Passware Kit Forensic 2018 Quick Start Guide
|
|
|
- Augusta White
- 5 years ago
- Views:
Transcription
1 Passware Kit Forensic 2018 Quick Start Guide This guide will walk you through the basic password recovery and decryption tasks Task 1: Detecting encrypted files and containers Task 2: Recovering a file password Task 3: Extracting passwords from a memory image Task 4: Decrypting a Keychain Task 5: Decrypting a VeraCrypt container Task 6: Using a custom dictionary Task 7: Customizing password recovery settings 1
2 Task 1: Detecting encrypted files and containers 1. On the Start page, click Find Encrypted Files: 2. Enable checkbox Scan for encrypted containers and disk images, click Browse and choose folder 1-DetectingEncryptedFiles to scan: 2
3 Click Scan. 3. Passware Kit lists the encrypted files along with the detailed information about them, such as: Recovery Complexity, Protection Flags, Date Modified, etc. Click Recovery Complexity to sort the files by the encryption strength. 3
4 4. Optionally: Select the files you want to decrypt starting from files with Instant Unprotection complexity and moving on to files with stronger encryption, such as archives or containers. Click Recover Password to proceed with password ecovery and decryption in batch mode. 4
5 5
6 Task 2: Recovering a file password 1. On the Start page, click Recover File Password: 2. Locate file Clover.doc and click Open. 6
7 3. Choose Use Predefined Settings: 7
8 4. Passware Kit applies its default dictionary to the file and recovers the password: 8
9 Task 3: Extracting passwords from a memory image (Passware Kit Forensic only) 1. On the Start page, click Memory Analysis: 2. At the Memory image field click Browse and locate file memory-mac.img. Click Open. 9
10 3. Enable checkboxes Mac User and Websites. Click Next: 4. Passware Kit extracts passwords for Mac users, as well as the list of open websites along with their login credentials 10
11 11
12 12
13 Task 4: Decrypting a Keychain (Passware Kit Forensic only) By default settings of macos, a Keychain password is the same as a Mac user password. Passware Kit leverages this feature to recover Keychain passwords with its dictionary, which includes previously recovered passwords for Mac users (in Task 3). The previously recovered passwords are automatically saved in Passware Kit dictionary to be reused for subsequent files. 1. On the Start page, click Recover File Password: 13
14 2. Locate file johndoe.keychain and click Open. 3. Click Use Predefined Settings: 4. Passware Kit runs default password recovery attacks, which include a dictionary with the previously found passwords. The File-Open password is recovered in seconds and Passware Kit extracts all the login credentials from the Keychain: 14
15 15
16 Task 5: Decrypting a VeraCrypt container 1. On the Start page, click Full Disk Encryption: 2. Choose VeraCrypt. 16
17 3. Click I have a memory image tab: 4. At the Encrypted VeraCrypt volume image file field click Browse, set All files (*.*) from the pull-down menu of the File name field and locate file vc.hc: 17
18 The decrypted volume image will be saved in the Destination file location. 18
19 5. At the Physical memory image file field click Browse and locate file vcmemory.bin. Click Decrypt: 19
20 6. Passware Kit removes the VeraCrypt encryption key and saves the decrypted image file: 20
21 Task 6: Using a custom dictionary Password for file Capital.zip is a capital name. To recover this type of password, use a list of capitals as a custom dictionary file. Such a list could be created manually as a text file or downloaded from wordlist resources, such as ftp://ftp.cerias.purdue.edu/pub/dict 1. On the Start page, click Recover File Password: 2. Locate file Capital.zip and click Open. 21
22 3. Click Advanced: Customize Settings: 4. Passware Kit displays the settings of the default password recovery attacks. Click Remove All to clear the list and start with your own settings: 22
23 23
24 5. Click Add Attack : 6. At the Dictionary Attack settings, choose Custom from the Dictionary pulldown menu: 24
25 7. At the Custom Dictionary Compiler window, click Browse, locate file capitals.txt (a custom list of capitals, which is supposed to be used as a dictionary) and click Open. Click Compile to proceed: 25
26 8. Passware Kit compiles the text file into a dictionary named Unfiltered-capitalsdictionary. Select this dictionary and click Add Attack. 26
27 27
28 9. Click Recover to proceed with the custom settings: 28
29 10. Passware Kit recovers the password for the file using the custom dictionary: 29
30 Task 7: Customizing password recovery settings If a pattern for a password is known, it can be specified in Passware Kit settings. For example, password for file placesihavebeen.zip is a city name followed with a year, i.e. London2015, Amsterdam2000, etc. To recover this type of password, use a custom dictionary file from Task On the Start page, click Recover File Password: 2. Locate file placesihavebeen.zip and click Open. 30
31 3. Click Advanced: Customize Settings: 4. Passware Kit displays the settings of the default password recovery attacks. Click Remove All to clear the list and start with your own settings: 31
32 32
33 5. Click Add Attack : 6. To specify pattern city + year, click Join Attacks. You will need to join a Dictionary (city names) attack and a Brute-force attack (numbers) together. Specify the overall range of password Length, if known: from 5 to 10 characters in this example. Click Add Attack: 33
34 34
35 7. Click [+] and choose a Dictionary attack: 8. From the Dictionary pull-down menu, choose Unfiltered-capitals-dictionary, which was previously compiled in Task 6 (steps 6-8 of Task 6). Click Add Attack: 35
36 9. Click [+] and choose a Brute-force attack: 36
37 10. At the Brute-force Attack settings, specify the length of the password s part: if it is a year, the range of Length is from 4 to 4 characters. Specify the Symbol Set: enable checkbox Numbers and disable all other checkboxes. At the Advanced Settings section, specify the Pattern of the passwords s part: if it is a year of current century, the pattern is 20* (the password s part will look like 2000, 2001,, 2099). Click Add Attack: 37
38 38
39 11. Click Recover to proceed with the custom settings: 39
40 12. Passware Kit recovers the password for the file using the custom settings: Congratulations! You have successfully completed all the tasks! 40
Acronis Backup & Recovery 11 Beta Advanced Editions
 Acronis Backup & Recovery 11 Beta Advanced Editions Quick Start Guide Table of contents 1 Main components... 3 2 Supported operating systems... 3 3 Where do I install the components?... 3 4 What you need
Acronis Backup & Recovery 11 Beta Advanced Editions Quick Start Guide Table of contents 1 Main components... 3 2 Supported operating systems... 3 3 Where do I install the components?... 3 4 What you need
How to Create a Signed QuickAdd Package
 Items needed to complete this task: Apple Developer account. (https://developer.apple.com) Mac Computer Section 1. Create a Certificate Signing Request (CSR) A Certificate Signing Request or CSR is a specially
Items needed to complete this task: Apple Developer account. (https://developer.apple.com) Mac Computer Section 1. Create a Certificate Signing Request (CSR) A Certificate Signing Request or CSR is a specially
Fairfield University Using Xythos for File Storage
 Fairfield University Using Xythos for File Storage Version 7.0 Table of Contents I: Accessing your Account...2 II: Uploading Files via the Web...2 III: Manage your Folders and Files via the Web...4 IV:
Fairfield University Using Xythos for File Storage Version 7.0 Table of Contents I: Accessing your Account...2 II: Uploading Files via the Web...2 III: Manage your Folders and Files via the Web...4 IV:
Restoring data from a backup
 Restoring data from a backup The following topics explain how to find a backup to restore and then perform a restore: Finding a backup to restore on page 98 Restoring to the original location on page 101
Restoring data from a backup The following topics explain how to find a backup to restore and then perform a restore: Finding a backup to restore on page 98 Restoring to the original location on page 101
This documentation is for clean installations with no prior Panopto software installed. For upgrade instructions, please see Upgrade to Panopto 4.6.
 Web Server Installation Overview This documentation is for clean installations with no prior Panopto software installed. For upgrade instructions, please see Upgrade to Panopto 4.6. Note: If you enter
Web Server Installation Overview This documentation is for clean installations with no prior Panopto software installed. For upgrade instructions, please see Upgrade to Panopto 4.6. Note: If you enter
Administering FileVault 2 on OS X Mountain Lion with the Casper Suite. Technical Paper Casper Suite v9.0 or Later 7 January 2015
 Administering FileVault 2 on OS X Mountain Lion with the Casper Suite Technical Paper Casper Suite v9.0 or Later 7 January 2015 JAMF Software, LLC 2015 JAMF Software, LLC. All rights reserved. JAMF Software
Administering FileVault 2 on OS X Mountain Lion with the Casper Suite Technical Paper Casper Suite v9.0 or Later 7 January 2015 JAMF Software, LLC 2015 JAMF Software, LLC. All rights reserved. JAMF Software
PcZealous [Professional] User Manual
![PcZealous [Professional] User Manual PcZealous [Professional] User Manual](/thumbs/82/86438296.jpg) STEPS TO INSTALL PcZEALOUS [Professional]: Double Click on the PcZealous [Professional] Setup.exe file. In the welcome screen as shown below, Click the Next button Read the Software License Agreement,
STEPS TO INSTALL PcZEALOUS [Professional]: Double Click on the PcZealous [Professional] Setup.exe file. In the welcome screen as shown below, Click the Next button Read the Software License Agreement,
Spectrum Business Cloud Backup Quick Start Guide
 Spectrum Business Cloud Backup Quick Start Guide Table of Contents Introduction... 3 Administrator... 4 Set Up Spectrum Business Cloud Backup Admin Account... 4 Create Administrator Account... 4 Edit Administrator
Spectrum Business Cloud Backup Quick Start Guide Table of Contents Introduction... 3 Administrator... 4 Set Up Spectrum Business Cloud Backup Admin Account... 4 Create Administrator Account... 4 Edit Administrator
Acronis Backup plugin for WHM and cpanel 1.0
 Acronis Backup plugin for WHM and cpanel 1.0 ADMINISTRATOR'S GUIDE Table of contents 1 Introduction...3 2 System requirements...3 3 Obtaining the Acronis product...3 4 Installing the Acronis Backup plugin
Acronis Backup plugin for WHM and cpanel 1.0 ADMINISTRATOR'S GUIDE Table of contents 1 Introduction...3 2 System requirements...3 3 Obtaining the Acronis product...3 4 Installing the Acronis Backup plugin
Acronis Backup plugin for WHM & cpanel 1.0
 Acronis Backup plugin for WHM & cpanel 1.0 ADMINISTRATOR S GUIDE Revision: 7/18/2017 Table of contents 1 Introduction...3 2 System requirements...3 3 Obtaining the Acronis product...4 4 Installing the
Acronis Backup plugin for WHM & cpanel 1.0 ADMINISTRATOR S GUIDE Revision: 7/18/2017 Table of contents 1 Introduction...3 2 System requirements...3 3 Obtaining the Acronis product...4 4 Installing the
Acronis Data Cloud plugin for ConnectWise Automate
 Acronis Data Cloud plugin for ConnectWise Automate USER S GUIDE Revision: 17.01.2018 Table of contents 1 Introduction...3 2 What s new in Update 3...3 3 What s new in Update 2...3 4 What s new in Update
Acronis Data Cloud plugin for ConnectWise Automate USER S GUIDE Revision: 17.01.2018 Table of contents 1 Introduction...3 2 What s new in Update 3...3 3 What s new in Update 2...3 4 What s new in Update
Computer Forensics: Investigating File and Operating Systems, Wireless Networks, and Storage, 2nd Edition. Chapter 7 Application Password Crackers
 Computer Forensics: Investigating File and Operating Systems, Wireless Networks, and Storage, 2nd Edition Chapter 7 Application Password Crackers Objectives After completing this chapter, you should be
Computer Forensics: Investigating File and Operating Systems, Wireless Networks, and Storage, 2nd Edition Chapter 7 Application Password Crackers Objectives After completing this chapter, you should be
RECOMMENDED PROCEDURE
 RECOMMENDED PROCEDURE Maintaining values entered in Information Store and downloading Financial Statements Template and VERSION 2.00 PROCEDURE SUMMARY 1. Open CaseWare Working Papers to go to Templates...
RECOMMENDED PROCEDURE Maintaining values entered in Information Store and downloading Financial Statements Template and VERSION 2.00 PROCEDURE SUMMARY 1. Open CaseWare Working Papers to go to Templates...
Jetico Central Manager Administrator Guide
 Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
Online Backup Client User Manual
 Software version 3.21 For Mac OS X September 2010 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or
Software version 3.21 For Mac OS X September 2010 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or
Security context. Technology. Solution highlights
 Code42 CrashPlan Security Code42 CrashPlan provides continuous, automatic desktop and laptop backup. Our layered approach to security exceeds industry best practices and fulfills the enterprise need for
Code42 CrashPlan Security Code42 CrashPlan provides continuous, automatic desktop and laptop backup. Our layered approach to security exceeds industry best practices and fulfills the enterprise need for
Administering FileVault 2 on OS X Mountain Lion with the Casper Suite. Technical Paper Casper Suite v August 2013
 Administering FileVault 2 on OS X Mountain Lion with the Casper Suite Technical Paper Casper Suite v8.6-8.7 14 August 2013 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software
Administering FileVault 2 on OS X Mountain Lion with the Casper Suite Technical Paper Casper Suite v8.6-8.7 14 August 2013 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software
Acronis Data Cloud plugin for ConnectWise Automate
 Acronis Data Cloud plugin for ConnectWise Automate USER'S GUIDE Revision: 24.08.2018 Table of contents 1 Introduction...3 2 What's new in Update 4...3 3 What's new in Update 3...3 4 What's new in Update
Acronis Data Cloud plugin for ConnectWise Automate USER'S GUIDE Revision: 24.08.2018 Table of contents 1 Introduction...3 2 What's new in Update 4...3 3 What's new in Update 3...3 4 What's new in Update
Virtual Desktop Infrastructure Setup for MacOS
 Virtual Desktop Infrastructure Setup for MacOS Virtual Desktop Infrastructure (VDI) allows you to connect to a virtual computer and use software that you don t have installed on your own computer or mobile
Virtual Desktop Infrastructure Setup for MacOS Virtual Desktop Infrastructure (VDI) allows you to connect to a virtual computer and use software that you don t have installed on your own computer or mobile
Virtual Desktop Infrastructure Setup for MacOS
 Virtual Desktop Infrastructure Setup for MacOS Virtual Desktop Infrastructure (VDI) allows you to connect to a virtual computer and use software that you don t have installed on your own computer or mobile
Virtual Desktop Infrastructure Setup for MacOS Virtual Desktop Infrastructure (VDI) allows you to connect to a virtual computer and use software that you don t have installed on your own computer or mobile
Talon FAST User Guide. Date Version Author Comments. November 15, Jaap van Duijvenbode Final Release
 Talon FAST 2.0.1 User Guide Date Version Author Comments November 15, 2012 2.0.1 Jaap van Duijvenbode Final Release 1 TABLE OF CONTENTS Talon FAST 2.0.1 User Guide... 1 Table of Contents... 2 1. Introduction
Talon FAST 2.0.1 User Guide Date Version Author Comments November 15, 2012 2.0.1 Jaap van Duijvenbode Final Release 1 TABLE OF CONTENTS Talon FAST 2.0.1 User Guide... 1 Table of Contents... 2 1. Introduction
Demonstration Instructions
 Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
ShareSync Get Started Guide for Mac
 ShareSync Get Started Guide for Mac ShareSync Overview ShareSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against data loss from ransomware, accidental
ShareSync Get Started Guide for Mac ShareSync Overview ShareSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against data loss from ransomware, accidental
CMPT 300: Operating Systems I Assignment 4
 POLICIES: CMPT 300: Operating Systems I Assignment 4 Due July 31, 2018 1. Coverage Chapters 10-15 2. Grade 10 points, 100% counted into the final grade 3. Individual or Group Individual based, but group
POLICIES: CMPT 300: Operating Systems I Assignment 4 Due July 31, 2018 1. Coverage Chapters 10-15 2. Grade 10 points, 100% counted into the final grade 3. Individual or Group Individual based, but group
Part 2 Uploading and Working with WebCT's File Manager and Student Management INDEX
 Part 2 Uploading and Working with WebCT's File Manager and Student Management INDEX Uploading to and working with WebCT's File Manager... Page - 1 uploading files... Page - 3 My-Files... Page - 4 Unzipping
Part 2 Uploading and Working with WebCT's File Manager and Student Management INDEX Uploading to and working with WebCT's File Manager... Page - 1 uploading files... Page - 3 My-Files... Page - 4 Unzipping
Jetico Central Manager. Administrator Guide
 Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
How to install and configure Microsoft OneDrive for Mac
 How to install and configure Microsoft OneDrive for Mac OneDrive is Microsoft s cloud based storage solution similar to Dropbox and Google Drive. OneDrive allows you to securely access your files from
How to install and configure Microsoft OneDrive for Mac OneDrive is Microsoft s cloud based storage solution similar to Dropbox and Google Drive. OneDrive allows you to securely access your files from
If your Mac keeps asking for the login keychain password
 If your Mac keeps asking for the login keychain password The password of your macos user account might not match the password of your login keychain. Either create a new login keychain or update it with
If your Mac keeps asking for the login keychain password The password of your macos user account might not match the password of your login keychain. Either create a new login keychain or update it with
AT&T Global Network Client for Mac User s Guide Version 2.0.0
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
The two bullets below provide instructions that will guide you through the process of setting up and connecting to the ILG VPN:
 ILG VPN Job Aid The two bullets below provide instructions that will guide you through the process of setting up and connecting to the ILG VPN: Before you can use the ILG VPN for the first time, you must
ILG VPN Job Aid The two bullets below provide instructions that will guide you through the process of setting up and connecting to the ILG VPN: Before you can use the ILG VPN for the first time, you must
Overview... 1 Accessing the Clean-Up System... 1 Understanding the Layout of the Login Attempts Tab... 2
 Clean-Up System Overview... 1 Accessing the Clean-Up System... 1 Understanding the Layout of the Login Attempts Tab... 2 Loading Files into the Login Attempts Tab... 3 Cleaning Login Attempts Files...
Clean-Up System Overview... 1 Accessing the Clean-Up System... 1 Understanding the Layout of the Login Attempts Tab... 2 Loading Files into the Login Attempts Tab... 3 Cleaning Login Attempts Files...
Researcher information
 Researcher information Starting January 1, 2014 researchers can be registered and orders can be submitted to Budapest City Archives online via the Digital Archives Portal (www.eleveltar.hu). You have to
Researcher information Starting January 1, 2014 researchers can be registered and orders can be submitted to Budapest City Archives online via the Digital Archives Portal (www.eleveltar.hu). You have to
USER GUIDE for Smartsheet VERSION 1, NOVEMBER 2014
 USER GUIDE for Smartsheet VERSION 1, NOVEMBER 2014 How it Works Simply create a Backupify account and authorize it to connect to your Smartsheet account- our application will do the rest. Every day, Backupify
USER GUIDE for Smartsheet VERSION 1, NOVEMBER 2014 How it Works Simply create a Backupify account and authorize it to connect to your Smartsheet account- our application will do the rest. Every day, Backupify
CryptoSafeGuard User Guide: Beta
 : Beta BackupAssist 10.1.0 will introduce CryptoSafeGuard, a new tool that protects your backups from ransomware attack and prevents ransomware-encrypted files from being backed up. CryptoSafeGuard will
: Beta BackupAssist 10.1.0 will introduce CryptoSafeGuard, a new tool that protects your backups from ransomware attack and prevents ransomware-encrypted files from being backed up. CryptoSafeGuard will
efolder BDR for Veeam VMware Continuity Cloud Guide
 efolder BDR for Veeam VMware Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM Accessing the Continuity Cloud Host uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION
efolder BDR for Veeam VMware Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM Accessing the Continuity Cloud Host uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION
Accessing the Curriculum Management System Off-campus Process for obtaining and installing a CMS certificate on a home Mac
 INFORMATION SERVICES ICT Service Delivery Accessing the Curriculum Management System Off-campus Process for obtaining and installing a CMS certificate on a home Mac Introduction This service enables staff
INFORMATION SERVICES ICT Service Delivery Accessing the Curriculum Management System Off-campus Process for obtaining and installing a CMS certificate on a home Mac Introduction This service enables staff
SecuriSync Get Started Guide for Windows
 SecuriSync Get Started Guide for Windows Intermedia Backup and File Sharing - SecuriSync SecuriSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against
SecuriSync Get Started Guide for Windows Intermedia Backup and File Sharing - SecuriSync SecuriSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against
1. INTRODUCTION to Object Storage
 1. INTRODUCTION to Object Storage Welcome to AURO Enterprise Cloud! This document will be help you get started using our Object Storage service. Object Storage is a storage system where objects are stored
1. INTRODUCTION to Object Storage Welcome to AURO Enterprise Cloud! This document will be help you get started using our Object Storage service. Object Storage is a storage system where objects are stored
Personal Online Banking Quick Start Guide
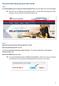 Personal Online Banking Quick Start Guide Step 1 Visit AmericanBank.com and locate the Personal Login ID box in the top right corner of the homepage. TIP: There are now two different online banking systems
Personal Online Banking Quick Start Guide Step 1 Visit AmericanBank.com and locate the Personal Login ID box in the top right corner of the homepage. TIP: There are now two different online banking systems
Vendor: Microsoft. Exam Code: Exam Name: MTA Security Fundamentals Practice Test. Version: Demo
 Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
Data Containers. User Guide
 Data Containers User Guide Contents 1. Overview... 2 Advantages of... 2 Data container options... 2 Migrating from VHD to VHDX... 3 2. Creating a Data container backup... 3 Creating a backup job... 3 Data
Data Containers User Guide Contents 1. Overview... 2 Advantages of... 2 Data container options... 2 Migrating from VHD to VHDX... 3 2. Creating a Data container backup... 3 Creating a backup job... 3 Data
BreakingVault SAP DataVault Security Storage vulnerabilities
 BreakingVault SAP DataVault Security Storage vulnerabilities Technical details Author: Fernando Russ (fruss@onapsis.com) Sr. Researcher Abstract: This document describes a series of vulnerabilities found
BreakingVault SAP DataVault Security Storage vulnerabilities Technical details Author: Fernando Russ (fruss@onapsis.com) Sr. Researcher Abstract: This document describes a series of vulnerabilities found
Welcome to InSite: A GUIDE TO PROOFING ONLINE. Getting Started Viewing Job Information Uploading Files Viewing Pages Requesting Corrections
 Welcome to InSite: A GUIDE TO PROOFING ONLINE Getting Started Viewing Job Information Uploading Files Viewing Pages Requesting Corrections PROOF.REGISTERGRAPHICS.COM *NOTE: There is no www in this address.
Welcome to InSite: A GUIDE TO PROOFING ONLINE Getting Started Viewing Job Information Uploading Files Viewing Pages Requesting Corrections PROOF.REGISTERGRAPHICS.COM *NOTE: There is no www in this address.
Gaining Access to encrypted networks
 Gaining Access to encrypted networks Everything we have learned so far we can do it without having to connect to the target network. We can get more accurate info and launch more effective attacks if we
Gaining Access to encrypted networks Everything we have learned so far we can do it without having to connect to the target network. We can get more accurate info and launch more effective attacks if we
Apple 9L Security Best Practices for Mac OS X v
 Apple Security Best Practices for Mac OS X v10.4 http://killexams.com/exam-detail/ A. SSL without certificates allows unsecure web mail. B. Enabling SSL from the pop - up menus does not require the use
Apple Security Best Practices for Mac OS X v10.4 http://killexams.com/exam-detail/ A. SSL without certificates allows unsecure web mail. B. Enabling SSL from the pop - up menus does not require the use
VPS instruction. Connecting to the Remote Desktop. Dear Client,
 Dear Client, Congratulations! You are signed up to use the market's most advanced, convenient technology VPS hosting from EXNESS. For more information about this service and its advantages, visit: https://www.exness.com/intl/ru/tools/vps
Dear Client, Congratulations! You are signed up to use the market's most advanced, convenient technology VPS hosting from EXNESS. For more information about this service and its advantages, visit: https://www.exness.com/intl/ru/tools/vps
User Guide Online Backup
 User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Getting Started with the Online Backup Software... 2 Installing the Online Backup Software... 2 Configuring a Device...
User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Getting Started with the Online Backup Software... 2 Installing the Online Backup Software... 2 Configuring a Device...
Filelocker-Yale s Secure File Transfer Service
 If you need to transfer large files, or large quantities of files, which would normally exceed the email attachment limit of 20MB, Yale s Filelocker transfer service can help. It is safe and secure for
If you need to transfer large files, or large quantities of files, which would normally exceed the email attachment limit of 20MB, Yale s Filelocker transfer service can help. It is safe and secure for
Asigra Cloud Backup v13.3 DS-Notebook Client User Guide. September 2017
 Asigra Cloud Backup v13.3 DS-Notebook Client User Guide Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Asigra Inc. Asigra
Asigra Cloud Backup v13.3 DS-Notebook Client User Guide Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Asigra Inc. Asigra
Identity Finder: Managing Your Results
 Updated 1/30/2012 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully
Updated 1/30/2012 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully
Code42 Security. Tech Specs Data Protection & Recovery
 Tech Specs Data Protection & Recovery Code42 Security Code42 provides continuous, automatic desktop and laptop backup. Our layered approach to security exceeds industry best practices and fulfills the
Tech Specs Data Protection & Recovery Code42 Security Code42 provides continuous, automatic desktop and laptop backup. Our layered approach to security exceeds industry best practices and fulfills the
Acronis Backup extension for Plesk
 Acronis Backup extension for Plesk ADMINISTRATOR S GUIDE Table of contents 1 Introduction...3 2 Software requirements...3 3 Limitations...3 4 Installing the extension...3 5 Enabling backup...4 6 Uninstalling
Acronis Backup extension for Plesk ADMINISTRATOR S GUIDE Table of contents 1 Introduction...3 2 Software requirements...3 3 Limitations...3 4 Installing the extension...3 5 Enabling backup...4 6 Uninstalling
Filtering - Zimbra
 Filtering Email - Zimbra Email filtering allows you to definite rules to manage incoming email. For instance, you may apply a filter on incoming email to route particular emails into folders or delete
Filtering Email - Zimbra Email filtering allows you to definite rules to manage incoming email. For instance, you may apply a filter on incoming email to route particular emails into folders or delete
Using RDX QuikStation and QuikStor with Acronis Backup
 Using RDX QuikStation and QuikStor with Acronis Backup INTEGRATION BRIEF Acronis Backup, in tandem with RDX Removable Storage, provides a solution for small and medium businesses that includes options
Using RDX QuikStation and QuikStor with Acronis Backup INTEGRATION BRIEF Acronis Backup, in tandem with RDX Removable Storage, provides a solution for small and medium businesses that includes options
BUSINESS CLOUD FAX By Northland Communications
 BUSINESS CLOUD FAX By Northland Communications QUICK REFERENCE GUIDE TABLE OF CONTENTS LOGGING INTO THE WEB CLIENT... CREATING + SENDING... HOW TO CREATE + SEND A FAX TO A WEB CLIENT. ADDING ATTACHMENTS...
BUSINESS CLOUD FAX By Northland Communications QUICK REFERENCE GUIDE TABLE OF CONTENTS LOGGING INTO THE WEB CLIENT... CREATING + SENDING... HOW TO CREATE + SEND A FAX TO A WEB CLIENT. ADDING ATTACHMENTS...
VMware Horizon Workspace Security Features WHITE PAPER
 VMware Horizon Workspace WHITE PAPER Table of Contents... Introduction.... 4 Horizon Workspace vapp Security.... 5 Virtual Machine Security Hardening.... 5 Authentication.... 6 Activation.... 6 Horizon
VMware Horizon Workspace WHITE PAPER Table of Contents... Introduction.... 4 Horizon Workspace vapp Security.... 5 Virtual Machine Security Hardening.... 5 Authentication.... 6 Activation.... 6 Horizon
VMware Mirage Web Manager Guide
 Mirage 5.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
Mirage 5.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
PowerSchool Parent Portal Directions
 P a g e 1 PowerSchool Parent Portal Directions If you need to create a new account OR if you need to link additional students to your account, please follow the instructions below. If you already have
P a g e 1 PowerSchool Parent Portal Directions If you need to create a new account OR if you need to link additional students to your account, please follow the instructions below. If you already have
NetBackup TM for VMware configuration
 289771 NetBackup TM for VMware configuration This document describes how to use NetBackup 6.5 with VMware virtual machines that run on VMware ESX servers. License requirements Features available in NetBackup
289771 NetBackup TM for VMware configuration This document describes how to use NetBackup 6.5 with VMware virtual machines that run on VMware ESX servers. License requirements Features available in NetBackup
Backup App V7. Quick Start Guide for Windows
 Backup App V7 Quick Start Guide for Windows Revision History Date Descriptions Type of modification 30 Jun 2016 First Draft New 25 Nov 2016 Added Restore Options to Ch 8 Restoring Data; Combined Technical
Backup App V7 Quick Start Guide for Windows Revision History Date Descriptions Type of modification 30 Jun 2016 First Draft New 25 Nov 2016 Added Restore Options to Ch 8 Restoring Data; Combined Technical
Getting Started with the Deployment Console and Deploying the Clients Per PXE Network Booting using their MAC address. Quick Guide
 Getting Started with the Deployment Console and Deploying the Clients Per PXE Network Booting using their MAC address Quick Guide Deployment Manager 2 Quick Guide 1 Introduction...3 1.1 Installing the
Getting Started with the Deployment Console and Deploying the Clients Per PXE Network Booting using their MAC address Quick Guide Deployment Manager 2 Quick Guide 1 Introduction...3 1.1 Installing the
Hyper-V Rapid Recovery - Recovery in Place
 Applicable Products These instructions apply to the following products: Barracuda Intronis Backup - MSP Hyper-V Rapid Recovery Restore Tabs The following table provides a description of the page features.
Applicable Products These instructions apply to the following products: Barracuda Intronis Backup - MSP Hyper-V Rapid Recovery Restore Tabs The following table provides a description of the page features.
Overview. Top. Welcome to SysTools MailXaminer
 Table of Contents Overview... 2 System Requirements... 3 Installation of SysTools MailXaminer... 4 Uninstall Software... 6 Software Menu Option... 8 Software Navigation Option... 10 Complete Steps to Recover,
Table of Contents Overview... 2 System Requirements... 3 Installation of SysTools MailXaminer... 4 Uninstall Software... 6 Software Menu Option... 8 Software Navigation Option... 10 Complete Steps to Recover,
RingCentral for Dropbox. User Guide
 RingCentral for Dropbox User Guide RingCentral for Dropbox User Guide Contents 2 Contents Introduction.............................................................. 3 About RingCentral for Dropbox.......................................................
RingCentral for Dropbox User Guide RingCentral for Dropbox User Guide Contents 2 Contents Introduction.............................................................. 3 About RingCentral for Dropbox.......................................................
Wireless Security Setup Guide
 Wireless Security Setup Guide NF10WV FAQs Wireless Security Overview To guard your home network against attack and prevent unauthorised access, it is very important that you follow this guide to secure
Wireless Security Setup Guide NF10WV FAQs Wireless Security Overview To guard your home network against attack and prevent unauthorised access, it is very important that you follow this guide to secure
e-storage Mail Archive e-storage Mai Archive
 e-storage Mai Archive 1 TABLE OF CONTENTS 1.0 Overview..... 4 2.0 e-storage Mail Archive..... 5 2.1 Introduction... 5 2.2 Requirements..... 6 2.3 Create new archive profile..... 7 2.3.1 Gmail Account......
e-storage Mai Archive 1 TABLE OF CONTENTS 1.0 Overview..... 4 2.0 e-storage Mail Archive..... 5 2.1 Introduction... 5 2.2 Requirements..... 6 2.3 Create new archive profile..... 7 2.3.1 Gmail Account......
9L0-412 Q&As. OS X Support Essentials 10.8 Exam. Pass Apple 9L0-412 Exam with 100% Guarantee
 9L0-412 Q&As OS X Support Essentials 10.8 Exam Pass Apple 9L0-412 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money Back Assurance
9L0-412 Q&As OS X Support Essentials 10.8 Exam Pass Apple 9L0-412 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money Back Assurance
Content Encryption Application (Windows)
 Content Encryption Application (Windows) Download & Install RioCrypt for Windows Download Link: https://www.instamojo.com/recordshield/riocrypt2 System Requirements: Windows 7, 8, 8.1, 10. DirectX 9.0c
Content Encryption Application (Windows) Download & Install RioCrypt for Windows Download Link: https://www.instamojo.com/recordshield/riocrypt2 System Requirements: Windows 7, 8, 8.1, 10. DirectX 9.0c
MEDIASEAL Encryptor Client Manual
 MEDIASEAL Encryptor Client Manual May 2018 Version 3.7.1 Fortium Technologies Ltd www.fortiumtech.com Copyright 2018 - Fortium Technologies Ltd Information contained in this document is subject to change
MEDIASEAL Encryptor Client Manual May 2018 Version 3.7.1 Fortium Technologies Ltd www.fortiumtech.com Copyright 2018 - Fortium Technologies Ltd Information contained in this document is subject to change
MSI Admin Tool User Guide
 MSI Admin Tool User Guide Introduction The MSI Admin Tool is a utility which allows you to pre-configure your Read&Write installation package prior to installation. The tool is primarily designed to be
MSI Admin Tool User Guide Introduction The MSI Admin Tool is a utility which allows you to pre-configure your Read&Write installation package prior to installation. The tool is primarily designed to be
SecureGuard VMS. SecureGuard All-In-One Quick Install Guide V. 2.5
 SecureGuard VMS Quick Install Guide V. 2.5 9/30/2018 2 Table of Contents Purpose... 3 Installation... 3 Setup... 4 Startup & Live View... 26 3 Purpose This is a step-by-step guide to installing the current
SecureGuard VMS Quick Install Guide V. 2.5 9/30/2018 2 Table of Contents Purpose... 3 Installation... 3 Setup... 4 Startup & Live View... 26 3 Purpose This is a step-by-step guide to installing the current
City of Mobile Setting Up your Account in Vendor Self Service (VSS)
 First time to Vendor Self-Service (VSS) and want to set up a vendor profile OR access your existing profile? Follow these steps. Please Note: These steps presume someone from your company has NOT already
First time to Vendor Self-Service (VSS) and want to set up a vendor profile OR access your existing profile? Follow these steps. Please Note: These steps presume someone from your company has NOT already
Wireless Printing in Mac OS X with IPP At Concordia University of Edmonton
 Wireless Printing in Mac OS X with IPP At Concordia University of Edmonton Overview Concordia offers access to the campus printer, CUCA_PRINT, through the Internet Printing Protocol which enables printing
Wireless Printing in Mac OS X with IPP At Concordia University of Edmonton Overview Concordia offers access to the campus printer, CUCA_PRINT, through the Internet Printing Protocol which enables printing
Read Naturally SE Update Windows Network Installation Instructions
 Windows Network This document explains how to apply the Read Naturally Software Edition 2.0.3 update to existing installations of SE version 2.0, 2.0.1, or 2.0.2. First update the SE server software, and
Windows Network This document explains how to apply the Read Naturally Software Edition 2.0.3 update to existing installations of SE version 2.0, 2.0.1, or 2.0.2. First update the SE server software, and
AccessData Advanced Forensics
 This advanced five-day course provides the knowledge and skills necessary to install, configure and effectively use Forensic Toolkit (FTK ), FTK Imager Password Recovery Toolkit (PRTK ) and Registry Viewer.
This advanced five-day course provides the knowledge and skills necessary to install, configure and effectively use Forensic Toolkit (FTK ), FTK Imager Password Recovery Toolkit (PRTK ) and Registry Viewer.
Internetwork Expert s CCNA Security Bootcamp. Securing Cisco Routers. Router Security Challenges
 Internetwork Expert s CCNA Security Bootcamp Securing Cisco Routers http:// Router Security Challenges As the system gets more complex, as do the vulnerabilities Key part of security team s job is to be
Internetwork Expert s CCNA Security Bootcamp Securing Cisco Routers http:// Router Security Challenges As the system gets more complex, as do the vulnerabilities Key part of security team s job is to be
Acronis Backup & Recovery 10 Advanced Editions
 Acronis Backup & Recovery 10 Advanced Editions Quick Start Guide This document describes how to install and start using any of the following editions of Acronis Backup & Recovery 10: Acronis Backup & Recovery
Acronis Backup & Recovery 10 Advanced Editions Quick Start Guide This document describes how to install and start using any of the following editions of Acronis Backup & Recovery 10: Acronis Backup & Recovery
Zadara Enterprise Storage in
 Zadara Enterprise Storage in Google Cloud Platform (GCP) Deployment Guide March 2017 Revision A 2011 2017 ZADARA Storage, Inc. All rights reserved. Zadara Storage / GCP - Deployment Guide Page 1 Contents
Zadara Enterprise Storage in Google Cloud Platform (GCP) Deployment Guide March 2017 Revision A 2011 2017 ZADARA Storage, Inc. All rights reserved. Zadara Storage / GCP - Deployment Guide Page 1 Contents
This guide details the deployment and initial configuration necessary to maximize the value of JetAdvantage Insights.
 HP JetAdvantage Insights Deployment Guide This guide details the deployment and initial configuration necessary to maximize the value of JetAdvantage Insights. 1. Overview HP JetAdvantage Insights provides
HP JetAdvantage Insights Deployment Guide This guide details the deployment and initial configuration necessary to maximize the value of JetAdvantage Insights. 1. Overview HP JetAdvantage Insights provides
Version 11. NOVASTOR CORPORATION NovaBACKUP
 NOVASTOR CORPORATION NovaBACKUP Version 11 2009 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
NOVASTOR CORPORATION NovaBACKUP Version 11 2009 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
running Recover My Files from the desktop icon (the program will open to the wizard); or,
 Page 1 of 6 Recover My Files Data Recovery Software English V3.98 When to Run a "Complete File Search" A "Complete File Search" is best used when files have been deleted and emptied from the Windows Recycle
Page 1 of 6 Recover My Files Data Recovery Software English V3.98 When to Run a "Complete File Search" A "Complete File Search" is best used when files have been deleted and emptied from the Windows Recycle
Lieberman Software. White Paper
 White Paper: Solving the Common Administrator Account Configuration Problem with the User Manager Pro Random Password Generator Module Rev 1 October 16, 2002 Written by Philip Lieberman (phil@lanicu.com)
White Paper: Solving the Common Administrator Account Configuration Problem with the User Manager Pro Random Password Generator Module Rev 1 October 16, 2002 Written by Philip Lieberman (phil@lanicu.com)
AT&T Global Network Client for Mac User s Guide Version 1.7.3
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
AccessData. Triage. Quick Start Guide
 AccessData Triage Quick Start Guide 3 AccessData Legal and Contact Information Document date: October 16, 2013 Legal Information 2013 AccessData Group, Inc All rights reserved. No part of this publication
AccessData Triage Quick Start Guide 3 AccessData Legal and Contact Information Document date: October 16, 2013 Legal Information 2013 AccessData Group, Inc All rights reserved. No part of this publication
Online Employment Application Guide
 Online Employment Application Guide This guide describes how to apply for jobs using the Government Jobs web site. The process consists of the following steps: Create An Account Find Jobs Apply for a Job
Online Employment Application Guide This guide describes how to apply for jobs using the Government Jobs web site. The process consists of the following steps: Create An Account Find Jobs Apply for a Job
Manual UCSFwpa Configuration for Windows 7
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
DATA PROTECTION. OneWorld Encrypted Messages USER GUIDE
 DATA PROTECTION OneWorld Encrypted Messages USER GUIDE Table of Contents 1 Why use Encrypted emails?...3 2 Activation and Login...4 2.1 Activating Your New OneWorld Encrypted Messages Account... 4 2.2
DATA PROTECTION OneWorld Encrypted Messages USER GUIDE Table of Contents 1 Why use Encrypted emails?...3 2 Activation and Login...4 2.1 Activating Your New OneWorld Encrypted Messages Account... 4 2.2
Troubleshooting. Participants List Displays Multiple Entries for the Same User
 Participants List Displays Multiple Entries for the Same User, page 1 Internet Explorer Browser Not Supported, page 2 "404 Page Not Found" Error Encountered, page 2 Cannot Start or Join Meeting, page 2
Participants List Displays Multiple Entries for the Same User, page 1 Internet Explorer Browser Not Supported, page 2 "404 Page Not Found" Error Encountered, page 2 Cannot Start or Join Meeting, page 2
WHITE PAPER. Authentication and Encryption Design
 WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
Unit III: Working with Windows and Applications. Chapters 5, 7, & 8
 Unit III: Working with Windows and Applications Chapters 5, 7, & 8 Learning Objectives In this unit, you will: Launch programs and navigate the Windows task bar. Perform common windows functions. Customize
Unit III: Working with Windows and Applications Chapters 5, 7, & 8 Learning Objectives In this unit, you will: Launch programs and navigate the Windows task bar. Perform common windows functions. Customize
Busey Lockbox... 3 Lockbox First Time Login... 3 Review Daily Deposits... 3 Search for Specific Checks... 4 View a Daily Summary Report...
 Busey Lockbox... 3 Lockbox First Time Login... 3 Review Daily Deposits... 3 Search for Specific Checks... 4 View a Daily Summary Report... 4 Exploring the Daily Summary Report... 4 2 Busey Lockbox Lockbox
Busey Lockbox... 3 Lockbox First Time Login... 3 Review Daily Deposits... 3 Search for Specific Checks... 4 View a Daily Summary Report... 4 Exploring the Daily Summary Report... 4 2 Busey Lockbox Lockbox
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/efsguide.htm
 Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the
Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the
Drone /12/2018. Threat Model. Description. Threats. Threat Source Risk Status Date Created
 Drone - 2 04/12/2018 Threat Model Description Threats Threat Source Risk Status Date Created Mobile Phone: Sensitive Data Leakage Smart Devices Mobile Phone: Session Hijacking Smart Devices Mobile Phone:
Drone - 2 04/12/2018 Threat Model Description Threats Threat Source Risk Status Date Created Mobile Phone: Sensitive Data Leakage Smart Devices Mobile Phone: Session Hijacking Smart Devices Mobile Phone:
VPN Client Configuration Guide
 VPN Client Configuration Guide For Windows Vista, 7 and Mac (up to version 10.11) Operating Systems Contents VPN Access... 1 VPN Permission Request... 1 VPN Client Installation & Activation... 1 Mapping
VPN Client Configuration Guide For Windows Vista, 7 and Mac (up to version 10.11) Operating Systems Contents VPN Access... 1 VPN Permission Request... 1 VPN Client Installation & Activation... 1 Mapping
Cigati Outlook Recovery. (Version 18.0)
 Cigati Outlook Email Recovery (Version 18.0) Overview Cigati Outlook Email Recovery Tool lets you repair deleted as well as corrupt Outlook emails with ease. The software is an advanced recovery tool which
Cigati Outlook Email Recovery (Version 18.0) Overview Cigati Outlook Email Recovery Tool lets you repair deleted as well as corrupt Outlook emails with ease. The software is an advanced recovery tool which
Quick Reference Guide Hosting WebEx Meetings
 Quick Reference Guide Hosting WebEx Meetings You can schedule meetings in advance, or start an instant meeting and invite participants to join you. They do not have to subscribe to WebEx. They simply click
Quick Reference Guide Hosting WebEx Meetings You can schedule meetings in advance, or start an instant meeting and invite participants to join you. They do not have to subscribe to WebEx. They simply click
Wireless Security Setup Guide
 Wireless Security Setup Guide NF17ACV FAQs Wireless Security Overview To guard your home network against attack and prevent unauthorised access, it is very important that you follow this guide to secure
Wireless Security Setup Guide NF17ACV FAQs Wireless Security Overview To guard your home network against attack and prevent unauthorised access, it is very important that you follow this guide to secure
HP BladeSystem Management Pack (v 1.x) for Microsoft System Center User Guide
 HP BladeSystem Management Pack (v 1.x) for Microsoft System Center User Guide Abstract This guide provides information on using the HP BladeSystem Management Pack for System Center version 1.x to manage
HP BladeSystem Management Pack (v 1.x) for Microsoft System Center User Guide Abstract This guide provides information on using the HP BladeSystem Management Pack for System Center version 1.x to manage
