Tracing Anonymous Mobile Attackers in Wireless Network
|
|
|
- Harold Lane
- 6 years ago
- Views:
Transcription
1 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July 2010 Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang *1, Shuhpyng Sheh *2 *1 Departent of Inforaton and Coputer Engneerng Chung Yuan Chrstan Unversty Chung L Cty, Taoyuan County 32054, Tawan *2 Departent of Coputer Scence & Inforaton Engneerng atonal Chao Tung Unversty Hsnchu Cty 300, Tawan hyang@cycu.edu.tw, ssp@cse.nctu.edu.tw do: /dcta.vol4.ssue4.16 Abstract In a floodng-based dstrbuted denal-of-servce (DDoS) attac, an adversary attepts to exhaust a target s coputng resource. To detect DDoS attacs n a networ envronent, IP tracebac ethods are deployed to deterne the orgn of attac pacets. Wth the ncrease n bandwdth of wreless networs, attacers ay choose ths edu fro whch to launch attacs. However, tracng the attacers n wreless networs s ore dffcult snce nteredate nodes ay ove or attacers ay change ther locaton to hde theselves. Thus, conventonal tracebac schees for wred networs cannot apply drectly to the wreless networ nfrastructure because the nteredate routers could be coprosed by an adversary. Therefore, we propose a flexble and lghtweght tracebac schee to deterne the source of attac pacets n a oble ad-hoc envronent. We wll deonstrate our ethod s ablty to trac the oveent of an attacer and recognze attac traffc launched by the sae attacer fro dfferent locatons. 1. Introducton Keywords: Wreless tracebac, Dstrbuted Denal of Servce Attac, Moble Wth the decreasng cost of access and ts ncreasng avalablty fro a plethora of devces and edus, the pact of attacs on the networ s becong ore sgnfcant and detrental. In a dstrbuted denal-of-servce (DDoS) attac, an adversary coprses a large nuber of hosts and uses the as zobes to generate large traffc flows aganst a target host. By consung the vct s resources, such as coputatonal power, eory usage, and networ bandwdth, the attacer can severely degrade or copletely deny noral servces [1]. Attac traffc ay coprse of SY pacets, ICMP pacets, or other 1 types of pacets [2][3]. owadays, any well-nown webstes, such as Yahoo! and Aazon, are under the threat of DDoS attac, resultng n llons of dollars n daage. The proble of DDoS stes fro the nature of the IP protocol desgn [4]. Because the IP protocol routes pacets by the destnaton address n the IP header wthout regard to the source address, an adversary ay nsert any address n the source address feld. Dependng upon the requested servce, the vct ay allocate resources for a host that s not expectng any servce. To cobat DDoS attacs, RFC 2827 [5] proposed ngress flters to chec that nbound traffc orgnates fro a vald IP address of an authorzed networ. Researchers have also suggested varous IP tracebac ethods, such as -trace [6], pacet loggng [7][8] and pacet arng [9][10][11], to detect the source of the attacs. In the -trace approach, Bellovn utlzes the ICMP pacet to probablstcally send tracebac nforaton. Unfortunately, routers frequently bloc ICMP essages because of ther securty rss. Pacet loggng requres extra storage overhead n routers along the route path to store tracebac data. In contrast, pacet arng utlzes the 16-bt ID feld of the IP header to save tracebac nforaton. Due to the lted aount of avalable bts n the header, pacet Ths wor was supported n part by atonal Scence Councl under the grants SC E
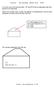
2 Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang, Shuhpyng Sheh arng schees probablstcally ar pacets wth partal tracebac nforaton. Therefore, the vct ust receve a suffcent aount of pacets to accurately reconstruct the attac path. To succeed n the wreless envronent, however, these schees requre odfcatons to adapt to the oblty of nodes. Wreless networs consst of nfrastructure ode and ad-hoc ode. In the nfrastructure ode, the wreless nodes connect drectly to the access pont (), whch acts as a edator between the wred and wreless networ. Conversely, nodes self-organze n the ad-hoc ode to create routng paths wth neghborng nodes. Dependng upon how ad-hoc routng protocols antan basc routng nforaton, they can be dvded nto proactve routng and reactve routng. Proactve routng protocols perodcally update the routng table even f there s no networ traffc. In contrast, reactve routng protocols only create routng paths as needed. Dynac Source Routng (DSR) [13] s a reactve routng protocol that eeps the full routng path n the header. Thus, nteredate nodes can forward pacets wth the header nforaton. Wth the growth of wreless devce usage and the ncrease n wreless bandwdth, adversares ay opt to generate attacs fro the wreless ad-hoc networ. The ablty to perfor IP tracebac n an adhoc networ wll becoe ore portant. Huang and Lee [14] developed a tracebac schee for adhoc networs based upon the SPIE schee [7]. SPIE aes use of a specal data structure, a bloo flter [15], to reduce the pacet loggng overhead on each router. Slarly, Huang and Lee s schee utlzes a tagged bloo flter, whch decreases the data overhead used to construct the ln graph. Wth the ln graph and neghbor lst, they can detect and locate a hotspot. In desgnng a tracebac schee, we want the ablty to trace an attac pacet to ts source n the adhoc networ. Snce nteredate and alcous nodes wthn the wreless networ can on, leave, or ove around, we would le our schee to be able to contnue tracng the attacer. That s, we would not consder that node as a new attacer. To the best of our nowledge, ths s the frst paper that acheves these goals. We organze the reander of ths paper as follows. In the next secton we elaborate on the networ archtecture and attac odel. ext, we descrbe our proposed schee n Secton 3 and evaluate ts ablty to detect attacers n Secton 4. Fnally, we conclude our fndngs n Secton Prelnares Before we begn, we dscuss our networ archtecture, assuptons, and threats. As depcted n Fgure 1, we focus on the attac odel n whch an adversary wthn an ad-hoc networ executes a DDoS attac aganst a reote server. When the server s Intruson Detecton Syste detects a DDoS attac, t ntates an IP tracebac on the wred networ to fnd the gateway. There exsts nuerous tracebac ethods [7][8][9][10][11] that can deterne the attac route fro the server to the end. To ferret out the adversary, the then perfors a trace on the wreless networ by utlzng our proposed schee. Our ethod eploys a cobnaton of loggng and pacet arng, whch t sends out of band (ICMP) to avod nterference wth tradtonal wred tracebac. To access the nternet n a wreless ad-hoc networ, one node acts as an and forwards pacets on behalf of eber nodes. Thus, ths node, whch we refer to as the, provdes a brdge between the wred and wreless doans. Our ad-hoc networ pleents the Dynac Source Routng (DSR) protocol to route essages aongst eber nodes. 162
3 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July 2010 Vct Ad-hoc etwor Attacer Assuptons Fgure 1. Archtecture We ae the followng assuptons: The ust possess enough coputaton, storage, and energy resources to perfor loggng and tracebac servces. The cannot be coprosed. Snce the handles loggng operatons, an under the control of an adversary cannot provde useful tracebac nforaton. Interedate nodes wthn the ad-hoc networ can be coprosed. Adversares ay change locatons wthn the ad-hoc networ or assocate wth other networs Threats An adversary ay attac the networ wth a varety of ethods. In the splest approach, the adversary captures a node and proceeds wth a DDoS attac aganst the server. In addton, the adversary ay nsert randoly generated source IP addresses nto attac pacets. Furtherore, the attacer ay relocate wthn ad-hoc networ to alter the routng path. 3. Wreless IP tracebac Schee We propose an IP tracebac schee (WTrac) to locate oble attacers n an ad-hoc networ. Frst, we descrbe how to create a Route Graph Hstory table. ext we show how an ars pacets. Last, we detal the process of how we tracebac oble adversares Routng Graph Hstory To pnpont attacers n a wreless networ, we need to deal wth the oblty ssues. When an receves a notce fro a vct s IDS, the wreless networ topology changes when a vct s under attac. Thus, we ntroduce Route Graph Hstory (RGH) to log the changes of the networ topology. Wth an s RGH table, we can have a snapshot of the networ topology when alcous pacets nvade the wreless networ. In the followng paragraphs we wll detal how to create a RGH table. In a dstrbuted syste, te synchronzaton s vtal n ensurng the transacton agreeents and events between nodes. However, te synchronzaton of all nodes requres hgher costs. To loosely synchronze te n a dstrbuted syste, we propose a RECORD_ROUTE() schee to collect the records and establsh a vrtual cloc T that represents the th change of the networ topology n an. 163
4 Te Sta p Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang, Shuhpyng Sheh Algorth RECORD_ROU TE() : Assuethe Current Testap at thes T P(, LR ) RGH(, LT ) CT T IF ( P(, LR ) or P(, LR ) P(, R ) ){ CT T 1 } IF(RGH(, CT) ){ RGH(, CT) P(, R )} Our ad-hoc networ odel contans n nodes, 2,, n wth access to the nternet through a gateway. LR ={LT 1, LT 2,,LT n } represents a lst of last updated testaps for node. P(,R ) sybolze the routng path startng fro th node that goes through route R to the, where R conssts of an ordered set of nodes. When the receves a pacet orgnatng fro at T, t checs whether the last updated path of node dffers fro the new pacet s path. If P(,R ) changes or does not exst, then the ncreases the vrtual cloc T to T +1 and records the new path P(,R ) wth the odfed testap T +1 n RGH(, T +1 ), where RGH(, T +1 ) eans -th colun and +1-th row n RGH table; otherwse, the cloc antans the sae value and the adds the unchanged path wth the current cloc P(,R ) to the RGH(, T ). ote that actual te ntervals between testaps are not necessarly the sae. That s, testap changes only when a route changes. T 4 T 3 P( 1,R 1) P( 2,R 2) P( 3,R 3) P( 2,R 2) T 3 P( 1,R 4) P( 2,R 2) P( 3,R 3) T 4 T 2 T 2 T 1 T 1 T 0 T Physcal Te(sec ) Fgure 2. Elapse of Testap on an Fgure 2 shows an exaple of antanng testap on an. Intally, testap s set to T 0. As Fgure 3(a) shows, when receves the frst pacet orgnatng fro at 2sec, t ncreases the testap to T 1 and records the path P(,R 1 )={,,, }on RGH table (Frst row of Table 1). Snce the node dd not sends any pacets to ths before recevng pacet P(,R 1 ). As Fgure 3(b) shows, the receves second pacet P( 2, R 1 ) at 4.5sec. Although the route fro 2 s sae wth the prevous route fro, the needs to ncrease the vrtual cloc to T 2 and records the path P( 2,R 1 )={ 2,,, } on RGH table. Snce the s RGH does not contan a prevous route for 2. It follows the sae procedure for the thrd pacet fro node 3 respectvely. For the fourth pacet fro node 2, the deternes the path of ths pacet s equvalent to the last updated path P( 2,R 2 ). Thus, t does not ncrease the vrtual cloc at T 3 ; however, the ust log ths path P( 2,R 2 ) snce ths route does not exst n the RGH table at te T 3. As Fgure 3(d) shows, when the receves the ffth pacet fro, t ncreases the testap to T 4 because the last updated 164
5 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July 2010 route of node,.e. R 1 ={,, }, s dfferent fro route R 4 ={, }, and records the path P(,R 4 ) on RGH table. Fnally, the log of pacets receved by ths s llustrated n Table 1. Table 1. Exaple RGH table ode Te 2 3 T 1 P(,R 1) T 2 P( 2,R 2) T 3 P( 2,R 2) P( 3,R 3) T 4 P(,R 4) P( 2,R 2) P( 3,R 3) We defne the graph G as the set of all routng paths durng te T. Thus, G { RGH ( 1, T ) RGH ( 2, T ) RGH ( n, T )} s the networ topology at te T. Fgure 3 shows exaples of networ topology constructed by usng the records of RGH table. On the thrd row of the table, two dsont paths are recorded at T. And the networ topology s drawn accordngly as Fgure 3(c) shows. At T 4, node follows dfferent route to send a pacet to the, and nodes 2 and 3 follow dentcal routes as before to route pacet to the. Then, the networ topology on the at T 4 wll loo le Fgure 3(d). Intally, the networ wll experence ore updates and changes to the global cloc as the populates the epty RGH table wth routng paths. When the networ stablzes, there should be fewer updates. odes whose routng paths rean null for an extended perod of te ay have left the networ. Durng an attac, however, the wll have to go through any updates as the adversary oves on the networ or spoofs any source routes. If we try to trace DDoS attacers fro vct to, we need to ar the pacet on an (a) (b) Fgure 3. Hstory etwor Topology n an (a) At testap T 1 (b) At testap T 2 (c) At testap T 3 (d) At testap T Pacet Marng Snce the extracts the source route fro each pacet s DSR header, t has a coplete vew of the ad-hoc networ s topology. However, forwardng a coplete source route to the server durng noral operatons s neffcent. To reduce networ bandwdth, the generates a hash to ar a pacet. The sends the pacet s ared data (MD) to the server wth the orgnal pacet out of band. The reason we send the MD out of band s to prevent the MD fro beng erased by wred tracebac ars. (c) (d) 165
6 Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang, Shuhpyng Sheh MD relates a pacet wth ts routng path and testap. It contans the pacet s testap, a hash of ts routng path, and a hash of the pacet s payload. That s, MD T HASH( RGH (, T ) ) HASH( Payload ), where s a strea concatenaton operator. The ar ncludes three parts and the frst s a testap, whch helps the recever now when the receves ths pacet. The second s the hash value of the wreless routng path, helpng the vct trace fro the to the attacer. The thrd part of the pacet ncludes ts hash value. Snce the ar s sent out of band, the hash value s used to connect attac pacet and the ar. As we assue the attac to be DDoS, the false postve can be elnated as ore and ore pacets coe n. We, therefore, recoend the dgest of pacet use the pacet header and soe bytes of payload as the nput of a unversal hash table. When the server receves the MD, t should retan the nforaton for a lted aount of te. For edate loo-up, the server puts the MD n a hash table, usng the payload hash as the ndex, and the testap and routng path hash as the value. Once detectng a DDoS attac, the server returns the MD to the, so that t can hunt down the attacer accordngly Moble Attacer Tracebac Schee When an adversary ntates a DoS attac on a server fro wreless ad-hoc networ, the adversary ay nsert randoly generated source IP addresses nto the attac pacets and then relocate wthn adhoc networ to alter the routng path. Therefore, the attac traffc that coes fro dfferent places could be launched by the sae attacer. If a tracng algorth cannot recognze the attac traffc whch probably coes fro the sae attacer, a nuber of attacers wll be recorded on a server. Also, t wll be dffcult for a vct to dentfy the current locaton of an attacer. However, the conventonal tracng algorths that are desgned for wred networ cannot trace oble attacers. Hence, an algorth MERGE_PATH s ntroduced to trace oble attacers and dentfy two attac traffc that coes fro two dfferent places but ght be launched by sae attacer l Attacers Fgure 4. Attac graph of Spoofed IP address attac. Gray nodes are attac nodes notfed by vcts When the receves an attac notce, t utlzes the algorth MERGE_PATH() to verfy whether the attacer s new or has ust sply oved; therefore, t can reduce the nuber of suspected attacers because soe of the do coe fro the sae source. After recevng an attac notce, an extracts fro the notce the MD wth P(,R ) and T, and checs f t atches the entry n ts RGH table. Snce an adversary ay spoof the address of the last hop along the wred networ, a satch s possble. As a result, the sply dscards ths attac notce. On the contrary, f the MD has ever appeared n the RGH table, t eans the server has successfully located the orgnatng. Therefore, the coences a search for the attacer wthn ts networ. When the tracs down the attacer, t adds ths node to the Attacer Lst (AL), a log of all alcous nodes at each nterval. The antans and 166
7 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July 2010 forwards the lst to the server. AL={AL 1, AL 2, AL 3,, AL n }, where AL =(,T n ) s -th attac node and testap receved and recorded n the. The notaton AL _= represents the attac node of the record AL, and AL _T= T n represents the testap of the record AL. Furtherore, the MERGE_PATH() erges attacers by tracng oveent n the attac graph. An attac graph at te T, denoted AG, represents a partal graph of G. That s, AG RGH (, T ), RGH (, T ),, RGH (, T )}, where AL. { 1 2 n The constructed graph AG s loop free because DSR s a loop free routng algorth. If a spoofng tool nserts a randoly generated source IP address nto attac pacets, as depcted n Fgure 4, lots of attac nodes route ther traffc through the sae nteredate node. The proposed schee MERGE_PATH() erges any two alcous nodes fro te T and fro te T n f the two nodes have the sae parent n a tree structure, so as to verfy whether the attacs are launched by the sae adversary. Three attac odels and ther tracng exaples wll be detaled below. If an adversary does not spoof the source address of ts attac pacets, the can trace the adversary by followng the attac graph. Even though the attacer changes locatons, he ust execute DSR s route dscovery to fnd a vald path to the. Snce any change of routes fro the attac source s recorded on the RGH table, attacers can be located because of attac graph tracng. As prevous attacng notces are generated for the sae attacer, the can reove all those notces fro AL to reduce the lst s sze. For exaple, as Fgure 5(a) shows, when the receves a new attac notce fro a vct (Fgure 5(b)), we erge the orgnal attac graph AG wth the new attac path nto a new attac graph. Snce the ovng adversary s attacng a vct, the erged attac graph, see Fgure 5(c), shows the attac traffc s launched by the source node 1, whch oves fro ts neghborng node 0 to node. Then, the old 1 s no longer needed and wll be reoved fro the attac graph. After reovng the duplcated nodes, the attac graph s shown as Fgure 5(d). n (a) (b) (c) (d) Fgure 5. Exaple of erged attac graphs, the gray nodes are dentfed attacers. (a) The attac graph before new attac notce. (b) recevng an attac notce. (c) The attac graph after the attac notce. (d) Attac graph after the ergng of two attacers
8 Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang, Shuhpyng Sheh As for those attacers who spoof ther source addresses, the ust generate an attac graph (AG) after gettng an attac notce because attac traffc that coes fro dfferent sources ay be launched by the sae attacer. AG conssts of the erged set of all MD that the receves,.e. AG { AG1, AG2,..., AGn }. Snce the routng path ay change as nteredate nodes on, ove, or leave the networ, a routng loop ay happen when ergng attac graphs fro dfferent te ntervals. If there s a loop n an attac graph, a tracng algorth ay fall nto the loop and ae t dffcult for the algorth to trace the source of the attac traffc. In order to reove a loop fro a graph, a path has to be reoved fro the graph to eep the graph loop free. We wll defne the to-bereoved path n the followng. We assue two attac graphs AG at T and AG at T, where T <T. If a sequence of nodes { s, p, q,, r, e } exsts n the graph AG=AG AG, where nodes s and e exst n the attac graphs AG and AG. SubP (AG,AG )={ p, q,, r } s a set of nodes n AG, not n AG. SubP (AG,AG )={ p, q,, r } s a set of nodes not n AG but n AG. The nodes { s, p, q,, r, e } wll be a loop n the erged graph AG (a) (b) (c) Fgure 6. Exaple of reovng loops fro an attac graph. (a) The attac graph before new attac notce. (b) recevng an attac notce. (c) The attac graph after the ergng of two attac graphs. (d) The attac graph after reovng a loop fro the graph. 1 (d) Snce the traffc oves fro node e to node s, t wll not choose the route SubP (AG,AG ) at T ; nstead, t uses the alternatve path SubP (AG,AG ) to route pacets. Therefore, MERGE_PATH() reoves the path SubP (AG,AG ) fro the erged graph AG so as to reove the loop fro the graph AG AG. Thus, the MERGE_PATH() traces an attacer fro the root of a tree to leaf nodes to locate 168
9 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July 2010 the attacer. Fgure 6 exeplfes the reovng of a loop fro a erged attac graph. When an receves an attac notce, ts rout s shown n Fgure 6(b). Because the ovng of nteredate nodes, the routng path wll begn to change fro the last transsson. We fnd the erged graph has a loop {, 9, 20, 0, } as Fgure 6(c) shows. Also, the nodes that send essages through node 0 do not follow the routng sequence (0,, ). Instead, the essage wll follow the route (0, 20,9, ). Because the pacets do not route through nodes (0,, ), we can reove the unwanted path (0,, ) fro the graph. Besdes, the tracng algorth can trace the attacer on the new loop-free attac graph. Algorth MERGE_PATH : Let IF ( ( IF AL { uberofattacers uberofattacers 1 Dff IF ( AL AL ( uberofattacers 1} ELSE { AG be an attacng nodesent fro a vct AG, T P( P(, T uberofattacers uberofattacers 1 Whle ( IF (( AL ) RGH ){ ) AL (( Dff (( Dff (( Dff, R _, T uberofattacers uberofattacers 1 AL AL AL }} AL AL ( } dscard the notce AG, R, T ) ) ) ( P( AL and no atch){ n 1) and ( AL 1) and ( AL 2) and ( AL, T )} P(, R, R ) AL and ( n ) AG) SubP ( AG, P( _ - parent _ - parent- parent _ - parent- parent - parent- parent)))){ ) SubP ( AG P(, R )), R )) - parent))or n - parent)) or Snce the nodes n an ad-hoc networ can be coprosed by an adversary, these coprosed nodes wll be steppng stone for attacers. Soetes an attacer coproses a host n the ddle of ts routng path and uses the coprosed nodes to reove all tracng clues fro the transtted pacets. When MERGE_PATH() traces the source of attac traffc, t wll dentfy the attac node as alcous users steppng stone, and the attac node wll not be a leaf of the attac graph. If the routng path fro the real attacer to the steppng stone s steady, the attacer can hde hself behnd the steppng stone and our schee cannot locate h. Then, he wll be logged on the and dentfed as another attacer,.e. hs steppng stone actually, n the attac graph. n Fgure 6(a) exeplfes a steppng stone n an attac graph. In the prevous Moble Attacer Tracng Schee, we focus on sngle access pont tracebac. However, t s possble for a oble attacer to roa fro one to another. When an attacer roas between two s, they should exchange ther RGH records wth each other to antan the correctness of pacet transsson, le regstraton nforaton n Moble IP. That s to say the s able to now the address of the roang nodes. When an attacer tres to generate attac pacets fro one to another, the two s RGH should be cobned to trace the attacer. 169
10 Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang, Shuhpyng Sheh For nstance, when an attacer roas fro 1 to 2, the vct can get RGH 1 and RGH 2 fro the traced. However, the proble of dstrbuted RGH s that the two RGHs are not synchronzed. That s to say, when RGHs are not synchronzed, the only way to erge two attacers s to scan all the tables for nown attacers and te slces. Hence, when we exchange RGH 1 and RGH 2, the two s can synchronze the two RGHs by atchng the two tables T ax. Wth regular exchange of RGH 1 and RGH 2, we can create the appng of T ax for 1 and 2 respectvely. Then, we can lt the scan sze of the table and synchronze the two RGHs. Fgure 7 llustrates how two RGHs eep ther own counters and synchronze each other. Fgure 7. Two Route Graph Hstory and synchronzaton To trace an attacer, we can use the orgnal approach, but the scan range wll have to extend fro a table to two and the testaps for the two tables need to be reapped. For nstance, as llustrated n Fgure 7, after the reappng, we fnd: T 1 on RGH 1 T 2 on RGH 2 ; T 4 on RGH 1 T 4 on RGH 2 ; T 6 and T 8 on RGH 1 T 7 on RGH Sulaton We use the ns2 sulator [17] to test our schee s ablty n locatng an adversary. In general, we setup the sulatons wth the default wreless envronent confguraton for channel, propagaton, ln layer type, nterface queue type, Meda Access Control, and antenna. For the DSR agent, we confgure the flow state and send buffer. ext, we center the n our test grd and enable t to forward pacets to the. Then, we generate 50 oble nodes usng the ns2 s ndep-utls/cu-scengen/setdest and log DSR pacets wth CMUTrace. Every node s able to send vald UDP pacets to. Malcous nodes ay ove through the networ at a faster but reasonable rate. Interedate nodes ay ove along a routng path. In the frst sulaton, we deonstrate our schee s ablty to dentfy a oble DoS attac by ergng attac graphs even though nteredate nodes oves durng attacs. In Fgure 8, we fnd that the networ sze does not affect the accuracy of our schee when we verfy that the attac traffc sent fro dfferent locatons s, n fact, generated fro the sae source. Then, we dentfy those attacs as one and erge the nto one. By consderng networ of up to 50 nodes, we are able to erge 90% of all attac traffc launched by the sae attacers. 170
11 Probablty Probablty Probablty Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July nodes 4 nodes 3 nodes 2 nodes etwor Sze Fgure 8. Effect of networ sze We fnd that exanng a larger nuber of oved nteredate nodes yelds hgher ergng rate. Snce the ovng of nteredate nodes ae the change of networ topology, t provdes ore nforaton for us to analyze the oveent of an attacer nodes 30 nodes 40 nodes 50 nodes uer of Movng Interedate odes Fgure 9. Effect of ovng routers ext, we wll prove that our schee s able to detect spoofed source IP addresses. As llustrated n Fgure 10, we fnd that our schee can successfully trace over 99% of all randoly generated source IP addresses etwor Sze Fgure 10. Spoofed IP address detecton rate 171
12 Probablty Tracng Anonyous Moble Attacers n Wreless etwor Mng Hour Yang, Shuhpyng Sheh Fnally, we test f our schee yelds the correct nuber of attacers between te ntervals. That s, our schee wll not double count a ovng adversary even though t tres to spoof ts source address. Fgure 11 llustrates that our schee can successfully hunt down adversares wth 99% accuracy Spoof Rate 5. Concluson Fgure 11. True postve rate In ths paper, we ntroduce a tracebac schee for wreless networs runnng Dynac Source Routng. Copared to exstng tracebac schees, our ethod can trace an adversary to ts source, even f he changes locatons. Furtherore, our schee can deterne f a set of attac pacets orgnate fro the adversary. Our sulatons show that our schee can detect duplcate attacers wth 99% effectveness. 6. References [1] Vern Paxson, "An analyss of usng reflectors for dstrbuted denal-of-servce attacs," ACM Cop. Co. Revew, vol. 31, no. 3, 2001.Author1_ae, Author2_ae, Web Cachng and Replcaton, Addson-Wesley(Publcaton_ ae), USA, 2014 [2] Davd Moore, GeoRrey M. Voeler, and Stefan Savage, "Inferrng nternet Denal-of-Servce actvty," n In proceedngs of the 2001 USEIX Securty Syposu, 2001, pp [3] Mcrosoft Corporaton, "Stop 0A n tcpp.sys when recevng out of band(oob) data," [4] J. Postel, "Ineternet Protocol," RFC 791, IETF, Spe [5] Paul Ferguson and Danel Sene, "etwor ngress flterng: Defeatng denal of servce attacs whch eploy IP source address spoofng," RFC 2827, IETF, May [6] Steven M. Bellovn, "Icp tracebac essages," IETF Draft, 2000, [7] Alex C. Snoeren, Crag Partrdge, Lus A. Sanchez, Chrstne E. Jones, Fabrce Tchaounto, Beverly Schwartz, Stephen T. Kent, and W. Tothy Strayers, "Hash-Based IP Tracebac," n ACM SIGCOMM '01, August [8] Alex C. Snoeren, Crag Partrdge, Lus A. Sanchez, Chrstne E. Jones, Fabrce Tchaounto, Beverly Schwartz, Stephen T. Kent, and W. Tothy Strayers, "Sngle-Pacet IP Tracebac," IEEE/ACM Transactons on etworng, vol. 10, no. 6, pp , Deceber [9] Stefan Savage, DavdWetherall, Anna Karln, and To Anderson, "etwor Support for IP Tracebac," IEEE/ACM Transactons on etworng, vol. 9, no. 3, pp , June [10] Hal Burch and Bll Cheswc, "Tracng anonyous pacets to ther approxate source," In Proc. USEIX LISA '00, Deceber [11] D. X. Song and A. Perrg, "Advanced and Authentcated Marng Schees for IP Tracebac Messages," n Proc. IEEE Infoco '01, Aprl [12] C. Perns, "Ad hoc on deand dstance vector (aodv) routng,"
13 Internatonal Journal of Dgtal Content Technology and ts Applcatons Volue 4, uber 4, July 2010 [13] Davd B. Johnson, Davd A. Maltz, and Yh-Chun Hu, "The Dynac Source Routng Protocol for Moble Ad Hoc etwors (DSR)," IETF Draft, 2004, [14] Y and Huang and Wene Lee, "Hotspot-based tracebac for oble ad hoc networs," n WSe '05: Proceedngs of the 4th ACM worshop on Wreless securty, ew Yor, Y, USA, 2005, pp , ACM Press. [15] Burton H. Bloo, "Space/Te Trade-ORs n Hash Codng wth Allowable Errors," Councaton of ACM, vol. 13, no. 7, pp , July [16] J. Reynolds J. Postel, "TELET PROTOCOL SPECIFICATIO," RFC 854, IETF, May [17] Steven McCanne and Sally Floyd, "ns etwor Sulator," 173
Introduction. Leslie Lamports Time, Clocks & the Ordering of Events in a Distributed System. Overview. Introduction Concepts: Time
 Lesle Laports e, locks & the Orderng of Events n a Dstrbuted Syste Joseph Sprng Departent of oputer Scence Dstrbuted Systes and Securty Overvew Introducton he artal Orderng Logcal locks Orderng the Events
Lesle Laports e, locks & the Orderng of Events n a Dstrbuted Syste Joseph Sprng Departent of oputer Scence Dstrbuted Systes and Securty Overvew Introducton he artal Orderng Logcal locks Orderng the Events
On-line Scheduling Algorithm with Precedence Constraint in Embeded Real-time System
 00 rd Internatonal Conference on Coputer and Electrcal Engneerng (ICCEE 00 IPCSIT vol (0 (0 IACSIT Press, Sngapore DOI: 077/IPCSIT0VNo80 On-lne Schedulng Algorth wth Precedence Constrant n Ebeded Real-te
00 rd Internatonal Conference on Coputer and Electrcal Engneerng (ICCEE 00 IPCSIT vol (0 (0 IACSIT Press, Sngapore DOI: 077/IPCSIT0VNo80 On-lne Schedulng Algorth wth Precedence Constrant n Ebeded Real-te
Security Enhanced Dynamic ID based Remote User Authentication Scheme for Multi-Server Environments
 Internatonal Journal of u- and e- ervce, cence and Technology Vol8, o 7 0), pp7-6 http://dxdoorg/07/unesst087 ecurty Enhanced Dynamc ID based Remote ser Authentcaton cheme for ult-erver Envronments Jun-ub
Internatonal Journal of u- and e- ervce, cence and Technology Vol8, o 7 0), pp7-6 http://dxdoorg/07/unesst087 ecurty Enhanced Dynamc ID based Remote ser Authentcaton cheme for ult-erver Envronments Jun-ub
Solutions to Programming Assignment Five Interpolation and Numerical Differentiation
 College of Engneerng and Coputer Scence Mechancal Engneerng Departent Mechancal Engneerng 309 Nuercal Analyss of Engneerng Systes Sprng 04 Nuber: 537 Instructor: Larry Caretto Solutons to Prograng Assgnent
College of Engneerng and Coputer Scence Mechancal Engneerng Departent Mechancal Engneerng 309 Nuercal Analyss of Engneerng Systes Sprng 04 Nuber: 537 Instructor: Larry Caretto Solutons to Prograng Assgnent
Secure Communication over Heterogeneous Networks with Clustered Mobile Ad hoc Extensions
 Secure Councaton over Heterogeneous Networs wth Clustered Moble Ad hoc Extensons Dtros Vogatzs, Spyrdon Vasslaras and Gregory S. Yovanof Athens Inforaton Technology e-al: {dvog, svas, gyov}@at.edu.gr Abstract
Secure Councaton over Heterogeneous Networs wth Clustered Moble Ad hoc Extensons Dtros Vogatzs, Spyrdon Vasslaras and Gregory S. Yovanof Athens Inforaton Technology e-al: {dvog, svas, gyov}@at.edu.gr Abstract
Merging Results by Using Predicted Retrieval Effectiveness
 Mergng Results by Usng Predcted Retreval Effectveness Introducton Wen-Cheng Ln and Hsn-Hs Chen Departent of Coputer Scence and Inforaton Engneerng Natonal Tawan Unversty Tape, TAIWAN densln@nlg.cse.ntu.edu.tw;
Mergng Results by Usng Predcted Retreval Effectveness Introducton Wen-Cheng Ln and Hsn-Hs Chen Departent of Coputer Scence and Inforaton Engneerng Natonal Tawan Unversty Tape, TAIWAN densln@nlg.cse.ntu.edu.tw;
An Efficient Fault-Tolerant Multi-Bus Data Scheduling Algorithm Based on Replication and Deallocation
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volue 16, No Sofa 016 Prnt ISSN: 1311-970; Onlne ISSN: 1314-4081 DOI: 10.1515/cat-016-001 An Effcent Fault-Tolerant Mult-Bus Data
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volue 16, No Sofa 016 Prnt ISSN: 1311-970; Onlne ISSN: 1314-4081 DOI: 10.1515/cat-016-001 An Effcent Fault-Tolerant Mult-Bus Data
A study of Adaptive Replication Technique in routing time-constrained messages (VoIP) in MANET
 A study of Adaptve Replcaton Technque n routng te-constraned essages (VoIP) n MANET SWATI SAXENA Research Scholar AIM & ACT Banasthal Vdyapth Banasthal, (Ra.) Dr. MADHAVI SINHA Asst. Prof. (HOD) Dept.
A study of Adaptve Replcaton Technque n routng te-constraned essages (VoIP) n MANET SWATI SAXENA Research Scholar AIM & ACT Banasthal Vdyapth Banasthal, (Ra.) Dr. MADHAVI SINHA Asst. Prof. (HOD) Dept.
Evaluation of an Enhanced Scheme for High-level Nested Network Mobility
 IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.15 No.10, October 2015 1 Evaluaton of an Enhanced Scheme for Hgh-level Nested Network Moblty Mohammed Babker Al Mohammed, Asha Hassan.
IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.15 No.10, October 2015 1 Evaluaton of an Enhanced Scheme for Hgh-level Nested Network Moblty Mohammed Babker Al Mohammed, Asha Hassan.
126 Int. J. Ad Hoc and Ubiquitous Computing, Vol. 1, No. 3, Djamel Djenouri*
 126 Int. J. Ad Hoc and Ubqutous Coputng, Vol. 1, No. 3, 2006 New power-aware routng protocol for oble ad hoc networks Djael Djenour* Basc Software Laboratory, CERIST Center of Research, Algers, Algera
126 Int. J. Ad Hoc and Ubqutous Coputng, Vol. 1, No. 3, 2006 New power-aware routng protocol for oble ad hoc networks Djael Djenour* Basc Software Laboratory, CERIST Center of Research, Algers, Algera
Handover Delay Estimation Method for IMS-Based Systems with Heterogeneous Access Networks
 Councatons 07; (): -7 http://www.scencepublshnggroup.co/j/co do: 0.8/j.co.0700. ISSN: 8-9 (Prnt); ISSN: 8-9 (Onlne) Handover Delay Estaton Method for IMS-Based Systes wth Heterogeneous Access Networks
Councatons 07; (): -7 http://www.scencepublshnggroup.co/j/co do: 0.8/j.co.0700. ISSN: 8-9 (Prnt); ISSN: 8-9 (Onlne) Handover Delay Estaton Method for IMS-Based Systes wth Heterogeneous Access Networks
Virtual Memory. Background. No. 10. Virtual Memory: concept. Logical Memory Space (review) Demand Paging(1) Virtual Memory
 Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
An Optimal Algorithm for Prufer Codes *
 J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
2016 International Conference on Sustainable Energy, Environment and Information Engineering (SEEIE 2016) ISBN:
 06 Internatonal Conference on Sustanable Energy, Envronent and Inforaton Engneerng (SEEIE 06) ISBN: 978--60595-337-3 A Study on IEEE 80. MAC Layer Msbehavor under Dfferent Back-off Algorths Trong Mnh HOANG,,
06 Internatonal Conference on Sustanable Energy, Envronent and Inforaton Engneerng (SEEIE 06) ISBN: 978--60595-337-3 A Study on IEEE 80. MAC Layer Msbehavor under Dfferent Back-off Algorths Trong Mnh HOANG,,
Color Image Segmentation Based on Adaptive Local Thresholds
 Color Iage Segentaton Based on Adaptve Local Thresholds ETY NAVON, OFE MILLE *, AMI AVEBUCH School of Coputer Scence Tel-Avv Unversty, Tel-Avv, 69978, Israel E-Mal * : llero@post.tau.ac.l Fax nuber: 97-3-916084
Color Iage Segentaton Based on Adaptve Local Thresholds ETY NAVON, OFE MILLE *, AMI AVEBUCH School of Coputer Scence Tel-Avv Unversty, Tel-Avv, 69978, Israel E-Mal * : llero@post.tau.ac.l Fax nuber: 97-3-916084
A Unified Approach to Survivability of Connection-Oriented Networks
 A Unfed Approach to Survvablty of Connecton-Orented Networs Krzysztof Walowa Char of Systes and Coputer Networs, Faculty of Electroncs, Wroclaw Unversty of Technology, Wybrzeze Wyspansego 27, 50-370 Wroclaw,
A Unfed Approach to Survvablty of Connecton-Orented Networs Krzysztof Walowa Char of Systes and Coputer Networs, Faculty of Electroncs, Wroclaw Unversty of Technology, Wybrzeze Wyspansego 27, 50-370 Wroclaw,
6.854 Advanced Algorithms Petar Maymounkov Problem Set 11 (November 23, 2005) With: Benjamin Rossman, Oren Weimann, and Pouya Kheradpour
 6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
Constructing Minimum Connected Dominating Set: Algorithmic approach
 Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
An Adaptive Sleep Strategy for Energy Conservation in Wireless Sensor Networks
 An Adaptve Sleep Strategy for Energy Conservaton n Wreless Sensor Networks Guseppe Anastas, Marco Cont, Maro D Francesco Abstract - In recent years, wreless sensor network deployents for real lfe applcatons
An Adaptve Sleep Strategy for Energy Conservaton n Wreless Sensor Networks Guseppe Anastas, Marco Cont, Maro D Francesco Abstract - In recent years, wreless sensor network deployents for real lfe applcatons
Multicast Tree Rearrangement to Recover Node Failures. in Overlay Multicast Networks
 Multcast Tree Rearrangeent to Recover Node Falures n Overlay Multcast Networks Hee K. Cho and Chae Y. Lee Dept. of Industral Engneerng, KAIST, 373-1 Kusung Dong, Taejon, Korea Abstract Overlay ultcast
Multcast Tree Rearrangeent to Recover Node Falures n Overlay Multcast Networks Hee K. Cho and Chae Y. Lee Dept. of Industral Engneerng, KAIST, 373-1 Kusung Dong, Taejon, Korea Abstract Overlay ultcast
A Theory of Non-Deterministic Networks
 A Theory of Non-Deternstc Networs Alan Mshcheno and Robert K rayton Departent of EECS, Unversty of Calforna at ereley {alan, brayton}@eecsbereleyedu Abstract oth non-deterns and ult-level networs copactly
A Theory of Non-Deternstc Networs Alan Mshcheno and Robert K rayton Departent of EECS, Unversty of Calforna at ereley {alan, brayton}@eecsbereleyedu Abstract oth non-deterns and ult-level networs copactly
User Behavior Recognition based on Clustering for the Smart Home
 3rd WSEAS Internatonal Conference on REMOTE SENSING, Vence, Italy, Noveber 2-23, 2007 52 User Behavor Recognton based on Clusterng for the Sart Hoe WOOYONG CHUNG, JAEHUN LEE, SUKHYUN YUN, SOOHAN KIM* AND
3rd WSEAS Internatonal Conference on REMOTE SENSING, Vence, Italy, Noveber 2-23, 2007 52 User Behavor Recognton based on Clusterng for the Sart Hoe WOOYONG CHUNG, JAEHUN LEE, SUKHYUN YUN, SOOHAN KIM* AND
Routing Time-Constrained Traffic in Wireless Sensor Networks
 Routng Te-Constraned Traffc n Wreless Sensor Networks Keal Akkaya and Mohaed Youns Departent of Coputer Scence and Electrcal Engneerng Unversty of Maryland, Baltore County Baltore, MD 2250 keal youns@cs.ubc.edu
Routng Te-Constraned Traffc n Wreless Sensor Networks Keal Akkaya and Mohaed Youns Departent of Coputer Scence and Electrcal Engneerng Unversty of Maryland, Baltore County Baltore, MD 2250 keal youns@cs.ubc.edu
ALM-FastReplica: Optimizing the Reliable Distribution of Large Files within CDNs
 ALM-FastReplca: Optzng the Relable Dstrbuton of Large Fles wthn CDNs Ludla Cherkasova Internet Systes and Storage Laboratory HP Laboratores Palo Alto HPL-005-64 Aprl 4, 005* E-al: cherkasova@hpl.hp.co
ALM-FastReplca: Optzng the Relable Dstrbuton of Large Fles wthn CDNs Ludla Cherkasova Internet Systes and Storage Laboratory HP Laboratores Palo Alto HPL-005-64 Aprl 4, 005* E-al: cherkasova@hpl.hp.co
Security Vulnerabilities of an Enhanced Remote User Authentication Scheme
 Contemporary Engneerng Scences, Vol. 7, 2014, no. 26, 1475-1482 HIKARI Ltd, www.m-hkar.com http://dx.do.org/10.12988/ces.2014.49186 Securty Vulnerabltes of an Enhanced Remote User Authentcaton Scheme Hae-Soon
Contemporary Engneerng Scences, Vol. 7, 2014, no. 26, 1475-1482 HIKARI Ltd, www.m-hkar.com http://dx.do.org/10.12988/ces.2014.49186 Securty Vulnerabltes of an Enhanced Remote User Authentcaton Scheme Hae-Soon
TN348: Openlab Module - Colocalization
 TN348: Openlab Module - Colocalzaton Topc The Colocalzaton module provdes the faclty to vsualze and quantfy colocalzaton between pars of mages. The Colocalzaton wndow contans a prevew of the two mages
TN348: Openlab Module - Colocalzaton Topc The Colocalzaton module provdes the faclty to vsualze and quantfy colocalzaton between pars of mages. The Colocalzaton wndow contans a prevew of the two mages
A New Scheduling Algorithm for Servers
 A New Schedulng Algorth for Servers Nann Yao, Wenbn Yao, Shaobn Ca, and Jun N College of Coputer Scence and Technology, Harbn Engneerng Unversty, Harbn, Chna {yaonann, yaowenbn, cashaobn, nun}@hrbeu.edu.cn
A New Schedulng Algorth for Servers Nann Yao, Wenbn Yao, Shaobn Ca, and Jun N College of Coputer Scence and Technology, Harbn Engneerng Unversty, Harbn, Chna {yaonann, yaowenbn, cashaobn, nun}@hrbeu.edu.cn
A system based on a modified version of the FCM algorithm for profiling Web users from access log
 A syste based on a odfed verson of the FCM algorth for proflng Web users fro access log Paolo Corsn, Laura De Dosso, Beatrce Lazzern, Francesco Marcellon Dpartento d Ingegnera dell Inforazone va Dotsalv,
A syste based on a odfed verson of the FCM algorth for proflng Web users fro access log Paolo Corsn, Laura De Dosso, Beatrce Lazzern, Francesco Marcellon Dpartento d Ingegnera dell Inforazone va Dotsalv,
Related-Mode Attacks on CTR Encryption Mode
 Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
3D vector computer graphics
 3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
Parallelism for Nested Loops with Non-uniform and Flow Dependences
 Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Equation Based Rate Control and Multiple Connections for Adaptive Video Streaming in Cellular Networks
 Equaton Based Rate Control and Multple Connectons for Adaptve Vdeo Streang n Cellular Networks A. Mardanan Dehkord and V. Tabataba Vakl Abstract Rate control s an portant ssue for vdeo streang n cellular
Equaton Based Rate Control and Multple Connectons for Adaptve Vdeo Streang n Cellular Networks A. Mardanan Dehkord and V. Tabataba Vakl Abstract Rate control s an portant ssue for vdeo streang n cellular
Energy-aware Delay-Constrained Routing in Wireless Sensor Networks
 Energy-aware Delay-Constraned Routng n Wreless Sensor Networks Keal Akkaya and Mohaed Youns Departent of Coputer Scence and Electrcal Engneerng Unversty of Maryland Baltore County, Baltore, MD 21250 {keal1,
Energy-aware Delay-Constraned Routng n Wreless Sensor Networks Keal Akkaya and Mohaed Youns Departent of Coputer Scence and Electrcal Engneerng Unversty of Maryland Baltore County, Baltore, MD 21250 {keal1,
AN ALGORITHM FOR ODD GRACEFULNESS OF THE TENSOR PRODUCT OF TWO LINE GRAPHS
 Internatonal ournal on applcatons of graph theory n wreless ad hoc networks and sensor networks (GRAPH-HOC) Vol.3, No., March 0 AN ALGORITHM FOR ODD GRACEFULNESS OF THE TENSOR PRODUCT OF TWO LINE GRAPHS
Internatonal ournal on applcatons of graph theory n wreless ad hoc networks and sensor networks (GRAPH-HOC) Vol.3, No., March 0 AN ALGORITHM FOR ODD GRACEFULNESS OF THE TENSOR PRODUCT OF TWO LINE GRAPHS
CMPS 10 Introduction to Computer Science Lecture Notes
 CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
Compiler Design. Spring Register Allocation. Sample Exercises and Solutions. Prof. Pedro C. Diniz
 Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Scheduling Workflow Applications on the Heterogeneous Cloud Resources
 Indan Journal of Scence and Technology, Vol 8(2, DOI: 0.7485/jst/205/v82/57984, June 205 ISSN (rnt : 0974-6846 ISSN (Onlne : 0974-5645 Schedulng Workflow Applcatons on the Heterogeneous Cloud Resources
Indan Journal of Scence and Technology, Vol 8(2, DOI: 0.7485/jst/205/v82/57984, June 205 ISSN (rnt : 0974-6846 ISSN (Onlne : 0974-5645 Schedulng Workflow Applcatons on the Heterogeneous Cloud Resources
Load Balancing Algorithm for Web Server Based on Weighted Minimal Connections
 Journal of Web ystes and Applcatons (2017) Vol. 1, Nuuber 1 Clausus centfc Press, Canada Load Balancng Algorth for Web erver Based on Weghted Mnal Connectons Pan Zhu1, a, Jangxng Zhang 2,b College of Inforaton
Journal of Web ystes and Applcatons (2017) Vol. 1, Nuuber 1 Clausus centfc Press, Canada Load Balancng Algorth for Web erver Based on Weghted Mnal Connectons Pan Zhu1, a, Jangxng Zhang 2,b College of Inforaton
Efficient Distributed File System (EDFS)
 Effcent Dstrbuted Fle System (EDFS) (Sem-Centralzed) Debessay(Debsh) Fesehaye, Rahul Malk & Klara Naherstedt Unversty of Illnos-Urbana Champagn Contents Problem Statement, Related Work, EDFS Desgn Rate
Effcent Dstrbuted Fle System (EDFS) (Sem-Centralzed) Debessay(Debsh) Fesehaye, Rahul Malk & Klara Naherstedt Unversty of Illnos-Urbana Champagn Contents Problem Statement, Related Work, EDFS Desgn Rate
Synchronous Distributed Wireless Network Emulator for High-Speed Mobility: Implementation and Evaluation
 Synchronous Dstrbuted Wreless Network Emulator for Hgh-Speed Moblty: Implementaton and Evaluaton Mnoru Kozum, Tomoch Ebata Yokohama Research Laboratory, Htach, Ltd., 292 Yoshda-cho, Totsuka-ku, Yokohama,
Synchronous Dstrbuted Wreless Network Emulator for Hgh-Speed Moblty: Implementaton and Evaluaton Mnoru Kozum, Tomoch Ebata Yokohama Research Laboratory, Htach, Ltd., 292 Yoshda-cho, Totsuka-ku, Yokohama,
Wightman. Mobility. Quick Reference Guide THIS SPACE INTENTIONALLY LEFT BLANK
 Wghtman Moblty Quck Reference Gude THIS SPACE INTENTIONALLY LEFT BLANK WIGHTMAN MOBILITY BASICS How to Set Up Your Vocemal 1. On your phone s dal screen, press and hold 1 to access your vocemal. If your
Wghtman Moblty Quck Reference Gude THIS SPACE INTENTIONALLY LEFT BLANK WIGHTMAN MOBILITY BASICS How to Set Up Your Vocemal 1. On your phone s dal screen, press and hold 1 to access your vocemal. If your
Research on Prediction Technique of Network Situation Awareness
 Research on Predcton Technque of Networ Stuaton Awareness Juan Wang,ZhGuang Qn,L Ye School of Coputer Scence and Engneerng Unversty of Electronc Scence and Technology Chengdu, Chna {wangjuan,qnzg}@uestc.edu.cn,
Research on Predcton Technque of Networ Stuaton Awareness Juan Wang,ZhGuang Qn,L Ye School of Coputer Scence and Engneerng Unversty of Electronc Scence and Technology Chengdu, Chna {wangjuan,qnzg}@uestc.edu.cn,
Human Face Recognition Using Radial Basis Function Neural Network
 Huan Face Recognton Usng Radal Bass Functon eural etwor Javad Haddadna Ph.D Student Departent of Electrcal and Engneerng Arabr Unversty of Technology Hafez Avenue, Tehran, Iran, 594 E-al: H743970@cc.au.ac.r
Huan Face Recognton Usng Radal Bass Functon eural etwor Javad Haddadna Ph.D Student Departent of Electrcal and Engneerng Arabr Unversty of Technology Hafez Avenue, Tehran, Iran, 594 E-al: H743970@cc.au.ac.r
Two-Factor User Authentication in Multi-Server Networks
 Internatonal Journal of ecurty and Its Applcatons Vol. 6, No., Aprl, 0 Two-Factor ser Authentcaton n Mult-erver Networks Chun-Ta L, Ch-Yao Weng,* and Chun-I Fan Department of Informaton Management, Tanan
Internatonal Journal of ecurty and Its Applcatons Vol. 6, No., Aprl, 0 Two-Factor ser Authentcaton n Mult-erver Networks Chun-Ta L, Ch-Yao Weng,* and Chun-I Fan Department of Informaton Management, Tanan
Outline. Third Programming Project Two-Dimensional Arrays. Files You Can Download. Exercise 8 Linear Regression. General Regression
 Project 3 Two-densonal arras Ma 9, 6 Thrd Prograng Project Two-Densonal Arras Larr Caretto Coputer Scence 6 Coputng n Engneerng and Scence Ma 9, 6 Outlne Quz three on Thursda for full lab perod See saple
Project 3 Two-densonal arras Ma 9, 6 Thrd Prograng Project Two-Densonal Arras Larr Caretto Coputer Scence 6 Coputng n Engneerng and Scence Ma 9, 6 Outlne Quz three on Thursda for full lab perod See saple
Non-Split Restrained Dominating Set of an Interval Graph Using an Algorithm
 Internatonal Journal of Advancements n Research & Technology, Volume, Issue, July- ISS - on-splt Restraned Domnatng Set of an Interval Graph Usng an Algorthm ABSTRACT Dr.A.Sudhakaraah *, E. Gnana Deepka,
Internatonal Journal of Advancements n Research & Technology, Volume, Issue, July- ISS - on-splt Restraned Domnatng Set of an Interval Graph Usng an Algorthm ABSTRACT Dr.A.Sudhakaraah *, E. Gnana Deepka,
Securing Quality-of-Service Route Discovery in On-Demand Routing for Ad Hoc Networks
 Securng Qualty-of-Servce Route Dscovery n On-Demand Routng for Ad Hoc Networks Yh-Chun Hu UC Berkeley yhchun@cs.cmu.edu Davd B. Johnson Rce Unversty dbj@cs.rce.edu ABSTRACT An ad hoc network s a collecton
Securng Qualty-of-Servce Route Dscovery n On-Demand Routng for Ad Hoc Networks Yh-Chun Hu UC Berkeley yhchun@cs.cmu.edu Davd B. Johnson Rce Unversty dbj@cs.rce.edu ABSTRACT An ad hoc network s a collecton
IP Camera Configuration Software Instruction Manual
 IP Camera 9483 - Confguraton Software Instructon Manual VBD 612-4 (10.14) Dear Customer, Wth your purchase of ths IP Camera, you have chosen a qualty product manufactured by RADEMACHER. Thank you for the
IP Camera 9483 - Confguraton Software Instructon Manual VBD 612-4 (10.14) Dear Customer, Wth your purchase of ths IP Camera, you have chosen a qualty product manufactured by RADEMACHER. Thank you for the
VRT012 User s guide V0.1. Address: Žirmūnų g. 27, Vilnius LT-09105, Phone: (370-5) , Fax: (370-5) ,
 VRT012 User s gude V0.1 Thank you for purchasng our product. We hope ths user-frendly devce wll be helpful n realsng your deas and brngng comfort to your lfe. Please take few mnutes to read ths manual
VRT012 User s gude V0.1 Thank you for purchasng our product. We hope ths user-frendly devce wll be helpful n realsng your deas and brngng comfort to your lfe. Please take few mnutes to read ths manual
Light Weight Distributed QoS Adapter in Large-Scale Ad hoc Networks. Seyed Hossein Hosseini Nazhad Ghazani 1, R.M.Alguliev 2
 Lght Weght Dstruted QoS Adapter n Large-Scale Ad hoc Networs Seyed Hossen Hossen Nazhad Ghazan, R.M.Algulev 2 Ph.D. Canddate, Insttute of Inforaton Technology of ANAS, Bau, Azerajan 2 Doctor of Techncal
Lght Weght Dstruted QoS Adapter n Large-Scale Ad hoc Networs Seyed Hossen Hossen Nazhad Ghazan, R.M.Algulev 2 Ph.D. Canddate, Insttute of Inforaton Technology of ANAS, Bau, Azerajan 2 Doctor of Techncal
Efficient Content Distribution in Wireless P2P Networks
 Effcent Content Dstrbuton n Wreless P2P Networs Qong Sun, Vctor O. K. L, and Ka-Cheong Leung Department of Electrcal and Electronc Engneerng The Unversty of Hong Kong Pofulam Road, Hong Kong, Chna {oansun,
Effcent Content Dstrbuton n Wreless P2P Networs Qong Sun, Vctor O. K. L, and Ka-Cheong Leung Department of Electrcal and Electronc Engneerng The Unversty of Hong Kong Pofulam Road, Hong Kong, Chna {oansun,
A Distributed Three-hop Routing Protocol to Increase the Capacity of Hybrid Wireless Networks
 Ths artcle has been accepted for publcaton n a future ssue of ths journal, but has not been fully edted. Content may change pror to fnal publcaton. Ctaton nformaton: DOI.9/TMC.25.2388476, IEEE Transactons
Ths artcle has been accepted for publcaton n a future ssue of ths journal, but has not been fully edted. Content may change pror to fnal publcaton. Ctaton nformaton: DOI.9/TMC.25.2388476, IEEE Transactons
Measuring Cohesion of Packages in Ada95
 Measurng Coheson of Packages n Ada95 Baowen Xu Zhenqang Chen Departent of Coputer Scence & Departent of Coputer Scence & Engneerng, Southeast Unversty Engneerng, Southeast Unversty Nanjng, Chna, 20096
Measurng Coheson of Packages n Ada95 Baowen Xu Zhenqang Chen Departent of Coputer Scence & Departent of Coputer Scence & Engneerng, Southeast Unversty Engneerng, Southeast Unversty Nanjng, Chna, 20096
Load Balancing for Hex-Cell Interconnection Network
 Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Detection and Avoidance Deadlock for Resource Allocation in Heterogeneous Distributed Platforms
 Internatonal Journal of Coputer Scence and Telecouncatons [Volue 6, Issue 2, February 2015] 1 ISSN 2047-3338 Detecton and Avodance Deadlock for Resource Allocaton n Heterogeneous Dstrbuted Platfors Ha
Internatonal Journal of Coputer Scence and Telecouncatons [Volue 6, Issue 2, February 2015] 1 ISSN 2047-3338 Detecton and Avodance Deadlock for Resource Allocaton n Heterogeneous Dstrbuted Platfors Ha
Advanced Computer Networks
 Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Generating Fuzzy Term Sets for Software Project Attributes using and Real Coded Genetic Algorithms
 Generatng Fuzzy Ter Sets for Software Proect Attrbutes usng Fuzzy C-Means C and Real Coded Genetc Algorths Al Idr, Ph.D., ENSIAS, Rabat Alan Abran, Ph.D., ETS, Montreal Azeddne Zah, FST, Fes Internatonal
Generatng Fuzzy Ter Sets for Software Proect Attrbutes usng Fuzzy C-Means C and Real Coded Genetc Algorths Al Idr, Ph.D., ENSIAS, Rabat Alan Abran, Ph.D., ETS, Montreal Azeddne Zah, FST, Fes Internatonal
DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS
 DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Arun Avudanayagam Yuguang Fang Wenjng Lou Department of Electrcal and Computer Engneerng Unversty of Florda Ganesvlle, FL 3261
DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Arun Avudanayagam Yuguang Fang Wenjng Lou Department of Electrcal and Computer Engneerng Unversty of Florda Ganesvlle, FL 3261
Connection-information-based connection rerouting for connection-oriented mobile communication networks
 Dstrb. Syst. Engng 5 (1998) 47 65. Prnted n the UK PII: S0967-1846(98)90513-7 Connecton-nformaton-based connecton reroutng for connecton-orented moble communcaton networks Mnho Song, Yanghee Cho and Chongsang
Dstrb. Syst. Engng 5 (1998) 47 65. Prnted n the UK PII: S0967-1846(98)90513-7 Connecton-nformaton-based connecton reroutng for connecton-orented moble communcaton networks Mnho Song, Yanghee Cho and Chongsang
A Novel Fuzzy Classifier Using Fuzzy LVQ to Recognize Online Persian Handwriting
 A Novel Fuzzy Classfer Usng Fuzzy LVQ to Recognze Onlne Persan Handwrtng M. Soleyan Baghshah S. Bagher Shourak S. Kasae Departent of Coputer Engneerng, Sharf Unversty of Technology, Tehran, Iran soleyan@ce.sharf.edu
A Novel Fuzzy Classfer Usng Fuzzy LVQ to Recognze Onlne Persan Handwrtng M. Soleyan Baghshah S. Bagher Shourak S. Kasae Departent of Coputer Engneerng, Sharf Unversty of Technology, Tehran, Iran soleyan@ce.sharf.edu
Optimization Methods: Integer Programming Integer Linear Programming 1. Module 7 Lecture Notes 1. Integer Linear Programming
 Optzaton Methods: Integer Prograng Integer Lnear Prograng Module Lecture Notes Integer Lnear Prograng Introducton In all the prevous lectures n lnear prograng dscussed so far, the desgn varables consdered
Optzaton Methods: Integer Prograng Integer Lnear Prograng Module Lecture Notes Integer Lnear Prograng Introducton In all the prevous lectures n lnear prograng dscussed so far, the desgn varables consdered
Simulation Based Analysis of FAST TCP using OMNET++
 Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Resource-Efficient Multi-Source Authentication Utilizing Split-Join One-Way Key Chain
 Resource-Effcent Mult-Source Authentcaton Utlzng Splt-Jon One-Way ey Chan Seonho Cho, un Sun, Hyeonsang Eom 3 Department of Computer Scence, Bowe State Unversty, Bowe, Maryland, U.S.A. Center for Secure
Resource-Effcent Mult-Source Authentcaton Utlzng Splt-Jon One-Way ey Chan Seonho Cho, un Sun, Hyeonsang Eom 3 Department of Computer Scence, Bowe State Unversty, Bowe, Maryland, U.S.A. Center for Secure
Concurrent Apriori Data Mining Algorithms
 Concurrent Apror Data Mnng Algorthms Vassl Halatchev Department of Electrcal Engneerng and Computer Scence York Unversty, Toronto October 8, 2015 Outlne Why t s mportant Introducton to Assocaton Rule Mnng
Concurrent Apror Data Mnng Algorthms Vassl Halatchev Department of Electrcal Engneerng and Computer Scence York Unversty, Toronto October 8, 2015 Outlne Why t s mportant Introducton to Assocaton Rule Mnng
Steps for Computing the Dissimilarity, Entropy, Herfindahl-Hirschman and. Accessibility (Gravity with Competition) Indices
 Steps for Computng the Dssmlarty, Entropy, Herfndahl-Hrschman and Accessblty (Gravty wth Competton) Indces I. Dssmlarty Index Measurement: The followng formula can be used to measure the evenness between
Steps for Computng the Dssmlarty, Entropy, Herfndahl-Hrschman and Accessblty (Gravty wth Competton) Indces I. Dssmlarty Index Measurement: The followng formula can be used to measure the evenness between
DESIGN AND ANALYSIS OF HASH FUNCTIONS
 DESIGN AND ANALYSIS OF HASH FUNCTIONS By Mural Krshna Reddy Danda Under the supervson of: Prncple Supervsor : Dr. Xun Y Co-supervsor : Dr. Alasdar McAndrew For the degree of Master of Scence by Research
DESIGN AND ANALYSIS OF HASH FUNCTIONS By Mural Krshna Reddy Danda Under the supervson of: Prncple Supervsor : Dr. Xun Y Co-supervsor : Dr. Alasdar McAndrew For the degree of Master of Scence by Research
Multi-Constraint Multi-Processor Resource Allocation
 Mult-Constrant Mult-Processor Resource Allocaton Ar R. B. Behrouzan 1, Dp Goswa 1, Twan Basten 1,2, Marc Gelen 1, Had Alzadeh Ara 1 1 Endhoven Unversty of Technology, Endhoven, The Netherlands 2 TNO Ebedded
Mult-Constrant Mult-Processor Resource Allocaton Ar R. B. Behrouzan 1, Dp Goswa 1, Twan Basten 1,2, Marc Gelen 1, Had Alzadeh Ara 1 1 Endhoven Unversty of Technology, Endhoven, The Netherlands 2 TNO Ebedded
Convolutional interleaver for unequal error protection of turbo codes
 Convolutonal nterleaver for unequal error protecton of turbo codes Sna Vaf, Tadeusz Wysock, Ian Burnett Unversty of Wollongong, SW 2522, Australa E-mal:{sv39,wysock,an_burnett}@uow.edu.au Abstract: Ths
Convolutonal nterleaver for unequal error protecton of turbo codes Sna Vaf, Tadeusz Wysock, Ian Burnett Unversty of Wollongong, SW 2522, Australa E-mal:{sv39,wysock,an_burnett}@uow.edu.au Abstract: Ths
OPTIMAL CONFIGURATION FOR NODES IN MIXED CELLULAR AND MOBILE AD HOC NETWORK FOR INET
 OPTIMAL CONFIGURATION FOR NODE IN MIED CELLULAR AND MOBILE AD HOC NETWORK FOR INET Olusola Babalola D.E. Department of Electrcal and Computer Engneerng Morgan tate Unversty Dr. Rchard Dean Faculty Advsor
OPTIMAL CONFIGURATION FOR NODE IN MIED CELLULAR AND MOBILE AD HOC NETWORK FOR INET Olusola Babalola D.E. Department of Electrcal and Computer Engneerng Morgan tate Unversty Dr. Rchard Dean Faculty Advsor
SRB: Shared Running Buffers in Proxy to Exploit Memory Locality of Multiple Streaming Media Sessions
 SRB: Shared Runnng Buffers n Proxy to Explot Memory Localty of Multple Streamng Meda Sessons Songqng Chen,BoShen, Yong Yan, Sujoy Basu, and Xaodong Zhang Department of Computer Scence Moble and Meda System
SRB: Shared Runnng Buffers n Proxy to Explot Memory Localty of Multple Streamng Meda Sessons Songqng Chen,BoShen, Yong Yan, Sujoy Basu, and Xaodong Zhang Department of Computer Scence Moble and Meda System
R s s f. m y s. SPH3UW Unit 7.3 Spherical Concave Mirrors Page 1 of 12. Notes
 SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
kccvoip.com basic voip training NAT/PAT extract 2008
 kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
F Geometric Mean Graphs
 Avalable at http://pvamu.edu/aam Appl. Appl. Math. ISSN: 1932-9466 Vol. 10, Issue 2 (December 2015), pp. 937-952 Applcatons and Appled Mathematcs: An Internatonal Journal (AAM) F Geometrc Mean Graphs A.
Avalable at http://pvamu.edu/aam Appl. Appl. Math. ISSN: 1932-9466 Vol. 10, Issue 2 (December 2015), pp. 937-952 Applcatons and Appled Mathematcs: An Internatonal Journal (AAM) F Geometrc Mean Graphs A.
Pattern Classification of Back-Propagation Algorithm Using Exclusive Connecting Network
 World Acade of Scence, Engneerng and Technolog 36 7 Pattern Classfcaton of Bac-Propagaton Algorth Usng Eclusve Connectng Networ Insung Jung, and G-Na Wang Abstract The obectve of ths paper s to a desgn
World Acade of Scence, Engneerng and Technolog 36 7 Pattern Classfcaton of Bac-Propagaton Algorth Usng Eclusve Connectng Networ Insung Jung, and G-Na Wang Abstract The obectve of ths paper s to a desgn
EXTENDED FORMAL SPECIFICATIONS OF 3D SPATIAL DATA TYPES
 - 1 - EXTENDED FORMAL SPECIFICATIONS OF D SPATIAL DATA TYPES - TECHNICAL REPORT - André Borrann Coputaton Cvl Engneerng Technsche Unverstät München INTRODUCTION Startng pont for the developent of a spatal
- 1 - EXTENDED FORMAL SPECIFICATIONS OF D SPATIAL DATA TYPES - TECHNICAL REPORT - André Borrann Coputaton Cvl Engneerng Technsche Unverstät München INTRODUCTION Startng pont for the developent of a spatal
Positive Semi-definite Programming Localization in Wireless Sensor Networks
 Postve Sem-defnte Programmng Localzaton n Wreless Sensor etworks Shengdong Xe 1,, Jn Wang, Aqun Hu 1, Yunl Gu, Jang Xu, 1 School of Informaton Scence and Engneerng, Southeast Unversty, 10096, anjng Computer
Postve Sem-defnte Programmng Localzaton n Wreless Sensor etworks Shengdong Xe 1,, Jn Wang, Aqun Hu 1, Yunl Gu, Jang Xu, 1 School of Informaton Scence and Engneerng, Southeast Unversty, 10096, anjng Computer
Support Strong Consistency for Mobile Dynamic Contents Delivery Network
 Nnth IEEE Internatonal Symposum on Multmeda 27 Support Strong Consstency for Moble Dynamc Contents Delvery Networ Zhou Su, Jro Katto and Yasuho Yasuda Graduate School of Scence and Engneerng, Waseda Unversty,
Nnth IEEE Internatonal Symposum on Multmeda 27 Support Strong Consstency for Moble Dynamc Contents Delvery Networ Zhou Su, Jro Katto and Yasuho Yasuda Graduate School of Scence and Engneerng, Waseda Unversty,
ELEC 377 Operating Systems. Week 6 Class 3
 ELEC 377 Operatng Systems Week 6 Class 3 Last Class Memory Management Memory Pagng Pagng Structure ELEC 377 Operatng Systems Today Pagng Szes Vrtual Memory Concept Demand Pagng ELEC 377 Operatng Systems
ELEC 377 Operatng Systems Week 6 Class 3 Last Class Memory Management Memory Pagng Pagng Structure ELEC 377 Operatng Systems Today Pagng Szes Vrtual Memory Concept Demand Pagng ELEC 377 Operatng Systems
Priority-Based Scheduling Algorithm for Downlink Traffics in IEEE Networks
 Prorty-Based Schedulng Algorthm for Downlnk Traffcs n IEEE 80.6 Networks Ja-Mng Lang, Jen-Jee Chen, You-Chun Wang, Yu-Chee Tseng, and Bao-Shuh P. Ln Department of Computer Scence Natonal Chao-Tung Unversty,
Prorty-Based Schedulng Algorthm for Downlnk Traffcs n IEEE 80.6 Networks Ja-Mng Lang, Jen-Jee Chen, You-Chun Wang, Yu-Chee Tseng, and Bao-Shuh P. Ln Department of Computer Scence Natonal Chao-Tung Unversty,
An Improved User Authentication and Key Agreement Scheme Providing User Anonymity
 35 JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 9, NO. 4, DECEMBER 0 An Improved User Authentcaton and Key Agreement Scheme Provdng User Anonymty Ya-Fen Chang and Pe-Yu Chang Abstract When accessng
35 JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 9, NO. 4, DECEMBER 0 An Improved User Authentcaton and Key Agreement Scheme Provdng User Anonymty Ya-Fen Chang and Pe-Yu Chang Abstract When accessng
STATIC MAPPING FOR OPENCL WORKLOADS IN HETEROGENEOUS COMPUTER SYSTEMS
 STATIC MAPPING FOR OPENCL WORKLOADS IN HETEROGENEOUS COMPUTER SYSTEMS 1 HENDRA RAHMAWAN, 2 KUSPRIYANTO, 3 YUDI SATRIA GONDOKARYONO School of Electrcal Engneerng and Inforatcs, Insttut Teknolog Bandung,
STATIC MAPPING FOR OPENCL WORKLOADS IN HETEROGENEOUS COMPUTER SYSTEMS 1 HENDRA RAHMAWAN, 2 KUSPRIYANTO, 3 YUDI SATRIA GONDOKARYONO School of Electrcal Engneerng and Inforatcs, Insttut Teknolog Bandung,
Routing in Degree-constrained FSO Mesh Networks
 Internatonal Journal of Hybrd Informaton Technology Vol., No., Aprl, 009 Routng n Degree-constraned FSO Mesh Networks Zpng Hu, Pramode Verma, and James Sluss Jr. School of Electrcal & Computer Engneerng
Internatonal Journal of Hybrd Informaton Technology Vol., No., Aprl, 009 Routng n Degree-constraned FSO Mesh Networks Zpng Hu, Pramode Verma, and James Sluss Jr. School of Electrcal & Computer Engneerng
A Fast Visual Tracking Algorithm Based on Circle Pixels Matching
 A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
A Fast Content-Based Multimedia Retrieval Technique Using Compressed Data
 A Fast Content-Based Multmeda Retreval Technque Usng Compressed Data Borko Furht and Pornvt Saksobhavvat NSF Multmeda Laboratory Florda Atlantc Unversty, Boca Raton, Florda 3343 ABSTRACT In ths paper,
A Fast Content-Based Multmeda Retreval Technque Usng Compressed Data Borko Furht and Pornvt Saksobhavvat NSF Multmeda Laboratory Florda Atlantc Unversty, Boca Raton, Florda 3343 ABSTRACT In ths paper,
Load-Balanced Anycast Routing
 Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
A Secure Hybrid Wireless Mesh Protocol for s Mesh Network*
 A Secure Hybrd Wreless Mesh Protocol for 802.11s Mesh Network* Md. Sharful Islam, Young Jg Yoon, Md. Abdul Hamd, and Choong Seon Hong** Department of Computer Engneerng, Kyung Hee Unversty, Republc of
A Secure Hybrd Wreless Mesh Protocol for 802.11s Mesh Network* Md. Sharful Islam, Young Jg Yoon, Md. Abdul Hamd, and Choong Seon Hong** Department of Computer Engneerng, Kyung Hee Unversty, Republc of
SLAM Summer School 2006 Practical 2: SLAM using Monocular Vision
 SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
A New Transaction Processing Model Based on Optimistic Concurrency Control
 A New Transacton Processng Model Based on Optmstc Concurrency Control Wang Pedong,Duan Xpng,Jr. Abstract-- In ths paper, to support moblty and dsconnecton of moble clents effectvely n moble computng envronment,
A New Transacton Processng Model Based on Optmstc Concurrency Control Wang Pedong,Duan Xpng,Jr. Abstract-- In ths paper, to support moblty and dsconnecton of moble clents effectvely n moble computng envronment,
A Traffic Aware Routing Protocol for Congestion Avoidance in Content-Centric Network
 , pp.69-80 http://dx.do.org/10.14257/jmue.2014.9.9.08 A Traffc Aware Routng Protocol for Congeston Avodance n Content-Centrc Network Jung-Jae Km 1, Mn-Woo Ryu 2*, S-Ho Cha 3 and Kuk-Hyun Cho 1 1 Dept.
, pp.69-80 http://dx.do.org/10.14257/jmue.2014.9.9.08 A Traffc Aware Routng Protocol for Congeston Avodance n Content-Centrc Network Jung-Jae Km 1, Mn-Woo Ryu 2*, S-Ho Cha 3 and Kuk-Hyun Cho 1 1 Dept.
Ensuring Basic Security and Preventing Replay Attack in a Query Processing Application Domain in WSN
 Ensurng Basc Securty and Preventng Replay Attack n a Query Processng Applcaton Doman n WSN Amrta Ghosal 1, Subr Halder 1, Sanjb Sur 2, Avshek Dan 2, and Spra DasBt 2 1 Dept. of Comp. Sc. & Engg, Dr. B.
Ensurng Basc Securty and Preventng Replay Attack n a Query Processng Applcaton Doman n WSN Amrta Ghosal 1, Subr Halder 1, Sanjb Sur 2, Avshek Dan 2, and Spra DasBt 2 1 Dept. of Comp. Sc. & Engg, Dr. B.
IJCTA Nov-Dec 2016 Available
 Dr K Santh et al, Internatonal Journal of Computer Technology & Applcatons,Vol 7(6),773-779 Optmzed Route Technque for DSR Routng Protocol n MANET Dr.K.Santh, Assocate Professor, Dept. of Computer Scence,
Dr K Santh et al, Internatonal Journal of Computer Technology & Applcatons,Vol 7(6),773-779 Optmzed Route Technque for DSR Routng Protocol n MANET Dr.K.Santh, Assocate Professor, Dept. of Computer Scence,
Extending Network Life by Using Mobile Actors in Cluster-based Wireless Sensor and Actor Networks
 Extendng Networ Lfe by Usng Moble Actors n Cluster-based Wreless Sensor and Actor Networs Nauman Aslam, Wllam Phllps, Wllam Robertson and S. Svaumar Department of Engneerng Mathematcs & Internetworng Dalhouse
Extendng Networ Lfe by Usng Moble Actors n Cluster-based Wreless Sensor and Actor Networs Nauman Aslam, Wllam Phllps, Wllam Robertson and S. Svaumar Department of Engneerng Mathematcs & Internetworng Dalhouse
Classifying Acoustic Transient Signals Using Artificial Intelligence
 Classfyng Acoustc Transent Sgnals Usng Artfcal Intellgence Steve Sutton, Unversty of North Carolna At Wlmngton (suttons@charter.net) Greg Huff, Unversty of North Carolna At Wlmngton (jgh7476@uncwl.edu)
Classfyng Acoustc Transent Sgnals Usng Artfcal Intellgence Steve Sutton, Unversty of North Carolna At Wlmngton (suttons@charter.net) Greg Huff, Unversty of North Carolna At Wlmngton (jgh7476@uncwl.edu)
Secure Distributed Cluster Formation in Wireless Sensor Networks
 Secure Dstrbuted Cluster Formaton n Wreless Sensor Networks Kun Sun Intellgent Automaton, Inc. ksun@-a-.com Pa Peng Opsware Inc. ppeng@opsware.com Clff Wang Army Research Offce clff.wang@us.army.ml Peng
Secure Dstrbuted Cluster Formaton n Wreless Sensor Networks Kun Sun Intellgent Automaton, Inc. ksun@-a-.com Pa Peng Opsware Inc. ppeng@opsware.com Clff Wang Army Research Offce clff.wang@us.army.ml Peng
DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT
 DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT Bran J. Wolf, Joseph L. Hammond, and Harlan B. Russell Dept. of Electrcal and Computer Engneerng, Clemson Unversty,
DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT Bran J. Wolf, Joseph L. Hammond, and Harlan B. Russell Dept. of Electrcal and Computer Engneerng, Clemson Unversty,
Identifying Key Factors and Developing a New Method for Classifying Imbalanced Sentiment Data
 Identfyng Key Factors and Developng a New Method for Classfyng Ibalanced Sentent Data Long-Sheng Chen* and Kun-Cheng Sun Abstract Bloggers opnons related to coercal products/servces ght have a sgnfcant
Identfyng Key Factors and Developng a New Method for Classfyng Ibalanced Sentent Data Long-Sheng Chen* and Kun-Cheng Sun Abstract Bloggers opnons related to coercal products/servces ght have a sgnfcant
Modelling Spatial Substructure in Wildlife Populations using an Approximation to the Shortest Path Voronoi Diagram
 18 th World IMACS / MODSIM Congress, Carns, Australa 13-17 July 2009 http://ssanz.org.au/ods09 Modellng Spatal Substructure n Wldlfe Populatons usng an Approxaton to the Shortest Path Vorono Dagra Stewart,
18 th World IMACS / MODSIM Congress, Carns, Australa 13-17 July 2009 http://ssanz.org.au/ods09 Modellng Spatal Substructure n Wldlfe Populatons usng an Approxaton to the Shortest Path Vorono Dagra Stewart,
AN INDEXING METHOD FOR SUPPORTING SPATIAL QUERIES IN STRUCTURED PEER-TO-PEER SYSTEMS
 AN INDEXING METHOD FOR SUPPORTING SPATIAL QUERIES IN STRUCTURED PEER-TO-PEER SYSTEMS Lngku Meng a, Wenun Xe a, *, Dan Lu a, b a School of Remote Sensng and Informaton Engneerng, Wuhan Unversty, Wuhan 4379,
AN INDEXING METHOD FOR SUPPORTING SPATIAL QUERIES IN STRUCTURED PEER-TO-PEER SYSTEMS Lngku Meng a, Wenun Xe a, *, Dan Lu a, b a School of Remote Sensng and Informaton Engneerng, Wuhan Unversty, Wuhan 4379,
1 Calculation and Analysis of Buffer
 Sep. 5 Journal of Electronc Scence and Technology of Chna Vol.3 No.3 ` Calculaton and Analyss of Destnaton Buffer for ulteda Servce n ole Ad Hoc Network ZHOU Zhong, AO Yu-ng, JIANG Zh-qong. School of Councaton
Sep. 5 Journal of Electronc Scence and Technology of Chna Vol.3 No.3 ` Calculaton and Analyss of Destnaton Buffer for ulteda Servce n ole Ad Hoc Network ZHOU Zhong, AO Yu-ng, JIANG Zh-qong. School of Councaton
Adaptive Energy and Location Aware Routing in Wireless Sensor Network
 Adaptve Energy and Locaton Aware Routng n Wreless Sensor Network Hong Fu 1,1, Xaomng Wang 1, Yngshu L 1 Department of Computer Scence, Shaanx Normal Unversty, X an, Chna, 71006 fuhong433@gmal.com {wangxmsnnu@hotmal.cn}
Adaptve Energy and Locaton Aware Routng n Wreless Sensor Network Hong Fu 1,1, Xaomng Wang 1, Yngshu L 1 Department of Computer Scence, Shaanx Normal Unversty, X an, Chna, 71006 fuhong433@gmal.com {wangxmsnnu@hotmal.cn}
