Detecting and Dealing with Compromised Accounts in Cloud Platforms
|
|
|
- Rose Reeves
- 6 years ago
- Views:
Transcription
1 Detecting and Dealing with Compromised Accounts in Cloud Platforms Nick Young - IT Manager, Application Administration Kevin McClain - Google Apps Administrator UNC CAUSE :45-2:30pm, Thursday October 6th
2 UNCG: Population Context ~30,000 enabled accounts ~23,000 actively used accounts 19,000 Student Accounts 4000 Employee Accounts
3 UNCG - How we got here - Incremental Improvements Pre No automated detection of compromised accounts Standardized pieces of the process Google Admin + IT Security + Service Desk What actions are taken for a compromised account AUTOMATION = Better, faster, stronger Trashing known phishing from UNCG Recipient Mailboxes (preventing more compromises) More source data
4 Start with the basics: Source Data Pre No automated detection of compromised accounts Only Google alerts for suspicious or suspendable activity Built Google Support Tool, aka GST (in-house PHP) Google Login Logs & Suspicious Activity Alerts via API Enterprise Authentication (Shibboleth) Logs via Splunk API Spring Duo Security (2FA) via Splunk API Late MyCloud (Citrix) logs via Splunk API
5 RULES & EXCEPTIONS
6 Compromise Rules - Types Successful Login IP Address Geolocation (Splunk / MaxMind) Event Type
7 Compromise Rules - IP Example : Known origin of phishing/compromises
8 Compromise Rules - Geolocation Examples Continent: Africa Country: Nigeria Geo-location: Manassas, Virginia, United States of America, North America
9 Compromise Rules - Multiple Country Logins Configurable time window 2 Countries within 2 hours Greensboro, NC at 9:00am; Lagos, Nigeria at 9:05am == Automatic Process as Compromise Greensboro, NC at 9:00am; Lagos, Nigeria at 11:01am == No Automatic Process
10 Compromise Exceptions Individual Username-based Exempts from automated processing Does not exempt from manual processing Time limited (start & end date) Automated notifications to user before end date Requires discussion with SD or Google Admin Traveling, Regular VPN use, Study Abroad etc NOT to allow foreign parents to access account
11 PHISHING (just briefly)
12 Phishing Detection & Cleanup 1. Mostly manual detection / reporting to Google Admins 2. Content Compliance Rules implemented in Google to prevent future/similar attacks 3. Log -> GST -> API = Move Phish to User s Trash 4. Notify Recipients that they were targeted, recommend 2FA 5. Process users as compromised if they report clicking/using on Phishing Link
13 ACTIONS
14
15
16 Compromised Account Actions - Google 1. Local Google Password Reset (IMAP, POP, Old Apps etc) 2. 3rd Party OAUTH Tokens removed 3. Forwarding Rules checked/removed 4. Account Suspended (prevents any activity) 5. Duo 2FA Enrollment Status checked via API 6. Remedy Ticket Created via API
17 Compromised Account Actions - Manual/Service Desk 1. Require reset of UNCG enterprise password Prevents login via Shibboleth / LDAP etc 2. Unsuspend Google Account after UNCG password reset 3. Contact User by Phone Explain incident Explain remediation steps (re-setup OAuth apps etc) Recommend 2FA Enrollment
18 METRICS Are we getting better at: Prevention? Detection? Making our users less-good targets?
19 Metrics: Total Phishing Attacks Processed 173 Since March 23rd 2015
20 Metrics: Average Phishing Attacks One Attack Every... 5 days 2 days 25 days March 1st 2015 To Dec 31st 2015 Jan 1st 2016 To July 31st 2016 Aug 1st 2016 To Oct 5th 2016
21 Metrics: Total Compromises Processed 3204 Since August 2014
22 Metrics: Average Total Compromises Per Day March 1st 2015 To Feb 29th 2016 March 1st 2016 To July 31st 2016 August 1st 2016 To Oct 5th 2016
23 Metrics: Average Employee Compromises Per Day March 1st 2015 To Feb 29th 2016 March 1st 2016 To July 31st 2016 August 1st 2016 To Oct 5th 2016
24 Metrics: Average Student Compromises Per Day March 1st 2015 To Feb 29th 2016 March 1st 2016 To July 31st 2016 August 1st 2016 To Oct 5th 2016
25 Other Stuff / What s Next Mandatory IT Security Training in Canvas, reports back to Banner for dept oversight (March 2016) Citrix, LDAP, more? added to source data set CloudLock API - add/replace parts of logic
26 Other Stuff / What s Next DMARC prevention of -spoofing - go.uncg.edu/dmarc Multiple Compromises == 2FA requirement Include data Classification + Access to sensitive data
27 Q & A
28 UNC Mel Radcliff UNCG Kevin McClain Nick Young Sched.org
Duo at BU. Our two-factor authentication plan
 Duo at BU Our two-factor authentication plan Tom Grundig - Information Security, Boston University Information Security Operations Manager SAP Security & GRC Lead Former Asst. Dir of Internal Audit Duo
Duo at BU Our two-factor authentication plan Tom Grundig - Information Security, Boston University Information Security Operations Manager SAP Security & GRC Lead Former Asst. Dir of Internal Audit Duo
Creating a Parent Account and setting up Notification preferences.
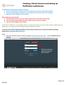 Creating a Parent Account and setting up Notification preferences. This document will walk you through the steps to: 1. Create a Parent Account so that you can have access to the courses your child is
Creating a Parent Account and setting up Notification preferences. This document will walk you through the steps to: 1. Create a Parent Account so that you can have access to the courses your child is
CHI Easy Access: Register From on the CHI Network
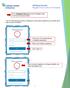 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
Two Factor Authentication
 Two Factor Authentication On December 15 th 2017 the Costpoint Cloud will require Two Factor Authentication when accessing User Manager and Citrix. Also, users will be required to access Costpoint Enterprise
Two Factor Authentication On December 15 th 2017 the Costpoint Cloud will require Two Factor Authentication when accessing User Manager and Citrix. Also, users will be required to access Costpoint Enterprise
ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0
 ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0 August 2017 Date Version Description August 2017 1.0 Initial Draft 1. Single Sign On... 2 2. To register for SSO on the Global ID webpage...
ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0 August 2017 Date Version Description August 2017 1.0 Initial Draft 1. Single Sign On... 2 2. To register for SSO on the Global ID webpage...
Solving for Compromised Credentials Across the Enterprise
 Solving for Compromised Credentials Across the Enterprise Boston University s Multi-Factor Authentication Implementation Tom Grundig, Assistant Director, Information Security, Boston University The Boston
Solving for Compromised Credentials Across the Enterprise Boston University s Multi-Factor Authentication Implementation Tom Grundig, Assistant Director, Information Security, Boston University The Boston
Texas Division How to Login and Register for My IT Support and ServiceNow
 Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
Hybrid Identity de paraplu in de cloud
 EXPERTS LIVE SUMMER NIGHT Hybrid Identity de paraplu in de cloud Robbert van der Zwan TSP EM+S Netherlands EXPERTS LIVE SUMMER NIGHT Robbert van der Zwan Robbert works as an Enterprise Mobility and Security
EXPERTS LIVE SUMMER NIGHT Hybrid Identity de paraplu in de cloud Robbert van der Zwan TSP EM+S Netherlands EXPERTS LIVE SUMMER NIGHT Robbert van der Zwan Robbert works as an Enterprise Mobility and Security
Enroll in Two factor Authentication - iphone
 OVERVIEW Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked you might not even know someone is accessing your account. Two factor authentication adds a second layer
OVERVIEW Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked you might not even know someone is accessing your account. Two factor authentication adds a second layer
How do I sign up for a Canvas account as a parent?
 How do I sign up for a Canvas account as a parent? Parents (Observers) can link their Canvas account to their student's account so they can see assignment dues dates, announcements, and other course content.
How do I sign up for a Canvas account as a parent? Parents (Observers) can link their Canvas account to their student's account so they can see assignment dues dates, announcements, and other course content.
MSU Authorized User Campus Access Procedure, Campus VPN
 MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
CUSTOMER PORTAL. Introduction and Guide
 CUSTOMER PORTAL Introduction and Guide CUSTOMER PORTAL The portal was built with you in mind - through it, you have 24/7 access to manage your account. This guide will help you get started. Using the portal,
CUSTOMER PORTAL Introduction and Guide CUSTOMER PORTAL The portal was built with you in mind - through it, you have 24/7 access to manage your account. This guide will help you get started. Using the portal,
The University of Toledo Intune End-User Enrollment Guide:
 The University of Toledo Intune End-User Enrollment Guide: Contents Enroll your Android device in Intune... 2 Enroll your ios device in Intune... 15 Enroll your Mac OS X device in Intune... 25 Enroll your
The University of Toledo Intune End-User Enrollment Guide: Contents Enroll your Android device in Intune... 2 Enroll your ios device in Intune... 15 Enroll your Mac OS X device in Intune... 25 Enroll your
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
Duo End User Education Templates
 Duo End User Education Email Templates Table of Contents Email Communication Best Practices Email Templates Email #1 - Duo is coming soon, no immediate action required. Email #2 - Duo is coming on ,
Duo End User Education Email Templates Table of Contents Email Communication Best Practices Email Templates Email #1 - Duo is coming soon, no immediate action required. Email #2 - Duo is coming on ,
SpiraTeam Help Desk Integration Guide Inflectra Corporation
 / SpiraTeam Help Desk Integration Guide Inflectra Corporation Date: July 23rd, 2018 Contents Introduction... 1 1. KronoDesk... 2 2. Zendesk... 7 Introduction SpiraTeam is an integrated Application Lifecycle
/ SpiraTeam Help Desk Integration Guide Inflectra Corporation Date: July 23rd, 2018 Contents Introduction... 1 1. KronoDesk... 2 2. Zendesk... 7 Introduction SpiraTeam is an integrated Application Lifecycle
Welcome! Ready To Secure Access to Your Microsoft Applications?
 Welcome! Ready To Secure Access to Your Microsoft Applications? During the Webinar Audio In presentation mode until end Control Panel View webinar in full screen mode Feel Free to submit written questions
Welcome! Ready To Secure Access to Your Microsoft Applications? During the Webinar Audio In presentation mode until end Control Panel View webinar in full screen mode Feel Free to submit written questions
Competitive Matrix - IRONSCALES vs Alternatives
 Competitive Matrix - IRONSCALES vs Alternatives Traditional Awareness and Training Features IRONSCALES SEG PhishMe Wombat Knowbe4 Sans Institute Simulation & Training Compliance PCI/DSS, HIPAA, GLBA to
Competitive Matrix - IRONSCALES vs Alternatives Traditional Awareness and Training Features IRONSCALES SEG PhishMe Wombat Knowbe4 Sans Institute Simulation & Training Compliance PCI/DSS, HIPAA, GLBA to
Who am I? Identity Product Group, CXP Team. Premier Field Engineer. SANS STI Student GWAPT, GCIA, GCIH, GCWN, GMOB
 @markmorow Who am I? Identity Product Group, CXP Team Premier Field Engineer SANS STI Student GWAPT, GCIA, GCIH, GCWN, GMOB Under the hood: Multiple backend services and hybrid components Hybrid Components
@markmorow Who am I? Identity Product Group, CXP Team Premier Field Engineer SANS STI Student GWAPT, GCIA, GCIH, GCWN, GMOB Under the hood: Multiple backend services and hybrid components Hybrid Components
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
Who am I? Identity Product Group, CXP Team. Premier Field Engineer. SANS STI Student GWAPT, GCIA, GCIH, GCWN, GMOB
 @markmorow Who am I? Identity Product Group, CXP Team Premier Field Engineer SANS STI Student GWAPT, GCIA, GCIH, GCWN, GMOB Active Directory Domain Services On-premises App Server Validate credentials
@markmorow Who am I? Identity Product Group, CXP Team Premier Field Engineer SANS STI Student GWAPT, GCIA, GCIH, GCWN, GMOB Active Directory Domain Services On-premises App Server Validate credentials
Wholesale Lockbox Quick Reference Guide: Administration
 Wholesale Lockbox Quick Reference Guide: Administration Table of Contents Adding Users... 2 Modifying Users... 3 Resetting Passwords... 5 Changing Your Password... 6 Deleting a User... 6 Contact Us...
Wholesale Lockbox Quick Reference Guide: Administration Table of Contents Adding Users... 2 Modifying Users... 3 Resetting Passwords... 5 Changing Your Password... 6 Deleting a User... 6 Contact Us...
June 2012 First Data PCI RAPID COMPLY SM Solution
 June 2012 First Data PCI RAPID COMPLY SM Solution You don t have to be a security expert to be compliant. Developer: 06 Rev: 05/03/2012 V: 1.0 Agenda Research Background Product Overview Steps to becoming
June 2012 First Data PCI RAPID COMPLY SM Solution You don t have to be a security expert to be compliant. Developer: 06 Rev: 05/03/2012 V: 1.0 Agenda Research Background Product Overview Steps to becoming
Getting Started with Duo Security Two-Factor Authentication (2FA)
 Getting Started with Duo Security Two-Factor Authentication (2FA) Table of Contents What is Two-Factor Authentication (2FA)?... 1 Why 2FA at Bates College?... 2 2FA Technologies... 3 Duo Protected Resources
Getting Started with Duo Security Two-Factor Authentication (2FA) Table of Contents What is Two-Factor Authentication (2FA)?... 1 Why 2FA at Bates College?... 2 2FA Technologies... 3 Duo Protected Resources
Compu&ng Services Strengthening Authen&ca&on. October 2016
 Compu&ng Services Strengthening Authen&ca&on October 2016 ID and password pair is the sole means of authen4ca4ng access AUTHENTICATION Current State o Email o File storage o Enterprise applica1ons (including
Compu&ng Services Strengthening Authen&ca&on October 2016 ID and password pair is the sole means of authen4ca4ng access AUTHENTICATION Current State o Email o File storage o Enterprise applica1ons (including
Road Condition Reporting System
 Road Condition Reporting System Highway User Administration Highway User Administration Login to Highway User Administration The RCRS is a Web-based system. To login to the RCRS Highway User Administration
Road Condition Reporting System Highway User Administration Highway User Administration Login to Highway User Administration The RCRS is a Web-based system. To login to the RCRS Highway User Administration
Using CSE Cisco Anyconnect with 2FA
 Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
News and Updates June 1, 2017
 Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
LinQ2FA. Helping You. Network. Direct Communication. Stay Fraud Free!
 LinQ2FA Stay Fraud Free! Helping You Direct Communication Secure to your Your customers Network LINQ2FA Stay Fraud Free! Enhance your security against cyber fraud with Two Factor Authentication Suitable
LinQ2FA Stay Fraud Free! Helping You Direct Communication Secure to your Your customers Network LINQ2FA Stay Fraud Free! Enhance your security against cyber fraud with Two Factor Authentication Suitable
Data Insight Feature Briefing Box Cloud Storage Support
 Data Insight Feature Briefing Box Cloud Storage Support This document is about the new Box Cloud Storage Support feature in Symantec Data Insight 5.0. If you have any feedback or questions about this document
Data Insight Feature Briefing Box Cloud Storage Support This document is about the new Box Cloud Storage Support feature in Symantec Data Insight 5.0. If you have any feedback or questions about this document
10 FOCUS AREAS FOR BREACH PREVENTION
 10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
10 FOCUS AREAS FOR BREACH PREVENTION Keith Turpin Chief Information Security Officer Universal Weather and Aviation Why It Matters Loss of Personally Identifiable Information (PII) Loss of Intellectual
AUTHENTICATION. Do You Know Who You're Dealing With? How Authentication Affects Prevention, Detection, and Response
 AUTHENTICATION Do You Know Who You're Dealing With? How Authentication Affects Prevention, Detection, and Response Who we are Eric Scales Mandiant Director IR, Red Team, Strategic Services Scott Koller
AUTHENTICATION Do You Know Who You're Dealing With? How Authentication Affects Prevention, Detection, and Response Who we are Eric Scales Mandiant Director IR, Red Team, Strategic Services Scott Koller
Guide to your CGIAR Network account Self Service tool
 Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
WP Voting Plugin - Ohiowebtech Video Extension - Youtube Documentation
 WP Voting Plugin - Ohiowebtech Video Extension - Youtube Documentation Overview This documentation includes details about the WP Voting Plugin - Video Extension Plugin for Youtube. This extension will
WP Voting Plugin - Ohiowebtech Video Extension - Youtube Documentation Overview This documentation includes details about the WP Voting Plugin - Video Extension Plugin for Youtube. This extension will
VMware AirWatch Google Sync Integration Guide Securing Your Infrastructure
 VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
Banner 9 Overview and Transition timeline August Edgar Coronel Paddy Wong
 Banner 9 Overview and Transition timeline August 2018 Edgar Coronel Paddy Wong v1 Banner Basics Banner 9 Overview Single Sign On Begin Transition! Using Banner 9 Demo Agenda Banner Basics Banner Forms
Banner 9 Overview and Transition timeline August 2018 Edgar Coronel Paddy Wong v1 Banner Basics Banner 9 Overview Single Sign On Begin Transition! Using Banner 9 Demo Agenda Banner Basics Banner Forms
USER MANUAL. SalesPort Salesforce Customer Portal for WordPress (Lightning Mode) TABLE OF CONTENTS. Version: 3.1.0
 USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
ManageEngine ADSelfService Plus
 Comparison Document ManageEngine ADSelfService Plus Vs Azure AD Self-Service Password Reset (SSPR) ManageEngine ADSelfService Plus vs. Azure AD Self-Service Password Reset (SSPR) Password reset tickets
Comparison Document ManageEngine ADSelfService Plus Vs Azure AD Self-Service Password Reset (SSPR) ManageEngine ADSelfService Plus vs. Azure AD Self-Service Password Reset (SSPR) Password reset tickets
Administrator IT Guide. Samsung Knox Configure Shared Device
 Administrator IT Guide Samsung Knox Configure Shared Device July 2017 Samsung Knox TM shared device A Samsung Knox shared device enables multiple users, or employees, to access the same device without
Administrator IT Guide Samsung Knox Configure Shared Device July 2017 Samsung Knox TM shared device A Samsung Knox shared device enables multiple users, or employees, to access the same device without
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitme
 SAAM2291BE Securing Access and Protecting Information in Office 365 with Workspace ONE Camilo Lotero Senior Technical Marketing Manager Adarsh Kesari Senior Systems Engineer #VMworld #SAAM2291BE Disclaimer
SAAM2291BE Securing Access and Protecting Information in Office 365 with Workspace ONE Camilo Lotero Senior Technical Marketing Manager Adarsh Kesari Senior Systems Engineer #VMworld #SAAM2291BE Disclaimer
Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts
 White Paper Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts Don t let stolen VPN credentials jeopardize your security March 2015 A TECHTARGET WHITE PAPER Most IT professionals take for
White Paper Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts Don t let stolen VPN credentials jeopardize your security March 2015 A TECHTARGET WHITE PAPER Most IT professionals take for
2-Step Verification. Summer 2018, Version 3. Table of Contents
 2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Administrator Manual. Last Updated: 15 March 2012 Manual Version:
 Administrator Manual Last Updated: 15 March 2012 Manual Version: 1.6 http://www.helpdeskpilot.com Copyright Information Under the copyright laws, this manual may not be copied, in whole or in part. Your
Administrator Manual Last Updated: 15 March 2012 Manual Version: 1.6 http://www.helpdeskpilot.com Copyright Information Under the copyright laws, this manual may not be copied, in whole or in part. Your
SurePassID ServicePass User Guide. SurePassID Authentication Server 2017
 SurePassID ServicePass User Guide SurePassID Authentication Server 2017 Introduction This technical guide shows how users can manage their SurePassID security tokens that are compatible with SurePassID
SurePassID ServicePass User Guide SurePassID Authentication Server 2017 Introduction This technical guide shows how users can manage their SurePassID security tokens that are compatible with SurePassID
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide
 STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
USE CASE IN ACTION Splunk + Komand
 USE CASE IN ACTION Splunk + Komand USE CASE IN ACTION - SPLUNK + KOMAND - 1 Automating response to endpoint threats using using Sysdig Falco, Splunk, Duo, and Komand Many security teams use endpoint threat
USE CASE IN ACTION Splunk + Komand USE CASE IN ACTION - SPLUNK + KOMAND - 1 Automating response to endpoint threats using using Sysdig Falco, Splunk, Duo, and Komand Many security teams use endpoint threat
Advantage Cloud Two-Factor Security Process
 Advantage Cloud Two-Factor Security Process Advantage Cloud Two-Factor Security Process Table of Contents: 1. Why use Two-Factor Authentication? 2. Two-Factor Authentication Guide for Faculty Members 3.
Advantage Cloud Two-Factor Security Process Advantage Cloud Two-Factor Security Process Table of Contents: 1. Why use Two-Factor Authentication? 2. Two-Factor Authentication Guide for Faculty Members 3.
User Guide: Adding a Device in Duo and Managing Settings
 User Guide: Adding a Device in Duo and Managing Settings The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for applications or web sites such
User Guide: Adding a Device in Duo and Managing Settings The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for applications or web sites such
Salesforce Security Guide
 Version 43.0, Summer 18 @salesforcedocs Last updated: June 21, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are other
Version 43.0, Summer 18 @salesforcedocs Last updated: June 21, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are other
LastPass Enterprise Recommended Policies Guide
 LastPass Enterprise Recommended Policies Guide This document will help guide you through common scenarios and selecting policies to enable on your LastPass Enterprise account. We will not cover all policies
LastPass Enterprise Recommended Policies Guide This document will help guide you through common scenarios and selecting policies to enable on your LastPass Enterprise account. We will not cover all policies
The State of the Raven. Jon Warbrick University of Cambridge Computing Service
 The State of the Raven Jon Warbrick University of Cambridge Computing Service jw35@cam.ac.uk Corvus corax Raven photo used under the terms of the GNU Free Documentation License. Author Pcb21. Raven Web
The State of the Raven Jon Warbrick University of Cambridge Computing Service jw35@cam.ac.uk Corvus corax Raven photo used under the terms of the GNU Free Documentation License. Author Pcb21. Raven Web
The benefits of synchronizing G Suite and Active Directory passwords
 The benefits of synchronizing G Suite and Active Directory passwords www.adselfserviceplus.com Enterprises are adopting more and more applications to enhance productivity and improve employees' user experience.
The benefits of synchronizing G Suite and Active Directory passwords www.adselfserviceplus.com Enterprises are adopting more and more applications to enhance productivity and improve employees' user experience.
Salesforce Security Guide
 Version 42.0, Spring 18 @salesforcedocs Last updated: February 13, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are
Version 42.0, Spring 18 @salesforcedocs Last updated: February 13, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are
Bomgar PA Integration with ServiceNow
 Bomgar PA Integration with ServiceNow 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of
Bomgar PA Integration with ServiceNow 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of
WDC RDS Connection for Android Users
 WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
VETtrak Canvas LMS Integration User Guide
 VETtrak Canvas LMS Integration User Guide Contents Canvas LMS Integration User Guide... 2 What does the Canvas LMS Integration do?... 2 How to use this Guide... 2 Configuration in VETtrak... 2 Security...
VETtrak Canvas LMS Integration User Guide Contents Canvas LMS Integration User Guide... 2 What does the Canvas LMS Integration do?... 2 How to use this Guide... 2 Configuration in VETtrak... 2 Security...
1 Introduction Requirements Architecture Feature List... 3
 Contents 1 Introduction... 2 1.1 Requirements... 2 1.2 Architecture... 3 1.3 Feature List... 3 1.3.1 Device Compliance status... 3 1.3.2 Auto grouping for devices... 4 1.4 Basic Deployment... 4 1.4.1 Prepare
Contents 1 Introduction... 2 1.1 Requirements... 2 1.2 Architecture... 3 1.3 Feature List... 3 1.3.1 Device Compliance status... 3 1.3.2 Auto grouping for devices... 4 1.4 Basic Deployment... 4 1.4.1 Prepare
Lifespan Guide for installing and using Multi-Factor Authentication (MFA)
 Lifespan Guide for installing and using Multi-Factor Authentication (MFA) Registering for MFA for the First Time... 2 Using MFA... 7 Using one of your alternate MFA Methods... 7 Making an MFA response
Lifespan Guide for installing and using Multi-Factor Authentication (MFA) Registering for MFA for the First Time... 2 Using MFA... 7 Using one of your alternate MFA Methods... 7 Making an MFA response
KACE GO Mobile App 5.0. Getting Started Guide
 KACE GO Mobile App 5.0 Getting Started Guide Table of Contents Using the KACE GO Mobile App...3 Getting Started...3 What features are included in this version of the KACE GO Mobile App?...3 How do I access
KACE GO Mobile App 5.0 Getting Started Guide Table of Contents Using the KACE GO Mobile App...3 Getting Started...3 What features are included in this version of the KACE GO Mobile App?...3 How do I access
Active Directory based password synchronization
 Active Directory based password synchronization www.adselfserviceplus.com Real-time password synchronization for cloud applications More and more enterprises are making the move to the cloud, which puts
Active Directory based password synchronization www.adselfserviceplus.com Real-time password synchronization for cloud applications More and more enterprises are making the move to the cloud, which puts
Salesforce Security Guide
 Version 37.0, Summer 16 @salesforcedocs Last updated: August 11, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are
Version 37.0, Summer 16 @salesforcedocs Last updated: August 11, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are
Administrator Guide: New Year Rollover & Login Service Changes. Administrator Guide
 Administrator Guide Summary of New Year Rollover & Login Service Changes Spring Summer 2013 2/19/2013 Spring/Summer 2013 1 Contents Summary... 3 Customer Benefits... 3 New Year Rollover Changes... 3 Account
Administrator Guide Summary of New Year Rollover & Login Service Changes Spring Summer 2013 2/19/2013 Spring/Summer 2013 1 Contents Summary... 3 Customer Benefits... 3 New Year Rollover Changes... 3 Account
Application Instructions for Incoming Reciprocal Exchange Students
 Application Instructions for Incoming Reciprocal Exchange Students If you have been approved by your home university to apply for exchange study at Texas A&M University for a semester or academic year,
Application Instructions for Incoming Reciprocal Exchange Students If you have been approved by your home university to apply for exchange study at Texas A&M University for a semester or academic year,
Vice President for Information Technology Status and Activity Report for April 2019
 Vice President for Information Technology Status and Activity Report for April 2019 Prepared by Timothy M. Chester, Vice President for Information Technology (VPIT) 1. Items Requiring Action Verify and
Vice President for Information Technology Status and Activity Report for April 2019 Prepared by Timothy M. Chester, Vice President for Information Technology (VPIT) 1. Items Requiring Action Verify and
River Bank & Trust Online Banking Initial Log In Instructions
 River Bank & Trust Online Banking Initial Log In Instructions Step 1: Go to River Bank & Trust s website (https://riverbankandtrust.com/). Locate the Online Banking Login box in the upper right corner
River Bank & Trust Online Banking Initial Log In Instructions Step 1: Go to River Bank & Trust s website (https://riverbankandtrust.com/). Locate the Online Banking Login box in the upper right corner
RSA Authentication Manager 8.2
 RSA Authentication Manager 8.2 Over 25,000 customers 50 60 million active tokens in circulation 10 million units shipped per year More than 50% market share RSA Ready Partner Program: 400 Partners with
RSA Authentication Manager 8.2 Over 25,000 customers 50 60 million active tokens in circulation 10 million units shipped per year More than 50% market share RSA Ready Partner Program: 400 Partners with
PTS Customer Protection Agreement
 PTS Customer Protection Agreement Revised: July 26, 2017 Thank you for choosing as your IT provider. Customer s Network environments with the most success have an in-house Network Administrator or someone
PTS Customer Protection Agreement Revised: July 26, 2017 Thank you for choosing as your IT provider. Customer s Network environments with the most success have an in-house Network Administrator or someone
POLICIES AND PROCEDURES
 Integrated Information Technology Services POLICIES AND PROCEDURES Utica College Email POLICY: Email is Utica College s sole accepted mechanism for official electronic communication in the normal conduct
Integrated Information Technology Services POLICIES AND PROCEDURES Utica College Email POLICY: Email is Utica College s sole accepted mechanism for official electronic communication in the normal conduct
Single Sign On through PingOne. Go to https://desktop.pingone.com/changehealthcare and click on the Change Healthcare IdentityIQ icon.
 What is IdentityIQ? IdentityIQ is Change Healthcare s governance-based Identity & Access Management (IAM) software solution that will become a one-stop shop for compliance, password management, and provisioning
What is IdentityIQ? IdentityIQ is Change Healthcare s governance-based Identity & Access Management (IAM) software solution that will become a one-stop shop for compliance, password management, and provisioning
Business Mobile Banking.
 Business Mobile Resource Guide Business Mobile Banking Business Mobile Banking gives business customers the ability to access their business accounts and perform a variety of banking functions from the
Business Mobile Resource Guide Business Mobile Banking Business Mobile Banking gives business customers the ability to access their business accounts and perform a variety of banking functions from the
PureEngage Cloud Release Note. Outbound
 PureEngage Cloud Release Note Outbound 1/2/2018 Outbound Note: Not all changes listed below may pertain to your deployment. November 13, 2017 (14.15.0) October 23, 2017 (14.14.0) September 21, 2017 (14.13.0)
PureEngage Cloud Release Note Outbound 1/2/2018 Outbound Note: Not all changes listed below may pertain to your deployment. November 13, 2017 (14.15.0) October 23, 2017 (14.14.0) September 21, 2017 (14.13.0)
Salesforce Security Guide
 Version 41.0, Winter 18 @salesforcedocs Last updated: December 6, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are
Version 41.0, Winter 18 @salesforcedocs Last updated: December 6, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are
Help Desk Guide. Originally released June 22, 2016 Revised July 24, 2017
 Help Desk Guide Originally released June 22, 2016 Revised July 24, 2017 Table of Contents Commonly-used terms Part 1: Overview Why do I need this guide? Part 2: Enrollment and activation What will the
Help Desk Guide Originally released June 22, 2016 Revised July 24, 2017 Table of Contents Commonly-used terms Part 1: Overview Why do I need this guide? Part 2: Enrollment and activation What will the
SpiraTeam Help Desk Integration Guide Inflectra Corporation
 / SpiraTeam Help Desk Integration Guide Inflectra Corporation Date: June 12, 2017 Contents Introduction... 1 1. Zendesk... 2 Introduction SpiraTeam is an integrated Application Lifecycle Management (ALM)
/ SpiraTeam Help Desk Integration Guide Inflectra Corporation Date: June 12, 2017 Contents Introduction... 1 1. Zendesk... 2 Introduction SpiraTeam is an integrated Application Lifecycle Management (ALM)
HIPAA Compliance discussion
 HIPAA Compliance discussion GoToWebinar Housekeeping: attendee participation Open and hide your control panel Join audio: Choose Mic & Speakers to use VoIP Choose Telephone and dial using the information
HIPAA Compliance discussion GoToWebinar Housekeeping: attendee participation Open and hide your control panel Join audio: Choose Mic & Speakers to use VoIP Choose Telephone and dial using the information
Protect My Ministry Integrated Background Checks for Fellowship One
 Protect My Ministry Integrated Background Checks for Fellowship One The Only Background Check Solution Utilizing the Newest Fellowship One API Integration and User Guide 2005-2012 Protect My Ministry Support:
Protect My Ministry Integrated Background Checks for Fellowship One The Only Background Check Solution Utilizing the Newest Fellowship One API Integration and User Guide 2005-2012 Protect My Ministry Support:
Security Automation Case Study Maricopa Community Colleges. Watch the full webinar replay
 Security Automation Case Study Maricopa Community Colleges Watch the full webinar replay Your Speakers Rich Lang Technical Director: Information Technology Security & Planning Maricopa Community Colleges
Security Automation Case Study Maricopa Community Colleges Watch the full webinar replay Your Speakers Rich Lang Technical Director: Information Technology Security & Planning Maricopa Community Colleges
THE CLOUD SECURITY CHALLENGE:
 THE CLOUD EMAIL SECURITY CHALLENGE: CLOSING THE CYBERSECURITY SKILLS GAP THROUGH AUTOMATION THE EMAIL SECURITY CHALLENGE Email remains at the heart of the business communications landscape. While nobody
THE CLOUD EMAIL SECURITY CHALLENGE: CLOSING THE CYBERSECURITY SKILLS GAP THROUGH AUTOMATION THE EMAIL SECURITY CHALLENGE Email remains at the heart of the business communications landscape. While nobody
Multi Factor Authentication
 Multi Factor Authentication Nick Sherman The University of Toledo 11/28/2017 Introduction Two step verification is an additional security step that helps protect your account by making it harder for other
Multi Factor Authentication Nick Sherman The University of Toledo 11/28/2017 Introduction Two step verification is an additional security step that helps protect your account by making it harder for other
SFU Connect Calendar. Guide. Sharing Calendars
 SFU Connect Calendar How-To Guide Sharing Calendars Last updated: January 2009 Table of Contents Creating a Share... 3 Share Properties Menu... 3 Sharing with Internal Users or Groups... 4 Sharing with
SFU Connect Calendar How-To Guide Sharing Calendars Last updated: January 2009 Table of Contents Creating a Share... 3 Share Properties Menu... 3 Sharing with Internal Users or Groups... 4 Sharing with
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
VMware AirWatch Google Sync Integration Guide Securing Your Infrastructure
 VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
VMware AirWatch Google Sync Integration Guide Securing Your Email Infrastructure Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
Duo Self-Enrollment Guide for Android Tablets
 Duo Self-Enrollment Guide for Android Tablets The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for web sites such as uab.box.com. In addition
Duo Self-Enrollment Guide for Android Tablets The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for web sites such as uab.box.com. In addition
Two-Factor Authentication User FAQ s
 Two-Factor Authentication User FAQ s What is Two-Factor Authentication (2FA)? What does Symantec Validation and ID Protection (VIP) do? I don t have a smartphone, what is my alternative? How many devices
Two-Factor Authentication User FAQ s What is Two-Factor Authentication (2FA)? What does Symantec Validation and ID Protection (VIP) do? I don t have a smartphone, what is my alternative? How many devices
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes
 VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes Workspace ONE UEM v9.6 Have documentation feedback? Submit
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes Workspace ONE UEM v9.6 Have documentation feedback? Submit
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your Android Phone. Overview. Job Aid: Outlook for Mobile - Android
 TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your Android Phone Job Aid: Outlook for Mobile - Android Overview The job aid is for Colleagues that want to access Outlook
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your Android Phone Job Aid: Outlook for Mobile - Android Overview The job aid is for Colleagues that want to access Outlook
Duo Multi-Factor Authentication Enrolling an ipad. Introduction
 Duo Multi-Factor Authentication Enrolling an ipad Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone s
Duo Multi-Factor Authentication Enrolling an ipad Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone s
Salesforce Security Guide
 Version 42.0, Spring 18 @salesforcedocs Last updated: April 19, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are other
Version 42.0, Spring 18 @salesforcedocs Last updated: April 19, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are other
Google Sync Integration Guide. VMware Workspace ONE UEM 1902
 Google Sync Integration Guide VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
Google Sync Integration Guide VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
Pulse Workspace Appliance. Administration Guide
 Pulse Workspace Appliance Administration Guide Product Release 2.0, 1743.1 Document Revisions 1.0 Published Date January 2018 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose, CA 95134 The Pulse
Pulse Workspace Appliance Administration Guide Product Release 2.0, 1743.1 Document Revisions 1.0 Published Date January 2018 Pulse Secure, LLC 2700 Zanker Road, Suite 200 San Jose, CA 95134 The Pulse
Sophos Central for partners and customers: overview and new features. Jonathan Shaw Senior Product Manager, Sophos Central
 Sophos Central for partners and customers: overview and new features Jonathan Shaw Senior Product Manager, Sophos Central What is Sophos Central? Partner Dashboard Admin Self Service Allows Partners to
Sophos Central for partners and customers: overview and new features Jonathan Shaw Senior Product Manager, Sophos Central What is Sophos Central? Partner Dashboard Admin Self Service Allows Partners to
IDG Services Metrics. Kerberos Usage. Weblogin Usage. Kerberos & Webauth Services. Kerberos & Webauth Users. Authentication Metrics
 IDG Services Metrics Authentication Metrics Kerberos Usage Weblogin Usage 3 6 25 5 2 15 1 5 Kerberos Auths Password Inputs 4 3 2 Forced Password Entry Password Logins Single Sign-On Total Logins Apr-9
IDG Services Metrics Authentication Metrics Kerberos Usage Weblogin Usage 3 6 25 5 2 15 1 5 Kerberos Auths Password Inputs 4 3 2 Forced Password Entry Password Logins Single Sign-On Total Logins Apr-9
Update Process and Recommendations
 www.novell.com/documentation Update Process and Recommendations ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents
www.novell.com/documentation Update Process and Recommendations ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents
Configuring User VPN For Azure
 Configuring User VPN For Azure Last updated: April 11, 2017 Aviatrix Systems, Inc. 411 High Street Palo Alto CA 94301 USA http://www.aviatrix.com Tel: +1 844.262.3100 Page 1 of 10 TABLE OF CONTENTS 1 Overview...3
Configuring User VPN For Azure Last updated: April 11, 2017 Aviatrix Systems, Inc. 411 High Street Palo Alto CA 94301 USA http://www.aviatrix.com Tel: +1 844.262.3100 Page 1 of 10 TABLE OF CONTENTS 1 Overview...3
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes
 VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes AirWatch v9.3 Have documentation feedback? Submit a Documentation
VMware AirWatch Integration with Apple School Manager Integrate with Apple's School Manager to automatically enroll devices and manage classes AirWatch v9.3 Have documentation feedback? Submit a Documentation
Compliance Manager ZENworks Mobile Management 2.7.x August 2013
 www.novell.com/documentation Compliance Manager ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
www.novell.com/documentation Compliance Manager ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your iphone. Overview. Job Aid: Outlook for Mobile - iphone
 TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your iphone Overview The job aid is for Colleagues that want to access Outlook (part of Office O365) work email on their mobile
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your iphone Overview The job aid is for Colleagues that want to access Outlook (part of Office O365) work email on their mobile
Product Questions: 62/3Case Study Version: 8.0
 Questions & Answers PDF P-1 Vendor: Microsoft Exam Code: MS-101 Exam Name: Microsoft 365 Mobility and Security Version: DEMO Product Questions: 62/3Case Study Version: 8.0 Case Study: A. Datum Overview
Questions & Answers PDF P-1 Vendor: Microsoft Exam Code: MS-101 Exam Name: Microsoft 365 Mobility and Security Version: DEMO Product Questions: 62/3Case Study Version: 8.0 Case Study: A. Datum Overview
Cyber Security and You: The Future of Physical Access in a Digital World. Chip Epps & Daniel Bailin HID Global
 Cyber Security and You: The Future of Physical Access in a Digital World Chip Epps & Daniel Bailin HID Global 1 Agenda Role of Smart Devices in Access Control Access Controls & Industry Examples Managing
Cyber Security and You: The Future of Physical Access in a Digital World Chip Epps & Daniel Bailin HID Global 1 Agenda Role of Smart Devices in Access Control Access Controls & Industry Examples Managing
