when interoperating with a Cisco Layer 3 Switch Situation: VLAN 1 shutdown, no IP on default VLAN on Cisco switch
|
|
|
- Carmella Henry
- 5 years ago
- Views:
Transcription
1 CONFIGURING VLANS ON MNS-6K AND MNS-6K-SECURE when interoperating with a Cisco Layer 3 Switch Situation: VLAN 1 shutdown, no IP on default VLAN on Cisco switch A Technical Brief from GarrettCom, Inc., for use with MNS 4.1/14,1 August 2008 SUMMARY Networks today use VLANs. It is necessary to create VLANs for security, traffic separation, traffic management and control, or for other reasons. Many networks use a Cisco Layer 3 switch such as the Catalyst 3570, Catalyst 6509 etc. to route traffic across these VLANs. For security reasons, many networks choose to shutdown the default VLAN (VLAN 1), assign a different VLAN as the default VLAN on the trunk port and not assign an IP address to this default VLAN. This technical brief uses the Cisco Catalyst 3570G-24P Layer 3 switch and shows how the Magnum 6K family of switches can participate in such a network. The technical details of how the Cisco switch is configured are omitted, but for completeness, the configuration is enclosed in Appendix 1. The necessary steps to configure MNS-6K and MNS-6K-SECURE Network Management Software (NMS) for the Magnum 6K family of switches are shown in detail. DIFFERENCES BETWEEN IOS AND MNS-6K This section is relevant for users familiar with the Cisco IOS commands and how VLANs are setup on the Cisco switch using the CLI interface. It explains the methodology differences in setting up the VLANs on Cisco IOS and GarrettCom s Magnum MNS-6K NMS. Devices such as computers, PC s, IED sensors etc. connected to the switch, do not send out tagged packets. Since the packet on the port is sent out untagged, each port on MNS-6K needs to be configured as to which VLAN to send the untagged packet to. On the Cisco switch IOS recommends using the switchport access vlan xx where xx is a defined VLAN. On MNS-6K, the VLAN has to be specified for specific VLAN tag. This is done by defining the default VLAN for that port (see Step 4 in this Technical Brief for further clarification.) Just as devices send untagged packets on a specific port, intercommunications between switches are done using 802.1q tagging. These ports are defined as trunk ports. On the trunk port the VLANs have to be tagged. On MNS-6K, this has to be explicitly configured. On Cisco IOS this is implicitly defined. Since this is implicitly done on Cisco IOS, most IOS users skip this step. This is explained in more detail in Step 3 in this technical brief. This summarizes the differences between how VLANs are setup on the Cisco switch vs how VLANs are setup on the MNS-6K Network Management Software (NMS). To understand this better, it is strongly recommended to follow the example shown in this technical brief GarrettCom Inc. Page 1
2 The details on how the Cisco switch is configured are not covered in this brief; however, the configuration used for the Cisco switch is included in Appendix 1. This Technical Brief looks at configuring the MNS-6K NMS using CLI commands. Finally, some frequently asked questions are also provided. One final note another source of confusion for many users configuring the VLANs is that MNS-6K version (and earlier) offer two different types of VLANs tag VLANs and port VLANs. While Cisco IOS offers these as well, by default, IOS uses tag VLAN. On MNS-6K, while configuring VLANs to interoperate with Cisco switches (or other switches from Foundry, 3Com etc.) it is recommended to use tag VLANs 1. NETWORK OVERVIEW The VLAN setup is discussed later in this section. The Cisco 3750G-24P switch running IOS (version 12.2) is configured for VLANs. The Cisco Layer 3 switch provides DHCP services for devices connected to each of the VLANs as well as routing services between the VLANs. The DHCP services provide IP addresses on the respective VLANs starting from 101 to 199. For details on the Cisco configuration, please see Appendix 1. The Cisco Switch uses VLAN 360 as a default VLAN. VLANs 10, 20, 100 are also defined. The interconnection from the Cisco switch to the Magnum 6K16V switch will be on Port #1 thus Port 1 will be the trunk port, using 802.1q (or in Cisco IOS terminology dot 1q encapsulation) on both switches. The port and VLAN usage on each port for the Cisco 3750G-24P 24 port switch are as follows: Port # 1 trunk port dot1q encapsulation for VLANs 360, 10, 20, 100 note VLAN 360 is defined ot be native here and VLAN 1 is deliberately shutdown Port # 2 shutdown (for administrative reasons) Port # 3-6 VLAN 10 Port # 7-12 default VLAN Port # VLAN 20 Port #17-20 Default VLAN Port # VLAN 100 SFP Ports Default VLAN The Magnum 6K switch used is an 8 port Magnum 6K16V switch Running MNS-6K version The commands used are the same for MNS-6K Version 4.0 as well as MNS-6K-SECURE version The port mapping for the Magnum 6K16V switch are as follows: Port #1 Trunk Port allowing tag VLANs 360, 10, 20, 100. VLAN 360 is the default VLAN Port #2 VLAN 10 Port #3 VLAN 20 Port #4 VLAN As of MNS-6K version 4.0 or MNS-6K-SECURE 14.0, only the tagged VLAN interface is shown. While the Port VLAN commands are available for backward compatibility, they are neither visible, nor documented, nor supported GarrettCom Inc. Page 2
3 TESTING THE SETUP The test plan entails testing the network services for each VLAN. This includes DHCP services routing services using commands such as ping and telnet. The steps followed are: 1) A computer is plugged into ports 2-4 on the Magnum 6K16V switch. Since each time the computer is plugged into a different VLAN, it should request via DHCP an IP address. The Cisco Switch being a DHCP server for the different VLANs will issue an IP address. If the request is being propagated properly, the PC will get the IP address for the respective VLAN. While changing the VLANs, it maybe necessary to release the IP address leased and request the IP address (done by the ipconfig command on the command interface on a Windows XP PC) 2) After the computer got its IP Address, the IP address was inspected for correctness of IP address range (mapping the IP address to the specific VLAN). See the VLAN IP address schema below. 3) The different routing interfaces on the different VLANs were pinged for connectivity 4) A telnet session is opened from the computer on the Magnum 6K16V switch to the Cisco switch, using the IP address of different VLAN. So for example, if the computer on the Magnum 6K16V switch is connected to port 3, it will be on VLAN 10. The computer will have the IP address x/24 (usually / ) and the telnet session would be with or see table below for IP addressing schema The VLAN IP addressing schema is as follows: IP schema VLAN routing IP Magnum 6K IP VLAN 360 VLAN 1 VLAN 10 VLAN 20 VLAN 100 None no IP None x/ x/ x/24 Address shutdown None native None / on trunk port NA NA /24 NA NA DGW = depends on L3 switch for routing 2008 GarrettCom Inc. Page 3
4 The information is summarized in the figure below GarrettCom 6K 16V /24 Trunk Port VLANs 360, 10, 20, 100 (VLAN 360 default) to 6 to 16 to 24 Routing & DHCP services Cisco 3750G-24P VLAN1 shutdown / / /24 Figure 1 Network schema The steps to configure MNS-6K are next discussed. The paper details the MNS-6K commands from the console port. The User Guide for CLI as well as the User Guide for SWM covers details on how to configure the console port. STEP 1 - Configuring IP Address for Magnum 6K Switch The first step is to setup the IP address. Since the Default VLAN id=1, MNS-6K switch will pick up the IP address from the DHCP services provided by the Cisco switch for the default VLAN. The commands for setting up the IP address are as follows: Magnum 6K16# ipconfig ip= mask= dgw= Boot Mode Changed to MANUAL. IP Parameters Set. Magnum 6K16# Figure 2 Setting IP address for the Magnum 6K switch. NOTE it is important to define the default router (in the case of MNS-6K it is called default gateway or dgw). After defining the dgw, you should be able to ping the different IP addresses of the VLAN interfaces Make sure the dgw is setup for the default gateway. Without the dgw definition, the routing functions will not work. Once the IP address is set, the CLI commands to setup the VLANs are discussed next. STEP 2 - CLI commands to Configure VLANs The CLI commands for configuring VLANs are from the VLAN command interface. Here we add VLAN 360 to port 1 ad that is the default VLAN id required to interoperate with the Cisco switch. To access those commands, use the vlan command as shown below GarrettCom Inc. Page 4
5 Magnum 6K16# vlan Magnum 6K16(tag-vlan)# vlan enable VLAN set to Tag-based. Magnum 6K16(tag-vlan)## add id=360 name=vlan360 port=1 Tag based vlan Added Successfully Vlan id : 360 Vlan Name :vlan360 Ports :1 Magnum 6K16(tag-vlan)## add id=10 name=vlan10 port=1,2 Tag based vlan Added Successfully Vlan id : 10 Vlan Name :vlan10 Ports :1,2 Magnum 6K16(tag-vlan)## add id=20 name=vlan20 port=1,3 Tag based vlan Added Successfully Vlan id : 20 Vlan Name :vlan20 Ports :1,3 Magnum 6K16(tag-vlan)## add id=100 name=vlan100 port=1,4 Tag based vlan Added Successfully Vlan id : 100 Vlan Name :vlan100 Ports :1,4 Magnum 6K16(tag-vlan)## Figure 3 First define the VLAN to be tagged. Once that is done, access the VLAN commands by using the vlan type=tag command. Use the add command to add the VLANs and the necessary ports to the VLANs. Refer to Figure 1 for how the VLANs are setup STEP 3 Set the trunk port to send out packets as tagged packets for the necessary VLANs This step is the most crucial step and is frequently neglected by people familiar with Cisco IOS. This step ensures that on port 1 (trunk port) all the VLANs are tagged. As discussed earlier, this step is implicitly done by Cisco IOS. For MNS-6K the VLANs on the trunk port have to be explicitly tagged. Magnum 6K16(tag-vlan)## set-port port=1 tagging id=10 status=tagged Port tagging enabled Magnum 6K16(tag-vlan)## set-port port=1 tagging id=20 status=tagged Port tagging enabled Magnum 6K16(tag-vlan)## set-port port=1 tagging id=100 status=tagged Port tagging enabled Magnum 6K16(tag-vlan)## 2008 GarrettCom Inc. Page 5
6 Figure 4 On the trunk port (port #1), set the VLANs to be tagged. This is done using the set-port command STEP 4 Define the access VLAN for the ports In this step, first define the default VLAN id on the trunk port (port 1) to be VLAN 360. This is done unsing the set-port command. The computer, PCs, IED devices etc. connected to the switch does not send out packets with the necessary tag information for the VLAN it should be on. Since it does not do that, one has to specify as to which VLAN tag will be added to the VLAN tag field when the packet traverses across VLANs. This is done by using the set-port command as shown below. For example, on port #2, the VLAN id of all packets will be VLAN 10. Magnum 6K16(tag-vlan)## set-port port=1 default id=360 Port default vlan id is set Magnum 6K16(tag-vlan)## set-port port=2 default id=10 Port default vlan id is set Magnum 6K16(tag-vlan)## set-port port=3 default id=20 Port default vlan id is set Magnum 6K16(tag-vlan)## set-port port=4 default id=100 Port default vlan id is set Magnum 6K16(tag-vlan)## Figure 5 Specify the default VLAN for each port corresponding to the VLAN tag which will be assigned to the packets STEP 5 Start the VLANs This step is the equivalent of the no shutdown command in IOS for all the different VLAN interfaces. Magnum 6K16(tag-vlan)## start vlan=all All pending VLAN's started. Magnum 6K16(tag-vlan)## Figure 6 Start all VLANs At this point one can ping all the VLANs and devices on the Cisco switch. Do not forget to exit out of the VLAN command subset before trying the ping command. Magnum 6K16(tag-vlan)## exit Magnum 6K16# ping is alive, count 1, time = 20ms Magnum 6K16# ping is alive, count 1, time = 20ms 2008 GarrettCom Inc. Page 6
7 Magnum 6K16# ping is alive, count 1, time = 20ms Magnum 6K16# Figure 7 After starting VLANs, devices can be pinged for connectivity Finally, save the configuration and test the settings. TESTING THE CONFIGURATION As discussed earlier, one way to test for the configuration is to ensure that the proper IP address is issued to the PC connected to a Magnum 6K port on the different VLANs. The DHCP request is made to the Cisco L3 switch by sending the request over the trunk port and routing the request to the proper VLAN interface. Once the proper IP address is issued, the ping command, the telnet command etc. are used to test connectivity. While switching from one VLAN to another, it maybe necessary to flush the IP address assigned to the PC. To do that, use the commands ipconfig /release and ipconfig /renew in a command window on a Windows XP system. For the test, plug the computer in ports 2, 3, 4 on the Magnum 6K switch. Make sure it is assigned the necessary IP address schema corresponding to the different VLANs defined. Here is an example of the ipconfig as well as the ping session from a PC on the Magnum 6K switch on port #3 (VLAN 20.) C:\> ipconfig Windows IP Configuration Ethernet adapter Local Area Connection: C:\> Connection-specific DNS Suffix. : yourdomain.com IP Address : Subnet Mask : Default Gateway : Figure 8 After starting VLANs, connecting the port # 2, 3, 4 should assign the proper IP addresses from the DHCP services on the Cisco switch. In this case, the computer is plugged into port #3 and it assigned the IP address schema for VLAN 20. Devices can be pinged for connectivity across the network 2008 GarrettCom Inc. Page 7
8 SUMMARY OF COMMANDS The commands used and the purpose are summarized below. ipconfig ip= mask= dgw= Set the IP address of MNS-6K switch vlan enable Set the VLAN type to be tagged vlan Access the VLAN commands add id=360 name=vlan360 port=1 Add VLAN 360 on trunk port only. add id=10 name=vlan10 port=1,2 Add VLAN 10 on ports 1 and 2. Port 1 is going to be on trunk port add id=20 name=vlan20 port=1,3 Add VLAN 20 on ports 1 and 3. Port 1 is going to be on trunk port add id=100 name=vlan100 port=1,4 Add VLAN 100 on ports 1 and 4. Port 1 is going to be on trunk port set-port port=1 tagging id=10 status=tagged On port #1, set VLAN with id=10 to be tagged set-port port=1 tagging id=20 status=tagged On port #1, set VLAN with id=20 to be tagged set-port port=1 tagging id=100 status=tagged On port #1, set VLAN with id=100 to be tagged set-port port=1 default id=360 On port #1, ensure that the default VLAN definition is set to 360 set-port port=2 default id=10 On port #2, ensure that all untagged packets get the tag of VLAN 10. This is done making VLAN 10 as the default VLAN for port #2 set-port port=3 default id=20 On port #3, ensure that all untagged packets get the tag of VLAN 20. This is done making VLAN 20 as the default VLAN for port #3 set-port port=4 default id=100 On port #4, ensure that all untagged packets get the tag of VLAN 100. This is done making VLAN 100 as the default VLAN for port #4 start vlan=all Start VLANs 2008 GarrettCom Inc. Page 8
9 FREQUENTLY ASKED QUESTIONS 1) Can I configure the switches so that the default VLAN id is set to 1 OR can I set the default VLAN to 1? Yes please see the technical brief on how to do that. 2) I cannot ping the default VLAN interface Cisco IOS shuts down the VLAN interfaces and the ports by default. You have to enable those interfaces before the connectivity works. On the Cisco switch, verify that the trunk port is not shutdown. If it is shutdown, enable it using the no shutdown command. Next, check to see if the VLAN IP address schema is defined properly for the respective VLANs. If not, fix the IP address schema. After confirming that, ensure that the default VLAN is not shutdown. If it is shutdown, enable it using the no shutdown command on the VLAN interface. Next check to see if routing is enabled and routes are defined (if needed). If routing is not enabled, please enable routing or make sure the default gateway definition is set properly. Test that by pinging the MNS-6K IP address and the DNS server defined for the network from the Cisco IOS interface. 3) I can ping the default VLAN IP address, I cannot ping the other VLAN IP addresses. Some Cisco devices will not respond to ping packets on a VLAN interface unless there is a device connected to the VLAN. If this happens, test the connectivity by plugging a computer into the VLAN and then try pinging the interface again. 4) Ping response is erratic I get a response from one device, while another device on the VLAN does not respond. What is going on? In these situations, it is possible that there is a Firewall on the network inspecting packets and dropping responses from one device while allowing responses from the other device. If you are sure there is no firewall, then check to see if there are ACL statements on the Cisco IOS which may cause this to happen. It is recommended to withdraw all firewall and ACL statements first, and then ensure that the connectivity works as desired. Once this is verified, add the security measures (firewall or ACL statements) next. This is generally a good practice to follow when adding a new device on the network GarrettCom Inc. Page 9
10 APPENDIX 1 IOS CONFIGURATION USED FOR THE CATALYST 3750G-24P SWITCH The configuration for a Cisco Catalyst 3750G switch is shown. The key configuration statements are highlighted and colored in red. The key points are: 1) On the trunk port (port #1) VLAN 360 is defined to be default 2) VLAN 1 (default VLAN by default) is shutdown 3) VLAN 360 has no IP address this is usually done for security reasons version 12.2 no service pad no service timestamps debug uptime service timestamps log datetime service password-encryption service sequence-numbers hostname 3750G boot-start-marker boot-end-marker no logging console enable password username adm privilege 15 password 7 121A0C F0D39282B username admin privilege 15 password A F1C2243 username administrator privilege 15 password F D3B303A no aaa new-model clock timezone PST -8 clock summer-time PDT recurring switch 1 provision ws-c3750g-24ps system mtu routing 1500 ip subnet-zero ip routing no ip domain-lookup ip dhcp excluded-address ip dhcp excluded-address ip dhcp excluded-address ip dhcp excluded-address ip dhcp excluded-address ip dhcp excluded-address ip dhcp pool vlan10 network default-router domain-name yourdomain.com lease 0 8 ip dhcp pool vlan20 network default-router Page 10
11 domain-name yourdomain.com lease 0 8 ip dhcp pool vlan100 network default-router domain-name yourdomain.com lease 0 8 ip multicast-routing distributed ip multicast multipath ip igmp profile 1 permit range spanning-tree mode pvst spanning-tree extend system-id vlan internal allocation policy ascending interface GigabitEthernet1/0/1 description Trunk port to GCI Switch switchport trunk encapsulation dot1q switchport trunk native vlan 360 switchport mode trunk interface GigabitEthernet1/0/2 shutdown interface GigabitEthernet1/0/3 switchport access vlan 10 interface GigabitEthernet1/0/4 switchport access vlan 10 interface GigabitEthernet1/0/5 switchport access vlan 10 interface GigabitEthernet1/0/6 switchport access vlan 10 interface GigabitEthernet1/0/7 Page 11
12 interface GigabitEthernet1/0/8 interface GigabitEthernet1/0/9 interface GigabitEthernet1/0/10 interface GigabitEthernet1/0/11 interface GigabitEthernet1/0/12 interface GigabitEthernet1/0/13 switchport access vlan 20 interface GigabitEthernet1/0/14 switchport access vlan 20 interface GigabitEthernet1/0/15 switchport access vlan 20 interface GigabitEthernet1/0/16 switchport access vlan 20 interface GigabitEthernet1/0/17 interface GigabitEthernet1/0/18 interface GigabitEthernet1/0/19 interface GigabitEthernet1/0/20 interface GigabitEthernet1/0/21 switchport access vlan 100 interface GigabitEthernet1/0/22 switchport access vlan 100 interface GigabitEthernet1/0/23 switchport access vlan 100 Page 12
13 interface GigabitEthernet1/0/24 switchport access vlan 100 interface GigabitEthernet1/0/25 interface GigabitEthernet1/0/26 interface GigabitEthernet1/0/27 interface GigabitEthernet1/0/28 interface Vlan1 no ip address shutdown interface Vlan10 ip address interface Vlan20 ip address interface Vlan100 ip address interface Vlan360 no ip address ip default-gateway ip classless ip http server ip http secure-server control-plane line con 0 line vty 0 4 exec-timeout 0 0 password F1C22434D000A0618 login local length 0 line vty 5 15 exec-timeout 0 0 password F D3B303A login local end Page 13
14 GarrettCom, Inc Westinghouse Dr. Fremont, CA PH: (510) FAX: (510) Web: GarrettCom, Inc. Printed in United States of America GarrettCom, Inc. reserves the right to change specifications, performance characteristics and/or model offerings without notice. GarrettCom is a registered trademark of GarrettCom Inc. Magnum, S-Ring, Link-Loss-Learn, Converter Switch, Convenient Switch and Personal Switch are trademarks of GarrettCom, Inc. NEBS is a registered trademark of Telcordia Technologies. UL is a registered trademark of Underwriters Labs. Page 14
Lab - Troubleshooting VLAN Configurations (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
CONFIGURATION DU SWITCH
 Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Lab - Configuring a Switch Management Address
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.2 255.255.255.0 N/A PC-A NIC 192.168.1.10 255.255.255.0 N/A Part 1: Configure a Basic Network
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.2 255.255.255.0 N/A PC-A NIC 192.168.1.10 255.255.255.0 N/A Part 1: Configure a Basic Network
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
Chapter 8 Lab 8-1, IP Service Level Agreements and Remote SPAN in a Campus Environment INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 8 Lab 8-1, IP Service Level Agreements and Remote SPAN in a Campus Environment INSTRUCTOR VERSION Topology Objectives Background Configure trunking, VTP, and SVIs. Implement IP
CCNPv7.1 SWITCH Chapter 8 Lab 8-1, IP Service Level Agreements and Remote SPAN in a Campus Environment INSTRUCTOR VERSION Topology Objectives Background Configure trunking, VTP, and SVIs. Implement IP
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
Using scripts to easily configure and maintain MNS-6K software
 Using scripts to easily configure and maintain MNS-6K software Configuration accuracy and configuration consistency are extended beyond the CLI or SWM standard commands for MNS-6K users Ease-Of-Use GarrettCom
Using scripts to easily configure and maintain MNS-6K software Configuration accuracy and configuration consistency are extended beyond the CLI or SWM standard commands for MNS-6K users Ease-Of-Use GarrettCom
Chapter 5 Lab 5-2 DHCP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-2 DHCP INSTRUCTOR VERSION Topology Objectives Configure DHCP for IPv4 Configure Stateless DHCP for IPv6 Configure Stateful DHCP for IPv6 Background To practice the various
CCNPv7.1 SWITCH Chapter 5 Lab 5-2 DHCP INSTRUCTOR VERSION Topology Objectives Configure DHCP for IPv4 Configure Stateless DHCP for IPv6 Configure Stateful DHCP for IPv6 Background To practice the various
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
Lab Configuring Basic Switch Settings (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
Lab Troubleshooting IPv4 and IPv6 Static Routes (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab - Configuring VLANs and Trunking (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3
Table of Contents. isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ
 king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
Lab - Configuring Basic DHCPv4 on a Router (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1 255.255.255.0 N/A G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 (DCE) 192.168.2.253
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1 255.255.255.0 N/A G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 (DCE) 192.168.2.253
Buy full file at
 14 Chapter 2 LAN Redundancy Chapter 2 LAN Redundancy 2.0.1.2 Class Activity Stormy Traffic ( ) Objective Explain the purpose of the Spanning Tree Protocol (STP) in a switched LAN environment with redundant
14 Chapter 2 LAN Redundancy Chapter 2 LAN Redundancy 2.0.1.2 Class Activity Stormy Traffic ( ) Objective Explain the purpose of the Spanning Tree Protocol (STP) in a switched LAN environment with redundant
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
Lab Catalyst 2950T and 3550 Series Basic Setup
 Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Device Interface IP Address Subnet Mask Default Gateway. Ports Assignment Network
 Felix Rohrer Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Felix Rohrer Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Skills Assessment Student Training
 Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Lab 6.4.2: Challenge Inter-VLAN Routing
 Lab 6.4.2: Challenge Inter-VLAN Routing Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.99.11 255.255.255.0 192.168.99.1 S2 VLAN
Lab 6.4.2: Challenge Inter-VLAN Routing Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.99.11 255.255.255.0 192.168.99.1 S2 VLAN
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System. Proposed by Jedadiah Casey. Introduction
 Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Chapter 7 Lab 7-1, Synchronizing Campus Network Devices using Network Time Protocol (NTP) INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 7 Lab 7-1, Synchronizing Campus Network Devices using Network Time Protocol (NTP) INSTRUCTOR VERSION Topology Objective Background Configure network to synchronize time using the
CCNPv7.1 SWITCH Chapter 7 Lab 7-1, Synchronizing Campus Network Devices using Network Time Protocol (NTP) INSTRUCTOR VERSION Topology Objective Background Configure network to synchronize time using the
QUESTION/SOLUTION SET LAB 4
 QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
Lab Configuring Port Address Translation (PAT) (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Device Interface IP Address Subnet Mask R1 G0/ N/A
 CSNB214 Packet Tracer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Objectives R1 G0/0 192.168.20.1 255.255.255.0 N/A S1 VLAN 10 S2 VLAN 10 G0/1 192.168.10.1 255.255.255.0
CSNB214 Packet Tracer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Objectives R1 G0/0 192.168.20.1 255.255.255.0 N/A S1 VLAN 10 S2 VLAN 10 G0/1 192.168.10.1 255.255.255.0
Lab 7 Configuring Basic Router Settings with IOS CLI
 Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab 5: Basic VLAN Configuration
 Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Lab Using the CLI to Gather Network Device Information Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Lab Configuring Dynamic and Static NAT (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3
 Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
Lab Managing Router Configuration Files with Terminal Emulation Software
 Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Chapter 3 Lab 3-1 Static VLANS, Trunking, and VTP
 CCNPv7.1 SWITCH Chapter 3 Lab 3-1 Static VLANS, Trunking, and VTP INSTRUCTOR VERSION Topology Objectives Setup a VTP v2 Domain. Create and maintain VLANs. Configure 802.1Q Trunking. Setup a VTP v3 Domain.
CCNPv7.1 SWITCH Chapter 3 Lab 3-1 Static VLANS, Trunking, and VTP INSTRUCTOR VERSION Topology Objectives Setup a VTP v2 Domain. Create and maintain VLANs. Configure 802.1Q Trunking. Setup a VTP v3 Domain.
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Lab - Troubleshooting DHCPv4 Topology
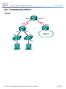 Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1
Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools
 Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools Physical Topology All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools Physical Topology All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
How to configure MB5000 Serial Port Bridge mode
 How to configure MB5000 Serial Port Bridge mode MB5000 has a configurable serial port. With this serial port, MB5000 can be used as DCE device to be connected with Cisco router s console port so that MB5000
How to configure MB5000 Serial Port Bridge mode MB5000 has a configurable serial port. With this serial port, MB5000 can be used as DCE device to be connected with Cisco router s console port so that MB5000
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
SSG Configuration Example
 APPENDIX A Example A-1 is a sample SSG configuration for the Cisco 10000 series router based on the topology in Figure A-1. The configuration includes AAA, PPP, SSG, and RADIUS. The SSG configuration enables
APPENDIX A Example A-1 is a sample SSG configuration for the Cisco 10000 series router based on the topology in Figure A-1. The configuration includes AAA, PPP, SSG, and RADIUS. The SSG configuration enables
IEEE 802.1Q Tunneling (QnQ) and L2PT on L2 Ports
 Revised: November 11, 2011, OL-20468-01 First Published: November 11, 2011 Last Updated: November 11, 2011 This feature provides Layer 2 Tunneling support for QnQ and Layer 2 Protocol Tunneling (L2PT)
Revised: November 11, 2011, OL-20468-01 First Published: November 11, 2011 Last Updated: November 11, 2011 This feature provides Layer 2 Tunneling support for QnQ and Layer 2 Protocol Tunneling (L2PT)
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Lab Configuring Switch Security Features Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 172.16.99.1 255.255.255.0 N/A S1 VLAN 99 172.16.99.11 255.255.255.0 172.16.99.1 PC-A NIC 172.16.99.3
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 172.16.99.1 255.255.255.0 N/A S1 VLAN 99 172.16.99.11 255.255.255.0 172.16.99.1 PC-A NIC 172.16.99.3
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 7 Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1.1 192.168.1.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 7 Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1.1 192.168.1.1
cable modem dhcp proxy nat on Cisco Cable Modems
 cable modem dhcp proxy nat on Cisco Cable Modems Document ID: 12176 Contents Introduction Prerequisites Requirements Components Used Conventions Dynamic NAT Versus Static NAT Configuration Using cable
cable modem dhcp proxy nat on Cisco Cable Modems Document ID: 12176 Contents Introduction Prerequisites Requirements Components Used Conventions Dynamic NAT Versus Static NAT Configuration Using cable
Lab Configuring EtherChannel
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask S1 VLAN 99 192.168.99.11 255.255.255.0 S2 VLAN 99 192.168.99.12 255.255.255.0 S3 VLAN 99 192.168.99.13 255.255.255.0 PC-A NIC
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask S1 VLAN 99 192.168.99.11 255.255.255.0 S2 VLAN 99 192.168.99.12 255.255.255.0 S3 VLAN 99 192.168.99.13 255.255.255.0 PC-A NIC
Lab Designing and Implementing a VLSM Addressing Scheme. Topology. Objectives. Background / Scenario
 CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
DHCP Server RADIUS Proxy
 The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
Interconnecting Cisco Networking Devices Part 1 ( )
 Interconnecting Cisco Networking Devices Part 1 (100-101) Exam Description: The 100-101 Interconnecting Cisco Networking Devices Part 1 (ICND1) is a 1.5- hour exam with 50 60 questions. The 100-101 Interconnecting
Interconnecting Cisco Networking Devices Part 1 (100-101) Exam Description: The 100-101 Interconnecting Cisco Networking Devices Part 1 (ICND1) is a 1.5- hour exam with 50 60 questions. The 100-101 Interconnecting
8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista
 8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista Introduction If Vista is not available in your classroom, you may complete this lab by viewing the figures in this document. Print and
8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista Introduction If Vista is not available in your classroom, you may complete this lab by viewing the figures in this document. Print and
CCNP Lab 006 Solution: HSRP and Switch Security
 ABOUT CONTACT FAQ JOIN HOME CCNA CCNP COMPTIA DESIGN You are here: Home / 101 CCNP Labs Solutions / CCNP Lab 006 Solution: HSRP and Switch Security CCNP Lab 006 Solution: HSRP and Switch Security Lab Objective:
ABOUT CONTACT FAQ JOIN HOME CCNA CCNP COMPTIA DESIGN You are here: Home / 101 CCNP Labs Solutions / CCNP Lab 006 Solution: HSRP and Switch Security CCNP Lab 006 Solution: HSRP and Switch Security Lab Objective:
Lab Troubleshooting VTP Configuration
 Lab 4.4.3 Troubleshooting VTP Configuration Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask S1 VLAN 99 172.17.99.11 255.255.255.0 S2 VLAN 99 172.17.99.12 255.255.255.0
Lab 4.4.3 Troubleshooting VTP Configuration Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask S1 VLAN 99 172.17.99.11 255.255.255.0 S2 VLAN 99 172.17.99.12 255.255.255.0
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab Configuring HSRP and GLBP Topology
 Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1
Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1
Initial Configuration for the Switch
 Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Configuring VLANs. Finding Feature Information. Prerequisites for VLANs
 Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Lab 1. CLI Navigation. Scenario. Initial Configuration for R1
 Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
CISCO SWITCH BEST PRACTICES GUIDE
 CISCO SWITCH BEST PRACTICES GUIDE Table of Contents (After Clicking Link Hit HOME to Return to TOC) 1) Add Hostname... 2 2) Add Username and Password... 2 3) Create Secret Password... 2 4) Encrypt Password...
CISCO SWITCH BEST PRACTICES GUIDE Table of Contents (After Clicking Link Hit HOME to Return to TOC) 1) Add Hostname... 2 2) Add Username and Password... 2 3) Create Secret Password... 2 4) Encrypt Password...
Chapter 4 Lab 4-2 Multiple Spanning Tree INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 4 Lab 4-2 Multiple Spanning Tree INSTRUCTOR VERSION Topology Objectives Implement Multiple Spanning Tree Leverage VTP version 3 with MST Background Cisco s Per VLAN Spanning Tree
CCNPv7.1 SWITCH Chapter 4 Lab 4-2 Multiple Spanning Tree INSTRUCTOR VERSION Topology Objectives Implement Multiple Spanning Tree Leverage VTP version 3 with MST Background Cisco s Per VLAN Spanning Tree
Policy Based Routing with the Multiple Tracking Options Feature Configuration Example
 Policy Based Routing with the Multiple Tracking Options Feature Configuration Example Document ID: 48003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
Policy Based Routing with the Multiple Tracking Options Feature Configuration Example Document ID: 48003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
SWITCH Lab Guide Labs powered by
 SWITCH Lab Guide 300-115 ii SWITCH 300-115 Lab Guide LM20170908/BV1.0 iii 25 C e n tur y Blvd., S te. 5 0 0, N a s hvill e, T N 37214 B o s o n.c o m To perform the labs referenced in this book, please
SWITCH Lab Guide 300-115 ii SWITCH 300-115 Lab Guide LM20170908/BV1.0 iii 25 C e n tur y Blvd., S te. 5 0 0, N a s hvill e, T N 37214 B o s o n.c o m To perform the labs referenced in this book, please
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example
 IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
Lab Configuring IPv6 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
(Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
Skills Assessment (OSPF) Student Training Exam
 Skills Assessment (OSPF) Student Training Exam Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 17 Addressing Table Assessment Objectives Device
Skills Assessment (OSPF) Student Training Exam Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 17 Addressing Table Assessment Objectives Device
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Skills Assessment (EIGRP) Student Training Exam
 Skills Assessment (EIGRP) Student Training Exam Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 16 Addressing Table Assessment Objectives Device
Skills Assessment (EIGRP) Student Training Exam Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 16 Addressing Table Assessment Objectives Device
Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram
 Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram Default Cisco Terminal Options: 9600 bits/second No hardware flow control 8-bit ASCII No parity 1 stop bit Setting
Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram Default Cisco Terminal Options: 9600 bits/second No hardware flow control 8-bit ASCII No parity 1 stop bit Setting
Configuring the WMIC for the First Time
 Configuring the WMIC for the First Time This document describes how to configure basic settings on a Cisco Wireless Mobile Interface Card (WMIC) for the first time. Before You Start Before you install
Configuring the WMIC for the First Time This document describes how to configure basic settings on a Cisco Wireless Mobile Interface Card (WMIC) for the first time. Before You Start Before you install
CCNA Semester 3 labs. Part 1 of 1 Labs for chapters 1 8
 CCNA Semester 3 labs Part 1 of 1 Labs for chapters 1 8 2.1.2.12 Lab - Building a Switched Network with Redundant Links 2.3.2.3 Lab - Configuring Rapid PVST+, PortFast and BPDU Guard 2.4.3.4 Lab - Configuring
CCNA Semester 3 labs Part 1 of 1 Labs for chapters 1 8 2.1.2.12 Lab - Building a Switched Network with Redundant Links 2.3.2.3 Lab - Configuring Rapid PVST+, PortFast and BPDU Guard 2.4.3.4 Lab - Configuring
Lab Catalyst 2950T and 3550 Series VTP Domain and VLAN Trunking
 Lab 2.9.2 Catalyst 2950T and 3550 Series VTP Domain and VLAN Trunking Objective Configure a VLAN trunk between two Cisco Catalyst WS-C2950T-24-EI switches and a Cisco Catalyst WS-C3550-24-EMI switch in
Lab 2.9.2 Catalyst 2950T and 3550 Series VTP Domain and VLAN Trunking Objective Configure a VLAN trunk between two Cisco Catalyst WS-C2950T-24-EI switches and a Cisco Catalyst WS-C3550-24-EMI switch in
Configuring VLANs. Finding Feature Information. Prerequisites for VLANs
 Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 8 Monitoring VLANs, page 22 Where to Go Next,
Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 8 Monitoring VLANs, page 22 Where to Go Next,
Retake - Skills Assessment Student Training (Answer Key)
 Retake - Skills Assessment Student Training (Answer Key) Name:. Topology Assessment Objectives Part 1: Develop the IPv4 Address Scheme (15 points, 0 minutes) Part 2: Configure Device IPv4 and Security
Retake - Skills Assessment Student Training (Answer Key) Name:. Topology Assessment Objectives Part 1: Develop the IPv4 Address Scheme (15 points, 0 minutes) Part 2: Configure Device IPv4 and Security
TEST PROJECT IT NETWORK SYSTEMS ADMINISTRATION
 TEST PROJECT IT NETWORK SYSTEMS ADMINISTRATION Submitted by: Cisco Systems CONTENTS CONTENTS... 2 MODULE D - TROUBLESHOOTING... 3 CONTENTS... 3 INTRODUCTION... 3 DESCRIPTION OF PROJECT AND TASKS... 3 LOGICAL
TEST PROJECT IT NETWORK SYSTEMS ADMINISTRATION Submitted by: Cisco Systems CONTENTS CONTENTS... 2 MODULE D - TROUBLESHOOTING... 3 CONTENTS... 3 INTRODUCTION... 3 DESCRIPTION OF PROJECT AND TASKS... 3 LOGICAL
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Catalyst Switches for Microsoft Network Load Balancing Configuration Example
 Catalyst Switches for Microsoft Network Load Balancing Configuration Example Document ID: 107995 Contributed by Shashank Singh, Cisco TAC Engineer. Dec 19, 2013 Contents Introduction Prerequisites Requirements
Catalyst Switches for Microsoft Network Load Balancing Configuration Example Document ID: 107995 Contributed by Shashank Singh, Cisco TAC Engineer. Dec 19, 2013 Contents Introduction Prerequisites Requirements
Table of Contents. co Configuring InterVLAN Routing and ISL/802.1Q Trunking on a Catalyst 2900XL/3500XL/2950 Switch Using An Extern
 outing and ISL/802.1Q Trunking on a Catalyst 2900XL/3500XL/2 co Configuring InterVLAN Routing and ISL/802.1Q Trunking on a Catalyst 2900XL/3500XL/2950 Switch Using An Extern Table of Contents Configuring
outing and ISL/802.1Q Trunking on a Catalyst 2900XL/3500XL/2 co Configuring InterVLAN Routing and ISL/802.1Q Trunking on a Catalyst 2900XL/3500XL/2950 Switch Using An Extern Table of Contents Configuring
Cisco Press CCIE Practical Studies CCIE Practice Lab: Enchilada Solutions
 Cisco Press CCIE Practical Studies CCIE Practice Lab: Solutions Cisco Press CCIE Practical Studies CCIE Practice Lab: LAB Book Chapter Book Page The 18 1161 Overview... 3 Technical Details... 3 Table 54-1:
Cisco Press CCIE Practical Studies CCIE Practice Lab: Solutions Cisco Press CCIE Practical Studies CCIE Practice Lab: LAB Book Chapter Book Page The 18 1161 Overview... 3 Technical Details... 3 Table 54-1:
CCNA Semester 3 labs. Labs for chapters 2 10
 CCNA Semester 3 labs Labs for chapters 2 10 2.1.4.5 Lab - Configure Extended VLANs, VTP, and DTP 2.2.2.5 Lab - Troubleshooting Inter-VLAN Routing 3.1.2.12 Lab - Building a Switched Network with Redundant
CCNA Semester 3 labs Labs for chapters 2 10 2.1.4.5 Lab - Configure Extended VLANs, VTP, and DTP 2.2.2.5 Lab - Troubleshooting Inter-VLAN Routing 3.1.2.12 Lab - Building a Switched Network with Redundant
Seattle Cisco Users Group
 Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Using Setup Mode to Configure a Cisco Networking Device
 Using Setup Mode to Configure a Cisco Networking Device First Published: August 9, 2005 Last Updated: December 3, 2010 Setup mode provides an interactive menu to help you to create an initial configuration
Using Setup Mode to Configure a Cisco Networking Device First Published: August 9, 2005 Last Updated: December 3, 2010 Setup mode provides an interactive menu to help you to create an initial configuration
Sample Business Ready Branch Configuration Listings
 APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
Lab Catalyst 2950T and 3550 Series VTP Domain and VLAN Trunking
 Lab 2.3.7.1 Catalyst 2950T and 3550 Series VTP Domain and VLAN Trunking Objective Configure a VLAN trunk between two Cisco Catalyst WS-C2950T-24-EI switches and a Cisco Catalyst WS-C3550-24-EMI switch
Lab 2.3.7.1 Catalyst 2950T and 3550 Series VTP Domain and VLAN Trunking Objective Configure a VLAN trunk between two Cisco Catalyst WS-C2950T-24-EI switches and a Cisco Catalyst WS-C3550-24-EMI switch
CCNA Semester 1 labs. Part 1 of 2 Labs for chapters 1 7
 CCNA Semester 1 labs Part 1 of 2 Labs for chapters 1 7 2.3.3.3 Lab - Building a Simple Network 2.3.3.4 Lab - Configuring a Switch Management Address 3.4.1.2 Lab - Using Wireshark to View Network Traffic
CCNA Semester 1 labs Part 1 of 2 Labs for chapters 1 7 2.3.3.3 Lab - Building a Simple Network 2.3.3.4 Lab - Configuring a Switch Management Address 3.4.1.2 Lab - Using Wireshark to View Network Traffic
Skills Assessment (EIGRP) Student Training Exam
 Skills Assessment (EIGRP) Student Training Exam Topology Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Device Interface IP Address Subnet
Skills Assessment (EIGRP) Student Training Exam Topology Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Device Interface IP Address Subnet
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
VLAN Configuration. Understanding VLANs CHAPTER
 CHAPTER 11 This chapter describes how to configure normal-range VLANs (VLAN IDs 1 to 1005) and extended-range VLANs (VLAN IDs 1006 to 4094) on the CGR 2010 ESM. It includes information about VLAN membership
CHAPTER 11 This chapter describes how to configure normal-range VLANs (VLAN IDs 1 to 1005) and extended-range VLANs (VLAN IDs 1006 to 4094) on the CGR 2010 ESM. It includes information about VLAN membership
Netw 3000 VLAN 1 LAB Darlene Redmond Ryan Gamblin January 19 th 2012
 Netw 3000 VLAN 1 LAB Darlene Redmond Ryan Gamblin January 19 th 2012 3. Attach a workstation to the Management VLAN and demonstrate a successful login to the switch at the privileged exec mode, with a
Netw 3000 VLAN 1 LAB Darlene Redmond Ryan Gamblin January 19 th 2012 3. Attach a workstation to the Management VLAN and demonstrate a successful login to the switch at the privileged exec mode, with a
