Joomla! Security: Avoid Getting Hacked
|
|
|
- Annice Shields
- 5 years ago
- Views:
Transcription
1 Joomla! Security: Avoid Getting Hacked Northern Virginia Joomla Users Group April 21, 2016 Dorothy Firsching, Ursa Major Consulting, LLC
2 Agenda Joomla! News and Plans Joomla! Updates Joomla! Certification Our JUG How to Avoid Getting Hacked 4/21/
3 Joomla! News Joomla! 3.5 bug regarding s Joomla! will fail catastrophically when trying to send an , including from Akeeba If the From or From Name in Global Configuration are Empty Invalid addresses in user accounts 4/21/
4 Joomla! 3.6+ plans As of 4/16/2016: Features currently being worked on: Custom Fields (Allon Moritz): progressing well, can use testing New media manager: needs testing New router (Hannes Papenberg): ready for testing Service layer (Chris Davenport): probably later Web services (Chris Davenport): probably in 3.7 Mobile app (Matias Aguirre): not sure of status Admin template (Cliff Pfeifer): scheduled for 3.7 Tentative aim: Late June 2016 for at least some features (depends when ready) See Google Joomla! CMS Development group for latest Alpha release soon 4/21/
5 Joomla! Certification Joomla! Certification Establish a standard Ensure competence and develop a qualified workforce Provide a documented measurement of knowledge Important role in choosing a Joomla! service provider First certification: Joomla! 3.x Administrator The badge received is valid for the lifetime of that major version that it covers Computer based, 60 questions - 90 minutes, multiple choice, in US $75 How to Prepare: Where: At a JLP, Joomla!Day, or JUG Our JUG Application to administer certification test is pending our certification as a JUG Need to submit photo of testing location and names of proctors / supervisors for testing 4/21/
6 Our JUG Status New website at Register or update your listing in the members directory! JUG was dropped by Joomla! But now re-approved. Joomla! Community Portal There are now no JUGs in Virginia Wanted us to change our name to include a city, e.g., Fairfax or Kings Park, and not a state. Answered: No. We are officially organized in Virginia with that name and have IRS tax exempt 501(c)(6) status! Wanted us to create a new logo that does not include the clover Joomla! logo It is OK now, under fair use. 4/21/
7 Upcoming NoVA JUG events May 19, 2016: Steve Burge, Best Joomla! Tips and Techniques June 16 open July 21 open What would you like to present or hear about? 4/21/
8 Other Upcoming Joomla Events New York: May 15, 2016 JoomlaCamp 2016 Joomlausersnj.com Minneapolis: July 17-18, 2016 Web and Marketing Conference 2 days, at Mall of America Denver: October 1, 2016 Chicago: September 17, 2016 Joomladaychicago.com 4/21/
9 How to Avoid Getting Hacked 1. Update Joomla! to Current Version Outdated Joomla! , code allow anybody to upload php scripts to your site via media manager. Remote code execution vulnerability: all versions up to (December 15, 2015) 2. Upgrade Extensions Upgrade extensions all the time Use Tools like managemyjoomla.com or watchful.li 4/21/
10 How to Avoid Getting Hacked 3. Upgrade Templates Templates, modules, frameworks E.g., RocketTheme SQL injection in sliders affected several hundred templates 4. Avoid Weak passwords Brute force attacks break weak passwords, e.g., pass123 Change username from admin or admin2 Allow access only from certain IP addresses Password protect the administrator folder Use secret URL parameters (Akeeba Admin Tools) 4/21/
11 How to Avoid Getting Hacked 5. Avoid Outdated or Poorly Configured Server Software Php before , running as CGI: remote execution exploit Can see the passwords, etc. in configuration.php Apache Symlinks Bug: Lets Hackers access other accounts on shared servers add SymLinksIfOwnerMatch to.htaccess 4/21/
12 How to Avoid Getting Hacked 6. Check for Bad File Permissions 755 for folders 644 for files Use Akeeba Admin Tools to Fix 7. Have account isolation! Watch out for test accounts and update or remove them, too1 8. Keep Malware off Your PC 4/21/
13 How to Avoid Getting Hacked 9. Configure Akeeba Admin Tools to Harden Joomla! Restrict editing user accounts Creating a custom.htaccess to stop various login and hack attempts you upon successful/unsuccessful administator logins Etc. 4/21/
14 How to Avoid Getting Hacked 10.Scan for File Changes PHP file scanner in Akeeba Admintools 11. Scan for Hacks Managemyjoomla.com Check for good practices you forgot Scan for potential hacks Update or remove bad files Manage extensions Schedule backups 4/21/
15 Try a Content Delivery Network (CDN) m/the-complete-guide-to-usingcloudflare-with-joomla.html A CDN can handle IP blocking also (Note: added by Thomas at the meeting) 4/21/
16 Set up your site to use SSL Note that Google gives ranking preference to sites using SSL free-extensions/cloudflare-for-joomla Or investigate getting your own certificate (Note: added by Thomas at the meeting) 4/21/
17 Read Joomla! Security News cklist tynews tyvulnerableextensions Sucuri: 4/21/
18 Example of Template Framework Update: Shape5 Template Framework is Vertex Current Version may be hard to notice on existing templates 4/21/
19 Shape5 Vertex Upgrade Log in and download the upgrade patch. n/itemid,96/task,cat_view/gid,307/ Extract the files Upload the extracted files and folders to the template s root folder. Go to Extensions/Template Manager and then open your templates configuration link. Save any changes that you wish and the upgrade is complete! Don t overlay Yourtemplate/index.php adjust positions Don t overlay css/custom.css adjust css Much easier to forget to do, if it does not appear in the control panel! Why isn t this using the Joomla! upgrade process? 4/21/
20 Upgrade to Widgetkit Current Version? Potential Pitfall Note that the best upgrade for Joomla! 3.x is called widgetkit_j25.zip! Widgetkit_j25.zip does run on Joomla! 3.x despite its name. Widgetkit_2.6.5_j3.zip is Widgetkit 2. You can t run both. 4/21/
21 Discussion 4/21/
New World ERP-eSuite
 New World ERP-eSuite 2018.1 INSTALLATION GUIDE April 9, 2018 Review important information for installing this release: SSL is required for esuite Services and Website servers. 2018 Tyler Technologies.
New World ERP-eSuite 2018.1 INSTALLATION GUIDE April 9, 2018 Review important information for installing this release: SSL is required for esuite Services and Website servers. 2018 Tyler Technologies.
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP.
 WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
Attacks Against Websites 3 The OWASP Top 10. Tom Chothia Computer Security, Lecture 14
 Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
FB Image Contest. Users Manual
 FB Image Contest Users Manual Table of contents Description.. 3 Step by step installation... 5 The administration interface.. 10 Creating a new contest... 13 Creating a Facebook Application.. 19 Adding
FB Image Contest Users Manual Table of contents Description.. 3 Step by step installation... 5 The administration interface.. 10 Creating a new contest... 13 Creating a Facebook Application.. 19 Adding
Dammit Jim, I m a Mac Admin, not a Web Developer
 Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Wordpress Security. GIMPA, November
 Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
MexBS Google Invisible Recaptcha v1.0.0 User Guide
 MexBS Google Invisible Recaptcha v1.0.0 User Guide Welcome to the MexBs family, and thank you for purchasing the "Google Invisible Recaptcha v1.0.0" Magento extension! In this document we will guide you
MexBS Google Invisible Recaptcha v1.0.0 User Guide Welcome to the MexBs family, and thank you for purchasing the "Google Invisible Recaptcha v1.0.0" Magento extension! In this document we will guide you
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
USER MANUAL. SuiteCRM / SugarCRM Customer Portal for Joomla TABLE OF CONTENTS. Version: 1.1
 USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Installation...2 Joomla Manual Plug-in installation...2 Plug-in Configuration...4 Joomla Configuration Settings...4 CRM Fields
USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Installation...2 Joomla Manual Plug-in installation...2 Plug-in Configuration...4 Joomla Configuration Settings...4 CRM Fields
How to create a secure WordPress install v1.1
 Table of Contents: Table of Contents:... 1 Introduction... 2 Installing WordPress... 2 Accessing your WordPress tables... 2 Changing your WordPress Table Prefix... 3 Before Installation... 3 Manually Change...
Table of Contents: Table of Contents:... 1 Introduction... 2 Installing WordPress... 2 Accessing your WordPress tables... 2 Changing your WordPress Table Prefix... 3 Before Installation... 3 Manually Change...
USER MANUAL. SuiteCRM Customer Portal for Joomla TABLE OF CONTENTS. Version: 2.0
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 SuiteCRM Plug-in Installation... 2 Joomla Manual Plug-in installation... 3 Plug-in
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 SuiteCRM Plug-in Installation... 2 Joomla Manual Plug-in installation... 3 Plug-in
INITIAL SIGN UP PLEASE READ THROUGH COMPLETELY TO SEE IF THIS ANSWERS ANY QUESTIONS
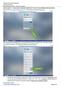 INITIAL SIGN UP PLEASE READ THROUGH COMPLETELY TO SEE IF THIS ANSWERS ANY QUESTIONS Use the URL http://lynx.portofvirginia.com/. You should see the following screen: At the bottom of the dialogue box,
INITIAL SIGN UP PLEASE READ THROUGH COMPLETELY TO SEE IF THIS ANSWERS ANY QUESTIONS Use the URL http://lynx.portofvirginia.com/. You should see the following screen: At the bottom of the dialogue box,
Access Type. For assistance
 INITIAL SIGN UP PLEASE READ THROUGH COMPLETELY TO SEE IF THIS ANSWERS ANY QUESTIONS Use the URL http://lynx.portofvirginia.com/. You should see the following screen: At the bottom of the dialogue box,
INITIAL SIGN UP PLEASE READ THROUGH COMPLETELY TO SEE IF THIS ANSWERS ANY QUESTIONS Use the URL http://lynx.portofvirginia.com/. You should see the following screen: At the bottom of the dialogue box,
1 Introduction. Table of Contents. Manual for
 Manual for www.lornasixsmith.com Table of Contents 1Introduction...1 2Log in...2 3Users...2 4What is the difference between pages and posts?...2 5Adding Images to the Media Library...2 6Adding Text to
Manual for www.lornasixsmith.com Table of Contents 1Introduction...1 2Log in...2 3Users...2 4What is the difference between pages and posts?...2 5Adding Images to the Media Library...2 6Adding Text to
Combating Common Web App Authentication Threats
 Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Portal User Guide. Best practice tips and shortcuts Icon Legend Informational notes about functions. Important warnings about a function
 Portal User Guide Tips Best practice tips and shortcuts Icon Legend Notes Warning Informational notes about functions Important warnings about a function Your Portal https://www.clientaxcess.com Your Portal
Portal User Guide Tips Best practice tips and shortcuts Icon Legend Notes Warning Informational notes about functions Important warnings about a function Your Portal https://www.clientaxcess.com Your Portal
epldt Web Builder Security March 2017
 epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
owncloud Android App Manual
 owncloud Android App Manual Release 2.0.0 The owncloud developers December 14, 2017 CONTENTS 1 Using the owncloud Android App 1 1.1 Getting the owncloud Android App...................................
owncloud Android App Manual Release 2.0.0 The owncloud developers December 14, 2017 CONTENTS 1 Using the owncloud Android App 1 1.1 Getting the owncloud Android App...................................
USER MANUAL. SuitePort - SuiteCRM Customer Portal for Joomla TABLE OF CONTENTS. Version: 1.1.0
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 SuiteCRM Plug-in Installation... 2 Joomla Manual Plug-in installation... 3 Plug-in
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 SuiteCRM Plug-in Installation... 2 Joomla Manual Plug-in installation... 3 Plug-in
AT&T Business Messaging Account Management
 Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Overview NOTE: Listing Overview. User Profile. Language Selection. Asset(s) View. Asset(s) Details. Editing Mode
 Overview Listing Overview User Profile Language Selection Asset(s) View Asset(s) Details Editing Mode NOTE: Some functions may not be available to all users depending on permissions granted. Some of the
Overview Listing Overview User Profile Language Selection Asset(s) View Asset(s) Details Editing Mode NOTE: Some functions may not be available to all users depending on permissions granted. Some of the
Client Portal FAQ's. Client Portal FAQ's. Why is the Portal more secure?
 Client Portal FAQ's Client Portal FAQ's Why is the Portal more secure? The Bishop Fleming Portal is powered by Virtual Cabinet who have a team of experts to ensure that the latest technologies and best
Client Portal FAQ's Client Portal FAQ's Why is the Portal more secure? The Bishop Fleming Portal is powered by Virtual Cabinet who have a team of experts to ensure that the latest technologies and best
shwedirectory v4.0 Php Web & Business Directory Script Top 12 Features of shwedirectory Premium Edition
 shwedirectory v4.0 Php Web & Business Directory Script Top 12 Features of shwedirectory Premium Edition 1. Admin Subdomain 2. Content Security Policy (CSP) Header 3. Subdomain for each city and country
shwedirectory v4.0 Php Web & Business Directory Script Top 12 Features of shwedirectory Premium Edition 1. Admin Subdomain 2. Content Security Policy (CSP) Header 3. Subdomain for each city and country
WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN
 WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN Document Control Document Properties Title Author Document Type Filename File location
WEB HOSTING SERVICE OPERATING PROCEDURES AND PROCESSES UNIVERSITY COMPUTER CENTER UNIVERSITY OF THE PHILIPPINES DILIMAN Document Control Document Properties Title Author Document Type Filename File location
Create quick link URLs for a candidate merge Turn off external ID links in candidate profiles... 4
 Credential Manager 1603 March 2016 In this issue Pearson Credential Management is proud to announce Generate quick link URLs for a candidate merge in the upcoming release of Credential Manager 1603, scheduled
Credential Manager 1603 March 2016 In this issue Pearson Credential Management is proud to announce Generate quick link URLs for a candidate merge in the upcoming release of Credential Manager 1603, scheduled
How-to Guide: Tenable Nessus for Microsoft Azure. Last Updated: April 03, 2018
 How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
VSP16. Venafi Security Professional 16 Course 04 April 2016
 VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
Guidelines for work on the Genebank KB site
 Guidelines for work on the Genebank KB site (By Geert Claessens. For extra information email to geert.jef.claessens@gmail.com) These guidelines are written for users of the Crop Genebank Knowledge Base
Guidelines for work on the Genebank KB site (By Geert Claessens. For extra information email to geert.jef.claessens@gmail.com) These guidelines are written for users of the Crop Genebank Knowledge Base
Joomla 2.5 User Change Password Frontend
 Joomla 2.5 User Change Password Frontend Add User Frontend makes it possible to add users to Joomla from the frontend. It will even Autogenerate username and password - Add users to Attention: Description
Joomla 2.5 User Change Password Frontend Add User Frontend makes it possible to add users to Joomla from the frontend. It will even Autogenerate username and password - Add users to Attention: Description
SharpSchool Chapter 7 USER MANUAL EXTERNAL LINK PAGE For more information, please visit:
 SHARPSCHOOL USER MANUAL CHAPTER 7 EXTERNAL LINK PAGE For more information, please visit: www.customernet.sharpschool.com www.sharpschool.com 0 TABLE OF CONTENTS 1. 2. 3. 4. INTRODUCTION... 1 KEY INFORMATION...
SHARPSCHOOL USER MANUAL CHAPTER 7 EXTERNAL LINK PAGE For more information, please visit: www.customernet.sharpschool.com www.sharpschool.com 0 TABLE OF CONTENTS 1. 2. 3. 4. INTRODUCTION... 1 KEY INFORMATION...
About the Tutorial. Audience. Prerequisites. Copyright & Disclaimer. Joomla
 About the Tutorial Joomla is an open source Content Management System (CMS), which is used to build websites and online applications. It is free and extendable which is separated into frontend templates
About the Tutorial Joomla is an open source Content Management System (CMS), which is used to build websites and online applications. It is free and extendable which is separated into frontend templates
Get Qualified User Manual
 MALTA ENTERPRISE Get Qualified User Manual Student Guide Contents 1. Logon... 3 2. Registration... 3 3. Profile... 3 Ongoing Applications... 3 Editing your profile... 4 Profile... 4 Account... 4 Password...
MALTA ENTERPRISE Get Qualified User Manual Student Guide Contents 1. Logon... 3 2. Registration... 3 3. Profile... 3 Ongoing Applications... 3 Editing your profile... 4 Profile... 4 Account... 4 Password...
1 TABLE OF CONTENT. User Manual v0.4
 User Manual v0.4 1 TABLE OF CONTENT 2 Install your addressbook... 2 2.1 Quick installation... 2 2.2 Manual installation... 2 2.3 Setup user and passwords... 2 2.3.1 Setup User with passwords... 2 2.3.2
User Manual v0.4 1 TABLE OF CONTENT 2 Install your addressbook... 2 2.1 Quick installation... 2 2.2 Manual installation... 2 2.3 Setup user and passwords... 2 2.3.1 Setup User with passwords... 2 2.3.2
Solutions Business Manager Web Application Security Assessment
 White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
Chapter 1: Let's Get Started
 Chapter 1: Let's Get Started Common Terminology Hosting Selection and Unique Needs What Is a Host? Choosing a Host Questions to Ask a Prospective Host Facilities Things to Ask Your Host about Facility
Chapter 1: Let's Get Started Common Terminology Hosting Selection and Unique Needs What Is a Host? Choosing a Host Questions to Ask a Prospective Host Facilities Things to Ask Your Host about Facility
Joomla 3.X Global Settings Part III Server Settings
 Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Casper Suite Release Notes. Version 8.7
 Casper Suite Release Notes Version 8.7 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
Casper Suite Release Notes Version 8.7 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
XIA Configuration Server
 XIA Configuration Server XIA Configuration Server v6 Cloud Services Quick Start Guide Tuesday, 20 May 2014 1 P a g e X I A C o n f i g u r a t i o n C l o u d S e r v i c e s Contents Overview... 3 Creating
XIA Configuration Server XIA Configuration Server v6 Cloud Services Quick Start Guide Tuesday, 20 May 2014 1 P a g e X I A C o n f i g u r a t i o n C l o u d S e r v i c e s Contents Overview... 3 Creating
Domain System Threat Landscape. Pablo Rodriguez Nic.pr Janelle McAlister - MarkMonitor
 Domain System Threat Landscape Pablo Rodriguez Nic.pr Janelle McAlister - MarkMonitor Agenda n History n Nic.PR Case Study q Registrar Perspective q Registry Perspective n Future solutions History n Over
Domain System Threat Landscape Pablo Rodriguez Nic.pr Janelle McAlister - MarkMonitor Agenda n History n Nic.PR Case Study q Registrar Perspective q Registry Perspective n Future solutions History n Over
Deltek Touch Expense for Ajera. Touch 1.0 Technical Installation Guide
 Deltek Touch Expense for Ajera Touch 1.0 Technical Installation Guide June 01, 2018 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical
Deltek Touch Expense for Ajera Touch 1.0 Technical Installation Guide June 01, 2018 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical
COMMON CRITERIA CERTIFICATION REPORT
 COMMON CRITERIA CERTIFICATION REPORT WorkCentre 7525/7530/7535/7545/7556 with FIPS 140-2 Compliance over SNMPv3 25 July 2016 v1.0 383-4-371 Government of Canada. This document is the property of the Government
COMMON CRITERIA CERTIFICATION REPORT WorkCentre 7525/7530/7535/7545/7556 with FIPS 140-2 Compliance over SNMPv3 25 July 2016 v1.0 383-4-371 Government of Canada. This document is the property of the Government
About the Tutorial. Audience. Prerequisites. Copyright & Disclaimer. WordPress
 About the Tutorial WordPress is an open source Content Management System (CMS), which allows the users to build dynamic websites and blog. WordPress is the most popular blogging system on the web and allows
About the Tutorial WordPress is an open source Content Management System (CMS), which allows the users to build dynamic websites and blog. WordPress is the most popular blogging system on the web and allows
Best Practices (PDshop Security Tips)
 Best Practices (PDshop Security Tips) For use with all versions of PDshop Revised: 12/29/17 PDshop.com / Copyright 2002-2018 All Rights Reserved. 1 Table of Contents Table of Contents... 2 Best Practices...
Best Practices (PDshop Security Tips) For use with all versions of PDshop Revised: 12/29/17 PDshop.com / Copyright 2002-2018 All Rights Reserved. 1 Table of Contents Table of Contents... 2 Best Practices...
Version 3.3 System Administrator Guide
 Version 3.3 System Administrator Guide This document provides information Ensemble Video System Administrators can use to design and implement an appropriate Ensemble Video organizational framework, manage
Version 3.3 System Administrator Guide This document provides information Ensemble Video System Administrators can use to design and implement an appropriate Ensemble Video organizational framework, manage
Why bother? Causes of data breaches OWASP. Top ten attacks. Now what? Do it yourself Questions?
 Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Create and Manage Partner Portals
 Create and Manage Partner Portals Salesforce, Summer 18 @salesforcedocs Last updated: June 20, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Create and Manage Partner Portals Salesforce, Summer 18 @salesforcedocs Last updated: June 20, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
COMMON CRITERIA CERTIFICATION REPORT
 COMMON CRITERIA CERTIFICATION REPORT WorkCentre 7845/7845i/7855/7855i 2016 Xerox ConnectKey Technology 12 August 2016 v1.0 383-4-382 Government of Canada. This document is the property of the Government
COMMON CRITERIA CERTIFICATION REPORT WorkCentre 7845/7845i/7855/7855i 2016 Xerox ConnectKey Technology 12 August 2016 v1.0 383-4-382 Government of Canada. This document is the property of the Government
Securing CS-MARS C H A P T E R
 C H A P T E R 4 Securing CS-MARS A Security Information Management (SIM) system can contain a tremendous amount of sensitive information. This is because it receives event logs from security systems throughout
C H A P T E R 4 Securing CS-MARS A Security Information Management (SIM) system can contain a tremendous amount of sensitive information. This is because it receives event logs from security systems throughout
Unified Security Platform. Security Center 5.4 Hardening Guide Version: 1.0. Innovative Solutions
 Unified Security Platform Security Center 5.4 Hardening Guide Version: 1.0 Innovative Solutions 2016 Genetec Inc. All rights reserved. Genetec Inc. distributes this document with software that includes
Unified Security Platform Security Center 5.4 Hardening Guide Version: 1.0 Innovative Solutions 2016 Genetec Inc. All rights reserved. Genetec Inc. distributes this document with software that includes
Grapevine web hosting user manual. 12 August 2005
 Grapevine web hosting user manual 12 August 2005 Grapevine web hosting user manual 2 Contents Contents... 2 Introduction... 4 System features... 4 How it looks... 5 Main navigation... 5 Reports... 6 Web
Grapevine web hosting user manual 12 August 2005 Grapevine web hosting user manual 2 Contents Contents... 2 Introduction... 4 System features... 4 How it looks... 5 Main navigation... 5 Reports... 6 Web
Securing ArcGIS for Server. David Cordes, Raj Padmanabhan
 Securing ArcGIS for Server David Cordes, Raj Padmanabhan Agenda Security in the context of ArcGIS for Server User and Role Considerations Identity Stores Authentication Securing web services Protecting
Securing ArcGIS for Server David Cordes, Raj Padmanabhan Agenda Security in the context of ArcGIS for Server User and Role Considerations Identity Stores Authentication Securing web services Protecting
Php-Brute-Force-Attack-Detector
 Defeating scanners Php-Brute-Force-Attack-Detector By Aung Khant (d0ubl3_h3lix) Version: Beta Date: Saturday, June 28, 2008 URL: http://yehg.net/lab/#tools Overview Nowadays, in web application mapping,
Defeating scanners Php-Brute-Force-Attack-Detector By Aung Khant (d0ubl3_h3lix) Version: Beta Date: Saturday, June 28, 2008 URL: http://yehg.net/lab/#tools Overview Nowadays, in web application mapping,
Version 3.1 System Administrator Guide
 Version 3.1 System Administrator Guide This document provides information Ensemble Video System Administrators can use to design and implement an appropriate Ensemble Video organizational framework, manage
Version 3.1 System Administrator Guide This document provides information Ensemble Video System Administrators can use to design and implement an appropriate Ensemble Video organizational framework, manage
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Web Application Penetration Testing
 Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
USER MANUAL. SugarPort - SugarCRM Customer Portal for Drupal TABLE OF CONTENTS. Version: 1.0
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Installation... 2 Drupal Manual Plug-in installation... 2 Plug-in Configuration... 4 Drupal Configuration Settings... 4
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Installation... 2 Drupal Manual Plug-in installation... 2 Plug-in Configuration... 4 Drupal Configuration Settings... 4
Password Reset Utility. Configuration
 Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
How-to Guide: Tenable.io for Microsoft Azure. Last Updated: November 16, 2018
 How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
Barracuda Web Application Firewall Foundation - WAF01. Lab Guide
 Barracuda Web Application Firewall Foundation - WAF01 Lab Guide Official training material for Barracuda certified trainings and Autorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Barracuda Web Application Firewall Foundation - WAF01 Lab Guide Official training material for Barracuda certified trainings and Autorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
About The Presentation 11/3/2017. Hacker HiJinx-Human Ways to Steal Data. Who We Are? Ethical Hackers & Security Consultants
 November 3, 2017 Hacker HiJinx-Human Ways to Steal Data Who We Are? Ethical Hackers & Security Consultants Respond To Incidents & Breaches Perform Digital Forensic Investigations Data Mine Internet Intelligence
November 3, 2017 Hacker HiJinx-Human Ways to Steal Data Who We Are? Ethical Hackers & Security Consultants Respond To Incidents & Breaches Perform Digital Forensic Investigations Data Mine Internet Intelligence
TFS Self-Service Password Reset Portal Getting Started Guide
 TFS Self-Service Password Reset Portal Getting Started Guide Texas A&M Forest Service (TFS) Information Resources Department (IR) A quick guide to getting started and using the TFS self-service password
TFS Self-Service Password Reset Portal Getting Started Guide Texas A&M Forest Service (TFS) Information Resources Department (IR) A quick guide to getting started and using the TFS self-service password
ShareSync Get Started Guide for Mac
 ShareSync Get Started Guide for Mac ShareSync Overview ShareSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against data loss from ransomware, accidental
ShareSync Get Started Guide for Mac ShareSync Overview ShareSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against data loss from ransomware, accidental
Casper Suite Release Notes. Version 8.7
 Casper Suite Release Notes Version 8.7 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
Casper Suite Release Notes Version 8.7 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
Web server reconnaissance
 Web server reconnaissance Reconnaissance and fingerprinting Finding information about a target web server/web site May be illegal to perform reconnaissance on a web server and web site without prior approval/permission.
Web server reconnaissance Reconnaissance and fingerprinting Finding information about a target web server/web site May be illegal to perform reconnaissance on a web server and web site without prior approval/permission.
Applying for Funding in Fluxx. Quick Start Instructions
 Applying for Funding in Fluxx Quick Start Instructions GETTING STARTED The Hogg Foundation Fluxx Grant Portal is optimized for use with Chrome or Safari browsers and using another browser may cause technical
Applying for Funding in Fluxx Quick Start Instructions GETTING STARTED The Hogg Foundation Fluxx Grant Portal is optimized for use with Chrome or Safari browsers and using another browser may cause technical
WordPress Security Plugins vs. WAF Services. A Comparative Test of WAF Accuracy in Security Solutions
 WordPress Security Plugins vs. WAF Services A Comparative Test of WAF Accuracy in Security Solutions Contents Abstract... 3 Introduction... 3 WAF Evaluation Criteria... 4 Results... 5 Pattern Analysis...
WordPress Security Plugins vs. WAF Services A Comparative Test of WAF Accuracy in Security Solutions Contents Abstract... 3 Introduction... 3 WAF Evaluation Criteria... 4 Results... 5 Pattern Analysis...
Why was an extra step of choosing a Security Image added to the sign-in process?
 General Information Why was an extra step of choosing a Security Image added to the sign-in process? Criminals can create websites that look very similar to legitimate business websites. We want to take
General Information Why was an extra step of choosing a Security Image added to the sign-in process? Criminals can create websites that look very similar to legitimate business websites. We want to take
CM Live Deal Documentation
 CM Live Deal Documentation Release 1.5.0-beta CMExtension April 12, 2015 Contents 1 Overview 3 1.1 Technical Requirements......................................... 3 1.2 Features..................................................
CM Live Deal Documentation Release 1.5.0-beta CMExtension April 12, 2015 Contents 1 Overview 3 1.1 Technical Requirements......................................... 3 1.2 Features..................................................
PHPBasket 4 Administrator Documentation
 PHPBasket 4 Please ensure you have the latest version of this document from http://www.phpbasket.com Contents CONTENTS 2 REQUIREMENTS 3 INSTALLATION 4 PREPARATION 4 UPLOAD 4 INSTALLATION 4 ADMINISTRATOR
PHPBasket 4 Please ensure you have the latest version of this document from http://www.phpbasket.com Contents CONTENTS 2 REQUIREMENTS 3 INSTALLATION 4 PREPARATION 4 UPLOAD 4 INSTALLATION 4 ADMINISTRATOR
CCH Client Axcess Portal User Guide
 CCH Client Axcess Portal User Guide Tips Best practice tips and shortcuts Icon Legend Notes Warning Informational notes about functions Important warnings about a function CCH Client Axcess https://www.clientaxcess.com
CCH Client Axcess Portal User Guide Tips Best practice tips and shortcuts Icon Legend Notes Warning Informational notes about functions Important warnings about a function CCH Client Axcess https://www.clientaxcess.com
Site Data Protection (SDP) Program Update
 Advanced Payments October 9, 2006 Site Data Protection (SDP) Program Update Agenda Security Landscape PCI Security Standards Council SDP Program October 9, 2006 SDP Program Update 2 Security Landscape
Advanced Payments October 9, 2006 Site Data Protection (SDP) Program Update Agenda Security Landscape PCI Security Standards Council SDP Program October 9, 2006 SDP Program Update 2 Security Landscape
1. NVR Connection Diagram Wizard Setup Access System Using Mobile Device Access System Using PC Client Software 5
 1 1. NVR Connection Diagram 2 2. Wizard Setup 3 3. Access System Using Mobile Device 4 4. Access System Using PC Client Software 5 5. Access System Using Internet Explorer 8 6. Recording Setup 9 Motion
1 1. NVR Connection Diagram 2 2. Wizard Setup 3 3. Access System Using Mobile Device 4 4. Access System Using PC Client Software 5 5. Access System Using Internet Explorer 8 6. Recording Setup 9 Motion
5 Using the App 6 Using the App - Lead Details 7 Using the App - Qualifers 8 Using the App - Notes, photos and voice
 User Guide Exhibitor Guide to the JET Engage Scanner App Contents 1 Getting Setup 2 Qualifiers - get the data you want 3 Qualifiers - the different types 4 Downloading the App 5 Using the App 6 Using the
User Guide Exhibitor Guide to the JET Engage Scanner App Contents 1 Getting Setup 2 Qualifiers - get the data you want 3 Qualifiers - the different types 4 Downloading the App 5 Using the App 6 Using the
SECURE CODING ESSENTIALS
 SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
OWASP Broken Web Application Project. When Bad Web Apps are Good
 OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
Tutorial: Lessons From A Real Mainframe Break-In Over the Internet
 Tutorial: Lessons From A Real Mainframe Break-In Over the Internet Stu Henderson 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 STU@STUHENDERSON.COM What You ll Hear Today Brief comments on why
Tutorial: Lessons From A Real Mainframe Break-In Over the Internet Stu Henderson 5702 Newington Road Bethesda, MD 20816 (301) 229-7187 STU@STUHENDERSON.COM What You ll Hear Today Brief comments on why
11 Most Common. WordPress Mistakes. And how to fix them
 11 Most Common WordPress Mistakes And how to fix them Introduction We all make mistakes from time to time but when it comes to WordPress, there are some mistakes that can have devastating consequences.
11 Most Common WordPress Mistakes And how to fix them Introduction We all make mistakes from time to time but when it comes to WordPress, there are some mistakes that can have devastating consequences.
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Palatine Youth Baseball/Softball Commissioner Web site Guide
 Key Activities and Tasks February Commissioners receive logins and instructions from a Webmaster or a Board Member (if you have not received yours by mid February, please contact pyb_webmaster@pyb.com)
Key Activities and Tasks February Commissioners receive logins and instructions from a Webmaster or a Board Member (if you have not received yours by mid February, please contact pyb_webmaster@pyb.com)
CCH Client Axcess Portal User Guide
 CCH Client Axcess Portal User Guide Last Updated: October 2017 Client Portal Access or paste the below link into your web browser https://www.clientaxcess.com/#/login Please call our office at 212.245.5900
CCH Client Axcess Portal User Guide Last Updated: October 2017 Client Portal Access or paste the below link into your web browser https://www.clientaxcess.com/#/login Please call our office at 212.245.5900
DreamFactory Security Guide
 DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
Lecture Overview. IN5290 Ethical Hacking. Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing
 Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Locate your Advanced Tools and Applications
 MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
Barracuda Web Application Firewall Advanced Security Features - WAF02
 Barracuda Web Application Firewall Advanced Security Features - WAF02 Lab Guide Official training material for Barracuda certified trainings and Autorized Training Centers. Edition 2018 Revision 1.1 campus.barracuda.com
Barracuda Web Application Firewall Advanced Security Features - WAF02 Lab Guide Official training material for Barracuda certified trainings and Autorized Training Centers. Edition 2018 Revision 1.1 campus.barracuda.com
akkadian Global Directory 3.0 System Administration Guide
 akkadian Global Directory 3.0 System Administration Guide Updated July 19 th, 2016 Copyright and Trademarks: I. Copyright: This website and its content is copyright 2014 Akkadian Labs. All rights reserved.
akkadian Global Directory 3.0 System Administration Guide Updated July 19 th, 2016 Copyright and Trademarks: I. Copyright: This website and its content is copyright 2014 Akkadian Labs. All rights reserved.
Admin Login Log. User Guide. Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9. Official Extension Page: Admin Login Log. User Guide: Admin Login Log Page 1
 Admin Login Log User Guide Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9 Official Extension Page: Admin Login Log User Guide: Admin Login Log Page 1 Table of contents: 1. Introduction.3 2.Extension Configuration..5
Admin Login Log User Guide Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9 Official Extension Page: Admin Login Log User Guide: Admin Login Log Page 1 Table of contents: 1. Introduction.3 2.Extension Configuration..5
akkadian Provisioning Manager Express
 akkadian Provisioning Manager Express Version 4.11.04 Release Notes September 14 th, 2017 Copyright and Trademarks: I. Copyright: This website and its content is copyright 2017 Akkadian Labs, LLC. All
akkadian Provisioning Manager Express Version 4.11.04 Release Notes September 14 th, 2017 Copyright and Trademarks: I. Copyright: This website and its content is copyright 2017 Akkadian Labs, LLC. All
BMC FootPrints 12 Integration with Remote Support
 BMC FootPrints 12 Integration with Remote Support 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
BMC FootPrints 12 Integration with Remote Support 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
CM Social Post Documentation
 CM Social Post Documentation Release 1.0.1 CMExtension March 15, 2016 Contents 1 Overview 3 2 Install & update 5 3 Facebook application 7 4 Facebook personal timeline plugin 13 5 Facebook page timeline
CM Social Post Documentation Release 1.0.1 CMExtension March 15, 2016 Contents 1 Overview 3 2 Install & update 5 3 Facebook application 7 4 Facebook personal timeline plugin 13 5 Facebook page timeline
Sophos UTM Web Application Firewall For: Microsoft Exchange Services
 How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
EMS ROOM SIGN APP Configuration Guide
 EMS ROOM SIGN APP Configuration Guide V44.1 Last Updated: November 6, 2018 EMS Software emssoftware.com/help 800.440.3994 2018 EMS Software, LLC. All Rights Reserved. Table of Contents CHAPTER 1: EMS Room
EMS ROOM SIGN APP Configuration Guide V44.1 Last Updated: November 6, 2018 EMS Software emssoftware.com/help 800.440.3994 2018 EMS Software, LLC. All Rights Reserved. Table of Contents CHAPTER 1: EMS Room
From the User Profile section of your employer account, select User Profile and enter your new password.
 Signing Into The Employer User Account On the ApplyToEducation Homepage (www.applytoeducation.com) sign in using your assigned username and password. If you forgot your username and/or password, click
Signing Into The Employer User Account On the ApplyToEducation Homepage (www.applytoeducation.com) sign in using your assigned username and password. If you forgot your username and/or password, click
Customer Compliance Portal. User Guide V2.0
 Customer Compliance Portal User Guide V2.0 0 Copyright 2016 Merchant Preservation Services, LLC. All rights reserved. CampusGuard, the Merchant Preservation Services logo, and the CampusGuard logo are
Customer Compliance Portal User Guide V2.0 0 Copyright 2016 Merchant Preservation Services, LLC. All rights reserved. CampusGuard, the Merchant Preservation Services logo, and the CampusGuard logo are
ACT Test Accessibility and Accommodations System (TAA) User Guide
 ACT Test Accessibility and Accommodations System (TAA) User Guide www.act.org ACT Test Accessibility and Accommodations System (TAA) User Guide Table of Contents Overview... 2 Introduction to the Test
ACT Test Accessibility and Accommodations System (TAA) User Guide www.act.org ACT Test Accessibility and Accommodations System (TAA) User Guide Table of Contents Overview... 2 Introduction to the Test
inforouter V8.0 Implementation Guide Active Innovations, Inc. A Document Management Company
 inforouter V8.0 Implementation Guide www.inforouter.com inforouter V8.0 implementation Guide This guide will take you through the step-by-step installation procedures required for a successful inforouter
inforouter V8.0 Implementation Guide www.inforouter.com inforouter V8.0 implementation Guide This guide will take you through the step-by-step installation procedures required for a successful inforouter
COVERED CALIFORNIA ENROLLMENT ASSISTANCE PROGRAM
 This document outlines all features and functions available to Entity Business Contacts in the Certification Portal. It details the functions that you as an Entity User have including the account registration
This document outlines all features and functions available to Entity Business Contacts in the Certification Portal. It details the functions that you as an Entity User have including the account registration
I. CHW Profile.. Page 1 II. Employer Profile Page 12 III. Training Partner/Instructor Profile.. Page 27
 Table of Contents I. CHW Profile.. Page 1 II. Employer Profile Page 12 III. Training Partner/Instructor Profile.. Page 27 I. CHW Profile MiCHWA s CHW Registry serves as a statewide database of all Community
Table of Contents I. CHW Profile.. Page 1 II. Employer Profile Page 12 III. Training Partner/Instructor Profile.. Page 27 I. CHW Profile MiCHWA s CHW Registry serves as a statewide database of all Community
Manually Using Cpanel
 How To Install Plugin Joomla 2.5 Template Manually Using Cpanel From here you can install your Templates, Plugins, Modules, Components and Simply select the template folder on your PC and upload it to
How To Install Plugin Joomla 2.5 Template Manually Using Cpanel From here you can install your Templates, Plugins, Modules, Components and Simply select the template folder on your PC and upload it to
0. Introduction On-demand. Manual Backups Full Backup Custom Backup Store Your Data Only Exclude Folders.
 Backup & Restore 0. Introduction..2 1. On-demand. Manual Backups..3 1.1 Full Backup...3 1.2 Custom Backup 5 1.2.1 Store Your Data Only...5 1.2.2 Exclude Folders.6 1.3 Restore Your Backup..7 2. On Schedule.
Backup & Restore 0. Introduction..2 1. On-demand. Manual Backups..3 1.1 Full Backup...3 1.2 Custom Backup 5 1.2.1 Store Your Data Only...5 1.2.2 Exclude Folders.6 1.3 Restore Your Backup..7 2. On Schedule.
