Understanding Online Social Network Usage from a Network Perspective
|
|
|
- Hilary Dickerson
- 5 years ago
- Views:
Transcription
1 Understanding Online Social Network Usage from a Network Perspective Fabian Schneider fabian@net.t-labs.tu-berlin.de Anja Feldmann Balachander Krishnamurthy Walter Willinger Work done while at AT&T Labs Research Technische Universtität Berlin / Deutsche Telekom Laboratories AT&T Labs Research Internet Measurement Conference 2009 Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
2 Motivation Introduction Motivation >600,000,000 users on Online Social Networks (OSNs)...and the number is still growing Open questions/challenges Which features are popular among OSN users? How much time do users spend interacting with OSNs? Is there a correlation between subsequent interactions? Relevance of OSN usage ISPs: data transport, connectivity OSN providers: develop and operate scalable systems R&D: Identify trends, suggest improvements, and new designs Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
3 Outline Introduction Outline 1 Approach 2 Session Characteristics 3 Feature Popularity 4 Dynamics within Sessions Sessions Session = Set of interactions of one user Features Feature = Action a user can perform 5 Conclusions Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
4 Approach General Approach General Approach 1 Reconstruct OSN clickstreams from anonymized packet-level traces Anonymized HTTP header traces from two large ISPs Used Bro 1 to extract HTTP request-response pairs (rr-pairs) 2 Map rr-pairs into sessions Sessions identified via SessionIDs (from HTTP Cookie header) Track logins and logouts Authenticated or offline state Cookies help if login or logout not observed 3 Classify rr-pairs Active (rr-pair resulting from user action) or Indirect (e.g. followup/embedded via HTTP Referer chain) Determine user actions, group into 13 categories 1 Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
5 Approach OSN Selection OSN Selection OSN Selection criteria: OSNs focussing on profiles (e. g., no YouTube,...) 2 globally popular 2 locally popular (well represented at one ISP) Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
6 Approach HTTP Header Traces HTTP Header Traces (anonymized) Collected at residential broadband networks of two commercial ISPs Each site connects 20, 000 DSL users Endace monitoring cards for packet capture Table: Overview of anonymized HTTP header traces. ID start date dur sites size rr-pairs ISP-A1 22 Aug 08 noon 24h all >5TB >80M ISP-A2 18 Sep 08 4am 48h all >10 TB >200 M ISP-A3 01 Apr 09 2am 24h all >6TB >170 M ISP-B1 21 Feb 08 7pm 25h OSNs >15GB >2M ISP-B2 14 Jun 08 8pm 38h OSNs >50GB >3M ISP-B3 23 Jun 08 10am >7d OSNs >110 GB >7M Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
7 Approach HTTP Header Traces HTTP Header Traces (anonymized) Collected at residential broadband networks of two commercial ISPs Each site connects 20, 000 DSL users Endace monitoring cards for packet capture Table: Overview of anonymized HTTP header traces. ID start date dur sites size rr-pairs ISP-A1 22 Aug 08 noon 24h all >5TB >80M ISP-A2 18 Sep 08 4am 48h all >10 TB >200 M ISP-A3 01 Apr 09 2am 24h all >6TB >170 M ISP-B1 21 Feb 08 7pm 25h OSNs >15GB >2M ISP-B2 14 Jun 08 8pm 38h OSNs >50GB >3M ISP-B3 23 Jun 08 10am >7d OSNs >110 GB >7M Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
8 Approach Manual Traces Manual Traces Data set: Active browsing while monitoring passively For customization Good faith effort to explore the feature set of the OSN Identify site names, relevant cookies, login/logout actions Identify URL patterns for action/category classification For validation Provides ground truth 95% of observed actions covered by manual traces Remaining actions classified as Guessed (if the URL contains a hint: /ajax/editphoto.php) Unknown Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
9 Approach Category Examples Category Examples Home All actions on the homepage once authenticated Profile Accessing and changing profiles, posting on walls, privacy settings Apps Applications (external and internal), only rr-pairs directed towards OSN servers Photos Uploading, tagging, and managing photos Friends Browsing, inviting, and accepting friends Offline All actions while unauthenticated, e. g., public profile browsing, registering Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
10 Caveats of our Approach Approach Caveats of our Approach No automated way for producing the URL patterns or extracting the relevant cookies External apps: Not tackled as hosted on different sites Requires customization to all/top external apps Navigation redirects could be leveraged Friendship graph: Cannot tell if two users are friends Requires parsing of payload (privacy!) Requires users to actually access their friend lists during observation Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
11 Outline Session Characteristics Outline 1 Approach 2 Session Characteristics 3 Feature Popularity 4 Dynamics within Sessions 5 Conclusions Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
12 Session Characteristics OSN Session Characteristics OSN Session Characteristics Volume of OSN sessions Consistent with a heavy-tailed distribution Facebook sessions: 200kB 10MB (StudiVZ: 50kB 5MB) Typical Web sessions: 100B 10kB, but heavier tail OSN session durations Most sessions are short: 1-5 minutes Few lasting for more than an hour (10% 20%) Very long (days) sessions observed for 7d trace Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
13 Outline Feature Popularity Outline 1 Approach 2 Session Characteristics 3 Feature Popularity 4 Dynamics within Sessions 5 Conclusions Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
14 Action Popularity Feature Popularity Action Popularity Active Facebook rr-pairs by category for ISP-A2 Percentage of RR Pairs [%] % messaging 22.7 % apps 19.4 % home 8.9 % profile 8.5 % photos 5.8 % offline 4.7 % friends 2.7 % search 1.5 % groups 1.2 % osnspecific active guessed active verified 0.9 % UNKNOWN 0.4 % other 0.4 % videos 0.1 % ads Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
15 Feature Popularity Action Popularity Action Popularity Active Facebook rr-pairs by category for ISP-A2 Percentage of RR Pairs [%] % messaging 22.7 % apps 19.4 % home Findings 8.9 % profile 8.5 % photos 5.8 % offline 4.7 % friends 2.7 % search 1.5 % groups 1.2 % osnspecific active guessed active verified small fraction of guessed (<3 %) & UNKNOWN 0.9 % UNKNOWN 0.4 % other 0.4 % videos 0.1 % ads Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
16 Feature Popularity Action Popularity Action Popularity Active Facebook rr-pairs by category for ISP-A2 Percentage of RR Pairs [%] % messaging 22.7 % apps 19.4 % home Findings 8.9 % profile 8.5 % photos 5.8 % offline 4.7 % friends 2.7 % search 1.5 % groups 1.2 % osnspecific active guessed active verified small fraction of guessed (<3 %) & UNKNOWN Top categories: Messaging, Apps, Home 0.9 % UNKNOWN 0.4 % other 0.4 % videos 0.1 % ads Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
17 Volume per Category Feature Popularity Volume per Category Active and indirect Facebook rr-pairs by category for ISP-A2 Percentage of HTTP Payload Bytes [%] % home 20.5 % profile 17.4 % photos 15.2 % apps 7.5 % offline 6.2 % friends 3.5 % messaging 1.3 % search 1.2 % videos download guessed upload guessed download verified upload verified 0.6 % groups 0.5 % UNKNOWN 0.4 % osnspecific 0.1 % other 0 % ads Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
18 Feature Popularity Volume per Category Volume per Category Active and indirect Facebook rr-pairs by category for ISP-A2 Percentage of HTTP Payload Bytes [%] % home 20.5 % profile 17.4 % photos 15.2 % apps Findings 7.5 % offline 6.2 % friends 3.5 % messaging 1.3 % search 1.2 % videos download guessed upload guessed download verified upload verified Home, Profile, and Photos rise in importance Upload only for Photos and Apps 0.6 % groups 0.5 % UNKNOWN 0.4 % osnspecific 0.1 % other 0 % ads Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
19 Feature Popularity Observations Feature Popularity: Observations Active Facebook rr-pairs per session by category for ISP-A2 Percentage Heterogeneous user base: Many users use only one feature category during a session. profile home messaging friends offline ads groups videos other UNKNOWN photos apps search osnspecific Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
20 Feature Popularity Observations Feature Popularity: Observations (cont d) OSN and all HTTP rr-pairs per hour for ISP-A2 OSN actions rest profile apps messaging photos Per hour usage: Time-of-day effects: similar for OSNs and all HTTP All HTTP Time [hours] Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
21 Feature Popularity Requested profiles Requested profiles Approach: Profiles represent a user in an OSN. Requests to profiles indicate interest in a user We distinguish three types of profiles: own, other, and public Method: Count which and how often profiles are requested Findings Types of profile requests: Majority to profiles of other users, 25-35% to own profile, 12% (22%) to public profiles: Facebook Pages (LinkedIn) Profile requests per Facebook session: mean number of requested profiles: 6 unique profiles: only 3 Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
22 Outline Dynamics within Sessions Outline 1 Approach 2 Session Characteristics 3 Feature Popularity 4 Dynamics within Sessions 5 Conclusions Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
23 Dynamics within Sessions Activity vs. Inactivity Periods Activity vs. Inactivity Periods Apply within session inactivity timeout of 5min: Sessions >1min: 50 % of users are active all time Sessions >40min: >95 % have inactivity periods Action after inactivity Top categories: Messaging, Home, Offline Distribution changes with the length of the pause Facebook action after inactivity period for ISP-A min 10min 20min messaging home offline profile photos friends search remain Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
24 Dynamics within Sessions Feature Sequences Feature Sequences Click sequences of Facebook for ISP-A2: Global transition probabilities 3% friends 5% profile arrows without labels are 1% 20% messaging 3% 2% 3% 2% 2% photos 8% 4% 5% home 9% 2% offline 2% Similar findings as Benevenuto et al for Orkut (IMC 09) Findings Messaging traps users; Home, Photos and Profile attract users to stay Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
25 Conclusions Summary Summary Findings: Most of the sessions are short (few minutes) and small in terms of volume (several MBytes) Long sessions are dominated by inactivity periods Top action categories are: Messaging, Apps, Home, Profile, and Photos. Facebook users are trapped by Messaging and Photos Future Work Expand analysis to other OSNs/external apps, and overcome caveats Evaluate new OSN designs with OSN user model (e. g., PeerSoN a ) a Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
26 Summary Conclusions Summary Findings: Most of the sessions are short (few minutes) and small in terms of volume (several MBytes) Long sessions are dominated by inactivity periods Top action categories are: Messaging, Apps, Home, Profile, and Photos. Facebook users are trapped by Messaging and Photos Time for Questions? Future Work Expand analysis to other OSNs/external apps, and overcome caveats Evaluate new OSN designs with OSN user model (e. g., PeerSoN a ) a Fabian Schneider (TU Berlin/DT Labs) Understanding OSN Usage IMC / 21
A First Look at Mobile Hand-held Device Traffic
 A First Look at Mobile Hand-held Device Traffic Gregor Maier, Fabian Schneider, and Anja Feldmann TU Berlin / Deutsche Telekom Laboratories Ernst-Reuter-Platz 7, 10589 Berlin, Germany {gregor fabian anja}@net.t-labs.tu-berlin.de
A First Look at Mobile Hand-held Device Traffic Gregor Maier, Fabian Schneider, and Anja Feldmann TU Berlin / Deutsche Telekom Laboratories Ernst-Reuter-Platz 7, 10589 Berlin, Germany {gregor fabian anja}@net.t-labs.tu-berlin.de
ISP-Aided Neighbor Selection for P2P Systems
 ISP-Aided Neighbor Selection for P2P Systems Anja Feldmann Vinay Aggarwal, Obi Akonjang, Christian Scheideler (TUM) Deutsche Telekom Laboratories TU-Berlin 1 P2P traffic
ISP-Aided Neighbor Selection for P2P Systems Anja Feldmann Vinay Aggarwal, Obi Akonjang, Christian Scheideler (TUM) Deutsche Telekom Laboratories TU-Berlin 1 P2P traffic
Multimedia Streaming. Mike Zink
 Multimedia Streaming Mike Zink Technical Challenges Servers (and proxy caches) storage continuous media streams, e.g.: 4000 movies * 90 minutes * 10 Mbps (DVD) = 27.0 TB 15 Mbps = 40.5 TB 36 Mbps (BluRay)=
Multimedia Streaming Mike Zink Technical Challenges Servers (and proxy caches) storage continuous media streams, e.g.: 4000 movies * 90 minutes * 10 Mbps (DVD) = 27.0 TB 15 Mbps = 40.5 TB 36 Mbps (BluRay)=
Annoyed Users: Ads and Ad-Block Usage in the Wild
 Annoyed Users: Ads and Ad-Block Usage in the Wild Enric Pujol TU Berlin Oliver Hohlfeld RWTH Aachen Anja Feldmann TU Berlin IMC 15 Tokyo, Japan 2 http://www.journalism.org/2015/04/29/digital-news-revenue-fact-sheet
Annoyed Users: Ads and Ad-Block Usage in the Wild Enric Pujol TU Berlin Oliver Hohlfeld RWTH Aachen Anja Feldmann TU Berlin IMC 15 Tokyo, Japan 2 http://www.journalism.org/2015/04/29/digital-news-revenue-fact-sheet
Peering at Peerings: On the Role of IXP Route Servers
 Peering at Peerings: On the Role of IXP Route Servers Contact: Philipp Richter (prichter@inet.tu-berlin.de) Paper: net.t-labs.tu-berlin.de/~prichter/imc238-richtera.pdf Philipp Richter TU Berlin Nikolaos
Peering at Peerings: On the Role of IXP Route Servers Contact: Philipp Richter (prichter@inet.tu-berlin.de) Paper: net.t-labs.tu-berlin.de/~prichter/imc238-richtera.pdf Philipp Richter TU Berlin Nikolaos
Malicious Activity and Risky Behavior in Residential Networks
 Malicious Activity and Risky Behavior in Residential Networks Gregor Maier 1, Anja Feldmann 1, Vern Paxson 2,3, Robin Sommer 2,4, Matthias Vallentin 3 1 TU Berlin / Deutsche Telekom Laboratories 2 International
Malicious Activity and Risky Behavior in Residential Networks Gregor Maier 1, Anja Feldmann 1, Vern Paxson 2,3, Robin Sommer 2,4, Matthias Vallentin 3 1 TU Berlin / Deutsche Telekom Laboratories 2 International
FG INET: Intelligent Networks
 FG INET: Intelligent Networks An-Institut Deutsche Telekom Laboratories Prof. Anja Feldmann, Ph.D. anja@net.t-labs.tu-berlin.de http://www.net.t-labs.tu-berlin.de/ 1 INET: Research Group Location Telefunkenhochhaus,
FG INET: Intelligent Networks An-Institut Deutsche Telekom Laboratories Prof. Anja Feldmann, Ph.D. anja@net.t-labs.tu-berlin.de http://www.net.t-labs.tu-berlin.de/ 1 INET: Research Group Location Telefunkenhochhaus,
FG INET: Intelligent Networks
 FG INET: Intelligent Networks An-Institut Deutsche Telekom Laboratories Prof. Anja Feldmann, Ph.D. anja@net.t-labs.tu-berlin.de http://www.net.t-labs.tu-berlin.de/ 1 INET: Research Group Location Telefunkenhochhaus,
FG INET: Intelligent Networks An-Institut Deutsche Telekom Laboratories Prof. Anja Feldmann, Ph.D. anja@net.t-labs.tu-berlin.de http://www.net.t-labs.tu-berlin.de/ 1 INET: Research Group Location Telefunkenhochhaus,
A First Look at QUIC in the Wild
 A First Look at QUIC in the Wild Jan Rüth 1, Ingmar Poese 2, Christoph Dietzel 3, Oliver Hohlfeld 1 1 : RWTH Aachen University 2 : Benocs GmbH 3 : TU Berlin / DE-CIX http://comsys.rwth-aachen.de/ London
A First Look at QUIC in the Wild Jan Rüth 1, Ingmar Poese 2, Christoph Dietzel 3, Oliver Hohlfeld 1 1 : RWTH Aachen University 2 : Benocs GmbH 3 : TU Berlin / DE-CIX http://comsys.rwth-aachen.de/ London
BLINC: Multilevel Traffic Classification in the Dark
 BLINC: Multilevel Traffic Classification in the Dark Thomas Karagiannis, UC Riverside Konstantina Papagiannaki, Intel Research Cambridge Michalis Faloutsos, UC Riverside The problem of workload characterization
BLINC: Multilevel Traffic Classification in the Dark Thomas Karagiannis, UC Riverside Konstantina Papagiannaki, Intel Research Cambridge Michalis Faloutsos, UC Riverside The problem of workload characterization
Participant Center User s Guide
 Participant Center User s Guide Your online Participant Center houses all the tools you ll need to begin fundraising for the Walk to End Alzheimer s. This guide provides the details you ll need to get
Participant Center User s Guide Your online Participant Center houses all the tools you ll need to begin fundraising for the Walk to End Alzheimer s. This guide provides the details you ll need to get
Application Detection
 The following topics describe Firepower System application detection : Overview:, on page 1 Custom Application Detectors, on page 6 Viewing or Downloading Detector Details, on page 14 Sorting the Detector
The following topics describe Firepower System application detection : Overview:, on page 1 Custom Application Detectors, on page 6 Viewing or Downloading Detector Details, on page 14 Sorting the Detector
A First Look at Modern Enterprise Traffic
 A First Look at Modern Enterprise Traffic Ruoming Pang, Princeton University Mark Allman (ICSI), Mike Bennett (LBNL), Jason Lee (LBNL), Vern Paxson (ICSI/LBNL), and Brian Tierney (LBNL) The Question What
A First Look at Modern Enterprise Traffic Ruoming Pang, Princeton University Mark Allman (ICSI), Mike Bennett (LBNL), Jason Lee (LBNL), Vern Paxson (ICSI/LBNL), and Brian Tierney (LBNL) The Question What
REACH SCREEN SYSTEMS. System Support Manual. User manual for operating the REACH Announcement Tool, Scheduling Tool, and Touch Screen Systems.
 REACH SCREEN SYSTEMS System Support Manual User manual for operating the REACH Announcement Tool, Scheduling Tool, and Touch Screen Systems. Table of Contents REACH Announcement Tool... 4 Overview... 4
REACH SCREEN SYSTEMS System Support Manual User manual for operating the REACH Announcement Tool, Scheduling Tool, and Touch Screen Systems. Table of Contents REACH Announcement Tool... 4 Overview... 4
Revisiting router architectures with Zipf
 Revisiting router architectures with Zipf Steve Uhlig Deutsche Telekom Laboratories/TU Berlin Nadi Sarrar, Anja Feldmann Deutsche Telekom Laboratories/TU Berlin Rob Sherwood, Xin Huang Deutsche Telekom
Revisiting router architectures with Zipf Steve Uhlig Deutsche Telekom Laboratories/TU Berlin Nadi Sarrar, Anja Feldmann Deutsche Telekom Laboratories/TU Berlin Rob Sherwood, Xin Huang Deutsche Telekom
10 Key Things Your VoIP Firewall Should Do. When voice joins applications and data on your network
 10 Key Things Your Firewall Should Do When voice joins applications and data on your network Table of Contents Making the Move to 3 10 Key Things 1 Security is More Than Physical 4 2 Priority Means Clarity
10 Key Things Your Firewall Should Do When voice joins applications and data on your network Table of Contents Making the Move to 3 10 Key Things 1 Security is More Than Physical 4 2 Priority Means Clarity
ARPA-E Energy Innovation Summit. A user guide for the official networking platform
 ARPA-E Energy Innovation Summit A user guide for the official networking platform GETTING STARTED Welcome to the ARPA-E Energy Innovation Summit, a members only networking application. This powerful app
ARPA-E Energy Innovation Summit A user guide for the official networking platform GETTING STARTED Welcome to the ARPA-E Energy Innovation Summit, a members only networking application. This powerful app
The Power of Prediction: Cloud Bandwidth and Cost Reduction
 The Power of Prediction: Cloud Bandwidth and Cost Reduction Eyal Zohar Israel Cidon Technion Osnat(Ossi) Mokryn Tel-Aviv College Traffic Redundancy Elimination (TRE) Traffic redundancy stems from downloading
The Power of Prediction: Cloud Bandwidth and Cost Reduction Eyal Zohar Israel Cidon Technion Osnat(Ossi) Mokryn Tel-Aviv College Traffic Redundancy Elimination (TRE) Traffic redundancy stems from downloading
Web, HTTP and Web Caching
 Web, HTTP and Web Caching 1 HTTP overview HTTP: hypertext transfer protocol Web s application layer protocol client/ model client: browser that requests, receives, displays Web objects : Web sends objects
Web, HTTP and Web Caching 1 HTTP overview HTTP: hypertext transfer protocol Web s application layer protocol client/ model client: browser that requests, receives, displays Web objects : Web sends objects
Welcome to the SIGGRAPH online networking tool!
 Welcome to the SIGGRAPH online networking tool! We look forward to seeing you at SIGGRAPH 2013! To help you maximize your connections, we'd like to welcome you to the integrated networking platform. This
Welcome to the SIGGRAPH online networking tool! We look forward to seeing you at SIGGRAPH 2013! To help you maximize your connections, we'd like to welcome you to the integrated networking platform. This
Information Sharing and User Privacy in the Third-party Identity Management Landscape
 Information Sharing and User Privacy in the Third-party Identity Management Landscape Anna Vapen¹, Niklas Carlsson¹, Anirban Mahanti², Nahid Shahmehri¹ ¹Linköping University, Sweden ²NICTA, Australia 2
Information Sharing and User Privacy in the Third-party Identity Management Landscape Anna Vapen¹, Niklas Carlsson¹, Anirban Mahanti², Nahid Shahmehri¹ ¹Linköping University, Sweden ²NICTA, Australia 2
Advancing the Art of Internet Edge Outage Detection
 Advancing the Art of Internet Edge Outage Detection ACM Internet Measurement Conference 2018 Philipp Richter MIT / Akamai Ramakrishna Padmanabhan University of Maryland Neil Spring University of Maryland
Advancing the Art of Internet Edge Outage Detection ACM Internet Measurement Conference 2018 Philipp Richter MIT / Akamai Ramakrishna Padmanabhan University of Maryland Neil Spring University of Maryland
Ohio Department of Transportation. SMS Update. District Bridge Engineers. Amjad Waheed, PE. Engineering Division Office of Structural Engineering
 Ohio Department of Transportation John R. Kasich, Governor Jerry Wray, Director SMS Update District Bridge Engineers Amjad Waheed, PE Engineering Division Office of Structural Engineering March 12, 2014
Ohio Department of Transportation John R. Kasich, Governor Jerry Wray, Director SMS Update District Bridge Engineers Amjad Waheed, PE Engineering Division Office of Structural Engineering March 12, 2014
A Multi-Perspective Analysis of Carrier-Grade NAT Deployment
 A Multi-Perspective Analysis of Carrier-Grade NAT Deployment Philipp Richter, Florian Wohlfart, Narseo Vallina-Rodriguez, Mark Allman, Randy Bush, Anja Feldmann, Christian Kreibich, Nicholas Weaver, and
A Multi-Perspective Analysis of Carrier-Grade NAT Deployment Philipp Richter, Florian Wohlfart, Narseo Vallina-Rodriguez, Mark Allman, Randy Bush, Anja Feldmann, Christian Kreibich, Nicholas Weaver, and
INTERNET ENGINEERING. HTTP Protocol. Sadegh Aliakbary
 INTERNET ENGINEERING HTTP Protocol Sadegh Aliakbary Agenda HTTP Protocol HTTP Methods HTTP Request and Response State in HTTP Internet Engineering 2 HTTP HTTP Hyper-Text Transfer Protocol (HTTP) The fundamental
INTERNET ENGINEERING HTTP Protocol Sadegh Aliakbary Agenda HTTP Protocol HTTP Methods HTTP Request and Response State in HTTP Internet Engineering 2 HTTP HTTP Hyper-Text Transfer Protocol (HTTP) The fundamental
Introduction. Can we use Google for networking research?
 Unconstrained Profiling of Internet Endpoints via Information on the Web ( Googling the Internet) Ionut Trestian1 Soups Ranjan2 Aleksandar Kuzmanovic1 Antonio Nucci2 1 Northwestern 2 Narus University Inc.
Unconstrained Profiling of Internet Endpoints via Information on the Web ( Googling the Internet) Ionut Trestian1 Soups Ranjan2 Aleksandar Kuzmanovic1 Antonio Nucci2 1 Northwestern 2 Narus University Inc.
Analyzing Cacheable Traffic in ISP Access Networks for Micro CDN applications via Content-Centric Networking
 Analyzing Cacheable Traffic in ISP Access Networks for Micro CDN applications via Content-Centric Networking Claudio Imbrenda Luca Muscariello Orange Labs Dario Rossi Telecom ParisTech Outline Motivation
Analyzing Cacheable Traffic in ISP Access Networks for Micro CDN applications via Content-Centric Networking Claudio Imbrenda Luca Muscariello Orange Labs Dario Rossi Telecom ParisTech Outline Motivation
Mosaic: Quantifying Privacy Leakage in Mobile Networks
 Mosaic: Quantifying Privacy Leakage in Mobile Networks Ning Xia (Northwestern University) Han Hee Song (Narus Inc.) Yong Liao (Narus Inc.) Marios Iliofotou (Narus Inc.) Antonio Nucci (Narus Inc.) Zhi-Li
Mosaic: Quantifying Privacy Leakage in Mobile Networks Ning Xia (Northwestern University) Han Hee Song (Narus Inc.) Yong Liao (Narus Inc.) Marios Iliofotou (Narus Inc.) Antonio Nucci (Narus Inc.) Zhi-Li
Internet Traffic Classification Using Machine Learning. Tanjila Ahmed Dec 6, 2017
 Internet Traffic Classification Using Machine Learning Tanjila Ahmed Dec 6, 2017 Agenda 1. Introduction 2. Motivation 3. Methodology 4. Results 5. Conclusion 6. References Motivation Traffic classification
Internet Traffic Classification Using Machine Learning Tanjila Ahmed Dec 6, 2017 Agenda 1. Introduction 2. Motivation 3. Methodology 4. Results 5. Conclusion 6. References Motivation Traffic classification
You are Who You Know and How You Behave: Attribute Inference Attacks via Users Social Friends and Behaviors
 You are Who You Know and How You Behave: Attribute Inference Attacks via Users Social Friends and Behaviors Neil Zhenqiang Gong Iowa State University Bin Liu Rutgers University 25 th USENIX Security Symposium,
You are Who You Know and How You Behave: Attribute Inference Attacks via Users Social Friends and Behaviors Neil Zhenqiang Gong Iowa State University Bin Liu Rutgers University 25 th USENIX Security Symposium,
Network performance through the eyes of customers
 ericsson.com/ mobility-report Network performance through the eyes of customers Extract from the Ericsson Mobility Report June 2018 2 Articles Network performance through the eyes of customers Understanding
ericsson.com/ mobility-report Network performance through the eyes of customers Extract from the Ericsson Mobility Report June 2018 2 Articles Network performance through the eyes of customers Understanding
Understanding Today s Mobile Device Shopper. Google/Compete, U.S. Mar 2011
 Understanding Today s Mobile Device Shopper Google/Compete, U.S. Mar 2011 Methodology This study was based on understanding the attitudes of online users who identified themselves as wireless purchasers
Understanding Today s Mobile Device Shopper Google/Compete, U.S. Mar 2011 Methodology This study was based on understanding the attitudes of online users who identified themselves as wireless purchasers
Functionality, Challenges and Architecture of Social Networks
 Functionality, Challenges and Architecture of Social Networks INF 5370 Outline Social Network Services Functionality Business Model Current Architecture and Scalability Challenges Conclusion 1 Social Network
Functionality, Challenges and Architecture of Social Networks INF 5370 Outline Social Network Services Functionality Business Model Current Architecture and Scalability Challenges Conclusion 1 Social Network
Cisco Service Control Online Advertising Solution Guide: Behavioral. Profile Creation Using Traffic Mirroring, Release 4.0.x
 CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Online Advertising Solution Guide: Behavioral Profile Creation Using Traffic Mirroring, Release 4.0.x 1 Overview 2 Configuring Traffic Mirroring
CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Online Advertising Solution Guide: Behavioral Profile Creation Using Traffic Mirroring, Release 4.0.x 1 Overview 2 Configuring Traffic Mirroring
2012 Bike MS Online Fundraising Guide
 2012 Bike MS Online Fundraising Guide Bike MS: Step by Step Guide Learn How To: Access Your Participant Center Fundraise With Facebook Navigate Your Participant Center Home Page Enter Gifts Received Offline
2012 Bike MS Online Fundraising Guide Bike MS: Step by Step Guide Learn How To: Access Your Participant Center Fundraise With Facebook Navigate Your Participant Center Home Page Enter Gifts Received Offline
The State of Mobile. EU5 Mobile Media Landscape and Trends. Alistair Hill, Sr. Analyst
 The State of Mobile EU5 Mobile Media Landscape and Trends Alistair Hill, Sr. Analyst June 10, 2010 Agenda comscore Mobile Data Mobile Media Trends Shifting Mobile Media Landscape Smartphones Summing Up
The State of Mobile EU5 Mobile Media Landscape and Trends Alistair Hill, Sr. Analyst June 10, 2010 Agenda comscore Mobile Data Mobile Media Trends Shifting Mobile Media Landscape Smartphones Summing Up
Energy profiler and Network analyzer Training Lab manual for
 Energy profiler and Network analyzer Training Lab manual for KEY FEATURES BLE SDK V2.0.0 or later This training demonstrates the of usage of the Energy profiler and the Network analyzer modules of Simplicity
Energy profiler and Network analyzer Training Lab manual for KEY FEATURES BLE SDK V2.0.0 or later This training demonstrates the of usage of the Energy profiler and the Network analyzer modules of Simplicity
SSFNET TCP Simulation Analysis by tcpanaly
 SSFNET TCP Simulation Analysis by tcpanaly Hongbo Liu hongbol@winlabrutgersedu Apr 16, 2000 Abstract SSFNET is a collection of SSF-based models for simulating Internet protocols and networks It is designed
SSFNET TCP Simulation Analysis by tcpanaly Hongbo Liu hongbol@winlabrutgersedu Apr 16, 2000 Abstract SSFNET is a collection of SSF-based models for simulating Internet protocols and networks It is designed
OSN Attack Automated Identity Theft Attacks
 OSN Attack Automated Identity Theft Attacks John LePage Department of Electrical & Computer Engineering Missouri University of Science and Technology jlpc5@mst.edu 9 November 2016 2014 John LePage Introduction
OSN Attack Automated Identity Theft Attacks John LePage Department of Electrical & Computer Engineering Missouri University of Science and Technology jlpc5@mst.edu 9 November 2016 2014 John LePage Introduction
TECHNOLOGY AND COMPUTERS TECH IT OUT AND LEARN NEW SKILLS THAT WILL KEEP YOU UP-TO-DATE.
 Queens Library TECHNOLOGY AND COMPUTERS TECH IT OUT AND LEARN NEW SKILLS THAT WILL KEEP YOU UP-TO-DATE. July 2017 Central Library 89-11 Merrick Boulevard Jamaica, 718-990-8625 INTRODUCTION TO COMPUTERS
Queens Library TECHNOLOGY AND COMPUTERS TECH IT OUT AND LEARN NEW SKILLS THAT WILL KEEP YOU UP-TO-DATE. July 2017 Central Library 89-11 Merrick Boulevard Jamaica, 718-990-8625 INTRODUCTION TO COMPUTERS
Review of Previous Lecture
 Review of Previous Lecture Network access and physical media Internet structure and ISPs Delay & loss in packet-switched networks Protocol layers, service models Some slides are in courtesy of J. Kurose
Review of Previous Lecture Network access and physical media Internet structure and ISPs Delay & loss in packet-switched networks Protocol layers, service models Some slides are in courtesy of J. Kurose
facebook a guide to social networking for massage therapists
 facebook a guide to social networking for massage therapists table of contents 2 3 5 6 7 9 10 13 15 get the facts first the importance of social media, facebook and the difference between different facebook
facebook a guide to social networking for massage therapists table of contents 2 3 5 6 7 9 10 13 15 get the facts first the importance of social media, facebook and the difference between different facebook
High-Level Political Forum on Sustainable Development HLPF Shriman Inc, HLPF 2018 Mobile Application Initial Mockup Screens 21-Feb-18
 High-Level Political Forum on Sustainable Development HLPF 2018 Welcome Screen The welcome screen will be displayed at first by default, when opening a mobile application. Signup / Login Screen Displays
High-Level Political Forum on Sustainable Development HLPF 2018 Welcome Screen The welcome screen will be displayed at first by default, when opening a mobile application. Signup / Login Screen Displays
The Internet today. Measuring the Internet: challenges and applications. Politecnico di Torino 7/12/2011. Speaker: Marco Mellia
 Measuring the Internet: challenges and applications Telecommunication Group presentation Speaker: Marco Mellia Politecnico di Torino 7/12/2011 The Internet today 2 A very complex scenario many eterogeneous
Measuring the Internet: challenges and applications Telecommunication Group presentation Speaker: Marco Mellia Politecnico di Torino 7/12/2011 The Internet today 2 A very complex scenario many eterogeneous
Aruba Central Guest Access Application
 Aruba Central Guest Access Application User Guide Copyright Information Copyright 2017Hewlett Packard Enterprise Development LP. Open Source Code This product includes code licensed under the GNU General
Aruba Central Guest Access Application User Guide Copyright Information Copyright 2017Hewlett Packard Enterprise Development LP. Open Source Code This product includes code licensed under the GNU General
Back-Office Web Traffic on the Internet. IMC 2014 Vancouver, BC, CANADA November 5-7, 2014
 Back-Office Web Traffic on the Internet Enric Pujol Philipp Richter Balakrishnan Chandrasekaran Georgios Smaragdakis Anja Feldmann Bruce Maggs Keung- Chi Ng TU- Berlin TU- Berlin Duke University MIT /
Back-Office Web Traffic on the Internet Enric Pujol Philipp Richter Balakrishnan Chandrasekaran Georgios Smaragdakis Anja Feldmann Bruce Maggs Keung- Chi Ng TU- Berlin TU- Berlin Duke University MIT /
On the State of ECN and TCP Options on the Internet
 On the State of ECN and TCP Options on the Internet PAM 2013, March 19, Hong Kong Mirja Kühlewind Sebastian Neuner Brian
On the State of ECN and TCP Options on the Internet PAM 2013, March 19, Hong Kong Mirja Kühlewind Sebastian Neuner Brian
Partitioning Social Networks for Time-dependent Queries
 Partitioning Social Networks for Time-dependent Queries Berenice Carrasco Yi Lu Department of ECE University of Illinois carrasc@illinois.edu, yilu@illinois.edu Joana M. F. da Trindade Department of Computer
Partitioning Social Networks for Time-dependent Queries Berenice Carrasco Yi Lu Department of ECE University of Illinois carrasc@illinois.edu, yilu@illinois.edu Joana M. F. da Trindade Department of Computer
ELEC6910Q Analytics and Systems for Social Media and Big Data Applications Lecture 4. Prof. James She
 ELEC6910Q Analytics and Systems for Social Media and Big Data Applications Lecture 4 Prof. James She james.she@ust.hk 1 Selected Works of Activity 4 2 Selected Works of Activity 4 3 Last lecture 4 Mid-term
ELEC6910Q Analytics and Systems for Social Media and Big Data Applications Lecture 4 Prof. James She james.she@ust.hk 1 Selected Works of Activity 4 2 Selected Works of Activity 4 3 Last lecture 4 Mid-term
How to use MySpace and comment on a photo OR send me a message updating me on what s happening over in Perth!
 How to use MySpace and comment on a photo OR send me a message updating me on what s happening over in Perth! Signing up to MySpace: 1. Firstly, open your internet homepage and type MySpaces s URL (www.myspace.com)
How to use MySpace and comment on a photo OR send me a message updating me on what s happening over in Perth! Signing up to MySpace: 1. Firstly, open your internet homepage and type MySpaces s URL (www.myspace.com)
Quick Reference Guide WEBSITE MESSAGING TOOLS ACCESSIBILITY
 Quick Reference Guide WEBSITE MESSAGING EMAIL TOOLS ACCESSIBILITY Important Information Student privacy is imperative. Do not publish surnames, home addresses, home phone numbers, grades or test scores
Quick Reference Guide WEBSITE MESSAGING EMAIL TOOLS ACCESSIBILITY Important Information Student privacy is imperative. Do not publish surnames, home addresses, home phone numbers, grades or test scores
Lecture 7b: HTTP. Feb. 24, Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Internet and Intranet Protocols and Applications Lecture 7b: HTTP Feb. 24, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu WWW - HTTP/1.1 Web s application layer protocol
Performance and Quality-of-Service Analysis of a Live P2P Video Multicast Session on the Internet
 Performance and Quality-of-Service Analysis of a Live P2P Video Multicast Session on the Internet Sachin Agarwal 1, Jatinder Pal Singh 1, Aditya Mavlankar 2, Pierpaolo Bacchichet 2, and Bernd Girod 2 1
Performance and Quality-of-Service Analysis of a Live P2P Video Multicast Session on the Internet Sachin Agarwal 1, Jatinder Pal Singh 1, Aditya Mavlankar 2, Pierpaolo Bacchichet 2, and Bernd Girod 2 1
Cookies, sessions and authentication
 Cookies, sessions and authentication TI1506: Web and Database Technology Claudia Hauff! Lecture 7 [Web], 2014/15 1 Course overview [Web] 1. http: the language of Web communication 2. Web (app) design &
Cookies, sessions and authentication TI1506: Web and Database Technology Claudia Hauff! Lecture 7 [Web], 2014/15 1 Course overview [Web] 1. http: the language of Web communication 2. Web (app) design &
Introduction to the Internet
 Introduction to the Internet CCST9015 8 th Sep, 2010 Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering 2 Internet in 2003 3 Internet Basics The Internet is a network that connects
Introduction to the Internet CCST9015 8 th Sep, 2010 Dr. Hayden Kwok-Hay So Department of Electrical and Electronic Engineering 2 Internet in 2003 3 Internet Basics The Internet is a network that connects
Experimental Study of Skype. Skype Peer-to-Peer VoIP System
 An Experimental Study of the Skype Peer-to-Peer VoIP System Saikat Guha (Cornell) Neil Daswani (Google) Ravi Jain (Google) IPTPS 2006 About Skype Voice over IP (VoIP) 50 million users Valued at $2.6 billion
An Experimental Study of the Skype Peer-to-Peer VoIP System Saikat Guha (Cornell) Neil Daswani (Google) Ravi Jain (Google) IPTPS 2006 About Skype Voice over IP (VoIP) 50 million users Valued at $2.6 billion
CMSC 332 Computer Networking Web and FTP
 CMSC 332 Computer Networking Web and FTP Professor Szajda CMSC 332: Computer Networks Project The first project has been posted on the website. Check the web page for the link! Due 2/2! Enter strings into
CMSC 332 Computer Networking Web and FTP Professor Szajda CMSC 332: Computer Networks Project The first project has been posted on the website. Check the web page for the link! Due 2/2! Enter strings into
BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents
 BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents Definitions... 2 Summary... 2 BIDMC Multi-Factor Authentication Enrollment... 3 Common Multi-Factor Authentication Enrollment Issues...
BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents Definitions... 2 Summary... 2 BIDMC Multi-Factor Authentication Enrollment... 3 Common Multi-Factor Authentication Enrollment Issues...
Automated Traffic Classification and Application Identification using Machine Learning. Sebastian Zander, Thuy Nguyen, Grenville Armitage
 Automated Traffic Classification and Application Identification using Machine Learning Sebastian Zander, Thuy Nguyen, Grenville Armitage {szander,tnguyen,garmitage}@swin.edu.au Centre for Advanced Internet
Automated Traffic Classification and Application Identification using Machine Learning Sebastian Zander, Thuy Nguyen, Grenville Armitage {szander,tnguyen,garmitage}@swin.edu.au Centre for Advanced Internet
Course Syllabus. Course Title. Who should attend? Course Description. PHP ( Level 1 (
 Course Title PHP ( Level 1 ( Course Description PHP '' Hypertext Preprocessor" is the most famous server-side programming language in the world. It is used to create a dynamic website and it supports many
Course Title PHP ( Level 1 ( Course Description PHP '' Hypertext Preprocessor" is the most famous server-side programming language in the world. It is used to create a dynamic website and it supports many
Understanding the Share of IPv6 Traffic in a Dual-Stack ISP
 Understanding the Share of IPv6 Traffic in a Dual-Stack ISP Enric Pujol, Philipp Richter, and Anja Feldmann PAM 2017, Sydney, Australia IPv6 adoption metrics User end hosts Server-side measurements e.g.,
Understanding the Share of IPv6 Traffic in a Dual-Stack ISP Enric Pujol, Philipp Richter, and Anja Feldmann PAM 2017, Sydney, Australia IPv6 adoption metrics User end hosts Server-side measurements e.g.,
A Hybrid Approach for Accurate Application Traffic Identification
 A Hybrid Approach for Accurate Application Traffic Identification Thesis Defence December 21, 2005 Young J. Won yjwon@postech.ac.kr Distributed Processing & Network Management Lab. Dept. of Computer Science
A Hybrid Approach for Accurate Application Traffic Identification Thesis Defence December 21, 2005 Young J. Won yjwon@postech.ac.kr Distributed Processing & Network Management Lab. Dept. of Computer Science
Empirical Characterization of P2P Systems
 Empirical Characterization of P2P Systems Reza Rejaie Mirage Research Group Department of Computer & Information Science University of Oregon http://mirage.cs.uoregon.edu/ Collaborators: Daniel Stutzbach
Empirical Characterization of P2P Systems Reza Rejaie Mirage Research Group Department of Computer & Information Science University of Oregon http://mirage.cs.uoregon.edu/ Collaborators: Daniel Stutzbach
Characterizing Privacy in Online Social Networks
 Characterizing Privacy in Online Social Networks Balachander Krishnamurthy, AT&T Labs Research Craig E. Wills, Worcester Polytechnic Institute ACM SIGCOMM Workshop on Online Social Networks Seattle, Washington
Characterizing Privacy in Online Social Networks Balachander Krishnamurthy, AT&T Labs Research Craig E. Wills, Worcester Polytechnic Institute ACM SIGCOMM Workshop on Online Social Networks Seattle, Washington
Identifying Traffic Differentiation in Mobile Networks
 Identifying Traffic Differentiation in Mobile Networks Arash Molavi Kakhki, Abbas Razaghpanah, Anke Li, Hyungjoon Koo, Rajesh Golani, David Choffnes, Phillipa Gill, Alan Mislove Northeastern University,
Identifying Traffic Differentiation in Mobile Networks Arash Molavi Kakhki, Abbas Razaghpanah, Anke Li, Hyungjoon Koo, Rajesh Golani, David Choffnes, Phillipa Gill, Alan Mislove Northeastern University,
Threats & Vulnerabilities in Online Social Networks
 Threats & Vulnerabilities in Online Social Networks Lei Jin LERSAIS Lab @ School of Information Sciences University of Pittsburgh 03-26-2015 201 Topics Focus is the new vulnerabilities that exist in online
Threats & Vulnerabilities in Online Social Networks Lei Jin LERSAIS Lab @ School of Information Sciences University of Pittsburgh 03-26-2015 201 Topics Focus is the new vulnerabilities that exist in online
Security of End User based Cloud Services Sang Young
 Security of End User based Cloud Services Sang Young Chairman, Mobile SIG Professional Information Security Association sang.young@pisa.org.hk Cloud Services you can choose Social Media Business Applications
Security of End User based Cloud Services Sang Young Chairman, Mobile SIG Professional Information Security Association sang.young@pisa.org.hk Cloud Services you can choose Social Media Business Applications
A Rendezvous-based Paradigm for Analysis of Solicited and Unsolicited Traffic
 A Rendezvous-based Paradigm for Analysis of Solicited and Unsolicited Traffic DUST 2012 May 15, 2012 David Plonka & Paul Barford {plonka,pb}@cs.wisc.edu Outline Rendezvous-based Traffic Analysis What is
A Rendezvous-based Paradigm for Analysis of Solicited and Unsolicited Traffic DUST 2012 May 15, 2012 David Plonka & Paul Barford {plonka,pb}@cs.wisc.edu Outline Rendezvous-based Traffic Analysis What is
7 The system should allow administrator to close a user profile. 8 The system shall make the old events invisible to avoid crowded geo scope.
 Requirement 1 2 3 4 5 6 Description The system shall upload pictures to a hashtag specified by the user, or to their current location The system shall allow a user to reserve a hashtag, allowing the user
Requirement 1 2 3 4 5 6 Description The system shall upload pictures to a hashtag specified by the user, or to their current location The system shall allow a user to reserve a hashtag, allowing the user
Lecture 9a: Sessions and Cookies
 CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
arxiv: v1 [cs.cy] 19 Jun 2018
![arxiv: v1 [cs.cy] 19 Jun 2018 arxiv: v1 [cs.cy] 19 Jun 2018](/thumbs/90/103047186.jpg) 1 You, the Web and Your Device: Longitudinal Characterization of Browsing Habits arxiv:1806.07158v1 [cs.cy] 19 Jun 2018 LUCA VASSIO, Politecnico di Torino IDILIO DRAGO, Politecnico di Torino MARCO MELLIA,
1 You, the Web and Your Device: Longitudinal Characterization of Browsing Habits arxiv:1806.07158v1 [cs.cy] 19 Jun 2018 LUCA VASSIO, Politecnico di Torino IDILIO DRAGO, Politecnico di Torino MARCO MELLIA,
Pinterest. What is Pinterest?
 Pinterest What is Pinterest? Pinterest is like an electronic bulletin board that allows users to save and share photos they find on the internet. Usually when a user pins a photo it is linked to a blog
Pinterest What is Pinterest? Pinterest is like an electronic bulletin board that allows users to save and share photos they find on the internet. Usually when a user pins a photo it is linked to a blog
Network Controller 3500 Quick Start Guide
 Network Controller 3500 Quick Start Guide Firmware Version 1.00.82 1. Configuring the Controller 1.1. Connect to the Controller: The default LAN IP Address of the Controller is: IP: 192.168.1.1 Set you
Network Controller 3500 Quick Start Guide Firmware Version 1.00.82 1. Configuring the Controller 1.1. Connect to the Controller: The default LAN IP Address of the Controller is: IP: 192.168.1.1 Set you
745: Advanced Database Systems
 745: Advanced Database Systems Yanlei Diao University of Massachusetts Amherst Outline Overview of course topics Course requirements Database Management Systems 1. Online Analytical Processing (OLAP) vs.
745: Advanced Database Systems Yanlei Diao University of Massachusetts Amherst Outline Overview of course topics Course requirements Database Management Systems 1. Online Analytical Processing (OLAP) vs.
Sitecore Experience Platform 8.0 Rev: September 13, Sitecore Experience Platform 8.0
 Sitecore Experience Platform 8.0 Rev: September 13, 2018 Sitecore Experience Platform 8.0 All the official Sitecore documentation. Page 1 of 455 Experience Analytics glossary This topic contains a glossary
Sitecore Experience Platform 8.0 Rev: September 13, 2018 Sitecore Experience Platform 8.0 All the official Sitecore documentation. Page 1 of 455 Experience Analytics glossary This topic contains a glossary
Lab 2. All datagrams related to favicon.ico had been ignored. Diagram 1. Diagram 2
 Lab 2 All datagrams related to favicon.ico had been ignored. Diagram 1 Diagram 2 1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running? According to the diagram
Lab 2 All datagrams related to favicon.ico had been ignored. Diagram 1 Diagram 2 1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running? According to the diagram
Online Strategies for Intra and Inter Provider Service Migration in Virtual Networks
 Online Strategies for Intra and Inter Provider Service Migration in Virtual Networks or/and: How to migrate / allocate resources when you don t know the future? Co-authors: Dushyant Arora Marcin Bienkowski
Online Strategies for Intra and Inter Provider Service Migration in Virtual Networks or/and: How to migrate / allocate resources when you don t know the future? Co-authors: Dushyant Arora Marcin Bienkowski
Drupal 7 Template. Page 1 of 27. Site Title. Navigation Tabs. Homepage Slide. Social Media. News article. Events. Links. Contact Information
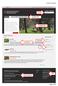 Site Title Navigation Tabs Homepage Slide News article Social Media Events Contact Information Links Page 1 of 27 Table of Contents USER ACCOUNT... 3 Edit Profile... 3 CONTENT... 5 ADD CONTENT... 5 BASIC
Site Title Navigation Tabs Homepage Slide News article Social Media Events Contact Information Links Page 1 of 27 Table of Contents USER ACCOUNT... 3 Edit Profile... 3 CONTENT... 5 ADD CONTENT... 5 BASIC
CSE 124: Networked Services Lecture-17
 Fall 2010 CSE 124: Networked Services Lecture-17 Instructor: B. S. Manoj, Ph.D http://cseweb.ucsd.edu/classes/fa10/cse124 11/30/2010 CSE 124 Networked Services Fall 2010 1 Updates PlanetLab experiments
Fall 2010 CSE 124: Networked Services Lecture-17 Instructor: B. S. Manoj, Ph.D http://cseweb.ucsd.edu/classes/fa10/cse124 11/30/2010 CSE 124 Networked Services Fall 2010 1 Updates PlanetLab experiments
Experimental Networking Research and Performance Evaluation
 Generating Realistic TCP Workloads Felix Hernandez-Campos Ph. D. Candidate Dept. of Computer Science Univ. of North Carolina at Chapel Hill Recipient of the 2001 CMG Fellowship Joint work with F. Donelson
Generating Realistic TCP Workloads Felix Hernandez-Campos Ph. D. Candidate Dept. of Computer Science Univ. of North Carolina at Chapel Hill Recipient of the 2001 CMG Fellowship Joint work with F. Donelson
User Guide NRC Research Press Journals Published by
 RP Mobile User Guide NRC Research Press Journals Published by ACCESS Accessing RP Mobile Open the browser on a compatible device and enter the URL www.nrcresearchpress.com. As you are accessing the site
RP Mobile User Guide NRC Research Press Journals Published by ACCESS Accessing RP Mobile Open the browser on a compatible device and enter the URL www.nrcresearchpress.com. As you are accessing the site
!!!!!! Digital Foundations
 Digital Foundations Digital Literacy Knowing which tools to use and how to use them. The goal of our workshop today is to improve your digital literacy so you strategically choose what to do online and
Digital Foundations Digital Literacy Knowing which tools to use and how to use them. The goal of our workshop today is to improve your digital literacy so you strategically choose what to do online and
SEARCHING FOR FRIENDS
 Step One In the top right hand corner, click on the Find Friends link. You will be redirected to a new page. In the bottom left hand side of the page you will see a text box labeled Search for People.
Step One In the top right hand corner, click on the Find Friends link. You will be redirected to a new page. In the bottom left hand side of the page you will see a text box labeled Search for People.
Internet Basics. Basic Terms and Concepts. Connecting to the Internet
 Internet Basics In this Learning Unit, we are going to explore the fascinating and ever-changing world of the Internet. The Internet is the largest computer network in the world, connecting more than a
Internet Basics In this Learning Unit, we are going to explore the fascinating and ever-changing world of the Internet. The Internet is the largest computer network in the world, connecting more than a
iapps Social Step by Step Guide to Create Facebook Pages, Twitter accounts, and LinkedIn Accounts
 iapps Social Step by Step Guide to Create Facebook Pages, Twitter accounts, and LinkedIn Accounts 1 Table of Contents Inroduction... 2 Creating a Facebook Business Page... 2 Creating a Twitter Account...
iapps Social Step by Step Guide to Create Facebook Pages, Twitter accounts, and LinkedIn Accounts 1 Table of Contents Inroduction... 2 Creating a Facebook Business Page... 2 Creating a Twitter Account...
Telkomtelstra Corporate Website Increase a Business Experience through telkomtelstra Website
 Telkomtelstra Corporate Website Increase a Business Experience through telkomtelstra Website Award for Innovation in Corporate Websites Asia Pacific Stevie Awards 2016 Table of Content Telkomtelstra Website
Telkomtelstra Corporate Website Increase a Business Experience through telkomtelstra Website Award for Innovation in Corporate Websites Asia Pacific Stevie Awards 2016 Table of Content Telkomtelstra Website
For information on troubleshooting common issues, see the Technical Support section in the online help.
 GIFTS Online Mobile GIFTS Online Mobile gives users a mobile version of their GIFTS Online system in order to easily access grant related information when it is not convenient to log into their main version
GIFTS Online Mobile GIFTS Online Mobile gives users a mobile version of their GIFTS Online system in order to easily access grant related information when it is not convenient to log into their main version
Concept: Traffic Flow. Prof. Anja Feldmann, Ph.D. Dr. Steve Uhlig
 Concept: Traffic Flow Prof. Anja Feldmann, Ph.D. Dr. Steve Uhlig 1 Passive measurement capabilities: Packet monitors Available data: All protocol information All content Possible analysis: Application
Concept: Traffic Flow Prof. Anja Feldmann, Ph.D. Dr. Steve Uhlig 1 Passive measurement capabilities: Packet monitors Available data: All protocol information All content Possible analysis: Application
1-1. Switching Networks (Fall 2010) EE 586 Communication and. September Lecture 10
 EE 586 Communication and Switching Networks (Fall 2010) Lecture 10 September 17 2010 1-1 Announcement Send me your group and get group ID HW3 (short) out on Monday Personal leave for next two weeks No
EE 586 Communication and Switching Networks (Fall 2010) Lecture 10 September 17 2010 1-1 Announcement Send me your group and get group ID HW3 (short) out on Monday Personal leave for next two weeks No
Google Analytics Reference Guide
 Google Analytics Reference Guide Updated: December 2017 Process for Gaining Access to Google Analytics 1. You will need to create a generic department email, such as cmich_ucomm@gmail.com. This can be
Google Analytics Reference Guide Updated: December 2017 Process for Gaining Access to Google Analytics 1. You will need to create a generic department email, such as cmich_ucomm@gmail.com. This can be
An In-depth Study of LTE: Effect of Network Protocol and Application Behavior on Performance
 An In-depth Study of LTE: Effect of Network Protocol and Application Behavior on Performance Authors: Junxian Huang, Feng Qian, Yihua Guo, Yuanyuan Zhou, Qiang Xu, Z. Morley Mao, Subhabrata Sen, Oliver
An In-depth Study of LTE: Effect of Network Protocol and Application Behavior on Performance Authors: Junxian Huang, Feng Qian, Yihua Guo, Yuanyuan Zhou, Qiang Xu, Z. Morley Mao, Subhabrata Sen, Oliver
liberate, (n): A library for exposing (traffic-classification) rules and avoiding them efficiently
 liberate, (n): A library for exposing (traffic-classification) rules and avoiding them efficiently Fangfan Li, Abbas Razaghpanah, Arash Molavi Kakhki, Arian Akhavan Niaki, David Choffnes, Phillipa Gill,
liberate, (n): A library for exposing (traffic-classification) rules and avoiding them efficiently Fangfan Li, Abbas Razaghpanah, Arash Molavi Kakhki, Arian Akhavan Niaki, David Choffnes, Phillipa Gill,
Guide to Yammer For Education Filed. There have been an increase in use of the social network applications in education system
 Guide to Yammer For Education Filed There have been an increase in use of the social network applications in education system such as Facebook, Twitter and Yammer. Yammer create by Microsoft Office Company
Guide to Yammer For Education Filed There have been an increase in use of the social network applications in education system such as Facebook, Twitter and Yammer. Yammer create by Microsoft Office Company
App Configuration: Updating the app after major website changes
 App Configuration: Updating the app after major website changes Introduction If your website has been re-organized or you have a new website provider, your Mobile Communication App will need updating.
App Configuration: Updating the app after major website changes Introduction If your website has been re-organized or you have a new website provider, your Mobile Communication App will need updating.
MEMBERSHIP & PARTICIPATION
 MEMBERSHIP & PARTICIPATION What types of activities can I expect to participate in? There are a variety of activities for you to participate in such as discussion boards, idea exchanges, contests, surveys,
MEMBERSHIP & PARTICIPATION What types of activities can I expect to participate in? There are a variety of activities for you to participate in such as discussion boards, idea exchanges, contests, surveys,
CERTIFICATE. P3 communications GmbH. Am Kraftversorgungsturm 3, D Aachen, Germany. hereby certifies that. Slovak Telekom a.s.
 CERTIFICATE P3 communications GmbH Am Kraftversorgungsturm 3, D 52070 Aachen, Germany hereby certifies that Slovak Telekom a.s. Bajkalská 28, 817 62 Bratislava Slovakia achieved Best in Test with a Total
CERTIFICATE P3 communications GmbH Am Kraftversorgungsturm 3, D 52070 Aachen, Germany hereby certifies that Slovak Telekom a.s. Bajkalská 28, 817 62 Bratislava Slovakia achieved Best in Test with a Total
Ning Frequently Asked Questions
 Ning Frequently Asked Questions Ning is a Web tool that allows anyone to create a customizable social network, allowing users to share pictures and videos, maintain blogs, communicate in chat and discussion
Ning Frequently Asked Questions Ning is a Web tool that allows anyone to create a customizable social network, allowing users to share pictures and videos, maintain blogs, communicate in chat and discussion
Looking Forward: Challenges in Mobile Security. John Mitchell Stanford University
 Looking Forward: Challenges in Mobile Security John Mitchell Stanford University Outline Mobile platform security SessionJuggler Using phone as authentication token SelectiveAuth Protecting resources on
Looking Forward: Challenges in Mobile Security John Mitchell Stanford University Outline Mobile platform security SessionJuggler Using phone as authentication token SelectiveAuth Protecting resources on
It s Not the Cost, It s the Quality! Ion Stoica Conviva Networks and UC Berkeley
 It s Not the Cost, It s the Quality! Ion Stoica Conviva Networks and UC Berkeley 1 A Brief History! Fall, 2006: Started Conviva with Hui Zhang (CMU)! Initial goal: use p2p technologies to reduce distribution
It s Not the Cost, It s the Quality! Ion Stoica Conviva Networks and UC Berkeley 1 A Brief History! Fall, 2006: Started Conviva with Hui Zhang (CMU)! Initial goal: use p2p technologies to reduce distribution
A look at your OneDrive page
 7/24/2014 Exploring OneDrive A look at your OneDrive page Greg Fritz ONEDRIVETIPS.COM Exploring your OneDrive Page If you have not completed setting up your OneDrive account please do so now, the information
7/24/2014 Exploring OneDrive A look at your OneDrive page Greg Fritz ONEDRIVETIPS.COM Exploring your OneDrive Page If you have not completed setting up your OneDrive account please do so now, the information
