Named Data Networking
|
|
|
- Anne Daniels
- 6 years ago
- Views:
Transcription
1 Named Data Networking Ronald van der Pol
2 Outline! Goal of this project! Shortcomings of current internet! NDN basics! NDN forwarding! Naming example! Security! Personal opinion
3 Goal of this project! Technology assessment of Named Data Networking! What is it?! How does it work?! What are the pros and cons?! Is it useful in NREN networking?! Demo at the end of the year to show potential use! Named Data Networking is a new way of data transport! Idea of Van Jacobson (PARC)! Supported by Lixia Zhang (UCLA & IRTF RRG co-chair)
4 Current Internet Communication between computers. Computers are have a name (identity) and address (location). Content is stored on these computers. Connect to a computer and retrieve data.
5 Internet Shortcomings! TCP/IP did a great job, but the problem has changed! More and more content delivery (YouTube, itunes, Facebook, BitTorrent, etc)! Irrelevant on which computer the content is stored! In current internet we connect to a specific server/website! Mobility (mobile devices, smartphones, tablets, etc)! Devices are constantly changing location in topology! location change è address change è identity change! Multicast (point to multipoint traffic, e.g streaming video)! Current internet has problems when everybody looks at the same content at the same time (breaking news, popular YouTube movie, live sport events)! Security! Data containers (communication links, servers) are secured, not the data itself
6 NDN Concepts! Each piece of data has a name / Packets say what, not who (no src or dst)! Two packet types: Interest & Data! Receiver sends an Interest, reply comes as Data packet Content Store interest packet name? name data Data packet
7 NDN Forwarder name Content Store data / FIB prefix face 0 Pending Interest Table name face / 0 1 / / 1 1, 2 2
8 Pending Interest Tables / PIT prefix PIT prefix PIT prefix /
9 2 nd Interest Packet / / /v / /v3 0 3 PIT prefix 0 / /v3 0 1 PIT prefix 1 0 / / /v3
10 Naming Example / latest version: / specific version: / sport nieuws all news of specific day: / all news of today: / foo foobar bar Semantics defined by applications, transparant for network v1 v2 v3
11 Security! Data itself is authenticated! Currently we secure links and servers (SSL, ACLs, etc.)! All NDN data packets are signed! Signature over name, data & metadata! Public key signatures! Binding between name and data (no name lookups needed)! It does not matter where you get your copy from! NDN data packets may be encrypted! For the network layer, the security information is just bits
12 Open Questions! Routing based on names! Packet formats! Efficiency! Content store parameters!.! Size?! When to purge data?! What data is purged first?
13 Personal Opinion! Many interesting aspects that seem to resolve real issues! NDN will not replace TCP/IP, but co-exist! Choose the protocol that solves your problem best Sometimes TCP/IP, sometimes NDN! Computers will have many interfaces (wired, WIFI, G4, etc) on many VPNs like CDN VPNs (Google, Amazon, music stores), social media VPNs (Twitter, Facebook, LinkedIn), Internet VPN, etc.)! NDN may finally solve the multicast problem! Natural and simple way of delivering same content to many receivers
14 Network Slices Interesting new services I just use them through an app! slide by Chip Elliott (GENI Program Office) Good old Internet Slice 0 Slice 1 Slice 1 Slice 2 Slice 3 Slice 4
15 Thank you Ronald van der Pol
OpenFlow Ronald van der Pol
 OpenFlow Ronald van der Pol Outline! Goal of this project! Why OpenFlow?! Basics of OpenFlow! Short Demo OpenFlow Overview! Initiative of Stanford University! Run network research experiments
OpenFlow Ronald van der Pol Outline! Goal of this project! Why OpenFlow?! Basics of OpenFlow! Short Demo OpenFlow Overview! Initiative of Stanford University! Run network research experiments
Named Data Networking (NDN) CLASS WEB SITE: NDN. Introduction to NDN. Updated with Lecture Notes. Data-centric addressing
 CLASS WEB SITE: http://upmcsms.weebly.com/ Updated with Lecture Notes Named Data Networking (NDN) Introduction to NDN Named Data Networking (NDN) IP NDN Host-centric addressing Data-centric addressing
CLASS WEB SITE: http://upmcsms.weebly.com/ Updated with Lecture Notes Named Data Networking (NDN) Introduction to NDN Named Data Networking (NDN) IP NDN Host-centric addressing Data-centric addressing
Introduction to Information Centric Networking
 Introduction to Information Centric Networking... with a Dash of Security Claudio Marxer Computer Networks Group University of Basel Switzerland Open Source IoT & Blockchain
Introduction to Information Centric Networking... with a Dash of Security Claudio Marxer Computer Networks Group University of Basel Switzerland Open Source IoT & Blockchain
Networking Named Content: Content-Centric Networking. John Rula
 Networking Named Content: Content-Centric Networking John Rula Overview Replacing traditional host based routing with named content routing Consumers request a data s name instead of a host (ip address)
Networking Named Content: Content-Centric Networking John Rula Overview Replacing traditional host based routing with named content routing Consumers request a data s name instead of a host (ip address)
Named Data Networking for 5G Wireless
 Named Data Networking for 5G Wireless Edmund Yeh Electrical and Computer Engineering Northeastern University New York University January 27, 2017 Overview NDN: a major information-centric networking architecture
Named Data Networking for 5G Wireless Edmund Yeh Electrical and Computer Engineering Northeastern University New York University January 27, 2017 Overview NDN: a major information-centric networking architecture
Named Data Networking. Lixia Zhang UCLA Computer Science Department August 12, 2014
 Named Data Networking Lixia Zhang UCLA Computer Science Department August 12, 2014 NDN Team Jeff Burke Van Jacobson (architect) Lixia Zhang Kim Claffy Christos Papadopoulos Beichuan Zhang Lan Wang Alex
Named Data Networking Lixia Zhang UCLA Computer Science Department August 12, 2014 NDN Team Jeff Burke Van Jacobson (architect) Lixia Zhang Kim Claffy Christos Papadopoulos Beichuan Zhang Lan Wang Alex
Running IoT Applications over ICN: A Guided Journey to NDN, RIOT, CCN-lite and NFN
 ACM ICN-2017 Tutorial 1 Running IoT Applications over ICN: A Guided Journey to NDN, RIOT, CCN-lite and NFN at the Freie Universität Berlin, Sep 26, 2017 Welcome and a gentle introduction to ICN Alex Afanasyev,
ACM ICN-2017 Tutorial 1 Running IoT Applications over ICN: A Guided Journey to NDN, RIOT, CCN-lite and NFN at the Freie Universität Berlin, Sep 26, 2017 Welcome and a gentle introduction to ICN Alex Afanasyev,
Named Data Networking
 Named Data Networking Patrick Crowley, John DeHart & the NDN Team 2013 China-America Frontiers of Engineering Symposium Beijing 5/15/2013 Goals for today Introduce Named Data Network (NDN) Illustrate NDN
Named Data Networking Patrick Crowley, John DeHart & the NDN Team 2013 China-America Frontiers of Engineering Symposium Beijing 5/15/2013 Goals for today Introduce Named Data Network (NDN) Illustrate NDN
Content Centric Networking
 Content Centric Networking Van Jacobson Palo Alto Research Center (PARC) IETF77 ISOC Internet Researchers meeting Anaheim, CA 24 March 2010 This talk describes ongoing PARC work on CCN (Content-centric
Content Centric Networking Van Jacobson Palo Alto Research Center (PARC) IETF77 ISOC Internet Researchers meeting Anaheim, CA 24 March 2010 This talk describes ongoing PARC work on CCN (Content-centric
Web as a Distributed System
 Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
Performance Study of CCNx
 Performance Study of CCNx Haowei Yuan Networking Research Seminar 3/18/2013 My Topic for Today Industry participation in content centric networking Emerging networks consortium Our performance study of
Performance Study of CCNx Haowei Yuan Networking Research Seminar 3/18/2013 My Topic for Today Industry participation in content centric networking Emerging networks consortium Our performance study of
Bedford / St.Martin s
 Bedford / St.Martin s Media & Culture Infographics July 2014 20 Jay Street Suite 828 Brooklyn New York 11201 USA T 718 797 2302 F 718 797 2307 www.toda.com New York / Hamburg / London Project Purpose Bedford
Bedford / St.Martin s Media & Culture Infographics July 2014 20 Jay Street Suite 828 Brooklyn New York 11201 USA T 718 797 2302 F 718 797 2307 www.toda.com New York / Hamburg / London Project Purpose Bedford
CS 356 Internet Security Protocols. Fall 2013
 CS 356 Internet Security Protocols Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5
CS 356 Internet Security Protocols Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5
Two different chat groups Between the three ships Between the carrier and the troops
 Chat Application Notional Tactical Network Two different chat groups Between the three ships Between the carrier and the troops C gro hat up 1 Chat group2 Loss cannot be tolerated In order delivery is
Chat Application Notional Tactical Network Two different chat groups Between the three ships Between the carrier and the troops C gro hat up 1 Chat group2 Loss cannot be tolerated In order delivery is
Software Defined Networks and OpenFlow. Courtesy of: AT&T Tech Talks.
 MOBILE COMMUNICATION AND INTERNET TECHNOLOGIES Software Defined Networks and Courtesy of: AT&T Tech Talks http://web.uettaxila.edu.pk/cms/2017/spr2017/temcitms/ MODULE OVERVIEW Motivation behind Software
MOBILE COMMUNICATION AND INTERNET TECHNOLOGIES Software Defined Networks and Courtesy of: AT&T Tech Talks http://web.uettaxila.edu.pk/cms/2017/spr2017/temcitms/ MODULE OVERVIEW Motivation behind Software
A1. Technical methodology
 A1. Technical methodology The Ofcom mobile research app project is the latest phase of Ofcom s work to measure mobile performance and the consumer experience of using mobile services. The new methodology
A1. Technical methodology The Ofcom mobile research app project is the latest phase of Ofcom s work to measure mobile performance and the consumer experience of using mobile services. The new methodology
From Internet Data Centers to Data Centers in the Cloud
 From Internet Data Centers to Data Centers in the Cloud This case study is a short extract from a keynote address given to the Doctoral Symposium at Middleware 2009 by Lucy Cherkasova of HP Research Labs
From Internet Data Centers to Data Centers in the Cloud This case study is a short extract from a keynote address given to the Doctoral Symposium at Middleware 2009 by Lucy Cherkasova of HP Research Labs
Connect to CCPL
 TECH NEWS Want to receive this publication by email each month? Sign up for our monthly newsletter! Send your request in an email to techteam@ccpl.org with your full name and phone number. We ll add you
TECH NEWS Want to receive this publication by email each month? Sign up for our monthly newsletter! Send your request in an email to techteam@ccpl.org with your full name and phone number. We ll add you
Named Data Networking Enabled WiFi in Challenged Communication Environments
 Named Data Networking Enabled WiFi in Challenged Communication Environments 1 Anthony Guardado, 1 Zilong Ye, 1 Huiping Guo 2 Lei Liu, 2 Liguang Xie, 2 Akira Ito 1 California State University, Los Angeles
Named Data Networking Enabled WiFi in Challenged Communication Environments 1 Anthony Guardado, 1 Zilong Ye, 1 Huiping Guo 2 Lei Liu, 2 Liguang Xie, 2 Akira Ito 1 California State University, Los Angeles
icloud History & Services Dr. Leon Chapman
 icloud History & Services Dr. Leon Chapman 1 icloud History & Services Apple ID & Accounts Overview Online Backup Services Cloud Storage & File Sharing 2 Off-Site Backup? icloud What is it? File storage?
icloud History & Services Dr. Leon Chapman 1 icloud History & Services Apple ID & Accounts Overview Online Backup Services Cloud Storage & File Sharing 2 Off-Site Backup? icloud What is it? File storage?
IPv6 at Google. Lorenzo Colitti
 IPv6 at Google Lorenzo Colitti lorenzo@google.com Why? IPv4 address space predictions (G. Huston) To put it into perspective... Iljitsch van Beijnum, Ars Technica Why IPv6? Cost Buying addresses will be
IPv6 at Google Lorenzo Colitti lorenzo@google.com Why? IPv4 address space predictions (G. Huston) To put it into perspective... Iljitsch van Beijnum, Ars Technica Why IPv6? Cost Buying addresses will be
KVH: The Power of One
 KVH: The Power of One The only end-to-end solution for connectivity and content delivery at sea Presented by: Vivian QUENET Vice President Sales, Asia Pacific mini-vsat Broadband The integrated communications
KVH: The Power of One The only end-to-end solution for connectivity and content delivery at sea Presented by: Vivian QUENET Vice President Sales, Asia Pacific mini-vsat Broadband The integrated communications
Don t make me think*!
 Don t make me think*! (How to provide online users with what they really need) Pinnacle Communications training Workshop 4 Your E-Image * A great usability book by Steve Krug, 17,49 on www.amazon.co.uk
Don t make me think*! (How to provide online users with what they really need) Pinnacle Communications training Workshop 4 Your E-Image * A great usability book by Steve Krug, 17,49 on www.amazon.co.uk
Worldwide Release. Your world, Secured ND-IM005. Wi-Fi Interception System
 Your world, Secured 2016 Worldwide Release System Overview Wi-Fi interception system is developed for police operations and searching of information leaks in the office premises, government agencies and
Your world, Secured 2016 Worldwide Release System Overview Wi-Fi interception system is developed for police operations and searching of information leaks in the office premises, government agencies and
How to Establish Loop-Free Multipath Routes in Named Data Networking?
 How to Establish Loop-Free Multipath Routes in Named Data Networking? NDNcomm 2017 Klaus Schneider, Beichuan Zhang March 24, 2017 The University of Arizona 1 Routing and Forwarding in IP Networks No Loop
How to Establish Loop-Free Multipath Routes in Named Data Networking? NDNcomm 2017 Klaus Schneider, Beichuan Zhang March 24, 2017 The University of Arizona 1 Routing and Forwarding in IP Networks No Loop
NDN Project Progress. Lan Wang University of Memphis IEEE INFOCOM 2014, April 30,
 NDN Project Progress Lan Wang University of Memphis IEEE INFOCOM 2014, April 30, 2014 www.named-data.net NDN Project Started in August 2010 12 institutions Lixia Zhang: Lead PI Van Jacobson: Architect
NDN Project Progress Lan Wang University of Memphis IEEE INFOCOM 2014, April 30, 2014 www.named-data.net NDN Project Started in August 2010 12 institutions Lixia Zhang: Lead PI Van Jacobson: Architect
Internet Architecture
 Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
IXP economic aspect and benefits
 IXP economic aspect and benefits M. Sall modou.sall@orange-sonatel.com Slide 1 ITU IXP Workshop September 28 th, 2015 Copyright Sonatel. All rights reserved Outline Context Content Distribution and Hosting
IXP economic aspect and benefits M. Sall modou.sall@orange-sonatel.com Slide 1 ITU IXP Workshop September 28 th, 2015 Copyright Sonatel. All rights reserved Outline Context Content Distribution and Hosting
Jianhui Zhang, Ph.D., Associate Prof. College of Computer Science and Technology, Hangzhou Dianzi Univ.
 Jianhui Zhang, Ph.D., Associate Prof. College of Computer Science and Technology, Hangzhou Dianzi Univ. Email: jh_zhang@hdu.edu.cn Copyright 2015 Pearson Education, Inc. Chapter 4: Networking and the Internet
Jianhui Zhang, Ph.D., Associate Prof. College of Computer Science and Technology, Hangzhou Dianzi Univ. Email: jh_zhang@hdu.edu.cn Copyright 2015 Pearson Education, Inc. Chapter 4: Networking and the Internet
ICN for Cloud Networking. Lotfi Benmohamed Advanced Network Technologies Division NIST Information Technology Laboratory
 ICN for Cloud Networking Lotfi Benmohamed Advanced Network Technologies Division NIST Information Technology Laboratory Information-Access Dominates Today s Internet is focused on point-to-point communication
ICN for Cloud Networking Lotfi Benmohamed Advanced Network Technologies Division NIST Information Technology Laboratory Information-Access Dominates Today s Internet is focused on point-to-point communication
Unit 4: Firewalls (I)
 Unit 4: Firewalls (I) What is a firewall? Types of firewalls Packet Filtering Statefull Application and Circuit Proxy Firewall services and limitations Writing firewall rules Example 1 Example 2 What is
Unit 4: Firewalls (I) What is a firewall? Types of firewalls Packet Filtering Statefull Application and Circuit Proxy Firewall services and limitations Writing firewall rules Example 1 Example 2 What is
Here(is(the(XML(Schema(that(describes(the(format:
 BuildingBusinessDashboardsusingXSLT,SVG,HTML5 Today seconomyhasdramaticallychangedthewaycompaniesdobusiness,havinganonlinepresenceisnolonger sufficient,andordermanagementsystemshavetobereal:timeandaccessibleonalargevarietyofdevices:
BuildingBusinessDashboardsusingXSLT,SVG,HTML5 Today seconomyhasdramaticallychangedthewaycompaniesdobusiness,havinganonlinepresenceisnolonger sufficient,andordermanagementsystemshavetobereal:timeandaccessibleonalargevarietyofdevices:
Expires: February 21, Huawei & USTC G. Wang. Huawei Technologies. August 20, 2013
 ICN Research Group Internet-Draft Intended status: Informational Expires: February 21, 2014 X. Zhang R. Ravindran Huawei Technologies H. Xie Huawei & USTC G. Wang Huawei Technologies August 20, 2013 Abstract
ICN Research Group Internet-Draft Intended status: Informational Expires: February 21, 2014 X. Zhang R. Ravindran Huawei Technologies H. Xie Huawei & USTC G. Wang Huawei Technologies August 20, 2013 Abstract
GUIDE Quickstart Guide. A Guide to Setting Up Your Hootsuite Dashboard
 GUIDE Quickstart Guide A Guide to Setting Up Your Hootsuite Dashboard QuickStart Guide Hootsuite Helps You Organize and Manage Your Social Media Hootsuite is a social media management dashboard. You can
GUIDE Quickstart Guide A Guide to Setting Up Your Hootsuite Dashboard QuickStart Guide Hootsuite Helps You Organize and Manage Your Social Media Hootsuite is a social media management dashboard. You can
ECE 650 Systems Programming & Engineering. Spring 2018
 ECE 650 Systems Programming & Engineering Spring 2018 Networking Introduction Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) Computer Networking A background of important areas
ECE 650 Systems Programming & Engineering Spring 2018 Networking Introduction Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) Computer Networking A background of important areas
CSE 123A Computer Netwrking
 CSE 123A Computer Netwrking Winter 2005 Mobile Networking Alex Snoeren presenting in lieu of Stefan Savage Today s s issues What are implications of hosts that move? Remember routing? It doesn t work anymore
CSE 123A Computer Netwrking Winter 2005 Mobile Networking Alex Snoeren presenting in lieu of Stefan Savage Today s s issues What are implications of hosts that move? Remember routing? It doesn t work anymore
Follow Me Cloud and Virtualization of (Multimedia) Services and Applications: Challenges and Possible Solutions
 Follow Me Cloud and Virtualization of (Multimedia) Services and Applications: Challenges and Possible Solutions André Gomes (1), Torsten Braun (1), Georgios Karagiannis (2), Morteza Karimzadeh (2), Marco
Follow Me Cloud and Virtualization of (Multimedia) Services and Applications: Challenges and Possible Solutions André Gomes (1), Torsten Braun (1), Georgios Karagiannis (2), Morteza Karimzadeh (2), Marco
Measuring KSA Broadband
 Measuring KSA Broadband Meqyas, Q2 218 Report In 217, the CITC in partnership with SamKnows launched a project to measure internet performance. The project, named Meqyas, gives internet users in Saudi
Measuring KSA Broadband Meqyas, Q2 218 Report In 217, the CITC in partnership with SamKnows launched a project to measure internet performance. The project, named Meqyas, gives internet users in Saudi
Supporting Mobility in MobilityFirst
 Supporting Mobility in MobilityFirst F. Zhang, K. Nagaraja, T. Nguyen, D. Raychaudhuri, Y. Zhang WINLAB, Rutgers University Technology Centre of NJ 671 Route 1, North Brunswick, NJ 08902, USA Mobile Data
Supporting Mobility in MobilityFirst F. Zhang, K. Nagaraja, T. Nguyen, D. Raychaudhuri, Y. Zhang WINLAB, Rutgers University Technology Centre of NJ 671 Route 1, North Brunswick, NJ 08902, USA Mobile Data
USER MANUAL. VIA IT Deployment Guide for Firmware 2.3 MODEL: P/N: Rev 7.
 USER MANUAL MODEL: VIA IT Deployment Guide for Firmware 2.3 P/N: 2900-300631 Rev 7 www.kramerav.com Contents 1 Introduction 1 1.1 User Experience 2 1.2 Pre-Deployment Planning 2 2 Connectivity 3 2.1 Network
USER MANUAL MODEL: VIA IT Deployment Guide for Firmware 2.3 P/N: 2900-300631 Rev 7 www.kramerav.com Contents 1 Introduction 1 1.1 User Experience 2 1.2 Pre-Deployment Planning 2 2 Connectivity 3 2.1 Network
6 TIPS FOR IMPROVING YOUR WEB PRESENCE
 6 TIPS FOR IMPROVING YOUR WEB PRESENCE 6 TIPS FOR IMPROVING YOUR WEB PRESENCE We all want to get noticed on the web. If you are running a business you want to be on the first page in Google via organic
6 TIPS FOR IMPROVING YOUR WEB PRESENCE 6 TIPS FOR IMPROVING YOUR WEB PRESENCE We all want to get noticed on the web. If you are running a business you want to be on the first page in Google via organic
App Configuration: Updating the app after major website changes
 App Configuration: Updating the app after major website changes Introduction If your website has been re-organized or you have a new website provider, your Mobile Communication App will need updating.
App Configuration: Updating the app after major website changes Introduction If your website has been re-organized or you have a new website provider, your Mobile Communication App will need updating.
Networking and Internetworking 1
 Networking and Internetworking 1 Today l Networks and distributed systems l Internet architecture xkcd Networking issues for distributed systems Early networks were designed to meet relatively simple requirements
Networking and Internetworking 1 Today l Networks and distributed systems l Internet architecture xkcd Networking issues for distributed systems Early networks were designed to meet relatively simple requirements
HIP Host Identity Protocol. October 2007 Patrik Salmela Ericsson
 HIP Host Identity Protocol October 2007 Patrik Salmela Ericsson Agenda What is the Host Identity Protocol (HIP) What does HIP try to solve HIP basics Architecture The HIP base exchange HIP basic features
HIP Host Identity Protocol October 2007 Patrik Salmela Ericsson Agenda What is the Host Identity Protocol (HIP) What does HIP try to solve HIP basics Architecture The HIP base exchange HIP basic features
Technology Terms for 2017
 We will get started in a few minutes!!! Technology Terms for 2017 Important Tech Terms that everyone who uses technology should know and the AgeWell Computer Education Center CEC Spring Kick Off Week!
We will get started in a few minutes!!! Technology Terms for 2017 Important Tech Terms that everyone who uses technology should know and the AgeWell Computer Education Center CEC Spring Kick Off Week!
Chapter 4: Networking and the Internet
 Chapter 4: Networking and the Internet 2015 Pearson Education Limited 2015 Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3 The World Wide Web 4.4 Internet Protocols
Chapter 4: Networking and the Internet 2015 Pearson Education Limited 2015 Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3 The World Wide Web 4.4 Internet Protocols
Nielsen List of Top 10 ios Mobile Apps
 Nielsen List of Top 10 ios Mobile Apps Nielsen's list of the most popular 10 mobile apps for ios in 2016 was dominated by just four technology giants: Google, Facebook, Apple and Amazon. The Nielsen organization
Nielsen List of Top 10 ios Mobile Apps Nielsen's list of the most popular 10 mobile apps for ios in 2016 was dominated by just four technology giants: Google, Facebook, Apple and Amazon. The Nielsen organization
6 Best MacBook Apps to. Back to Gazelle. SIGN IN / REGISTER Facebook Twitter RSS Youtube
 Back to Gazelle SIGN IN / REGISTER Facebook Twitter RSS Youtube Apple News How-To s Sell Your iphone Sell Your Android Sell Other Gadgets Take Care of Your Devices Fix Common Problems Product Reviews Mobile
Back to Gazelle SIGN IN / REGISTER Facebook Twitter RSS Youtube Apple News How-To s Sell Your iphone Sell Your Android Sell Other Gadgets Take Care of Your Devices Fix Common Problems Product Reviews Mobile
Developing Microsoft Azure Solutions (70-532) Syllabus
 Developing Microsoft Azure Solutions (70-532) Syllabus Cloud Computing Introduction What is Cloud Computing Cloud Characteristics Cloud Computing Service Models Deployment Models in Cloud Computing Advantages
Developing Microsoft Azure Solutions (70-532) Syllabus Cloud Computing Introduction What is Cloud Computing Cloud Characteristics Cloud Computing Service Models Deployment Models in Cloud Computing Advantages
Hybrid Information-Centric Networking
 Hybrid Information-Centric Networking ICN inside the Internet Protocol Luca Muscariello, Principal Engineer Giovanna Carofiglio, Distinguished Engineer Jordan Augé, Michele Papalini, Mauro Sardara, Alberto
Hybrid Information-Centric Networking ICN inside the Internet Protocol Luca Muscariello, Principal Engineer Giovanna Carofiglio, Distinguished Engineer Jordan Augé, Michele Papalini, Mauro Sardara, Alberto
NDN Project Progress Report. March 20, 2012 AsiaFI NDN Research Workshop
 NDN Project Progress Report March 20, 2012 AsiaFI NDN Research Workshop Named Data Networking (NDN) NSF FIA 3 year project Lixia Zhang (lead) Jim Thornton (manager) Deborah Estrin (advisor) Van Jacobson
NDN Project Progress Report March 20, 2012 AsiaFI NDN Research Workshop Named Data Networking (NDN) NSF FIA 3 year project Lixia Zhang (lead) Jim Thornton (manager) Deborah Estrin (advisor) Van Jacobson
SOCIAL MEDIA. Charles Murphy
 SOCIAL MEDIA Charles Murphy Social Media Overview 1. Introduction 2. Social Media Areas Blogging Bookmarking Deals Location-based Music Photo sharing Video 3. The Fab Four FaceBook Google+ Linked In Twitter
SOCIAL MEDIA Charles Murphy Social Media Overview 1. Introduction 2. Social Media Areas Blogging Bookmarking Deals Location-based Music Photo sharing Video 3. The Fab Four FaceBook Google+ Linked In Twitter
Cybersecurity in 2016 and Lessons learned
 Cybersecurity in 2016 and Lessons learned Dr. Yu Cai Associate Professor Program Chair, Computer Network & System Administration School of Technology Michigan Technological University cai@mtu.edu A Quick
Cybersecurity in 2016 and Lessons learned Dr. Yu Cai Associate Professor Program Chair, Computer Network & System Administration School of Technology Michigan Technological University cai@mtu.edu A Quick
Chapter 4 The Internet
 Chapter 4 The Internet Dr. Farzana Rahman Assistant Professor Department of Computer Science James Madison University Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3
Chapter 4 The Internet Dr. Farzana Rahman Assistant Professor Department of Computer Science James Madison University Chapter 4: Networking and the Internet 4.1 Network Fundamentals 4.2 The Internet 4.3
YOUR MEDIA DELIVERED
 YOUR MEDIA DELIVERED SUBSPLASH PLATFORM Apps Web Player Podcasting The all-in-one solution to present and manage your content across multiple channels. HOW DOES IT WORK? UPLOAD ENCODE ORGANIZE SHARE Upload
YOUR MEDIA DELIVERED SUBSPLASH PLATFORM Apps Web Player Podcasting The all-in-one solution to present and manage your content across multiple channels. HOW DOES IT WORK? UPLOAD ENCODE ORGANIZE SHARE Upload
Introduction to Computer Science. William Hsu Department of Computer Science and Engineering National Taiwan Ocean University
 Introduction to Computer Science William Hsu Department of Computer Science and Engineering National Taiwan Ocean University Chapter 4: Networking and the Internet No one owns the Internet, and only one
Introduction to Computer Science William Hsu Department of Computer Science and Engineering National Taiwan Ocean University Chapter 4: Networking and the Internet No one owns the Internet, and only one
Converting CVT Account to Microsoft Account
 Email: Converting CVT Email Account to Microsoft Email Account If you need any assistance with this process, please contact us: Copper Valley Telecom Solutions Team 329 Fairbanks Drive, Valdez, AK 99686
Email: Converting CVT Email Account to Microsoft Email Account If you need any assistance with this process, please contact us: Copper Valley Telecom Solutions Team 329 Fairbanks Drive, Valdez, AK 99686
Introduction to the Internet
 Introduction to the Internet CCST9015 8 th Sep, 2010 Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering 2 Internet in 2003 3 Internet Basics The Internet is a network that connects
Introduction to the Internet CCST9015 8 th Sep, 2010 Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering 2 Internet in 2003 3 Internet Basics The Internet is a network that connects
White paper. April Messaging
 White paper April 2011 Messaging This document This Sony Ericsson White paper is intended to give enterprise users an overview of specific smartphone features and provide details in relevant areas of technology.
White paper April 2011 Messaging This document This Sony Ericsson White paper is intended to give enterprise users an overview of specific smartphone features and provide details in relevant areas of technology.
AUDIENCE PARTICIPATION PORTION OF PROGRAM
 AUDIENCE PARTICIPATION PORTION OF PROGRAM PLEASE SET YOUR PHONES TO AIRPLANE MODE NOW OR TURN OFF PHONE S WI-FI HANDS-ON DEMO WON T BE POSSIBLE WITHOUT SUFFICIENT BANDWIDTH, WHICH IS VERY LIMITED IN THE
AUDIENCE PARTICIPATION PORTION OF PROGRAM PLEASE SET YOUR PHONES TO AIRPLANE MODE NOW OR TURN OFF PHONE S WI-FI HANDS-ON DEMO WON T BE POSSIBLE WITHOUT SUFFICIENT BANDWIDTH, WHICH IS VERY LIMITED IN THE
Online Entertainment
 STREAMING DOWNLOAD Your guide to Online Entertainment 1 Contents 1.0 Introduction Page 03 2.0 Online entertainment 2.1 What is online entertainment? Page 04 2.2 What forms of online entertainment are available?
STREAMING DOWNLOAD Your guide to Online Entertainment 1 Contents 1.0 Introduction Page 03 2.0 Online entertainment 2.1 What is online entertainment? Page 04 2.2 What forms of online entertainment are available?
Communications Software. CSE 123b. CSE 123b. Spring Lecture 10: Mobile Networking. Stefan Savage
 CSE 123b CSE 123b Communications Software Spring 2003 Lecture 10: Mobile Networking Stefan Savage Quick announcement My office hours tomorrow are moved to 12pm May 6, 2003 CSE 123b -- Lecture 10 Mobile
CSE 123b CSE 123b Communications Software Spring 2003 Lecture 10: Mobile Networking Stefan Savage Quick announcement My office hours tomorrow are moved to 12pm May 6, 2003 CSE 123b -- Lecture 10 Mobile
Quick announcement. CSE 123b Communications Software. Last class. Today s issues. The Mobility Problem. Problems. Spring 2003
 CSE 123b Communications Software Quick announcement My office hours tomorrow are moved to 12pm Spring 2003 Lecture 10: Mobile Networking Stefan Savage May 6, 2003 CSE 123b -- Lecture 10 Mobile IP 2 Last
CSE 123b Communications Software Quick announcement My office hours tomorrow are moved to 12pm Spring 2003 Lecture 10: Mobile Networking Stefan Savage May 6, 2003 CSE 123b -- Lecture 10 Mobile IP 2 Last
Bring Your Own Device (BYOD) Policy
 Bring Your Own Device (BYOD) Policy To allow students to engage with digital learning Newcastle High School has 13 computer rooms, a wireless network with access across the whole school, a large number
Bring Your Own Device (BYOD) Policy To allow students to engage with digital learning Newcastle High School has 13 computer rooms, a wireless network with access across the whole school, a large number
Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk SOLUTIONS
 Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk Date: January 17 th 2006 at 14:00 18:00 SOLUTIONS 1. General (5p) a) Draw the layered
Examination 2D1392 Protocols and Principles of the Internet 2G1305 Internetworking 2G1507 Kommunikationssystem, fk Date: January 17 th 2006 at 14:00 18:00 SOLUTIONS 1. General (5p) a) Draw the layered
STREAMING DEVICES & STREAMING SERVICES. Ford s Colony Computer & Technology Club May 16, 2016
 STREAMING DEVICES & STREAMING SERVICES Ford s Colony Computer & Technology Club May 16, 2016 WHAT IS STREAMING? Streaming media is multimedia that is constantly received by and presented to an end-user
STREAMING DEVICES & STREAMING SERVICES Ford s Colony Computer & Technology Club May 16, 2016 WHAT IS STREAMING? Streaming media is multimedia that is constantly received by and presented to an end-user
VPN World. MENOG 16 Istanbul-Turkey. By Ziad Zubidah Network Security Specialist
 VPN World MENOG 16 Istanbul-Turkey By Ziad Zubidah Network Security Specialist What is this Van used for?! Armed Van It used in secure transporting for valuable goods from one place to another. It is bullet
VPN World MENOG 16 Istanbul-Turkey By Ziad Zubidah Network Security Specialist What is this Van used for?! Armed Van It used in secure transporting for valuable goods from one place to another. It is bullet
IT-Security Challenges in the Internet of Things. Christian Graffer Product Manager Endian
 IT-Security Challenges in the Internet of Things Christian Graffer Product Manager Endian Who is Endian? Founded in 2003 at Bolzano, Italy, by a team of experienced network specialists and Linux enthusiasts
IT-Security Challenges in the Internet of Things Christian Graffer Product Manager Endian Who is Endian? Founded in 2003 at Bolzano, Italy, by a team of experienced network specialists and Linux enthusiasts
CSCD 330 Network Programming
 CSCD 330 Network Programming Lecture 9 Transport Layer Winter 2019 Reading: Begin Chapter 3 Some Material in these slides from J.F Kurose and K.W. Ross All material copyright 1996-2007 1 Outline Overview
CSCD 330 Network Programming Lecture 9 Transport Layer Winter 2019 Reading: Begin Chapter 3 Some Material in these slides from J.F Kurose and K.W. Ross All material copyright 1996-2007 1 Outline Overview
CSE 123b Communications Software
 CSE 123b Communications Software Spring 2004 Lecture 9: Mobile Networking Stefan Savage Quick announcements Typo in problem #1 of HW #2 (fixed as of 1pm yesterday) Please consider chapter 4.3-4.3.3 to
CSE 123b Communications Software Spring 2004 Lecture 9: Mobile Networking Stefan Savage Quick announcements Typo in problem #1 of HW #2 (fixed as of 1pm yesterday) Please consider chapter 4.3-4.3.3 to
Quick announcements. CSE 123b Communications Software. Today s issues. Last class. The Mobility Problem. Problems. Spring 2004
 CSE 123b Communications Software Spring 2004 Lecture 9: Mobile Networking Quick announcements Typo in problem #1 of HW #2 (fixed as of 1pm yesterday) Please consider chapter 4.3-4.3.3 to be part of the
CSE 123b Communications Software Spring 2004 Lecture 9: Mobile Networking Quick announcements Typo in problem #1 of HW #2 (fixed as of 1pm yesterday) Please consider chapter 4.3-4.3.3 to be part of the
DRAFT. Measuring KSA Broadband. Meqyas, Q Report
 DRAFT Measuring KSA Broadband Meqyas, Q3 218 Report In 217, the CITC in partnership with SamKnows launched a project to measure internet performance. The project, named Meqyas, gives internet users in
DRAFT Measuring KSA Broadband Meqyas, Q3 218 Report In 217, the CITC in partnership with SamKnows launched a project to measure internet performance. The project, named Meqyas, gives internet users in
FilesAnywhere Features List
 FilesAnywhere Feature List FilesAnywhere Page 1 of 9 Contents Basic Features... 3 Advanced Features... 7 Enterprise Features... 9 FilesAnywhere Page 2 of 9 Basic Features No File Size Limit: There is no
FilesAnywhere Feature List FilesAnywhere Page 1 of 9 Contents Basic Features... 3 Advanced Features... 7 Enterprise Features... 9 FilesAnywhere Page 2 of 9 Basic Features No File Size Limit: There is no
Chapter 1 Introduction
 Chapter 1 Introduction A note on the use of these Powerpoint slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Chapter 1 Introduction A note on the use of these Powerpoint slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Access control and policy configuration, tools for security administration. Norman Wu, Ziwei Hu
 Access control and policy configuration, tools for security administration Norman Wu, Ziwei Hu Outline Access control introduction Demos of different access control systems A quick look at papers Other
Access control and policy configuration, tools for security administration Norman Wu, Ziwei Hu Outline Access control introduction Demos of different access control systems A quick look at papers Other
ECS 15; Lectures 17 and 18. The Internet. What is the internet, and how does it work? TA feedback
 ECS 15; Lectures 17 and 18 The Internet What is the internet, and how does it work? TA feedback Python -- Run your code!! Term paper: Start a paragraph with the point of the paragraph, not in modern times
ECS 15; Lectures 17 and 18 The Internet What is the internet, and how does it work? TA feedback Python -- Run your code!! Term paper: Start a paragraph with the point of the paragraph, not in modern times
Steady stream of bits 9/6/2014 5:02:53 PM. Edward Jackson
 DB1 As noted in this unit's reading, there are three main categories of streaming video systems. Name the three categories, give a brief comparison of the categories, then state (and support) your own
DB1 As noted in this unit's reading, there are three main categories of streaming video systems. Name the three categories, give a brief comparison of the categories, then state (and support) your own
Developing Microsoft Azure Solutions (70-532) Syllabus
 Developing Microsoft Azure Solutions (70-532) Syllabus Cloud Computing Introduction What is Cloud Computing Cloud Characteristics Cloud Computing Service Models Deployment Models in Cloud Computing Advantages
Developing Microsoft Azure Solutions (70-532) Syllabus Cloud Computing Introduction What is Cloud Computing Cloud Characteristics Cloud Computing Service Models Deployment Models in Cloud Computing Advantages
Slide 1. Opera Max. Migrating the next billion smartphone users for better app experience
 Slide 1 Opera Max Migrating the next billion smartphone users for better app experience The 3 Consideration in the Next Billion Migration Slide 2 Cost of ownership (Device) Cost of usage (Data) Network
Slide 1 Opera Max Migrating the next billion smartphone users for better app experience The 3 Consideration in the Next Billion Migration Slide 2 Cost of ownership (Device) Cost of usage (Data) Network
Mobility at Northwestern
 NUIT Tech Talk Mobility at Northwestern November 16, 2010 Matt Gruhn Michael Jones Distributed Support Specialist Technical Services Analyst Today s Agenda Mobile Services at NU E-mail and Calendar WiFi
NUIT Tech Talk Mobility at Northwestern November 16, 2010 Matt Gruhn Michael Jones Distributed Support Specialist Technical Services Analyst Today s Agenda Mobile Services at NU E-mail and Calendar WiFi
Armoring your mobile workforce warriors for the 21st century
 Armoring your mobile workforce warriors for the 21st century with System Center Configuration Manager 2012 R2 --- Advanced Warfare --- Tim De Keukelaere Kenny Buntinx Feb 9 th 2015 About Kenny @KennyBuntinx
Armoring your mobile workforce warriors for the 21st century with System Center Configuration Manager 2012 R2 --- Advanced Warfare --- Tim De Keukelaere Kenny Buntinx Feb 9 th 2015 About Kenny @KennyBuntinx
Computer Networking Introduction
 Computer Networking Introduction Halgurd S. Maghdid Software Engineering Department Koya University-Koya, Kurdistan-Iraq Lecture No.3 Chapter 1: roadmap 1.1 what is the Internet? 1.2 network edge end systems,
Computer Networking Introduction Halgurd S. Maghdid Software Engineering Department Koya University-Koya, Kurdistan-Iraq Lecture No.3 Chapter 1: roadmap 1.1 what is the Internet? 1.2 network edge end systems,
Getting to know your ipad exploring the settings, App store, Mail
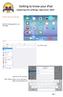 Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
10 ways to securely optimize your network. Integrate WAN acceleration with next-gen firewalls to enhance performance, security and control
 10 ways to securely optimize your network Integrate WAN acceleration with next-gen firewalls to enhance performance, security and control Table of Contents Secure network optimization 3 #1. Application
10 ways to securely optimize your network Integrate WAN acceleration with next-gen firewalls to enhance performance, security and control Table of Contents Secure network optimization 3 #1. Application
Converting CVT Account to Another Account
 Email: Converting CVT Email Account to Another Email Account If you need any assistance with this process, please contact us: Copper Valley Telecom Solutions Team 329 Fairbanks Drive, Valdez, AK 99686
Email: Converting CVT Email Account to Another Email Account If you need any assistance with this process, please contact us: Copper Valley Telecom Solutions Team 329 Fairbanks Drive, Valdez, AK 99686
Chapter 6: Distributed Systems: The Web. Fall 2012 Sini Ruohomaa Slides joint work with Jussi Kangasharju et al.
 Chapter 6: Distributed Systems: The Web Fall 2012 Sini Ruohomaa Slides joint work with Jussi Kangasharju et al. Chapter Outline Web as a distributed system Basic web architecture Content delivery networks
Chapter 6: Distributed Systems: The Web Fall 2012 Sini Ruohomaa Slides joint work with Jussi Kangasharju et al. Chapter Outline Web as a distributed system Basic web architecture Content delivery networks
Developing Enterprise Cloud Solutions with Azure
 Developing Enterprise Cloud Solutions with Azure Java Focused 5 Day Course AUDIENCE FORMAT Developers and Software Architects Instructor-led with hands-on labs LEVEL 300 COURSE DESCRIPTION This course
Developing Enterprise Cloud Solutions with Azure Java Focused 5 Day Course AUDIENCE FORMAT Developers and Software Architects Instructor-led with hands-on labs LEVEL 300 COURSE DESCRIPTION This course
WiFi Issues In The Wild A view from the cloud
 WiFi Issues In The Wild A view from the cloud #WLPC Phoenix 2018 KN Gopinath (VP of Engineering) Karan Gupta (Senior Researcher) Mojo Cloud Architecture - Inception in 2007, Evolving Continuously 1 Management
WiFi Issues In The Wild A view from the cloud #WLPC Phoenix 2018 KN Gopinath (VP of Engineering) Karan Gupta (Senior Researcher) Mojo Cloud Architecture - Inception in 2007, Evolving Continuously 1 Management
Square Credit Card Reader Customer Service Phone Number
 Square Credit Card Reader Customer Service Phone Number Square-Up Customer Support Phone Number and Contact Information / Contact Square Or, contact us anytime to discuss a mobile credit card processing
Square Credit Card Reader Customer Service Phone Number Square-Up Customer Support Phone Number and Contact Information / Contact Square Or, contact us anytime to discuss a mobile credit card processing
CSCI-1680 WWW Rodrigo Fonseca
 CSCI-1680 WWW Rodrigo Fonseca Based partly on lecture notes by Scott Shenker and John Jannotti Precursors 1945, Vannevar Bush, Memex: a device in which an individual stores all his books, records, and
CSCI-1680 WWW Rodrigo Fonseca Based partly on lecture notes by Scott Shenker and John Jannotti Precursors 1945, Vannevar Bush, Memex: a device in which an individual stores all his books, records, and
Protocol Layers, Security Sec: Application Layer: Sec 2.1 Prof Lina Battestilli Fall 2017
 CSC 401 Data and Computer Communications Networks Protocol Layers, Security Sec:1.5-1.6 Application Layer: Sec 2.1 Prof Lina Battestilli Fall 2017 Outline Computer Networks and the Internet (Ch 1) 1.1
CSC 401 Data and Computer Communications Networks Protocol Layers, Security Sec:1.5-1.6 Application Layer: Sec 2.1 Prof Lina Battestilli Fall 2017 Outline Computer Networks and the Internet (Ch 1) 1.1
CREATING AN OUTSTANDING WEBSITE FOR EVERY BUSINESS
 CREATING AN OUTSTANDING WEBSITE FOR EVERY BUSINESS 1.1 Design When designing and building a website today, it s essential for businesses to think about how users will access their website. Research undertaken
CREATING AN OUTSTANDING WEBSITE FOR EVERY BUSINESS 1.1 Design When designing and building a website today, it s essential for businesses to think about how users will access their website. Research undertaken
Going Mobile at Northwestern
 NUIT Tech Talk Going Mobile at Northwestern May 17, 2011 NUIT Support Center staff Today s Agenda Popular Mobile Devices iphone/ipod Touch Android Phone Windows Phone 7 BlackBerry Laptops, Tablets, and
NUIT Tech Talk Going Mobile at Northwestern May 17, 2011 NUIT Support Center staff Today s Agenda Popular Mobile Devices iphone/ipod Touch Android Phone Windows Phone 7 BlackBerry Laptops, Tablets, and
10 WEBSITE MISTAKES EVEN GREAT MARKETERS CAN MAKE. Jessica Bybee-Dziedzic Saffire
 10 WEBSITE MISTAKES EVEN GREAT MARKETERS CAN MAKE Jessica Bybee-Dziedzic Saffire BUT SOMETHING WAS MISSING We wanted to HELP MORE PEOPLE! Beautiful, Unique Designs PRINT-AT-HOME TICKETS SCANNING
10 WEBSITE MISTAKES EVEN GREAT MARKETERS CAN MAKE Jessica Bybee-Dziedzic Saffire BUT SOMETHING WAS MISSING We wanted to HELP MORE PEOPLE! Beautiful, Unique Designs PRINT-AT-HOME TICKETS SCANNING
Ronald van der Pol
 Ronald van der Pol Contributors! " Ronald van der Pol! " Freek Dijkstra! " Pieter de Boer! " Igor Idziejczak! " Mark Meijerink! " Hanno Pet! " Peter Tavenier Outline! " Network bandwidth
Ronald van der Pol Contributors! " Ronald van der Pol! " Freek Dijkstra! " Pieter de Boer! " Igor Idziejczak! " Mark Meijerink! " Hanno Pet! " Peter Tavenier Outline! " Network bandwidth
High-speed Traffic Analysis Using ntopng: The New Features
 High-speed Traffic Analysis Using ntopng: The New Features High Speed Traffic Analysen mit ntopng: Die neuen Features Luca Deri Some History In 1998, the original ntop has been created.
High-speed Traffic Analysis Using ntopng: The New Features High Speed Traffic Analysen mit ntopng: Die neuen Features Luca Deri Some History In 1998, the original ntop has been created.
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 Mobile IP 2 Mobile Network Layer: Problems and Concerns Entities and Terminology in Mobile IP Mobile Indirect Routing Mobile IP Agent Advertisement Registration
Mohammad Hossein Manshaei manshaei@gmail.com 1393 Mobile IP 2 Mobile Network Layer: Problems and Concerns Entities and Terminology in Mobile IP Mobile Indirect Routing Mobile IP Agent Advertisement Registration
Entertainment Services: The future is mobile White Paper December 2016
 Entertainment Services: The future is mobile White Paper December 2016 Entertainment Services: The future is mobile White Paper Published December 2016 Version 1.0 Report Number: 042016-07 igr 12400 W.
Entertainment Services: The future is mobile White Paper December 2016 Entertainment Services: The future is mobile White Paper Published December 2016 Version 1.0 Report Number: 042016-07 igr 12400 W.
ARCHITECTURE INTEROPERABILITY BETWEEN CLOUD COMPUTING AND NAMED DATA NETWORKING: SECURITY ISSUES ON REVIEW
 ARCHITECTURE INTEROPERABILITY BETWEEN CLOUD COMPUTING AND NAMED DATA NETWORKING: SECURITY ISSUES ON REVIEW 1 Sulaiman Yakubu Yunus, 2 Umar Abubakar Abdullahi and 3 Magaji Yunusa Rabi u 1 Computer Science
ARCHITECTURE INTEROPERABILITY BETWEEN CLOUD COMPUTING AND NAMED DATA NETWORKING: SECURITY ISSUES ON REVIEW 1 Sulaiman Yakubu Yunus, 2 Umar Abubakar Abdullahi and 3 Magaji Yunusa Rabi u 1 Computer Science
Online Video Playbook. Written by: Johnny Beirne
 Online Video Playbook Written by: Johnny Beirne Table of Contents Introduction... 1 On-camera...... 2 Animation...... 3 Animated GIFs........ 4 Screen Capture Tutorials... 5 Smart Phone Videos...... 6
Online Video Playbook Written by: Johnny Beirne Table of Contents Introduction... 1 On-camera...... 2 Animation...... 3 Animated GIFs........ 4 Screen Capture Tutorials... 5 Smart Phone Videos...... 6
