Finding Stable Extremal Region Boundaries
|
|
|
- Marvin McKinney
- 5 years ago
- Views:
Transcription
1 Finding Stable Extremal Region Boundaries Hayko Riemenschneider, Michael Donoser, and Horst Bischof Institute for Computer Graphics and Vision Graz University of Technology, Austria Abstract This paper introduces a novel boundary detection framework finding the most stable region boundaries in grayscale images. In contrast to common detection algorithms as Canny, which only analyze local discontinuities in image brightness our method also integrates mid-level information by analyzing regions that support the local gradient magnitudes. We build a component tree where every node contains a single connected region obtained from thresholding the input image and edges define the spatial relations between the nodes. Then connected nodes at different levels in the tree are compared by a simplified chamfer matching method. Matching regions have boundaries that stay similar over several image intensities, and thus contribute as stable edges to the final result. Since the component tree can be calculated in linear time and chamfer matching between nodes in the component tree is reduced to an analysis of the distance transformation, results are obtained in a very efficient manner. Furthermore, the proposed detection algorithm automatically labels all identified boundaries during calculation avoiding the required post-processing of connecting and labeling edge responses for usage in a detection framework. We compare our method against standard Canny and the Berkeley edge detector on the ETHZ shape classes and the Weizmann horses dataset, which both demonstrate better performance in reducing clutter. 1 Introduction Edge detection is one of the most intensively studied problems in computer vision. It is used in many applications like object detection, stereo matching, segmentation or tracking. Extracting edges mainly has the purpose of reducing the data amount while retaining the important information about the image content. In general, edge detection methods can be divided into unsupervised approaches which simply analyze local intensity differences and the recently popular group of supervised methods, which try to learn the appearance of edges, e. g. for specific tasks [5] or in a more general way for natural images [12, 13]. Of course, learning based methods provide improved results, nevertheless these methods have the main drawback of high computation time, for example in the range of 12 seconds [5] and 90 seconds [25]. Also for new specific tasks, they require ground truth labeling to learn a new detector. Therefore, purely local edge detectors are still of high interest because of their computational simplicity. This work was supported by the Austrian Research Promotion Agency (FFG) project FIT-IT CityFit (815971/ GLE/ROD) and the Austrian Science Fund (FWF) under the doctoral program Confluence of Vision and Graphics W1209.
2 Although edge detection has many different applications in computer vision, in this paper we mainly focus on the application of detecting objects in cluttered images. Recently many different shape cue based detection frameworks [6, 19, 21] were proposed achieving state-of-the-art results on reference datasets outperforming appearance based methods. All these methods still rely on a post-processed Canny edge [2] or Berkeley detection [13] result as input. Post-processing is necessary because the most object detection frameworks require labeled lists of connected edges in images, which is mostly done by analyzing T-junctions and building multiple branches of the obtained edges, or even complex contour grouping [7]. In this paper we introduce a novel boundary detection framework which outperforms local detectors as for example the Canny detector by additionally analyzing mid-level cues, i. e. regions that support the local gradient magnitude are analyzed to extract the most stable edges. We are able to remove a lot of noise in the edge images, preserving the important edges for detection. Furthermore, our method allows labeling of all obtained edges during calculation. Therefore, no post-processing is required and the results can be directly used in standard object detection frameworks. The outline of the paper is as follows. Section 2 gives an overview of the related works for Canny and Berkeley edge detection. Section 3 describes our novel boundary detection method in detail. Our method returns a list of labeled, connected edges that can be passed to any detection framework. In Section 4 we demonstrate on the well-known ETHZ shape classes dataset, that our proposed detection method outperforms other methods in the scope of object detection. Finally, Section 5 discusses our results and gives an outlook on future work in this area. 2 Related Work The most commonly used edge detection method is Canny [2]. It provides a simple and fast technique with the goals of many detections, accurate localization and single response per edge. The method itself is split in multiple stages. First, a Gaussian blurring is applied to reduce the noise of individual pixels. Second, a Gaussian derivative response is calculated in two directions and their magnitudes. These individual gradients are used to determine the maximum response of four directions, i. e. 0, 45, 90, 135 degree. The gradient image undergoes a non-maxima suppression to filter out weaker responses. An important aspect here is the thresholding of gradient responses, which is done by hysteresis thresholding in Canny. Hysteresis uses two thresholds, where gradients below the low threshold are not marked, and those above the high threshold are marked as edges. The gradient values which fall between the thresholds are only marked as an edge, if they are connected to an edge of strong gradients. In this work, we investigate the standard behavior of edge detection methods. For this purpose the Canny edge detection is run with standard thresholds, which are automatically calculated based on the gradient information. The high threshold is set to a value so that more than 70% of the pixels are not edges. In terms of strong responses, this results to edges for only the top 30% of the gradients. The low threshold is set to 40% of the high threshold. This is the standard method of automatic thresholding for Canny as it is implemented in Matlab. The Berkeley edge detector [13] is a supervised algorithm usually tuned to natural scenes. The method works by analyzing changes in image intensity, oriented energy, brightness gradient, color gradient, texture gradient and localized texture gradient. These image features are then combined to improve detection of natural boundaries. For the combination process supervised learning is applied which uses a ground truth dataset given by multiple human segmentations. In an experiment with humans
3 they asked them to draw boundaries of equally important things in the images. The results are accurate object boundaries. This ground truth was used in a logistic regression model to learn an optimal combination of the image features. The evaluation benchmark for their experiments is called the Berkeley segmentation benchmark and is publicly available 1. It will be the basis for our experiments in Section 4 and is described in more detail there. 3 Extremal Region Boundary Analysis Our boundary detection method is based on analyzing a specific data structure named the component tree, which can be build for any connected graph with node values coming from a totally ordered set. For example any grayscale image fulfills this requirement. Nevertheless, also color images can be analyzed if an ordering of the color pixels is provided, for example as shown by Forssén [8]. Section 3.1 describes how the component tree is built in an efficient manner. For detection of the edges, we then analyze the tree by comparing the outer contour of regions at different levels in the component tree by a simple partial shape matching method. In such a way we are able to measure the boundary stability of every region and to return the stable ones as our boundary detection result. In Section 3.2 this is explained in detail. 3.1 Component Tree For detecting stable boundaries in the image we analyze connected regions of binary threshold results, which Matas et al. denoted as extremal regions. Therefore we build a hierarchical data structure named component tree for the input grayscale image. The component tree, originally introduced in statistics [9, 24] for classification and clustering, was redefined by Jones [10] as a representation of a gray-level image that contains information about each image component and the links that exist between components at sequential gray-levels in the image. Jones further defines it as a set of nodes connected by a set of edges [10]. A component tree is an acyclic directed graph with nodes corresponding to pixels, or later extremal regions, and edges defining the relationships between their intensity levels. The root node connects all components merged into a complete representation of the input image. At any chosen intensity level of the hierarchy, the component tree contains the extremal regions detected at this level, see Figure 1 for an illustration of the component tree as a graph, a layered hierarchy and the underlying image information. The component tree inherently encodes the structure of the image by inclusion of a lower intensity level in the next intensity level. A component tree allows to quickly access extremal regions and to store the necessary meta-information in its nodes. There exist several approaches [4, 11, 15, 16, 17, 20] to build component trees. The approach by Najman and Couprie [16] delivers the best runtime complexity to maintain even in worstcase a very efficient algorithm. The most cited reference by Salembier et al. [20] proposes an algorithm determined to be of quadratic runtime for general cases [17]. However, for reduced ranges such as grayscale images, the algorithm would be twice as fast as Najman and Couprie. Najman and Couprie [16] describe an algorithm to build the component tree in quasi-linear time. The term quasi is an amortization of the costs required for the union / find problem, as described by Tarjan [23]. In detail the worst-case complexity is O(N α(n)) with α(n) being the inverse Ackermann 1
4 (a) Graph (b) Layers (c) Image Figure 1: Illustration of a component tree: a) Graph of connected region nodes with the intensity levels on the axis and the region sizes next to nodes. The root contains all pixels of the image. Corresponding hierarchical layers as shown in [10]. The rightmost part c) shows the corresponding image which is represented by the component tree. The component tree inherently encodes the structure of the image, for example by separating the lighter areas by splits in the tree structure. function, i. e. practically linear. Thus, the only other dependency is the sort process. For our approach a CountingSort [3] delivers the required linear complexity for sorting the image data. The high-level idea of [16] is to scan the nodes and their neighbors, which are initially just the pixels of an image. This is done in decreasing order of their intensity to group them whether they are of the same level or establish a hierarchical organization in partial trees. Najman and Couprie make use of two disjoint sets, one to build the partial trees and another to maintain the set of equivalent nodes. They define canonical nodes to be the dominant nodes chosen as representatives in a set of equivalent nodes or in a partial tree. The concept of union by rank, allowing the union of two sets to return a canonical node, is designed to stop complete degeneration of the tree. The second technique known as path compression creates a reference list of each node s root. This allows maintaining a low cost when finding and accessing the respective root nodes from any node within a partial tree without navigating up to the root. In these terms, every canonical node and its connected pixels represent an extremal region. Thus, for every node we can retrieve the pixels for the extremal region, its intensity level, the location of the region and its hierarchy in relation to other extremal regions. The component tree is also the basis for the calculation of Maximally Stable Extremal Regions (MSERs) [14]. Recently Nistér and Stewénius [18] even showed that calculating MSERs is possible in linear time. The distance transform only operates in a local window around the region contour and thus also only requires linear time. 3.2 Stable Extremal Regions Boundaries We now use the calculated component tree described in Section 3.1 for detecting and labeling boundaries in the input image. The underlying idea is quite similar to the detection of Maximally Stable Extremal Regions (MSER) as proposed by Matas et al. [14]. MSER detection also uses the component tree as data structure and returns the most stable nodes (extremal regions) of the tree as interest region detection results. The stability is estimated by comparing region sizes between nodes in adjacent levels of the tree. In our case we also estimate a stability value per node, but this time analyzing a boundary stability between the regions. Thus, in contrast to MSER detection which compares region sizes, we measure
5 how similar the outer contour of the regions is, i. e. if parts of the region boundary remain more or less the same over several levels of the component tree. We denote a region R g i as the extremal region in the component tree at the threshold g and unique identifier i. We define the stability value Ψ(R g i ) of a region R g i by comparing its neighboring region R g k, which is the extremal regions upwards the component tree. Starting from region R g i we move along the tree until a region with gray value g is found. Let C j and C k be the corresponding region boundaries for the current region and its neighbor, respectively. To measure the contour similarity and to identify similar parts between the regions, we apply a simplified version of the chamfer matching. Since regions within the tree can only grow and always are fixed at the same location, chamfer matching is reduced to an analysis of the distance transformation values. Here we describe the most simple approach of standard chamfer matching, but please note that more sophisticated methods, such as the rotational chamfer matching of Shotton et al. [22], or in general any partial shape matching method can be used in this step. Thus, as a first step we calculate the distance transformation DT j for the binary map containing the boundary pixels of C j. This distance transformation DT j allows to find partial matches between the boundaries C j and C k by finding connected chains C k C k fulfilling C k C k DT j ( Ck ) θ, (1) where θ is a maximum boundary distance parameter. Then, for a region R g i the stability value Ψ(R g i ) is set to the average chamfer distance of the matched boundary pixels C k by Ψ(R g i ) = 1 N N ( ) DT j Ck, (2) n=1 where N is the number of matched pixel. In this way we get a similarity measure Ψ(R g i ) and matched connected boundary chains for every comparison, and thus every extremal region. The idea is to integrate mid-level information by analyzing regions and matching boundaries that support the local gradient magnitudes. The parameter θ is set to ten and controls how much change in the contour is allowed. The parameter is two and describes how much contrast or intensity levels in terms of the component tree hierarchy are considered. After calculation of the stability values for every node in the component tree, we detect the most stable ones within the tree and return the corresponding boundary chains as detection result. Since every boundary can be uniquely assigned to a node in the tree, a unique ID can be assigned to every boundary detection. Therefore, cumbersome post-processing to connect and clean edges as for example required for the Canny or the Berkeley edge detector is not necessary. Please note, that the boundary detection results are quite different from simply returning the boundaries of an MSER detection result. First, since we find similar outer contours between extremal regions at different intensity levels, the returned boundaries need not be closed and can represent only part of region s outer contour. Furthermore, since our analysis focuses on whether local parts of the boundary are stable and not only the region sizes. The MSERs for the same image can differ significantly.
6 (a) Input (b) Score response (c) Our boundary labels Figure 2: Example of the detection process. For an input image a) a component tree is built for all intensity levels. Outer contour matching between the extremal regions returns a score for each boundary match, which summed up creates b) the score response. The final result c) are the boundary detections and their unique labels. Refer to Figure 2 for an illustration of the steps when processing an input image and the retrieved gradient and label results. The component tree is build for the intensity levels of the image. The chamfer matching returns a score for every boundary fragment of the extremal regions. The sum over all these scores is returned as a gradient map. However, the final results are our boundary detections and their unique labels, as shown in the right-most part of the figure. (a) 1009 (b) 1009 (c) 1011 (d) 1011 (e) 1014 (f) 1014 (g) 1016 (h) 1016 (i) 2127 (j) 2127 (k) 2167 (l) 2167 Figure 3: Overview of the ETHZ shape classes [7] (here only apple logos) and their respective ground truth and some horses from the Weizmann dataset [1]. These ground truths are used in the evaluation of edge detection results.
7 # P R F ETHZ apple logo # P R F Weizmann horses Human segmentation Human segmentation Our detector BEL Horse edges [5] Berkeley edges [13] Our detector Canny edges [2] Canny edges [2] Table 1: Comparison over the overall F-measure performance of each algorithm for the two datasets ETHZ shape class apple logo [7] and Weizmann horses [1]. Please note, that the benchmark is very strict given that only boundaries of the apple logo and horses are marked in the human ground truth segmentation. Our boundary detector provides an encouraging improvement over the Berkeley and Canny edge responses. 4 Experiments and Discussion The focus of the experimental evaluation lies in demonstrating the reduced noise and high retrieval of valuable stable edges. For this we employ the Berkeley segmentation benchmark, which allows to measure the quality of edge maps compared to human ground truth data. In this work we use the ETHZ shape classes [7] and Weizmann horses [1], and a set of figure / ground segmentations as ground truth. For the ETHZ dataset, we created the figure / ground segmentation, whereas for the Weizmann horses it was provided. In both cases the segmentations are object specific and based on the actual image data. Thus, the results are very accurate given the specific object, see Figure 3 for a small subset of ground truth examples. For evaluation of the results respective to this new defined ground truth data, the edge detection results are compared to the ground truth in the same manner as in the Berkeley segmentation benchmark. This is the pixelwise comparison between two binary images. The result of each edge detection process is a set of binary edges in the image. The Berkeley benchmark prefers softmaps, which encode all responses of the edge detector and then determines the best threshold. However, this is not the focus of our evaluation. We wish to show that given the standard thresholds provided by an edge detector (without any manual tuning), our boundary detector provides exacter edges and far less noise than for example a Canny or Berkeley edge detection. We use precision and recall as measures for evaluation. Precision in our case is the probability that a detected boundary pixel is a true boundary pixel. Recall is the probability that a true boundary pixel is detected by the algorithm. Further, we calculate the F-measure as a final comparison value defined as weighted harmonic mean of precision and recall: P = T P d T P d + F P d and R = T P d and F = 2 P R T P d + F N d P + R (3) where T P d are all true boundary pixels detected and the denominators (T P d +F P d ) and (T P d +F N d ) are all boundary pixels given by the algorithm and all boundary pixels defined in the ground truth data, respectively. The Berkeley benchmark provides precision and recall curves for each threshold of the image. Since all edge responses tested here are binary, we retrieve a single value per image. Using binary responses we can focus on the actual edges returned by an edge detector, rather than all the noisy unimportant responses. We convert our boundary detection labels also to binary edge masks. Table 1 shows the result of the experiments. For comparison we tested the automatic threshold for a Canny edge detection, all edges of the Berkeley edge detector, which is provided for the ETHZ
8 dataset, and our detection results. A similar procedure was followed for the Weizmann horse dataset, here we give results for provided edge response from Boosted Edge Learning (BEL) for horses, again standard Canny edge response and finally our boundary detector. The improvement of our boundary detector are encouraging for both dataset (20% gain for ETHZ and 12% gain for the Weizmann over standard Canny). For the learned detectors, we achieve better results than the Berkeley detector (10%) and worse results against the BEL results specifically trained to horses while our approach does not use any prior shape information. The advantages of our algorithm are clear when looking at Figure 4. Our boundary detector produces far less noise when detecting edges. Only boundaries are returned which are stable due to their support from larger regions. This removes a lot of the cluttered edges which are present in other edge detection algorithms. Occasionally some edges are missing, which are present in the highly dense responses of Canny, which reflects in the lower recall than other detection methods. In general, the precision values are very low since our evaluation strategy is very strict. Only boundaries of the respective object class are marked as true boundaries, and thus any other strong edge response is seen as a false positive. This is less severe in the case of the Weizmann horses, since the horses are the only dominant object in the images. There exists a lot more background information with strong edges for the ETHZ shape classes. The second advantage is the implicit labeling returned by our approach. In contrast to the edge responses from Canny or Berkeley, our boundaries are connected and uniquely labeled. This provides a major benefit. First, no post-processing is required to dissect edges from the cluttered responses and split at T-junctions. Second, no additional linking into lists is required. And most valuable complex perceptual grouping is not needed. Our boundary detector inherently provides grouped and connected boundaries, which would otherwise require costly and sometimes destructive post-processing 2. Of course, in the future we have to evaluate in more detail how boundary detection influences a subsequent object detection step. It would be interesting to see if the removal of noisy edges only reduces computation time or if even detection quality can be improved. 5 Conclusion and Outlook This paper introduced a novel boundary detection algorithm, based on the idea of analyzing extremal regions within a component tree and measuring their boundary stability by a shape comparison. The benefit of this detector is the integration of context information in terms of support by connected regions. Experimental evaluations using the Berkeley segmentation benchmark on different datasets proved that our detector demonstrates significant improvement over standard approaches like Canny edge detection. It accurately removes noise and clutter and delivers a cleaner, more precise and still rich edge response. Future work will focus on the integration of other partial shape matching methods for evaluation of the stability. We will test our detector response in different detection frameworks and investigate the benefit when integrating color similar to Forssén [8]. Another idea is to learn the appearance for certain classes as new input to improve the detection results. Finally, an interesting idea is to evaluate the repeatability of our stable boundary detector for use as interest points. 2 Splitting an edge response at a T-junction leaves three or more edges only as parts of the original edge behind. Their complete contour is lost unless costly merging of all combinations or perceptual grouping is performed
9 Figure 4: Results for the ETHZ shape class apple logo [7] and Weizmann horses [1] shown from left to right by the 1) input images, 2) the human ground truth, 3) the Berkeley [13] and 4) Canny edge [2] responses, and 5) our boundary detection labels. These results show the improvement of our boundary detector over the standard edge responses of other detection algorithms. Our detector returns far less noise and still precise stable edges, and additionally the boundary responses are already connected and uniquely labeled. This removes the requirement for expensive post-processing and grouping required for other methods. Please note, the edges are thickened for better visual appearance and our boundary labels are best viewed in color.
10 References [1] E. Borenstein and S. Ullman. Learning to Segment. In Proceedings of the European Conference on Computer Vision (ECCV), volume 3, pages , [2] J. Canny. A computational approach to edge detection. IEEE Transations Pattern Analysis Machine Intelligence (PAMI), 8(6): , November [3] T. Cormen, Ch. Leiserson, and R. Rivest. Introduction to Algorithms. The MIT Press, June [4] M. Couprie, L. Najman, and G. Bertrand. Quasi-Linear Algorithms for the Topological Watershed. Journal of Mathematical Imaging and Vision (JMIV), 22(2 3): , January [5] P. Dollar, Z. Tu, and S. Belongie. Supervised Learning of Edges and Object Boundaries. In Proceedings of the Conference on Computer Vision and Pattern Recognition (CVPR), pages , Washington, DC, USA, [6] V. Ferrari, L. Fevrier, F. Jurie, and C. Schmid. Groups of Adjacent Contour Segments for Object Detection. IEEE Transations Pattern Analysis Machine Intelligence (PAMI), 30(1):36 51, January [7] V. Ferrari, T. Tuytelaars, and L. Van Gool. Object Detection by Contour Segment Networks. In Proceedings of the European Conference on Computer Vision (ECCV), volume 3, pages 14 28, [8] P. Forssén. Maximally Stable Colour Regions for Recognition and Matching. In Proceedings of the Conference on Computer Vision and Pattern Recognition (CVPR), Minneapolis, USA, June IEEE Computer Society, IEEE. [9] J. Hartigan. Statistical theory in clustering. Journal of Classification (JOC), 2:63 76, [10] R. Jones. Component trees for image filtering and segmentation. In IEEE Workshop on Nonlinear Signal and Image Processing (NSIP), September [11] R. Jones. Connected filtering and segmentation using component trees. Journal of Computer Vision and Image Understanding (CVIU), 75(3): , [12] S. Konishi, A. Yuille, J. Coughlan, and S. Zhu. Statistical edge detection: learning and evaluating edge cues. IEEE Transactions on Pattern Analysis and Machine Intelligence (PAMI), 25:57 74, January [13] D. Martin, C. Fowlkes, and J. Malik. Learning to detect natural image boundaries using local brightness, color, and texture cues. IEEE Transactions on Pattern Analysis and Machine Intelligence (PAMI), 26(5): , [14] J. Matas, O. Chum, U. Martin, and T. Pajdla. Robust Wide Baseline Stereo from Maximally Stable Extremal Regions. In Proceedings of British Machine Vision Conference (BMVC), volume 1, pages , [15] V. Mosorov and T. M. Kowalski. The development of component tree structure for grayscale image segmentation. In Conference on Modern Problems of Radio Engineering, Telecommunications and Computer Science (TCSET), pages , February 2002.
11 [16] L. Najman and M. Couprie. Quasi-linear algorithm for the component tree. In L. Latecki, D. Mount, and A. Wu, editors, IS&T/SPIE Symposium on Electronic Imaging, Vision Geometry XII, volume 5300, pages , [17] L. Najman and M. Couprie. Building the Component Tree in Quasi-Linear Time. IEEE Transactions on Image Processing (TIP), 15(11): , November [18] D. Nistér and H. Stewénius. Linear Time Maximally Stable Extremal Regions. In Proceedings of the European Conference on Computer Vision (ECCV), pages , Berlin, Heidelberg, Springer-Verlag. [19] A. Opelt, A. Pinz, and A. Zisserman. A Boundary-Fragment-Model for Object Detection. In Proceedings of the European Conference on Computer Vision (ECCV), volume 2, pages , [20] P. Salembier, A. Oliveras, and L. Garrido. Anti-extensive connected operators for image and sequence processing. IEEE Transactions on Image Processing (TIP), 7(4): , April [21] J. Shotton, A. Blake, and R. Cipolla. Contour-Based Learning for Object Detection. In Proceedings of International Conference on Computer Vision (ICCV), pages , [22] J. Shotton, A. Blake, and R. Cipolla. Multiscale Categorical Object Recognition Using Contour Fragments. IEEE Transactions on Pattern Analysis and Machine Intelligence (PAMI), 30(7): , [23] R. Tarjan. Efficiency of a Good But Not Linear Set Union Algorithm. Journal of the ACM (JACM), 22(2): , April [24] D. Wishart. Mode analysis: A generalization of the nearest neighbor which reduces chaining effects. A. J. Cole, editor, Numerical Taxonomy, 2: , [25] S. Zheng, Z. Tu, and A. Yuille. Detecting Object Boundaries Using Low-, Mid-, and High-level Information. In Proceedings of the Conference on Computer Vision and Pattern Recognition (CVPR), 2007.
Bag of Optical Flow Volumes for Image Sequence Recognition 1
 RIEMENSCHNEIDER, DONOSER, BISCHOF: BAG OF OPTICAL FLOW VOLUMES 1 Bag of Optical Flow Volumes for Image Sequence Recognition 1 Hayko Riemenschneider http://www.icg.tugraz.at/members/hayko Michael Donoser
RIEMENSCHNEIDER, DONOSER, BISCHOF: BAG OF OPTICAL FLOW VOLUMES 1 Bag of Optical Flow Volumes for Image Sequence Recognition 1 Hayko Riemenschneider http://www.icg.tugraz.at/members/hayko Michael Donoser
Efficient Maximally Stable Extremal Region (MSER) Tracking
 Efficient Maximally Stable Extremal Region (MSER) Tracking Michael Donoser and Horst Bischof Institute for Computer Graphics and Vision Graz University of Technology {donoser,bischof}@icg.tu-graz.ac.at
Efficient Maximally Stable Extremal Region (MSER) Tracking Michael Donoser and Horst Bischof Institute for Computer Graphics and Vision Graz University of Technology {donoser,bischof}@icg.tu-graz.ac.at
Discovering Visual Hierarchy through Unsupervised Learning Haider Razvi
 Discovering Visual Hierarchy through Unsupervised Learning Haider Razvi hrazvi@stanford.edu 1 Introduction: We present a method for discovering visual hierarchy in a set of images. Automatically grouping
Discovering Visual Hierarchy through Unsupervised Learning Haider Razvi hrazvi@stanford.edu 1 Introduction: We present a method for discovering visual hierarchy in a set of images. Automatically grouping
Specular 3D Object Tracking by View Generative Learning
 Specular 3D Object Tracking by View Generative Learning Yukiko Shinozuka, Francois de Sorbier and Hideo Saito Keio University 3-14-1 Hiyoshi, Kohoku-ku 223-8522 Yokohama, Japan shinozuka@hvrl.ics.keio.ac.jp
Specular 3D Object Tracking by View Generative Learning Yukiko Shinozuka, Francois de Sorbier and Hideo Saito Keio University 3-14-1 Hiyoshi, Kohoku-ku 223-8522 Yokohama, Japan shinozuka@hvrl.ics.keio.ac.jp
Robust Online Object Learning and Recognition by MSER Tracking
 Computer Vision Winter Workshop 28, Janez Perš (ed.) Moravske Toplice, Slovenia, February 4 6 Slovenian Pattern Recognition Society, Ljubljana, Slovenia Robust Online Object Learning and Recognition by
Computer Vision Winter Workshop 28, Janez Perš (ed.) Moravske Toplice, Slovenia, February 4 6 Slovenian Pattern Recognition Society, Ljubljana, Slovenia Robust Online Object Learning and Recognition by
Edges and Binary Image Analysis April 12 th, 2018
 4/2/208 Edges and Binary Image Analysis April 2 th, 208 Yong Jae Lee UC Davis Previously Filters allow local image neighborhood to influence our description and features Smoothing to reduce noise Derivatives
4/2/208 Edges and Binary Image Analysis April 2 th, 208 Yong Jae Lee UC Davis Previously Filters allow local image neighborhood to influence our description and features Smoothing to reduce noise Derivatives
Discriminative Learning of Contour Fragments for Object Detection
 KONTSCHIEDER et al.: DISCRIMINATIVE CONTOUR FRAGMENT LEARNING 1 Discriminative Learning of Contour Fragments for Object Detection Peter Kontschieder kontschieder@icg.tugraz.at Hayko Riemenschneider hayko@icg.tugraz.at
KONTSCHIEDER et al.: DISCRIMINATIVE CONTOUR FRAGMENT LEARNING 1 Discriminative Learning of Contour Fragments for Object Detection Peter Kontschieder kontschieder@icg.tugraz.at Hayko Riemenschneider hayko@icg.tugraz.at
Shape Descriptors for Maximally Stable Extremal Regions
 Shape Descriptors for Maximally Stable Extremal Regions Per-Erik Forssén and David G. Lowe Department of Computer Science University of British Columbia {perfo,lowe}@cs.ubc.ca Abstract This paper introduces
Shape Descriptors for Maximally Stable Extremal Regions Per-Erik Forssén and David G. Lowe Department of Computer Science University of British Columbia {perfo,lowe}@cs.ubc.ca Abstract This paper introduces
Supervised texture detection in images
 Supervised texture detection in images Branislav Mičušík and Allan Hanbury Pattern Recognition and Image Processing Group, Institute of Computer Aided Automation, Vienna University of Technology Favoritenstraße
Supervised texture detection in images Branislav Mičušík and Allan Hanbury Pattern Recognition and Image Processing Group, Institute of Computer Aided Automation, Vienna University of Technology Favoritenstraße
Detecting Printed and Handwritten Partial Copies of Line Drawings Embedded in Complex Backgrounds
 9 1th International Conference on Document Analysis and Recognition Detecting Printed and Handwritten Partial Copies of Line Drawings Embedded in Complex Backgrounds Weihan Sun, Koichi Kise Graduate School
9 1th International Conference on Document Analysis and Recognition Detecting Printed and Handwritten Partial Copies of Line Drawings Embedded in Complex Backgrounds Weihan Sun, Koichi Kise Graduate School
Evaluation and comparison of interest points/regions
 Introduction Evaluation and comparison of interest points/regions Quantitative evaluation of interest point/region detectors points / regions at the same relative location and area Repeatability rate :
Introduction Evaluation and comparison of interest points/regions Quantitative evaluation of interest point/region detectors points / regions at the same relative location and area Repeatability rate :
UNSUPERVISED OBJECT MATCHING AND CATEGORIZATION VIA AGGLOMERATIVE CORRESPONDENCE CLUSTERING
 UNSUPERVISED OBJECT MATCHING AND CATEGORIZATION VIA AGGLOMERATIVE CORRESPONDENCE CLUSTERING Md. Shafayat Hossain, Ahmedullah Aziz and Mohammad Wahidur Rahman Department of Electrical and Electronic Engineering,
UNSUPERVISED OBJECT MATCHING AND CATEGORIZATION VIA AGGLOMERATIVE CORRESPONDENCE CLUSTERING Md. Shafayat Hossain, Ahmedullah Aziz and Mohammad Wahidur Rahman Department of Electrical and Electronic Engineering,
Edges and Binary Images
 CS 699: Intro to Computer Vision Edges and Binary Images Prof. Adriana Kovashka University of Pittsburgh September 5, 205 Plan for today Edge detection Binary image analysis Homework Due on 9/22, :59pm
CS 699: Intro to Computer Vision Edges and Binary Images Prof. Adriana Kovashka University of Pittsburgh September 5, 205 Plan for today Edge detection Binary image analysis Homework Due on 9/22, :59pm
3 October, 2013 MVA ENS Cachan. Lecture 2: Logistic regression & intro to MIL Iasonas Kokkinos
 Machine Learning for Computer Vision 1 3 October, 2013 MVA ENS Cachan Lecture 2: Logistic regression & intro to MIL Iasonas Kokkinos Iasonas.kokkinos@ecp.fr Department of Applied Mathematics Ecole Centrale
Machine Learning for Computer Vision 1 3 October, 2013 MVA ENS Cachan Lecture 2: Logistic regression & intro to MIL Iasonas Kokkinos Iasonas.kokkinos@ecp.fr Department of Applied Mathematics Ecole Centrale
Robust Zero Watermarking for Still and Similar Images Using a Learning Based Contour Detection
 Robust Zero Watermarking for Still and Similar Images Using a Learning Based Contour Detection Shahryar Ehsaee and Mansour Jamzad (&) Department of Computer Engineering, Sharif University of Technology,
Robust Zero Watermarking for Still and Similar Images Using a Learning Based Contour Detection Shahryar Ehsaee and Mansour Jamzad (&) Department of Computer Engineering, Sharif University of Technology,
[ ] Review. Edges and Binary Images. Edge detection. Derivative of Gaussian filter. Image gradient. Tuesday, Sept 16
![[ ] Review. Edges and Binary Images. Edge detection. Derivative of Gaussian filter. Image gradient. Tuesday, Sept 16 [ ] Review. Edges and Binary Images. Edge detection. Derivative of Gaussian filter. Image gradient. Tuesday, Sept 16](/thumbs/89/98496315.jpg) Review Edges and Binary Images Tuesday, Sept 6 Thought question: how could we compute a temporal gradient from video data? What filter is likely to have produced this image output? original filtered output
Review Edges and Binary Images Tuesday, Sept 6 Thought question: how could we compute a temporal gradient from video data? What filter is likely to have produced this image output? original filtered output
From Partial Shape Matching through Local Deformation to Robust Global Shape Similarity for Object Detection
 CVPR 2 From Partial Shape Matching through Local Deformation to Robust Global Shape Similarity for Object Detection Tianyang Ma and Longin Jan Latecki Dept. of Computer and Information Sciences, Temple
CVPR 2 From Partial Shape Matching through Local Deformation to Robust Global Shape Similarity for Object Detection Tianyang Ma and Longin Jan Latecki Dept. of Computer and Information Sciences, Temple
Beyond Bags of Features
 : for Recognizing Natural Scene Categories Matching and Modeling Seminar Instructed by Prof. Haim J. Wolfson School of Computer Science Tel Aviv University December 9 th, 2015
: for Recognizing Natural Scene Categories Matching and Modeling Seminar Instructed by Prof. Haim J. Wolfson School of Computer Science Tel Aviv University December 9 th, 2015
Learning and Inferring Depth from Monocular Images. Jiyan Pan April 1, 2009
 Learning and Inferring Depth from Monocular Images Jiyan Pan April 1, 2009 Traditional ways of inferring depth Binocular disparity Structure from motion Defocus Given a single monocular image, how to infer
Learning and Inferring Depth from Monocular Images Jiyan Pan April 1, 2009 Traditional ways of inferring depth Binocular disparity Structure from motion Defocus Given a single monocular image, how to infer
Global Probability of Boundary
 Global Probability of Boundary Learning to Detect Natural Image Boundaries Using Local Brightness, Color, and Texture Cues Martin, Fowlkes, Malik Using Contours to Detect and Localize Junctions in Natural
Global Probability of Boundary Learning to Detect Natural Image Boundaries Using Local Brightness, Color, and Texture Cues Martin, Fowlkes, Malik Using Contours to Detect and Localize Junctions in Natural
Effects Of Shadow On Canny Edge Detection through a camera
 1523 Effects Of Shadow On Canny Edge Detection through a camera Srajit Mehrotra Shadow causes errors in computer vision as it is difficult to detect objects that are under the influence of shadows. Shadow
1523 Effects Of Shadow On Canny Edge Detection through a camera Srajit Mehrotra Shadow causes errors in computer vision as it is difficult to detect objects that are under the influence of shadows. Shadow
Previously. Edge detection. Today. Thresholding. Gradients -> edges 2/1/2011. Edges and Binary Image Analysis
 2//20 Previously Edges and Binary Image Analysis Mon, Jan 3 Prof. Kristen Grauman UT-Austin Filters allow local image neighborhood to influence our description and features Smoothing to reduce noise Derivatives
2//20 Previously Edges and Binary Image Analysis Mon, Jan 3 Prof. Kristen Grauman UT-Austin Filters allow local image neighborhood to influence our description and features Smoothing to reduce noise Derivatives
Boundaries and Sketches
 Boundaries and Sketches Szeliski 4.2 Computer Vision James Hays Many slides from Michael Maire, Jitendra Malek Today s lecture Segmentation vs Boundary Detection Why boundaries / Grouping? Recap: Canny
Boundaries and Sketches Szeliski 4.2 Computer Vision James Hays Many slides from Michael Maire, Jitendra Malek Today s lecture Segmentation vs Boundary Detection Why boundaries / Grouping? Recap: Canny
Computer Vision I - Basics of Image Processing Part 2
 Computer Vision I - Basics of Image Processing Part 2 Carsten Rother 07/11/2014 Computer Vision I: Basics of Image Processing Roadmap: Basics of Digital Image Processing Computer Vision I: Basics of Image
Computer Vision I - Basics of Image Processing Part 2 Carsten Rother 07/11/2014 Computer Vision I: Basics of Image Processing Roadmap: Basics of Digital Image Processing Computer Vision I: Basics of Image
Combining Top-down and Bottom-up Segmentation
 Combining Top-down and Bottom-up Segmentation Authors: Eran Borenstein, Eitan Sharon, Shimon Ullman Presenter: Collin McCarthy Introduction Goal Separate object from background Problems Inaccuracies Top-down
Combining Top-down and Bottom-up Segmentation Authors: Eran Borenstein, Eitan Sharon, Shimon Ullman Presenter: Collin McCarthy Introduction Goal Separate object from background Problems Inaccuracies Top-down
Investigating How and When Perceptual Organization Cues Improve Boundary Detection in Natural Images
 Investigating How and When Perceptual Organization Cues Improve Boundary Detection in Natural Images Leandro A. Loss, George Bebis, Mircea Nicolescu Computer Vision Laboratory University of Nevada, Reno
Investigating How and When Perceptual Organization Cues Improve Boundary Detection in Natural Images Leandro A. Loss, George Bebis, Mircea Nicolescu Computer Vision Laboratory University of Nevada, Reno
Speeding up the Detection of Line Drawings Using a Hash Table
 Speeding up the Detection of Line Drawings Using a Hash Table Weihan Sun, Koichi Kise 2 Graduate School of Engineering, Osaka Prefecture University, Japan sunweihan@m.cs.osakafu-u.ac.jp, 2 kise@cs.osakafu-u.ac.jp
Speeding up the Detection of Line Drawings Using a Hash Table Weihan Sun, Koichi Kise 2 Graduate School of Engineering, Osaka Prefecture University, Japan sunweihan@m.cs.osakafu-u.ac.jp, 2 kise@cs.osakafu-u.ac.jp
Fusing shape and appearance information for object category detection
 1 Fusing shape and appearance information for object category detection Andreas Opelt, Axel Pinz Graz University of Technology, Austria Andrew Zisserman Dept. of Engineering Science, University of Oxford,
1 Fusing shape and appearance information for object category detection Andreas Opelt, Axel Pinz Graz University of Technology, Austria Andrew Zisserman Dept. of Engineering Science, University of Oxford,
Comparison between Various Edge Detection Methods on Satellite Image
 Comparison between Various Edge Detection Methods on Satellite Image H.S. Bhadauria 1, Annapurna Singh 2, Anuj Kumar 3 Govind Ballabh Pant Engineering College ( Pauri garhwal),computer Science and Engineering
Comparison between Various Edge Detection Methods on Satellite Image H.S. Bhadauria 1, Annapurna Singh 2, Anuj Kumar 3 Govind Ballabh Pant Engineering College ( Pauri garhwal),computer Science and Engineering
Fuzzy based Multiple Dictionary Bag of Words for Image Classification
 Available online at www.sciencedirect.com Procedia Engineering 38 (2012 ) 2196 2206 International Conference on Modeling Optimisation and Computing Fuzzy based Multiple Dictionary Bag of Words for Image
Available online at www.sciencedirect.com Procedia Engineering 38 (2012 ) 2196 2206 International Conference on Modeling Optimisation and Computing Fuzzy based Multiple Dictionary Bag of Words for Image
Edge Detection Using Convolutional Neural Network
 Edge Detection Using Convolutional Neural Network Ruohui Wang (B) Department of Information Engineering, The Chinese University of Hong Kong, Hong Kong, China wr013@ie.cuhk.edu.hk Abstract. In this work,
Edge Detection Using Convolutional Neural Network Ruohui Wang (B) Department of Information Engineering, The Chinese University of Hong Kong, Hong Kong, China wr013@ie.cuhk.edu.hk Abstract. In this work,
CS6716 Pattern Recognition
 CS6716 Pattern Recognition Aaron Bobick School of Interactive Computing Administrivia PS3 is out now, due April 8. Today chapter 12 of the Hastie book. Slides (and entertainment) from Moataz Al-Haj Three
CS6716 Pattern Recognition Aaron Bobick School of Interactive Computing Administrivia PS3 is out now, due April 8. Today chapter 12 of the Hastie book. Slides (and entertainment) from Moataz Al-Haj Three
Noise Robustness of Irregular LBP Pyramids
 Noise Robustness of Irregular LBP Pyramids Christoph Körner, Ines Janusch, Walter G. Kropatsch Pattern Recognition and Image Processing (PRIP) Vienna University of Technology, Austria {christoph,ines,krw}@prip.tuwien.ac.at
Noise Robustness of Irregular LBP Pyramids Christoph Körner, Ines Janusch, Walter G. Kropatsch Pattern Recognition and Image Processing (PRIP) Vienna University of Technology, Austria {christoph,ines,krw}@prip.tuwien.ac.at
Topic 4 Image Segmentation
 Topic 4 Image Segmentation What is Segmentation? Why? Segmentation important contributing factor to the success of an automated image analysis process What is Image Analysis: Processing images to derive
Topic 4 Image Segmentation What is Segmentation? Why? Segmentation important contributing factor to the success of an automated image analysis process What is Image Analysis: Processing images to derive
Deep Tracking: Biologically Inspired Tracking with Deep Convolutional Networks
 Deep Tracking: Biologically Inspired Tracking with Deep Convolutional Networks Si Chen The George Washington University sichen@gwmail.gwu.edu Meera Hahn Emory University mhahn7@emory.edu Mentor: Afshin
Deep Tracking: Biologically Inspired Tracking with Deep Convolutional Networks Si Chen The George Washington University sichen@gwmail.gwu.edu Meera Hahn Emory University mhahn7@emory.edu Mentor: Afshin
Feature Detectors - Canny Edge Detector
 Feature Detectors - Canny Edge Detector 04/12/2006 07:00 PM Canny Edge Detector Common Names: Canny edge detector Brief Description The Canny operator was designed to be an optimal edge detector (according
Feature Detectors - Canny Edge Detector 04/12/2006 07:00 PM Canny Edge Detector Common Names: Canny edge detector Brief Description The Canny operator was designed to be an optimal edge detector (according
Similar Fragment Retrieval of Animations by a Bag-of-features Approach
 Similar Fragment Retrieval of Animations by a Bag-of-features Approach Weihan Sun, Koichi Kise Dept. Computer Science and Intelligent Systems Osaka Prefecture University Osaka, Japan sunweihan@m.cs.osakafu-u.ac.jp,
Similar Fragment Retrieval of Animations by a Bag-of-features Approach Weihan Sun, Koichi Kise Dept. Computer Science and Intelligent Systems Osaka Prefecture University Osaka, Japan sunweihan@m.cs.osakafu-u.ac.jp,
Bundling Features for Large Scale Partial-Duplicate Web Image Search
 Bundling Features for Large Scale Partial-Duplicate Web Image Search Zhong Wu, Qifa Ke, Michael Isard, and Jian Sun Microsoft Research Abstract In state-of-the-art image retrieval systems, an image is
Bundling Features for Large Scale Partial-Duplicate Web Image Search Zhong Wu, Qifa Ke, Michael Isard, and Jian Sun Microsoft Research Abstract In state-of-the-art image retrieval systems, an image is
Review of Filtering. Filtering in frequency domain
 Review of Filtering Filtering in frequency domain Can be faster than filtering in spatial domain (for large filters) Can help understand effect of filter Algorithm: 1. Convert image and filter to fft (fft2
Review of Filtering Filtering in frequency domain Can be faster than filtering in spatial domain (for large filters) Can help understand effect of filter Algorithm: 1. Convert image and filter to fft (fft2
Edge detection. Winter in Kraków photographed by Marcin Ryczek
 Edge detection Winter in Kraków photographed by Marcin Ryczek Edge detection Goal: Identify sudden changes (discontinuities) in an image Intuitively, edges carry most of the semantic and shape information
Edge detection Winter in Kraków photographed by Marcin Ryczek Edge detection Goal: Identify sudden changes (discontinuities) in an image Intuitively, edges carry most of the semantic and shape information
A Robust Method for Circle / Ellipse Extraction Based Canny Edge Detection
 International Journal of Research Studies in Science, Engineering and Technology Volume 2, Issue 5, May 2015, PP 49-57 ISSN 2349-4751 (Print) & ISSN 2349-476X (Online) A Robust Method for Circle / Ellipse
International Journal of Research Studies in Science, Engineering and Technology Volume 2, Issue 5, May 2015, PP 49-57 ISSN 2349-4751 (Print) & ISSN 2349-476X (Online) A Robust Method for Circle / Ellipse
Local invariant features
 Local invariant features Tuesday, Oct 28 Kristen Grauman UT-Austin Today Some more Pset 2 results Pset 2 returned, pick up solutions Pset 3 is posted, due 11/11 Local invariant features Detection of interest
Local invariant features Tuesday, Oct 28 Kristen Grauman UT-Austin Today Some more Pset 2 results Pset 2 returned, pick up solutions Pset 3 is posted, due 11/11 Local invariant features Detection of interest
Edge Detection. Computer Vision Shiv Ram Dubey, IIIT Sri City
 Edge Detection Computer Vision Shiv Ram Dubey, IIIT Sri City Previous two classes: Image Filtering Spatial domain Smoothing, sharpening, measuring texture * = FFT FFT Inverse FFT = Frequency domain Denoising,
Edge Detection Computer Vision Shiv Ram Dubey, IIIT Sri City Previous two classes: Image Filtering Spatial domain Smoothing, sharpening, measuring texture * = FFT FFT Inverse FFT = Frequency domain Denoising,
Edge and corner detection
 Edge and corner detection Prof. Stricker Doz. G. Bleser Computer Vision: Object and People Tracking Goals Where is the information in an image? How is an object characterized? How can I find measurements
Edge and corner detection Prof. Stricker Doz. G. Bleser Computer Vision: Object and People Tracking Goals Where is the information in an image? How is an object characterized? How can I find measurements
A Clustering Based Method for Edge Detection in Hyperspectral Images
 A Clustering Based Method for Edge Detection in Hyperspectral Images V.C. Dinh 1,2, Raimund Leitner 2, Pavel Paclik 3,andRobertP.W.Duin 1 1 ICT Group, Delft University of Technology, Delft, The Netherlands
A Clustering Based Method for Edge Detection in Hyperspectral Images V.C. Dinh 1,2, Raimund Leitner 2, Pavel Paclik 3,andRobertP.W.Duin 1 1 ICT Group, Delft University of Technology, Delft, The Netherlands
Solution: filter the image, then subsample F 1 F 2. subsample blur subsample. blur
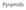 Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Motion illusion, rotating snakes
 Motion illusion, rotating snakes Local features: main components 1) Detection: Find a set of distinctive key points. 2) Description: Extract feature descriptor around each interest point as vector. x 1
Motion illusion, rotating snakes Local features: main components 1) Detection: Find a set of distinctive key points. 2) Description: Extract feature descriptor around each interest point as vector. x 1
RSRN: Rich Side-output Residual Network for Medial Axis Detection
 RSRN: Rich Side-output Residual Network for Medial Axis Detection Chang Liu, Wei Ke, Jianbin Jiao, and Qixiang Ye University of Chinese Academy of Sciences, Beijing, China {liuchang615, kewei11}@mails.ucas.ac.cn,
RSRN: Rich Side-output Residual Network for Medial Axis Detection Chang Liu, Wei Ke, Jianbin Jiao, and Qixiang Ye University of Chinese Academy of Sciences, Beijing, China {liuchang615, kewei11}@mails.ucas.ac.cn,
A Hierarchical Compositional System for Rapid Object Detection
 A Hierarchical Compositional System for Rapid Object Detection Long Zhu and Alan Yuille Department of Statistics University of California at Los Angeles Los Angeles, CA 90095 {lzhu,yuille}@stat.ucla.edu
A Hierarchical Compositional System for Rapid Object Detection Long Zhu and Alan Yuille Department of Statistics University of California at Los Angeles Los Angeles, CA 90095 {lzhu,yuille}@stat.ucla.edu
Selection of Scale-Invariant Parts for Object Class Recognition
 Selection of Scale-Invariant Parts for Object Class Recognition Gy. Dorkó and C. Schmid INRIA Rhône-Alpes, GRAVIR-CNRS 655, av. de l Europe, 3833 Montbonnot, France fdorko,schmidg@inrialpes.fr Abstract
Selection of Scale-Invariant Parts for Object Class Recognition Gy. Dorkó and C. Schmid INRIA Rhône-Alpes, GRAVIR-CNRS 655, av. de l Europe, 3833 Montbonnot, France fdorko,schmidg@inrialpes.fr Abstract
Applying Catastrophe Theory to Image Segmentation
 Applying Catastrophe Theory to Image Segmentation Mohamad Raad, Majd Ghareeb, Ali Bazzi Department of computer and communications engineering Lebanese International University Beirut, Lebanon Abstract
Applying Catastrophe Theory to Image Segmentation Mohamad Raad, Majd Ghareeb, Ali Bazzi Department of computer and communications engineering Lebanese International University Beirut, Lebanon Abstract
DIGITAL IMAGE PROCESSING
 The image part with relationship ID rid2 was not found in the file. DIGITAL IMAGE PROCESSING Lecture 6 Wavelets (cont), Lines and edges Tammy Riklin Raviv Electrical and Computer Engineering Ben-Gurion
The image part with relationship ID rid2 was not found in the file. DIGITAL IMAGE PROCESSING Lecture 6 Wavelets (cont), Lines and edges Tammy Riklin Raviv Electrical and Computer Engineering Ben-Gurion
Local Image Features
 Local Image Features Computer Vision CS 143, Brown Read Szeliski 4.1 James Hays Acknowledgment: Many slides from Derek Hoiem and Grauman&Leibe 2008 AAAI Tutorial This section: correspondence and alignment
Local Image Features Computer Vision CS 143, Brown Read Szeliski 4.1 James Hays Acknowledgment: Many slides from Derek Hoiem and Grauman&Leibe 2008 AAAI Tutorial This section: correspondence and alignment
Digital Image Processing Lecture 7. Segmentation and labeling of objects. Methods for segmentation. Labeling, 2 different algorithms
 Digital Image Processing Lecture 7 p. Segmentation and labeling of objects p. Segmentation and labeling Region growing Region splitting and merging Labeling Watersheds MSER (extra, optional) More morphological
Digital Image Processing Lecture 7 p. Segmentation and labeling of objects p. Segmentation and labeling Region growing Region splitting and merging Labeling Watersheds MSER (extra, optional) More morphological
Edge and Texture. CS 554 Computer Vision Pinar Duygulu Bilkent University
 Edge and Texture CS 554 Computer Vision Pinar Duygulu Bilkent University Filters for features Previously, thinking of filtering as a way to remove or reduce noise Now, consider how filters will allow us
Edge and Texture CS 554 Computer Vision Pinar Duygulu Bilkent University Filters for features Previously, thinking of filtering as a way to remove or reduce noise Now, consider how filters will allow us
Using the Kolmogorov-Smirnov Test for Image Segmentation
 Using the Kolmogorov-Smirnov Test for Image Segmentation Yong Jae Lee CS395T Computational Statistics Final Project Report May 6th, 2009 I. INTRODUCTION Image segmentation is a fundamental task in computer
Using the Kolmogorov-Smirnov Test for Image Segmentation Yong Jae Lee CS395T Computational Statistics Final Project Report May 6th, 2009 I. INTRODUCTION Image segmentation is a fundamental task in computer
Edge detection. Winter in Kraków photographed by Marcin Ryczek
 Edge detection Winter in Kraków photographed by Marcin Ryczek Edge detection Goal: Identify sudden changes (discontinuities) in an image Intuitively, most semantic and shape information from the image
Edge detection Winter in Kraków photographed by Marcin Ryczek Edge detection Goal: Identify sudden changes (discontinuities) in an image Intuitively, most semantic and shape information from the image
Analysis of Image and Video Using Color, Texture and Shape Features for Object Identification
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 16, Issue 6, Ver. VI (Nov Dec. 2014), PP 29-33 Analysis of Image and Video Using Color, Texture and Shape Features
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 16, Issue 6, Ver. VI (Nov Dec. 2014), PP 29-33 Analysis of Image and Video Using Color, Texture and Shape Features
CS 2770: Computer Vision. Edges and Segments. Prof. Adriana Kovashka University of Pittsburgh February 21, 2017
 CS 2770: Computer Vision Edges and Segments Prof. Adriana Kovashka University of Pittsburgh February 21, 2017 Edges vs Segments Figure adapted from J. Hays Edges vs Segments Edges More low-level Don t
CS 2770: Computer Vision Edges and Segments Prof. Adriana Kovashka University of Pittsburgh February 21, 2017 Edges vs Segments Figure adapted from J. Hays Edges vs Segments Edges More low-level Don t
TRANSPARENT OBJECT DETECTION USING REGIONS WITH CONVOLUTIONAL NEURAL NETWORK
 TRANSPARENT OBJECT DETECTION USING REGIONS WITH CONVOLUTIONAL NEURAL NETWORK 1 Po-Jen Lai ( 賴柏任 ), 2 Chiou-Shann Fuh ( 傅楸善 ) 1 Dept. of Electrical Engineering, National Taiwan University, Taiwan 2 Dept.
TRANSPARENT OBJECT DETECTION USING REGIONS WITH CONVOLUTIONAL NEURAL NETWORK 1 Po-Jen Lai ( 賴柏任 ), 2 Chiou-Shann Fuh ( 傅楸善 ) 1 Dept. of Electrical Engineering, National Taiwan University, Taiwan 2 Dept.
Patch Descriptors. CSE 455 Linda Shapiro
 Patch Descriptors CSE 455 Linda Shapiro How can we find corresponding points? How can we find correspondences? How do we describe an image patch? How do we describe an image patch? Patches with similar
Patch Descriptors CSE 455 Linda Shapiro How can we find corresponding points? How can we find correspondences? How do we describe an image patch? How do we describe an image patch? Patches with similar
Deformable Part Models
 CS 1674: Intro to Computer Vision Deformable Part Models Prof. Adriana Kovashka University of Pittsburgh November 9, 2016 Today: Object category detection Window-based approaches: Last time: Viola-Jones
CS 1674: Intro to Computer Vision Deformable Part Models Prof. Adriana Kovashka University of Pittsburgh November 9, 2016 Today: Object category detection Window-based approaches: Last time: Viola-Jones
Shape recognition with edge-based features
 Shape recognition with edge-based features K. Mikolajczyk A. Zisserman C. Schmid Dept. of Engineering Science Dept. of Engineering Science INRIA Rhône-Alpes Oxford, OX1 3PJ Oxford, OX1 3PJ 38330 Montbonnot
Shape recognition with edge-based features K. Mikolajczyk A. Zisserman C. Schmid Dept. of Engineering Science Dept. of Engineering Science INRIA Rhône-Alpes Oxford, OX1 3PJ Oxford, OX1 3PJ 38330 Montbonnot
CS334: Digital Imaging and Multimedia Edges and Contours. Ahmed Elgammal Dept. of Computer Science Rutgers University
 CS334: Digital Imaging and Multimedia Edges and Contours Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines What makes an edge? Gradient-based edge detection Edge Operators From Edges
CS334: Digital Imaging and Multimedia Edges and Contours Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines What makes an edge? Gradient-based edge detection Edge Operators From Edges
Large-Scale Traffic Sign Recognition based on Local Features and Color Segmentation
 Large-Scale Traffic Sign Recognition based on Local Features and Color Segmentation M. Blauth, E. Kraft, F. Hirschenberger, M. Böhm Fraunhofer Institute for Industrial Mathematics, Fraunhofer-Platz 1,
Large-Scale Traffic Sign Recognition based on Local Features and Color Segmentation M. Blauth, E. Kraft, F. Hirschenberger, M. Böhm Fraunhofer Institute for Industrial Mathematics, Fraunhofer-Platz 1,
Ulrik Söderström 16 Feb Image Processing. Segmentation
 Ulrik Söderström ulrik.soderstrom@tfe.umu.se 16 Feb 2011 Image Processing Segmentation What is Image Segmentation? To be able to extract information from an image it is common to subdivide it into background
Ulrik Söderström ulrik.soderstrom@tfe.umu.se 16 Feb 2011 Image Processing Segmentation What is Image Segmentation? To be able to extract information from an image it is common to subdivide it into background
Detection of a Single Hand Shape in the Foreground of Still Images
 CS229 Project Final Report Detection of a Single Hand Shape in the Foreground of Still Images Toan Tran (dtoan@stanford.edu) 1. Introduction This paper is about an image detection system that can detect
CS229 Project Final Report Detection of a Single Hand Shape in the Foreground of Still Images Toan Tran (dtoan@stanford.edu) 1. Introduction This paper is about an image detection system that can detect
Object Detection with Partial Occlusion Based on a Deformable Parts-Based Model
 Object Detection with Partial Occlusion Based on a Deformable Parts-Based Model Johnson Hsieh (johnsonhsieh@gmail.com), Alexander Chia (alexchia@stanford.edu) Abstract -- Object occlusion presents a major
Object Detection with Partial Occlusion Based on a Deformable Parts-Based Model Johnson Hsieh (johnsonhsieh@gmail.com), Alexander Chia (alexchia@stanford.edu) Abstract -- Object occlusion presents a major
Edge Detection CSC 767
 Edge Detection CSC 767 Edge detection Goal: Identify sudden changes (discontinuities) in an image Most semantic and shape information from the image can be encoded in the edges More compact than pixels
Edge Detection CSC 767 Edge detection Goal: Identify sudden changes (discontinuities) in an image Most semantic and shape information from the image can be encoded in the edges More compact than pixels
Figure-Ground Segmentation Techniques
 Figure-Ground Segmentation Techniques Snehal P. Ambulkar 1, Nikhil S. Sakhare 2 1 2 nd Year Student, Master of Technology, Computer Science & Engineering, Rajiv Gandhi College of Engineering & Research,
Figure-Ground Segmentation Techniques Snehal P. Ambulkar 1, Nikhil S. Sakhare 2 1 2 nd Year Student, Master of Technology, Computer Science & Engineering, Rajiv Gandhi College of Engineering & Research,
Construction of Precise Local Affine Frames
 Construction of Precise Local Affine Frames Andrej Mikulik, Jiri Matas, Michal Perdoch, Ondrej Chum Center for Machine Perception Czech Technical University in Prague Czech Republic e-mail: mikulik@cmp.felk.cvut.cz
Construction of Precise Local Affine Frames Andrej Mikulik, Jiri Matas, Michal Perdoch, Ondrej Chum Center for Machine Perception Czech Technical University in Prague Czech Republic e-mail: mikulik@cmp.felk.cvut.cz
Hough Regions for Joining Instance Localization and Segmentation
 Hough Regions for Joining Instance Localization and Segmentation Hayko Riemenschneider 1,2, Sabine Sternig 1, Michael Donoser 1, Peter M. Roth 1, and Horst Bischof 1 1 Institute for Computer Graphics and
Hough Regions for Joining Instance Localization and Segmentation Hayko Riemenschneider 1,2, Sabine Sternig 1, Michael Donoser 1, Peter M. Roth 1, and Horst Bischof 1 1 Institute for Computer Graphics and
Computer Vision I. Announcements. Fourier Tansform. Efficient Implementation. Edge and Corner Detection. CSE252A Lecture 13.
 Announcements Edge and Corner Detection HW3 assigned CSE252A Lecture 13 Efficient Implementation Both, the Box filter and the Gaussian filter are separable: First convolve each row of input image I with
Announcements Edge and Corner Detection HW3 assigned CSE252A Lecture 13 Efficient Implementation Both, the Box filter and the Gaussian filter are separable: First convolve each row of input image I with
Learning Class-specific Edges for Object Detection and Segmentation
 Learning Class-specific Edges for Object Detection and Segmentation Mukta Prasad 1, Andrew Zisserman 1, Andrew Fitzgibbon 2, M. Pawan Kumar 3 and P. H. S. Torr 3 http://www.robots.ox.ac.uk/ {mukta,vgg}
Learning Class-specific Edges for Object Detection and Segmentation Mukta Prasad 1, Andrew Zisserman 1, Andrew Fitzgibbon 2, M. Pawan Kumar 3 and P. H. S. Torr 3 http://www.robots.ox.ac.uk/ {mukta,vgg}
IMAGE RETRIEVAL USING VLAD WITH MULTIPLE FEATURES
 IMAGE RETRIEVAL USING VLAD WITH MULTIPLE FEATURES Pin-Syuan Huang, Jing-Yi Tsai, Yu-Fang Wang, and Chun-Yi Tsai Department of Computer Science and Information Engineering, National Taitung University,
IMAGE RETRIEVAL USING VLAD WITH MULTIPLE FEATURES Pin-Syuan Huang, Jing-Yi Tsai, Yu-Fang Wang, and Chun-Yi Tsai Department of Computer Science and Information Engineering, National Taitung University,
2D image segmentation based on spatial coherence
 2D image segmentation based on spatial coherence Václav Hlaváč Czech Technical University in Prague Center for Machine Perception (bridging groups of the) Czech Institute of Informatics, Robotics and Cybernetics
2D image segmentation based on spatial coherence Václav Hlaváč Czech Technical University in Prague Center for Machine Perception (bridging groups of the) Czech Institute of Informatics, Robotics and Cybernetics
A Framework for Multiple Radar and Multiple 2D/3D Camera Fusion
 A Framework for Multiple Radar and Multiple 2D/3D Camera Fusion Marek Schikora 1 and Benedikt Romba 2 1 FGAN-FKIE, Germany 2 Bonn University, Germany schikora@fgan.de, romba@uni-bonn.de Abstract: In this
A Framework for Multiple Radar and Multiple 2D/3D Camera Fusion Marek Schikora 1 and Benedikt Romba 2 1 FGAN-FKIE, Germany 2 Bonn University, Germany schikora@fgan.de, romba@uni-bonn.de Abstract: In this
Computer Vision I. Announcement. Corners. Edges. Numerical Derivatives f(x) Edge and Corner Detection. CSE252A Lecture 11
 Announcement Edge and Corner Detection Slides are posted HW due Friday CSE5A Lecture 11 Edges Corners Edge is Where Change Occurs: 1-D Change is measured by derivative in 1D Numerical Derivatives f(x)
Announcement Edge and Corner Detection Slides are posted HW due Friday CSE5A Lecture 11 Edges Corners Edge is Where Change Occurs: 1-D Change is measured by derivative in 1D Numerical Derivatives f(x)
Beyond Bags of features Spatial information & Shape models
 Beyond Bags of features Spatial information & Shape models Jana Kosecka Many slides adapted from S. Lazebnik, FeiFei Li, Rob Fergus, and Antonio Torralba Detection, recognition (so far )! Bags of features
Beyond Bags of features Spatial information & Shape models Jana Kosecka Many slides adapted from S. Lazebnik, FeiFei Li, Rob Fergus, and Antonio Torralba Detection, recognition (so far )! Bags of features
Spam Filtering Using Visual Features
 Spam Filtering Using Visual Features Sirnam Swetha Computer Science Engineering sirnam.swetha@research.iiit.ac.in Sharvani Chandu Electronics and Communication Engineering sharvani.chandu@students.iiit.ac.in
Spam Filtering Using Visual Features Sirnam Swetha Computer Science Engineering sirnam.swetha@research.iiit.ac.in Sharvani Chandu Electronics and Communication Engineering sharvani.chandu@students.iiit.ac.in
Online Object Tracking with Proposal Selection. Yang Hua Karteek Alahari Cordelia Schmid Inria Grenoble Rhône-Alpes, France
 Online Object Tracking with Proposal Selection Yang Hua Karteek Alahari Cordelia Schmid Inria Grenoble Rhône-Alpes, France Outline 2 Background Our approach Experimental results Summary Background 3 Tracking-by-detection
Online Object Tracking with Proposal Selection Yang Hua Karteek Alahari Cordelia Schmid Inria Grenoble Rhône-Alpes, France Outline 2 Background Our approach Experimental results Summary Background 3 Tracking-by-detection
Edges and Binary Image Analysis. Thurs Jan 26 Kristen Grauman UT Austin. Today. Edge detection and matching
 /25/207 Edges and Binary Image Analysis Thurs Jan 26 Kristen Grauman UT Austin Today Edge detection and matching process the image gradient to find curves/contours comparing contours Binary image analysis
/25/207 Edges and Binary Image Analysis Thurs Jan 26 Kristen Grauman UT Austin Today Edge detection and matching process the image gradient to find curves/contours comparing contours Binary image analysis
Improving Recognition through Object Sub-categorization
 Improving Recognition through Object Sub-categorization Al Mansur and Yoshinori Kuno Graduate School of Science and Engineering, Saitama University, 255 Shimo-Okubo, Sakura-ku, Saitama-shi, Saitama 338-8570,
Improving Recognition through Object Sub-categorization Al Mansur and Yoshinori Kuno Graduate School of Science and Engineering, Saitama University, 255 Shimo-Okubo, Sakura-ku, Saitama-shi, Saitama 338-8570,
AK Computer Vision Feature Point Detectors and Descriptors
 AK Computer Vision Feature Point Detectors and Descriptors 1 Feature Point Detectors and Descriptors: Motivation 2 Step 1: Detect local features should be invariant to scale and rotation, or perspective
AK Computer Vision Feature Point Detectors and Descriptors 1 Feature Point Detectors and Descriptors: Motivation 2 Step 1: Detect local features should be invariant to scale and rotation, or perspective
Edge Detection. CSC320: Introduction to Visual Computing Michael Guerzhoy. René Magritte, Decalcomania. Many slides from Derek Hoiem, Robert Collins
 Edge Detection René Magritte, Decalcomania Many slides from Derek Hoiem, Robert Collins CSC320: Introduction to Visual Computing Michael Guerzhoy Discontinuities in Intensity Source: Robert Collins Origin
Edge Detection René Magritte, Decalcomania Many slides from Derek Hoiem, Robert Collins CSC320: Introduction to Visual Computing Michael Guerzhoy Discontinuities in Intensity Source: Robert Collins Origin
An Evaluation of Volumetric Interest Points
 An Evaluation of Volumetric Interest Points Tsz-Ho YU Oliver WOODFORD Roberto CIPOLLA Machine Intelligence Lab Department of Engineering, University of Cambridge About this project We conducted the first
An Evaluation of Volumetric Interest Points Tsz-Ho YU Oliver WOODFORD Roberto CIPOLLA Machine Intelligence Lab Department of Engineering, University of Cambridge About this project We conducted the first
Video Google: A Text Retrieval Approach to Object Matching in Videos
 Video Google: A Text Retrieval Approach to Object Matching in Videos Josef Sivic, Frederik Schaffalitzky, Andrew Zisserman Visual Geometry Group University of Oxford The vision Enable video, e.g. a feature
Video Google: A Text Retrieval Approach to Object Matching in Videos Josef Sivic, Frederik Schaffalitzky, Andrew Zisserman Visual Geometry Group University of Oxford The vision Enable video, e.g. a feature
Medial Features for Superpixel Segmentation
 Medial Features for Superpixel Segmentation David Engel Luciano Spinello Rudolph Triebel Roland Siegwart Heinrich H. Bülthoff Cristóbal Curio Max Planck Institute for Biological Cybernetics Spemannstr.
Medial Features for Superpixel Segmentation David Engel Luciano Spinello Rudolph Triebel Roland Siegwart Heinrich H. Bülthoff Cristóbal Curio Max Planck Institute for Biological Cybernetics Spemannstr.
Structure Guided Salient Region Detector
 Structure Guided Salient Region Detector Shufei Fan, Frank Ferrie Center for Intelligent Machines McGill University Montréal H3A2A7, Canada Abstract This paper presents a novel method for detection of
Structure Guided Salient Region Detector Shufei Fan, Frank Ferrie Center for Intelligent Machines McGill University Montréal H3A2A7, Canada Abstract This paper presents a novel method for detection of
Previously. Part-based and local feature models for generic object recognition. Bag-of-words model 4/20/2011
 Previously Part-based and local feature models for generic object recognition Wed, April 20 UT-Austin Discriminative classifiers Boosting Nearest neighbors Support vector machines Useful for object recognition
Previously Part-based and local feature models for generic object recognition Wed, April 20 UT-Austin Discriminative classifiers Boosting Nearest neighbors Support vector machines Useful for object recognition
Small Object Segmentation Based on Visual Saliency in Natural Images
 J Inf Process Syst, Vol.9, No.4, pp.592-601, December 2013 http://dx.doi.org/10.3745/jips.2013.9.4.592 pissn 1976-913X eissn 2092-805X Small Object Segmentation Based on Visual Saliency in Natural Images
J Inf Process Syst, Vol.9, No.4, pp.592-601, December 2013 http://dx.doi.org/10.3745/jips.2013.9.4.592 pissn 1976-913X eissn 2092-805X Small Object Segmentation Based on Visual Saliency in Natural Images
FACULTY OF ENGINEERING AND INFORMATION TECHNOLOGY DEPARTMENT OF COMPUTER SCIENCE. Project Plan
 FACULTY OF ENGINEERING AND INFORMATION TECHNOLOGY DEPARTMENT OF COMPUTER SCIENCE Project Plan Structured Object Recognition for Content Based Image Retrieval Supervisors: Dr. Antonio Robles Kelly Dr. Jun
FACULTY OF ENGINEERING AND INFORMATION TECHNOLOGY DEPARTMENT OF COMPUTER SCIENCE Project Plan Structured Object Recognition for Content Based Image Retrieval Supervisors: Dr. Antonio Robles Kelly Dr. Jun
Postprint.
 http://www.diva-portal.org Postprint This is the accepted version of a paper presented at 14th International Conference of the Biometrics Special Interest Group, BIOSIG, Darmstadt, Germany, 9-11 September,
http://www.diva-portal.org Postprint This is the accepted version of a paper presented at 14th International Conference of the Biometrics Special Interest Group, BIOSIG, Darmstadt, Germany, 9-11 September,
Color Image Segmentation
 Color Image Segmentation Yining Deng, B. S. Manjunath and Hyundoo Shin* Department of Electrical and Computer Engineering University of California, Santa Barbara, CA 93106-9560 *Samsung Electronics Inc.
Color Image Segmentation Yining Deng, B. S. Manjunath and Hyundoo Shin* Department of Electrical and Computer Engineering University of California, Santa Barbara, CA 93106-9560 *Samsung Electronics Inc.
A Simplified Texture Gradient Method for Improved Image Segmentation
 A Simplified Texture Gradient Method for Improved Image Segmentation Qi Wang & M. W. Spratling Department of Informatics, King s College London, London, WC2R 2LS qi.1.wang@kcl.ac.uk Michael.Spratling@kcl.ac.uk
A Simplified Texture Gradient Method for Improved Image Segmentation Qi Wang & M. W. Spratling Department of Informatics, King s College London, London, WC2R 2LS qi.1.wang@kcl.ac.uk Michael.Spratling@kcl.ac.uk
Object Recognition Using Junctions
 Object Recognition Using Junctions Bo Wang 1, Xiang Bai 1, Xinggang Wang 1, Wenyu Liu 1, Zhuowen Tu 2 1. Dept. of Electronics and Information Engineering, Huazhong University of Science and Technology,
Object Recognition Using Junctions Bo Wang 1, Xiang Bai 1, Xinggang Wang 1, Wenyu Liu 1, Zhuowen Tu 2 1. Dept. of Electronics and Information Engineering, Huazhong University of Science and Technology,
Three-Dimensional Computer Vision
 \bshiaki Shirai Three-Dimensional Computer Vision With 313 Figures ' Springer-Verlag Berlin Heidelberg New York London Paris Tokyo Table of Contents 1 Introduction 1 1.1 Three-Dimensional Computer Vision
\bshiaki Shirai Three-Dimensional Computer Vision With 313 Figures ' Springer-Verlag Berlin Heidelberg New York London Paris Tokyo Table of Contents 1 Introduction 1 1.1 Three-Dimensional Computer Vision
The most cited papers in Computer Vision
 COMPUTER VISION, PUBLICATION The most cited papers in Computer Vision In Computer Vision, Paper Talk on February 10, 2012 at 11:10 pm by gooly (Li Yang Ku) Although it s not always the case that a paper
COMPUTER VISION, PUBLICATION The most cited papers in Computer Vision In Computer Vision, Paper Talk on February 10, 2012 at 11:10 pm by gooly (Li Yang Ku) Although it s not always the case that a paper
CS534: Introduction to Computer Vision Edges and Contours. Ahmed Elgammal Dept. of Computer Science Rutgers University
 CS534: Introduction to Computer Vision Edges and Contours Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines What makes an edge? Gradient-based edge detection Edge Operators Laplacian
CS534: Introduction to Computer Vision Edges and Contours Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines What makes an edge? Gradient-based edge detection Edge Operators Laplacian
By Suren Manvelyan,
 By Suren Manvelyan, http://www.surenmanvelyan.com/gallery/7116 By Suren Manvelyan, http://www.surenmanvelyan.com/gallery/7116 By Suren Manvelyan, http://www.surenmanvelyan.com/gallery/7116 By Suren Manvelyan,
By Suren Manvelyan, http://www.surenmanvelyan.com/gallery/7116 By Suren Manvelyan, http://www.surenmanvelyan.com/gallery/7116 By Suren Manvelyan, http://www.surenmanvelyan.com/gallery/7116 By Suren Manvelyan,
