Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption.
|
|
|
- Samson McLaughlin
- 5 years ago
- Views:
Transcription
1
2 INSTALLATION Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption. From this point on, you may install any additional IdentaMaster plugins to enable other biometric devices. Install a plug-in package, attach its biometric device, and you will be all set. Our 'plug-ins' are fully compatible with the IdentaMaster application and won't give you any hassle. Be sure to check our site for new offers. You may add other biometric plug-ins and scanners at any time.
3 LICENSE ACTIVATION Once installed, you will be prompted to enter IdentaMaster Application License key and address. After that, you will be prompted to enter Plugin License key. You will be able to start using IdentaMaster features once activation is complete. Note! If you purchase another biometric plugin's license, go to the 'Licensing' tab, select 'Update' and re-enter the new license.
4 TESTING SCANNER If you properly installed a biometric plug-in, its scanners can be tested in the Test Scanner panel. A properly connected device will show a fingerprint image on the right. Don't forget place your magic finger on the scanner surface! REGISTERING USER ACCOUNTS Select the User Enrollment tab to register a particular windows account you would like to enable with biometrics. While doing this, select logon mode password and /or biometrics and re-enter the user account's password. Note: If you change your windows account password, it needs to be reentered.
5 AVOIDING LOGON ISSUES To avoid potential login issues, it is best to select the Password or Biometrics option. This allows you to access the user profile using your password in case biometric enrollment is not successful. BIOMETRIC ENROLLMENT You can now begin user enrollment. Go to the User Enrollment tab, pick the user, and select Update enrollment, choose the biometric provider you want to use depends on available biometric technology enrollment procedure may be different. Please read our manuals HOW TO ENROLL USER S BIOMETRIC PROFILE. You will find it on the Learning Center page of our site identamaster.com/pro.
6 ENCRYPTING FILES To encrypt files or folders, right-click on them and select 'Biosecure' from the drop-down menu. Once encryption is completed, the file will be saved with the extension.izbiosecure. While setting up encryption, you can choose to keep the original files as well as delete them. Note: You may store encrypted files on any platforms (Dropbox, Google drive, etc). Only you can decrypt your files with our wonderful IdentaMaster! DECRYPTING FILES Decrypting an encrypted file is done in the same way. Right-click the file and select 'Biosecure' to begin the decryption process.
7 ENTIRE DRIVE ENCRYPTION If you have a drive, partition on drive or USB storage device, you will take advantage of IdentaMaster s Drive encryption solution. IdentaMaster seamlessly integrated with Microsoft technology built into windows. HD volumes will be strongly protected, meaning only permitted user would unlock it and get access to its resource after passing biometric authentication. By login on that PC with IdentaMaster s biometrically enabled capabilities and passing biometric authentication, external drive will be immediately unlocked for update. After signing off, that drive locked up again, so no one beside administrator and assigned users access it on that PC or any other PC. NOT JUST FINGERPRINTS? We are regularly updating our site to include other available biometric factors (such as finger vein or palm reader technology). We will also be adding other factors such as iris, voice, and facial recognition. USING BIOMETRICS HAS NEVER BEEN THIS EASY!
8
Zodiac iclass OPERATOR GUIDE
 Zodiac iclass OPERATOR GUIDE June 2008 Page 2 of 19 Table of Contents Introduction... 4 PC Requirements... 4 Installing the USB Fingerprint Scanner (Hamster)... 5 Installing the USB Smartcard Programmer...
Zodiac iclass OPERATOR GUIDE June 2008 Page 2 of 19 Table of Contents Introduction... 4 PC Requirements... 4 Installing the USB Fingerprint Scanner (Hamster)... 5 Installing the USB Smartcard Programmer...
Zodiac iclass II OPERATOR GUIDE
 Zodiac iclass II OPERATOR GUIDE July 2013 Page 2 of 24 Table of Contents INTRODUCTION... 4 PC REQUIREMENTS... 5 INSTALLING THE USB FINGERPRINT SCANNER (HAMSTER)... 5 INSTALLING THE USB SMARTCARD PROGRAMMER
Zodiac iclass II OPERATOR GUIDE July 2013 Page 2 of 24 Table of Contents INTRODUCTION... 4 PC REQUIREMENTS... 5 INSTALLING THE USB FINGERPRINT SCANNER (HAMSTER)... 5 INSTALLING THE USB SMARTCARD PROGRAMMER
Secure Single Sign On with FingerTec OFIS
 Secure Single Sign On with FingerTec OFIS User Guide CONTENTS 3 1 INTRODUCTION Welcome to OFIS Gateway 4-11 2 INSTALLATION & SETUP Registering Your OFIS Gateway Installing & Setting Up Your OFIS Gateway
Secure Single Sign On with FingerTec OFIS User Guide CONTENTS 3 1 INTRODUCTION Welcome to OFIS Gateway 4-11 2 INSTALLATION & SETUP Registering Your OFIS Gateway Installing & Setting Up Your OFIS Gateway
NEXT BIOMETRICS NB-3020-U2 WINDOWS 10 INSTALLATION GUIDE VERSION: 1.0
 NEXT BIOMETRICS NB-3020-U2 WINDOWS 10 INSTALLATION GUIDE VERSION: 1.0 NB-3020-U2 Windows 10 Installation Guide 2 CONTENTS 1 DEVICE INSTALLATION... 3 2 ADDING FINGERPRINT TO YOUR WINDOWS ACCOUNT... 5 3
NEXT BIOMETRICS NB-3020-U2 WINDOWS 10 INSTALLATION GUIDE VERSION: 1.0 NB-3020-U2 Windows 10 Installation Guide 2 CONTENTS 1 DEVICE INSTALLATION... 3 2 ADDING FINGERPRINT TO YOUR WINDOWS ACCOUNT... 5 3
Start Here. P5100 Fingerprint Reader. Quick Installation Guide. Verifi. IMPORTANT. This installation manual is for Windows 10.
 Verifi P5100 Fingerprint Reader with ROBOFORM PASSWORD MANAGER Start Here IMPORTANT. This installation manual is for Windows 10 Quick Installation Guide Windows Logon Make sure you have the following:
Verifi P5100 Fingerprint Reader with ROBOFORM PASSWORD MANAGER Start Here IMPORTANT. This installation manual is for Windows 10 Quick Installation Guide Windows Logon Make sure you have the following:
Start Here. P5100 Fingerprint Reader. Quick Installation Guide. Verifi. IMPORTANT. This installation manual is for Windows 8.1.
 Verifi P5100 Fingerprint Reader with ROBOFORM PASSWORD MANAGER Start Here IMPORTANT. This installation manual is for Windows 8.1 Quick Installation Guide Windows Logon Make sure you have the following:
Verifi P5100 Fingerprint Reader with ROBOFORM PASSWORD MANAGER Start Here IMPORTANT. This installation manual is for Windows 8.1 Quick Installation Guide Windows Logon Make sure you have the following:
Start Here. Quick Installation Guide. Verifi. IMPORTANT. Always install the Software prior to Hardware Installation ENTERPRISE
 Verifi ENTERPRISE Start Here IMPORTANT. Always install the Software prior to Hardware Installation Quick Installation Guide Windows XP Fast User Switching Compatible QAS 097 022505 PG1 RA About the Reader
Verifi ENTERPRISE Start Here IMPORTANT. Always install the Software prior to Hardware Installation Quick Installation Guide Windows XP Fast User Switching Compatible QAS 097 022505 PG1 RA About the Reader
ModeChanger
 35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
ikey Tiny USB Fingerprint Reader User Manual
 ikey Tiny USB Fingerprint Reader User Manual Introduction KINGMAX new product ikey Tiny USB Finger Print Reader is especially designed for customers convenience. It can be seen as your Password Manager,
ikey Tiny USB Fingerprint Reader User Manual Introduction KINGMAX new product ikey Tiny USB Finger Print Reader is especially designed for customers convenience. It can be seen as your Password Manager,
KEDIA TECHNOLOGIES LTD 1. Quick Start. Pre requisites :
 Quick Start Congratulations on purchasing KEDIA USB fingerprint reader: a versatile, high quality scanning device that can be used for a variety of security applications. We at KEDIA appreciate your business!
Quick Start Congratulations on purchasing KEDIA USB fingerprint reader: a versatile, high quality scanning device that can be used for a variety of security applications. We at KEDIA appreciate your business!
Spec-ops Password Reset Enrollment and Usage
 ORIGINAL DOCUMENT DATE: 12/11/2015 LAST REVISION: 1/7/2016 Spec-ops Password Reset Enrollment and Usage Index Announcement... Page 1 Quick Links, Best Practices, and Enrollment... Page 2 Using the new
ORIGINAL DOCUMENT DATE: 12/11/2015 LAST REVISION: 1/7/2016 Spec-ops Password Reset Enrollment and Usage Index Announcement... Page 1 Quick Links, Best Practices, and Enrollment... Page 2 Using the new
Table of Contents. 1. Before You Start AH650 Fingerprint Flash Drive at a Glance System Partition Safety Instructions...
 Table of Contents 1. Before You Start... 2 1.1 AH650 Fingerprint Flash Drive at a Glance... 2 1.2 System Partition... 3 1.3 Safety Instructions... 3 2. Running the Fingerprint Management Application...
Table of Contents 1. Before You Start... 2 1.1 AH650 Fingerprint Flash Drive at a Glance... 2 1.2 System Partition... 3 1.3 Safety Instructions... 3 2. Running the Fingerprint Management Application...
ReACT New User Setup, Password Reset and Account Unlock Instructions
 ReAct is a tool that will replace the current password reset system. In order to use ReAct you have to enroll and setup your challenge questions. Once enrolled you will have easy access to reset your password
ReAct is a tool that will replace the current password reset system. In order to use ReAct you have to enroll and setup your challenge questions. Once enrolled you will have easy access to reset your password
FFP Fingerprint USB Flash Drive User Manual
 FFP Fingerprint USB Flash Drive User Manual Fingerprint encryption USB3.0 High speed Multiple platform support Quick Start 1. Plug-in the flash drive to an USB port on your computer, and click CD Drive:
FFP Fingerprint USB Flash Drive User Manual Fingerprint encryption USB3.0 High speed Multiple platform support Quick Start 1. Plug-in the flash drive to an USB port on your computer, and click CD Drive:
DRACONEM RGB Touch ID Gaming Mouse Pad with Fingerprint Security
 Challenge Is The Game DRACONEM RGB Touch ID Gaming Mouse Pad with Fingerprint Security Software Guide 01 Index Challenge Is The Game Page 3 Page 7 Page 16 Page 22 Installing the software lregistering your
Challenge Is The Game DRACONEM RGB Touch ID Gaming Mouse Pad with Fingerprint Security Software Guide 01 Index Challenge Is The Game Page 3 Page 7 Page 16 Page 22 Installing the software lregistering your
Zodiac Max OPERATOR GUIDE
 Zodiac Max OPERATOR GUIDE February 2015 Table of Contents INTRODUCTION... 5 PC Requirements... 6 USB Driver Installation... 7 ZODIAC SINGLE-STATION SOFTWARE... 8 Software Installation... 8 Communications
Zodiac Max OPERATOR GUIDE February 2015 Table of Contents INTRODUCTION... 5 PC Requirements... 6 USB Driver Installation... 7 ZODIAC SINGLE-STATION SOFTWARE... 8 Software Installation... 8 Communications
Fingerprint Authentication Guide
 Fingerprint Authentication Guide What is fingerprint authentication? An electronic device is used to capture a digital image of a fingerprint pattern. This image is digitally processed to create a biometric
Fingerprint Authentication Guide What is fingerprint authentication? An electronic device is used to capture a digital image of a fingerprint pattern. This image is digitally processed to create a biometric
OmniPass 2.0 User's Guide. Version 1.2
 OmniPass 2.0 User's Guide Version 1.2 i Copyright Copyright 2002 Softex Incorporated. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
OmniPass 2.0 User's Guide Version 1.2 i Copyright Copyright 2002 Softex Incorporated. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Signup for Multi-Factor Authentication
 What is Multi-Factor Authentication? Multi-Factor Authentication (MFA) helps safeguard access to data and applications while maintaining simplicity for users. It provides additional security by requiring
What is Multi-Factor Authentication? Multi-Factor Authentication (MFA) helps safeguard access to data and applications while maintaining simplicity for users. It provides additional security by requiring
DigitalPersona Pro Enterprise
 DigitalPersona Pro Enterprise Quick Start Guide Version 5 DATA PROTECTION REMOTE ACCESS SECURE COMMUNICATION STRONG AUTHENTICATION ACCESS RECOVERY SINGLE SIGN-ON DigitalPersona Pro Enterprise DigitalPersona
DigitalPersona Pro Enterprise Quick Start Guide Version 5 DATA PROTECTION REMOTE ACCESS SECURE COMMUNICATION STRONG AUTHENTICATION ACCESS RECOVERY SINGLE SIGN-ON DigitalPersona Pro Enterprise DigitalPersona
USB 2.0 Ultimate Card Reader
 Manual USB 2.0 Ultimate Card Reader english Manual_Page 2 Content 1. Installation 3 2. Functions of Application Software 4 A. The File Management Function 4 B. The File-Security Function 4 C. The Private
Manual USB 2.0 Ultimate Card Reader english Manual_Page 2 Content 1. Installation 3 2. Functions of Application Software 4 A. The File Management Function 4 B. The File-Security Function 4 C. The Private
MU2a Authentication, Authorization & Accounting Questions and Answers with Explainations
 98-367 MU2a Authentication, Authorization & Accounting Questions and Answers with Explainations Which are common symptoms of a virus infection? (Lesson 5 p 135-136) Poor system performance. Unusually low
98-367 MU2a Authentication, Authorization & Accounting Questions and Answers with Explainations Which are common symptoms of a virus infection? (Lesson 5 p 135-136) Poor system performance. Unusually low
Once a USB drive has been inserted into an encrypted machine, the Dell Data Protection software will recognize the unencrypted device.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Stealth HD Bio Quick Start Guide
 Stealth HD Bio Quick Start Guide Copyright 2011 MXI Security. All rights reserved. This document may not be reproduced or transmitted in any form (whether now known or hereinafter discovered or developed),
Stealth HD Bio Quick Start Guide Copyright 2011 MXI Security. All rights reserved. This document may not be reproduced or transmitted in any form (whether now known or hereinafter discovered or developed),
Guide to your CGIAR Network account Self Service tool
 Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Guide to your CGIAR Network account Self Service tool The self-service tool allows you to: Change Password: Change your current password from anywhere using your web browser. Reset Password: Reset your
Working with the Sigma series should be done on a Test environment before going *Live*
 Working with the Sigma series should be done on a Test environment before going *Live* You just got a Sigma Lite and you need to set it up, here are some basic steps to get you started. **This PDF is only
Working with the Sigma series should be done on a Test environment before going *Live* You just got a Sigma Lite and you need to set it up, here are some basic steps to get you started. **This PDF is only
Charter Pacific Biometrics Acquisition
 Charter Pacific Biometrics Acquisition Charter Pacific Biometrics Acquisition Charter Pacific has executed a Share Purchase Agreement to acquire 100% of Microlatch. Charter Pacific/Microlatch has a patent
Charter Pacific Biometrics Acquisition Charter Pacific Biometrics Acquisition Charter Pacific has executed a Share Purchase Agreement to acquire 100% of Microlatch. Charter Pacific/Microlatch has a patent
BOCHK Mobile Token FAQ
 BOCHK Mobile Token FAQ 1. What is "Mobile Token"? "Mobile Token" is a feature of BOCHK Mobile App. Upon activation of "Mobile Token" with a designated mobile device ("mobile phone"), you can use it immediately
BOCHK Mobile Token FAQ 1. What is "Mobile Token"? "Mobile Token" is a feature of BOCHK Mobile App. Upon activation of "Mobile Token" with a designated mobile device ("mobile phone"), you can use it immediately
Biometric Security Roles & Resources
 Biometric Security Roles & Resources Part 1 Biometric Systems Skip Linehan Biometrics Systems Architect, Raytheon Intelligence and Information Systems Outline Biometrics Overview Biometric Architectures
Biometric Security Roles & Resources Part 1 Biometric Systems Skip Linehan Biometrics Systems Architect, Raytheon Intelligence and Information Systems Outline Biometrics Overview Biometric Architectures
BIOMETRIC MECHANISM FOR ONLINE TRANSACTION ON ANDROID SYSTEM ENHANCED SECURITY OF. Anshita Agrawal
 BIOMETRIC MECHANISM FOR ENHANCED SECURITY OF ONLINE TRANSACTION ON ANDROID SYSTEM 1 Anshita Agrawal CONTENTS Introduction Biometric Authentication Fingerprints Proposed System Conclusion References 2 INTRODUCTION
BIOMETRIC MECHANISM FOR ENHANCED SECURITY OF ONLINE TRANSACTION ON ANDROID SYSTEM 1 Anshita Agrawal CONTENTS Introduction Biometric Authentication Fingerprints Proposed System Conclusion References 2 INTRODUCTION
OurPartnerPortal.com
 OurPartnerPortal.com New users to OurPartnerPortal.com will receive an auto-generated email providing the website address to log into www.ourpartnerportal.com with their user name and a temporary password.
OurPartnerPortal.com New users to OurPartnerPortal.com will receive an auto-generated email providing the website address to log into www.ourpartnerportal.com with their user name and a temporary password.
Entrée Smart ID User Manual
 Entrée Smart ID User Manual Thank you for using the Entrée Smart ID product. This user manual will guide you to adventure the wonderful features of the product. 1. How to install Entrée Smart ID software
Entrée Smart ID User Manual Thank you for using the Entrée Smart ID product. This user manual will guide you to adventure the wonderful features of the product. 1. How to install Entrée Smart ID software
Manual Download. Please visit SUNIX website by searching keyword isafe or KEY-256UN1 for detail.
 Manual Download Please visit SUNIX website http://www.sunix.com by searching keyword isafe or KEY-256UN1 for detail. 1 User s Manual Copyright Copyright 2014 SUNIX Co., Ltd. All Rights Reserved. No part
Manual Download Please visit SUNIX website http://www.sunix.com by searching keyword isafe or KEY-256UN1 for detail. 1 User s Manual Copyright Copyright 2014 SUNIX Co., Ltd. All Rights Reserved. No part
Setting up Virdi integration with Paxton Net2 Server
 Setting up Virdi integration with Paxton Net2 Server Overview Integrating Virdi biometric readers with the Paxton Net2 system is made possible by using UNIS4 and QEManager (the software required can be
Setting up Virdi integration with Paxton Net2 Server Overview Integrating Virdi biometric readers with the Paxton Net2 system is made possible by using UNIS4 and QEManager (the software required can be
A. Getting Started About e-access Enrolling in e-access: Authenticating your account Login... 5
 Contents A. Getting Started... 3 1. About e-access... 3 2. Enrolling in e-access:... 3 3. Authenticating your account... 5 4. Login... 5 B. Fix a Problem... 6 1. Provided the wrong email address during
Contents A. Getting Started... 3 1. About e-access... 3 2. Enrolling in e-access:... 3 3. Authenticating your account... 5 4. Login... 5 B. Fix a Problem... 6 1. Provided the wrong email address during
Table Of Contents Introduction & System requirements: Steps to install the SecomSDK Installer package. 3
 TABLE OF CONTENTS Table Of Contents 1 1. Introduction & System requirements: 2 2. Steps to install the SecomSDK Installer package. 3 3. Manual Installation of Sennheiser Sametime plugin. 10 3.1. Steps
TABLE OF CONTENTS Table Of Contents 1 1. Introduction & System requirements: 2 2. Steps to install the SecomSDK Installer package. 3 3. Manual Installation of Sennheiser Sametime plugin. 10 3.1. Steps
Demonstration Instructions
 Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
Meeting the requirements of PCI DSS 3.2 standard to user authentication
 Meeting the requirements of PCI DSS 3.2 standard to user authentication Using the Indeed Identity products for authentication In April 2016, the new PCI DSS 3.2 version was adopted. Some of this version
Meeting the requirements of PCI DSS 3.2 standard to user authentication Using the Indeed Identity products for authentication In April 2016, the new PCI DSS 3.2 version was adopted. Some of this version
INTUS 1600PS Palm Vein Authentication
 INTUS 1600PS Palm Vein Authentication PalmSecure TM is a mark from Fujitsu Page 1 Biometry what s the use of it? І Need for trustable and automated person identification. І Addition / replacement of traditional
INTUS 1600PS Palm Vein Authentication PalmSecure TM is a mark from Fujitsu Page 1 Biometry what s the use of it? І Need for trustable and automated person identification. І Addition / replacement of traditional
Eaget Fingerprint Flash Drive
 Eaget Fingerprint Flash Drive User Manual Fingerprint Encryption High speed identification Dual Storage Metal Case Table of Contents 1. Before You Start... 1 1.1For Users...1 1.2Parameter and Compatible
Eaget Fingerprint Flash Drive User Manual Fingerprint Encryption High speed identification Dual Storage Metal Case Table of Contents 1. Before You Start... 1 1.1For Users...1 1.2Parameter and Compatible
Controlsoft Identity and Access Management Software Controlsoft Identity Access Client Software
 Controlsoft Identity Access Client Software IA Client Software Installation Guide v8.0.229 2018 Controlsoft Ltd 9010-0046 Issue 8 Page 1 of 24 29/10/2018 Contents 1. Introduction... 2 1.1. PC Specifications...
Controlsoft Identity Access Client Software IA Client Software Installation Guide v8.0.229 2018 Controlsoft Ltd 9010-0046 Issue 8 Page 1 of 24 29/10/2018 Contents 1. Introduction... 2 1.1. PC Specifications...
NetIQ Advanced Authentication Framework - Client. User's Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework - Client User's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 4 About This Document 4 NetIQ Advanced Authentication Framework Overview
NetIQ Advanced Authentication Framework - Client User's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 4 About This Document 4 NetIQ Advanced Authentication Framework Overview
BioPassport TM Enterprise Server
 BioPassport TM Enterprise Server The BioPassport Enterprise AD Server is the intelligence behind all of IdentAlink s biometric modules. Password management for a network or application can cost hundreds
BioPassport TM Enterprise Server The BioPassport Enterprise AD Server is the intelligence behind all of IdentAlink s biometric modules. Password management for a network or application can cost hundreds
Stuart Hall ICTN /10/17 Advantages and Drawbacks to Using Biometric Authentication
 Stuart Hall ICTN 4040 601 04/10/17 Advantages and Drawbacks to Using Biometric Authentication As technology advances, so must the means of heightened information security. Corporate businesses, hospitals
Stuart Hall ICTN 4040 601 04/10/17 Advantages and Drawbacks to Using Biometric Authentication As technology advances, so must the means of heightened information security. Corporate businesses, hospitals
SICM INSTALLATION MANUAL ADDENDUM
 PASSPORT TECHNOLOGIES INC. SICM INSTALLATION MANUAL ADDENDUM USER INTERFACE GUIDE JANUARY 2017 WWW.PASSPORTTECHNOLOGIES.COM Page 1 of 11 Copyright 2017 Copyright 2016 PASSPORT TECHNOLOGIES INC. All rights
PASSPORT TECHNOLOGIES INC. SICM INSTALLATION MANUAL ADDENDUM USER INTERFACE GUIDE JANUARY 2017 WWW.PASSPORTTECHNOLOGIES.COM Page 1 of 11 Copyright 2017 Copyright 2016 PASSPORT TECHNOLOGIES INC. All rights
Axicon Verifier User Guide
 Axicon Verifier User Guide Setup and Basic Settings The Axicon barcode verifier software provides many tools for analysing various technical aspects of a barcode providing a detailed insight into the quality
Axicon Verifier User Guide Setup and Basic Settings The Axicon barcode verifier software provides many tools for analysing various technical aspects of a barcode providing a detailed insight into the quality
Biometric Technology
 Biometric Technology Contents Biometric Technology M2SYS is a leading global provider of biometric technology and software solutions with 16 years of real-world experience. Our experience enables us to
Biometric Technology Contents Biometric Technology M2SYS is a leading global provider of biometric technology and software solutions with 16 years of real-world experience. Our experience enables us to
Using Sigma and Sigma Lite readers with Secure Admin
 Using Sigma and Sigma Lite readers with Secure Admin Requirements Sigma to L1 Legacy Sigma Lite to L1 Legacy Working with Secure Admin Scenario One Scenario Two Scenario Three Copy Templates from Database
Using Sigma and Sigma Lite readers with Secure Admin Requirements Sigma to L1 Legacy Sigma Lite to L1 Legacy Working with Secure Admin Scenario One Scenario Two Scenario Three Copy Templates from Database
Moving HRtrack to a new computer
 First Reference Moving HRtrack to a new computer Process at a Glance Confirm the location of your HRtrack data Install HRtrack on the new computer Copy the HRtrack data folder from the old computer to
First Reference Moving HRtrack to a new computer Process at a Glance Confirm the location of your HRtrack data Install HRtrack on the new computer Copy the HRtrack data folder from the old computer to
Portals 14 What is a portal? 14 Hardware 15 RS232 to RS USB to RS TCP/IP to RS Add a Serial Portal 16 Add a Network portal 16
 PROS LITE User Manual Version 2.0.0 www.visual-plus.com Table of Contents Getting Started 5 Starting PROS Lite 5 Create a Portal 5 Adding a control panel 6 Adding a user 7 Upload users to a controller
PROS LITE User Manual Version 2.0.0 www.visual-plus.com Table of Contents Getting Started 5 Starting PROS Lite 5 Create a Portal 5 Adding a control panel 6 Adding a user 7 Upload users to a controller
End User Password Self Service Procedures
 End User Password Self Service Procedures End User Password Self Service Procedures Page 1 of 19 Document Information Name: Author: Phone#: Email ID: End User Password Self Service Procedures Corporate
End User Password Self Service Procedures End User Password Self Service Procedures Page 1 of 19 Document Information Name: Author: Phone#: Email ID: End User Password Self Service Procedures Corporate
Advanced Biometric Access Control Training Course # :
 Advanced Biometric Access Control Training Course # : 14-4156 Content A. Objectives 5 mins B. History of EAC- 10 mins C. Electronic Access Control in Todays World 20 mins D. Essential Components of Electronic
Advanced Biometric Access Control Training Course # : 14-4156 Content A. Objectives 5 mins B. History of EAC- 10 mins C. Electronic Access Control in Todays World 20 mins D. Essential Components of Electronic
Dropbox is a free service that lets you bring all your photos, docs, and videos anywhere. This means that any file you save to your Dropbox will
 1 Dropbox is a free service that lets you bring all your photos, docs, and videos anywhere. This means that any file you save to your Dropbox will automatically save to all your computers, phones and even
1 Dropbox is a free service that lets you bring all your photos, docs, and videos anywhere. This means that any file you save to your Dropbox will automatically save to all your computers, phones and even
Getting started with ActiveSecurity MyLogin
 1 (5) Getting started with ActiveSecurity MyLogin 1 Introduction This document contains instructions for starting to use Aventra s ActiveSecurity MyLogin software and explanations of the basic settings.
1 (5) Getting started with ActiveSecurity MyLogin 1 Introduction This document contains instructions for starting to use Aventra s ActiveSecurity MyLogin software and explanations of the basic settings.
Axxis Biometrics LLC. BioAxxis L113 Fingerprint Door Lock Programming Kit
 Axxis Biometrics LLC BioAxxis L113 Fingerprint Door Lock Programming Kit Revision 0.14 Dec 2005 Table of Contents 1. Introduction... 2 Product Overview... 2 Main Features... 2 Packing Lists... 3 2. Operation
Axxis Biometrics LLC BioAxxis L113 Fingerprint Door Lock Programming Kit Revision 0.14 Dec 2005 Table of Contents 1. Introduction... 2 Product Overview... 2 Main Features... 2 Packing Lists... 3 2. Operation
Table of contents. 2 Samsung Care. 3 Know Your Device. 5 S Pen. 7 Device Setup. 12 Home Screen. 18 Apps. 19 Calls. 20 Voic .
 Table of contents 2 Samsung Care 3 Know Your Device 5 S Pen 7 Device Setup 12 Home Screen 18 Apps 19 Calls 20 Voicemail 21 Contacts 22 Messages 24 Camera 25 Internet 26 Connections 27 Security Samsung
Table of contents 2 Samsung Care 3 Know Your Device 5 S Pen 7 Device Setup 12 Home Screen 18 Apps 19 Calls 20 Voicemail 21 Contacts 22 Messages 24 Camera 25 Internet 26 Connections 27 Security Samsung
Mobile Banking Guide-Web Enabled Devices
 Mobile Banking Guide-Web Enabled Devices Enrolling in Web Mobile Banking Log into SRB Online Banking at www.sugarriverbank.com. Select Options Mobile Settings Web Mobile Banking Select to enable web access,
Mobile Banking Guide-Web Enabled Devices Enrolling in Web Mobile Banking Log into SRB Online Banking at www.sugarriverbank.com. Select Options Mobile Settings Web Mobile Banking Select to enable web access,
ThinkVantage Fingerprint Software
 ThinkVantage Fingerprint Software 12 2 1First Edition (February 2006) Copyright Lenovo 2006. Portions Copyright International Business Machines Corporation 2006. All rights reserved. U.S. GOVERNMENT
ThinkVantage Fingerprint Software 12 2 1First Edition (February 2006) Copyright Lenovo 2006. Portions Copyright International Business Machines Corporation 2006. All rights reserved. U.S. GOVERNMENT
Benefitfocus Mobile App. User Guide
 Benefitfocus Mobile App User Guide Table of Contents Mobile App Overview... 3 Mobile App Access... 4 Activating the Mobile App... 4 Navigating the Mobile App... 8 Completing Required Training Items...
Benefitfocus Mobile App User Guide Table of Contents Mobile App Overview... 3 Mobile App Access... 4 Activating the Mobile App... 4 Navigating the Mobile App... 8 Completing Required Training Items...
Client Configuration Guide
 Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
ALLDAY TIME SYSTEMS LTD. Allday PT1400 Biometric User Guide
 Allday PT1400 Biometric User Guide Entering the Administration Menu. On first use of the PT1400 Terminal the Terminal Administration menu can be accessed by simply holding down the M/OK button for 5 seconds
Allday PT1400 Biometric User Guide Entering the Administration Menu. On first use of the PT1400 Terminal the Terminal Administration menu can be accessed by simply holding down the M/OK button for 5 seconds
Accessing your Inter-Library Loan document via the British Library s On Demand service
 Accessing your Inter-Library Loan document via the British Library s On Demand service When you request an article from a journal or conference proceedings, or a book chapter, it will be supplied by the
Accessing your Inter-Library Loan document via the British Library s On Demand service When you request an article from a journal or conference proceedings, or a book chapter, it will be supplied by the
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
TOTALPASS SMALL BUSINESS PREMIUM BIOMETRIC QUICK START GUIDE PLEASE READ THIS FIRST. Version:
 TOTALPASS SMALL BUSINESS PREMIUM BIOMETRIC QUICK START GUIDE PLEASE READ THIS FIRST Version: 020115 1 UNPACK THE BOX Please confirm the contents of your system. If any item is missing, contact our support
TOTALPASS SMALL BUSINESS PREMIUM BIOMETRIC QUICK START GUIDE PLEASE READ THIS FIRST Version: 020115 1 UNPACK THE BOX Please confirm the contents of your system. If any item is missing, contact our support
How to Install Dawson Diagnostic Wizard A. Edit Your Mac System Preferences
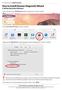 How to Install Dawson Diagnostic Wizard A. Edit Your Mac System Preferences 1. Open your Mac System Preferences under the apple menu, circled in red below. 2. Select Security & Privacy, circled in red
How to Install Dawson Diagnostic Wizard A. Edit Your Mac System Preferences 1. Open your Mac System Preferences under the apple menu, circled in red below. 2. Select Security & Privacy, circled in red
Hardening Fingerprint Authentication Systems Using Intel s SGX Enclave Technology. Interim Progress Report
 Hardening Fingerprint Authentication Systems Using Intel s SGX Enclave Technology Interim Progress Report DELL-EMC Envision the Future Competition 2018 Table of Contents List of Figures... 3 List of tables...
Hardening Fingerprint Authentication Systems Using Intel s SGX Enclave Technology Interim Progress Report DELL-EMC Envision the Future Competition 2018 Table of Contents List of Figures... 3 List of tables...
Digital Certificate Service (DCS) - User Guide
 Digital Certificate Service (DCS) - User Guide Information Security Branch Contents Using this Guide... 3 User Requirements... 3 Secure E-mail Messaging... 4 Send a Secure E-mail Message... 4 Receive a
Digital Certificate Service (DCS) - User Guide Information Security Branch Contents Using this Guide... 3 User Requirements... 3 Secure E-mail Messaging... 4 Send a Secure E-mail Message... 4 Receive a
Encrypting Removable Media
 For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data
For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data
Match On Card MINEX 2
 Match On Card MINEX 2 CTST 2008 Conference Consuelo Bangs Sagem Morpho, Inc. What is MOC? Match on Card (MOC) is the process of sending a biometric template from a live capture device to the card The card
Match On Card MINEX 2 CTST 2008 Conference Consuelo Bangs Sagem Morpho, Inc. What is MOC? Match on Card (MOC) is the process of sending a biometric template from a live capture device to the card The card
FSN-PalmSecureID-for ATM Machines
 T he application of biometric solutions in ATMs and electronic point-of-sale solutions provide a high- security environment. By using a smartcard, on which the client's unique palm vein pattern is stored,
T he application of biometric solutions in ATMs and electronic point-of-sale solutions provide a high- security environment. By using a smartcard, on which the client's unique palm vein pattern is stored,
Step 3 ROS Administrator
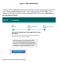 Step 3 ROS Administrator To continue the ROS registration process when you receive the system password text or email, click on the "I have my system password" button, or go to www.revenue.ie and click
Step 3 ROS Administrator To continue the ROS registration process when you receive the system password text or email, click on the "I have my system password" button, or go to www.revenue.ie and click
Quick Reference Guide
 Quick Reference Guide Unlocked ¹ Table of Contents 2 Samsung Care 3 Know your device 5 Device setup 9 Home screen 12 Volume and ringtones 13 Hello Bixby 14 Useful apps 15 Calls 16 Voicemail 17 Contacts
Quick Reference Guide Unlocked ¹ Table of Contents 2 Samsung Care 3 Know your device 5 Device setup 9 Home screen 12 Volume and ringtones 13 Hello Bixby 14 Useful apps 15 Calls 16 Voicemail 17 Contacts
Biometric Offender Movement
 Biometric Offender Movement Case Study Northern Ireland Prison Service CTA 2011 Patricia O Hagan, CEO Edward Hanna, Technical Director Agenda Background Northern Ireland Prison Service (NIPS) biometric
Biometric Offender Movement Case Study Northern Ireland Prison Service CTA 2011 Patricia O Hagan, CEO Edward Hanna, Technical Director Agenda Background Northern Ireland Prison Service (NIPS) biometric
Table of Contents. Table of Figures. 2 Wave Systems Corp. Client User Guide
 2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
The MSU Department of Mathematics "Account Manager" can be used for the following:
 MSU Department of Mathematics Account Manager Tutorial Overview The MSU Department of Mathematics "Account Manager" can be used for the following: Change your Math account password Reset a forgotten password
MSU Department of Mathematics Account Manager Tutorial Overview The MSU Department of Mathematics "Account Manager" can be used for the following: Change your Math account password Reset a forgotten password
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
Advanced Authentication 6.0 includes new features, improves usability, and resolves several previous issues.
 Advanced Authentication 6.0 Release Notes May 2018 Advanced Authentication 6.0 includes new features, improves usability, and resolves several previous issues. Many of these improvements were made in direct
Advanced Authentication 6.0 Release Notes May 2018 Advanced Authentication 6.0 includes new features, improves usability, and resolves several previous issues. Many of these improvements were made in direct
DEKART Logon for Lotus Notes. Users Guide. Pages 41
 DEKART Logon for Lotus Notes Users Guide Pages 41 2004 Annotation: The following document contains a general description how to use Dekart Logon for Lotus Notes. DSSSCT File: LNLOGONeng.DOC Ref.: DLNLOGON002
DEKART Logon for Lotus Notes Users Guide Pages 41 2004 Annotation: The following document contains a general description how to use Dekart Logon for Lotus Notes. DSSSCT File: LNLOGONeng.DOC Ref.: DLNLOGON002
BioBridge. IDenticard PremiSys. Quick Start Guide
 BioBridge IDenticard PremiSys Quick Start Guide Table of Contents Introduction... 3 Support... 3 Setting up BioBridge... 4 Wiegand Profiles... 4 Biometric Device Profile... 5 Biometric Device(s)... 6 User
BioBridge IDenticard PremiSys Quick Start Guide Table of Contents Introduction... 3 Support... 3 Setting up BioBridge... 4 Wiegand Profiles... 4 Biometric Device Profile... 5 Biometric Device(s)... 6 User
Document Signing Certificate Getting Started Guide
 Certificate Services Document Signing Certificate Getting Started Guide Using the SafeNet Authentication Client: 8.3 Document issue: 1.0 Date of issue: March 2017 For software release 12.1 Document Signing
Certificate Services Document Signing Certificate Getting Started Guide Using the SafeNet Authentication Client: 8.3 Document issue: 1.0 Date of issue: March 2017 For software release 12.1 Document Signing
Download and Install RootsMagic for Mac
 Download and Install RootsMagic for Mac This Magic Guide covers: A. Finding the RootsMagic Installer on RootsMagic.com B. Downloading with Safari C. Downloading with Google Chrome D. Installing RootsMagic
Download and Install RootsMagic for Mac This Magic Guide covers: A. Finding the RootsMagic Installer on RootsMagic.com B. Downloading with Safari C. Downloading with Google Chrome D. Installing RootsMagic
SETUP FOR OUTLOOK (Updated October, 2018)
 EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
River Bank & Trust Online Banking Initial Log In Instructions
 River Bank & Trust Online Banking Initial Log In Instructions Step 1: Go to River Bank & Trust s website (https://riverbankandtrust.com/). Locate the Online Banking Login box in the upper right corner
River Bank & Trust Online Banking Initial Log In Instructions Step 1: Go to River Bank & Trust s website (https://riverbankandtrust.com/). Locate the Online Banking Login box in the upper right corner
version: User Manual
 version: 11.2.0 User Manual Contents Introduction... 6 Support... 6 Overview... 7 What is a client?... 7 What is a server?... 7 What is a fingerprint enrollment device?... 7 What is a Biometric Device?...
version: 11.2.0 User Manual Contents Introduction... 6 Support... 6 Overview... 7 What is a client?... 7 What is a server?... 7 What is a fingerprint enrollment device?... 7 What is a Biometric Device?...
USER MANUAL. TL400B Fingerprint Lock with Voice Guide Feature. Version: 1.1 Date: Jul. 2017
 USER MANUAL TL400B Fingerprint Lock with Voice Guide Feature Version: 1.1 Date: Jul. 2017 1 Content Read Before Use 1 Safety Caution 1 Structure 2 Basic Function 3 User Introduction 3 Operation and Voice
USER MANUAL TL400B Fingerprint Lock with Voice Guide Feature Version: 1.1 Date: Jul. 2017 1 Content Read Before Use 1 Safety Caution 1 Structure 2 Basic Function 3 User Introduction 3 Operation and Voice
GeisingerConnect PingID Mobile App Enrollment Guide
 Purpose of this Guide This guide is intended for users who need to enroll in the PingID mobile device app to use PingID for logging into GeisingerConnect. If you replace your phone, please contact the
Purpose of this Guide This guide is intended for users who need to enroll in the PingID mobile device app to use PingID for logging into GeisingerConnect. If you replace your phone, please contact the
Protecting your data with Windows 10 BitLocker
 Microsoft IT Showcase Protecting your data with Windows 10 BitLocker Microsoft BitLocker Drive Encryption technology uses the strongest publicly available encryption to protect your computer s data. It
Microsoft IT Showcase Protecting your data with Windows 10 BitLocker Microsoft BitLocker Drive Encryption technology uses the strongest publicly available encryption to protect your computer s data. It
Merchant Toolkit. Multi-Factor Authentication
 Merchant Toolkit Multi-Factor Authentication Multi-Factor Authentication (MFA) What is it? Multi-Factor Authentication, or MFA, is an enhanced log in method that requires users to provide at least two
Merchant Toolkit Multi-Factor Authentication Multi-Factor Authentication (MFA) What is it? Multi-Factor Authentication, or MFA, is an enhanced log in method that requires users to provide at least two
DS-K2600 Series Access Controller. Quick Setup Guide. Ness V1.0
 DS-K2600 Series Access Controller Quick Setup Guide Ness V1.0 This is a Quick Setup Guide for Ness Version of Hikvision DS-K2604 4 Door Access Controllers. For full details refer Ness Full User Manual
DS-K2600 Series Access Controller Quick Setup Guide Ness V1.0 This is a Quick Setup Guide for Ness Version of Hikvision DS-K2604 4 Door Access Controllers. For full details refer Ness Full User Manual
Installation Guide. ZKAccess CLASSIC 3.5. www. zkaccess.com
 Installation Guide ZKAccess CLASSIC.5 www. zkaccess.com Contents Downloading... Installation & Adding an Area...4 Adding an Area...5 Adding a Device...6 To add a standalone device:... 6 To add an Access
Installation Guide ZKAccess CLASSIC.5 www. zkaccess.com Contents Downloading... Installation & Adding an Area...4 Adding an Area...5 Adding a Device...6 To add a standalone device:... 6 To add an Access
U.are.U Biometric Device Setup in Maitre D
 U.are.U Biometric Device Setup in Maitre D (Maitre D 2002, and later versions of Maitre D) Configuring the U.are.U Biometric device in Windows Installation The drivers and application will have to be installed
U.are.U Biometric Device Setup in Maitre D (Maitre D 2002, and later versions of Maitre D) Configuring the U.are.U Biometric device in Windows Installation The drivers and application will have to be installed
Setting up your Cooperating Personnel Account
 Setting up your Cooperating Personnel Account To set up your Cooperating Personnel Account, click on link in the To Retrieve your password, click here message. On the next screen, put the email address
Setting up your Cooperating Personnel Account To set up your Cooperating Personnel Account, click on link in the To Retrieve your password, click here message. On the next screen, put the email address
System Process Document Define Condition Processes. Department Responsibility/Role File Name. Define Condition Processes Trigger:
 Department Responsibility/Role File Name Define Condition Processes_SPD_20141224095142 Revision Document Generation Date Date Modified Last Changed by ctbrand2 12/18/2014 Status sent for review 12.25 12/24/2014
Department Responsibility/Role File Name Define Condition Processes_SPD_20141224095142 Revision Document Generation Date Date Modified Last Changed by ctbrand2 12/18/2014 Status sent for review 12.25 12/24/2014
device management The following policies can be applied to Knox container of Samsung devices. [Android OS, Samsung Only(Knox2+)]
![device management The following policies can be applied to Knox container of Samsung devices. [Android OS, Samsung Only(Knox2+)] device management The following policies can be applied to Knox container of Samsung devices. [Android OS, Samsung Only(Knox2+)]](/thumbs/96/127708785.jpg) Knox container device management policy The following policies can be applied to Knox container of Samsung devices. System group Screen capture Clipboard Share list Google account synchronization App crash
Knox container device management policy The following policies can be applied to Knox container of Samsung devices. System group Screen capture Clipboard Share list Google account synchronization App crash
Deprecating the Password: A Progress Report. Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018
 Deprecating the Password: A Progress Report Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018 The password problem Alpha-numeric passwords are hard for humans to remember and easy
Deprecating the Password: A Progress Report Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018 The password problem Alpha-numeric passwords are hard for humans to remember and easy
Overview. DigitalPersona Logon for Windows Data Sheet. DigitalPersona s Composite Authentication transforms
 DigitalPersona Logon for Windows Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond two-factor
DigitalPersona Logon for Windows Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond two-factor
Jumble Encryption for Microsoft Outlook
 Jumble Email Encryption for Microsoft Outlook Jumble provides truly usable and secure email encryption by integrating with existing email clients. Users can easily and securely communicate from their email
Jumble Email Encryption for Microsoft Outlook Jumble provides truly usable and secure email encryption by integrating with existing email clients. Users can easily and securely communicate from their email
Student Registration Instructions
 Student Registration Instructions Before you begin, you will need a 10-character Class Code provided by your instructor and a 20-character ALEKS Access Code. If you do not have an access code, you can
Student Registration Instructions Before you begin, you will need a 10-character Class Code provided by your instructor and a 20-character ALEKS Access Code. If you do not have an access code, you can
TOTALPASS SMALL BUSINESS PREMIUM BIOMETRIC QUICK START GUIDE PLEASE READ THIS FIRST
 TOTALPASS SMALL BUSINESS PREMIUM BIOMETRIC QUICK START GUIDE PLEASE READ THIS FIRST Version: 102016 1 UNPACK THE BOX Please confirm the contents of your system. If any item is missing, contact our support
TOTALPASS SMALL BUSINESS PREMIUM BIOMETRIC QUICK START GUIDE PLEASE READ THIS FIRST Version: 102016 1 UNPACK THE BOX Please confirm the contents of your system. If any item is missing, contact our support
Command Center Access Control Software
 Command Center Access Control Software System Administration and User Guide Version 2.0 Mailing Address: NextgenID, Ltd. 10226 San Pedro, Suite 100 San Antonio, TX 78216 USA Contacts: Phone: (210) 530-9991
Command Center Access Control Software System Administration and User Guide Version 2.0 Mailing Address: NextgenID, Ltd. 10226 San Pedro, Suite 100 San Antonio, TX 78216 USA Contacts: Phone: (210) 530-9991
