transmissions (data object + remote endpoint pairs) individually Focus on those transmissions that most contribute to the objec2ve func2on 13
14 USW- DSS Candidate Approach Assign each data object a discrete value that relates each shared object to a mission cri2cality (across all data types) è Tier Value Dynamically update as parameters change Tier profile to be customized by Warfare Commander and disseminated by the system For each locally produced {data object, des@na@on planorm} pair, track the remote state of that object using 2mestamp è State Matrix For each entry in the State Matrix, calculate a (con2nuous) Urgency è Urgency Matrix a func2on of 2er, 2me- lateness, displacement error, categoriza2on error, other criteria Rank- order the Urgency Matrix by highest priority è Transmission Priority Vector (TPV) Remove transmissions for known unreachable units Select highest priority bytes from the TPV to each des2na2on plaxorm Not to exceed outgoing capacity of the source, incoming capacity of des2na2ons BW capacity based on last packet(s), with configurable default values and maxima Provide a parallel periodic synchroniza2on using similar object- level priori2es Under Development using USW- DSS Build 2 as Demo System 14
15 Prototype Objec2ves Demonstrate that a given Synchroniza2on State can be obtained with reduced bandwidth Demonstrate that for a fixed bandwidth, an improved Synchroniza2on State can be obtained Demonstrate that improved operator control over data exchange priori2es is possible Demonstrate that improved operator awareness over the state of shared tac2cal informa2on is possible 15
16 Tradi2onal Data Priori2za2on Data Type 1 Δ Shared Data Set Set Cap & Priority Dest n A Data Type 2 Data Type N Δ Shared Data Set Set Cap & Priority Δ Shared Set Cap & Data Set Priority Available Real- Time Human Ac2ons Output Queue Dest n B Dest n N Effec2ve But Coarse- Grained and Reliant on Human Interven2on to Modify Sezngs when BW is Constrained 16
17 Classic Feedback Loop Reference Input + - Controller System System Output Measurement Enables System Response Faster Than A Human Could Respond 17
18 Intelligent Data Priori2za2on Δ Tier Profile Available Real- Time Commander Ac2ons Data Type 1 Δ Shared Data Set Calculate Urgency Dest n A Data Type 2 Data Type N Δ Shared Data Set Δ Shared Data Set Assign Tier By {object, dest} pairs Consider latency, error, etc Output Queue Dest n B Dest n N Available Real- Time User Ac2ons Es2mate Remote State Real- Time System Ac2ons Transmission Status Sync Query Response Feedback Loop and {Object, Des@na@on}- Level Priori2za2on Enable More Granular, Automa2c, Objec2ve- Oriented Data Priori2za2on 18
19 Conclusion Systems with no data priori2za2on capability risk mission accomplishment or require significant operator interven2on Systems with coarse- grained data priori2za2on approaches provide a certain measure of control and ensure the flow of certain types of data under adverse network condi2ons An approach which emphasizes synchroniza2on goals at a system level and adapts to changes in data content, mission relevance, and network condi2ons can exceed the performance of today s genera2on of C4I systems 19
20 Ques2ons 20
An Approach for Establishing and Managing Strike and Battle Group Compositions Across Disconnected, Intermittent and Limited (DIL) Naval Networks
 An Approach for Establishing and Managing Strike and Battle Group Compositions Across Disconnected, Intermittent and Limited (DIL) Naval Networks Matthew Fisher Tom Burns Nik Keapproth March 10th, 2010
An Approach for Establishing and Managing Strike and Battle Group Compositions Across Disconnected, Intermittent and Limited (DIL) Naval Networks Matthew Fisher Tom Burns Nik Keapproth March 10th, 2010
EXHIBIT R-2, RDT&E Budget Item Justification RDT&E, N / BA-05. COST ($ in Millions) FY 2006 FY 2007 FY 2008 FY 2009 FY 2010 FY 2011 FY 2012 FY 2013
 EXHIBIT R-2, RDT&E Budget Item Justification APPROPRIATION/BUDGET ACTIVITY RDT&E, N / BA-05 R-1 ITEM NOMENCLATURE 0604518N Combat Information Center Conversion COST ($ in Millions) FY 2006 FY 2007 FY 2008
EXHIBIT R-2, RDT&E Budget Item Justification APPROPRIATION/BUDGET ACTIVITY RDT&E, N / BA-05 R-1 ITEM NOMENCLATURE 0604518N Combat Information Center Conversion COST ($ in Millions) FY 2006 FY 2007 FY 2008
Preliminary ACTL-SLOW Design in the ACS and OPC-UA context. G. Tos? (19/04/2016)
 Preliminary ACTL-SLOW Design in the ACS and OPC-UA context G. Tos? (19/04/2016) Summary General Introduc?on to ACS Preliminary ACTL-SLOW proposed design Hardware device integra?on in ACS and ACTL- SLOW
Preliminary ACTL-SLOW Design in the ACS and OPC-UA context G. Tos? (19/04/2016) Summary General Introduc?on to ACS Preliminary ACTL-SLOW proposed design Hardware device integra?on in ACS and ACTL- SLOW
Keep the Lights on and the Informa3on Flowing
 Keep the Lights on and the Informa3on Flowing Daniel Kirschen Donald W. and Ruth Mary Close Professor of Electrical Engineering University of Washington 1 Acknowledgements Prof. François Bouffard (McGill
Keep the Lights on and the Informa3on Flowing Daniel Kirschen Donald W. and Ruth Mary Close Professor of Electrical Engineering University of Washington 1 Acknowledgements Prof. François Bouffard (McGill
Distributed Systems. Communica3on and models. Rik Sarkar 2015/2016. University of Edinburgh
 Distributed Systems Communica3on and models Rik Sarkar 2015/2016 University of Edinburgh Models Expecta3ons/assump3ons about things Every idea or ac3on anywhere is based on a model Determines what can
Distributed Systems Communica3on and models Rik Sarkar 2015/2016 University of Edinburgh Models Expecta3ons/assump3ons about things Every idea or ac3on anywhere is based on a model Determines what can
Effect of Router Buffers on Stability of Internet Conges8on Control Algorithms
 Effect of Router Buffers on Stability of Internet Conges8on Control Algorithms Somayeh Sojoudi Steven Low John Doyle Oct 27, 2011 1 Resource alloca+on problem Objec8ve Fair assignment of rates to the users
Effect of Router Buffers on Stability of Internet Conges8on Control Algorithms Somayeh Sojoudi Steven Low John Doyle Oct 27, 2011 1 Resource alloca+on problem Objec8ve Fair assignment of rates to the users
Cyber Security and Power System Communica4ons Essen4al Parts of a Smart Grid Infrastructure. Talal El Awar
 Cyber Security and Power System Communica4ons Essen4al Parts of a Smart Grid Infrastructure Author: Goran N. Ericsson, Senior Member, IEEE Talal El Awar Submi.ed in Par3al Fulfillment of the Course Requirements
Cyber Security and Power System Communica4ons Essen4al Parts of a Smart Grid Infrastructure Author: Goran N. Ericsson, Senior Member, IEEE Talal El Awar Submi.ed in Par3al Fulfillment of the Course Requirements
Distributed Systems. Communica3on and models. Rik Sarkar Spring University of Edinburgh
 Distributed Systems Communica3on and models Rik Sarkar Spring 2018 University of Edinburgh Models Expecta3ons/assump3ons about things Every idea or ac3on anywhere is based on a model Determines what can
Distributed Systems Communica3on and models Rik Sarkar Spring 2018 University of Edinburgh Models Expecta3ons/assump3ons about things Every idea or ac3on anywhere is based on a model Determines what can
Ontology engineering. Valen.na Tamma. Based on slides by A. Gomez Perez, N. Noy, D. McGuinness, E. Kendal, A. Rector and O. Corcho
 Ontology engineering Valen.na Tamma Based on slides by A. Gomez Perez, N. Noy, D. McGuinness, E. Kendal, A. Rector and O. Corcho Summary Background on ontology; Ontology and ontological commitment; Logic
Ontology engineering Valen.na Tamma Based on slides by A. Gomez Perez, N. Noy, D. McGuinness, E. Kendal, A. Rector and O. Corcho Summary Background on ontology; Ontology and ontological commitment; Logic
Orchestrated Network Services with LSO, SDN and NFV
 Host Sponsor Co- Sponsor Orchestrated Network Services with LSO, SDN and NFV Darryl Stork Regional Director WebNMS 1 PresentaBon Agenda Overview of LSO, SDN, NFV, and the Third Network Using LSO, SDN and
Host Sponsor Co- Sponsor Orchestrated Network Services with LSO, SDN and NFV Darryl Stork Regional Director WebNMS 1 PresentaBon Agenda Overview of LSO, SDN, NFV, and the Third Network Using LSO, SDN and
Today s Objec2ves. Kerberos. Kerberos Peer To Peer Overlay Networks Final Projects
 Today s Objec2ves Kerberos Peer To Peer Overlay Networks Final Projects Nov 27, 2017 Sprenkle - CSCI325 1 Kerberos Trusted third party, runs by default on port 88 Security objects: Ø Ticket: token, verifying
Today s Objec2ves Kerberos Peer To Peer Overlay Networks Final Projects Nov 27, 2017 Sprenkle - CSCI325 1 Kerberos Trusted third party, runs by default on port 88 Security objects: Ø Ticket: token, verifying
What were his cri+cisms? Classical Methodologies:
 1 2 Classifica+on In this scheme there are several methodologies, such as Process- oriented, Blended, Object Oriented, Rapid development, People oriented and Organisa+onal oriented. According to David
1 2 Classifica+on In this scheme there are several methodologies, such as Process- oriented, Blended, Object Oriented, Rapid development, People oriented and Organisa+onal oriented. According to David
Model- Based Security Tes3ng with Test Pa9erns
 Model- Based Security Tes3ng with Test Pa9erns Julien BOTELLA (Smartes5ng) Jürgen GROSSMANN (FOKUS) Bruno LEGEARD (Smartes3ng) Fabien PEUREUX (Smartes5ng) Mar5n SCHNEIDER (FOKUS) Fredrik SEEHUSEN (SINTEF)
Model- Based Security Tes3ng with Test Pa9erns Julien BOTELLA (Smartes5ng) Jürgen GROSSMANN (FOKUS) Bruno LEGEARD (Smartes3ng) Fabien PEUREUX (Smartes5ng) Mar5n SCHNEIDER (FOKUS) Fredrik SEEHUSEN (SINTEF)
Network core and metrics
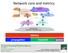 Network core and metrics latency propaga-on transmit queue Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and
Network core and metrics latency propaga-on transmit queue Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and
Assessing Medical Device. Cyber Risks in a Healthcare. Environment
 Assessing Medical Device Medical Devices Security Cyber Risks in a Healthcare Phil Englert Director Technology Operations Environment Catholic Health Ini
Assessing Medical Device Medical Devices Security Cyber Risks in a Healthcare Phil Englert Director Technology Operations Environment Catholic Health Ini
Link Layer. w/ credit to Rick Graziani (Cabrillo) for some of the anima<ons
 Link Layer w/ credit to Rick Graziani (Cabrillo) for some of the anima
Link Layer w/ credit to Rick Graziani (Cabrillo) for some of the anima
Wireless Mul*hop Ad Hoc Networks
 Wireless Mul*hop Guevara Noubir noubir@ccs.neu.edu Some slides are from Nitin Vaidya s tutorial. Infrastructure vs. Ad Hoc Wireless Networks Infrastructure networks: One or several Access- Points (AP)
Wireless Mul*hop Guevara Noubir noubir@ccs.neu.edu Some slides are from Nitin Vaidya s tutorial. Infrastructure vs. Ad Hoc Wireless Networks Infrastructure networks: One or several Access- Points (AP)
Autonomous Threat Hun?ng With Niddel And Splunk Enterprise Security: Mars Inc. Customer Case Study
 Copyright 2016 Splunk Inc. Autonomous Threat Hun?ng With Niddel And Splunk Enterprise Security: Mars Inc. Customer Case Study Alex Pinto Chief Data Scien?st, Niddel Greg Poniatowski Security Service Area
Copyright 2016 Splunk Inc. Autonomous Threat Hun?ng With Niddel And Splunk Enterprise Security: Mars Inc. Customer Case Study Alex Pinto Chief Data Scien?st, Niddel Greg Poniatowski Security Service Area
Key Nego(a(on Protocol & Trust Router
 Key Nego(a(on Protocol & Trust Router dra6- howle:- radsec- knp ABFAB, IETF 80 31 March, Prague. Introduc(on The ABFAB architecture does not require any par(cular AAA strategy for connec(ng RPs to IdPs.
Key Nego(a(on Protocol & Trust Router dra6- howle:- radsec- knp ABFAB, IETF 80 31 March, Prague. Introduc(on The ABFAB architecture does not require any par(cular AAA strategy for connec(ng RPs to IdPs.
Mul$media Networking. #10 QoS Semester Ganjil 2012 PTIIK Universitas Brawijaya
 Mul$media Networking #10 QoS Semester Ganjil 2012 PTIIK Universitas Brawijaya Schedule of Class Mee$ng 1. Introduc$on 2. Applica$ons of MN 3. Requirements of MN 4. Coding and Compression 5. RTP 6. IP Mul$cast
Mul$media Networking #10 QoS Semester Ganjil 2012 PTIIK Universitas Brawijaya Schedule of Class Mee$ng 1. Introduc$on 2. Applica$ons of MN 3. Requirements of MN 4. Coding and Compression 5. RTP 6. IP Mul$cast
Design Principles & Prac4ces
 Design Principles & Prac4ces Robert France Robert B. France 1 Understanding complexity Accidental versus Essen4al complexity Essen%al complexity: Complexity that is inherent in the problem or the solu4on
Design Principles & Prac4ces Robert France Robert B. France 1 Understanding complexity Accidental versus Essen4al complexity Essen%al complexity: Complexity that is inherent in the problem or the solu4on
Integra(on of Accident Management Strategies into Sta(on Opera(on Fred Dermarkar Vice President Engineering Strategy Ontario Power Generation
 Integra(on of Accident Management Strategies into Sta(on Opera(on Fred Dermarkar Vice President Engineering Strategy Ontario Power Generation IAEA International Expert Meeting on Human and Organizational
Integra(on of Accident Management Strategies into Sta(on Opera(on Fred Dermarkar Vice President Engineering Strategy Ontario Power Generation IAEA International Expert Meeting on Human and Organizational
Autonomic Mul,- Agents Security System for mul,- layered distributed architectures. Chris,an Contreras
 Autonomic Mul,- s Security System for mul,- layered distributed architectures Chris,an Contreras Agenda Introduc,on Mul,- layered distributed architecture Autonomic compu,ng system Mul,- System (MAS) Autonomic
Autonomic Mul,- s Security System for mul,- layered distributed architectures Chris,an Contreras Agenda Introduc,on Mul,- layered distributed architecture Autonomic compu,ng system Mul,- System (MAS) Autonomic
Stacking it Up Experimental Observa6ons on the opera6on of Dual Stack Services
 Stacking it Up Experimental Observa6ons on the opera6on of Dual Stack Services Geoff Huston, APNIC Labs 1 If working with one protocol has its problems 2 Then just how much damage can we do by joining
Stacking it Up Experimental Observa6ons on the opera6on of Dual Stack Services Geoff Huston, APNIC Labs 1 If working with one protocol has its problems 2 Then just how much damage can we do by joining
International SOF Coordination Center (ISCC)
 International SOF Coordination Center (ISCC) 19 th ICCRTS 17 June 2014 Paper ID 004 Mr. Ken D. Teske Mr. Michael D. Tisdel Mr. William C. Fleser 1 Agenda The Concept The OV-1 View Required Capabilities
International SOF Coordination Center (ISCC) 19 th ICCRTS 17 June 2014 Paper ID 004 Mr. Ken D. Teske Mr. Michael D. Tisdel Mr. William C. Fleser 1 Agenda The Concept The OV-1 View Required Capabilities
Conges'on. Last Week: Discovery and Rou'ng. Today: Conges'on Control. Distributed Resource Sharing. Conges'on Collapse. Conges'on
 Last Week: Discovery and Rou'ng Provides end-to-end connectivity, but not necessarily good performance Conges'on logical link name Michael Freedman COS 461: Computer Networks Lectures: MW 10-10:50am in
Last Week: Discovery and Rou'ng Provides end-to-end connectivity, but not necessarily good performance Conges'on logical link name Michael Freedman COS 461: Computer Networks Lectures: MW 10-10:50am in
1/10/16. RPC and Clocks. Tom Anderson. Last Time. Synchroniza>on RPC. Lab 1 RPC
 RPC and Clocks Tom Anderson Go Synchroniza>on RPC Lab 1 RPC Last Time 1 Topics MapReduce Fault tolerance Discussion RPC At least once At most once Exactly once Lamport Clocks Mo>va>on MapReduce Fault Tolerance
RPC and Clocks Tom Anderson Go Synchroniza>on RPC Lab 1 RPC Last Time 1 Topics MapReduce Fault tolerance Discussion RPC At least once At most once Exactly once Lamport Clocks Mo>va>on MapReduce Fault Tolerance
15,000+ Networks, 5 Million+ Users:
 15,000+ Networks, 5 Million+ Users: T&E Net Centric Challenges March 1, 2010 John Illgen Sector Director, Modeling & Simulation Topics 2 Why, How, What, Result Simulation and T&E Example Where have we
15,000+ Networks, 5 Million+ Users: T&E Net Centric Challenges March 1, 2010 John Illgen Sector Director, Modeling & Simulation Topics 2 Why, How, What, Result Simulation and T&E Example Where have we
April 17, Ronald Layne Manager, Data Quality and Data Governance
 Ensuring the highest quality data is delivered throughout the university providing valuable information serving individual and organizational need April 17, 2015 Ronald Layne Manager, Data Quality and
Ensuring the highest quality data is delivered throughout the university providing valuable information serving individual and organizational need April 17, 2015 Ronald Layne Manager, Data Quality and
Decision making for autonomous naviga2on. Anoop Aroor Advisor: Susan Epstein CUNY Graduate Center, Computer science
 Decision making for autonomous naviga2on Anoop Aroor Advisor: Susan Epstein CUNY Graduate Center, Computer science Overview Naviga2on and Mobile robots Decision- making techniques for naviga2on Building
Decision making for autonomous naviga2on Anoop Aroor Advisor: Susan Epstein CUNY Graduate Center, Computer science Overview Naviga2on and Mobile robots Decision- making techniques for naviga2on Building
CLOUD SERVICES. Cloud Value Assessment.
 CLOUD SERVICES Cloud Value Assessment www.cloudcomrade.com Comrade a companion who shares one's ac8vi8es or is a fellow member of an organiza8on 2 Today s Agenda! Why Companies Should Consider Moving Business
CLOUD SERVICES Cloud Value Assessment www.cloudcomrade.com Comrade a companion who shares one's ac8vi8es or is a fellow member of an organiza8on 2 Today s Agenda! Why Companies Should Consider Moving Business
Asaf Cidon, Assaf Eisenman, Mohammad Alizadeh and Sachin KaH
 Cli$anger: Scaling Performance Cliffs in Memory Caches [NSDI 2016] Cache OS: Data Center Dynamic Cache Management Asaf Cidon, Assaf Eisenman, Mohammad Alizadeh and Sachin KaH 1 Key-Value Caches are Essen1al
Cli$anger: Scaling Performance Cliffs in Memory Caches [NSDI 2016] Cache OS: Data Center Dynamic Cache Management Asaf Cidon, Assaf Eisenman, Mohammad Alizadeh and Sachin KaH 1 Key-Value Caches are Essen1al
Alignment and Image Comparison. Erik Learned- Miller University of Massachuse>s, Amherst
 Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison
Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison
A MAC protocol for Reliable Broadcast Communica7ons in Wireless Network- on- Chip
 A MAC protocol for Reliable Broadcast Communica7ons in Wireless Network- on- Chip Sergi Abadal (abadal@ac.upc.edu) Albert Mestres, Josep Torrellas, Eduard Alarcón, and Albert Cabellos- Aparicio UPC and
A MAC protocol for Reliable Broadcast Communica7ons in Wireless Network- on- Chip Sergi Abadal (abadal@ac.upc.edu) Albert Mestres, Josep Torrellas, Eduard Alarcón, and Albert Cabellos- Aparicio UPC and
Storwize in IT Environments Market Overview
 Storwize in IT Environments Market Overview Topic Challenges in Tradi,onal IT Environment Types of informa,on Storage systems required Storage for private clouds where tradi,onal IT is involved Storwize
Storwize in IT Environments Market Overview Topic Challenges in Tradi,onal IT Environment Types of informa,on Storage systems required Storage for private clouds where tradi,onal IT is involved Storwize
A- SAS : An Adap*ve High- Availability Scheme for Distributed Stream Processing Systems
 A- SAS : An Adap*ve High- Availability Scheme for Distributed Stream Processing Systems Hiroaki SHIOKAWA (University of Tsukuba, Japan) Hiroyuki KITAGAWA (University of Tsukuba, Japan) Hideyuki KAWASHIMA
A- SAS : An Adap*ve High- Availability Scheme for Distributed Stream Processing Systems Hiroaki SHIOKAWA (University of Tsukuba, Japan) Hiroyuki KITAGAWA (University of Tsukuba, Japan) Hideyuki KAWASHIMA
Alignment and Image Comparison
 Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison
Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison Erik Learned- Miller University of Massachuse>s, Amherst Alignment and Image Comparison
Con$nuous Audi$ng and Risk Management in Cloud Compu$ng
 Con$nuous Audi$ng and Risk Management in Cloud Compu$ng Marcus Spies Chair of Knowledge Management LMU University of Munich Scien$fic / Technical Director of EU Integrated Research Project MUSING Cloud
Con$nuous Audi$ng and Risk Management in Cloud Compu$ng Marcus Spies Chair of Knowledge Management LMU University of Munich Scien$fic / Technical Director of EU Integrated Research Project MUSING Cloud
Today s Objec2ves. AWS/MR Review Final Projects Distributed File Systems. Nov 3, 2017 Sprenkle - CSCI325
 Today s Objec2ves AWS/MR Review Final Projects Distributed File Systems Nov 3, 2017 Sprenkle - CSCI325 1 Inverted Index final input files have been posted Another email out to AWS Google cloud Nov 3, 2017
Today s Objec2ves AWS/MR Review Final Projects Distributed File Systems Nov 3, 2017 Sprenkle - CSCI325 1 Inverted Index final input files have been posted Another email out to AWS Google cloud Nov 3, 2017
Extending Heuris.c Search
 Extending Heuris.c Search Talk at Hebrew University, Cri.cal MAS group Roni Stern Department of Informa.on System Engineering, Ben Gurion University, Israel 1 Heuris.c search 2 Outline Combining lookahead
Extending Heuris.c Search Talk at Hebrew University, Cri.cal MAS group Roni Stern Department of Informa.on System Engineering, Ben Gurion University, Israel 1 Heuris.c search 2 Outline Combining lookahead
Architectural Requirements Phase. See Sommerville Chapters 11, 12, 13, 14, 18.2
 Architectural Requirements Phase See Sommerville Chapters 11, 12, 13, 14, 18.2 1 Architectural Requirements Phase So7ware requirements concerned construc>on of a logical model Architectural requirements
Architectural Requirements Phase See Sommerville Chapters 11, 12, 13, 14, 18.2 1 Architectural Requirements Phase So7ware requirements concerned construc>on of a logical model Architectural requirements
Usability Tes2ng Usability and Correctness. About Face (1995) Alan Cooper. About Face (1995) Alan Cooper. Why Evaluate?
 2 Usability and Correctness Usability How easy is the system to use? How learnable is the system? Correctness Does the system do what it says it will do? Usability and correctness are two different criteria.
2 Usability and Correctness Usability How easy is the system to use? How learnable is the system? Correctness Does the system do what it says it will do? Usability and correctness are two different criteria.
Architectures, and Protocol Design Issues for Mobile Social Networks: A Survey
 Applica@ons, Architectures, and Protocol Design Issues for Mobile Social Networks: A Survey N. Kayastha,D. Niyato, P. Wang and E. Hossain, Proceedings of the IEEEVol. 99, No. 12, Dec. 2011. Sabita Maharjan
Applica@ons, Architectures, and Protocol Design Issues for Mobile Social Networks: A Survey N. Kayastha,D. Niyato, P. Wang and E. Hossain, Proceedings of the IEEEVol. 99, No. 12, Dec. 2011. Sabita Maharjan
Fluxo. Improving the Responsiveness of Internet Services with Automa7c Cache Placement
 Fluxo Improving the Responsiveness of Internet Services with Automac Cache Placement Alexander Rasmussen UCSD (Presenng) Emre Kiciman MSR Redmond Benjamin Livshits MSR Redmond Madanlal Musuvathi MSR Redmond
Fluxo Improving the Responsiveness of Internet Services with Automac Cache Placement Alexander Rasmussen UCSD (Presenng) Emre Kiciman MSR Redmond Benjamin Livshits MSR Redmond Madanlal Musuvathi MSR Redmond
Automated System Analysis using Executable SysML Modeling Pa8erns
 Automated System Analysis using Executable SysML Modeling Pa8erns Maged Elaasar* Modelware Solu
Automated System Analysis using Executable SysML Modeling Pa8erns Maged Elaasar* Modelware Solu
RouteBricks: Exploi2ng Parallelism to Scale So9ware Routers
 RouteBricks: Exploi2ng Parallelism to Scale So9ware Routers Mihai Dobrescu and etc. SOSP 2009 Presented by Shuyi Chen Mo2va2on Router design Performance Extensibility They are compe2ng goals Hardware approach
RouteBricks: Exploi2ng Parallelism to Scale So9ware Routers Mihai Dobrescu and etc. SOSP 2009 Presented by Shuyi Chen Mo2va2on Router design Performance Extensibility They are compe2ng goals Hardware approach
Introduction to Securing Critical Infrastructure
 Her kan tekst skrives Her kan tekst skrives Introduction to Securing Critical Infrastructure Her kan tekst skrives Keith Frederick CISSP, CAP, CRISC, Author securenok.com Topics A)acks on the Oil and Gas
Her kan tekst skrives Her kan tekst skrives Introduction to Securing Critical Infrastructure Her kan tekst skrives Keith Frederick CISSP, CAP, CRISC, Author securenok.com Topics A)acks on the Oil and Gas
Ensemble- Based Characteriza4on of Uncertain Features Dennis McLaughlin, Rafal Wojcik
 Ensemble- Based Characteriza4on of Uncertain Features Dennis McLaughlin, Rafal Wojcik Hydrology TRMM TMI/PR satellite rainfall Neuroscience - - MRI Medicine - - CAT Geophysics Seismic Material tes4ng Laser
Ensemble- Based Characteriza4on of Uncertain Features Dennis McLaughlin, Rafal Wojcik Hydrology TRMM TMI/PR satellite rainfall Neuroscience - - MRI Medicine - - CAT Geophysics Seismic Material tes4ng Laser
COSC 310: So*ware Engineering. Dr. Bowen Hui University of Bri>sh Columbia Okanagan
 COSC 310: So*ware Engineering Dr. Bowen Hui University of Bri>sh Columbia Okanagan 1 Admin A2 is up Don t forget to keep doing peer evalua>ons Deadline can be extended but shortens A3 >meframe Labs This
COSC 310: So*ware Engineering Dr. Bowen Hui University of Bri>sh Columbia Okanagan 1 Admin A2 is up Don t forget to keep doing peer evalua>ons Deadline can be extended but shortens A3 >meframe Labs This
Crea?ng Cloud Apps with Oracle Applica?on Builder Cloud Service
 Crea?ng Cloud Apps with Oracle Applica?on Builder Cloud Service Shay Shmeltzer Director of Product Management Oracle Development Tools and Frameworks @JDevShay hpp://blogs.oracle.com/shay This App you
Crea?ng Cloud Apps with Oracle Applica?on Builder Cloud Service Shay Shmeltzer Director of Product Management Oracle Development Tools and Frameworks @JDevShay hpp://blogs.oracle.com/shay This App you
Benjamin Holland, Ganesh Ram Santhanam, Payas Awadhutkar, and Suresh Kothari {bholland, gsanthan, payas,
 Statically-informed Dynamic Analysis Tools to Detect Algorithmic Complexity Vulnerabilities 16th IEEE Interna,onal Working Conference on Source Code Analysis and Manipula,on (SCAM 2016) October 2, 2016
Statically-informed Dynamic Analysis Tools to Detect Algorithmic Complexity Vulnerabilities 16th IEEE Interna,onal Working Conference on Source Code Analysis and Manipula,on (SCAM 2016) October 2, 2016
MapReduce, Apache Hadoop
 Czech Technical University in Prague, Faculty of Informaon Technology MIE-PDB: Advanced Database Systems hp://www.ksi.mff.cuni.cz/~svoboda/courses/2016-2-mie-pdb/ Lecture 12 MapReduce, Apache Hadoop Marn
Czech Technical University in Prague, Faculty of Informaon Technology MIE-PDB: Advanced Database Systems hp://www.ksi.mff.cuni.cz/~svoboda/courses/2016-2-mie-pdb/ Lecture 12 MapReduce, Apache Hadoop Marn
NetSecOps: Policy-Driven, Knowledge-Centric, Holis<c Network Security Opera<ons
 NetSecOps: Policy-Driven, Knowledge-Centric, Holis
NetSecOps: Policy-Driven, Knowledge-Centric, Holis
ECE 1749H: Interconnec1on Networks for Parallel Computer Architectures: Interface with System Architecture. Prof. Natalie Enright Jerger
 ECE 1749H: Interconnec1on Networks for Parallel Computer Architectures: Interface with System Architecture Prof. Natalie Enright Jerger Systems and Interfaces Look at how systems interact and interface
ECE 1749H: Interconnec1on Networks for Parallel Computer Architectures: Interface with System Architecture Prof. Natalie Enright Jerger Systems and Interfaces Look at how systems interact and interface
Link Layer. w/ much credit to Cisco CCNA and Rick Graziani (Cabrillo)
 Link Layer w/ much credit to Cisco CCNA and Rick Graziani (Cabrillo) Administra>via How are the labs going? Telnet- ing into Linux as root In /etc/pam.d/remote comment out line auth required pam_securely.so
Link Layer w/ much credit to Cisco CCNA and Rick Graziani (Cabrillo) Administra>via How are the labs going? Telnet- ing into Linux as root In /etc/pam.d/remote comment out line auth required pam_securely.so
AWS Iden)ty And Access Management (IAM) Manohar Rapolu
 AWS Iden)ty And Access Management (IAM) Manohar Rapolu Topics Introduc5on Principals Authen5ca5on Authoriza5on Other Key Feature -> Mul5 Factor Authen5ca5on -> Rota5ng Keys -> Resolving Mul5ple Permissions
AWS Iden)ty And Access Management (IAM) Manohar Rapolu Topics Introduc5on Principals Authen5ca5on Authoriza5on Other Key Feature -> Mul5 Factor Authen5ca5on -> Rota5ng Keys -> Resolving Mul5ple Permissions
MapReduce, Apache Hadoop
 NDBI040: Big Data Management and NoSQL Databases hp://www.ksi.mff.cuni.cz/ svoboda/courses/2016-1-ndbi040/ Lecture 2 MapReduce, Apache Hadoop Marn Svoboda svoboda@ksi.mff.cuni.cz 11. 10. 2016 Charles University
NDBI040: Big Data Management and NoSQL Databases hp://www.ksi.mff.cuni.cz/ svoboda/courses/2016-1-ndbi040/ Lecture 2 MapReduce, Apache Hadoop Marn Svoboda svoboda@ksi.mff.cuni.cz 11. 10. 2016 Charles University
DASH7 Alliance Protocol
 DASH7 Alliance Protocol D7A Meeting Paris June 16 th, 2014 Yordan Tabakov PAG Chair yordan@wizzilab.com ORIGINES The DASH7 Alliance Protocol originates from ISO/IEC 18000-7 ISO/IEC 18000 is an interna@onal
DASH7 Alliance Protocol D7A Meeting Paris June 16 th, 2014 Yordan Tabakov PAG Chair yordan@wizzilab.com ORIGINES The DASH7 Alliance Protocol originates from ISO/IEC 18000-7 ISO/IEC 18000 is an interna@onal
Secure Architecture Principles
 Secure Architecture Principles Isola3on and Least Privilege Access Control Concepts Opera3ng Systems Browser Isola3on and Least Privilege Original slides were created by Prof. John Mitchel Secure Architecture
Secure Architecture Principles Isola3on and Least Privilege Access Control Concepts Opera3ng Systems Browser Isola3on and Least Privilege Original slides were created by Prof. John Mitchel Secure Architecture
Spanning Tree and Datacenters
 Spanning Tree and Datacenters EE 122, Fall 2013 Sylvia Ratnasamy http://inst.eecs.berkeley.edu/~ee122/ Material thanks to Mike Freedman, Scott Shenker, Ion Stoica, Jennifer Rexford, and many other colleagues
Spanning Tree and Datacenters EE 122, Fall 2013 Sylvia Ratnasamy http://inst.eecs.berkeley.edu/~ee122/ Material thanks to Mike Freedman, Scott Shenker, Ion Stoica, Jennifer Rexford, and many other colleagues
Network Mobility Management: APPLICATION REQUIREMENTS & MOBILITY MODELS
 Network Mobility Management: APPLICATION REQUIREMENTS & MOBILITY MODELS h"p://www.cs.unibo.it./difelice/sm/ Mobile Systems Prof. Marco Di Felice Department of Computer Science and Engineering University
Network Mobility Management: APPLICATION REQUIREMENTS & MOBILITY MODELS h"p://www.cs.unibo.it./difelice/sm/ Mobile Systems Prof. Marco Di Felice Department of Computer Science and Engineering University
Coupled Conges,on Control for RTP Media. Safiqul Islam, Michael Welzl, Stein Gjessing and Naeem Khademi Department of Informa,cs University of Oslo
 Coupled Conges,on Control for RTP Media Safiqul Islam, Michael Welzl, Stein Gjessing and Naeem Khademi Department of Informa,cs University of Oslo Problem statement Each Flow has its own Conges@on Control
Coupled Conges,on Control for RTP Media Safiqul Islam, Michael Welzl, Stein Gjessing and Naeem Khademi Department of Informa,cs University of Oslo Problem statement Each Flow has its own Conges@on Control
Business Case Components
 How to Build A SOC Agenda Mission Business Case Components Regulatory requirements SOC Terminology Technology Components Events categories Staff Requirements Organiza>on s Considera>ons Training Requirements
How to Build A SOC Agenda Mission Business Case Components Regulatory requirements SOC Terminology Technology Components Events categories Staff Requirements Organiza>on s Considera>ons Training Requirements
Interconnec(on in the Internet: the policy challenge. David Clark MIT CFP May, 2011
 Interconnec(on in the Internet: the policy challenge David Clark MIT CFP May, 2011 Open interconnec
Interconnec(on in the Internet: the policy challenge David Clark MIT CFP May, 2011 Open interconnec
Quan'fying QoS Requirements of Network Services: A Cheat- Proof Framework
 Quan'fying QoS Requirements of Network Services: A Cheat- Proof Framework Kuan- Ta Chen Academia Sinica Chen- Chi Wu Na3onal Taiwan University Yu- Chun Chang Na3onal Taiwan University Chin- Laung Lei Na3onal
Quan'fying QoS Requirements of Network Services: A Cheat- Proof Framework Kuan- Ta Chen Academia Sinica Chen- Chi Wu Na3onal Taiwan University Yu- Chun Chang Na3onal Taiwan University Chin- Laung Lei Na3onal
Symantec Data Loss Preven2on 12.5 Demo Presenta2on
 Symantec Data Loss Preven2on 12.5 Demo Presenta2on 1 Our Understanding PROJECT DRIVERS & DATA TO PROTECT Regulatory compliance PCI, GLBA Data inventory and cleansing SSNs, CCNs [Replace these bullet points
Symantec Data Loss Preven2on 12.5 Demo Presenta2on 1 Our Understanding PROJECT DRIVERS & DATA TO PROTECT Regulatory compliance PCI, GLBA Data inventory and cleansing SSNs, CCNs [Replace these bullet points
RTP Taxonomy & Rela.onships
 RTP Taxonomy & Rela.onships dra%- lennox- raiarea- rtp- grouping- taxonomy- 03 IETF 88 @Authors 1 Changes Since - 02 Major re- write Sec.on 2, Concepts, re- structured to a conceptual media chain with
RTP Taxonomy & Rela.onships dra%- lennox- raiarea- rtp- grouping- taxonomy- 03 IETF 88 @Authors 1 Changes Since - 02 Major re- write Sec.on 2, Concepts, re- structured to a conceptual media chain with
Ar#ficial Intelligence
 Ar#ficial Intelligence Advanced Searching Prof Alexiei Dingli Gene#c Algorithms Charles Darwin Genetic Algorithms are good at taking large, potentially huge search spaces and navigating them, looking for
Ar#ficial Intelligence Advanced Searching Prof Alexiei Dingli Gene#c Algorithms Charles Darwin Genetic Algorithms are good at taking large, potentially huge search spaces and navigating them, looking for
Mul$media Networking. #5 Real- Time Transport Protocol Semester Ganjil 2012 PTIIK Universitas Brawijaya
 Mul$media Networking #5 Real- Time Transport Protocol Semester Ganjil 2012 PTIIK Universitas Brawijaya Schedule of Class Mee$ng 1. Introduc$on 2. Applica$ons of MN 3. Requirements of MN 4. Coding and Compression
Mul$media Networking #5 Real- Time Transport Protocol Semester Ganjil 2012 PTIIK Universitas Brawijaya Schedule of Class Mee$ng 1. Introduc$on 2. Applica$ons of MN 3. Requirements of MN 4. Coding and Compression
Broadcas(ng Video in Dense g Networks Using Applica(on FEC and Mul(cast
 Broadcas(ng Video in Dense 802.11g Networks Using Applica(on FEC and Mul(cast Last update: 6-10-2011 Dr James Martin School of Computing Clemson University Clemson, SC jim.martin@cs.clemson.edu Dr James
Broadcas(ng Video in Dense 802.11g Networks Using Applica(on FEC and Mul(cast Last update: 6-10-2011 Dr James Martin School of Computing Clemson University Clemson, SC jim.martin@cs.clemson.edu Dr James
SEDA An architecture for Well Condi6oned, scalable Internet Services
 SEDA An architecture for Well Condi6oned, scalable Internet Services Ma= Welsh, David Culler, and Eric Brewer University of California, Berkeley Symposium on Operating Systems Principles (SOSP), October
SEDA An architecture for Well Condi6oned, scalable Internet Services Ma= Welsh, David Culler, and Eric Brewer University of California, Berkeley Symposium on Operating Systems Principles (SOSP), October
Introduc)on to Probabilis)c Latent Seman)c Analysis. NYP Predic)ve Analy)cs Meetup June 10, 2010
 Introduc)on to Probabilis)c Latent Seman)c Analysis NYP Predic)ve Analy)cs Meetup June 10, 2010 PLSA A type of latent variable model with observed count data and nominal latent variable(s). Despite the
Introduc)on to Probabilis)c Latent Seman)c Analysis NYP Predic)ve Analy)cs Meetup June 10, 2010 PLSA A type of latent variable model with observed count data and nominal latent variable(s). Despite the
Special Publication
 Special Publication 800-171 Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations Patricia Toth NIST MEP What is Information Security? Personnel Security Cybersecurity
Special Publication 800-171 Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations Patricia Toth NIST MEP What is Information Security? Personnel Security Cybersecurity
Using Classical Planners for Tasks with Con5nuous Ac5ons in Robo5cs
 Using Classical Planners for Tasks with Con5nuous Ac5ons in Robo5cs Stuart Russell Joint work with Siddharth Srivastava, Lorenzo Riano, Pieter Abbeel Using Classical Planners for Tasks with Con5nuous Ac5ons
Using Classical Planners for Tasks with Con5nuous Ac5ons in Robo5cs Stuart Russell Joint work with Siddharth Srivastava, Lorenzo Riano, Pieter Abbeel Using Classical Planners for Tasks with Con5nuous Ac5ons
Networking: Hardware, Rou?ng and new Challenges
 Mestrado em Engenharia Informá?ca e de Computadores Master Degree (MSc) in Informa?on Systems and Computer Engineering Administração e Gestão de Infra-estruturas de IT IT Infrastructure Management and
Mestrado em Engenharia Informá?ca e de Computadores Master Degree (MSc) in Informa?on Systems and Computer Engineering Administração e Gestão de Infra-estruturas de IT IT Infrastructure Management and
TerraSwarm. A Machine Learning and Op0miza0on Toolkit for the Swarm. Ilge Akkaya, Shuhei Emoto, Edward A. Lee. University of California, Berkeley
 TerraSwarm A Machine Learning and Op0miza0on Toolkit for the Swarm Ilge Akkaya, Shuhei Emoto, Edward A. Lee University of California, Berkeley TerraSwarm Tools Telecon 17 November 2014 Sponsored by the
TerraSwarm A Machine Learning and Op0miza0on Toolkit for the Swarm Ilge Akkaya, Shuhei Emoto, Edward A. Lee University of California, Berkeley TerraSwarm Tools Telecon 17 November 2014 Sponsored by the
The Meter-ON project. Marco Baron Enel Distribuzione. Steering the implementation of smart metering solutions throughout Europe
 Steering the implementa.on of smart metering solu.ons throughout Europe The Meter-ON project Steering the implementation of smart metering solutions throughout Europe Session 47: Operational challenges
Steering the implementa.on of smart metering solu.ons throughout Europe The Meter-ON project Steering the implementation of smart metering solutions throughout Europe Session 47: Operational challenges
NSF EAGER Collabora/ve Research Project: Towards a Unified Wireless Network Involving Reconfigurable Devices. Project Overview and Status
 NSF EAGER Collabora/ve Research Project: Towards a Unified Wireless Network Involving Reconfigurable Devices Project Overview and Status Last update: 5/6/2010 Principal Investigators Dr James Martin School
NSF EAGER Collabora/ve Research Project: Towards a Unified Wireless Network Involving Reconfigurable Devices Project Overview and Status Last update: 5/6/2010 Principal Investigators Dr James Martin School
Founda'ons of So,ware Engineering. Lecture 11 Intro to QA, Tes2ng Claire Le Goues
 Founda'ons of So,ware Engineering Lecture 11 Intro to QA, Tes2ng Claire Le Goues 1 Learning goals Define so;ware analysis. Reason about QA ac2vi2es with respect to coverage and coverage/adequacy criteria,
Founda'ons of So,ware Engineering Lecture 11 Intro to QA, Tes2ng Claire Le Goues 1 Learning goals Define so;ware analysis. Reason about QA ac2vi2es with respect to coverage and coverage/adequacy criteria,
Mul$media Techniques in Android. Some of the informa$on in this sec$on is adapted from WiseAndroid.com
 Mul$media Techniques in Android Some of the informa$on in this sec$on is adapted from WiseAndroid.com Mul$media Support Android provides comprehensive mul$media func$onality: Audio: all standard formats
Mul$media Techniques in Android Some of the informa$on in this sec$on is adapted from WiseAndroid.com Mul$media Support Android provides comprehensive mul$media func$onality: Audio: all standard formats
UNCLASSIFIED. R-1 ITEM NOMENCLATURE PE N: Surface ASW
 Exhibit R-2, RDT&E Budget Item Justification: PB 2012 Navy DATE: February 2011 COST ($ in Millions) FY 2010 FY 2011 FY 2013 FY 2014 FY 2015 FY 2016 Navy Page 1 of 10 R-1 Line Item #41 To Program Element
Exhibit R-2, RDT&E Budget Item Justification: PB 2012 Navy DATE: February 2011 COST ($ in Millions) FY 2010 FY 2011 FY 2013 FY 2014 FY 2015 FY 2016 Navy Page 1 of 10 R-1 Line Item #41 To Program Element
Collateral Damage. Impact of Frequent Policy Changes on Vendors and Customers
 Collateral Damage Impact of Frequent Policy Changes on Vendors and Customers Joshua Brickman Director, Security Evalua:ons Oracle Global Product Security Glenn BruneFe Dis:nguished Security Architect Oracle
Collateral Damage Impact of Frequent Policy Changes on Vendors and Customers Joshua Brickman Director, Security Evalua:ons Oracle Global Product Security Glenn BruneFe Dis:nguished Security Architect Oracle
Libraries are wri4en in C/C++ and compiled for the par>cular hardware.
 marakana.com 1 marakana.com 2 marakana.com 3 marakana.com 4 Libraries are wri4en in C/C++ and compiled for the par>cular hardware. marakana.com 5 The Dalvik virtual machine is a major piece of Google's
marakana.com 1 marakana.com 2 marakana.com 3 marakana.com 4 Libraries are wri4en in C/C++ and compiled for the par>cular hardware. marakana.com 5 The Dalvik virtual machine is a major piece of Google's
Tightly Integrated: Mike Cormier Bill Thackrey. Achieving Fast Time to Value with Splunk. Managing Directors Splunk Architects Concanon LLC
 Copyright 2014 Splunk Inc. Tightly Integrated: Achieving Fast Time to Value with Splunk Mike Cormier Bill Thackrey Managing Directors Splunk Cer@fied Architects Concanon LLC Disclaimer During the course
Copyright 2014 Splunk Inc. Tightly Integrated: Achieving Fast Time to Value with Splunk Mike Cormier Bill Thackrey Managing Directors Splunk Cer@fied Architects Concanon LLC Disclaimer During the course
OSNT A Community-owned platform for high-performance and low-cost network testing
 May, 14 2015 OSNT A Community-owned platform for high-performance and low-cost network testing Gianni Antichi gianni.antichi@cl.cam.ac.uk 1 Let s start with the context. We all know why we need network
May, 14 2015 OSNT A Community-owned platform for high-performance and low-cost network testing Gianni Antichi gianni.antichi@cl.cam.ac.uk 1 Let s start with the context. We all know why we need network
What Embedded can learn from IT Testing Techniques. Parasoft Rix Groenboom Mirosław Zielinski
 What Embedded can learn from IT Testing Techniques Parasoft Rix Groenboom (rixg@parasoft.com) Mirosław Zielinski (mirek@parasoft.com) Agenda Introduction Industry trends Inspiration from IT Suggestions
What Embedded can learn from IT Testing Techniques Parasoft Rix Groenboom (rixg@parasoft.com) Mirosław Zielinski (mirek@parasoft.com) Agenda Introduction Industry trends Inspiration from IT Suggestions
CCW Workshop Technical Session on Mobile Cloud Compu<ng
 CCW Workshop Technical Session on Mobile Cloud Compu
CCW Workshop Technical Session on Mobile Cloud Compu
Exadata Resource Management: Achieve Mind- blowing Performance, Consistently
 Managed Services Cloud Services Consul3ng Services Licensing Exadata Resource Management: Achieve Mind- blowing Performance, Consistently UTOUG Fall Symposium 2015 Kasey Parker Enterprise Architect Kasey.Parker@centroid.com
Managed Services Cloud Services Consul3ng Services Licensing Exadata Resource Management: Achieve Mind- blowing Performance, Consistently UTOUG Fall Symposium 2015 Kasey Parker Enterprise Architect Kasey.Parker@centroid.com
Where we are in the Course
 Where we are in the Course Star9ng the Transport Layer! Builds on the network layer to deliver data across networks for applica9ons with the desired reliability or quality Applica9on Transport Network
Where we are in the Course Star9ng the Transport Layer! Builds on the network layer to deliver data across networks for applica9ons with the desired reliability or quality Applica9on Transport Network
Leveraging User Session Data to Support Web Applica8on Tes8ng
 Leveraging User Session Data to Support Web Applica8on Tes8ng Authors: Sebas8an Elbaum, Gregg Rotheermal, Srikanth Karre, and Marc Fisher II Presented By: Rajiv Jain Outline Introduc8on Related Work Tes8ng
Leveraging User Session Data to Support Web Applica8on Tes8ng Authors: Sebas8an Elbaum, Gregg Rotheermal, Srikanth Karre, and Marc Fisher II Presented By: Rajiv Jain Outline Introduc8on Related Work Tes8ng
Cybersecurity Curricular Guidelines
 Cybersecurity Curricular Guidelines Ma2 Bishop, University of California Davis, co-chair Diana Burley The George Washington University, co-chair Sco2 Buck, Intel Corp. Joseph J. Ekstrom, Brigham Young
Cybersecurity Curricular Guidelines Ma2 Bishop, University of California Davis, co-chair Diana Burley The George Washington University, co-chair Sco2 Buck, Intel Corp. Joseph J. Ekstrom, Brigham Young
11/12/11. Objec&ves Overview. Databases, Data, and Informa&on. Objec&ves Overview. Databases, Data, and Informa&on. Databases, Data, and Informa&on
 Objec&ves Overview Define the term,, and explain how a interacts with and informa:on Define the term, integrity, and describe the quali:es of valuable informa:on Discuss the terms character, field, record,
Objec&ves Overview Define the term,, and explain how a interacts with and informa:on Define the term, integrity, and describe the quali:es of valuable informa:on Discuss the terms character, field, record,
Navy Cyber Resilience
 Unclassified Navy Cyber Resilience 20160614 Mr. Troy Johnson From cybersecurity to cyber resilience 2 Disconnected response through stove-piped assessments & initiatives across the enterprise: Operation
Unclassified Navy Cyber Resilience 20160614 Mr. Troy Johnson From cybersecurity to cyber resilience 2 Disconnected response through stove-piped assessments & initiatives across the enterprise: Operation
Large-scale Testbed and Cyber Range Organiza6on and Design
 CYBER RANGE ORGANIZATION AND DESIGN Large-scale Testbed and Cyber Range Organiza6on and Design Razvan Beuran, Ken-ichi Chinen Outline 1. Mo9va9on & overview 2. Making use of StarBED 3. Case studies 4.
CYBER RANGE ORGANIZATION AND DESIGN Large-scale Testbed and Cyber Range Organiza6on and Design Razvan Beuran, Ken-ichi Chinen Outline 1. Mo9va9on & overview 2. Making use of StarBED 3. Case studies 4.
Crowdsourcing the Acquisi3on and Analysis of Mobile Videos for Disaster Response
 IEEE Big Data 2015, October 31, 2015 Crowdsourcing the Acquisi3on and Analysis of Mobile Videos for Disaster Response Presented by Hien To Dr. Seon Ho Kim Integrated Media Systems Center University of
IEEE Big Data 2015, October 31, 2015 Crowdsourcing the Acquisi3on and Analysis of Mobile Videos for Disaster Response Presented by Hien To Dr. Seon Ho Kim Integrated Media Systems Center University of
Evaluating and Improving Software Usability
 Evaluating and Improving Software Usability 902 : Thursday, 9:30am - 10:45am Philip Lew www.xbosoft.com Understand, Evaluate and Improve 2 Agenda Introduc7on Importance of usability What is usability?
Evaluating and Improving Software Usability 902 : Thursday, 9:30am - 10:45am Philip Lew www.xbosoft.com Understand, Evaluate and Improve 2 Agenda Introduc7on Importance of usability What is usability?
Opera&ng Systems ECE344
 Opera&ng Systems ECE344 Lecture 10: Scheduling Ding Yuan Scheduling Overview In discussing process management and synchroniza&on, we talked about context switching among processes/threads on the ready
Opera&ng Systems ECE344 Lecture 10: Scheduling Ding Yuan Scheduling Overview In discussing process management and synchroniza&on, we talked about context switching among processes/threads on the ready
CS144 An Introduc8on to Computer Networks
 CS144 An Introduc8on to Computer Networks Packet Switching Philip Levis Oct 11, 2017 Packet Switching A Source R1 R2 R3 B Des8na8on R4 - Packets are routed individually, by looking up address in router
CS144 An Introduc8on to Computer Networks Packet Switching Philip Levis Oct 11, 2017 Packet Switching A Source R1 R2 R3 B Des8na8on R4 - Packets are routed individually, by looking up address in router
Embedded Compu+ng. Bill Drake Strategic Technology Manager Emerson Climate Technologies White Rodgers
 Bill Drake Strategic Technology Manager Emerson Climate Technologies White Rodgers Design and Opera+ng Constraints Power Cost User Interface I/O Heat Opera+onal Timing Robust Opera+on Recovery Security
Bill Drake Strategic Technology Manager Emerson Climate Technologies White Rodgers Design and Opera+ng Constraints Power Cost User Interface I/O Heat Opera+onal Timing Robust Opera+on Recovery Security
Search Engines. Informa1on Retrieval in Prac1ce. Annota1ons by Michael L. Nelson
 Search Engines Informa1on Retrieval in Prac1ce Annota1ons by Michael L. Nelson All slides Addison Wesley, 2008 Evalua1on Evalua1on is key to building effec$ve and efficient search engines measurement usually
Search Engines Informa1on Retrieval in Prac1ce Annota1ons by Michael L. Nelson All slides Addison Wesley, 2008 Evalua1on Evalua1on is key to building effec$ve and efficient search engines measurement usually
