How to create a secure WordPress install v1.1
|
|
|
- Juniper Boone
- 6 years ago
- Views:
Transcription
1 Table of Contents: Table of Contents:... 1 Introduction... 2 Installing WordPress... 2 Accessing your WordPress tables... 2 Changing your WordPress Table Prefix... 3 Before Installation... 3 Manually Change... 3 Through WP Prefix Table Changer... 4 Preparing the Blog... 5 Changing your Admin Username... 5 Create a new limited access user... 5 Hardening your WP Install... 7 Restricting wp-content & wp-includes... 7 Restricting wp-admin... 7 Block all except your IP... 7 Password Required -.htpasswd... 7 The.htaccess file... 7 The.htpasswd file... 8 MUSTHAVE Plugins... 8 WPIDS - Detect Intrusions... 8 WordPress Plugin Tracker Are you updated?... 9 WordPress Online Security Scanner The End P a g e
2 Introduction This paper provides you with all necessary information to improve the security for your blog. We try to describe the steps in an easy, understandable way without to much tech talk, so that you can easily follow them and you don t run into problems with applying these changes to secure your blog. All information can be found on BlogSecurity.net; this paper serves as a compact guide to secure your blog. We will strive to keep this document updated, so check back regularly. If you have questions, problems, ideas or something else related to this paper, feel free to contact us. Important: Before using any of the techniques outlined is this paper please perform a full backup of your WP files and Database. See our 5 failsafe steps to upgrade WordPress for help. Installing WordPress Accessing your WordPress tables Before you even start to install your blog it is important to choose the right type of database user with the right permissions. The idea behind this vital step is to use a limited database user to administrate your blog. In the event that your blog is compromised, the attacker will struggle to escalate his/her privileges outside of your blog (i.e. the rest of the web server or hosted account). Note: Never let a web application access the database with a root user. In short, you are looking for trouble. Your user-account should have no global SQL privileges as well as limited access to the database where your WordPress tables reside. It s enough to give your user the following rights in order to perform all daily tasks: For Data: SELECT, INSERT, UPDATE, DELETE For Structures: CREATE, ALTER, DROP If you re only allowed to run one database with your hosting account, but you can create multiple users within this database, create a user whose access is limited to the WordPress tables spoken of. The privileges should be: For Data: SELECT, INSERT, UPDATE, DELETE For Structures: ALTER Why are we doing this? It s for your security, so if an attacker gains access to your blog and is able to run queries, these queries are then limited only to your WordPress installation and not the rest of your databases. 2 P a g e
3 Changing your WordPress Table Prefix To mitigate SQL injection threats you should change the default WordPress prefix from wp_ to something more random like 4i32a_. Often attackers use public exploits of the Internet. These exploits will likely rely on the fact that most WordPress installations use the table prefix, wp_. Changing this will make it more difficult for an attacker to successfully run exploits. To easily recognize which prefix stands for which web application you can keep something within the prefix of the application, such as wp_4i32a_ or wp4i32a_. It s just important to modify it, so an attacker can t easily guess your WordPress prefix. Before Installation If you just start to install WordPress this step is quite easy to achieve, all you need to do is to change this line from the WP-CONFIG.PHP file: $table_prefix = wp_ ; to something different, for our example: $table_prefix = 4i32a_ ; After that you can simply run the installation routine of WordPress and all tables and fields are created with your different WordPress prefix. Manually Change You want to change the table prefix on an existing installation it requires a few additional steps. This use to be a tedious process and explained below, however, for the quick solution see the next section. The first step is to open your WP-CONFIG.PHP file and change that line: $table_prefix = wp_ ; To use the previous example again we re using the prefix 4i32a_ so our line should look like this: $table_prefix = 4i32a_ ; Now that this is done we need to rename all WordPress tables to match the new prefix, to achieve that we need to run a SQL Command 1 within a web interface like PHPMyAdmin or similar, as WordPress doesn t allow it to change the prefix directly. So these tables: wp_categories, wp_comments, wp_link2cat, wp_links, wp_options, wp_post2cat, wp_postmeta, wp_posts, wp_usermeta, wp_users Should become this: 1 Example Query: RENAME TABLE wp_categories TO 4i32a_categories 3 P a g e
4 4i32a_categories, 4i32a_comments, 4i32a_link2cat, 4i32a_links, 4i32a_options, 4i32a_post2cat, 4i32a_postmeta, 4i32a_posts, 4i32a_usermeta, 4i32a_users Now you may think that we re done right? But that s not the case. WordPress includes some values with the table prefix as well. In order to be able to use your blog we need to change them first. Within the table wp_options 2 we need to change the value of one record for the field option_name from wp_user_roles to 4i32a_user_roles 3. Now you need to replace two 4 other values in this table: wp_usermeta. The values wp_autosave_draft_ids and wp_user_level for the field meta_key need to be changed to the new prefix: 4i32a_autosave_draft_ids and 4i32a_user_level. That s it! But BlogSecurity has made this even easier with WP Prefix Table Changer. Through WP Prefix Table Changer We created a plugin called WP Prefix Table Changer, which automates the whole process of renaming your WordPress tables and the mentioned table entries. After you downloaded the plugin from BlogSecurity.net, you just need to extract the files into your WordPress plugin-folder, which should be WORDPRESS/WP-CONTENT/PLUGINS. After this you need to enter the WP-Admin area and enable the WP Prefix Table Changer Plugin. After the activation a new submenu tab appears within the plugin page menu called Prefix Changer, click on it. On that page you see the following: As you can see you this blog is using the default database WP Prefix. Now change that displayed prefix to something random, meaningless like our old example 4i32a_. Once done, just click the Start Renaming button and the plugin starts to rename all table names from wp_ to your selected random string. It should be noted that 3 rd Party Component Tables are also changed, as they need that new prefix too. 2 The default prefix is used, to avoid confusions that could occur if we would use the new prefix 3 UPDATE 4i32a_options SET option_name='4i32a_user_roles' WHERE option_name='wp_user_roles' LIMIT 1 4 Note: it can be that these fields don t exist currently, as they re just created when they re needed, once they get created they get the correct value automatically 4 P a g e
5 The plugin s last step is to change the prefix within the WP-CONFIG.PHP file. You ll get a message if this process has succeeded or failed. If the process is successful the WP- CONFIG.PHP file will be made read-only (644) for security purposes, if the process failed the file is mostly unwriteable already. So if the process failed all you need is to open the WP-CONFIG.PHP file manually and change the table prefix to your new random prefix. Preparing the Blog Now your blog is installed and some excellent security fundamentals are in place, well done! Next we are going to make some changes to your WP-users, in order to improve the security. Changing your Admin Username You should rename your default administration account from admin to something harder to guess, as all currently available WP versions are vulnerable to User Enumeration. Changing the default admin account to another name will help mitigate password brute force attacks. Note: You must assume the attacker will know your username. Therefore, ensure that you have chosen a strong password. Login with your Admin account and create a new user, which holds the role Administrator. Set the username to something that is hard to guess or enumerate. Give him a password (something not so easy to guess, with non alphanumeric characters) and so on, you can use the same as for your old Admin account, as we are going to delete that. After the account is created you need to switch the account you re using currently. Now you re logged in with your new admin account. It s time to drop your old admin. Create a new limited access user Before we start with that step you should grap yourself a copy of the plugin Role Manager by imweb-gefunden. This plugin will enable you to set granular WP user permissions for each user. After you activated the plugin, create a new user account with the features that you like. The less that your user account is able to do the better your security will be; your new user should have no higher role than Contributor. The role of Contributor may not have enough rights by default, therefore we installed the Role Manager plugin before. That plugin allows it to set additional rights for each user that he wouldn t normally have with his role, you can change the role rights or even create new roles. 5 P a g e
6 As a standard we suggest new users be given contributor level access, however, this plugin allows you a lot more flexibility. As seen below. See: Role Manager information. If you have multiple users, it is best to change the rights for the additional role, or maybe you should even create a new role as you want to run some users within normal roles as well. When creating users, be wary of allowing untrusted users access to roles such as upload files, general plugin access, edit files/pages/posts, import and unfiltered html, as these roles give the user a lot of power. In two words, be wise. Changing the role rights with Role Manager 6 P a g e
7 Hardening your WP Install 5 This will cover how to protect your admin area from unauthorised access. This step is easier to achieve for single user blogs, and can be a real pain for multiple user blogs. You have to decide if you want to shoulder that in order to secure your blog or not, but you should. Restricting wp-content & wp-includes In this step we re going to limit the access to these directories, we re mainly going to generally deny everything, except the request for images, CSS and some JavaScript files. You need to put this code into your.htaccess file for the folders WP-CONTENT & WP-INCLUDES: Order Allow,Deny Deny from all <Files ~ ".(css jpe?g png gif js)$"> Allow from all </Files> Note: You may want add specific PHP file(s) access for certain templates and plugins. Restricting wp-admin Block all except your IP If you run a single user blog, you may want to restrict access to your WP-ADMIN directory via IP. Make sure you have a static IP address (one that doesn t change) before doing this. The.HTACCESS file within WP-ADMIN should look like that: Order deny,allow Allow from a.b.c.d #That s your static IP Deny from all Save the file and try to access the wp-admin folder through a web proxy; it should be blocked if everything is working correctly. After that try access it directly with your IP (a.b.c.d). If everything works correctly WP-ADMIN will now be restricted only to the IP(s) of your choice. Password Required -.htpasswd Certainly the preferred option is to use password protection. This means you can still access your admin directory from anywhere, however, it adds an additional security layer. The.htaccess file he.htaccess file within WP-ADMIN should look like that: AuthUserFile /srv/www/user1/.htpasswd #this file should be outside your webroot. AuthType Basic 5 The original article can be found here: 7 P a g e
8 AuthName Blog require user youruser #making this username difficult to guess can help mitigate password brute force attacks. The.htpasswd file This file 6 should, as already mentioned, be placed somewhere out of your web directory, ideally one folder above it. To generate the password encrypted you can use: but many others are available as well, simply input your username and your plain password into this form and then write the outputted code into the.htpasswd file, your file should now look like this: Yourusr:$a983seJ/a25.Aa Now test it to see if everything is working; if that isn t the case, rewrite the encrypted password. MUSTHAVE Plugins Not every plugin is potentially a additional security risk. This list of plugins can greatly improve the security of your blog. WPIDS - Detect Intrusions BlogSecurity have ported PHPIDS (Intrusion Detection System) into WordPress. PHPIDS is able to detect various intrusion attempts. We use this facility to block dangerous attacks. Every intrusion is logged in the database, so you can keep track and take the necessary steps if needed. You re able to get an if the impact was bigger than a defined value (every intrusion has its own threat score). You can also block the attacker s IP for a given amount of days if the threat isn t scored lowly, however, in all cases WPIDS will attempt to sanitise bad input. You can get your copy from the official PHPIDS website. Note: In order to be able to use this plugin you need to run at least PHP or higher. A new version of WPIDS will be released shortly that includes BlogSec s recent addition, WP- Lockdown, so keep posted. 6 More information about that file can be found here: 8 P a g e
9 WordPress Plugin Tracker Are you updated? If you just installed your blog and all plugins from the developer website you should already be running the latest version. You should install the WordPress Plugin Tracker plugin to keep track if you re using the latest plugin versions. After you installed and activated the plugin, run it to see if your plugins are the current versions. You should see something like this: This is how the example page of the Plugin Release Tracker looks If some plugins aren t up to date, you ll be notified about it and by clicking on the title of the plugin to the left, you re easily forwarded to the plugin page where you can grab the update. So it s easy to keep your blog updated. 9 P a g e
10 WordPress Online Security Scanner BlogSecurity has written a WordPress security checking tool, to check your blog for common security weaknesses. It is excellent at enumerating plugins, checking for Cross-Site Scripting vulnerabilities and much more. WP-Scanner is a free online service and has tested more then 5000 blogs to date. Check out more information here. The End We reached the end of our whitepaper. We hope you enjoyed it, and that you ll have success implementing these vital security steps. Its always a pleasure to get feedback and your stories so please contact us. 10 P a g e
SO, ARE YOU READY? HERE WE GO:
 Date: 28/09/2012 Procedure: How To Move WordPress To A New Server Or Host Source: LINK Permalink: LINK Created by: HeelpBook Staff Document Version: 1.0 HOW TO MOVE WORDPRESS TO A NEW SERVER OR HOST It
Date: 28/09/2012 Procedure: How To Move WordPress To A New Server Or Host Source: LINK Permalink: LINK Created by: HeelpBook Staff Document Version: 1.0 HOW TO MOVE WORDPRESS TO A NEW SERVER OR HOST It
How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic
 How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic 2010 Marian Krajcovic You may NOT resell or giveaway this ebook! 1 If you have many WordPress blogs and especially
How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic 2010 Marian Krajcovic You may NOT resell or giveaway this ebook! 1 If you have many WordPress blogs and especially
Adding a Admin account to Wordpress database
 Copyright 2016 TBehr Services LLC Adding a Admin account to Wordpress database TBEHR Services, LLC (Software) Version 1..0 AUTHOR: TERRENCE BEHRENS COPYRIGHT 2014 TBEHR SERVICES LLC MODIFIED: 5/5/2016
Copyright 2016 TBehr Services LLC Adding a Admin account to Wordpress database TBEHR Services, LLC (Software) Version 1..0 AUTHOR: TERRENCE BEHRENS COPYRIGHT 2014 TBEHR SERVICES LLC MODIFIED: 5/5/2016
Using PHPMyAdmin with WordPress
 Using PHPMyAdmin with WordPress A basic run-down of some of the things you may want to do manually on your WordPress database. (Using PHPMyAdmin) Kenneth Hargis Managing Partner ken@orphicworkshop.com
Using PHPMyAdmin with WordPress A basic run-down of some of the things you may want to do manually on your WordPress database. (Using PHPMyAdmin) Kenneth Hargis Managing Partner ken@orphicworkshop.com
11 Most Common. WordPress Mistakes. And how to fix them
 11 Most Common WordPress Mistakes And how to fix them Introduction We all make mistakes from time to time but when it comes to WordPress, there are some mistakes that can have devastating consequences.
11 Most Common WordPress Mistakes And how to fix them Introduction We all make mistakes from time to time but when it comes to WordPress, there are some mistakes that can have devastating consequences.
Wordpress Security. GIMPA, November
 Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP.
 WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
Making Multisite Work for You BEN BYRNE CORNERSHOP CREATIVE
 1 2 Making Multisite Work for You BEN BYRNE CORNERSHOP CREATIVE 3 What is Multisite? 4 Multisite is Multiple sites using one installation Shared codebase Shared database but mostly separate tables Used
1 2 Making Multisite Work for You BEN BYRNE CORNERSHOP CREATIVE 3 What is Multisite? 4 Multisite is Multiple sites using one installation Shared codebase Shared database but mostly separate tables Used
WordPress Tutorial for Beginners with Step by Step PDF by Stratosphere Digital
 WordPress Tutorial for Beginners with Step by Step PDF by Stratosphere Digital This WordPress tutorial for beginners (find the PDF at the bottom of this post) will quickly introduce you to every core WordPress
WordPress Tutorial for Beginners with Step by Step PDF by Stratosphere Digital This WordPress tutorial for beginners (find the PDF at the bottom of this post) will quickly introduce you to every core WordPress
Architecture. Steven M. Bellovin October 31,
 Architecture Steven M. Bellovin October 31, 2016 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
Architecture Steven M. Bellovin October 31, 2016 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
For more info on Cloud9 see their documentation:
 Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Using.htaccess to Restrict OU Directory by Usernames and Passwords in an.htpasswd File
 Using.htaccess to Restrict OU Directory by Usernames and Passwords in an.htpasswd File (Last updated on 9/3/2015 by lucero@uark.edu) This method requires the management of three files,.htaccess,.htpasswd,
Using.htaccess to Restrict OU Directory by Usernames and Passwords in an.htpasswd File (Last updated on 9/3/2015 by lucero@uark.edu) This method requires the management of three files,.htaccess,.htpasswd,
WordPress Maintenance For Beginners
 WordPress Maintenance For Beginners Content Pages, posts, users, links, widgets, menus, comments, products, etc. Media Images, documents, videos, music, etc. Plugins Function, features, and facilities.
WordPress Maintenance For Beginners Content Pages, posts, users, links, widgets, menus, comments, products, etc. Media Images, documents, videos, music, etc. Plugins Function, features, and facilities.
oit
 This handout is for passwordprotecting content on people. umass.edu or courses.umass.edu Web sites. To protect content on www.umass.edu-level sites, see our HTPASSWD to Password- Protect Pages on Campus
This handout is for passwordprotecting content on people. umass.edu or courses.umass.edu Web sites. To protect content on www.umass.edu-level sites, see our HTPASSWD to Password- Protect Pages on Campus
Making Multisite Work for You
 1 cshp.co/wcsac-multisite Making Multisite Work for You BEN BYRNE CORNERSHOP CREATIVE 2 What is Multisite? 3 Multisite is Multiple sites using one installation Shared codebase & database Used by wordpress.com,
1 cshp.co/wcsac-multisite Making Multisite Work for You BEN BYRNE CORNERSHOP CREATIVE 2 What is Multisite? 3 Multisite is Multiple sites using one installation Shared codebase & database Used by wordpress.com,
oit Using HTPASSWD to Password Protect Pages on Campus Web Server Web sites UMass Offi ce of Information Technologies
 oit UMass Offi ce of Information Technologies This handout is for passwordprotecting content on www.umass. edu-level sites. To protect content on people.umass.edu or courses. umass.edu Web sites, see our
oit UMass Offi ce of Information Technologies This handout is for passwordprotecting content on www.umass. edu-level sites. To protect content on people.umass.edu or courses. umass.edu Web sites, see our
Customizing DAZ Studio
 Customizing DAZ Studio This tutorial covers from the beginning customization options such as setting tabs to the more advanced options such as setting hot keys and altering the menu layout. Introduction:
Customizing DAZ Studio This tutorial covers from the beginning customization options such as setting tabs to the more advanced options such as setting hot keys and altering the menu layout. Introduction:
Web Servers and Security
 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache has 49%; IIS has 36% (source: http://news.netcraft.com/archives/2008/09/30/
Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache has 49%; IIS has 36% (source: http://news.netcraft.com/archives/2008/09/30/
Web insecurity Security strategies General security Listing of server-side risks Language specific security. Web Security.
 Web Security Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming Web Security Slide 1/25 Outline Web insecurity Security strategies General security Listing of server-side risks Language
Web Security Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming Web Security Slide 1/25 Outline Web insecurity Security strategies General security Listing of server-side risks Language
John Coggeshall Copyright 2006, Zend Technologies Inc.
 PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
Client Care Plan. Critical WordPress website care and support for your peace of mind, ongoing results & growth. So much more than just maintenance.
 Find out more at: lovedadesign.co.uk Client Care Plan. Critical WordPress website care and support for your peace of mind, ongoing results & growth. So much more than just maintenance. WordPress Website
Find out more at: lovedadesign.co.uk Client Care Plan. Critical WordPress website care and support for your peace of mind, ongoing results & growth. So much more than just maintenance. WordPress Website
Troubleshooting Guide for Migrating WordPress Installations
 by Leigh Cotnoir, 2016 http://learn.leighcotnoir.com Troubleshooting Guide for Migrating WordPress Installations When you are trying to migrate a WordPress website from one server to another, you might
by Leigh Cotnoir, 2016 http://learn.leighcotnoir.com Troubleshooting Guide for Migrating WordPress Installations When you are trying to migrate a WordPress website from one server to another, you might
Oceanica Theme Documentation
 Oceanica Theme Documentation Updated on December 29, 2017 Installation Import sample data Import sample data from xml file. Import sample data from.sql file. Set up the front page Edit front page Site
Oceanica Theme Documentation Updated on December 29, 2017 Installation Import sample data Import sample data from xml file. Import sample data from.sql file. Set up the front page Edit front page Site
Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003
 Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003 A system or combination of systems that enforces a boundary between two or more networks - NCSA
Firewalls Network Security: Firewalls and Virtual Private Networks CS 239 Computer Software March 3, 2003 A system or combination of systems that enforces a boundary between two or more networks - NCSA
Quick Start Editors Guide. For Your. MyVFW WebSite
 Quick Start Editors Guide For Your MyVFW WebSite Welcome to your new MyVFW.org website. This guide is intended to provide a quick overview of some of the basic features of your new post website and is,
Quick Start Editors Guide For Your MyVFW WebSite Welcome to your new MyVFW.org website. This guide is intended to provide a quick overview of some of the basic features of your new post website and is,
WordPress Maintenance For Beginners
 WordPress Maintenance For Beginners Content Pages, posts, users, links, widgets, menus, comments, products, etc. Media Images, documents, videos, music, etc. Plugins Function, features, and facilities.
WordPress Maintenance For Beginners Content Pages, posts, users, links, widgets, menus, comments, products, etc. Media Images, documents, videos, music, etc. Plugins Function, features, and facilities.
MTAT Research Seminar in Cryptography The Security of Mozilla Firefox s Extensions
 MTAT.07.019 Research Seminar in Cryptography The Security of Mozilla Firefox s Extensions Kristjan Krips 1 Introduction Mozilla Firefox has 24.05% of the recorded usage share of web browsers as of October
MTAT.07.019 Research Seminar in Cryptography The Security of Mozilla Firefox s Extensions Kristjan Krips 1 Introduction Mozilla Firefox has 24.05% of the recorded usage share of web browsers as of October
epldt Web Builder Security March 2017
 epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
Navigate 1. Help & Support Help Support Third - party plugin Support Policy 2. Introduction FAQS 3. Plugin Quick View Plugin Contact Form 7
 Navigate 1. Help & Support 1.1. Help 1.2. Support 1.2.1. Third - party plugin 1.2.2. Support Policy 2. Introduction 2.1. FAQS 3. Plugin 3.1. Quick View Plugin 3.2. Contact Form 7 3.3. Visual Composer 3.4.
Navigate 1. Help & Support 1.1. Help 1.2. Support 1.2.1. Third - party plugin 1.2.2. Support Policy 2. Introduction 2.1. FAQS 3. Plugin 3.1. Quick View Plugin 3.2. Contact Form 7 3.3. Visual Composer 3.4.
Step by Step Guide Domain Security Pro
 Step by Step Guide Domain Security Pro by Mark Dulisse Copyright 2013 DomainSecurityPro.com Page 1 Copyright 2013 by DomainSecurityPro.com All rights reserved. No part of this publication may be reproduced,
Step by Step Guide Domain Security Pro by Mark Dulisse Copyright 2013 DomainSecurityPro.com Page 1 Copyright 2013 by DomainSecurityPro.com All rights reserved. No part of this publication may be reproduced,
How to Use WordPress
 How to Use WordPress Introduction... 1 When to Use WordPress... 1 WordPress vs. WordPress.com... 1 WordPress... 1 WordPress.com... 2 Getting Started... 2 WordPress.com... 2 WordPress software... 3 Logging
How to Use WordPress Introduction... 1 When to Use WordPress... 1 WordPress vs. WordPress.com... 1 WordPress... 1 WordPress.com... 2 Getting Started... 2 WordPress.com... 2 WordPress software... 3 Logging
0. Introduction On-demand. Manual Backups Full Backup Custom Backup Store Your Data Only Exclude Folders.
 Backup & Restore 0. Introduction..2 1. On-demand. Manual Backups..3 1.1 Full Backup...3 1.2 Custom Backup 5 1.2.1 Store Your Data Only...5 1.2.2 Exclude Folders.6 1.3 Restore Your Backup..7 2. On Schedule.
Backup & Restore 0. Introduction..2 1. On-demand. Manual Backups..3 1.1 Full Backup...3 1.2 Custom Backup 5 1.2.1 Store Your Data Only...5 1.2.2 Exclude Folders.6 1.3 Restore Your Backup..7 2. On Schedule.
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Are You Avoiding These Top 10 File Transfer Risks?
 Are You Avoiding These Top 10 File Transfer Risks? 1. 2. 3. 4. Today s Agenda Introduction 10 Common File Transfer Risks Brief GoAnywhere MFT Overview Question & Answer HelpSystems Corporate Overview.
Are You Avoiding These Top 10 File Transfer Risks? 1. 2. 3. 4. Today s Agenda Introduction 10 Common File Transfer Risks Brief GoAnywhere MFT Overview Question & Answer HelpSystems Corporate Overview.
Copyright 2012 BlogDesigns Web: Meer informatie?
 Copyright 2012 BlogDesigns Web: www.blogdesigns.nl E-mail: handleiding@.nl Meer informatie? info@blogdesigns.nl V3-2013 Introduction WordPress is a user-friendly content management system (CMS) that gives
Copyright 2012 BlogDesigns Web: www.blogdesigns.nl E-mail: handleiding@.nl Meer informatie? info@blogdesigns.nl V3-2013 Introduction WordPress is a user-friendly content management system (CMS) that gives
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma
 Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Architecture. Steven M. Bellovin October 27,
 Architecture Steven M. Bellovin October 27, 2015 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
Architecture Steven M. Bellovin October 27, 2015 1 Web Servers and Security The Web is the most visible part of the net Two web servers Apache (open source) and Microsoft s IIS dominate the market Apache
5. A small dialog window appears; enter a new password twice (this is different from Dori!) and hit Go.
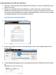 Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
Version USER GUIDE
 Magento Extension RSS feed Version 1.0.0 USER GUIDE Last update: Aug 15 th, 2013 DragonFroot.com RSS feed v1-0 Content 1. Introduction 2. Installation 3. Configuration 4. Troubleshooting 5. Contact us
Magento Extension RSS feed Version 1.0.0 USER GUIDE Last update: Aug 15 th, 2013 DragonFroot.com RSS feed v1-0 Content 1. Introduction 2. Installation 3. Configuration 4. Troubleshooting 5. Contact us
Last modification of document: by Tomasz Dobrzyński
 Thank you for purchasing Gonzales. If you have any questions that are beyond the scope of this help file, please feel free to contact me using following form. If you need my help with installation or plugin
Thank you for purchasing Gonzales. If you have any questions that are beyond the scope of this help file, please feel free to contact me using following form. If you need my help with installation or plugin
Linux Local Security about Passwords and Data NZPAPER.BLOGSPOT.COM. Nz Paper Linux and Web Application Security. Zeeshan Khan 4/15/2013
 1 Linux Local Security about Passwords and Data NZPAPER.BLOGSPOT.COM Nz Paper Linux and Web Application Security Zeeshan Khan 4/15/2013 2 Abstract: As Passwords and other Linux Data play an important role
1 Linux Local Security about Passwords and Data NZPAPER.BLOGSPOT.COM Nz Paper Linux and Web Application Security Zeeshan Khan 4/15/2013 2 Abstract: As Passwords and other Linux Data play an important role
Deploy and Configure Microsoft LAPS. Step by step guide and useful tips
 Deploy and Configure Microsoft LAPS Step by step guide and useful tips 2 Table of Contents Challenges today... 3 What is LAPS... 4 Emphasis and Tips... 5 How LAPS Work... 6 Components... 6 Prepare, Deploy
Deploy and Configure Microsoft LAPS Step by step guide and useful tips 2 Table of Contents Challenges today... 3 What is LAPS... 4 Emphasis and Tips... 5 How LAPS Work... 6 Components... 6 Prepare, Deploy
Security Aspects Control Rationale Best Practices Self-Assessment (Click all that applicable) 1. Security Policy and Security Management
 Seven Habits of Cyber Security for SMEs Security Aspects Control Rationale Best Practices Self-Assessment (Click all that applicable) 1. Security Policy and Security Management Security Policy is an important
Seven Habits of Cyber Security for SMEs Security Aspects Control Rationale Best Practices Self-Assessment (Click all that applicable) 1. Security Policy and Security Management Security Policy is an important
SOCE Wordpress User Guide
 SOCE Wordpress User Guide 1. Introduction Your website runs on a Content Management System (CMS) called Wordpress. This document outlines how to modify page content, news and photos on your website using
SOCE Wordpress User Guide 1. Introduction Your website runs on a Content Management System (CMS) called Wordpress. This document outlines how to modify page content, news and photos on your website using
System Structure. Steven M. Bellovin December 14,
 System Structure Steven M. Bellovin December 14, 2015 1 Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin December 14, 2015
System Structure Steven M. Bellovin December 14, 2015 1 Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin December 14, 2015
Application Authorization with SET ROLE. Aurynn Shaw, Command Prompt, Inc. PGCon 2010
 Application Authorization with SET ROLE Aurynn Shaw, Command Prompt, Inc. PGCon 2010 Hi Hi Aurynn Shaw DBA/Lead Dev/PM/etc @ Command Prompt * Today we re talking about AuthZ in PG * Benefits, drawbacks,
Application Authorization with SET ROLE Aurynn Shaw, Command Prompt, Inc. PGCon 2010 Hi Hi Aurynn Shaw DBA/Lead Dev/PM/etc @ Command Prompt * Today we re talking about AuthZ in PG * Benefits, drawbacks,
We aren t getting enough orders on our Web site, storms the CEO.
 In This Chapter Introducing how Ajax works Chapter 1 Ajax 101 Seeing Ajax at work in live searches, chat, shopping carts, and more We aren t getting enough orders on our Web site, storms the CEO. People
In This Chapter Introducing how Ajax works Chapter 1 Ajax 101 Seeing Ajax at work in live searches, chat, shopping carts, and more We aren t getting enough orders on our Web site, storms the CEO. People
DOWNLOAD PDF SQL SERVER 2012 STEP BY STEP
 Chapter 1 : Microsoft SQL Server Step by Step - PDF Free Download - Fox ebook Your hands-on, step-by-step guide to building applications with Microsoft SQL Server Teach yourself the programming fundamentals
Chapter 1 : Microsoft SQL Server Step by Step - PDF Free Download - Fox ebook Your hands-on, step-by-step guide to building applications with Microsoft SQL Server Teach yourself the programming fundamentals
Symlink attacks. Do not assume that symlinks are trustworthy: Example 1
 Symlink attacks Do not assume that symlinks are trustworthy: Example 1 Application A creates a file for writing in /tmp. It assumes that since the file name is unusual, or because it encodes A's name or
Symlink attacks Do not assume that symlinks are trustworthy: Example 1 Application A creates a file for writing in /tmp. It assumes that since the file name is unusual, or because it encodes A's name or
How To Change My Wordpress Database
 How To Change My Wordpress Database Password On Instagram Account Built by one of the world's largest Instagram browsers INK361, this comprehensive widget that can showcase your Instagram account in the
How To Change My Wordpress Database Password On Instagram Account Built by one of the world's largest Instagram browsers INK361, this comprehensive widget that can showcase your Instagram account in the
Web Application Security Evaluation
 Web Application Security Evaluation Jack Wilson Abertay University White Paper BSc Ethical Hacking 2016/2017 TABLE OF CONTENTS 1. Introduction..3 2. Vulnerabilities Discovered and Countermeasures...4 2.1
Web Application Security Evaluation Jack Wilson Abertay University White Paper BSc Ethical Hacking 2016/2017 TABLE OF CONTENTS 1. Introduction..3 2. Vulnerabilities Discovered and Countermeasures...4 2.1
Installing Dolphin on Your PC
 Installing Dolphin on Your PC Note: When installing Dolphin as a test platform on the PC there are a few things you can overlook. Thus, this installation guide won t help you with installing Dolphin on
Installing Dolphin on Your PC Note: When installing Dolphin as a test platform on the PC there are a few things you can overlook. Thus, this installation guide won t help you with installing Dolphin on
Lecture Overview. IN5290 Ethical Hacking. Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing
 Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Security issues. Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith
 Security issues Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith Criteria D3 D3 Recommend ways to improve web security when using web server scripting Clean browser input Don
Security issues Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith Criteria D3 D3 Recommend ways to improve web security when using web server scripting Clean browser input Don
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
If you re the administrator on any network,
 Let s do an inventory! If you re the administrator on any network, chances are you ve already faced the need to make an inventory. In fact, keeping a list of all the computers, monitors, software and other
Let s do an inventory! If you re the administrator on any network, chances are you ve already faced the need to make an inventory. In fact, keeping a list of all the computers, monitors, software and other
Introducing Thrive - The Ultimate In WordPress Blog Design & Growth
 Introducing Thrive - The Ultimate In WordPress Blog Design & Growth Module 1: Download 2 Okay, I know. The title of this download seems super selly. I have to apologize for that, but never before have
Introducing Thrive - The Ultimate In WordPress Blog Design & Growth Module 1: Download 2 Okay, I know. The title of this download seems super selly. I have to apologize for that, but never before have
Linking Reports to your Database in Crystal Reports 2008
 Linking Reports to your Database in Crystal Reports 2008 After downloading and saving a report on your PC, either (1) browse-to the report using Windows Explorer and double-click on the report file or
Linking Reports to your Database in Crystal Reports 2008 After downloading and saving a report on your PC, either (1) browse-to the report using Windows Explorer and double-click on the report file or
A (sample) computerized system for publishing the daily currency exchange rates
 A (sample) computerized system for publishing the daily currency exchange rates The Treasury Department has constructed a computerized system that publishes the daily exchange rates of the local currency
A (sample) computerized system for publishing the daily currency exchange rates The Treasury Department has constructed a computerized system that publishes the daily exchange rates of the local currency
java -jar Xmx2048mb /Applications/burpsuite_pro_v1.5.jar
 Training: An Introduction to Burp Suite Part One By Mike Sheward Burp suite provides a solid platform for launching a web application security assessment. In this guide we re going to introduce the features
Training: An Introduction to Burp Suite Part One By Mike Sheward Burp suite provides a solid platform for launching a web application security assessment. In this guide we re going to introduce the features
Holistic Database Security
 Holistic Database Security 1 Important Terms Exploit: Take advantage of a flaw or feature Attack Surface: Any node on the network that can be attacked. That can be the UI, People, anything that touches
Holistic Database Security 1 Important Terms Exploit: Take advantage of a flaw or feature Attack Surface: Any node on the network that can be attacked. That can be the UI, People, anything that touches
5 MANAGING USER ACCOUNTS AND GROUPS
 MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
Table of Contents. 1. Introduction 1. 1 Overview Business Context Glossary...3
 Table of Contents 1. Introduction 1. 1 Overview......2 1. 2 Business Context.. 2 1. 3 Glossary...3 2. General Description 2. 1 Product/System Functions..4 2. 2 User Characteristics and Objectives 4 2.
Table of Contents 1. Introduction 1. 1 Overview......2 1. 2 Business Context.. 2 1. 3 Glossary...3 2. General Description 2. 1 Product/System Functions..4 2. 2 User Characteristics and Objectives 4 2.
CS 356 Operating System Security. Fall 2013
 CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
Bitcoin for WooCommerce Documentation
 Bitcoin for WooCommerce Documentation Release 3.0.1 EliteCoderLab June 13, 2015 Contents 1 Table of Contents 3 2 Installation 5 2.1 Server Requirements........................................... 5 2.2
Bitcoin for WooCommerce Documentation Release 3.0.1 EliteCoderLab June 13, 2015 Contents 1 Table of Contents 3 2 Installation 5 2.1 Server Requirements........................................... 5 2.2
Backend IV: Authentication, Authorization and Sanitization. Tuesday, January 13, 15
 6.148 Backend IV: Authentication, Authorization and Sanitization The Internet is a scary place Security is a big deal! TODAY What is security? How will we try to break your site? Authentication,
6.148 Backend IV: Authentication, Authorization and Sanitization The Internet is a scary place Security is a big deal! TODAY What is security? How will we try to break your site? Authentication,
Joomla! Security: Avoid Getting Hacked
 Joomla! Security: Avoid Getting Hacked Northern Virginia Joomla Users Group April 21, 2016 Dorothy Firsching, Ursa Major Consulting, LLC dfirsching@ursamajorconsulting.com Agenda Joomla! News and Plans
Joomla! Security: Avoid Getting Hacked Northern Virginia Joomla Users Group April 21, 2016 Dorothy Firsching, Ursa Major Consulting, LLC dfirsching@ursamajorconsulting.com Agenda Joomla! News and Plans
Installing the PC-Kits SQL Database
 1 Installing the PC-Kits SQL Database The Network edition of VHI PC-Kits uses a SQL database. Microsoft SQL is a database engine that allows multiple users to connect to the same database. This document
1 Installing the PC-Kits SQL Database The Network edition of VHI PC-Kits uses a SQL database. Microsoft SQL is a database engine that allows multiple users to connect to the same database. This document
(System) Integrity attacks System Abuse, Malicious File upload, SQL Injection
 Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
AppWizard Installation/Upgrade Guide (v.4.00)
 AppWizard Installation/Upgrade Guide (v.4.00) Last Updated: 15 September 2010 1 Introduction This manual is intended for the installation or upgrade of AppWizard 5.00. Please ensure that all steps are
AppWizard Installation/Upgrade Guide (v.4.00) Last Updated: 15 September 2010 1 Introduction This manual is intended for the installation or upgrade of AppWizard 5.00. Please ensure that all steps are
Web Host. Choosing a. for Your WordPress Site. What is web hosting, and why do you need it?
 You ve registered a domain name, and you know you want to use WordPress to create your online presence. The next question is, where are you going to build your website? This report will help you choose
You ve registered a domain name, and you know you want to use WordPress to create your online presence. The next question is, where are you going to build your website? This report will help you choose
Passwords. Twitter UN: IDANRV Twitter PW: idanrv1. Thank You
 Passwords Twitter UN: IDANRV Twitter PW: idanrv1 Thank You USER'S MANUAL TABLE OF CONTENTS Page # 1.1 SYSTEM OVERVIEW... 4 1.2 DEFINITIONS & ACRONYMS... 4 1.3 REFERENCES... 4 2.0 INSTALLATION... 5 2.1
Passwords Twitter UN: IDANRV Twitter PW: idanrv1 Thank You USER'S MANUAL TABLE OF CONTENTS Page # 1.1 SYSTEM OVERVIEW... 4 1.2 DEFINITIONS & ACRONYMS... 4 1.3 REFERENCES... 4 2.0 INSTALLATION... 5 2.1
Designing a System. We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin April 10,
 Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin April 10, 2007 1 Some of Our Tools Encryption Authentication mechanisms Access
Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin April 10, 2007 1 Some of Our Tools Encryption Authentication mechanisms Access
It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to
 1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
Dammit Jim, I m a Mac Admin, not a Web Developer
 Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Welcome To Account Manager 2.0
 Account Manager 2.0 Manage Unlimited FileMaker Servers, Databases, Privileges, and Users Effortlessly! The ultimate tool for FileMaker Database Administrators. Welcome To Account Manager 2.0 What Is Account
Account Manager 2.0 Manage Unlimited FileMaker Servers, Databases, Privileges, and Users Effortlessly! The ultimate tool for FileMaker Database Administrators. Welcome To Account Manager 2.0 What Is Account
MANUAL FORCED MATRIX MLM PRO. v2.5
 MANUAL FORCED MATRIX MLM PRO v2.5 TABLE OF CONTENTS Section Page # Getting Started 3 Overview 3 Installation 3 WP Admin Settings 4 Dashboard 4 Create First User 4 Settings Overview 5 General Settings 7
MANUAL FORCED MATRIX MLM PRO v2.5 TABLE OF CONTENTS Section Page # Getting Started 3 Overview 3 Installation 3 WP Admin Settings 4 Dashboard 4 Create First User 4 Settings Overview 5 General Settings 7
OWASP TOP 10. By: Ilia
 OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
SECURE CODING ESSENTIALS
 SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
shortcut Tap into learning NOW! Visit for a complete list of Short Cuts. Your Short Cut to Knowledge
 shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
Solutions Business Manager Web Application Security Assessment
 White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Instructions 1 Elevation of Privilege Instructions
 Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3-6 players. Play starts with the 3 of Tampering. Play
Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3-6 players. Play starts with the 3 of Tampering. Play
Sucuri Webinar Transcription
 Sucuri Webinar Transcription Caleb Lane 1 Hi, thanks for the introduction, Val. Welcome everyone to the webinar. Before we get started, I want to just go over a few things and then the main topics we ll
Sucuri Webinar Transcription Caleb Lane 1 Hi, thanks for the introduction, Val. Welcome everyone to the webinar. Before we get started, I want to just go over a few things and then the main topics we ll
Instructions 1. Elevation of Privilege Instructions. Draw a diagram of the system you want to threat model before you deal the cards.
 Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3 6 players. Play starts with the 3 of Tampering. Play
Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3 6 players. Play starts with the 3 of Tampering. Play
Human vs Artificial intelligence Battle of Trust
 Human vs Artificial intelligence Battle of Trust Hemil Shah Co-CEO & Director Blueinfy Solutions Pvt Ltd About Hemil Shah hemil@blueinjfy.net Position -, Co-CEO & Director at BlueInfy Solutions, - Founder
Human vs Artificial intelligence Battle of Trust Hemil Shah Co-CEO & Director Blueinfy Solutions Pvt Ltd About Hemil Shah hemil@blueinjfy.net Position -, Co-CEO & Director at BlueInfy Solutions, - Founder
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Web Hosting. Important features to consider
 Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
NWIC EDITOR GUIDE August 2016
 NWIC EDITOR GUIDE August 2016 THEME NAME: CLEVERCOURSE logging in: GO TO nwic.edu/wp-login.php blogs.nwic.edu/wp-login.php foundation.nwic.edu/wp-login.php Please note that your Username is your full nwic.edu
NWIC EDITOR GUIDE August 2016 THEME NAME: CLEVERCOURSE logging in: GO TO nwic.edu/wp-login.php blogs.nwic.edu/wp-login.php foundation.nwic.edu/wp-login.php Please note that your Username is your full nwic.edu
This chapter introduces you to the multisite feature that s built into the
 Chapter 1: An Introduction to Multiple Sites In This Chapter Discovering where multiple sites began Exploring what you can do with multiple sites Configuring your web server This chapter introduces you
Chapter 1: An Introduction to Multiple Sites In This Chapter Discovering where multiple sites began Exploring what you can do with multiple sites Configuring your web server This chapter introduces you
Ruby on Rails Secure Coding Recommendations
 Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
A Security Admin's Survival Guide to the GDPR.
 A Security Admin's Survival Guide to the GDPR www.manageengine.com/log-management Table of Contents Scope of this guide... 2 The GDPR requirements that need your attention... 2 Prep steps for GDPR compliance...
A Security Admin's Survival Guide to the GDPR www.manageengine.com/log-management Table of Contents Scope of this guide... 2 The GDPR requirements that need your attention... 2 Prep steps for GDPR compliance...
TOP DEVELOPERS MINDSET. All About the 5 Things You Don t Know.
 MINDSET TOP DEVELOPERS All About the 5 Things You Don t Know 1 INTRODUCTION Coding and programming are becoming more and more popular as technology advances and computer-based devices become more widespread.
MINDSET TOP DEVELOPERS All About the 5 Things You Don t Know 1 INTRODUCTION Coding and programming are becoming more and more popular as technology advances and computer-based devices become more widespread.
OpenDrive Wordpress Plugin Guide
 OpenDrive Wordpress Plugin Guide Version 2.0.1 OpenDrive Online storage, backup and cloud content management Contents 1. Drive 3 1.1 Drive... 3 1.2 Working with files... 4 1.2.1 Work with a particular
OpenDrive Wordpress Plugin Guide Version 2.0.1 OpenDrive Online storage, backup and cloud content management Contents 1. Drive 3 1.1 Drive... 3 1.2 Working with files... 4 1.2.1 Work with a particular
Mobile Login extension User Manual
 extension User Manual Magento 2 allows your customers convenience and security of login through mobile number and OTP. Table of Content 1. Extension Installation Guide 2. Configuration 3. API Settings
extension User Manual Magento 2 allows your customers convenience and security of login through mobile number and OTP. Table of Content 1. Extension Installation Guide 2. Configuration 3. API Settings
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
WHILE YOU RE GETTING ORGANIZED
 CAMPTECH.CA WHILE YOU RE GETTING ORGANIZED 1. Go to camptech.ca/wordpress and download the PDF of slides. 2. If you have to leave early, please remember to fill out the (100% anonymous) feedback form on
CAMPTECH.CA WHILE YOU RE GETTING ORGANIZED 1. Go to camptech.ca/wordpress and download the PDF of slides. 2. If you have to leave early, please remember to fill out the (100% anonymous) feedback form on
Managing User Accounts
 Contents User Accounts 2 Passwords 3 Common User Account Settings 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. The basic operation of a file transfer server boils
Contents User Accounts 2 Passwords 3 Common User Account Settings 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. The basic operation of a file transfer server boils
Participation Status Report STUDIO ELEMENTS I KATE SOHNG
 2015 Participation Status Report STUDIO ELEMENTS I KATE SOHNG Table of Contents I. Wataru... 1 A. JQuery discussion... 1 B. Other JavaScript libraries... 1 C. CakePHP framework... 2 D. Webpage feedback...
2015 Participation Status Report STUDIO ELEMENTS I KATE SOHNG Table of Contents I. Wataru... 1 A. JQuery discussion... 1 B. Other JavaScript libraries... 1 C. CakePHP framework... 2 D. Webpage feedback...
WordPress Security Implementation Guideline
 WordPress Security Implementation Guideline Good practices and epic fails of WordPress implementations About Me Information Security Consultant Application Security Secure SDLC Dan VASILE http://www.pentest.ro
WordPress Security Implementation Guideline Good practices and epic fails of WordPress implementations About Me Information Security Consultant Application Security Secure SDLC Dan VASILE http://www.pentest.ro
