Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache
|
|
|
- Antony Rice
- 5 years ago
- Views:
Transcription
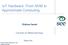
1 Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache Fazal Hameed Technische Universität Dresden Center for Advancing Electronics Dresden Germany Christian Menard Technische Universität Dresden Center for Advancing Electronics Dresden Germany Jeronimo Castrillon Technische Universität Dresden Center for Advancing Electronics Dresden Germany ABSTRACT Recent research has proposed die-stacked Last Level Cache (LLC) to overcome the Memory Wall. Lately, Spin-Transfer-Torque Random Access Memory (STT-RAM) caches have been recommended as they provide improved energy efficiency compared to DRAM caches. However, the recently proposed STT-RAM cache architecture unnecessarily dissipates energy by fetching unneeded cache lines into the row buffer. In this paper, we propose a Selective Read Policy for STT-RAM. This policy only fetches those cache lines into the row buffer that are likely to be reused. This reduces the number of cache line reads and thereby reduces the energy consumption. Further, we propose two key performance optimizations namely Row Buffer Tags Bypass Policy and LLC Data Cache. Both optimizations reduce the LLC access latency and therefore improve the overall performance. For evaluation, we implement our proposed architecture in the Zesto simulator and run different combinations of SPEC2006 benchmarks on an 8-core system. We show that our synergetic policies reduce the average LLC dynamic energy consumption by 72.6% and improve the system performance by 1.3% compared to the recently proposed STT-RAM LLC. Compared to the state-of-theart DRAM LLC, our architecture reduces the LLC dynamic energy consumption by 90.6% and improves system performance by 1.4%. CCS CONCEPTS Hardware Non-volatile memory; ACM Reference format: Fazal Hameed, Christian Menard, and Jeronimo Castrillon Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache. In Proceedings of International Symposium on Memory Systems, Washington DC, USA, October 2 5, 2017 (MEMSYS 17), 11 pages. DOI: /nnnnnnn.nnnnnnn 1 INTRODUCTION AND MOTIVATION Conventional off-chip memories do not fulfil the bandwidth and latency requirements of complex applications running on multi-core Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. Copyrights for components of this work owned by others than ACM must be honored. Abstracting with credit is permitted. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. Request permissions from permissions@acm.org. MEMSYS 17, Washington DC, USA 2017 ACM. 978-x-xxxx-xxxx-x/YY/MM... $15.00 DOI: /nnnnnnn.nnnnnnn Distribution of lines reused befor RB eviction 100% 80% 60% 40% 20% 0% >4 Mix_01 Mix_02 Mix_03 Mix_04 Mix_05 Mix_06 Average Figure 1: Distribution of number of unique lines reused before RB eviction using 2KB RB size for SPEC2006 application mixes (see Table 2) systems [6]. The limited number of I/O pins provided by the packaging induces a gap between processor and memory performance. This widening gap is known as the Memory Wall [41] and severely limits the performance of applications with large memory and bandwidth requirements. A potential solution to mitigate the memory wall problem is to employ die-stacked technologies [1, 22, 24, 38]. These technologies integrate processor and memory dies employing a low latency and high bandwidth interconnect. To abate the number of high latency accesses to bandwidth-limited off-chip memory, recent research proposed to implement the die-stacked memory as a large capacity Last-Level-Cache (LLC) [7 13, 16, 27]. Previously, on-chip DRAM memory has been adopted as LLC for performance improvement due to its capacity advantage compared to an area equivalent SRAM cache [9 11, 16, 27]. However, the DRAM LLC dissipates a significant portion of chip power budget due to its high refresh and dynamic energy consumption. Therefore, recent research has advocated the use of non-volatile Spin-Transfer- Torque Random Access Memory (STT-RAM) as LLC [13]. By exploiting the non-volatility characteristics of STT-RAM, the energy consumption of the LLC can be reduced significantly compared to DRAM. Typically, a high capacity STT-RAM holds multiple banks and each bank is provided with a Row Buffer (RB) [13, 23]. The total energy consumption in existing STT-RAM LLC is dominated by reading data from an STT-RAM bank into the RB [13]. To reduce the energy consumption of STT-RAM LLC, we exploit the fact that most of the cache lines are unnecessarily fetched into the RB as they are not likely to be reused in the near future. Figure 1 shows
2 MEMSYS 17, October 2 5, 2017, Washington DC, USA Fazal Hameed, Christian Menard, and Jeronimo Castrillon that the probability for the RB content to be accessed before RB eviction is less than 40%. Therefore, we fetch only those cache lines into the RB that are likely to be reused. This reduces the number of RB fetches significantly and, therefore, also reduces the dynamic energy consumption of an STT-RAM LLC. However, identifying the likelihood for a cache line to be reused induces a high tag access latency when using existing tag read policy [9, 13, 27]. Therefore, we also propose a novel RB Tags Bypass Policy that provides fast access to LLC tags. More precisely, we make the following contributions: (1) We classify lines of an STT-RAM row into highly-reused and lowly-reused lines. (2) We propose a Selective Read Policy that only fetches highlyreused lines of an STT-RAM row into the RB. By avoiding the need to fetch lowly-reused lines, we reduce the energy consumption significantly. (3) While the Selective Read Policy saves energy it also induces a latency penalty. To improve the performance, we propose a RB Tags Bypass Policy. (4) To further improve the performance, we also propose a small LLC Data Cache (LDC) that stores lines which are likely to be accessed later. Lines that hit in the LDC are accessed with much lower latency. 2 BACKGROUND This section presents details of the organization for the recently proposed LLC. Further, this section describes the basic operating principles of STT-RAM and qualitatively compares STT-RAM to DRAM. 2.1 State-of-the-art LLC Organization Figure 2a illustrates the organization of the previously proposed LLC [9, 10, 13]. The LLC is split into multiple memory banks each equipped with a row buffer (RB). Each bank is organized as a series of rows that are split into columns. In this paper, we assume an LLC size of 256 MB, a row size of 2048 bytes and a column size of 64 bytes. The LLC is implemented as a set-associative cache. Recent research proposed various set mapping policies [9, 10, 13, 27, 31]. For this paper, we use the most recently proposed policy LAMOST that was used for DRAM [9, 10] LLCs and STT-RAM LLC [13]. In the LAMOST policy, the tags and lines of an LLC are stored in the same row. Each 2KB LLC row comprises 4 sets with 7-way associativity. Each set contains 7 cache lines and a tag column. The cache lines have a size of 64 bytes. Each tag has a size of 31 bits and in each tag column 7 31 = 217 bits are used for the 7 tag entries. This leaves 295 bits of each tag column unused. In this paper, we assume 44-bit physical addresses. The address is split into multiple parts as depicted in Figure 2b. The 18 most significant bits identify the LLC-tag. The next 12 bits select a row within a bank and the following 6 bits select a memory bank within the LLC. 2 bits are used to identify the set within a row and the remaining 6 least significant bits identify a byte within a cache line. Figure 3 shows how main memory blocks are mapped to a particular bank, row, and set using the LAMOST policy. All the Legend Row Buffer Row TC-k Tag column CL-j CL: Cache Line j for set k within a set Tag-m Tag for cache line m within a set LLC Cache Bank Bank Bank Set-0 Set-1 Set-2 Set-3 TC-1 CL-0 CL-1 CL-2 CL-3 CL-4 CL-5 CL-6 64 bytes = 512 bits Tag-0 Tag-1 Tag-2 Tag-3 Tag-4 Tag-5 Tag-6 (b) (a) 64 bytes Unused 31 bits 31 bits 295 bits LLC-Tag 18 bits Valid 1 bit Dirty 1 bit 2048-Bytes LRU 3 bits LLC-Tag 18 bits (a) LLC LAMOST organization Main Memory Address (44 bits) Row-id 12 bits Bank-id 6 bits Set-id 2 bits (b) Address organization Line offset 6 bits Coherence 8 bits Figure 2: Typical LLC and address organization using the LAMOST policy [9, 10, 13] for an 8-core system with 256 MB LLC size, 64 banks, 2 kb row buffer size and 44-bit physical addresses SB s in Main Memory SB-0 SB SB SB-1 SB SB st Block 2 nd Block 3 rd Block 4 th Block 1 st Block 2 nd Block 3 rd Block 4 th Block Bank-0/Row-0 Bank-0/Row-0 Bank-0/Row-0 Bank-0/Row-0 Bank-1/Row-0 Bank-1/Row-0 Bank-1/Row-0 Bank-1/Row-0 Set-0 Set-1 Set-2 Set-3 Set-0 Set-1 Set-2 Set-3 Figure 3: Bank/row/set mapping for LAMOST policy [9, 10, 13]. SB stands for super-block blocks that are mapped to the same row are referred to as a superblock (SB). With the LAMOST policy, each super-block consists of 4 consecutive 64 byte memory blocks.
3 Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache MEMSYS 17, October 2 5, 2017, Washington DC, USA Write-0 For each bank, the RB holds a copy of the row that was retrieved last. The RB allows for exploiting bank-level parallelism while keeping a shared command, address, and data bus. A controller or access scheduler is employed do avoid any conflicts on the shared buses. In order to access a cache line, the controller issues a command that fetches the corresponding row from the bank to the bank s row buffer. Successive requests to cache lines that are contained within the same row are serviced directly without fetching the row again. This is referred to as a row buffer hit. An access to a line that is contained in a different row, requires to fetch this row into the RB. This is referred to as a row buffer miss. The access latency and energy of an RB hit is much lower compared to that of an RB miss. Therefore, an application with high row buffer locality (many row buffer hits) has better performance and lower energy consumption than a similar application with low row buffer locality. While we assume a specific setting with fixed row, column, LLC, and physical address size, the concepts presented in this paper can be applied to other settings as well. 2.2 Basic Operating Principles of DRAM and STT-RAM In DRAM, data is stored as a charge in a bit-cell. During a DRAM cell read operation, the charge stored in the capacitor is shared with the bitline. The sense amplifier that is connected to each bitline detects the voltage change which is then translated to either logical 0 or logical 1. The sense amplifier consists of cross-coupled transistors that amplify the small differential signal that appears on the bitline following the charge transfer from the bit-cell. In DRAM, all the sense amplifiers that are connected to the bitlines are referred to as the row buffer. Due to this physical connection, the RB and the bit-cells in the DRAM bank are tightly coupled. An STT-RAM bit-cell uses a Magnetic Tunnel Junction (MTJ) device to store the information. The MTJ is made of two independent ferromagnetic layers, the reference layer and the free layer (see Figure 4a). The magnetic orientation of the reference layer is fixed. However, the magnetic orientation of the free layer can be freely rotated. It can be parallel or anti-parallel to the reference layer. Depending on the magnetic orientation of the free layer, the resistance of the MTJ cell changes. In the parallel state, the resistance is low and the cell stores a logical 0. In the anti-parallel state, the resistance is high and the cell stores a logical 1. To read the value from a bit-cell, a voltage is applied between the source line and the bitline (see Figure 4b). This causes a low current to flow through the MTJ. The sense amplifier uses this current to detect the resistance state of the MTJ cell and decides for logical 0 or logical 1, which then can be stored in the row buffer. 2.3 STT-RAM RB Bypass and Partial Write Optimizations In DRAM, the RB (i.e. sense amplifiers) and the bit-cells are tightly coupled due to charge sharing. Therefore, any read/write operation in DRAM requires the data to be fetched into the RB. A prominent characteristic of STT-RAM is the decoupled organization [13, 23, 29] of its sense amplifiers and the RB (Figure 5). This is a major advantage over DRAM for the following three reasons. Iw > Ic Parallel (P) MgO Low Resistance Free Layer (FL) Reference Layer (RL) (a) Anti-Parallel (AP) MgO High Resistance Iw > Ic Write-1 MTJ Word Line (WL) Bit Line (BL) Access Transistor Source Line (SL) Figure 4: An STT-RAM bit-cell (a) and the Magnetic Tunnel Junction device (b) that stores a single bit of information. Bit-line Sense-line Write Amplifier Write Bypass Sense Amplifier + VRD - Row Buffer Sense Amplifiers and Row Buffer are decoupled Column Select (b) Read Bypass Write Driver Read Latch Figure 5: An STT-RAM peripheral circuit that supports both, memory access via a row buffer and direct access to the STT- RAM array via a bypass [13, 23]. (1) It is possible to bypass the RB in STT-RAM. The read or write operation can be performed directly on the STT-RAM bank bit cells without the need to fetch the data into the RB. This RB bypassing has been leveraged recently [13, 23] to improve performance and energy efficiency by increasing the row buffer locality. (2) Read or write operations can be performed directly on the RB without requiring the sense amplifiers. An STT-RAM bank column access does not necessarily requires the RB. (3) The STT-RAM bank and the RB can operate independently on different rows which improves access parallelism. Traditionally, on an RB miss, the newly requested row is always fetched in the row buffer. However, if the row that is currently stored in the RB is likely to experience RB hits, it should not be replaced by a row that is likely to experience an RB miss. Therefore, the traditional policy does not work well due to the following reasons. First, eviction of useful rows (i.e. that are likely to experience RB hits) reduces the RB hit rate and therefore reduces the overall performance. Second, a low RB hit rate leads to a large number of RB fetches which significantly increases the energy consumption. Considering the cache access types (read, write, and writeback), the writeback access is particularly bad. An access after a writeback has a chance of less than 5% to hit the RB [13]. Therefore, recent work [13, 23] has proposed to bypass the RB for the writeback access and to perform the cache writeback operation directly on an STT-RAM column. This optimization improves both performance and energy efficiency by increasing RB hit rate and avoiding unnecessary RB evictions. To further reduce the energy consumption, the partial write optimization proposed in [23] only writes dirty columns from the
4 MEMSYS 17, October 2 5, 2017, Washington DC, USA Fazal Hameed, Christian Menard, and Jeronimo Castrillon L1 Core 0 L2 Tag Cache LLC Data Cache Miss Predictor L1 Core 1 L2 L3 SRAM Cache Miss Hit Main Memory Controller STT Controller Selective Read Policy Address and control RB Bypass Policy (tags) Data L1 Core N-1 L2 Main Memory STT-RAM Last-Level- Cache Our Contributions Figure 6: An STT-RAM based LLC architecture for an N-core system highlighting our contributions. RB back to the STT-RAM array after an RB eviction. Both, the RB bypass and the partial write optimization are very easy to implement in STT-RAM due to its decoupled organization of the sense amplifiers and the RB as depicted in Figure 5. 3 PROPOSED STT-RAM LLC ARCHITECTURE Based on the state-of-the-art discussed in the previous section, this section discusses our novel STT-RAM based LLC architecture. 3.1 Overview Figure 6 depicts an overview of the STT-RAM based LLC architecture and highlights our contributions. Similar to [13, 23], the proposed architecture uses RB bypass and partial write optimizations (recall Section 2.3) which improves performance and energy consumption compared to the traditional policy. Our LLC uses the same organization as the one proposed in [9, 10, 13] and shown in Figure 2. A disadvantage of existing LLC RB policy [9, 10, 13, 27, 31] is that it always fetches an entire row into the RB while the majority of columns within the row are not accessed again. To reduce the energy consumption, we mark LLC lines as lowly reused and highly reused lines. Based on this distinction, we propose a Selective Read Policy that only fetches the useful STT-RAM columns into the RB. However, when we apply the Selective Read Policy, the existing tag read policy incurs high access latencies. To reduce this latency, we propose a novel RB Tags Bypass Policy. To further reduce the access latency and improve the LLC performance, we also propose the usage of a novel LLC Data Cache (LDC). 3.2 Selective Read Policy The basic tenet of our proposed Selective Read Policy is to reduce STT-RAM energy costs by eliminating unnecessary STT-RAM array column reads. When we only fetch those cache lines that are likely to be reused, we avoid unnecessarily fetching data from the STT- RAM array and thereby reduce the energy consumption. In order to quantify how often LLC lines in the RB are reused, we perform a simple experiment. For this, we use a state-of-the-art STT-RAM LLC with 2kB RB size, the LAMOST set mapping policy, and the STT-RAM optimizations discussed in Section 2.3. We run a series of SPEC2006 [2, 15] application mixes as listed in Table 2 and count the number of lines that are reused in the RB before eviction. Figure 1 displays the results of this experiment. Figure 1 clearly shows that the majority of RB fetches are unnecessary, as none of the lines in the RB are accessed again in over 60% of the cases. The number of times that more then 4 lines in the RB are reused before eviction is less than 2%. This observation provides the motivation to fetch only those lines into the RB that are likely to be reused. The RB has a low utilization due to the bank/row/set mapping (Figure 2b) of the LAMOST policy as shown in Figure 3. Since the super blocks that are mapped to the sets of the same LLC row are spacial distant, it is unlikely that subsequent accesses hit the RB. However, adjusting the mapping policy in favour of a higher RB hit rate would decrease the LLC hit rate. This trade-off in finding an ideal mapping policy is beyond the scope of this paper. We focus on improving the energy efficiency for the existing state-of-the-art LAMOST policy. In order to only fetch lines into the RB that are likely to be reused, we classify the LLC lines as highly-reused and lowly-reused lines. We mark one line for each of the 4 sets within an LLC row as highly-reused. When selecting the highly-reused line of a set, we distinguish two cases. If a block of the currently requested super-block is present in the set, then the corresponding line is highly-reused. This considers the fact, that subsequent accesses are likely to be within the same super-block. If a set does not contain a block of the currently requested super-block, the least recently used (LRU) line of this set is the highly-reused line. This considers the fact, that this line is likely to be replaced on a subsequent access. Then, the line will need to be written back to the main memory if it is dirty. Therefore, it is likely to be reused. We illustrate the Selective Read Policy using a simple example as illustrated in Figure 7. We assume a super block S b that contains four adjacent memory blocks named b 0, b 1, b 2, and b 3. The blocks are mapped to the sets Set 0, Set 1, Set 2, and Set 3, respectively. Further, we assume that block b 2 is currently requested. On an RB miss, the corresponding row needs to be fetched into the RB. Traditionally, the complete row would be fetched. However, using the Selective Read Policy we only fetch the 4 highly-reused lines. In the example in Figure 7, the highly-reused lines are marked by arrows. The lines L 0 of Set 0 and L 4 of Set 2 are highly-reused lines since they hold the blocks b 0 and b 2 of the currently accessed super-block S b. The other blocks of S b (b 1 and b 3 ) are not currently present in the sets Set 1 and Set 3. Therefore, the LRU lines in these sets are marked as highly reused. In order to decide which line is highly-reused, the 4 tag columns need to be fetched first. Then, the 4 highly-reused lines are fetched into the RB. Our proposal requires a total of 8 column reads on an RB miss compared to 32 column reads in a traditional LLC architecture. If a subsequent request misses the RB, the RB is evicted and the whole process is repeated. However, if a subsequent request hits the RB, we need to check if the requested line is present in the RB. Since we only fetch the highly-reused lines of each row, not all lines
5 Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache MEMSYS 17, October 2 5, 2017, Washington DC, USA One 2KB row contains 4 cache sets with 7-way associativity Set-0 Set-1 Set-2 Set-3 Row j Col T 0 L 0 L 1 L 2 L 3 L 4 L 5 L 6 T 1 L 0 L 1 L 2 L 3 L 4 L 5 L 6 T 2 L 0 L 1 L 2 L 3 L 4 L 5 L 6 T 3 L 0 L 1 L 2 L 3 L 4 L 5 L b 0 b 2 Highly-reused line Highly-reused line Highly-reused line Highly-reused line Legend T k Tag column for set k within a row L m Cache Line m within a set LRU line within a cache set Blocks belonging to the requested super-block Figure 7: Example illustrating the Selective Read Policy using LAMOST organization and 2KB row size are present in the RB. If the line is present in the RB, we can directly serve the request. Otherwise, we likely encountered the rare case in Figure 1 where more than 4 lines of a row are reused. Therefore, we now fetch the complete row from the STT-RAM array to the RB. The implementation of the Selective Read Policy induces an additional hardware overhead. In order to keep track of which lines are currently present in the RB, we need to store a present bit for each line in the row. This requires 28 bits per STT-RAM bank. This is a total overhead of 224 bytes for our LLC organization with 64 banks. 3.3 Latency Breakdown In this section, we analyze the latencies that occur in an STT-RAM based LLC architecture. We assume the LLC architecture depicted in Figure 6 along with a Tag-Cache. We further assume a request to block b 2 as in Figure 7. The latency breakdown for various scenarios in state-of-the-art LLC architectures is explained in the following: RB miss and Tag-Cache miss in LAMOST. Figure 8a shows the latency breakdown of a RB and Tag-Cache miss without employing the Selective Read Policy. This latency includes 18 cycles for row activation (ACT), 18 cycles for column access latency (CAS) to access the tag column (i.e. T 2 ), two cycles to transfer the relevant tag column on the bus (i.e. RD T 2 ), one cycle for the tag check, another 18 cycles to access the requested cache line, and two cycles to read the cache line (i.e. RD CL). This is a total of 59 cycles. After that, the controller issues successive read request to prefetch the remaining tag columns (i.e. RD T 0, T 1, and T 3 ) into the Tag- Cache. The additional latency required to read the non-requested tag columns (i.e. T 0, T 1, and T 3 ) is 6 cycles. This extra latency overhead is repayed by future hits in the Tag-Cache leveraging the temporal locality of application. Therefore, the RB/Tag-Cache miss latency is 59 cycles. RB miss and Tag-Cache hit. A Tag-Cache hit does not require an extra CAS command to access the tag column T 2, which is required to identify the location of the requested line. Therefore, read requests that hit in the Tag-Cache (Figure 8b) have a much lower latency (i.e. 40 cycles) compared to the Tag-Cache miss. (a) (b) (c) ACT (ROW) CAS (T2) ACT: Row activation latency (18) Tag Check latency (1) Bus latency for one block (2) CAS: Column Access latency (18) CAS (T0) CAS (LINE) Row ready in the RB RD T2 RD CL ACT (ROW) 40 cycles RB miss Latency 59 cycles CAS (LINE) CAS (T3) CAS (T1) Row ready in the RB RD CL 22 cycles CAS (LINE) (RB hit: Tag-Cache hit) RD CL RB hit Latency 41 cycles Tag-Cache latency (2) CL: Cache line RD T1 RD T0 RD T3 (RB miss: Tag-Cache hit) Figure 8: The latency incurred in LAMOST policy for various scenarios (a) RB miss and Tag-Cache miss (b) RB miss and Tag-Cache hit (c) RB hit and Tag-Cache hit RB hit and Tag-Cache hit. Read requests that hit both in the RB and the Tag-Cache do not require an extra ACT command to fetch the requested row in the RB. Therefore, these requests are serviced much faster (i.e. 22 cycles) as illustrated in Figure 8c. 3.4 RB Tags Bypass Policy The LLC tag read policy in [10, 11, 13, 16] always fetches the tags (and the lines) in the RB before inserting them in the Tag-Cache. However, this policy worsens the RB and Tag-Cache miss latency for the Selective Read Policy which is shown in Figure 9a. The Selective Read Policy requires two row activations. One for fetching the 4 tag columns and one subsequent activation for fetching the
6 MEMSYS 17, October 2 5, 2017, Washington DC, USA Fazal Hameed, Christian Menard, and Jeronimo Castrillon (a) 84 cycles ACT (T0,T1,T2,T3) CAS (T0,T1,T2,T3) ACT (Partial) CAS (LINE) 30 bits Main Memory Address (44 bits) 6 bits 2 bits 6 bits (b) Tag-blocks in the RB Tag-blocks in Tag-Cache 66 cycles ACT (T0,T1,T2,T3) ACT (Parital) CAS (LINE) Tag-blocks in Tag-Cache Useful lines in the RB RD CL 18 cycles saved RD CL SB-Tag LDC Associativity (8) LDC Set-Index Tag-2 Line offset SB: Super-block Data Blocks (8) ACT: Row activation latency (18) Tag Check latency partial read (2) CL: Cache line Bus latency for one block (2) CAS: Column Access latency (18) Figure 9: The RB miss and Tag-Cache miss latency with Selective Read Policy using (a) existing tag read policy (b) controller optimizations exploiting RB bypassing for the tags Sets in LDC (64) Table 1: Latencies for read requests in various scenarios in our proposed LLC architecture excluding controller latency RB Hit Tag-Cache Cache Line Figure Hit Latency No No 66 cycles 9b No Yes 40 cycles 8b Yes No 41 cycles 8a Yes Yes 22 cycles 8c SB-Miss SB-Tag- Compare SB-Hit Tag-2 Compare LDC miss LDC hit Valid Dirty Tag Data 1 bit 1 bit 32 bits 3 bits SB-Tag LRU Tag-2 highly-reused lines. Furthermore, additional 26 cycles (18 cycles for CAS and 8 cycles for the bus transfer) will be required to read all the tags from the RB into the Tag-Cache. Therefore, the RB miss and Tag-Cache miss latency is 84 cycles for the Selective Read Policy in combination with the existing tag reading policy. The additional latency overhead for an RB and Tag-Cache miss using the Selective Read Policy is 25 cycles (84-59 = 25) when compared to the LAMOST policy. In order to reduce this latency overhead, we propose to bypass the RB for accessing the tags by exploiting the decoupled organization of the sense amplifiers and the RB in STT-RAM. Instead of fetching the tags into the RB, we store them directly in the Tag-Cache. Figure 9b shows the sequence of commands to read the tags and the cache line for this scenario. By avoiding the CAS command for fetching the tags from the RB, the latency is reduced by 18 cycles to a total of 66 cycles. Apart from reducing the access latency, the RB Tags Bypass Policy also reduces energy consumption, as the write energy for storing the tags in the RB and the read energy for reading the tags from the RB to the Tag-Cache are avoided. To further improve performance, we update tags that are present directly in the Tag-Cahe and do not immediately write them back to the STT-RAM. Since an STT-RAM write is more expensive than a write to the Tag-Cache, this approach potentially saves energy and reduces latency. In contrast to our approach, existing LLC architectures originally used for DRAM architectures [9, 10, 26, 27] always update the tags both in the Tag-Cache and the memory bank. In our implementation, the tags are only written back to the STT-RAM array after they are evicted from the Tag-Cache. Figure 10: LLC Data Cache Organization (LDC) 3.5 LLC Data-Cache Organization The access latency of reading a line from the STT-RAM array varies from 22 to 66 cycles depending on the scenario (see Table 1). To further reduce the latency, we extend our LLC architecture by a small on-chip SRAM structure called LLC Data-Cache (LDC) that holds the LLC cache lines that are likely to be accessed in the future. Figure 6 shows the addition of the LDC to the existing LLC architecture. Figure 10 illustrates the organization of the LDC. It holds 64 sets with 8-way associativity and has a total size of 34.5 kb. LLC access that hit the LDC are serviced in only 2 cycles, due to the small structure. This accelerates LDC hits significantly compared to the 22 to 66 cycles for STT-RAM accesses. On an LDC access, the LDC set-index field of a main memory address selects a set in the LDC. All tag fields in this set are then compared to the tag fields of the memory address to identify an LDC hit. The SB-Tag field of the memory address corresponds to the super-block and the Tag-2 field identifies the block within a super-block. Figure 11 shows the control flow of the LDC controller in our proposed LLC architecture. On each LLC request, the LDC is accessed first in order to identify an LDC hit. If the access hits the LDC, the request is serviced directly and an STT-RAM access is avoided. Otherwise, the request needs to be serviced regularly by the LLC. New lines are only inserted into the LDC on LLC read hits. In all other cases, the LDC is left unchanged. On an LLC read
7 Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache MEMSYS 17, October 2 5, 2017, Washington DC, USA LLC request 66 cycles 2 cycles CAS (b 0 ) LDC hit? Yes Read/Write CL from/to LDC ACT (T0,T1,T2,T3) ACT (Parital) CAS (b 2 ) RD b 0 No Read Req? Yes LLC hit? Yes ACT: Row activation latency (18) Bus latency for one block (2) Tag-blocks in Tag-Cache Useful lines in the RB RD b 2 Tag Check latency partial read (2) CAS: Column Access latency (18) No Do nothing No Yes Adjacent blocks in LDC? No Figure 12: The RB/Tag-Cache miss latency with LDC using the proposed LDC insertion policy in Figure 11 for the illustrating example in Figure 7 Load adjacent blocks into LDC Figure 11: LDC lookup and insertion policy hit, not the currently requested block is written to the LDC, but all adjacent blocks of the corresponding super-block are loaded to the LDC. The proposed LDC insertion policy exploits the temporal and spatial locality of applications as adjacent blocks of a super-block are likely be accessed in the near future. Note that all the blocks of the super-block (SB) are mapped to the same LDC set. To elaborate our LDC insertion policy, we use the example from Figure 7. We assume that b 2 is currently requested and that b 0 does not reside in the LDC. Since the request to b 2 hits the LLC, the block is transported to the lower level caches (i.e. L3, L2, and L1) and finally to the requesting core. Since b 2 will be stored in the L1 cache, further requests to b 2 are unlikely to arrive at the LLC. Therefore, b 2 is not inserted into the LDC. However, adjacent blocks of the same super-block are very likely to be accessed in the near feature. Therefore, all adjacent blocks are that are present in the LLC are loaded to the LDC. In the example, b 0 is loaded to the LDC after the read request to b 2. Figure 12 shows the latency breakdown of an RB and Tag-Cache miss for the above example using the proposed LDC insertion policy in Figure 11. First, the LLC controller loads the tag columns from an STT-RAM array into the Tag-Cache and identifies the highlyreused lines (see Figure 7) of the row. Then, the highly-reused lines are loaded into the RB. Subsequently, read requests are sent to read the blocks b 2 and b 0 from the RB. b 2 is forwarded to the L3 cache and b 0 is stored in the LDC. Requesting b 0 in addition to b 2 only incurs an overhead of 2 cycles as illustrated in Figure 12. This latency overhead depends upon the number of adjacent blocks that are currently present in the LLC. It ranges from 0 to 6 cycles for 0 to 3 present blocks, respectively. The latency overhead for reading additional blocks to fill LDC is compensated by future hits in the LDC, exploiting the fact that these blocks will most likely be accessed later (confer to Figure 17 for evaluation). 3.6 Summary In order to reduce the number of cache lines that are read unnecessarily to the RB, we introduced the Selective Read Policy. Using this policy, only one line of each of the 4 sets within a row is fetched into the row buffer. These 4 lines are likely to be reused on a subsequent access. For each line in a bank we store a presence bit to keep track of the lines currently residing in that bank. If an access hits the RB but the corresponding line is not present in the RB, the whole row is fetched to the RB. (i.e. less than 2% of the time for all application mixes). In order to identify the highly-reused line of a set, first the tag columns of the row need to be analyzed. To reduce the latency for tag column reads and to further reduce the energy consumption, we do not load the tag columns into the RB but load them directly to the Tag-Cache. This is referred to as RB Tags Bypass Policy. In addition, we update present tags directly in the Tag-Cache and write them back to the STT-RAM array only after eviction from the Tag-Cache. As shown in Table 1, the service times for LLC requests lies in a range from 22 to 66 cycles. To further exploit the temporal and spacial locality of typical applications, we introduced an additional LLC Data Cache (LDC) that holds lines that are likely to be used in future requests. A hit in the LDC, reduces the service time for the request to only 2 cycles. Similar to the work in [13], our STT-RAM architecture bypasses the RB and Tag-Cache for writebacks. Further, we do not insert lines into the LDC for writes and writebacks. 4 EVALUATION This section gives a brief overview of the simulator infrastructure that we used for evaluation and describes a set of benchmarks. It also presents qualitative and quantitative comparisons to state-ofthe-art approaches. 4.1 Experimental Setup We evaluate our STT-RAM LLC architecture using the Zesto X86 simulator [28]. Zesto provides detailed cycle accurate models of the core mirco-architecture and of the cache hierarchy. For our benchmarks, we model an 8-core system where each core runs a single application from the SPEC2006 benchmark suite [2, 15]. We simulate a total of 6 application mixes as shown in Table 2. The parameters of the system configuration used for simulation are listed in Table 3. We extensively modified the DDR memory model of Zesto to reflect the distinct characteristics of STT-RAM similar to the work in [13, 23]. Most importantly, we model the non-volatility and high write latency of STT-RAM. The modified
8 MEMSYS 17, October 2 5, 2017, Washington DC, USA Table 2: SPEC2006 application mixes used as benchmarks for evaluation. Values in parenthesis denote the number of instances used for that particular application. Mix 01 Mix 02 Mix 03 Mix 04 Mix 05 Mix 06 astar.t, bzip, leslie3d.r, libquantum, omnetpp, milc, soplex.r, leslie3d.t astar.t(2), leslie3d.r(2), libquantum(2), mcf, astar.b bzip(2), leslie3d.t(2), milc, omnetpp, soplex.r, astar.b astar.t, leslie3d.r, milc, omnetpp(2), soplex.r(2), leslie3d.t bzip, leslie3d.r(2), astar.t, mcf, milc(2), libquantum soplex.r, astar.b, omnetpp(2), libquantum, leslie3d.t(2), bzip Table 3: Configuration details as used in the experiments Core Private L1 Private L2 Shared L3 Shared LLC (DRAM or STT-RAM) t W R 3.2 GHz, out-of-order, 4-issue 32 kb, 8-way associativity, 2 cycles latency 512 kb, 8-way associativity, 5 cycles latency 8 MB, 8-way associativity, 20 cycles latency 4 channels, 2 kb RB, 256 MB, 64 banks, 256-bit channel width, 2 cycle bus latency, t RCD -t RP -t CAS = (cycles) 18 and 38 cycles for DRAM and STT-RAM Tag-Cache 27 kb, 2 cycle latency [10, 11, 16] Miss Predictor Main Memory (DRAM) Map-I [31], 256 entries 2 channels, 16 kb row buffer, 64-bit channel width, 800 MHz bus frequency, tras-trcd-trp-tcastwr = (cycles) STT-RAM LLC model considers bus contention, queuing delays, as well as bank and row buffer conflicts. We extracted the energy values of various micro-architectural structures using NVSIM [5] and Cacti [30, 37] and configured Zesto accordingly. Table 4 shows the energy values for various operations. These values, include the energy consumed by, e.g., row and column decoders, sense amplifiers, multiplexers, write drivers, and read latches. For evaluation, we compare the following LLC configurations: DRAM-Base DRAM LLC without any optimizations [9, 10]. STT-Base STT-RAM LLC without any optimizations. STT-WP STT-RAM LLC including the state-of-the-art writeback RB bypass [13] and partial write optimizations [23] described in Section 2.3. STT-WP-SR-naive State-of-the-art STT-RAM LLC extended by our Selective Read Policy as described in Section 3.2 using existing tag read policy in [10, 11]. STT-WP-SR-TagOpt State-of-the-art STT-RAM LLC extended by our Selective Read Policy using the RB Tags Bypass Policy from Section 3.4. STT-WP-SR-TagOpt-LDC STT-WP-SR-TagOpt extended by the LLC Data Cache (LDC) from Section 3.5. Fazal Hameed, Christian Menard, and Jeronimo Castrillon Table 4: Dynamic energy consumption of various components detailed in Table 3 Overall Normalized HM-IPC Operation DRAM Array Read/Write DRAM Precharge DRAM RB Access STT-RAM Array Read STT-RAM Array Write STT-RAM RB Access Tag-Cache Access (27.2 KB) LLC Data Cache (LDC) (34.5 KB) Energy [nj/column] 4.63 [nj/column] [nj/column] [nj/column] [nj/column] [nj/column] 0.97 [nj/access] 1.12 [nj/access] DRAM-Base STT-Base STT-WP STT-WP-SR-naive STT-WP-SR-TagOpt STT-WP-SR-TagOpt-LDC Mix_01 Mix_02 Mix_03 Mix_04 Mix_05 Mix_06 Figure 13: Measured harmonic mean instruction per cycle (HM-IPC) for the 6 application mixes and different configurations For all configurations, we make the following assumptions: (1) We use the LAMOST LLC set mapping policy [9, 10] (see Figure 2) (2) We employ a MAP-I predictor for predicting LLC cache misses as in [31] and Tag-Cache as in [10, 11, 16]. (3) We assume an LLC with 4 channels, 256 bits bus width per channel, 2 cycles bus latency, and 2kB RB size. (4) We assume that writes to the STT-RAM array incur 20 cycles extra latency compared to a DRAM array. We assume t W R (write recovery time) to be 18 cycles for DRAM and 38 cycles for STT-RAM. (5) We employ the Simpoint tool [14] to choose the region of interest (ROI) for each benchmark in the application mix. (6) We use FR-FCFS (First Ready First Come First Serve) access scheduling [32] for the LLC. 4.2 Performance and Energy Measurements Figure 13 shows the performance results for all evaluated configurations normalized to DRAM-Base configuration. As depicted, our STT-WP-SR-TagOpt-LDC configuration improves the average performance by 1.4%, 5.6%, and 1.3% compared to DRAM-Base, STT-Base, and STT-WP configurations, respectively. The energy benefits of the STT-WP-SR-TagOpt-LDC configuration can be observed in Figure 14. As shown, the average energy consumption is reduced by 90.6% compared to DRAM-base and 91.2% compared to STT-Base. While the writeback RB bypass policy proposed in [13] already saves a large amount of energy, our
9 Efficient STT-RAM Last-Level-Cache Architecture to replace DRAM Cache MEMSYS 17, October 2 5, 2017, Washington DC, USA LLC Dynamic Energy Consumption DRAM-Ref DRAM-Non-Ref STT-Energy LLC Dynamic Energy Consumption 100% 80% 60% 40% 20% STT-Array-Write-Energy STT-Array-Read-Energy STT-RB-Energy Overheads 0% STT-WP STT-WP-SR-naive STT-WP-SR-TagOpt STT-WP-SR-TagOpt-LDC Figure 14: Average LLC dynamic energy consumption for various configurations normalized to DRAM-Base configuration [9, 10] Figure 16: Average LLC dynamic energy consumption of various configurations. Values are normalized to the STT-WP configuration for reference. Overheads include the energy consumed by the Tag-Cache and the LDC LLC RB hit rate 60% 50% 40% 30% 20% 10% 0% DRAM-Base STT-Base STT-WP Mix_01 Mix_02 Mix_03 Mix_04 Mix_05 Mix_06 Average Figure 15: LLC RB hit rate for various configurations Selective Read Policy further reduces this energy consumption by 72.2% by eliminating unnecessary STT-RAM reads. In the following, we compare the various configurations in more detail. Comparing DRAM-Base and STT-Base. Simply replacing the DRAM arrays by STT-RAM arrays does not provide any benefits in performance or energy consumption. On the contrary, we observe an average performance degradation of 4.3% and a 6.1% increased energy consumption for STT-RAM compared to DRAM. This is mostly due to the high latency and energy consumption of write operations in STT-RAM. However, due to the decoupled organization of STT-RAM, our optimizations can reduce the number of write operations in an STT-RAM LLC and significantly decrease the energy consumption. This is illustrated in the following. Comparing STT-Base and STT-WP. Applying the writeback RB bypass policy [13], significantly improves the performance and energy consumption of an STT-RAM LLC. In the STT-Base configuration, a writeback always overwrites the RB, which might cause eviction of highly-reused rows. The writeback row, however, is unlikely to be reused on a subsequent access. Bypassing the RB for writeback operations, increases the RB hit rate from 32.2% to 39.5% as illustrated in Figure 15. This improves the performance by 4.8% on average for our application mixes. In addition to the writeback RB bypass policy, the STT-WP configuration also applies the partial write optimization [23]. As a consequence of both optimizations, the LLC dynamic energy consumption is reduced by 69.2% compared to the STT-Base configuration. Impact of the Selective Read Policy. Although the STT-WP configuration is more energy efficient than the STT-Base configuration, it still incurs an unnecessarily high energy consumption by reading unneeded lines from the STT-RAM array to the RB. Applying our Selective Read Policy (see Section 3.2) further reduces the energy consumption by 72.2% compared to the STT-WP configuration. Figure 16 illustrates the energy improvement of configurations that use the Selective Read Policy. However, the Selective Read Policy degrade the performance by an average of 3.6% compared to the STT-WP configuration (see Figure 13) due to an increased RB and Tag-Cache miss latency (see Figure 9a). Impact of the RB Tags Bypass Policy. Since the Selective Read Policy suffers from an increased RB and Tag-Cache miss latency, it has a limited performance. We proposed the RB Tags Bypass Policy (Section 3.4), which bypasses the RB for tag access, to overcome this limitation. As shown in Figure 9, this optimization reduces the latency from 84 to 66 cycles. Furthermore, the RB Tags Bypass Policy reduces the energy consumption, as it avoids duplicate storage of tags. As a result, the STT-WP-SR-TagOpt configuration improves the average performance by 2.9% and reduces the LLC dynamic energy consumption 14.7% compared to the STT-WP-SR-naive configuration. Impact of the LDC. The STT-WP-SR-TagOpt configuration improves performance compared to the STT-WP-SR-naive configuration. However, it still degrades the performance by 0.8% on average compared to the state-of-the-art STT-WP configuration. To further improve the performance, we proposed a small structure called LDC Data Cache (LDC) (see Section 3.5). The inclusion of LDC improves the performance by 1.3% and 2% compared to the STT- WP and STT-WR-SR-TagOpt configurations. The proposed LDC accelerates access latency to cache lines as an STT-RAM read can be avoided when the line is present in the LDC. As illustrated in Figure 17, the LLC hit for a read request is 47.5% on average for all application mixes. On the downside, the STT-WP-SR-TagOpt-LDC configuration increases LLC dynamic energy consumption by 4.3% compared to the STT-WP-SR-TagOpt configuration due to reading extra columns from the STT-RAM array.
10 MEMSYS 17, October 2 5, 2017, Washington DC, USA Fazal Hameed, Christian Menard, and Jeronimo Castrillon LDC hit rate for a read request that hit in LLC 60% 50% 40% 30% 20% 10% 0% Mix_01 Mix_02 Mix_03 Mix_04 Mix_05 Mix_06 Figure 17: LDC hit rate for a read request that hits in LLC 5 RELATED WORK Existing LLC architectures (mostly DRAM-based) can be catergorized into block-based and page-based designs. Block-based LLCs [9 11, 16, 25, 27, 31, 33, 34] use a small line size (i.e. 64 byte) while page-based LLCs [17 20, 40] use a large line size (i.e. 1KB/2KB). The advantage of page-based designs is that they leverage the spatial locality of applications by storing entire pages in the LLC. However, the large page size has a high price. The excessive prefetching leads to a high usage of memory bandwidth which makes it unsuitable for multi-core system running diverse applications. Another drawback of page-based LLC is that not all blocks within the large page are accessed prior to page evictions, which may exacerbate the performance. In contrast to page-based LLCs, we employ a block-based LLC to mitigate the excessive memory bandwidth utilization problem. The large memory requirements of new applications have forced the industry to increase the LLC size. For instance, IBM POWER7 processor [3, 39] employs a 32 MB DRAM LLC. The DRAM based LLC architectures [9 11, 16 20, 25, 27, 31, 33, 34, 40] consume a significant portion of chip power budget due to high leakage and refresh energy which increases with the LLC size. To mitigate the power scalability of DRAM, recently STT-RAM LLC architecture [13] have been proposed as a promising alternative to DRAM LLC. Independent of the LLC architecture (i.e. block-based or page based; DRAM based or STT-RAM based), all of the above mentioned studies always fetch the content of an entire row into the row buffer after a row buffer miss. This leads to an unnecessarily high energy consumption, since most of the columns will not be used. Our proposal is unique in that it only fetches those lines into the row buffer which are likely to be accessed later. Many architectural techniques have been presented for energy and performance trade-offs in STT-RAM caches [21, 35, 36]. They relax the non-volatility of STT-RAM by tuning the MTJ volume to improve its write latency and energy requirements at the cost of additional refresh overheads. However, these techniques are not suitable for larger STT-RAM due to high energy requirements for refreshing MTJ cells periodically. In contrast, our proposal exploits the non-volatility characteristics of STT-RAM. Other circuit level energy and latency reduction techniques that exploit heterogeneity in the switching time of the STT-RAM bit Avg cell have been introduced in [4, 42]. However, these circuit level techniques are orthogonal to our work and can be combined with our proposal in order to further improve performance and energy efficiency of STT-RAM LLC. 6 CONCLUSIONS This paper presents novel policies to improve the performance and energy efficiency in STT-RAM LLC architectures. We demonstrate that existing LLC architectures unnecessarily fetch large amounts of data into the row buffer while the majority of the data is not reused. Our Selective Read Policy exploits this fact to reduces the energy consumption by decreasing the number of STT-RAM reads. While this introduces a latency penalty, we decrease the access latency by a new Row Buffer Tags Bypass Policy optimization. Finally, the LLC Data Cache (LDC) organization is proposed to improve the performance by further reducing the access latency. Our results on SPEC 2006 benchmarks show that our synergestic policies are effective in improving the average performance (1.3% and 1.4%) and energy consumption (90.6% and 72.6%) compared to the state state-of-the-art proposal for DRAM and STT-RAM LLC. With these optimizations STT-RAM becomes an effective Last-Level-Cache alternative to DRAM. ACKNOLEDGMENTS This work was partly supported by the German Research Foundation (DFG) within the Cluster of Excellence Center for Advancing Electronics Dresden (cfaed). REFERENCES [1] Hybrid Memory Cube Consortium: Hybrid Memory Cube Specification. (2013). [2] Standard Performance Evaluation Corporation. (2017). [Online; accessed 10-March-2017]. [3] R. X. Arroyo, R. J. Harrington, S. P. Hartman, and T. Nguyen IBM POWER7 Systems. IBM Journal of Research and Development 55, 3 (2011), 2:1 2:13. [4] R. Bishnoi, F. Oboril, M. Ebrahimi, and M.B. Tahoori Avoiding Unnecessary Write Operations in STT-MRAM for Low Power Implementation. In Proceedings of the 15th International Symposium on Quality Electronic Design (ISQED 14) [5] X. Dong, C. Xu, Y. Xie, and N.P. Jouppi NVSim: A Circuit-Level Performance, Energy, and Area Model for Emerging Nonvolatile Memory. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems 31, 7 (July 2012), [6] Darryl Gove CPU2006 Working Set Size. SIGARCH Computer Architecture News 35, 1 (March 2007), [7] Fazal Hameed, L. Bauer, and J. Henkel Adaptive Cache Management for a Combined SRAM and DRAM Cache Hierarchy for Multi-Cores. In Proceedings of the 15th conference on Design, Automation and Test in Europe (DATE) [8] Fazal Hameed, L. Bauer, and J. Henkel Reducing Inter-Core Cache Contention with an Adaptive Bank Mapping Policy in DRAM Cache. In IEEE International Conference on Hardware/Software Codesign and System Synthesis (CODES+ISSS 13). [9] Fazal Hameed, L. Bauer, and J. Henkel Simultaneously Optimizing DRAM Cache Hit Latency and Miss Rate via Novel Set Mapping Policies. In International Conference on Compilers, Architecture, and Synthesis for Embedded Systems (CASES 13). [10] Fazal Hameed, L. Bauer, and J. Henkel Reducing Latency in an SRAM/DRAM Cache Hierarchy via a Novel Tag-Cache Architecture. In Proceedings of the 51st Design Automation Conference (DAC 14). [11] Fazal Hameed, L. Bauer, and J. Henkel Architecting On-Chip DRAM Cache for Simultaneous Miss Rate and Latency Reduction. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems 35, 4 (April 2016), [12] Fazal Hameed and Jeronimo Castrillon Rethinking On-chip DRAM Cache for Simultaneous Performance and Energy Optimization (to appear). In Proceedings of the 19th conference on Design, Automation and Test in Europe (DATE).
Rethinking On-chip DRAM Cache for Simultaneous Performance and Energy Optimization
 Rethinking On-chip DRAM Cache for Simultaneous Performance and Energy Optimization Fazal Hameed and Jeronimo Castrillon Center for Advancing Electronics Dresden (cfaed), Technische Universität Dresden,
Rethinking On-chip DRAM Cache for Simultaneous Performance and Energy Optimization Fazal Hameed and Jeronimo Castrillon Center for Advancing Electronics Dresden (cfaed), Technische Universität Dresden,
Evaluating STT-RAM as an Energy-Efficient Main Memory Alternative
 Evaluating STT-RAM as an Energy-Efficient Main Memory Alternative Emre Kültürsay *, Mahmut Kandemir *, Anand Sivasubramaniam *, and Onur Mutlu * Pennsylvania State University Carnegie Mellon University
Evaluating STT-RAM as an Energy-Efficient Main Memory Alternative Emre Kültürsay *, Mahmut Kandemir *, Anand Sivasubramaniam *, and Onur Mutlu * Pennsylvania State University Carnegie Mellon University
Lecture 14: Cache Innovations and DRAM. Today: cache access basics and innovations, DRAM (Sections )
 Lecture 14: Cache Innovations and DRAM Today: cache access basics and innovations, DRAM (Sections 5.1-5.3) 1 Reducing Miss Rate Large block size reduces compulsory misses, reduces miss penalty in case
Lecture 14: Cache Innovations and DRAM Today: cache access basics and innovations, DRAM (Sections 5.1-5.3) 1 Reducing Miss Rate Large block size reduces compulsory misses, reduces miss penalty in case
Multilevel Memories. Joel Emer Computer Science and Artificial Intelligence Laboratory Massachusetts Institute of Technology
 1 Multilevel Memories Computer Science and Artificial Intelligence Laboratory Massachusetts Institute of Technology Based on the material prepared by Krste Asanovic and Arvind CPU-Memory Bottleneck 6.823
1 Multilevel Memories Computer Science and Artificial Intelligence Laboratory Massachusetts Institute of Technology Based on the material prepared by Krste Asanovic and Arvind CPU-Memory Bottleneck 6.823
Chapter 5B. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5B Large and Fast: Exploiting Memory Hierarchy One Transistor Dynamic RAM 1-T DRAM Cell word access transistor V REF TiN top electrode (V REF ) Ta 2 O 5 dielectric bit Storage capacitor (FET gate,
Chapter 5B Large and Fast: Exploiting Memory Hierarchy One Transistor Dynamic RAM 1-T DRAM Cell word access transistor V REF TiN top electrode (V REF ) Ta 2 O 5 dielectric bit Storage capacitor (FET gate,
Donn Morrison Department of Computer Science. TDT4255 Memory hierarchies
 TDT4255 Lecture 10: Memory hierarchies Donn Morrison Department of Computer Science 2 Outline Chapter 5 - Memory hierarchies (5.1-5.5) Temporal and spacial locality Hits and misses Direct-mapped, set associative,
TDT4255 Lecture 10: Memory hierarchies Donn Morrison Department of Computer Science 2 Outline Chapter 5 - Memory hierarchies (5.1-5.5) Temporal and spacial locality Hits and misses Direct-mapped, set associative,
Lecture-14 (Memory Hierarchy) CS422-Spring
 Lecture-14 (Memory Hierarchy) CS422-Spring 2018 Biswa@CSE-IITK The Ideal World Instruction Supply Pipeline (Instruction execution) Data Supply - Zero-cycle latency - Infinite capacity - Zero cost - Perfect
Lecture-14 (Memory Hierarchy) CS422-Spring 2018 Biswa@CSE-IITK The Ideal World Instruction Supply Pipeline (Instruction execution) Data Supply - Zero-cycle latency - Infinite capacity - Zero cost - Perfect
Couture: Tailoring STT-MRAM for Persistent Main Memory. Mustafa M Shihab Jie Zhang Shuwen Gao Joseph Callenes-Sloan Myoungsoo Jung
 Couture: Tailoring STT-MRAM for Persistent Main Memory Mustafa M Shihab Jie Zhang Shuwen Gao Joseph Callenes-Sloan Myoungsoo Jung Executive Summary Motivation: DRAM plays an instrumental role in modern
Couture: Tailoring STT-MRAM for Persistent Main Memory Mustafa M Shihab Jie Zhang Shuwen Gao Joseph Callenes-Sloan Myoungsoo Jung Executive Summary Motivation: DRAM plays an instrumental role in modern
Introduction to memory system :from device to system
 Introduction to memory system :from device to system Jianhui Yue Electrical and Computer Engineering University of Maine The Position of DRAM in the Computer 2 The Complexity of Memory 3 Question Assume
Introduction to memory system :from device to system Jianhui Yue Electrical and Computer Engineering University of Maine The Position of DRAM in the Computer 2 The Complexity of Memory 3 Question Assume
Evalua&ng STT- RAM as an Energy- Efficient Main Memory Alterna&ve
 Evalua&ng STT- RAM as an Energy- Efficient Main Memory Alterna&ve Emre Kültürsay *, Mahmut Kandemir *, Anand Sivasubramaniam *, and Onur Mutlu * Pennsylvania State University Carnegie Mellon University
Evalua&ng STT- RAM as an Energy- Efficient Main Memory Alterna&ve Emre Kültürsay *, Mahmut Kandemir *, Anand Sivasubramaniam *, and Onur Mutlu * Pennsylvania State University Carnegie Mellon University
EFFICIENTLY ENABLING CONVENTIONAL BLOCK SIZES FOR VERY LARGE DIE- STACKED DRAM CACHES
 EFFICIENTLY ENABLING CONVENTIONAL BLOCK SIZES FOR VERY LARGE DIE- STACKED DRAM CACHES MICRO 2011 @ Porte Alegre, Brazil Gabriel H. Loh [1] and Mark D. Hill [2][1] December 2011 [1] AMD Research [2] University
EFFICIENTLY ENABLING CONVENTIONAL BLOCK SIZES FOR VERY LARGE DIE- STACKED DRAM CACHES MICRO 2011 @ Porte Alegre, Brazil Gabriel H. Loh [1] and Mark D. Hill [2][1] December 2011 [1] AMD Research [2] University
A Comprehensive Analytical Performance Model of DRAM Caches
 A Comprehensive Analytical Performance Model of DRAM Caches Authors: Nagendra Gulur *, Mahesh Mehendale *, and R Govindarajan + Presented by: Sreepathi Pai * Texas Instruments, + Indian Institute of Science
A Comprehensive Analytical Performance Model of DRAM Caches Authors: Nagendra Gulur *, Mahesh Mehendale *, and R Govindarajan + Presented by: Sreepathi Pai * Texas Instruments, + Indian Institute of Science
OAP: An Obstruction-Aware Cache Management Policy for STT-RAM Last-Level Caches
 OAP: An Obstruction-Aware Cache Management Policy for STT-RAM Last-Level Caches Jue Wang, Xiangyu Dong, Yuan Xie Department of Computer Science and Engineering, Pennsylvania State University Qualcomm Technology,
OAP: An Obstruction-Aware Cache Management Policy for STT-RAM Last-Level Caches Jue Wang, Xiangyu Dong, Yuan Xie Department of Computer Science and Engineering, Pennsylvania State University Qualcomm Technology,
Unleashing the Power of Embedded DRAM
 Copyright 2005 Design And Reuse S.A. All rights reserved. Unleashing the Power of Embedded DRAM by Peter Gillingham, MOSAID Technologies Incorporated Ottawa, Canada Abstract Embedded DRAM technology offers
Copyright 2005 Design And Reuse S.A. All rights reserved. Unleashing the Power of Embedded DRAM by Peter Gillingham, MOSAID Technologies Incorporated Ottawa, Canada Abstract Embedded DRAM technology offers
ELEC 5200/6200 Computer Architecture and Design Spring 2017 Lecture 7: Memory Organization Part II
 ELEC 5200/6200 Computer Architecture and Design Spring 2017 Lecture 7: Organization Part II Ujjwal Guin, Assistant Professor Department of Electrical and Computer Engineering Auburn University, Auburn,
ELEC 5200/6200 Computer Architecture and Design Spring 2017 Lecture 7: Organization Part II Ujjwal Guin, Assistant Professor Department of Electrical and Computer Engineering Auburn University, Auburn,
Performance and Power Solutions for Caches Using 8T SRAM Cells
 Performance and Power Solutions for Caches Using 8T SRAM Cells Mostafa Farahani Amirali Baniasadi Department of Electrical and Computer Engineering University of Victoria, BC, Canada {mostafa, amirali}@ece.uvic.ca
Performance and Power Solutions for Caches Using 8T SRAM Cells Mostafa Farahani Amirali Baniasadi Department of Electrical and Computer Engineering University of Victoria, BC, Canada {mostafa, amirali}@ece.uvic.ca
The University of Adelaide, School of Computer Science 13 September 2018
 Computer Architecture A Quantitative Approach, Sixth Edition Chapter 2 Memory Hierarchy Design 1 Programmers want unlimited amounts of memory with low latency Fast memory technology is more expensive per
Computer Architecture A Quantitative Approach, Sixth Edition Chapter 2 Memory Hierarchy Design 1 Programmers want unlimited amounts of memory with low latency Fast memory technology is more expensive per
The Memory Hierarchy & Cache Review of Memory Hierarchy & Cache Basics (from 350):
 The Memory Hierarchy & Cache Review of Memory Hierarchy & Cache Basics (from 350): Motivation for The Memory Hierarchy: { CPU/Memory Performance Gap The Principle Of Locality Cache $$$$$ Cache Basics:
The Memory Hierarchy & Cache Review of Memory Hierarchy & Cache Basics (from 350): Motivation for The Memory Hierarchy: { CPU/Memory Performance Gap The Principle Of Locality Cache $$$$$ Cache Basics:
DASCA: Dead Write Prediction Assisted STT-RAM Cache Architecture
 DASCA: Dead Write Prediction Assisted STT-RAM Cache Architecture Junwhan Ahn *, Sungjoo Yoo, and Kiyoung Choi * junwhan@snu.ac.kr, sungjoo.yoo@postech.ac.kr, kchoi@snu.ac.kr * Department of Electrical
DASCA: Dead Write Prediction Assisted STT-RAM Cache Architecture Junwhan Ahn *, Sungjoo Yoo, and Kiyoung Choi * junwhan@snu.ac.kr, sungjoo.yoo@postech.ac.kr, kchoi@snu.ac.kr * Department of Electrical
Reducing DRAM Latency at Low Cost by Exploiting Heterogeneity. Donghyuk Lee Carnegie Mellon University
 Reducing DRAM Latency at Low Cost by Exploiting Heterogeneity Donghyuk Lee Carnegie Mellon University Problem: High DRAM Latency processor stalls: waiting for data main memory high latency Major bottleneck
Reducing DRAM Latency at Low Cost by Exploiting Heterogeneity Donghyuk Lee Carnegie Mellon University Problem: High DRAM Latency processor stalls: waiting for data main memory high latency Major bottleneck
EE414 Embedded Systems Ch 5. Memory Part 2/2
 EE414 Embedded Systems Ch 5. Memory Part 2/2 Byung Kook Kim School of Electrical Engineering Korea Advanced Institute of Science and Technology Overview 6.1 introduction 6.2 Memory Write Ability and Storage
EE414 Embedded Systems Ch 5. Memory Part 2/2 Byung Kook Kim School of Electrical Engineering Korea Advanced Institute of Science and Technology Overview 6.1 introduction 6.2 Memory Write Ability and Storage
2 Improved Direct-Mapped Cache Performance by the Addition of a Small Fully-Associative Cache and Prefetch Buffers [1]
![2 Improved Direct-Mapped Cache Performance by the Addition of a Small Fully-Associative Cache and Prefetch Buffers [1] 2 Improved Direct-Mapped Cache Performance by the Addition of a Small Fully-Associative Cache and Prefetch Buffers [1]](/thumbs/73/69207197.jpg) EE482: Advanced Computer Organization Lecture #7 Processor Architecture Stanford University Tuesday, June 6, 2000 Memory Systems and Memory Latency Lecture #7: Wednesday, April 19, 2000 Lecturer: Brian
EE482: Advanced Computer Organization Lecture #7 Processor Architecture Stanford University Tuesday, June 6, 2000 Memory Systems and Memory Latency Lecture #7: Wednesday, April 19, 2000 Lecturer: Brian
Lecture 8: Virtual Memory. Today: DRAM innovations, virtual memory (Sections )
 Lecture 8: Virtual Memory Today: DRAM innovations, virtual memory (Sections 5.3-5.4) 1 DRAM Technology Trends Improvements in technology (smaller devices) DRAM capacities double every two years, but latency
Lecture 8: Virtual Memory Today: DRAM innovations, virtual memory (Sections 5.3-5.4) 1 DRAM Technology Trends Improvements in technology (smaller devices) DRAM capacities double every two years, but latency
CSE 431 Computer Architecture Fall Chapter 5A: Exploiting the Memory Hierarchy, Part 1
 CSE 431 Computer Architecture Fall 2008 Chapter 5A: Exploiting the Memory Hierarchy, Part 1 Mary Jane Irwin ( www.cse.psu.edu/~mji ) [Adapted from Computer Organization and Design, 4 th Edition, Patterson
CSE 431 Computer Architecture Fall 2008 Chapter 5A: Exploiting the Memory Hierarchy, Part 1 Mary Jane Irwin ( www.cse.psu.edu/~mji ) [Adapted from Computer Organization and Design, 4 th Edition, Patterson
Chapter 5 Large and Fast: Exploiting Memory Hierarchy (Part 1)
 Department of Electr rical Eng ineering, Chapter 5 Large and Fast: Exploiting Memory Hierarchy (Part 1) 王振傑 (Chen-Chieh Wang) ccwang@mail.ee.ncku.edu.tw ncku edu Depar rtment of Electr rical Engineering,
Department of Electr rical Eng ineering, Chapter 5 Large and Fast: Exploiting Memory Hierarchy (Part 1) 王振傑 (Chen-Chieh Wang) ccwang@mail.ee.ncku.edu.tw ncku edu Depar rtment of Electr rical Engineering,
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address space at any time Temporal locality Items accessed recently are likely to
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address space at any time Temporal locality Items accessed recently are likely to
ELEC-H-473 Microprocessor architecture Caches
 ELEC-H-473 Microprocessor architecture Caches Lecture 05 Dragomir MILOJEVIC dragomir.milojevic@ulb.ac.be 2013 Previously on ELEC-H-473 Reasons that cause pipeline inefficiency : Variance in execution time
ELEC-H-473 Microprocessor architecture Caches Lecture 05 Dragomir MILOJEVIC dragomir.milojevic@ulb.ac.be 2013 Previously on ELEC-H-473 Reasons that cause pipeline inefficiency : Variance in execution time
Tiered-Latency DRAM: A Low Latency and A Low Cost DRAM Architecture
 Tiered-Latency DRAM: A Low Latency and A Low Cost DRAM Architecture Donghyuk Lee, Yoongu Kim, Vivek Seshadri, Jamie Liu, Lavanya Subramanian, Onur Mutlu Carnegie Mellon University HPCA - 2013 Executive
Tiered-Latency DRAM: A Low Latency and A Low Cost DRAM Architecture Donghyuk Lee, Yoongu Kim, Vivek Seshadri, Jamie Liu, Lavanya Subramanian, Onur Mutlu Carnegie Mellon University HPCA - 2013 Executive
Balancing DRAM Locality and Parallelism in Shared Memory CMP Systems
 Balancing DRAM Locality and Parallelism in Shared Memory CMP Systems Min Kyu Jeong, Doe Hyun Yoon^, Dam Sunwoo*, Michael Sullivan, Ikhwan Lee, and Mattan Erez The University of Texas at Austin Hewlett-Packard
Balancing DRAM Locality and Parallelism in Shared Memory CMP Systems Min Kyu Jeong, Doe Hyun Yoon^, Dam Sunwoo*, Michael Sullivan, Ikhwan Lee, and Mattan Erez The University of Texas at Austin Hewlett-Packard
Memory. Lecture 22 CS301
 Memory Lecture 22 CS301 Administrative Daily Review of today s lecture w Due tomorrow (11/13) at 8am HW #8 due today at 5pm Program #2 due Friday, 11/16 at 11:59pm Test #2 Wednesday Pipelined Machine Fetch
Memory Lecture 22 CS301 Administrative Daily Review of today s lecture w Due tomorrow (11/13) at 8am HW #8 due today at 5pm Program #2 due Friday, 11/16 at 11:59pm Test #2 Wednesday Pipelined Machine Fetch
Mohsen Imani. University of California San Diego. System Energy Efficiency Lab seelab.ucsd.edu
 Mohsen Imani University of California San Diego Winter 2016 Technology Trend for IoT http://www.flashmemorysummit.com/english/collaterals/proceedi ngs/2014/20140807_304c_hill.pdf 2 Motivation IoT significantly
Mohsen Imani University of California San Diego Winter 2016 Technology Trend for IoT http://www.flashmemorysummit.com/english/collaterals/proceedi ngs/2014/20140807_304c_hill.pdf 2 Motivation IoT significantly
15-740/ Computer Architecture Lecture 19: Main Memory. Prof. Onur Mutlu Carnegie Mellon University
 15-740/18-740 Computer Architecture Lecture 19: Main Memory Prof. Onur Mutlu Carnegie Mellon University Last Time Multi-core issues in caching OS-based cache partitioning (using page coloring) Handling
15-740/18-740 Computer Architecture Lecture 19: Main Memory Prof. Onur Mutlu Carnegie Mellon University Last Time Multi-core issues in caching OS-based cache partitioning (using page coloring) Handling
Chapter 2: Memory Hierarchy Design Part 2
 Chapter 2: Memory Hierarchy Design Part 2 Introduction (Section 2.1, Appendix B) Caches Review of basics (Section 2.1, Appendix B) Advanced methods (Section 2.3) Main Memory Virtual Memory Fundamental
Chapter 2: Memory Hierarchy Design Part 2 Introduction (Section 2.1, Appendix B) Caches Review of basics (Section 2.1, Appendix B) Advanced methods (Section 2.3) Main Memory Virtual Memory Fundamental
CS356: Discussion #9 Memory Hierarchy and Caches. Marco Paolieri Illustrations from CS:APP3e textbook
 CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
Architectural Aspects in Design and Analysis of SOTbased
 Architectural Aspects in Design and Analysis of SOTbased Memories Rajendra Bishnoi, Mojtaba Ebrahimi, Fabian Oboril & Mehdi Tahoori INSTITUTE OF COMPUTER ENGINEERING (ITEC) CHAIR FOR DEPENDABLE NANO COMPUTING
Architectural Aspects in Design and Analysis of SOTbased Memories Rajendra Bishnoi, Mojtaba Ebrahimi, Fabian Oboril & Mehdi Tahoori INSTITUTE OF COMPUTER ENGINEERING (ITEC) CHAIR FOR DEPENDABLE NANO COMPUTING
Chapter 2: Memory Hierarchy Design Part 2
 Chapter 2: Memory Hierarchy Design Part 2 Introduction (Section 2.1, Appendix B) Caches Review of basics (Section 2.1, Appendix B) Advanced methods (Section 2.3) Main Memory Virtual Memory Fundamental
Chapter 2: Memory Hierarchy Design Part 2 Introduction (Section 2.1, Appendix B) Caches Review of basics (Section 2.1, Appendix B) Advanced methods (Section 2.3) Main Memory Virtual Memory Fundamental
The Memory Hierarchy & Cache
 Removing The Ideal Memory Assumption: The Memory Hierarchy & Cache The impact of real memory on CPU Performance. Main memory basic properties: Memory Types: DRAM vs. SRAM The Motivation for The Memory
Removing The Ideal Memory Assumption: The Memory Hierarchy & Cache The impact of real memory on CPU Performance. Main memory basic properties: Memory Types: DRAM vs. SRAM The Motivation for The Memory
A Brief Compendium of On Chip Memory Highlighting the Tradeoffs Implementing SRAM,
 A Brief Compendium of On Chip Memory Highlighting the Tradeoffs Implementing, RAM, or edram Justin Bates Department of Electrical and Computer Engineering University of Central Florida Orlando, FL 3816-36
A Brief Compendium of On Chip Memory Highlighting the Tradeoffs Implementing, RAM, or edram Justin Bates Department of Electrical and Computer Engineering University of Central Florida Orlando, FL 3816-36
Memory Hierarchy and Caches
 Memory Hierarchy and Caches COE 301 / ICS 233 Computer Organization Dr. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
Memory Hierarchy and Caches COE 301 / ICS 233 Computer Organization Dr. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
CS698Y: Modern Memory Systems Lecture-16 (DRAM Timing Constraints) Biswabandan Panda
 CS698Y: Modern Memory Systems Lecture-16 (DRAM Timing Constraints) Biswabandan Panda biswap@cse.iitk.ac.in https://www.cse.iitk.ac.in/users/biswap/cs698y.html Row decoder Accessing a Row Access Address
CS698Y: Modern Memory Systems Lecture-16 (DRAM Timing Constraints) Biswabandan Panda biswap@cse.iitk.ac.in https://www.cse.iitk.ac.in/users/biswap/cs698y.html Row decoder Accessing a Row Access Address
Revolutionizing Technological Devices such as STT- RAM and their Multiple Implementation in the Cache Level Hierarchy
 Revolutionizing Technological s such as and their Multiple Implementation in the Cache Level Hierarchy Michael Mosquera Department of Electrical and Computer Engineering University of Central Florida Orlando,
Revolutionizing Technological s such as and their Multiple Implementation in the Cache Level Hierarchy Michael Mosquera Department of Electrical and Computer Engineering University of Central Florida Orlando,
Lecture notes for CS Chapter 2, part 1 10/23/18
 Chapter 2: Memory Hierarchy Design Part 2 Introduction (Section 2.1, Appendix B) Caches Review of basics (Section 2.1, Appendix B) Advanced methods (Section 2.3) Main Memory Virtual Memory Fundamental
Chapter 2: Memory Hierarchy Design Part 2 Introduction (Section 2.1, Appendix B) Caches Review of basics (Section 2.1, Appendix B) Advanced methods (Section 2.3) Main Memory Virtual Memory Fundamental
Embedded Systems Design: A Unified Hardware/Software Introduction. Outline. Chapter 5 Memory. Introduction. Memory: basic concepts
 Hardware/Software Introduction Chapter 5 Memory Outline Memory Write Ability and Storage Permanence Common Memory Types Composing Memory Memory Hierarchy and Cache Advanced RAM 1 2 Introduction Memory:
Hardware/Software Introduction Chapter 5 Memory Outline Memory Write Ability and Storage Permanence Common Memory Types Composing Memory Memory Hierarchy and Cache Advanced RAM 1 2 Introduction Memory:
Embedded Systems Design: A Unified Hardware/Software Introduction. Chapter 5 Memory. Outline. Introduction
 Hardware/Software Introduction Chapter 5 Memory 1 Outline Memory Write Ability and Storage Permanence Common Memory Types Composing Memory Memory Hierarchy and Cache Advanced RAM 2 Introduction Embedded
Hardware/Software Introduction Chapter 5 Memory 1 Outline Memory Write Ability and Storage Permanence Common Memory Types Composing Memory Memory Hierarchy and Cache Advanced RAM 2 Introduction Embedded
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface. 5 th. Edition. Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
CS 152 Computer Architecture and Engineering. Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste
a) Memory management unit b) CPU c) PCI d) None of the mentioned
 1. CPU fetches the instruction from memory according to the value of a) program counter b) status register c) instruction register d) program status word 2. Which one of the following is the address generated
1. CPU fetches the instruction from memory according to the value of a) program counter b) status register c) instruction register d) program status word 2. Which one of the following is the address generated
ECE 485/585 Microprocessor System Design
 Microprocessor System Design Lecture 5: Zeshan Chishti DRAM Basics DRAM Evolution SDRAM-based Memory Systems Electrical and Computer Engineering Dept. Maseeh College of Engineering and Computer Science
Microprocessor System Design Lecture 5: Zeshan Chishti DRAM Basics DRAM Evolution SDRAM-based Memory Systems Electrical and Computer Engineering Dept. Maseeh College of Engineering and Computer Science
18-447: Computer Architecture Lecture 25: Main Memory. Prof. Onur Mutlu Carnegie Mellon University Spring 2013, 4/3/2013
 18-447: Computer Architecture Lecture 25: Main Memory Prof. Onur Mutlu Carnegie Mellon University Spring 2013, 4/3/2013 Reminder: Homework 5 (Today) Due April 3 (Wednesday!) Topics: Vector processing,
18-447: Computer Architecture Lecture 25: Main Memory Prof. Onur Mutlu Carnegie Mellon University Spring 2013, 4/3/2013 Reminder: Homework 5 (Today) Due April 3 (Wednesday!) Topics: Vector processing,
Chapter 5A. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5A Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) Fast, expensive Dynamic RAM (DRAM) In between Magnetic disk Slow, inexpensive Ideal memory Access time of SRAM
Chapter 5A Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) Fast, expensive Dynamic RAM (DRAM) In between Magnetic disk Slow, inexpensive Ideal memory Access time of SRAM
Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
COMPUTER ARCHITECTURES
 COMPUTER ARCHITECTURES Random Access Memory Technologies Gábor Horváth BUTE Department of Networked Systems and Services ghorvath@hit.bme.hu Budapest, 2019. 02. 24. Department of Networked Systems and
COMPUTER ARCHITECTURES Random Access Memory Technologies Gábor Horváth BUTE Department of Networked Systems and Services ghorvath@hit.bme.hu Budapest, 2019. 02. 24. Department of Networked Systems and
Computer Architecture. Memory Hierarchy. Lynn Choi Korea University
 Computer Architecture Memory Hierarchy Lynn Choi Korea University Memory Hierarchy Motivated by Principles of Locality Speed vs. Size vs. Cost tradeoff Locality principle Temporal Locality: reference to
Computer Architecture Memory Hierarchy Lynn Choi Korea University Memory Hierarchy Motivated by Principles of Locality Speed vs. Size vs. Cost tradeoff Locality principle Temporal Locality: reference to
registers data 1 registers MEMORY ADDRESS on-chip cache off-chip cache main memory: real address space part of virtual addr. sp.
 13 1 CMPE110 Computer Architecture, Winter 2009 Andrea Di Blas 110 Winter 2009 CMPE Cache Direct-mapped cache Reads and writes Cache associativity Cache and performance Textbook Edition: 7.1 to 7.3 Third
13 1 CMPE110 Computer Architecture, Winter 2009 Andrea Di Blas 110 Winter 2009 CMPE Cache Direct-mapped cache Reads and writes Cache associativity Cache and performance Textbook Edition: 7.1 to 7.3 Third
EC 513 Computer Architecture
 EC 513 Computer Architecture Cache Organization Prof. Michel A. Kinsy The course has 4 modules Module 1 Instruction Set Architecture (ISA) Simple Pipelining and Hazards Module 2 Superscalar Architectures
EC 513 Computer Architecture Cache Organization Prof. Michel A. Kinsy The course has 4 modules Module 1 Instruction Set Architecture (ISA) Simple Pipelining and Hazards Module 2 Superscalar Architectures
Chapter Seven. Large & Fast: Exploring Memory Hierarchy
 Chapter Seven Large & Fast: Exploring Memory Hierarchy 1 Memories: Review SRAM (Static Random Access Memory): value is stored on a pair of inverting gates very fast but takes up more space than DRAM DRAM
Chapter Seven Large & Fast: Exploring Memory Hierarchy 1 Memories: Review SRAM (Static Random Access Memory): value is stored on a pair of inverting gates very fast but takes up more space than DRAM DRAM
Spring 2018 :: CSE 502. Cache Design Basics. Nima Honarmand
 Cache Design Basics Nima Honarmand Storage Hierarchy Make common case fast: Common: temporal & spatial locality Fast: smaller, more expensive memory Bigger Transfers Registers More Bandwidth Controlled
Cache Design Basics Nima Honarmand Storage Hierarchy Make common case fast: Common: temporal & spatial locality Fast: smaller, more expensive memory Bigger Transfers Registers More Bandwidth Controlled
Phase Change Memory An Architecture and Systems Perspective
 Phase Change Memory An Architecture and Systems Perspective Benjamin C. Lee Stanford University bcclee@stanford.edu Fall 2010, Assistant Professor @ Duke University Benjamin C. Lee 1 Memory Scaling density,
Phase Change Memory An Architecture and Systems Perspective Benjamin C. Lee Stanford University bcclee@stanford.edu Fall 2010, Assistant Professor @ Duke University Benjamin C. Lee 1 Memory Scaling density,
ECE 152 Introduction to Computer Architecture
 Introduction to Computer Architecture Main Memory and Virtual Memory Copyright 2009 Daniel J. Sorin Duke University Slides are derived from work by Amir Roth (Penn) Spring 2009 1 Where We Are in This Course
Introduction to Computer Architecture Main Memory and Virtual Memory Copyright 2009 Daniel J. Sorin Duke University Slides are derived from work by Amir Roth (Penn) Spring 2009 1 Where We Are in This Course
Cache/Memory Optimization. - Krishna Parthaje
 Cache/Memory Optimization - Krishna Parthaje Hybrid Cache Architecture Replacing SRAM Cache with Future Memory Technology Suji Lee, Jongpil Jung, and Chong-Min Kyung Department of Electrical Engineering,KAIST
Cache/Memory Optimization - Krishna Parthaje Hybrid Cache Architecture Replacing SRAM Cache with Future Memory Technology Suji Lee, Jongpil Jung, and Chong-Min Kyung Department of Electrical Engineering,KAIST
Emerging NVM Memory Technologies
 Emerging NVM Memory Technologies Yuan Xie Associate Professor The Pennsylvania State University Department of Computer Science & Engineering www.cse.psu.edu/~yuanxie yuanxie@cse.psu.edu Position Statement
Emerging NVM Memory Technologies Yuan Xie Associate Professor The Pennsylvania State University Department of Computer Science & Engineering www.cse.psu.edu/~yuanxie yuanxie@cse.psu.edu Position Statement
CS 152 Computer Architecture and Engineering. Lecture 6 - Memory
 CS 152 Computer Architecture and Engineering Lecture 6 - Memory Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste! http://inst.eecs.berkeley.edu/~cs152!
CS 152 Computer Architecture and Engineering Lecture 6 - Memory Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste! http://inst.eecs.berkeley.edu/~cs152!
Energy-Efficient Spin-Transfer Torque RAM Cache Exploiting Additional All-Zero-Data Flags
 Energy-Efficient Spin-Transfer Torque RAM Cache Exploiting Additional All-Zero-Data Flags Jinwook Jung, Yohei Nakata, Masahiko Yoshimoto, and Hiroshi Kawaguchi Graduate School of System Informatics, Kobe
Energy-Efficient Spin-Transfer Torque RAM Cache Exploiting Additional All-Zero-Data Flags Jinwook Jung, Yohei Nakata, Masahiko Yoshimoto, and Hiroshi Kawaguchi Graduate School of System Informatics, Kobe
CS 320 February 2, 2018 Ch 5 Memory
 CS 320 February 2, 2018 Ch 5 Memory Main memory often referred to as core by the older generation because core memory was a mainstay of computers until the advent of cheap semi-conductor memory in the
CS 320 February 2, 2018 Ch 5 Memory Main memory often referred to as core by the older generation because core memory was a mainstay of computers until the advent of cheap semi-conductor memory in the
Memory Hierarchy. Slides contents from:
 Memory Hierarchy Slides contents from: Hennessy & Patterson, 5ed Appendix B and Chapter 2 David Wentzlaff, ELE 475 Computer Architecture MJT, High Performance Computing, NPTEL Memory Performance Gap Memory
Memory Hierarchy Slides contents from: Hennessy & Patterson, 5ed Appendix B and Chapter 2 David Wentzlaff, ELE 475 Computer Architecture MJT, High Performance Computing, NPTEL Memory Performance Gap Memory
AC-DIMM: Associative Computing with STT-MRAM
 AC-DIMM: Associative Computing with STT-MRAM Qing Guo, Xiaochen Guo, Ravi Patel Engin Ipek, Eby G. Friedman University of Rochester Published In: ISCA-2013 Motivation Prevalent Trends in Modern Computing:
AC-DIMM: Associative Computing with STT-MRAM Qing Guo, Xiaochen Guo, Ravi Patel Engin Ipek, Eby G. Friedman University of Rochester Published In: ISCA-2013 Motivation Prevalent Trends in Modern Computing:
ARCHITECTURAL APPROACHES TO REDUCE LEAKAGE ENERGY IN CACHES
 ARCHITECTURAL APPROACHES TO REDUCE LEAKAGE ENERGY IN CACHES Shashikiran H. Tadas & Chaitali Chakrabarti Department of Electrical Engineering Arizona State University Tempe, AZ, 85287. tadas@asu.edu, chaitali@asu.edu
ARCHITECTURAL APPROACHES TO REDUCE LEAKAGE ENERGY IN CACHES Shashikiran H. Tadas & Chaitali Chakrabarti Department of Electrical Engineering Arizona State University Tempe, AZ, 85287. tadas@asu.edu, chaitali@asu.edu
Addressing the Memory Wall
 Lecture 26: Addressing the Memory Wall Parallel Computer Architecture and Programming CMU 15-418/15-618, Spring 2015 Tunes Cage the Elephant Back Against the Wall (Cage the Elephant) This song is for the
Lecture 26: Addressing the Memory Wall Parallel Computer Architecture and Programming CMU 15-418/15-618, Spring 2015 Tunes Cage the Elephant Back Against the Wall (Cage the Elephant) This song is for the
Addendum to Efficiently Enabling Conventional Block Sizes for Very Large Die-stacked DRAM Caches
 Addendum to Efficiently Enabling Conventional Block Sizes for Very Large Die-stacked DRAM Caches Gabriel H. Loh Mark D. Hill AMD Research Department of Computer Sciences Advanced Micro Devices, Inc. gabe.loh@amd.com
Addendum to Efficiently Enabling Conventional Block Sizes for Very Large Die-stacked DRAM Caches Gabriel H. Loh Mark D. Hill AMD Research Department of Computer Sciences Advanced Micro Devices, Inc. gabe.loh@amd.com
A Spherical Placement and Migration Scheme for a STT-RAM Based Hybrid Cache in 3D chip Multi-processors
 , July 4-6, 2018, London, U.K. A Spherical Placement and Migration Scheme for a STT-RAM Based Hybrid in 3D chip Multi-processors Lei Wang, Fen Ge, Hao Lu, Ning Wu, Ying Zhang, and Fang Zhou Abstract As
, July 4-6, 2018, London, U.K. A Spherical Placement and Migration Scheme for a STT-RAM Based Hybrid in 3D chip Multi-processors Lei Wang, Fen Ge, Hao Lu, Ning Wu, Ying Zhang, and Fang Zhou Abstract As
Spring 2016 :: CSE 502 Computer Architecture. Caches. Nima Honarmand
 Caches Nima Honarmand Motivation 10000 Performance 1000 100 10 Processor Memory 1 1985 1990 1995 2000 2005 2010 Want memory to appear: As fast as CPU As large as required by all of the running applications
Caches Nima Honarmand Motivation 10000 Performance 1000 100 10 Processor Memory 1 1985 1990 1995 2000 2005 2010 Want memory to appear: As fast as CPU As large as required by all of the running applications
Adapted from instructor s supplementary material from Computer. Patterson & Hennessy, 2008, MK]
![Adapted from instructor s supplementary material from Computer. Patterson & Hennessy, 2008, MK] Adapted from instructor s supplementary material from Computer. Patterson & Hennessy, 2008, MK]](/thumbs/80/82108809.jpg) Lecture 17 Adapted from instructor s supplementary material from Computer Organization and Design, 4th Edition, Patterson & Hennessy, 2008, MK] SRAM / / Flash / RRAM / HDD SRAM / / Flash / RRAM/ HDD SRAM
Lecture 17 Adapted from instructor s supplementary material from Computer Organization and Design, 4th Edition, Patterson & Hennessy, 2008, MK] SRAM / / Flash / RRAM / HDD SRAM / / Flash / RRAM/ HDD SRAM
Power Reduction Techniques in the Memory System. Typical Memory Hierarchy
 Power Reduction Techniques in the Memory System Low Power Design for SoCs ASIC Tutorial Memories.1 Typical Memory Hierarchy On-Chip Components Control edram Datapath RegFile ITLB DTLB Instr Data Cache
Power Reduction Techniques in the Memory System Low Power Design for SoCs ASIC Tutorial Memories.1 Typical Memory Hierarchy On-Chip Components Control edram Datapath RegFile ITLB DTLB Instr Data Cache
CENG3420 Lecture 08: Memory Organization
 CENG3420 Lecture 08: Memory Organization Bei Yu byu@cse.cuhk.edu.hk (Latest update: February 22, 2018) Spring 2018 1 / 48 Overview Introduction Random Access Memory (RAM) Interleaving Secondary Memory
CENG3420 Lecture 08: Memory Organization Bei Yu byu@cse.cuhk.edu.hk (Latest update: February 22, 2018) Spring 2018 1 / 48 Overview Introduction Random Access Memory (RAM) Interleaving Secondary Memory
INSTITUTO SUPERIOR TÉCNICO. Architectures for Embedded Computing
 UNIVERSIDADE TÉCNICA DE LISBOA INSTITUTO SUPERIOR TÉCNICO Departamento de Engenharia Informática Architectures for Embedded Computing MEIC-A, MEIC-T, MERC Lecture Slides Version 3.0 - English Lecture 16
UNIVERSIDADE TÉCNICA DE LISBOA INSTITUTO SUPERIOR TÉCNICO Departamento de Engenharia Informática Architectures for Embedded Computing MEIC-A, MEIC-T, MERC Lecture Slides Version 3.0 - English Lecture 16
Chapter 8 Memory Basics
 Logic and Computer Design Fundamentals Chapter 8 Memory Basics Charles Kime & Thomas Kaminski 2008 Pearson Education, Inc. (Hyperlinks are active in View Show mode) Overview Memory definitions Random Access
Logic and Computer Design Fundamentals Chapter 8 Memory Basics Charles Kime & Thomas Kaminski 2008 Pearson Education, Inc. (Hyperlinks are active in View Show mode) Overview Memory definitions Random Access
CSE502: Computer Architecture CSE 502: Computer Architecture
 CSE 502: Computer Architecture Memory / DRAM SRAM = Static RAM SRAM vs. DRAM As long as power is present, data is retained DRAM = Dynamic RAM If you don t do anything, you lose the data SRAM: 6T per bit
CSE 502: Computer Architecture Memory / DRAM SRAM = Static RAM SRAM vs. DRAM As long as power is present, data is retained DRAM = Dynamic RAM If you don t do anything, you lose the data SRAM: 6T per bit
Cache Memory COE 403. Computer Architecture Prof. Muhamed Mudawar. Computer Engineering Department King Fahd University of Petroleum and Minerals
 Cache Memory COE 403 Computer Architecture Prof. Muhamed Mudawar Computer Engineering Department King Fahd University of Petroleum and Minerals Presentation Outline The Need for Cache Memory The Basics
Cache Memory COE 403 Computer Architecture Prof. Muhamed Mudawar Computer Engineering Department King Fahd University of Petroleum and Minerals Presentation Outline The Need for Cache Memory The Basics
CS 152 Computer Architecture and Engineering. Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste!
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste!
Effective Memory Access Optimization by Memory Delay Modeling, Memory Allocation, and Slack Time Management
 International Journal of Computer Theory and Engineering, Vol., No., December 01 Effective Memory Optimization by Memory Delay Modeling, Memory Allocation, and Slack Time Management Sultan Daud Khan, Member,
International Journal of Computer Theory and Engineering, Vol., No., December 01 Effective Memory Optimization by Memory Delay Modeling, Memory Allocation, and Slack Time Management Sultan Daud Khan, Member,
CSE502: Computer Architecture CSE 502: Computer Architecture
 CSE 502: Computer Architecture Memory Hierarchy & Caches Motivation 10000 Performance 1000 100 10 Processor Memory 1 1985 1990 1995 2000 2005 2010 Want memory to appear: As fast as CPU As large as required
CSE 502: Computer Architecture Memory Hierarchy & Caches Motivation 10000 Performance 1000 100 10 Processor Memory 1 1985 1990 1995 2000 2005 2010 Want memory to appear: As fast as CPU As large as required
Chapter Seven. Memories: Review. Exploiting Memory Hierarchy CACHE MEMORY AND VIRTUAL MEMORY
 Chapter Seven CACHE MEMORY AND VIRTUAL MEMORY 1 Memories: Review SRAM: value is stored on a pair of inverting gates very fast but takes up more space than DRAM (4 to 6 transistors) DRAM: value is stored
Chapter Seven CACHE MEMORY AND VIRTUAL MEMORY 1 Memories: Review SRAM: value is stored on a pair of inverting gates very fast but takes up more space than DRAM (4 to 6 transistors) DRAM: value is stored
Advanced Memory Organizations
 CSE 3421: Introduction to Computer Architecture Advanced Memory Organizations Study: 5.1, 5.2, 5.3, 5.4 (only parts) Gojko Babić 03-29-2018 1 Growth in Performance of DRAM & CPU Huge mismatch between CPU
CSE 3421: Introduction to Computer Architecture Advanced Memory Organizations Study: 5.1, 5.2, 5.3, 5.4 (only parts) Gojko Babić 03-29-2018 1 Growth in Performance of DRAM & CPU Huge mismatch between CPU
CENG 3420 Computer Organization and Design. Lecture 08: Cache Review. Bei Yu
 CENG 3420 Computer Organization and Design Lecture 08: Cache Review Bei Yu CEG3420 L08.1 Spring 2016 A Typical Memory Hierarchy q Take advantage of the principle of locality to present the user with as
CENG 3420 Computer Organization and Design Lecture 08: Cache Review Bei Yu CEG3420 L08.1 Spring 2016 A Typical Memory Hierarchy q Take advantage of the principle of locality to present the user with as
Mainstream Computer System Components
 Mainstream Computer System Components Double Date Rate (DDR) SDRAM One channel = 8 bytes = 64 bits wide Current DDR3 SDRAM Example: PC3-12800 (DDR3-1600) 200 MHz (internal base chip clock) 8-way interleaved
Mainstream Computer System Components Double Date Rate (DDR) SDRAM One channel = 8 bytes = 64 bits wide Current DDR3 SDRAM Example: PC3-12800 (DDR3-1600) 200 MHz (internal base chip clock) 8-way interleaved
An introduction to SDRAM and memory controllers. 5kk73
 An introduction to SDRAM and memory controllers 5kk73 Presentation Outline (part 1) Introduction to SDRAM Basic SDRAM operation Memory efficiency SDRAM controller architecture Conclusions Followed by part
An introduction to SDRAM and memory controllers 5kk73 Presentation Outline (part 1) Introduction to SDRAM Basic SDRAM operation Memory efficiency SDRAM controller architecture Conclusions Followed by part
15-740/ Computer Architecture, Fall 2011 Midterm Exam II
 15-740/18-740 Computer Architecture, Fall 2011 Midterm Exam II Instructor: Onur Mutlu Teaching Assistants: Justin Meza, Yoongu Kim Date: December 2, 2011 Name: Instructions: Problem I (69 points) : Problem
15-740/18-740 Computer Architecture, Fall 2011 Midterm Exam II Instructor: Onur Mutlu Teaching Assistants: Justin Meza, Yoongu Kim Date: December 2, 2011 Name: Instructions: Problem I (69 points) : Problem
WALL: A Writeback-Aware LLC Management for PCM-based Main Memory Systems
 : A Writeback-Aware LLC Management for PCM-based Main Memory Systems Bahareh Pourshirazi *, Majed Valad Beigi, Zhichun Zhu *, and Gokhan Memik * University of Illinois at Chicago Northwestern University
: A Writeback-Aware LLC Management for PCM-based Main Memory Systems Bahareh Pourshirazi *, Majed Valad Beigi, Zhichun Zhu *, and Gokhan Memik * University of Illinois at Chicago Northwestern University
BIBIM: A Prototype Multi-Partition Aware Heterogeneous New Memory
 HotStorage 18 BIBIM: A Prototype Multi-Partition Aware Heterogeneous New Memory Gyuyoung Park 1, Miryeong Kwon 1, Pratyush Mahapatra 2, Michael Swift 2, and Myoungsoo Jung 1 Yonsei University Computer
HotStorage 18 BIBIM: A Prototype Multi-Partition Aware Heterogeneous New Memory Gyuyoung Park 1, Miryeong Kwon 1, Pratyush Mahapatra 2, Michael Swift 2, and Myoungsoo Jung 1 Yonsei University Computer
Reducing Hit Times. Critical Influence on cycle-time or CPI. small is always faster and can be put on chip
 Reducing Hit Times Critical Influence on cycle-time or CPI Keep L1 small and simple small is always faster and can be put on chip interesting compromise is to keep the tags on chip and the block data off
Reducing Hit Times Critical Influence on cycle-time or CPI Keep L1 small and simple small is always faster and can be put on chip interesting compromise is to keep the tags on chip and the block data off
Migration Based Page Caching Algorithm for a Hybrid Main Memory of DRAM and PRAM
 Migration Based Page Caching Algorithm for a Hybrid Main Memory of DRAM and PRAM Hyunchul Seok Daejeon, Korea hcseok@core.kaist.ac.kr Youngwoo Park Daejeon, Korea ywpark@core.kaist.ac.kr Kyu Ho Park Deajeon,
Migration Based Page Caching Algorithm for a Hybrid Main Memory of DRAM and PRAM Hyunchul Seok Daejeon, Korea hcseok@core.kaist.ac.kr Youngwoo Park Daejeon, Korea ywpark@core.kaist.ac.kr Kyu Ho Park Deajeon,
CMU Introduction to Computer Architecture, Spring 2014 HW 5: Virtual Memory, Caching and Main Memory
 CMU 18-447 Introduction to Computer Architecture, Spring 2014 HW 5: Virtual Memory, Caching and Main Memory Instructor: Prof. Onur Mutlu TAs: Rachata Ausavarungnirun, Varun Kohli, Xiao Bo Zhao, Paraj Tyle
CMU 18-447 Introduction to Computer Architecture, Spring 2014 HW 5: Virtual Memory, Caching and Main Memory Instructor: Prof. Onur Mutlu TAs: Rachata Ausavarungnirun, Varun Kohli, Xiao Bo Zhao, Paraj Tyle
COMPUTER ORGANIZATION AND DESIGN
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
CENG4480 Lecture 09: Memory 1
 CENG4480 Lecture 09: Memory 1 Bei Yu byu@cse.cuhk.edu.hk (Latest update: November 8, 2017) Fall 2017 1 / 37 Overview Introduction Memory Principle Random Access Memory (RAM) Non-Volatile Memory Conclusion
CENG4480 Lecture 09: Memory 1 Bei Yu byu@cse.cuhk.edu.hk (Latest update: November 8, 2017) Fall 2017 1 / 37 Overview Introduction Memory Principle Random Access Memory (RAM) Non-Volatile Memory Conclusion
CANDY: Enabling Coherent DRAM Caches for Multi-Node Systems
 CANDY: Enabling Coherent DRAM Caches for Multi-Node Systems Chiachen Chou Aamer Jaleel Moinuddin K. Qureshi School of Electrical and Computer Engineering Georgia Institute of Technology {cc.chou, moin}@ece.gatech.edu
CANDY: Enabling Coherent DRAM Caches for Multi-Node Systems Chiachen Chou Aamer Jaleel Moinuddin K. Qureshi School of Electrical and Computer Engineering Georgia Institute of Technology {cc.chou, moin}@ece.gatech.edu
OVERCOMING THE MEMORY WALL FINAL REPORT. By Jennifer Inouye Paul Molloy Matt Wisler
 OVERCOMING THE MEMORY WALL FINAL REPORT By Jennifer Inouye Paul Molloy Matt Wisler ECE/CS 570 OREGON STATE UNIVERSITY Winter 2012 Contents 1. Introduction... 3 2. Background... 5 3. 3D Stacked Memory...
OVERCOMING THE MEMORY WALL FINAL REPORT By Jennifer Inouye Paul Molloy Matt Wisler ECE/CS 570 OREGON STATE UNIVERSITY Winter 2012 Contents 1. Introduction... 3 2. Background... 5 3. 3D Stacked Memory...
k -bit address bus n-bit data bus Control lines ( R W, MFC, etc.)
 THE MEMORY SYSTEM SOME BASIC CONCEPTS Maximum size of the Main Memory byte-addressable CPU-Main Memory Connection, Processor MAR MDR k -bit address bus n-bit data bus Memory Up to 2 k addressable locations
THE MEMORY SYSTEM SOME BASIC CONCEPTS Maximum size of the Main Memory byte-addressable CPU-Main Memory Connection, Processor MAR MDR k -bit address bus n-bit data bus Memory Up to 2 k addressable locations
Memory Technology. Caches 1. Static RAM (SRAM) Dynamic RAM (DRAM) Magnetic disk. Ideal memory. 0.5ns 2.5ns, $2000 $5000 per GB
 Memory Technology Caches 1 Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per GB Ideal memory Average access time similar
Memory Technology Caches 1 Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per GB Ideal memory Average access time similar
A Low-Power Hybrid Magnetic Cache Architecture Exploiting Narrow-Width Values
 A Low-Power Hybrid Magnetic Cache Architecture Exploiting Narrow-Width Values Mohsen Imani, Abbas Rahimi, Yeseong Kim, Tajana Rosing Computer Science and Engineering, UC San Diego, La Jolla, CA 92093,
A Low-Power Hybrid Magnetic Cache Architecture Exploiting Narrow-Width Values Mohsen Imani, Abbas Rahimi, Yeseong Kim, Tajana Rosing Computer Science and Engineering, UC San Diego, La Jolla, CA 92093,
Memory Technology. Chapter 5. Principle of Locality. Chapter 5 Large and Fast: Exploiting Memory Hierarchy 1
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface Chapter 5 Large and Fast: Exploiting Memory Hierarchy 5 th Edition Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface Chapter 5 Large and Fast: Exploiting Memory Hierarchy 5 th Edition Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic
