MessageLabs Intelligence: October 2006 Do you want spam with that spam?
|
|
|
- Moris Casey
- 5 years ago
- Views:
Transcription
1 Be certain MessageLabs Intelligence: October 2006 Do you want spam with that spam? Introduction Welcome to the October edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for October 2006, to keep you informed regarding the ongoing fight against viruses, spam and other unwelcome content. Top line results of this report include: Spam 72.9% in October (an increase of 8.5% since September) Viruses One in s in October contained malware (a decrease of 0.12% since September) Phishing One in 190 s comprised a phishing attack (a decrease of 0.06% since September) October marks the beginning of the spam season this year in the run up to the holiday period, with MessageLabs seeing a sharp increase in levels this month, especially in the past few weeks. As predicted in the September/Q3 MessageLabs Intelligence report, spam is not going away. This increase is largely attributed to the huge rise in botnet activity over the past few weeks. There are two contributing factors compounding this issue, and it is as yet unclear as to whether there is any link between them. The first culprit is the aggressive level of activity around one particular trojan dropper called Warezov. Tens of thousands of copies of each variant are dispatched in numerous batches, where each batch is subtly different from the previous ones. Even a few bytes changed in the code will allow the trojan to pass undetected through traditional anti-virus protection. Being a dropper it is uncertain as to what the trojan is being used for, however it seems clear that there is a connection with the huge rise in spam levels around the world. The second driver of increased spam is another trojan, dubbed SpamThru which is responsible for a great deal of the botnet activity behind increased levels of spam this month. Analysis of SpamThru shows that the SpamThru makers are releasing new strains at regular intervals in order to confound traditional anti-virus signature detection. Using the spam cannon technique mentioned in previous reports, SpamThru utilizes a template for each spam it sends and by combining it with a list of addresses, each zombie is then able to pump out millions of spam s. Although designed to turn the infected computer into a spam-sending zombie, SpamThru employs an interesting device to circumvent the closure of the command-and-control channel. Usually, the control channel (or mother-ship) is located on an Internet Relay Chat (IRC) server under the control of the botnet master, and if this channel is disrupted, he/she may lose control of the entire botnet. However, rather than relying upon a central mother-ship for the control channel, each SpamThru zombie is able to learn about the other zombies in the botnet and relay that information when requested. Command and control is still centralized with SpamThru but should the control channel become disrupted, the botnet controller can regain control of the botnet by having access to just a single zombie machine on the botnet. SpamThru also attempts to neutralize anti-virus software by corrupting the local hosts file, inserting dummy addresses to override genuine anti-virus update URLs. SpamThru also downloads an illegal copy of Kaspersky Anti-Virus onto the infected computer, scanning the PC for viruses, whilst ensuring that it bypasses its own components. Interestingly, any MessageLabs 2006
2 other malware found on the system is removed the next time Windows reboots. With stagnant spam levels being the norm in recent months and significant increases being a distant memory, spam appears to be having a resurgence and will garner the attention, recently owned by viruses and phishing, through aggressive new techniques. Global Trends & Content Analysis MessageLabs Anti-Spam and Anti-Virus Services focus on identifying and averting unwanted communications originating from new and unknown bad sources and which are addressed to valid recipients. Skeptic Anti-Spam Protection: In October 2006, the global ratio of spam in traffic from new and unknown bad sources, for which the recipient addresses were deemed valid, was 72.9% (1 in s), an increase of 8.5% on the previous month. This is the sharpest rise in spam levels since January 2006, when an increase of 9.2% was observed. Spam rate 72.9% Current Trend Outlook % 90% 80% 70% 60% Peak: July % Six Month Avg. 64.5% Last Month 64.4% % The figure of 72.9% is actually lower than the true spam figure since MessageLabs deployed additional layers of defense at its network perimeter in early 2005, known as Traffic Management. This enables MessageLabs to control the amount of bandwidth that is given to absolutely known bad-sources of spam, and then to throttle those connections, slowing them down to a crawl so that to the spammer, they appear to be talking to a very slow modem. This in turn makes it incredibly painful for spammers attempting to send their spam to MessageLabs clients as it is effectively pushing back the spam to their networks by slowing-down their ability to send lots of spam. Consequently, many such connections eventually time-out or move on to softer targets. If we look at the amount of spam hitting MessageLabs honey-pots, which are unprotected by comparison, this figure would be much closer to 88.7%. For further information, please refer to the section on Traffic Management later in this report. 2
3 Skeptic Anti-Virus and Trojan Protection: The global ratio of -borne viruses in traffic from new and previously unknown bad sources destined for valid recipients, was 1 in s (1.0%) in October, a decrease of 0.12% since last month. Virus rate 1 in Current Trend Outlook 23 1 in in 0 1 in 20 1 in 40 1 in 60 1 in 80 Peak: Apr 04 1 in 10.4 Six Month Avg. 1 in 92.1 Last Month 1 in in 100 Although virus levels have seemingly fallen, this figure contradicts the true picture of the latest virus patterns. October witnessed a great deal of activity where dozens of copies of the Warezov dropper were mass-mailed in batches, where each batch of executables was modified in an attempt to avoid signature based detection. This resulted in a continuous burst of new viruses unable to be detected by traditional means, continually extending the window of vulnerability between release and protection. The net effect was an explosion in the number of spam-sending zombies on the internet, further aggravating an already acute spam problem. Phishing: October showed a slight decrease of 0.06% in the proportion of phishing attacks compared with the previous month. One in 190 (0.53%) s comprised some form of phishing attack. When judged as a proportion of all -borne threats such as viruses and trojans, the number of phishing s has stabilized after a significant increase of 30.7% the month before. 52.9% of all malicious s intercepted by MessageLabs in October were phishing attacks, an increase of 0.5% on the previous month. Phishing 1 in 190 Current Trend Outlook 23 1 in in 0 1 in in in in in 500 Peak: Jan 05 1 in 127 Six Month Avg. 1 in 332 Last Month 1 in in 600 Phishing attacks continue to be targeted mostly at those banks that have not currently deployed any two-factor authentication security measures. Banks that have deployed this technology are still being subjected to attacks, but on a much lesser scale. October also saw the release of Microsoft Internet Explorer 7.0 and Mozilla Firefox 2.0, both of which include additional anti-phishing countermeasures, so it remains to be seen as to what effect this will have on the nature of phishing attacks over the coming months. 3
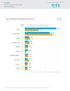
4 Skeptic Web Security Services Version 2.0: In July 2006, MessageLabs launched version 2.0 of its Web Security Services, built on MessageLabs proprietary technology. Web Security Services using Skeptic paves the way for the introduction of MessageLabs Converged Threat Analysis, taking the very latest threat and reputation information from other protocols, such as , and applying that knowledge to web traffic. It can be seen from the chart below that the most common trigger for policy-based filtering, applied by MessageLabs for its business clients, is Proxies & Translators (38.4%). This category includes remote proxies for anonymous surfing, search engine caches that circumvent filtering and web-based translation sites that circumvent filtering, for example, Babelfish and Proxify. Web Security Services (Version 2.0) Activity: Policy-Based Filtering Web Viruses and Trojans Potentially Unwanted Programs Proxies & Translators 38.4% Advertisements & Popups 31.1% Spyware 10.8% Adult/Sexually Explicit 4.4% Streaming Media 2.7% Chat 1.8% Blogs & Forums 1.6% Unclassified 1.5% Gambling 1.1% Downloads 1.0% Backdoor.Win32.Hupigon.clt 38.0% Trojan.Win32.Diamin.ez 27.9% Trojan-Clicker.HTML.Agent.a 12.6% VBS/Psyme 3.3% Phish-BankFraud.eml.b 2.0% Downloader-ABJ 1.4% Suspicious IFrame -c 1.2% W32/Bagle.gen 1.0% Trojan-Downloader.HTML.Agent.ae 1.0% JS/Wonka 0.9% Adware-SaveNow 55.1% Adware-ISTbar.b 23.1% Adware-abetterintrnt.gen.a 21.5% Adware-ZangoSA 0.4% The Unclassified category identifies new and previously uncategorized sites that may potentially need to be prohibited. The Unclassified category affords more confidence when defining new rules, which means that newly detected malicious sites may be handled more appropriately until categorized, thereby safeguarding against sites which appear and disappear within a 24 to 48 hour timeframe; such sites may be used for disreputable purposes, such as hosting phishing and spam sites, information stealing trojans and other fraudulent activities. Analysis of web security activity also shows that 94.4% of interceptions occur as the result of a rule triggered by a policy which has been implemented by a system administrator. However, 5.6% of interceptions are also the result of malware or potentially unwanted programs, including adware and spyware that was detected heuristically by Skeptic.
5 Geographical Breakdown: Based on Targeted Countries Monthly Analysis: By analyzing the geographical dispersal of traffic where possible, MessageLabs compiles data that shows the impact and vulnerability rates of spam and viruses specific to geographies. The charts below reflect impact and ratios for October Spam rate by geography Top 5 Israel 84.4% United States 72.2% Ireland 71.1% Hong Kong 69.6% Germany 66.3% Lowest Spain Japan 42.9% 35.7% In October, the top-5 countries in receipt of the majority of spam are largely unchanged from the previous month, however, there have been some position fluctuations. Israel retained the top-spot, with an increase of 9.1%. The US moved into second place with a rise of 11.5%, whilst Ireland slipped into third place with a rise of 6.9%. Further increases were borne in Hong Kong and Germany, by 9.2% and 8.7% respectively. Even the countries at the foot of the table witnessed significant increases this month, Spain by 6.8% and Japan increasing by 10.7%. The largest rise was in India, which had the lowest spam levels in September. In October, spam levels jumped by a massive 21.0% from 28.3% to 49.3%. Virus rate by geography Top 5 India 1 in 16.0 Ireland 1 in 24.3 Germany 1 in 36.1 Singapore 1 in 49.8 Spain 1 in 52.6 Lowest Netherlands United States 1 in in India remains the hardest hit country in terms of virus activity, where 6.24% (1 in 16) of inbound traffic contains a virus, trojan or other form of malware. This represents a fall of 1.47% since September. Virus levels in Ireland however increased by 0.30% to 4.12% (1 in 24.3) of traffic. Virus activity in the US fell by 0.36% to 0.74% (1 in 135.7) of s, pushing it to the bottom of the table this month. Although this may seem a rather enviable position, the ratio of borne virus traffic is still uncomfortably high regardless. Australia elevated from being near the foot of the table in the previous month, to a mid-table ranking in October; increasing by 0.38% to 1.19% (1 in 84.1) of traffic. 5
6 Vertical Industry Breakdown Monthly Analysis: By analyzing the market distribution of traffic where possible, MessageLabs compiles data that shows the impact and vulnerability rates of spam and viruses specific to major industry sectors. The charts below reflect impacts and ratios for October Spam rate by vertical Top 5 Education 76.2% Manufacturing 73.6% IT Services 72.8% Telecoms 70.1% Retail 68.1% Virus rate by vertical Top 5 Business Support Services 1 in 30.3 Education 1 in 44.8 Wholesale 1 in 48.2 Gov/Public Sector 1 in 73.4 Non-Profit 1 in 75.2 Lowest Finance Gov/Public Sector 56.2% 48.8% Lowest Health Care Telecoms 1 in in Education, Manufacturing and Telecoms remain in the top-5 verticals listing, all achieving 10.0% or higher increases this month. These sectors are joined by IT Services, which levels rose the most significantly of all sectors, by 18.2% and rose from 10th position in September, and Retail with an 10.8% rise in levels. Overall, spam levels across all sectors have increased in October, with Recreation having the lowest increase of 1.9%. The Public Sector has climbed from 8th position in September to push Manufacturing out of the top-5 industries most affected by virus attacks. This is in spite of a drop of 0.16% to 1.36% (1 in 73.4) of inbound traffic. Virus traffic destined for Business Support Services fell by 3.69% to 3.30% (1 in 30.3) of s, the most significant decrease of all sectors. Overall, virus traffic fell across almost all industry sectors in October, only with Building/ Construction and Recreation receiving minor increases. 6
7 Traffic Management (Protocol Level) Traffic Management continues to reduce the overall message volume through techniques operating at the protocol level. Unwanted senders are identified and connections to the mail server are slowed down using features embedded in the TCP protocol. Incoming volumes of known spam are significantly slowed, while ensuring legitimate is expedited. In October, MessageLabs processed over 2.35 billion SMTP connections per day, of which 92.2% of these connections were throttled back as a result of traffic management protocol controls for traffic that was unequivocally malicious or unwanted. Connection Management Connection Management is particularly effective in stopping directory harvest, brute force and denial of service attacks, where unwanted senders send high volumes of messages to force spam into an organization or disrupt business communications. Connection Management works at the SMTP level using techniques that verify legitimate connections to the mail server, and is comprised of the following: SMTP Validation: Identifies unwanted originating from known spam and virus sending sources, where the source can unequivocally be identified as an open proxy or a botnet, and rejects the connection accordingly. In October, an average of 4.7% of inbound messages were intercepted from botnets and other known malicious sources and rejected as a consequence. Registered User Address Validation: Reduces the overall volume of s for registered domains, by discarding connections for which the recipients are identified as invalid or non-existent. In October, an average of 11.4% of recipient addresses were identified as invalid; these were attempted directory attacks upon domains that were therefore prevented. Summary The table below details the current impact of traffic and connection management techniques on unwanted volume being measured by MessageLabs Intelligence. Without these additional multiple layers of defense, spam traffic destined for MessageLabs clients in October would otherwise account for around 88.7% of global traffic, an increase of 6.6% on the previous month. Region Traffic Management SMTP Validation User Validation (protocol control) (behaviour analysis) (directory attacks) USA 94.20% 4.10% 12.00% UK 90.00% 5.60% 11.40% Europe 88.10% 4.90% 11.80% Asia Pacific 80.30% 2.90% 5.40% Worldwide 92.20% 4.70% 11.40% Effects of Traffic Management Techniques MessageLabs is a leading provider of integrated messaging and web security services, with over 15,000 clients ranging from small business to the Fortune 500 located in more than 80 countries. MessageLabs provides a range of managed security services to protect, control, encrypt and archive communications across , Web and Instant Messaging. These services are delivered by MessageLabs globally distributed infrastructure and supported 24/7 by security experts. This provides a convenient and cost-effective solution for managing and reducing risk and providing certainty in the exchange of business information. For more information, please visit For further information on MessageLabs Intelligence, please visit and register to receive regular alerts and reports. NB: All figures mentioned in this report were correct at the time of going to press. 7
8 Appendices Appendix I: Spam Rate by Geography (October 2006) October September Change Australia 60.30% 47.70% 12.60% Austria 61.30% 52.10% 9.20% Belgium 54.30% 52.70% 1.60% Canada 65.90% 51.40% 14.50% France 58.80% 51.40% 7.40% Germany 66.30% 57.60% 8.70% Hong Kong 69.60% 60.40% 9.20% India 49.30% 28.30% 21.00% Ireland 71.10% 64.20% 6.90% Israel 84.40% 73.60% 10.80% Italy 60.90% 54.00% 6.90% Japan 35.70% 25.00% 10.70% Netherlands 59.10% 48.00% 11.10% Singapore 65.30% 55.40% 9.90% Spain 42.90% 36.10% 6.80% Sweden 52.40% 39.20% 13.20% Switzerland 52.70% 42.50% 10.20% United Arab Emirates 63.50% 53.60% 9.90% United Kingdom 61.40% 51.40% 10.00% United States 72.20% 60.70% 11.50% 8
9 Appendix II: Virus Rate by Geography (October 2006) October September Change Australia 1.19% 0.81% 0.38% Austria 0.89% 0.97% -0.08% Belgium 0.75% 0.52% 0.23% Canada 0.76% 0.96% -0.20% France 1.47% 1.98% -0.51% Germany 2.77% 3.27% -0.50% Hong Kong 1.85% 2.28% -0.43% India 6.24% 7.71% -1.47% Ireland 4.12% 3.82% 0.30% Israel 0.94% 1.01% -0.07% Italy 1.00% 1.18% -0.18% Japan 1.25% 1.38% -0.13% Netherlands 0.75% 0.89% -0.14% Singapore 2.01% 2.20% -0.19% Spain 1.90% 3.14% -1.24% Sweden 1.01% 1.12% -0.11% Switzerland 1.26% 1.47% -0.21% United Arab Emirates 1.70% 3.24% -1.54% United Kingdom 1.29% 1.19% 0.10% United States 0.74% 1.10% -0.36% 9
10 Appendix III: Spam Rate by Vertical (October 2006) October September Change Accom/Catering 60.50% 52.80% 7.70% Building/Cons 57.70% 49.50% 8.20% Chem/Pharm 65.60% 57.60% 8.00% Education 76.20% 62.90% 13.30% Estate Agents 60.00% 54.20% 5.80% Finance 56.20% 46.70% 9.50% General Services 57.20% 53.50% 3.70% Gov/Public Sector 48.80% 40.70% 8.10% Health Care 66.40% 56.80% 9.60% IT Services 72.80% 54.60% 18.20% Manufacturing 73.60% 62.30% 11.30% Marketing/Media 67.30% 56.50% 10.80% Mineral/Fuel 61.30% 52.60% 8.70% Non-Profit 63.90% 54.80% 9.10% Prof Services 66.00% 56.10% 9.90% Recreation 60.80% 58.90% 1.90% Retail 68.10% 57.30% 10.80% Telecoms 70.10% 60.10% 10.00% Transport /Util 68.10% 57.70% 10.40% Wholesale 66.30% 56.70% 9.60% 10
11 Appendix IV: Virus Rate by Vertical (October 2006) October September Change Accom/Catering 1.31% 1.53% -0.22% Building/Cons 1.04% 0.99% 0.05% Business Support Services 3.30% 6.99% -3.69% Chem/Pharm 0.79% 1.01% -0.22% Education 2.23% 2.39% -0.16% Finance 1.18% 1.01% 0.17% General Services 1.08% 1.17% -0.09% Gov/Public Sector 1.36% 1.52% -0.16% Health Care 0.65% 0.75% -0.10% IT Services 0.66% 0.71% -0.05% Manufacturing 1.18% 1.55% -0.37% Marketing/Media 1.01% 1.14% -0.13% Mineral/Fuel 1.18% 1.31% -0.13% Non-Profit 1.33% 1.54% -0.21% Prof Services 0.89% 0.92% -0.03% Recreation 1.03% 1.02% 0.01% Retail 0.92% 1.07% -0.15% Telecoms 0.43% 0.54% -0.11% Transport /Util 1.01% 1.20% -0.19% Wholesale 2.07% 2.78% -0.71% 11
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam
 Be certain MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam Introduction Welcome to the August 2007 edition of the MessageLabs Intelligence monthly report. This report
Be certain MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam Introduction Welcome to the August 2007 edition of the MessageLabs Intelligence monthly report. This report
May 2011 Intelligence Report
 Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of
Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of
Israel Internet Security Threat Profile
 Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim
 Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim Manager, Client & Partner Services, Asia 1 Agenda 2010 Threats Targeted Attacks Defense Against Targeted Attacks Questions 2
Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim Manager, Client & Partner Services, Asia 1 Agenda 2010 Threats Targeted Attacks Defense Against Targeted Attacks Questions 2
Top 10 Global Threat Rank by Source
 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE?
 >MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
IBM Express Managed Security Services for Security. Anti-Virus Administrator s Guide. Version 5.31
 IBM Express Managed Security Services for Email Security Anti-Virus Administrator s Guide Version 5.31 Table of Contents 1. Service overview...3 1.1 Welcome... 3 1.2 Anti-Virus (AV) features... 3 1.3 How
IBM Express Managed Security Services for Email Security Anti-Virus Administrator s Guide Version 5.31 Table of Contents 1. Service overview...3 1.1 Welcome... 3 1.2 Anti-Virus (AV) features... 3 1.3 How
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Kaspersky Security Network
 The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
For example, if a message is both a virus and spam, the message is categorized as a virus as virus is higher in precedence than spam.
 About Anti-Spam NOTE: Anti-Spam is a separate, licensed feature that provides a quick, efficient, and effective way to add anti-spam, anti-phishing, and anti-virus capabilities to your existing firewall.
About Anti-Spam NOTE: Anti-Spam is a separate, licensed feature that provides a quick, efficient, and effective way to add anti-spam, anti-phishing, and anti-virus capabilities to your existing firewall.
Marshal s Defense-in-Depth Anti-Spam Engine
 Marshal s Defense-in-Depth Anti-Spam Engine January 2008 Contents Overview 2 Features 3 Summary 6 This whitepaper explores the underlying anti-spam and anti-phishing defense technology in Marshal s world
Marshal s Defense-in-Depth Anti-Spam Engine January 2008 Contents Overview 2 Features 3 Summary 6 This whitepaper explores the underlying anti-spam and anti-phishing defense technology in Marshal s world
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Using Centralized Security Reporting
 This chapter contains the following sections: Centralized Email Reporting Overview, on page 1 Setting Up Centralized Email Reporting, on page 2 Working with Email Report Data, on page 4 Understanding the
This chapter contains the following sections: Centralized Email Reporting Overview, on page 1 Setting Up Centralized Email Reporting, on page 2 Working with Email Report Data, on page 4 Understanding the
Easy Activation Effortless web-based administration that can be activated in as little as one business day - no integration or migration necessary.
 Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Red Condor had. during. testing. Vx Technology high availability. AntiSpam,
 Lab Testing Summary Report July 21 Report 167 Product Category: Email Security Solution Vendors Tested: MessageLabs/Symantec MxLogic/McAfee SaaS Products Tested: - Cloudfilter; MessageLabs/Symantec Email
Lab Testing Summary Report July 21 Report 167 Product Category: Email Security Solution Vendors Tested: MessageLabs/Symantec MxLogic/McAfee SaaS Products Tested: - Cloudfilter; MessageLabs/Symantec Email
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
All-in one security for large and medium-sized businesses.
 All-in one security for large and medium-sized businesses www.entensys.com sales@entensys.com Overview UserGate UTM provides firewall, intrusion detection, anti-malware, spam and content filtering, and
All-in one security for large and medium-sized businesses www.entensys.com sales@entensys.com Overview UserGate UTM provides firewall, intrusion detection, anti-malware, spam and content filtering, and
Training UNIFIED SECURITY. Signature based packet analysis
 Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Security report Usuario de Test
 Security report Usuario de Test Servidor Cloud Period: 2018/MAY/13-2018/MAY/20 INDEX SUMMARY 2 Overview 3 Comparison with other users 5 Services and IPs included in this report 6 Traffic 7 Inbound and
Security report Usuario de Test Servidor Cloud Period: 2018/MAY/13-2018/MAY/20 INDEX SUMMARY 2 Overview 3 Comparison with other users 5 Services and IPs included in this report 6 Traffic 7 Inbound and
PineApp Mail Secure SOLUTION OVERVIEW. David Feldman, CEO
 PineApp Mail Secure SOLUTION OVERVIEW David Feldman, CEO PineApp Mail Secure INTRODUCTION ABOUT CYBONET CORE EXPERIENCE PRODUCT LINES FACTS & FIGURES Leader Product Company Servicing Multiple Vertical
PineApp Mail Secure SOLUTION OVERVIEW David Feldman, CEO PineApp Mail Secure INTRODUCTION ABOUT CYBONET CORE EXPERIENCE PRODUCT LINES FACTS & FIGURES Leader Product Company Servicing Multiple Vertical
Symantec Security.cloud
 Data Sheet: Messaging Security filters unwanted messages and protects mailboxes from targeted attacks. The service has selflearning capabilities and Symantec intelligence to deliver highly effective and
Data Sheet: Messaging Security filters unwanted messages and protects mailboxes from targeted attacks. The service has selflearning capabilities and Symantec intelligence to deliver highly effective and
Small Office Security 2. Mail Anti-Virus
 Small Office Security 2 Mail Anti-Virus Table of content Table of content... 1 Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/Disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus...
Small Office Security 2 Mail Anti-Virus Table of content Table of content... 1 Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/Disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus...
CISCO NETWORKS BORDERLESS Cisco Systems, Inc. All rights reserved. 1
 CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR ITALY
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR ITALY 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR ITALY 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR JAPAN
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR JAPAN 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR JAPAN 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR SOUTH AFRICA
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR SOUTH AFRICA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR SOUTH AFRICA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR UAE
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR UAE 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR UAE 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
MARKET NEWSLETTER No 69 February 2013
 Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
DMARC Continuing to enable trust between brand owners and receivers
 DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
Second International Barometer of Security in SMBs
 1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
Global DDoS Threat Landscape
 DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
A Review Paper on Network Security Attacks and Defences
 EUROPEAN ACADEMIC RESEARCH Vol. IV, Issue 12/ March 2017 ISSN 2286-4822 www.euacademic.org Impact Factor: 3.4546 (UIF) DRJI Value: 5.9 (B+) A Review Paper on Network Security Attacks and ALLYSA ASHLEY
EUROPEAN ACADEMIC RESEARCH Vol. IV, Issue 12/ March 2017 ISSN 2286-4822 www.euacademic.org Impact Factor: 3.4546 (UIF) DRJI Value: 5.9 (B+) A Review Paper on Network Security Attacks and ALLYSA ASHLEY
Commtouch Messaging Security for Hosting Providers
 Commtouch Messaging Security for Hosting Providers September 2009 nospam@commtouch.com www.commtouch.com blog.commtouch.com About Commtouch Since 1991 NASDAQ: CTCH Profitable Double digit growth Over 100
Commtouch Messaging Security for Hosting Providers September 2009 nospam@commtouch.com www.commtouch.com blog.commtouch.com About Commtouch Since 1991 NASDAQ: CTCH Profitable Double digit growth Over 100
Internet Security Mail Anti-Virus
 Internet Security 2012 Mail Anti-Virus Table of Contents Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus... 2 Changing Mail
Internet Security 2012 Mail Anti-Virus Table of Contents Mail Anti-Virus... 2 What is Mail Anti-Virus... 2 Enabling/disabling Mail Anti-Virus... 2 Operation algorithm of Mail Anti-Virus... 2 Changing Mail
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR INDIA
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR INDIA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR INDIA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Kaspersky PURE 2.0. Mail Anti-Virus: security levels
 Mail Anti-Virus: security levels Content Mail Anti-Virus. Security levels... 2 Operation algorithm of Mail Anti-Virus... 2 Security levels of Mail Anti-Virus... 2 Customizing security level... 4 Creating
Mail Anti-Virus: security levels Content Mail Anti-Virus. Security levels... 2 Operation algorithm of Mail Anti-Virus... 2 Security levels of Mail Anti-Virus... 2 Customizing security level... 4 Creating
Perimeter Defenses T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN
 T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
JPCERT/CC Incident Handling Report [January 1, March 31, 2018]
![JPCERT/CC Incident Handling Report [January 1, March 31, 2018] JPCERT/CC Incident Handling Report [January 1, March 31, 2018]](/thumbs/89/100577955.jpg) JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Prolexic Attack Report Q4 2011
 Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR BRAZIL
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR BRAZIL 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR BRAZIL 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Cisco s Appliance-based Content Security: IronPort and Web Security
 Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
EMC GLOBAL DATA PROTECTION INDEX STUDY KEY FINDINGS & RESULTS FOR THE NETHERLANDS
 EMC GLOBAL DATA PROTECTION INDEX STUDY KEY FINDINGS & RESULTS FOR THE NETHERLANDS 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH
EMC GLOBAL DATA PROTECTION INDEX STUDY KEY FINDINGS & RESULTS FOR THE NETHERLANDS 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR HONG KONG
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR HONG KONG 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR HONG KONG 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
FORGING A TRUE GLOBAL CONNECTION - BROADBAND PASSES 500 MILLION SUBSCRIBERS. One in every five of the world s households now has broadband
 FORGING A TRUE GLOBAL CONNECTION - BROADBAND PASSES 500 MILLION SUBSCRIBERS One in every five of the world s households now has broadband 20 September 2010, Hong Kong Broadband has taken a significant
FORGING A TRUE GLOBAL CONNECTION - BROADBAND PASSES 500 MILLION SUBSCRIBERS One in every five of the world s households now has broadband 20 September 2010, Hong Kong Broadband has taken a significant
Ryan KS office thesee
 SERVERR and WORKSTATION REMOTE MANAGEMENT SERVICES Ryan Dental Systems Dental Computer Systems Support and Sales 303 2 nd Street, PO Box 194, Inland NE 68954 5506 SW 31stPh: 402-461-5575 Terrace Topeka
SERVERR and WORKSTATION REMOTE MANAGEMENT SERVICES Ryan Dental Systems Dental Computer Systems Support and Sales 303 2 nd Street, PO Box 194, Inland NE 68954 5506 SW 31stPh: 402-461-5575 Terrace Topeka
Unit 2 Assignment 2. Software Utilities?
 1 Unit 2 Assignment 2 Software Utilities? OBJECTIVES Identify software utility types and examples of common software Why are software utilities used? Identify and describe the various networking threats.
1 Unit 2 Assignment 2 Software Utilities? OBJECTIVES Identify software utility types and examples of common software Why are software utilities used? Identify and describe the various networking threats.
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR APJ
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR APJ 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR APJ 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY
 RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
RSA FRAUDACTION ANTI-PHISHING SERVICE: BENEFITS OF A COMPREHENSIVE MITIGATION STRATEGY RSA CYOTA PROJECT PROPOSAL RSA FRAUDACTION ANTI-PHISHING SERVICE V.1 2011 Overview This brief highlights the benefits
Basic Concepts in Intrusion Detection
 Technology Technical Information Services Security Engineering Roma, L Università Roma Tor Vergata, 23 Aprile 2007 Basic Concepts in Intrusion Detection JOVAN GOLIĆ Outline 2 Introduction Classification
Technology Technical Information Services Security Engineering Roma, L Università Roma Tor Vergata, 23 Aprile 2007 Basic Concepts in Intrusion Detection JOVAN GOLIĆ Outline 2 Introduction Classification
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Get Max Internet Security where to buy software for students ]
![Get Max Internet Security where to buy software for students ] Get Max Internet Security where to buy software for students ]](/thumbs/87/95239861.jpg) Get Max Internet Security where to buy software for students ] Description: Features of Max Secure Internet Security 2013 Exciting, Easy to understand GUI Easy, Quick installation Get immediate protection
Get Max Internet Security where to buy software for students ] Description: Features of Max Secure Internet Security 2013 Exciting, Easy to understand GUI Easy, Quick installation Get immediate protection
EMC GLOBAL DATA PROTECTION INDEX STUDY KEY RESULTS & FINDINGS FOR THE USA
 EMC GLOBAL DATA PROTECTION INDEX STUDY KEY RESULTS & FINDINGS FOR THE USA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX STUDY KEY RESULTS & FINDINGS FOR THE USA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Phishing in the Age of SaaS
 Phishing in the Age of SaaS AN ESSENTIAL GUIDE FOR BUSINESSES AND USERS The Cloud Security Platform Q3 2017 intro Phishing attacks have become the primary hacking method used against organizations. In
Phishing in the Age of SaaS AN ESSENTIAL GUIDE FOR BUSINESSES AND USERS The Cloud Security Platform Q3 2017 intro Phishing attacks have become the primary hacking method used against organizations. In
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR INDONESIA
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR INDONESIA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GlOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR INDONESIA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GlOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR SOUTH KOREA
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR SOUTH KOREA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR SOUTH KOREA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Fighting the. Botnet Ecosystem. Renaud BIDOU. Page 1
 Fighting the Botnet Ecosystem Renaud BIDOU Page 1 Bots, bots, bots Page 2 Botnet classification Internal Structure Command model Propagation mechanism 1. Monolithic Coherent, all features in one binary
Fighting the Botnet Ecosystem Renaud BIDOU Page 1 Bots, bots, bots Page 2 Botnet classification Internal Structure Command model Propagation mechanism 1. Monolithic Coherent, all features in one binary
Protecting Against Application DDoS A acks with BIG-IP ASM: A Three- Step Solution
 Protecting Against Application DDoS A acks with BIG-IP ASM: A Three- Step Solution Today's security threats increasingly involve application-layer DDoS attacks mounted by organized groups of attackers
Protecting Against Application DDoS A acks with BIG-IP ASM: A Three- Step Solution Today's security threats increasingly involve application-layer DDoS attacks mounted by organized groups of attackers
Use and Abuse of Anti-Spam White/Black Lists
 Page 1 of 5 Use and Abuse of Anti-Spam White/Black Lists September 26, 2006 White and Black lists are standard spam filters. Their typically simple interface, provide a way to quickly identify emails as
Page 1 of 5 Use and Abuse of Anti-Spam White/Black Lists September 26, 2006 White and Black lists are standard spam filters. Their typically simple interface, provide a way to quickly identify emails as
The Application Usage and Risk Report End User Application Trends in the Enterprise - Country Specific Findings
 The Application Usage and Risk Report End User Application Trends in the Enterprise - Country Specific Findings December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com
The Application Usage and Risk Report End User Application Trends in the Enterprise - Country Specific Findings December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR TURKEY
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR TURKEY 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR TURKEY 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Sales Training
 Sales Training Extensible Content Security 16.03.2010 2009 WatchGuard Technologies Market Opportunity Total Addressable Market, ($M) Total Addressable Market by Segment, ($M) 16,000 14,000 11.2% CAGR 16,000
Sales Training Extensible Content Security 16.03.2010 2009 WatchGuard Technologies Market Opportunity Total Addressable Market, ($M) Total Addressable Market by Segment, ($M) 16,000 14,000 11.2% CAGR 16,000
Data Communication. Chapter # 5: Networking Threats. By: William Stalling
 Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR AMERICAS
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR AMERICAS 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR AMERICAS 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
McAfee Labs Threat Report
 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR AUSTRALIA
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR AUSTRALIA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR AUSTRALIA 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Ethical Hacking and. Version 6. Spamming
 Ethical Hacking and Countermeasures Version 6 Module XL Spamming News Source: http://www.nzherald.co.nz/ Module Objective This module will familiarize you with: Spamming Techniques used by Spammers How
Ethical Hacking and Countermeasures Version 6 Module XL Spamming News Source: http://www.nzherald.co.nz/ Module Objective This module will familiarize you with: Spamming Techniques used by Spammers How
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS AND RESULTS FOR FRANCE
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS AND RESULTS FOR FRANCE 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS AND RESULTS FOR FRANCE 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Cyber Threat Intelligence Report
 Cyber Threat Intelligence Report March, 2015 www.threat2alert.com Part of the Nettitude Group Report # 1: March 2015 This report shows the following activity has been seen recently from our Cyber Threat
Cyber Threat Intelligence Report March, 2015 www.threat2alert.com Part of the Nettitude Group Report # 1: March 2015 This report shows the following activity has been seen recently from our Cyber Threat
Holiday Hotspots. Wi-Fi Intelligence. A Wi-Fi Roaming Case Study
 Holiday Hotspots Wi-Fi Intelligence A Wi-Fi Roaming Case Study Holiday Hotspots: A Wi-Fi Roaming Case Study 7,800 Customers +40 Countries Devicescape Network Usage April, 2017 Most of us can t do without
Holiday Hotspots Wi-Fi Intelligence A Wi-Fi Roaming Case Study Holiday Hotspots: A Wi-Fi Roaming Case Study 7,800 Customers +40 Countries Devicescape Network Usage April, 2017 Most of us can t do without
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR MEXICO
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR MEXICO 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR MEXICO 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Product info. PCKeeper - Ver Windows 10. PCKeeper Antivirus - Ver Windows 10. BRATISLAVA, Slovakia, Sept 2, 2016
 Essentware S.A. the official owner of PCKeeper brand informs it s users that both of company products have successfully passed the Windows 10 compatibility qualification. PCKeeper Live and PCKeeper Antivirus
Essentware S.A. the official owner of PCKeeper brand informs it s users that both of company products have successfully passed the Windows 10 compatibility qualification. PCKeeper Live and PCKeeper Antivirus
Digital EAGLEs. Outlook and perspectives
 2016 Digital EAGLEs Outlook and perspectives Fixed and Mobile broadband adoption rates in the next decade Changes in Fixed-Broadband penetration 2014-25 Changes in Mobile-Broadband penetration 2014-25
2016 Digital EAGLEs Outlook and perspectives Fixed and Mobile broadband adoption rates in the next decade Changes in Fixed-Broadband penetration 2014-25 Changes in Mobile-Broadband penetration 2014-25
MESSAGING SECURITY GATEWAY. Solution overview
 MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
McAfee Firewall Enterprise: The only Firewall with the Intelligence to Continuously, Automatically Reduce the Risk and Threat Exposure of Your Network
 : The only Firewall with the Intelligence to Continuously, Automatically Reduce the Risk and Threat Exposure of Your Network Reputation filtering with TrustedSource and Geo-Location costeffectively minimizes
: The only Firewall with the Intelligence to Continuously, Automatically Reduce the Risk and Threat Exposure of Your Network Reputation filtering with TrustedSource and Geo-Location costeffectively minimizes
Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking
 NETWORK MANAGEMENT II Proxy Servers Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking resources from the other
NETWORK MANAGEMENT II Proxy Servers Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking resources from the other
Real Security. In Real Time. White Paper. Preemptive Malware Protection through Outbreak Detection
 Real Security. In Real Time. White Paper Preemptive Malware Protection through Detection Table of Contents Executive Summary...2 Response Time to New s The Achilles Heel of the Anti-Virus Industry...3
Real Security. In Real Time. White Paper Preemptive Malware Protection through Detection Table of Contents Executive Summary...2 Response Time to New s The Achilles Heel of the Anti-Virus Industry...3
Smart Service Packs. Providing customer recruitment, retention & new revenue streams. 1 Smart Service Packs
 Smart Service Packs Providing customer recruitment, retention & new revenue streams 1 Smart Service Packs Mobile messaging has been a runaway success, yet the basic service has changed little since its
Smart Service Packs Providing customer recruitment, retention & new revenue streams 1 Smart Service Packs Mobile messaging has been a runaway success, yet the basic service has changed little since its
Spam Evolution Report: October 2009
 Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
STANDARD BROADBAND & FIBRE BROADBAND PLANS
 STANDARD BROADBAND & FIBRE BROADBAND PLANS Terms & Conditions for Consumer Customers Version 8.0 Date 24 th October 2017 1 General You can join one of our Standard Broadband or Fibre Broadband plans. To
STANDARD BROADBAND & FIBRE BROADBAND PLANS Terms & Conditions for Consumer Customers Version 8.0 Date 24 th October 2017 1 General You can join one of our Standard Broadband or Fibre Broadband plans. To
RSA Web Threat Detection
 RSA Web Threat Detection Online Threat Detection in Real Time Alaa Abdulnabi. CISSP, CIRM RSA Pre-Sales Manager, TEAM Region 1 Web Threat Landscape In the Wild Begin Session Login Transaction Logout Web
RSA Web Threat Detection Online Threat Detection in Real Time Alaa Abdulnabi. CISSP, CIRM RSA Pre-Sales Manager, TEAM Region 1 Web Threat Landscape In the Wild Begin Session Login Transaction Logout Web
Secure solutions for advanced threats
 Secure solutions for advanced email threats Threat-centric email security Cosmina Calin Virtual System Engineer November 2016 Get ahead of attackers with threat-centric security solutions In our live Security
Secure solutions for advanced email threats Threat-centric email security Cosmina Calin Virtual System Engineer November 2016 Get ahead of attackers with threat-centric security solutions In our live Security
The Mimecast Security Risk Assessment Quarterly Report May 2017
 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 Many organizations think their current email security systems
The Mimecast Email Security Risk Assessment Quarterly Report May 2017 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 Many organizations think their current email security systems
GFI MailSecurity 2011 for Exchange/SMTP. Administration & Configuration Manual
 GFI MailSecurity 2011 for Exchange/SMTP Administration & Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and
GFI MailSecurity 2011 for Exchange/SMTP Administration & Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and
