Kaspersky PURE 2.0. Anti-Banner: lists of allowed and blocked web-addresses
|
|
|
- Robert Rice
- 6 years ago
- Views:
Transcription
1 Anti-Banner: lists of allowed and blocked web-addresses
2 Content Anti-Banner. Lists of allowed and blocked web-addresses... 2 Creating the list of blocked and allowed banner addresses... 2 Exporting and importing the lists of addresses
3 Anti-Banner. Lists of allowed and blocked web-addresses Creating the list of blocked and allowed banner addresses Additionally to the scan methods Anti-Banner checks the banner addresses with the masks from the list of blocked or allowed addresses if they are used. Using the lists of blocked and allowed banners addresses, you can allow banners to be downloaded for a specified group of addresses and block them for another group. Create a list of blocked address masks to let Anti-Banner block download and display of banners from the addresses that correspond to those masks. Create a list of allowed address masks to let Anti- Banner download and display banners from the addresses that correspond to those masks. To create a list of blocked addresses, do the following: 1. In the right part of the Settings window of the Anti-Banner component, in the Additional section, check the Use the list of blocked URLs box. 2. Click the Settings 3. Click the Add button, to add a new mask. 2 7
4 4. In the Address mask (URL) window enter a blocked banner mask and click the OK 5. When all the necessary masks are added, in the Blocked URLs window click the OK 6. In the Settings window click the Apply You do not have to delete a mask to stop using it, unchecking the corresponding box next to it will be sufficient for the purpose. To create and use the list of allowed addresses, perform the following actions: 1. In the right part of the Settings window of the Anti-Banner component, in the Additional section, check the Use the list of allowed URLs box. 2. Click the Settings 3 7
5 3. Click the Add button, to add a new mask. 4. In the Address mask (URL) window enter an allowed banner mask and click the OK 5. When all the necessary masks are added, in the Allowed URLs window click the OK 4 7
6 6. In the Settings window click the Apply To exclude a mask from the list of allowed URLs, uncheck the corresponding box next to the address mask. Exporting and importing the lists of addresses After you have created the lists of allowed or blocked banner addresses, you can use them repeatedly: for example, export banner addresses to a similar list on another computer with Kaspersky PURE installed on it. To do this: 1. Make export copy records from the list into a file. 2. Move the file you have saved to another computer (for example, send it by or use a removable data medium). 3. Make import add the records from the file to the list of the same type on another computer. While exporting the list, you can copy either the selected list element only, or the entire list. While importing the list, you can add the new elements to the existing list, or replace the existing list with the one being imported. 5 7
7 To export banner addresses from the list of allowed or blocked URLs, perform the following steps: 1. In the right part of the Settings window of the Anti-Banner component, in the Additional section, click the Settings button located in the line with the name of the list from which you should copy addresses into a file (list of blocked or allowed URLs). 2. In the window that opens, check the boxes next to the addresses that you need to include in the file. 3. Click the Export 4. In the window, take one of the following actions: click the Yes button if you need to include only selected addresses in the file; click the No button if you need to include the entire list in the file. 6 7
8 5. In the Save as window, enter a name for the file you want to save and click the Save To import banner addresses from a file to the list of allowed or blocked URLs, perform the following actions: 1. In the right part of the Settings window of the Anti-Banner component, in the Additional section, click the Settings button located in the line with the name of the list into which you need to add addresses from a file (list of allowed or blocked URLs). 2. In the window that opens, click the Import 3. If the list is not empty, a window opens offering you to add items to be imported. In this window, take one of the following actions: click the Yes button if you want to add records from the file into the list; click the No button if you want to replace the existing records with the list from the file. 4. In the Open file window, select the file with the list of records that you want to import and click the Open 5. Click the OK 6. In the Settings window click the OK 7 7
Kaspersky PURE 2.0. Exclusions
 Exclusions Content Exclusions... 2 Trusted zone... 2 Creating the list of trusted applications... 3 Creating exclusion rules... 5 1 10 Exclusions Trusted zone Trusted zone is a list of objects created
Exclusions Content Exclusions... 2 Trusted zone... 2 Creating the list of trusted applications... 3 Creating exclusion rules... 5 1 10 Exclusions Trusted zone Trusted zone is a list of objects created
Kaspersky PURE 2.0. Mail Anti-Virus: security levels
 Mail Anti-Virus: security levels Content Mail Anti-Virus. Security levels... 2 Operation algorithm of Mail Anti-Virus... 2 Security levels of Mail Anti-Virus... 2 Customizing security level... 4 Creating
Mail Anti-Virus: security levels Content Mail Anti-Virus. Security levels... 2 Operation algorithm of Mail Anti-Virus... 2 Security levels of Mail Anti-Virus... 2 Customizing security level... 4 Creating
KASPERSKY LAB. Kaspersky Administration Kit version 6.0. Reference Book
 KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
Internet Security Mail Anti-Virus
 Internet Security 2012 Mail Anti-Virus Table of Contents Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus... 2 Changing Mail
Internet Security 2012 Mail Anti-Virus Table of Contents Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus... 2 Changing Mail
ABF Software Issues Caused by Anti-Virus Programs
 ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
Small Office Security 2. Scan PC for viruses and vulnerabilities
 Small Office Security 2 Scan PC for viruses and vulnerabilities Table of content Table of content... 1 Scan PC for viruses... 2 What is Scan... 2 Starting scan... 2 Starting scan from the main application
Small Office Security 2 Scan PC for viruses and vulnerabilities Table of content Table of content... 1 Scan PC for viruses... 2 What is Scan... 2 Starting scan... 2 Starting scan from the main application
Table of contents. Pure PHP/ASP Upload AddOn Pack Manual DMXzone
 Table of contents Table of contents... 1 About Pure PHP/ASP Upload Add-on Pack... 2 Features in Detail... 3 The Basics: Using Delete File(s) Before Record Server Behavior... 8 Advanced: Using Delete File
Table of contents Table of contents... 1 About Pure PHP/ASP Upload Add-on Pack... 2 Features in Detail... 3 The Basics: Using Delete File(s) Before Record Server Behavior... 8 Advanced: Using Delete File
Small Office Security 2. Mail Anti-Virus
 Small Office Security 2 Mail Anti-Virus Table of content Table of content... 1 Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/Disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus...
Small Office Security 2 Mail Anti-Virus Table of content Table of content... 1 Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/Disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus...
Using McAfee VirusScan Enterprise 7.0 and 7.1 with Cisco CallManager. Application Note
 Using McAfee VirusScan Enterprise 7.0 and 7.1 with Cisco CallManager Application Note Copyright 2003 Cisco Systems, Inc. Page 1 of 16 August 16, 2004 Table of Contents Introduction... 3 Installation...
Using McAfee VirusScan Enterprise 7.0 and 7.1 with Cisco CallManager Application Note Copyright 2003 Cisco Systems, Inc. Page 1 of 16 August 16, 2004 Table of Contents Introduction... 3 Installation...
pure::variants Server Support Plug-In Manual
 pure-systems GmbH Copyright 2003-2008 pure-systems GmbH 2008 Table of Contents 1. Introduction... 1 2. Create A New Variant Server Project... 1 3. Import An Existing Variant Server Project... 2 4. Change
pure-systems GmbH Copyright 2003-2008 pure-systems GmbH 2008 Table of Contents 1. Introduction... 1 2. Create A New Variant Server Project... 1 3. Import An Existing Variant Server Project... 2 4. Change
Internet Security Application Control
 Internet Security 2012 Application Control Table of Contents Application Control... 2 What is Application Control... 2 Operational algorithm of Application Control... 2 Enabling/disabling Application Control...
Internet Security 2012 Application Control Table of Contents Application Control... 2 What is Application Control... 2 Operational algorithm of Application Control... 2 Enabling/disabling Application Control...
Creating an Accessible Word Document. PC Computer. Revised November 27, Adapted from resources created by the Sonoma County Office of Education
 Creating an Accessible Word Document PC Computer Revised November 27, 2018 Adapted from resources created by the Sonoma County Office of Education Title the Document Add an official title to the document
Creating an Accessible Word Document PC Computer Revised November 27, 2018 Adapted from resources created by the Sonoma County Office of Education Title the Document Add an official title to the document
Export SharePoint Sites
 Export SharePoint Sites Export SharePoint Sites wizard is designed to assist with exporting SharePoint sites to a specified PWA. To start the wizard click File Export Export SharePoint Sites. Step 1 -
Export SharePoint Sites Export SharePoint Sites wizard is designed to assist with exporting SharePoint sites to a specified PWA. To start the wizard click File Export Export SharePoint Sites. Step 1 -
There are two aspects to the interface between BankLink Practice and Concept Cash Manager:
 Concept Cash Manager There are two aspects to the interface between BankLink Practice and Concept Cash Manager: Copying a chart from Concept Cash Manager into BankLink Practice Transferring transactions
Concept Cash Manager There are two aspects to the interface between BankLink Practice and Concept Cash Manager: Copying a chart from Concept Cash Manager into BankLink Practice Transferring transactions
Creating an Allocation Rule
 Works Allocation Profiles and Rules This guide provides the information needed to maintain allocation profiles and rules. You must be a Program Administrator or Accountant to perform these tasks. Within
Works Allocation Profiles and Rules This guide provides the information needed to maintain allocation profiles and rules. You must be a Program Administrator or Accountant to perform these tasks. Within
Systemair MagiCAD plugin for Revit
 User s Guide 1 Contents Chapter 1. General 3 About this document... 3 Installing the software... 3 Required third-party software... 3 Installation... 3 Starting the program... 4 Chapter 2. Functions 5
User s Guide 1 Contents Chapter 1. General 3 About this document... 3 Installing the software... 3 Required third-party software... 3 Installation... 3 Starting the program... 4 Chapter 2. Functions 5
Installation Guide of Kaspersky Tablet Security *** Notice
 Installation Guide of Kaspersky Tablet Security *** Notice To protect your purchase right and to receive service and information, the scratch card contains Serial Number. Please use this Serial Number
Installation Guide of Kaspersky Tablet Security *** Notice To protect your purchase right and to receive service and information, the scratch card contains Serial Number. Please use this Serial Number
Data Quality : Profile Analysis On Join Condition
 Name of Solution: Data Quality : Profile Analysis On Join Condition Business Requirement: The purpose of this solution is to explain what is Join profile analysis and how it can be used. Solution URL:
Name of Solution: Data Quality : Profile Analysis On Join Condition Business Requirement: The purpose of this solution is to explain what is Join profile analysis and how it can be used. Solution URL:
Anti-Virus Interface of Kaspersky
 Anti-Virus 2012 Interface of Kaspersky Anti-Virus 2012 Table of Contents Interface of Kaspersky Anti-Virus 2012... 2 Application icon in the Microsoft Windows taskbar notification area... 2 Main window
Anti-Virus 2012 Interface of Kaspersky Anti-Virus 2012 Table of Contents Interface of Kaspersky Anti-Virus 2012... 2 Application icon in the Microsoft Windows taskbar notification area... 2 Main window
Accessing your Check Point VPN
 NOTE: The VPN only provides remote access to the network, any required native applications will need to be compatible with your local system. STEP 1 Open your Internet Explorer web browser and enter the
NOTE: The VPN only provides remote access to the network, any required native applications will need to be compatible with your local system. STEP 1 Open your Internet Explorer web browser and enter the
Vision Screener. Short Manual 8. Downloading software updates. Plusoptix GmbH Neumeyerstrasse Nuremberg Germany
 Vision Screener Short Manual 8 Downloading software updates Plusoptix GmbH Neumeyerstrasse 48 90411 Nuremberg Germany www.plusoptix.com Edition: 09/17/2018 Table of Contents 1 Downloading software updates
Vision Screener Short Manual 8 Downloading software updates Plusoptix GmbH Neumeyerstrasse 48 90411 Nuremberg Germany www.plusoptix.com Edition: 09/17/2018 Table of Contents 1 Downloading software updates
IBM. Migration Cookbook. Migrating from License Metric Tool and Tivoli Asset Discovery for Distributed 7.5 to License Metric Tool 9.
 IBM License Metric Tool 9.x Migration Cookbook Migrating from License Metric Tool and Tivoli Asset Discovery for Distributed 7.5 to License Metric Tool 9.x IBM IBM License Metric Tool 9.x Migration Cookbook
IBM License Metric Tool 9.x Migration Cookbook Migrating from License Metric Tool and Tivoli Asset Discovery for Distributed 7.5 to License Metric Tool 9.x IBM IBM License Metric Tool 9.x Migration Cookbook
Install Kaspersky Endpoint Security for Mac Version b (This user guide is applicable to Mac OS X 10.9 macos )
 Install Kaspersky Endpoint Security for Mac Version 10.2.1.319b (This user guide is applicable to Mac OS X 10.9 macos 10.14.) Contents A. Download Kaspersky Endpoint Security 10 for Mac... 1 B. Install
Install Kaspersky Endpoint Security for Mac Version 10.2.1.319b (This user guide is applicable to Mac OS X 10.9 macos 10.14.) Contents A. Download Kaspersky Endpoint Security 10 for Mac... 1 B. Install
This module gives the user the ability to create a file to transfer data from CAMAvision to another computer system such as the tax administration
 This module gives the user the ability to create a file to transfer data from CAMAvision to another computer system such as the tax administration program. Typically values, reconciliation and exemption
This module gives the user the ability to create a file to transfer data from CAMAvision to another computer system such as the tax administration program. Typically values, reconciliation and exemption
IDVisor Pro ID Scanner. User s Guide AGE VERIFICATION MACHINE
 IDVisor Pro ID Scanner User s Guide AGE VERIFICATION MACHINE IDVisor Pro User s Guide Page 2 of 20 Copyright Copyright 2002-2015 TokenWorks, Inc. Printed in the USA Information in this document is subject
IDVisor Pro ID Scanner User s Guide AGE VERIFICATION MACHINE IDVisor Pro User s Guide Page 2 of 20 Copyright Copyright 2002-2015 TokenWorks, Inc. Printed in the USA Information in this document is subject
OneSecure VPN Remote User Installation & Configuration Guide
 OneSecure VPN Remote User Installation & Configuration Guide 3/11/2015 CONTENTS Download Client Software 02 Install Client Software 03 Enable Client Software 07 Configure the Connection 08 WELCOME Welcome
OneSecure VPN Remote User Installation & Configuration Guide 3/11/2015 CONTENTS Download Client Software 02 Install Client Software 03 Enable Client Software 07 Configure the Connection 08 WELCOME Welcome
Software Keycode Installation Guide
 Software Keycode Installation Guide 2002 Nortel Networks Corporation PO909884 Issue 03 Software Keycode Installation Guide Introduction This document provides instructions for enabling Software Keycodes
Software Keycode Installation Guide 2002 Nortel Networks Corporation PO909884 Issue 03 Software Keycode Installation Guide Introduction This document provides instructions for enabling Software Keycodes
& More Date Range Gadgets Date Depends on the Report Run Date
 Gadgets Email & More Date Range Gadgets Allows you to choose a specific date, before or after a date or a range of dates using the Workflows calendar gadget. Date Depends on the Report Run Date Allows
Gadgets Email & More Date Range Gadgets Allows you to choose a specific date, before or after a date or a range of dates using the Workflows calendar gadget. Date Depends on the Report Run Date Allows
EPIQ & Affiniti Report Template Editor
 EPIQ & Affiniti Report Template Editor QuickGuide About the Report Template Editor Available on and off-cart (PC only) for EPIQ Evolution.0 and Affiniti AOS.5 systems and higher. The Report Template Editor
EPIQ & Affiniti Report Template Editor QuickGuide About the Report Template Editor Available on and off-cart (PC only) for EPIQ Evolution.0 and Affiniti AOS.5 systems and higher. The Report Template Editor
Accomplish CashManager
 Accomplish CashManager This information supports the interface between BankLink Practice 5.4 or later, and Accomplish Cash Manager version 10 or later. There are two aspects to the interface between BankLink
Accomplish CashManager This information supports the interface between BankLink Practice 5.4 or later, and Accomplish Cash Manager version 10 or later. There are two aspects to the interface between BankLink
VoiceThread QuickGuide: Groups and Contacts Overview
 Office of Distance Education VoiceThread QuickGuide: Groups and Contacts Overview Use this document if a VoiceThread has been created and is ready to be shared with others. VoiceThread Group feature allows
Office of Distance Education VoiceThread QuickGuide: Groups and Contacts Overview Use this document if a VoiceThread has been created and is ready to be shared with others. VoiceThread Group feature allows
HOW TO CONFIGURE AND USE A TRAUMACAD PLUG-IN WITH PHILIPS ISITE
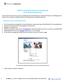 HOW TO CONFIGURE AND USE A TRAUMACAD PLUG-IN WITH PHILIPS ISITE This document describes the process of configuring the TraumaCad plug-in inside isite Enterprise or Radiology which allows a user to export
HOW TO CONFIGURE AND USE A TRAUMACAD PLUG-IN WITH PHILIPS ISITE This document describes the process of configuring the TraumaCad plug-in inside isite Enterprise or Radiology which allows a user to export
Crot. Installation instructions & Tutorial. Anti plagiarism solutions. Desktop version. (c) Crot: Anti plagiarism solutions
 Crot Anti plagiarism solutions Desktop version Installation instructions & Tutorial This document is under development. Please send all your enquiries to moodlecrot[@]gmail.com Contents Installation...
Crot Anti plagiarism solutions Desktop version Installation instructions & Tutorial This document is under development. Please send all your enquiries to moodlecrot[@]gmail.com Contents Installation...
Operator Manual Maintenance Tool - Browse Tool
 Maintenance Tool Browse Tool Operator Manual Maintenance Tool Browse Tool Product Version: 4.6 Version of this manual: 2.0.3 2016 Inepro B.V. All rights reserved Table of Contents What is the Browse Tool?
Maintenance Tool Browse Tool Operator Manual Maintenance Tool Browse Tool Product Version: 4.6 Version of this manual: 2.0.3 2016 Inepro B.V. All rights reserved Table of Contents What is the Browse Tool?
VPN Service Access Manual(windows7)
 VPN Service Access Manual(windows7) 0 This is a user manual for accessing VPN under the following terminal environments. Windows 7 SP1 with BIG-IP Edge Client P 2 Windows 7 SP1 with IE 9.0 P 7 Windows
VPN Service Access Manual(windows7) 0 This is a user manual for accessing VPN under the following terminal environments. Windows 7 SP1 with BIG-IP Edge Client P 2 Windows 7 SP1 with IE 9.0 P 7 Windows
Web Client Installation under Windows 7 and Windows Vista
 Web Client Installation under Windows 7 and Windows Vista Due to extended and enhanced security features of Windows 7, Windows Vista, and Internet Explorer, the installation of the Web client is different
Web Client Installation under Windows 7 and Windows Vista Due to extended and enhanced security features of Windows 7, Windows Vista, and Internet Explorer, the installation of the Web client is different
Trusted Stackware series. Rev D.O.I-Net Co., Ltd. Document No:TST E
 Generic USB Flash Memory Device Plug -in for TruGate User s Guide Rev. 1.0.4 D.O.I-Net Co., Ltd. Document No:TST-10-005E Disclaimers 1. D.O.I-Net Co., Ltd. shall not take responsibility for any direct
Generic USB Flash Memory Device Plug -in for TruGate User s Guide Rev. 1.0.4 D.O.I-Net Co., Ltd. Document No:TST-10-005E Disclaimers 1. D.O.I-Net Co., Ltd. shall not take responsibility for any direct
VPN Service Access Manual(windows10)
 VPN Service Access Manual(windows10) 0 This is a user manual for accessing VPN under the following terminal environments. Windows 10 with BIG-IP Edge Client P 2 Windows 10 with IE 11.0 P 7 Windows 10 with
VPN Service Access Manual(windows10) 0 This is a user manual for accessing VPN under the following terminal environments. Windows 10 with BIG-IP Edge Client P 2 Windows 10 with IE 11.0 P 7 Windows 10 with
Webmail: Basics. Folders:
 Webmail: Basics To use webmail: Webmail can be accessed from any computer that has an internet connection. Type webmail.osceola.k12.wi.us in the address bar. (Note that there is no www preceding this URL:
Webmail: Basics To use webmail: Webmail can be accessed from any computer that has an internet connection. Type webmail.osceola.k12.wi.us in the address bar. (Note that there is no www preceding this URL:
A weekly Spa Day for your Computer
 A weekly Spa Day for your Computer To keep your PC running smoothly and clean, I recommend this procedure on a weekly basis: 1. ATF Cleaner Double Click on ATF Cleaner on your desktop, Check Select All
A weekly Spa Day for your Computer To keep your PC running smoothly and clean, I recommend this procedure on a weekly basis: 1. ATF Cleaner Double Click on ATF Cleaner on your desktop, Check Select All
MYOB Accountants Office
 MYOB Accountants Office There are two aspects to the interface between BankLink Practice and MYOB AO: Copying the client chart from MYOB AO into BankLink Practice Transferring coded transactions from BankLink
MYOB Accountants Office There are two aspects to the interface between BankLink Practice and MYOB AO: Copying the client chart from MYOB AO into BankLink Practice Transferring coded transactions from BankLink
How to install Internet Security for Android app
 How to install Internet Security for Android app 1. Go to Google Play Store app. 2. In the dialog window enter Kaspersky Mobile Antivirus: Web Security & AppLock. Tap INSTALL to allow the app to install
How to install Internet Security for Android app 1. Go to Google Play Store app. 2. In the dialog window enter Kaspersky Mobile Antivirus: Web Security & AppLock. Tap INSTALL to allow the app to install
ForeScout Extended Module for Symantec Endpoint Protection
 ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
D-Link (Europe) Ltd. 4 th Floor Merit House Edgware Road London HA7 1DP U.K. Tel: Fax:
 Product: DFL-500 Internet Firewall Index Setup Introduction...2 Set Up Using Web Configurator...3 Setting Up Internal IP Address using CLI...4 Setting UP External IP Address Manually Using CLI...4 How
Product: DFL-500 Internet Firewall Index Setup Introduction...2 Set Up Using Web Configurator...3 Setting Up Internal IP Address using CLI...4 Setting UP External IP Address Manually Using CLI...4 How
Lab - Configure Browser Settings in Windows 8
 Introduction In this lab, you will configure browser settings in Microsoft Internet Explorer. Recommended Equipment A computer with Windows 8 An Internet connection Step 1: Set Internet Explorer as the
Introduction In this lab, you will configure browser settings in Microsoft Internet Explorer. Recommended Equipment A computer with Windows 8 An Internet connection Step 1: Set Internet Explorer as the
Silk Test Silk4NET Tutorial
 Silk Test 14.0 Silk4NET Tutorial Micro Focus 575 Anton Blvd., Suite 510 Costa Mesa, CA 92626 Copyright Micro Focus 2013. All rights reserved. Portions Copyright 1992-2009 Borland Software Corporation (a
Silk Test 14.0 Silk4NET Tutorial Micro Focus 575 Anton Blvd., Suite 510 Costa Mesa, CA 92626 Copyright Micro Focus 2013. All rights reserved. Portions Copyright 1992-2009 Borland Software Corporation (a
Electronic Portfolios with Google Sites Create Your Site
 Create a Google Account- Follow steps at http://sites.google.co m (sign up, and sign in) Create Your Site Click create site 1.Keep the blank template 2.Name your site 3.Type the code 4.Click create site
Create a Google Account- Follow steps at http://sites.google.co m (sign up, and sign in) Create Your Site Click create site 1.Keep the blank template 2.Name your site 3.Type the code 4.Click create site
Manual Physical Inventory Upload Created on 3/17/2017 7:37:00 AM
 Created on 3/17/2017 7:37:00 AM Table of Contents... 1 Page ii Procedure After completing this topic, you will be able to manually upload physical inventory. Navigation: Microsoft Excel > New Workbook
Created on 3/17/2017 7:37:00 AM Table of Contents... 1 Page ii Procedure After completing this topic, you will be able to manually upload physical inventory. Navigation: Microsoft Excel > New Workbook
Content... 2 CSSNEXPORTORDER. structure
 Table of Content... 2 Overview CSSNEXPORTORDER... 4... CSSN_STOP_EXPORT_IF_SUCCESSFULL 3... 4 General URL structure...... 3 5 FTP... 6 Email... 7 Application..... 8 The CSSN applications can export data
Table of Content... 2 Overview CSSNEXPORTORDER... 4... CSSN_STOP_EXPORT_IF_SUCCESSFULL 3... 4 General URL structure...... 3 5 FTP... 6 Email... 7 Application..... 8 The CSSN applications can export data
Xtender. Activity Guide. P a g e 1 10
 Xtender Activity Guide P a g e 1 10 ACTIVITY 1.1 LOGIN & BASIC NAVIGATION To understand how to access Xtender and the basic elements we want you to have time to navigate in the tool using the training
Xtender Activity Guide P a g e 1 10 ACTIVITY 1.1 LOGIN & BASIC NAVIGATION To understand how to access Xtender and the basic elements we want you to have time to navigate in the tool using the training
Xpy4002-KX, Xpy4004-KX and Xpy8004-KX. setup with DDNS and mobile application
 Xpy4002-KX, Xpy4004-KX and Xpy8004-KX setup with DDNS and mobile application Xpy4002-KX, Xpy4004-KX and Xpy8004-KX setup with DDNS and mobile application Preliminary steps: 1. 2. 3. Nexxt Solutions DVR
Xpy4002-KX, Xpy4004-KX and Xpy8004-KX setup with DDNS and mobile application Xpy4002-KX, Xpy4004-KX and Xpy8004-KX setup with DDNS and mobile application Preliminary steps: 1. 2. 3. Nexxt Solutions DVR
Chemotaxis Data Processing: Creating an Analysis Job
 essenbioscience.com/incucyte TECH NOTE IncuCyte ZOOM Live-Cell Imaging System Chemotaxis Data Processing: Creating an Analysis Job Data processing analyzes and summarizes qualitative images into quantitative
essenbioscience.com/incucyte TECH NOTE IncuCyte ZOOM Live-Cell Imaging System Chemotaxis Data Processing: Creating an Analysis Job Data processing analyzes and summarizes qualitative images into quantitative
Agilent Seahorse XF Imaging & Cell Counting Software
 Tech Note Agilent Seahorse XF Imaging & Cell Counting Software Adjusting Analysis Parameters in BioTek Gen5 for Difficult to Count Cell Lines This document describes how to use BioTek s Gen5 software to
Tech Note Agilent Seahorse XF Imaging & Cell Counting Software Adjusting Analysis Parameters in BioTek Gen5 for Difficult to Count Cell Lines This document describes how to use BioTek s Gen5 software to
Large images added to a webpage can have a detrimental effect to your site.
 1. Photo Resizing Large images added to a webpage can have a detrimental effect to your site. Large images are slow to load and can frustrate users of your site who may leave your site rather than wait
1. Photo Resizing Large images added to a webpage can have a detrimental effect to your site. Large images are slow to load and can frustrate users of your site who may leave your site rather than wait
Dell Latitude ST Best Practices Guide
 Dell Latitude ST Best Practices Guide This document describes optional changes that can be deployed on the Dell Latitude ST tablet to enhance performance. Several options are discussed in this document:
Dell Latitude ST Best Practices Guide This document describes optional changes that can be deployed on the Dell Latitude ST tablet to enhance performance. Several options are discussed in this document:
How to Make Videos and Export View Sequences
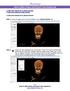 How to Make Videos and Export View Sequences Create view sequences in Volume Render Create view sequences with models Create view sequences in Volume Render Step 1: Open up image scan in Invivo5 software.
How to Make Videos and Export View Sequences Create view sequences in Volume Render Create view sequences with models Create view sequences in Volume Render Step 1: Open up image scan in Invivo5 software.
FUJITSU Cloud IaaS Trusted Public S5 Set & Delete Private IP Address Spaces
 FUJITSU Cloud IaaS Trusted Public S5 Set & Delete Private IP Address Spaces This guide describes the process for setting and deleting IaaS Trusted Public S5 Private IP Address Ranges How to Set Up a Private
FUJITSU Cloud IaaS Trusted Public S5 Set & Delete Private IP Address Spaces This guide describes the process for setting and deleting IaaS Trusted Public S5 Private IP Address Ranges How to Set Up a Private
How to create and edit a source reference
 How to create and edit a source reference Modified on: Tue, Jul 12, 2016 at 1:51 PM How to create a source reference 1. Click Sources in the navigation bar at the top of the screen to begin adding references
How to create and edit a source reference Modified on: Tue, Jul 12, 2016 at 1:51 PM How to create a source reference 1. Click Sources in the navigation bar at the top of the screen to begin adding references
User Guide. For version 0.5, January Download the latest version from jnetmap.sourceforge.net
 User Guide For version 0.5, January 2011 Download the latest version from jnetmap.sourceforge.net Table of Contents Introduction...1 Quick Start...1 Opening and saving files...1 Passwords...1 Editing a
User Guide For version 0.5, January 2011 Download the latest version from jnetmap.sourceforge.net Table of Contents Introduction...1 Quick Start...1 Opening and saving files...1 Passwords...1 Editing a
BDM ApplicationXTender Running Queries and Managing Student Data
 BDM ApplicationXTender Running Queries and Managing Student Data INFORMATION TECHNOLOGY SERVICES Table of Contents Overview - Banner Document Management (BDM) and ApplicationXTender 3 Accessing Banner
BDM ApplicationXTender Running Queries and Managing Student Data INFORMATION TECHNOLOGY SERVICES Table of Contents Overview - Banner Document Management (BDM) and ApplicationXTender 3 Accessing Banner
Silk Test Silk4NET Tutorial
 Silk Test 13.5 Silk4NET Tutorial Micro Focus 575 Anton Blvd., Suite 510 Costa Mesa, CA 92626 Copyright 2012 Micro Focus. All rights reserved. Portions Copyright 1992-2009 Borland Software Corporation (a
Silk Test 13.5 Silk4NET Tutorial Micro Focus 575 Anton Blvd., Suite 510 Costa Mesa, CA 92626 Copyright 2012 Micro Focus. All rights reserved. Portions Copyright 1992-2009 Borland Software Corporation (a
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Tutorial: set up of measurement recipe with database
 Tutorial: set up of measurement recipe with database This tutorial explains 1. how to create a recipe to perform repeated measurements at a given place on the wafer 2. how to make a data analysis routine
Tutorial: set up of measurement recipe with database This tutorial explains 1. how to create a recipe to perform repeated measurements at a given place on the wafer 2. how to make a data analysis routine
NAVAIR Aviation Logistics Environment (ALE)
 NAVAIR 6.8.4 Aviation Logistics Environment (ALE) Guide for Requesting System Access to DECision Knowledge Programming for Logistics Analysis and Technical Evaluation (DECKPLATE) Document Version: 1.0
NAVAIR 6.8.4 Aviation Logistics Environment (ALE) Guide for Requesting System Access to DECision Knowledge Programming for Logistics Analysis and Technical Evaluation (DECKPLATE) Document Version: 1.0
Monsters Template Installation Instructions
 Monsters Template Installation Instructions Thank using our Monsters Theme for Cherwell Service Management. Please follow the instructions below to install your new theme: *As with any business software
Monsters Template Installation Instructions Thank using our Monsters Theme for Cherwell Service Management. Please follow the instructions below to install your new theme: *As with any business software
Operating the COULTER COUNTER
 Coulter_User_protocol.doc Page 1 of 8 Operating the COULTER COUNTER Start the Computer Put on the Coulter Counter (right side of the machine) Log_in in WINDOWS XP (username and password) Start Multisizer
Coulter_User_protocol.doc Page 1 of 8 Operating the COULTER COUNTER Start the Computer Put on the Coulter Counter (right side of the machine) Log_in in WINDOWS XP (username and password) Start Multisizer
HP ALM Overview. Exercise Outline. Administration and Customization Lab Guide
 HP ALM 11.00 Administration and Customization Lab Guide Overview This Lab Guide contains the exercises for Administration and Customization of HP ALM 11 Essentials training. The labs are designed to enhance
HP ALM 11.00 Administration and Customization Lab Guide Overview This Lab Guide contains the exercises for Administration and Customization of HP ALM 11 Essentials training. The labs are designed to enhance
ULTRAVISION 3. Technical Guidelines Release 3.8R7. UltraVision, a complete UT and Phased Array inspection package!
 ULTRAVISION 3 Technical Guidelines Release 3.8R7 UltraVision, a complete UT and Phased Array inspection package! www.zetec.com Table of Content 1 Calibration Tool... 3 1.1 Import/Export TCG Improvement...
ULTRAVISION 3 Technical Guidelines Release 3.8R7 UltraVision, a complete UT and Phased Array inspection package! www.zetec.com Table of Content 1 Calibration Tool... 3 1.1 Import/Export TCG Improvement...
BANNER 9 QUICK NAVIGATION GUIDE
 Application Navigator Application Navigator provides a single interface to navigate the Banner 9 JAVA pages. It is a tool that allows you to go back and forth between the current Banner forms and the new
Application Navigator Application Navigator provides a single interface to navigate the Banner 9 JAVA pages. It is a tool that allows you to go back and forth between the current Banner forms and the new
Table of contents. Zip Processor 3.0 DMXzone.com
 Table of contents About Zip Processor 3.0... 2 Features In Detail... 3 Before you begin... 6 Installing the extension... 6 The Basics: Automatically Zip an Uploaded File and Download it... 7 Introduction...
Table of contents About Zip Processor 3.0... 2 Features In Detail... 3 Before you begin... 6 Installing the extension... 6 The Basics: Automatically Zip an Uploaded File and Download it... 7 Introduction...
This program assumes you have basic knowledge or htaccess redirection.
 Instructions Intro 404bypass is designed to help you avoid 404 errors by generating a redirect file for your website. This is especially helpful when a redesign leads to pages being assigned a new URL.
Instructions Intro 404bypass is designed to help you avoid 404 errors by generating a redirect file for your website. This is especially helpful when a redesign leads to pages being assigned a new URL.
ColorCert Custom Mediastrips
 ColorCert Custom Mediastrips Version History August 7th 2015 - Version 1.0 March 31 st 2017 - Version 1.1 (Updated support links) Scope This document describes the definition and usage of Custom Mediastrips.
ColorCert Custom Mediastrips Version History August 7th 2015 - Version 1.0 March 31 st 2017 - Version 1.1 (Updated support links) Scope This document describes the definition and usage of Custom Mediastrips.
J. Vilmsi Tallinn Estonia Flak Installation Guide
 Flak Installation Guide Table of Contents Terms and Definitions... 3 Flak description... 4 Flak's functions... 4 System Requirements for Flak Device... 4 Installation of Drivers... 5 Device Compatibility
Flak Installation Guide Table of Contents Terms and Definitions... 3 Flak description... 4 Flak's functions... 4 System Requirements for Flak Device... 4 Installation of Drivers... 5 Device Compatibility
Intelligence2day. Administration Manual
 Intelligence2day Administration Manual Comintelli 2017 Contents 1. Introduction... 3 2. Topics... 4 2.1 Add a subtopic... 4 2.2 Classification: Define topic rules... 5 2.2.1 Add rules that includes keywords...
Intelligence2day Administration Manual Comintelli 2017 Contents 1. Introduction... 3 2. Topics... 4 2.1 Add a subtopic... 4 2.2 Classification: Define topic rules... 5 2.2.1 Add rules that includes keywords...
Configuring Data Masking. Version: 7.3
 Configuring Data Masking Version: 7.3 Copyright 2015 Intellicus Technologies This document and its content is copyrighted material of Intellicus Technologies. The content may not be copied or derived from,
Configuring Data Masking Version: 7.3 Copyright 2015 Intellicus Technologies This document and its content is copyrighted material of Intellicus Technologies. The content may not be copied or derived from,
Time Zones, Access Groups, Cards and Users. Technical Support Engineering Rosslare Security NA For more information please see
 Time Zones, Access Groups, Cards and Users Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.com This Guide will discuss how to manage user access. This will
Time Zones, Access Groups, Cards and Users Technical Support Engineering Rosslare Security NA For more information please see www.axtraxng.com This Guide will discuss how to manage user access. This will
Gurusoft DSQ: User Guide Self Registration
 2018 Gurusoft DSQ: User Guide Self Registration Gurusoft Pte Ltd Version: v1.00 2/9/2018 Table of Contents Self Registration... 2 User ID and Password... 3 How to Log In... 3 How to Add/Delete a Mall and
2018 Gurusoft DSQ: User Guide Self Registration Gurusoft Pte Ltd Version: v1.00 2/9/2018 Table of Contents Self Registration... 2 User ID and Password... 3 How to Log In... 3 How to Add/Delete a Mall and
BAE Systems employee app - installation Guide
 BAE Systems employee app - installation Guide The App was created for BAE Systems for distribution to employees in Saudi Arabia for the delivery of Company related news. It is a proprietary enterprise
BAE Systems employee app - installation Guide The App was created for BAE Systems for distribution to employees in Saudi Arabia for the delivery of Company related news. It is a proprietary enterprise
Tanium Protect User Guide. Version 1.9.3
 Tanium Protect User Guide Version 1.9.3 January 08, 2019 The information in this document is subject to change without notice. Further, the information provided in this document is provided as is and is
Tanium Protect User Guide Version 1.9.3 January 08, 2019 The information in this document is subject to change without notice. Further, the information provided in this document is provided as is and is
Creating New VPL (Visual Programming Language) for PWCT Lesson (6)
 Creating New VPL (Visual Programming Language) for PWCT Lesson (6) In this lesson we are going to learn how to generate an interaction page contains a checkbox and how to write the code mask script to
Creating New VPL (Visual Programming Language) for PWCT Lesson (6) In this lesson we are going to learn how to generate an interaction page contains a checkbox and how to write the code mask script to
Comprehensive Spam Quarantine Setup Guide on Security Appliance (ESA) and Security Management Appliance (SMA)
 Comprehensive Spam Quarantine Setup Guide on Email Security Appliance (ESA) and Security Management Appliance (SMA) Contents Introduction Procedure Configure Local Spam Quarantine on the ESA Enable Quarantine
Comprehensive Spam Quarantine Setup Guide on Email Security Appliance (ESA) and Security Management Appliance (SMA) Contents Introduction Procedure Configure Local Spam Quarantine on the ESA Enable Quarantine
Inxmail Professional 4.4 in five steps (test accounts)
 How-to Inxmail Professional 4.4 in five steps (test accounts) Use this document as an introduction to help get you started with Inxmail Professional. The five steps presented here take you through the
How-to Inxmail Professional 4.4 in five steps (test accounts) Use this document as an introduction to help get you started with Inxmail Professional. The five steps presented here take you through the
CHAPTER 2: USER EXPERIENCE ENHANCEMENTS
 Chapter 2: User Experience Enhancements CHAPTER 2: USER EXPERIENCE ENHANCEMENTS Objectives Introduction The objectives are: View sub-grids and notes in the Microsoft Dynamics CRM Outlook client. Use a
Chapter 2: User Experience Enhancements CHAPTER 2: USER EXPERIENCE ENHANCEMENTS Objectives Introduction The objectives are: View sub-grids and notes in the Microsoft Dynamics CRM Outlook client. Use a
CLIENT DASHBOARD. With Cloud Communication Solution (C.C.S).
 CLIENT DASHBOARD. CLIENT DASHBOARD Content CCS Presentation... 3 SMS... 3 Channels... 3 Requirement... 3 1.1 To read before connect... 4 1.2 Glossary of symbols... 5 1.3 CONNECTION... 6 1.3.1 Choice of
CLIENT DASHBOARD. CLIENT DASHBOARD Content CCS Presentation... 3 SMS... 3 Channels... 3 Requirement... 3 1.1 To read before connect... 4 1.2 Glossary of symbols... 5 1.3 CONNECTION... 6 1.3.1 Choice of
Configuring and Using AMT on TS130. Lenovo ThinkServer
 Lenovo ThinkServer August 31, 2011 Contents Overview... 3 Enabling and Configuring AMT on TS130... 3 Provisioning AMT on TS130 Using Manual Configuration Method... 4 AMT Configuration with Web Interface...
Lenovo ThinkServer August 31, 2011 Contents Overview... 3 Enabling and Configuring AMT on TS130... 3 Provisioning AMT on TS130 Using Manual Configuration Method... 4 AMT Configuration with Web Interface...
Multi-User Importing Instructions from an Existing ACT! Database
 Multi-User Importing Instructions from an Existing ACT! Database Thank you for purchasing an Act4Advisors Network License. These instructions are designed to help you import data from an existing ACT!
Multi-User Importing Instructions from an Existing ACT! Database Thank you for purchasing an Act4Advisors Network License. These instructions are designed to help you import data from an existing ACT!
Scantron Operating Instructions
 Scantron Operating Instructions Getting Started: 1. Remove the cover and turn on the Scantron machine. The ON/OFF switch is located on the back on the machine towards your right. 2. Log in to the computer
Scantron Operating Instructions Getting Started: 1. Remove the cover and turn on the Scantron machine. The ON/OFF switch is located on the back on the machine towards your right. 2. Log in to the computer
How to Activate Student Log in to the student Registration system (also known as My Community Education or Banner ).
 How to Activate Student E-Mail 1. Log in to the student Registration system (also known as My Community Education or Banner ). 2. The new account notice shows at the top of the screen once signed in. Click
How to Activate Student E-Mail 1. Log in to the student Registration system (also known as My Community Education or Banner ). 2. The new account notice shows at the top of the screen once signed in. Click
Monitoring Location Servers and Site
 8 CHAPTER This chapter describes how to monitor location servers by configuring and viewing alarms, events, and logs. It also describes how to use Cisco WCS to view location server, client and asset tag
8 CHAPTER This chapter describes how to monitor location servers by configuring and viewing alarms, events, and logs. It also describes how to use Cisco WCS to view location server, client and asset tag
Orgnazition of This Part
 Orgnazition of This Part Table of Contents Tutorial: Organization of This Part...1 Lesson 1: Starting JReport Enterprise Server and Viewing Reports...3 Introduction...3 Installing JReport Enterprise Server...3
Orgnazition of This Part Table of Contents Tutorial: Organization of This Part...1 Lesson 1: Starting JReport Enterprise Server and Viewing Reports...3 Introduction...3 Installing JReport Enterprise Server...3
ADOBE 9A Adobe Illustrator CS ACE. Download Full Version :
 ADOBE 9A0-035 Adobe Illustrator CS ACE Download Full Version : https://killexams.com/pass4sure/exam-detail/9a0-035 QUESTION: 121 You want to set crop marks directly in your artwork and specify a user defined
ADOBE 9A0-035 Adobe Illustrator CS ACE Download Full Version : https://killexams.com/pass4sure/exam-detail/9a0-035 QUESTION: 121 You want to set crop marks directly in your artwork and specify a user defined
SETTING UP DOCUSCAN AND CREATING CUSTOM SCAN SETTINGS
 SETTING UP DOCUSCAN AND CREATING CUSTOM SCAN SETTINGS Summit Brokerage Services User Guide June 2012 SETTING UP DOCUSCAN AND CREATING CUSTOM SCAN SETTINGS As explained before, Docupace does provide its
SETTING UP DOCUSCAN AND CREATING CUSTOM SCAN SETTINGS Summit Brokerage Services User Guide June 2012 SETTING UP DOCUSCAN AND CREATING CUSTOM SCAN SETTINGS As explained before, Docupace does provide its
2007, 2008 FileMaker, Inc. All rights reserved.
 Bento User s Guide 2007, 2008 FileMaker, Inc. All rights reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker, the file folder logo, Bento and the Bento logo are either
Bento User s Guide 2007, 2008 FileMaker, Inc. All rights reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker, the file folder logo, Bento and the Bento logo are either
AVG Business Edition Remote Administration
 AVG Business Edition Remote Administration User Manual Document revision AVG.02 (1/7/2018) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective
AVG Business Edition Remote Administration User Manual Document revision AVG.02 (1/7/2018) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective
WINTHROP UNIVERSITY. Banner 9 Admin Pages PURCHASE REQUISITION TRAINING MANUAL
 WINTHROP UNIVERSITY Banner 9 Admin Pages PURCHASE REQUISITION TRAINING MANUAL TABLE OF CONTENTS Signing In/Out..3 Entering A Requisition..4 15 Requisition Screen/FPAREQN....4 Requestor/Delivery Information..5
WINTHROP UNIVERSITY Banner 9 Admin Pages PURCHASE REQUISITION TRAINING MANUAL TABLE OF CONTENTS Signing In/Out..3 Entering A Requisition..4 15 Requisition Screen/FPAREQN....4 Requestor/Delivery Information..5
10. Container Search and Operations
 10. Container Search and Operations Container (inventory) search, edit, transfer, dispose Overview This quick guide will show you how to search the internal inventory and make changes by transferring,
10. Container Search and Operations Container (inventory) search, edit, transfer, dispose Overview This quick guide will show you how to search the internal inventory and make changes by transferring,
Fundtech JRE 1.7 Update 45 Issues and Resolution
 Fundtech JRE 1.7 Update 45 Issues and Resolution 10/17/2013 Summary of Issues Oracle released JRE 1.7 update 45 in the late morning of 10/15/2013. Changes in this version of the JRE created the following
Fundtech JRE 1.7 Update 45 Issues and Resolution 10/17/2013 Summary of Issues Oracle released JRE 1.7 update 45 in the late morning of 10/15/2013. Changes in this version of the JRE created the following
Kaspersky Security for Windows Server
 Kaspersky Security for Windows Server User's Guide Application version: 10.1.0.622 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Kaspersky Security for Windows Server User's Guide Application version: 10.1.0.622 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
DPI-SSL. DPI-SSL Overview
 DPI-SSL Document Scope This document describes the DPI-SSL feature available in SonicOS 5.6. This document contains the following sections: DPI-SSL Overview section on page 1 Using DPI-SSL section on page
DPI-SSL Document Scope This document describes the DPI-SSL feature available in SonicOS 5.6. This document contains the following sections: DPI-SSL Overview section on page 1 Using DPI-SSL section on page
CYAN SECURE WEB Installing on Windows
 CYAN SECURE WEB September 2009 Applies to: 1.7 and above Table of Contents 1 Introduction... 2 2 Preparation... 2 3 Network Integration... 3 3.1 Out-of-line Deployment... 3 3.2 DMZ Deployment... 3 4 Proxy
CYAN SECURE WEB September 2009 Applies to: 1.7 and above Table of Contents 1 Introduction... 2 2 Preparation... 2 3 Network Integration... 3 3.1 Out-of-line Deployment... 3 3.2 DMZ Deployment... 3 4 Proxy
