LTRNMS-3002 Network Compliance and Network and Application Monitoring with Prime Infrastructure 3.0
|
|
|
- Felicity Owens
- 6 years ago
- Views:
Transcription
1 LTRNMS-3002 Network Compliance and Network and Application Monitoring with Prime Infrastructure 3.0 Getting Started with the lab... 2 Lab Topology... 2 Connection to the lab... 3 Create your environment... 3 Populating device Inventory... 4 Using a VCenter as discovery Source... 6 Creating Device group... 9 Endpoint Subnet association Prepare a new Overview dashboard Part 1 : Compliance Exercise 1: Enabling Compliance Exercise 2: EOX/PSIRT Report: Exercise 3: Using predefined Compliance Policies Exercise 4: Creation of a simple user defined policy Exercise 5: Creation of a user defined policy with configuration block and simple regex Exercise 6: Creation of a user defined policy using command output scope Exercise 7: Creation of a user defined policy testing multiple instances of a command. 47 Part 2 : Device Monitoring Exercise 1: Out of the box Devices monitoring Exercise 2: Customizing device monitoring Exercise 3: Monitoring UCS servers Part 3: Application Monitoring Exercise 1: Using NAM as a datasource Exercise 2: AVC Readiness Assessment on router Exercise 3: AVC profiles Exercise 4: Interface configuration Deploy a QoS profile Deploy an AVC profile Exercise 5: Device Data Sources Exercise 6: QoS and AVC monitoring on interfaces Exercise 7: Monitoring application with Service Assurance and Application Performance Dashboard Exercise 7: Customize your Dashboard... 88
2 Getting started with the lab Lab Topology The lab infrastructure deployment is shown below. 2 student groups see the same POD devices. However students in East group will modify only the East devices (SW-PODx-E, RTR-PODx-E) and Students in West group will modify only the West devices (SW-PODx-W, RTR-PODx-W. Some devices (readonly) are shared. Each student group has its own Prime Infrastructure 3.0 and its own NAM 6.2. Below are the addresses of important elements of the pods POD East Device type Name IP address Credentials Switch SW-PODx-E x.1 Router RTR-PODx-E x.3 Prime Infrastructure PI-PODx-E x root/public123
3 POD West Device type Name IP address Credentials Switch SW-PODx-W x.2 Router SW-PODx-W x.4 Prime Infrastructure PI-PODx-W x root/public123 Shared Device type Name IP address Credentials Fabric Interconnect vnam NAM-PODx x admin/cisco Connection to the lab You must use Cisco AnyconnectVPN client. Launch it and use primelab-eu.cisco.com as server Username: pi-lab Password: CLBerlin Create your environment Launch your Prime Infrastructure server:
4 Connect using Username: root Password: Public123 Select Dashboard/Network Summary/Overview Populating device Inventory There are 3 ways to populate the inventory: adding a single device doing a bulk import configuring an automatic device discovery In this section you will do a bulk import
5 Go to Inventory/Device Management/Network Devices Select Bulk Import Select the file called podx.csv where x is your pod number (East and West will use the same file). Click Import. You can check the status of the job in Administration/Dashboards/ Job Dashboard After a couple of minutes, due to synchronization, you should see your devices managed in Inventory/Device Management/Network Devices
6 Using a vcenter as discovery source From Inventory/Device Management/Compute Devices, Select Cisco UCS Server and click on the Fabric Interconnect Click Schematic and expand as much as you can. You should be able to see the Chassis and the Blades
7 To have more information on the ESX DataCenter environment, you will add now the ESX vcenter. This will give you the visibility on the datacenters, clusters, hosts and VMs. Select Inventory/Compute Devices Select Discovery Sources Add device Add the vcenter:
8 IP: Port: 443 Username: cl16 Password: LTRNMS3002 After a few seconds, the discovery source becomes synchronized You can see the DataCenters, cluster, hosts and VMs. Explore.
9 To monitor resources on servers and VMs, select Datacenter and click Start Monitoring. (Note: it is possible to be more specific, and to monitor only specific hosts or specific VMs.) Creating Device group You will create 2 device groups (location groups) called East and West, respectively for East devices and for West Devices. You will use them later. Select Inventory/Group Management/Network Device Groups
10 Click +, to add a group Create a location group called East, using the location attribute and the condition contains East Do the same for West location group Endpoint association In your network, most of the endpoints from East use IP addresses *.* and most of the endpoints from West use IP addresses *.*
11 For monitoring purpose, it s important to associate these endpoints subnets to the appropriate locations. Select Services/Application Visibility & Control/Endpoint Association (Note for the remaining of the guide we will use AV&C for Application Visibility and Control) Select + Associate the *.* subnets to East Save Associate the *.* subnets to West Prepare a new Overview dashboard You will create below, an empty dashboard that you will use later in the lab Select Dashboard/Overview/General On upper right corner, click settings, then Add New Dashboards.
12 Give a name: CL16-PODx-East (or West). Click on the Dashboard Tab. You have an Empty Overview Dashboard Select the configure icon in upper right corner, and click Set Current Page As Home Now each time you will click on, you will jump to this dashboard Part 1: Compliance Exercise 1: Enabling Compliance
13 Objective: Learn how to enable the compliance feature By default Compliance is disabled, but it should have been previously enabled on your system. In the exercise you will just verify that it s the case, (and enable it if needed). Verify that you have the Compliance entries, under Configuration/Compliance If not, select Administration/Settings/System Settings/General/Server Select Compliance Service / Enable. Click Save and do a login/logout Exercise 2: EOX/PSIRT Report: Objective: Know how to activate EOX and PSIRT analysis Before visualizing a PSIRT of EOX report, you must first activate it. Select Reports/PSIRT and EOX
14 As you can see, there is no data available Click Schedule Job You can click also View Job Details to see the status of the Job Don t wait it takes time. You will see the result later Do Exercise 3 and come back here after. If you select Hardware EOX, you should see 2 devices with EOX announcements
15 Click on to see the EOL announcement. (Internet Access is needed) Exercise 3: Auditing using predefined Compliance Policies Objective: In this exercise you will use an existing compliance policy to verify the compliance of the passwords with security rules. The policy will test the encryption, the encryption level and the password length. You will learn: - How to create a Compliance Profile using Predefined Compliance Policies - How to create an audit job to execute this Compliance Profile - How to visualize the Audit Report generated by the execution of the previous job Select Configuration/Compliance/Profiles
16 Select + to add a new profile Give a name to this Profile Click + Add, to Add Compliance Policies In Audit and Management folder, select User Passwords
17 Keep only the first 5 rules (it will be enough to have violations!!) Click Save You have created the profile. Click the execute icon (see below)
18 Select the 2 switches Execute the job now, without recurrence From Configuration/Compliance/Jobs, you can see the job in Running state.
19 Click the refresh button after 1 minute to see the result: It should report a failure Click the Failure link to have details Below you see 5 rules, 6 violations (not necessarily the same number of violation everywhere), click Next You can see the details of each violation
20 Click previous and select Export as HTML Visualize the report Exercise 4: Creation of a simple user defined policy Objective: In this exercise, you will create a simple policy to verify that the system clock has been configured with both timezone and summer-timezone. You will verify that timestamps have been also properly configured on syslog and debug messages. The compliance will test the existence of the commands: o o o o clock timezone <timezone> clock summer-time <summer-timezone> recurring service timestamps debug datetime localtime show-timezone service timestamps log datetime localtime show-timezone <timezone> and <summer-timezone> will be passed as parameters (Rule Inputs).
21 You will learn: - How to create a policy - How to add rules in a policy - How to add rule inputs to rules - How to define condition and actions in a rule Select Configuration/ Compliance /Policies Click + to add a policy, give a name Timezone, and click Create Click New to add a new rule Give a Name then click Next
22 Select IOS and IOS-XE then click Next Click New, to create the first parameter (Rule Input) Provide: - the name of the parameter: timezone - click generate to generate the Identifier of the parameter (you will use the parameter by its Identifier ) - Select the Scope: Execution. This means that the parameter is for auditing, the other possible scope is fix, when the parameter is only used to fix the CLI - Select: Input Required - Give a Default value: CET, stands for Central Europe Time
23 Create a second rule input called Summer-timezone Remark: when you generate a parameter are converted to _, _ is also added to the beginning of the parameter. Default value is CEST for Central Europe Summer Time You have now two parameters, click Next
24 You will add now the condition and actions The condition will check if the configuration contains the string: o clock timezone <_timezone> Where _timezone is the identifier of the rule input Define the scope: Configuration Define the Condition Match Criteria
25 Define now the actions you want to take in case of match/no match If the condition matches, Continue, means test the next condition If condition doesn t match, Raise a Violation and Continue (to the next condition) Customize the severity and the violation message.
26 Click ok: the condition is created. Click new to add the second condition to test the summer-timezone. Condition: (See below the input rule syntax <_summer_time>)
27 Actions: Matches: continue Does not Match: Raise a Violation and Continue Click OK to save and add a new condition to verify the debug timestamp configuration With the actions - Matches: Continue - Does not Match : Raise a violation and Continue
28 Click OK to save the condition/actions. Click New to add the last condition to verify the syslog timestamp configuration Condition: Contains the string : service timestamps log datetime localtime showtimezone Action - matches : do not raise a violation ( no other rule to test) - Does not match: Raise a Violation
29 Click ok to save the condition You have 4 conditions/actions in the rule. Click Create to save the Rule The rule is created, as well as the policy Now you will create a Profile (as you did in previous exercise) to use this policy.
30 Select Configuration/Compliance/Profile, + and give a name Click Add, to add a policy and check your policy in the user defined policies folder Keep the default value for the Rule Inputs: CET for the timezone and CEST for the summer-timezone Execute the profile
31 Select the switches Run the job immediately In Configuration/Compliance/Jobs, wait for the job to complete See the result Exercise 5: Creation of a user defined policy with configuration blocks and simple regex Objective: In this exercise, you will create a policy, which will check that all switch ports, which are explicitly configured in trunk mode, are also configured with a list of allowed VLANs.
32 You will learn: - how to parse a configuration per blocks, as you need to test for each interface. - how to use regex (very basic here) and how to capture a matching group The rule will contain 3 conditions Condition/Action 1: Find Interface block Scope: Configuration Parse as blocks: Yes. Define block start : ^interface.*, ^=> start with,.=> any character * => any number of times Condition: match the regex: interface (.*) => the parenthesis will allow to capture the interface name. The id will be <1.1>, 1: Condition 1, 1: first captured parameter Match Action: Continue Doesn t match Action: Do not Raise a violation Condition/Action 2: Is it a trunk? Scope: Previously matched block. We want to stay in the block interface Condition: match the string: switchport mode trunk Match Action: Continue Doesn t match Action: Do not Raise a violation Condition/Action 3: are allowed vlan configured? Scope: Previously matched block. We want to stay in the block interface Condition: match the string: switchport trunk allowed vlan Match Action: Do not raise a violation Doesn t match Action: Raise a violation: message misconfigured trunk on <1.1>. <1.1> refers to the interface name captured on condition1! Select Configuration/ Compliance /Policies
33 Click + to add a policy, give a name trunk, and click Create Click New to add a new rule Give a Name then click Next Select IOS and IOS-XE then click Next
34 Skip the rule input In condition and actions, click +New to add the first condition Condition/Action 1: Find Interface block Scope: Configuration Parse as blocks: Yes. Define block start: ^interface.*, ^=> starts with,.=> any character * => any number of times
35 Condition: match the regex: interface (.*) => the parenthesis will allow to capture the interface name. The id will be <1.1>, 1: Condition 1, 1: first captured parameter Match Action: Continue Doesn t match action: Do not Raise a violation Click OK and add a second condition Condition/Action 2: Is it a trunk? Scope: Previously matched block. We want to stay in the block interface Condition: match the string: switchport mode trunk Match Action: Continue
36 Doesn t match Action: Do not Raise a violation Click OK and add the last condition Condition/Action 3: are allowed vlan configured? Scope: Previously matched block. We want to stay in the block interface Condition: match the string: switchport trunk allowed vlan Match Action: Do not raise a violation Doesn t match Action: Raise a violation: message misconfigured trunk on <1.1>. <1.1> refers to the interface name captured by condition1!
37 Click Create Now you will create again a Profile Select Configuration/Compliance/Profile, + and give a name Click Add, to add a policy and check your policy in the user defined policies folder
38 Execute the profile Select the switches and run the job immediately In Configuration/Compliance/Jobs, wait for the job to complete
39 See the result You can check in the configuration archive Exercise 6: Creation of a user defined policy using command output scope Objective: In this exercise, you will create a policy, which will check that your switches are configured either in VTP client or in VTP server mode in a VTP domain that you passed as parameter (Rule Input) Unfortunately, it s not possible to test the configuration, as the VTP information is not always visible in the configuration see below: In VTP transparent mode, VTP information is visible in the configuration
40 However, in VTP client or VTP server mode, the VTP information is not in the configuration, but is visible through a command show vtp status This is the same behaviour with VTP server mode. You need to test the output of a show vtp status The rule will contain 2 conditions Condition/Action 1: Check the vtp domain Scope: show command: show vtp status Condition: Match the expression VTP Domain Name\s*:\s<_vtp_domain>
41 Match Action: Continue Doesn t match Action: Raise a Violation Condition/Action 2: check the vtp mode Scope: show command: show vtp status Condition: Matches the expression VTP Operating\s*:\s(Server Client) Match Action: Do not Raise a violation Doesn t match Action: Raise a violation Select Configuration/ Compliance /Policies Click + to add a policy, give a name VTP, and click Create Click New to add a new rule Give a Name then click Next
42 Select IOS and IOS-XE then Next Add the VTP domain as rule input. Put your pod name as default value, for example POD1 if you are either POD1W or POD1E.
43 In condition and actions, click +New to add the first condition Condition/Action 1: Check the vtp domain Scope: show command: show vtp status Condition: Match the expression VTP Domain Name\s*:\s<_vtp_domain>
44 Match Action: Continue Doesn t match Action: Raise a Violation Condition/Action 2: check the VTP mode Scope: show command: show vtp status Condition: Matches the expression: VTP Operating Mode\s*:\s(Server Client)
45 Match Action: Do not Raise a Violation Doesn t match Action: Raise a Violation Click Save Create now the profile Select Configuration/Compliance/Profile, + and give a name
46 Select Add, to add a policy and check your policy in the user defined policies folder The Rule Input vtp domain should be your POD Execute the profile Select the switches And run the job immediately In Configuration/Compliance/Jobs, wait for the job to complete
47 Visualize the result Exercise 7: Creation of a user defined policy testing multiple instances of a command Objective: In IOS, some commands can have multiple instances. For example, you can have multiple snmp-server community, multiple logging destinations, multiple ntp server. It s easy to check that a specific instance of a command exists. For example: snmp-server community pilab-ro RO must exist. But how can you test that another instance with a different community name does not exist? In this exercise, you will learn a method to solve this issue.
48 Imagine that the rule is to have 2 readonly communities (passed as parameters), and one rw community (passed as parameter). How can you write the policy? The rule has 3 inputs for the communities <_com_ro1>, <_com_ro2>, <_com_rw>. The rule has 5 conditions/actions: Condition/Action 1: Check the first read-only community Scope: Configuration Condition: contains the string snmp-server community <_com_ro1> RO Match Action: Continue Doesn t match Action: Raise a Violation and Continue Condition/Action 2: Check the second readonly community Scope: Configuration Condition: contains the string snmp-server community <_com_ro2> RO Match Action: Continue Doesn t match Action: Raise a Violation and Continue Condition/Action 3: Check the readwrite community Scope: Configuration Condition: contains the string snmp-server community <_com_rw> RW Match Action : Continue Doesn t match Action : Raise a violation and continue If we stop here, and have no violation, we are sure that the mandatory communities exist but we don t know if an unwanted community exist as well. One possible trick, is to consider now, each snmp-server community xxx RO as a configuration block of 1 line! Condition/Action 4: Check if unwanted RO community exists Scope: Configuration Parse as blocks: Yes. Define block start: ^snmp-server community \S* RO - Condition: match the expression: snmp-server community (?:<_com_ro1> <_com_ro2>) RO.* - Where (?:<_com_ro1> <_com_ro2>) means either <_com_ro1> or <_com_ro2> but without capturing as parameter (.?: means non capturing group). - RO.* => because we accept to have an access-list! Match Action: Continue Doesn t match Action: Raise a Violation and Continue
49 Condition/Action 5: Check if unwanted RW community exists Scope: Configuration Parse as blocks: Yes. Define block start : ^snmp-server community \S* RW Condition: match the expression: snmp-server community <_com_rw> RW.* Match Action: No violation Doesn t match Action: Raise a violation Select Configuration/ Compliance /Policies Click + to add a policy, give a name SNMP, and click Create Click New to add a new rule Give a Name then click Next
50 Select IOS and IOS-XE then Next Add the 3 rule inputs, for the snmp communities (2 RO, 1 RW). As default values for RO community, use public and snmpro and use private for the RW community.
51
52 In condition and actions, click +New to add the first condition Condition/Action 1: Check the first readonly community Scope: Configuration Condition: contains the string snmp-server community <_com_ro1> RO
53 Match Action: Continue Doesn t match Action: Raise a Violation and Continue Condition/Action 2: Check the second readonly community Scope: Configuration Condition: contains the string snmp-server community <_com_ro2> RO Match Action: Continue Doesn t match Action: Raise a Violation and Continue
54 Condition/Action 3: Check the readwrite community Scope: Configuration Condition: contains the string snmp-server community <_com_rw> RW Match Action: Continue Doesn t match Action: Raise a Violation and Continue Condition/Action 4: Check if unwanted RO community exists Scope: Configuration Parse as blocks: Yes. Define block start : ^snmp-server community \S* RO Condition: match the expression: snmp-server community (?:<_com_ro1> <_com_ro2>) RO.*
55 Match Action: Continue Doesn t match Action: Raise a Violation and Continue Condition/Action 5: Check if unwanted RW community exists Scope: Configuration Parse as blocks: Yes. Define block start: ^snmp-server community \S* RW Condition: match the expression: snmp-server community <_com_rw> RW.*
56 Match Action: Does Not Raise a Violation Doesn t match Action : Raise a Violation
57 Click save/create to create the policy Create now the profile Select Configuration/Compliance/Profile, + and give a name Click Add, to add a policy and check your policy in the user defined policies folder Keep the rule inputs values as below Execute the profile Select the switches
58 and run the job immediately In Configuration/Compliance/Jobs, wait for the job to complete Visualize the result You can confirm with the configuration archive. Do you know how to do it? (There is a trick) Here are POD1W, snmp communities
59 Here are POD1 E snmp communities Part 2: Device Monitoring Exercise 1: Out of the box Devices monitoring Prime Infrastructure uses monitoring policies to monitor wired devices (Health and interfaces). Select Monitor/Monitoring Tools/Monitoring Policies You can see the monitoring policies. Some are active by default, some have associated thresholds. For the policies Device Health and Interface Health, click on the links under Activation history and Details What do you notice?
60 Click now on Auto monitoring Examine which parameters are polled for devices and Interfaces (Link and Trunk Ports)
61 Wireless devices are not monitored using monitoring policies but monitoring jobs. You can see the jobs used for wireless from: Administration/Dashboards/Job Dashboard Examine now the Overview dashboards for devices Dashboards/Overview/Network Devices
62 (You can change the layout) Click the icon on one of your devices to launch the device 360
63 Click a device IP address to launch the Performance Dashboard for the device Examine now the Overview Dashboard for Interfaces Select Dashboard/Overview/Network Interfaces
64 Drill Down to one interface to launch the Performance Dashboard/Interface As you see the interface is polled, but the traffic is very low (close to 0%) Mouse Over the upper right corner of the Interface Tx and Rw Utilization dashlet, and click the edit icon Change display unit from Percent to Bits per second
65 Save and close and see the result Exercise 2: Customizing device monitoring In this exercise, you will customize the device monitoring. You will use the 2 device groups (location groups) called East and West created at the beginning of the lab. You will create a new monitoring policy to monitor only the device from your location group (either East or West). Select Monitor/ Monitoring Tools/ Monitoring Policies and click Add
66 Select the Device Health Policy Type Expand Device Selection Select the location group East or West Give a name to the policy, keep the default polling intervals and click save and activate
67 Confirm that the policy is created Confirm the policy is active on appropriate devices Go to your personal dashboard by clicking on You have an Empty Overview Dashboard called CL16 PODx, (created early in the lab).
68 From the setting icon (upper right corner), Select Add Dashlets Add the following Dashlets Network Topology Top N CPU Utilization Top N Interface Utilization Add a Filter : Site You can see the Dashboard
69 Edit The Network Topology Dashlet (mouse over upper right corner) Select the group East or West, depending of your pod, and save and close Edit the Top N Interfaces Dashlet Select Link Ports as Port Group and Change the Title In the Site filter, Select East or West, depending on your pod and click Go
70 Now you have changed the behaviour of your dashboard. This Dashboard: displays your location topology, displays the monitored metrics of the devices (CPU) of your location, displays the monitored metrics of the link ports of your location. In addition, the devices from your location have a specific monitoring policy (with a different interval in this case) Exercise 3: Monitoring UCS servers Explore the Datacenter Dashboards. On Dashboard/Data Center /Compute, select the Data Center (PI-LAB) and click Go You can drill down to a Host to enter Dashboard / Data Center /Host Go also to Monitor / Compute Device.
71 Find YOUR VM, it is called PI30-CL16-PODxy (x is the pod number, y is W for West or E for East) and display its performance metrics. Display also the performance metrics of the host where your VM runs. Below, from Virtual Machines, use Quick Filter to search you VM Click on it: You can have details on your VM and go to the host and the cluster Part 3: Application Monitoring In this part you will learn: How to configure a NAM as a data source for application monitoring How to configure QOS and Application Visibility on routers How to monitor applications Exercise 1: Using NAM as a data source. A NAM is part of your inventory. At this time you can only use it as a network device. To use it as a data source for application monitoring, you must enable it. Select Services/ AV&C/ Data Sources
72 At the bottom, you should see the NAM in disabled state Select it and click Enable You should see it in enabled state. If you expand it, you should see the DATA PORT. This is the NAM port which collects traffic and that you will use as a data source.
73 Exercise 2: AVC Readiness Assessment on router Prime Infrastructure provides an assessment tool for AVC and QoS. This tools gives you the status of your routers regarding AVC capability and configuration. Select Services/Application Visibility and Control/Readiness Assessment In the example below, both routers are AVC capable, one as already AVC configured. One is running protocol pack 11, the other protocol pack 13. Protocol packs contains the information used by NBAR2 to classify protocols. Protocol packs are periodically distributed to recognize new applications or to provide bug fixes. Prime Infrastructure provides a repository for the protocol packs. Protocol packs can be downloaded from CCO and uploaded to Prime Infrastructure, and then they can be loaded to the routers. Exercise 3: AVC profiles
74 AVC profiles are configuration templates that can be deployed on interfaces. There are 3 categories QoS Classification Profiles define how application traffic can be identified (based on NBAR2) and marked. 3 default profiles are provided out of the box according to Cisco best practices: 5 classes, 8 classes and 12 classes profiles. New profiles can be added QoS Action Profiles define the egress actions, which will occur on egress traffic: (Queuing, Priority Queuing, BW reservation, shaping ). 3 default profiles are provided (5,8,12 classes) out of the box. They can be modified and new profiles can be added. Application visibility Profiles define the monitoring actions (URL monitoring, traffic volume, Application Response Time, Voice/Video metrics). Objectives: The goal of this lab is to create a new QoS classification profile that will include the traffic to/from your management platform in the class TRANSACTIONAL DATA Step 1: Adding a new QoS Classification Profile Select Services/AV&C/AVC Profiles Select + to add a new profile
75 Choose Create Classification Profile Give a name (PILAB-QOS), and choose 5-class profile Step 2: Adding a new classification rule to classify the traffic to/from your Prime Infrastructure Server Click Add to add your classification rule (see image above) A new entry appears at the bottom Click Change the type from NBAR to L3/L4 (you will classify using your own PI IP address ) Select Apply IP/Port symmetrically Put YOUR PI IP address ( xy)
76 Click OK Step 3: choose the class of service Select now the QoS class (Transactional-Data) Save the line Save the profile Exercise 4: Interface configuration This feature allows enabling AVC/QoS profiles on interface or interface groups In this exercise, you will deploy both a QoS profile (the Classification Profile you created in the previous exercise), and an AVC profile (to enable traffic Statistics, Application Monitoring, Voice/Video Monitoring) on the internal interface of your router. If you are on East, the interface is g0/0/1 (router 4331) If you are on West, the interface is vlan1 (router 892)
77 Deploy a QoS profile Select Services/ AV&C/ Interface Configuration Select the appropriate interface on your router (You can use the quick filter ) Click Enable QoS Then select your profile (PILAB-QOS) You can preview the CLI. You should see the ACL for your PI server.
78 Then deploy Check the status of the job in Administration/Job Dashboard Deploy an AVC profile Select Services/ AVC/ Interface Configuration Select the internal interface of your router as previously. Notice that you see it with QoS enabled
79 Select Enable App Visibility Choose App Visibility & Performance (IPv4 and IPv6) You can see the CLI. If you are familiar with AVC CLI, you can see that Prime Infrastructure uses the ezpm framework (Easy Performance Monitor) if the router can support it. Click Deploy and wait the job completes. If you go back to interface configuration, you can see that App Visibility Policy is deployed
80 Select now Inventory/Group Management/Port groups Expand Port Groups/System Defined and select AVC Configured Interfaces. You should see your router port. AVC Configured interfaces is automatically populated with the ports where QoS or AVC is configured Select Monitor/Monitoring Tools/ Monitoring Policies A Policy exists by default called Interface-AVC. This policy monitors interfaces from the port group AVC configured interfaces. It is not activated by default. Activate it! The policy becomes active. You can click details to see on which interfaces
81 Exercise 5: Device Data Sources You have deployed AVC profiles. The effect is to configure metering agents on your router. Metering agents are able to provide statistics for Application traffic, Application Response Time and Voice and Video parameters (jitter and loss). These metrics are exported using Netflow V9 or IPFIX. These exports create data sources in Prime Infrastructure. To view the data sources: Select Services/AV&C/Data Sources Select your data source (RTR-PODx-y) and see the netflow templates. You will have probably several templates, depending of what you have enabled and depending on the traffic patterns on the network.
82 If you want details on the contents of the export, you can drill down to a template by clicking on it. You will see the fields of the netflow records and the exporting devices (your router) (Note: you can also go to this same page from Services/AV&C/Netflow Templates) Exercise 6: QoS and AVC monitoring on interfaces Previously, you enabled monitoring on the port group AVC configured interfaces. This port group contains the interfaces where you enabled AVC or QOS
83 Search for your router RTR-PODx-y in the search tool bar. Click on the router name link. Click on the icon to launch the 360 view. Select interface and scroll to the interface where you enable AVC. You can see that Top3 applications data is provided. Click now on the interface name link in device 360 This launches the Interface Dashboard for this interface You see interface details and interface Tx/RX (data polled through SNMP)
84 Then you see data collected through AVC (Application volume, Top N client, Number of clients and DSCP information) You see also data from Class Based QoS monitoring. To visualize data on the Top QoS Class Map Statistics Trend dashlet, you need to select In traffic and either Pre or Post policy rate (probably there is no drop)
85 Exercise 7: Monitoring application with Service Assurance and Application Performance Dashboard Service Assurance Dashboard is the main Overview Dashboard to display Application metrics Go to Dashboard/ Overview/ Service Assurance Explore the dashboard Focuse on the Top N Applications Dashlet
86 Click on the edit icon Expand the data sources By default all data sources are aggregated Change to data source RTR-PODx-y (netflow) then vnam-podx (NAM ) to see the difference. Click the bar of the RTP Application to drill down to a performance dashboard for Application
87 From Analysis in the upper right corner, Add the Dashlet Application ART You should see No data. Why? Change to another Application, tcp based, for example ssh
88 Look the Application ART Analysis dashlet. You should have data. Do you understand this graph? Exercise 7: Customize your Dashboard Click dashlets. to launch your dashboard, and click setting (upper right corner) to add Add the dashlets: Top N applications Worst Site by transaction time Top N Clients Top N servers
89 End of LAB
Perform Configuration Audits Using Compliance
 How To Perform a Compliance Audit, page 1 Enable and Disable Compliance Auditing, page 2 Create a New Compliance Policy, page 2 Create Compliance Policy Rules, page 3 Create a Compliance Profile That Contains
How To Perform a Compliance Audit, page 1 Enable and Disable Compliance Auditing, page 2 Create a New Compliance Policy, page 2 Create Compliance Policy Rules, page 3 Create a Compliance Profile That Contains
Data Collection and Background Tasks
 This section contains the following topics: Control Data Collection Jobs, on page 1 How Data Retention Settings Affect Web GUI Data, on page 1 About Historical Data Retention, on page 2 Performance and
This section contains the following topics: Control Data Collection Jobs, on page 1 How Data Retention Settings Affect Web GUI Data, on page 1 About Historical Data Retention, on page 2 Performance and
Overview of Cisco Prime Collaboration Assurance
 Overview of Cisco Prime Collaboration Assurance Cisco Prime Collaboration is a comprehensive video and voice service assurance and management system with a set of monitoring, troubleshooting, and reporting
Overview of Cisco Prime Collaboration Assurance Cisco Prime Collaboration is a comprehensive video and voice service assurance and management system with a set of monitoring, troubleshooting, and reporting
WhatsUp Gold. Evaluation Guide
 WhatsUp Gold Evaluation Guide Table of Contents This guide provides and overview of WhatsUp Gold. Refer to our Online Help for more details. Section Step 1: Getting Started Description Installation requirements
WhatsUp Gold Evaluation Guide Table of Contents This guide provides and overview of WhatsUp Gold. Refer to our Online Help for more details. Section Step 1: Getting Started Description Installation requirements
Overview of Cisco Prime Collaboration Assurance and Analytics Business
 Overview of Cisco Prime Collaboration Assurance and Analytics Business Cisco Prime Collaboration Assurance and Analytics Business is a monitoring and data analytics management application system that allows
Overview of Cisco Prime Collaboration Assurance and Analytics Business Cisco Prime Collaboration Assurance and Analytics Business is a monitoring and data analytics management application system that allows
Add and Organize Devices
 This chapter contains the following topics: Add Devices to Prime Infrastructure, on page 1 Import Devices from Another Source, on page 7 Create Device Import CSV Files, on page 7 Add Devices Manually (New
This chapter contains the following topics: Add Devices to Prime Infrastructure, on page 1 Import Devices from Another Source, on page 7 Create Device Import CSV Files, on page 7 Add Devices Manually (New
Technology Overview. Overview CHAPTER
 CHAPTER 2 Revised: July 29, 2013, This overview of AVC technology includes the following topics: Overview, page 2-1 AVC Features and Capabilities, page 2-2 AVC Architecture, page 2-4 Interoperability of
CHAPTER 2 Revised: July 29, 2013, This overview of AVC technology includes the following topics: Overview, page 2-1 AVC Features and Capabilities, page 2-2 AVC Architecture, page 2-4 Interoperability of
vrealize Operations Management Pack for NSX for vsphere 2.0
 vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Cisco Software Defined Access (SDA)
 Cisco Software Defined Access (SDA) Transformational Approach to Network Design & Provisioning Sanjay Kumar Regional Manager- ASEAN, Cisco Systems What is network about? Source: google.de images Security
Cisco Software Defined Access (SDA) Transformational Approach to Network Design & Provisioning Sanjay Kumar Regional Manager- ASEAN, Cisco Systems What is network about? Source: google.de images Security
ForeScout Extended Module for Tenable Vulnerability Management
 ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
Media Path Analysis. Analyzing Media Paths Using IP SLA. Before You Begin. This section contains the following:
 This section contains the following: Analyzing Media Paths Using IP SLA, page 1 Analyzing Media Paths Using VSAA, page 3 Managing a Video Test Call, page 6 Analyzing Media Paths Using IP SLA To start a
This section contains the following: Analyzing Media Paths Using IP SLA, page 1 Analyzing Media Paths Using VSAA, page 3 Managing a Video Test Call, page 6 Analyzing Media Paths Using IP SLA To start a
Configure Controller and AP Settings
 Configure SNMP Credentials for Rogue AP Tracing, on page 1 Configure Protocols for CLI Sessions, on page 2 Enable Unified AP Ping Reachability Settings on the Prime Infrastructure, on page 2 Refresh Controllers
Configure SNMP Credentials for Rogue AP Tracing, on page 1 Configure Protocols for CLI Sessions, on page 2 Enable Unified AP Ping Reachability Settings on the Prime Infrastructure, on page 2 Refresh Controllers
Get Started with Cisco DNA Center
 About Cisco DNA Center, on page 1 Log In, on page 1 Log In for the First Time as a Network Administrator, on page 2 Default Home Page, on page 3 Use Global Search, on page 5 Where to Start, on page 6 About
About Cisco DNA Center, on page 1 Log In, on page 1 Log In for the First Time as a Network Administrator, on page 2 Default Home Page, on page 3 Use Global Search, on page 5 Where to Start, on page 6 About
This section provides reference information on the following topics: Understanding NAM Behavior GUI Field Descriptions Report Descriptions
 APPENDIXB This section provides reference information on the following topics: Understanding NAM Behavior GUI s Report s Understanding NAM Behavior This section includes details on how NAM works including
APPENDIXB This section provides reference information on the following topics: Understanding NAM Behavior GUI s Report s Understanding NAM Behavior This section includes details on how NAM works including
Traffic and Performance Visibility for Cisco Live 2010, Barcelona
 Traffic and Performance Visibility for Cisco Live 2010, Barcelona Background Cisco Live is Cisco's annual premier education and training event for IT, networking, and communications professionals. Cisco
Traffic and Performance Visibility for Cisco Live 2010, Barcelona Background Cisco Live is Cisco's annual premier education and training event for IT, networking, and communications professionals. Cisco
Network Operations Analytics
 Network Operations Analytics Solution Guide Version 2.4.4 (Build 2.4.4.0.x) June 2016 Copyright 2012-2016 NetFlow Logic Corporation. All rights reserved. Patents Pending. Contents Introduction... 2 Solution
Network Operations Analytics Solution Guide Version 2.4.4 (Build 2.4.4.0.x) June 2016 Copyright 2012-2016 NetFlow Logic Corporation. All rights reserved. Patents Pending. Contents Introduction... 2 Solution
Navigating Cisco EPN Manager
 Navigating Cisco EPN Manager Cisco EPN Manager 1.2 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
Navigating Cisco EPN Manager Cisco EPN Manager 1.2 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
NERC Compliance Use Cases
 NERC Compliance Use Cases Overview For network and IT teams who work in the Energy sector, the North American Energy Reliability Corporation Critical Infrastructure Protection (NERC-CIP) standards provide
NERC Compliance Use Cases Overview For network and IT teams who work in the Energy sector, the North American Energy Reliability Corporation Critical Infrastructure Protection (NERC-CIP) standards provide
AuditConfigurationArchiveandSoftwareManagementChanges (Network Audit)
 This section contains the following topics: Audit Configuration Archive and Software Management Changes (Network Audit), on page 1 Audit Changes Made By Users (Change Audit), on page 1 Audit Actions Executed
This section contains the following topics: Audit Configuration Archive and Software Management Changes (Network Audit), on page 1 Audit Changes Made By Users (Change Audit), on page 1 Audit Actions Executed
Monitoring and Analysis
 CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
Monitoring Data CHAPTER
 CHAPTER 4 The Monitor tab provides options for viewing various types of monitored data. There are options for: Overview of Data Collection and Data Sources, page 4-2 Viewing the Monitor Overview Charts,
CHAPTER 4 The Monitor tab provides options for viewing various types of monitored data. There are options for: Overview of Data Collection and Data Sources, page 4-2 Viewing the Monitor Overview Charts,
NetBrain Instant Trial Edition 5.2. Quick Start Workbook
 NetBrain Instant Trial Edition 5.2 Quick Start Workbook NetBrain ITE 5.2 Quick Start Workbook Thank you for downloading NetBrain Instant Trial Edition (ITE). This workbook will help you make the most of
NetBrain Instant Trial Edition 5.2 Quick Start Workbook NetBrain ITE 5.2 Quick Start Workbook Thank you for downloading NetBrain Instant Trial Edition (ITE). This workbook will help you make the most of
Operating and Monitoring the Network
 CHAPTER 6 Under the Operate tab, Prime NCS (WAN) provides tools to help you monitor your network on a daily basis, as well as perform other day-to-day or ad hoc operations relating to network device inventory
CHAPTER 6 Under the Operate tab, Prime NCS (WAN) provides tools to help you monitor your network on a daily basis, as well as perform other day-to-day or ad hoc operations relating to network device inventory
Table of Contents HOL-1701-CHG-5
 Table of Contents Lab Overview: vrealize Operations Application Monitoring: Challenge Lab... 2 Lab Overview... 3 Lab Guidance... 5 Module 1 - Configuring a Custom Application (15 minutes)... 10 Introduction...
Table of Contents Lab Overview: vrealize Operations Application Monitoring: Challenge Lab... 2 Lab Overview... 3 Lab Guidance... 5 Module 1 - Configuring a Custom Application (15 minutes)... 10 Introduction...
IWAN APIC-EM Application Cisco Intelligent WAN
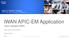 IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
Monitor Device and Network Health and Performance
 Monitor Device and Network Health and Performance This chapter contains the following topics: How Device Health and Performance Is Monitored: Monitoring Policies, on page 1 Set Up Basic Device Health Monitoring,
Monitor Device and Network Health and Performance This chapter contains the following topics: How Device Health and Performance Is Monitored: Monitoring Policies, on page 1 Set Up Basic Device Health Monitoring,
One Management Realized, with Cisco Prime Infrastructure Manage Complexity. Manage Effectively. Manage Intelligently. Closing
 One Management Realized, with Cisco Prime Infrastructure Manage Complexity Manage Effectively Manage Intelligently Closing 2 2013 Cisco and/or its affiliates. All rights reserved. Internet of Things 99%
One Management Realized, with Cisco Prime Infrastructure Manage Complexity Manage Effectively Manage Intelligently Closing 2 2013 Cisco and/or its affiliates. All rights reserved. Internet of Things 99%
Installing vrealize Network Insight
 vrealize Network Insight 3.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
vrealize Network Insight 3.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
Cisco Unified Service Statistics Manager 8.7
 Deployment Guide Cisco Unified Service Statistics Manager 8.7 Deployment Best Practices For further information, questions and comments please contact ask-ucms@cisco.com 2012 Cisco and/or its affiliates.
Deployment Guide Cisco Unified Service Statistics Manager 8.7 Deployment Best Practices For further information, questions and comments please contact ask-ucms@cisco.com 2012 Cisco and/or its affiliates.
Demo Lab Guide OpenManage Network Manager
 Demo Lab Guide OpenManage Network Manager OpenManage Essentials Walk Through and Configuration Product Domain: Networking Author: Ruairi Mongan Version: 1.01 Date: 20/11/2014 1 Dell Demo Center https://demos.dell.com
Demo Lab Guide OpenManage Network Manager OpenManage Essentials Walk Through and Configuration Product Domain: Networking Author: Ruairi Mongan Version: 1.01 Date: 20/11/2014 1 Dell Demo Center https://demos.dell.com
vrealize Operations Management Pack for NSX for vsphere 3.5.0
 vrealize Operations Management Pack for NSX for vsphere 3.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 3.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vcenter Operations Management Pack for NSX-vSphere
 vcenter Operations Management Pack for NSX-vSphere vcenter Operations Manager 5.8 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
vcenter Operations Management Pack for NSX-vSphere vcenter Operations Manager 5.8 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Securing Containers Using a PNSC and a Cisco VSG
 Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 4 About
Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 4 About
vrealize Operations Management Pack for NSX for vsphere 3.0
 vrealize Operations Management Pack for NSX for vsphere 3.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 3.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3
 Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
Quick Start Guide (SDN)
 NetBrain Integrated Edition 7.1 Quick Start Guide (SDN) Version 7.1 Last Updated 2018-07-24 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Discovering and Visualizing
NetBrain Integrated Edition 7.1 Quick Start Guide (SDN) Version 7.1 Last Updated 2018-07-24 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Discovering and Visualizing
vrealize Network Insight Installation Guide
 vrealize Network Insight Installation Guide vrealize Network Insight 3.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vrealize Network Insight Installation Guide vrealize Network Insight 3.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
This section contains context-sensitive Online Help content for the Web Client > Dashboard tab.
 This section contains context-sensitive Online Help content for the Web Client > tab. Summary, page 1 Network, page 6 Storage, page 9 Compute, page 15 Summary The intent of the Summary dashboard is to
This section contains context-sensitive Online Help content for the Web Client > tab. Summary, page 1 Network, page 6 Storage, page 9 Compute, page 15 Summary The intent of the Summary dashboard is to
Configuring APIC Accounts
 This chapter contains the following sections: Adding an APIC Account, page 1 Viewing APIC Reports, page 3 Assigning an APIC account to a Pod, page 15 Handling APIC Failover, page 15 Adding an APIC Account
This chapter contains the following sections: Adding an APIC Account, page 1 Viewing APIC Reports, page 3 Assigning an APIC account to a Pod, page 15 Handling APIC Failover, page 15 Adding an APIC Account
Introducing Cisco UCS Central 2.0
 This chapter includes the following sections: Overview of Central 2.0 Features, on page 1 Behavior Changes in Release 2.0, on page 7 Multi-version Management Support, on page 8 Feature Support Matrix,
This chapter includes the following sections: Overview of Central 2.0 Features, on page 1 Behavior Changes in Release 2.0, on page 7 Multi-version Management Support, on page 8 Feature Support Matrix,
WhatsConfigured v3.1 User Guide
 WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
HPE Intelligent Management Center
 HPE Intelligent Management Center Service Health Manager Administrator Guide Abstract This guide provides introductory, configuration, and usage information for Service Health Manager (SHM). It is for
HPE Intelligent Management Center Service Health Manager Administrator Guide Abstract This guide provides introductory, configuration, and usage information for Service Health Manager (SHM). It is for
Configure System Parameters
 This section includes the following:, page 1 Cisco Prime Collaboration allows you to configure system parameters for Cisco Prime Collaboration Assurance. The following are the system configuration parameters
This section includes the following:, page 1 Cisco Prime Collaboration allows you to configure system parameters for Cisco Prime Collaboration Assurance. The following are the system configuration parameters
Configuring Cisco Performance Monitor
 This document contains information about and instructions for configuring Cisco Performance Monitor. Finding Feature Information, page 1 Information About Cisco Performance Monitor, page 1 Restrictions
This document contains information about and instructions for configuring Cisco Performance Monitor. Finding Feature Information, page 1 Information About Cisco Performance Monitor, page 1 Restrictions
Installing vrealize Network Insight. VMware vrealize Network Insight 3.3
 VMware vrealize Network Insight 3.3 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware Web site also provides the latest product updates.
VMware vrealize Network Insight 3.3 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware Web site also provides the latest product updates.
Configuring AVC to Monitor MACE Metrics
 This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
Setting up. Discovering the Network. Planning Discovery Runs CHAPTER
 CHAPTER 3 After you install Prime NCS (WAN) and launch the browser, read the following sections to learn how to get started using Prime NCS (WAN): Discovering the Network, page 3-1 Setting Up Site Profiles,
CHAPTER 3 After you install Prime NCS (WAN) and launch the browser, read the following sections to learn how to get started using Prime NCS (WAN): Discovering the Network, page 3-1 Setting Up Site Profiles,
Quick Start Guide (SDN)
 NetBrain Integrated Edition 7.1 Quick Start Guide (SDN) Version 7.1a Last Updated 2018-09-03 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Discovering and Visualizing
NetBrain Integrated Edition 7.1 Quick Start Guide (SDN) Version 7.1a Last Updated 2018-09-03 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Discovering and Visualizing
vrealize Network Insight Installation Guide
 vrealize Network Insight Installation Guide vrealize Network Insight 3.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vrealize Network Insight Installation Guide vrealize Network Insight 3.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
NetBrain Quick Start Guide For End Users
 NetBrain Quick Start Guide For End Users Dynamic Documentation Network Analysis Visual Troubleshooting Automation Qapp Network Change Management Thin Client NetBrain Technologies, Inc. 2004-2015. All rights
NetBrain Quick Start Guide For End Users Dynamic Documentation Network Analysis Visual Troubleshooting Automation Qapp Network Change Management Thin Client NetBrain Technologies, Inc. 2004-2015. All rights
AVC Configuration. Unified Policy CLI CHAPTER
 CHAPTER 3 Revised: February 7, 2013, This chapter addresses AVC configuration and includes the following topics: Unified Policy CLI, page 3-1 Metric Producer Parameters, page 3-2 Reacts, page 3-2 NetFlow/IPFIX
CHAPTER 3 Revised: February 7, 2013, This chapter addresses AVC configuration and includes the following topics: Unified Policy CLI, page 3-1 Metric Producer Parameters, page 3-2 Reacts, page 3-2 NetFlow/IPFIX
Introduction... 2 Assumptions... 2
 HP Network Node Manager ispi Performance for Traffic Software Version: 9.20 Deployment by Example Table of Contents Introduction... 2 Assumptions... 2 Installation... 3 Installing the HP NNMi Extension
HP Network Node Manager ispi Performance for Traffic Software Version: 9.20 Deployment by Example Table of Contents Introduction... 2 Assumptions... 2 Installation... 3 Installing the HP NNMi Extension
ForeScout CounterACT. Configuration Guide. Version 1.1
 ForeScout CounterACT Hybrid Cloud Module: VMware NSX Plugin Version 1.1 Table of Contents About VMware NSX Integration... 3 Use Cases... 3 Additional VMware Documentation... 3 About this Plugin... 3 Dependency
ForeScout CounterACT Hybrid Cloud Module: VMware NSX Plugin Version 1.1 Table of Contents About VMware NSX Integration... 3 Use Cases... 3 Additional VMware Documentation... 3 About this Plugin... 3 Dependency
Provisioning: Working with Pre-Configuration
 CHAPTER 6 QPM provides you with Pre-Configuration feature to define certain values and features that will be used while working with policies. The following topics describe the macros used in QPM: Working
CHAPTER 6 QPM provides you with Pre-Configuration feature to define certain values and features that will be used while working with policies. The following topics describe the macros used in QPM: Working
Use Plug and Play to Deploy New Devices
 About Plug and Play, page 1 Prerequisites for Using Plug and Play, page 2 Plug and Play Workflow, page 2 Use the Plug and Play Dashboard to Monitor New Device Deployments, page 4 Create Plug and Play Profiles
About Plug and Play, page 1 Prerequisites for Using Plug and Play, page 2 Plug and Play Workflow, page 2 Use the Plug and Play Dashboard to Monitor New Device Deployments, page 4 Create Plug and Play Profiles
DEPLOYING BASIC CISCO WIRELESS LANS (WDBWL)
 [Type a quote from the document or the summary of an interesting point. You can position the text box anywhere in the document. Use the Drawing Tools tab to change the formatting of the pull quote text
[Type a quote from the document or the summary of an interesting point. You can position the text box anywhere in the document. Use the Drawing Tools tab to change the formatting of the pull quote text
PnP Deep Dive Hands-on with APIC-EM and Prime Infrastructure
 LTRNMS-2007 PnP Deep Dive Hands-on with APIC-EM and Prime Infrastructure Thomas Gerneth, Julian Mueller,Tobias Huelsdau Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after
LTRNMS-2007 PnP Deep Dive Hands-on with APIC-EM and Prime Infrastructure Thomas Gerneth, Julian Mueller,Tobias Huelsdau Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after
LiveAction Training Lab Workbook
 LiveAction Training Lab Workbook Copyright 2018, LiveAction, Inc. All rights reserved. This product and related documentation are protected by copyright and distribution under licensing restricting their
LiveAction Training Lab Workbook Copyright 2018, LiveAction, Inc. All rights reserved. This product and related documentation are protected by copyright and distribution under licensing restricting their
Setting Up the Network for Monitoring
 2 CHAPTER Before Prime Collaboration can start monitoring the voice and video endpoints in your network, you must complete several tasks. Table 2-1 provides information about the prerequisites for monitoring
2 CHAPTER Before Prime Collaboration can start monitoring the voice and video endpoints in your network, you must complete several tasks. Table 2-1 provides information about the prerequisites for monitoring
NetBrain OE System Quick Start Guide
 NetBrain Technologies Inc. NetBrain OE System Quick Start Guide For Operator Edition Administrators Table of Contents 1. Install NetBrain OE System... 3 1.1 Install Gateway Server... 4 1.2 Install Network
NetBrain Technologies Inc. NetBrain OE System Quick Start Guide For Operator Edition Administrators Table of Contents 1. Install NetBrain OE System... 3 1.1 Install Gateway Server... 4 1.2 Install Network
NetBrain Quick Start Guide For End Users
 NetBrain Quick Start Guide For End Users Dynamic Documentation Network Analysis Visual Troubleshooting Automation Qapp Network Change Management Thin Client NetBrain Technologies, Inc. 2004-2016. All rights
NetBrain Quick Start Guide For End Users Dynamic Documentation Network Analysis Visual Troubleshooting Automation Qapp Network Change Management Thin Client NetBrain Technologies, Inc. 2004-2016. All rights
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0)
 UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
Cisco Virtual Application Container Services 2.0 Lab v1
 Cisco Virtual Application Container Services 2.0 Lab v1 Last Updated: 02-SEP-2015 About This Solution Cisco Virtual Application Container Services (VACS) enables simplified deployment of Secure Application
Cisco Virtual Application Container Services 2.0 Lab v1 Last Updated: 02-SEP-2015 About This Solution Cisco Virtual Application Container Services (VACS) enables simplified deployment of Secure Application
vrealize Operations Manager Customization and Administration Guide vrealize Operations Manager 6.4
 vrealize Operations Manager Customization and Administration Guide vrealize Operations Manager 6.4 vrealize Operations Manager Customization and Administration Guide You can find the most up-to-date technical
vrealize Operations Manager Customization and Administration Guide vrealize Operations Manager 6.4 vrealize Operations Manager Customization and Administration Guide You can find the most up-to-date technical
Securing Containers Using a PNSC and a Cisco VSG
 Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 3 About
Securing Containers Using a PNSC and a Cisco VSG This chapter contains the following sections: About Prime Network Service Controllers, page 1 Integrating a VSG into an Application Container, page 3 About
NetBrain Instant Trial Edition 5.1. Quick Start Workbook
 NetBrain Instant Trial Edition 5.1 Quick Start Workbook NetBrain ITE 5.1 Quick Start Workbook Thank you for downloading NetBrain Instant Trial Edition (ITE). This workbook will help you make the most of
NetBrain Instant Trial Edition 5.1 Quick Start Workbook NetBrain ITE 5.1 Quick Start Workbook Thank you for downloading NetBrain Instant Trial Edition (ITE). This workbook will help you make the most of
Azure for On-Premises Administrators Practice Exercises
 Azure for On-Premises Administrators Practice Exercises Overview This course includes optional practical exercises where you can try out the techniques demonstrated in the course for yourself. This guide
Azure for On-Premises Administrators Practice Exercises Overview This course includes optional practical exercises where you can try out the techniques demonstrated in the course for yourself. This guide
Forescout. Configuration Guide. Version 2.4
 Forescout Version 2.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 2.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Wired Network Summary Data Overview
 Wired Network Summary Data Overview Cisco Prime Infrastructure 3.1 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE.
Wired Network Summary Data Overview Cisco Prime Infrastructure 3.1 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE.
Cisco Prime Infrastructure 3.0
 Guide Cisco Prime Infrastructure 3.0 Deployment Guide 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 63 Contents Scope... 5 Introduction...
Guide Cisco Prime Infrastructure 3.0 Deployment Guide 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 63 Contents Scope... 5 Introduction...
WhatsUp Gold Getting Started Guide v16.4
 WhatsUp Gold Getting Started Guide v16.4 Contents CHAPTER 1 Welcome Welcome to WhatsUp Gold... 1 About WhatsUp Gold... 1 WhatsUp Gold Editions... 2 Deploying Deploying WhatsUp Gold... 5 STEP 1: Prepare
WhatsUp Gold Getting Started Guide v16.4 Contents CHAPTER 1 Welcome Welcome to WhatsUp Gold... 1 About WhatsUp Gold... 1 WhatsUp Gold Editions... 2 Deploying Deploying WhatsUp Gold... 5 STEP 1: Prepare
NetBrain Consultant Edition (CE)
 NetBrain Consultant Edition (CE) Quick Start Guide NetBrain Technologies, Inc. 2004-2013. All rights reserved +1.800.605.7964 support@netbraintech.com www.netbraintech.com Contents 1. Introduction 1) Install
NetBrain Consultant Edition (CE) Quick Start Guide NetBrain Technologies, Inc. 2004-2013. All rights reserved +1.800.605.7964 support@netbraintech.com www.netbraintech.com Contents 1. Introduction 1) Install
Overview of the NAM Traffic Analyzer
 CHAPTER 1 These topics provide information about using the various components of the NAM Traffic Analyzer: Introducing the NAM Traffic Analyzer, page 1-1 Using the NAM Graphical User Interface A Closer
CHAPTER 1 These topics provide information about using the various components of the NAM Traffic Analyzer: Introducing the NAM Traffic Analyzer, page 1-1 Using the NAM Graphical User Interface A Closer
Administration and monitoring of the Cisco Data Center with Cisco DCNM
 Administration and monitoring of the Cisco Data Center with Cisco DCNM Paul Dunon Consulting SE Network Management Emeric Calabrese Consulting SE Data Center Agenda DCNM Solution overview Best Practices
Administration and monitoring of the Cisco Data Center with Cisco DCNM Paul Dunon Consulting SE Network Management Emeric Calabrese Consulting SE Data Center Agenda DCNM Solution overview Best Practices
Design Guide for Cisco ACI with Avi Vantage
 Page 1 of 23 Design Guide for Cisco ACI with Avi Vantage view online Overview Cisco ACI Cisco Application Centric Infrastructure (ACI) is a software defined networking solution offered by Cisco for data
Page 1 of 23 Design Guide for Cisco ACI with Avi Vantage view online Overview Cisco ACI Cisco Application Centric Infrastructure (ACI) is a software defined networking solution offered by Cisco for data
Manage Your Inventory
 About Inventory About Inventory, on page 1 Inventory and Cisco ISE Authentication, on page 2 Display Information About Your Inventory, on page 2 Types of Devices in the DNA Center Inventory, on page 6
About Inventory About Inventory, on page 1 Inventory and Cisco ISE Authentication, on page 2 Display Information About Your Inventory, on page 2 Types of Devices in the DNA Center Inventory, on page 6
Managing System Administration Settings
 This chapter contains the following sections: Setting up the Outgoing Mail Server, page 2 Working with Email Templates, page 2 Configuring System Parameters (Optional), page 5 Updating the License, page
This chapter contains the following sections: Setting up the Outgoing Mail Server, page 2 Working with Email Templates, page 2 Configuring System Parameters (Optional), page 5 Updating the License, page
NetFlow Monitoring. NetFlow Monitoring
 , page 1 NetFlow Limitations, page 2 Creating a Flow Record Definition, page 3 Viewing Flow Record Definitions, page 4 Defining the Exporter Profile, page 4 Creating a Flow Collector, page 5 Creating a
, page 1 NetFlow Limitations, page 2 Creating a Flow Record Definition, page 3 Viewing Flow Record Definitions, page 4 Defining the Exporter Profile, page 4 Creating a Flow Collector, page 5 Creating a
Monitor Application Health
 About Application Experience, on page 1 Enable Cisco NetFlow Collection, on page 1 View the Application Experience of a Client Device, on page 2 Monitor the Health of All Applications, on page 3 Monitor
About Application Experience, on page 1 Enable Cisco NetFlow Collection, on page 1 View the Application Experience of a Client Device, on page 2 Monitor the Health of All Applications, on page 3 Monitor
Cisco SD-AVC User Guide, Release 1.1.0
 First Published: 2017-10-22 Last Modified: 2017-10-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2017-10-22 Last Modified: 2017-10-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
C H A P T E R Reports Note Cisco Prime Network Control System Configuration Guide OL
 CHAPTER 14 The Cisco NCS reporting is necessary to monitor the system and network health as well as troubleshoot problems. A number of reports can be generated to run on an immediate and scheduled basis.
CHAPTER 14 The Cisco NCS reporting is necessary to monitor the system and network health as well as troubleshoot problems. A number of reports can be generated to run on an immediate and scheduled basis.
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
VMware vrealize Operations for Horizon Administration. 20 SEP 2018 VMware vrealize Operations for Horizon 6.6
 VMware vrealize Operations for Horizon Administration 20 SEP 2018 VMware vrealize Operations for Horizon 6.6 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware vrealize Operations for Horizon Administration 20 SEP 2018 VMware vrealize Operations for Horizon 6.6 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware vrealize Operations for Horizon Administration. Modified on 3 JUL 2018 VMware vrealize Operations for Horizon 6.4
 VMware vrealize Operations for Horizon Administration Modified on 3 JUL 2018 VMware vrealize Operations for Horizon 6.4 You can find the most up-to-date technical documentation on the VMware website at:
VMware vrealize Operations for Horizon Administration Modified on 3 JUL 2018 VMware vrealize Operations for Horizon 6.4 You can find the most up-to-date technical documentation on the VMware website at:
Cisco Prime Network Client Overview
 CHAPTER 1 Cisco Prime Network (Prime Network) provides a suite of GUI tools that offer an intuitive interface for managing the network and services, and for performing required system administration activities.
CHAPTER 1 Cisco Prime Network (Prime Network) provides a suite of GUI tools that offer an intuitive interface for managing the network and services, and for performing required system administration activities.
Deploying Devices. Cisco Prime Infrastructure 3.1. Job Aid
 Deploying Devices Cisco Prime Infrastructure 3.1 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION,
Deploying Devices Cisco Prime Infrastructure 3.1 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION,
NetBrain OE 5.1 On-Site Trial. Quick Start Workbook
 NetBrain OE 5.1 On-Site Trial Quick Start Workbook NetBrain 5.1 Quick Start Workbook Thank you for downloading NetBrain. This workbook will help you make the most of your trial by introducing you to essential
NetBrain OE 5.1 On-Site Trial Quick Start Workbook NetBrain 5.1 Quick Start Workbook Thank you for downloading NetBrain. This workbook will help you make the most of your trial by introducing you to essential
CounterACT Wireless Plugin
 CounterACT Wireless Plugin Version 1.7.0 Table of Contents About the Wireless Plugin... 4 Wireless Network Access Device Terminology... 5 How It Works... 6 About WLAN Controller/Lightweight Access Points...
CounterACT Wireless Plugin Version 1.7.0 Table of Contents About the Wireless Plugin... 4 Wireless Network Access Device Terminology... 5 How It Works... 6 About WLAN Controller/Lightweight Access Points...
Creating Application Containers
 This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
This chapter contains the following sections: General Application Container Creation Process, page 1 Creating Application Container Policies, page 2 About Application Container Templates, page 5 Creating
VMware vrealize Operations for Horizon Installation
 VMware vrealize Operations for Horizon Installation vrealize Operations for Horizon 6.4 Installation vrealize Operations for Horizon 6.4 This document supports the version of each product listed and supports
VMware vrealize Operations for Horizon Installation vrealize Operations for Horizon 6.4 Installation vrealize Operations for Horizon 6.4 This document supports the version of each product listed and supports
Note that you can also use the password command but the secret command gives you a better encryption algorithm.
 Router Device Security Lab Configuring Secure Passwords 1. Configure the enable secret and password enable password TRUSTME enable secret letmein Look at the configuration: show config terminal Note the
Router Device Security Lab Configuring Secure Passwords 1. Configure the enable secret and password enable password TRUSTME enable secret letmein Look at the configuration: show config terminal Note the
Introducing Cisco UCS Central 1.3
 This chapter includes the following sections: Overview of Cisco UCS Central 1.3 Features, page 1 Overview of Cisco UCS Central 1.3 Features Cisco UCS Central, release 1.3 allows you to take charge of the
This chapter includes the following sections: Overview of Cisco UCS Central 1.3 Features, page 1 Overview of Cisco UCS Central 1.3 Features Cisco UCS Central, release 1.3 allows you to take charge of the
Advanced Application Reporting USER GUIDE
 Advanced Application Reporting USER GUIDE CONTENTS 1.0 Preface: About This Document 5 2.0 Conventions 5 3.0 Chapter 1: Introducing Advanced Application Reporting 6 4.0 Features and Benefits 7 5.0 Product
Advanced Application Reporting USER GUIDE CONTENTS 1.0 Preface: About This Document 5 2.0 Conventions 5 3.0 Chapter 1: Introducing Advanced Application Reporting 6 4.0 Features and Benefits 7 5.0 Product
vrealize Operations Management Pack for NSX for Multi-Hypervisor
 vrealize Operations Management Pack for This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more
vrealize Operations Management Pack for This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more
Cisco ACI with Cisco AVS
 This chapter includes the following sections: Cisco AVS Overview, page 1 Cisco AVS Installation, page 6 Key Post-Installation Configuration Tasks for the Cisco AVS, page 43 Distributed Firewall, page 62
This chapter includes the following sections: Cisco AVS Overview, page 1 Cisco AVS Installation, page 6 Key Post-Installation Configuration Tasks for the Cisco AVS, page 43 Distributed Firewall, page 62
Introducing Cisco UCS Central 1.4
 This chapter includes the following sections: Overview of Cisco UCS Central 1.4 Features, page 1 Behavior and Design Changes in HTML5 UI, page 10 Multi-version Management Support, page 11 Feature Support
This chapter includes the following sections: Overview of Cisco UCS Central 1.4 Features, page 1 Behavior and Design Changes in HTML5 UI, page 10 Multi-version Management Support, page 11 Feature Support
CHAPTER. Introduction
 CHAPTER 1 This chapter describes the Prime Central for HCS software. This software is intended for use in a Managed Service Provider (MSP) Network Operations Center (NOC). Prime Central for HCS provides
CHAPTER 1 This chapter describes the Prime Central for HCS software. This software is intended for use in a Managed Service Provider (MSP) Network Operations Center (NOC). Prime Central for HCS provides
NAM Deployment CHAPTER
 CHAPTER 6 This chapter describes usage scenarios for the Cisco Prime Network Analysis Module 5.1. Each scenario focuses on a need to be addressed or a problem to be solved. The scenario takes into account
CHAPTER 6 This chapter describes usage scenarios for the Cisco Prime Network Analysis Module 5.1. Each scenario focuses on a need to be addressed or a problem to be solved. The scenario takes into account
"Charting the Course... Implementing Cisco Quality of Service (QOS) Course Summary
 Course Summary Description v2.5 provides learners with in-depth knowledge of QoS requirements, conceptual models such as best effort, IntServ, and DiffServ, and the implementation of QoS on Cisco platforms.
Course Summary Description v2.5 provides learners with in-depth knowledge of QoS requirements, conceptual models such as best effort, IntServ, and DiffServ, and the implementation of QoS on Cisco platforms.
