NOTE: This setting is applicable only for local users.
|
|
|
- Shonda Tabitha O’Brien’
- 6 years ago
- Views:
Transcription
1 How do I better user access security in NetScaler MAS? NetScaler Management and Analytics System is a centralized network management, analytics, and orchestration solution. From a single platform, administrators can view, automate, and manage network services for their distributed NetScaler deployments. In addition to reducing operational costs and simplifying tasks, MAS provides real-time analytics to help administrators identify and address application performance and security issues across the application infrastructure. Further, NetScaler MAS provides application-level visibility through the lifecycle and integration with external orchestration systems. A system like NetScaler MAS is accessed by many administrators and it is important that some user access security aspects are taken care of to ensure the MAS system is protected. Here are some of the things an administrator can configure/enable to better MAS user access security. 1) Enabling Strong Password A strong password policy ensures that a MAS user s password is complex thereby making it more secure. The complex password policy feature includes two types of checks: a) Character based check: These checks ensure that required character types such as uppercase, lowercase, numeric, etc. are part of the password. If password complexity is enabled, MAS checks for the following in the password: At least one lower case character, At least one upper case character, At least one numeric character, At least one special character b) Length based check This check ensures that the length of the password is above the minimum value. If password complexity is enabled, MAS checks for the length of the password to be minimum four. The minimum password length is a configurable option in MAS. (Maximum length is 128) NOTE: This setting is applicable only for local users. To configure strong password, you need to enable password policy. Go to MAS UI and navigate to System module under User Administration. Select Password Policy and check the Enable Password Complexity checkbox. You may also choose to configure minimum password length.
2 2) Configure User Lockout Scenario One way to avoid hacking attempt is to configure a user lockout setting wherein based on the number of failed authentication attempts, a user is locked out of the system. The user remains locked out for a certain period of time which is configurable in system. Example: If a user has x invalid login attempts, then he will be locked out for y seconds. Default values are: 3 for invalid login attempts (maximum 10) and 30 seconds for user lockout interval NOTE: This setting is applicable only for local users.
3 To configure user lockout, Go to MAS UI and navigate to System module under User Administration. Select user lockout configuration and check the Enable User Lockout checkbox. You can then configure the Invalid Login Attempts and User Lockout Interval values 3) Configure Session Timeout This is particularly helpful to proactively prevent any unauthorized users from taking control of system if the session is unattended for long time. You can configure session timeout settings to ensure that a user is logged out if his session remains inactive/idle for x minutes. To configure session timeout, you can either do it at system level or per user level a) System level settings: Go to MAS UI and navigate to System module under System Administration. Select Change System Settings. In the next UI Enable checkbox Enable Session Timeout and input the values for session timeout. This setting will be applicable to all users.
4 b) User level settings: Go to MAS UI and navigate to System module under User Administration. Select User and click on Add button. In the next UI enable checkbox Configure Session Timeout and input the values for session timeout. This will be applicable to that specific user.
5
Passwords, PINs, and Authentication Rule Management
 Passwords, PINs, and Authentication Rule Management In Cisco Unity Connection, authentication rules govern user passwords, PINs, and account lockouts for all user accounts. We recommend that you define
Passwords, PINs, and Authentication Rule Management In Cisco Unity Connection, authentication rules govern user passwords, PINs, and account lockouts for all user accounts. We recommend that you define
Rev X 341. Table 111. Access Levels and Descriptions
 9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
View your employment information online!
 View your employment information online! Preferred Family Healthcare (PFH) offers a secure online environment for employees to view their pay stubs*, current benefit enrollments, and confirm personal information.
View your employment information online! Preferred Family Healthcare (PFH) offers a secure online environment for employees to view their pay stubs*, current benefit enrollments, and confirm personal information.
Security Management System Camera Configuration Axis IP Device (Stream Profile Support)
 Security Management System Camera Configuration Axis IP Device (Stream Profile Support) Introduction Security Management System software supports several video source makes and models. This includes IP
Security Management System Camera Configuration Axis IP Device (Stream Profile Support) Introduction Security Management System software supports several video source makes and models. This includes IP
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
Managing Security for the Analyst Software on Stand-alone Windows 7 Workstations Blair C. James, Patrick Quinn-Paquet
 WHITE PAPER Analyst Software Validation Service Managing Security for the Analyst Software on Stand-alone Windows 7 Workstations Blair C. James, Patrick Quinn-Paquet Managing Security for the Analyst Software
WHITE PAPER Analyst Software Validation Service Managing Security for the Analyst Software on Stand-alone Windows 7 Workstations Blair C. James, Patrick Quinn-Paquet Managing Security for the Analyst Software
Security Management System - Managing Infinova 307X NVR channels. Video display in Security Management System server software
 Security Management System - Managing Infinova 307X NVR channels This document describes steps to configure Infinova 307X NVR cameras in Security Management System software. Note Microsoft Visual C++ 2015
Security Management System - Managing Infinova 307X NVR channels This document describes steps to configure Infinova 307X NVR cameras in Security Management System software. Note Microsoft Visual C++ 2015
Secure Transfer Site (STS) User Manual
 Secure Transfer Site (STS) User Manual (Revised 3/1/12) Table of Contents Basic System Display Information... 3 Command Buttons with Text... 3 Data Entry Boxes Required / Enabled... 3 Connecting to the
Secure Transfer Site (STS) User Manual (Revised 3/1/12) Table of Contents Basic System Display Information... 3 Command Buttons with Text... 3 Data Entry Boxes Required / Enabled... 3 Connecting to the
Avaya Aura Communication Manager / Session Manager 6.3 Configuration Guide
 Valcom SIP devices can integrate with Avaya Aura Communication Manager and Avaya Aura Session Manager as SIP endpoints. Some devices are single-channel (using one SIP extension), while other devices can
Valcom SIP devices can integrate with Avaya Aura Communication Manager and Avaya Aura Session Manager as SIP endpoints. Some devices are single-channel (using one SIP extension), while other devices can
New Password Reset for Dental Connect Provider
 New Password Reset for Dental Connect Provider 1 INDEX Access Dental Connect for Providers:... 3 1. Username verification:... 4 1.1 user name not provided:... 5 1.2 Invalid user name:... 6 1.3 Invalid
New Password Reset for Dental Connect Provider 1 INDEX Access Dental Connect for Providers:... 3 1. Username verification:... 4 1.1 user name not provided:... 5 1.2 Invalid user name:... 6 1.3 Invalid
Family/Student Access Security Configuration
 Family/Student Access Security Configuration Security Configuration Student Login/Password Configuration Guardian Login/Password Configuration Security Configuration The Security Configuration allows you
Family/Student Access Security Configuration Security Configuration Student Login/Password Configuration Guardian Login/Password Configuration Security Configuration The Security Configuration allows you
Hearing Care Dashboard
 Hearing Care Dashboard Registration & Management Hearing Care Dashboard: Register and Manage Your Organization Hearing Care Anywhere is Starkey s remote programming system. The Hearing Care Dashboard is
Hearing Care Dashboard Registration & Management Hearing Care Dashboard: Register and Manage Your Organization Hearing Care Anywhere is Starkey s remote programming system. The Hearing Care Dashboard is
How to Integrate RSA SecurID with the Barracuda Web Application Firewall
 How to Integrate RSA SecurID with the Barracuda Web Application Firewall The Barracuda Web Application Firewall can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA
How to Integrate RSA SecurID with the Barracuda Web Application Firewall The Barracuda Web Application Firewall can be configured as a RADIUS client to the RSA SecurID Server System, comprised of the RSA
Managing the Mobility Express Network
 Under the Management tab on the navigation pane, an admin users can do the following: 1 Configure access to the Mobility Express controller 2 Manage Admin Accounts 3 Configure Time 4 Perform a Software
Under the Management tab on the navigation pane, an admin users can do the following: 1 Configure access to the Mobility Express controller 2 Manage Admin Accounts 3 Configure Time 4 Perform a Software
VISIONTRACKER FREQUENTLY ASKED QUESTIONS FAQ
 VISIONTRACKER FREQUENTLY ASKED QUESTIONS FAQ 1. FREQUENTLY ASKED QUESTIONS 1.1. TABLE OF CONTENTS 1. Frequently Asked Questions... 1 1.1. Table of Contents... 1 1.2. How to Open or Search for a Saved Application...
VISIONTRACKER FREQUENTLY ASKED QUESTIONS FAQ 1. FREQUENTLY ASKED QUESTIONS 1.1. TABLE OF CONTENTS 1. Frequently Asked Questions... 1 1.1. Table of Contents... 1 1.2. How to Open or Search for a Saved Application...
1. TABLE OF CONTENTS. 1. Table of Contents Guide Instructions Access Tririga Reset Your Password... 8
 Access TRIRIGA 1. TABLE OF CONTENTS 1. Table of Contents... 2 2. Guide Instructions... 3 2.1 Guide Instructions... 3 3. Access Tririga... 4 4. Reset Your Password... 8 4.1 Password Reset... 8 Version Date:
Access TRIRIGA 1. TABLE OF CONTENTS 1. Table of Contents... 2 2. Guide Instructions... 3 2.1 Guide Instructions... 3 3. Access Tririga... 4 4. Reset Your Password... 8 4.1 Password Reset... 8 Version Date:
AppScaler SSO Active Directory Guide
 Version: 1.0.3 Update: April 2018 XPoint Network Notice To Users Information in this guide is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
Version: 1.0.3 Update: April 2018 XPoint Network Notice To Users Information in this guide is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
McAfee Security Connected Integrating epo and MFECC
 McAfee Security Connected Integrating epo and MFECC Table of Contents Overview 3 User Accounts & Privileges 3 Prerequisites 3 Configuration Steps 3 Value Add 12 FOR INTERNAL AND CHANNEL USE ONLY Rev 1
McAfee Security Connected Integrating epo and MFECC Table of Contents Overview 3 User Accounts & Privileges 3 Prerequisites 3 Configuration Steps 3 Value Add 12 FOR INTERNAL AND CHANNEL USE ONLY Rev 1
Examples of Cisco APE Scenarios
 CHAPTER 5 This chapter describes three example scenarios with which to use Cisco APE: Access to Asynchronous Lines, page 5-1 Cisco IOS Shell, page 5-3 Command Authorization, page 5-5 Note For intructions
CHAPTER 5 This chapter describes three example scenarios with which to use Cisco APE: Access to Asynchronous Lines, page 5-1 Cisco IOS Shell, page 5-3 Command Authorization, page 5-5 Note For intructions
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
COINS OA Enhancement: User Security Enhancements
 Document Ref: OA_CE-SY003 (PDR 23235) Date: June 2, 2014 Document Version: 1.0 Modules Affected: System Earliest available version of COINS: COINS OA v11.01 Documentation Updated: This document may contain
Document Ref: OA_CE-SY003 (PDR 23235) Date: June 2, 2014 Document Version: 1.0 Modules Affected: System Earliest available version of COINS: COINS OA v11.01 Documentation Updated: This document may contain
W H IT E P A P E R. Salesforce Security for the IT Executive
 W HITEPAPER Salesforce Security for the IT Executive Contents Contents...1 Introduction...1 Background...1 Settings Related to Security and Compliance...1 Password Settings... 1 Session Settings... 2 Login
W HITEPAPER Salesforce Security for the IT Executive Contents Contents...1 Introduction...1 Background...1 Settings Related to Security and Compliance...1 Password Settings... 1 Session Settings... 2 Login
Release Notes Version 1.0.0
 Release Notes Version 1.0.0 Copyright 1991-2015 Ipswitch, Inc. All rights reserved. This document, as well as the software described in it, is furnished under license and may be used or copied only in
Release Notes Version 1.0.0 Copyright 1991-2015 Ipswitch, Inc. All rights reserved. This document, as well as the software described in it, is furnished under license and may be used or copied only in
Manual for configuring VPN in Windows 7
 Manual for configuring VPN in Windows 7 A. Installing the User Digital Signing Certificate (DSC) 1. Once your receive the DSC, please acknowledge it by replying it to the same email address to get the
Manual for configuring VPN in Windows 7 A. Installing the User Digital Signing Certificate (DSC) 1. Once your receive the DSC, please acknowledge it by replying it to the same email address to get the
Welcome (slide 1) Welcome to the Florida Department of Education Single Sign-On tutorial for hosted user login and navigation.
 LOGIN AND NAVIGATION FOR HOSTED USERS Welcome (slide 1) Welcome to the Florida Department of Education Single Sign-On tutorial for hosted user login and navigation. These tutorials are designed to provide
LOGIN AND NAVIGATION FOR HOSTED USERS Welcome (slide 1) Welcome to the Florida Department of Education Single Sign-On tutorial for hosted user login and navigation. These tutorials are designed to provide
Logging into LTC Instant Access the First Time
 Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu a. from the LTC website Current Students>Technology & Logins>LTC Instant Access Enter your
Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu a. from the LTC website Current Students>Technology & Logins>LTC Instant Access Enter your
USING THE CLOVIS ONCOLOGY IME/IIT PORTAL: FREQUENTLY ASKED QUESTIONS FAQ. Version 1.0
 USING THE CLOVIS ONCOLOGY IME/IIT PORTAL: FREQUENTLY ASKED QUESTIONS FAQ Version 1.0 1. FREQUENTLY ASKED QUESTIONS 1.1. TABLE OF CONTENTS 1. Frequently Asked Questions... 1 1.1. Table of Contents... 1
USING THE CLOVIS ONCOLOGY IME/IIT PORTAL: FREQUENTLY ASKED QUESTIONS FAQ Version 1.0 1. FREQUENTLY ASKED QUESTIONS 1.1. TABLE OF CONTENTS 1. Frequently Asked Questions... 1 1.1. Table of Contents... 1
SCP Embraer Supplier Guide
 SCP Embraer Supplier Guide Revised 1 Contents Introduction... 5 Getting Started... 5 How to Log In to SCP... 5 Steps to Complete First Time Login... 6 Steps to Log-in to SCP... 7 General Navigation and
SCP Embraer Supplier Guide Revised 1 Contents Introduction... 5 Getting Started... 5 How to Log In to SCP... 5 Steps to Complete First Time Login... 6 Steps to Log-in to SCP... 7 General Navigation and
The ADC Guide to Managing Hybrid (IT and DevOps) Application Delivery
 The ADC Guide to Managing Hybrid (IT and DevOps) Application Delivery Digital Transformation Is Changing the Way that Applications Are Managed and Delivered To meet the growing challenges of a competitive
The ADC Guide to Managing Hybrid (IT and DevOps) Application Delivery Digital Transformation Is Changing the Way that Applications Are Managed and Delivered To meet the growing challenges of a competitive
Understanding Admin Access and RBAC Policies on ISE
 Understanding Admin Access and RBAC Policies on ISE Contents Introduction Prerequisites Requirements Components Used Configure Authentication Settings Configure Admin Groups Configure Admin Users Configure
Understanding Admin Access and RBAC Policies on ISE Contents Introduction Prerequisites Requirements Components Used Configure Authentication Settings Configure Admin Groups Configure Admin Users Configure
Best Practices Benchmarking Application
 1 1. Introduction For the purposes of this user manual, all menu items are visible in all screen shots. Depending upon the users privileges, the user s menu option may vary from what is shown in the screen
1 1. Introduction For the purposes of this user manual, all menu items are visible in all screen shots. Depending upon the users privileges, the user s menu option may vary from what is shown in the screen
UT HEALTH SAN ANTONIO HANDBOOK OF OPERATING PROCEDURES
 ACCESS MANAGEMENT Policy UT Health San Antonio shall adopt access management processes to ensure that access to Information Resources is restricted to authorized users with minimal access rights necessary
ACCESS MANAGEMENT Policy UT Health San Antonio shall adopt access management processes to ensure that access to Information Resources is restricted to authorized users with minimal access rights necessary
VI. Corente Services Client
 VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide. Figure 9-1 Port Security Global Settings window
 9. Security DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide Port Security 802.1X AAA RADIUS TACACS IMPB DHCP Server Screening ARP Spoofing Prevention MAC Authentication Web-based
9. Security DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide Port Security 802.1X AAA RADIUS TACACS IMPB DHCP Server Screening ARP Spoofing Prevention MAC Authentication Web-based
How to autoprovision a NetScaler VPX on SDX for load balancing OpenStack workloads
 How to autoprovision a NetScaler VPX on SDX for load balancing OpenStack workloads Introduction The on demand consumption model has become a de facto standard in cloud computing. To support this model
How to autoprovision a NetScaler VPX on SDX for load balancing OpenStack workloads Introduction The on demand consumption model has become a de facto standard in cloud computing. To support this model
1. General Description... 2
 Created by Lindhoudt Harald Date of Creation May 12 th, 2010 Released by Glatz Klaus Date of Release May 21 st, 2010 TABLE OF CONTENT 1. General Description... 2 2. End-user Portal Services instructions...
Created by Lindhoudt Harald Date of Creation May 12 th, 2010 Released by Glatz Klaus Date of Release May 21 st, 2010 TABLE OF CONTENT 1. General Description... 2 2. End-user Portal Services instructions...
Registration and Login
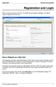 Registration and Login When a parent accesses txconnect, the following Login page is displayed. The parent needs to register as a new user. How to Register as a New User The registration process is self-administered,
Registration and Login When a parent accesses txconnect, the following Login page is displayed. The parent needs to register as a new user. How to Register as a New User The registration process is self-administered,
Dialog Box Displaying the VPN Connection Status.
 By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
AVID Reports. User Manager
 AVID Reports User Manager Table of Contents Overview... 3 User Manager Features... 4 Application Toolbar...4 Add New User...4 Export to Excel...4 Help...4 User Account List...4 Sorting...4 Editing...4
AVID Reports User Manager Table of Contents Overview... 3 User Manager Features... 4 Application Toolbar...4 Add New User...4 Export to Excel...4 Help...4 User Account List...4 Sorting...4 Editing...4
OAM 2FA Value-Added Module (VAM) Deployment Guide
 OAM 2FA Value-Added Module (VAM) Deployment Guide Copyright Information 2018. SecureAuth is a copyright of SecureAuth Corporation. SecureAuth s IdP software, appliances, and other products and solutions,
OAM 2FA Value-Added Module (VAM) Deployment Guide Copyright Information 2018. SecureAuth is a copyright of SecureAuth Corporation. SecureAuth s IdP software, appliances, and other products and solutions,
VISIONTRACKER FREQUENTLY ASKED QUESTIONS FAQ
 VISIONTRACKER FREQUENTLY ASKED QUESTIONS FAQ FREQUENTLY ASKED QUESTIONS 1.1. TABLE OF CONTENTS 1. Frequently Asked Questions... 1 1.1. Table of Contents... 1 1.2. How to View or Open a Saved Application...
VISIONTRACKER FREQUENTLY ASKED QUESTIONS FAQ FREQUENTLY ASKED QUESTIONS 1.1. TABLE OF CONTENTS 1. Frequently Asked Questions... 1 1.1. Table of Contents... 1 1.2. How to View or Open a Saved Application...
Configuring Administrator Usernames and Passwords. Information About Configuring Administrator Usernames and Passwords
 Configuring Administrator Usernames and Passwords, on page 1 Creating a Lobby Ambassador Account, on page 2 Configuring Guest User Accounts, on page 5 Password Policies, on page 6 Configuring Administrator
Configuring Administrator Usernames and Passwords, on page 1 Creating a Lobby Ambassador Account, on page 2 Configuring Guest User Accounts, on page 5 Password Policies, on page 6 Configuring Administrator
CAQH Solutions TM EnrollHub TM Provider User Guide Chapter 5 Manage Users. Table of Contents
 CAQH Solutions TM EnrollHub TM Provider User Guide Chapter 5 Manage Users Table of Contents 5 MANAGE USERS 2 5.1 PROVIDER USER ROLES 3 5.2 ADD NEW USERS 3 5.3 EDIT EXISTING USERS 5 5.4 DELETE EXISTING
CAQH Solutions TM EnrollHub TM Provider User Guide Chapter 5 Manage Users Table of Contents 5 MANAGE USERS 2 5.1 PROVIDER USER ROLES 3 5.2 ADD NEW USERS 3 5.3 EDIT EXISTING USERS 5 5.4 DELETE EXISTING
Grandstream Networks, Inc. UCM6100 Security Manual
 Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Introduction. Overview of HCM. HCM Dashboard CHAPTER
 CHAPTER 1 This chapter describes the Hosted Collaboration Mediation (HCM) software. It includes: Overview of HCM, page 1-1 Terminology Used in HCM, page 1-2 HCM Dashboard Architecture, page 1-3 Starting
CHAPTER 1 This chapter describes the Hosted Collaboration Mediation (HCM) software. It includes: Overview of HCM, page 1-1 Terminology Used in HCM, page 1-2 HCM Dashboard Architecture, page 1-3 Starting
Read the following information carefully, before you begin an upgrade.
 Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
Credential Policy CHAPTER
 CHAPTER 21 Cisco Unified Communications Manager authenticates user login credentials before allowing system access. To help secure user accounts, you can specify settings for failed logon attempts, lockout
CHAPTER 21 Cisco Unified Communications Manager authenticates user login credentials before allowing system access. To help secure user accounts, you can specify settings for failed logon attempts, lockout
WISE-580x Data Logger Application Example
 WISE-580x Data Logger Application Example Scenario: In a factory wastewater water level monitoring application, a WISE-5800 is connected to an I-7012FD module, the AI channel 0 of this module is connected
WISE-580x Data Logger Application Example Scenario: In a factory wastewater water level monitoring application, a WISE-5800 is connected to an I-7012FD module, the AI channel 0 of this module is connected
FINANCIAL INFORMATION FORUM 5 Hanover Square New York, New York 10004
 FINANCIAL INFORMATION FORUM 5 Hanover Square New York, New York 10004 212-422-8568 Via Electronic Delivery August 3, 2018 Mr. Vas Rajan Chief Information Security Officer ThesysCAT, LLC 1740 Broadway New
FINANCIAL INFORMATION FORUM 5 Hanover Square New York, New York 10004 212-422-8568 Via Electronic Delivery August 3, 2018 Mr. Vas Rajan Chief Information Security Officer ThesysCAT, LLC 1740 Broadway New
Change My Password User Guide
 Help Desk Password Reset Instructions IT Operation Dallas County Support Community College Services Change My Password User Guide Version: 1.0 Release Date: 8/5/2018 Information Technology Operation Support
Help Desk Password Reset Instructions IT Operation Dallas County Support Community College Services Change My Password User Guide Version: 1.0 Release Date: 8/5/2018 Information Technology Operation Support
Securing Privileged Access and the SWIFT Customer Security Controls Framework (CSCF)
 Securing Privileged Access and the SWIFT Customer Security Controls Framework (CSCF) A Guide to Leveraging Privileged Account Security to Assist with SWIFT CSCF Compliance Table of Contents Executive Summary...
Securing Privileged Access and the SWIFT Customer Security Controls Framework (CSCF) A Guide to Leveraging Privileged Account Security to Assist with SWIFT CSCF Compliance Table of Contents Executive Summary...
Using the vrealize Orchestrator Operations Client. vrealize Orchestrator 7.5
 Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Using the vrealize Orchestrator Operations Client vrealize Orchestrator 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
VMware Skyline Collector Installation and Configuration Guide. VMware Skyline 1.4
 VMware Skyline Collector Installation and Configuration Guide VMware Skyline 1.4 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
VMware Skyline Collector Installation and Configuration Guide VMware Skyline 1.4 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Level 3 - Bechtel Internal & Select External Distribution Reston t bechtel.com 1 INFRASTRUCTURE MINING & METALS
 INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS ServiceNow Password Reset Portal Effective February 7, 2017, the functionality to unlock your Bechtel network account
INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS ServiceNow Password Reset Portal Effective February 7, 2017, the functionality to unlock your Bechtel network account
Architecture Assessment Case Study. Single Sign on Approach Document PROBLEM: Technology for a Changing World
 Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
vrealize Suite Lifecycle Manager 1.0 Installation and Management vrealize Suite 2017
 vrealize Suite Lifecycle Manager 1.0 Installation and Management vrealize Suite 2017 vrealize Suite Lifecycle Manager 1.0 Installation and Management You can find the most up-to-date technical documentation
vrealize Suite Lifecycle Manager 1.0 Installation and Management vrealize Suite 2017 vrealize Suite Lifecycle Manager 1.0 Installation and Management You can find the most up-to-date technical documentation
User Management in Resource Manager
 CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
ForeScout CounterACT. Configuration Guide. Version 4.1
 ForeScout CounterACT Network Module: VPN Concentrator Plugin Version 4.1 Table of Contents About the VPN Concentrator Plugin... 3 What to Do... 3 Requirements... 3 CounterACT Requirements... 3 Supported
ForeScout CounterACT Network Module: VPN Concentrator Plugin Version 4.1 Table of Contents About the VPN Concentrator Plugin... 3 What to Do... 3 Requirements... 3 CounterACT Requirements... 3 Supported
MyPatientVisit Patient Portal User Guide
 Table of Contents Patient Setup and Login to the Patient Portal...2 Patient Registration... 2 Security Questions... 3 Patient Portal Dashboard...4 Patient s Dashboard... 4 Patient Documents in mydocuments
Table of Contents Patient Setup and Login to the Patient Portal...2 Patient Registration... 2 Security Questions... 3 Patient Portal Dashboard...4 Patient s Dashboard... 4 Patient Documents in mydocuments
erequest Frequently Asked Questions
 Which browsers work with? The following browsers are compatible with version 3.5. Internet Explorer version 8 Internet Explorer version 9 Firefox (Mozilla) Chrome (version 28) Safari (prior to version
Which browsers work with? The following browsers are compatible with version 3.5. Internet Explorer version 8 Internet Explorer version 9 Firefox (Mozilla) Chrome (version 28) Safari (prior to version
NetScaler Analysis and Reporting. Goliath for NetScaler Installation Guide v4.0 For Deployment on VMware ESX/ESXi
 NetScaler Analysis and Reporting Goliath for NetScaler Installation Guide v4.0 For Deployment on VMware ESX/ESXi (v4.0) Document Date: October 2016 www.goliathtechnologies.com 1 Legal Notices Goliath for
NetScaler Analysis and Reporting Goliath for NetScaler Installation Guide v4.0 For Deployment on VMware ESX/ESXi (v4.0) Document Date: October 2016 www.goliathtechnologies.com 1 Legal Notices Goliath for
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
Volante NACHA ISO20022 Validator AMI User Guide
 Volante NACHA ISO20022 Validator AMI User Guide 1. About Volante NACHA ISO20022 Validator AMI User Guide This document is referenced in the REST Services Deployment Guide. This outlines the available REST
Volante NACHA ISO20022 Validator AMI User Guide 1. About Volante NACHA ISO20022 Validator AMI User Guide This document is referenced in the REST Services Deployment Guide. This outlines the available REST
Forescout. Configuration Guide. Version 4.2
 Forescout Version 4.2 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 4.2 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Introduction to Personal Computers Using Windows 8 Course 01 - Getting to Know PCs and the Windows 8 User Interface
 Introduction to Personal Computers Using Windows 8 Course 01 - Getting to Know PCs and the Windows 8 User Interface Slide 1 Course 01: Getting to Know PCs and the Windows 8 User Interface Identify Components
Introduction to Personal Computers Using Windows 8 Course 01 - Getting to Know PCs and the Windows 8 User Interface Slide 1 Course 01: Getting to Know PCs and the Windows 8 User Interface Identify Components
Updating Astea Mobile URLs
 Updating Astea Mobile URLs Table of Contents UPDATING THE ASTEA APPLICATION SERVER URL... 4 RESETTING YOUR PASSWORD UPON INITIAL LOGIN... 7 CHANGING YOUR PASSWORD... 10 ACCESSING THE UPDATED TRAINING MATERIALS...
Updating Astea Mobile URLs Table of Contents UPDATING THE ASTEA APPLICATION SERVER URL... 4 RESETTING YOUR PASSWORD UPON INITIAL LOGIN... 7 CHANGING YOUR PASSWORD... 10 ACCESSING THE UPDATED TRAINING MATERIALS...
MyTeleMed iphone User Guide
 Table of Contents Log In 2 Incorrect Login Information 2 Registering your iphone 2 Main Menu 3 Messages 3 Compose a New Message 4 Message Recipients 4 Archiving Messages 4 Message Detail 5 Add Comments
Table of Contents Log In 2 Incorrect Login Information 2 Registering your iphone 2 Main Menu 3 Messages 3 Compose a New Message 4 Message Recipients 4 Archiving Messages 4 Message Detail 5 Add Comments
Web and MAC Authentication
 3 Web and MAC Authentication Contents Overview..................................................... 3-2 Client Options.............................................. 3-3 General Features............................................
3 Web and MAC Authentication Contents Overview..................................................... 3-2 Client Options.............................................. 3-3 General Features............................................
Application Note. Using RADIUS with G6 Devices
 Using RADIUS with G6 Devices MICROSENS GmbH & Co. KG Küferstr. 16 59067 Hamm/Germany Tel. +49 2381 9452-0 FAX +49 2381 9452-100 E-Mail info@microsens.de Web www.microsens.de Summary This Application Note
Using RADIUS with G6 Devices MICROSENS GmbH & Co. KG Küferstr. 16 59067 Hamm/Germany Tel. +49 2381 9452-0 FAX +49 2381 9452-100 E-Mail info@microsens.de Web www.microsens.de Summary This Application Note
Greenville CSD Parent Guide to SchoolTool
 Accessing your student s on-line SchoolTool school records is now a simple matter. There are several things that need to be done to begin this process. 1. Send your email address to us Your current email
Accessing your student s on-line SchoolTool school records is now a simple matter. There are several things that need to be done to begin this process. 1. Send your email address to us Your current email
Key File Generation. November 14, NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171
 Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
PowerTeacher Administrator User Guide. PowerTeacher Gradebook
 PowerTeacher Gradebook Released June 2011 Document Owner: Documentation Services This edition applies to Release 2.3 of the PowerTeacher Gradebook software and to all subsequent releases and modifications
PowerTeacher Gradebook Released June 2011 Document Owner: Documentation Services This edition applies to Release 2.3 of the PowerTeacher Gradebook software and to all subsequent releases and modifications
Login Instructions for Falck MyCare
 Login Instructions for Falck MyCare Because of the new General Data Protection Regulation (GDPR) on the protection of personal data, we have upgraded our Falck MyCare booking system to a newer and safer
Login Instructions for Falck MyCare Because of the new General Data Protection Regulation (GDPR) on the protection of personal data, we have upgraded our Falck MyCare booking system to a newer and safer
End User Password Self Service Procedures
 End User Password Self Service Procedures End User Password Self Service Procedures Page 1 of 19 Document Information Name: Author: Phone#: Email ID: End User Password Self Service Procedures Corporate
End User Password Self Service Procedures End User Password Self Service Procedures Page 1 of 19 Document Information Name: Author: Phone#: Email ID: End User Password Self Service Procedures Corporate
PROCESS AUTOMATION. MANUAL VisuNet Control Center Version 4.1
 PROCESS AUTOMATION MANUAL VisuNet Control Center Version 4.1 With regard to the supply of products, the current issue of the following document is applicable: The General Terms of Delivery for Products
PROCESS AUTOMATION MANUAL VisuNet Control Center Version 4.1 With regard to the supply of products, the current issue of the following document is applicable: The General Terms of Delivery for Products
MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017
 MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017 General Contents General... 3 1 Requirements... 4 1.1 Citrix client... 4 1.2 Citrix NetScaler (Access Gateway) plugin... 4 1.3 SMS Passcode...
MYPLACE USER GUIDE User Guide for myplace.hexagon.com March 08, 2017 General Contents General... 3 1 Requirements... 4 1.1 Citrix client... 4 1.2 Citrix NetScaler (Access Gateway) plugin... 4 1.3 SMS Passcode...
Configuring Communication Services
 This chapter includes the following sections: Configuring HTTP, on page 1 Configuring SSH, on page 2 Configuring XML API, on page 3 Enabling Redfish, on page 3 Configuring IPMI, on page 4 Configuring SNMP,
This chapter includes the following sections: Configuring HTTP, on page 1 Configuring SSH, on page 2 Configuring XML API, on page 3 Enabling Redfish, on page 3 Configuring IPMI, on page 4 Configuring SNMP,
Digital Certificate Service (DCS) - User Guide
 Digital Certificate Service (DCS) - User Guide Information Security Branch Contents Using this Guide... 3 User Requirements... 3 Secure E-mail Messaging... 4 Send a Secure E-mail Message... 4 Receive a
Digital Certificate Service (DCS) - User Guide Information Security Branch Contents Using this Guide... 3 User Requirements... 3 Secure E-mail Messaging... 4 Send a Secure E-mail Message... 4 Receive a
Configuration of Microsoft SQL Server Express
 Configuration of Microsoft SQL Server Express Copyright 2017 NetSupport Ltd All rights reserved Configuration of Microsoft SQL Server Express and NetSupport DNA Installation Requirements If installing
Configuration of Microsoft SQL Server Express Copyright 2017 NetSupport Ltd All rights reserved Configuration of Microsoft SQL Server Express and NetSupport DNA Installation Requirements If installing
Citrix Receiver for Universal Windows Platform
 Citrix Receiver for Universal Windows Platform Jul 18, 2017 Citrix Receiver for Universal Windows Platform (UWP) is client software available for download from the Microsoft store. It enables users to
Citrix Receiver for Universal Windows Platform Jul 18, 2017 Citrix Receiver for Universal Windows Platform (UWP) is client software available for download from the Microsoft store. It enables users to
Using the AETA Remote Access service
 Using the AETA Remote Access service 1. Background AETA codecs can all be controlled via an IP interface, and for instance a computer can easily take control over a codec when it is connected on the same
Using the AETA Remote Access service 1. Background AETA codecs can all be controlled via an IP interface, and for instance a computer can easily take control over a codec when it is connected on the same
Security. 9.1 User IDs and Security Levels. 9.2 User Privileges and Policies CHAPTER
 9 CHAPTER This chapter provides information about Cisco ONS 15454 users and security. To provision security, refer to the Cisco ONS 15454 Procedure Guide. Chapter topics include: 9.1 User IDs and Levels,
9 CHAPTER This chapter provides information about Cisco ONS 15454 users and security. To provision security, refer to the Cisco ONS 15454 Procedure Guide. Chapter topics include: 9.1 User IDs and Levels,
Joomla User Guide Ver 3
 LiveHelp Server Joomla User Guide Ver 3 Introduction The process of configuration and implementation of the LiveHelp server is divided into four stages, which are detailed below. The approximate time of
LiveHelp Server Joomla User Guide Ver 3 Introduction The process of configuration and implementation of the LiveHelp server is divided into four stages, which are detailed below. The approximate time of
VPN/RDP Laptop and Workstation Usage instructions:
 VPN/RDP Laptop and Workstation Usage instructions: This document details how to use the laptops and workstations provided to users which connect to the secure NEST environment using VPN connectivity. Note
VPN/RDP Laptop and Workstation Usage instructions: This document details how to use the laptops and workstations provided to users which connect to the secure NEST environment using VPN connectivity. Note
Introduction. CloudIQ Overview. CloudIQ Requirements. Customer Registers at support.emc.com
 Introduction This Quick-Start Guide describes how CloudIQ can be enabled, and used with, any number of SC Series storage systems. Onboarding is the process of finding compatible CloudIQ systems, configuring
Introduction This Quick-Start Guide describes how CloudIQ can be enabled, and used with, any number of SC Series storage systems. Onboarding is the process of finding compatible CloudIQ systems, configuring
Commonfund Client Reporting Portal
 Commonfund Single Sign On Help Effective Tuesday, February 18, 2014, Commonfund has implemented a new, single sign-on login that provides enhanced security and flexibility in managing your login credentials.
Commonfund Single Sign On Help Effective Tuesday, February 18, 2014, Commonfund has implemented a new, single sign-on login that provides enhanced security and flexibility in managing your login credentials.
Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard
 Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure
Ensuring Desktop Central Compliance to Payment Card Industry (PCI) Data Security Standard Introduction Manage Engine Desktop Central is part of ManageEngine family that represents entire IT infrastructure
AT&T Business Messaging Account Management
 Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
NETCONF Client GUI. Client Application Files APPENDIX
 APPENDIX B The NETCONF client is a simple GUI client application that can be used to understand the implementation of the NETCONF protocol in Cisco E-DI. This appendix includes the following information:
APPENDIX B The NETCONF client is a simple GUI client application that can be used to understand the implementation of the NETCONF protocol in Cisco E-DI. This appendix includes the following information:
Security in Confirmit Software - Individual User Settings
 Security in Confirmit Software - Individual User Settings Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 1 of 5 1 Using HTTPS in Confirmit Horizons SSL certificates are installed for
Security in Confirmit Software - Individual User Settings Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 1 of 5 1 Using HTTPS in Confirmit Horizons SSL certificates are installed for
User Guide for the Key s Client Portal
 User Guide for the Key s Client Portal The Client portal is one of a series of enhancements enabling Advisers to interact with their Clients securely and remotely. This deployment offers a Client interface
User Guide for the Key s Client Portal The Client portal is one of a series of enhancements enabling Advisers to interact with their Clients securely and remotely. This deployment offers a Client interface
Cisco NAC Profiler UI User Administration
 CHAPTER 14 Topics in this chapter include: Overview, page 14-1 Managing Cisco NAC Profiler Web User Accounts, page 14-2 Enabling RADIUS Authentication for Cisco NAC Profiler User Accounts, page 14-7 Changing
CHAPTER 14 Topics in this chapter include: Overview, page 14-1 Managing Cisco NAC Profiler Web User Accounts, page 14-2 Enabling RADIUS Authentication for Cisco NAC Profiler User Accounts, page 14-7 Changing
Google 2 factor authentication User Guide
 Google 2 factor authentication User Guide Description: Updated Date: This guide describes how to setup Two factor authentication for your Google account. March, 2018 Summary ITSC is pleased to launch Two
Google 2 factor authentication User Guide Description: Updated Date: This guide describes how to setup Two factor authentication for your Google account. March, 2018 Summary ITSC is pleased to launch Two
Avaya Integrated Management Release User Administration User Guide
 Avaya Integrated Management Release 4.0.1 User Administration User Guide 14-601847 Issue 1 June 2007 2007 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information
Avaya Integrated Management Release 4.0.1 User Administration User Guide 14-601847 Issue 1 June 2007 2007 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information
Tennessee Technological University Policy No Password Management
 Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Security Management System Central Monitoring Station with Push Mode Connectivity
 Security Management System Central Monitoring Station with Push Mode Connectivity Introduction Security Management System supports distributed deployment architecture, which involves (a) Central Monitoring
Security Management System Central Monitoring Station with Push Mode Connectivity Introduction Security Management System supports distributed deployment architecture, which involves (a) Central Monitoring
Print Audit 5 - Step by Step Walkthrough
 Print Audit 5 - Step by Step Walkthrough IMPORTANT: READ THIS BEFORE PERFORMING A PRINT AUDIT 5 INSTALLATION Print Audit 5 is a desktop application that you must install on every computer where you want
Print Audit 5 - Step by Step Walkthrough IMPORTANT: READ THIS BEFORE PERFORMING A PRINT AUDIT 5 INSTALLATION Print Audit 5 is a desktop application that you must install on every computer where you want
E mail Setup Guide for Microsoft Outlook 2002, 2003 & 2007
 E mail Setup Guide for Microsoft Outlook 2002, 2003 & 2007 Summary of Settings Incoming mail server (POP3): mail.everythinggraphic.com Outgoing mail server (SMTP): mail.everythinggraphic.com Important:
E mail Setup Guide for Microsoft Outlook 2002, 2003 & 2007 Summary of Settings Incoming mail server (POP3): mail.everythinggraphic.com Outgoing mail server (SMTP): mail.everythinggraphic.com Important:
GARMCO E-Tendering System Guideline
 Gulf Aluminium Rolling Mill Company GARMCO E-Tendering System Guideline Frequently Asked Questions How to Login to the E-Tendering System?... 2 How to Recover Your Password?... 3 How to Register to the
Gulf Aluminium Rolling Mill Company GARMCO E-Tendering System Guideline Frequently Asked Questions How to Login to the E-Tendering System?... 2 How to Recover Your Password?... 3 How to Register to the
New Jersey Department of the Treasury Division of Purchase and Property
 New Jersey Department of the Treasury Division of Purchase and Property Quick Reference Guide: LOGIN/PASSWORD ASSISTANCE Seller Administrators Rev. 3/12/2018 12:37 PM Table of Contents 1. Purpose... 3
New Jersey Department of the Treasury Division of Purchase and Property Quick Reference Guide: LOGIN/PASSWORD ASSISTANCE Seller Administrators Rev. 3/12/2018 12:37 PM Table of Contents 1. Purpose... 3
