JUNIPER INTEGRATION HOW TO USE PINSAFE TO AUTHENTICATE A JUNIPER SSL VPN SWIVEL SECURE VICTORIA AVENUE HARROGATE HG1 1EL
|
|
|
- Myron Houston
- 6 years ago
- Views:
Transcription
1 JUNIPER INTEGRATION HOW TO USE PINSAFE TO AUTHENTICATE A JUNIPER SSL VPN SWIVEL SECURE VICTORIA AVENUE HARROGATE HG1 1EL
2 JUNIPER INTEGRATION NOTE CONTENTS CONTENTS...2 INTRODUCTION...3 PREQUISITES...3 ENHANCEMENT...4 Modifying pinsafe.js...4 Creating An Anonymous Login Server...4 Creating An Anonymous User Role...5 Creating An Anonymous User Realm...5 Map All Users To The Anon Realm...6 Creating a Sign in Policy...7 Editing the User Role UI...7 Selective Rewriting Rule...8 Set Idle Timeout...9 Verifying Installation...10 Additional Information...10 Appendix A PINSAFE.JS EXPLAINED
3 INTRODUCTION This document outlines the steps required to implement the enhanced Juniper integration solution. It is an improved solution that removes the requirement for the PINsafe server to have an externally accessible IP address. PREQUISITES You require a Juniper VPN server with correct licenses installed to modify and upload the login page. A PINsafe server is required to perform authentication. If the Single Channel Enhancement is not used to mask the PINsafe server IP address then the PINsafe server must be accessible from the internet to provide the Single Channel images. The Juniper server used for this document was NetScreen-SA-2000 Advanced Simultaneous Users, with System Version 5.3R3.1 Release (build 10741). 3
4 ENHANCEMENT This section outlines the steps required to mask the PINsafe server so its IP address is not required to publicly visible when using the Single Channel Turing Image. The basis of the solution is to allow an anonymous user to access the PINsafe server during authentication. Note that this is treated as an additional session and therefore uses an additional license for process of authentication. The session will timeout and the licence released; the timeout period can be set as required, eg to five minutes. In this way when the javascript runs in the client browser it actually requests the image via the Juniper SSL server and the SSL proxies the request. Therefore the PINsafe server only needs to be accessible from SSL server rather than the internet. MODIFYING PINSAFE.JS The pinsafe.js java script needs to be modified to point to access the TURing image via the Juniper server as follows: //URL of radiusturing page on the PINsafe server... var surl=" IP hostname>/pinsafe/scimage,danainfo=<ip of PINsafe server>,port=8080,sso=u+?username="; CREATING AN ANONYMOUS LOGIN SERVER Select the page Authentication/Auth. Servers, from the Select New Server, set it to Anonymous Server then click on New Server, and enter a name for the server, eg PINsafeAnon Figure 1. Creating an Anonymous Server 4
5 CREATING AN ANONYMOUS USER ROLE Select the page Users/User Roles and from this select New Role, enter a name for the role, ensure only UI and Web are selected and then click on Save Changes. Figure 2. Creating an Anonymous Role CREATING AN ANONYMOUS USER REALM Select the page Users/User Realm and from this select New, enter a name for the realm, and ensure that Authentication is set to the Anonymous Authentication Server created above then click on Save Changes. 5
6 Figure 3. Creating Anonymous Realm MAP ALL USERS TO THE ANON REALM Select the Role Mapping page from User Realm/Anon Realm/Role Mapping, then select new. Assign Users to this realm; as shown below Figure 4. Mapping Users to the Anonymous Realm 6
7 CREATING A SIGN IN POLICY Ensure that the correct signing in pages are all in place and set the sign in policy to point at the anonymous realm. Select Authentication/Signing In/Sign-in Policy, select the./* URL or the PINsafe login page URL and set the Authentication Realm to the Anonymous realm created, then click on Save Changes. Figure 5. Setting Signing-In Policy EDITING THE USER ROLE UI Select the UI page from Users/User Role/anonymous role created/general/ui. On the section Start Page click on Custom page and modify the URL to represent the original sign in page which should already have been created. 7
8 Figure 6. Setting Custom Login page SELECTIVE REWRITING RULE This rule prevents the address details for the server from being over-written, it must be listed before the default rewrite everything rule. Select Resource Policies/Web/Selective Rewriting and then New Policy. Enter a name for the policy and under the resources enter the SSL hostname or IP address, followed by the connection and a * for sub folders eg: hostname:80,443/* Select Policy Applies to Selected Roles, selecting the anonymous role, and then select the Action Don t rewrite content: Do not redirect to target web server, then select Save Changes. 8
9 Figure 7. Selective Rewriting Configuration Figure 8. Showing PINsafe re-routing prior to global rewrite policy SET IDLE TIMEOUT Anonymous users count towards the number of concurrent sessions for each login, although they are only briefly used. To prevent the system from filling up with many concurrent anonymous users set the Idle Timeout value to a low value. Select Users/User Roles/ anonymous 9
10 role/general/session Options. Then from the session lifetime section change the Idle Timeout to a value such as 5 minutes. Figure 9. Setting Session Timeout VERIFYING INSTALLATION Navigate to the Juniper login page. The customisation is visible in the addition of a One Time Code field and a TURing button. Attempting to login with a correct username and password but no one time code should result in failure. Only when a correct PINsafe one time code is entered in should the user be logged in. The Single Channel Turing Image should not reveal the internal IP address of the PINsafe server. The PINsafe logs will contain entries of all authentication attempts. ADDITIONAL INFORMATION For assistance in the PINsafe installation and configuration please contact your reseller or Swivel Secure support at support@swivelsecure.com 10
11 APPENDIX A PINSAFE.JS EXPLAINED //~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ // //Configuration section... //Prompt wording... var sotcprompt = "Enter your OTC:"; //URL of radiusturing page on the PINsafe server... var surl=" //Names of the username and password texboxes in the page that's calling this script... var snameofusernametext = "username"; var snameofpasswordtext = "password"; This is the prompt that will appear on the login page instead of Password //End configuration section... // //~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ These are the names of the fields on the login page. //See if we're on the right 'page', ie. username field is present... var bexists = (document.getelementsbyname(snameofusernametext)[0]!= null); Add the button, but hide it initially. Call ShowTuring when pressed document.write("<input type=button name=btnturing value=turing onclick=showturing() class='submitbutton' stylehidden='visibility:hidden; position: absolute; left:250;top:302;width:75;'>"); document.write("<img id=imgturing name=imgturing style='visibility:hidden;position: absolute; left:100;top:350;'>"); If we are on a login page, make button visible Add the TURing image, but hide it initially if (bexists){ document.getelementsbyname("btnturing")[0].style.visibility="visible"; try { var tablecount = document.getelementsbytagname("table").length; //Try and determine which page we are on from the table count and update the appropriate //table cell with the OTC prompt if (tablecount == 3) Workout where to write OTC prompt document.getelementsbytagname("td")[10].childnodes[0].nodevalue = sotcprompt; else if (tablecount == 5) 11
12 document.getelementsbytagname("td")[13].childnodes[0].nodevalue = sotcprompt; } catch (e){ alert ("An error occurred in PINsafe Extensions:\n\n" + e); } } function ShowTuring() { if (bexists) { suser=document.getelementsbyname(snameofusernametext)[0].value; if (suser=="") { alert ("Please enter your username first!"); document.getelementsbyname(snameofusernametext)[0].focus() }else{ //Find the image using Mozilla compatible pproach... varimg = document.getelementbyid("imgturing"); //Set the image SRC and make it visible varimg.src = surl + suser; varimg.style.visibility = "visible"; If button pressed and username entered, retrieve image from PINsafe //Alternative approach - show image in Popup //window.showmodaldialog(surl + suser,null,"dialogwidth=305px;dialogheight=110px;status:no;scroll:no;help:no;") } //Set focus to the OTC input document.getelementsbyname(snameofpasswordtext)[0].focus() } } 12
JUNIPER INTEGRATION HOW TO USE PINSAFE TO AUTHENTICATE A JUNIPER SSL VPN SWIVEL SECURE VICTORIA AVENUE HARROGATE HG1 1EL
 JUNIPER INTEGRATION HOW TO USE PINSAFE TO AUTHENTICATE A JUNIPER SSL VPN SWIVEL SECURE VICTORIA AVENUE HARROGATE HG1 1EL JUNIPER INTEGRATION NOTE CONTENTS CONTENTS...2 History...2 Issue...2 Details...2
JUNIPER INTEGRATION HOW TO USE PINSAFE TO AUTHENTICATE A JUNIPER SSL VPN SWIVEL SECURE VICTORIA AVENUE HARROGATE HG1 1EL JUNIPER INTEGRATION NOTE CONTENTS CONTENTS...2 History...2 Issue...2 Details...2
Integrating Swivel Secure s Pinsafe into Fortinet SSL VPN login
 Integrating Swivel Secure s Pinsafe into Fortinet SSL VPN login Overview PinSafe from Swive Secure is an enhance authentication system that utilizes both single and dual factor authentication. The essence
Integrating Swivel Secure s Pinsafe into Fortinet SSL VPN login Overview PinSafe from Swive Secure is an enhance authentication system that utilizes both single and dual factor authentication. The essence
Aventail Integration
 Aventail Integration SonicWall Aventail clientless SSL VPN Gateway Integration Guide Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS
Aventail Integration SonicWall Aventail clientless SSL VPN Gateway Integration Guide Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS
Joomla 1.6 Integration
 Joomla 1.6 Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 5.3 Setting
Joomla 1.6 Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 5.3 Setting
Juniper SA 8.x Integration
 Juniper SA 8.x Integration Contents 1 Overview 2 Prerequisites 3 File Downloads 4 Baseline 5 Architecture 6 Installation 6.1 Swivel Configuration 6.1.1 Configuring the RADIUS server 6.1.2 Enabling Session
Juniper SA 8.x Integration Contents 1 Overview 2 Prerequisites 3 File Downloads 4 Baseline 5 Architecture 6 Installation 6.1 Swivel Configuration 6.1.1 Configuring the RADIUS server 6.1.2 Enabling Session
Table of Contents 1 Citrix Access Gateway 5 VPX Introduction...1
 Table of Contents 1 Citrix Access Gateway 5 VPX...1 1.1 Introduction...1 2 Citrix Access Gateway Access Controller 5.0...2 3 Citrix Access Gateway Advanced 4.x...3 4 Introduction...4 5 Prerequisites...5
Table of Contents 1 Citrix Access Gateway 5 VPX...1 1.1 Introduction...1 2 Citrix Access Gateway Access Controller 5.0...2 3 Citrix Access Gateway Advanced 4.x...3 4 Introduction...4 5 Prerequisites...5
Barracuda SSL VPN Integration
 Barracuda SSL VPN Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 6 Barracuda
Barracuda SSL VPN Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 6 Barracuda
Citrix Access Gateway Enterprise Edition 10
 Citrix Access Gateway Enterprise Edition 10 Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with
Citrix Access Gateway Enterprise Edition 10 Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with
Citrix Netscaler Gateway 11
 Citrix Netscaler Gateway 11 Contents 1 Introduction 2 Prerequisites 2.1 Note on upgrading the Netscaler 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session
Citrix Netscaler Gateway 11 Contents 1 Introduction 2 Prerequisites 2.1 Note on upgrading the Netscaler 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session
F5 APM Integration. This article describes how to integrate the F5 Big-IP Access Policy Manager with Swivel. The article covers two aspects:
 F5 APM Integration Contents 1 F5 Big-IP Access Policy Manager (APM) Integration Notes 2 RADIUS Integration 2.1 Test the RADIUS authentication 3 Logon page Customisation 3.1 Removing the Automatic TURing
F5 APM Integration Contents 1 F5 Big-IP Access Policy Manager (APM) Integration Notes 2 RADIUS Integration 2.1 Test the RADIUS authentication 3 Logon page Customisation 3.1 Removing the Automatic TURing
Table of Contents 1 Cisco AnyConnect...1
 Table of Contents 1 Cisco AnyConnect...1 2 Introduction...2 3 Cisco AnyConnect Integration...3 4 Cisco AnyConnect Client Integration...4 4.1 Configure the Cisco ASA...4 4.2 Install the Cisco AnyConnect
Table of Contents 1 Cisco AnyConnect...1 2 Introduction...2 3 Cisco AnyConnect Integration...3 4 Cisco AnyConnect Client Integration...4 4.1 Configure the Cisco ASA...4 4.2 Install the Cisco AnyConnect
Stonesoft Integration
 Stonesoft Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Setting up the RADIUS NAS 5.3 Enabling Session creation
Stonesoft Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Setting up the RADIUS NAS 5.3 Enabling Session creation
HOB Remote Desktop VPN
 HOB Remote Desktop VPN Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 5.3 Setting
HOB Remote Desktop VPN Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configuring the RADIUS server 5.2 Enabling Session creation with username 5.3 Setting
Microsoft OWA 2013 IIS Integration
 Microsoft OWA 2013 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 4 File Downloads 5 Architecture 6 Installation 6.1 Software Installation 6.2 Configuration of the IIS Filter 6.2.1
Microsoft OWA 2013 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 4 File Downloads 5 Architecture 6 Installation 6.1 Software Installation 6.2 Configuration of the IIS Filter 6.2.1
Microsoft OWA 2007 IIS Integration
 Microsoft OWA 2007 IIS Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Installation 5.1 Software Installation 5.2 Configuration of the IIS Filter 5.2.1 Swivel Settings 5.2.2
Microsoft OWA 2007 IIS Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Installation 5.1 Software Installation 5.2 Configuration of the IIS Filter 5.2.1 Swivel Settings 5.2.2
Aventail Remote Access
 Aventail Remote Access Shortly after your account is setup on Aventail, you will receive an email with the following subject line: PINsafe Account Details The email contains a 4 digit PIN which you will
Aventail Remote Access Shortly after your account is setup on Aventail, you will receive an email with the following subject line: PINsafe Account Details The email contains a 4 digit PIN which you will
Microsoft IIS version 6 Integration
 Microsoft IIS version 6 Integration Contents 1 Overview 2 Prerequisites 3 PINsafe Configuration 4 Configuring the IIS Server 4.1 Install the PINsafeIISFilter.exe 4.2 Configure the ISAPI filter 4.3 Create
Microsoft IIS version 6 Integration Contents 1 Overview 2 Prerequisites 3 PINsafe Configuration 4 Configuring the IIS Server 4.1 Install the PINsafeIISFilter.exe 4.2 Configure the ISAPI filter 4.3 Create
Microsoft Windows GINA login
 Microsoft Windows GINA login Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configure a Swivel Agent 5.2 Create a Third Party Authentication 6 Terminal Services
Microsoft Windows GINA login Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configure a Swivel Agent 5.2 Create a Third Party Authentication 6 Terminal Services
Microsoft ISA 2006 Integration. Microsoft Internet Security and Acceleration Server (ISA) Integration Notes Introduction
 Microsoft ISA 2006 Integration Contents 1 Microsoft Internet Security and Acceleration Server (ISA) Integration Notes 2 Introduction 3 Prerequisites 3.1 ISA 2006 Filter 3.2 TMG Filter 4 Baseline 5 Architecture
Microsoft ISA 2006 Integration Contents 1 Microsoft Internet Security and Acceleration Server (ISA) Integration Notes 2 Introduction 3 Prerequisites 3.1 ISA 2006 Filter 3.2 TMG Filter 4 Baseline 5 Architecture
Checkpoint SecureClient Integration
 Checkpoint SecureClient Integration Version 1.1 March 2010, Updated March 2014 Checkpoint SecureClient Integration Guide Contents 1 Introduction 1.1 Prerequisites 1.2 Baseline 1.3 Architecture 2 Swivel
Checkpoint SecureClient Integration Version 1.1 March 2010, Updated March 2014 Checkpoint SecureClient Integration Guide Contents 1 Introduction 1.1 Prerequisites 1.2 Baseline 1.3 Architecture 2 Swivel
Microsoft OWA 2010 IIS Integration
 Microsoft OWA 2010 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 3.1 Additional Prerequisites for Version 2.9 4 File Downloads 4.1 OWA Filter Change History 5 Architecture 6 Installation
Microsoft OWA 2010 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 3.1 Additional Prerequisites for Version 2.9 4 File Downloads 4.1 OWA Filter Change History 5 Architecture 6 Installation
SSL VPN Web Portal User Guide
 The SSL VPN web portal provides easy access to your organization s web resources via the web browser on your desktop or mobile device. The SSL VPN web portal's responsive interface automatically detects
The SSL VPN web portal provides easy access to your organization s web resources via the web browser on your desktop or mobile device. The SSL VPN web portal's responsive interface automatically detects
Secure Remote Access with Comprehensive Client Certificate Management
 APPLICATION NOTE SA Series SSL VPN Appliances and MultiFactor SecureAuth Solution Secure Remote Access with Comprehensive Client Certificate Management Copyright 2009, Juniper Networks, Inc. 1 Table of
APPLICATION NOTE SA Series SSL VPN Appliances and MultiFactor SecureAuth Solution Secure Remote Access with Comprehensive Client Certificate Management Copyright 2009, Juniper Networks, Inc. 1 Table of
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access)
 Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access) Published June 2015 Why do certain web-based applications have issues through the rewrite engine compared to accessing the resource
Secure Access Troubleshooting Rewrite related issues (Core/Web Based Access) Published June 2015 Why do certain web-based applications have issues through the rewrite engine compared to accessing the resource
Implementation Guide for protecting Juniper SSL VPN with BlackShield ID
 Implementation Guide for protecting Juniper SSL VPN with BlackShield ID Copyright Copyright 2011, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed,
Implementation Guide for protecting Juniper SSL VPN with BlackShield ID Copyright Copyright 2011, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed,
Taskbar for Windows. Contents. Overview. Prerequisites. Versions. PositiveID Support. Installer
 Taskbar for Windows Contents 1 Overview 1.1 Versions 1.2 PositiveID Support 1.3 Installer 2 Prerequisites 3 Architecture 4 Swivel Server Configuration 4.1 Enabling Session creation with username 5 Taskbar
Taskbar for Windows Contents 1 Overview 1.1 Versions 1.2 PositiveID Support 1.3 Installer 2 Prerequisites 3 Architecture 4 Swivel Server Configuration 4.1 Enabling Session creation with username 5 Taskbar
SSL VPN Web Portal User Guide
 The SSL VPN web portal provides easy access to your organization s web resources via the web browser on your desktop or mobile device. The SSL VPN web portal's responsive interface automatically detects
The SSL VPN web portal provides easy access to your organization s web resources via the web browser on your desktop or mobile device. The SSL VPN web portal's responsive interface automatically detects
Oracle WebLogic. Overview. Prerequisites. Baseline. Architecture. Installation. Contents
 Oracle WebLogic Contents 1 Overview 2 Prerequisites 3 Baseline 4 Architecture 5 Installation 5.1 Swivel Integration Configuration 5.1.1 Configuring Swivel for Agent XML Authentication 5.1.2 Configuring
Oracle WebLogic Contents 1 Overview 2 Prerequisites 3 Baseline 4 Architecture 5 Installation 5.1 Swivel Integration Configuration 5.1.1 Configuring Swivel for Agent XML Authentication 5.1.2 Configuring
Microsoft UAG Integration
 Microsoft UAG Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Installation 5.1 Configure The Swivel Server 5.1.1 Configure a RADIUS NAS entry 5.1.2 Configure Single Channel
Microsoft UAG Integration Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Installation 5.1 Configure The Swivel Server 5.1.1 Configure a RADIUS NAS entry 5.1.2 Configure Single Channel
San Jacinto College. Secure SSL VPN Instruction Manual. Contents
 1 San Jacinto College Secure SSL VPN Instruction Manual The new Secure SSL VPN provides a more secure and convenient method of accessing San Jacinto College resources remotely. This document provides an
1 San Jacinto College Secure SSL VPN Instruction Manual The new Secure SSL VPN provides a more secure and convenient method of accessing San Jacinto College resources remotely. This document provides an
Exam : JN Title : Juniper Networks Certified Internet Assoc(JNCIA-SSL) Exam. Version : Demo
 Exam : JN0-561 Title : Juniper Networks Certified Internet Assoc(JNCIA-SSL) Exam Version : Demo 1. Which model does not support clustering? A. SA700 B. SA2000 C. SA4000 D. SA6000 Answer: A 2. What is a
Exam : JN0-561 Title : Juniper Networks Certified Internet Assoc(JNCIA-SSL) Exam Version : Demo 1. Which model does not support clustering? A. SA700 B. SA2000 C. SA4000 D. SA6000 Answer: A 2. What is a
2 Oracle WebLogic Overview Prerequisites Baseline Architecture...6
 Table of Contents 1 Oracle Access Manager Integration...1 1.1 Overview...1 1.2 Prerequisites...1 1.3 Deployment...1 1.4 Integration...1 1.5 Authentication Process...1 2 Oracle WebLogic...2 3 Overview...3
Table of Contents 1 Oracle Access Manager Integration...1 1.1 Overview...1 1.2 Prerequisites...1 1.3 Deployment...1 1.4 Integration...1 1.5 Authentication Process...1 2 Oracle WebLogic...2 3 Overview...3
IVE Quick Startup Guide - OS 4.0
 IVE Quick Startup Guide - OS 4.0 Initial Setup Once you receive the IVE device, unpack the IVE and connect it to a PC or Laptop using the console (null modem) cable provided with the IVE. You have to connect
IVE Quick Startup Guide - OS 4.0 Initial Setup Once you receive the IVE device, unpack the IVE and connect it to a PC or Laptop using the console (null modem) cable provided with the IVE. You have to connect
How to Integrate RSA SecurID with the Barracuda Web Application Firewall
 How to Integrate RSA SecurID with the Barracuda Web Application Firewall The Barracuda Web Application Firewall can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA
How to Integrate RSA SecurID with the Barracuda Web Application Firewall The Barracuda Web Application Firewall can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA
Using Microsoft Azure Active Directory MFA as SAML IdP with Pulse Connect Secure. Deployment Guide
 Using Microsoft Azure Active Directory MFA as SAML IdP with Pulse Connect Secure Deployment Guide v1.0 May 2018 Introduction This document describes how to set up Pulse Connect Secure for SP-initiated
Using Microsoft Azure Active Directory MFA as SAML IdP with Pulse Connect Secure Deployment Guide v1.0 May 2018 Introduction This document describes how to set up Pulse Connect Secure for SP-initiated
Tivoli Common Reporting V Cognos report in a Tivoli Integrated Portal dashboard
 Tivoli Common Reporting V2.1.1 Cognos report in a Tivoli Integrated Portal dashboard Preethi C Mohan IBM India Ltd. India Software Labs, Bangalore +91 80 40255077 preethi.mohan@in.ibm.com Copyright IBM
Tivoli Common Reporting V2.1.1 Cognos report in a Tivoli Integrated Portal dashboard Preethi C Mohan IBM India Ltd. India Software Labs, Bangalore +91 80 40255077 preethi.mohan@in.ibm.com Copyright IBM
Clientless SSL VPN Remote Users
 This chapter summarizes configuration requirements and tasks for the user remote system. It also helps users get started with Clientless SSL VPN. It includes the following sections: Make sure that the
This chapter summarizes configuration requirements and tasks for the user remote system. It also helps users get started with Clientless SSL VPN. It includes the following sections: Make sure that the
Sentry SSO with Netscaler
 Sentry SSO with Netscaler Contents 1 Introduction 2 Overview 3 Configure Netscaler Login 4 Configuring Netscaler 5 Configuring Sentry Login 6 Configuring Sentry RADIUS 7 SSO 8 Authentication with AD/LDAP
Sentry SSO with Netscaler Contents 1 Introduction 2 Overview 3 Configure Netscaler Login 4 Configuring Netscaler 5 Configuring Sentry Login 6 Configuring Sentry RADIUS 7 SSO 8 Authentication with AD/LDAP
Android. Configuring Mobile Client user access on the Swivel virtual or hardware appliance
 Android Contents 1 The Swivel Android Client Overview 2 Prerequisites 3 Swivel Configuration 3.1 Configuring Mobile Client user access on the Swivel virtual or hardware appliance 3.2 Configuring the Swivel
Android Contents 1 The Swivel Android Client Overview 2 Prerequisites 3 Swivel Configuration 3.1 Configuring Mobile Client user access on the Swivel virtual or hardware appliance 3.2 Configuring the Swivel
Deliver and manage customer VIP POCs. The lab will be directed and provide you with step-by-step walkthroughs of key features.
 SR L15 Hands-On Lab Description Protecting Corporate Networks with Symantec Validation and ID Protection At the end of this lab, you should be able to Technically present and answer questions from your
SR L15 Hands-On Lab Description Protecting Corporate Networks with Symantec Validation and ID Protection At the end of this lab, you should be able to Technically present and answer questions from your
BIG-IP Access Policy Manager : Portal Access. Version 12.1
 BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
SSL VPN (Virtual Private Network) Service
 PolyU Admin VPN SSL VPN (Virtual Private Network) Service Installation and User Guide Table of Contents 1. Introduction... 2 2. System Requirements... 2 3. Session lifetime... 2 4. Installation and Login
PolyU Admin VPN SSL VPN (Virtual Private Network) Service Installation and User Guide Table of Contents 1. Introduction... 2 2. System Requirements... 2 3. Session lifetime... 2 4. Installation and Login
Management Console User s Guide (AST 2500 Chipset)
 Management Console User s Guide (AST 2500 Chipset) Version: 1.2 Table of Contents Using Your Management Console... 2 Management Console Key Features and Functions... 3 Software Install... 4 Prerequisites
Management Console User s Guide (AST 2500 Chipset) Version: 1.2 Table of Contents Using Your Management Console... 2 Management Console Key Features and Functions... 3 Software Install... 4 Prerequisites
How to connect to the University of Exeter VPN service
 How to connect to the University of Exeter VPN service *****Important Part of the process of using the VPN service involves the automatic download and installation of Juniper Network Connect software,
How to connect to the University of Exeter VPN service *****Important Part of the process of using the VPN service involves the automatic download and installation of Juniper Network Connect software,
User Guide Published: 08/02/2010
 User Guide Published: 08/02/2010 Table of Contents 1 Revision History... 4 2 Introduction... 5 3 Accessing the TRAC Connect System... 5 3.1 Getting Started... 5 3.2 Registration... 8 3.3 Login... 11 3.4
User Guide Published: 08/02/2010 Table of Contents 1 Revision History... 4 2 Introduction... 5 3 Accessing the TRAC Connect System... 5 3.1 Getting Started... 5 3.2 Registration... 8 3.3 Login... 11 3.4
VMware View (Horizon)
 VMware View (Horizon) Contents 1 Introduction 2 Credits 3 Prerequisites 4 Baseline 5 Architecture 6 Swivel Configuration 6.1 Configuring the RADIUS server 6.2 Setting up the RADIUS NAS 6.3 Enabling Session
VMware View (Horizon) Contents 1 Introduction 2 Credits 3 Prerequisites 4 Baseline 5 Architecture 6 Swivel Configuration 6.1 Configuring the RADIUS server 6.2 Setting up the RADIUS NAS 6.3 Enabling Session
Configuring the CSS for Device Management
 CHAPTER 2 Configuring the CSS for Device Management Before you can use the WebNS Device Management user interface software, you need to perform the tasks described in the following sections: WebNS Device
CHAPTER 2 Configuring the CSS for Device Management Before you can use the WebNS Device Management user interface software, you need to perform the tasks described in the following sections: WebNS Device
Windows quick start instructions Pg. 1. OS X quick start instructions Pg. 4. ios quick start instructions Pg. 6
 Page 1 of 12 Windows quick start instructions Pg. 1 OS X quick start instructions Pg. 4 ios quick start instructions Pg. 6 Android quick start instructions Pg. 9 Windows Quick Start Instructions STEP 1
Page 1 of 12 Windows quick start instructions Pg. 1 OS X quick start instructions Pg. 4 ios quick start instructions Pg. 6 Android quick start instructions Pg. 9 Windows Quick Start Instructions STEP 1
Integration Guide. SafeNet Authentication Service. Strong Authentication for Juniper Networks SSL VPN
 SafeNet Authentication Service Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Service Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
Click Studios. Passwordstate. Remote Session Launcher. Installation Instructions
 Passwordstate Remote Session Launcher Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Passwordstate Remote Session Launcher Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Clientless SSL VPN End User Set-up
 71 CHAPTER This section is for the system administrator who sets up Clientless (browser-based) SSL VPN for end users. It summarizes configuration requirements and tasks for the user remote system. It also
71 CHAPTER This section is for the system administrator who sets up Clientless (browser-based) SSL VPN for end users. It summarizes configuration requirements and tasks for the user remote system. It also
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
Mobile Access Guide Using WhatsUp Gold Mobile Access
 Mobile Access Guide Using WhatsUp Gold Mobile Access Contents CHAPTER 1 Using WhatsUp Gold Mobile Access Managing WhatsUp Gold Mobile Access... 1 Accessing WhatsUp Gold from a mobile device... 2 CHAPTER
Mobile Access Guide Using WhatsUp Gold Mobile Access Contents CHAPTER 1 Using WhatsUp Gold Mobile Access Managing WhatsUp Gold Mobile Access... 1 Accessing WhatsUp Gold from a mobile device... 2 CHAPTER
Using VPN. Provider Staff
 Using VPN Provider Staff 1 Internet Explorer (32-bit) Enter https://vpn.djj.state.fl.us in the address bar You will need to use IE-32bit. 64-bit machines have the IE 64-bit option as well. To check this
Using VPN Provider Staff 1 Internet Explorer (32-bit) Enter https://vpn.djj.state.fl.us in the address bar You will need to use IE-32bit. 64-bit machines have the IE 64-bit option as well. To check this
Juniper Networks SSL VPN Integration Guide
 Juniper Networks SSL VPN Integration Guide Introduction Overview Terms Setting Up an Authentication Server Creating a User Role Creating a User Realm Setting Up Your Sign In URL top Introduction This document
Juniper Networks SSL VPN Integration Guide Introduction Overview Terms Setting Up an Authentication Server Creating a User Role Creating a User Realm Setting Up Your Sign In URL top Introduction This document
JN0-355 Q&As. Junos Pulse Secure Access, Specialist (JNCIS-SA) Pass Juniper JN0-355 Exam with 100% Guarantee
 JN0-355 Q&As Junos Pulse Secure Access, Specialist (JNCIS-SA) Pass Juniper JN0-355 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money
JN0-355 Q&As Junos Pulse Secure Access, Specialist (JNCIS-SA) Pass Juniper JN0-355 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money
HTTP 1.1 Web Server and Client
 The feature provides a consistent interface for users and applications by implementing support for HTTP 1.1 in Cisco IOS XE software-based devices. When combined with the HTTPS feature, the feature provides
The feature provides a consistent interface for users and applications by implementing support for HTTP 1.1 in Cisco IOS XE software-based devices. When combined with the HTTPS feature, the feature provides
The process of creating a Mobile Connect connection is slightly different depending on which type of SonicWall appliance you are connecting to.
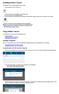 Installing Mobile Connect SonicWall Mobile Connect is installed through the Chrome Web Store. 1 On your Chromebook, click the Web Store icon. 2 In the Search field, type in SonicWall Mobile Connect, and
Installing Mobile Connect SonicWall Mobile Connect is installed through the Chrome Web Store. 1 On your Chromebook, click the Web Store icon. 2 In the Search field, type in SonicWall Mobile Connect, and
ForeScout CounterACT. Configuration Guide. Version 4.1
 ForeScout CounterACT Network Module: VPN Concentrator Plugin Version 4.1 Table of Contents About the VPN Concentrator Plugin... 3 What to Do... 3 Requirements... 3 CounterACT Requirements... 3 Supported
ForeScout CounterACT Network Module: VPN Concentrator Plugin Version 4.1 Table of Contents About the VPN Concentrator Plugin... 3 What to Do... 3 Requirements... 3 CounterACT Requirements... 3 Supported
Sticky Notes for Cognos Analytics by Tech Data BSP Software
 Sticky Notes for Cognos Analytics by Tech Data BSP Software Installation Guide Sticky Notes for Cognos Analytics is an easy to install extension that allows report authors to record notes directly from
Sticky Notes for Cognos Analytics by Tech Data BSP Software Installation Guide Sticky Notes for Cognos Analytics is an easy to install extension that allows report authors to record notes directly from
Upgrade Guide. Platform Compatibility. SonicWALL Aventail E-Class SRA EX-Series v Secure Remote Access
 Secure Remote Access This document describes the process of obtaining your SonicWALL Aventail E-Class SRA EX-Series update file, verifying it, and installing it on an existing appliance. Updating a clustered
Secure Remote Access This document describes the process of obtaining your SonicWALL Aventail E-Class SRA EX-Series update file, verifying it, and installing it on an existing appliance. Updating a clustered
Welcome to the CP Portal
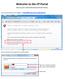 Welcome to the CP Portal Access your school documents from home Launch Internet Explorer and navigate to: https://files.cpcsc.k12.in.us/htcomnet/ Click on Continue to this website (not recommended) Key
Welcome to the CP Portal Access your school documents from home Launch Internet Explorer and navigate to: https://files.cpcsc.k12.in.us/htcomnet/ Click on Continue to this website (not recommended) Key
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
4TRESS AAA. Out-of-Band Authentication (SMS) and Juniper Secure Access Integration Handbook. Document Version 2.3 Released May hidglobal.
 4TRESS AAA Out-of-Band Authentication (SMS) and Juniper Secure Access Integration Handbook Document Version 2.3 Released May 2013 hidglobal.com Table of Contents List of Figures... 3 1.0 Introduction...
4TRESS AAA Out-of-Band Authentication (SMS) and Juniper Secure Access Integration Handbook Document Version 2.3 Released May 2013 hidglobal.com Table of Contents List of Figures... 3 1.0 Introduction...
Accessing the MBA Applications Page
 Accessing DeGroote MBA Apps on Windows 7/8 The DeGroote School of Business has implemented Microsoft RemoteApp to deliver applications to its students remotely over the local McMaster network and Internet
Accessing DeGroote MBA Apps on Windows 7/8 The DeGroote School of Business has implemented Microsoft RemoteApp to deliver applications to its students remotely over the local McMaster network and Internet
Should you encounter any issues or have questions as you go through this registration process, please send an to:
 User Registration In order to use EFIS 2.0, a one-time registration process is required. This document outlines the steps required to register your user account and access EFIS 2.0: This registration process
User Registration In order to use EFIS 2.0, a one-time registration process is required. This document outlines the steps required to register your user account and access EFIS 2.0: This registration process
SCRIPT REFERENCE. UBot Studio Version 4. The Browser Commands
 SCRIPT REFERENCE UBot Studio Version 4 The Browser Commands Navigate This command will navigate to whatever url you insert into the url field within the command. In the section of the command labeled Advanced,
SCRIPT REFERENCE UBot Studio Version 4 The Browser Commands Navigate This command will navigate to whatever url you insert into the url field within the command. In the section of the command labeled Advanced,
How can I view my W2 on Vibe?
 How can I view my W2 on Vibe? Within this document you will find easy How To, step by step instructions for logging onto Vibe and accessing your W2. How to Logon: In your browser s address bar, type the
How can I view my W2 on Vibe? Within this document you will find easy How To, step by step instructions for logging onto Vibe and accessing your W2. How to Logon: In your browser s address bar, type the
AD218 Working with Customers via the IBM Lotus Sametime Links Toolkit. Carl Tyler Instant Technologies
 AD218 Working with Customers via the IBM Lotus Sametime Links Toolkit Carl Tyler Instant Technologies Agenda What is Lotus Sametime Links (STLinks) Adding STLinks to your site Building a STLinks queuing
AD218 Working with Customers via the IBM Lotus Sametime Links Toolkit Carl Tyler Instant Technologies Agenda What is Lotus Sametime Links (STLinks) Adding STLinks to your site Building a STLinks queuing
Testing Documentation
 Testing Documentation Create-A-Page Group 9: John Campbell, Matthew Currier, Dan Martin 5/1/2009 This document defines the methods for testing Create-A-Page, as well as the results of those tests and the
Testing Documentation Create-A-Page Group 9: John Campbell, Matthew Currier, Dan Martin 5/1/2009 This document defines the methods for testing Create-A-Page, as well as the results of those tests and the
Pulse Secure Policy Secure
 Policy Secure RSA SecurID Ready Implementation Guide Last Modified: November 19, 2014 Partner Information Product Information Partner Name Pulse Secure Web Site http://www.pulsesecure.net/ Product Name
Policy Secure RSA SecurID Ready Implementation Guide Last Modified: November 19, 2014 Partner Information Product Information Partner Name Pulse Secure Web Site http://www.pulsesecure.net/ Product Name
Storage Made Easy Cloud Appliance installation Guide
 dev.storagemadeeasy.com Storage Made Easy Cloud Appliance installation Guide 4 min read original Configuring the SME Appliance The configuration server allows you to configure - Static IP address - Domain
dev.storagemadeeasy.com Storage Made Easy Cloud Appliance installation Guide 4 min read original Configuring the SME Appliance The configuration server allows you to configure - Static IP address - Domain
Cisco Unified Serviceability
 Cisco Unified Serviceability Introduction, page 1 Installation, page 5 Introduction This document uses the following abbreviations to identify administration differences for these Cisco products: Unified
Cisco Unified Serviceability Introduction, page 1 Installation, page 5 Introduction This document uses the following abbreviations to identify administration differences for these Cisco products: Unified
Configuring Proxy Settings. STEP 1: (Gathering Proxy Information) Windows
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
Barracuda Networks SSL VPN
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: October 24, 2013 Product Information Partner Name Barracuda Networks Web Site https://www.barracuda.com/ Product Name Barracuda
RSA SecurID Ready Implementation Guide Partner Information Last Modified: October 24, 2013 Product Information Partner Name Barracuda Networks Web Site https://www.barracuda.com/ Product Name Barracuda
Remote VPN Remote access for personal devices
 Remote VPN Remote access for personal devices About Remote VPN Remote VPN provides staff and students with secure, authenticated remote access to personal and shared network filespace and to web-based
Remote VPN Remote access for personal devices About Remote VPN Remote VPN provides staff and students with secure, authenticated remote access to personal and shared network filespace and to web-based
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER
 DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
HTTP 1.1 Web Server and Client
 HTTP 1.1 Web Server and Client Finding Feature Information HTTP 1.1 Web Server and Client Last Updated: June 01, 2011 The HTTP 1.1 Web Server and Client feature provides a consistent interface for users
HTTP 1.1 Web Server and Client Finding Feature Information HTTP 1.1 Web Server and Client Last Updated: June 01, 2011 The HTTP 1.1 Web Server and Client feature provides a consistent interface for users
UI-9 OS Installation Guide in SmartCLOUD Director. CITIC Telecom CPC. OS Installation Guide in SmartCLOUD Director
 CITIC Telecom CPC OS Installation Guide in SmartCLOUD Director February 2016 This is a quick start guide for user who is totally new to SmartCLOUD Director. In this guide, we will demonstrate 2 ways on
CITIC Telecom CPC OS Installation Guide in SmartCLOUD Director February 2016 This is a quick start guide for user who is totally new to SmartCLOUD Director. In this guide, we will demonstrate 2 ways on
Google Apps Integration
 Google Apps Integration Contents 1 Using Swivel for Google Apps Authentication 2 Prerequisites 3 Google SSO 4 Swivel and Google Apps 5 User Experience 6 Install the Swivel Google software 7 Create private
Google Apps Integration Contents 1 Using Swivel for Google Apps Authentication 2 Prerequisites 3 Google SSO 4 Swivel and Google Apps 5 User Experience 6 Install the Swivel Google software 7 Create private
Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide
 Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide Policy Manager for IBM WebSphere DataPower Configuration Guide SOAPMDP_Config_7.2.0 Copyright Copyright 2015 SOA Software, Inc. All rights
Policy Manager for IBM WebSphere DataPower 7.2: Configuration Guide Policy Manager for IBM WebSphere DataPower Configuration Guide SOAPMDP_Config_7.2.0 Copyright Copyright 2015 SOA Software, Inc. All rights
Web Push Notification
 Web Push Notification webkul.com/blog/web-push-notification-for-magento2/ On - January 13, 2017 This impressive module allows you to send push notification messages directly to the web browser. The biggest
Web Push Notification webkul.com/blog/web-push-notification-for-magento2/ On - January 13, 2017 This impressive module allows you to send push notification messages directly to the web browser. The biggest
Web Device Manager Guide
 Juniper Networks EX2500 Ethernet Switch Web Device Manager Guide Release 3.0 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Part Number: 530-029704-01,
Juniper Networks EX2500 Ethernet Switch Web Device Manager Guide Release 3.0 Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USA 408-745-2000 www.juniper.net Part Number: 530-029704-01,
Joomla User Guide Ver 3
 LiveHelp Server Joomla User Guide Ver 3 Introduction The process of configuration and implementation of the LiveHelp server is divided into four stages, which are detailed below. The approximate time of
LiveHelp Server Joomla User Guide Ver 3 Introduction The process of configuration and implementation of the LiveHelp server is divided into four stages, which are detailed below. The approximate time of
Client 2. Authentication 5
 Pipeline Pilot Web Port Support Guide April 2011 Contents Requirements 2 Requirements 2 Server 2 Client 2 Web Port Access 3 Authentication 5 Introduction Pipeline Pilot Web Port is a web-based application
Pipeline Pilot Web Port Support Guide April 2011 Contents Requirements 2 Requirements 2 Server 2 Client 2 Web Port Access 3 Authentication 5 Introduction Pipeline Pilot Web Port is a web-based application
Lotus Notes Domino 6/ 6.5 Developing Web Applications.
 Lotus 190-612 Notes Domino 6/ 6.5 Developing Web Applications http://killexams.com/exam-detail/190-612 QUESTION: 81 Rob uses Macromedia Dreamweaver MX to create HTML files, style sheets and JavaScript
Lotus 190-612 Notes Domino 6/ 6.5 Developing Web Applications http://killexams.com/exam-detail/190-612 QUESTION: 81 Rob uses Macromedia Dreamweaver MX to create HTML files, style sheets and JavaScript
Checklist. Version 2.0 October 2015
 Version 2.0 October 2015 Checklist Table of Contents Setup Issues 3 Virtual Services Platform 3 Device LinkUp 5 Desktop LP 6 VPN LP 6 Usage 7 Virtual Services Platform 7 VPN LP 7 Migration 8 AppDirect
Version 2.0 October 2015 Checklist Table of Contents Setup Issues 3 Virtual Services Platform 3 Device LinkUp 5 Desktop LP 6 VPN LP 6 Usage 7 Virtual Services Platform 7 VPN LP 7 Migration 8 AppDirect
DreamFactory Customer Privacy and Security Whitepaper Delivering Secure Applications on Salesforce.com
 DreamFactory Customer Privacy and Security Whitepaper Delivering Secure Applications on Salesforce.com By Bill Appleton, CTO, DreamFactory Software billappleton@dreamfactory.com Introduction DreamFactory
DreamFactory Customer Privacy and Security Whitepaper Delivering Secure Applications on Salesforce.com By Bill Appleton, CTO, DreamFactory Software billappleton@dreamfactory.com Introduction DreamFactory
Examples of Cisco APE Scenarios
 CHAPTER 5 This chapter describes three example scenarios with which to use Cisco APE: Access to Asynchronous Lines, page 5-1 Cisco IOS Shell, page 5-3 Command Authorization, page 5-5 Note For intructions
CHAPTER 5 This chapter describes three example scenarios with which to use Cisco APE: Access to Asynchronous Lines, page 5-1 Cisco IOS Shell, page 5-3 Command Authorization, page 5-5 Note For intructions
Sentry SSO with Cisco ASA
 Sentry SSO with Cisco ASA Contents 1 Introduction 2 Configure Cisco ASA 3 Configure Swivel Sentry 4 Configure RADIUS NAS on Swivel Core 5 SSO 6 Known Issues/Limitations Introduction This Document describes
Sentry SSO with Cisco ASA Contents 1 Introduction 2 Configure Cisco ASA 3 Configure Swivel Sentry 4 Configure RADIUS NAS on Swivel Core 5 SSO 6 Known Issues/Limitations Introduction This Document describes
Managing GSS Devices from the GUI
 CHAPTER 1 This chapter describes how to configure and manage your Global Site Selector Manager (GSSM) and Global Site Selector (GSS) devices from the primary GSSM graphical user interface. It includes
CHAPTER 1 This chapter describes how to configure and manage your Global Site Selector Manager (GSSM) and Global Site Selector (GSS) devices from the primary GSSM graphical user interface. It includes
Hypersocket SSO. Lee Painter HYPERSOCKET LIMITED Unit 1, Vision Business Centre, Firth Way, Nottingham, NG6 8GF, United Kingdom. Getting Started Guide
 Hypersocket SSO Getting Started Guide Lee Painter HYPERSOCKET LIMITED Unit 1, Vision Business Centre, Firth Way, Nottingham, NG6 8GF, United Kingdom Table of Contents PREFACE... 4 DOCUMENT OBJECTIVE...
Hypersocket SSO Getting Started Guide Lee Painter HYPERSOCKET LIMITED Unit 1, Vision Business Centre, Firth Way, Nottingham, NG6 8GF, United Kingdom Table of Contents PREFACE... 4 DOCUMENT OBJECTIVE...
Cloud Help for Community Managers...3. Release Notes System Requirements Administering Jive for Office... 6
 for Office Contents 2 Contents Cloud Help for Community Managers...3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
for Office Contents 2 Contents Cloud Help for Community Managers...3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
IT Access Portal User Guide (Employees)
 IT Access Portal User Guide (Employees) Introduction The University of Salford IT Access Portal provides University employees with secure, off-campus access to core IT applications and resources; for example:
IT Access Portal User Guide (Employees) Introduction The University of Salford IT Access Portal provides University employees with secure, off-campus access to core IT applications and resources; for example:
Table of Contents. 1. Background Logging In Account Setup Requests Submissions Discussions...
 Trust Safety: PwC Connect Tool Upload Release: Final Updated November 2018 Table of Contents 1. Background... 3 2. Logging In... 4 3. Account Setup... 8 3. Requests... 9 4. Submissions... 10 5. Discussions...
Trust Safety: PwC Connect Tool Upload Release: Final Updated November 2018 Table of Contents 1. Background... 3 2. Logging In... 4 3. Account Setup... 8 3. Requests... 9 4. Submissions... 10 5. Discussions...
User pages for RM Portico
 Using gives you access to your files on your school or college network from a browser on any computer (including desktops, laptops, tablets, netbooks and smartphones; for more information see Appendix
Using gives you access to your files on your school or college network from a browser on any computer (including desktops, laptops, tablets, netbooks and smartphones; for more information see Appendix
Import Data Connection from an SAP Universe
 Import Data Connection from an SAP Universe SAP Analytics Cloud allows you to connect to SAP Universe and import your data. NOTE: It is recommended that the SAP Cloud Platform Cloud Connector (SAP CP CC)
Import Data Connection from an SAP Universe SAP Analytics Cloud allows you to connect to SAP Universe and import your data. NOTE: It is recommended that the SAP Cloud Platform Cloud Connector (SAP CP CC)
Polytechnic e-learning: LMS Manual - LECTURER
 Polytechnic e-learning: LMS Manual - LECTURER JPP & USTM 2014 TABLE OF CONTENTS 1. ACCESSING LMS... 1 2. LOG IN... 1 3. MANAGE STUDENT SELF-ENROLMENT... 1 4. MANAGE COURSE LANDING PAGE... 1 5. MANAGE COURSE
Polytechnic e-learning: LMS Manual - LECTURER JPP & USTM 2014 TABLE OF CONTENTS 1. ACCESSING LMS... 1 2. LOG IN... 1 3. MANAGE STUDENT SELF-ENROLMENT... 1 4. MANAGE COURSE LANDING PAGE... 1 5. MANAGE COURSE
HTTP 1.1 Web Server and Client
 HTTP 1.1 Web Server and Client Last Updated: October 12, 2011 The HTTP 1.1 Web Server and Client feature provides a consistent interface for users and applications by implementing support for HTTP 1.1
HTTP 1.1 Web Server and Client Last Updated: October 12, 2011 The HTTP 1.1 Web Server and Client feature provides a consistent interface for users and applications by implementing support for HTTP 1.1
