Duo at BU. Our two-factor authentication plan
|
|
|
- Marlene Campbell
- 5 years ago
- Views:
Transcription
1 Duo at BU Our two-factor authentication plan
2 Tom Grundig - Information Security, Boston University Information Security Operations Manager SAP Security & GRC Lead Former Asst. Dir of Internal Audit Duo Project A little of this, a little of that
3 Where we left of last We got phished. Bad. People were tricked by a believable message into giving their passwords to the bad guys Spear-phishers and their tactics Message crafted for BU Sent to a small number of selected people Strike on weekends & holidays, when you are less protected Goals To collect information that will let them steal money: Passwords, social security numbers, bank account or credit card numbers
4 Response Short-term Creation of a notification tool that to alert users when you re their direct deposit account or home address is changed Requiring you to enter the existing bank account be entered before it can be changed Before you can change your bank routing information, confirm your existing account number Confirm Revamp Spam Assassin Code Extended Validate Certificates
5 Response Long-term - Goals Address problem, not the symptom Problem Compromised credentials The only real defense is to use something more than just knowledge Integrate with current authentication plans Modern and flexible option Rapid deployment Easy to administer and support Affordable Need a Big Win
6 Response Long-term - Challenges Social/Political Unions, Faculty, Past History Technical Short Timeframe Needed to act while issue was fresh Potential Costs Can t be seen as a Road block
7 Two-Factor Authentication for everyone
8
9 Duo Security why it works for us Strategic & Affordable From InCommon/Internet2 Integrates with our strategic weblogin replacement Simple and flexible No tokens required Rapid initial setup Single-button confirmation when using the app Also supports text message, phone calls, tokens and other approaches Can remember a device for 30 days (single-user systems only) Only need to do your two-factor confirmation once a month Work anywhere in the world Can work with no connection
10 The Plan
11 (in a good way)
12 The Plan (seriously this time) Scope & Timeline Analysis & Stakeholder Support Team Build & Test Communication Roll-Out Support
13 Scope & Timeline Who - All BU Employees Staff, Faculty, Student Employees What - Protect SAP initially Integrate with Shibboleth Login When Starting June 2014 PoC needed within days Technical completion approx 1 month Phased Roll-Out
14 Analysis and Stakeholder Support Analysis Technical as well as Social/Political Support from the highest levels President Sr. VP for Financial Affairs VP of Information Services & Technology Exec Dir. of Information Security Reviewed with Council of Deans as well as Key Business Units
15 The Team Internal Experts in various areas Project Management Architecture and Engineering Identity & Access Management Process and Operations Business Area Input & Audit Quality Assurance Documentation and Training Communication Service Desk
16 Build & Test Infrastructure Layout F5 load balancer in front of 3 Centos 5 VM instances with short-term source IP affinity to ensure that entire IdP transaction occurs on same instance. Each instance has 2 vcpus and 4G of memory and standard disk allocation (64G). Kerberos passwords are validated using our campus MIT Kerberos 5 servers while attribute resolution uses OpenLDAP servers with a copy of our campus database. Software Stack Oracle Java 1.6 Tomcat Shibboleth IdP Duo integration is out of the box using the instructions at: Only Boston University change was our branded login page. Cloud Service Considerations Fail closed Back up users Features Changes
17 Communication Started with a letter from The Top Follow-Up memos from IS&T Focus Groups & Road Shows Step by Step documentation Training Videos BU website bu.edu/tech/duo Docs, videos, faqs, banners Targeted s to enrolled groups
18 Roll-Out June Pilot - All of IS&T, SAP Support Team and Users with access to regulated data July Open Opt In Period September- Staff October- Faculty November Student Employees mandatory for any/all users who access SAP
19 Support 70 Duo Administrators (!!!) Information Security Service Desk Desktop Support IT Partners
20 So How s it going?
21 Statistics so far Pilot - 487users 46 tickets in first month (pilot) Opt In (7/7-today) have opted in (360 on first day) Staff 58% Faculty 28% Student 14% 77 tickets 1428 devices 729 ios 244 Landline 291 Android 135 Other 20 Windows Phone 9 BlackBerry
22 What s Next Duo to replace all current 2 nd Factor tools NC-Pass (Mainframe) Defender (Quest Terminal Services) Duo s potential for new services Win RDP, VMWare, Cisco, RADIUS
23 Questions?
24 More information Reporting phishing attempts particularly ones that try to masquerade as BU to: Visit A link and a video on the Data Protection Standards How To Section Avoid Phishing Choose a Strong Password (that s easy to remember)
Solving for Compromised Credentials Across the Enterprise
 Solving for Compromised Credentials Across the Enterprise Boston University s Multi-Factor Authentication Implementation Tom Grundig, Assistant Director, Information Security, Boston University The Boston
Solving for Compromised Credentials Across the Enterprise Boston University s Multi-Factor Authentication Implementation Tom Grundig, Assistant Director, Information Security, Boston University The Boston
Monitise. RSA Adaptive Authentication On-Premise Implementation Guide. Partner Information. Monitise Mobile Banking Solution
 RSA Adaptive Authentication On-Premise Implementation Guide Partner Information Last Modified: June 12, 2013 Product Information Partner Name Web Site www.monitise.com Product Name Version & Platform 5.0
RSA Adaptive Authentication On-Premise Implementation Guide Partner Information Last Modified: June 12, 2013 Product Information Partner Name Web Site www.monitise.com Product Name Version & Platform 5.0
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Modern two-factor authentication: Easy. Affordable. Secure.
 Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Detecting and Dealing with Compromised Accounts in Cloud Platforms
 Detecting and Dealing with Compromised Accounts in Cloud Platforms Nick Young - IT Manager, Application Administration Kevin McClain - Google Apps Administrator UNC CAUSE 2016 1:45-2:30pm, Thursday October
Detecting and Dealing with Compromised Accounts in Cloud Platforms Nick Young - IT Manager, Application Administration Kevin McClain - Google Apps Administrator UNC CAUSE 2016 1:45-2:30pm, Thursday October
Texas A&M University: Learning Management System General & Application Controls Review
 Overall Conclusion Overall, the controls established over the primary learning management system at Texas A&M University, Blackboard Learn (ecampus), are effective in providing reasonable assurance that
Overall Conclusion Overall, the controls established over the primary learning management system at Texas A&M University, Blackboard Learn (ecampus), are effective in providing reasonable assurance that
Duo End User Education Templates
 Duo End User Education Email Templates Table of Contents Email Communication Best Practices Email Templates Email #1 - Duo is coming soon, no immediate action required. Email #2 - Duo is coming on ,
Duo End User Education Email Templates Table of Contents Email Communication Best Practices Email Templates Email #1 - Duo is coming soon, no immediate action required. Email #2 - Duo is coming on ,
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
Vice President for Information Technology Status and Activity Report for April 2019
 Vice President for Information Technology Status and Activity Report for April 2019 Prepared by Timothy M. Chester, Vice President for Information Technology (VPIT) 1. Items Requiring Action Verify and
Vice President for Information Technology Status and Activity Report for April 2019 Prepared by Timothy M. Chester, Vice President for Information Technology (VPIT) 1. Items Requiring Action Verify and
Keep the Door Open for Users and Closed to Hackers
 Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
POLICIES AND PROCEDURES
 Integrated Information Technology Services POLICIES AND PROCEDURES Utica College Email POLICY: Email is Utica College s sole accepted mechanism for official electronic communication in the normal conduct
Integrated Information Technology Services POLICIES AND PROCEDURES Utica College Email POLICY: Email is Utica College s sole accepted mechanism for official electronic communication in the normal conduct
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: Concordia University of Edmonton Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that
Participant Name: Concordia University of Edmonton Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that
DUO SECURITY SETUP INSTRUCTIONS
 DUO SECURITY SETUP INSTRUCTIONS Click on a link below to jump to a section Guide Contents INTRODUCTION TO DUO... 1 REQUESTING ACCESS... 2 EMAIL... 2 DEVICE OPTIONS... 2 ENROLLMENT GUIDE... 3 SETUP USING
DUO SECURITY SETUP INSTRUCTIONS Click on a link below to jump to a section Guide Contents INTRODUCTION TO DUO... 1 REQUESTING ACCESS... 2 EMAIL... 2 DEVICE OPTIONS... 2 ENROLLMENT GUIDE... 3 SETUP USING
hidglobal.com HID ActivOne USER FRIENDLY STRONG AUTHENTICATION
 HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
Information & Technology Services. Opting in for Multi-Factor Authentication
 Information & Technology Services Opting in for Multi-Factor Authentication Login to mycampus.astate.edu When logged in, After you have logged in successfully, you should see folders on the left side of
Information & Technology Services Opting in for Multi-Factor Authentication Login to mycampus.astate.edu When logged in, After you have logged in successfully, you should see folders on the left side of
IAM Project Overview & Milestones
 IAM Project Overview & Milestones TABLE OF CONTENTS IAM PROJECT SUCCESS FACTORS 3 PROJECT SCOPE 3 IN SCOPE 3 OUT OF SCOPE 4 IAM NOW VS. FUTURE 5 IAM NOW 5 IAM IN THE FUTURE 7 IAM PROJECT END STATE 8 ACCESS
IAM Project Overview & Milestones TABLE OF CONTENTS IAM PROJECT SUCCESS FACTORS 3 PROJECT SCOPE 3 IN SCOPE 3 OUT OF SCOPE 4 IAM NOW VS. FUTURE 5 IAM NOW 5 IAM IN THE FUTURE 7 IAM PROJECT END STATE 8 ACCESS
ManageEngine ADSelfService Plus
 Comparison Document ManageEngine ADSelfService Plus Vs Azure AD Self-Service Password Reset (SSPR) ManageEngine ADSelfService Plus vs. Azure AD Self-Service Password Reset (SSPR) Password reset tickets
Comparison Document ManageEngine ADSelfService Plus Vs Azure AD Self-Service Password Reset (SSPR) ManageEngine ADSelfService Plus vs. Azure AD Self-Service Password Reset (SSPR) Password reset tickets
2-Step Verification. Summer 2018, Version 3. Table of Contents
 2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
AAI-SSO with Active Directory. Kerberos Login Handler
 AAI-SSO with Active Directory Kerberos Login Handler Project Overview One of FHNW s AAA projects Use case: SSO for AAI Applications with Active Directory domain logins Project goal: Development of a Kerberos
AAI-SSO with Active Directory Kerberos Login Handler Project Overview One of FHNW s AAA projects Use case: SSO for AAI Applications with Active Directory domain logins Project goal: Development of a Kerberos
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
News and Updates June 1, 2017
 Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Whitepaper on AuthShield Two Factor Authentication with SAP
 Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
Whitepaper on AuthShield Two Factor Authentication with SAP By AuthShield Labs Pvt. Ltd Table of Contents Table of Contents...2 1.Overview...4 2. Threats to account passwords...5 2.1 Social Engineering
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
ISE North America Leadership Summit and Awards
 ISE North America Leadership Summit and Awards November 6-7, 2013 Presentation Title: Presenter: Presenter Title: Company Name: Embracing Cyber Security for Top-to-Bottom Results Larry Wilson Chief Information
ISE North America Leadership Summit and Awards November 6-7, 2013 Presentation Title: Presenter: Presenter Title: Company Name: Embracing Cyber Security for Top-to-Bottom Results Larry Wilson Chief Information
2013 InterWorks, Page 1
 2013 InterWorks, Page 1 The BYOD Phenomenon 68% of devices used by information workers to access business applications are ones they own themselves, including laptops, smartphones, and tablets. IT organizations
2013 InterWorks, Page 1 The BYOD Phenomenon 68% of devices used by information workers to access business applications are ones they own themselves, including laptops, smartphones, and tablets. IT organizations
UofM Secure Wireless 2/14/2018. Brought to you by: umtech & The Center for Teaching & Learning
 UofM Secure Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website 2/14/2018
UofM Secure Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website 2/14/2018
Microsoft Refurbisher Programs. Program Overview for MAR & RRP
 Microsoft Refurbisher Programs Program Overview for MAR & RRP Programs Overview Microsoft Refurbisher Programs offer refurbishers reduced royalty software licenses for genuine Microsoft software, tools
Microsoft Refurbisher Programs Program Overview for MAR & RRP Programs Overview Microsoft Refurbisher Programs offer refurbishers reduced royalty software licenses for genuine Microsoft software, tools
E mail, Calendar, and Contacts Transition Project. Faculty Senate Executive Board Briefing
 E mail, Calendar, and Contacts Transition Project Faculty Senate Executive Board Briefing Virtual Teams The Blue Print Employees (Faculty, Staff and Student Employees) Students GT Email Address Received
E mail, Calendar, and Contacts Transition Project Faculty Senate Executive Board Briefing Virtual Teams The Blue Print Employees (Faculty, Staff and Student Employees) Students GT Email Address Received
CE Advanced Network Security Phishing I
 CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
<Partner Name> <Partner Product> RSA SECURID ACCESS. VMware Horizon View 7.2 Clients. Standard Agent Client Implementation Guide
 RSA SECURID ACCESS Standard Agent Client Implementation Guide VMware Horizon View 7.2 Clients Daniel R. Pintal, RSA Partner Engineering Last Modified: September 14, 2017
RSA SECURID ACCESS Standard Agent Client Implementation Guide VMware Horizon View 7.2 Clients Daniel R. Pintal, RSA Partner Engineering Last Modified: September 14, 2017
IAM Security & Privacy Policies Scott Bradner
 IAM Security & Privacy Policies Scott Bradner November 24, 2015 December 2, 2015 Tuesday Wednesday 9:30-10:30 a.m. 10:00-11:00 a.m. 6 Story St. CR Today s Agenda How IAM Security and Privacy Policies Complement
IAM Security & Privacy Policies Scott Bradner November 24, 2015 December 2, 2015 Tuesday Wednesday 9:30-10:30 a.m. 10:00-11:00 a.m. 6 Story St. CR Today s Agenda How IAM Security and Privacy Policies Complement
BULLDOG CONNECTION YOUR PERSONAL ACCOUNT & CONNECTION TO SC STATE UNIVERSITY
 BULLDOG CONNECTION YOUR PERSONAL ACCOUNT & CONNECTION TO SC STATE UNIVERSITY www.scsu.edu Current Students SCSU APPS SCSU APPS PORTAL After inputting your: - First Name - Last Name - PIN - Birthdate
BULLDOG CONNECTION YOUR PERSONAL ACCOUNT & CONNECTION TO SC STATE UNIVERSITY www.scsu.edu Current Students SCSU APPS SCSU APPS PORTAL After inputting your: - First Name - Last Name - PIN - Birthdate
Office 365 Buyers Guide: Best Practices for Securing Office 365
 Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
Office 365 Buyers Guide: Best Practices for Securing Office 365 Microsoft Office 365 has become the standard productivity platform for the majority of organizations, large and small, around the world.
AXIAD IDS CLOUD SOLUTION. Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure
 AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
Updating Astea Mobile URLs
 Updating Astea Mobile URLs Table of Contents UPDATING THE ASTEA APPLICATION SERVER URL... 4 RESETTING YOUR PASSWORD UPON INITIAL LOGIN... 7 CHANGING YOUR PASSWORD... 10 ACCESSING THE UPDATED TRAINING MATERIALS...
Updating Astea Mobile URLs Table of Contents UPDATING THE ASTEA APPLICATION SERVER URL... 4 RESETTING YOUR PASSWORD UPON INITIAL LOGIN... 7 CHANGING YOUR PASSWORD... 10 ACCESSING THE UPDATED TRAINING MATERIALS...
User Guide: Adding a Device in Duo and Managing Settings
 User Guide: Adding a Device in Duo and Managing Settings The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for applications or web sites such
User Guide: Adding a Device in Duo and Managing Settings The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for applications or web sites such
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How Cyber-Criminals Steal and Profit from your Data
 How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
Business Treasury Management Services. Important Information About Your New Treasury Management Services
 Business Treasury Management Services Important Information About Your New Treasury Management Services Member FDIC Equal Housing Lender Welcome To Citizens Business Bank At Citizens Business Bank, we
Business Treasury Management Services Important Information About Your New Treasury Management Services Member FDIC Equal Housing Lender Welcome To Citizens Business Bank At Citizens Business Bank, we
MSU Authorized User Campus Access Procedure, Campus VPN
 MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
ELLUCIAN GO HOW-TO GUIDE
 ELLUCIAN GO HOW-TO GUIDE 03.31.17 CONTENTS GET THE ELLUCIAN GO APP... CHOOSE ACM AS YOUR SCHOOL... SIGN IN... ELLUCIAN GO MENU... REGISTER FOR COURSES... MY SCHEDULE... MY GRADES... MY FINANCIALS... ACADEMICS
ELLUCIAN GO HOW-TO GUIDE 03.31.17 CONTENTS GET THE ELLUCIAN GO APP... CHOOSE ACM AS YOUR SCHOOL... SIGN IN... ELLUCIAN GO MENU... REGISTER FOR COURSES... MY SCHEDULE... MY GRADES... MY FINANCIALS... ACADEMICS
Business Online Banking. Conversion Guide IMPORTANT INFORMATION ABOUT YOUR NEW BUSINESS ONLINE BANKING SERVICES. Version103117
 Business Online Banking Conversion Guide IMPORTANT INFORMATION ABOUT YOUR NEW BUSINESS ONLINE BANKING SERVICES Version103117 Business Online Banking Conversion Information This guide provides an overview
Business Online Banking Conversion Guide IMPORTANT INFORMATION ABOUT YOUR NEW BUSINESS ONLINE BANKING SERVICES Version103117 Business Online Banking Conversion Information This guide provides an overview
Identity & Access Management: Changes for FAS and Beyond. May 6, p.m. FAS Standing Committee on IT Barker Center Plimpton Room
 Identity & Access Management: Changes for FAS and Beyond May 6, 2015 12 p.m. FAS Standing Committee on IT Barker Center Plimpton Room Agenda The Vision for Harvard Identity & Access Management Business
Identity & Access Management: Changes for FAS and Beyond May 6, 2015 12 p.m. FAS Standing Committee on IT Barker Center Plimpton Room Agenda The Vision for Harvard Identity & Access Management Business
Related Labs: Introduction to Universal Access and F5 SAML IDP (Self-paced)
 PRESENTED BY: Related Labs: Introduction to Universal Access and F5 SAML IDP (Self-paced) One of the main problems that customers face with the adoption of SaaS and cloud-based apps is how to deliver the
PRESENTED BY: Related Labs: Introduction to Universal Access and F5 SAML IDP (Self-paced) One of the main problems that customers face with the adoption of SaaS and cloud-based apps is how to deliver the
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
Enrolling Devices in Duo
 Enrolling Devices in Duo To use ArchPass, UGA s two-step login powered by Duo you will need to enroll a device with the Duo application. You can enroll any smartphone, mobile phone, landline phone or tablet.
Enrolling Devices in Duo To use ArchPass, UGA s two-step login powered by Duo you will need to enroll a device with the Duo application. You can enroll any smartphone, mobile phone, landline phone or tablet.
Information Technology Services. Informational Report for the Board of Trustees October 11, 2017 Prepared effective August 31, 2017
 Information Technology Services Informational Report for the Board of Trustees October 11, 2017 Prepared effective August 31, 2017 Information Technology Services TABLE OF CONTENTS UPDATE ON PROJECTS &
Information Technology Services Informational Report for the Board of Trustees October 11, 2017 Prepared effective August 31, 2017 Information Technology Services TABLE OF CONTENTS UPDATE ON PROJECTS &
5 Reasons to Choose Parallels RAS Over Citrix Solutions
 White Paper Parallels Remote Application Server 5 Reasons to Choose Parallels RAS Over Citrix Solutions 5 Reasons to Choose RAS Over Citrix Solutions 01 Table of Contents Introduction...3 Parallels Helps
White Paper Parallels Remote Application Server 5 Reasons to Choose Parallels RAS Over Citrix Solutions 5 Reasons to Choose RAS Over Citrix Solutions 01 Table of Contents Introduction...3 Parallels Helps
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
But it Was Such a Little Phish February 2016 Webinar
 But it Was Such a Little Phish February 2016 Webinar Firestorm Insights February 2016 1000 Holcomb Woods Parkway Suite 130 Roswell, GA 30076 770-643-1114 Fax: 1-800-418-9088 www.firestorm.com Page Intentionally
But it Was Such a Little Phish February 2016 Webinar Firestorm Insights February 2016 1000 Holcomb Woods Parkway Suite 130 Roswell, GA 30076 770-643-1114 Fax: 1-800-418-9088 www.firestorm.com Page Intentionally
Mobile Banking Frequently Asked Questions
 Mobile Banking Frequently Asked Questions What types of Mobile Banking does Midwest BankCentre offer? We offer three types of Mobile Banking: Mobile Apps allows you to easily connect to Midwest BankCentre
Mobile Banking Frequently Asked Questions What types of Mobile Banking does Midwest BankCentre offer? We offer three types of Mobile Banking: Mobile Apps allows you to easily connect to Midwest BankCentre
The following is a presentation for the Virginia Tech Carilion School of Medicine highlighting the services available through the online Hokie Spa
 The following is a presentation for the Virginia Tech Carilion School of Medicine highlighting the services available through the online Hokie Spa system. 1 To begin, log into the system at www.hokiespa.vt.edu.
The following is a presentation for the Virginia Tech Carilion School of Medicine highlighting the services available through the online Hokie Spa system. 1 To begin, log into the system at www.hokiespa.vt.edu.
FUJITSU Cloud Service S5. Introduction Guide. Ver. 1.3 FUJITSU AMERICA, INC.
 FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 FUJITSU AMERICA, INC. 1 FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 Date of publish: September, 2011 All Rights Reserved, Copyright FUJITSU
FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 FUJITSU AMERICA, INC. 1 FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 Date of publish: September, 2011 All Rights Reserved, Copyright FUJITSU
SYSTEM LOGIN/PASSWORD SUPPORT
 SYSTEM LOGIN/PASSWORD SUPPORT Why am I unable to log into the system? What if I forgot my password? Why do I need to create Security Questions/Answers? Why does it ask me if I want to remember this computer?
SYSTEM LOGIN/PASSWORD SUPPORT Why am I unable to log into the system? What if I forgot my password? Why do I need to create Security Questions/Answers? Why does it ask me if I want to remember this computer?
Overview. Premium Data Sheet. DigitalPersona. DigitalPersona s Composite Authentication transforms the way IT
 DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
Student Portal Quick Start Guide
 Student Portal Quick Start Guide My Home Page Quick Links These are quick links available on the top of the portal screen. These are also available through the menu groups on the side. Personalize View
Student Portal Quick Start Guide My Home Page Quick Links These are quick links available on the top of the portal screen. These are also available through the menu groups on the side. Personalize View
Self-Service Portal Registering, downloading & activating a soft token
 Self-Service Portal Registering, downloading & activating a soft token Document issue: 3.2 Date of issue: September 2014 Contents Introduction... 3 About two-factor authentication... 3 About egrid authentication...
Self-Service Portal Registering, downloading & activating a soft token Document issue: 3.2 Date of issue: September 2014 Contents Introduction... 3 About two-factor authentication... 3 About egrid authentication...
Your partner for Success. CCIE Security Lab Access Guide
 Your partner for Success CCIE Security Lab Access Guide Contents Getting Access to the POD... 3 DEVICE ACCESS... 5 How to access the devices... 5 Starting the lab environment: https://www.youtube.com/watch?v=rymvbjci70e...
Your partner for Success CCIE Security Lab Access Guide Contents Getting Access to the POD... 3 DEVICE ACCESS... 5 How to access the devices... 5 Starting the lab environment: https://www.youtube.com/watch?v=rymvbjci70e...
1.1. HOW TO START? 1.2. ACCESS THE APP
 Table of Contents 1. Get Started 1.1. How to start? 1.2. Access the app 1.3. Username and password 2. Mobile Banking features 3. Security 4. Accounts and inquiries 5. Transfers and beneficiaries 6. Charges
Table of Contents 1. Get Started 1.1. How to start? 1.2. Access the app 1.3. Username and password 2. Mobile Banking features 3. Security 4. Accounts and inquiries 5. Transfers and beneficiaries 6. Charges
FORUM Business Online Banking
 FORUM Business Online Banking FORUM Business Online Banking has a new look but still offers the same level of service and security. Complete privacy, controlled through encryption and passwords, ensures
FORUM Business Online Banking FORUM Business Online Banking has a new look but still offers the same level of service and security. Complete privacy, controlled through encryption and passwords, ensures
Duo Enrollment for DA Employees
 Duo Enrollment for DA Employees Duo s Multi-Factor Authentication will be used to authenticate DA employees when using DA Portal, DA s Outlook Web Access (OWA), and DA s O365. It is RECOMMENDED to have
Duo Enrollment for DA Employees Duo s Multi-Factor Authentication will be used to authenticate DA employees when using DA Portal, DA s Outlook Web Access (OWA), and DA s O365. It is RECOMMENDED to have
How to access Launchpad and Textbooks online
 Quest Tech Tips Launchpad & Textbooks Online Directions (front and back) How to setup your mobile device to receive school/district notifications (front and back) Edline parent instructions Free Microsoft
Quest Tech Tips Launchpad & Textbooks Online Directions (front and back) How to setup your mobile device to receive school/district notifications (front and back) Edline parent instructions Free Microsoft
Automated Context and Incident Response
 Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Phishing Attacks. Mendel Rosenblum. CS142 Lecture Notes - Phishing Attack
 Phishing Attacks Mendel Rosenblum Phishing Basic idea: Get unsuspecting users to visit an evil Web site Convince them that the evil Web site is actually a legitimate site (such as a bank or PayPal) Trick
Phishing Attacks Mendel Rosenblum Phishing Basic idea: Get unsuspecting users to visit an evil Web site Convince them that the evil Web site is actually a legitimate site (such as a bank or PayPal) Trick
Five Reasons It s Time For Secure Single Sign-On
 Five Reasons It s Time For Secure Single Sign-On From improved security to increased customer engagement, secure single sign-on is a smart choice. Executive Overview While cloud-based applications provide
Five Reasons It s Time For Secure Single Sign-On From improved security to increased customer engagement, secure single sign-on is a smart choice. Executive Overview While cloud-based applications provide
Timesheet Submission in Academica TRIO Upward Bound Summer Program June 25, 2018 Room 1700
 Timesheet Submission in Academica TRIO Upward Bound Summer Program June 25, 2018 Room 1700 Presentation created by Brittany Thomas *BEFORE WE BEGIN. If you have not already, you will need to call Computing
Timesheet Submission in Academica TRIO Upward Bound Summer Program June 25, 2018 Room 1700 Presentation created by Brittany Thomas *BEFORE WE BEGIN. If you have not already, you will need to call Computing
Canadian Access Federation: Trust Assertion Document (TAD)
 Participant Name: University of Guelph Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Participant Name: University of Guelph Canadian Access Federation: Trust Assertion Document (TAD) 1. Purpose A fundamental requirement of Participants in the Canadian Access Federation is that they assert
Identity Management as a Service
 Identity Management as a Service The Challenge Today s technological landscape is one of permanent change. While connections to digital services and mobile devices grow, securing the data generated by
Identity Management as a Service The Challenge Today s technological landscape is one of permanent change. While connections to digital services and mobile devices grow, securing the data generated by
Multi-Platform Enterprise Mobility Management. Perfectly balancing end-user and corporate needs
 B U I L T T 0 K E E P Y O U R B U S I N E S S M O V I N G Multi-Platform Enterprise Mobility Management Perfectly balancing end-user and corporate needs Enterprise mobility is enabling organizations to
B U I L T T 0 K E E P Y O U R B U S I N E S S M O V I N G Multi-Platform Enterprise Mobility Management Perfectly balancing end-user and corporate needs Enterprise mobility is enabling organizations to
Registering an Android Tablet for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an Android Tablet for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members.
University Information Technology Services Technology Outreach Registering an Android Tablet for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members.
In addition to these resources, our staff will be on hand to help walk you through any questions or concerns you have post-conversion.
 Dear Valued Member, In an effort to better support your financial needs, United 1st Federal Credit Union will convert the former Community United core data processing system platform to the current United
Dear Valued Member, In an effort to better support your financial needs, United 1st Federal Credit Union will convert the former Community United core data processing system platform to the current United
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
Kerberos for the Web Current State and Leverage Points
 Kerberos for the Web Current State and Leverage Points Executive Advisory Board Meeting and Financial Services Security Summit New York, 3-4 November 2008. Towards Kerberizing Web Identity and Services
Kerberos for the Web Current State and Leverage Points Executive Advisory Board Meeting and Financial Services Security Summit New York, 3-4 November 2008. Towards Kerberizing Web Identity and Services
IT Service Level Agreement
 The Glasgow School of Art IT Service Level Agreement September 2016 Policy Control Title IT Service Level Agreement Date Approved Sep 2016 Approving Bodies Executive Group Implementation Date September
The Glasgow School of Art IT Service Level Agreement September 2016 Policy Control Title IT Service Level Agreement Date Approved Sep 2016 Approving Bodies Executive Group Implementation Date September
1 IAM Program Launch. 2 Agenda. 3 Introductions. Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications
 1 IAM Program Launch Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications Kickstart an IAM program with discovery of business and IT requirements 2 Agenda Who? Introductions. Why?
1 IAM Program Launch Managing the User Lifecycle Across On-Premises and Cloud-Hosted Applications Kickstart an IAM program with discovery of business and IT requirements 2 Agenda Who? Introductions. Why?
Top 5 Reasons. The Business Case for Bomgar Remote Support
 Top 5 Reasons The Business Case for Bomgar Remote Support You already know Bomgar will help you connect to remote people, devices, and networks securely and efficiently. Now you need to get your team on
Top 5 Reasons The Business Case for Bomgar Remote Support You already know Bomgar will help you connect to remote people, devices, and networks securely and efficiently. Now you need to get your team on
Case Study Identity Management at Texas A&M University
 Case Study Identity Management at Texas A&M University Susan Neitsch Lead Software Applications Developer, Texas A&M University The Problem: delivering a centralized email service Climate Late 1990s Students
Case Study Identity Management at Texas A&M University Susan Neitsch Lead Software Applications Developer, Texas A&M University The Problem: delivering a centralized email service Climate Late 1990s Students
Local. Responsive. Reliable.
 Local. Responsive. Reliable. FAQs WHAT IS myvrb? myvrb is the new name of your online and mobile banking experience at Valley Republic Bank. While you will continue to access online and mobile banking
Local. Responsive. Reliable. FAQs WHAT IS myvrb? myvrb is the new name of your online and mobile banking experience at Valley Republic Bank. While you will continue to access online and mobile banking
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
Mobile Banking FAQ. 1 P a g e 1 0 / 1 9 /
 Mobile Banking FAQ Q) Can anyone sign up for Mobile Banking? A) Mobile Banking enables any consumer with online banking to access their account information from a mobile device. Mobile Banking offers three
Mobile Banking FAQ Q) Can anyone sign up for Mobile Banking? A) Mobile Banking enables any consumer with online banking to access their account information from a mobile device. Mobile Banking offers three
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
Online Services User Guide
 Online Services User Guide Welcome to Online & Mobile Banking! Whether you re online or using a mobile device, manage your money whenever and wherever it s convenient for you. Access Visit BankMidwest.com
Online Services User Guide Welcome to Online & Mobile Banking! Whether you re online or using a mobile device, manage your money whenever and wherever it s convenient for you. Access Visit BankMidwest.com
Mobile Banking with Mobile Deposit FAQs
 Mobile Banking with Mobile Deposit FAQs Getting Started Q. What is Mobile Banking? Mobile Banking is our mobile service that brings banking to your mobile phone & tablets. Mobile Banking allows you to
Mobile Banking with Mobile Deposit FAQs Getting Started Q. What is Mobile Banking? Mobile Banking is our mobile service that brings banking to your mobile phone & tablets. Mobile Banking allows you to
Censornet. CensorNet Unified Security Service (USS) FREEDOM. VISIBILITY. PROTECTION. Lars Gotlieb Regional Manager DACH
 Censornet CensorNet Unified Security Service (USS) FREEDOM. VISIBILITY. PROTECTION. Lars Gotlieb Regional Manager DACH Censornet???? Former SMS passcode. One of the leading vendors in Multi factor authentifaction!
Censornet CensorNet Unified Security Service (USS) FREEDOM. VISIBILITY. PROTECTION. Lars Gotlieb Regional Manager DACH Censornet???? Former SMS passcode. One of the leading vendors in Multi factor authentifaction!
Are You Flirting with Risk?
 Are You Flirting with Risk? RSA Live Webcast October 15, 2013 Jessica Stanford Sr. Product Marketing Manager, RSA Authentication 1 2 3 4 5 RSA AUTHENTICATION MANAGER 8.0 Agenda Password Problem Market
Are You Flirting with Risk? RSA Live Webcast October 15, 2013 Jessica Stanford Sr. Product Marketing Manager, RSA Authentication 1 2 3 4 5 RSA AUTHENTICATION MANAGER 8.0 Agenda Password Problem Market
Business Mobile Banking.
 Business Mobile Resource Guide Business Mobile Banking Business Mobile Banking gives business customers the ability to access their business accounts and perform a variety of banking functions from the
Business Mobile Resource Guide Business Mobile Banking Business Mobile Banking gives business customers the ability to access their business accounts and perform a variety of banking functions from the
PROGRESS REPORT of TECHNOLOGY PLAN 2016 INITIATIVES AS OF FEBRUARY 28, 2013
 PROGRESS REPORT of TECHNOLOGY PLAN 2016 INITIATIVES AS OF FEBRUARY 28, 2013 The Tier 1 Initiatives were tied to Strategic Plan 2013 and the Program Review & Planning process. They offered desirable benefits
PROGRESS REPORT of TECHNOLOGY PLAN 2016 INITIATIVES AS OF FEBRUARY 28, 2013 The Tier 1 Initiatives were tied to Strategic Plan 2013 and the Program Review & Planning process. They offered desirable benefits
CHI Easy Access: Register From on the CHI Network
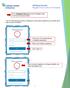 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
 Part of the AdEPT Group Why Managed WiFi? The need to be connected is ever increasing and the internet can be a powerful tool for education. As devices get smaller and more portable it s vital that schools
Part of the AdEPT Group Why Managed WiFi? The need to be connected is ever increasing and the internet can be a powerful tool for education. As devices get smaller and more portable it s vital that schools
Minfy MS Workloads Use Case
 Contents Scope... 3 About CUSTOMER... Error! Bookmark not defined. Use Case Description... 3 Technical Stack... 3 AWS Architecture... Error! Bookmark not defined. AWS Solution Overview... 4 Risk Identified
Contents Scope... 3 About CUSTOMER... Error! Bookmark not defined. Use Case Description... 3 Technical Stack... 3 AWS Architecture... Error! Bookmark not defined. AWS Solution Overview... 4 Risk Identified
ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit We Make Banking About You
 ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit Member FDIC We Make Banking About You 1-800-288-2229 www.abbybank.com 1 Account Access To log into your ebanking account, go to www.abbybank.com.
ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit Member FDIC We Make Banking About You 1-800-288-2229 www.abbybank.com 1 Account Access To log into your ebanking account, go to www.abbybank.com.
SOFTWARE DEMONSTRATION
 SOFTWARE DEMONSTRATION IDENTITY AND ACCESS MANAGEMENT SOFTWARE AND SERVICES RFP 644456 DEMONSTRATION AGENDA Executive Summary Technical Overview Break User Interfaces and Experience Multi-Campus and Inter-Campus
SOFTWARE DEMONSTRATION IDENTITY AND ACCESS MANAGEMENT SOFTWARE AND SERVICES RFP 644456 DEMONSTRATION AGENDA Executive Summary Technical Overview Break User Interfaces and Experience Multi-Campus and Inter-Campus
Internal Audit Report DATA CENTER LOGICAL SECURITY
 Internal Audit Report DATA CENTER LOGICAL SECURITY Report No. SC 12 06 June 2012 David Lane Principal IT Auditor Jim Dougherty Principal Auditor Approved Barry Long, Director Internal Audit & Advisory
Internal Audit Report DATA CENTER LOGICAL SECURITY Report No. SC 12 06 June 2012 David Lane Principal IT Auditor Jim Dougherty Principal Auditor Approved Barry Long, Director Internal Audit & Advisory
LinQ2FA. Helping You. Network. Direct Communication. Stay Fraud Free!
 LinQ2FA Stay Fraud Free! Helping You Direct Communication Secure to your Your customers Network LINQ2FA Stay Fraud Free! Enhance your security against cyber fraud with Two Factor Authentication Suitable
LinQ2FA Stay Fraud Free! Helping You Direct Communication Secure to your Your customers Network LINQ2FA Stay Fraud Free! Enhance your security against cyber fraud with Two Factor Authentication Suitable
