Lecture 6. Lecturer: Ronitt Rubinfeld Scribes: Chen Ziv, Eliav Buchnik, Ophir Arie, Jonathan Gradstein
|
|
|
- Blaise Hart
- 5 years ago
- Views:
Transcription
1 Subliear Time Algorithms November, 0 Lecture 6 Lecturer: Roitt Rubifeld Scribes: Che Ziv, Eliav Buchik, Ophir Arie, Joatha Gradstei Lesso overview. Usig the oracle reductio framework for approximatig the size of maximal matchigs (ad vertex covers) i a subliear umber of queries.. Implemetatio of the oracle.. Approximatig the average degree of a graph. Vertex cover approximatio usig Maximal matchig Cotiuig our effort from the last lecture to compute the vertex cover of a graph by simulatig a distributed algorithm we will try get a approximatio usig the graph maximal matchig.. Maximal matchig.. Matchig Matchig (M) of a graph G = (V, E) is a set of such that o two edges share a commo vertex... Maximal VS Maximum Maximal matchig (M M) is a matchig that caot be icreased without violatig the matchig. Maximum matchig is a matchig with maximum umber of edges. Example cosider the followig graph 0 Possible maximal matchig (red edges) 0 Possible maximum matchig (red edges) 0. Relatio betwee vertex cover ad M M Remider: V C is a set of vertices such that each edge of the graph is icidet to at least oe vertex of the set. V C MM : (u, v) MM at least u or v is i the V C (defiitio of V C). Sice the edges i the MM do t share a vertex it is clear that V C MM V C MM : We will create a V C from the MM. (u, v) MM we will add u, v to the V C. Oce we fiished
2 costructig the V C if exists a edge (u, v ) that is ot covered by the V C the we could have added this edge to the MM without violatig the Matchig cotradictig the assumptio of MM. We costructed a V C of size MM thus the optimal is less tha that. Assumig we ca compute the MM we get a approximatio to the V C. The algorithm that we will see will fid a approximatio to the MM i sub liear time thus yieldig a approximatio to the V C.. Greedy M M algorithm Data: G = (V, E) Result: M M ; for (u, v) E do if u or v is matched the M M (u, v) ed ed Algorithm : Maximal matchig algorithm Claim. M is a maximal matchig Proof: Lets assume that exists a edge e = (u, v) such that e / M ad {e} M is a matchig. Lets simulate the algorithm up to the poit that the algorithm ecouters the edge, sice M {e} is a matchig the algorithm will add the edge to M with cotradictio to the assumptio.. Oracle reductio framework Assume that we are give a oracle O such that give a edge e the oracle outputs "YES" if e MM ad "NO" else. Give that we have such a oracle we ca build a sub liear algorithm to estimate the MM. Data: G = (V, E), O Result: estimate of MM S 8 ɛ odes sampled iid; v S, defie X v ; for v S do if w N(v) such that O((v, w)) = "YES" the X v = else X v = 0 ed ed Output (( Xv S )) + ɛ ; Algorithm : Maximal matchig algorithm Claim. The expected output of the algorithm is MM + ɛ Proof: E[ X v ] = E[X v ] E[X v ] = S E[X v ] We sample iid the odes from the graph thus the probability of samplig a ode i the maximal matchig is MM. S E[X v ] = S MM
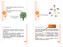
3 Plugig the result to the output of the algorithm E[(( S E[ X v )) S + ɛ )] = X v ] + ɛ = S E[ X v ] + ɛ S MM + ɛ S = MM + ɛ.. Boudig the error probability X v are idetically distributed Beroulli radom variables with p = MM probability > e ɛ S (p ɛ) S < X v < (p + ɛ) S therefore by Hoeffdig s iequality with ( MM ɛ) S < Takig S to be 0 ɛ yields that with probability > Sice the algorithm adds a additioal ɛ MM ɛ < S X v < ( MM + ɛ) S X v < MM + ɛ to the output result MM < S This completes the error boudig of the algorithm. Implemetatio of the oracle X v < MM + ɛ Remark. Give a order o the edges of the graph, the greedy sequetial algorithm for maximal matchig (defied earlier) determiistically outputs a uique maximal matchig. Defiitio. Give a order o the edges, the depedecy chai of edge e is the set of all adjacet edges to e that precede it i the order. Note that i the greedy sequetial algorithm, the decisio whether to iclude a edge i the matchig or ot depeds oly o the depedecy chai of this edge. Hece to implemet a oracle O M we ca cosider oly the depedecy chai of the queried edge ad check recursively whether the depedecy chai edges are i the matchig. The problem with this approach is that the depedecy chais ca be very log: Figure : Example for two differet rakigs that result i log depedecy chais. Note that i both cases i order to determie whether the edge marked e belogs to M the algorithm must recursively check all edges precedig it i the rakig To overcome the difficulty of log depedecy chais, we assig a radom orderig (rakig) to the edges. Formally, defie the rakig as r : E [0, ). We also assume edges have distict rakigs: e, e E, r(e) r(e ).
4 We ll see later that with this radom order the expected size of the depedecy chais is ot too log. The implemetatio of the oracle is as follows: Iput : A edge e ad rakig r : E [0, ) Output: "Yes" if e M ad "No" otherwise for every edge e adjacet to e do if r(e ) < r(e) the recursively ru this algorithm o e ; if received that e M the retur "No"; ed ed ed retur "Yes"; Algorithm : Oracle for determiig whether e M The correctess of this algorithm follows directly from the correctess of the greedy algorithm. Figure is a example of a executio of the algorithm. Claim. The expected umber of queries performed by the oracle algorithm is O( O(d) ). Corollary. The total query complexity of the algorithm usig this oracle is O( O(d) ɛ ) Proof of claim. For each e E cosider the tree of queries that are recursively called by the algorithm. The root of this tree is e, ad the childre of each ode i the tree are its adjacet edges (we allow edges to appear several times i the tree). By the algorithm, the paths i the tree that are explored are mootoe decreasig i rakig. Give a. The values of the edges are chose i.i.d from r : E [0, ). Therefore, each permutatio of the k + edges occurs with equal probability. Oly oe of these permutatios (r gives distict values for each edge) is mootoe decreasig, which meas that: path of legth k (correspodig to k + edges) the probability that it is mootoe decreasig is (k+)! P r[a path of legth k is explored] = (k + )! Every edge has up to d eighbors, so the umber of odes i the k-th level of the tree is bouded by (d) k. Therefore: which implies that: E[# of paths explored at distace k] E[total # of edges explored] k=0 (d)k (k + )! (d) k (k + )! ed d For each ode we must check all of its eighbors (of which there may be d), so the expected sample complexity of the oracle algorithm is bouded by: which is of course also O( O(d) ), as eeded. d E[total # of edges explored] = O(e d ) Remark. Our algorithm uses O() samples i the worst case. We ca boud the sample complexity by forcibly cuttig off the oracle (ad outputtig radomly) after it has used c O(d) samples for some costat c, which by Markov s iequality will esure that there is a low probability of this happeig, ad hece a low probability of error. Remark. There are some recet improvemets to this algorithm that have almost liear sample complexity i d.
5 Figure : The oracle will determie whether the edge 0. (bolded) is part of the maximal matchig. We ll cosider all its adjacet edges: this edge comes after 0., so we ll skip it we ll check it recursively: this edge comes after 0., so we ll skip it this edge comes after 0., so we ll skip it. 0. is part of the maximal matchig. 0. is part of the maximal matchig so 0. is t part of the maximal matchig we ll check it recursively: this edge comes after 0., so we ll skip it we ll check it recursively: this edge comes after 0., so we ll skip it this edge comes after 0., so we ll skip it. 0. is part of the maximal matchig. 0. is part of the maximal matchig so 0. is t part of the maximal matchig.. All the adjacet edges of 0. are t part of the maximal matchig, therefore 0. is part of the maximal matchig. Approximatig average degree For a give graph G, we would like to approximate the average degree, which is defied to be d = We will make several assumptios:. G is a simple graph: it does ot cotai multiple edges or loops.. G is ot "ultraspare", meaig: E = m = Ω(). v V d(v).. Our model is slightly differet to the graph model see before, which will allow us to make stroger queries: (a) Degree queries: retur d(v) for iput vertex v. (b) Neighbor queries: for iput vertex v ad idex j, retur the j-th eighbor of v.
6 A attempt at a aive solutio Radomly choose v,..., v s vertices, ad output s s i= d(v i). The problem with this approach is that for certai iput graphs the variace ca be very high. Cosider for example the star graph o vertices, where oe vertex has eighbors ad all the rest have oe eighbor. The average degree is which approaches. However, ay sample that we choose that does t happe to cotai the ceter will retur a estimate of, which is a bad multiplicative error. This allow us to coclude that we must make Ω() queries for this approach to be effective. I the ext lecture, we ll see a subliear algorithm for approximatig the average degree. 6
Big-O Analysis. Asymptotics
 Big-O Aalysis 1 Defiitio: Suppose that f() ad g() are oegative fuctios of. The we say that f() is O(g()) provided that there are costats C > 0 ad N > 0 such that for all > N, f() Cg(). Big-O expresses
Big-O Aalysis 1 Defiitio: Suppose that f() ad g() are oegative fuctios of. The we say that f() is O(g()) provided that there are costats C > 0 ad N > 0 such that for all > N, f() Cg(). Big-O expresses
condition w i B i S maximum u i
 ecture 10 Dyamic Programmig 10.1 Kapsack Problem November 1, 2004 ecturer: Kamal Jai Notes: Tobias Holgers We are give a set of items U = {a 1, a 2,..., a }. Each item has a weight w i Z + ad a utility
ecture 10 Dyamic Programmig 10.1 Kapsack Problem November 1, 2004 ecturer: Kamal Jai Notes: Tobias Holgers We are give a set of items U = {a 1, a 2,..., a }. Each item has a weight w i Z + ad a utility
Big-O Analysis. Asymptotics
 Big-O Aalysis 1 Defiitio: Suppose that f() ad g() are oegative fuctios of. The we say that f() is O(g()) provided that there are costats C > 0 ad N > 0 such that for all > N, f() Cg(). Big-O expresses
Big-O Aalysis 1 Defiitio: Suppose that f() ad g() are oegative fuctios of. The we say that f() is O(g()) provided that there are costats C > 0 ad N > 0 such that for all > N, f() Cg(). Big-O expresses
Combination Labelings Of Graphs
 Applied Mathematics E-Notes, (0), - c ISSN 0-0 Available free at mirror sites of http://wwwmaththuedutw/ame/ Combiatio Labeligs Of Graphs Pak Chig Li y Received February 0 Abstract Suppose G = (V; E) is
Applied Mathematics E-Notes, (0), - c ISSN 0-0 Available free at mirror sites of http://wwwmaththuedutw/ame/ Combiatio Labeligs Of Graphs Pak Chig Li y Received February 0 Abstract Suppose G = (V; E) is
Random Graphs and Complex Networks T
 Radom Graphs ad Complex Networks T-79.7003 Charalampos E. Tsourakakis Aalto Uiversity Lecture 3 7 September 013 Aoucemet Homework 1 is out, due i two weeks from ow. Exercises: Probabilistic iequalities
Radom Graphs ad Complex Networks T-79.7003 Charalampos E. Tsourakakis Aalto Uiversity Lecture 3 7 September 013 Aoucemet Homework 1 is out, due i two weeks from ow. Exercises: Probabilistic iequalities
Homework 1 Solutions MA 522 Fall 2017
 Homework 1 Solutios MA 5 Fall 017 1. Cosider the searchig problem: Iput A sequece of umbers A = [a 1,..., a ] ad a value v. Output A idex i such that v = A[i] or the special value NIL if v does ot appear
Homework 1 Solutios MA 5 Fall 017 1. Cosider the searchig problem: Iput A sequece of umbers A = [a 1,..., a ] ad a value v. Output A idex i such that v = A[i] or the special value NIL if v does ot appear
CIS 121 Data Structures and Algorithms with Java Spring Stacks, Queues, and Heaps Monday, February 18 / Tuesday, February 19
 CIS Data Structures ad Algorithms with Java Sprig 09 Stacks, Queues, ad Heaps Moday, February 8 / Tuesday, February 9 Stacks ad Queues Recall the stack ad queue ADTs (abstract data types from lecture.
CIS Data Structures ad Algorithms with Java Sprig 09 Stacks, Queues, ad Heaps Moday, February 8 / Tuesday, February 9 Stacks ad Queues Recall the stack ad queue ADTs (abstract data types from lecture.
Computational Geometry
 Computatioal Geometry Chapter 4 Liear programmig Duality Smallest eclosig disk O the Ageda Liear Programmig Slides courtesy of Craig Gotsma 4. 4. Liear Programmig - Example Defie: (amout amout cosumed
Computatioal Geometry Chapter 4 Liear programmig Duality Smallest eclosig disk O the Ageda Liear Programmig Slides courtesy of Craig Gotsma 4. 4. Liear Programmig - Example Defie: (amout amout cosumed
Lecturers: Sanjam Garg and Prasad Raghavendra Feb 21, Midterm 1 Solutions
 U.C. Berkeley CS170 : Algorithms Midterm 1 Solutios Lecturers: Sajam Garg ad Prasad Raghavedra Feb 1, 017 Midterm 1 Solutios 1. (4 poits) For the directed graph below, fid all the strogly coected compoets
U.C. Berkeley CS170 : Algorithms Midterm 1 Solutios Lecturers: Sajam Garg ad Prasad Raghavedra Feb 1, 017 Midterm 1 Solutios 1. (4 poits) For the directed graph below, fid all the strogly coected compoets
Lecture 1: Introduction and Strassen s Algorithm
 5-750: Graduate Algorithms Jauary 7, 08 Lecture : Itroductio ad Strasse s Algorithm Lecturer: Gary Miller Scribe: Robert Parker Itroductio Machie models I this class, we will primarily use the Radom Access
5-750: Graduate Algorithms Jauary 7, 08 Lecture : Itroductio ad Strasse s Algorithm Lecturer: Gary Miller Scribe: Robert Parker Itroductio Machie models I this class, we will primarily use the Radom Access
Improved Random Graph Isomorphism
 Improved Radom Graph Isomorphism Tomek Czajka Gopal Paduraga Abstract Caoical labelig of a graph cosists of assigig a uique label to each vertex such that the labels are ivariat uder isomorphism. Such
Improved Radom Graph Isomorphism Tomek Czajka Gopal Paduraga Abstract Caoical labelig of a graph cosists of assigig a uique label to each vertex such that the labels are ivariat uder isomorphism. Such
Sorting in Linear Time. Data Structures and Algorithms Andrei Bulatov
 Sortig i Liear Time Data Structures ad Algorithms Adrei Bulatov Algorithms Sortig i Liear Time 7-2 Compariso Sorts The oly test that all the algorithms we have cosidered so far is compariso The oly iformatio
Sortig i Liear Time Data Structures ad Algorithms Adrei Bulatov Algorithms Sortig i Liear Time 7-2 Compariso Sorts The oly test that all the algorithms we have cosidered so far is compariso The oly iformatio
Graphs. Minimum Spanning Trees. Slides by Rose Hoberman (CMU)
 Graphs Miimum Spaig Trees Slides by Rose Hoberma (CMU) Problem: Layig Telephoe Wire Cetral office 2 Wirig: Naïve Approach Cetral office Expesive! 3 Wirig: Better Approach Cetral office Miimize the total
Graphs Miimum Spaig Trees Slides by Rose Hoberma (CMU) Problem: Layig Telephoe Wire Cetral office 2 Wirig: Naïve Approach Cetral office Expesive! 3 Wirig: Better Approach Cetral office Miimize the total
CIS 121 Data Structures and Algorithms with Java Spring Stacks and Queues Monday, February 12 / Tuesday, February 13
 CIS Data Structures ad Algorithms with Java Sprig 08 Stacks ad Queues Moday, February / Tuesday, February Learig Goals Durig this lab, you will: Review stacks ad queues. Lear amortized ruig time aalysis
CIS Data Structures ad Algorithms with Java Sprig 08 Stacks ad Queues Moday, February / Tuesday, February Learig Goals Durig this lab, you will: Review stacks ad queues. Lear amortized ruig time aalysis
15-859E: Advanced Algorithms CMU, Spring 2015 Lecture #2: Randomized MST and MST Verification January 14, 2015
 15-859E: Advaced Algorithms CMU, Sprig 2015 Lecture #2: Radomized MST ad MST Verificatio Jauary 14, 2015 Lecturer: Aupam Gupta Scribe: Yu Zhao 1 Prelimiaries I this lecture we are talkig about two cotets:
15-859E: Advaced Algorithms CMU, Sprig 2015 Lecture #2: Radomized MST ad MST Verificatio Jauary 14, 2015 Lecturer: Aupam Gupta Scribe: Yu Zhao 1 Prelimiaries I this lecture we are talkig about two cotets:
Fundamentals of Media Processing. Shin'ichi Satoh Kazuya Kodama Hiroshi Mo Duy-Dinh Le
 Fudametals of Media Processig Shi'ichi Satoh Kazuya Kodama Hiroshi Mo Duy-Dih Le Today's topics Noparametric Methods Parze Widow k-nearest Neighbor Estimatio Clusterig Techiques k-meas Agglomerative Hierarchical
Fudametals of Media Processig Shi'ichi Satoh Kazuya Kodama Hiroshi Mo Duy-Dih Le Today's topics Noparametric Methods Parze Widow k-nearest Neighbor Estimatio Clusterig Techiques k-meas Agglomerative Hierarchical
Lecture 5. Counting Sort / Radix Sort
 Lecture 5. Coutig Sort / Radix Sort T. H. Corme, C. E. Leiserso ad R. L. Rivest Itroductio to Algorithms, 3rd Editio, MIT Press, 2009 Sugkyukwa Uiversity Hyuseug Choo choo@skku.edu Copyright 2000-2018
Lecture 5. Coutig Sort / Radix Sort T. H. Corme, C. E. Leiserso ad R. L. Rivest Itroductio to Algorithms, 3rd Editio, MIT Press, 2009 Sugkyukwa Uiversity Hyuseug Choo choo@skku.edu Copyright 2000-2018
Xiaozhou (Steve) Li, Atri Rudra, Ram Swaminathan. HP Laboratories HPL Keyword(s): graph coloring; hardness of approximation
 Flexible Colorig Xiaozhou (Steve) Li, Atri Rudra, Ram Swamiatha HP Laboratories HPL-2010-177 Keyword(s): graph colorig; hardess of approximatio Abstract: Motivated b y reliability cosideratios i data deduplicatio
Flexible Colorig Xiaozhou (Steve) Li, Atri Rudra, Ram Swamiatha HP Laboratories HPL-2010-177 Keyword(s): graph colorig; hardess of approximatio Abstract: Motivated b y reliability cosideratios i data deduplicatio
6.854J / J Advanced Algorithms Fall 2008
 MIT OpeCourseWare http://ocw.mit.edu 6.854J / 18.415J Advaced Algorithms Fall 2008 For iformatio about citig these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advaced Algorithms
MIT OpeCourseWare http://ocw.mit.edu 6.854J / 18.415J Advaced Algorithms Fall 2008 For iformatio about citig these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advaced Algorithms
Fundamental Algorithms
 Techische Uiversität Müche Fakultät für Iformatik Lehrstuhl für Effiziete Algorithme Dmytro Chibisov Sadeep Sadaada Witer Semester 2007/08 Solutio Sheet 6 November 30, 2007 Fudametal Algorithms Problem
Techische Uiversität Müche Fakultät für Iformatik Lehrstuhl für Effiziete Algorithme Dmytro Chibisov Sadeep Sadaada Witer Semester 2007/08 Solutio Sheet 6 November 30, 2007 Fudametal Algorithms Problem
1 Graph Sparsfication
 CME 305: Discrete Mathematics ad Algorithms 1 Graph Sparsficatio I this sectio we discuss the approximatio of a graph G(V, E) by a sparse graph H(V, F ) o the same vertex set. I particular, we cosider
CME 305: Discrete Mathematics ad Algorithms 1 Graph Sparsficatio I this sectio we discuss the approximatio of a graph G(V, E) by a sparse graph H(V, F ) o the same vertex set. I particular, we cosider
On (K t e)-saturated Graphs
 Noame mauscript No. (will be iserted by the editor O (K t e-saturated Graphs Jessica Fuller Roald J. Gould the date of receipt ad acceptace should be iserted later Abstract Give a graph H, we say a graph
Noame mauscript No. (will be iserted by the editor O (K t e-saturated Graphs Jessica Fuller Roald J. Gould the date of receipt ad acceptace should be iserted later Abstract Give a graph H, we say a graph
Examples and Applications of Binary Search
 Toy Gog ITEE Uiersity of Queeslad I the secod lecture last week we studied the biary search algorithm that soles the problem of determiig if a particular alue appears i a sorted list of iteger or ot. We
Toy Gog ITEE Uiersity of Queeslad I the secod lecture last week we studied the biary search algorithm that soles the problem of determiig if a particular alue appears i a sorted list of iteger or ot. We
Lecture 2: Spectra of Graphs
 Spectral Graph Theory ad Applicatios WS 20/202 Lecture 2: Spectra of Graphs Lecturer: Thomas Sauerwald & He Su Our goal is to use the properties of the adjacecy/laplacia matrix of graphs to first uderstad
Spectral Graph Theory ad Applicatios WS 20/202 Lecture 2: Spectra of Graphs Lecturer: Thomas Sauerwald & He Su Our goal is to use the properties of the adjacecy/laplacia matrix of graphs to first uderstad
c-dominating Sets for Families of Graphs
 c-domiatig Sets for Families of Graphs Kelsie Syder Mathematics Uiversity of Mary Washigto April 6, 011 1 Abstract The topic of domiatio i graphs has a rich history, begiig with chess ethusiasts i the
c-domiatig Sets for Families of Graphs Kelsie Syder Mathematics Uiversity of Mary Washigto April 6, 011 1 Abstract The topic of domiatio i graphs has a rich history, begiig with chess ethusiasts i the
Major CSL Write your name and entry no on every sheet of the answer script. Time 2 Hrs Max Marks 70
 NOTE:. Attempt all seve questios. Major CSL 02 2. Write your ame ad etry o o every sheet of the aswer script. Time 2 Hrs Max Marks 70 Q No Q Q 2 Q 3 Q 4 Q 5 Q 6 Q 7 Total MM 6 2 4 0 8 4 6 70 Q. Write a
NOTE:. Attempt all seve questios. Major CSL 02 2. Write your ame ad etry o o every sheet of the aswer script. Time 2 Hrs Max Marks 70 Q No Q Q 2 Q 3 Q 4 Q 5 Q 6 Q 7 Total MM 6 2 4 0 8 4 6 70 Q. Write a
Some cycle and path related strongly -graphs
 Some cycle ad path related strogly -graphs I. I. Jadav, G. V. Ghodasara Research Scholar, R. K. Uiversity, Rajkot, Idia. H. & H. B. Kotak Istitute of Sciece,Rajkot, Idia. jadaviram@gmail.com gaurag ejoy@yahoo.co.i
Some cycle ad path related strogly -graphs I. I. Jadav, G. V. Ghodasara Research Scholar, R. K. Uiversity, Rajkot, Idia. H. & H. B. Kotak Istitute of Sciece,Rajkot, Idia. jadaviram@gmail.com gaurag ejoy@yahoo.co.i
Algorithms Chapter 3 Growth of Functions
 Algorithms Chapter 3 Growth of Fuctios Istructor: Chig Chi Li 林清池助理教授 chigchi.li@gmail.com Departmet of Computer Sciece ad Egieerig Natioal Taiwa Ocea Uiversity Outlie Asymptotic otatio Stadard otatios
Algorithms Chapter 3 Growth of Fuctios Istructor: Chig Chi Li 林清池助理教授 chigchi.li@gmail.com Departmet of Computer Sciece ad Egieerig Natioal Taiwa Ocea Uiversity Outlie Asymptotic otatio Stadard otatios
Algorithm. Counting Sort Analysis of Algorithms
 Algorithm Coutig Sort Aalysis of Algorithms Assumptios: records Coutig sort Each record cotais keys ad data All keys are i the rage of 1 to k Space The usorted list is stored i A, the sorted list will
Algorithm Coutig Sort Aalysis of Algorithms Assumptios: records Coutig sort Each record cotais keys ad data All keys are i the rage of 1 to k Space The usorted list is stored i A, the sorted list will
Recursive Estimation
 Recursive Estimatio Raffaello D Adrea Sprig 2 Problem Set: Probability Review Last updated: February 28, 2 Notes: Notatio: Uless otherwise oted, x, y, ad z deote radom variables, f x (x) (or the short
Recursive Estimatio Raffaello D Adrea Sprig 2 Problem Set: Probability Review Last updated: February 28, 2 Notes: Notatio: Uless otherwise oted, x, y, ad z deote radom variables, f x (x) (or the short
The Adjacency Matrix and The nth Eigenvalue
 Spectral Graph Theory Lecture 3 The Adjacecy Matrix ad The th Eigevalue Daiel A. Spielma September 5, 2012 3.1 About these otes These otes are ot ecessarily a accurate represetatio of what happeed i class.
Spectral Graph Theory Lecture 3 The Adjacecy Matrix ad The th Eigevalue Daiel A. Spielma September 5, 2012 3.1 About these otes These otes are ot ecessarily a accurate represetatio of what happeed i class.
CIS 121 Data Structures and Algorithms with Java Fall Big-Oh Notation Tuesday, September 5 (Make-up Friday, September 8)
 CIS 11 Data Structures ad Algorithms with Java Fall 017 Big-Oh Notatio Tuesday, September 5 (Make-up Friday, September 8) Learig Goals Review Big-Oh ad lear big/small omega/theta otatios Practice solvig
CIS 11 Data Structures ad Algorithms with Java Fall 017 Big-Oh Notatio Tuesday, September 5 (Make-up Friday, September 8) Learig Goals Review Big-Oh ad lear big/small omega/theta otatios Practice solvig
Graphs. Shortest Path and Topological Sort
 Graphs Shortest Path ad Topological Sort Example Relatioal Networks School Friedship Network (from Moody 2001) Yeast Metabolic Network (from https://www.d.edu/~etworks/cell/) Terrorist Network (by Valdis
Graphs Shortest Path ad Topological Sort Example Relatioal Networks School Friedship Network (from Moody 2001) Yeast Metabolic Network (from https://www.d.edu/~etworks/cell/) Terrorist Network (by Valdis
CS473-Algorithms I. Lecture 2. Asymptotic Notation. CS 473 Lecture 2 1
 CS473-Algorithms I Lecture Asymptotic Notatio CS 473 Lecture 1 O-otatio (upper bouds) f() = O(g()) if positive costats c, 0 such that e.g., = O( 3 ) 0 f() cg(), 0 c 3 c c = 1 & 0 = or c = & 0 = 1 Asymptotic
CS473-Algorithms I Lecture Asymptotic Notatio CS 473 Lecture 1 O-otatio (upper bouds) f() = O(g()) if positive costats c, 0 such that e.g., = O( 3 ) 0 f() cg(), 0 c 3 c c = 1 & 0 = or c = & 0 = 1 Asymptotic
Design and Analysis of Algorithms Notes
 Desig ad Aalysis of Algorithms Notes Notes by Wist Course taught by Dr. K Amer Course started: Jauary 4, 013 Course eded: December 13, 01 Curret geeratio: December 18, 013 Listigs 1 Array sum pseudocode.................................
Desig ad Aalysis of Algorithms Notes Notes by Wist Course taught by Dr. K Amer Course started: Jauary 4, 013 Course eded: December 13, 01 Curret geeratio: December 18, 013 Listigs 1 Array sum pseudocode.................................
Lecture Notes 6 Introduction to algorithm analysis CSS 501 Data Structures and Object-Oriented Programming
 Lecture Notes 6 Itroductio to algorithm aalysis CSS 501 Data Structures ad Object-Orieted Programmig Readig for this lecture: Carrao, Chapter 10 To be covered i this lecture: Itroductio to algorithm aalysis
Lecture Notes 6 Itroductio to algorithm aalysis CSS 501 Data Structures ad Object-Orieted Programmig Readig for this lecture: Carrao, Chapter 10 To be covered i this lecture: Itroductio to algorithm aalysis
Polynomial Functions and Models. Learning Objectives. Polynomials. P (x) = a n x n + a n 1 x n a 1 x + a 0, a n 0
 Polyomial Fuctios ad Models 1 Learig Objectives 1. Idetify polyomial fuctios ad their degree 2. Graph polyomial fuctios usig trasformatios 3. Idetify the real zeros of a polyomial fuctio ad their multiplicity
Polyomial Fuctios ad Models 1 Learig Objectives 1. Idetify polyomial fuctios ad their degree 2. Graph polyomial fuctios usig trasformatios 3. Idetify the real zeros of a polyomial fuctio ad their multiplicity
prerequisites: 6.046, 6.041/2, ability to do proofs Randomized algorithms: make random choices during run. Main benefits:
 Itro Admiistrivia. Sigup sheet. prerequisites: 6.046, 6.041/2, ability to do proofs homework weekly (first ext week) collaboratio idepedet homeworks gradig requiremet term project books. questio: scribig?
Itro Admiistrivia. Sigup sheet. prerequisites: 6.046, 6.041/2, ability to do proofs homework weekly (first ext week) collaboratio idepedet homeworks gradig requiremet term project books. questio: scribig?
Priority Queues. Binary Heaps
 Priority Queues Biary Heaps Priority Queues Priority: some property of a object that allows it to be prioritized with respect to other objects of the same type Mi Priority Queue: homogeeous collectio of
Priority Queues Biary Heaps Priority Queues Priority: some property of a object that allows it to be prioritized with respect to other objects of the same type Mi Priority Queue: homogeeous collectio of
Basic allocator mechanisms The course that gives CMU its Zip! Memory Management II: Dynamic Storage Allocation Mar 6, 2000.
 5-23 The course that gives CM its Zip Memory Maagemet II: Dyamic Storage Allocatio Mar 6, 2000 Topics Segregated lists Buddy system Garbage collectio Mark ad Sweep Copyig eferece coutig Basic allocator
5-23 The course that gives CM its Zip Memory Maagemet II: Dyamic Storage Allocatio Mar 6, 2000 Topics Segregated lists Buddy system Garbage collectio Mark ad Sweep Copyig eferece coutig Basic allocator
Solution printed. Do not start the test until instructed to do so! CS 2604 Data Structures Midterm Spring, Instructions:
 CS 604 Data Structures Midterm Sprig, 00 VIRG INIA POLYTECHNIC INSTITUTE AND STATE U T PROSI M UNI VERSI TY Istructios: Prit your ame i the space provided below. This examiatio is closed book ad closed
CS 604 Data Structures Midterm Sprig, 00 VIRG INIA POLYTECHNIC INSTITUTE AND STATE U T PROSI M UNI VERSI TY Istructios: Prit your ame i the space provided below. This examiatio is closed book ad closed
CS200: Hash Tables. Prichard Ch CS200 - Hash Tables 1
 CS200: Hash Tables Prichard Ch. 13.2 CS200 - Hash Tables 1 Table Implemetatios: average cases Search Add Remove Sorted array-based Usorted array-based Balaced Search Trees O(log ) O() O() O() O(1) O()
CS200: Hash Tables Prichard Ch. 13.2 CS200 - Hash Tables 1 Table Implemetatios: average cases Search Add Remove Sorted array-based Usorted array-based Balaced Search Trees O(log ) O() O() O() O(1) O()
Heaps. Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
 Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 201 Heaps 201 Goodrich ad Tamassia xkcd. http://xkcd.com/83/. Tree. Used with permissio uder
Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 201 Heaps 201 Goodrich ad Tamassia xkcd. http://xkcd.com/83/. Tree. Used with permissio uder
Lower Bounds for Sorting
 Liear Sortig Topics Covered: Lower Bouds for Sortig Coutig Sort Radix Sort Bucket Sort Lower Bouds for Sortig Compariso vs. o-compariso sortig Decisio tree model Worst case lower boud Compariso Sortig
Liear Sortig Topics Covered: Lower Bouds for Sortig Coutig Sort Radix Sort Bucket Sort Lower Bouds for Sortig Compariso vs. o-compariso sortig Decisio tree model Worst case lower boud Compariso Sortig
The Closest Line to a Data Set in the Plane. David Gurney Southeastern Louisiana University Hammond, Louisiana
 The Closest Lie to a Data Set i the Plae David Gurey Southeaster Louisiaa Uiversity Hammod, Louisiaa ABSTRACT This paper looks at three differet measures of distace betwee a lie ad a data set i the plae:
The Closest Lie to a Data Set i the Plae David Gurey Southeaster Louisiaa Uiversity Hammod, Louisiaa ABSTRACT This paper looks at three differet measures of distace betwee a lie ad a data set i the plae:
Thompson s Group F (p + 1) is not Minimally Almost Convex
 Thompso s Group F (p + ) is ot Miimally Almost Covex Claire Wladis Thompso s Group F (p + ). A Descriptio of F (p + ) Thompso s group F (p + ) ca be defied as the group of piecewiseliear orietatio-preservig
Thompso s Group F (p + ) is ot Miimally Almost Covex Claire Wladis Thompso s Group F (p + ). A Descriptio of F (p + ) Thompso s group F (p + ) ca be defied as the group of piecewiseliear orietatio-preservig
An Efficient Algorithm for Graph Bisection of Triangularizations
 A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045 Oe Brookigs Drive St. Louis, Missouri 63130-4899, USA jaegerg@cse.wustl.edu
A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045 Oe Brookigs Drive St. Louis, Missouri 63130-4899, USA jaegerg@cse.wustl.edu
2. ALGORITHM ANALYSIS
 2. ALGORITHM ANALYSIS computatioal tractability survey of commo ruig times 2. ALGORITHM ANALYSIS computatioal tractability survey of commo ruig times Lecture slides by Kevi Waye Copyright 2005 Pearso-Addiso
2. ALGORITHM ANALYSIS computatioal tractability survey of commo ruig times 2. ALGORITHM ANALYSIS computatioal tractability survey of commo ruig times Lecture slides by Kevi Waye Copyright 2005 Pearso-Addiso
CIS 121. Introduction to Trees
 CIS 121 Itroductio to Trees 1 Tree ADT Tree defiitio q A tree is a set of odes which may be empty q If ot empty, the there is a distiguished ode r, called root ad zero or more o-empty subtrees T 1, T 2,
CIS 121 Itroductio to Trees 1 Tree ADT Tree defiitio q A tree is a set of odes which may be empty q If ot empty, the there is a distiguished ode r, called root ad zero or more o-empty subtrees T 1, T 2,
CSC165H1 Worksheet: Tutorial 8 Algorithm analysis (SOLUTIONS)
 CSC165H1, Witer 018 Learig Objectives By the ed of this worksheet, you will: Aalyse the ruig time of fuctios cotaiig ested loops. 1. Nested loop variatios. Each of the followig fuctios takes as iput a
CSC165H1, Witer 018 Learig Objectives By the ed of this worksheet, you will: Aalyse the ruig time of fuctios cotaiig ested loops. 1. Nested loop variatios. Each of the followig fuctios takes as iput a
arxiv: v2 [cs.ds] 24 Mar 2018
![arxiv: v2 [cs.ds] 24 Mar 2018 arxiv: v2 [cs.ds] 24 Mar 2018](/thumbs/81/83887444.jpg) Similar Elemets ad Metric Labelig o Complete Graphs arxiv:1803.08037v [cs.ds] 4 Mar 018 Pedro F. Felzeszwalb Brow Uiversity Providece, RI, USA pff@brow.edu March 8, 018 We cosider a problem that ivolves
Similar Elemets ad Metric Labelig o Complete Graphs arxiv:1803.08037v [cs.ds] 4 Mar 018 Pedro F. Felzeszwalb Brow Uiversity Providece, RI, USA pff@brow.edu March 8, 018 We cosider a problem that ivolves
Module 8-7: Pascal s Triangle and the Binomial Theorem
 Module 8-7: Pascal s Triagle ad the Biomial Theorem Gregory V. Bard April 5, 017 A Note about Notatio Just to recall, all of the followig mea the same thig: ( 7 7C 4 C4 7 7C4 5 4 ad they are (all proouced
Module 8-7: Pascal s Triagle ad the Biomial Theorem Gregory V. Bard April 5, 017 A Note about Notatio Just to recall, all of the followig mea the same thig: ( 7 7C 4 C4 7 7C4 5 4 ad they are (all proouced
THE PROBLEM THE PROBLEM (1) THE PROBLEM (2) THE MINIMUM ENERGY BROADCAST PROBLEM THE MINIMUM SPANNING TREE
 THE MINIMUM ENERGY BROADCAST PROBLEM I.E. THE MINIMUM SPANNING TREE PROBLEM Prof. Tiziaa Calamoeri Network Algorithms A.y. 05/ THE PROBLEM THE PROBLEM () THE PROBLEM () What does it meas sufficietly close?!
THE MINIMUM ENERGY BROADCAST PROBLEM I.E. THE MINIMUM SPANNING TREE PROBLEM Prof. Tiziaa Calamoeri Network Algorithms A.y. 05/ THE PROBLEM THE PROBLEM () THE PROBLEM () What does it meas sufficietly close?!
Pseudocode ( 1.1) Analysis of Algorithms. Primitive Operations. Pseudocode Details. Running Time ( 1.1) Estimating performance
 Aalysis of Algorithms Iput Algorithm Output A algorithm is a step-by-step procedure for solvig a problem i a fiite amout of time. Pseudocode ( 1.1) High-level descriptio of a algorithm More structured
Aalysis of Algorithms Iput Algorithm Output A algorithm is a step-by-step procedure for solvig a problem i a fiite amout of time. Pseudocode ( 1.1) High-level descriptio of a algorithm More structured
n n B. How many subsets of C are there of cardinality n. We are selecting elements for such a
 4. [10] Usig a combiatorial argumet, prove that for 1: = 0 = Let A ad B be disjoit sets of cardiality each ad C = A B. How may subsets of C are there of cardiality. We are selectig elemets for such a subset
4. [10] Usig a combiatorial argumet, prove that for 1: = 0 = Let A ad B be disjoit sets of cardiality each ad C = A B. How may subsets of C are there of cardiality. We are selectig elemets for such a subset
The isoperimetric problem on the hypercube
 The isoperimetric problem o the hypercube Prepared by: Steve Butler November 2, 2005 1 The isoperimetric problem We will cosider the -dimesioal hypercube Q Recall that the hypercube Q is a graph whose
The isoperimetric problem o the hypercube Prepared by: Steve Butler November 2, 2005 1 The isoperimetric problem We will cosider the -dimesioal hypercube Q Recall that the hypercube Q is a graph whose
CHAPTER IV: GRAPH THEORY. Section 1: Introduction to Graphs
 CHAPTER IV: GRAPH THEORY Sectio : Itroductio to Graphs Sice this class is called Number-Theoretic ad Discrete Structures, it would be a crime to oly focus o umber theory regardless how woderful those topics
CHAPTER IV: GRAPH THEORY Sectio : Itroductio to Graphs Sice this class is called Number-Theoretic ad Discrete Structures, it would be a crime to oly focus o umber theory regardless how woderful those topics
An Efficient Algorithm for Graph Bisection of Triangularizations
 Applied Mathematical Scieces, Vol. 1, 2007, o. 25, 1203-1215 A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045, Oe
Applied Mathematical Scieces, Vol. 1, 2007, o. 25, 1203-1215 A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045, Oe
Strong Complementary Acyclic Domination of a Graph
 Aals of Pure ad Applied Mathematics Vol 8, No, 04, 83-89 ISSN: 79-087X (P), 79-0888(olie) Published o 7 December 04 wwwresearchmathsciorg Aals of Strog Complemetary Acyclic Domiatio of a Graph NSaradha
Aals of Pure ad Applied Mathematics Vol 8, No, 04, 83-89 ISSN: 79-087X (P), 79-0888(olie) Published o 7 December 04 wwwresearchmathsciorg Aals of Strog Complemetary Acyclic Domiatio of a Graph NSaradha
Data diverse software fault tolerance techniques
 Data diverse software fault tolerace techiques Complemets desig diversity by compesatig for desig diversity s s limitatios Ivolves obtaiig a related set of poits i the program data space, executig the
Data diverse software fault tolerace techiques Complemets desig diversity by compesatig for desig diversity s s limitatios Ivolves obtaiig a related set of poits i the program data space, executig the
Minimum Spanning Trees
 Miimum Spaig Trees Miimum Spaig Trees Spaig subgraph Subgraph of a graph G cotaiig all the vertices of G Spaig tree Spaig subgraph that is itself a (free) tree Miimum spaig tree (MST) Spaig tree of a weighted
Miimum Spaig Trees Miimum Spaig Trees Spaig subgraph Subgraph of a graph G cotaiig all the vertices of G Spaig tree Spaig subgraph that is itself a (free) tree Miimum spaig tree (MST) Spaig tree of a weighted
CS 111: Program Design I Lecture # 7: First Loop, Web Crawler, Functions
 CS 111: Program Desig I Lecture # 7: First Loop, Web Crawler, Fuctios Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 18, 2018 What will this prit? x = 5 if x == 3: prit("hi!")
CS 111: Program Desig I Lecture # 7: First Loop, Web Crawler, Fuctios Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 18, 2018 What will this prit? x = 5 if x == 3: prit("hi!")
Last class. n Scheme. n Equality testing. n eq? vs. equal? n Higher-order functions. n map, foldr, foldl. n Tail recursion
 Aoucemets HW6 due today HW7 is out A team assigmet Submitty page will be up toight Fuctioal correctess: 75%, Commets : 25% Last class Equality testig eq? vs. equal? Higher-order fuctios map, foldr, foldl
Aoucemets HW6 due today HW7 is out A team assigmet Submitty page will be up toight Fuctioal correctess: 75%, Commets : 25% Last class Equality testig eq? vs. equal? Higher-order fuctios map, foldr, foldl
Planar graphs. Definition. A graph is planar if it can be drawn on the plane in such a way that no two edges cross each other.
 Plaar graphs Defiitio. A graph is plaar if it ca be draw o the plae i such a way that o two edges cross each other. Example: Face 1 Face 2 Exercise: Which of the followig graphs are plaar? K, P, C, K,m,
Plaar graphs Defiitio. A graph is plaar if it ca be draw o the plae i such a way that o two edges cross each other. Example: Face 1 Face 2 Exercise: Which of the followig graphs are plaar? K, P, C, K,m,
Mathematical Stat I: solutions of homework 1
 Mathematical Stat I: solutios of homework Name: Studet Id N:. Suppose we tur over cards simultaeously from two well shuffled decks of ordiary playig cards. We say we obtai a exact match o a particular
Mathematical Stat I: solutios of homework Name: Studet Id N:. Suppose we tur over cards simultaeously from two well shuffled decks of ordiary playig cards. We say we obtai a exact match o a particular
Exact Minimum Lower Bound Algorithm for Traveling Salesman Problem
 Exact Miimum Lower Boud Algorithm for Travelig Salesma Problem Mohamed Eleiche GeoTiba Systems mohamed.eleiche@gmail.com Abstract The miimum-travel-cost algorithm is a dyamic programmig algorithm to compute
Exact Miimum Lower Boud Algorithm for Travelig Salesma Problem Mohamed Eleiche GeoTiba Systems mohamed.eleiche@gmail.com Abstract The miimum-travel-cost algorithm is a dyamic programmig algorithm to compute
ENGI 4421 Probability and Statistics Faculty of Engineering and Applied Science Problem Set 1 Descriptive Statistics
 ENGI 44 Probability ad Statistics Faculty of Egieerig ad Applied Sciece Problem Set Descriptive Statistics. If, i the set of values {,, 3, 4, 5, 6, 7 } a error causes the value 5 to be replaced by 50,
ENGI 44 Probability ad Statistics Faculty of Egieerig ad Applied Sciece Problem Set Descriptive Statistics. If, i the set of values {,, 3, 4, 5, 6, 7 } a error causes the value 5 to be replaced by 50,
CSE 2320 Notes 8: Sorting. (Last updated 10/3/18 7:16 PM) Idea: Take an unsorted (sub)array and partition into two subarrays such that.
 CSE Notes 8: Sortig (Last updated //8 7:6 PM) CLRS 7.-7., 9., 8.-8. 8.A. QUICKSORT Cocepts Idea: Take a usorted (sub)array ad partitio ito two subarrays such that p q r x y z x y y z Pivot Customarily,
CSE Notes 8: Sortig (Last updated //8 7:6 PM) CLRS 7.-7., 9., 8.-8. 8.A. QUICKSORT Cocepts Idea: Take a usorted (sub)array ad partitio ito two subarrays such that p q r x y z x y y z Pivot Customarily,
Some non-existence results on Leech trees
 Some o-existece results o Leech trees László A.Székely Hua Wag Yog Zhag Uiversity of South Carolia This paper is dedicated to the memory of Domiique de Cae, who itroduced LAS to Leech trees.. Abstract
Some o-existece results o Leech trees László A.Székely Hua Wag Yog Zhag Uiversity of South Carolia This paper is dedicated to the memory of Domiique de Cae, who itroduced LAS to Leech trees.. Abstract
CMSC Computer Architecture Lecture 10: Caches. Prof. Yanjing Li University of Chicago
 CMSC 22200 Computer Architecture Lecture 10: Caches Prof. Yajig Li Uiversity of Chicago Midterm Recap Overview ad fudametal cocepts ISA Uarch Datapath, cotrol Sigle cycle, multi cycle Pipeliig Basic idea,
CMSC 22200 Computer Architecture Lecture 10: Caches Prof. Yajig Li Uiversity of Chicago Midterm Recap Overview ad fudametal cocepts ISA Uarch Datapath, cotrol Sigle cycle, multi cycle Pipeliig Basic idea,
Improving Template Based Spike Detection
 Improvig Template Based Spike Detectio Kirk Smith, Member - IEEE Portlad State Uiversity petra@ee.pdx.edu Abstract Template matchig algorithms like SSE, Covolutio ad Maximum Likelihood are well kow for
Improvig Template Based Spike Detectio Kirk Smith, Member - IEEE Portlad State Uiversity petra@ee.pdx.edu Abstract Template matchig algorithms like SSE, Covolutio ad Maximum Likelihood are well kow for
Ones Assignment Method for Solving Traveling Salesman Problem
 Joural of mathematics ad computer sciece 0 (0), 58-65 Oes Assigmet Method for Solvig Travelig Salesma Problem Hadi Basirzadeh Departmet of Mathematics, Shahid Chamra Uiversity, Ahvaz, Ira Article history:
Joural of mathematics ad computer sciece 0 (0), 58-65 Oes Assigmet Method for Solvig Travelig Salesma Problem Hadi Basirzadeh Departmet of Mathematics, Shahid Chamra Uiversity, Ahvaz, Ira Article history:
2 X = 2 X. The number of all permutations of a set X with n elements is. n! = n (n 1) (n 2) nn e n
 1 Discrete Mathematics revisited. Facts to remember Give set X, the umber of subsets of X is give by X = X. The umber of all permutatios of a set X with elemets is! = ( 1) ( )... 1 e π. The umber ( ) k
1 Discrete Mathematics revisited. Facts to remember Give set X, the umber of subsets of X is give by X = X. The umber of all permutatios of a set X with elemets is! = ( 1) ( )... 1 e π. The umber ( ) k
Administrative UNSUPERVISED LEARNING. Unsupervised learning. Supervised learning 11/25/13. Final project. No office hours today
 Admiistrative Fial project No office hours today UNSUPERVISED LEARNING David Kauchak CS 451 Fall 2013 Supervised learig Usupervised learig label label 1 label 3 model/ predictor label 4 label 5 Supervised
Admiistrative Fial project No office hours today UNSUPERVISED LEARNING David Kauchak CS 451 Fall 2013 Supervised learig Usupervised learig label label 1 label 3 model/ predictor label 4 label 5 Supervised
9 x and g(x) = 4. x. Find (x) 3.6. I. Combining Functions. A. From Equations. Example: Let f(x) = and its domain. Example: Let f(x) = and g(x) = x x 4
 1 3.6 I. Combiig Fuctios A. From Equatios Example: Let f(x) = 9 x ad g(x) = 4 f x. Fid (x) g ad its domai. 4 Example: Let f(x) = ad g(x) = x x 4. Fid (f-g)(x) B. From Graphs: Graphical Additio. Example:
1 3.6 I. Combiig Fuctios A. From Equatios Example: Let f(x) = 9 x ad g(x) = 4 f x. Fid (x) g ad its domai. 4 Example: Let f(x) = ad g(x) = x x 4. Fid (f-g)(x) B. From Graphs: Graphical Additio. Example:
Message Authentication Codes. Reading: Chapter 4 of Katz & Lindell
 Message Autheticatio Codes Readig: Chapter 4 of Katz & Lidell 1 Message autheticatio Bob receives a message m from Alice, he wats to ow (Data origi autheticatio) whether the message was really set by Alice.
Message Autheticatio Codes Readig: Chapter 4 of Katz & Lidell 1 Message autheticatio Bob receives a message m from Alice, he wats to ow (Data origi autheticatio) whether the message was really set by Alice.
Symmetric Class 0 subgraphs of complete graphs
 DIMACS Techical Report 0-0 November 0 Symmetric Class 0 subgraphs of complete graphs Vi de Silva Departmet of Mathematics Pomoa College Claremot, CA, USA Chaig Verbec, Jr. Becer Friedma Istitute Booth
DIMACS Techical Report 0-0 November 0 Symmetric Class 0 subgraphs of complete graphs Vi de Silva Departmet of Mathematics Pomoa College Claremot, CA, USA Chaig Verbec, Jr. Becer Friedma Istitute Booth
Math 216A Notes, Week 4
 Math 216A Notes, Week 4 Scribe: Jaso Erbele Disclaimer: These otes are ot early as polished ad quite possibly ot early as correct) as a published paper. Please use them at your ow risk. 1. Probabilistic
Math 216A Notes, Week 4 Scribe: Jaso Erbele Disclaimer: These otes are ot early as polished ad quite possibly ot early as correct) as a published paper. Please use them at your ow risk. 1. Probabilistic
How do we evaluate algorithms?
 F2 Readig referece: chapter 2 + slides Algorithm complexity Big O ad big Ω To calculate ruig time Aalysis of recursive Algorithms Next time: Litterature: slides mostly The first Algorithm desig methods:
F2 Readig referece: chapter 2 + slides Algorithm complexity Big O ad big Ω To calculate ruig time Aalysis of recursive Algorithms Next time: Litterature: slides mostly The first Algorithm desig methods:
Data Structures and Algorithms. Analysis of Algorithms
 Data Structures ad Algorithms Aalysis of Algorithms Outlie Ruig time Pseudo-code Big-oh otatio Big-theta otatio Big-omega otatio Asymptotic algorithm aalysis Aalysis of Algorithms Iput Algorithm Output
Data Structures ad Algorithms Aalysis of Algorithms Outlie Ruig time Pseudo-code Big-oh otatio Big-theta otatio Big-omega otatio Asymptotic algorithm aalysis Aalysis of Algorithms Iput Algorithm Output
What are we going to learn? CSC Data Structures Analysis of Algorithms. Overview. Algorithm, and Inputs
 What are we goig to lear? CSC316-003 Data Structures Aalysis of Algorithms Computer Sciece North Carolia State Uiversity Need to say that some algorithms are better tha others Criteria for evaluatio Structure
What are we goig to lear? CSC316-003 Data Structures Aalysis of Algorithms Computer Sciece North Carolia State Uiversity Need to say that some algorithms are better tha others Criteria for evaluatio Structure
Order statistics. Order Statistics. Randomized divide-andconquer. Example. CS Spring 2006
 406 CS 5633 -- Sprig 006 Order Statistics Carola We Slides courtesy of Charles Leiserso with small chages by Carola We CS 5633 Aalysis of Algorithms 406 Order statistics Select the ith smallest of elemets
406 CS 5633 -- Sprig 006 Order Statistics Carola We Slides courtesy of Charles Leiserso with small chages by Carola We CS 5633 Aalysis of Algorithms 406 Order statistics Select the ith smallest of elemets
Hash Tables. Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015.
 Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 2015 Hash Tables xkcd. http://xkcd.com/221/. Radom Number. Used with permissio uder Creative
Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 2015 Hash Tables xkcd. http://xkcd.com/221/. Radom Number. Used with permissio uder Creative
. Written in factored form it is easy to see that the roots are 2, 2, i,
 CMPS A Itroductio to Programmig Programmig Assigmet 4 I this assigmet you will write a java program that determies the real roots of a polyomial that lie withi a specified rage. Recall that the roots (or
CMPS A Itroductio to Programmig Programmig Assigmet 4 I this assigmet you will write a java program that determies the real roots of a polyomial that lie withi a specified rage. Recall that the roots (or
Chapter 11. Friends, Overloaded Operators, and Arrays in Classes. Copyright 2014 Pearson Addison-Wesley. All rights reserved.
 Chapter 11 Frieds, Overloaded Operators, ad Arrays i Classes Copyright 2014 Pearso Addiso-Wesley. All rights reserved. Overview 11.1 Fried Fuctios 11.2 Overloadig Operators 11.3 Arrays ad Classes 11.4
Chapter 11 Frieds, Overloaded Operators, ad Arrays i Classes Copyright 2014 Pearso Addiso-Wesley. All rights reserved. Overview 11.1 Fried Fuctios 11.2 Overloadig Operators 11.3 Arrays ad Classes 11.4
Minimum Spanning Trees
 Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 0 Miimum Spaig Trees 0 Goodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig a Network Suppose
Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 0 Miimum Spaig Trees 0 Goodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig a Network Suppose
Convergence results for conditional expectations
 Beroulli 11(4), 2005, 737 745 Covergece results for coditioal expectatios IRENE CRIMALDI 1 ad LUCA PRATELLI 2 1 Departmet of Mathematics, Uiversity of Bologa, Piazza di Porta Sa Doato 5, 40126 Bologa,
Beroulli 11(4), 2005, 737 745 Covergece results for coditioal expectatios IRENE CRIMALDI 1 ad LUCA PRATELLI 2 1 Departmet of Mathematics, Uiversity of Bologa, Piazza di Porta Sa Doato 5, 40126 Bologa,
15 UNSUPERVISED LEARNING
 15 UNSUPERVISED LEARNING [My father] advised me to sit every few moths i my readig chair for a etire eveig, close my eyes ad try to thik of ew problems to solve. I took his advice very seriously ad have
15 UNSUPERVISED LEARNING [My father] advised me to sit every few moths i my readig chair for a etire eveig, close my eyes ad try to thik of ew problems to solve. I took his advice very seriously ad have
Switching Hardware. Spring 2018 CS 438 Staff, University of Illinois 1
 Switchig Hardware Sprig 208 CS 438 Staff, Uiversity of Illiois Where are we? Uderstad Differet ways to move through a etwork (forwardig) Read sigs at each switch (datagram) Follow a kow path (virtual circuit)
Switchig Hardware Sprig 208 CS 438 Staff, Uiversity of Illiois Where are we? Uderstad Differet ways to move through a etwork (forwardig) Read sigs at each switch (datagram) Follow a kow path (virtual circuit)
EE123 Digital Signal Processing
 Last Time EE Digital Sigal Processig Lecture 7 Block Covolutio, Overlap ad Add, FFT Discrete Fourier Trasform Properties of the Liear covolutio through circular Today Liear covolutio with Overlap ad add
Last Time EE Digital Sigal Processig Lecture 7 Block Covolutio, Overlap ad Add, FFT Discrete Fourier Trasform Properties of the Liear covolutio through circular Today Liear covolutio with Overlap ad add
The size Ramsey number of a directed path
 The size Ramsey umber of a directed path Ido Be-Eliezer Michael Krivelevich Bey Sudakov May 25, 2010 Abstract Give a graph H, the size Ramsey umber r e (H, q) is the miimal umber m for which there is a
The size Ramsey umber of a directed path Ido Be-Eliezer Michael Krivelevich Bey Sudakov May 25, 2010 Abstract Give a graph H, the size Ramsey umber r e (H, q) is the miimal umber m for which there is a
A study on Interior Domination in Graphs
 IOSR Joural of Mathematics (IOSR-JM) e-issn: 2278-5728, p-issn: 219-765X. Volume 12, Issue 2 Ver. VI (Mar. - Apr. 2016), PP 55-59 www.iosrjourals.org A study o Iterior Domiatio i Graphs A. Ato Kisley 1,
IOSR Joural of Mathematics (IOSR-JM) e-issn: 2278-5728, p-issn: 219-765X. Volume 12, Issue 2 Ver. VI (Mar. - Apr. 2016), PP 55-59 www.iosrjourals.org A study o Iterior Domiatio i Graphs A. Ato Kisley 1,
Pattern Recognition Systems Lab 1 Least Mean Squares
 Patter Recogitio Systems Lab 1 Least Mea Squares 1. Objectives This laboratory work itroduces the OpeCV-based framework used throughout the course. I this assigmet a lie is fitted to a set of poits usig
Patter Recogitio Systems Lab 1 Least Mea Squares 1. Objectives This laboratory work itroduces the OpeCV-based framework used throughout the course. I this assigmet a lie is fitted to a set of poits usig
Minimum Spanning Trees. Application: Connecting a Network
 Miimum Spaig Tree // : Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. oodrich ad R. Tamassia, Wiley, Miimum Spaig Trees oodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig
Miimum Spaig Tree // : Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. oodrich ad R. Tamassia, Wiley, Miimum Spaig Trees oodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig
Our Learning Problem, Again
 Noparametric Desity Estimatio Matthew Stoe CS 520, Sprig 2000 Lecture 6 Our Learig Problem, Agai Use traiig data to estimate ukow probabilities ad probability desity fuctios So far, we have depeded o describig
Noparametric Desity Estimatio Matthew Stoe CS 520, Sprig 2000 Lecture 6 Our Learig Problem, Agai Use traiig data to estimate ukow probabilities ad probability desity fuctios So far, we have depeded o describig
Running Time ( 3.1) Analysis of Algorithms. Experimental Studies. Limitations of Experiments
 Ruig Time ( 3.1) Aalysis of Algorithms Iput Algorithm Output A algorithm is a step- by- step procedure for solvig a problem i a fiite amout of time. Most algorithms trasform iput objects ito output objects.
Ruig Time ( 3.1) Aalysis of Algorithms Iput Algorithm Output A algorithm is a step- by- step procedure for solvig a problem i a fiite amout of time. Most algorithms trasform iput objects ito output objects.
COMP Parallel Computing. PRAM (1): The PRAM model and complexity measures
 COMP 633 - Parallel Computig Lecture 2 August 24, 2017 : The PRAM model ad complexity measures 1 First class summary This course is about parallel computig to achieve high-er performace o idividual problems
COMP 633 - Parallel Computig Lecture 2 August 24, 2017 : The PRAM model ad complexity measures 1 First class summary This course is about parallel computig to achieve high-er performace o idividual problems
CMPT 125 Assignment 2 Solutions
 CMPT 25 Assigmet 2 Solutios Questio (20 marks total) a) Let s cosider a iteger array of size 0. (0 marks, each part is 2 marks) it a[0]; I. How would you assig a poiter, called pa, to store the address
CMPT 25 Assigmet 2 Solutios Questio (20 marks total) a) Let s cosider a iteger array of size 0. (0 marks, each part is 2 marks) it a[0]; I. How would you assig a poiter, called pa, to store the address
Analysis of Algorithms
 Aalysis of Algorithms Iput Algorithm Output A algorithm is a step-by-step procedure for solvig a problem i a fiite amout of time. Ruig Time Most algorithms trasform iput objects ito output objects. The
Aalysis of Algorithms Iput Algorithm Output A algorithm is a step-by-step procedure for solvig a problem i a fiite amout of time. Ruig Time Most algorithms trasform iput objects ito output objects. The
Python Programming: An Introduction to Computer Science
 Pytho Programmig: A Itroductio to Computer Sciece Chapter 6 Defiig Fuctios Pytho Programmig, 2/e 1 Objectives To uderstad why programmers divide programs up ito sets of cooperatig fuctios. To be able to
Pytho Programmig: A Itroductio to Computer Sciece Chapter 6 Defiig Fuctios Pytho Programmig, 2/e 1 Objectives To uderstad why programmers divide programs up ito sets of cooperatig fuctios. To be able to
