What s really new in Windows 10?
|
|
|
- Julia Day
- 5 years ago
- Views:
Transcription
1 Sami Laiho Senior Technical Fellow, MVP Adminize.com / Win-fu.com sami@adminize.com What s really new in Windows 10? Configuration Manager
2 Forgive my English When most get Administrator or Spanish get Administrador we get JÄRJESTELMÄNVALVOJA
3 Sami Laiho Senior Technical Fellow adminize.com IT Admin since 1996 MCT since 2001 (MCT Regional Lead Finland) MVP in Windows OS since 2011 Specializes in and trains: Troubleshooting Security Centralized Management Active Directory Hacking Penetration testing Social Engineering Trophies: Ignite 2015 Best male presenter ;) (#2 out of 1000 speakers) TechEd Europe 2014 Best session TechEd North America Best session, Best speaker TechEd Australia Best session, Best speaker TechEd Europe Best Session by an external speaker
4 AMAZING!!!! A Start-Menu!!! (NOW WITH 2048 things!!) Virtual Desktops!!! Running applications in Windows!!! A transparent Command Prompt!!!
5 Last Windows Windows 7 and 10 are good options Windows 8? Windows 8.1? If your customer says they are not going to Windows 10 they are lying Sami Laiho Windows RT?
6 Windows RT Windows 10 upgrade
7 Upgrade is recommended Until now it has always been a less recommended way to upgrade and has always said to result in poor performance compared to a clean install You can opt out or delay the adoption Long Time Servicing Branch This is part of a bigger picture: Flight upgrades Home users forced to use Windows Update Windows Update for Business
8 DEMO Upgrade Settings
9 Provision packages Transform a purchased OEM-installed PC to an Enterprise device Trying to make CYOD easier Windows Phone has an Enterprise-version so I hope this works
10 Fixed ConHost.exe
11 DEMO Conhost.exe
12 Biometrics No more passwords! Two-factor authentication for everyone! First factor to be Biometrics, PIN, face recognition Smartcards and other physical tokens are easily forgotten so let s use something that s easier to remember to take with you Your computers TPM Windows 10 phone Windows Hello and Windows Passport
13 DEMO Windows Hello
14
15 New Store and Universal Apps Only way to make Windows fly in the current world of devices is to make the Store work Only way to make the Store work is to make the developers happy with it and get more apps in it Two phases: 1. Emulation for ios and Android apps, and support for App-V packages 2. Make the store more sexy and appealing to devs Xbox plays a crucial role in this Volume licensing, reusable licenses and Azure AD authentication are a must
16 Azure AD Path to here Windows 7 Domain Windows Microsoft Account Windows 10 + Azure AD -account Windows 10 is the first OS really connected to Azure AAD should be called Azure Authentication Services (for now at least) Sami Laiho
17 MDM InTune, SCCM and 3rd party supported better than before Not only for BYOD anymore Three scenarios
18 Hardware features Windows Hello and RealSense 3D Cameras DirectX 12 Wireless Charging Software Guard Extensions (SGX) _81_SGX_DL_100_small.pdf USB Type C and USB 3.1 ThunderBolt 3.0 (40Gbps Two daisy-chained 4K displays)
19 Hardware features Intel Skylake enhancements Keyword spotter algorithm WiGig technology, which can transfer data at 7Gbps DDR4 memory, which will improve internal data transfer between memory, processor and other components SIMD.js for Edge Single Instruction, Multiple Data (SIMD) CPU Speed Shift (30ms 1ms) Sensor Hub Image Signal Processor
20 DEMO CPU Shift
21 Continuum
22 Virtual memory size and ASLR 22
23 IOMMU I/O Memory Management Unit MMU for devices, as opposed to processors Where an MMU translates virtual to physical addresses for a CPU accessing your system's memory, an IOMMU translates virtual to physical addresses for devices Hardware based protection against DMA-access Protects against buggy drivers and malicious code Works with SLAT Makes sure a device or VM won t have access to physical memory addresses not meant for them Known as: Intel VT-d / AMD-Vi
24 Memory Compression 24
25 To fit a new page old might need to be paged out TABLE PAGEFILE NEW PAGE
26 Compress the pages TABLE
27 Compressed pages on a table TABLE
28 Compressed pages on a table TABLE
29 Memory Compression! SYSTEM-process (User Mode memory) Working set (RAM) Default Store Modified list Standby list Pagefile (Disk) Kernel Mode memory Free list
30 Device Drivers Microsoft Signatures to be REQUIRED for Windows 10 Kernel-Mode Drivers To distribute you will have to: Sign your driver package with your company s code signing certificate Login to the Microsoft Hardware Developer Portal Upload your signed driver package Agree to a few particulars Download the Microsoft signed files (within minutes) Why? driver signing is vulnerable to exploitation Bad guys have managed to steal certificates some have even managed to acquire code signing certs on their own
31 Device Guard
32 Isolated User Mode
33 Traditional Kernel Mode vs User Mode USER MODE KERNEL MODE
34 Normal and Secure mode NORMAL MODE SECURE MODE USER MODE ISOLATED USER MODE KERNEL SECURE KERNEL HYPERVISOR
35 Isolated User Mode Protects User Mode from the code in the Kernel Mode Normally Kernel has full visibility to User Mode processes memory
36 Secure Kernel IUM is on top of Secure Kernel (Secure System) Not a real Kernel but more a proxy that talks to the real Kernel but marshalls the transactions and does sanity checks Does not implement stuff that the normal kernel already does Secure Kernel cannot be extended like the normal Only accessible by Microsoft not 3rd party All CryptoCode, Challenge/Response is here so it stays private to the Virtual Secure Mode
37 Traditional Kernel Mode vs User Mode USER MODE ISOLATED USER MODE KERNEL MODE SHARED BUFFER (Masrshall) SECURE KERNEL HYPERVISOR
38 How come the Kernel is not able to access the memory of the Secure Kernel?
39 Traditional Virtual memory Process 0 PAGETABLE PROCESS 0 V-Address P-Address ACCESSMASK xxxx yyyy z-z-z x R-X Virtuall Address 6789? Process 1 PAGETABLE PROCESS 0 V-Address P-Address ACCESSMASK xxxx yyyy z-z-z x RW- Virtuall Address 6789?
40 Kernel has access to the Page Table so why wouldn t it have access to the memory?
41 Hypervisors and VMs PAGETABLE VM 1 GPA SPA ACCESSMASK xxxx yyyy z-z-z x R-X VIRTUAL RAM Physical Address? PAGETABLE VM 2 GPA SPA ACCESSMASK xxxx yyyy z-z-z x R-X VIRTUAL RAM Physical Address? SLAT
42 Kernel and Secure Kernel have their own SLAT s USER MODE ISOLATED USER MODE SLAT KERNEL MODE SHARED BUFFER (Masrshall) HYPERVISOR SECURE KERNEL SLAT
43 Hypervisors and VMs PAGETABLE KERNEL KERNEL GPA SPA ACCESSMASK x R - - SLAT SECURE KERNEL (VSM) VIRTUAL RAM SLAT PAGETABLE VSM GPA SPA ACCESSMASK x RWX VIRTUAL RAM
44 So what is VSM? Really? It s not really a VM but a functionality possible because of virtualization technology (Kind-Of-Semi-Almost-VM) This could be multiplied easily to many VMs
45 Enabling VSM bcdedit /set vsmlaunchtype auto
46 Trustlets Processes running in Virtual Secure Mode Currently not available for developers In the future anything that needs Secrets to stay secret Currently three trustlets LSAISO = Credential Guard vtpm = Virtual TPM HVCI = Kernel Mode Code Integrity If a trustlet shuts down all keys are gone and the secrets are safe
47 Device Guard Device Guard requires: UEFI Secure Boot with non-microsoft UEFI CA removed from the UEFI database. TPM 1.2 Virtualization support enabled by default in the system firmware (BIOS): Virtualization extensions (e.g., Intel VT-x, AMD RVI) SLAT (e.g., Intel EPT, AMD RVI) IOMMU (e.g., Intel VT-d, AMD-Vi) UEFI BIOS configured to prevent an unauthorized user from disabling Device Guard hardware security features. Kernel mode drivers must be Microsoft signed and compatible with hypervisorenforced code integrity. Windows 10 Enterprise only
48 DEMO Process Dump
49 Nested Virtualization 49
50 Containers Containers are a new level of virtualization I see it like App-V for Operating Systems Two different levels: Server Containers and Hyper-V Containers More info:
51 Server Containers USER MODE KERNEL MODE 51
52 Server Containers USER MODE (Windows Processes Appliacation Processes) CONTAINER USER MODE (Windows Processes Appliacation Processes) Memory Manager File System Device Drivers Scheduler, etc. KERNEL MODE 52
53 Hyper-V Containers Optimized Virtual Machine USER MODE (Windows Processes Appliacation Processes) Core Windows Processes CONTAINER USER MODE (Windows Processes Appliacation Processes) KERNEL MODE KERNEL MODE Hyper-V Hypervisor 53
54 Hyper-V inside of Hyper-V
55 Contact Blog: Free newsletter: GOj Websites: Video-based training: Later: NOW: Nächster Event: Freitag 17. Juni Digicomp Bern (begrenzte Anzahl Teilnehmer möglich)
Moving from Reactive to Proactive Security. Sami Laiho Adminize / Intility Senior Technical Fellow, MVP April 28 th New-York City
 Moving from Reactive to Proactive Security Sami Laiho Adminize / Intility Senior Technical Fellow, MVP April 28 th New-York City Thanks to our Organizers! Tome Tanasovski PowerShell MVP Blog: http://powertoe.wordpress.com/
Moving from Reactive to Proactive Security Sami Laiho Adminize / Intility Senior Technical Fellow, MVP April 28 th New-York City Thanks to our Organizers! Tome Tanasovski PowerShell MVP Blog: http://powertoe.wordpress.com/
How Windows Security Really Works?
 Sami Laiho Senior Technical Fellow, MVP Adminize.com / Win-fu.com sami@adminize.com BLOG.WIN-FU.COM @samilaiho How Windows Security Really Works? Configuration Manager Sami Laiho Senior Technical Fellow
Sami Laiho Senior Technical Fellow, MVP Adminize.com / Win-fu.com sami@adminize.com BLOG.WIN-FU.COM @samilaiho How Windows Security Really Works? Configuration Manager Sami Laiho Senior Technical Fellow
Windows 10 edition. Find out which. is right for you. Core features. Familar, and better than ever Home Pro Enterprise Education Mobile.
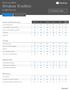 Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
BDPA Conference Windows 10
 BDPA Conference Windows 10 Tommy Patterson- Sr Technical Evangelist @tommy_patterson Do The you digital have economy what it takes to succeed? Are cybersecurity threats keeping you up at night? Your people
BDPA Conference Windows 10 Tommy Patterson- Sr Technical Evangelist @tommy_patterson Do The you digital have economy what it takes to succeed? Are cybersecurity threats keeping you up at night? Your people
Adminizer. Sami Laiho Senior Technical Fellow adminize.com
 Adminizer Sami Laiho Senior Technical Fellow adminize.com Why should I keep on reading? If you don t want to have to remember or change your local admin passwords If you don t want to give users permanent
Adminizer Sami Laiho Senior Technical Fellow adminize.com Why should I keep on reading? If you don t want to have to remember or change your local admin passwords If you don t want to give users permanent
Desktop features placemat
 Desktop features placemat Home Pro Enterprise Existing Differentiated Features in Win7 /Win8.1 Domain Join and Group Policy Management Existing Win7 / Win 8.1 Enterprise features Windows 10: Management
Desktop features placemat Home Pro Enterprise Existing Differentiated Features in Win7 /Win8.1 Domain Join and Group Policy Management Existing Win7 / Win 8.1 Enterprise features Windows 10: Management
benefits for customers with subscriptions in CSP
 Windows 10 upgrade benefits for customers with subscriptions in CSP Windows 10 upgrade benefits for customers Resources and guidance for organizations upgrading from Windows 7 and Windows 8/8.1 with subscriptions
Windows 10 upgrade benefits for customers with subscriptions in CSP Windows 10 upgrade benefits for customers Resources and guidance for organizations upgrading from Windows 7 and Windows 8/8.1 with subscriptions
How Shielded VMs Protect Your Data
 How Shielded VMs Protect Your Data Jan Marek MVP MCC MCT MCSE MCSD Head of CDM & marek@kpcs.cz Architect @ KPCS CZ www.atom.ms www.kpcs.cz www.janmarek.eu Traditional Security Services (AD, MSSQL, ShP)
How Shielded VMs Protect Your Data Jan Marek MVP MCC MCT MCSE MCSD Head of CDM & marek@kpcs.cz Architect @ KPCS CZ www.atom.ms www.kpcs.cz www.janmarek.eu Traditional Security Services (AD, MSSQL, ShP)
UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies
 GOLD PARTNER: Hlavní partner: Hlavní odborný partner: UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies Ing. Ondřej Ševeček GOPAS a.s. MCSM:Directory MVP:Security CISA CISM CEH CHFI ondrej@sevecek.com
GOLD PARTNER: Hlavní partner: Hlavní odborný partner: UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies Ing. Ondřej Ševeček GOPAS a.s. MCSM:Directory MVP:Security CISA CISM CEH CHFI ondrej@sevecek.com
HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER. New protection capabilities in Windows Server 2016
 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER New protection capabilities in Windows Server 2016 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT AND MICROSOFT CERTIFIED
HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER New protection capabilities in Windows Server 2016 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT AND MICROSOFT CERTIFIED
Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering. Key Threats Internet was just growing Mail was on the verge
 Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Use EMS to protect your mobile data and mobile app
 Use EMS to protect your mobile data and mobile app Peter Daalmans Senior Consultant, Enterprise Mobility MVP CTGlobal. pds@ctglobalservices.com PETER DAALMANS Enterprise Mobility MVP @ CTGlobal Blog: https://peterdaalmans.com
Use EMS to protect your mobile data and mobile app Peter Daalmans Senior Consultant, Enterprise Mobility MVP CTGlobal. pds@ctglobalservices.com PETER DAALMANS Enterprise Mobility MVP @ CTGlobal Blog: https://peterdaalmans.com
Online Resources. Compare Windows 10 Editions. Setup a device for anyone to use (Kiosk mode)
 Online Resources Compare Windows 10 Editions https://www.microsoft.com/en-us/windowsforbusiness/compare Setup a device for anyone to use (Kiosk mode) https://technet.microsoft.com/en-us/library/mt219050(v=vs.85).aspx
Online Resources Compare Windows 10 Editions https://www.microsoft.com/en-us/windowsforbusiness/compare Setup a device for anyone to use (Kiosk mode) https://technet.microsoft.com/en-us/library/mt219050(v=vs.85).aspx
Identity & Access Management
 Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
ASSURANCE CONTINUITY MAINTENANCE REPORT FOR. Microsoft Windows 10 IPsec VPN Client (VPNPP14)
 TM ASSURANCE CONTINUITY MAINTENANCE REPORT FOR Microsoft Windows 10 IPsec VPN Client (VPNPP14) Microsoft Windows 10 IPsec VPN Client (VPNPP14) Maintenance Report Number: CCEVS-VR-VID10753-2017a Date of
TM ASSURANCE CONTINUITY MAINTENANCE REPORT FOR Microsoft Windows 10 IPsec VPN Client (VPNPP14) Microsoft Windows 10 IPsec VPN Client (VPNPP14) Maintenance Report Number: CCEVS-VR-VID10753-2017a Date of
Backup, File Backup copies of individual files made in order to replace the original file(s) in case it is damaged or lost.
 Glossary A Active Directory a directory service that inventories, secures and manages the users, computers, rules and other components of a Microsoft Windows network. This service is typically deployed
Glossary A Active Directory a directory service that inventories, secures and manages the users, computers, rules and other components of a Microsoft Windows network. This service is typically deployed
WINDOWS 10 ENTERPRISE New Security Features
 WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
Installing and Configuring Windows 10 (698)
 Installing and Configuring Windows 10 (698) Implement Windows Prepare for installation requirements Determine hardware requirements and compatibility; choose between an upgrade and a clean installation;
Installing and Configuring Windows 10 (698) Implement Windows Prepare for installation requirements Determine hardware requirements and compatibility; choose between an upgrade and a clean installation;
Windows Devices. Device Capabilities. Premium. Entry
 Windows Devices $ Premium Entry Device Capabilities Windows 10 IoT $ Premium Windows 10 IoT Enterprise Desktop Shell, Win32 apps, Universal Windows Apps and Drivers 1 GB RAM, 16 GB Storage X86 Windows
Windows Devices $ Premium Entry Device Capabilities Windows 10 IoT $ Premium Windows 10 IoT Enterprise Desktop Shell, Win32 apps, Universal Windows Apps and Drivers 1 GB RAM, 16 GB Storage X86 Windows
Microsoft. MS-101 EXAM Microsoft 365 Mobility and Security. m/ Product: Demo File
 Page No 1 https://www.dumpsplanet.com m/ Microsoft MS-101 EXAM Microsoft 365 Mobility and Security Product: Demo File For More Information: MS-101-dumps Question: 1 Your company uses Windows Defender Advanced
Page No 1 https://www.dumpsplanet.com m/ Microsoft MS-101 EXAM Microsoft 365 Mobility and Security Product: Demo File For More Information: MS-101-dumps Question: 1 Your company uses Windows Defender Advanced
Hardening the Modern Windows Client Let s NOT break it this time
 Hardening the Modern Windows Client Let s NOT break it this time Raymond P.L. Comvalius Raymond Comvalius IT Infra Architect/Trainer MVP Windows IT Pro Zelfstandig sinds 1998 Agenda History of Hardening
Hardening the Modern Windows Client Let s NOT break it this time Raymond P.L. Comvalius Raymond Comvalius IT Infra Architect/Trainer MVP Windows IT Pro Zelfstandig sinds 1998 Agenda History of Hardening
Windows 10 Basics For Windows 7 and 8 users
 Windows 10 Basics For Windows 7 and 8 users Introduction Windows 7/Vista/XP users first need to read Windows 10 Primer, particularly to understand Apps, User Accounts & One Drive. See also the Hints &
Windows 10 Basics For Windows 7 and 8 users Introduction Windows 7/Vista/XP users first need to read Windows 10 Primer, particularly to understand Apps, User Accounts & One Drive. See also the Hints &
Avigilon Control Center Virtual Matrix User Guide
 Avigilon Control Center Virtual Matrix User Guide Version 5.0.2 PDF-ACCVM-A-Rev2 Copyright 2013 Avigilon. All rights reserved. The information presented is subject to change without notice. No copying,
Avigilon Control Center Virtual Matrix User Guide Version 5.0.2 PDF-ACCVM-A-Rev2 Copyright 2013 Avigilon. All rights reserved. The information presented is subject to change without notice. No copying,
Microsoft Windows Exam Objectives
 Microsoft Windows Exam 70-698 s The following correlates the objectives for Microsoft Windows Exam 70-698 (Installing and Configuring Windows 10) to the chapters and sections where they are covered in
Microsoft Windows Exam 70-698 s The following correlates the objectives for Microsoft Windows Exam 70-698 (Installing and Configuring Windows 10) to the chapters and sections where they are covered in
Virtual Pc Manual Windows Xp Mode Windows 7 Home Basic
 Virtual Pc Manual Windows Xp Mode Windows 7 Home Basic Microsoft distributes a Windows XP virtual machine called Windows XP Mode, which you can download if you're running Windows 7, as I explained earlier.
Virtual Pc Manual Windows Xp Mode Windows 7 Home Basic Microsoft distributes a Windows XP virtual machine called Windows XP Mode, which you can download if you're running Windows 7, as I explained earlier.
Operating System Security
 Operating System Security Operating Systems Defined Hardware: I/o...Memory.CPU Operating Systems: Windows or Android, etc Applications run on operating system Operating Systems Makes it easier to use resources.
Operating System Security Operating Systems Defined Hardware: I/o...Memory.CPU Operating Systems: Windows or Android, etc Applications run on operating system Operating Systems Makes it easier to use resources.
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
PLATFORM CONVERGENCE JOURNEY
 Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
Improve productivity with modernized PCs and Windows 10. Christopher Choong, DTM Field Marketing Manager
 Improve productivity with modernized PCs and Windows 10 Christopher Choong, DTM Field Marketing Manager Impressive innovation. Inside and out. 3 4 It s an important time to refresh Design Every product
Improve productivity with modernized PCs and Windows 10 Christopher Choong, DTM Field Marketing Manager Impressive innovation. Inside and out. 3 4 It s an important time to refresh Design Every product
Universal Windows Applications
 1 Universal Windows Applications From an IT Admin view Partner: 2 Roger Zander itnetx AG, Workplace Solutions Microsoft MVP: Enterprise Client Management Author: Client Center, Collection Commander, RuckZuck.
1 Universal Windows Applications From an IT Admin view Partner: 2 Roger Zander itnetx AG, Workplace Solutions Microsoft MVP: Enterprise Client Management Author: Client Center, Collection Commander, RuckZuck.
Fencing the Cloud. Roger Casals. Senior Director Product Management. Shared vision for the Identity: Fencing the Cloud 1
 Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Windows 10 Management Technologies: What s New. Michael Niehaus Senior Product Marketing Manager, Windows Microsoft
 Windows 10 Management Technologies: What s New Michael Niehaus Senior Product Marketing Manager, Windows Microsoft Business needs are evolving. Windows 10 offers to meet those needs. MANAGEMENT CHOICES
Windows 10 Management Technologies: What s New Michael Niehaus Senior Product Marketing Manager, Windows Microsoft Business needs are evolving. Windows 10 offers to meet those needs. MANAGEMENT CHOICES
Windows 10. scalable IT services & solutions. October 25, Bruce Ward, VP of Business Strategy. Dan Sharp, Senior Consultant
 Windows 10 October 25, 2018 Helping you grow your business with Bruce Ward, VP of Business Strategy scalable IT services & solutions Dan Sharp, Senior Consultant for today s challenges & tomorrow s vision.
Windows 10 October 25, 2018 Helping you grow your business with Bruce Ward, VP of Business Strategy scalable IT services & solutions Dan Sharp, Senior Consultant for today s challenges & tomorrow s vision.
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
Past, Present, and Future Justin Johnson Senior Principal Firmware Engineer
 Dell Firmware Security Past, Present, and Future Justin Johnson Senior Principal Firmware Engineer justin.johnson1@dell.com Dell Security 2 What does BIOS do? Configure and Test System Memory Configure
Dell Firmware Security Past, Present, and Future Justin Johnson Senior Principal Firmware Engineer justin.johnson1@dell.com Dell Security 2 What does BIOS do? Configure and Test System Memory Configure
Armoring your mobile workforce warriors for the 21st century
 Armoring your mobile workforce warriors for the 21st century with System Center Configuration Manager 2012 R2 --- Advanced Warfare --- Tim De Keukelaere Kenny Buntinx Feb 9 th 2015 About Kenny @KennyBuntinx
Armoring your mobile workforce warriors for the 21st century with System Center Configuration Manager 2012 R2 --- Advanced Warfare --- Tim De Keukelaere Kenny Buntinx Feb 9 th 2015 About Kenny @KennyBuntinx
Addendum. McAfee Virtual Advanced Threat Defense
 Addendum McAfee Virtual Advanced Threat Defense 3.10.2 COPYRIGHT 2017 Intel Corporation TRADEMARK ATTRIBUTIONS Intel and the Intel logo are registered trademarks of the Intel Corporation in the US and/or
Addendum McAfee Virtual Advanced Threat Defense 3.10.2 COPYRIGHT 2017 Intel Corporation TRADEMARK ATTRIBUTIONS Intel and the Intel logo are registered trademarks of the Intel Corporation in the US and/or
Co se změnilo ve Windows 10 z pohledu IT administrátora
 Co se změnilo ve Windows 10 z pohledu IT administrátora Kamil Roman MCSE: Mobility MCSE: Cloud Platform and Infrastructure MCSA MCITP MCT konzultace@kamilrt.net @KamilRT Agenda 1. Windows as a Service
Co se změnilo ve Windows 10 z pohledu IT administrátora Kamil Roman MCSE: Mobility MCSE: Cloud Platform and Infrastructure MCSA MCITP MCT konzultace@kamilrt.net @KamilRT Agenda 1. Windows as a Service
IVE Quick Startup Guide - OS 4.0
 IVE Quick Startup Guide - OS 4.0 Initial Setup Once you receive the IVE device, unpack the IVE and connect it to a PC or Laptop using the console (null modem) cable provided with the IVE. You have to connect
IVE Quick Startup Guide - OS 4.0 Initial Setup Once you receive the IVE device, unpack the IVE and connect it to a PC or Laptop using the console (null modem) cable provided with the IVE. You have to connect
Inside Windows 10. Howard Burpee
 Inside Windows 10 1 Why Windows 10? 7 ate 9 Too much code refers to Windows 9 Or 2 3 Due date In April, AMD s CEO, Lisa Su let slip that Windows 10 will be provided (to OEMs only?) by the end of July Microsoft
Inside Windows 10 1 Why Windows 10? 7 ate 9 Too much code refers to Windows 9 Or 2 3 Due date In April, AMD s CEO, Lisa Su let slip that Windows 10 will be provided (to OEMs only?) by the end of July Microsoft
MCSA Windows 10. A Success Guide to Prepare- Installing and Configuring Windows 10. edusum.com
 70-698 MCSA Windows 10 A Success Guide to Prepare- Installing and Configuring Windows 10 edusum.com Table of Contents Introduction to 70-698 Exam on Installing and Configuring Windows 10... 2 Microsoft
70-698 MCSA Windows 10 A Success Guide to Prepare- Installing and Configuring Windows 10 edusum.com Table of Contents Introduction to 70-698 Exam on Installing and Configuring Windows 10... 2 Microsoft
Spring 2017 :: CSE 506. Introduction to. Virtual Machines. Nima Honarmand
 Introduction to Virtual Machines Nima Honarmand Virtual Machines & Hypervisors Virtual Machine: an abstraction of a complete compute environment through the combined virtualization of the processor, memory,
Introduction to Virtual Machines Nima Honarmand Virtual Machines & Hypervisors Virtual Machine: an abstraction of a complete compute environment through the combined virtualization of the processor, memory,
Mobile Field Worker Security Advocate Series: Customer Conversation Guide. Research by IDC, 2015
 Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Windows 10 was it worth the wait? Clive G4NAQ
 Windows 10 was it worth the wait? Clive G4NAQ Windows 10 Preview Windows 10 was released over 6 months ago as a technical preview The general look and feel did not change significantly during the preview
Windows 10 was it worth the wait? Clive G4NAQ Windows 10 Preview Windows 10 was released over 6 months ago as a technical preview The general look and feel did not change significantly during the preview
Configuration Manager
 Wally Mead Product Owner / MVP Cireson Wally.mead@cireson.com @wally_mead Upgrading to System Center Configuration Manager Configuration Manager Today s Agenda Migrating from Configuration Manager 2007
Wally Mead Product Owner / MVP Cireson Wally.mead@cireson.com @wally_mead Upgrading to System Center Configuration Manager Configuration Manager Today s Agenda Migrating from Configuration Manager 2007
Keeping Current with Windows 10. Jon Anderson Senior Systems Consultant, Now Micro December 5 th, 2018
 Keeping Current with Windows 10 Jon Anderson Senior Systems Consultant, Now Micro December 5 th, 2018 Device Lifecycle Company Hardware Reseller (Dell, HP, Lenovo, and more) OEM (Digital Signage, Kiosks,
Keeping Current with Windows 10 Jon Anderson Senior Systems Consultant, Now Micro December 5 th, 2018 Device Lifecycle Company Hardware Reseller (Dell, HP, Lenovo, and more) OEM (Digital Signage, Kiosks,
Consultant since many years. Mainly working with defense and public sector. MCSE on Windows Server 2000 security ;-)
 About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
Windows ierīces Enterprise infrastruktūrā. Aris Dzērvāns Microsoft
 Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Citrix XenMobile and Windows 10
 White Paper Citrix XenMobile and Windows 10 Citrix XenMobile and Windows 10 With version 10, Windows has moved the once desktop operating system firmly into the era of the mobility and the cloud. Windows
White Paper Citrix XenMobile and Windows 10 Citrix XenMobile and Windows 10 With version 10, Windows has moved the once desktop operating system firmly into the era of the mobility and the cloud. Windows
TPM v.s. Embedded Board. James Y
 TPM v.s. Embedded Board James Y What Is A Trusted Platform Module? (TPM 1.2) TPM 1.2 on the Enano-8523 that: How Safe is your INFORMATION? Protects secrets from attackers Performs cryptographic functions
TPM v.s. Embedded Board James Y What Is A Trusted Platform Module? (TPM 1.2) TPM 1.2 on the Enano-8523 that: How Safe is your INFORMATION? Protects secrets from attackers Performs cryptographic functions
Windows 10 listening tour. What is REALLY on the minds of our customers?
 Windows 10 listening tour What is REALLY on the minds of our customers? What we are (really) hearing We need to adopt new technologies as fast as our customers No more big deployments Security is a top
Windows 10 listening tour What is REALLY on the minds of our customers? What we are (really) hearing We need to adopt new technologies as fast as our customers No more big deployments Security is a top
What s new in System Center Configuration Manager Current Branch? Ievgen Liashov
 What s new in System Center Configuration Manager Current Branch? Ievgen Liashov http://liashov.com http://en.liashov.com admin@sccm.com.ua Introduction IT engineer at METSYS, Paris 14 years experience
What s new in System Center Configuration Manager Current Branch? Ievgen Liashov http://liashov.com http://en.liashov.com admin@sccm.com.ua Introduction IT engineer at METSYS, Paris 14 years experience
Protecting Keys/Secrets in Network Automation Solutions. Dhananjay Pavgi, Tech Mahindra Ltd Srinivasa Addepalli, Intel
 Protecting Keys/Secrets in Network Automation Solutions Dhananjay Pavgi, Tech Mahindra Ltd Srinivasa Addepalli, Intel Agenda Introduction Private Key Security Secret Management Tamper Detection Summary
Protecting Keys/Secrets in Network Automation Solutions Dhananjay Pavgi, Tech Mahindra Ltd Srinivasa Addepalli, Intel Agenda Introduction Private Key Security Secret Management Tamper Detection Summary
IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP
 IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP North America Latin America Europe 877.224.8077 info@coalfire.com coalfire.com Coalfire sm and CoalfireOne sm are registered service
IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP North America Latin America Europe 877.224.8077 info@coalfire.com coalfire.com Coalfire sm and CoalfireOne sm are registered service
One Ring to Rule them All
 One Ring to Rule them All A primer on virtualization enhanced security @SimonCrosby Co-founder & CTO Introduction We use micro-virtualization to secure endpoints We serve enterprises and government agencies
One Ring to Rule them All A primer on virtualization enhanced security @SimonCrosby Co-founder & CTO Introduction We use micro-virtualization to secure endpoints We serve enterprises and government agencies
About the XenClient Enterprise Solution
 About the XenClient Enterprise Solution About the XenClient Enterprise Solution About the XenClient Enterprise Solution XenClient Enterprise is a distributed desktop virtualization solution that makes
About the XenClient Enterprise Solution About the XenClient Enterprise Solution About the XenClient Enterprise Solution XenClient Enterprise is a distributed desktop virtualization solution that makes
What s New in Hyper-V 2016/1709/1803/2019
 What s New in Hyper-V 2016/1709/1803/2019 Jan Marek Head of CDM & ATOM Architect @ KPCS CZ MVP: Cloud and Datacenter Management MCC MCT MCSE marek@kpcs.cz www.atom.ms Agenda SAC vs. LTSC Hyper-V and System
What s New in Hyper-V 2016/1709/1803/2019 Jan Marek Head of CDM & ATOM Architect @ KPCS CZ MVP: Cloud and Datacenter Management MCC MCT MCSE marek@kpcs.cz www.atom.ms Agenda SAC vs. LTSC Hyper-V and System
CONFIGURING BASIC MACOS MANAGEMENT: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE
 GUIDE FEBRUARY 2019 PRINTED 26 FEBRUARY 2019 CONFIGURING BASIC MACOS MANAGEMENT: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience
GUIDE FEBRUARY 2019 PRINTED 26 FEBRUARY 2019 CONFIGURING BASIC MACOS MANAGEMENT: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience
Bromium: Virtualization-Based Security
 Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
INFLUENTIAL OPERATING SYSTEM RESEARCH: SECURITY MECHANISMS AND HOW TO USE THEM CARSTEN WEINHOLD
 Faculty of Computer Science Institute of Systems Architecture, Operating Systems Group INFLUENTIAL OPERATING SYSTEM RESEARCH: SECURITY MECHANISMS AND HOW TO USE THEM CARSTEN WEINHOLD OVERVIEW Fundamental
Faculty of Computer Science Institute of Systems Architecture, Operating Systems Group INFLUENTIAL OPERATING SYSTEM RESEARCH: SECURITY MECHANISMS AND HOW TO USE THEM CARSTEN WEINHOLD OVERVIEW Fundamental
Use Microsoft EMS. to Protect your Mobile Data and Mobile Apps. Chris Nackers Nackers Consulting
 Use Microsoft EMS to Protect your Mobile Data and Mobile Apps Chris Nackers http://chrisnackers.com chris@nackersconsulting.com Nackers Consulting Peter Daalmans http://configmgrblog.com, peter@daalmans.com
Use Microsoft EMS to Protect your Mobile Data and Mobile Apps Chris Nackers http://chrisnackers.com chris@nackersconsulting.com Nackers Consulting Peter Daalmans http://configmgrblog.com, peter@daalmans.com
Leveraging Azure Services for a Scalable Windows Remote Desktop Deployment
 WEBINAR Leveraging Azure Services for a Scalable Windows Remote Desktop Deployment May 16 2018 About Me 18+ years in IT Blog at www.ciraltos.com, Twitter @ciraltos Work at Bowman and Brooke LLP as IT Infrastructure
WEBINAR Leveraging Azure Services for a Scalable Windows Remote Desktop Deployment May 16 2018 About Me 18+ years in IT Blog at www.ciraltos.com, Twitter @ciraltos Work at Bowman and Brooke LLP as IT Infrastructure
Virginia Western Community College ITN 110 Client Operating System (Windows 10)
 ITN 110 Client Operating System (Windows 10) Prerequisites Co-requisite: TEL 150 Course Description Covers installation, configuration, administration, management, maintenance, and troubleshooting of the
ITN 110 Client Operating System (Windows 10) Prerequisites Co-requisite: TEL 150 Course Description Covers installation, configuration, administration, management, maintenance, and troubleshooting of the
MCSA Windows 10. A Success Guide to Prepare- Microsoft Configuring Windows Devices. edusum.com
 70-697 MCSA Windows 10 A Success Guide to Prepare- Microsoft Configuring Windows Devices edusum.com Table of Contents Introduction to 70-697 Exam on Microsoft Configuring Windows Devices... 2 Microsoft
70-697 MCSA Windows 10 A Success Guide to Prepare- Microsoft Configuring Windows Devices edusum.com Table of Contents Introduction to 70-697 Exam on Microsoft Configuring Windows Devices... 2 Microsoft
Avigilon Control Center Virtual Matrix User Guide. Version 5.4.2
 Avigilon Control Center Virtual Matrix User Guide Version 5.4.2 2006-2014 Avigilon Corporation. All rights reserved. Unless expressly granted in writing, no license is granted with respect to any copyright,
Avigilon Control Center Virtual Matrix User Guide Version 5.4.2 2006-2014 Avigilon Corporation. All rights reserved. Unless expressly granted in writing, no license is granted with respect to any copyright,
The PKI Lie. The OWASP Foundation Attacking Certificate Based Authentication. OWASP & WASC AppSec 2007 Conference
 The PKI Lie Attacking Certificate Based Authentication Ofer Maor CTO, Hacktics OWASP & WASC AppSec 2007 Conference San Jose Nov 2007 Copyright 2007 - The OWASP Foundation Permission is granted to copy,
The PKI Lie Attacking Certificate Based Authentication Ofer Maor CTO, Hacktics OWASP & WASC AppSec 2007 Conference San Jose Nov 2007 Copyright 2007 - The OWASP Foundation Permission is granted to copy,
Kolding June 12, 2018
 Windows 10 for IoT solutions Dmitry Teteruk Cloud Solution Architect Kolding June 12, 2018 #IoTinActionMS Core aspects of the Internet of Things Devices Analytics Data Connectivity EDGE AND CLOUD COMPUTING
Windows 10 for IoT solutions Dmitry Teteruk Cloud Solution Architect Kolding June 12, 2018 #IoTinActionMS Core aspects of the Internet of Things Devices Analytics Data Connectivity EDGE AND CLOUD COMPUTING
Windows Server 2012 Top Ten
 Who am I? 11 Time Microsoft MVP Author of the Windows FAQ Senior Contributing Editor for Windows IT Pro magazine Latest book available Microsoft Virtualization Secrets Speaker at Tech Ed, Windows Connections
Who am I? 11 Time Microsoft MVP Author of the Windows FAQ Senior Contributing Editor for Windows IT Pro magazine Latest book available Microsoft Virtualization Secrets Speaker at Tech Ed, Windows Connections
How Parallels RAS Enhances Microsoft RDS. White Paper Parallels Remote Application Server
 How Parallels RAS Enhances Microsoft RDS White Paper Parallels Remote Application Server Table of Contents Introduction... 3 Overview of Microsoft Remote Desktop Services... 3 Microsoft RDS Pain Points...
How Parallels RAS Enhances Microsoft RDS White Paper Parallels Remote Application Server Table of Contents Introduction... 3 Overview of Microsoft Remote Desktop Services... 3 Microsoft RDS Pain Points...
GSE/Belux Enterprise Systems Security Meeting
 MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
Business Whitepaper. Windows 10 considerations for adoption
 Windows 10 considerations for adoption Table of contents Management highlights 1 A new continuous release model 1 Applications written once for any device 4 Security is different why it matters 5 Operations
Windows 10 considerations for adoption Table of contents Management highlights 1 A new continuous release model 1 Applications written once for any device 4 Security is different why it matters 5 Operations
WHITE PAPER Migrating to Windows 10: a practical guide
 WHITE PAPER Migrating to Windows 10: a practical guide Look before you leap Things to consider before migrating to Windows 10 2 There s a bunch of good reasons to migrate all the Windowsdevices in your
WHITE PAPER Migrating to Windows 10: a practical guide Look before you leap Things to consider before migrating to Windows 10 2 There s a bunch of good reasons to migrate all the Windowsdevices in your
HP Manageability Integration Kit HP Client Management Solutions
 HP Manageability Integration Kit HP Client Management Solutions July 2018 925167-004 Table of contents 1 Overview... 10 2 System requirements... 11 2.1 Supported Microsoft System Center Configuration Manager
HP Manageability Integration Kit HP Client Management Solutions July 2018 925167-004 Table of contents 1 Overview... 10 2 System requirements... 11 2.1 Supported Microsoft System Center Configuration Manager
Azure RemoteApp Past, present & future Let s talk ARA use cases!
 Azure RemoteApp Past, present & future Let s talk ARA use cases! Freek Berson Wortell RDSGurus.com Microsoft RDS MVP @fberson Themicrosoftplatform.net Dr. Benny Tritsch DrTritsch.com RDSGurus.com Microsoft
Azure RemoteApp Past, present & future Let s talk ARA use cases! Freek Berson Wortell RDSGurus.com Microsoft RDS MVP @fberson Themicrosoftplatform.net Dr. Benny Tritsch DrTritsch.com RDSGurus.com Microsoft
Windows 10 and the Enterprise. Craig A. Brown Prepared for: GMIS
 Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Secure access to your enterprise. Enforce risk-based conditional access in real time
 Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
9 Years in Consulting. Broad experience in Microsoft Infrastructure solutions. Specialised in Windows 10 & Surface familly
 About 9 Years in Consulting Broad experience in Microsoft Infrastructure solutions Specialised in Windows 10 & Surface familly We know Windows XP Windows 7 wasn t easy It often took between 3-7 years!
About 9 Years in Consulting Broad experience in Microsoft Infrastructure solutions Specialised in Windows 10 & Surface familly We know Windows XP Windows 7 wasn t easy It often took between 3-7 years!
Various editions of Windows 7
 Various editions of Windows 7 ( and their relationship to Windows Vista and XP) Windows 7 Windows Vista Windows XP Starter 1 Starter Starter Home Basic Basic Home Edition Home Premium Home Premium Media
Various editions of Windows 7 ( and their relationship to Windows Vista and XP) Windows 7 Windows Vista Windows XP Starter 1 Starter Starter Home Basic Basic Home Edition Home Premium Home Premium Media
Six Myths of Windows RT Revealed!
 Si Myths of Windows RT Revealed! Si Myths of Windows RT Revealed! There has been a lot of (mis)information being circulated about capabilities of Windows RT, the new Microsoft tablet operating system for
Si Myths of Windows RT Revealed! Si Myths of Windows RT Revealed! There has been a lot of (mis)information being circulated about capabilities of Windows RT, the new Microsoft tablet operating system for
Allan Hirt Cluster MVP
 Allan Hirt Cluster MVP E-mail: allan@sqlha.com Website: http://www.sqlha.com Blog: http://www.sqlha.com/blog Twitter: SQLHA Hypervisor This is what allows you to run other operating systems under your
Allan Hirt Cluster MVP E-mail: allan@sqlha.com Website: http://www.sqlha.com Blog: http://www.sqlha.com/blog Twitter: SQLHA Hypervisor This is what allows you to run other operating systems under your
How I Learned to Stop Worrying and Love the Internet of Things
 SESSION ID: SSC-W07 How I Learned to Stop Worrying and Love the Internet of Things Steven Sprague CEO Rivetz Corp @skswave The Big Shift Known Networks Ports Firewalls Packets SSL Known Devices Identity
SESSION ID: SSC-W07 How I Learned to Stop Worrying and Love the Internet of Things Steven Sprague CEO Rivetz Corp @skswave The Big Shift Known Networks Ports Firewalls Packets SSL Known Devices Identity
Windows 10 Why start migrating now!
 Windows 10 Why start migrating now! Piet Carpentier Senior IT Consultant Xylos About Me Piet Carpentier Sr IT Consultant Email : Piet.carpentier@xylos.com Twitter: @dafter LinkedIn: https://be.linkedin.com/in/pcarpentier
Windows 10 Why start migrating now! Piet Carpentier Senior IT Consultant Xylos About Me Piet Carpentier Sr IT Consultant Email : Piet.carpentier@xylos.com Twitter: @dafter LinkedIn: https://be.linkedin.com/in/pcarpentier
W11 Hyper-V security. Jesper Krogh.
 W11 Hyper-V security Jesper Krogh jesper_krogh@dell.com Jesper Krogh Speaker intro Senior Solution architect at Dell Responsible for Microsoft offerings and solutions within Denmark Specialities witin:
W11 Hyper-V security Jesper Krogh jesper_krogh@dell.com Jesper Krogh Speaker intro Senior Solution architect at Dell Responsible for Microsoft offerings and solutions within Denmark Specialities witin:
Microsoft Installing and Configuring Windows 10.
 Microsoft 70-698 Installing and Configuring Windows 10 http://killexams.com/pass4sure/exam-detail/70-698 QUESTION: 121 In this section, you will see one or more sets of questions with the same scenario
Microsoft 70-698 Installing and Configuring Windows 10 http://killexams.com/pass4sure/exam-detail/70-698 QUESTION: 121 In this section, you will see one or more sets of questions with the same scenario
Windows 2000 Flavors Windows 200 ws 0 Profess 0 P ional Windows 2000 Server Windows 200 ws 0 Advan 0 A ced Server Windows 2000 Datacen ter Server 2
 Copyright 2006 Heathkit Company, Inc. All Rights Reserved Lab 9-3 Windows 2000 Pre-Installation Windows 2000 Flavors Windows 2000 Professional Windows 2000 Server Windows 2000 Advanced Server Windows 2000
Copyright 2006 Heathkit Company, Inc. All Rights Reserved Lab 9-3 Windows 2000 Pre-Installation Windows 2000 Flavors Windows 2000 Professional Windows 2000 Server Windows 2000 Advanced Server Windows 2000
Edge Device Manager R15 Release Notes
 2017-03 Software releases are created to add new features, make enhancements or correct defects. These releases are tested on all current, actively shipping platforms and operating systems as applicable.
2017-03 Software releases are created to add new features, make enhancements or correct defects. These releases are tested on all current, actively shipping platforms and operating systems as applicable.
WORKPLACE Data Leak Prevention: Keeping your sensitive out of the public domain. Frans Oudendorp Ronny de Jong
 Data Leak Prevention: Keeping your sensitive out of the public domain Frans Oudendorp Ronny de Jong Session objectives & takeaways Session objectives: Overview of information protection solutions How to
Data Leak Prevention: Keeping your sensitive out of the public domain Frans Oudendorp Ronny de Jong Session objectives & takeaways Session objectives: Overview of information protection solutions How to
Consulting Solutions WHITE PAPER Citrix XenDesktop XenApp Planning Guide: Virtualization Best Practices
 Consulting Solutions WHITE PAPER Citrix XenDesktop XenApp Planning Guide: Virtualization Best Practices www.citrix.com Overview Desktop virtualization comprises of many different types of virtual desktops.
Consulting Solutions WHITE PAPER Citrix XenDesktop XenApp Planning Guide: Virtualization Best Practices www.citrix.com Overview Desktop virtualization comprises of many different types of virtual desktops.
Man-In-The-Browser Attacks. Daniel Tomescu
 Man-In-The-Browser Attacks Daniel Tomescu 1 About me Work and education: Pentester @ KPMG Romania Moderator @ Romanian Security Team MSc. Eng. @ University Politehnica of Bucharest OSCP, CREST CRT Interests:
Man-In-The-Browser Attacks Daniel Tomescu 1 About me Work and education: Pentester @ KPMG Romania Moderator @ Romanian Security Team MSc. Eng. @ University Politehnica of Bucharest OSCP, CREST CRT Interests:
INTEGRATING WITH DELL CLIENT COMMAND SUITE: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE
 GUIDE SEPTEMBER 2018 PRINTED 4 MARCH 2019 INTEGRATING WITH DELL CLIENT COMMAND SUITE: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience
GUIDE SEPTEMBER 2018 PRINTED 4 MARCH 2019 INTEGRATING WITH DELL CLIENT COMMAND SUITE: VMWARE WORKSPACE ONE OPERATIONAL TUTORIAL VMware Workspace ONE Table of Contents Overview Introduction Purpose Audience
ABOUT ZEPCAM SOFTWARE INSTALLATION MANAGEMENT AND BACKUPS. Description What is it Installation requirement Server requirement
 1 ABOUT ZEPCAM SOFTWARE Description What is it Installation requirement Server requirement INSTALLATION Create a bootable USB Networking Disk partitioning Bootloader configuration Setup Registration Administrator
1 ABOUT ZEPCAM SOFTWARE Description What is it Installation requirement Server requirement INSTALLATION Create a bootable USB Networking Disk partitioning Bootloader configuration Setup Registration Administrator
Big and Bright - Security
 Big and Bright - Security Big and Bright Security Embedded Tech Trends 2018 Does this mean: Everything is Big and Bright our security is 100% effective? or There are Big security concerns but Bright solutions?
Big and Bright - Security Big and Bright Security Embedded Tech Trends 2018 Does this mean: Everything is Big and Bright our security is 100% effective? or There are Big security concerns but Bright solutions?
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
Hardening with Hardware
 Hardening with Hardware How Windows is using hardware to improve security David dwizzzle Weston Device Security Group Manager Microsoft, Windows and Devices is not a security boundary Security boundaries
Hardening with Hardware How Windows is using hardware to improve security David dwizzzle Weston Device Security Group Manager Microsoft, Windows and Devices is not a security boundary Security boundaries
GLOBALPROTECT. Key Usage Scenarios and Benefits. Remote Access VPN Provides secure access to internal and cloud-based business applications
 GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
Authentication Technology for a Smart eid Infrastructure.
 Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Lecture 44 Blockchain Security I (Overview)
 Blockchains Architecture, Design and Use Cases Prof. Sandip Chakraborty Prof. Praveen Jayachandran Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 44 Blockchain
Blockchains Architecture, Design and Use Cases Prof. Sandip Chakraborty Prof. Praveen Jayachandran Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 44 Blockchain
Hands-On Lab. Windows Azure Virtual Machine Roles. Lab version: Last updated: 12/14/2010. Page 1
 Hands-On Lab Windows Azure Virtual Machine Roles Lab version: 2.0.0 Last updated: 12/14/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: CREATING AND DEPLOYING A VIRTUAL MACHINE ROLE IN WINDOWS AZURE...
Hands-On Lab Windows Azure Virtual Machine Roles Lab version: 2.0.0 Last updated: 12/14/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: CREATING AND DEPLOYING A VIRTUAL MACHINE ROLE IN WINDOWS AZURE...
SECURE OFFICE OF THE FUTURE
 ** SECURE OFFICE OF THE FUTURE HP Today Powering 430 of the Global Fortune 500 Companies Working with 250,000+ Channel Partners 18,000+ patents 2 PCs & 1 Printer ship every second HP Business Personal
** SECURE OFFICE OF THE FUTURE HP Today Powering 430 of the Global Fortune 500 Companies Working with 250,000+ Channel Partners 18,000+ patents 2 PCs & 1 Printer ship every second HP Business Personal
Avigilon Control Center Virtual Matrix User Guide
 Avigilon Control Center Virtual Matrix User Guide Version 5.2 PDF-ACCVM-B-Rev1 2013-2014 Avigilon Corporation. All rights reserved. Unless expressly granted in writing, no license is granted with respect
Avigilon Control Center Virtual Matrix User Guide Version 5.2 PDF-ACCVM-B-Rev1 2013-2014 Avigilon Corporation. All rights reserved. Unless expressly granted in writing, no license is granted with respect
