IBM 企业移动平台初探. 刘达 IBM 应用开发商合作部
|
|
|
- Kenneth Daniels
- 6 years ago
- Views:
Transcription
1 IBM 企业移动平台初探 刘达 IBM 应用开发商合作部 2
2 议程 IBM 移动开发平台简介 IBM Worklight 简介 IBM Worklight 的架构分析 其他相关移动开发技术和产品 Mobile is a significant component of the evolution of computing Mobile/Wireless/Cloud Web/Desktop Client/Server Host/Mainframe Mobile is different: Transformational business models Faster lifecycles, more iterative Fragmentation drives movement to open standards
3 Mobile is an enterprise priority Growth in Internet Connected Devices Mobile and Cloud are top spending priorities for CIOs WW Media Tablets WW Notebooks WW PCs WW Smartphones Unit Volumes (Millions) E 2013E 2014E 2015E Source: Wells Fargo Securities, January 23, 2012 Fostering the People: The Shift to Engagement Apps Dramatic Growth in Mobile Devices Mobile data traffic exceeded voice in Shipments of Smartphones exceeded total PC shipments for the first time in Billion mobile connected devices are expected to be in use by IBM Global CIO Study 2 Wireless Industry News, August 26, Economist Mobile handset dominance is difficult to predict 1995 Palm 500,000 units sold in 6mts. 70% market share 2001 Nokia 40% Market share of all mobile phones 2008 RIM Fastest growing stock. 56% of smartphones, 77% 3yr CAGR (19.7% share in 10/ Apple Most valuable company in the world, 27.3% of US smartphones Android Has 43.7 of the US smartphone market 10/11
4 Mobile presents an enormous set of opportunities Business to Enterprise Business to Consumer Increase worker productivity Improved claims processing Increase revenue through sales engagements Extend existing applications to mobile workers and customers Reducing fuel, gas, or fleet maintenance costs that are relevant in particular industries Increase employee responsiveness and decision making speed Resolve internal IT issues faster Reduce personnel cost (utilizing personal owned instead of corporate issued devices) Improve customer satisfaction Deeper customer engagement and loyalty Drive increased sales through Personalized offers Customer service Competitive differentiator Improve brand perception Deeper insight into customer buying behavior for up sell and cross sell Improve in store experience with mobile concierge services Trends in Enterprise Mobility The need for business agility along with changing employee behaviors will require enterprises to mitigate operational risk associated with mobility Number and Types of Devices are Evolving Mobility is Driving the Consumerization of IT Increasing Demand for Enterprise Applications Security Requirements Becoming More Complex 1 Billion smart phones and 1.2 Billion Mobile workers by 2014 Large enterprises expect to triple their smartphone user base by % of large enterprises supporting personally-owned devices Billions of downloads from App Stores; longer term trend for app deployment 20%of mobile workers are getting business apps from app stores today 50% of organizations plan to deploy mobile apps within 12 months Threats from rogue applications and social engineering expected to double by % of all apps send device info or personal details
5 Uniqueness of Mobile Mobile Devices are Shared More Often Smartphones and tablets are multipurpose personal devices. Therefore, users share them with friends, and family more often than traditional computing devices laptops and desktops. Social norms on privacy are different when accessing filesystems vs. mobile apps Mobile Devices are Used in More Locations Smartphones and tablets are frequently used in challenging wireless situations that contrast with laptop friendly remote access centers. Laptops are used in a limited number of trusted locations Mobile Devices prioritize User Experience Smartphones and tablets place a premium on user experience and any security protocol that diminishes the experiences will not be adopted or will be circumvented. Workstation level security cannot be assumed unless they are dedicated devices Mobile Devices have multiple personas Smartphones and tablets may have multiple personas entertainment device, work tool, etc. Each persona is used in a different context. Users may want to employ a different security model for each persona without affecting another. Mobile Devices are Diverse Smartphones and tablets employ a variety of different platforms and have numerous applications aimed at pushing the boundaries of collaboration. The standard interaction paradigms used on laptops and desktops cannot be assumed. Primer on Mobile Apps Browser-based Mobile Applications Description: Web application resides on server and is accessed via the Internet using a browser. Advantages: Relatively low development costs Version management Ubiquitous channel for application delivery Disadvantages: Network latency Bandwidth consumption Limited access to device capabilities (i.e. accelerometer, GPS, camera, contacts etc.) Advancements: Tools to provide native lookand-feel Standards (i.e. HTML5) offering greater access to device capabilities, some offline support, and client side execution Techniques to mimic user experience in launching applications Native Applications Description: An application that is mainly acquired through app stores and installed on the device. Platform specific SDKs required for development. Advantages: Rich user experience Offline computing Access to device capabilities Disadvantages: Development and maintenance costs required to support multiple platforms $50k-$150k per app Version support Externally controlled delivery channels (app stores) Advancements: Development frameworks with in-built business models for monetizing applications Hybrid Applications Description: Installed application built using web technologies (i.e. JavaScript, CSS, HTML) that leverage platform specific wrappers to access to device capabilities. Advantages: Reduced development costs over native applications Can support offline computing Access to some of the device capabilities Disadvantages: Inclusion of third-party wrappers could impact performance Version support & management Advancements: Frameworks for building hybrid applications maturing Tools to provide native lookand-feel Improvements in performance
6 Evolving Mobile Landscape - Challenges Mobile Development is more expensive than traditional Web App Development: Which smartphone? Which tablet? Which form factor? ios, Android, Blackberry, Windows Phone All of the above.. Skills? Web or native apps? Java or Objective C? Or other? Maintenance? Separate software stacks for each major OS Separate applications for each major OS How do I keep software current? Security? Encryption? Authentication? Response to stolen/lost devices? Management? Can I see my apps? Can I disable them remotely? Enterprise Integration? How do I build cross-channel app? Since the Mobile field is still evolving, so an enterprise would want to pick a platform that can adapt to the future. Challenges of Enterprise Mobility Adapting to the Bring Your Own Device (BYOD) to Work Trend Device Management and Security Application management Achieving Data Separation Privacy Corporate Data protection Providing secure access to enterprise applications & data Secure connectivity Identity, Access and Authorization Developing Secure Mobile Apps Vulnerability testing Designing an Adaptive Security Posture Policy Management Security Intelligence
7 Driving Key Set of Mobile Security Requirements Mobile devices are not only computing platforms but also communication devices, hence mobile security is multi-faceted, driven by customers operational priorities Mobile Security Intelligence Mobile Device Management Data, Network and Access Security App/Test Development Mobile Device Management Acquire/Deploy Register Activation Content Mgmt Manage/Monitor Self Service Reporting Retire De-provision Mobile Device Security Management Device wipe and lockdown Password Management Configuration Policy Compliance Mobile Threat Management Anti-malware Anti-spyware Anti-spam Firewall/IPS Web filtering Web Reputation Mobile Information Protection Data encryption (device, file and app) Mobile data loss prevention Mobile Network Protection Secure Communications (VPN) Edge Protection Mobile Identity and Access Management Identity Management Authorize & Authenticate Certificate Management Multi-factor Secure Mobile Application Development Vulnerability testing Mobile app testing Enforced by tools Enterprise policies Mobile Applications i.e. Native, Hybrid, Web Application Mobile Application Platforms and Containers Device Platforms 30 device Manufacturers, 10 operating platforms i.e. ios, Android, Windows Mobile, Symbian, etc. IBM Mobile Enterprise: A Platform For Mobile Initiatives Banking Insurance Healthcare Telecom Retail Government Others IBM Enterprise Mobile Platform Business Results Extending business to mobile customers and workforce Improve operational efficiencies and reduce costs Differentiate the customer experience Enable new services and business models Workforce Optimization Product and Service Innovation Customer Care and Insights 3 rd Party Mobility Services Social Collaboration User Notification Location Services Mobile Payments Social Mobile Commerce Build mobile applications Connect to, and run backend systems in support of mobile Manage mobile devices and applications Secure my mobile business Extend existing business capabilities to mobile devices Transform the business by creating new opportunities
8 Terminologies Mobile Enterprise Application Platform (MEAP) Address the difficulties for developing mobile software by managing of the diversity of devices, networks and user groups at the time of deployment and throughout the mobile solution lifecycle. Comprises of : Mobile middleware server handles all system integration, security, communications, scalability, cross-platform support etc Mobile client app runs on the device and connect to the middleware server. Mobile Device Management (MDM) To secure, monitor, manage and support mobile devices deployed across enterprises. Generally for B2E (business to employee devices) Functionalities typically includes over-the-air distribution of applications, data and configuration.
9 The IBM Mobile Platform (i.e., what you need to build and effectively incorporate mobile apps with your business) Security Gateway Rational Lifecycle Tivoli Security Worklight Mobile Platform IBM Mobile Platform Mobile Device Management Elastic Caching SOA & Connectivity Analytics Decision Management Enterprise Apps Business Process Management Connectivity MQTT, Broker, CastIron 议程 IBM 移动开发平台简介 IBM Worklight 简介 IBM Worklight 的架构分析 其他相关移动开发技术和产品
10 Worklight At a Glance Apps Development Build once. Run anywhere. Android, ios, Blackberry, Microsoft, igoogle, Facebook app, Adobe AIR Runtime Skins for different resolutions Standards based language Application Lifecycle Management Centralized Build Process Security Secured offline access On device encryption of user data Single sign-on mechanism SSL encryption Protection against reverse engineering vulnerabilities Multi-factor authentication Enterprise Integration Direct access to back-end systems Leverage existing SOA services Server-side caching Application Management App distribution App Version management Remote disabling apps Direct Update Push Notification service management Analytics and Usage report Middleware WebSphere Application Server Reliable, Highly Available and Scalable Worklight Overview Built on Eclipse and Integrate with RAD Worklight Studio The most complete, extensible development environment with maximum code reuse and per-device optimization Runs on WAS 7 Worklight Server Mobile middleware offering unified push notifications, version management, security and integration Runs on devices Worklight Runtime Components Extensive libraries and client APIs that expose and interface with native device functionality and the Worklight Server Integrated with WAS Admin Console Worklight Console A web-based console for real-time analytics and control of your mobile apps and infrastructure
11
12 议程 IBM 移动开发平台简介 IBM Worklight 简介 IBM Worklight 的架构分析 其他相关移动开发技术和产品 Apps Development with Worklight Studio Eclipse-based IDE Integrate with Rational Application Developer Combining native and standard web technologies in one multiplatform app Environment-specific optimization 3rd-party libraries integration Device SDK integration Back-end connectivity utilities
13 Supported Application Types Supports a variety of application types Mobile iphone ipad Android BlackBerry Windows Phone Mobile web app Desktop Windows 7 and Vista Adobe AIR Mac OS Dashboard Web Applications Facebook igoogle Embedded web page Worklight Mobile Application Types Web Apps Hybrid Apps - Web Hybrid Apps - Mixed Native Apps Written in HTML5 JavaScript and CSS3. Quick and cheap to develop, but less powerful than native. Source code consists of web code and included Worklight libraries and executed in a native shell. User augments web code with native language for unique needs and maximized user experience. Platform-specific. Requires unique expertise, pricey and long to develop. Can deliver higher user experience. Mobile Browser Worklight Runtime Worklight Runtime Native Application Web Code <!DOCTYPE html PUBLIC <html> <! - - created <head><title>xyz</title> </head> <body> </p> </body> </html> Web Code <!DOCTYPE html PUBLIC <html> <! - - created <head><title>xyz</title </head> </body> </html> <!DOCTY PE html PUBLIC created </p> </body> </html> Web Native Device APIs Device APIs Device APIs
14 Mobile Application Types Comparation What are Hybrid Apps? Install as Native Apps For example: For ios, it will have an IPA file extension For Android, it will have an APK file extension Can be uploaded to Apple AppStore and Android Market Worklight Runtime Component is deployed with the app which can interpret HTML5 code. Full access to device features (such as camera, GPS etc) Code in web language, run as native app Worklight Runtime Component Web Code <!DOCTYPE html PUBLIC <html> <! - - created <head><title>xyz</title </head> </body> </html> Device APIs Deployed Native App
15 Single Shared Codebase Common code placed in primary file Environment optimization code is maintained separately Incorporated Device SDKs Android and Blackberry SDK
16 Incorporated Device SDKs ios SDK Integrating Best-in-class Tools Worklight is compatible with prominent HTML5 libraries and tools: 32
17 Worklight Client Architecture
18
19 Runtime Skinning Use Cases Different Screen Sizes Different Screen Densities Different Input Method Support for HTML5 Example Mobile Skin on Android
20 Example Mobile Skin on ipad Build and Deploy Build all and Deploy Create the vendor project Deploy server portion of the app to Worklight server
21 Centralized Build Integration with Rational Team Concert Worklight Build System Mobile Development Lifecycle Management Individual Developer Workstation Rational Application Developer Rational Team Concert Server Native Mobile Toolkits & Emulators RTC Repository Central Team Server Rational Team Concert Team Build Engine Shared Build Server Builder Rational Application Developer Web & Mobile Tools Rational Team Concert Eclipse Client Worklight Studio Eclipse Client RIM SDK Android SDK ios SDK
22 Worklight Server Distribution of mobile web apps Enterprise connectivity: Secure client/server connectivity Direct access to enterprise back-end data and transaction capabilities Authentication enforcement Client control: Application version management and remote disabling Direct update of application code Unified Push Notifications Aggregation of usage statistics 43 Direct Update On-device Logic App Store 1 Download Worklight Runtime 2 Transfer Pre-packaged resources 1.Web resources packaged with app to ensure initial offline availability 2.Web resources transferred to app's cache storage Worklight Server 4 3 Check for updates Web resources Update web resource Cached resources 3.App checks for updates On startup On foreground 4.Updated web resources downloaded when necessary 44
23 Back-end Integration Secure back-end integration XML-based declarative specification (JSON) Multi-source data mashups Eclipse plug-in supporting autocomplete and validation Simplified adapter testing Server-side debugging (soon) Web services and JDBC integration Access to session data and user properties Server side Caching Leverage existing SOA services and ESB 45 Push Notification Receiving Notification on the Device 46
24 Unified Push Notifications Device Runtime Components Framework for server integration: Secure server connectivity Authentication Remote disable & notification Push registration Dynamic page loading & caching (soon) Event reporting for analytics & audit Cross-platform compatibility layer Runtime Skinning Secure encrypted storage 48
25 Securing Mobile Apps Protecting data on the device Secure Encrypted Offline challenge- offline authentication response on cache startup Jailbreak App and authenticity malware testing detection Enforcing Security Updates Remote Direct disable update Streamline Corporate Security Process Shell as organization al sandbox Robust Authentication and Authorization Application Security Authenticatio n integration framework Data protection realms Using device id as 2 nd factor Proven platform security SSL with server identity verification Code obfuscation 49 Mechanism Benefits Details Encrypted offline cache SSL identity verification for AJAX Client code attestation Remote code updates Remote disable of specific versions Authentication process framework Server-side safeguards Device identification Mobile Security Measures Protect against stealing sensitive information via malware, stolen devices Protect against man-in-themiddle attacks Prevent impersonation by phishing apps Protect apps from manipulation by malware Ensure timely propagation of critical security updates to entire install base Ensure timely propagation of critical security updates to entire install base Lower the cost and complexity of robust integration with the authentication infrastructure Prevention of SQL injection XSRF protection Prevent account-hijacking Uses AES256 and PCKS #5 for on-device encrypted storage of appgenerated information, with random server-generated numbers for high security Allows user authentication when server is offline Implemented in JS (highly obfuscated) with optional native performance enhancements Client-side AJAX framework automatically verifies Worklight-server credentials Challenge-response based mechanism for proving client-application identity Uses tamper-resistant self-inspecting code New versions of the code can be distributed without requiring update of the app (currently JS/HTML) Server-side console allows configuration of allowed app versions. Administrator can force users to install security updates to the native code Server-side architecture for integration with back-end authentication infrastructure based on JAAS, with Authentication realms Client-side framework for asynchronous login requests on session expiration Prepared-statement enforcement Validation of submitted data against session cookie Safely report device ID to the server Identifying a user with specific devices
26 Mechanism Benefits Details Enterprise SSO integration VPN alternative Mobile Security Measures Leverage existing enterprise authentication facilities and user credentials Enable employeeowned devices Enable the secure delivery and operation of mobile applications for employee owned devices or device types not allowed on the corporate network Enable the secure delivery in cases where the installation of VPN client on mobile devices is not possible or complicated to manage Client side mechanism obtains and encrypts user credentials, sends to the server with requests Encryption incorporates user-supplied PIN, Server side secret and deviceid Credentials cannot be retrieved from lost or stolen device Client side and server side framework act as SSL based VPN Network access control and policies pre-configured in the client side framework layer Network access and security measures updated using server side framework On device encrypted storage to prevent compromise of sensitive data Worklight Console Application Version Management Push management Usage reports and analytics Reports of custom application events Configurable audit log Administrative dashboards for: Deployed applications Installed adapters Push notifications Data export to BI enterprise systems
27 Dynamic Control of Deployed Apps Centralized control of all installed applications and adapters Remotely disable apps by device and version Customize user messages Push Services Management
28 Advanced Reporting Functionality
Mobile Devices prioritize User Experience
 Mobile Security 1 Uniqueness of Mobile Mobile Devices are Shared More Often Mobile Devices are Used in More Locations Mobile Devices prioritize User Experience Mobile Devices have multiple personas Mobile
Mobile Security 1 Uniqueness of Mobile Mobile Devices are Shared More Often Mobile Devices are Used in More Locations Mobile Devices prioritize User Experience Mobile Devices have multiple personas Mobile
Mobile Security using IBM Endpoint Manager Mobile Device Management
 Mobile Security using IBM Endpoint Manager Mobile Device Management Mahendra Chopra Security Solution Architect @ IBM CIO Lab, Innovation mahendra.chopra@in.ibm.com Agenda Market Trends Mobile Security?
Mobile Security using IBM Endpoint Manager Mobile Device Management Mahendra Chopra Security Solution Architect @ IBM CIO Lab, Innovation mahendra.chopra@in.ibm.com Agenda Market Trends Mobile Security?
IBM Mobile Enterprise: IBM Worklight Overview
 IBM Mobile Enterprise: IBM Worklight Overview Agenda IBM Mobile Enterprise Overview IBM Worklight Overview Business Partner Opportunities IBM Worklight Advanced Features (Optional) 2 Unit Volumes (Millions)
IBM Mobile Enterprise: IBM Worklight Overview Agenda IBM Mobile Enterprise Overview IBM Worklight Overview Business Partner Opportunities IBM Worklight Advanced Features (Optional) 2 Unit Volumes (Millions)
WebSphere Puts Business In Motion. Put People In Motion With Mobile Apps
 WebSphere Puts Business In Motion Put People In Motion With Mobile Apps Use Mobile Apps To Create New Revenue Opportunities A clothing store increases sales through personalized offers Customers can scan
WebSphere Puts Business In Motion Put People In Motion With Mobile Apps Use Mobile Apps To Create New Revenue Opportunities A clothing store increases sales through personalized offers Customers can scan
Introduction to Worklight Integration IBM Corporation
 Introduction to Worklight Integration Agenda IBM Mobile Foundation Introduction to Worklight How to Integrate Worklight Adapters WebAPI HTTP & SOAP Database (SQL) WebSphere Message Broker Cast Iron 2 IBM
Introduction to Worklight Integration Agenda IBM Mobile Foundation Introduction to Worklight How to Integrate Worklight Adapters WebAPI HTTP & SOAP Database (SQL) WebSphere Message Broker Cast Iron 2 IBM
Implementing Your BYOD Mobility Strategy An IT Checklist and Guide
 Implementing Your BYOD Mobility Strategy An IT Checklist and Guide 2012 Enterproid IBYOD: 120221 Content 1. Overview... 1 2. The BYOD Checklist... 1 2.1 Application Choice... 1 2.2 Installation and Configuration...
Implementing Your BYOD Mobility Strategy An IT Checklist and Guide 2012 Enterproid IBYOD: 120221 Content 1. Overview... 1 2. The BYOD Checklist... 1 2.1 Application Choice... 1 2.2 Installation and Configuration...
The IBM MobileFirst Platform
 The IBM MobileFirst Platform Curtis Miles IBM MobileFirst Solution Architect April 14, 2015 What is the IBM MobileFirst Platform? A modular set " of libraries, tools, and runtimes " that help you " easily
The IBM MobileFirst Platform Curtis Miles IBM MobileFirst Solution Architect April 14, 2015 What is the IBM MobileFirst Platform? A modular set " of libraries, tools, and runtimes " that help you " easily
MaaS360 Secure Productivity Suite
 MaaS360 Secure Productivity Suite Frequently Asked Questions (FAQs) What is MaaS360 Secure Productivity Suite? MaaS360 Secure Productivity Suite integrates a set of comprehensive mobile security and productivity
MaaS360 Secure Productivity Suite Frequently Asked Questions (FAQs) What is MaaS360 Secure Productivity Suite? MaaS360 Secure Productivity Suite integrates a set of comprehensive mobile security and productivity
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
Introducing KASPERSKY ENDPOINT SECURITY FOR BUSINESS
 Introducing KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 Business drivers and their impact on IT AGILITY Move fast, be nimble and flexible 66% of business owners identify business agility as a priority EFFICIENCY
Introducing KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 Business drivers and their impact on IT AGILITY Move fast, be nimble and flexible 66% of business owners identify business agility as a priority EFFICIENCY
Transforming IT: From Silos To Services
 Transforming IT: From Silos To Services Chuck Hollis Global Marketing CTO EMC Corporation http://chucksblog.emc.com @chuckhollis IT is being transformed. Our world is changing fast New Technologies New
Transforming IT: From Silos To Services Chuck Hollis Global Marketing CTO EMC Corporation http://chucksblog.emc.com @chuckhollis IT is being transformed. Our world is changing fast New Technologies New
BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE
 BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE OUR ORGANISATION AND SPECIALIST SKILLS Focused on delivery, integration and managed services around Identity and Access Management.
BEYOND AUTHENTICATION IDENTITY AND ACCESS MANAGEMENT FOR THE MODERN ENTERPRISE OUR ORGANISATION AND SPECIALIST SKILLS Focused on delivery, integration and managed services around Identity and Access Management.
Connect and Transform Your Digital Business with IBM
 Connect and Transform Your Digital Business with IBM 1 MANAGEMENT ANALYTICS SECURITY MobileFirst Foundation will help deliver your mobile apps faster IDE & Tools Mobile App Builder Development Framework
Connect and Transform Your Digital Business with IBM 1 MANAGEMENT ANALYTICS SECURITY MobileFirst Foundation will help deliver your mobile apps faster IDE & Tools Mobile App Builder Development Framework
BYOD Success Kit. Table of Contents. Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips
 Table of Contents Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips 2 Current State of BYOD in the Enterprise Defining BYOD Bring-Your-Own-Device (BYOD): a business practice
Table of Contents Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips 2 Current State of BYOD in the Enterprise Defining BYOD Bring-Your-Own-Device (BYOD): a business practice
Kony MobileFabric. Release Notes. On-Premises. Release 6.5. Document Relevance and Accuracy
 Kony MobileFabric Release Notes On-Premises Release 6.5 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and the document version stated on
Kony MobileFabric Release Notes On-Premises Release 6.5 Document Relevance and Accuracy This document is considered relevant to the Release stated on this title page and the document version stated on
How to Evaluate a Next Generation Mobile Platform
 How to Evaluate a Next Generation Mobile Platform appcelerator.com Introduction Enterprises know that mobility presents an unprecedented opportunity to transform businesses and build towards competitive
How to Evaluate a Next Generation Mobile Platform appcelerator.com Introduction Enterprises know that mobility presents an unprecedented opportunity to transform businesses and build towards competitive
Securing Office 365 with MobileIron
 Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
Trend Micro Guide and solution to help embrace Consumerization and BYOD. James Walker EMEA Product Marketing Manager 26 September 2012
 Trend Micro Guide and solution to help embrace Consumerization and BYOD James Walker EMEA Product Marketing Manager 26 September 2012 Agenda Consumerization What is it? What should I do? Mobile Security
Trend Micro Guide and solution to help embrace Consumerization and BYOD James Walker EMEA Product Marketing Manager 26 September 2012 Agenda Consumerization What is it? What should I do? Mobile Security
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
Applications the centerpiece of a BYOD environment.
 Applications the centerpiece of a BYOD environment. November 2012 Summary Most businesses, today, realize that it has become a necessity to offer solutions to help employees better manage agendas and activities
Applications the centerpiece of a BYOD environment. November 2012 Summary Most businesses, today, realize that it has become a necessity to offer solutions to help employees better manage agendas and activities
Speaker Introduction Who Mate Barany, VMware Manuel Mazzolin, VMware Peter Schmitt, Deutsche Bahn Systel Why VMworld 2017 Understanding the modern sec
 SIE3197BE Secure Your Windows 10 and Office 365 Deployment with VMware Security Solutions Mate Barany, VMware Manuel Mazzolin, VMware Peter Schmitt, Deutsche Bahn Systel #VMworld #SIE3197BE Speaker Introduction
SIE3197BE Secure Your Windows 10 and Office 365 Deployment with VMware Security Solutions Mate Barany, VMware Manuel Mazzolin, VMware Peter Schmitt, Deutsche Bahn Systel #VMworld #SIE3197BE Speaker Introduction
6/16/2015. Mobile on IBM i. Wayne Bowers Evolution of User Interface. rich client or browser. Traditional in-house
 Mobile on IBM i Wayne Bowers wbowers@us.ibm.com Evolution of User Interface rich client or browser Traditional in-house mobile 2 1 Mobile services are now a must-have 10B+ mobile devices in the world by
Mobile on IBM i Wayne Bowers wbowers@us.ibm.com Evolution of User Interface rich client or browser Traditional in-house mobile 2 1 Mobile services are now a must-have 10B+ mobile devices in the world by
Total Threat Protection. Whitepaper
 Total Threat Protection Whitepaper Organizations Are Caught Between a Growing Threat Landscape and Resource Limitations Today s organizations continue to struggle with providing adequate protection in
Total Threat Protection Whitepaper Organizations Are Caught Between a Growing Threat Landscape and Resource Limitations Today s organizations continue to struggle with providing adequate protection in
The Mobile Risk Management Company. Overview of Fixmo and Mobile Risk Management (MRM) Solutions
 The Mobile Risk Management Company Overview of Fixmo and Mobile Risk Management (MRM) Solutions Company Proprietary Information Copyright Fixmo Inc., 2012 Introduction to Fixmo Founded on a simple idea:
The Mobile Risk Management Company Overview of Fixmo and Mobile Risk Management (MRM) Solutions Company Proprietary Information Copyright Fixmo Inc., 2012 Introduction to Fixmo Founded on a simple idea:
Application management in Nokia: Getting the most from Company Apps
 Application management in Nokia: Getting the most from Case Study 2 Contents 1 Challenge...3 2...5 2.1 Deployment options...5 2.2 App security and authentication...7 2.3 Nokia...7 3 Company Hub...9 3.1
Application management in Nokia: Getting the most from Case Study 2 Contents 1 Challenge...3 2...5 2.1 Deployment options...5 2.2 App security and authentication...7 2.3 Nokia...7 3 Company Hub...9 3.1
RHM Presentation. Maas 360 Mobile device management
 RHM Presentation Maas 360 Mobile device management Strong adoption in the enterprise Manufacturing Financial Consumer Healthcare Public Others 2 Trusted by over 9,000 customers Recognized Industry Leadership
RHM Presentation Maas 360 Mobile device management Strong adoption in the enterprise Manufacturing Financial Consumer Healthcare Public Others 2 Trusted by over 9,000 customers Recognized Industry Leadership
BYOD Business year of decision!
 Bucharest, Romania April 24, 2013 BYOD Business year of decision! Cisco on Cisco Christoph Nienhaus IT Leader for EMEAR Central - DACH 2011 2012 Cisco and/or its affiliates. All rights reserved. Cisco
Bucharest, Romania April 24, 2013 BYOD Business year of decision! Cisco on Cisco Christoph Nienhaus IT Leader for EMEAR Central - DACH 2011 2012 Cisco and/or its affiliates. All rights reserved. Cisco
The Inflection Point in the Application Ecosystem
 The Inflection Point in the Application Ecosystem The post-pc era the data explosion 0111010101101010101010101010101010101010110101010101010101010101010101010101 0101010101101011011011011101011100000010110101001101011110011010101010110101
The Inflection Point in the Application Ecosystem The post-pc era the data explosion 0111010101101010101010101010101010101010110101010101010101010101010101010101 0101010101101011011011011101011100000010110101001101011110011010101010110101
Managing BYOD Networks
 Managing BYOD Networks SPS-2013 Raghu Iyer raghu.iyer@nevisnetworks.com 1 What is BYOD Bring Your Own Device Are you allowing a Rogue? SPS-2013 Raghu Iyer raghu.iyer@nvisnetworks.com 2 Why BYOD Increased
Managing BYOD Networks SPS-2013 Raghu Iyer raghu.iyer@nevisnetworks.com 1 What is BYOD Bring Your Own Device Are you allowing a Rogue? SPS-2013 Raghu Iyer raghu.iyer@nvisnetworks.com 2 Why BYOD Increased
IBM Worklight Proof of Technology by Jane Fung
 IBM Worklight Proof of Technology by Jane Fung Welcome to the Technical Exploration Center Survey Introductions Access restrictions Restrooms Emergency Exits Breakfast / Lunch / Snacks Special meal requirements?
IBM Worklight Proof of Technology by Jane Fung Welcome to the Technical Exploration Center Survey Introductions Access restrictions Restrooms Emergency Exits Breakfast / Lunch / Snacks Special meal requirements?
Sentinet for BizTalk Server SENTINET
 Sentinet for BizTalk Server SENTINET Sentinet for BizTalk Server 1 Contents Introduction... 2 Sentinet Benefits... 3 SOA and API Repository... 4 Security... 4 Mediation and Virtualization... 5 Authentication
Sentinet for BizTalk Server SENTINET Sentinet for BizTalk Server 1 Contents Introduction... 2 Sentinet Benefits... 3 SOA and API Repository... 4 Security... 4 Mediation and Virtualization... 5 Authentication
The Device Has Left the Building
 The Device Has Left the Building Mobile Security Made Easy With Managed PKI Christian Brindley Principal Systems Engineer, Symantec Identity and Information Protection Agenda 1 2 3 Mobile Trends and Use
The Device Has Left the Building Mobile Security Made Easy With Managed PKI Christian Brindley Principal Systems Engineer, Symantec Identity and Information Protection Agenda 1 2 3 Mobile Trends and Use
Cisco Borderless Networks Value Proposition
 Cisco Borderless Networks Value Proposition Enabling the Borderless Organization 2011 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 Why Borderless Networks? Cisco s Architectural Approach
Cisco Borderless Networks Value Proposition Enabling the Borderless Organization 2011 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 Why Borderless Networks? Cisco s Architectural Approach
IBM API Connect: Introduction to APIs, Microservices and IBM API Connect
 IBM API Connect: Introduction to APIs, Microservices and IBM API Connect Steve Lokam, Sr. Principal at OpenLogix @openlogix @stevelokam slokam@open-logix.com (248) 869-0083 What do these companies have
IBM API Connect: Introduction to APIs, Microservices and IBM API Connect Steve Lokam, Sr. Principal at OpenLogix @openlogix @stevelokam slokam@open-logix.com (248) 869-0083 What do these companies have
Secure IT consumeration (BYOD), users will like you How to make secure access for smart mobile devices
 Michal Zlesák Area Sales Manager Michal.zlesak@enterasys.com Secure IT consumeration (BYOD), users will like you How to make secure access for smart mobile devices A Siemens Enterprise Communications Company
Michal Zlesák Area Sales Manager Michal.zlesak@enterasys.com Secure IT consumeration (BYOD), users will like you How to make secure access for smart mobile devices A Siemens Enterprise Communications Company
THE MOBILE HELIX DATA SECURITY PLATFORM
 SECURE ENTERPRISE HTML5 THE MOBILE HELIX DATA SECURITY PLATFORM A MOBILE HELIX WHITEPAPER THE MOBILE HELIX DATA SECURITY PLATFORM The innovation in mobility has created an incredible opportunity to innovate
SECURE ENTERPRISE HTML5 THE MOBILE HELIX DATA SECURITY PLATFORM A MOBILE HELIX WHITEPAPER THE MOBILE HELIX DATA SECURITY PLATFORM The innovation in mobility has created an incredible opportunity to innovate
GLOBALPROTECT. Key Usage Scenarios and Benefits. Remote Access VPN Provides secure access to internal and cloud-based business applications
 GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
Oracle Mobile Application Framework
 Oracle Mobile Application Framework Oracle Mobile Application Framework (Oracle MAF) is a hybrid-mobile development framework that enables development teams to rapidly develop single-source applications
Oracle Mobile Application Framework Oracle Mobile Application Framework (Oracle MAF) is a hybrid-mobile development framework that enables development teams to rapidly develop single-source applications
Say Yes to BYOD How Fortinet Enables You to Protect Your Network from the Risk of Mobile Devices WHITE PAPER
 Say Yes to BYOD How Fortinet Enables You to Protect Your Network from the Risk of Mobile Devices WHITE PAPER FORTINET Say Yes to BYOD PAGE 2 Introduction Bring Your Own Device (BYOD) and consumerization
Say Yes to BYOD How Fortinet Enables You to Protect Your Network from the Risk of Mobile Devices WHITE PAPER FORTINET Say Yes to BYOD PAGE 2 Introduction Bring Your Own Device (BYOD) and consumerization
Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management
 Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management June 29, 2011 1 Forward-Looking Statements This presentation
Mobile Security Overview Rob Greer, VP Endpoint Management and Mobility Product Management Dave Cole, Sr. Director Consumer Mobile Product Management June 29, 2011 1 Forward-Looking Statements This presentation
Paper. Delivering Strong Security in a Hyperconverged Data Center Environment
 Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Oracle Mobile Hub. Complete Mobile Platform
 Oracle Mobile Hub Mobile is everywhere and has changed nearly every facet of our lives. The way we work, play, socialize and interact with one another have all been revolutionized by mobile devices. More
Oracle Mobile Hub Mobile is everywhere and has changed nearly every facet of our lives. The way we work, play, socialize and interact with one another have all been revolutionized by mobile devices. More
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience.
 The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
Build Mobile Cloud Apps Effectively Using Oracle Mobile Cloud Services (MCS)
 Build Mobile Cloud Apps Effectively Using Oracle Mobile Cloud Services (MCS) Presented by: John Jay King Download this paper from: 1 Session Objectives Understand the need for something like Oracle Mobile
Build Mobile Cloud Apps Effectively Using Oracle Mobile Cloud Services (MCS) Presented by: John Jay King Download this paper from: 1 Session Objectives Understand the need for something like Oracle Mobile
ALCATEL-LUCENT OPENTOUCH PERSONAL CLOUD A Revolution in Communications Applications for Enterprise End Users
 ALCATEL-LUCENT OPENTOUCH PERSONAL CLOUD A Revolution in Communications Applications for Enterprise End Users For the past 30 years, enterprise communications have been built around the personal computer,
ALCATEL-LUCENT OPENTOUCH PERSONAL CLOUD A Revolution in Communications Applications for Enterprise End Users For the past 30 years, enterprise communications have been built around the personal computer,
Cisco Integration Platform
 Data Sheet Cisco Integration Platform The Cisco Integration Platform fuels new business agility and innovation by linking data and services from any application - inside the enterprise and out. Product
Data Sheet Cisco Integration Platform The Cisco Integration Platform fuels new business agility and innovation by linking data and services from any application - inside the enterprise and out. Product
BYOD the HP Way: Secure, Device-Agnostic Network Access Management Jochen Fischer Solution Architect (MASE) September 2013
 BYOD the HP Way: Secure, Device-Agnostic Network Access Management Jochen Fischer Solution Architect (MASE) September 2013 Bring Your Own???? 2 Bring Your Own Device cannot be ignored About 50% Workers
BYOD the HP Way: Secure, Device-Agnostic Network Access Management Jochen Fischer Solution Architect (MASE) September 2013 Bring Your Own???? 2 Bring Your Own Device cannot be ignored About 50% Workers
Data Loss Prevention Whitepaper. When Mobile Device Management Isn t Enough. Your Device Here. Good supports hundreds of devices.
 Data Loss Prevention Whitepaper When Mobile Device Management Isn t Enough Your Device Here. Good supports hundreds of devices. Contents Shifting Security Landscapes 3 Security Challenges to Enterprise
Data Loss Prevention Whitepaper When Mobile Device Management Isn t Enough Your Device Here. Good supports hundreds of devices. Contents Shifting Security Landscapes 3 Security Challenges to Enterprise
Phil Schwan Technical
 Phil Schwan Technical Architect pschwan@projectleadership.net @philschwan Today s challenges Users Devices Apps Data Users expect to be able to work in any location and have access to all their work resources.
Phil Schwan Technical Architect pschwan@projectleadership.net @philschwan Today s challenges Users Devices Apps Data Users expect to be able to work in any location and have access to all their work resources.
SAP Security in a Hybrid World. Kiran Kola
 SAP Security in a Hybrid World Kiran Kola Agenda Cybersecurity SAP Cloud Platform Identity Provisioning service SAP Cloud Platform Identity Authentication service SAP Cloud Connector & how to achieve Principal
SAP Security in a Hybrid World Kiran Kola Agenda Cybersecurity SAP Cloud Platform Identity Provisioning service SAP Cloud Platform Identity Authentication service SAP Cloud Connector & how to achieve Principal
Consumerization. Copyright 2014 Trend Micro Inc. IT Work Load
 Complete User Protection Consumerization IT Work Load 2 Then... File/Folder & Removable Media Email & Messaging Web Access Employees IT Admin 3 Now! File/Folder & Removable Media Email & Messaging Web
Complete User Protection Consumerization IT Work Load 2 Then... File/Folder & Removable Media Email & Messaging Web Access Employees IT Admin 3 Now! File/Folder & Removable Media Email & Messaging Web
How Next Generation Trusted Identities Can Help Transform Your Business
 SESSION ID: SPO-W09B How Next Generation Trusted Identities Can Help Transform Your Business Chris Taylor Senior Product Manager Entrust Datacard @Ctaylor_Entrust Identity underpins our PERSONAL life 2
SESSION ID: SPO-W09B How Next Generation Trusted Identities Can Help Transform Your Business Chris Taylor Senior Product Manager Entrust Datacard @Ctaylor_Entrust Identity underpins our PERSONAL life 2
STREAMLINED CERTIFICATION PATHS
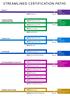 STREAMLINED CERTIFICATION PATHS MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2016 Cloud Platform & Infrastructure Linux on Azure Cloud Platform PRODUCTIVITY Server 2016 Productivity Office
STREAMLINED CERTIFICATION PATHS MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2016 Cloud Platform & Infrastructure Linux on Azure Cloud Platform PRODUCTIVITY Server 2016 Productivity Office
ENTERPRISE MOBILITY TRENDS
 ENTERPRISE MOBILITY TRENDS Raghuram Nair, Nandakishore Bellore Enterprise Mobility has emerged as a top technology trend globally. Every enterprise with a mobile workforce has an imperative to deploy a
ENTERPRISE MOBILITY TRENDS Raghuram Nair, Nandakishore Bellore Enterprise Mobility has emerged as a top technology trend globally. Every enterprise with a mobile workforce has an imperative to deploy a
Six steps to control the uncontrollable
 Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Copyright 2012, Oracle and/or its affiliates. All rights reserved.
 1 Copyright 2012, Oracle and/or its affiliates. All rights reserved. Developing Mobile Applications for ios and Android the Oracle Way Frédéric Desbiens Principal Product Manager Application Development
1 Copyright 2012, Oracle and/or its affiliates. All rights reserved. Developing Mobile Applications for ios and Android the Oracle Way Frédéric Desbiens Principal Product Manager Application Development
SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT
 DATASHEET SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT Silver level EMM Enterprise Mobility Management for Corporate-owned and BYOD devices BlackBerry Enterprise Service 10 is a powerful device,
DATASHEET SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT Silver level EMM Enterprise Mobility Management for Corporate-owned and BYOD devices BlackBerry Enterprise Service 10 is a powerful device,
Mobile Payment Application Security. Security steps to take while developing Mobile Application s. SISA Webinar.
 Mobile Payment Application Security Security steps to take while developing Mobile Application s About SISA Payment Security Specialists PCI Certification Body (PCI Qualified Security Assessor) Payment
Mobile Payment Application Security Security steps to take while developing Mobile Application s About SISA Payment Security Specialists PCI Certification Body (PCI Qualified Security Assessor) Payment
Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere. How Okta enables a Zero Trust solution for our customers
 Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere How Okta enables a Zero Trust solution for our customers Okta Inc. 301 Brannan Street, Suite 300 San Francisco, CA 94107 info@okta.com
Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere How Okta enables a Zero Trust solution for our customers Okta Inc. 301 Brannan Street, Suite 300 San Francisco, CA 94107 info@okta.com
AXIAD IDS CLOUD SOLUTION. Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure
 AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
WEB-APIs DRIVING DIGITAL INNOVATION
 WEB-APIs DRIVING DIGITAL INNOVATION Importance of Web-APIs Simply put, Web-APIs are the medium to make a company s digital assets consumable to any channel, which has a current or latent need. It helps
WEB-APIs DRIVING DIGITAL INNOVATION Importance of Web-APIs Simply put, Web-APIs are the medium to make a company s digital assets consumable to any channel, which has a current or latent need. It helps
Enterprise Redefined, Mobility Your Way
 Enterprise Redefined, Mobility Your Way Content 1 2 3 Fast-rising Enterprise Mobility Huawei Enterprise Mobility Solution Success Stories 1 Mobile working through BYOD are growing around world enterprise
Enterprise Redefined, Mobility Your Way Content 1 2 3 Fast-rising Enterprise Mobility Huawei Enterprise Mobility Solution Success Stories 1 Mobile working through BYOD are growing around world enterprise
Enhancing and Extending Microsoft SharePoint 2013 for Secure Mobile Access and Management
 SharePoint 2013 and Colligo Apps Enhancing and Extending Microsoft SharePoint 2013 for Secure Mobile Access and Email Management SharePoint 2013 is the latest release of Microsoft s leading business collaboration
SharePoint 2013 and Colligo Apps Enhancing and Extending Microsoft SharePoint 2013 for Secure Mobile Access and Email Management SharePoint 2013 is the latest release of Microsoft s leading business collaboration
MOBILIZE YOUR ENTERPRISE WITH TELERIK SOLUTIONS
 MOBILIZE YOUR ENTERPRISE WITH TELERIK SOLUTIONS Work doesn t just happen in the office. Technology is changing the way organizations operate. Today s business environment requires your employees to take
MOBILIZE YOUR ENTERPRISE WITH TELERIK SOLUTIONS Work doesn t just happen in the office. Technology is changing the way organizations operate. Today s business environment requires your employees to take
How to Secure Your Cloud with...a Cloud?
 A New Era of Thinking How to Secure Your Cloud with...a Cloud? Eitan Worcel Offering Manager - Application Security on Cloud IBM Security 1 2016 IBM Corporation 1 A New Era of Thinking Agenda IBM Cloud
A New Era of Thinking How to Secure Your Cloud with...a Cloud? Eitan Worcel Offering Manager - Application Security on Cloud IBM Security 1 2016 IBM Corporation 1 A New Era of Thinking Agenda IBM Cloud
1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 7
 1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 7 ORACLE PRODUCT LOGO 20. oktober 2011 Hotel Europa Sarajevo Platform
1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 7 ORACLE PRODUCT LOGO 20. oktober 2011 Hotel Europa Sarajevo Platform
Hosted Exchange. Presented by Joseph Lee
 Hosted Exchange Presented by Joseph Lee Hosted Exchange Hosted Exchange provides users with essential productivity tools and admins with control, simplicity and choice. Hosted Exchange For users: High
Hosted Exchange Presented by Joseph Lee Hosted Exchange Hosted Exchange provides users with essential productivity tools and admins with control, simplicity and choice. Hosted Exchange For users: High
BYOD: BRING YOUR OWN DEVICE.
 white paper BYOD: BRING YOUR OWN DEVICE. On-BOaRDING and Securing DEVICES IN YOUR Corporate NetWORk PrepaRING YOUR NetWORk to MEEt DEVICE DEMaND The proliferation of smartphones and tablets brings increased
white paper BYOD: BRING YOUR OWN DEVICE. On-BOaRDING and Securing DEVICES IN YOUR Corporate NetWORk PrepaRING YOUR NetWORk to MEEt DEVICE DEMaND The proliferation of smartphones and tablets brings increased
Mobile Middleware Course. Mobile Platforms and Middleware. Sasu Tarkoma
 Mobile Middleware Course Mobile Platforms and Middleware Sasu Tarkoma Role of Software and Algorithms Software has an increasingly important role in mobile devices Increase in device capabilities Interaction
Mobile Middleware Course Mobile Platforms and Middleware Sasu Tarkoma Role of Software and Algorithms Software has an increasingly important role in mobile devices Increase in device capabilities Interaction
Luckily, our enterprise had most of the back-end (services, middleware, business logic) already.
 2 3 4 The point here is that for real business applications, there is a connected back-end for services. The mobile part of the app is just a presentation layer that is unique for the mobile environment.
2 3 4 The point here is that for real business applications, there is a connected back-end for services. The mobile part of the app is just a presentation layer that is unique for the mobile environment.
Security Guide Zoom Video Communications Inc.
 Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless
Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless
PKI is Alive and Well: The Symantec Managed PKI Service
 PKI is Alive and Well: The Symantec Managed PKI Service Marty Jost Product Marketing, User Authentication Lance Handorf Technical Enablement, PKI Solutions 1 Agenda 1 2 3 PKI Background: Problems and Solutions
PKI is Alive and Well: The Symantec Managed PKI Service Marty Jost Product Marketing, User Authentication Lance Handorf Technical Enablement, PKI Solutions 1 Agenda 1 2 3 PKI Background: Problems and Solutions
Bring Your Own Device. Peter Silva Technical Marketing Manager
 Bring Your Own Device Peter Silva Technical Marketing Manager Bring-Your-Own-Device (BYOD) Personal devices for business apps Why implement BYOD? Increase employee satisfaction, productivity Reduce mobile
Bring Your Own Device Peter Silva Technical Marketing Manager Bring-Your-Own-Device (BYOD) Personal devices for business apps Why implement BYOD? Increase employee satisfaction, productivity Reduce mobile
CIO Forum Maximize the value of IT in today s economy
 CIO Forum Maximize the value of IT in today s economy Laura Scott, Vice President Service Product Line Sales Global Technology Services IT infrastructure is reaching a breaking point. 85% idle In distributed
CIO Forum Maximize the value of IT in today s economy Laura Scott, Vice President Service Product Line Sales Global Technology Services IT infrastructure is reaching a breaking point. 85% idle In distributed
Pick A Winner! In What Tool Should I Develop My Next App?
 Pick A Winner! In What Tool Should I Develop My Next App? Mia Urman, CEO, AuraPlayer Inc. @miaurman @auraplayer Who is Mia Urman? miaurman@auraplayer.com Oracle ACE Director & Development Geek for over
Pick A Winner! In What Tool Should I Develop My Next App? Mia Urman, CEO, AuraPlayer Inc. @miaurman @auraplayer Who is Mia Urman? miaurman@auraplayer.com Oracle ACE Director & Development Geek for over
Extending Enterprise Applications to Mobile - Key Considerations. Zensar Technologies Sep 2011
 Extending Enterprise Applications to Mobile - Key Considerations Zensar Technologies Sep 2011 AGENDA Section 1: Trends & Adoption across industry Section 2: Enterprise Mobile Application Development --
Extending Enterprise Applications to Mobile - Key Considerations Zensar Technologies Sep 2011 AGENDA Section 1: Trends & Adoption across industry Section 2: Enterprise Mobile Application Development --
Enabling Compliance for Physical and Cyber Security in Mobile Devices
 Enabling Compliance for Physical and Cyber Security in Mobile Devices Brandon Arcement & Chip Epps HID Global Sept 12, 2016 1630-1730 ET Agenda Smart Devices vs. Traditional Cards Mobility Infrastructure
Enabling Compliance for Physical and Cyber Security in Mobile Devices Brandon Arcement & Chip Epps HID Global Sept 12, 2016 1630-1730 ET Agenda Smart Devices vs. Traditional Cards Mobility Infrastructure
Why is Office 365 the right choice?
 Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Copyright 2014, Oracle and/or its affiliates. All rights reserved.
 1 Introduction to the Oracle Mobile Development Platform Dana Singleterry Product Management Oracle Development Tools Global Installed Base: PCs vs Mobile Devices 3 Mobile Enterprise Challenges In Pursuit
1 Introduction to the Oracle Mobile Development Platform Dana Singleterry Product Management Oracle Development Tools Global Installed Base: PCs vs Mobile Devices 3 Mobile Enterprise Challenges In Pursuit
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Ch 1: The Mobile Risk Ecosystem. CNIT 128: Hacking Mobile Devices. Updated
 Ch 1: The Mobile Risk Ecosystem CNIT 128: Hacking Mobile Devices Updated 1-12-16 The Mobile Ecosystem Popularity of Mobile Devices Insecurity of Mobile Devices The Mobile Risk Model Mobile Network Architecture
Ch 1: The Mobile Risk Ecosystem CNIT 128: Hacking Mobile Devices Updated 1-12-16 The Mobile Ecosystem Popularity of Mobile Devices Insecurity of Mobile Devices The Mobile Risk Model Mobile Network Architecture
CISCO NETWORKS BORDERLESS Cisco Systems, Inc. All rights reserved. 1
 CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
Mobility, Security Concerns, and Avoidance
 By Jorge García, Technology Evaluation Centers Technology Evaluation Centers Mobile Challenges: An Overview Data drives business today, as IT managers and security executives face enormous pressure to
By Jorge García, Technology Evaluation Centers Technology Evaluation Centers Mobile Challenges: An Overview Data drives business today, as IT managers and security executives face enormous pressure to
Transformation Through Innovation
 Transformation Through Innovation A service provider strategy to prosper from digitization People will have 11.6 billion mobile-ready devices and connections by 2020. For service providers to thrive today
Transformation Through Innovation A service provider strategy to prosper from digitization People will have 11.6 billion mobile-ready devices and connections by 2020. For service providers to thrive today
API, DEVOPS & MICROSERVICES
 API, DEVOPS & MICROSERVICES RAPID. OPEN. SECURE. INNOVATION TOUR 2018 April 26 Singapore 1 2018 Software AG. All rights reserved. For internal use only THE NEW ARCHITECTURAL PARADIGM Microservices Containers
API, DEVOPS & MICROSERVICES RAPID. OPEN. SECURE. INNOVATION TOUR 2018 April 26 Singapore 1 2018 Software AG. All rights reserved. For internal use only THE NEW ARCHITECTURAL PARADIGM Microservices Containers
SECURE, CENTRALIZED, SIMPLE
 1 SECURE, CENTRALIZED, SIMPLE Multi-platform Enterprise Mobility Management Whitepaper 2 Controlling it all from one place BlackBerry Enterprise Service 10 (BES10) is an end-to-end, multi-platform, device,
1 SECURE, CENTRALIZED, SIMPLE Multi-platform Enterprise Mobility Management Whitepaper 2 Controlling it all from one place BlackBerry Enterprise Service 10 (BES10) is an end-to-end, multi-platform, device,
Overview. Premium Data Sheet. DigitalPersona. DigitalPersona s Composite Authentication transforms the way IT
 DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
Changing face of endpoint security
 Changing face of endpoint security S A N T H O S H S R I N I V A S A N C I S S P, C I S M, C R I S C, C E H, C I S A, G S L C, C G E I T D I R E C T O R S H A R E D S E R V I C E S, H C L T E C H N O L
Changing face of endpoint security S A N T H O S H S R I N I V A S A N C I S S P, C I S M, C R I S C, C E H, C I S A, G S L C, C G E I T D I R E C T O R S H A R E D S E R V I C E S, H C L T E C H N O L
STREAMLINED CERTIFICATION PATHS
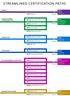 STREAMLINED CERTIFICATION PATHS MOBILITY Windows 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Cloud Platform Cloud Platform & Infrastructure Linux on Azure PRODUCTIVITY Productivity Office 365 APP BUILDER
STREAMLINED CERTIFICATION PATHS MOBILITY Windows 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Cloud Platform Cloud Platform & Infrastructure Linux on Azure PRODUCTIVITY Productivity Office 365 APP BUILDER
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Mobile Field Worker Security Advocate Series: Customer Conversation Guide. Research by IDC, 2015
 Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Enterprise Caching in a Mobile Environment IBM Redbooks Solution Guide
 Enterprise Caching in a Mobile Environment IBM Redbooks Solution Guide In the current global enterprise business environment, with the millions of applications running across Apple ios, Android, Windows
Enterprise Caching in a Mobile Environment IBM Redbooks Solution Guide In the current global enterprise business environment, with the millions of applications running across Apple ios, Android, Windows
Determining the Best Approach
 2 Determining the Best Approach The remaining chapters of this book cover the capabilities of the BlackBerry application platform and then dig into each application development option in detail. Before
2 Determining the Best Approach The remaining chapters of this book cover the capabilities of the BlackBerry application platform and then dig into each application development option in detail. Before
Sentinet for Microsoft Azure SENTINET
 Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
Thomas Lippert Principal Product Manager. Sophos Mobile. Spring 2017
 Thomas Lippert Principal Product Manager Sophos Mobile Spring 2017 Market Overview Trends Security or data breaches involving mobile devices are on the rise More people use mobile devices for work than
Thomas Lippert Principal Product Manager Sophos Mobile Spring 2017 Market Overview Trends Security or data breaches involving mobile devices are on the rise More people use mobile devices for work than
Five Tips to Mastering Enterprise Mobility
 Five Tips to Mastering Enterprise Mobility Table of Contents Introduction Tip 1: Assess Your Environment Tip 2: Review Security Protocols Tip 3: Be Smart About BYOD Tip 4: Consider Customized Mobility
Five Tips to Mastering Enterprise Mobility Table of Contents Introduction Tip 1: Assess Your Environment Tip 2: Review Security Protocols Tip 3: Be Smart About BYOD Tip 4: Consider Customized Mobility
Next Generation Privilege Identity Management
 White Paper Next Generation Privilege Identity Management Nowadays enterprise IT teams are focused on adopting and supporting newer devices, applications and platforms to address business needs and keep
White Paper Next Generation Privilege Identity Management Nowadays enterprise IT teams are focused on adopting and supporting newer devices, applications and platforms to address business needs and keep
A Mobile Security Checklist: The Top Ten Threats to Your Enterprise Today. White Paper
 A Mobile Security Checklist: The Top Ten Threats to Your Enterprise Today White Paper As enterprises mobilize business processes, more and more sensitive data passes through and resides on mobile devices.
A Mobile Security Checklist: The Top Ten Threats to Your Enterprise Today White Paper As enterprises mobilize business processes, more and more sensitive data passes through and resides on mobile devices.
A Layered Approach to Fraud Mitigation. Nick White Product Manager, FIS Payments Integrated Financial Services
 A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
A Layered Approach to Fraud Mitigation Nick White Product Manager, FIS Payments Integrated Financial Services Session Agenda Growing Fraud Concerns Old Habits Die Hard Maneuvering through the Barriers
